Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Related Rants

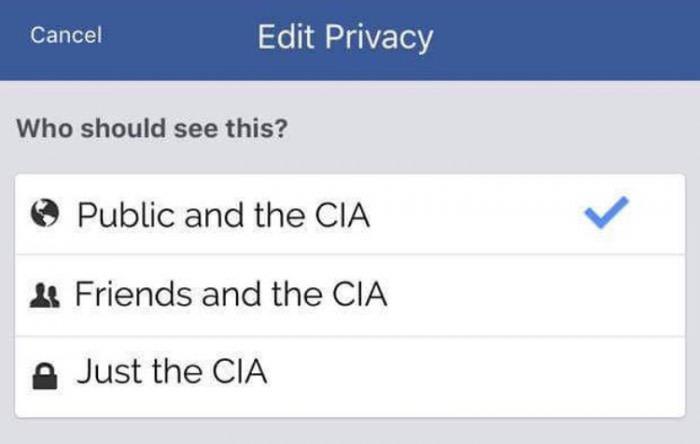 Privacy is a legend
Privacy is a legend Did you say security?
Did you say security?
OpenSSH has announced plans to drop support for it's SHA-1 authentication method.
According to the report of ZDNet : The OpenSSH team currently considered SHA-1 hashing algorithm insecure (broken in real-world attack in February 2017 when Google cryptographers disclosed SHAttered attack which could make two different files appear as they had the same SHA-1 file signature). The OpenSSH project will be disabling the 'ssh-rsa' (which uses SHA-1) mode by default in a future release, they also plan to enable the 'UpdateHostKeys' feature by default which allow servers to automatically migrate from the old 'ssh-rsa' mode to better authentication algorithms.
random
developers
privacy
security