Details
-
AboutI like trolling people using \u202e :)
-
SkillsJava, C++
-
LocationGermany
Joined devRant on 3/17/2017
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
-
Does someone have an idea how to use synproxy and nat (dnat and snat) together on one machine? It's basically a router which should also act as a ddos filter, but when I install synproxy, the natting doesn't work anymore...
I can't really find something on the internet so help would be appreciated.
Thanks in advance1 -
Hey there!
If some of you could maybe answer me a question about iptables, that would be great. Link to the full question below.
To summarize it, I have a sub-chain which matches packets using hashlimit and if this traffic is below 100 pps from that IP, it returns back to the INPUT chain, else the packet is dropped.
There is only one thing I don't get, the rule in the INPUT chain which jumps to my sub-chain matches a lot more packets then all my sub-chain rules together! Where do these packets go? It's like they don't match anything after that jump.
I asked this question on serverfault so here goes the link: https://serverfault.com/questions/...4 -
I've got a Linux Server running with 2 NVMe disks in RAID 1 configuration using mdadm. But if I want to create a big file, say 4GB, the whole system starts to hang.
I found out it's because of the journaling process which gives the CPU a long IOWAIT.
My problem is, I want to unzip a huge file, but this results in an immense server hang. Is there any way to do this without the server hang?
I unzip it inside of a docker container, if that is of any help.7 -
Tell me, which letter do you see:🇺
And which do you see here:🇻
And then tell me on which OS/browser you are viewing this.
(on my phone, Android 8, they seem to be switched, first should be U and second V)31 -
Well that's indeed kinda funny
But I'd really like to know if it all had to do with Google Cloud Networking, because they had a failure of their systems in us-east1 for 25 hours and it fits the time in some way (https://status.cloud.google.com/inc...).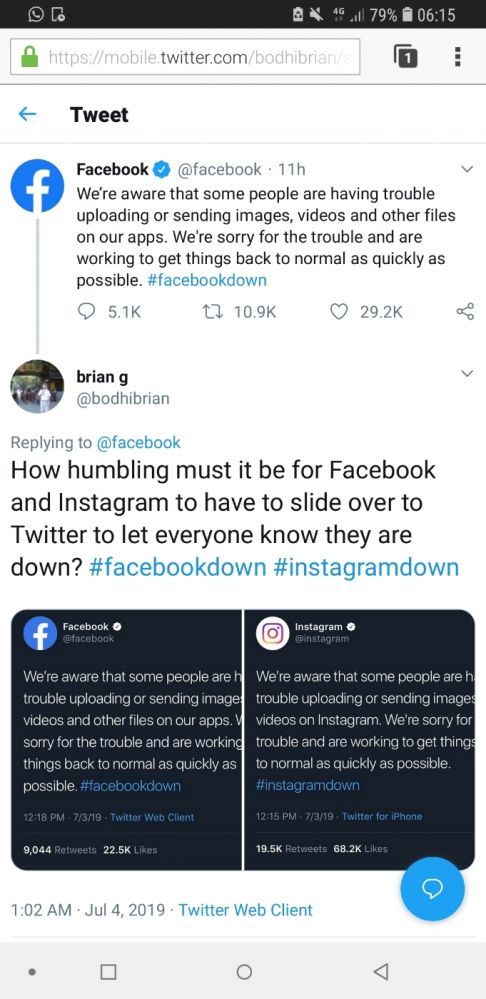 2
2 -
Today was fucking awesome!
I always wanted to do a project in C++ since I've been more of a Java guy for years now.
And today, I finally wrote a full console program in C++! (For windows, it's a .exe)
The purpose of that program is to show if a file has a file lock on it (because of copying for example).
It started as simple as that, but got complicated quickly:
- It needs colors! So I added colors.
- Just a single file? Boring. I need wildcards, so I can put a * for anything in the file name! Jup.
- Just one directory? Boring. I need a recursive directory walk! Got it.
- But wait! There has to be an option to switch between recursive and wildcard/single mode! So I checked if the first argument equals "-r"! Hacky but works.
- Oh uh... that spams a lot now! The purpose was to show locked files, so I need another argument to specify that I only want to see locked files! Damn now it get's hard... I need a Linux-like command line argument parser (this -h and -s "hello" stuff). So I took the opportunity to write one myself! Done.
- Refactoring everything to use my new fancy parser...
- Adding more and more arguments, just because I can:
- "-d" hides "access denied" messages
- "-l" shows only locked files
- "-r" activates recursive directory walk
- "-f" formats everything nicely, basically printf("%-150.150s | %s", filename, locked); a maximum width which get's truncated if too long so everything lines up nicely
- "-h" which of course displays the help page
- "-w file" watches a file, if the file is locked it will refresh every 500ms, if it's still locked nothing happens, if it's unlocked, the program prints "unlocked" in green and exits. And yes, it does have a rotating line (something like this: "-" "\" "|" "/" "-" and so forth...)
That project was just awesome to make. I learn languages fastest if I just do a big project in them, and today, I really learned a lot.
Thank you for reading all this!3 -
There is this thing called the Pulfrich effect (https://youtu.be/Q-v4LsbFc5c a Tom Scott video about this).
Since I have 3 monitors, I decided to write a small C++ program which copies the image from the first monitor to the second and, with 5ms delay, also to the third.
That way I can sit down like 5 meters away and squint a bit to make both copies overlap. This creates a 3D effect for about half of the time of any moving video.
If you watched the video at the top you should know why, if the right image comes later the background has to move as in the video, and vice-versa.
Just some random thing that came to my mind and it's actually awesome! -
Got new hardware for my minecraft server!
Intel I7-8068K 6 Cores 12 Threads 5.1GHz
64GB DDR4 RAM 2666MHz
2x 512GB NVMe (RAID 1)
First time I have ever used a 5GHz CPU I am so excited!12 -
I just found a new WhatsApp Crash Exploit. Full denial of service right there. An attacker could send a message to a Chat (be it private Chat or group Chat) and everyone who receives the message has no chance of starting WhatsApp again. It crashes and won't restart.
Tested on latest version on Samsung Galaxy S6 and S8. Don't know if it works on other versions but I am pretty sure it does. (It's midnight here, noone online to test)
The fun thing is, I knew this Bug for a long time but when I last tested it, nothing happened. Which means this Crash is only possible because someone at WhatsApp programmed a new Feature...19 -
Since I love playing music on my piano, and because I love programming, I created this:
A program which uses YIN (some kind of FFT algorithm) to create this audio spectrum. It can read from any audio source, be it microphone or the computers audio output. There are 3 lines in the graph at the bottom:
Both magenta lines, both are movable, allow you to just select a part of the audio spectrum to show, which is very useful if you just want to get the chords out of a song, or just the notes.
The cyan line can also be moved, it tells the program the lower limit to calculate the actual notes/chords from the frequency bars (which are calculated by the FFT algorithm).
In the top right of the spectrum is, in magenta color, one single note. It shows the currently loudest frequency as a note.
In the top right corner is a simple image of a one-octave piano. Every note over the cyan line will be shown on this piano. This is very useful for chords.
Since compression will fuck this image up, here is a link: https://i.gyazo.com/fbbee76faecbac3...
What do you think about it? I fucking love it. 2
2 -
I have a Server with the IP address
x.x.233.61
For clarification, this is the public IP, it does not start with 192 or 172 or whatever local IP.
When I pinged 8.8.8.8 it said
From x.x.1.1: Destination Net Unreachable
After asking my Hoster what this IP address was, he said it would be the router.
In a traceroute to 8.8.8.8 this IP never appears.
Since these ping problems are now fixed, this IP never appears anywhere. If it really is the Server racks router, is there any way to get that IP in Linux?4 -
In my school, eleventh grade (so nearly "Abitur", A levels), we got the task to create a program which will be running on every computer here which should replace the Classbook (like a book where homework and lessons and stuff is written down).
Now, the class before mine already did a part of that, a program to share who is ill/not at school, with a mark whether it is excused or not.
So far so good. They all seemed not that bad when they were presenting it to us. Then, the first thing: they didn't know what git is. Well, okay I thought.
Next, there was this password field to access the program. One of them entered the password and clicked enter. That seemed suspiciously fast for an actual secure login. So fast, the password could have been in the Code...
Yesterday I copied that program and put it into a decompiler.
And... I was right.
There were the login credentials in plain text. Also, haven't thought of it but, IP address + username + password + database name were there in plain text, too.
Guess I am going to rewrite this program down to the core2 -
Yesterday someone from my class asked me if I could hack a netflix account for him because his one-month trial will be over soon.
I have nothing more to say.8 -
Follow-up to my previous story: https://devrant.com/rants/1969484/...
If this seems to long to read, skip to the parts that interest you.
~ Background ~
Maybe you know TeamSpeak, it's basically a program to talk with other people on servers. In TeamSpeak you can generate identities, every identity has a security level. On your server you can set a minimum security level you need to connect. Upgrading the security level takes longer as the level goes up.
~ Technical background ~
The security level is computed by doing this:
SHA1(public_key + offset)
Where public_key is your public key in Base64 and offset is an 8 Byte unsigned long. Offset is incremented and the whole thing is hashed again. The security level comes from the amount of Zero-Bits at the beginning of the resulting hash.
My plan was to use my GPU to do this, because I heared GPUs are good at hashing. And now, I got it to work.
~ How I did it ~
I am using a start offset of 0, create 255 Threads on my GPU (apparently more are not possible) and let them compute those hashes. Then I increment the offset in every thread by 255. The GPU also does the job of counting the Zero-Bits, when there are more than 30 Zero-Bits I print the amount plus the offset to the console.
~ The speed ~
Well, speed was the reason I started this. It's faster than my CPU for sure. It takes about 2 minutes and 40 seconds to compute 2.55 Billion hashes which comes down to ~16 Million hashes per second.
Is this speed an expected result, is it slow or fast? I don't know, but for my needs, it is fucking fast!
~ What I learned from this ~
I come from a Java background and just recently started C/C++/C#. Which means this was a pretty hard challenge, since OpenCL uses C99 (I think?). CUDA sadly didn't work on my machine because I have an unsupported GPU (NVIDIA GeForce GTX 1050 Ti). I learned not to execute an endless loop on my GPU, and so much more about C in general. Though it was small, it was an amazing project.1 -
OpenCL...
Okay so I'm completely new to OpenCL and I just put some stuff together to get a simple GPU Kernel running. Well that worked pretty good.
The reason I got into OpenCL was because I wanted to do some simple SHA1 cracking on my GPU. What I did was, I got a fast implementation of SHA1 from the internet, which works perfect in normal C++, but for OpenCL I have to rewrite some things. So I replaced all the memset and memcpy and so on with simple for loops and it still worked. Now, this should work on OpenCL, too, I thaught. God I was wrong!
Somehow the clBuildKernel got executed normally, but when I try to access the returned value (the error code) I get an Access Violation? It just doesn't make any sense to me?
Well I will try some stuff tomorrow again and I will find a solution for sure, but still, until now I just don't understand it. -
Is it possible to install TeamViewer/AnyDesk on a Debian Server (there is no Display attached to it so it has no real Desktop)?
I installed KDE and xrdp on it and that worked, the problem is that TeamViewer and also AnyDesk have a problem because they both can't find/use the fake RDP Desktop. Well and RDP is just so fucking slow...
So if anyone has some experience in this, I'd appreciate some help.6 -
My dad got this scammy E-Mail today...
The strange thing was, the sender and recipient were the same address, but I'll get back to that.
Unfortunately, I can't show it to you, but it said something like this:
"As you can see, I wrote this E-Mail from *YOUR* address. I have hacked your Account. Please pay me 300$ in bitcoin to this address: (address here) ..."
You get the point.
Now... my dad was pretty worried about the Account actually beeing hacked. One of his coworkers also got the same E-Mail. I told him that it's easy to fake the 'From' Header of an E-Mail, at least with the mail command on Linux. So I ssh'd into one of my Servers and sent him an E-Mail from lol@lol.de. Obviously, he didn't expect it to be that easy. Now he believes me that this is a scam and will tell his coworkers tomorrow.
From what I read in that E-Mail there was no part about recipient specific stuff, so I guess someone just wrote one text and made a simple bash Script for that... as you can see, people really do fall for this shit.
Now one question: is there a way to track down the Servers the E-Mail went through? Or is there anything one can do, apart from ignoring it?10 -
OKAY WHAT THE FUCK JAVA.
At school we were assigned the task to do Huffman's algorithm. Since I am way ahead of all the others, I made a GUI for that. (Btw, we use BlueJ for Java, it's just painful)
Now... I made a JTextField to put the output, which would be any character from 0x0 to 0xFFFF, into it.
Apparently, there is a bug in the setText method, which throws random NullPointerExceptions right into your face if you give it those Unicode characters.
So I looked it up:
It was a Bug, in JDK 1.6.something, where putting a 0xFFFF together with a 0x10000 would cause this. Now you may think, do we still have 1.6? No, we have 1.8 v171, WHY THE FUCK DOES THIS SHIT GIVE ME A NPE?! THE WORST PART IS I CAN'T DO ANYTHING ABOUT IT!
AND IT HAS THE WORST UNDEFINED BEHAVIOR:
1. NPE, nothing else happens
2. The Text box just gets invisible, but the border stays visible + NPE
3. The box completely disappears + NPE
Try-catching it doesn't do anything, everytime I fill the box with text, one of those options happens, and the box was never to be seen again! NOT EVEN CREATING A NEW TEXT BOX AND ADDING IT TO MY WINDOW WORKS.6 -
Amazing how one can easily browse the web nowadays...
A popup to allow notifications, that shitty cookie information, a subscription box and a fucking video that automatically starts playing while drowning my mobile internet.
Maybe I'll write another rant about the actual topic I looked up... 7
7 -
I JUST CAN NOT UPDATE THAT ONE SERVER TO DEBIAN 9
- it has no /dev/sda but a /dev/ploopXXXXX which is mounted as / but I can't see it
- uname says it's Linux 2.6.32-042stab126.2 and it says Debian some lines later in the ssh login
- there is no boot loader (I can't find it)
- lsb_release tells me it's running Debian 9.6 stretch, I put stretch into the apt sources
- in /boot there are 2 different versions: 3.16.0-7-amd64 and 4.9.0-8-amd64
- and I do not have physical access to it
WHAT THE FUCK AM I SUPPOSED TO DO?!
I wanted to install OpenVPN on it but that Linux Version doesn't support the Tunnel Interface /dev/net/tun8 -
Any good async (if possible, also pipeline based) Networking libraries for C++ on Linux? I want to create a small Server which should be able to handle a big amount of TCP connections (~500) at the same time, using threadpools maybe, something like Netty for Java would be the best.9
-
Visual Studio and its compatibility with Linux applications.
I don't know if I'm the only one, but this is my setup:
- Visual Studio 2017 on Windows 10
- Ubuntu 18.04 subsystem on Windows
I just can't do any Linux coding in Visual Studio... it is using my subsystem as a Remote Compiler and debugger, and a simple Hello World program does build and run successfully, but EVERY SINGLE LINE HAS ERRORS! It can't find stdio.h! Not a single include file works! They get auto-completed so it knows where the files are, but apparently opening them to see all the methods is too much for Visual Studio! I'd say the problem has something to do with IntelliSense since only inside the IDE my code has errors, compiling (which happens on the subsystem) works like a charm.2 -
Doing the stuff we learned in math today in C on my phone in portrait mode on a root server in my ssh app with mobile data in my free time in school is just some next level shit
 6
6 -
Having fun with some kind of pointers in Java right now...
This is a small program which first gets the address of the String variable and then 100 times the address of the addr variable, prints that address and dereferences it 101 times, to get the actual String back. But does it have an actual use case?
Apart from that, it's interesting to find out about how Java handles memory and stuff...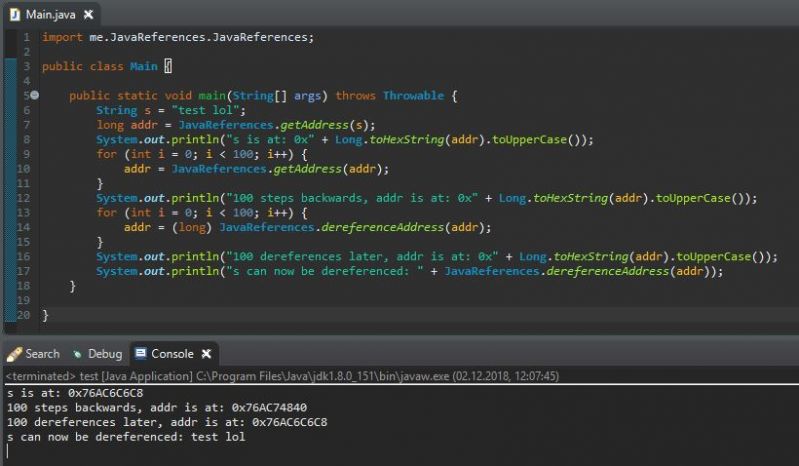 2
2 -
Very long story ahead!
Yesterday in the evening a friend of mine (calling him F from now on) became the target of something new to me...
Apparently one can fake his phone number through some fishy ways and call people with that number. Someone (we think we might know who it was, the why is at the end) did this yesterday to F.
Here's the whole story:
We were just talking together on a TeamSpeak Server (a program to talk to others on the internet) when suddenly another friend said: "F, why did you just call me three times in a row?" That was the first thing that was a bit suspicious. After that, F got calls from random numbers (even Afghanistan, we are German), and they said something like "Have fun with the police coming to your house". Then there was silence. 10 minutes later his phone rang and there were a ton of pizza delivery services in his town that apparently got pizza orders from him. Then there was silence, again. Suddenly someone with a hidden number called him, a woman's voice said they were the police and if F doesn't stop calling the police there will be consequences. F then told her what was going on but I think she didn't really care. She then wanted to know where F lives, but I told him not to say that, because if it is the police they can find it out by themself and if it's not, they don't need to know that.
Now, a short break: There is some fake information going around about where F lives. I can't remember when we found out but the attacker thought he would actually live there. No idea what happened at that location...
Now back to the story:
Time went by, nothing really happened. Suddenly F shouted: "There are blue lights outside! The police is here!" He muted his microphone and (the following is what he told us what happened) went down to the door (remember, he is 16) and there were two police men. They were asking about why he called the police. F explained what we knew until then, about number spoofing and stuff... They sent a more technical person to him, he understood what F was trying to explain. The police men drove away and he came back to tell us what happened. (Now we get back to what I heared myself.) The mom came in, screamed something that I couldn't understand, and F went offline. We searched who the attacker could have been. And we are pretty sure we found him. That guy connected to our Minecraft server (that's where I know F from) with his real IP, and his main account, which made it easy to search. He also got a static IP which means it doesn't change. We also got some information that in the recent days this guy was talking about VoIP spoofing and such stuff. Another friend of mine, a bit older, found some proofs and I think he will go to the police.
That's it. Thanks for reading.7 -
Does anyone know which bytes represent
mov rcx, 0x7FF0000000 (some qword)
mov rdx, 0x12345678 (some dword)
?
Or where I can find this?4
