Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "table-of-contents"
-
https://git.kernel.org/…/ke…/... sure some of you are working on the patches already, if you are then lets connect cause, I am an ardent researcher for the same as of now.
So here it goes:
As soon as kernel page table isolation(KPTI) bug will be out of embargo, Whatsapp and FB will be flooded with over-night kernel "shikhuritee" experts who will share shitty advices non-stop.
1. The bug under embargo is a side channel attack, which exploits the fact that Intel chips come with speculative execution without proper isolation between user pages and kernel pages. Therefore, with careful scheduling and timing attack will reveal some information from kernel pages, while the code is running in user mode.
In easy terms, if you have a VPS, another person with VPS on same physical server may read memory being used by your VPS, which will result in unwanted data leakage. To make the matter worse, a malicious JS from innocent looking webpage might be (might be, because JS does not provide language constructs for such fine grained control; atleast none that I know as of now) able to read kernel pages, and pawn you real hard, real bad.
2. The bug comes from too much reliance on Tomasulo's algorithm for out-of-order instruction scheduling. It is not yet clear whether the bug can be fixed with a microcode update (and if not, Intel has to fix this in silicon itself). As far as I can dig, there is nothing that hints that this bug is fixable in microcode, which makes the matter much worse. Also according to my understanding a microcode update will be too trivial to fix this kind of a hardware bug.
3. A software-only remedy is possible, and that is being implemented by all major OSs (including our lovely Linux) in kernel space. The patch forces Translation Lookaside Buffer to flush if a context switch happens during a syscall (this is what I understand as of now). The benchmarks are suggesting that slowdown will be somewhere between 5%(best case)-30%(worst case).
4. Regarding point 3, syscalls don't matter much. Only thing that matters is how many times syscalls are called. For example, if you are using read() or write() on 8MB buffers, you won't have too much slowdown; but if you are calling same syscalls once per byte, a heavy performance penalty is guaranteed. All processes are which are I/O heavy are going to suffer (hostings and databases are two common examples).
5. The patch can be disabled in Linux by passing argument to kernel during boot; however it is not advised for pretty much obvious reasons.
6. For gamers: this is not going to affect games (because those are not I/O heavy)
Meltdown: "Meltdown" targeted on desktop chips can read kernel memory from L1D cache, Intel is only affected with this variant. Works on only Intel.
Spectre: Spectre is a hardware vulnerability with implementations of branch prediction that affects modern microprocessors with speculative execution, by allowing malicious processes access to the contents of other programs mapped memory. Works on all chips including Intel/ARM/AMD.
For updates refer the kernel tree: https://git.kernel.org/…/ke…/...
For further details and more chit-chats refer: https://lwn.net/SubscriberLink/...
~Cheers~
(Originally written by Adhokshaj Mishra, edited by me. ) 22
22 -
After a long time just reading your posts, here's my first post:
Just for clarification: I'm studying electrical engineering in Germany. During your time at university, you have to work half a year as a intern to get some practical experience. So I'm in a position where I mainly have to say "yes" to work that is given to me. Also I'm working with a lot of PLC programmers, so I'm nearly the only one who programs non-PLC stuff at the department.
But now it's time for my rant (and also my most satisfying optimization ever). In the job interview for the internship, my task at the company was described as C# programmer. I only programmed C and Python before, but C# looked interesting and so I learned C# from ground up in the summer before the internship. I quite liked it and I was really happy on my first day of work. Then I was greeted with this message: "I know you are hired as C# programmer, but could you please look into this VBA program, it takes 55 seconds until it finishes its task and that's to slow". So I (midly angry because I had to do VBA and not C#) started the program and it was really horribly slow (it just created a table with certain contents from a very big imported symbol file). I then opened up the source code and immideately saw bad code. The guy who wrote it basically just clicked on the macro recording button and used the recorded mouse clicks in the source code. The code was like: Click on cell A1 -> copy cell A1 -> move to sheet XY -> click on cell A2 -> paste copied stuff and so on... I never 'programmed' in VBA before, so I used my knowledge of 'real' programming languages to do this task. After using some arrays and for-loops, which did not iterate over all the 1.000.000 unused cells after the last used one, the program took only 3 seconds after it finished the new table! Everybody was quite impressed, which led to much more VBA optimization... That was clearly not my goal haha :)9 -
Long rant ahead.. 5k characters pretty much completely used. So feel free to have another cup of coffee and have a seat 🙂
So.. a while back this flash drive was stolen from me, right. Well it turns out that other than me, the other guy in that incident also got to the police 😃
Now, let me explain the smiley face. At the time of the incident I was completely at fault. I had no real reason to throw a punch at this guy and my only "excuse" would be that I was drunk as fuck - I've never drank so much as I did that day. Needless to say, not a very good excuse and I don't treat it as such.
But that guy and whoever else it was that he was with, that was the guy (or at least part of the group that did) that stole that flash drive from me.
Context: https://devrant.com/rants/2049733 and https://devrant.com/rants/2088970
So that's great! I thought that I'd lost this flash drive and most importantly the data on it forever. But just this Friday evening as I was meeting with my friend to buy some illicit electronics (high voltage, low frequency arc generators if you catch my drift), a policeman came along and told me about that other guy filing a report as well, with apparently much of the blame now lying on his side due to him having punched me right into the hospital.
So I told the cop, well most of the blame is on me really, I shouldn't have started that fight to begin with, and for that matter not have drunk that much, yada yada yada.. anyway he walked away (good grief, as I was having that friend on visit to purchase those electronics at that exact time!) and he said that this case could just be classified then. Maybe just come along next week to the police office to file a proper explanation but maybe even that won't be needed.
So yeah, great. But for me there's more in it of course - that other guy knows more about that flash drive and the data on it that I care about. So I figured, let's go to the police office and arrange an appointment with this guy. And I got thinking about the technicalities for if I see that drive back and want to recover its data.
So I've got 2 phones, 1 rooted but reliant on the other one that's unrooted for a data connection to my home (because Android Q, and no bootable TWRP available for it yet). And theoretically a laptop that I can put Arch on it no problem but its display backlight is cooked. So if I want to bring that one I'd have to rely on a display from them. Good luck getting that done. No option. And then there's a flash drive that I can bake up with a portable Arch install that I can sideload from one of their machines but on that.. even more so - good luck getting that done. So my phones are my only option.
Just to be clear, the technical challenge is to read that flash drive and get as much data off of it as possible. The drive is 32GB large and has about 16GB used. So I'll need at least that much on whatever I decide to store a copy on, assuming unchanged contents (unlikely). My Nexus 6P with a VPN profile to connect to my home network has 32GB of storage. So theoretically I could use dd and pipe it to gzip to compress the zeroes. That'd give me a resulting file that's close to the actual usage on the flash drive in size. But just in case.. my OnePlus 6T has 256GB of storage but it's got no root access.. so I don't have block access to an attached flash drive from it. Worst case I'd have to open a WiFi hotspot to it and get an sshd going for the Nexus to connect to.
And there we have it! A large storage device, no root access, that nonetheless can make use of something else that doesn't have the storage but satisfies the other requirements.
And then we have things like parted to read out the partition table (and if unchanged, cryptsetup to read out LUKS). Now, I don't know if Termux has these and frankly I don't care. What I need for that is a chroot. But I can't just install Arch x86_64 on a flash drive and plug it into my phone. Linux Deploy to the rescue! 😁
It can make chrooted installations of common distributions on arm64, and it comes extremely close to actual Linux. With some Linux magic I could make that able to read the block device from Android and do all the required sorcery with it. Just a USB-C to 3x USB-A hub required (which I have), with the target flash drive and one to store my chroot on, connected to my Nexus. And fixed!
Let's see if I can get that flash drive back!
P.S.: if you're into electronics and worried about getting stuff like this stolen, customize it. I happen to know one particular property of that flash drive that I can use for verification, although it wasn't explicitly customized. But for instance in that flash drive there was a decorative LED. Those are current limited by a resistor. Factory default can be say 200 ohm - replace it with one with a higher value. That way you can without any doubt verify it to be yours. Along with other extra security additions, this is one of the things I'll be adding to my "keychain v2".10 -
What a new years start..
"Kernel memory leaking Intel processor design flaw forces Linux, Windows redesign"
"Crucially, these updates to both Linux and Windows will incur a performance hit on Intel products. The effects are still being benchmarked, however we're looking at a ballpark figure of five to 30 per cent slow down"
"It is understood the bug is present in modern Intel processors produced in the past decade. It allows normal user programs – from database applications to JavaScript in web browsers – to discern to some extent the layout or contents of protected kernel memory areas."
"The fix is to separate the kernel's memory completely from user processes using what's called Kernel Page Table Isolation, or KPTI. At one point, Forcefully Unmap Complete Kernel With Interrupt Trampolines, aka FUCKWIT, was mulled by the Linux kernel team, giving you an idea of how annoying this has been for the developers."
>How can this security hole be abused?
"At worst, the hole could be abused by programs and logged-in users to read the contents of the kernel's memory."
https://theregister.co.uk/2018/01/... 22
22 -
tl;dr:
The Debian 10 live disc and installer say: Heavens me, just look at the time! I’m late for my <segmentation fault
—————
tl:
The Debian 10 live cd and its new “calamares” installer are both complete crap. I’ve never had any issues with installing Debian prior to this, save with getting WiFi to work (as expected). But this version? Ugh. Here are the things I’ve run into:
Unknown root password; easy enough to get around as there is no user password; still annoying after the 10th time.
Also, the login screen doesn’t work off-disc because it won’t accept a blank password, so don’t idle or you’ll get locked out.
The lock screen is overzealous and hard-locks the computer after awhile; not even the magic kernel keys work!
The live disc doesn’t have many standard utilities, or a graphical partition editor. Thankfully I’m comfortable with fdisk.
The graphical installer (calamares) randomly segfaults, even from innocuous things like clicking [change partition] when you don’t have a partition selected. Derp.
It also randomly segfaults while writing partitions to disk — usually on the second partition.
It strangely seems less likely to segfault if the partitions are already there, even if it needs to “reformat” (recreate) them.
It also defaults to using MBR instead of GPT for the partition table, despite the tooltip telling you that MBR is deprecated and limited, and that GPT is recommended for new systems. You cannot change this without doing the partitions manually.
If you do the partitions manually and it can’t figure out where to install things, it just crashes. This is great because you can’t tell it where to install things, and specifying mount points like /boot, /, and /home don’t seem to be enough.
It also tries installing 32bit grub instead of 64bit, causing the grub installer to fail.
If you tell it to install grub on /boot, it complains when that partition isn’t encrypted — fair — but if you tell it to encrypt /boot like it wants you to, it then tries installing grub on the encrypted partition it just created, apparently without decrypting it, so that obviously fails — specific error: cannot read file system.
On the rare chance that everything else goes correctly, the install process can still segfault.
The log does include entries for errors, but doesn’t include an error message. Literally: “ERROR: Installation failed:” and the log ends. Helpful!
If the installer doesn’t segfault and the install process manages to complete, the resulting install might not even boot, even when installed without any drive encryption. Why? My guess is it never bothered to install Grub, or put it in the wrong place, or didn’t mark it as bootable, or who knows what.
Even when using the live disc that includes non-free firmware (including Ath9k) it still cannot detect my wlan card (that uses Ath9k).
I’ve attempted to install thirty plus times now, and only managed to get a working install once — where I neglected to include the Ath9k firmware.
I’m now trying the cli-only installer option instead of the live session; it seems to behave at least. I’m just terrified that the resulting install will be just as unstable as the live session.
All of this to copy the contents of my encrypted disks over so I can use them on a different system. =/
I haven’t decided which I’m going with next, but likely Arch, Void, or Gentoo. I’d go with Qubes if I had more time to experiment.
But in all seriousness, the Debian devs need some serious help. I would be embarrassed if I released this quality of hot garbage.
(This same system ran both Debian 8 and 9 flawlessly for years)15 -
My pm requested me to estimate few tasks on a new project(single page app), the problem was that he was creator of these tasks, so we ended up with
- Create back button
- Create next button
- Create table with contents
... etc
As I prefer to take things literally I estimated each task as they literally should (5 min for adding buttons etc). So all tasks together were estimated for about 5h, while whole project was estimated for 100MD. After few talks and discussions we ended up with:
- Create back button
- Create back button logic
- Create next button
- Create next button logic
etc1 -
WooCommerce is shit
Just try to find anything in the documentation on their retarded website and you will get what I am talking about.
A billion of unstructured links. With absolutely no sidebar or table of contents.
IMPOSSIBLE to find any fuck there.
It is far easier to build an e-store from scratch, than to customize their ugly monster.
Now look Laravel or PHPunit documentation to compare how it should be.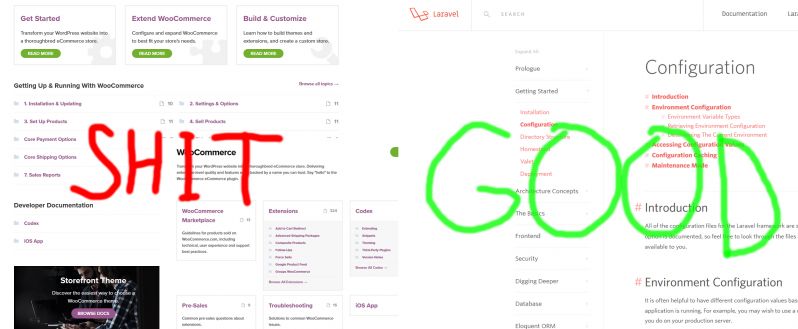
-
As you problably know, Gmail sends mails to you when you create a new gmail account. These mails are about what you can do gmail etc.
But they send 3 mails! Why? Wouldnt it just be easier to send one and have a table of contents.
Sending one mail containing all info also takes less space in the list of mails you get.
Stupid google 8
8 -
[rant]
From the bottom of my heart I swear the thing that frustrates me the most in this industry is over complicating simple things. Making simple ideas overly convoluted makes me cry.
I mean why have a dedicated Windows server, that you login to via Windows Remote desktop, just to edit a Word document in a bespoke program that is running running Microsoft Word inside it anyway. Why not just just Word? Why spend a year developing such a system for a problem that simply doesn'y exist.
I asked what benefit this has over me just editing a Word file myself on my laptop. In short, their answer was none.
The other apparent benefit to the system was the ability to jump to specific parts of the document. Well after showing them how to do a table of contents, they saw no need for their existing system.
I'm amazed sometimes how simple ides get discussed to death, unnecessary mammoth systems get built, that ultimately solve a problem that does not exist.
[/rant] 3
3 -
Is there any extension for visual studio code that allows markdown to be exported as proper linked TOC PDF? I have tried now atleast 5 different combinations, pandoc, convert markdown etc. and they all produce either really non matching content (pandoc) or don't link the table of contents right. (but atleast show the content 1:1 of what the preview is..)2
-
I’ve developed a love/hate relationship with wkhtmltopdf.
I’ve also apparently lost the ability to sleep properly.
These may be related things.11 -
Way too long story short: Needed to figure out how to use jQuery to update a table that had no classes or IDs to help you tell what's inside it. Worked out a looping structure to read the contents of the cell with the dependent data in each row, and then update the cell that needed changing depending on the value of the first cell.
Minified the solution and dropped it into the console. Worked exactly right on the first try. -
I’m fucked off tonight.
I’m having to pull a very complex data set out of dB and loop through results in a table.
Easy, done, but one of the Columns I’m pulling out needs further broken down. It’s a comma delimited string.
I can’t get the data, and inside the same loop explode that string so that the contents can be handled independently.
Raging! I have foreach loops inside foreach loops and arrays inside objects that are inside arrays.
I’m going to bed furious.2
