Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
 pajaja17228yNow that's a unique approach that shows thinking outside the box. Too bad it's so stupid.
pajaja17228yNow that's a unique approach that shows thinking outside the box. Too bad it's so stupid. -
That could be fun, cookies can be changed clientside so i hope there is some sanity checks in place.
-
 kurtr124768y@ItsNotMyFault No checks - also has public registration and the db user is admin with full privileges.
kurtr124768y@ItsNotMyFault No checks - also has public registration and the db user is admin with full privileges. -
 lotd76788y@ocab19 don't see it in that picture.
lotd76788y@ocab19 don't see it in that picture.
But yeah, it wouldn't surprise me if the database is connected on root...
Related Rants

 Everyone always says the previous developer was crap, sometimes you're right
Everyone always says the previous developer was crap, sometimes you're right So apparently this is an official company in the UK
So apparently this is an official company in the UK
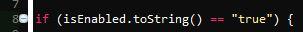
If you thought your legacy code was bad, this is what I'm dealing with. The below SQL is stored in a cookie on login and executed to on every further request to determine the user / privileges.
undefined
legacy code
wk58
sql injection
bad cookie