Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "it security hackers"
-
A group of Security researchers has officially fucked hardware-level Intel botnet officially branded as "Intel Management Engine" they did so by gathering it all the autism they were able to get from StackOverflow mods... though they officially call it a Buffer Overflow.
On Wednesday, in a presentation at Black Hat Europe, Positive Technologies security researchers Mark Ermolov and Maxim Goryachy plan to explain the firmware flaws they found in Intel Management Engine 11, along with a warning that vendor patches for the vulnerability may not be enough.
Two weeks ago, the pair received thanks from Intel for working with the company to disclose the bugs responsibility. At the time, Chipzilla published 10 vulnerability notices affecting its Management Engine (ME), Server Platform Services (SPS), and Trusted Execution Engine (TXE).
The Intel Management Engine, which resides in the Platform Controller Hub, is a coprocessor that powers the company's vPro administrative features across a variety of chip families. It has its own OS, MINIX 3, a Unix-like operating system that runs at a level below the kernel of the device's main operating system.
It's a computer designed to monitor your computer. In that position, it has access to most of the processes and data on the main CPU. For admins, it can be useful for managing fleets of PCs; it's equally appealing to hackers for what Positive Technologies has dubbed "God mode."
The flaws cited by Intel could let an attacker run arbitrary code on affected hardware that wouldn't be visible to the user or the main operating system. Fears of such an attack led Chipzilla to implement an off switch, to comply with the NSA-developed IT security program called HAP.
But having identified this switch earlier this year, Ermolov and Goryachy contend it fails to protect against the bugs identified in three of the ten disclosures: CVE-2017-5705, CVE-2017-5706, and CVE-2017-5707.
The duo say they found a locally exploitable stack buffer overflow that allows the execution of unsigned code on any device with Intel ME 11, even if the device is turned off or protected by security software.
For more of the complete story go here:
https://blackhat.com/eu-17/...
https://theregister.co.uk/2017/12/...
I post mostly daily news, commentaries and such on my site for anyone that wish to drop by there 19
19 -
I wonder why banks are always so terribly insecure, given how much money there's for grabs in there for hackers.
Just a while ago I got a new prepaid credit card from bpost, our local postal service that for some reason also does banking. The reason for that being that - thank you 'Murica! - a lot of websites out there don't accept anything but credit cards and PayPal. Because who in their right mind wouldn't use credit cards, right?! As it turns out, it's pretty much every European I've spoken to so far.
That aside, I got that card, all fine and dandy, it's part of the Mastercard network so at least I can get my purchases from those shitty American sites that don't accept anything else now. Looked into the manual of it because bpost's FAQ isn't very clear about what my login data for their online customer area now actually is. Not that their instruction manual was either.
I noticed in that manual that apparently the PIN code can't be changed (for "security reasons", totally not the alternative that probably they didn't want to implement it), and that requesting a forgotten PIN code can be done with as little as calling them up, and they'll then send the password - not a reset form, the password itself! IN THE FUCKING MAIL.
Because that's apparently how financial institutions manage their passwords. The fact that they know your password means that they're storing it in plain text, probably in a database with all the card numbers and CVC's next to it. Wouldn't that be a treasure trove for cybercriminals, I wonder? But YOU the customer can't change your password, because obviously YOU wouldn't be able to maintain a secure password, yet THEY are obviously the ones with all the security and should be the ones to take out of YOUR hands the responsibility to maintain YOUR OWN password.
Banking logic. I fucking love it.
As for their database.. I reckon that that's probably written in COBOL too. Because why wouldn't you.23 -
!rant
The change log from notepad++ update. The last paragraph is the cream!
" The issue of a hijacked DLL concerns scilexer.dll (needed by Notepad++) on a compromised PC, which is replaced by a modified scilexer.dll built by the CIA. When Notepad++ is launched, the modified scilexer.dll is loaded instead of the original one.
It doesn't mean that CIA is interested in your coding skill or in your sex message content typed in Notepad++, but rather it prevents raising any red flags while the DLL does data collection in the background.
It's not a vulnerability/security issue in Notepad++, but for remedying this issue, from this release (v7.3.3) forward, notepad++.exe checks the certificate validation in scilexer.dll before loading it. If the certificate is missing or invalid, then it just won't be loaded, and Notepad++ will fail to launch.
Checking the certificate of DLL makes it harder to hack. Note that once users’ PCs are compromised, the hackers can do anything on the PCs. This solution only prevents from Notepad++ loading a CIA homemade DLL. It doesn't prevent your original notepad++.exe from being replaced by modified notepad++.exe while the CIA is controlling your PC.
Just like knowing the lock is useless for people who are willing to go into my house, I still shut the door and lock it every morning when I leave home. We are in a f**king corrupted world, unfortunately. "2 -
PM ordered me to not use encryption for customer authentication links because we want to be able so send same link if the user loose it. "we have to prioritize usability over security". At least I can tell future hackers it's not my fault..
 10
10 -
Taking IT classes in college. The school bought us all lynda and office365 accounts but we can't use them because the classroom's network has been severed from the Active Directory server that holds our credentials. Because "hackers." (The non-IT classrooms don't have this problem, but they also don't need lynda accounts. What gives?)
So, I got bored, and irritated, so I decided to see just how secure the classroom really was.
It wasn't.
So I created a text file with the following rant and put it on the desktop of the "locked" admin account. Cheers. :)
1. don't make a show of "beefing up security" because that only makes people curious.
I'm referring of course to isolating the network. This wouldn't be a problem except:
2. don't restrict the good guys. only the bad guys.
I can't access resources for THIS CLASS that I use in THIS CLASS. That's a hassle.
It also gives me legitimate motivation to try to break your security.
3. don't secure it if you don't care. that is ALSO a hassle.
I know you don't care because you left secure boot off, no BIOS password, and nothing
stopping someone from using a different OS with fewer restrictions, or USB tethering,
or some sort malware, probably, in addition to security practices that are
wildly inconsistent, which leads me to the final and largest grievance:
4. don't give admin priveledges to an account without a password.
seriously. why would you do this? I don't understand.
you at least bothered to secure the accounts that don't even matter,
albeit with weak and publicly known passwords (that are the same on all machines),
but then you went and left the LEAST secure account with the MOST priveledges?
I could understand if it were just a single-user machine. Auto login as admin.
Lots of people do that and have a reason for it. But... no. I just... why?
anyway, don't worry, all I did was install python so I could play with scripting
during class. if that bothers you, trust me, you have much bigger problems.
I mean you no malice. just trying to help.
For real. Don't kick me out of school for being helpful. That would be unproductive.
Plus, maybe I'd be a good candidate for your cybersec track. haven't decided yet.
-- a guy who isn't very good at this and didn't have to be
have a nice day <3
oh, and I fixed the clock. you're welcome.2 -
Oh well, it was just a countdown until somebody finds a way to create the mask.
"On Friday, Vietnamese security firm Bkav released a blog post and video showing that—by all appearances—they'd cracked Face ID with a composite mask of 3-D-printed plastic, silicone, makeup, and simple paper cutouts, which in combination tricked an iPhone X into unlocking."
"But they say that it was based in part on the realization that Face ID's sensors only checked a portion of a face's features, which WIRED had previously confirmed in our own testing."
source: https://wired.com/story/...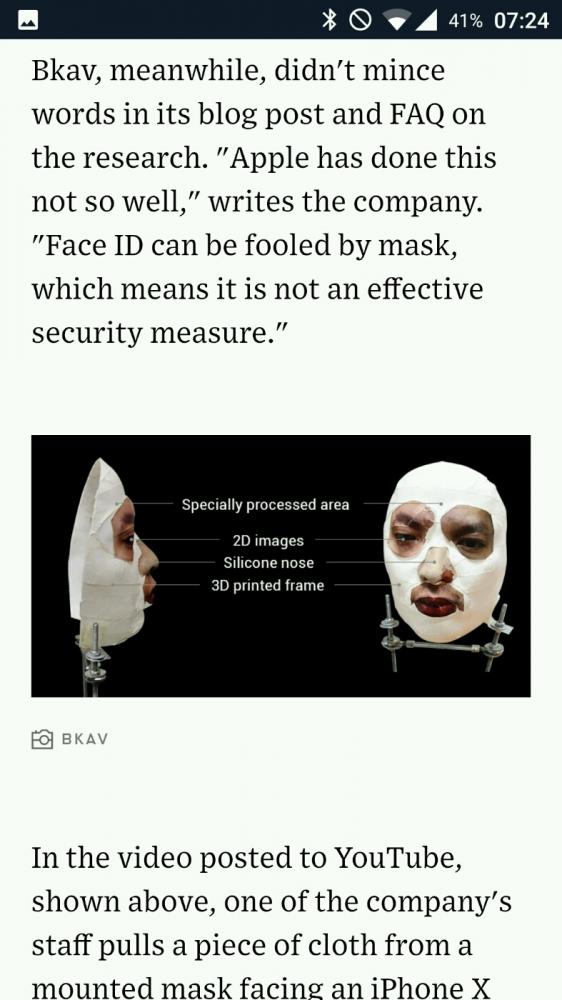 5
5 -
Hmm...recently I've seen an increase in the idea of raising security awareness at a user level...but really now , it gets me thinking , why not raise security awareness at a coding level ? Just having one guy do encryption and encoding most certainly isn't enough for an app to be considered secure . In this day an age where most apps are web based and even open source some of them , I think that first of all it should be our duty to protect the customer/consumer rather than make him protect himself . Most of everyone knows how to get user input from the UI but how many out here actually think that the normal dummy user might actually type unintentional malicious code which would break the app or give him access to something he shouldn't be allowed into ? I've seen very few developers/software architects/engineers actually take the blame for insecure code . I've seen people build apps starting on an unacceptable idea security wise and then in the end thinking of patching in filters , encryptions , encodings , tokens and days before release realise that their app is half broken because they didn't start the whole project in a more secure way for the user .
Just my two cents...we as devs should be more aware of coding in a way that makes apps more secure from and for the user rather than saying that we had some epic mythical hackers pull all the user tables that also contained unhashed unencrypted passwords by using magix . It certainly isn't magic , it's just our bad coding that lets outside code interact with our own code . -
At a previous job I bumped heads with the IT person a lot because he would spread misinformation about technology so the owners would never replace him. This was conversation with the VP:
VP: Hey I just got a new security setup at my house and I can monitor everything with my phone.
Me: That's cool.
VP: I'm rethinking it because [IT guy] said it was very dangerous to have, what do you think?
Me: ....? What did he say was dangerous about it?
VP: He said hackers could then gain access to cameras and plan the perfect time to rob me since it's in the cloud.
Me: I seriously doubt anyone is planning an Ocean's 11 heist to steal your TV.
VP: Yea I thought it sounded weird when he told me.3 -
I find it hilarious the total misconception of hacking that the general public has. I tell people I know cyber security (Not as much as a lot of people around here) but it is a hobby of mine and I find it very useful/interesting.
But I can't stop but laugh when someone is like, can you get all the text messages my bf receives?
Can you hack this for me can you back that?
C'mon even if I knew how to do that without being caught you think I would even admit that to you. Do hackers just walk around with an index card pasted to their forehead of their skill? It's not even slightly reasonable to think this lol even for someone who doesn't know about the field -
Rant considering the latest Cyber attack and the news around it.
(A recap: a lot of Windows computers were infected with ransomware (due to security hole on Windows), which demanded 300$ in bitcoins to unlock data. After 3 days the price would double, and after 7 days the data was to be deleted)
1) In our country, one of the biggest companies was attacked (car factory). The production stopped and they got for around 1 000 000€ damage in less than 24h (1300 people without work). The news said that they were attacked because they are such a big company and were charged more, as the hackers "knew who they were dealing with" - another reason being the fact that the text was in croatian (which is our neighbor country), but noone realized that it is just a simple google translate of english text - which is obviously not true. The hackers neither know nor care who is hacked, and will charge everyone the same. They only care about the payment.
2) In UK whole (or large part) of medical infrastructure went down. The main thing everyone was saying was: "Nobody's data is stolen". Which, again, is obvious. But noone said anything about data being deleted after a week, which includes pretty much whole electronic medical record of everyone and is pretty serious.
And by the way, the base of the ransomware is code which was stolen from NSA.
All that millions and millions of dollars of damage could be avoided by simply paying the small fee.
The only thing that is good is that (hopefully) the people will learn the importance of backups. And opening weird emails.
P.S. I fucking hate all that 'hacky thingys' they have all over the news.5 -
1. It's gonna be more and more specialized - to the point where we'll equal or even outdo the medical profession. Even today, you can put 100 techs/devs into a room and not find two doing the same job - that number will rise with the advent of even more new fields, languages and frameworks.
2. As most end users enjoy ignoring all security instructions, software and hardware will be locked down. This will be the disadvantage of developers, makers and hackers equally. The importance of social engineering means the platform development will focus on protecting the users from themselves, locking out legitimate tinkerers in the process.
3. With the EU getting into the backdoor game with eTLS (only 20 years after everyone else realized it's shit), informational security will reach an all-time low as criminals exploit the vulnerabilities that the standard will certainly have.
4. While good old-fashioned police work still applies to the internet, people will accept more and more mass surveillance as the voices of reason will be silenced. Devs will probably hear more and more about implementing these or joining the resistance.
5. We'll see major leaks, both as a consequence of mass-surveillance (done incompetently and thus, insecurely) and as activist retaliation.
6. As the political correctness morons continue invading our communities and projects, productivity will drop. A small group of more assertive devs will form - not pretty or presentable, but they - we - get shit done for the rest.
7. With IT becoming more and more public, pseudo-knowledge, FUD and sales bullshit will take over and, much like we're already seeing it in the financial sector, drown out any attempt of useful education. There will be a new silver-bullet, it will be useless. Like the rest. Stick to brass (as in IDS/IPS, Firewall, AV, Education), less expensive and more effective.
8. With the internet becoming a part of the real life without most people realizing it and/or acting accordingly, security issues will have more financial damages and potentially lethal consequences. We've already seen insulin pumps being hacked remotely and pacemakers' firmware being replaced without proper authentication. This will reach other areas.
9. After marijuana is legalized, dev productivity will either plummet or skyrocket. Or be entirely unaffected. Who cares, I'll roll the next one.
10. There will be new JS frameworks. The world will turn, it will rain.1 -
I got so many concerns/questions about the EU chat control and the future. Sorry for my long rant lol:
1) What about projects that are on life support and no active development?
2) What about chat application in video games or the chat service on the website of a local shop
3) What about false flags? Like that parent who got into legal trouble for sharing a picture of his kid with a doctor to get a medical opinion on some skin condition. (might misremember the details)
4) What about false flags like instagram banning accounts and forwarding it to the police department and over-exhausting the resources of the police (accidental 'DDOS' of their personel)
5) What if the content shared in country A is legally OK but not in country B. What if you then travel there? Or if your participant is from that country B.
6) What about content that is taboo but should be OK to discussed? Like puberty or hormonal discussions online? Some subreddits like "stopsmoking" is now also regional banned by Reddit in the UK to avoid any unneeded risks. That is bad. YouTube had some problem where adult content existed on their platform but labeled as educational.
7) What if you encrypt messages before sending it. Will you be banned just in case? What if you need support with an app and you send an encrypted application crash log that came from your computer, will you now be banned just in case?
8) What if you like privacy and have those apps for innocent purposes. Is having those apps now illegal
9) What if criminals use apps from Asia or Africa or somewhere where this law is not present/enforced. Or what if they create a simple app with this encryption. It is not difficult to make one.
10) Before 2001, airport security was very lax but then 9/11 happened and the security increased. It never went back to the state before. Since they have or will have this check, what will them stop it from expanding it after the next disaster of an unrelated accident (like terrorist attack).
11) What if those services miss a case? Will the company that allows this to be send now have legal trouble?
12) What if users are using metaphors or practice self-censorship to avoid flagged words? We see it with monetization in social media (like murder or killing is replaced with "unaliving")
13) It will be just an other problem to start a new company with limited budget. So start-ups will just have a bit harder time to break into the market.
14) this might just push users away from mainstream options
15) it's just an other attack vector for hackers to use
16) Do we want to have private companies be able to scan our messages because they are contracted by the government? They can have their own bias to satisfy their shareholders. What if they are invested by the Big Oil so critic towards the Big Oil is altered? How certain can you be this won't happen now or in the future. Reddit Admin did that before so who knows at this point.
17) Anonymity will disappear.
18) Different companies verify users and store this data so this seems like a major cyberrisk and identity theft waiting to happen
19) fragmentation of users. it is now annoying that some family or friends don't use whatsapp but use telegram and the other way around. You might need +5 chat application to keep contact and lose social relationships.
20) Is AI detected messages even legal proof in court?
21) What if you talk about video games and flag the AI system this way? Or use abbreviation from a niche community that also overlaps with flagged words (like checkpoint being abbreviated as CP) or just the language with poor support or use a 'dialect' in your chat that trips up the software.
22) What if your phone is stolen and they send those messages in your name or this is done remotely.
23) What if you are sharing old family pictures and there is 1 and only 1 odd picture that just barely trips up the system.
24) Games like 'Beyond human' also has gameplay that hurts a fictional child which fits the storyline and acts as shock value. Will this be banned
25) The newer population will see this as normal so what will they find acceptable if they can now vote7 -
"The Phoenix project" alternative ending:
Bill Palmer manages to avert disaster with heroic efforts, working 18 hours per day for weeks.
His wife files for divorce. He starts to sleep at office, next to the servers room.
At the last moment a huge hacker attack almost destroys everything, but he finally manages to announce that Phoenix is ready on time, security auditing passed and any kind of great improvements.
Steve, the CEO, calls him and says: "are you crazy? we put you on an impossible project with short notice to make you fail! All our investors have been secretly short selling our stocks, so now they are waiting a big failure to cash in. We also paid korean hackers to bring you on your knees. But you are really stubborn! "
All Phoenix Project is rolled back, huge shit happens, stocks fall, investors ripe great benefits. All IT is outsourced to an external company (owned by members of the board)
Bill is fired. His reputation tainted by the failure, he can't find job anymore. his technical skills and knowledge are out of date.
As he didn't have time to take care of divorce he has lost also all his personal wealth.
He writes a book about his experience, well, actually a rant, but the company sues him forcing him to pay more money.
In the final scene, police arrests him, drunk while trying to burn a server farm with matches. -
Dude at work floats the idea of creating separate Github accounts for personal and work for security. My response:
While we're discussing options, we should also consider maintaining a list of users as a CSV^H^H^H MS Excel file, and install an authentication server that runs off the laptop of an "IT Administrator". That way it'll be super secure because hackers cannot access any system outside of working hours, as well as the days that said admin is off from work. 2
2 -
Avoided IoT(IoS - InternetOfShit) for a long time now, due to the security concerns with retail products.
Now I looked into 433 Transceiver + Arduino solutions.. to build something myself, just for the lolz.
Theory:
Smallest Arduino I found has 32 KByte of programmable memory, a tiny tiny crypto library could take around 4 KBytes...
Set a symetric crypto key for each homebrewn device / sensor / etc, send the info and commands (with time of day as salt for example) encrypted between Server <-> IoT gadget, ciphertext would have checksum appended, magic and ciphertext length prepended.
Result:
Be safe from possible drive-by attacks, still have a somewhat reliable communication?!
Ofc passionate hackers would be still able to crack it, no doubt.
Question: Am I thinking too simple? Am I describing just the standard here?14 -
I can't believe companies fucking do this! If your users PIIs gets fucking leaked or the security is breached in any god-damned way it's YOUR FUCKING JOB to let the affected users know! 57 million users got affected! What the fucking fuck? I think they should pass proper laws where companies have to tell the victims about breaches, especially when it's at a such a huge scale. I get it that it's wasn't under Uber but some third party; but even so Uber should have talked about the level of security in their SLAs and maybe performed regular audits.
This is ridiculous!
https://darkreading.com/attacks-bre... 5
5 -
I'd love to get into a career within the cyber security industry.
Anyone got advice?
I've played around with Kali/Parrot and setup a proxmox box to perform pen testing and have a fair number of PDF ebooks and audio books on networks, security and pen testing12 -
PHP is so insecure and vulnerable that it makes me feel unsafe. It has so many features and settings that can lead to security risks, such as register_globals, magic_quotes, and allow_url_fopen. It also has so many functions that can execute arbitrary code or commands, such as eval, exec, and system.
It is like PHP was designed by a bunch of hackers who wanted to exploit every possible loophole.8 -
Recovering Investment Losses with GearHead Engineers Cyber Security Services
In today’s increasingly digital financial landscape, investors face growing threats from cybercriminals targeting everything from brokerage accounts to blockchain-based assets. For individuals and businesses alike, falling victim to a cyberattack or financial scam can be devastating. Fortunately, firms like GearHead Engineers, known for their advanced cybersecurity services, are stepping in to help investors recover losses and, more importantly, prevent future breaches.
The Rise of Cyber-Investment Threats
As digital platforms have become the norm for managing investments, they’ve also become a prime target for hackers. Common threats include:
* Phishing scams that trick users into revealing login credentials.
* Ransomware attacks on financial firms.
* Malware that siphons personal and financial data.
* DeFi and cryptocurrency hacks exploiting insecure smart contracts or user wallets.
The financial implications can be enormous, especially when assets are stolen, trading accounts are compromised, or confidential investment strategies are exposed.
GearHead Engineers: A Cybersecurity Partner for Investors
GearHead Engineers specializes in protecting financial data, systems, and transactions with comprehensive cybersecurity strategies tailored to modern digital investment environments. Their services include:
* Threat Detection & Response: 24/7 monitoring of systems to identify unusual activity before it becomes a serious threat.
* Incident Forensics: In the event of a breach, GearHead Engineers conduct thorough investigations to trace the source, identify vulnerabilities, and assist in recovery efforts.
* Asset Recovery Support: While not a financial firm, GearHead can coordinate with law enforcement and digital forensics specialists to trace stolen digital assets, especially in cryptocurrency-related incidents.
* Security Audits & Penetration Testing: Preemptive testing of platforms and networks to find and fix security holes before hackers do.
* Cyber Insurance Advisory: Guidance on cyber insurance coverage and how to maximize your protection and potential reimbursement in case of a loss.
Real-World Application: Turning Loss into Learning
Clients who’ve suffered financial loss due to cyber incidents often find that working with cybersecurity experts like GearHead Engineers is a turning point. Not only can the firm help assess whether any funds are recoverable (especially in crypto and digital asset cases), but it also strengthens the client's defense moving forward.
By implementing robust firewalls, multi-factor authentication, encryption, and behavioral analytics, GearHead Engineers empowers investors to take control of their digital financial security.
Conclusion: Proactive Security is Smart Investment Strategy
Recovering from a cyberattack is never easy, but it’s possible—especially with the right partners. GearHead Engineers brings a unique blend of technical expertise and practical support to help victims of cyber fraud bounce back and secure their future. For investors, engaging in strong cybersecurity isn’t just risk management—it’s a smart investment in itself.4 -
How I was Able to Recover My Lost Cryptocurrency with the help of OPTIMISTIC HACKER GAIUS
My name is Mark Wong and I'm from Barcelona, Spain.
Before my computer was stolen two weeks ago, I had been saving in my cryptocurrency wallet for years. I was upset and thought there was no chance I would ever get my data and assets back. I went to the authorities, but they were unable to assist me in recovering my cryptocurrency assets. It wasn't until I found a website about the https: // optimistichackergaius. c o m company, a reputable security firm that has been successfully recovering cryptocurrency and data for years. I contacted them regarding my account, and within 72 hours, OPTIMISTIC HACKER GAIUS was able to recover my cryptocurrency assets and data, as well as protect my wallet and data from hackers. I sincerely appreciate it for their service, and I can guarantee that they have a 100% success rate. 1
1 -
WIZARD ASSET RECOVERY THE BEST EXPERTS FOR BITCOIN AND CRYPTO
Empowering Recovery: Wizard Asset Recovery as Your Trusted Bitcoin and Crypto Expert
In the vast and evolving landscape of cryptocurrency, the unfortunate reality of scams, hacks, and thefts looms large, posing significant risks to investors worldwide. Amidst the chaos, the need for reliable and effective recovery services has never been more crucial. Join us on a comprehensive exploration as we unveil Wizard Asset Recovery as the ultimate solution for recovering lost Bitcoin and crypto assets, empowering individuals and businesses to reclaim what is rightfully theirs and restore financial security.
Understanding the Challenges of Cryptocurrency Recovery
Cryptocurrency recovery presents a myriad of challenges, from navigating complex blockchain transactions to dealing with elusive hackers and fraudulent schemes. The decentralized nature of cryptocurrencies, coupled with the anonymity they provide, often makes it challenging to trace and recover lost funds. Additionally, the lack of regulatory oversight and jurisdictional issues further complicate recovery efforts, leaving victims feeling overwhelmed and helpless. In the face of these challenges, the expertise of a trusted recovery expert becomes invaluable.
Introducing Wizard Asset Recovery: Your Trusted Partner in Cryptocurrency Recovery
Wizard Asset Recovery emerges as a beacon of trust and expertise in the realm of cryptocurrency recovery, offering a comprehensive suite of services designed to address the unique needs of each client. As a leading recovery expert, Wizard Asset Recovery boasts a team of seasoned professionals with extensive experience in navigating the complexities of cryptocurrency theft and fraud. Their proven track record of success, coupled with their commitment to client satisfaction, sets them apart as the go to solution for recovering lost Bitcoin and crypto assets.
Why Choose Wizard Asset Recovery?
1. Expertise and Experience: With years of experience in cryptocurrency recovery, Wizard Asset Recovery possesses the knowledge, skills, and resources necessary to tackle even the most challenging cases with precision and efficiency.
2. Comprehensive Services: From initial consultation to forensic analysis and legal advocacy, Wizard Asset Recovery offers a comprehensive range of services tailored to meet the unique needs of each client.
3. Transparency and Communication: Throughout the recovery process, Wizard Asset Recovery maintains transparent communication with clients, providing regular updates and guidance every step of the way.
4. Proven Track Record: With numerous successful recoveries and satisfied clients, Wizard Asset Recovery has established itself as a trusted leader in the field of cryptocurrency recovery, earning accolades for its dedication to excellence and client satisfaction.
How Wizard Asset Recovery Works:
1. Initial Consultation: Contact Wizard Asset Recovery via email or WhatsApp to schedule an initial consultation. Provide details about the loss of your Bitcoin or crypto assets, including any evidence or documentation you may have.
2. Assessment and Proposal: Upon engagement, Wizard Asset Recovery will conduct a thorough assessment of your case and provide a tailored proposal outlining their recommended approach to recovery and associated costs.
3. Recovery Process: Leveraging advanced technology and forensic analysis, Wizard Asset Recovery will work tirelessly to trace and recover your lost Bitcoin or crypto assets, keeping you informed and updated on the progress of your case.
4. Resolution and Support: Throughout the recovery process, Wizard Asset Recovery will provide ongoing support and guidance, advocating for your interests and ensuring a satisfactory resolution to your case.
Reclaiming Financial Security with Wizard Asset Recovery
In the face of cryptocurrency theft or fraud, Wizard Asset Recovery stands as a trusted partner for individuals and businesses seeking restitution. With their expertise, dedication, and client centric approach, Wizard Asset Recovery empowers clients to reclaim their lost Bitcoin and crypto assets, restoring financial security and peace of mind. Don't let the complexities of cryptocurrency recovery deter you – trust in Wizard Asset Recovery to guide you through the process with confidence and expertise.
Contact Information:
Email: wizardassetrecovery@gmx.us
Reclaim your financial sovereignty today with Wizard Asset Recovery. Let their team of experts navigate the complexities of cryptocurrency recovery on your behalf, allowing you to reclaim what is rightfully yours and move forward with confidence.7 -
**HOW TO RECOVER YOUR MONEY FROM FAKE CRYPTO INVESTMENT SCAMMERS → CONTACT HACKATHON TECH SOLUTION**
It all began innocently enough, with the allure of quick gains and financial freedom beckoning me into the world of cryptocurrency investments. Little did I know, this journey would lead me down a path of deceit and betrayal. On the first of last month, I took the plunge and invested $3000 in USDT, hoping to see my money grow. To my delight, by the 15th of the month, I received a withdrawal of $10,000, fueling my excitement and confidence in the investment platform. With newfound optimism, I decided to up the ante, investing $50,000 with the expectation of reaping even greater returns. However, as the withdrawal deadline approached, reality came crashing down around me. It became painfully clear that I had been duped, lured in by promises of riches that were nothing but empty lies. My hard-earned money was gone, vanished into the digital abyss, and I was left reeling from the betrayal. Determined to reclaim what was rightfully mine, I embarked on a journey of seeking recovery experts who could help me navigate the treacherous waters of online fraud. Yet, at every turn, I encountered charlatans and impostors, preying on the vulnerability of those who had been deceived. It was in my darkest hour that I stumbled upon a glimmer of hope – a review praising the commendable work of HACKATHON TECH SOLUTION, a team of ethical hackers dedicated to righting the wrongs of cybercrime. With nothing left to lose, I placed my trust in their capable hands, praying for a miracle. And miraculously, a miracle is what I received. HACKATHON TECH SOLUTION not only delivered on their promise but exceeded all expectations, successfully recovering my lost funds with a level of expertise and professionalism that left me in awe. In return for their invaluable service, they requested a modest 10% fee, a small price to pay for the restoration of my financial security. Thanks to the unwavering dedication of HACKATHON TECH SOLUTION, I am once again standing on solid ground, free from the shackles of financial fraud. My faith in humanity has been restored, and while the scars of my ordeal may linger, they serve as a solemn reminder to tread carefully in the digital realm. To anyone who finds themselves in a similar predicament, I urge you not to lose hope. Reach out to HACKATHON TECH SOLUTION and take the first step towards reclaiming what is rightfully yours. In a world fraught with deception, they are a beacon of light, guiding you towards justice and resolution. Trust in HACKATHON TECH SOLUTION– your ally in the fight against cybercrime.Reach out to HACKATHON TECH SOLUTIONS via below contact details
Email: info(@)hackathontechsolution(.)com
Website:www(.)hackathontechsolutions(.)com
Whatsapp: +31 6 47999256
Telegram: @hackathontechsolutions4 -
Email: casefile @ shi -us . com
I lost my MacBook laptop some time ago alongside my iphone 16, in that process all my crypto coinbase accounts, about 3 of them, I had difficulties logging in and I consulted lots of agencies to assist but all to no avail, until I came across Santoshi Hackers Intelligence and within a twinkle of an eye it was all done.
If you suspect your Credit card, email & password, Facebook, Instagram, twitter Accounts has been hacked, you need to Recover stolen money from scammers, reports the incident to Santoshi Hackers Intelligence they can help you recover your BTC by providing an experience team of security experts and forensic investigators who can investigate the loss, identify the source of the compromise, Santoshi we help you retrieve your stolen currency, in addition, Santoshi Hackers Intelligence can provide you with educational materials for staying safe online and give you access to cutting_edge cyber threat intelligence. They can also identify potential security breaches or vulnerabilities that may have led to the loss of your information.
Above is the email address to reach Santoshi Hackers Intelligence.1 -
HOW TO RECOVER STOLEN OR LOST BITCOIN/MALICE CYBER RECOVERY WILL SOLVE YOUR PROBLEMS
Empowering Recovery: Choose Malice Cyber as Your Trusted Bitcoin and Crypto Expert
In the vast and evolving landscape of cryptocurrency, the unfortunate reality of scams, hacks, and thefts looms large, posing significant risks to investors worldwide. Amidst the chaos, the need for reliable and effective recovery services has never been more crucial. Join us on a comprehensive exploration as we unveil Malice Cyber Recovery as the ultimate solution for recovering lost Bitcoin and crypt assets, empowering individuals and businesses to reclaim what is rightfully theirs and restore financial security.
Understanding the Challenges of Cryptocurrency Recovery
Cryptocurrency recovery presents a myriad of challenges, from navigating complex blockchain transactions to dealing with elusive hackers and fraudulent schemes. The decentralized nature of cryptocurrencies, coupled with the anonymity they provide, often makes it challenging to trace and recover lost funds. Additionally, the lack of regulatory oversight and jurisdictional issues further complicate recovery efforts, leaving victims feeling overwhelmed and helpless. In the face of these challenges, the expertise of a trusted recovery expert becomes invaluable.
Introducing Malice Cyber Recovery: Your Trusted Partner in Cryptocurrency Recovery
Malice Cyber Recovery emerges as a beacon of trust and expertise in the realm of cryptocurrency recovery, offering a comprehensive suite of services designed to address the unique needs of each client. As a leading recovery expert, Malice Cyber Recovery boasts a team of seasoned professionals with extensive experience in navigating the complexities of cryptocurrency theft and fraud. Their proven track record of success, coupled with their commitment to client satisfaction, sets them apart as the go to solution for recovering lost Bitcoin and crypto assets.
Why Choose Malice Cyber Recovery?
Expertise and Experience: With years of experience in cryptocurrency recovery, Malice Cyber Recovery possesses the knowledge, skills, and resources necessary to tackle even the most challenging cases with precision and efficiency.
Comprehensive Services: From initial consultation to forensic analysis and legal advocacy, Malice Cyber Recovery offers a comprehensive range of services tailored to meet the unique needs of each client.
Transparency and Communication: Throughout the recovery process, Malice Cyber Recovery maintains transparent communication with clients, providing regular updates and guidance every step of the way.
Proven Track Record: With numerous successful recoveries and satisfied clients, Malice Cyber Recovery has established itself as a trusted leader in the field of cryptocurrency recovery, earning accolades for its dedication to excellence and client satisfaction.
How Malice Cyber Recovery Works:
Initial Consultation: Contact Malice Cyber Recovery via email or WhatsApp to schedule an initial consultation. Provide details about the loss of your Bitcoin or crypto assets, including any evidence or documentation you may have.
Assessment and Proposal: Upon engagement, Malice Cyber Recovery will conduct a thorough assessment of your case and provide a tailored proposal outlining their recommended approach to recovery and associated costs.
Recovery Process: Leveraging advanced technology and forensic analysis, Malice Cyber Recovery will work tirelessly to trace and recover your lost Bitcoin or crypto assets, keeping you informed and updated on the progress of your case.
Resolution and Support: Throughout the recovery process, Malice Cyber Recovery will provide ongoing support and guidance, advocating for your interests and ensuring a satisfactory resolution to your case.
Reclaiming Financial Security with Malice Cyber Recovery
In the face of cryptocurrency theft or fraud, Malice Cyber Recovery stands as a trusted partner for individuals and businesses seeking restitution. With their expertise, dedication, and client-centric approach, Malice Cyber Recovery empowers clients to reclaim their lost Bitcoin and crypto assets, restoring financial security and peace of mind. Don't let the complexities of cryptocurrency recovery deter you – trust in Malice Cyber Recovery to guide you through the process with confidence and expertise.
Reclaim your financial sovereignty today with Malice Cyber Recovery. Let their team of experts navigate the complexities of cryptocurrency recovery on your behalf, allowing you to reclaim what is rightfully yours and move forward with confidence. 1
1 -
Empowering Recovery: Choose Malice Cyber as Your Trusted Bitcoin and Crypto Expert
In the vast and evolving landscape of cryptocurrency, the unfortunate reality of scams, hacks, and thefts looms large, posing significant risks to investors worldwide. Amidst the chaos, the need for reliable and effective recovery services has never been more crucial. Join us on a comprehensive exploration as we unveil Malice Cyber Recovery as the ultimate solution for recovering lost Bitcoin and crypto assets, empowering individuals and businesses to reclaim what is rightfully theirs and restore financial security.
Understanding the Challenges of Cryptocurrency Recovery
Cryptocurrency recovery presents a myriad of challenges, from navigating complex blockchain transactions to dealing with elusive hackers and fraudulent schemes. The decentralized nature of cryptocurrencies, coupled with the anonymity they provide, often makes it challenging to trace and recover lost funds. Additionally, the lack of regulatory oversight and jurisdictional issues further complicate recovery efforts, leaving victims feeling overwhelmed and helpless. In the face of these challenges, the expertise of a trusted recovery expert becomes invaluable.
Introducing Malice Cyber Recovery: Your Trusted Partner in Cryptocurrency Recovery
Malice Cyber Recovery emerges as a beacon of trust and expertise in the realm of cryptocurrency recovery, offering a comprehensive suite of services designed to address the unique needs of each client. As a leading recovery expert, Malice Cyber Recovery boasts a team of seasoned professionals with extensive experience in navigating the complexities of cryptocurrency theft and fraud. Their proven track record of success, coupled with their commitment to client satisfaction, sets them apart as the go to solution for recovering lost Bitcoin and crypto assets.
Why Choose Malice Cyber Recovery?
Expertise and Experience: With years of experience in cryptocurrency recovery, Malice Cyber Recovery possesses the knowledge, skills, and resources necessary to tackle even the most challenging cases with precision and efficiency.
Comprehensive Services: From initial consultation to forensic analysis and legal advocacy, Malice Cyber Recovery offers a comprehensive range of services tailored to meet the unique needs of each client.
Transparency and Communication: Throughout the recovery process, Malice Cyber Recovery maintains transparent communication with clients, providing regular updates and guidance every step of the way.
Proven Track Record: With numerous successful recoveries and satisfied clients, Malice Cyber Recovery has established itself as a trusted leader in the field of cryptocurrency recovery, earning accolades for its dedication to excellence and client satisfaction.
How Malice Cyber Recovery Works:
Initial Consultation: Contact Malice Cyber Recovery via email or WhatsApp to schedule an initial consultation. Provide details about the loss of your Bitcoin or crypto assets, including any evidence or documentation you may have.
Assessment and Proposal: Upon engagement, Malice Cyber Recovery will conduct a thorough assessment of your case and provide a tailored proposal outlining their recommended approach to recovery and associated costs.
Recovery Process: Leveraging advanced technology and forensic analysis, Malice Cyber Recovery will work tirelessly to trace and recover your lost Bitcoin or crypto assets, keeping you informed and updated on the progress of your case.
Resolution and Support: Throughout the recovery process, Malice Cyber Recovery will provide ongoing support and guidance, advocating for your interests and ensuring a satisfactory resolution to your case.
Reclaiming Financial Security with Malice Cyber Recovery
In the face of cryptocurrency theft or fraud, Malice Cyber Recovery stands as a trusted partner for individuals and businesses seeking restitution. With their expertise, dedication, and client centric approach, Malice Cyber Recovery empowers clients to reclaim their lost Bitcoin and crypto assets, restoring financial security and peace of mind. Don't let the complexities of cryptocurrency recovery deter you – trust in Malice Cyber Recovery to guide you through the process with confidence and expertise.
Reclaim your financial sovereignty today with Malice Cyber Recovery. Let their team of experts navigate the complexities of cryptocurrency recovery on your behalf, allowing you to reclaim what is rightfully yours and move forward with confidence. 17
17 -
After a catastrophic hack, recovering one's bitcoin holdings can be a difficult and complicated process, but it is possible to recover what was lost with the correct advice and knowledge. In my situation, I was the victim of a very skilled cyberattack that caused my digital assets to instantly disappear from my cryptocurrency wallet. As I struggled with the fact that my financial security had been torn away, panic and despair crept in. But I didn't lose hope, and after doing a lot of research, I found Lee Ultimate Hacker service that is well-known for its capacity to locate and retrieve stolen cryptocurrency. When I contacted their staff, they listened carefully to the specifics of my experience and responded in a kind and sympathetic manner. The Lee specialists started painstakingly tracking the movements of my stolen money, traversing the complex world of cryptocurrency transactions, by utilizing their extensive understanding of blockchain technology and hacking techniques. They pursued the digital trail with unwavering resolve, revealing the intricate network of wallets and exchangers the hackers had employed to hide their activities. The Lee Ultimate team was able to locate my missing assets using their advanced investigative methods and state-of-the-art equipment, which paved the way for the recovery procedure.
What followed was a delicate and intricate operation, as the Lee professionals collaborated with law enforcement agencies and cryptocurrency exchanges to freeze the illicit funds and initiate the retrieval process. This involved navigating a maze of legal and technical hurdles, but the team's expertise and persistence paid off, and eventually, I was overjoyed to see my cryptocurrency holdings restored to my rightful wallet. The sense of relief and restored peace of mind was palpable, and I am forever grateful to the Lee team for their tireless efforts in guiding me through this harrowing ordeal and helping me reclaim what was rightfully mine. For more insight; L E E U L T I M A T E H A C K E R @ A O L . C O M
t e l e g r a m : L E E U L T I M A T E
w h @ t s a p p + 1 ( 7 1 5 ) 3 1 4 - 9 2 4
8 -
HIRE META TECH RECOVERY PRO TO SALVAGE LOST BITCOIN INVESTMENT.META TECH RECOVERY PRO
As a retired doc, I never thought I'd get scammed, especially not out of a whopping $98,000 in Bitcoin, thanks to a terrible forex deal. It was a crazy, hard-to-believe ordeal that left me financially drowned and lost. Realizing I'd seemingly lost all my savings was, to put it mildly, a lot to handle. But, amidst all this financial chaos, hope was restored when I found reviews about META TECH RECOVERY PRO. This sad ordeal started with what looked like a mouth-watering investment. Unfortunately, it was an existing organized fraud scheme, I only realized that after getting in touch with META TECH RECOVERY PRO. The truth hit me hard, and I was left dealing with the fallout, clueless about what to do. The digital world's complexity and the tricky process of getting back lost money made me feel helpless. Luckily, while looking for answers, I saw reviews raving about the skills of META TECH RECOVERY PRO's hackers. Out for a solution, I decided to contact them. The reviews talked about how they helped people like me recover lost Bitcoin investments. With a mix of doubt and hope, I figured I'd give it a try, thinking there might be a chance to get back what I'd lost. In no time, they showed off their digital skills by successfully getting back all my lost funds. I can't even begin to describe how grateful and relieved I felt. Having META TECH RECOVERY PRO on my side was amazing and super helpful. If you, like me, have been ripped off by fake forex brokers and scammers, it's good to know that META TECH RECOVERY PRO is there to help. Their expertise, reliability, and dedication to helping those who've been scammed online are truly impressive. I think having them in your corner gives you a sense of security and a way to get back what's rightfully yours. I wholeheartedly recommend META TECH RECOVERY PRO to anyone who needs help getting back what was stolen from them. You can reach them using the details below:
M e t a t e c h @ W r i t e m e. C o m
W / S +1 4 6 9 6 9 2 8 0 4 9.
THANK YOU. 1
1 -
🚀 “I Wanted GitHub Copilot in My Pocket — So I Built It Myself”
For years, I’ve had this weird habit of coding from random places — cafés, buses, hospital waiting rooms, you name it. But every time inspiration hit, I found myself thinking the same thing:
“Man, I wish I could just use Copilot on my phone.”
It’s 2025. We’ve got AI writing novels, generating music, and summarizing 500-page research papers in 2 seconds — yet somehow, GitHub Copilot still refuses to leave the comfort of VS Code on desktop.
So I decided to fix that.
💡 The Idea
It started as frustration — a “wouldn’t it be cool if” moment. I was halfway through an idea for a small project on a train, and my brain screamed:
“Why can’t I just ask Copilot to finish this function right now?”
VS Code was sitting at home, my laptop was dead, and all I had was my phone.
That night, I scribbled this into my notes app:
“Bridge Copilot from VS Code → phone → secure channel → no cloud.”
At the time, it sounded insane. Who even wants to make their life harder by reverse-engineering Copilot responses and piping them into React Native?
Apparently — me.
🧩 The Architecture (aka “How to Lose Sleep in 4 Easy Steps”)
The system ended up like this:
VS Code Extension <-> WebSocket <-> Discovery API (Go + Redis) <-> React Native App
Here’s how it works:
The VS Code extension runs locally, listening to Copilot’s output stream.
A Go backend acts as a matchmaker — helping my phone and PC find each other securely.
The mobile app connects via WebSocket and authenticates with a 6-digit pairing code.
Once paired, they talk directly. No repo data leaves your machine.
It’s like a tiny encrypted tunnel between your phone and VS Code — only it’s not VPN magic, just some careful WebSocket dancing and token rotation.
🛠️ The Stack
Frontend (Mobile): React Native (Expo)
Backend: Go + Redis for connection brokering
VS Code Extension: TypeScript
Security: JWT + rotating session keys
AI Layer: GitHub Copilot (local interface)
🧠 The Challenges
There’s a difference between an “idea” and a “12-hour debugging nightmare that makes you question your life choices.”
Cross-Network Discovery:
How to connect phone and desktop on different networks?
→ A lightweight Redis broker that just handles handshakes.
Security:
I wasn’t making a mini TeamViewer for hackers.
→ Added expiring pairing codes, user-approval dialogs, and local-only token storage.
Copilot Response Streaming:
Copilot doesn’t have a nice public API.
→ Hooked into VS Code’s Copilot output and streamed it over WebSocket.
(Yes, 2% genius and 98% madness.)
UX:
The first version had a 10-second delay.
After optimizing WebSocket batching and Redis latency, it’s now near-instant.
🤯 The “Holy Sh*t, It Works” Moment
The first time my phone sent a prompt — and my VS Code actually answered with Copilot’s suggestion — I legit screamed.
Like, full-on victory dance in the middle of the night.
There’s something surreal about watching your phone chat with your desktop like they’re old coding buddies.
Now I can literally say:
“Copilot, write me a REST API,”
and my phone responds with fully generated code pulled from my local VS Code instance.
No VPN. No cloud syncing. Just pure, geeky magic.
⚡ The Lessons
The hardest problems aren’t technical — they’re psychological.
Fighting “this is impossible” is the real challenge.
Speed matters more than perfection.
Devs don’t want beauty; they want responsiveness. Anything over 1s feels broken.
Security must never be an afterthought.
I treated this like a bank tunnel between devices, not a toy.
Build for yourself first.
I didn’t make this for investors or glory — I made it because I wanted it.
That’s the best reason to build anything.
🧭 The Future
Now that it’s working, I’m turning this experiment into something shareable.
The dream: an app that lets every developer carry Copilot wherever they go — safely and instantly.
Imagine debugging on your couch, or editing code in bed, or just whispering to your AI assistant while waiting for coffee.
Phones today are more powerful than early NASA computers.
Why shouldn’t they also be your code editor sidekick?
So yeah, that’s my story.
I built VSCoder Copilot — because I wanted to code from anywhere, and I refused to wait for permission.
If you’ve ever built something just to scratch your own itch, you already know this feeling.
That mix of frustration, caffeine, and late-night triumph that reminds you why you fell in love with coding in the first place.
Because at the end of the day, that’s what we do:
We make ideas real — one ridiculous hack at a time. 💻🔥9 -
Learn how to recover lost or stolen cryptocurrency with thorough methods and professional advice. This procedure entails comprehending the complexities of blockchain technology, seeing possible weaknesses, and using cutting-edge recovery methods. You may improve the security of your digital assets by learning about the different techniques that hackers employ. Furthermore, using expert recovery tools and services can greatly improve your chances of recovering cryptocurrency that has been lost or stolen. To protect your investments in the constantly changing world of digital currencies, be proactive and knowledgeable. My name is Patrick Hills, and I would like to talk about how I became a victim of a fraudulent investment scheme nine weeks ago. I couldn't resist the allure of this company's claim to double my income in two weeks. However, the company turned out to be fraudulent, thus I ended up in the wrong hands. They requested more money when I tried to withdraw my alleged earnings after the allotted time. When I learned I had lost everything I had invested, it was a sad time. I started learning how to recover cryptocurrency that has been lost or stolen. In my frustration and desperation, I turned to the internet, hoping to find a solution or at least some guidance. During my search, I stumbled upon numerous reviews praising Wizard James for his expertise in helping people recover lost cryptocurrency. Intrigued and hopeful, I reached out to him for assistance. In addition to recovering my stolen Bitcoin, Wizard James Recovery spent time teaching me Java coding. I now possess the knowledge necessary to better defend myself against scams of this nature in the future thanks to my newfound ability. Wizard James Recovery has given me greater security and knowledge about protecting my digital assets.
Do not hesitate to get in touch with Wizard James Recovery if you need assistance recovering your stolen cryptocurrencies in a similar circumstance. His knowledge and advice can be quite helpful in getting back what you've lost and giving you the means to avoid losing it again.
In conclusion, retrieving lost or stolen cryptocurrency calls for a trifecta of resources, awareness, and diligence. You may better safeguard your digital assets by being aware of potential dangers and comprehending the intricacies of blockchain technology. Asking professionals like Wizard James for help Your chances of recovering and gaining useful talents to stop losses in the future can both be greatly increased with Wizard James Recovery. To protect your interests in the ever-changing world of digital currencies, remain knowledgeable, proactive, and armed with the required resources. Reach them at WIZARDJAMESRECOVERY @ USA . COM right now.1 -
HOW TO RECOVER MONEY LOST TO A FAKE INVESTMENT PLATFORM INTERNET HIRE FOLKWIN EXPERT RECOVERY.
It is so easy to make mistakes while traveling: you are excited, distracted, and sometimes a bit too casual with your security. That's precisely what happened when I accessed my Bitcoin wallet on a public Wi-Fi network during a trip. I sat in a café, sipping my coffee, thinking, "What could go wrong?" Spoiler alert: everything.
I logged in to my wallet, just checking balances and making a few small transfers. But the moment I got on the public network, a hacker struck. I had stupidly left the door wide open, and someone dove in. By the time I tried to log out and lock everything down, it was too late-I was shut out of my $250,000 Bitcoin wallet.
The panic set in faster than I could react. How had I been so careless? Public Wi-Fi is notorious for being unsecured, and yet I took that risk. I had always heard the horror stories of people losing their crypto to hackers, but I never thought it would happen to me. I felt like a complete idiot.
But thankfully, this is where the story turns around. I knew I needed help, and I needed it fast. That's when I called FOLKWIN EXPERT RECOVERY. They got back to me in no time, and to my relief, their team didn't judge me; they just got down to work. I told them my situation-a mixture of embarrassment and frustration. Yet, the calm and professional composure of the people made me feel everything would be alright. They told me then that they had dealt with worse and would recover my money.
In the days that followed, a call came from FOLKWIN EXPERT RECOVERY -it was the news I had been praying for. My wallet had been recovered, and my $250,000, which I'd thought I lost, was safe and sound. I cannot even explain it. Suddenly, a load was lifted off my shoulders.
But that was not all. FOLKWIN EXPERT RECOVERY not only recovered my funds but also took the time to explain how I could protect my wallet while on the road. Now, I always use a VPN when connecting to public Wi-Fi, and I am so much more careful with my security practices.
It’s amazing how a single moment of carelessness can lead to disaster, but I’m grateful for FOLKWIN EXPERT RECOVERY’s expertise in saving me from my own mistake. I’m smarter now, and my Bitcoin wallet is safer than ever. Contact Details below:
WhatsApp:+1 (740)705-0711 or email: FOLKWINEXPERTRECOVERY @ TECH-CENTER (dot) COM for assistance.
Thanks,
Shirley Davis. 1
1 -
I received a prompt and professional response within a single business day of contacting DUNE NECTAR WEB EXPERT. This swift action, in stark contrast to the frustrating delays I had previously encountered, immediately instilled confidence. Their expertise in cybersecurity, particularly within the cryptocurrency domain, is evident in their comprehensive approach. They deeply understand blockchain technology, cryptocurrency protocols, and the intricate methods fraudsters employ. Furthermore, their reputation for integrity and skill is well-established within the industry. Numerous testimonials and case studies highlight their success in recovering stolen digital assets for victims of various cryptocurrency scams. Their dedication to assisting victims is not merely a marketing strategy; it is a core principle guiding their operations. The organization's commitment to ethical practices and client confidentiality further enhances its credibility. Their professional and compassionate approach, characterized by clear communication and regular updates, provided much-needed reassurance during a stressful period. The successful recovery of a significant portion of my stolen assets is a testament to their exceptional abilities and unwavering dedication to their clients. In conclusion, DUNE NECTAR WEB EXPERT offers a vital service in combating the pervasive issue of cryptocurrency fraud, providing a beacon of hope for victims seeking to reclaim their lost assets and regain a sense of security in the digital landscape. Consult DUNE NECTAR WEB EXPERT, as they are worthy and reliable professional hackers your money will count for when you hire them. E-mail (Support @ Dunenectarwebexpert . Com ) Telegram (@Dunenectarwebexpert )
 1
1 -
HIRE THE BEST BITCOIN RECOVERY EXPERT; HOW TO SAFELY RECOVER STOLEN CRYPTOCURRENCY VISIT CYBER CONSABLE INTELLIGENCE
I’ve always felt confident navigating the world of cryptocurrency. As a software engineer, I understood the ins and outs of wallets, private keys, and blockchain security, which made me feel secure in my investments. So, when I found a promising platform that seemed like a great opportunity, I invested $250,000 without hesitation. Unfortunately, I soon learned that my confidence would be shattered by a sophisticated cyber attack. It started with small, unauthorized transactions in my wallet. At first, I thought it was a mistake, but as the activity continued, I realized something was wrong. My wallet had been compromised, but not in the way I had expected. Instead of a simple hack, I had fallen victim to a virus attack. The virus was a piece of malware designed specifically to target cryptocurrency wallets. It infiltrated my system through a vulnerability I hadn’t noticed. Once inside, the virus silently monitored my wallet, captured my private keys, and gave the hackers full access to my funds. It was stealthy and nearly undetectable. The attackers didn’t need to log into my account manually; they could control everything remotely, draining my wallet without my knowledge. I was completely blindsided. As someone familiar with tech, I knew how advanced this virus was. It wasn’t just a typical phishing attack, it was a targeted, silent assault on my financial assets. As my funds disappeared, I realized I might never be able to recover them. Desperate, I turned to a trusted colleague who had gone through a similar situation. They recommended Cyber Constable Intelligence, a company that specializes in recovering stolen crypto assets. I contacted them immediately, and their team quickly started investigating. Cyber Constable Intelligence explained how the virus had exploited a weak point in my security. Using advanced tools, they traced the stolen funds across the blockchain and located them. After a thorough recovery process, they managed to return the entire $250,000.Thanks to their expertise and quick action, I was able to recover my funds. The experience was a wake-up call about how vulnerable even the most cautious can be to sophisticated attacks. Without Cyber Constable Intelligence, I would have lost everything, and I’m grateful for their skill in reversing the damage caused by the virus.
Here's Their Info Below
WhatsApp: 1 (252) 378-7611
mail: cyberconstable @ coolsite net
Website info; www cyberconstableintelligence com1 -
BEST BITCOIN RECOVERY EXPERT: A COMPREHENSIVE GUIDE WITH RAPID DIGITAL RECOVERY
A crypto influencer on TikTok posted about his $100,000 recovery with Rapid Digital Recovery. I was hyped along with him and decided to follow it, just in case. At that time, I wasn't worried, as I did have everything: two-factor authentication, backups on cold storage, and strong passwords. I thought I was untouchable. Wrong.
Months later, I woke up to a nightmare: my wallet, holding $320,000, was completely drained. I checked my email-nothing. I checked my security logs-no alerts. How did this happen? I scrambled through every account, searching for clues. That's when I saw it—a phishing attack. I had clicked on a link for a fake update weeks prior, and the hackers had been patiently waiting for their moment.
Panic set in. I scoured the internet for solutions, but every forum post, every so-called "expert" I contacted-all were saying the same thing: Once it's gone, it's gone. But then I remembered that TikTok post. I DMed the influencer, desperate for an honest answer: Is Rapid Digital Recovery actually legit? The response came immediately. "100%. They saved me. Reach out now."
Website: https: // rapid digital recovery. org
That was all I needed. I contacted Rapid Digital Recovery, hoping for a miracle. From the very first message, they were professional, calm, and insanely knowledgeable. They asked the right questions, identified how my funds had been stolen, and immediately set their forensic recovery tools in motion. While I was drowning in anxiety, they worked methodically, patiently, and relentlessly.
What sapp: +1 4.14 8.0 71.4 8.5
Hours felt like days, then the message came: "We've recovered your funds." I reread it a total of three times. Every last dollar was back. I had gone from devastation to absolute disbelief and relief.
Not only did they recover my money, but they also educated me on what had gone wrong. They walked me through better security practices, helped me secure my wallets properly, and ensured that I'd never fall for the same trick again.
That TikTok post? It saved me. And now, I'm the one telling everyone I know: Follow Rapid Digital Recovery before you ever need them.
Email: rapid digital recovery (@) execs. com 1
1 -
SURVIVING THE BYBIT HACK HOW CRYPTO RECOVERY CONSULTANT SECURE MY ASSETS
It was the kind of morning that left my heart pounding in my chest. My phone buzzed with a series of alerts—emails, messages, all talking about one thing: Bybit had been hacked. North Korean hackers had breached the exchange, and the total losses were over 1.5 billion dollars in cryptocurrency, Ethereum to be precise. My stomach churned as I read, realizing I was one of the many affected. I had been an avid Ethereum investor, with a substantial amount of my savings tied up in the coin. The idea of losing it all was unbearable. But panic was no help, so I immediately began searching for solutions. That’s when I stumbled across a company that specialized in crypto recovery and securing your asset, CRYPTO RECOVERY CONSULTANT. Their website promised to assist with situations just like mine. Skeptical but desperate, I reached out, hoping for a miracle. To my surprise, a representative called me within minutes. They explained that they had experience securing wallets from compromised exchanges and securing coins during massive hacks like the Bybit breach. After a brief consultation, they assured me they could secure my Ethereum by implementing a stronger security system that would block any unauthorized access. They guided me step-by-step, helping me transfer my assets to a more secure wallet and setting up additional layers of protection that I never even knew existed. Thanks to their swift action and expertise, I felt a weight lift from my shoulders. The hackers wouldn’t be able to touch my Ethereum now. My coins were safe, protected by multi-signature authentication, cold storage, and state-of-the-art encryption. Without CRYPTO RECOVERY CONSULTANT, I would have lost everything. Their quick thinking and advanced security measures saved my assets from the grasp of cybercriminals. I couldn’t be more grateful. Now, I sleep soundly, knowing that my Ethereum is safe, all thanks to them. cryptorecoveryconsultant312[@]zohomail,,,com cryptorecoveryconsultant[@]cash4u,,,com 1
1 -
A crypto influencer on TikTok posted about his $100,000 recovery with CRANIX ETHICAL SOLUTIONS HAVEN. I was hyped along with him and decided to follow it, just in case. At that time, I wasn't worried, as I did have everything: two-factor authentication, backups on cold storage, and strong passwords. I thought I was untouchable. Wrong. Months later, I woke up to a nightmare: my wallet, holding $320,000, was completely drained. I checked my email-nothing. I checked my security logs-no alerts. How did this happen? I scrambled through every account, searching for clues. That's when I saw it—a phishing attack. I had clicked on a link for a fake update weeks prior, and the hackers had been patiently waiting for their moment. Panic set in. I scoured the internet for solutions, but every forum post, every so-called "expert" I contacted-all were saying the same thing: Once it's gone, it's gone. But then I remembered that TikTok post. I contacted the influencer, desperate for an honest answer: Is CRANIX ETHICAL SOLUTIONS HAVEN actually legit? The response came immediately. "100%. They saved me. Reach out now." That was all I needed. I contacted CRANIX ETHICAL SOLUTIONS HAVEN, hoping for a miracle. From the very first message, they were professional, calm, and insanely knowledgeable. They asked the right questions, identified how my funds had been stolen, and immediately set their forensic recovery tools in motion. While I was drowning in anxiety, they worked methodically, patiently, and relentlessly. Hours felt like days, then the message came: "We've recovered your funds." I reread it a total of three times. Every last dollar was back. I had gone from devastation to absolute disbelief and relief. Not only did they recover my money, but they also educated me on what had gone wrong. They walked me through better security practices, helped me secure my wallets properly, and ensured that I'd never fall for the same trick again. That TikTok post? It saved me. And now, I'm the one telling everyone I know: Follow CRANIX ETHICAL SOLUTIONS HAVEN before you ever need them.
EMAIL: cranixethicalsolutionshaven @ post . com
WHATSAPP: +44 7460 622730
TELEGRAM: @ cranixethicalsolutionshaven1 -
I’ve always felt confident navigating the world of cryptocurrency. As a software engineer, I understood the ins and outs of wallets, private keys, and blockchain security, which made me feel secure in my investments. So, when I found a promising platform that seemed like a great opportunity, I invested $250,000 without hesitation. Unfortunately, I soon learned that my confidence would be shattered by a sophisticated cyber attack. It started with small, unauthorized transactions in my wallet. At first, I thought it was a mistake, but as the activity continued, I realized something was wrong. My wallet had been compromised, but not in the way I had expected. Instead of a simple hack, I had fallen victim to a virus attack. The virus was a piece of malware designed specifically to target cryptocurrency wallets. It infiltrated my system through a vulnerability I hadn’t noticed. Once inside, the virus silently monitored my wallet, captured my private keys, and gave the hackers full access to my funds. It was stealthy and nearly undetectable. The attackers didn’t need to log into my account manually; they could control everything remotely, draining my wallet without my knowledge. I was completely blindsided. As someone familiar with tech, I knew how advanced this virus was. It wasn’t just a typical phishing attack, it was a targeted, silent assault on my financial assets. As my funds disappeared, I realized I might never be able to recover them. Desperate, I turned to a trusted colleague who had gone through a similar situation. They recommended Hack Buster Recovery, a company that specializes in recovering stolen crypto assets.
 1
1 -
My crypto wallet was compromised when I lost my secret phrase.
Hackers got a hold of my crypto wallet after I lost the seed phrase to my crypto wallet which I had saved to my email.
I had to go through all possible options to get it figured out but I couldn’t, the support system of Coinbase couldn’t help even when I had secured my account with the special seed phrase for extra security, and that was how I lost access to $2m worth of crypto coins.
This was my life savings and investment from my business partners which I had secured in my crypto wallet. Fortunately, I happen to stumble upon a post about MorphoHack Cyber Service, a crypto wallet and funds recovery company. I contacted this team and told them about the whole situation, while I was a bit reluctant about trusting them with my information, it happened there was nothing I couldn’t do to get my funds back so I went with everything they asked, and to my greatest satisfaction, MorphoHack cyber-service was able to give me access to my crypto wallet including securing my crypto wallet from future attempts. I’m in shock and short of words but if you wish to get a hold of them, you can find their contact details below.
MAIL:MorphoHack@CyberServices. com
WHATS APP:+1 213 672- 4092
WEB:MORPHOHACK.WIXSITE. COM/ CYBER1 -
How Hackers Gained Access to My Crypto Wallet and Sensitive Data through a Keylogger sent to my device through a phishing email.
I’ll advise others to be wary of the kind of emails they open, as this happened a few weeks ago when a phishing email was sent to my email unknowingly to me that it was a keylogger with the intent of stealing my private information and if not for the intervention of Morphohack Cyber Services, I would have been cleaned out completely. I contacted Morphohack Cyber Services a week after that incident and they detected the keylogger in my computer which has been there for months stealing my private information. If my crypto wallet was not drained, I would not have been aware of the keylogger in my device. Morphohack was able to secure my devices and retrieve my crypto wallet including the crypto assets. Their sophisticated security features and malware can beat any hacking tools available and they are very professional and ethical. Morphohack is a lifesaver and I hugely recommend their services. Their E-mail. Morphohack@Cyberservices. com & WhatsApp. +1 - 213 - 672 - 40921 -
Building Fortresses, not Firewalls: Ethical Hacking Meets Software Development
In the digital age, security is no longer an afterthought; it's the bedrock upon which our online world rests. Yet, traditional security measures often resemble fortresses – imposing, but vulnerable to unseen cracks and tunnels. To truly safeguard our systems, we need to think like the enemy, like the nimble figures scaling those walls: ethical hackers.
Enter the exciting realm of DevSecOps, where ethical hacking practices are woven into the very fabric of the software development lifecycle (SDLC). This proactive approach is akin to building castles with security in mind, each brick meticulously laid to withstand even the most cunning siege.
Why Ethical Hacking in SDLC?
Imagine developing a critical piece of software, only to discover a gaping security hole after launch. The damage could be catastrophic, exposing sensitive data and eroding trust. Ethical hacking flips this script. By integrating penetration testing, vulnerability assessments, and threat modeling throughout the SDLC, we proactively hunt for weaknesses before they can be exploited.
Think of it as a friendly sparring match, where the ethical hacker throws their best punches to expose vulnerabilities, allowing the development team to fortify the software's defenses. This constant testing and refining leads to robust, secure systems that can withstand real-world attacks.
Benefits of DevSecOps:
1. Reduced Costs and Risks: Early detection and patching of vulnerabilities are far cheaper than dealing with a full-blown data breach.
2. Improved Software Quality: Security becomes an inherent part of the development process, leading to more reliable and trustworthy software.
3. Enhanced Brand Reputation: Demonstrating a proactive approach to security builds trust with customers and stakeholders.
Putting it into Practice:
Integrating ethical hacking into the SDLC requires a cultural shift. Developers, security professionals, and testers need to work together seamlessly, sharing knowledge and fostering a collaborative environment. Here are some key practices:
1. Threat Modeling: Identify potential threats and attack vectors early in the development process.
2. Static and Dynamic Code Analysis: Use automated tools to detect vulnerabilities in code.
3. Penetration Testing: Simulate real-world attacks to uncover hidden weaknesses.
4. Security Awareness Training: Educate developers and other stakeholders about security best practices.
Tools of the Trade:
A plethora of tools empowers ethical hackers and security professionals in their quest for a more secure digital world. Some popular options include:
1. Kali Linux: A distribution packed with security tools for penetration testing.
2. Burp Suite: A web application security testing platform.
3. Metasploit: A framework for developing and executing exploit code.
4. Wireshark: A network traffic analyzer for identifying suspicious activity.
The Future of Security:
As technology evolves, so too must our security practices. DevSecOps, with its embrace of ethical hacking, is at the forefront of this evolution. By building security into the very fabric of software development, we can create a safer, more resilient digital world for everyone.
Remember, in the ongoing battle against cyber threats, ethical hackers are not the enemy; they are our allies, the architects of digital fortresses that stand strong against the shadows. So, let's embrace DevSecOps, sharpen our ethical hacking skills, and build a future where security is not just an afterthought, but a fundamental principle.
I encourage you to explore the world of DevSecOps and ethical hacking. Whether you're a seasoned developer or just starting your journey, there's always more to learn and contribute. Together, we can build a more secure digital future, one line of code and one vulnerability patch at a time.
Do you have any questions about DevSecOps or ethical hacking? Share your thoughts and experiences in the comments below! -
HIRE TECHNOCRATE RECOVERY PROFESSIONAL CYBER HACKERS
I’ve always been cautious with online security, especially in the crypto world. I changed my Bitcoin wallet password monthly, thinking it was the best way to stay safe. However, I went a bit overboard one time, creating a password so complex I couldn’t remember it. When I locked myself out, panic set in. After countless failed recovery attempts, I reached out to TECHNOCRATE RECOVERY, a trusted name in the crypto community. They worked quickly and professionally, recovering my funds in days and giving me peace of mind. They also helped me set up a more practical, secure password strategy. Lesson learned: Security is important, but simplicity matters too. Thanks to TECHNOCRATE RECOVERY, I’m now more secure and sleep easy knowing my assets are safe.
Contact below details for urgent help
Phone Contact: +1573 3563 708
Send a Message: technocratrecovery@contractor.n et1 -
Soft wear tech is a platform designed to help you recover lost coins, wallets, and cryptocurrencies.
When thieves stole a staggering $900,000 worth of Bitcoin from my digital wallet, I was devastated. As an experienced cryptocurrency investor, I had always taken pride in my security measures, believing my assets were safe. Nonetheless, these skilled hackers breached my defenses and made off with my hard-earned digital coins, leaving me not only with a significant financial loss but also with a feeling of violated trust and security.
Refusing to let the criminals get away with their actions, I took immediate steps to address the situation. I reported the theft to the authorities, fully aware that tracing cryptocurrency transactions is notoriously difficult. However, I was determined to pursue every avenue available. That’s when I discovered the innovative services offered by SOFT WEAR TECH, a company specializing in tracking and recovering stolen digital assets.
The dedicated team at SOFT WEAR TECH quickly sprang into action, meticulously analyzing the blockchain transaction data to follow the money trail. Thanks to their exceptional investigative skills and cutting-edge tools, they were able to pinpoint the location of my stolen Bitcoin and initiate the recovery process. It was a long and arduous battle, with the thieves attempting to cover their tracks and move the funds. Yet, the SOFT WEAR TECH team remained resolute, outsmarting the criminals at every turn.
After weeks of relentless effort, they successfully reclaimed my $900,000 in Bitcoin and returned it to me. I was overjoyed—not only was my investment restored, but I also felt a sense of triumph over those who thought they could escape unscathed. This experience has heightened my vigilance and commitment to security in cryptocurrency investing, and I am deeply grateful to have had the SOFT WEAR TECH team fighting to protect what belongs to me.
For inquiries, feel free to reach out via
Email: softweartech5@gmail.
Email: softewar.tech@yandex
Phone : +1 9594003352 -
Lost Bitcoin Recovery Experience After Laptop Theft and No Wallet Backup
I never thought a spilt second would change my entire life, I was sitting in a cafe working on a project the next thing in a blink of an eye I lost my laptop, that had my entire financial investment of $730,000 worth of Bitcoin, I went from being calm to erratic going up and down looking if I could locate it, finally accepted that I had lost it. Everything was gone my important work tool, and the worst part was I hadn’t backed up my wallet, I desperately began searching for solutions so I went on research mode, but I wasn’t sure if there was anyone out here who could recovery stolen cryptocurrency, I held on to the little hope that I had and continued with my search when I came across several testimonials about LEE ULTIMATE HACKER a hacker that was able to track and recover stolen Bitcoin, I contacted LEEULTIMATEHACKER @ AOL . COM
telegram: LEEULTIMATE
wh@tsapp +1 (715) 314 - 9248 and after consultation, they took me through steps on how they’ll recover my lost funds, they asked me critical questions and I explained it to them that I didn’t have a back up and needed help, they reassured me that they will be able to help me recovery my lost funds, LEE ULTIMATE HACKERS team worked with me with such professionalism until the last step, using advanced blockchain tracking and forensic tools to trace my stolen assets, after only a week of work I finally got a call from LEE ULTIMATE HACKER customer service that they had fully recovered my money, on top of it they helped me improve my security through their app providing real time security alerts ,encrypted backups and anti- theft that was new to me, I learnt a lot about digital security i also experienced hopeless situation that could be turned around for the best all thanks to LEE ULTIMATE HACKER reach out to them for all your complex recovery problem.2 -
HOW MY CARBON NEUTRAL BITCOIN WAS HELD HOSTAGE AND RESCUED BY ASSET RESCUE SPECIALIST
I believed in a cleaner tomorrow, one where blockchain and renewable energy were not enemies. My wind farm was proof. Excess energy powered my Bitcoin mining machines, a closed loop. It was the future. Until the ransomware attack.
My turbines hummed one morning as they always did, but my mining operation? Gone. My wallet? Locked. One message replaced my screen:
"Create a payment of 5 BTC to free your information. You have 72 hours."
The irony? My carbon-neutral Bitcoin had been taken hostage.
I panicked. I had crafted my system for survival, yet here I was, stuck. Perplexed, I went to industry colleagues. That's when one panelist from a Clean Energy Summit contacted me:
"Consider ASSET RESCUE SPECIALIST. They provide blockchain forensics, and they're carbon neutral!"
I was desperate but skeptical. During my first call, their personnel were talking my language, both security and sustainability. They did not just care about Bitcoin; they cared about why I was mining it.
Their approach? Genius. Instead of negotiating with the hackers, they reverse-engineered the ransomware. My infrastructure had been attacked through a zero-day vulnerability in the grid software, not my specific setup.
This wasn't a solo problem. This was an energy security emergency for the entire region.
Over 12 frenetic days, ASSET RESCUE SPECIALIST, worked with good-faith hackers and clean-energy engineers. They did not simply recover my Bitcoin without giving a ransom to attackers, they also fixed the flaw that had jeopardized our grid in the first place.
When I was finally able to log back in to my wallet, I felt like I'd regained not only my Bitcoin, but command over my vision.
My wind farm is now more secure than ever. ASSET RESCUE SPECIALIST, even helped us implement decentralized security protocols to prevent future hacks. And the icing on the cake? Their carbon offsets make their entire operation all about aligning with my emphasis on sustainability.
I once believed that Bitcoin and green energy were the perfect pair, but now I understand security is the third leg.
If you work in cleantech and disaster strikes? ASSET RESCUE SPECIALIST, is not a rescue team, they are a renewable power. 1
1 -
HACKER TO ASSIST ME RECOVER MY LOST CRYPTO HIRE SLAYER COIN RECOVERY
Life’s unpredictability struck me hard on a sweltering afternoon, as I juggled the relentless demands of taxi driving with dreams of a secure future for my family. Every fare I accepted, every mile I logged, was a step toward stability until a single lapse in judgment threatened to erase it all. Exhausted after a long shift, I stopped at a dimly lit café to check my Bitcoin wallet, clinging to the hope that my investments might one day lift us out of financial uncertainty. The public Wi-Fi was convenient, but in my haste, I didn’t consider the risks. Minutes later, hackers had stripped away $34,000, a sum representing years of sacrifice, sleepless nights, and promises to my children.The “access denied” message felt like a physical blow. My hands trembled as I reloaded the app, praying it was a glitch. But reality sank in: my family’s safety net was gone. Guilt consumed me. How could I explain this to my wife and children? I pictured my daughter’s college fund vanishing, my wife’s trusting smile crumbling under the weight of my mistake. Desperation drove me to scour the internet, where countless recovery scams preyed on vulnerability. Then, I stumbled upon SLAYER COIN RECOVERY, a lifeline in a sea of doubt.Their team responded instantly, blending expertise with empathy. “We’ll do everything possible,” their agent assured me, voice steady yet kind. They decoded the breach: the public network had been a trap, my login credentials intercepted. Over days that felt like eternities, they navigated blockchain complexities and cyber trails, updating me with unwavering transparency. When they finally restored access, tears blurred my screen $34,000 shone in my wallet, intact.This ordeal taught me invaluable lessons about vigilance and the importance of safeguarding my digital assets, revealing humanity’s remarkable capacity for good. SLAYER COIN RECOVERY didn’t just retrieve my lost funds; they salvaged my faith in second chances and the kindness of strangers. Their dedication transformed a moment of despair into a story of resilience and hope.Now, I take proactive measures to secure my investments, using military grade encryption and practicing safe online habits. I’ve become an advocate for digital security, sharing my experience with fellow taxi drivers and anyone willing to listen. I emphasize the importance of using secure networks and being cautious with personal information in a world rife with cyber threats.Moreover, the kindness I received from the SLAYER COIN RECOVERY team inspired me to pay it forward. I volunteer my time to help others navigate their financial challenges, offering guidance and sharing resources to empower those in vulnerable situations.My family’s future is no longer a gamble but a testament to resilience and the power of human connection. I’ve learned that even in the darkest moments, hope can be reclaimed through the support of others. It’s not just about the money; it’s about the lessons learned and the relationships forged in adversity. I carry the spirit of those who helped me as I navigate life’s complexities, determined to build a brighter future for my family and inspire others to do the same.If you ever find yourself in a similar situation, I wholeheartedly
+1(672)768-8701
recommend SLAYER COIN RECOVERY2
