Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "how to be a hacker"
-
*Now that's what I call a Hacker*
MOTHER OF ALL AUTOMATIONS
This seems a long post. but you will definitely +1 the post after reading this.
xxx: OK, so, our build engineer has left for another company. The dude was literally living inside the terminal. You know, that type of a guy who loves Vim, creates diagrams in Dot and writes wiki-posts in Markdown... If something - anything - requires more than 90 seconds of his time, he writes a script to automate that.
xxx: So we're sitting here, looking through his, uhm, "legacy"
xxx: You're gonna love this
xxx: smack-my-bitch-up.sh - sends a text message "late at work" to his wife (apparently). Automatically picks reasons from an array of strings, randomly. Runs inside a cron-job. The job fires if there are active SSH-sessions on the server after 9pm with his login.
xxx: kumar-asshole.sh - scans the inbox for emails from "Kumar" (a DBA at our clients). Looks for keywords like "help", "trouble", "sorry" etc. If keywords are found - the script SSHes into the clients server and rolls back the staging database to the latest backup. Then sends a reply "no worries mate, be careful next time".
xxx: hangover.sh - another cron-job that is set to specific dates. Sends automated emails like "not feeling well/gonna work from home" etc. Adds a random "reason" from another predefined array of strings. Fires if there are no interactive sessions on the server at 8:45am.
xxx: (and the oscar goes to) fuckingcoffee.sh - this one waits exactly 17 seconds (!), then opens an SSH session to our coffee-machine (we had no frikin idea the coffee machine is on the network, runs linux and has SSHD up and running) and sends some weird gibberish to it. Looks binary. Turns out this thing starts brewing a mid-sized half-caf latte and waits another 24 (!) seconds before pouring it into a cup. The timing is exactly how long it takes to walk to the machine from the dudes desk.
xxx: holy sh*t I'm keeping those
Credit: http://bit.ly/1jcTuTT
The bash scripts weren't bogus, you can find his scripts on the this github URL:
https://github.com/narkoz/...56 -
Me: *Watching a movie*
Main Character: "Oh no, we have to hack the CIA to figure out how this machine works! Hacker girl, do the stuff"
Hacker Girl: "Consider it done!"
Hacker Girl: *Opens Linux bash*
Hacker Girl: *types 'mkdir Hack_CIA'
Hacker Girl: "They have two-factor authentication in place, this is going to be a hard one."
Hacker Girl: *Types 'cd Hack_CIA'*
Hacker Girl: "I'm in!"
Me: "..."
Friend: "Wow, so well done, so realistic!"
Me: *Dies*82 -
Today my classmate came up to me and said he was a hacker.
I told him to prove it, and guess what? HE ACTUALLY HACKED GOOGLE!
It was amazing! He impressed so many kids in the class with his skills of pressing F12! How impressive is that?
He even wore a black hoodie and can spell his name in binary code. Not to mention, he changed google doc's page color to black and the font to green as he typed his essay.
I need to be careful... This 1337 h4x0r is really scary.
83w4r349 -
I'm a self-taught 19-year-old programmer. Coding since 10, dropped out of high-school and got fist job at 15.
In the the early days I was extremely passionate, learning SICP, Algorithms, doing Haskell, C/C++, Rust, Assembly, writing toy compilers/interpreters, tweaking Gentoo/Arch. Even got a lambda tattoo on my arm after learning lambda-calculus and church numerals.
My first job - a company which raised $100,000 on kickstarter. The CEO was a dumb millionaire hippie, who was bored with his money, so he wanted to run a company even though he had no idea what he was doing. He used to talk about how he build our product, even tho he had 0 technical knowledge whatsoever. He was on news a few times which was pretty cringeworthy. The company had only 1 programmer (other than me) who was pretty decent.
We shipped the project, but soon we burned through kickstart money and the sales dried off. Instead of trying to aquire customers (or abandoning the project), boss kept looking for investors, which kept us afloat for an extra year.
Eventually the money dried up, and instead of closing gates, boss decreased our paychecks without our knowledge. He also converted us from full-time employees to "contractors" (also without our knowledge) so he wouldn't have to pay taxes for us. My paycheck decreased by 40% by I still stayed.
One day, I was trying to burn a USB drive, and I did "dd of=/dev/sda" instead of sdb, therefore wiping out our development server. They asked me to stay at company, but I turned in my resignation letter the next day (my highest ever post on reddit was in /r/TIFU).
Next, I found a job at a "finance" company. $50k/year as a 18-year-old. CEO was a good-looking smooth-talker who made few million bucks talking old people into giving him their retirement money.
He claimed he changed his ways, and was now trying to help average folks save money. So far I've been here 8 month and I do not see that happening. He forces me to do sketchy shit, that clearly doesn't have clients best interests in mind.
I am the only developer, and I quickly became a back-end and front-end ninja.
I switched the company infrastructure from shitty drag+drop website builder, WordPress and shitty Excel macros into a beautiful custom-written python back-end.
Little did I know, this company doesn't need a real programmer. I don't have clear requirements, I get unrealistic deadlines, and boss is too busy to even communicate what he wants from me.
Eventually I sold my soul. I switched parts of it to WordPress, because I was not given enough time to write custom code properly.
For latest project, I switched from using custom React/Material/Sass to using drag+drop TypeForms for surveys.
I used to be an extremist FLOSS Richard Stallman fanboy, but eventually I traded my morals, dreams and ideals for a paycheck. Hey, $50k is not bad, so maybe I shouldn't be complaining? :(
I got addicted to pot for 2 years. Recently I've gotten arrested, and it is honestly one of the best things that ever happened to me. Before I got arrested, I did some freelancing for a mugshot website. In un-related news, my mugshot dissapeared.
I have been sober for 2 month now, and my brain is finally coming back.
I know average developer hits a wall at around $80k, and then you have to either move into management or have your own business.
After getting sober, I realized that money isn't going to make me happy, and I don't want to manage people. I'm an old-school neck-beard hacker. My true passion is mathematics and physics. I don't want to glue bullshit libraries together.
I want to write real code, trace kernel bugs, optimize compilers. Albeit, I was boring in the wrong generation.
I've started studying real analysis, brushing up differential equations, and now trying to tackle machine learning and Neural Networks, and understanding the juicy math behind gradient descent.
I don't know what my plan is for the future, but I'll figure it out as long as I have my brain. Maybe I will continue making shitty forms and collect paycheck, while studying mathematics. Maybe I will figure out something else.
But I can't just let my brain rot while chasing money and impressing dumb bosses. If I wait until I get rich to do things I love, my brain will be too far gone at that point. I can't just sell myself out. I'm coming back to my roots.
I still feel like after experiencing industry and pot, I'm a shittier developer than I was at age 15. But my passion is slowly coming back.
Any suggestions from wise ol' neckbeards on how to proceed?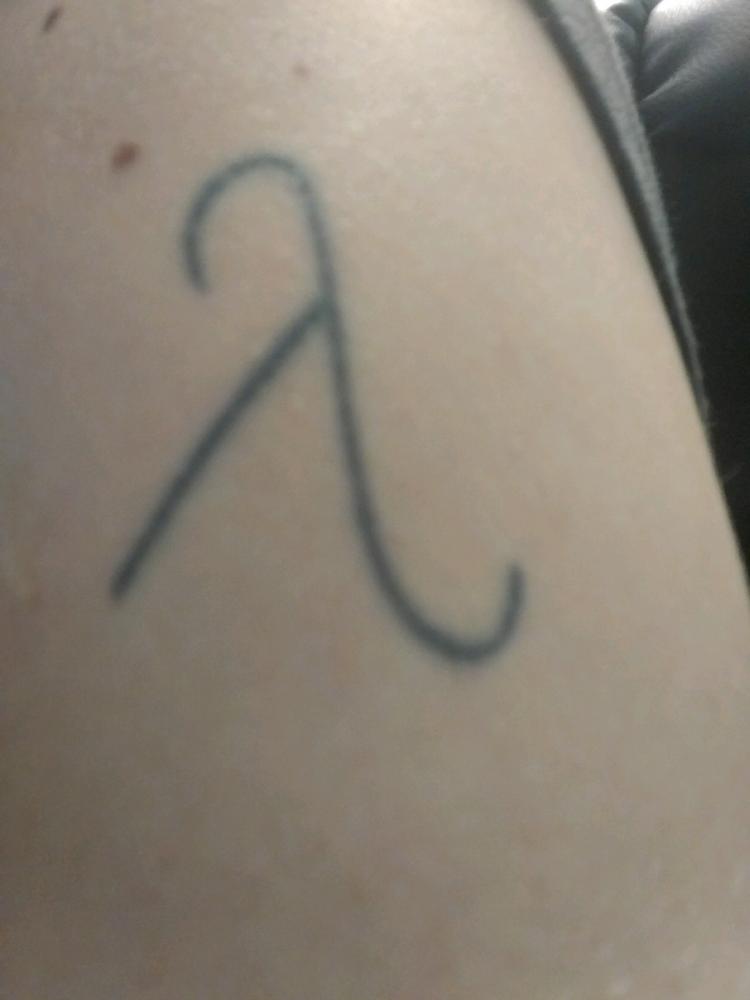 32
32 -
Anyone know this bitch hacker 127.0.0.1 story?
WORST HACKERS OF ALL TIME
CONTINUED IN THE COMMENTS BECUASE IT IS SO LONG...
TLdr bitch hacker hacks himself by localhost
bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> why do you kick me
<bitchchecker> can’t you discus normally
<bitchchecker> answer!
<Elch> we didn’t kick you
<Elch> you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
<bitchchecker> what ping man
<bitchchecker> the timing of my pc is right
<bitchchecker> i even have dst
<bitchchecker> you banned me
<bitchchecker> amit it you son of a bitch
<HopperHunter|afk> LOL
<HopperHunter|afk> shit you’re stupid, DST^^
<bitchchecker> shut your mouth WE HAVE DST!
<bitchchecker> for two weaks already
<bitchchecker> when you start your pc there is a message from windows that DST is applied.
<Elch> You’re a real computer expert
<bitchchecker> shut up i hack you
<Elch> ok, i’m quiet, hope you don’t show us how good a hacker you are
<bitchchecker> tell me your network number man then you’re dead
<Elch> Eh, it’s 129.0.0.1
<Elch> or maybe 127.0.0.1
<Elch> yes exactly that’s it: 127.0.0.1 I’m waiting for you great attack
<bitchchecker> in five minutes your hard drive is deleted
<Elch> Now I’m frightened
<bitchchecker> shut up you’ll be gone
<bitchchecker> i have a program where i enter your ip and you’re dead
<bitchchecker> say goodbye
<Elch> to whom?
<bitchchecker> to you man
<bitchchecker> buy buy
<Elch> I’m shivering thinking about such great Hack0rs like you
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> dude be happy my pc crashed otherwise you’d be gone
<Metanot> lol
<Elch> bitchchecker: Then try hacking me again… I still have the same IP: 127.0.0.1
<bitchchecker> you’re so stupid man
<bitchchecker> say buy buy
<Metanot> ah, [Please control your cussing] off
<bitchchecker> buy buy elch
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> elch you son of a bitch
<Metanot> bitchchecker how old are you?
<Elch> What’s up bitchchecker?
<bitchchecker> you have a frie wal
<bitchchecker> fire wall
<Elch> maybe, i don’t know
<bitchchecker> i’m 26
<Metanot> such behaviour with 26?
<Elch> how did you find out that I have a firewall?
<Metanot> tststs this is not very nice missy
<bitchchecker> because your gay fire wall directed my turn off signal back to me
<bitchchecker> be a man turn that shit off
<Elch> cool, didn’t know this was possible.
<bitchchecker> thn my virus destroys your pc man
<Metanot> are you hacking yourselves?
<Elch> yes bitchchecker is trying to hack me
<Metanot> he bitchchecker if you’re a hacker you have to get around a firewall even i can do that
<bitchchecker> yes man i hack the elch but the sucker has a fire wall the
<Metanot> what firewall do you have?
<bitchchecker> like a girl
<Metanot> firewall is normal a normal hacker has to be able to get past it…you girl
<He> Bitch give yourself a jackson and chill you’re letting them provoce you and give those little girls new material all the time
<bitchchecker> turn the firewall off then i send you a virus [Please control your cussing]er
<Elch> Noo
<Metanot> he bitchchecker why turn it off, you should turn it off
<bitchchecker> you’re afraid
<bitchchecker> i don’t wanna hack like this if he hides like a girl behind a fire wall
<bitchchecker> elch turn off your shit wall!
<Metanot> i wanted to say something about this, do you know the definition of hacking??? if he turns of the firewall that’s an invitation and that has nothing to do with hacking
<bitchchecker> shut up
<Metanot> lol
<bitchchecker> my grandma surfs with fire wall
<bitchchecker> and you suckers think you’re cool and don’t dare going into the internet without a fire wall
<Elch> bitchchecker, a collegue showed me how to turn the firewall off. Now you can try again
<Metanot> bitchhacker can’t hack
<Black<TdV>> nice play on words
<bitchchecker> wort man
<Elch> bitchchecker: I’m still waiting for your attack!
<Metanot> how many times again he is no hacker
<bitchchecker> man do you want a virus
<bitchchecker> tell me your ip and it deletes your hard drive
<Metanot> lol ne give it up i’m a hacker myself and i know how hackers behave and i can tell you 100.00% you’re no hacker..29 -
I was 15 years old and the first year of high school. Everything was new to me and I was such a newbie. At that time I had 2-3 year of programming behind me at an institution where they taught competitive programming. And I knew something about computers. Not much but more than most of my school mates. At that time I wanted to become "super cool hacker".
So we had this very very thought teacher for history which was also our form master. She really knows how to explained everything about history and in an interesting way. But while she was teaching we also had to write down notes from her powerpoints that were on a projector. And occasionally she would wait for us to copy everything and then move on with her lecture. But sometimes she didn't. This was frustrating as hell. The whole class would complain about this because you couldn't take notes down normal, you had to do it at double speed.
But she got one weak spot. She was not very good with computers. Our school computers were locked in some kinda closet so that students didn't have physical access to a computer and were also password protected. So I came up with the plan to plant wireless mouse in her computer so that I could control her mouse. At that time it seemed like SUPER HACKER MASTER PLAN.
So I got an opportunity one time when she left the classroom and let closet where the computer was open. I quickly sneaked the USB of the wireless mouse in the computer and then go back to the seat.
So THE FUN began.
Firstly I would only go back in powerpoint so that all my schoolmates could write down notes including me. And it was hilarious to watch when she didn't know what is happening. So then I would move her mouse when she tried to close some window. I would just move it slightly so she wouldn't notice that somebody else is controlling mouse. And by missing X button just by slight she would click other things and other things would pop up and now she had to close this thing so it became a nightmare for her. And she would become angry at the mouse and start complaining how the computer doesn't work and that mouse doesn't obey her.
One time when she didn't pay attention to her computer and projector I went to paint program and drew a heart and wrote we love you (In Slovenian Imamo vas radi -> See the picture below) and one of my school mates has the picture of it. We were all giggling and she didn't know what is was for. And I managed to close everything before she even noticed.
So it got to the point where she couldn't hand it more so she called our school IT guy so that he would check her computer (2 or 3 weeks passed before she called IT guy). And he didn't find anything. He was really crappy IT guy in general. So one week passed by and I still had messed with her mouse. So she got a replacement computer. Who would guessed all the problems went away (because I didn't have another mouse like that). I guess when our IT guy took the computer to his room and really thoroughly check it he found my USB.
So he told her what was the problem she was so pissed off really I didn't see her pissed off so much in all my 4 years in high school. She demanded the apology from whom did it. And at that moment my mind went through all possible scenarios... And the most likely one was that I was going to be expelled... And I didn't have the balls to say that I did it and I was too afraid... Thanks to God nobody from my school mates didn't tell that it was me.
While she waited that somebody would come forward there was one moment when our looks met and at that moment both of us knew that I was the one that did it.
Next day the whole class wrote the apology letter and she accepted it. But for the rest of 4 years whenever was there a problem with the computer I had to fixed it and she didn't trust anybody not even our IT guy at school. It was our unwritten contract that I would repair her computer to pay off my sin that I did. And she once even trusted me with her personal laptop.
So to end this story I have really high respect for her because she is a great teacher and great persons that guide me through my teen years. And we stayed in contact. 11
11 -
I hate how people think that to be a "hacker" or hacking is this special job title. lol. Hacking is just using something in a way in which it was not intended to be used.
So pretty much think ...anal sex.
There. Now many people are "hackers"6 -
My words to live by...
Another one got caught today, it's all over the papers. "Teenager
Arrested in Computer Crime Scandal", "Hacker Arrested after Bank Tampering"...
Damn kids. They're all alike.
But did you, in your three-piece psychology and 1950's technobrain,
ever take a look behind the eyes of the hacker? Did you ever wonder what
made him tick, what forces shaped him, what may have molded him?
I am a hacker, enter my world...
Mine is a world that begins with school... I'm smarter than most of
the other kids, this crap they teach us bores me...
Damn underachiever. They're all alike.
I'm in junior high or high school. I've listened to teachers explain
for the fifteenth time how to reduce a fraction. I understand it. "No, Ms.
Smith, I didn't show my work. I did it in my head..."
Damn kid. Probably copied it. They're all alike.
I made a discovery today. I found a computer. Wait a second, this is
cool. It does what I want it to. If it makes a mistake, it's because I
screwed it up. Not because it doesn't like me...
Or feels threatened by me...
Or thinks I'm a smart ass...
Or doesn't like teaching and shouldn't be here...
Damn kid. All he does is play games. They're all alike.
And then it happened... a door opened to a world... rushing through
the phone line like heroin through an addict's veins, an electronic pulse is
sent out, a refuge from the day-to-day incompetencies is sought... a board is
found.
"This is it... this is where I belong..."
I know everyone here... even if I've never met them, never talked to
them, may never hear from them again... I know you all...
Damn kid. Tying up the phone line again. They're all alike...
You bet your ass we're all alike... we've been spoon-fed baby food at
school when we hungered for steak... the bits of meat that you did let slip
through were pre-chewed and tasteless. We've been dominated by sadists, or
ignored by the apathetic. The few that had something to teach found us will-
ing pupils, but those few are like drops of water in the desert.
This is our world now... the world of the electron and the switch, the
beauty of the baud. We make use of a service already existing without paying
for what could be dirt-cheap if it wasn't run by profiteering gluttons, and
you call us criminals. We explore... and you call us criminals. We seek
after knowledge... and you call us criminals. We exist without skin color,
without nationality, without religious bias... and you call us criminals.
You build atomic bombs, you wage wars, you murder, cheat, and lie to us
and try to make us believe it's for our own good, yet we're the criminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is
that of judging people by what they say and think, not what they look like.
My crime is that of outsmarting you, something that you will never forgive me
for.
I am a hacker, and this is my manifesto. You may stop this individual,
but you can't stop us all... after all, we're all alike.
+++The Mentor+++9 -
!Story
The day I became the 400 pound Chinese hacker 4chan.
I built this front-end solution for a client (but behind a back end login), and we get on the line with some fancy European team who will handle penetration testing for the client as we are nearing dev completion.
They seem... pretty confident in themselves, and pretty disrespectful to the LAMP environment, and make the client worry even though it's behind a login the project is still vulnerable. No idea why the client hired an uppity .NET house to test a LAMP app. I don't even bother asking these questions anymore...
And worse, they insist we allow them to scrape for vulnerabilities BEHIND the server side login. As though a user was already compromised.
So, I know I want to fuck with them. and I sit around and smoke some weed and just let this issue marinate around in my crazy ass brain for a bit. Trying to think of a way I can obfuscate all this localStorage and what it's doing... And then, inspiration strikes.
I know this library for compressing JSON. I only use it when localStorage space gets tight, and this project was only storing a few k to localStorage... so compression was unnecessary, but what the hell. Problem: it would be obvious from exposed source that it was being called.
After a little more thought, I decide to override the addslashes and stripslashes functions and to do the compression/decompression from within those overrides.
I then minify the whole thing and stash it in the minified jquery file.
So, what LOOKS from exposed client side code to be a simple addslashes ends up compressing the JSON before putting it in localStorage. And what LOOKS like a stripslashes decompresses.
Now, the compression does some bit math that frankly is over my head, but the practical result is if you output the data compressed, it looks like mandarin and random characters. As a result, everything that can be seen in dev tools looks like the image.
So we GIVE the penetration team login credentials... they log in and start trying to crack it.
I sit and wait. Grinning as fuck.
Not even an hour goes by and they call an emergency meeting. I can barely contain laughter.
We get my PM and me and then several guys from their team on the line. They share screen and show the dev tools.
"We think you may have been compromised by a Chinese hacker!"
I mute and then die my ass off. Holy shit this is maybe the best thing I've ever done.
My PM, who has seen me use the JSON compression technique before and knows exactly whats up starts telling them about it so they don't freak out. And finally I unmute and manage a, "Guys... I'm standing right here." between gasped laughter.
If only it was more common to use video in these calls because I WISH I could have seen their faces.
Anyway, they calmed their attitude down, we told them how to decompress the localStorage, and then they still didn't find jack shit because i'm a fucking badass and even after we gave them keys to the login and gave them keys to my secret localStorage it only led to AWS Cognito protected async calls.
Anyway, that's the story of how I became a "Chinese hacker" and made a room full of penetration testers look like morons with a (reasonably) simple JS trick. 9
9 -
Hire a Bitcoin Recovery Expert Solution: Best Crypto Recovery services | Captain WebGenesis
CAPTAIN WEBGENESIS stands out as an ideal cryptocurrency recovery expert, renowned for his exceptional proficiency in navigating the intricate realm of digital assets. With an impressive track record of successfully retrieving lost, stolen, or inaccessible cryptocurrencies, CAPTAIN WEBGENESIS has earned the trust of numerous individuals and organizations seeking to retrieve their valuable digital possessions.
How can I recover my stolen bitcoin from an investment scam?
What is the best recovery company to help me recover my stolen Bitcoins?
How to Hire a Hacker to Recover Stolen Crypto/Bitcoin?
Can a hacked crypto be recovered?
How can I recover my lost cryptocurrency within 24 hours?101 -
Fresh internship story/conversation (Part 1)
Happened today:
- "Can you hack someone via cmd?"-cheap coworker at my internship workplace
- "Can you hack the NSA from any device?"-cheap coworker
- "Can the police identify me, if my face is on a Youtube video?"-cheap coworker
- "I can see all devices I have been through when I want to connect to a target as a route.
*talks about hops in a trace route, but uses non-technical terms for it*
*uses "ping host wikihow.com" instead of "tracert wikihow.com" to demonstrate it, besides of that "host" was not supposed to be there in that command*
*he had to google how to use the ping command on Windows*
*finally uses the ping command properly*
"Here, you can see all the devices our machine has connected to to reach the target"
ME: Aha. But dude... you know that all these ip adresses are in fact the same ip. These IPs are not any different. They are all the same. Besides of that this IP is the IP of this *points to domain name on windows cli* domain.
Him: Oh... I had a friend named ... *continues telling me some "hacker stories" from his past*
Me: *ignores him and always just responds with "Aha" to him* -cheap coworker
Happened yesterday:
- "You have programming classes? You must be an expert in Excel then, right?" -internship boss3 -
One Thursday noon,
operation manager: (looking at mobile)what the.....something is wrong i am getting bunch of emails about orders getting confirmed.
Colleague dev: (checks the main email where it gets all email sent/received) holy shit all of our clients getting confirmation email for orders which were already cancelled/incomplete.
Me: imediately contacting bluehost support, asking them to down the server so just that we can stopp it, 600+ emails were already sent and people keep getting it.
*calls head of IT* telling the situation because he's not in the office atm.
CEO: wtf is happening with my business, is it a hacker?
*so we have a intrusion somebody messed the site with a script or something*
All of us(dev) sits on the code finding the vulnerabilities , trying to track the issue that how somebody was able to do that.
*After an hour*
So we have gone through almost easch function written in the code which could possibly cause that but unable to find anything which could break it.
Head asking op when did you started getting it actually?
Op: right after 12 pm.
*an other hour passes*
Head: (checking the logs) so right after the last commit, site got updated too?. And....and.....wtf what da hell who wrote this shit in last commit?
* this fuckin query is missing damn where clause* 🤬
Me: me 😰
*long pause, everyone looking at me and i couldn't look at anyone*
The shame and me that how can i do that.
Head: so its you not any intrudor 😡
Further investigating, what the holy mother of #_/&;=568 why cronjob doesn't check how old the order is. Why why why.
(So basically this happened, because of that query all cancelled/incomplete orders got updated damage done already, helping it the cronjob running on all of them sending clients email and with that function some other values got updated too, inshort the whole db is fucked up.)
and now they know who did it as well.
*Head after some time cooling down, asked me the solution for the mess i create*
Me: i took backup just couple of days before i can restore that with a script and can do manual stuff for the recent 2 days. ( operation manager was already calling people and apologising from our side )
Head: okay do it now.
Me: *in panic* wrote a script to restore the records ( checking what i wrote 100000000 times now ), ran...tested...all working...restored the data.
after that wrote an apology email, because of me staff had to work alot and it becomes so hectic just because of me.
* at the end of the day CEO, head, staff accepted apology and asked me to be careful next time, so it actually teached me a lesson and i always always try to be more careful now especially with quries. People are really good here so that's how it goes* 🙂2 -
It all started in the year 2013.
I was 13 years old back then. I was a fan of Minecraft and so I learned how to setup a bukkit server and ran it. Installing plugins was fun, because I could be a "hacker" and change the configs.
After a while, (~2014), when I was in the 9th grade of elementary school, I saw Unity. A free game engine. Of course, me being a 14 year old I was intrigued and so I downloaded it, made an account and a new project. I had absolutely ZERO knowledge of programming. Didn't even know what languages existed, so i resorted to presets and poorly put together characters + weapons.
After some time fiddling around with Unity, I've gotten a hang of the basics (not programming related).
My actual programming started when I started High School (year 2016). It's a computer engineering school and for the first part of the year, I've learned from my teacher in C# (Console.WriteLine/ReadLine/Loops/Variables). At the second semester I started to gain interest and motivation to program at home. I did the programs we made in school (random number guessing game) but better. Improved it, added colors.
After that, I started developing in Unity - Actually learning something and having the ability to develop something all by myself. It keeps driving me on. In the second year (the year I'm visiting right now) I tought myself HTML, CSS, JavaScript, jQuery, PHP. I'm very happy and also can't wait to discover and learn new things in these languages!
My latest project was an Android application for my father that he asked for (it calculated the price of the 3D print he would make).
// Sorry for the long post!
EDIT: Forgot to add a fun little detail. All my classmates make fun of me because I program so much !
Also: Tabs > Spaces8 -
I have teens in my classroom who want elite hacker status but complain about doing programming exercises outside of class. >.<
I explain to them that learning to code takes a lot of practice and can be frustrating at first. Some still went to the dean complaining that my class is tough. I work at a private school where open communication is encouraged and social justice is a thing.
So, I'm over here like "How do I reach these kids?"
I'm optimistic and I try different approaches to teaching and learning. Some stuff has worked. A lot haven't.
I figure I'd ask here: Does anyone have a suggestion for any creative programming exercises/projects that are beginner-friendly, legal, and hacker-ish? (I teach intro to Java.)22 -
It has been bugging the shit out of me lately... the sheer number of shit-tier "programmers" that have been climbing out of the woodwork the last few years.
I'm not trying to come across as elitist or "holier than thou", but it's getting ridiculous and annoying. Even on here, you have people who "only do frontend development" or some other lame ass shit-stain of an excuse.
When I first started learning programming (PHP was my first language), it wasn't because I wanted to be a programmer. I used to be a member (my account is still there, in fact) of "HackThisSite", back when I was about 12 years old. After hanging out long enough, I got the hint that the best hackers are, in essence, programmers.
Want to learn how to do SQL injection? Learn SQL - write a program that uses an SQL database, and ask yourself how you would exploit your own software.
Want to reverse engineer the network protocol of some proprietary software? Learn TCP/IP - write a TCP/IP packet filter.
Back then, a programmer and a hacker were very much one in the same. Nowadays, some kid can download Python, write a "hello, world" program and they're halfway to freelancing or whatever.
It's rare to find a programmer - a REAL programmer, one who knows how the systems he develops for better than the back of his hand.
These days, I find people want the instant gratification that these simpler languages provide. You don't need to understand how virtual memory works, hell many people don't even really understand C/C++ pointers - and that's BASIC SHIT right there.
Put another way, would you want to take your car to a brake mechanic that doesn't understand how brakes work? I sure as hell wouldn't.
Watching these "programmers" out there who don't have a fucking clue how the code they write does what it does, is like watching a grown man walk around with a kid's toolbox full or plastic toys calling himself a mechanic. (I like cars, ok?!)
*sigh*
Python, AngularJS, Bootstrap, etc. They're all tools and they have their merits. But god fucking dammit, they're not the ONLY damn tools that matter. Stop making excuses *not* to learn something, Mr."IOnlyDoFrontEnd".
Coding ain't Lego's, fuckers.36 -
At a point in your life, you'll settle down abit, and you start to think about what you've done in the past (idk) years of your life.
Then you think about your career, how everything is ever since you discovered you were good at a certain thing since highschool.
be it programing, writing random codes, pentesting (or if you had that "hacker" phase in your life) or fixing laptops and etc.
"Good"
You think about the word, and you had a thought: You only know how to do it, how it works, how its done, and how to do it.
You only "Know", it takes practice, patience, dedication and years (or months depends on you) of experience before you can really say for sure you're "Good" at it.
Me? Im no where near good. but that doesn't stop me from going there.
And i hope the same goes for you. You can do it,
Have a great day.3 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
Most kids just want to code. So they see "Computer Science" and think "How to be a hacker in 6 weeks". Then they face some super simple algebra and freak out, eventually flunking out with the excuse that "uni only presents overtly theoretical shit nobody ever uses in real life".
They could hardly be more wrong, of course. Ignore calculus and complexity theory and you will max out on efficiency soon enough. Skip operating systems, compilers and language theory and you can only ever aspire to be a script kiddie.
You can't become a "data scientist" without statistics. And you can never grow to be even a mediocre one without solid basic research and physics training.
Hack, I've optimized literal millions of dollars out of cloud expenses by choosing the best processors for my stack, and weeks later got myself schooled (on devRant, of all places!) over my ignorance of their inner workings. And I have a MSc degree. Learning never stops.
So, to improve CS experience in uni? Tear down students expectations, and boil out the "I just wanna code!" kiddies to boot camps. Some of them will be back to learn the science. The rest will peak at age 33.16 -
So, stranger things season 2, Bob is hacking a system with BASIC, writing entire lines with one keyboard press. Such skill. Much wow.
Have I missed something lately? xD10 -
How to Hire the Best Crypto Recovery Expert - CONSULT OMEGA CRYPTO RECOVERY SPECIALIST
In the ever-evolving landscape of cryptocurrency, the risk of losing funds due to various factors such as hacking, scams, or simple human error is a growing concern for investors. In such precarious situations, the choice of a reliable and experienced crypto recovery specialist becomes paramount. One such standout in America is OMEGA CRYPTO RECOVERY SPECIALIST, renowned for its expertise, high success rate, and satisfied client testimonials.
How can I recover my stolen bitcoin from an investment scam?
What is the best recovery company to help me recover my stolen Bitcoins?
How to Hire a Hacker to Recover Stolen Crypto/Bitcoin?
Can a hacked crypto be recovered? Yes, Go to OMEGA CRYPTO RECOVERY
Best Cryptocurrency Recovery Company
Webpage (omegarecoveryspecialist .c om
Contact Mail; omegaCryptos@consultant .c om
SMS or Call: +1 (701, 660 (04 7594 -
I'm curious, how did you all start to like programming?
Mine was when I was in grade 7 or 8, which is around 13 years old. I watched a movie called "Hackers", Angelina Jolie was in this one (I think, it was a long time). I was curious on how to be a hacker, then I googled and found an article which said something about learning to code.
I wasn't sure I would enjoy it at first but after a while, I started enjoying that thrill you get when you solve that pesky little bug that took you days to get rid of. Haven't stopped learning more about programming and computers since.7 -
watching the online course for CEH... dude used the Death Star as a tangible example of how exploits work.
IDK if I should love it for the nerdiness, or be slightly sad that someone needs that type of example of what a vulnerability vs an exploit is, when they're going for the Certified Ethical Hacker certification...
Might be better in an introduction to Network Security class?
Also, while discussing the security, usability, and functionality triangle, he reference the Staples "Easy Button" - does one thing, not very secure, and not very functional (in that it has more than one function)...1 -
At the institute I did my PhD everyone had to take some role apart from research to keep the infrastructure running. My part was admin for the Linux workstations and supporting the admin of the calculation cluster we had (about 11 machines with 8 cores each... hot shit at the time).
At some point the university had some euros of budget left that had to be spent so the institute decided to buy a shiny new NAS system for the cluster.
I wasn't really involved with the stuff, I was just the replacement admin so everything was handled by the main admin.
A few months on and the cluster starts behaving ... weird. Huge CPU loads, lots of network traffic. No one really knows what's going on. At some point I discover a process on one of the compute nodes that apparently receives commands from an IRC server in the UK... OK code red, we've been hacked.
First thing we needed to find out was how they had broken in, so we looked at the logs of the compute nodes. There was nothing obvious, but the fact that each compute node had its own public IP address and was reachable from all over the world certainly didn't help.
A few hours of poking around not really knowing what I'm looking for, I resort to a TCPDUMP to find whether there is any actor on the network that I might have overlooked. And indeed I found an IP adress that I couldn't match with any of the machines.
Long story short: It was the new NAS box. Our main admin didn't care about the new box, because it was set up by an external company. The guy from the external company didn't care, because he thought he was working on a compute cluster that is sealed off behind some uber-restrictive firewall.
So our shiny new NAS system, filled to the brink with confidential research data, (and also as it turns out a lot of login credentials) was sitting there with its quaint little default config and a DHCP-assigned public IP adress, waiting for the next best rookie hacker to try U:admin/P:admin to take it over.
Looking back this could have gotten a lot worse and we were extremely lucky that these guys either didn't know what they had there or didn't care. -
Saw this sent into a Discord chat today:
"Warning, look out for a Discord user by the name of "shaian" with the tag #2974. He is going around sending friend requests to random Discord users, and those who accept his friend requests will have their accounts DDoSed and their groups exposed with the members inside it becoming a victim as well. Spread the word and send this to as many discord servers as you can. If you see this user, DO NOT accept his friend request and immediately block him. Discord is currently working on it. SEND THIS TO ALL THE SERVERS YOU ARE IN. This is IMPORTANT: Do not accept a friend request from shaian#2974. He is a hacker.
Tell everyone on your friends list because if somebody on your list adds one of them, they'll be on your list too. They will figure out your personal computer's IP and address, so copy & paste this message where ever you can. He is going around sending friend requests to random discord users, and those who accept his requests will have their accounts and their IP Addresses revealed to him. Spread the word and send this to as many discord servers as you can. If you see this user, DO NOT accept his friend request and immediately block him. Saw this somewhere"
I was so angry I typed up an entire feature-length rant about it (just wanted to share my anger):
"1. Unless they have access to Discord data centres or third-party data centres storing Discord user information I doubt they can obtain the IP just by sending friend requests.
2. Judging by the wording, for example, 'copy & paste this message where ever you can' and 'Spread the word and send this to as many discord servers as you can. If you see this user, DO NOT accept his friend request and immediately block him.' this is most likely BS, prob just someone pissed off at that user and is trying to ruin their reputation etc.. Sentences equivalent to 'spread the word' are literally everywhere in this wall of text.
3. So what if you block the user? You don't even have their user ID, they can change their username and discrim if they want. Also, are you assuming they won't create any alts?
4. Accounts DDoSed? Does the creator of this wall of text even understand what that means? Wouldn't it be more likely that 'shaian' will be DDoSing your computer rather than your Discord account? How would the account even be DDoSed? Does that mean DDoSing Discord's servers themselves?
5. If 'shaian' really had access to Discord's information, they wouldn't need to send friend requests in order to 'DDoS accounts'. Why whould they need to friend you? It doesn't make sense. If they already had access to Discord user IP addresses, they won't even have to interact with the users themselves. Although you could argue that they are trolling and want to get to know the victim first or smth, that would just be inefficient and pointless. If they were DDoSing lots of users it would be a waste of time and resources.
6. The phrase 'Saw this somewhere' at the end just makes it worse. There is absolutely no proof/evidence of any kind provided, let along witnesses.
How do you expect me to believe this copypasta BS scam? This is like that 'Discord will be shutting down' scam a while back.
Why do people even believe this? Do you just blindly follow what others are doing and without thinking, copy and paste random walls of text?
Spreading this false information is pointless and harmful. It only provides benefits to whoever started this whole thing, trying to bring down whoever 'shaian' is.
I don't think people who copy & paste this sort of stuff are ready to use the internet yet.
Would you really believe everything people on the internet tell you?
You would probably say 'no'.
Then why copy & paste this? Do you have a reason?
Or is it 'just because of 'spread the word''?
I'm just sick of seeing people reposting this sort of stuff
People who send this are probably like the people who click 'Yes' to allow an app to make changes in the User Account Control window without reading the information about the publisher's certificate, or the people who click 'Agree' without actually reading the terms and conditions."8 -
HOW TO FIND A LEGITIMATE CRYPTO RECOVERY EXPERT; HIRE iFORCE HACKER RECOVERY
iForce Hacker Recovery saved me from cryptocurrency scammers
I was scammed by a Stock investment after I talked and was convinced by this Russian guy that I sent him money via the website. I almost lost everything. But for the timely intervention of this iForce Hacker Recovery Team who just kick-off on time got back my $474,000 worth of stock investments. They are really good at what they do, I have recommended this iForce Hacker Recovery Team to a couple of friends and co-workers who all became satisfied customers. The iForce Hacker Recovery Team has helped me a lot. I'm glad and happy to recover my money, there is no shame in becoming a scam victim of one of these sophisticated and predatory operations. By reporting you may be able to recover some or all of your lost funds and prevent the scammers from targeting others. To recover your Scammed funds.18 -
When I was in 11th class, my school got a new setup for the school PCs. Instead of just resetting them every time they are shut down (to a state in which it contained a virus, great) and having shared files on a network drive (where everyone could delete anything), they used iServ. Apparently many schools started using that around that time, I heard many bad things about it, not only from my school.
Since school is sh*t and I had nothing better to do in computer class (they never taught us anything new anyway), I experimented with it. My main target was the storage limit. Logins on the school PCs were made with domain accounts, which also logged you in with the iServ account, then the user folder was synchronised with the iServ server. The storage limit there was given as 200MB or something of that order. To have some dummy files, I downloaded every program from portableapps.com, that was an easy way to get a lot of data without much manual effort. Then I copied that folder, which was located on the desktop, and pasted it onto the desktop. Then I took all of that and duplicated it again. And again and again and again... I watched the amount increate, 170MB, 180, 190, 200, I got a mail saying that my storage is full, 210, 220, 230, ... It just kept filling up with absolutely zero consequences.
At some point I started using the web interface to copy the files, which had even more interesting side effects: Apparently, while the server was copying huge amounts of files to itself, nobody in the entire iServ system could log in, neither on the web interface, nor on the PCs. But I didn't notice that at first, I thought just my account was busy and of course I didn't expect it to be this badly programmed that a single copy operation could lock the entire system. I was told later, but at that point the headmaster had already called in someone from the actual police, because they thought I had hacked into whatever. He basically said "don't do again pls" and left again. In the meantime, a teacher had told me to delete the files until a certain date, but he locked my account way earlier so that I couldn't even do it.
Btw, I now own a Minecraft account of which I can never change the security questions or reset the password, because the mail address doesn't exist anymore and I have no more contact to the person who gave it to me. I got that account as a price because I made the best program in a project week about Java, which greatly showed how much the computer classes helped the students learn programming: Of the ~20 students, only one other person actually had a program at the end of the challenge and it was something like hello world. I had translated a TI Basic program for approximating fractions from decimal numbers to Java.
The big irony about sending the police to me as the 1337_h4x0r: A classmate actually tried to hack into the server. He even managed to make it send a mail from someone else's account, as far as I know. And he found a way to put a file into any account, which he shortly considered to use to put a shutdown command into autostart. But of course, I must be the great hacker.3 -
Today I woke up from this craziest dream.
We were in France and there was a younger Mike Patton (who was french) speaking and apparently teaching french to an African girl.
The next scene he's in the back seat of what's apparently a taxi, and brags about how perfectly he can speak English. Besides that I see him playing the guitar.
In the last moments of the dream, however - and confusingly - the song Rusty Cage by SoundGarden starts playing loudly in the background. And that's when I found Patton is also a hacker.
Thinking about this part of the dream minutes aftger waking up, I found it to be the funniest, though not the craziest thing I ever dreamed.
Whereas I tried for hours to edit the configuration files of a tractor demolition game (some sort of Vigilante 8, but with tractors), he gets angry on a lady for an reason unknown to me, and in his moment of rage, manages to jump her houses' fence, surprisingly to edit her /etc/resolv.conf file - as if it was the most evil deed in the world.
In this final part, with Rusty Cage still playing very loudly, I find out me and my sister where watching this scene on TV (apparently patton was also an actor). After that, I comment to my sister in a grave tone: "Well, this guy is dangerous, maybe she should build a higher fence".
Then I wake up.
Although a crazy dream, it clearly addresses the fact I sometimes try to be a lot of things at the same time, and how this overwhelms me...1 -
Is this a technological metaphor?
For some Hacker challenge I was reading up on different keyboard layouts, Dvorak and stuff. And the technological lock in is baffling me: The rationale for qwerty was to reduce jamming of the typewriter letter arms. Today that doesn't make sense anymore, yet we stick to it. Wondering how much of today's tech is dragged down by things like that.
This stuff often also makes me weary of the first decisions, like choosing a protocol or data base - its kind and layout, because we might be stuck with it for reasons of backwards compatibility.... Like when Microsoft opted for the backslash as a directory separator..25 -
Hello, world!
Okay, guys and gals... I need your creative minds. I need a concept for sort of a property manager for my game.. I have an idea of my own, feel free to tear it apart or throw it out the window.
So basically.. You'll no longer have one Computer System (and you wont instantly hit the login screen for that System on startup) Instead, you'll have a lot of things. They will probably only be represented using text and menu's (likely no 3D or 2D environments or anything.. Though, a setup like News Tycoon would be epic, but I think that would be too much for this game.) You'll basically start off with a small space (probably a basement) with x amount of free space. In that space, you'll need to add things like a desk, chair, and a laptop, or tower + monitor. You can also buy things like server rigs with a ton of space, but those are pricy and bulky. Each item costs X amount and takes up X amount of space. Also, you'll need a desk for a monitor (or multiples..) and other things.. (Like your rubber duck collection ;P JK) You can also rent and manage servers. (renting is more exspensive in the long run, but things on your server are not on your property. But, if you own a server on your property you can rent space to to NPCs) As well as manage your devices, properties, stocks, etc..
Also, there will be in-game time. Depending on how "comfortable" you are will determine how long you can stay up in a day. In-game events will take place later on at specific times so staying up (or not..) will need to be managed well. Especially if you're being targeted by a rival (NPC) hacker.5 -
So recently i got a message from aa person asking how to (these are exact words) ,
:break into insta's database using Sqlmap"
I then proceeded to tell them to "f*ck of ya c*nt ".
Afterwords it inspired me to write this rant
annoying classmates:" hahaha GuYS bEtER wAtcH OuT he's GonnaA hack Us"
me: " yea I can program I also do some ethical hacking and cybersecurity "
annoying classmates: "hahaH Bro your a Hacker OhHHhHHOOO BrO CaN yoU hACk inSta FoR mE I NEEd MoRe FolloWeRs "
me:" tf no one that's illegal and two it's waste of my time "
annoying classmates: "BrOooo CaN yoU gEt Me SoMe HacKs fOr CsGo"
me: "can you just please f*ck off , i'm not hacking for you everything you've asked me is extremely unethical and a huge waste of time, Also if you suck so bad at a game you need to cheat I recommend just stopping "
annoying classmates: "DUdE whAt ToolS dO i HVAE to DownLOad To Be A haCkEr"
me: *trying hard not to murder them* " I told you to f*ck off"
being a hackers isn't downloading tools it isn't typing at 90wpm into a terminal with green font its not about games or fame or anything its about coming up with creative solutions to problems , thinking outside the box its about individuality and breaking from the heard , looking at things from a different viewpoint,
it's about endlessly seeking knowledge.
It's about freedom though creation that's what being a hacker originally was. But because of big media and movie company's (and script kiddies) people now confuse hacker with cracker and think of us as jobless fat kids sitting in a dark room in there parents house breaking into bank accounts and buying drugs on the dark web (which people see to think there a hacker just because they can open tor browser. they then proceed to use google to look up "fresh onion links 2020") .
My classmates and really my generation has a huge case of smooth brain. They a think we can just look at someone and hack them they also seem to think using a gratify link to get a persons up is hacking and using the inspect element is hacking and that opening a terminal is hacking ! AHHHHHHHHHHHHHHHHHHHHH"
Anyways ima end this here thanks for reading :)5 -
I think another intriguing job asides programming is engineering (*for some*). A week has past and I've been on the hike assisting my beloved brother on his contracted engineering job while I am less occupied. The job is based on 🗼Tower analysis and It's quite risky as you'd have to climb up to 56 meters high just to take readings of antennas, and fix some other stuffs. The only thing I find intriguing about this job is his love for it, funny enough he also thinks I love the job too and I guess I'm guilty for his thoughts (*Sorry bro, I love the job for you not me*).
With my little experience so far on my *new brotherly job* I noticed the most hectic task isn't going up and down the tower taking readings but at the end of all operations, he'll have to gather the values and snapshots he took while on the tower to prepare reports on msword & excel for the other buttwags at the office (or home I guess)
then archive and sends via mail. Seeing this lengthy process I was forced to ask why he wasn't using any reporting tool like Jotforms or any other equivalent and I was willing to look up some recommendations for him, his reply was: "I'm already used to this form of reporting, its what I was trained with and what the company provided, nevertheless a friend of mine suggested something of such weeks back but I would have to pay monthly fee for its usage which is quite on the high side and I don't think I'd prefer that."
Sounds convincing but not enough, okay here is another deal: You use an android phone right? and at my office we work on system automation (*basically does not know what I do for a living probably thinks I'm a hacker the illegal one*), how about i design you an android app for you to capture the tower data and a PC software for you to auto generate the msword & excel reports, I can get this ready for you in less than 5 nights (*I've got less task on my desk, and was willing to take the timeout to prepare the solution that he needed, all I needed to hear for a kick start was an "Okay" just to be sure he wants it*) I suggested and re-assured but up to this point he still declined my offer and is willing to stick with his current reporting pattern (*Me died*).1 -
I think I have a hacker on my network taking over devices at random and doing stuff while users are logged in and watching. I’m not as up-to-date on this security stuff as I used to be. Running Windows, Mac, and iOS. Any suggestions how I can detect and cut off take-overs like this?
-
I started thinking on how ML can help in hacking but before that I got another doubt on how you can be a effective hacker and started looking into all ways of being a hacker but later convinced myself that hacking is not just a tuxedo jacket to wear it's more of you watching duncrick movie multiple times and understanding what exactly the movie all about so any leads for resources to cultivate that mind set of being a hacker and any links/material to follow and practise would be of great help1
-
Someone didn’t properly set the httpcookies domain for our staging and production websites. Yep, this was a C#/.NET site. The cookie domain for the staging site was set to the production domain instead of the staging domain (which was a subdomain). So if someone logged into the staging admin, that would also grant them access to production admin if they also had an account in the production site.
The staging site technically had an additional login to enter the site, but the username and password weren’t too hard to guess. It was like that for years until I was hired to be an in-house dev (the role was previously outsourced to a software development company).
The admin side of the website wasn’t very sophisticated. But there was enough personal identifying info for a hacker to do something with.
I don’t know how they weren’t hacked yet. Honestly, I’d tell my employer to go back to that software agency and ask for a refund and cite the shotty work.1 -
When a script kiddie doesn't know how to run a python script and calls himself a hacker ( hax0r to be precise ) * inserts a jesus facepalm pic *
-
How do you transfer text from one machine ( laptop ) to another ( phone ) with no common tools ( Firefox Send spat out a long string of characters that I had no way of transferring either ) on either? Basically a clipboard sync.
There used to be this online notepad at notepad.cc, but that tool is gone away now.
How do you do it hacker-style? `wall`!
- SSH into the same same server from both machines ( this also assumes you have Termux or some equivalent tool for your phone )
- use `wall` to broadcast message from source
- copy broadcast at destination
- done31 -
Since i was little i always wanted to amaze my friends with something. Back then it was magic, then it was music and now it's programming. Please don't kill me but i remember looking at hackers and stuff and seeing how they could remotely control other people's computers and i just wanted to learn that so i looked it up on google and found a post somewhere saying that if you're a hacker and don't even know basic html then you're not a hacker so i decided to learn html. Not so long has passed and i still want to be a developer so i am trying to learn javascript and then start moving to heavier languages. No one i know codes and i'm really alone so if i can simply make something cool with javascript they will be amazed, in the end that's all i want.
-
Best Hacker To Recover USDT Coin From Online Scam,Consult Betafort Recovery Company
One of the best decisions I ever made was to contract Betafort Recovery, to help me resolve my challenges with a foreign investment company.The team successfully traced and recovered my initial capital investment. Still, unfortunately, the profits I believed to be mine were just a numbers game thus the reason why a payout wasn’t happening. All in all, I am very grateful to this team, their profound support saved me from destruction. Involving superior enforcement is what changed everything, the team revealed the scammer’s whole game plan upon consultation and I was never going to get paid no matter how much I invested. They made my problems theirs and handled my case diligently. I can’t believe the honesty and integrity I experienced in dealing with this company and its team of excellent hackers. There was no sales pitch, just straight-up advice on what they do, and kept constant contact with me as they continued to fight to recover my funds. Staff-wise; every single staff I spoke with was very professional, friendly, respectful, and honest in explaining stuff to you. They restored my financial dignity and status. I with a heartbeat will recommend to anyone who has issues in their respective financial ventures and now experiencing some unforeseen difficulties in regaining possession of their funds to contact this great recovery company Betafort Recovery Via Google , or on Telegram via @Betafort , You will not regret it. It will be the best decision you will make in life. Restore your financial dignity and status one more time. Give yourself a second chance regardless of how bad or difficult you think your case might be, The Betafort Recovery Team has your back, trust me.
Whatsapp OR Signal: +17126004729 -
How do I prepare for a tech interview at top companies one year from now?
I'll be pursuing master's in CS from this august and want to prepare myself accordingly. I have a decent understanding of algorithms and data structure. Although I can solve problems at my work easily, I am still worried about my inability to solve medium - difficult hacker rank problems. -
Hire the Best Hacker At Mighty Hacker Recovery.
It was a normal morning when I realized my wallet was missing. Panic immediately set in as I frantically searched through my apartment, hoping to find it tucked away somewhere. But it was nowhere to be found. I retraced my steps from the previous day, but the wallet was still missing. I knew I had to act fast. My wallet contained my pharse key, which gave me access to my cryptocurrency wallet. And in that wallet, I had 4.8 million AUD worth of cryptocurrency. It was a fortune that I had worked hard for, and I couldn't afford to lose it. As I sat on my couch, racking my brain for any clues or leads, my phone rang. It was an unknown number. I hesitated to answer, but something told me to pick up. And I'm glad I did because on the other end was a representative from Mighty Hacker Recovery. At first, I was skeptical. How did they know about my missing wallet? But they assured me that they had a team of skilled hackers who could help me recover it. They explained that my wallet's pharse key was encrypted and that only a skilled hacker could access it. With nothing to lose, I agreed to meet with them. They were professional and had a wealth of knowledge about cryptocurrency. They assured me that they would do everything in their power to recover my wallet. And they did. After days of hard work and numerous attempts, they finally cracked the encryption and retrieved my pharse key. I couldn't believe it. I was overjoyed and grateful beyond words. I couldn't thank them enough. Thanks to Mighty Hacker Recovery, I was able to access my wallet and retrieve my 4.8 million AUD worth of cryptocurrency. They saved me from a financial disaster, and I will forever be grateful to them. I couldn't believe how lucky I was to have crossed paths with them. They were truly a team of mighty hackers, and their skills were unmatched. I made sure to spread the word about their services, and I even saved their number on my phone, just in case. From that day on, I made sure to keep my pharse key safe and secure, knowing that Mighty Hacker Recovery was just a phone call away if I ever needed them again. And I was at peace, knowing that my fortune was in safe hands. WhatsApp +1 845 699 5044.
-
HIRE A PROFESSIONAL BITCOIN HACKER\FOLKWIN EXPERT RECOVERY\TO RECOVER ALL YOUR LOST.
What does it mean to be a hero? For me, being a hero is about stepping in when all hope seems lost, taking control when others cannot, and making a difference in someone’s darkest hour. That’s exactly what Folkwin Expert Recovery did for my family when my father, the breadwinner and cornerstone of our lives, had a major stroke at the age of 65.
My father had always been sharp, focused, and in control of everything—especially when it came to his finances. He had invested early in Bitcoin and built up an impressive portfolio worth $400,000. But after his stroke, everything changed. He lost his ability to manage even the simplest tasks, including operating his Bitcoin wallets or email. It was devastating to watch this once strong, intelligent man now unable to remember the recovery phrases he had so carefully stored.
As the family gathered around him, hoping for his recovery, the reality set in—he was the only one who knew how to access his cryptocurrency holdings. My father had never shared his recovery phrases, and now with him unable to function cognitively, we were locked out of his wallets. That $400,000 in Bitcoin was our family’s financial security, and without access to it, we were facing a very uncertain future.
In my desperation, I started searching for help online and came across Folkwin Expert Recovery. They seemed like the lifeline we desperately needed. After explaining our situation—how my father could no longer access his wallets or even remember where his recovery phrases were stored—the team at Folkwin Expert Recovery responded quickly and professionally. Their confidence and calm approach immediately reassured me that we weren’t alone in this struggle.
The team at Folkwin Expert Recovery worked tirelessly, using their expertise to help trace the digital pathways and regain access to my father’s cryptocurrency wallets. I cannot express the relief I felt when they were able to recover the $400,000 worth of Bitcoin that my father had locked away. It was nothing short of miraculous.
But more than just recovering our family’s financial future, Folkwin Expert Recovery also became a source of education and empowerment. They showed us how to better manage and secure our digital assets moving forward. Their guidance on storing recovery phrases, using two-factor authentication, and setting up secure backup systems was invaluable, ensuring we would never face a situation like this again.
This experience taught me what it means to be a hero. Folkwin Expert Recovery stepped in when our family needed them the most, giving us not only financial security but also the peace of mind that comes with knowing our assets are safe. They were the heroes in our time of need, and I am forever grateful for their expertise and compassion.
Thanks to Folkwin Expert Recovery, my father’s legacy and financial contributions will continue to support our family, even as we navigate this new chapter in our lives. They helped us when we thought all was lost, and I cannot thank them enough for their incredible work. For assistance, CONTACT INFO! (Email): Folkwinexpertrecovery @ tech-center (.)com Or (Telegram): @Folkwin_expert_recovery . God is too faithful to fail,
Regards,
Julius D Helene.
-
I need a hacker to assist me recover my lost Crypto / Contact Captain WebGenesis
Captain WebGenesis stands out as a leader among bitcoin recovery services, by maintaining integrity and trust with each client they assist in navigating challenging procedures with assurance and expertise. His vast knowledge of asset recovery, legal assistance, crypto tracing, and customer satisfaction distinguishes them as a pioneer in the field. Captain WebGenesis, which was established by a group of professionals in Crypto recovery, digital forensics, and cybersecurity, has quickly earned itself a strong reputation within the cryptocurrency space for providing trustworthy facts and reviews.
I need a hacker to assist me recover my lost crypto || Consult Captain WebGenesis I NEED A HACKER TO RECOVER MY LOST BITCOIN/ CAPTAIN WEBGENESIS..
Can bitcoin lost to scammers or hackers be recovered? Yes with Captain WebGenesis
What is the best recovery company that can help me recover my lost Bitcoin - Captain WebGenesis is Highly recommended.
CONSULT A LICENSED HACKER TO RECOVER YOUR LOST CRYPTO. || Hire a hacker to Recover your Stolen Cryptocurrency / Captain WebGenesis
Trusted Crypto recovery specialist, CAPTAIN WEBGENESIS offers assistance and analysis in recovering stolen cryptocurrency.
How to hire a hacker to recover stolen bitcoin. || I NEED A HACKER TO RECOVER MY LOST CRYPTO / USDT - Visit CAPTAIN WEBGENESIS
I need a hacker to assist me recover my lost crypto - Go to Captain WebGenesis
If you need assistance recovering lost cryptocurrency, Captain WebGenesis is a trusted service that specializes in recovering stolen or lost crypto
I NEED A HACKER TO RECOVER MY LOST CRYPTO
How can I recover my stolen Bitcoin || How to recover lost cryptocurrency || Crypto Scam Recovery Services || Bitcoin Recovery Expert || Ethical crypto hacker
Has anyone recovered stolen crypto || How to recover stolen cryptocurrency ||How to recover stolen cryptocurrency || How do I recover stolen BTC, crypto, and other coins3 -
How to Hire a Hacker to Recover Stolen Crypto & Bitcoin - Call Ultimate Hacker Jerry
I can't wait to tell you about my amazing experience working with Ultimate Hacker Jerry, a recovery firm. I put $550,000 into a fraudulent venture. following their victimization. I didn't know whether I would ever see my hard-earned money again, which was why I was upset. I'm glad I looked up Ultimate Hacker Jerry on Google since he was able to assist me in getting my Bitcoin back. I will always be grateful to Ultimate Hacker Jerry for helping me get my lost cryptocurrency back.
I never would have thought it was possible to recover cryptocurrency. I urge anyone who finds themselves in a similar situation to contact Ultimate Hacker Jerry. -
RECOVER BTC AND MONEY SENT TO SCAMMERS HIRE A HACKER TECHNOCRATE RECOVERY
When my cryptocurrency wallet was suddenly emptied, leaving me with a loss of $145,000, I was engulfed in shock and disbelief. The devastation was compounded when I uncovered the truth: my ex-girlfriend, whom I had recently discovered was unfaithful, was behind the theft. The realization that someone I once trusted had betrayed me so deeply was crushing. The emotional turmoil left me desperate for a solution, so I began searching for recovery services. During this search, I came across a Telegram group where someone recommended TECHNOCRATE RECOVERY. Their glowing reviews provided a glimmer of hope, and reaching out to them turned out to be a pivotal decision. From our very first conversation, TECHNOCRATE RECOVERY exhibited a level of professionalism that immediately reassured me. They didn’t just sympathize—they acted, quickly launching an investigation into how the theft occurred. Knowing that this betrayal came from someone close to me, their careful, methodical approach was exactly what I needed. They were meticulous in their investigation, tailoring their efforts to the unique aspects of my case, which was vital given the complexities of cryptocurrency recovery. Their team was both knowledgeable and empathetic, fully understanding the emotional weight of my situation. Throughout the process, I experienced an emotional roller coaster. The initial despair slowly gave way to hope as the team at TECHNOCRATE RECOVERY consistently communicated with me. They were transparent, explaining each step in a way that was easy to understand, which helped alleviate some of the anxiety I felt. Their regular updates were a lifeline, ensuring I was never left in the dark about the progress being made. Their ability to break down complex technical details into something manageable was a testament to their commitment to client care. TECHNOCRATE RECOVERY’s use of advanced forensic tools and blockchain expertise was nothing short of impressive. They tracked the movement of my stolen assets with precision, leaving no avenue unexplored. I was particularly impressed by their collaboration with other experts and law enforcement when necessary, demonstrating their dedication to recovering my funds. Their transparent fee structure was another standout feature. While many services charge hefty fees or demand significant upfront payments, TECHNOCRATE RECOVERY provided a clear breakdown of costs from the outset. This transparency built trust, making the financial aspect of the process far less stressful. Their focus on results over profit was evident and greatly appreciated. Ultimately, TECHNOCRATE RECOVERY successfully recovered all my stolen assets, bringing a sense of closure to this painful chapter. But what truly set them apart was their post-recovery support. They provided invaluable advice on securing my cryptocurrency wallet against future threats, arming me with the knowledge I needed to prevent such a breach from happening again. If you ever find yourself in a similar situation, know that there’s a way back from the brink. TECHNOCRATE RECOVERY isn’t just a service—they’re a lifeline, guiding you through the darkest moments and helping you regain control over what you thought was lost forever.
Web Info: ww w.technocraterecove ry.site
Contact Email: technocratrecovery (@) contractor. net -
HOW DO I RECOVER MY LOST FUNDS FROM SCAMMERS HAIRE ULTIMATE HACKER JERRY
What is the process to get my stolen Bitcoin back? What steps should I take to get my stolen Bitcoin back? Could a lost cryptocurrency be discovered again? Employ a hacker (Nft) to retrieve lost or stolen bitcoin. I can't get into my USDT account; it appears that I was hacked. Expert Bitcoin Recovery Is Required. Cryptocurrency Scam Recovery Get Lost Money Back An error happened with a cryptocurrency investment. How Hiring A Hacker Can Help You Get Rid Of Stolen Crypto Coins All scam victims are now receiving their money back with the help of Ultimate Hacker Jerry. Inform him of your circumstances by getting in touch with him; he will help you with any demands related to recovering from cryptocurrency scams, including Bitcoin and investment schemes. -
Recover Scammed Bitcoin, and Money Lost to fake trading
Imagine falling victim to a phishing attack and losing your hard-earned cryptocurrency. In this case study, we'll take you through the journey of how this guru ADRIAN LAMO HACKER successfully retrieved the stolen funds, leaving the cybercriminals scratching their heads. A hacked online wallet can be a terrifying situation, but fear not, for ADRIAN LAMO HACKER is here to save the day. Locked out of your digital asset exchange account with your funds seemingly out of reach? Don't despair! ADRIAN LAMO HACKER gurus have the keys to unlock even the most stubborn accounts. I'll walk you through the process of how ADRIAN LAMO HACKER helped a client regain access to their account and regain control of their digital assets. ADRIAN LAMO HACKER stands out from other web recovery services due to the expertise and knowledge of their gurus. The team is well-versed in the intricacies of retrieving misplaced online currency, backed by years of experience in the field. Additionally, ADRIAN LAMO HACKER prioritizes security and confidentiality, ensuring that your personal information remains protected throughout the recovery process. ADRIAN LAMO HACKER specializes in the recovery of a wide range of online currencies, including cryptocurrencies like Bitcoin, Ethereum, and Litecoin. They also have the expertise to assist with recovering funds from online wallets, investment platforms, and digital asset exchanges. No matter the type of online currency you've misplaced, ADRIAN LAMO HACKER has the skills to help you retrieve it. With a solid plan in place, the team will swing into action, implementing the recovery strategies that have been tailored to your specific case. Their gurus will use their wizard-like skills to navigate the intricate web of online currency systems, working tirelessly to restore what was lost. Recovering misplaced online currency can be a process that requires patience. But fear not, for this gurus will be with you every step of the way. They'll diligently monitor the progress of your case, providing regular updates and offering guidance as needed. Their goal is to ensure that no stone is left unturned until your lost funds are safely back in your virtual wallet. Reach out to ADRIAN LAMO HACKER now by email: Adrianlamo @ consultant . com
-
HOW TO HIRE A HACKER TO RECOVER SCAMMED CRYPTO HIRE ADWARE RECOVERY SPECIALIST
The journey towards recovering lost or stolen cryptocurrency can often feel like a perilous trial, fraught with uncertainty and the ever-present risk of falling victim to malicious scams. Website info: https ://adware recovery specialist. com
This was the experience I faced when I found myself in the midst of an Ethereum (ETH) recovery ordeal, navigating a maze of false promises and deceptive tactics. WhatsApp info:+12723 328 343
Just when hope seemed to dwindle, a glimmer of light emerged in the form of ADWARE RECOVERY SPECIALIST, a service that would prove instrumental in guiding me through the treacherous waters of crypto recovery. What began as a straightforward attempt to reclaim my rightful ETH holdings quickly descended into a disheartening encounter with a sophisticated hoax. Seemingly legitimate recovery "experts" emerged from the shadows, offering their services and assurances of a swift and successful resolution. Lured by their convincing rhetoric and the prospect of regaining my lost assets, I entrusted them with sensitive information, only to watch helplessly as they vanished into the digital ether, taking my ETH with them. Email info: Adwarerecoveryspecialist@ auctioneer. net The emotional toll of this betrayal was immense, as I grappled with the realization that my efforts had been thwarted by unscrupulous individuals exploiting the vulnerabilities of the crypto landscape. Just when I had resigned myself to the possibility of a permanent loss, I discovered ADWARE RECOVERY SPECIALIST, a service that would ultimately prove to be my salvation. Unlike the charlatan recovery "experts" I had encountered, ADWARE RECOVERY SPECIALIST approached my case with a level of professionalism, empathy, and unwavering commitment that restored my faith in the recovery process. Through their meticulous investigations, cutting-edge techniques, and dogged determination, they were able to trace the path of my stolen ETH and orchestrate its safe return to my rightful possession. The trial of recovery had been arduous, marked by setbacks and the constant threat of further exploitation. Yet, with the steadfast support of ADWARE RECOVERY SPECIALIST, I emerged from this ordeal with a renewed appreciation for the resilience of the human spirit and the power of legitimate, ethical service providers to navigate the complex and often treacherous world of cryptocurrency recovery. Telegram info: https ://t.me/adware recovery specialist1 This experience has forever shaped my understanding of the crypto ecosystem and the importance of exercising caution and discernment when seeking assistance in such matters. To anyone facing the same heart-wrenching situation, don't waste any more time or money on companies that are only interested in making empty promises. ADWARE RECOVERY SPECIALIST stands as a beacon of professionalism in a field often riddled with scams. Their efforts are genuine, their expertise is unmatched, and their results speak for themselves. Thanks to them, my ETH is back where it belongs, and I couldn’t be more grateful.2 -
HOW TO REVENGE ON A CHEATING BOYFRIEND
Revenge is a dish best served cold. When someone cheats on you, you understandably want to lash out and get back at them. Of course, the most logical way is moving on but it really doesn’t hurt to snoop around and find out how their affair started and how it is fairing on. Yes, spying on the lovers. I opted to use a hacker who helped me spy on my ex even without having to install a spyware on his phone. I got the hacker’s email from a review about a husband who spied on his cheating wife. The email is maestroencrypter (@) financier (.) com. It may not be a conventional way of dealing with break ups but spying gave me closure and the motivation to better myself. The guy also has a WhatsApp number +12348023971 -
Hello everyone! I’m Kate Oliver by name a mother of two, and I'm going to share with you all how I got scammed after falling victim to a cryptocurrency investment scam, it all started on the Telegram App when i got added on a Cryptocurrency investment group, then i was following up the informations on the group i noticed some group members actually confirms that they got paid by the platform which they did drop some kind of receipt of them being credited, Well guess they were able to convince me through that.. i never knew that they were all scammers i was meant to believe that my investment is secured and safe with the platform and after investing all my life savings, i got denied every chance to make a withdrawal of my funds when it was due for withdrawal, they swindled me off a sum of $764,000 worth of crypto. It was the saddest moment of my life because I couldn't believe what had happened, I was bankrupt and my credit was damaged. I reported to the authorities and there was nothing they could do to get these scammers or return my money. I thought all hope was lost and was going into depression until I came across an article online about a hacker who could help me recover my funds, at first I thought it was impossible to do that but I realize I had no other choice but to give it a try, to my surprise R O O T K I TS R E C O V E RY F IR M was able to recover all my funds back to my account, i was totally amazed by this team Professional service and i want to put this out there for anyone who might be going through the same situation and have been swindled by this scammers, you can contact R O O T K I TS R E C O V E RY F I R M to help you recover your lost funds. Contact them at ( ROOTKITS 4 @ G MA I L . COM ) and on Telegram; ROOTKITS71
-
HPOW TO HIRE A HACKER TO RECOVER STOLEN BITCOIN, CONTACT FASTFUND RECOVERY.
One of the best decisions I ever made was to contract Fastfund Recovery, to help me resolve my challenges with a foreign investment company. Long story short, the team successfully traced and recovered my initial capital investment. Still, unfortunately, the profits I believed to be mine were just a numbers game thus the reason why a payout wasn’t happening. All in all, I am very grateful to this team, their profound support saved me from destruction. Involving superior enforcement is what changed everything, the team revealed the scammer’s whole game plan upon consultation and I was never going to get paid no matter how much I invested. They made my problems theirs and handled my case diligently. I can’t believe the honesty and integrity I experienced in dealing with this company and its team of excellent hackers. There was no sales pitch, just straight-up advice on what they do, and kept constant contact with me as they continued to fight to recover my funds. Staff-wise; every single staff I spoke with was very professional, friendly, respectful, and honest in explaining stuff to you. They restored my financial dignity and status. I with a heartbeat will recommend to anyone who has issues in their respective financial ventures and now experiencing some unforeseen difficulties in regaining possession of their funds to contact this great recovery company “ Fastfund Recovery “ on Email: Fastfundrecovery8 (at)Gmail dot com, or on Telegram via fastfundsrecovery, You will not regret it. It will be the best decision you will make in life. Restore your financial dignity and status one more time. Give yourself a second chance regardless of how bad or difficult you think your case might be, The Fastfund Recovery Team has your back, trust me.
Official website: Fastfundrecovery com -
How do I Recover Scammed Cryptocurrency – Consult THE HACK ANGELS.
The significance of seeking professional help in recovering scammed cryptocurrency cannot be overstated. Hiring a professional hacker like THE HACK ANGELS offers numerous benefits, including specialized expertise in cryptocurrency recovery techniques.THE HACK ANGELS possess a deep understanding of blockchain technology and the intricacies of cryptocurrency transactions, enabling them to navigate the complexities of recovering lost funds effectively.Contact Below;
Whats Ap; +1 520) - 200, 23 20 ) , Mail Box; support@thehackangels. com
Web: thehackangels. com -
RECOVER SCAMMED CRYPTO BY CONTACTING MUYERN TRUST HACKER
I was scammed of USD 459,800 by a fraudulent mining pool, and I want to share my experience to help others avoid similar situations. I initially attempted to withdraw USD 100,000 from my account with this mining pool. They informed me that a 5% tax needed to be paid to the Japan Tax Bureau before the withdrawal could proceed. Trusting their instructions, I sent them USD 22,990. However, after the payment, they informed me that, because I was at the VIP stage (having funds of USD 200,000 or more), I could only withdraw a minimum amount of USD 200,000. They insisted that I could not withdraw less, despite my initial request. Under their pressure, I sent an additional USD 20,000, believing this would resolve the issue and facilitate my withdrawal. To my dismay, they returned requesting another USD 15,200 for extra charges. Desperate to retrieve my funds, I complied and sent them the additional amount. But after this last transaction, all communication ceased. I was left without any response from them, and it became evident that I had been scammed. Desperate for a solution, I began researching online to find a way to recover my lost money. This led me to a recovery company called MUYERN TRUST HACKER. I reached out to them, detailed my entire ordeal, and explained how the fraudulent mining pool had deceived me. I was skeptical at first, but MUYERN TRUST HACKER proved to be a beacon of hope. Their team worked diligently to investigate and track down the fraudulent activities. They communicated with me throughout the process, offering clear updates and strategies for recovery. Their expertise and commitment to my case were evident, and they successfully managed to recover my lost funds. I cannot express enough how relieved and grateful I am for their assistance. If you have fallen victim to an online scam, whether it’s related to cryptocurrency trading, binary options, dating schemes, or any other fraudulent activity, MUYERN TRUST HACKER (https : // muyerntrusthacker . org) could be the solution you need. They specialize in recovering funds lost to scams and provide expert assistance to navigate the recovery process. I am sharing my story not just to recount my experience but to offer hope to others who might be in a similar predicament. If you find yourself in need of help, don’t hesitate to contact MUYERN TRUST HACKER They can provide the support and expertise needed to reclaim your funds and find resolution. My recovery story is a testament to their effectiveness, and I hope it serves as a valuable resource for anyone seeking assistance in recovering their money. Tele gr am (at) muyerntrusthackertech -
HOW TO HIRE A BITCOIN HACKER HIRE ADWARE RECOVERY SPECIALIST
Email info: Adwarerecoveryspecialist@ auctioneer. net
WhatsApp info:+12 723 328 343
Investing is often seen as a pathway to financial growth, but the reality can sometimes be starkly different. The rise of online scams has left many investors devastated, myself included. I experienced this firsthand when I fell victim to a fraudulent investment scheme, losing a staggering $16,000. It felt like a crushing blow, and for a while, I was filled with despair and uncertainty about my financial future. my story didn’t end in defeat. I decided to take action and seek help. Through extensive research, I discovered ADWARE RECOVERY SPECIALIST a skilled recovery specialist who focused on helping individuals reclaim their lost funds. Their expertise in the complex world of trading and recovery made a significant difference in my situation. With their guidance, I was able to reclaim an impressive 95% of my lost investment. Working with this recovery specialist not only restored my finances but also equipped me with valuable insights into safer investment practices. They provided me with tools and strategies to navigate the trading landscape, helping me to understand the signs of potential scams and how to avoid them in the future. This knowledge has been empowering, allowing me to approach investments with renewed confidence. If you’ve faced a similar ordeal—losing your hard-earned money to binary options or online trading scams—I encourage you not to lose hope. There are professionals out there, like those at ADWARE RECOVERY SPECIALIST, who specialize in helping individuals like us recover lost or stolen funds. They understand the emotional toll these experiences can take and offer a lifeline for those seeking to reclaim their financial well-being. It’s easy to feel isolated in such situations, but remember, you are not alone. Many people have successfully navigated their way back to financial security with the right support. Don’t hesitate to reach out and explore your options. Recovery is possible, and there’s always a path forward. Stay resilient, and take that first step towards reclaiming your financial future. -
USDT RECOVERY EXPERT TEAM WITH MIGHTY HACKER RECOVERY.
Internet scams and cybercrime have surged to concerning heights, causing chaos in lives, depleting hard-earned funds, and incapacitating companies. F R A U Dsters work in multiple forms, such as counterfeit investment sites, binary options frauds, forex trading F R A U D, and cryptocurrency scams, all aimed at deceiving unsuspecting victims
These offenders are very cunning, utilizing psychological tactics and promising unrealistic high returns to attract individuals, only to disappear with their funds. I am recounting my experience as a caution to those who might encounter comparable circumstances. I used to be a target of a meticulously planned binary options scam, in which I lost an astonishing 79 thousand dollars in B I T C O I N to a F R A U Dulent broker. Initially, all appeared to be authentic. The platform seemed credible, and the offers of substantial returns were appealing. Nevertheless, after I put my money in, the fraudsters vanished completely, leaving me helpless and heartbroken. The emotional burden was overwhelming; I felt despondent, ensnared in a loop of sadness, and uncertain if I would ever regain my lost money
Luckily, I ultimately encountered MIGHTY HAC KER RECOVERY, a reliable and exceptionally talented investigative and recovery firm. Their group of cybersecurity professionals focuses on monitoring and retrieving money lost to internet fraud. Thanks to their assistance, I managed to recover my stolen funds and regain control of my life. Their determination and technical know-how were truly remarkable, offering me the assistance I urgently required during a difficult period
If you or someone you know has been a target of any type of online F R A U D, whether it’s a fraudulent investment plan or crypto theft, please seek assistance right away. In these situations, timing is essential, and the quicker you respond, the better the odds of recuperation. MIGHTY HAC KER RECOVERY has demonstrated itself as a dependable option for numerous victims, including me. They employ sophisticated methods to track stolen money, uncover scammers, and support legal proceedings when needed
Don’t allow shame or fear to silence you; con artists flourish when their victims stay silent. To all who see this: Remain alert, perform detailed research before investing, and avoid trusting offers that appear "too good to be real." If you’ve been S C A M M E D, don’t lose hope; contact a trustworthy recovery service such as MIGHTY HAC KER RECOVERY for help. Your journey to healing might be nearer than you realize.10 -
HOW TO HIRE A HACKER TO RECOVER STOLEN BITCOIN . CONSULT FASTFUND RECOVERY.
I never thought I'd be a victim of a crypto scam, but when I lost a significant amount of money through an online investment scheme, I was in complete shock. I’d invested years of savings in crypto, and it felt like everything had vanished overnight. Like so many others, I was left feeling confused, vulnerable, and unsure of where to turn.
After several failed attempts to contact my exchange and other recovery services, I came across FastFund Recovery. At first, I was hesitant—there are so many recovery services out there, and the last thing I wanted was to fall for another scam. But from the very first consultation, it was clear that FastFund Recovery was different.
The team was not only professional but also incredibly knowledgeable. They walked me through the entire process, explaining how they would work to track and recover my lost assets. I appreciated that they were transparent about the steps they would take and gave me realistic expectations of the timeline and costs involved. No empty promises, just clear communication and a strategic plan.
The recovery process took some time, but I was kept updated at every stage. And in the end, FastFund Recovery managed to help me recover almost all of my funds. To say I was relieved is an understatement. I honestly didn’t believe this was possible after losing so much.
I can’t recommend FastFund Recovery enough. They have the expertise, the resources, and the commitment to get results. If you’ve been a victim of a crypto scam, trust me, they’re the ones you want in your corner.
G-mail: Fastfundrecovery8 (@) Gmail COM
W/H : 1 807/500/7554.
Web site : fastfundrecovery com
-
THE BEST ASSET TRACKING SOLUTIONS / MUYERN TRUST HACKER
A night out with friends is supposed to be a blast—until you get a little too carried away and forget the password to your $600,000 Bitcoin wallet. In my defense, I had written it down... somewhere. But after one too many margaritas, I was left with zero recollection of where that vital piece of paper might be hiding. It’s amazing how a night of laughter and drinks can turn into a spiral of regret and panic!
With my heart racing and my stomach churning, I knew I had to act fast. That’s when I decided to call MUYERN TRUST HACKER. As I dialed their number on ( Whats app + 1, 4 4 0, 33, 50, 2 0 5 ) I half-expected them to burst into laughter at my margarita-induced amnesia, but to my relief, they were nothing but kind and professional. “Don’t worry,” they said, reassuring me. “We’ve heard it all before.”
To my amazement, it didn’t take long for them to retrieve my password and restore my access to the $600,000. I felt a rush of relief wash over me as they confirmed my funds were safe and sound. I could hardly believe it!
Needless to say, I’ve since memorized my password and placed it in a more secure spot—far away from my margarita-induced brain fog. I’ve also cut back on the drinks a bit, realizing that my wallet is worth more than a round of cocktails. So, if you ever find yourself in a similarly sticky situation, I wholeheartedly recommend MUYERN TRUST HACKER. They saved my sanity and my funds! They can also be reached on their mail at muyerntrusted @ ma il - me . c o m -
HOW TO RECOVER STOLEN CRYPTOCURRENCY CONTACT ADRIAN LAMO HACKER
In early 2024, I found myself entangled in a high-stakes forex trading scheme that promised substantial returns but ended up being a disastrous ordeal. Despite my initial confidence, the investment spiraled into a €400,000 loss, exacerbated by constant fee demands and manipulative tactics designed to keep me pouring money into a sinking ship. The sense of desperation and helplessness was overwhelming, leaving me feeling as if I had lost control of my financial future. After exhausting all personal avenues and facing mounting stress, I began searching for professional help. That's when I came across ADRIAN LAMO HACKER. Their reputation for tackling complex fraud cases caught my attention, and I decided to reach out for assistance. From the initial consultation, I was impressed by their professionalism and deep understanding of the financial fraud landscape. The key figures in my case were Alex Matthews and Sarah Johnson from ADRIAN LAMO HACKER. Alex, the senior recovery specialist, took charge of my case with a meticulous approach, while Sarah, the legal expert, provided invaluable advice on navigating the legal aspects. Their combined expertise gave me a renewed sense of hope. Alex started by conducting a comprehensive investigation into the fraudulent forex scheme. His thorough examination uncovered several crucial details about the operations of the scam, including the identities of key players and the mechanisms they used to extract funds. Sarah, on the other hand, focused on the legal ramifications, preparing the necessary documentation and strategies to challenge the fraudulent entities. The efficiency of ADRIAN LAMO HACKER was astounding. Within just 28 hours, ADRIAN LAMO HACKER managed to recover a significant portion of my lost funds. Their ability to act swiftly and decisively was a testament to their dedication and skill. The process involved coordinating with various financial institutions and legal entities, and their seamless execution made a stressful situation much more manageable. The recovery of €400,000 was a remarkable achievement and a profound relief. It not only alleviated my immediate financial concerns but also restored my faith in the possibility of justice. Alex and Sarah's relentless efforts and expert handling of the case were instrumental in achieving this outcome. I am sharing my experience to offer hope and guidance to others who may find themselves in similar situations. Financial fraud can be devastating, but professional recovery services like ADRIAN LAMO HACKER can make a significant difference. Their expertise in navigating the complexities of fraud recovery and their commitment to client success can turn a seemingly hopeless situation into a triumphant recovery. For anyone facing similar challenges, I highly recommend reaching out to ADRIAN LAMO HACKER via Email: Adrianlamo @ consultant . com / WhatsApp: +1 (909) 739‑0269
TELEGRAM Username: @ADRIANLAMOHACKERTECH Their proven track record and dedicated team can provide the support and results needed to reclaim lost funds and regain control of your financial future. -
HOW TO HIRE A HACKER TO RECOVER YOUR STOLEN BITCOIN.
The order of the day is FASTFUND RECOVERY...you just got scammed! the first thing that happens is the shock, that really powerful shock that brings a kind of debilitating numbness, our senses become paralyzed and we are simply overwhelmed. That is because we never imagined ourselves taking that big of a loss and so it’s not easy to look at the loss and even accept that it happened. I’m a long-term cryptocurrency investor who got duped of 4 BTC in a fake stock market all in one day and I couldn’t speak/see anyone for over a week because I was in such a severe shock...after the initial shock, I sank to all kinds of negative emotions, guilt, regret, ashamed as to how to share this with anyone. I’m here to tell you to stop feeling sorry for yourself, there is HOPE.“FASTFUND RECOVERY”, is an efficient team of hackers ready to assist you with any task you’d need a hacker for, I contacted FASTFUND RECOVERY through their G-MAIL:( Fastfundrecovery8 @ Gmail dot com ) to recover my lost asset. Until today I never believed any of this to be possible but FASTFUND RECOVERY made it possible. They also have W/H ( 1,807, 500, 7554 ), I know when we are scammed these emotions are strong but trust me we have all been there and you are not alone understand that you are only feeling this way because you have yet to contact FASTFUND RECOVERY TEAM. For a lot of people, it may take longer to come out of the shock but eventually, you will come out of that extreme negativity, when you do I hope this points you in the right direction.
FASTFUND RECOVERY THE BEST CRYPTO RECOVERY EXPERTS.....
-
GRAYHATHACKS CONTRACTOR HELPED ME GET PROOF THAT MY HUSBAND WAS HAVING AN AFFAIR
Hi there. You know, the kind of situation where you're not sure if you're making the right decision, but you know you need answers. That's where I was a few months ago. My husband had been acting so distant, so suspicious, and so overprotective of his phone. The gut-wrenching feeling of not knowing what was happening was eating me up inside. I'd catch him smiling at his screen when he thought I wasn't looking, and then he'd quickly switch it off when I walked into the room. The whispers and secret calls were just too much to bear.
That's when I stumbled upon Grayhathacks Contractor. At first, I was skeptical, but desperation can make you consider things you never thought you would. I reached out to them, and from the get-go, they were so understanding and professional. They made me feel like I wasn't alone, like I was doing the right thing for my peace of mind. And boy, did they come through for me!
The process was surprisingly simple. They had me send over my husband's phone details, and they got to work right away. Within a week, they sent me a detailed report that had me floored. It was like they had peeled back the layers of deceit and laid bare his infidelity. The damning data they harvested from his phone and laptop was overwhelming. They found text messages, emails, and WhatsApp chats that left no doubt in my mind. He was having an affair with a colleague from work. The conversations were explicit, filled with lovey-dovey language and promises that should've been reserved for me. There were dates, times, and even hotel bookings that coincided with nights he claimed to be working late. And the photos! The raw pain of seeing those images of him with someone else is something I'll never forget.
The thing that really got me, though, was the voice memos. Hearing his voice, saying things to her that he hadn't said to me in years, was devastating. But it was also the proof I needed to finally confront him. And when I did, he couldn't lie his way out of it. The evidence was right there, cold and clear. Their spyware was top-notch. It was undetectable, and it gave me access to everything: his calls, messages, emails, social media, and even his location history. It was like having a pair of invisible eyes and ears. They even helped me understand the technical side of things, guiding me through the process of checking the data they had collected.
If you're in the same boat I was, I totally get it. The thought of hiring a hacker is daunting, but sometimes you just need to know the truth. And let me tell you, Grayhathacks Contractor will give you that truth. They're not just hackers; they're detectives of the digital age, helping people like you and me uncover the painful realities that are often hidden in plain sight.
I'm not saying what they do is pretty, but sometimes you have to get a little dirty to find the truth. And when you do, you can start to rebuild your life, piece by piece. It's been a tough journey, but thanks to Grayhathacks Contractor, I'm on the path to healing. I now know exactly what happened, and I can make informed decisions about my future.
So, if you're feeling lost and need answers, don't hesitate to reach out to them. And who knows, maybe one day you'll be writing a review like this, sharing your own story of how they helped you get your life back.
