Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "breached"
-
Oh fuck and boy Jesus, how on earth is this still a thing 😦
MD fucking 5 is not a fucking “secure” crypto algorithm.
This site has 14 million breached accounts with fucking MD5 hashes.
I think I’ve had to much internet for today.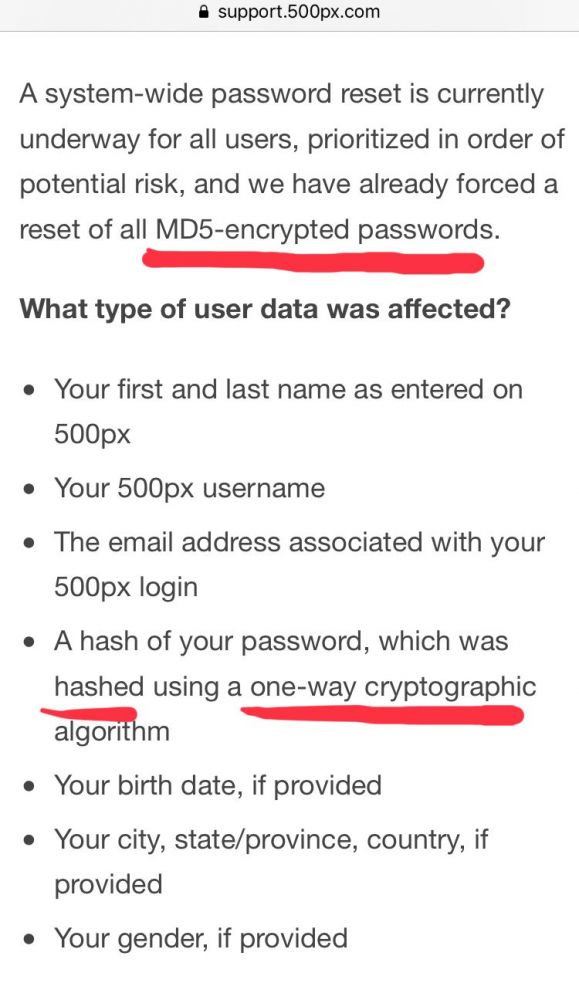 17
17 -
I am part of a team running a rather big Discord bot. One day last year late in October some dude tried to tell us that he and his "team" had breached our infrastructure. I noticed he was full of shit and started trolling him back, and actually putting him under pressure to develop a solution for us, pretending to want to pay them for it. At the end, our bold hero ended up "losing their job" AND "their house burning down" to get out of it again, lol wat.
The whole resulting conversation is available as a set of screenshots: https://imgur.com/a/vczyX
Enjoy!4 -
YouTube: SPENDING 24 HOURS IN PRISON CHALLENGE (GONE WRONG) (GONE SEXUAL) (COPS CALLED)
devRant: SPENDING 24 HOURS STRAIGHT ON DEVRANT TELLING EVERYONE THAT APPLE IS BAD AND MY SECURITY IS BETTER (GONE WRONG) (DATA BREACHED) (DFOX CALLED)20 -
"Our central servers firewall has been breached" - Doesn't even work on a server or anything, just his laptop
"How many proxies do we have left?"
"Around 10.200"
I don't take responsibility for any brain damage -
Soooo.. facebook got breached today, 50 million accounts compromised. I'm sure that will help their stock price.. 😂
Change your passwords, ladies and gents!11 -
When i was younger, lesser experienced and more naive than now; i got away with a lot of things. By lot of things i mean security flaws in my applications and overall architecture. I realise now i could've so easily been pawned.
Not that i claim to be totally secure even now, or would ever. It is a process, slow and painful one - Learning.
What i wish to point out is the role of favorable probability (non believers would call it luck). Security is so much about it. You get away with so many things for so long. And bang one day the roll of dice is unfavorable. On such rare occasions, just look back and wonder - damn i should've been breached long ago.rant hindsight security fail looking back security luck vulnerabilities food for thought musings naive probability2 -
Facebook founder and CEO Mark Zuckerberg broke several days of silence in the face of a raging privacy storm to go on CNN this week to say he was sorry. He also admitted the company had made mistakes; said it had breached the trust of users; and said he regretted not telling Facebookers at the time their information had been misappropriated.
From techcrunch article.13 -
I can cope with the workload and the silly client requests but I think my bullshit-threshold is very close to being breached.
One more thing and I'm not sure my brain will be able to act fast enough to stop my mouth shouting a horrible string of profanity.2 -
Tip: Use the same password on all services. That way, if one gets breached, you still remember the password to the others so that you can change your password there.1
-
I can't believe companies fucking do this! If your users PIIs gets fucking leaked or the security is breached in any god-damned way it's YOUR FUCKING JOB to let the affected users know! 57 million users got affected! What the fucking fuck? I think they should pass proper laws where companies have to tell the victims about breaches, especially when it's at a such a huge scale. I get it that it's wasn't under Uber but some third party; but even so Uber should have talked about the level of security in their SLAs and maybe performed regular audits.
This is ridiculous!
https://darkreading.com/attacks-bre...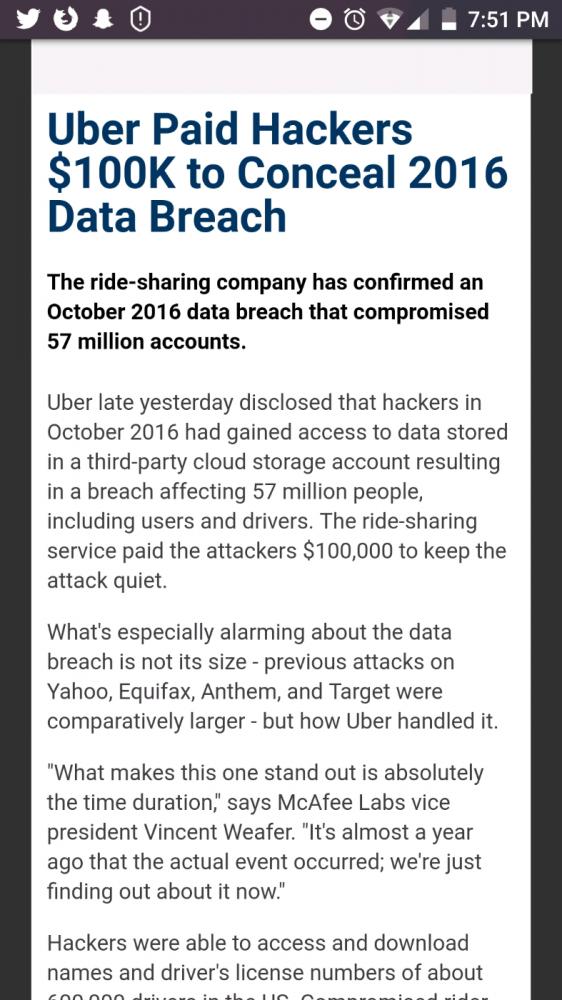 5
5 -
Disclaimer: This is all theoretical. Neither me nor my friend (with whom I discussed this) are stupid enough to even try to pursue this, but as an idea, i believe it might generate cool/new ideas/ways for handling secure communications across social groups.
Let's do some role play. Let's design a delivery app for drug dealers, think Seamless or Uber Eats, but for drugs. Not for big deliveries, like kilograms of coke, but smaller stuff. Maybe a few grams of it or something. The clients could rate dealers, and vide-versa. This would build a level of trust within the system. There would be no names, just anonymous reviews, ratings, and prices. Only the info you'd need to know.
The biggest (only?) problem we found (besides legality) was that, how would you prove that you're a client and not a snitch (or cop). This would have to somehow be handled both on signup, as well as when ordering (let's imagine that all who are clients are pure and won't ever snitch).
One of the ways we found to combat this was to have the app invite-only. This would, in theory, do away with the problem of having snitches signing up. However, what if the phone got stolen/breached by a snitch, and they also got full access to the account. One way we thought we could combat this would be with a "dispose number" or something similar. Basically, you call a number, or send a text, or message a Signal bot etc, which would lead to the account's instant termination, no traces of that user left. Hence, a dispose number.
The flow of the app would be as follows:
A client wants some amount of heroin. He opens the app, searches for a dealer, sends the him the desired amount, and in return gets back a price from the dealer. If both parties agree on the amount and price, the deal would start.
The app would then select a random time (taken from the client's selected timeframe and the dealer's "open" time) and a location (within a certain radius of both them, somewhere in between them both for convenience). If both of them accept the time and place, they'll have to meet up at said time and place.
The actual delivery could also be done using two dead drops - the client drops the money at one of them, the dealer drops the goods at the other one. Yes, this might be subject to abuse, but it wouldn't be that bad. I doubt that clients would make huge orders to unknown/badly rated dealers, as well as dealers accepting offers from badly rated clients. My idea is that they would start small, just so if they do lose their money/goods, the actual loss wouldn't be as big for them, but for the other party, having bad ratings would mean less clients willing to buy or dealers willing to sell.
A third way would be to use crypto, but the reason I left this as the last one is because it's not that wide-spread yet, at least not in local drug dealing. With this method, the client would initiate the order, the crypto would be sent to either the dealer or an escrow account, the dealer would then drop the goods at a random place and let the client know where to go to get them. After the client has gotten the goods, they could both review/rate the quality as well as the overall experience with that dealer, which would either make or break the dealer's upcoming deals. This would be pretty much like other DNM's, but on a local scale, making deliveries faster.
So far, this would seem like something that would work. Are there any ideas that might improve this? Anything that might make things more secure/anonymous?
My reason for this post is to spark a conversation about security and anonymity, not to endorse drugs or other illegal stuff.
Cheers!
PS. Really loving the new PC design of devRant14 -
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
Soft wear tech is a platform designed to help you recover lost coins, wallets, and cryptocurrencies.
When thieves stole a staggering $900,000 worth of Bitcoin from my digital wallet, I was devastated. As an experienced cryptocurrency investor, I had always taken pride in my security measures, believing my assets were safe. Nonetheless, these skilled hackers breached my defenses and made off with my hard-earned digital coins, leaving me not only with a significant financial loss but also with a feeling of violated trust and security.
Refusing to let the criminals get away with their actions, I took immediate steps to address the situation. I reported the theft to the authorities, fully aware that tracing cryptocurrency transactions is notoriously difficult. However, I was determined to pursue every avenue available. That’s when I discovered the innovative services offered by SOFT WEAR TECH, a company specializing in tracking and recovering stolen digital assets.
The dedicated team at SOFT WEAR TECH quickly sprang into action, meticulously analyzing the blockchain transaction data to follow the money trail. Thanks to their exceptional investigative skills and cutting-edge tools, they were able to pinpoint the location of my stolen Bitcoin and initiate the recovery process. It was a long and arduous battle, with the thieves attempting to cover their tracks and move the funds. Yet, the SOFT WEAR TECH team remained resolute, outsmarting the criminals at every turn.
After weeks of relentless effort, they successfully reclaimed my $900,000 in Bitcoin and returned it to me. I was overjoyed—not only was my investment restored, but I also felt a sense of triumph over those who thought they could escape unscathed. This experience has heightened my vigilance and commitment to security in cryptocurrency investing, and I am deeply grateful to have had the SOFT WEAR TECH team fighting to protect what belongs to me.
For inquiries, feel free to reach out via
Email: softweartech5@gmail.
Email: softewar.tech@yandex
Phone : +1 9594003352 -
SURVIVING THE BYBIT HACK HOW CRYPTO RECOVERY CONSULTANT SECURE MY ASSETS
It was the kind of morning that left my heart pounding in my chest. My phone buzzed with a series of alerts—emails, messages, all talking about one thing: Bybit had been hacked. North Korean hackers had breached the exchange, and the total losses were over 1.5 billion dollars in cryptocurrency, Ethereum to be precise. My stomach churned as I read, realizing I was one of the many affected. I had been an avid Ethereum investor, with a substantial amount of my savings tied up in the coin. The idea of losing it all was unbearable. But panic was no help, so I immediately began searching for solutions. That’s when I stumbled across a company that specialized in crypto recovery and securing your asset, CRYPTO RECOVERY CONSULTANT. Their website promised to assist with situations just like mine. Skeptical but desperate, I reached out, hoping for a miracle. To my surprise, a representative called me within minutes. They explained that they had experience securing wallets from compromised exchanges and securing coins during massive hacks like the Bybit breach. After a brief consultation, they assured me they could secure my Ethereum by implementing a stronger security system that would block any unauthorized access. They guided me step-by-step, helping me transfer my assets to a more secure wallet and setting up additional layers of protection that I never even knew existed. Thanks to their swift action and expertise, I felt a weight lift from my shoulders. The hackers wouldn’t be able to touch my Ethereum now. My coins were safe, protected by multi-signature authentication, cold storage, and state-of-the-art encryption. Without CRYPTO RECOVERY CONSULTANT, I would have lost everything. Their quick thinking and advanced security measures saved my assets from the grasp of cybercriminals. I couldn’t be more grateful. Now, I sleep soundly, knowing that my Ethereum is safe, all thanks to them. cryptorecoveryconsultant312[@]zohomail,,,com cryptorecoveryconsultant[@]cash4u,,,com 1
1 -
TOP CRYPTO RECOVERY HACKER HIRE SPYWARE CYBER
In the cryptocurrency world, I experienced what felt like a shipwreck. One fateful day, I discovered that my digital wallet, the fortress of my hard-earned investments, had been breached. A malicious spyware had infiltrated my devices, tracking my every digital move and siphoning away my funds. Panic set in as I watched my cryptocurrency dwindle to nothing, and despair clouded my judgment. In the depths of my frustration, I stumbled across a dedicated cybersecurity team specializing in recovery solutions. Their expertise shone like a beacon; they understood the complexities of both the digital and cryptographic seas. After an initial consultation, they embarked on the challenging task of examining my devices, employing advanced spyware detection and removal protocols. As the team untangled the web of malicious code, I felt a glimmer of hope. Days turned into nights of collecting evidence and tracing digital fingerprints left by the intruder. Ultimately, their persistent efforts paid off. Not only did they recover my stolen assets, but they secured my digital wallet for future transactions.Today, I stand invigorated—not just by the recovery of my lost cryptocurrency, but by the peace of mind that comes from knowing I am now shielded from future threats. Thanks to the incredible capabilities of cybersecurity professionals and the lessons I learned, I’m back in the saddle, wiser and more resilient. My experience serves as a powerful reminder: in the ever-evolving landscape of technology, vigilance and expert help can illuminate the darkest paths.
WhatsApp: + 1.6.4.6.4.1.0.7.7.4.2.
Email: spyware@ cybergal . com
How do I recover my lost crypto?
What is the recovery key in crypto?
How to recover lost bitcoin private key?
How do you recover stolen cryptocurrency?
How to claim unclaimed Bitcoin?
Legitimate crypto recovery company Spyware Cyber
Recover Bitcoin wallet without phrase
How to recover Blockchain password without backup phrase
lost crypto wallet finder
Blockchain recovery Department
#Tag on how to recover my lost cryptocurrency
#Tag on how to recover my lost cryptocurrency #cryptorecovery, #lostcrypto, #seedphrase, #walletrecovery, #blockchainrecovery, #recovermycrypto, #cryptohelp, #lostwallet, #cryptosupport.
WhatsApp: + 1.6.4.6.4.1.0.7.7.4.2.
Email: spyware@ cybergal . com -
BEST DIGITAL ASSETS RECOVERY COMPANY 2025 (TRUST GEEKS HACK EXPERT)
E m a i l. Trustgeekshackexpert[At]fastservice[Dot]com
T e l e g r a m. Trustgeekshackexpert
w h a t's A p p. +1 7 1 9 4 9 2 2 6 9 3
Back in January, I got caught up in a cryptocurrency scam that really turned my life upside down. I invested a jaw-dropping $214,000 in BNB on what I thought was a legitimate crypto site. For a while, everything seemed to be going smoothly, and I was excited about the returns I was expecting. But then, when I tried to withdraw my profits, everything fell apart. The scammers froze my account and demanded more money, claiming I had breached some sort of agreement. I was completely devastated and felt trapped in a nightmare. It got so overwhelming that I started having dark thoughts about ending it all. Thankfully, my family noticed I was struggling and stepped in when I finally opened up about what was happening. During one of our talks, my niece mentioned a group called (Trust Geeks Hack Expert). She had heard they helped people recover their stolen cryptocurrencies, and I was intrigued. I thought, “Could this be my saving grace?” So, I decided to reach out to them and explain my situation in detail. To my surprise, (Trust Geeks Hack Expert) was incredibly responsive and compassionate. They reassured me that they had dealt with cases like mine before and would do everything they could to help. I was a bit skeptical, but I was also desperate for a solution. Amazingly, within about three days if I remember correctly they managed to recover the entire $214,000 that I had lost! I was in shock. It felt like a huge burden had been lifted off my shoulders. If you’re reading this and you’ve fallen victim to a crypto scam, I can’t recommend (Trust Geeks Hack Expert) enough. They are truly exceptional at what they do. Reach out for help, and don’t hesitate to contact them. (Trust Geeks Hack Expert)2

