Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "md5"
-
My school.
We have free WiFi access, but you need to login into your personal student account to use it.
Turns out, SQL Injection works.
It gets worse.
Table name "schueler".
SELECT *
Well.
Got all data on all students.
Name, address, phone number, passwords in plain.
I reported it using an anonymous email. Partially fixed. Standard quotes now get eacaped. Still, passwords are now MD5.47 -
Another one, teach secure programming for fucks sake! This always happened at my study:
Me: so you're teaching the students doing mysql queries with php, why not teach them PDO/prepared statements by default? Then they'll know how to securely run queries from the start!
Teachers: nah, we just want to go with the basics for now!
Me: why not teach the students hashing through secure algorithms instead of always using md5?
Teacher: nah, we just want to make sure they know the basics :)
For fucks fucking sake, take your fucking responsibilities.31 -
I was reviewing one dev's work. It was in PHP. He used MD5 for password hashing. I told him to use to password_hash function as MD5 is not secure...
He said no we can't get a password from MD5 hashed string. It's one way hashing...
So I asked him to take couple of passwords from the users table and try to decode those in any online MD5 decoder and call me after that if he still thinks MD5 is secure.
I have not got any call from him since.18 -
Google: Don't use a password from another site, or something too obvious like your pet's name.
Me: 5f4dcc3b5aa765d61d8327deb882cf9917 -
"The password must be 6 to 32 characters long and must contain atleast one uppercase character, one lowercase character, a special character, the md5 hash of your last name, a dried olive branch and the blood of a unicorn."5
-
I was registering for a website, and on a whim, I used this as my username:
null'); PRINT('Hello');--
And sure enough, the login system went down. The next day it was still down, so I went to Twitter to tell the people running the site that this was why, but to my surprise, I see them saying they had been hacked.
Based on the timing, I'm pretty sure they're referring to this, but they are saying user info was stolen. *facepalm*
They later said they stored passwords salted with a fixed salt and hashed with fucking md5, at which point I was glad not to have done any more business with them.
How incompetent can these fucking people be?!14 -
https://google.com”f people near me wanted to show me something.
Person: Check out this zero-day exploit! I hacked into the system using a cloud-based cryptographically secure MD5 hash finite automata firewall HTML code API!
Me: Erm...what exactly did you hack?
Person: *shows screen while smirking*
It was a shell simulator website running “ping https://google.com”7 -
Oh fuck and boy Jesus, how on earth is this still a thing 😦
MD fucking 5 is not a fucking “secure” crypto algorithm.
This site has 14 million breached accounts with fucking MD5 hashes.
I think I’ve had to much internet for today.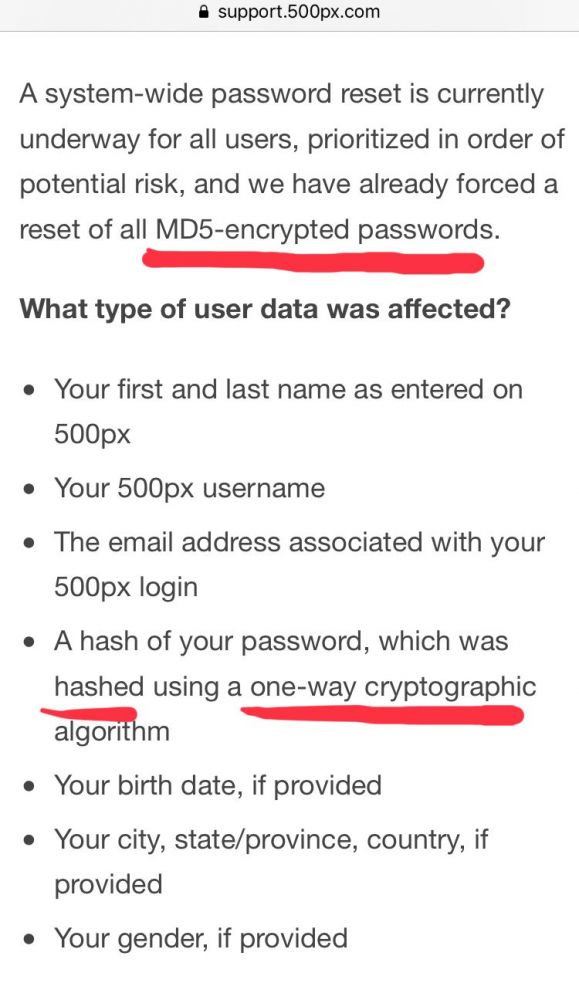 17
17 -
!security
(Less a rant; more just annoyance)
The codebase at work has a public-facing admin login page. It isn't linked anywhere, so you must know the url to log in. It doesn't rate-limit you, or prevent attempts after `n` failures.
The passwords aren't stored in cleartext, thankfully. But reality isn't too much better: they're salted with an arbitrary string and MD5'd. The salt is pretty easy to guess. It's literally the company name + "Admin" 🙄
Admin passwords are also stored (hashed) in the seeds.rb file; fortunately on a private repo. (Depressingly, the database creds are stored in plain text in their own config file, but that's another project for another day.)
I'm going to rip out all of the authentication cruft and replace it with a proper bcrypt approach, temporary lockouts, rate limiting, and maybe with some clientside hashing, too, for added transport security.
But it's friday, so I must unfortunately wait. :<13 -
No, MD5 hash is not a safe way to store our users' passwords. I don't care if its been written in the past and still works. I've demonstrated how easy it is to reverse engineer and rainbow attack. I've told you your own password for the site! Now please let me fix it before someone else forces you to. We're too busy with other projects right now? Oh, ok then, I'll just be quiet and ignore our poor security. Whilst I'm busy getting on with my other work, could you figure out what we're gonna do with the tatters of our client's business (in which our company owns a stake) in the aftermath of the attack?7
-
I am working on a project with a retard.
I am supposed to focus on the mobile apps but the backend guy doesn't know shit about REST.I spend more time teaching him how to serialize data into JSON and telling him not to store passwords as plaintext(He's now using md5 despite me telling him to use bcrypt) than developing the mobile apps am supposed to.
Guess who will be blamed for missing the deadline?
Yea, it's me.
Guess who will get the credits for the backend i am developing?
Yea, it's him.
Fuck!12 -
Password hashing using md5, it is 2016!! I have seen a sys admin update a user password using a MySQL query23
-
Just saw this in the code I'm reviewing:
function encryptOTP(otp){
var enc = MD5(otp);
return enc;
}13 -
TIL that TI has no goddamn chill
Texas Instruments released the TI-83+ calculator model in 1996. The Z80 was not at all stock and has the following features:
- 3 access levels (priveleged kernel, kernel, user)
- Locking Flash (R/O when locked for most pages, some pages protected and unreadable as well, only unlockable from protected Flash pages by reading a certain order of bits then setting a port)
- Locking hardware ports (lock state always the same as flash)
- Customizable execution whitelist range (via locked ports)
- Configurable hardware (Flash/RAM size changeable in software via locked ports, max RAM is 8MB which is fucking mental compared to the 64k in the thing)
- Userland virtualization (always-on)
- Reset on violation of security model
- Multithreading
- Software-overclockable CPU
- Hardware MD5 and cert handling
TI made a calculator in 1996 with security features PCs wouldn't see until like 2010 what the *actual* fuck10 -
English teacher :prepare a recipe of your favorite meal
Me :yeah sure
Title :how to prepare md5 seasoned with salt.
Procedure :
$salt="*+3256_$@";
$userpass="12345aeiou";
$md5hash=md5($userpass.$salt);
echo $md5hash;3 -
A popular social media website in my country (which my friends and I were working on it's new design) was hacked and everyone on the dev side of the website was invited to the ministry of communications, believing we were going to discuss security of user data. The other guys (working on the back-end) were friends with the CEO (if you want to call it that) and naturally came to the meeting. They started to talk about the girls of their city. Meanwhile about 1.2 million user data encrypted with MD5 was out there.6
-
Massive payment gateway (not gonna say names) with more then 10k transactions / hour telling md5 is one of most secure encryptions they have. Only to made worse by the fact that they send the key and hashed key in the same request.
I am advising all our clients to change payment gateway asap if they use this one.1 -
Found that out that one of our company's internal API (I hope it's only internal) is exposing some personal data. After finally getting the right people involved they said they'd fix it 'immediately'.
5 days later I check and now there is more personal data exposed...which includes personal security questions and the hashed answers to said questions.
And of course they are using a secure hashing mechanism...right? Wrong. md5, no salt
Sigh...5 -
A few years ago I found a public AWS S3 bucket owned by a fortune 500 company containing a database dump backup with all of their users unsalted md5 hashed passwords.
I didn't report it because I don't want to get sued or charged. I don't know whether it's still public or not.6 -
That moment when you find out your school is using unsalted md5 passwords, and your school project requires using it too... FUCK4
-
2 things I'm working on now:
#1 a personal project I am hoping to commercialize and turn it into my moneymaker. Hoping it'd at least be enough to pay the bills and put food on my table so I could forget 9/5 for good. But it has a potential of becoming a much, MUCH bigger thing. This would need the right twist tho, and I'm not sure if I am "the right twister" :) We'll see.
#2 smth I'm thinking of opensourcing once finished -- a new form of TLS. This model could be unbreakable by even quantum computing once it's mature enough to crack conventional TLS. I'm probably gonna use md5 or smth even weakier - I'm leveraging the weakness of hashing functions to make my tool stronger :)
I mean how long can we be racing with more powerful computers, eh? Why not use our weakneses to make them our strengths?
Unittests are already passing, I just haven't polished all the corner-cases and haven't worked out a small piece of the initialization process yet. But it's very close6 -
When I just started making things in PHP, I always taught that md5 encryption was the best thing out there.. Once I learned that it was the most easy way to break I changed to SHA1. What were I thinking? I now use a custom generated SALT for each user and encrypt with SHA512, should be safe for a while, right?
 7
7 -
$md5 = md5_file($file_uri);
=> Returns false
Mmh...
die(is_readable($file_uri));
=> Returns false
[Mmh intensifies]
if(!is_readable($file_uri)) {
chmod($file_uri, 0777);
}
=> Chmod() returns false
GAAAAH FUCK THIS I CALL IT A DAY6 -
Client asked us to modify site made in some obscure CMS. Authentication on AJAX request is done by sending email and password as plaintext in header and then it would do md5 on server side5
-
This was actually written by a Junior of mine (and if it wasn't for me having to review it, it would have made it to production):
- Admi password was just an MD5 in the javascript.
- Javascript would validate the password input.
- Javascript would then send a POST request to a PHP script.
- On display, the HTML of the news article wasn't HTML escaped.
My brain: "Let's just send this XSS vector to this PHP script"4 -
How to log in to CMS Of Doom™...
What could go wrong?
MD5 password hashing? HTTP links? Extracting the whole $_POST array? 8
8 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
I wrote an auth today.
Without frameworks. Without dependencies. Without under-the-hood magic. Without abstract pluggable adaptor modules for the third-party auth library with 63 vulnerabilities and 1252 GitHub issues. Without security vulnerabilities showing up in NPM log. Without dependency of a dependency of a dependency using md5 and Math.random() under the hood for historical reasons, and now we're fucked, because this is the only lib for our framework, and we have no time to write our own replacement. Without all that shit.
Rock-solid, on top of scrypt. Stateless and efficient.
It felt amazing.9 -
I'd never do anything "risky" in a prod environment if I considered it so at the time, but in retrospect there's *lots* of things considered risky now (both from a security and good practice viewpoint) that were standard practice not long ago:
- Not using any form of version control
- No tests (including no unit tests)
- Not considering XSS vulnerabilities
- Completely ignoring CSRF vulnerabilities
- Storing passwords as unsalted MD5 hashes (heck that was considered very *secure* in the days of plaintext password storage.)
...etc. I'm guilty of all of those previously. I daresay in the future there will be yet more things that may be standard practice now, but become taboos we look back on with similar disdain.1 -
Brilliant Stakeholder: of course communication with our backend will be encrypted with an algorithm I'll confidentially share with you once the contract is signed
Senior Developer: npm install md51 -
It's a tie between 3 things for me.
1. md5 hashed passwords
2. post variable concatenated into sql with no checks
3. admin login over http
sad thing is that all 3 was one website I redid a few years ago8 -
Sometimes lack of confidence in one area reveals oversight cockyness in stronger areas:
Set up a simple login system from Unity engine to php to mysql db, using android device ID as the login id. Set up database column to accept 32 length varchar for MD5 hashed strings, as I knew the method I was getting the android device ID was automatically being hashed that way and more or less was what I wanted anyway.
Spend 2 days wondering why it would insert the logins with 0 issue, but could never retrieve them. Due to lack of web development and PHP skills, I assumed I was screwing up the handling of mysqli_num_rows() (to check whether I was inserting or selecting in the query) or simply screwing up my SQL queries.
Rewrite the code a few times, even went back to a method I had used in the past.
Today it dawned on me that my testing machines deviceID had been getting trimmed to the 32 character limit. Turns out I didn't account for my workstations device ID to be automatically hashed like the android device id is.
For 2 days I was obtaining and sending a 40 character string to a 32 character limit varchar and blaming my lack of PHP skills........
Back to my niche I go!1 -
I discovered a commit message from one of my (senior) colleagues today. It made me shudder. It read, 'Just adding some changes made outside of source control and deployed (over last 12 months)'.
I genuinely think he can't follow any processes he didn't design. He controls the servers too, so it's not like any pipeline would prevent him from just doing what he wants. It's a bit scary to be honest, he thinks MD5 is a secure password hash! -
Still more fallout from Yahoo in 2003.
I thought back then we already established that MD5 hashing is not security? 1
1 -
We had to add licensing to a program of us. In the end we chose a small java-library for that and i wrote a convenience script that creates a valid license.
But the script got its input from static strings and that was its doom.
My boss cloned the repo with the script (and jars), replaced the strings with real world data and pushed.
For his conveinience, because there were several clients, he copied the data-section, commented out the first one and put another data into the second section. This happened a few times and HE PUSHED AGAIN.
Now this repository contains a fine record of everyones licenses and their passwords. I know it shouldn't bother me, but it still gets my eye twitching, just like md5-hashing on passwords (which actually happens on that licensed project)2 -
I had joined a new company and got access to their codebase. They were updating password on MD5 hash of user name and their email in get request. No password validation, no token based authentication, nothing.
Eg
...com/change_password/email=(plainemail)&name= MD5(name)
That's it, you get change user password. -
!rant
Just got a message from a recruiter. It was something different. There was a link with a ZIP file and a bunch of files in it. Plus two MD5 hashes. You should now find the correct private key and the encrypted message to decrypt it with the key. This gave you the password to get further in the application process.
Not particularly difficult, but a refreshing change from the usual blah blah.1 -
Created an md5 hash for the admin user's pw on a personal project and the hash starts with "bad666...".
Is md5 telling me something?
Hmm...8 -
Here's a fucking challenge:
Generate an MD5 hash in React Native!
crypto - NOPE deprecated, react native throws when you try to import it anyway
react-native-crypto - NOPE, needs to make use of a shim that recursively edits node_modules... hmmmm yeah you think thats a good thing to have?
react-native-fast-crypto - NOPE, no TypeScript types, no documentation in general, only supports sha512?! WTF
garbage fucking idiot tooling stupid dumbass stupid splat splat barf splat21 -
Turns out MD5 collisions are hard to iterate through. Max combinations of bytes in a 100,000 byte file is (as calculated by Python:)
413502433742660544726868172195767861427618658445205343992065892230166930397146583182005172845204489533665188550385797247605830027690030912310887164176364954875069038057666590769687571726193148717652368418744731692453987107907857683242360451588862381980796040785447771748097295949966591258383632274557701138287596503423452399232536933583768184114874795654760979888748015241761933209111943015224044366005903481415990946152075730054176507652408593662525624208010788644701872255643844493769499469673271219048262961476704374776988472648537308308011235412742501908803475102336862442166237905095612511941476299337727729022024118389323121828087330601048095646801171259973845170877342411799823272475101891307296782554819753985119403152255745494789644397312746702721825997945525576
i'm getting 1227.97 iterations a second. (Note: no, not using C, i don't know enough to do it in C. If someone wants to take my script, redo it in C, and send it to me for comparison, that'd be great.)12 -
I decided to run the ROCKYOU password list to see if there are any patterns in md5 hashing, not sure why but I am starting to confuse myself and I need a new pair of eyes to have a look.
in advance, sorry for the shitty image, that lappy is a temporary solution.
So the very accurate and not bias numbers show that the letter "0" appears more than the rest, would there be any use in let's say ordering the wordlist with words that have the most "0" and "7" in their hash to appear at the top?
I believe I might be trying to stretch the numbers and see a pattern where there is none but its worth a shot I think.
Note:
- These numbers come from only about ~14m words
My thinking trail is that if statisticaly these hashes are more likely to appear, they are more likely to be the one I am looking for? 3
3 -
OK, I'm spoiled Linux bra^H^H^Huser, so MD5, SHA1,... checksums for distributions' ISO files are something I take for granted but is really that hard for Microsoft to provide same for Windows 10 ISOs (plain and simple info, not something that require equilibristics and deep diving into MSDN site) ?!2
-
Trainee accidentally said md5 is an encryption... Gave him the "functional specification of OpenPGP on ISO Smartcards". He learns OpenPGP now, before he reads that I hope.
-
A friend of mine who wants to learn about Linux has a stronger will than me, as I think installing Linux in 2020 is gonna break me but he's still stoked as shit. I'm fucking serious. He asked me to install several distros, in order of interest (because they all fucking failed, because of fucking course they did) on a USB HDD he was using just for this.
We tried, in order:
Arch: initramfs wiped his Windows HDD when it crashed. IDFK how, but it zeroed the top 32KB of the drive. It wasn't even the right HDD...
Linux Mint: nvidia drivers refused to see his GPU after install. No matter what we did. Live media saw it fine until it was installed on the external drive, too.
Debian: Installer couldn't see the external HDD, ever. No matter what we did. It had a /dev entry, lsblk and fdisk saw it, I could format and mount it, but the installer crashed when it refreshed the device list when it was present. Every goddamn time.
Fedora: Installer broke halfway through as an executable (or 70) were corrupted, but the disc matched the ISO and the ISO sums correctly, so this is apparently how it was packed and shipped.
CentOS: Refused to boot. Just entirely. GRUB would go to load the kernel and it'd hang.
All ISOs and discs were verified as matching provided sums using MD5 and SHA256. How the fuck is Linux so fucking hard to get working on older hardware in 2020? Worked great in 2008, worked great in 2018, why is 2020 such a goddamn issue?11 -
One of our clients old CMS was completely hand written, allowed execution of PHP files in the uploads directory with an uploader that was publicly accessible, and the "security" was MD5 hashed passwords. Oh and the username/password for the admin user was password.
-
2016 and the passwords were stored in plain text. I pointed it out, they said they'll use md5 instead :/
PS: Ended up fixing it for them with HMAC-SHA256 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
>making bruteforce MD5 collision engine in Python 2 (requires MD5 and size of original data, partial-file bruteforce coming soon)
>actually going well, in the ballpark of 8500 urandom-filled tries/sec for 10 bytes (because urandom may find it faster than a zero-to-FF fill due to in-practice files not having many 00 bytes)
>never resolves
>SOMEHOW manages to cut off the first 2 chars of all generated MD5 hashes
>fuck, fixed
>implemented tries/sec counter at either successful collision or KeyboardInterrupt
>implemented "wasted roll" (duplicate urandom rolls) counter at either collision success or KeyboardInterrupt
>...wait
>wasted roll counter is always at either 0% or 99%
>spend 2 hours fucking up a simple percentage calculation
>finally fixed
>implement pre-bruteforce calculation of maximum try count assuming 5% wasted rolls (after a couple hours of work for one equation because factorials)
>takes longer than the bruteforce itself for 10 bytes
this has been a rollercoaster but damn it's looking decent so far. Next is trying to further speed things up using Cython! (owait no, MicroPeni$ paywalled me from Visual Studio fucking 2010)4 -
Okay so if a company decides to use md5 for hashing passwords after a million users already registered how the hell will they transition to any other way of storing passwords. As they don't have plaintext to convert them into the new hashing function.12
-
When your redirect url passed as get parameter to 'secure' the login you pass bade64 envoded string with path, length and (salted) md5 hash ....
why God why you secure a redirect you do 302 to on success1 -
Level of fuckity fuck mood.
After changing dozens of build plans in Bamboo, the build system of poo...
How to verify that nothing has gone wrong?
Poking the database, you'll be surprised that Bamboo stores the buildplan definition as XML.
Another surprise: Some of the keys / values have typos.
Yeah. You read that right. There are typos inside the XML...
Now together with Postgres, we can use XPATH and have some fun.
UNNEST(COALESCE(XPATH('/configuration/buildTasks/taskDefinition[userDescription[contains(text(),"Bleep")]]', build_definition.xml_definition_data::xml)::varchar[], ARRAY['']))
Lovely wrapping via coalesce for some null safety.
Now we get da task definitions for fields having user description text containing bleep.
Wrapping it in two REGEXP_REPLACE to strip out stupid identifiers....
REGEXP_REPLACE(REGEXP_REPLACE(...., '<id>\d+</id>', ''), '<oid>\d+</oid>', ''))
Then wrap that in MD5.
Boom. Lots of MD5 sums to help you identify if the configs are identical for a task or not.
Now wrapping that in another select to group by the MD5 and filter out the non identical ones.
I hate it how sometimes one has to seemingly do a full 2 hour dance for something as stupid as validation.
I'm pretty glad though for XML and XPATH.
Cause otherwise that would have been a whole can of worms I don't wanna think about....2 -
Does anybody know how to create a JSON list of all files in a folder with path+filename, md5 hash, file name and size? My client wished that I rework an open source launcher which is reading an HTML file in JSON format5
-
There were probably odd bits and peices before this, but the first one I did with a friend must have been a "password cracker" to attempt to crack MD5 hashed passwords. Was simple as anything, but worked quite effectively.
-
Been wondering about something and can't figure out if I am a retard or a genius 😂.
If MD5 is so outdated and should not be used to store password hashes (let's say for whatever reason you cannot effectively switch to another algorithm) wouldn't it just be easier and more secure to just re-encrypt the hash again, so just MD5 the MD5 hash... in theory, wouldn't that make the hash virtually uncrackable because instead of trying to brute force actual real words, you now have a hash of essentially random characters which have no relation to the others, and even then, suppose you manage to crack the hash, you will get another hash to crack before getting to the password?5 -
I need MD5/original size (in bytes) pairs to test my engine and see if i can get back the originals in any reasonable amount of time.
Any offers?8 -
I feel no motivation until we're past this fucked up hump and all the tech that is relevant and theory that was kind of crap remains the same and in the same foreground position and all the chommies die or go away.
I can't even finish the next line of code I know I already wrote to spawn a crap ton of md5 and file structure scans for quick disk vs disk inventory.
that i knew actually worked.
i mean if i hide proof this time period existed in teh fucking woods again they'd just use dogs to find it.
guess its time to make news.1 -
For a few days I failed to see that I need to add one string escape instead of re-writing the whole S3 file upload logic to hash file names using md5. :( Context: We were not able to retrieve some files with international letters (like German, Chinese, etc) in their names because of weirdly escaped signed URL to S3.
-
Since tar is apparently faster than cp
It’s making me wonder
Which is faster
Md5/sha with a comparison against the copied files
Or diff ?5 -
I recently started working on laravel. As the community says it was easy to get along with the framework and its methodologies. But then i had to do multiple login with framework in same domain.
Oh man, i spent a week to make it work. All those guards and middlewares realted to login was driving me crazy. The concept was clear, but somehow the framework was like "You! I shall make you spend a week for my satisfaction". The project demo was nearing and i was doing all kind of stuff i found. Atlast after continous tries it worked. Never in my 4+ years as a developer i had to face such an issue with login.
So here is how it works,if anyone faces the same issue:
(This case is beneficial if you're using table structures different from default laravel auth table structures)
1. Define the guards for each in auth.php
Eg:
'users' => [
'driver' => 'session',
'provider' => 'users',
],
'client' => [
'driver' => 'session',
'provider' => 'client',
],
'admin' => [
'driver' => 'session',
'provider' => 'admins',
],
2. Define providers for each guards in auth.php
'users' => [
'driver' => 'eloquent',
'model' => <Model Namespace>::class,
'table' => '<table name>', //Optional. You can define it in the model also
],
'admins' => [
'driver' => 'eloquent',
'model' => <Model Namespace>::class,
],
'client' => [
'driver' => 'eloquent',
'model' => <Model Namespace>::class,
],
Similarly you can define passwords for resetting passwords in auth.php
3. Edit login controller in app/Http/Controller/Auth folder accordingly
a. Usually this particular line of code is used for authentication
Auth::guard('<guard name>')->attempt(['email' => $request->email, 'password' => $request->password]);
b. If above mentioned method doesn't work, You can directly login using login method
EG:
$user = <model namespace>::where([
'username' => $request->username,
'password' => md5($request->password),
])->first();
Auth::guard('<guard name>')->login($user);
4. If you're using custom build table to store user details, then you should adjust the model for that particular table accordingly. NOTE: The model extends Authenticatable
EG
class <model name> extends Authenticatable
{
use Notifiable;
protected $table = "<table name>";
protected $guard = '<guard name>';
protected $fillable = [
'name' , 'username' , 'email' , 'password'
];
protected $hidden = [
'password' ,
];
//Below changes are optional, according to your need
public $timestamps = false;
const CREATED_AT = 'created_time';
const UPDATED_AT = 'updated_time';
//To get your custom id field, in this case username
public function getId()
{
return $this->username;
}
}
5. Create login views according to the user types you required
6. Update the RedirectIfAuthenticated middleware for auth redirections after login
7. Make sure to not use the default laravel Auth routes. This may cause some inconsistancy in workflow
The laravel version which i worked on and the solution is for is Laravel 6.x1 -
Is there a standard around checking the checksum of a bundled weapp to make sure it's the same as what the open source codebase would compile to?
I'm working on some opensource blockchain interface software and obviously blockchain passwords are pretty important, so we do all transaction signing client side and password storage client side, but there's no point doing that if the user can't verify that the password isn't being sent off to some server in secret, but the only way to ensure that is with open source software + a checksum check upon loading, because opensource software doesn't mean the deployed version is the exact opensource branch version.
Any ideas?1




