Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Related Rants

 Everyone always says the previous developer was crap, sometimes you're right
Everyone always says the previous developer was crap, sometimes you're right So apparently this is an official company in the UK
So apparently this is an official company in the UK
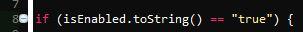
This tuesday I saw a really badly made PHP web application. Two actually. I was giving a time estimate for how long it would take to transfer these applications to our servers. While I was reading the code it became apparent that they had more security holes than Emmental cheese. Most views had obvious SQL-injection vulnerabilities and most probably XSS too. Although I didn't think too look for XSS in the moment. It just puzzled me that this bad code even exists.
But cherry on top was that the password wasn't checked at all. The login form was on the organization's website and was sent to the selected application. But the password wasn't checked in the application. And this was made by a real Finnish software development firm, like what the fuck.
Time to redo the applications I guess. Not like there's anything wrong in that if they pay for it.
rant
bad code
xss
holeseverywhere
such wow
sql injection
wk234