Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "wk25"
-
Picked up a legacy site to re-build, turns out just adding:
'?admin=1'
to the query string gave you full admin rights to the entire site without having to authenticate. The site was live for 2 years.3 -
One of our customer thought it would be too unsecure to send us his AWS credentials by email. So he printed it and sent it as registered mail to us. The password we received was "hallo123".6
-
A guy named Valter couldn't register on this website because the developer blacklisted *ALTER*, amongst other words, to prevent SQL injection.11
-
Password complexity checker for big car rental company is set to insane mode
☑️ 30 char
☑️ symbols
☑️ numbers
☑️ upper & lower
❎ still 'too weak'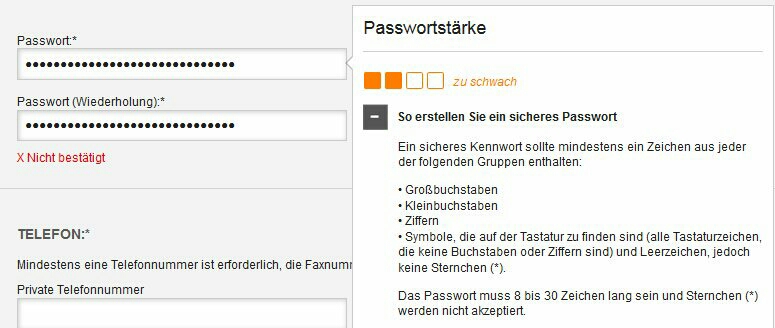 10
10 -
Working with a radio chip we selected because it had built-in encryption. Cannot make the encryption work, thus in contact with the manufacturer:
"- I cannot make the encryption work, it's like the chip doesn't want to take a key.
- which key do you use?
- does it matter?
- well yes, you can't just use any key!
- why not?
- you need to get an approved key from us.
- why is that?
- so that your competitors can't read your data!
- ...
- ...
- so the way to get working keys is to get them from you?
- of course!
- keys are 256 bits. Can we potentially use all of them?
- OF COURSE NOT!
- how many can we get from you?
- one! We reserve it from your company.
- are you telling me that all units within a company will need to have the exact same encryption key?
- yes!
- so anyone with our product could eavesdrop another same product?
- well yes, but it's all within your own products.
- ...
- ...
- that's not how encryption is supposed to work.
- but it's safe, your competitors cannot eavesdrop!
- I'm out of here."
(We finally found a satisfactory work-around, but i am still pissed at them)9 -
My boss wrote the password to access the office on his whiteboard, which you could see from outside of the building.3
-
Boot up a Linux live usb on a Windows machine, then rename cmd.exe to utilman.exe and after rebooting select accessibility options which now opens a command line and then 'net user username owned' to reset user 'username' password to 'owned'. Been using this for years..13
-
When you see a web service API accepting a SQL query in one of its JSON fields and the evil starts growing within you..
DROP ALL DATABASES
Just because you can! 4
4 -
Way to many...
- Passwords stored in plain text on the year 2014
- Not supporting HTTPS because to expensive
- Hidden admin URLS
- Databases available all over the internet
- Client Side validation
- IoT5 -
Humans!
The amount of sensitive, private, and secure information you can get just by asking someone for it is truly astounding.5 -
The best I have seen and exploited was years ago with a web shop that allowed me to set my own check-out price by just inspecting the element and setting the desired price. It just happily advanced to the next step where they invoked the payment provider with my custom price. Unfortunately the shop doesn't exist anymore. I have encountered many more security leaks but this one was so easy and lucrative to exploit.3
-
Ex-boss (who boasted 20 years of programming exp.) Would not let us work on a web project saying we didn't have enough experience and said he'd do it alone... Fast forward to 3 days before presenting to client, we get to check the log in interface and immediately find that there's no actual security, no validation... Just 2 text boxes with hard coded users and no way to add more without creating them in db... And if you knew the next page's URL you can actually skip the login... Needless to say he was removed from the project that instant and we (interns at the time) had to do everything from scratch. A 3 months project done in 2 days. Never been more stressed in my life :'(11
-
This one tops the pile for best ... err worst security feature.
<script type = "text/JavaScript">
If( userType != "admin" )
window.location.href = "http://www.example.com";
</script>
What could possibly go wrong?2 -
logger.info(String.Format(" User {0} changed their password from {1} to {2}", username, oldPassword, newPassword))
Production system. Plaintext log.10 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
// during testing, fortunately!
addresses = [
'user1@blah.com',
...
]
x=0
while ( x < addresses.length ) {
toEmail = addresses[x]
sendEmail ( toEmail )
// forget to increment x
}
// user1 not too happy4 -
$search = $_GET ['search'];
$table = $_GET ['table'];
$query= mysqli_query ("$search FROM $Table");
😲😲😢😢8 -
Once browsing through Google play store under what's new area of an app i found this:
*Removed bugs
*Added bugs to fix later6 -
My coworker shared account keys of Amazon aws on a public repo at Github. Took me around 3 days to find out and about 20 ec2 instances were created and running by a hacker...6
-
Not exactly a security bug, but there was a company that made a Django app for some internal work and later open sourced it. I was browsing through the code and I saw that the config file had an IP address and a hashed password for the database credentials
When I tried to use them, I was able to login directly to their read replica RDBMS, I had access to all their customer data (including phones & home addresses)
Being the saint I am, I informed them of the ignorance made by their developer and was presented with some cool swag.5 -
School online class system keeps track of every students' username and password. They are all accessible by typing passwords.txt after the address1
-
left a company over 3 years ago because they wanted me to dumb my code down so that the other devs could understand it. they wouldn't allow me to use classes in my code lol. anyway, 3+ years later figured I would try to log in to some of the admin panels... passwords still the same. MySQL dbs... passwords the same... cpanel... passwords the same. smh. even if I still worked there the passwords should be changed every so often. top notch security right there. funniest part is they don't even do backups or use VCS for the code. sad sad company. glad I'm no longer there. my personal projects have more security, redundancy and fail over lol4
-
I once ran into a CAPTCHA that was hard coded with a simple math problem. Every time it asked what 5 + 1 is.4
-
Just inherited a web application, worst security ever, all it does is call an unsecured application that does an active directory call, verifies the user name exists and then grants the role that the username is assigned. That is it oh and if you can find your way into the admin panel anyone can edit anyone else's role.
Come to find out this application got the dev who designed it a promotion to lead. 5
5 -
Password hashing using md5, it is 2016!! I have seen a sys admin update a user password using a MySQL query23
-
Boss insisted that verification link needs to be clicked from same IP address as account registration. Many arguments later, decision is final, we will ignore the numerous ways that this will be a burden to our users.
*Code code, test test, deploy*
We're getting a lot of traffic, we need this bitch to scale! *auto-scale and load balance all the things*
Account creation begins breaking at random, some people receiving the "Your IP address doesn't match" error. Look at login history table, what the shit... All recent logins coming from internal IP addressohfuckmylife need to look at X-Forwarded-For header for actual IP behind load balancer.
IP address matching feature stays. I am sad, drink away sadness.4 -
Many years ago at school the machines were imaged using Norton Ghost. A floppy disk containing Norton Ghost and it's configuration would be put into the machine, which would automatically start the imaging process.
When these floppy disks inevitably started erroring they'd be tossed into the rubbish bin. I grabbed one of these broken disks, inserted it a few times until my machine would recognise it, and hey presto, the config file along with the domain admin password were now visible.1 -
Sending a confirmation email to a newly created account with both the user name and password in the mail body.
See here for a list:
http://plaintextoffenders.com2 -
As someone who uses both Windows and MacOS, it's fucking impossible to type {} or $ on the first try. EVERY DAMN TIME I DO IT WRONG!11
-
public String getDbPasswd(){
try{
String dbPasswd = SomeInhouseEncryptionLib.getPasswd("/hard/coded/path/to/key");
return dbPasswd;
} catch(Exception e){
LOGGER.log(Level.SEVERE,e)
return "the-actual-password";
}
return null;
}
And this is now in production
FML3 -
Unencrypted, plain text passwords stored in SQL, from lowest role all the way up through Admin. In the same system, they had a "backdoor" password that would log in any user...
-
The "Change Password" function autofilled the old password. Dev told be it didn't matter because "if you set the field type to password you can't see it".4
-
Worst security issue : being able to make a money transfer with no auth and changing freely the bank account in the POST params...
Dev excuse : "I didn't know my job was also to take care about security."2 -
So, what have We learned in this week (wk25)?
There are two types of websites.
The Website, which allows setting passwords Like "123", and the Website that says that your firstname is too weak and must contain lowercase, uppercase letters, requires three or more Numbers and at least two Special characters. -
Whilst I was browsing the university website I came across a directory that allowed directory listings. Amongst all the .pl files was one named something.pl.old. Rather than interpreting the file the web server returned the raw source, including domain credentials for one of the network admins.1
-
In one of our webinterfaces you could swap between users once you logged in by changing the user in the link.
Not intended but our support is using this "feature" frequently because then they don't have to log in again when helping another client so it's not planned to be fixed4 -
So this is how they "teach" us in school...As a part time dev I was completely shocked when I saw this in our materials. What do you think? Should I drop the teachers tables to give him a lesson?
 14
14 -
If($password = $password2) {
//login
}
Keep in mind that password is the salted and hashed input and password2 is the Salter and hashed pw in the database...
Who needs passwords am I right?8 -
Where I work, the password needed to retrieve your paycheck in the system is your birthday. (Like November 3rd = 0311).
Guess it's no secrete how much money everyone makes?!
Oh... it's the passcode on our keycards as well!
The company has 2000+ employees and and makes more than $35 mil a year6 -
They added a javascript that checks the login info. Worst part an if statement was the only thing keeping you from logging in without the correct password
-
Massive payment gateway (not gonna say names) with more then 10k transactions / hour telling md5 is one of most secure encryptions they have. Only to made worse by the fact that they send the key and hashed key in the same request.
I am advising all our clients to change payment gateway asap if they use this one.1 -
I once found a MongoDB cluster open to the internet with no authentication with nearly a terabyte of data that backed a CRM service whose customers included Microsoft and Adobe to name a few.7
-
I hacked a browser game a few years ago for fun and the exploit I found and used was basically this:
<$php
$f = $_GET['f'];
$p = $_GET['p'];
$f($p);
So it was possible to pass a function and it's parameter in the URL to the server. The author used this to include() sub pages. I to highlight_file()s.2 -
Updating code for big client.
Find that they are not encrypting passwords in the database and are not sanitizing user input from forms.
Do not trust the user!2 -
So I worked in a company whose WiFi password was 1234567890 and they on the network they had a NAS that was not secured with the passwords to all the clients servers and online accounts on the root.
-
Well on my last full-time job, that ware using cookies for authentication (not something new, eh?). The thing is, you see, the cookies had the 'accountId' which if you change to another number, kaboom you're that account, oh but that was not all, there was an option to mark the account type in there 'accountType', which was kind of obvious in VLE (virtual learning environment), 'Teacher', 'Student', 'Manager' put what of those values and boom you are that role for the session
Thing was open of SQL injection from the login form, from said cookies and form every part you can pass input to it, when I raised the question to my TL he said 'no one is going to know about thatt, I don't see what is the problem', then escalated to higher management 'oh well speak to *tl_guy*'
Oh and bonus points for it being written in ASP CLASSIC in 2014+ (I was supposed to rewrite, but ended up patching ASP code and writing components in PHP)
In 2015-2016, in a private college, charging kind-of big money per year1 -
My predecessor used auth as a bool. The only way he kept basic users from accessing admin functions was by including the word "admin" or "user" in the URL so any user could be the administrator by just changing the URL parameters after logging in
For example, mysite.com/admin/editorderdetails vs. mysite.com/user/editorderdetails -
There is a red button in a briefcase that launches nukes if you got access code.
We then gave it to a emotionally unstable hothead.
Left a post-it with admin password inside briefcase.3 -
Siemens Step7 code block protection (PLC's).. It was designed to lock code that you don't want others to be able to read. All blocks are in a dbf file, so you just need to find the block record and uncomment one line, voila - source code available.
Given the massive use of Siemens PLC's on plants all over the world, and the simplicity of hacking via S7 protocol, usually Internet connected, it's a breeze to steal or modify the controllers code with possible critical implications.
Enter Stuxnet.1 -
Earlier this year I had to deploy an "emergency" fix to production for (luckily) an internal facing, but customer impacting, web application.
It was only the login page they were changing. I backed up the original, copied the new file into place, and marked my task complete.
Then I went and read the details on the incident. Someone discovered that if you supply ANY valid username and leave the password blank, you're in! Put the wrong password and you're blocked, of course. But blank? You must be legit!
Curious, I looked at the timestamp on the original file I had backed up to see how long it had been like this.
4 years.2 -
Since we are using the same password on all our servers (both QA and Production environment) my team somehow decided that it would be easier to copy the private SSH key for to ALL servers and add the public key to the authorized.keys file.
This way we SSH without password and easily add it to new servers, it also means that anyone who gets into one server can get to all of them.
I wasn't a fan of the same password on all servers, but this private key copying is just going against basic security principles.
Do they want rogue connections? Because that's how you get them.1 -
Probably the worst security I've ever seen is a website I used to visit that had their "Forgot your password?" system change the password of the account to the user's username and didn't even send an email confirmation before doing it.3
-
Work at a banking software company, one bug allowed bankers to book a deal after quote expired. So i could theoretically buy something at yesterday's rate. Dev forgot the "btnBook.enabled=false"5
-
A team at school spent 3-4months on an eStore web app, for selling items. The title was "Securing your eStore".
When they were done with their presentation, the examinator asked: "But... You haven't said a thing about the security part."
"Oh, sure we did, as we showed you, we added validation on the email address and credit card text fields etc. If you press the Pay button here, you will get an alert()-dialog telling you which fields are invalid..."2 -
Major state insurance provider, all past and current members data stored unencrypted (including SSN, date of birth, home address, etc.). All developers and contract developers had read access to it. Reported it, nothing was done. Reported it again in my exit interview. Was basically told they had intrusion detection systems in place so it was not an issue.4
-
Padlocked the router... no idea where the physical key was supposed to go to gain access to the network though cause I couldnt find a keyhole in my computer
 1
1 -
Client asked us to modify site made in some obscure CMS. Authentication on AJAX request is done by sending email and password as plaintext in header and then it would do md5 on server side5
-
I'm tasked with hacking a million dollar production machine and all the PLCs have the same password for the root user, which also happens to be the name of the company producing this shit....5
-
Using the Windows XP address book.......at a school.....for teachers details.....accessible to all students.
Then they wonder how the teachers were getting so many prank calls. -
Thought I'd share another one with you. Last year I saw a turorial posted on LinkedIn about how to create a captcha in ASP.NET. The turorial itself wasn't that bad but it made me laugh so hard because the writer thought of a neat way to input the desired captcha code to the handler that generated the image. Guess how? In the query string. That totally defeats its purpose. How on earth did he come up with that. So much for securing your form submission through captcha. Of course when I commented about it he didn't reply. I hope no one actually used that tutorial.2
-
When a university-wide mailing list system restricts posting to a list based solely on the From address... I was able to telnet port 25 from an outside server (so obviously no SPF either), pretend I'm admin@, and send a message to all students and staff...2
-
It's a tie between 3 things for me.
1. md5 hashed passwords
2. post variable concatenated into sql with no checks
3. admin login over http
sad thing is that all 3 was one website I redid a few years ago8 -
Student Account Password at the university. No changes the default. It's their DOB and first two letters of the name.
Injection steps:
Open Database ( I am the Placement Representative )
Copy DOB
Paste
Add the first two alphabet
Unlocked3 -
PHP Websites configuration data stored in _hidden/config.inc
Yep, that .inc extension made it world readable. 1
1 -
Tarball of source code from a big manufacturer served on their open src page...
They forgot to delete the .git subdir!
Private keys and signing tools for everybody!!!!
P.S It's fixed by now, don't get your hopes up :P1 -
Admin home page secured well, but every CRUD page available without admin authentication on prod environment... for at least 3 weeks
-
I've seen JavaScript client-side app that was connecting directly to DB using hardcoded (obfuscated, lol) DB password xD
And yes, there was no DB setting that this user is read-only and only from few tables. It was like GRANT * ON *. -
When a national organization leaves the administrator password on a tool that manages the entire IT Department to the default password.
Also when said default password is publicly documented, known by all trained administrators of this tool, and said tool is exposed to the Internet. -
My friend and i once found our school district's admin panel for everything related to networks in each and every school of the district...
-
Code in index.php: if(!isset($_COCKIE['access'] == '123') {
echo 'Denied'; die;
}
And then there was the access.php which set the cookie.
So you had to go to foo.com/access.php which displayed a white page and set the cookie. Then navigate back to foo.com for access2 -
Last year, one of our government organizations' websites' edit page was editable without login credentials... People can easily modify or even delete a company. They had a login functionality for employees and was pretty much useless.
-
I checked out this new hybrid app that was released by some local senior developers.
Turns out that on my user profile, my user ID is set as the value of a hidden field and changing it to any other user ID and saving the form will update the profile of that user. Including changing the password.
The password reset form also allows me to change the user ID to reset that user's password.
Speaking of passwords, the value of the password field on the profile is my actual password in plain text.
Yes, I said this app was released by a couple of "senior developers". One has over 15 years of experience and the other works at an IT company that builds online banking systems. They appear to have outsourced this side project to some other development team but... Come on. At least take one quick look at the source code before releasing it, why don't you?
I don't even...1 -
I committed my credentials and pushed to GitHub once. Took me a week to notice. Luckily it was just a personal project and no one noticed.
-
- Implemented oauth1 - no body hashing
- URL contains credentials in plain text
- Used Azure API management feature as a proxy of the our API, however the documentation was on the our API, thus exposing the API URL with no management to developers.
- easy resource DDoSing because each trial user got a DB, the registration process did not have bot checks. You could literally freeze the db instance by spamming registration requests. -
At my last place we launched a new payment page and added logging.
Who ever set the logging up didn't obfuscate the user card details and stored them in the db for anyone with access to see. :-O1 -
A hidden page that you enter a user name and it displays the encrypted and unencrypted versions of their password... It was quickly deleted after I stumbled across it. I assume it was to test a homemade encryption algorithm that wasn't worth much anyway, passwords shouldn't be reversible
-
Passwords are limited to 8 characters and stored in plain text. In the beginning of the year they give your password in a little piece of paper... I just gave up and started using my name as the password...
Found in the web portal used to buy school meals and consult card balance in Portugal (called GIAE). -
I know a doctor's practice which gives you your first name as a default password for your account. Watertight security for all these medical records :)
-
By changing a single query param any document could be downloaded. Been in production quite a while.1
-
Basic REST server authentication: pass a valid username in the URL of your request and you can publish trade and market data that's used by other systems.
I think they're moving to oAuth now but... These developers are slow and only do things when a gun (Sr. Management) is held to their heads. -
The worst bug?
Skipping a payment with 20 chars of js
System was in production like this for two year... -
Testing an application we were going to partner with. My colleague and I where able from the login screen to drop all databases including the system ones and use xp command to send email and access the server.1
-
Wouldn't call it a feature. More like worst practice. Data manager (and my boss at the time) kept using our website as a way to host large files 3rd party vendors/partners could download instead of using one of the many secure transfer methods out there to send them data. This was sometimes extremely sensitive data. No authentication or security that I could find. I went ballistic on him after seeing that.
-
This, thankfully, I didn't create myself. A shop I recently ordered something from had the worst username / password default combo.
After registration they gave you a default Password, your zip code. And your unchangeable username is your customer id, a five digit number which just increments for each new user. And because it is a shop which is only used by people of the same region there are maybe 10 different zip codes. -
My work's website being unsupported with Django security patches. I bring this up with management and say we should upgrade ASAP. Apparently that wasn't possible because the sysadmins refused to upgrade their old version of RedHat so we can't use anything that doesn't support Python 2.6.... To this day it still runs on Django 1.6.2
-
Some of our applications use a Java keystore that requires a password. The password is encrypted and stored in a database. The applications retrieve it when needed, decrypts it and uses it. The password is..... password
-
I'm currently a student in college. First semester of first year for the first 'real' programming course the school has offered, and we realized that they have told everyone to store their server login info in a connectvars.php file. 45 minutes and three tests later we had a script that was capable of outputting the username / password combo for any account on the schools server who had taken that course, ever.
-
There was a hidden input with the calculated price from the client. It was passed to the backend. It was not validated on the backend. The customer was charged that amount. It would have taken a long time to fix...
-
Steam hone number support. I lost my phone and forgot my number, and to change the number on the steam account, you need the old number.
-
One of the largest "modern" payment startup/service here in India has a password requirement of "8-15" characters. One Number and one character atleast. Doesnt support special characters. And did I mention it won't allow previous passwords.2
-
A team blacklisted a series of words in order to prevent XSS. Obviously they failed terribly. Like they filtered 'alert(' and crap like that. Like a hacker is going to alert stuff using xss. I opened a bug to their team.1
-
2016 and the passwords were stored in plain text. I pointed it out, they said they'll use md5 instead :/
PS: Ended up fixing it for them with HMAC-SHA256 -
No joke at my old shool computer system. We couldn't install anything on our accounts. As a joke I tried admin and no password. Didn't work. My friend pressed "q" with no password. Got a message "Totally not bloatware is now installing." Amazing.9
-
A download portal (paid, for GPL sourced software *ugh*) - checking by mail address, query:
email=mail@addr.com
... seems like php code was checking string equality by:
if query == valid_string
WORKED AROUND WITH:
email[]= in the http request
So, remember:
ALWAYS check with ===1 -
Public link to data of students, teachers, everyone. Address, mobile numbers, emails, parents numbers and more.
-
WEP security on a brand new wifi rollout. Do it for the legacy because no one knew the scanner gun (like target or walmart has) could operate on WPA Personal or even....802.1x Kerberos Security login. At least it was *something* but the whole place was on windows xp and server 2003.
It is 2016. Lets learn our technologies and read the manuals. -
In my beginning days I made a website with a login screen and no thoughts on the URL or browser history...
What a dumbass! -
One of our clients old CMS was completely hand written, allowed execution of PHP files in the uploads directory with an uploader that was publicly accessible, and the "security" was MD5 hashed passwords. Oh and the username/password for the admin user was password.
-
This moment if you are realizing that you are sitting since one hour in the waiting room of your doctor just to talk five minutes with him.1
-
When our app encounters an error, it shows an alert with an option to copy the error details to the clipboard, that includes the full stack trace, broadcasting to the world that we are coding in C#. Also, our page URLs show .aspx at the end, so anyone using it can see details of our implementation. Not exactly world-stopping since the desktop portal is only available on customer servers and the ipad app requires username/password AND pin authentication. But still....
-
Was working in an n-tier website, standard Web forms, BAL, DAL, database architecture. Validation and processing of data done in the BAL. Not the best idea, but whatever. Well apparently some developer thought it was too much work to pass his data through the BAL, so he directly accessed the DAL, performing zero validation on the data being passed in. Luckily, this was in a non-critical part of the site but the PM at the time nearly had a heart attack when I told him.
-
Token for App -> backend authentication is generated one time when the user signs up. Sniff it once and you've got access to the user account forever.
Passwords are hashed with one round of SHA1, no salt.
Everything including login data is sent over plain HTTP.
Luckily I got permission to fix that mess1 -
Security issues I encountered:
- Passwords stored as plain text until last year.
- Sensitive data over http until last year.
- Webservice without user/pass authentication. -
Token for App -> Backend communication was the username of the affected account. Wanna change anything you want for any user in the system? Just need their username and you're good to go.
-
A school computer system that didn't have any sort of boot protection, at all, like I was able to access certain files on the school system using a USB stick (course I didn't copy or look at them, that would just be unethical)
-
Released the product to customers without realising someone had pre-filled a production test accounted login at the login screen. Obviously it was used for testing purposes and the dev forgot to remove it before committing.
I loled when I found out about it, and some customers started to login and made transactions.
When I checked the commit history... It was under my name :/2 -
Security theater is not security.
I am still on my mother's cell plan. I pay for it, but she is the primary account holder. We are grandfathered into unlimited no restrictions data, and a new phone yearly, so yeah, not giving that up.
Anyway, when i go to the store to manage the account they say, 'sorry, Sarah needs to come in as the primary account holder.'
'I am sarah' I tell them. I am lying, they know I am lying, and they know I know.
But they have no choice but to go along. I even asked once; they are not allowed to ask for proof of id. I don't know why.
It's just security theater.1 -
Json host files of a whole server networks root server passwords under the webservers configs directory open to the public.
-
This weeks a joke right 😂, the recent day 0 Microsoft bug that allows anyone to get hacked, and allow someone to do whatever the hell they want.(as you can pretend to be any program on the computer)
Or the super user hack on Linux recently patched... Day 0....
The fact 80% of devs implement oauth incorrectly... So their user accounts are hackable...
Need I go on?1 -
Let's see:
No archival of data on a database server with over 5000 high profile customers using no encryption whatsoever with telnet open on LAN, every user on the same account in the office using the companies name as the password... But hey there are security cameras! -
Using memcpy() instead of copy_to_user() in a kernel module. One could overwrite kernel space memory, by passing a kernel space address as destination address.
-
The all too common passwords stored in clear text. When brought up with the developer they couldn't see the problem.
-
Once on a project the authentication request for a service was done... through http... with the username and password as parameter in the URL... in plain text
-
Does someone remember this update years ago in the magento community edition that added a file in the root web directory that just printed all database credentials to the browser?
-
Web application that you could read a file from UNIX. Problem, I'd you changed the URL, you could view any file, including any password file
-
Permissions service that allows users completely unknown to the system full access.
If you happen to be a known user, but just happen to hate being restricted, just remove the connection configuration on the client side, you get full permissions anyway. -
As back end developer, I rarely have hands on production environment. When it happens, I need to ask my way around and since the office is empty that day, I ask the client directly. They give me a URL. Right away, I ask the credentials.
"Just connect to the URL"
"You mean, you have an open access of this software, having critical information of more than 50 000 persons, to the web?"
*Silence* "hahaha it appears that way"
Thankfully, a tactful manager handled the situation astutely and we never heard about it anymore.
Don't we love all happy ending? -
Only last month I removed a file called 'statuspage.aspx', this file has been sat there for years on our customer sites.
The file did one simple query on the database to ensure connectivity, this query dumped the admin username and password to the page, no encryption.
Needless to say we rolled out ab emergency update... Not quite sure how that made it through QA! -
A "REST API" that was using nonsecured HTTP as protokoll and send the users pwd in the basic auth header
-
Passwordless Unix login leading to a console menu. You can then FTP in for free and remove ~/.login . Boom ! Shell access! And I already had a superuser access from another "dialog" asking to confirm a dangerous action with the superuser's password. Boom! Root access !!
-
Websites that have a password length limit that's way too short and/or don't allow symbols.
Example, I think EA has a password limit to 15 characters and doesn't allow spaces, underscores or even symbols, meaning that your password must be only letters and numbers, which is quite unsecure. -
The fact that the Wordfence plugin exists kind of admits to everyone WordPress is not very secure in the first place...
-
Whenever a site tells me the password I entered has already been used? I mean how are you supposed to know if you are salting and hashing the password.. Oh wait you probably just save it in plain text!! Please don't!!7
-
A controller action taking a string input and directly accessing the file system with it, returning the file.
-
Single Sign on Authentication for a growing product suite? Sure, just validate the user's credentials in the dashboard and then pass their role to the product's web app via query parameter. No need for tokens or an auth server!
-
HTML entities not handled on a social network site based on php...
that's you can post with a <script> and it will run when published.
Everybody with conn or access to the post will be affected1









