Ranter
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Comments
-
You can start by talking about nmap, you know what it does
You can configure the services such that it's not susceptible to banner grabbing and that unwanted services are disabled -
Make sure your dns servers are configured properly so zone transfers could be avoided
-
 xalys15887y@justasithlord what risk do you think is imposed if you don’t allow zone transfers but do allow AXFR from :: ?
xalys15887y@justasithlord what risk do you think is imposed if you don’t allow zone transfers but do allow AXFR from :: ? -
@xalys aren't zone transfers and AXFR queries the same? I think they're the same
So if you allow it to be done from everywhere then that'd be like giving away your internal network structure away to whoever requests for it
Related Rants
-
 JannikHv2
JannikHv2 When you realize that you're googling an error message you've implemented yourself
When you realize that you're googling an error message you've implemented yourself -
 inf3cti0n955
inf3cti0n955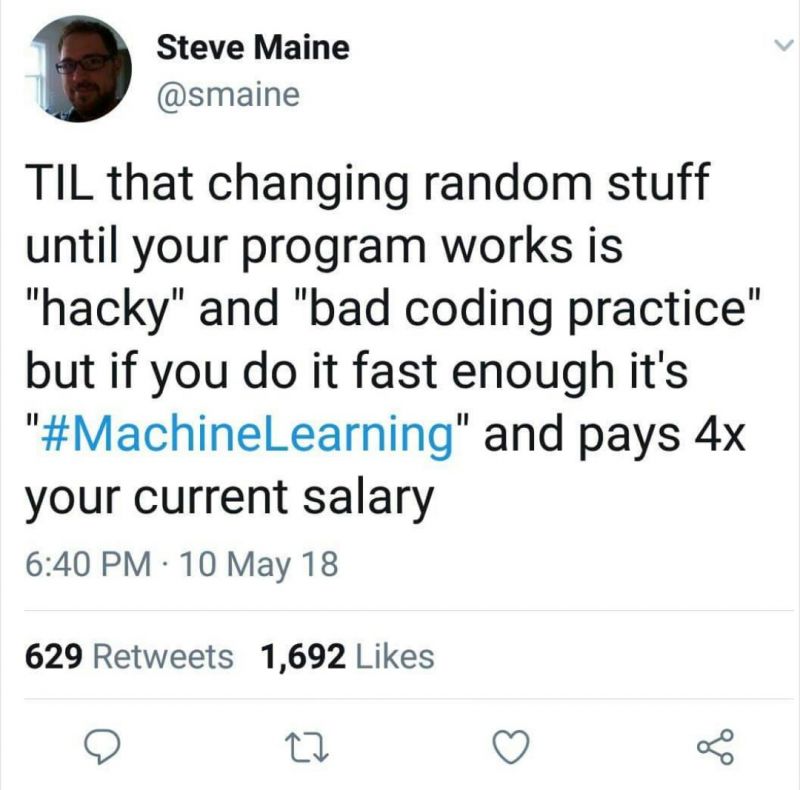 That's exactly how I started, am I a Machine!? ... learning Machine Learning
That's exactly how I started, am I a Machine!? ... learning Machine Learning -
 PieInOblivion5Teacher: "Whats that key thingy?" Class: "You mean the keyboard?" Teacher: "Yes, that one!" I shit you not, s...
PieInOblivion5Teacher: "Whats that key thingy?" Class: "You mean the keyboard?" Teacher: "Yes, that one!" I shit you not, s...

A bit confused !
Must prepare an article about network pentest and defense .
Since its a very wide topic and I've been told not to just mention tools , I'm confused about categorizing these tests !
Also the footprinting stage is not likely to have any defense !(no attack is lunched yet :) )
So... Any idea?
rant
article
network pentest
confused