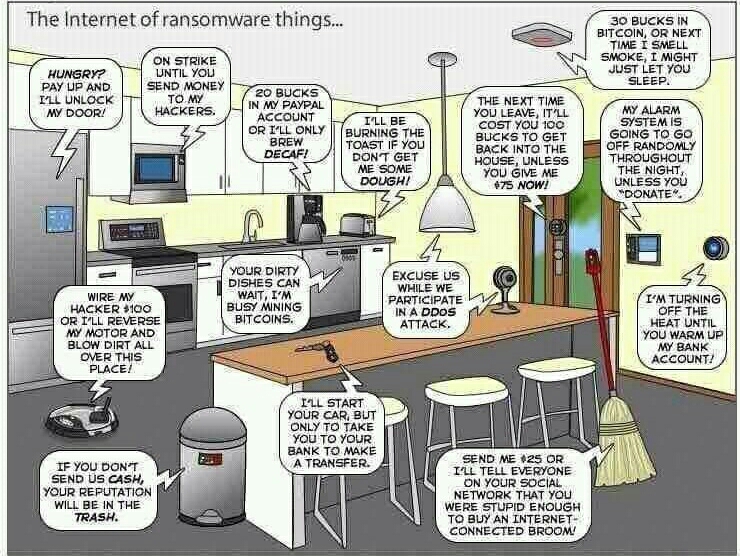
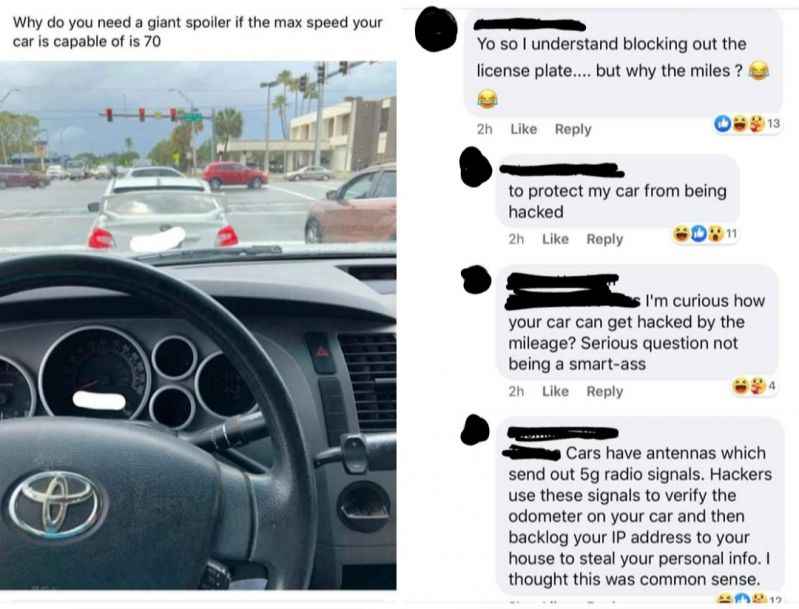
Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "hackers"
-
A hacker deleted the despacito video from youtube.
Those are not the hackers we deserve, but the hackers we need.16 -
I'm at Disney world and the Windows OS was exposed on one of the machines at a ride so pulled up CMD and ran "tree C:/" then played sample music on full blast. Get on my level hackers :^)
 10
10 -
CW: The SQL injection vulnerability isn't important because our code is proprietary so hackers won't find it.
Me: <censored>7 -
Anyone know this bitch hacker 127.0.0.1 story?
WORST HACKERS OF ALL TIME
CONTINUED IN THE COMMENTS BECUASE IT IS SO LONG...
TLdr bitch hacker hacks himself by localhost
bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> why do you kick me
<bitchchecker> can’t you discus normally
<bitchchecker> answer!
<Elch> we didn’t kick you
<Elch> you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
<bitchchecker> what ping man
<bitchchecker> the timing of my pc is right
<bitchchecker> i even have dst
<bitchchecker> you banned me
<bitchchecker> amit it you son of a bitch
<HopperHunter|afk> LOL
<HopperHunter|afk> shit you’re stupid, DST^^
<bitchchecker> shut your mouth WE HAVE DST!
<bitchchecker> for two weaks already
<bitchchecker> when you start your pc there is a message from windows that DST is applied.
<Elch> You’re a real computer expert
<bitchchecker> shut up i hack you
<Elch> ok, i’m quiet, hope you don’t show us how good a hacker you are
<bitchchecker> tell me your network number man then you’re dead
<Elch> Eh, it’s 129.0.0.1
<Elch> or maybe 127.0.0.1
<Elch> yes exactly that’s it: 127.0.0.1 I’m waiting for you great attack
<bitchchecker> in five minutes your hard drive is deleted
<Elch> Now I’m frightened
<bitchchecker> shut up you’ll be gone
<bitchchecker> i have a program where i enter your ip and you’re dead
<bitchchecker> say goodbye
<Elch> to whom?
<bitchchecker> to you man
<bitchchecker> buy buy
<Elch> I’m shivering thinking about such great Hack0rs like you
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> dude be happy my pc crashed otherwise you’d be gone
<Metanot> lol
<Elch> bitchchecker: Then try hacking me again… I still have the same IP: 127.0.0.1
<bitchchecker> you’re so stupid man
<bitchchecker> say buy buy
<Metanot> ah, [Please control your cussing] off
<bitchchecker> buy buy elch
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> elch you son of a bitch
<Metanot> bitchchecker how old are you?
<Elch> What’s up bitchchecker?
<bitchchecker> you have a frie wal
<bitchchecker> fire wall
<Elch> maybe, i don’t know
<bitchchecker> i’m 26
<Metanot> such behaviour with 26?
<Elch> how did you find out that I have a firewall?
<Metanot> tststs this is not very nice missy
<bitchchecker> because your gay fire wall directed my turn off signal back to me
<bitchchecker> be a man turn that shit off
<Elch> cool, didn’t know this was possible.
<bitchchecker> thn my virus destroys your pc man
<Metanot> are you hacking yourselves?
<Elch> yes bitchchecker is trying to hack me
<Metanot> he bitchchecker if you’re a hacker you have to get around a firewall even i can do that
<bitchchecker> yes man i hack the elch but the sucker has a fire wall the
<Metanot> what firewall do you have?
<bitchchecker> like a girl
<Metanot> firewall is normal a normal hacker has to be able to get past it…you girl
<He> Bitch give yourself a jackson and chill you’re letting them provoce you and give those little girls new material all the time
<bitchchecker> turn the firewall off then i send you a virus [Please control your cussing]er
<Elch> Noo
<Metanot> he bitchchecker why turn it off, you should turn it off
<bitchchecker> you’re afraid
<bitchchecker> i don’t wanna hack like this if he hides like a girl behind a fire wall
<bitchchecker> elch turn off your shit wall!
<Metanot> i wanted to say something about this, do you know the definition of hacking??? if he turns of the firewall that’s an invitation and that has nothing to do with hacking
<bitchchecker> shut up
<Metanot> lol
<bitchchecker> my grandma surfs with fire wall
<bitchchecker> and you suckers think you’re cool and don’t dare going into the internet without a fire wall
<Elch> bitchchecker, a collegue showed me how to turn the firewall off. Now you can try again
<Metanot> bitchhacker can’t hack
<Black<TdV>> nice play on words
<bitchchecker> wort man
<Elch> bitchchecker: I’m still waiting for your attack!
<Metanot> how many times again he is no hacker
<bitchchecker> man do you want a virus
<bitchchecker> tell me your ip and it deletes your hard drive
<Metanot> lol ne give it up i’m a hacker myself and i know how hackers behave and i can tell you 100.00% you’re no hacker..29 -
I just started playing around with machine learning in Python today. It's so fucking amazing, man!
All the concepts that come up when you search for tutorials on YouTube (you know, neural networks, SVM, Linear/Logic regression and all that fun stuff) seem overwhelming at first. I must admit, it took me more than 5 hours just to get everything set up the way it should be but, the end result was so satisfying when it finally worked (after ~100 errors).
If any of you guys want to start, I suggest visiting these YouTube channels:
- https://youtube.com/channel/...
- http://youtube.com/playlist/...9 -
I thought I was a hardcore geek until I came on here.
Super chill enviroment tho
Programmers are some of the nicest people you will meet.
Except the 12 year old hackers.4 -
I heard of it for the first time. And well, this sounds disgusting.
If this happens, I'll seriously start a revolution of hackers fighting internet providers. Seriously 9
9 -
This actually happend in my secondary school class. A new guy came to our class. The whole family moved from another city.
*new guy want to start conversation with me*
new guy: "So you into computers and stuff like that?"
me: "Yes" *seems like a cool guy , want to develop the conversation further* "what about you man? do you like computers? do yo program or smth?"
*new guy wants to look cool in front of me*
new guy: " Yeah dude, actually I am hacker"
*me saying to myself, oh fuck not again this shit*
he continues with: " Once I got into the NASA system"
*switches mode to making fun of him*
me: "what the fuck man? really? that´s freaking cool, how you manage to do that? "
new guy: " you know the thing when you press F10 when starting a comupter? "
me: "You mean BIOS?"
new guy : "yeah yeah man through that shit"
* I am done, laughing my ass off and walks away*1 -
i just love /r/hacking, best funny pics reddit i have ever seen.
Also, who would have tought rhat hackers are some of the most politest people? 7
7 -
On the first class of cryptography professor says, "Hackers are people who dropped out of school, didn't obey their parents and turned to drugs and alcohol and steal money from people by hacking their facebook."
Then goes on to say, "People tend to keep their birthdate as their debit card's PIN so hacker checks their facebook account, finds their birthdate and goes to ATM machine and hacks their bank account."
I was speechless.7 -
LoL (I wanted to write only LoL for this rant but you need to write atleast 6 characters, ....oh I think now it's sufficient)
 4
4 -
Best computer/hacking/tech TV and movies?
I'll start the list with some of my favorites.
1. Hackers
2. The Net
3. Jumpin Jack Flash
4. Antitrust
5. Swordfish
6. Wargames
7. Mr Robot
Anyone else?33 -
I hate how people think that to be a "hacker" or hacking is this special job title. lol. Hacking is just using something in a way in which it was not intended to be used.
So pretty much think ...anal sex.
There. Now many people are "hackers"6 -
Was asked to check the sales team server as it was running slow.
Apart from redundant processes and users with too much permissions I found a "Cobol" folder under one of the sales team member's home folder.
If it weren't the sales people I would immediately disregard this as trolling but with them it's quite possible that this is a real attempt to learn programming...
...most likely from the facebook ads with the hooded guys that offer to teach you to code in 10 days for $800. 5
5 -
Israeli government hackers hacked into Kaspersky’s network in 2015 and caught Russian government hackers red-handed hacking US government hackers with the help of Kaspersky.
In other words — Russia spying on America, Israel spying on Russia and America spying on everyone.10 -
Disabling pasting into a password field in 2020 with password managers, is retarded. That's it that's the rant. Doesn't matter if you think password managers are good or not. Its still retarded that there's a 40 something year old dumbfuck manager who told a web designer at EA to disable pasting into a fucking password field because he was dumb enough to think it stopped hackers or some shit like that.14
-
!rant
Guys... I've figured it out. Instead of wearing black hoodies, we should all wear white turtlenecks. We'll be the ultimate hackers. No one would suspect a hipster of being h4XX0r mastermind.10 -
Now that I have time to approach my ultimate dream ( being the pro penrester ) , asked a hacker for a road map and he gave me (U'll rarely see such open hackers that share knowledge :) )
Surprisingly I've been familiar with all the topics but being the most pro , requires u to be pro in every single topic .
Guess what ? I'm starting from basic linux commands all over again 😂
echo 'hello world :/' 25
25 -
Christmas song for UNIX hackers:
better !pout !cry
better watchout
lpr why
santa claus < north pole > town
cat /etc/passed > list
ncheck list
ncheck list
cat list | grep naughty > nogiftlist
cat list | grep nice > giftlist
santa claus < north pole > town
who | grep sleeping
who | grep awake
who | egrep 'bad|good'
for (goodness sake) {
be good
}
(By Frank Carey, AT&T Bell Laboratories, 1985 )1 -
"[In the future, there will be two types of people.] People who tell computers what to do, and people who are told by computers what to do." - Marc Andreessen
I guess we'll be the ones who tell the computers what to do.3 -
Noob: "Hey guyz! Im now a hacker! Look at this cool script"
Legit programmer: "oh wow! How does it work?"
Noob: "I have no idea. I found it on the internet "
LP: .........1 -
Arch users are literally like vegans, or guys who study the law - they can’t live normally if they don’t tell you that they use it. Just because you can install it, doesn’t make you instantly a Linux god. It’s like Kali users that they think that they’re hackers if they install it, or MacBook users that think that they are “kool kids” because they have a laptop that thousands of other people have.
Nobody. Cares.10 -
PM ordered me to not use encryption for customer authentication links because we want to be able so send same link if the user loose it. "we have to prioritize usability over security". At least I can tell future hackers it's not my fault..
 10
10 -
Really cool. Tesla gave two hackers that found a vulnerability in the Model 3 free cars as a reward. More companies should do that, instead of getting all pissy. I would hope a company wants to know what their vulnerabilities are so that they can avoid embarrassment and the loss of money.2
-
When someone says they are a 'HACKER' whereas all they do is watch videos of 'How to hack a GMail account' on YouTube and read 'Learn to hack in 24 hours' , while having no knowledge of networking, security protocols and ports.10
-
The moment when you are able to identify the programming language in the movie you are watching and you know they are doing bullshit...2
-
Hey hackers!
Just found root-me.org !
Cool enough to turn me on.
I've just finished first 8 challangrs which were piece of cake.
Let's see how it goes 😎2 -
{spoilers, i guess...}
In season 1 episode 4 of Mr.Robot, Elliott plans on using a Raspberry Pi to heat up the storage facility in order to destroy the cassette tapes stored there. If he can get the temperature high enough, it would render those tapes useless. I was just wondering, can a hack like this take place in real life?11 -
You know a company is ripping you off when they charge £79 for a fucking charger and it breaks in 1 year. Fuck you Apple2
-
Some people tape up inputs like camera and mic to keep gov and hackers out of their private lives.
Me, I'm an exhibitionist.1 -
Friend (girl) of my friends realized that I’m a programmer and dated me. She wanted me to hack her ex boyfriend Facebook account.
She abused/used me sexually as long I explain to her that programmers aren’t hackers and I can’t hack fb account.
I feel bad for her! 😂😂3 -
Where the fuck my privacy go?
I'm paying you to listen to music or watch films, I don't want you to create a damm profile my taste or "learn" what might like.
If it was a free service, fine, I'd understand, but I am fucking pying you. I should have the option to completely disable your arse sniffing software.
I know some of them provide a "private mode", but I want that to be the default, I am paying for the god damn service :/6 -
Somebody ranted about austria searching for hackers? well germany does too
"How do you protect your ship from digital attackwaves" - "do what really matters" 9
9 -
!Rant
To all my fellow developers, hackers and programmers. Can't we all come together to agree that... Finally pushing that big update you have been working and struggling on for so long... is one of the most satisfying feelings ever! <3 -
When kids watch tutorials on youtube and think they wanna become black hat hackers and tell everyone that thay are black hat hackers 😂😂
Source : reddit 6
6 -
When i started to get into computers i didn't know a shit about Linux, i had the typical idea that is for hackers. Now i see how things that we use everyday like the phone uses it.
#againstignorance3 -
As the news that hackers have kept new "pirates of the Caribbean" on hold, this kind of comment reassures the trust or acts as reverse psychology to pay up.
Any ways they have got better customer service than any other big corporates 1
1 -
Hackers hid backdoor in CCleaner, with 2 billion downloads and 2.3 million greatly affected and detected so far, go fuck yourself you Windows fucking gloating noob fanboys showing off how you clean your C with CCleaner like a breeze, go clean your ass now and hope there's no backdoor there! 🖕8
-
Damn hackers! Within the course of a week, the internet of my country has been DDOS-attacked three times! Last week the attacks came from Russia or China". Yesterday they came from Russia and Ukraina. Is this a part of the Russian military exercises Zapad 17? Well, when an important part of the infrastructure is down and thousands of civilians are affected, it's for real and not an exercise.31
-
Can anyone recommend any good IT / hacker related films that are not HACKERS or THE MATRIX. Thanks.12
-
This morning I was looking in our database in order to solve a problem with a user registration and I accidentally noticed some users registered with unusual email addresses (temporary mail services, Russian providers and so on...).
I immediately thought about malicious users so I dug into the logs and I found that the registration requests started from an IP address belonging to our company (we have static IP addresses). My first reaction was: «OMG! Russian hackers infiltrated into our systems and started registering new users!»
So, I found the coworker owning the laptop from which the requests were sent and I went to him in order to warn him that someone violated his computer.
And he said: «Ah! Those 7 users? Yeah, I was doing some tests, I registered them. My email address was already registered so I created some new ones».
Really, man? Really? WTF5 -
Call at 5am, meeting in the office at 5.15am, leave office at 5.30am on route to airport because the customer doesn't know how to use the system. It turned out to be nothing :/2
-
Watching a piece (a Belgian TV series) about hackers
- Police IT dpt takes a burned down computer (literally burned down -- black from the smoke), plug it into the mains and remove a graphics card. To collect evidence from.
- A policeman from IT dpt is browsing some company's website (while at the police station), looking at their clients. Address bar says: 127.0.0.1.
- The police hacker is browsing some forum. She got the post author's IP and MAC addresses from that forum post metainfo.
<img src="awkward.jpeg" alt="Awkward...">
<img src="confused_jackie.jpeg" alt="Awkward..."> 19
19 -
Hey hackers! 😀
Does making a camera disconnected from the network using deauth packets , mean the camera won't send any data to the sarver/admin?
Does that make the camera useless and made the camera disabled?30 -
Dear Dark Side #3
Honor the hackers who made your childhood:
Store text in .nfo
Trigger a midi when someone makes a patch
Send ASCII art to your graphics dept5 -
In my opinion
php is shit
js is shit
now what we have with babel-preset-php is converting shit to shit. it's a fucking shit storm.
https://gitlab.com/kornelski/...8 -
Do you guys think it’s time “Hackers” gets its 2020 remake? I know it was cheesy for its time (1995) but 8 year old me was INTO that music video montage direction and that movie inspired was what inspired me to get into tinkering with electronics/embedded systems.
Rewatching it tonight and the casting is so on point, too.5 -
Had someone call saying "they are going to help me with protecting against the hackers". I played around for awhile until he asked what operating system I had. When I said linux the gig was up. He knew I was messing with him....2
-
Never felt the need for a stressball until I started using those damn automatic checkout machines ...
The f***** juice is in the f***** bagging area and I dont need no f***** help. Who the f*** coded this shit ***** ***** *****3 -
Well, here is another Intel CPU flaw.
I'm starting to think that all these were done on purpose...
https://thehackernews.com/2019/05/...3 -
At a previous job I bumped heads with the IT person a lot because he would spread misinformation about technology so the owners would never replace him. This was conversation with the VP:
VP: Hey I just got a new security setup at my house and I can monitor everything with my phone.
Me: That's cool.
VP: I'm rethinking it because [IT guy] said it was very dangerous to have, what do you think?
Me: ....? What did he say was dangerous about it?
VP: He said hackers could then gain access to cameras and plan the perfect time to rob me since it's in the cloud.
Me: I seriously doubt anyone is planning an Ocean's 11 heist to steal your TV.
VP: Yea I thought it sounded weird when he told me.3 -
When Hackathon Hackers uses "node.js" so much that I'm not sure if it's actually useful or just a joke anymore....4
-
My 17 year old cousin got inspired by Hollywood movie and said he wanted to be an Hacker. Now, who can explain him the shit that's shown on the silver screen isn't practical in real life. The life of programmers, hackers is rather about learning continuously throught their life rather than hacking into a quantum computer through a gaming console.
🤬6 -
I hate it when my friends think they're hackers just because they were able to jailbreak their phones.4
-
Overconfidence is striking again. Some companies are really begging for it... Found this cup in the kitchen of a client. And it is the slogan of an external contractor. It says: this network is unavailable for hackers. I think this is worth at least a triple facepalm
 1
1 -
Just reminiscing when back in the "old days" video games had cheats built in...
Proton men and the flying Dutchman IN AOE3...
Now have to find hackers to create trainer apps that change values in memory and bypass cheat detection...7 -
Soon every hacker can move to Toronto and play real-life Watch Dogs.
https://amp.theguardian.com/comment... -
I used to think the "hackers" in movies were so cool, with the scrolling matrix like text. Now I just laugh because I know how stupid and unrealistic most of it is 😆.1
-
Damn you hackers!
This is why it pays to hide your login page with WordPress, luckily not been hacked yet.
They are persistent if nothing else them Bots. 😱 1
1 -
Fuck you Chrome Canary. You tell me to update and then keep crashing.
Well admittedly it is Canary :o1 -
I just love it to giggle at "hackers" in movies/series.
"He used an ARP to 'crack' the hostname of the server"
And then a countdown when the Server is hacked...7 -
comment your favorite tv shows for em coders n hackers here!
ill start:
mr robot, it crowd and silicon valley7 -
😂😂😂 lol oh no what will we do when hackers takeover the world by printing an endless stream of planetary gears. Shame on you Harvard for such a poor picture choice.

-
DevRant colors :
White - Gray - Black
White hat hacker , gray hat hacker and black hat hackers
Just something random ..5 -
I just feel that the Intel stuff going now has been in the past year.
Maybe the hackers found it, selled about 5 times in the deep web. Then one reported to the officials, and they are releasing a statement in 2018.
tldr Hackers want devs to go mad from the start of 2018.
a.k.a FUCKWIT3 -
Fuck you BBC, I just want toblosten to fucking radio and you tell me that I "need" to sign in.
I do not want you to tell me what to losten to. I do not want "relevant" content, just want to listen to 30 mins of news.
Then you say it is easy to signup, but then ask for my exact date of birth as the first question wtf ... 5
5 -
If I were to change all my passwords into hashes (so take a random word and hash it, ex 'table') and then use those on various websites, would people ever guess that my password is _an actual hash_ rather than a password in hashed form if they were to see it? Would such a meta-hash be safer if 'hackers' were to find it unencrypted?8
-
Watched some documentary about Russian hackers. Journalist: I need to learn their language. - starts programming/hacking course, sees a shell and a python: runs away. 'That ain't for me.'
At least he tried tho.
Later he finds some Ukrainian hackers. One had a strangely familiar logo on his laptop. Rewind a bit: its hackthebox.
Just had my first blood there. So.. I'm a hacker, too? Good enough for Arte doc's?5 -
I really get annoyed when people claim that they are programmers or hackers, when all they did is copy a vbs script they found online.4
-
Marketing material for a RasPi-based device that, supposedly, secures all your traffic from hackers by (translated) "encrypting traffic to your router" and "sharding and dispersing your data, so nobody can read it".
Stay tuned to see what it actually does (waiting for an email reply from it's creator) 6
6 -
Every time I try to use TypeScript for something, everything I learned a month ago is deprecated. Tsconfig keeps changing. The way to get and set up definition files has changed like 5 times now. From downloading, all the way to referencing. Can we please just settle on something now?1
-
I had a training about secure software engineering recently. Today was the corresponding exam.
One of the questions was a list of 4 hackers and you should pick the one who was in jail.
That question was so unreal... I was speechless.4 -
Every time I log into a server for a client:
Important notice: only employees of xyz are authorised to use this equipment.
Our client outsources their it to another company, someone from that company sent me details of a server for me to install our software. They licence our software, I am not an employee. I guess it must scare off the hackers?1 -
Enter one word in terminal and hack fucking government's, CIA's, NSA's, websites, database and servers, just like hackers in movies do.
If I failed to achieve this, would love to hack Sony's website and post a message on all their websites
"We make terrible mobile phone" -
For fuck sake, stop complaining about the number of js libs. There is just as many if not more c/c++/c#/java/python/ruby/php... libs.
Just because they are available on npm or github, it doesn't mean you have to fucking see/read/use it1 -
Judging by the amount of bitcoin recovery ad spam here on devrant, there must be a huge amount of people somehow losing their bitcoins on a daily basis.
Thank god those altruistic scammers… *ahem* I mean hackers of course… are there to help.7 -
There is a subreddit collecting media scenes which shows “hackers” and discussing them.
https://reddit.com/r/...: -
Why hospitals,trains,banks and others use this stupid vulnerable OS called Windows and why the hell they need to be connected to the public internet?
Heck I even think Microsoft does one hand with hackers.8 -
My group set up a Linux Dev server. We got hacked by Chinese hackers. We set it up again but even more secure with only people inside the uni can access it. We got hacked again.Turns out one of the modules in a container was using an outdated CentOS version. P.S The malicious file on the server was called kk.love.1
-
Work on projects that produce something that solves one of my existing problems.
Also dev environment matters. One of those hackers desk setups would be fine. Nothing too fancy, just need a functional one. -
One time, i would put a random stacktrace / error log containing fake server credentials/ card info etc on a page/ action letting those "hackers" waste their time digging into it.. only to found out that the server is just a repo of (i would like to say porn butthats still a win situation) useless things1
-
!gamingRant
What annoys my the most in gaming, is when gamers refer to cheaters as "hackers". THEY AREN'T. They are SCRIPT KITTIES. I'm sure most of us here would consider ourselves hackers, and we can all agree that hacking takes time, motivation, and most of all, skill. Cheaters in video games are the lowest of the low. The just download and install scripts written by real hackers. This triggers me beyond words and all caps. What do you all think?7 -
Why don't hackers or super coders in tv/movies use mouse? I can't even think of working without a mouse!6
-
Woah dude, where do I sign? 😱
Seriously though, it's the second email of the sort today. The recipient is not even my address, and from some subtle cues (cf. "ethical hacking service", "untracable", "victim never suspect"), he's probably a very bad developer too. Dear "Ruben Villanueva", you're just a f***ing a**hole, I hope you die painfully, dumbface. 5
5 -
You know what's a great app? Termux! It's amazing. Yesterday I tried running apache on it and it worked! If you haven't tried it yet, you really should, it's great. For those of you that don't know, it's basically a custom Linux evnvironment that doesn't require root acces. You can use it for ssh, you can use vim in it, python, standard commands etc. I'm definietly thinking about buying stuff like the customization to support the developer. Btw. Along with "Hackers keyboard" it's even better!
-
Anyone else a fan of Android: Netrunner? I believe it's one of the only (tabletop) games that depict hackers accurately2
-
No the problem is if Tech companies aren't doing it... hackers will anyway?
https://futurism.com/darpa-stop-dee... 1
1 -
Last night the Russians stroke again. It's become obvious that these Ddos attacks are not performed by just some casual hackers, but are part of cyber warfare - just as I suspected in one of my rants a couple of weeks ago6
-
I want to break my win 10 password which I have forgot . I know one method of breaking the passcode by using bootable Device . Is there any other method to other than using bootable device for breaking the passcode? please suggest some technique9
-
I see lots of script kiddies these days that call themselves software developers or hackers. Their shitty code is flooding the world, so write more code you fuckers and let the world burn2
-
Oh no, apparently GDPR is worse than we thought. Just look at the linked thread. The government needs not to touch anything
https://twitter.com/alexstamos/...2 -
PHP is so insecure and vulnerable that it makes me feel unsafe. It has so many features and settings that can lead to security risks, such as register_globals, magic_quotes, and allow_url_fopen. It also has so many functions that can execute arbitrary code or commands, such as eval, exec, and system.
It is like PHP was designed by a bunch of hackers who wanted to exploit every possible loophole.8 -
When did it become so hard to come up with usernames that dont contain your name or year of birth ...4
-
A co-worker ask me to translate my "comments" (*which are in facts annotations) to french since it's private code and as it "plays hackers game". The same coworker writes his methods starting with a uppercase.
This is bothering me a lot.
I want to quit.1 -
I thought devRant week count would have overflowed and gone back to 1.
Qhat sort of year has more than 52 weeks, feels like the estimates PMs give ... -
I'd love to get into a career within the cyber security industry.
Anyone got advice?
I've played around with Kali/Parrot and setup a proxmox box to perform pen testing and have a fair number of PDF ebooks and audio books on networks, security and pen testing12 -
The feeling of evil satisfaction when your boss asks you to build a killswitch into a client's project.
Just call me Zero Cool.3 -
Infosec : I have started a telegram channel.
Join and spread the word..
Link : Hack3rB0x 🔊
https://t.me/hack3rb0x1 -
I want to setup a website, I have a few questions.
What's SEO and how does it affect my website?
Where should I setup?
Also how should I set it up to prevent hackers from damaging my site?11 -
About to submit a form to get a scholarship to a government website, and guess what. Errors everywhere. Why are they like this? These government websites are also known to be very vulnerable to hackers2
-
Anyone going to defcon in a couple weeks? If not, you should think about it. Quite the experience in hacker culture!9
-
Before now, Twitter was under a bitcoin twister verified attack ( that is my name for it ), now Snapchat is on a photo exposing viral attack.
is this World War including hackers, messing with social media handles.
World War 3 will be fought online, i know yeah.1 -
The consistency of php standard lib function is astonishing. array_map, array_reduce ...
Why do I have to use php7 😢😢😭😭😭1 -
How are you building your products today?
-> What is your tech stack?
-> Your reasons for choosing them?
-> Any pain points you can help other indie hackers avoid?
I will start with mine -11 -
Unlock the secrets of the digital world with our latest video, "Hire the Best Hacker 2025!" Discover how Mighty Hacker Recovery can assist you in retrieving your lost bitcoins, upgrading your school scores, and enhancing credit card limits. Whether you're facing financial challenges or seeking academic improvement, our expert hackers offer tailored solutions to meet your needs.
Join us as we explore the incredible capabilities of skilled hackers in 2025. Don’t forget to like and share this video with anyone who might benefit from our services!
Hire the Best Hacker 2025! Bitcoin Recovery & More
USDT trade key for withdrawal contact Mighty Hacker Recovery on Whatsapp +1.8.4.5.6.9.9.5.0.4.4.
How to recover my lost usdt online/ contact Mighty Hacker Recovery.
What can you do to retrieve USDT if it was mistakenly sent to the wrong wallet address? contact Mighty Hacker Recovery.
How to recover my lost usdt online? contact Mighty Hacker Recovery
Hire expert Certified Ethical Hackers at Mighty Hacker Recovery.
Hackers contact number near me contact Mighty Hacker Recovery
#Hacker2025 #BitcoinRecovery #CreditCardUpgrade #ScoreUpgrade #MightyHackerRecovery #Cybersecurity #TechSolutions
Hacker Near By me contact Mighty Hacker Recovery
Who can I call about a hacker? Call Mighty Hacker Recovery Whatsapp +1.8.4.5.6.9.9.5.0.4.4
Hire a Local Hacker Near Me for Enhanced Cybersecurity Whatsapp +1.8.4.5.6.9.9.5.0.4.4
Hire expert Certified Ethical Hackers for any job Whatsapp +1.8.4.5.6.9.9.5.0.4.4
Ethical hackers academy reddit contact Mighty Hacker Recovery8 -
Happy Friday. Facebook just disclosed hackers have exploited multiple vulnerabilities to get access to potentially 50 million users. I guess... no weekend for the blue team? https://mobile.twitter.com/dnvolz/...
-
If I wanted to do some 1990s hackers shit, but more for this time period is there a way i can autopilot the apps on a smartphone that offer those crappy free numbers and auto-dial with them and feed / receive audio information into/from them via a program ?3
-
Ok , so about #wannacry project all we need is group of good programmers and ethitical hackers even black ,any way who wanna join us ? Lets make money3
-
Contact (backendrecoverATrescueteamDOTcom) for your lost cryptocurrency recovery. No other hackers comes close to his professionalism.1
-
Yes I totally agree with this. It happened at a point where I was forced to go hire a hacker to get it fixed in 4 days. Although I had to pay lesser than 10K to get it done but it was worth all the penny I gave them. These hackers are now my bestfriend.{ hacktechspy(at) gm ail c om} . This has been almost a year now. FYI They are super responsive and fast.3
-
After trying a few spyware programs for several productive hours, I eventually came across a recommendation for Recovery Nerd, a group of expert hackers, who performed an outstanding job. I will never again have to search the internet for hackers. But you might be wondering if your spouse is doing something behind your back. You believe your husband or wife is deceiving you. Discover the truth and find mental tranquility with these amazing hackers. Reach them via email at recoverynerd @ mail . com, or by SMS, phone, or WhatsApp at +6 488 893-280.3
-
HOW TO RECOVER STOLEN CRYPTO LOST TO ONLINE TRADING INVESTMENT SCAM
Hoffman Law Bitcoin Recovery to the rescue! I thought I’d lost $42,500 to a crypto scam, but their expert hackers worked magic to recover my funds and the profit I was promised! Don’t let scammers get away with your money – Hoffman Law Recovery are the real MVPs. Highly recommend their services!
Quickly reach out to Hoffman Law Recovery for free consultation2 -
Yes I totally agree with this. It happened at a point where I was forced to go hire a hacker to get it fixed in 4 days. Although I had to pay lesser than 10K to get it done but it was worth all the penny I gave them. These hackers are now my bestfriend.{ jbeespyhack(at) gm ail c om} . This has been almost a year now. FYI They are super responsive and fast.2
-
optimum hackers recovery expert
I’m still very amazed and short of words because I didn’t know the difference between a legitimate hacker and fake until I came across optimum hackers recovery which made a major impart on my lost and stolen digital assets cryptocurrency . At first I was skeptical that optimum hackers recovery experts is fake but , but I was shocked and amazed when found out that optimum hackers experts are real and legitimate . Optimum hackers recovery are good and honest digital asset recovery saving thousands of invested lost crypto all over the world, they help secure your data base and sensitive information keeping it all safe and secured .That brings me to a reminder about the professional and incredible ability of the optimum hacker. I’m Bruce Elton 7 months ago I lost crypto worth $632,740, and that’s all the money I had saved and worked for all my life leaving at a very poor situation ,I lost everything I had including my house car I got frustrated and depressed to the extent of taking my own life by committing suicide ,I got into garbage recycling to eat and we don’t get garbage recycled daily, I worked 3 times a week ,and I got into drugs due the depressed one lucky day for I came across optimum hackers recovery post online ,my story changed for good ,the ultimate hacker bruce Elton helped me in recovering back my $632,740 back with his special optimum hacking tools and he also thought me how to protect myself and stay safe even on the dark web .with every assurance I have, any one with a lost/or stolen digital assets that you will get every penny you’ve lost all fully recovered within period of 24 hours ..
Contact: optimum hackers recovery experts
Whatsapp: @+1 .2.5.6.2.5.6.8.6.3.6 1
1 -
Telegram, (At) Trustgeekshackexpert
Whats Ap, (+1.4.0.6. 2.1.8.6.9.0.0)
Email, (trustgeekshackexpert(At)fastservice(Dot)come)
A virtual mentor who guides you through the academic maze, offering insights, tips, and a helping hand when you need it most. That's TrustGeeks Hack Expert in a nutshell. Although it would be wonderful, TrustGeeks Hack Expert isn't some sort of magical wand-waving sorcery. It's a clever digital tool meant to assist pupils in rising above academic setbacks and achieving success. Consider it your reliable ally on the journey to academic success. Before stumbling upon TrustGeeks Hack Expert, I was practically treading water in the sea of academia. My grades were more like a rollercoaster ride than a steady incline, and I could barely keep up with assignments. It felt like I was stuck in a never-ending whirlpool of confusion and stress. you're staring at your not-so-stellar grades, feeling like you need a magic wand to turn things around. Enter TrustGeeks Hack Expert, the revolutionary tool that promises to sprinkle some academic excellence dust on your performance. contact TrustGeeks Hack Expert with the information above.. -
You may be suspecting that your wife is cheating on you. The doubts linger, causing anxiety and sleepless nights. In a desperate search for the truth, he turns to TrustGeeks Hack Expert, a renowned digital forensics company known for its expertise in uncovering hidden information. And so, the curious case begins. TrustGeeks Hack Expert embarked on a mission to unveil the hidden messages that held the potential to confirm or dispel the husband's suspicions. Using their arsenal of expert techniques, they began the intricate digital investigation process. The first step involved collecting all the necessary details, such as the communication platforms used, usernames, and any available passwords.
With the information in hand, the team at TrustGeeks Hack Expert delved deep into the digital realm, employing cutting-edge forensic tools to recover deleted messages and uncover hidden conversations. Once the messages were retrieved, they underwent a meticulous examination, deciphering the content and ensuring their authenticity for future use. The final step involved presenting the uncovered messages to the client, providing him with the concrete evidence he needed to confront his wife and make informed decisions about his relationship. Thanks to the wizardry of TrustGeeks Hack Expert, the truth was uncovered, and the husband was equipped with the knowledge he sought. A selection of services designed especially to unearth the truth behind messages from an unfaithful spouse are provided by TrustGeeks Hack Expert. Their team of professionals is proficient in data recovery, digital forensics, and meticulous tracking methods. With their help, people can obtain the proof they require to validate their suspicions and make wise choices regarding their relationships. Even though there may be a lot of grounds for suspicion, it's crucial to conduct the inquiry in an ethical manner. TrustGeeks Hack Expert is aware of how delicate these circumstances can be, and they take care to make sure that all of their procedures follow moral and legal guidelines. Their mission is to give people the information they need while protecting their right to privacy and secrecy. TrustGeeks Hack Expert proficiency in digital forensics and data recovery is just one of their many skills. They have the ability to retrieve erased emails, messages, and other digital traces that might contain information about the secrets of an unfaithful spouse. They are able to resurrect material that has been concealed and offer it as proof by employing sophisticated strategies. TrustGeeks Hack Expert is aware of the significance of social media surveillance in this day and age, as these platforms play a big part in communication. They are able to monitor messaging apps, keep tabs on online activities, and even offer phone tracking services. People can use their knowledge to better understand their partner's interactions, which enables them to make defensible decisions. Remember, while discovering a cheating spouse can be a painful experience, having access to expert techniques like those offered by TrustGeeks Hack Expert can provide the clarity and evidence needed to move forward. Trust in their expertise and let them guide you through the process, armed with wit, personality, and a dash of digital magic.
Communicate with TrustGeeks Hack Expert through:
whats App +1 406- 218- 6900
Telegram User: @ Trustgeekshackexpert
Best Wishes -
The majority of information on the internet may be added to, removed, altered, and so on, and they can be useful to you in a number of ways. As a group of skilled hackers, we put your needs first. You can be confident that we will protect your privacy!.
Among the services we offer are the following ones:.
*. Consulting Services.
*. Recovery of Email Passwords.
*. Hacking Email.
*. Database Access.
*. Credit Repair [tradelines for installments and revolving loans].
*. Payment of student loans.
*. Bug bounty (penetration testing).
*. Hack a phone to snoop on anyone, including a spouse who is unfaithful.
*. Criminal record clearance.
*. Recovering lost money from capital investments and binary options.
*. Improvement of School Grades... and much more.
If your particular job isn't on the list, you can still get in touch with us, and we'll be pleased to assist you.
We also offer blog posts on hack news/updates, hack tutorials etc.
BLOG: hackburgblog . noblogs . org
WEBSITE: hackburg . co
CONTACT us: hackburg @ cryptolab . net3 -
I have just allowed '*' on the rack-cors host configuration. Yiiiiihhhhaaaaa.. no cors problems on Rails again.
But hackers will go fuck my api. -
I never believed that hackers can be able to recover lost or stolen crypto currencies until I met (BACKENDRECOVERatRESCUETEAMdotCOM). He made the recovery process so easy. I am forever grateful to him for helping get my life back on track.1
-
The SCHWARTZ RECOVERY HACKERS is a global licensed forensic organization that can help you recover Funds From Cryptocurrency and Bitcoin Scam. By hiring SCHWARTZ RECOVERY HACKERS SERVICES’ crypto recovery specialists, you equip yourself with a committed team that will put in endless effort on your behalf to recover your stolen funds.
Visit SCHWARTZ RECOVERY HACKERS’s website at
Contact;
Email (schwartzsoftwarehackingprogram at gmail dot com )
Whatsapp +4(477)(412)(64851)4 -
Email: casefile @ shi -us . com
I lost my MacBook laptop some time ago alongside my iphone 16, in that process all my crypto coinbase accounts, about 3 of them, I had difficulties logging in and I consulted lots of agencies to assist but all to no avail, until I came across Santoshi Hackers Intelligence and within a twinkle of an eye it was all done.
If you suspect your Credit card, email & password, Facebook, Instagram, twitter Accounts has been hacked, you need to Recover stolen money from scammers, reports the incident to Santoshi Hackers Intelligence they can help you recover your BTC by providing an experience team of security experts and forensic investigators who can investigate the loss, identify the source of the compromise, Santoshi we help you retrieve your stolen currency, in addition, Santoshi Hackers Intelligence can provide you with educational materials for staying safe online and give you access to cutting_edge cyber threat intelligence. They can also identify potential security breaches or vulnerabilities that may have led to the loss of your information.
Above is the email address to reach Santoshi Hackers Intelligence.1 -
My Bitcoin Recovery Experience With The Hack Angels.
I highly recommend the service of The Hack Angels to everyone who wishes to recover lost money either bitcoin or other cryptocurrencies from these online scammers, wallet hackers, or if you ever sent bitcoins to the wrong wallet address. I was able to recover my lost bitcoins from online swindlers in less than two days after contacting them. They are the best professional hackers out there and I’m truly thankful for their help in recovering all I lost. If you need their service too, here is their contact information.
Mail Box; support@thehackangels. com (thehackangels. com)
Whats Ap; +1 520) - 200, 23 20 -
Hello! I am Jane from New York, and I would like to thank OPTIMUM HACKERS RECOVERY for their unwavering efforts in assisting me in getting back the bitcoin that I lost to a fraudulent investment forum. After reading testimonials regarding their excellent service, I want to get in touch with them and explain everything that has happened. I was able to quickly retrieve my lost bitcoin after providing all the necessary details and collaborating with their expert. I appreciate OPTIMUM HACKERS RECOVERY for saving my life. To anyone who needs their services, I heartily recommend them.
Mail: support(@)optimumhackersrecovery(.)com
Website: https(://)optimumhackersrecovery(.)com
WhatsApp: + 1,2,5,6,2,5,6,8,6,3,61 -
Attention Housing and Real Estate and Cryptocurrency Scam Victims! If you’ve fallen victim to a any of these scam and lost your hard-earned money, you’re not alone. I was once a vitim until i come across (STORMBYTE HACKERS RETRIEVER) They help me recover my funds and guide me through this challenging situation.
Don’t let scammers take advantage of you any longer! Contact (STORMBYTE HACKERS RETRIEVER) today for support and to explore your recovery options. Together, we can fight back and reclaim what’s rightfully yours!
📞 +1 (562) 572-9348)
✉️ Stormbytehackersretriever @ protonmail. com2 -
Get in touch with Hackron Hackers for all your hack related such as; Cloning, Tracking, Spying, Retrieving of deleted text messages,Recovery of lost funds, Hack social media accounts. There service is safe and secure. Get in touch with them via this email: hackrontech @ gmail com2
-
Yesterday, I confirmed the recovery of my scammed coins.. I just want to put this out there that this is possible and not a miracle.. I was scammed of $35,000 btc and I was blocked off the account.. It was a problem for me, not being able to access my money and my account regardless of speaking to the help service SCHWARTZ RECOVERY HACKERS. Thanks to schwartzsoftwarehackingprogram at gmail dot com or +44 77 41 26 48 51 WhatsApp. Today being 2nd January 2025 am a happy man for having all my funds back in my position SCHWARTZ RECOVERY HACKERS keep to there words and handle the situation with a good technology
 8
8 -
Santoshi Hackers Intelligence can help you recover your BTC by providing an experienced team of security experts and forensic investigators who can investigate the loss, identify the source of the compromise, and provide technical services to help you retrieve your stolen currency. In addition, Santoshi Hackers Intelligence can provide you with educational materials for staying safe online and give you access to cutting-edge cyber threat intelligence.
1] you need to retrieve your passwords Social Media Accounts consult SHI.
Major Cryptocurrencies SHI, Professional with to recover any misplaced or corrupted wallet hacked by scammers SHI is the answer you need. Bitcoin ( BTC) Ethereum (ETC) Binance Coin (BNB) Tether (USDT)-Stablecoin USD Coin ( USDC) (XRP) Card.2 -
SEARCHING FOR EXPERT HACKERS VISIT TECHNOCRATE RECOVERY
Are you a victim of online scam, I highly recommend reaching out to TECHNOCRATE RECOVERY. They specialize in helping victims recover lost funds. Don’t let scammers win—recovery is possible.
LEARN MORE:
Telephone: +1573 3563 708
Contact Email: technocratrecovery@ contractor.n et1 -
There is a team of reliable andcompetent hackers ready at any given
time to carry out any given job, Erase criminal records
Hacking of school data base, Hack any Email account
Hack and improve your credit card, Social Media Accounts: Instragram,
Facebook, Twitter, Whatsapp etc. contact: hacktechspy@gmailcom4 -
How to Recover Your Stolen Crypto Funds with Zenith Hackers Intelligent
Have you ever experienced the heartbreaking agony of losing your cryptocurrency assets due to hacks, scams, or forgotten wallets? Let me introduce you to ZENITH HACKERS INTELLIGENT, your ideal ally in cryptocurrency recovery! Many people have used their skills to successfully navigate the intricate labyrinth of blockchain networks and restore access to their hard-earned cryptocurrency. Imagine waking up one day and discovering that your lost investments have been successfully retrieved! ZENITH HACKERS INTELLIGENT restores hope and empowers cryptocurrency enthusiasts by tackling seemingly hard tasks. With them at your side, you're not simply recovering funds; you're regaining financial independence! Don't wait any longer—let Zenith transform your misery into ecstasy today!
Visit Website; zenithhackers. com
Whatsapp/Call- +44(755)248-6027
Email; Zenithintel@ consultant. com7 -
Hello everyone, my name is Hayes Woodie . Am from Los Angeles California. I want to introduce a good testimonies
Are you experiencing great difficulty accessing your bitcoin wallet or, for some reason, are you becoming a victim of btc scammers? You can trust Schwartz Software Hackers Services to successfully retrieve your stolen funds. Schwartz Software Hackers Services assisted me in regaining access to my Bitcoin wallet after I had lost it. I input a URL incorrectly and lost access to my wallet, which had a lot of money. I'm relieved that Schwartz Software Hackers Services helped me and prevented anything from being taken from my wallet by acting quickly. I'm appreciative of this. They can also assist you in recovery of your stolen funds or funds being held by fake investment scheme
Email: (schwartzsoftwarehackingprogram at gmail dot com) 1
1 -
Bwhahahah! Even after the excitement, business disruption, unpleasantness and pain, GDPR fails at its one job
https://newstatesman.com/science-te...1 -
How To Hire A Professional To Change Your Grades
In the competitive world of education, the pressure to maintain perfect grades can be overwhelming. Students face countless assignments, exams, and projects, all of which contribute to their overall academic performance. Being a student in the university, college, or high school can be stressful. Having poor final grades can be devastating to a graduation and career trajectory. Having the mindset of not graduating and repeating a harder test have forced students to seek hacker to change school grades and statistic is on the high on grade change globally.
When you need a hacker to change your university grades, think of genuine hackers for hire, and ethical hackers also comes to mind. Don't hesitate to send a mail to TECHIEMAESTRO at INBOX dot RU
He's the best professional for hire. I hereby recommend him everyone. He also provides other range of hacking related services.2 -
Investing in cryptocurrency is a good idea. At the start of my cryptocurrency journey, I invested in a faux trading company who took over 90,000 Dogecoin and 2 BTC from me. It was a hell of a time for me, I was in urgent need for a recovery expert to get my funds and Century Hackers Recovery came to my rescue. He was useful from the point of contact to the end when he retrieved my funds from the bogus company and placed me on a genuine trading platform where I earned lot of profits. I’ll urge you to use the services of Century Hackers if you are in a similar situation which I was at that time. Send a mail today Via Email: century[@]cyberservices[.]com
WhatsApp: +1[386] [260] [8052]1 -
My purpose in writing is to educate the general public about PROFESSIONAL WIZARD HACKERS RECOVERY . If you ever need hacking services, look no further. I found myself in a difficult situation after losing almost $415,000 USD in bitcoin. I was distraught, divasted and thought I had hit my lowest point, I had no chance of recovering my investment. When I came across PROFESSIONAL WIZARD HACKERS, everything changed completely. The PROFESSIONAL WIZARD HACKERS stepped in and quickly assisted me in recovering my entire refund. They guarantee their clients the highest level of happiness and their services are highly recommended and very low cost with fast respond. Contact customer service via whatsapp: +44 7442 684 963
fast reply: professionalwizardrecovery at gmail dot com
Email address: ( professionalwizardrecovery at programmer dot net )1 -
Yes! Having the mentality of not graduating and having to repeat difficult exams forces students to look for hackers to change school grades and worldwide statistics are on the high-grade change. It is very easy to find a hacker on the internet and accept his services. Anyone can do this at home through their mobile and internet.1
-
My name is Frank S. Monnett, and I want to share my incredible experience with Santoshi Hackers Intelligence (SHI). On June 1, 2023, I faced a devastating loss of $65,600 through my Coinbase account. When the SHI team explained how they would use Tokenomics to recover my funds, I was initially skeptical, thinking it might just be another marketing gimmick.
To my absolute shock, within less than 24 hours, I saw my $65,600 successfully restored to my Coinbase Ethereum wallet. SHI’s expertise in cybersecurity and their deep understanding of the crypto ecosystem are nothing short of remarkable.
SHI plays no games—they are professionals who deliver on their promises. I cannot thank the team enough for their swift and effective action on my case. I wholeheartedly recommend Santoshi Hackers Intelligence to anyone facing similar issues. Their work is truly extraordinary!5 -
A RELIEF FOR CRYPTO SCAM VICTIMS THROUGH SYNACK HACKERS
I understand the frustration and stress associated with lost funds through investment scams. They got me and did away with almost half a million dollars. Luckily, I have some influences around who introduced me to an organization called Synack Hackers. As specialists in crypto recovery, the team of expert professionals is dedicated to helping individuals and businesses reclaim their lost money lost to investment scams. With their proven track record and exceptional customer service, they are the go-to company for fund recovery in Montreal and beyond. We were able to track them down and got the complete amount. Reach out to Synack Hackers via the following contact information.
Email: (synackhack{@}tech{-}center{.}com)9 -
Posted on indie hackers if anyone fancies reading my short blog on launching SongBox
https://indiehackers.com/forum/... -
Employ Zenith Hacker Intelligent Now! Expert in Cryptocurrency Recovery?
Subject: Services for Cryptocurrency Recovery
Are you having trouble recovering your cryptocurrency? You don't need to search any farther! I'm happy to present Zenith Hackers, knowledgeable, accomplished professionals in this domain. Zenith Hackers Intelligent can help you effectively recover your assets because of their vast experience and track record of success.
For a customized consultation,
Contact : +44 7552 486027
Secure your investments now without delay!1 -
Don't go further looking for a hacker jbeespyhack at gmail com has proved that there's still a genuine hacker. After my past with some hackers. Stay safe3
-
Hire Zenith's Hackers Intelligent To Recover Lost or Stolen Crypto/Bitcoin
As a CBS News Anchor, I, Anthony Mason, wish to extend my heartfelt gratitude to Zenith's Hackers Intelligent. Their expertise was instrumental in recovering my lost cryptocurrency valued at $860,000 USD in Ethereum. Their commitment and professionalism during this challenging time were truly commendable. If you're facing similar difficulties or need assistance with your investments, I highly recommend reaching out to them for a customized consultation.
For inquiries, contact:
Email: Zenithintel @ consultant. c om
Web: w w w. zenithhackersintel. co m
CBS News Anchor, Anthony Mason Asher
- CBS News Anchor
- Recover Ethereum
- Zenith's Hackers Intelligent
- Lost crypto assets
- Digital currency recovery3 -
(backendrecoverATrescueteamDOTcom) is the best hacker on lost Bitcoin recovery. Before meeting him I had already encountered five different hackers whom I contacted to help me recover my lost Bitcoin, they all turned out to be fake. I'm glad I didn't give up trying to recover my money from those scammers and I'm glad for my inlaw that introduced me to him. He successfully my €95,0001
-
Who has ever been a victim of a scam? Lost your wallet or money to fake hackers online? I'll implore you to contact this trustworthy hacker and recovery expert Backendrecover. I was a victim of fake people posing as binary options and bitcoin investors, I lost the sum of $45,000 and 1BTC from my bitcoin wallet to them. It took a while before I realized they were scams and this really hurt .Then an in-law of mine heard about it and recommended to me a recovery hack specialist . He helped me recover my lost bitcoins and the fakes were caught and made to pay for what they did to me .if you have lost any amount to online scams and you’re seeking to recover them, in fake hackers, online dating scams, btc wallet hack, fake binary investors .Reach out to (hackingprofessional3 gmail com) to help you ,and you will be so glad you did so.1
-
Employ Zenith Hacker Intelligent Now! Expert in Cryptocurrency Recovery?
Subject: Services for Cryptocurrency Recovery
Are you having trouble recovering your cryptocurrency? You don't need to search any farther! I'm happy to present Zenith Hackers, knowledgeable, accomplished professionals in this domain. Zenith Hackers Intelligent can help you effectively recover your assets because of their vast experience and track record of success.
For a customized consultation,
Secure your investments now without delay!2