Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "pentesting"
-
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
So I've been looking for a Linux sysadmin job for a while now. I get a lot of rejections daily and I don't mind that because they can give me feedback as for what I am doing wrong. But do you know what really FUCKING grinds my FUCKING gears?
BEING REJECTED BASED ON LEVEL OF EDUCATION/NOT HAVING CERTIFICATIONS FOR CERTAIN STUFF. Yes, I get that you can't blindly hire anyone and that you have to filter people out but at least LOOK AT THEIR FUCKING SKILLSET.
I did MBO level (the highest sub level though) as study which is considered to be the lowest education level in my country. lowest education level meaning that it's mostly focused on learning through doing things rather than just learning theory.
Why the actual FUCK is that, for some fucking reason, supposed to be a 'lower level' than HBO or Uni? (low to high in my country: MBO, HBO, Uni). Just because I learn better by doing shit instead of solely focusing on the theory and not doing much else does NOT FUCKING MEAN THAT I AM DUMBER OR LESS EDUCATED ON A SUBJECT.
So in the last couple of months, I've literally had rejections with reasons like
- 'Sorry but we require HBO level as people with this level can analyze stuff better in general which is required for this job.'. - Well then go fuck yourself. Just because I have a lower level of education doesn't FUCKING mean that I can't analyze shit at a 'lower level' than people who've done HBO.
- 'You don't seem to have a certificate for linux server management so it's a no go, sorry!' - Kindly go FUCK yourself. Give me a couple of barebones Debian servers and let me install a whole setup including load balancers, proxies if fucking neccesary, firewalls, web servers, FUCKING Samba servers, YOU FUCKING NAME IT. YES, I CAN DO THAT BUT SOLELY BECAUSE I DON'T HAVE THAT FUCKING CERTIFICATE APPEARANTLY MEANS THAT I AM TOO INCOMPETENT TO DO THAT?! Yes. I get that you have to filter shit but GUESS WHAT. IT'S RIGHT THERE IN MY FUCKING RESUME.
- 'Sorry but due to this role being related to cyber security, we can't hire anyone lower than HBO.' - OH SO YOUR LEVEL OF EDUCATION DEFINES HOW GOOD YOU ARE/CAN BE AT CYBER SECURITY RELATED STUFF? ARE YOU MOTHERFUCKING RETARDED? I HAVE BEEN DOING SHIT RELATED TO CYBER SECURITY SINCE I WAS 14-15 FUCKiNG YEARS OLD. I AM FAMILIAR WITH LOADS OF TOOLS/HACKING TECHNIQUES/PENTESTING/DEFENSIVE/OFFENSIVE SECURITY AND SO ON AND YOU ARE TELLING ME THAT I NEED A HIGHER LEVEL OF FUCKING EDUCATION?!?!? GO FUCKING FUCK YOURSELF.
And I can go on like this for a while. I wish some companies I come across would actually look at skills instead of (only) study levels and certifications. Those other companies can go FUCK THEMSELVES.39 -
I really have this fucking love/hate relationship with application security.
For a lot of stuff that I write, user input has to be validated, authentication is required and so on and I do love looking into that, pentesting my own applications to death and thinking about the security architecture of the application itself.
But, sometimes, I just want to focus on the fucking features and then it annoys the living hell out of me that securing an application can take so much time and brain power.
Yay and grrrr, I guess.8 -
Paranoid Developers - It's a long one
Backstory: I was a freelance web developer when I managed to land a place on a cyber security program with who I consider to be the world leaders in the field (details deliberately withheld; who's paranoid now?). Other than the basic security practices of web dev, my experience with Cyber was limited to the OU introduction course, so I was wholly unprepared for the level of, occasionally hysterical, paranoia that my fellow cohort seemed to perpetually live in. The following is a collection of stories from several of these people, because if I only wrote about one they would accuse me of providing too much data allowing an attacker to aggregate and steal their identity. They do use devrant so if you're reading this, know that I love you and that something is wrong with you.
That time when...
He wrote a social media network with end-to-end encryption before it was cool.
He wrote custom 64kb encryption for his academic HDD.
He removed the 3 HDD from his desktop and stored them in a safe, whenever he left the house.
He set up a pfsense virtualbox with a firewall policy to block the port the student monitoring software used (effectively rendering it useless and definitely in breach of the IT policy).
He used only hashes of passwords as passwords (which isn't actually good).
He kept a drill on the desk ready to destroy his HDD at a moments notice.
He started developing a device to drill through his HDD when he pushed a button. May or may not have finished it.
He set up a new email account for each individual online service.
He hosted a website from his own home server so he didn't have to host the files elsewhere (which is just awful for home network security).
He unplugged the home router and began scanning his devices and manually searching through the process list when his music stopped playing on the laptop several times (turns out he had a wobbly spacebar and the shaking washing machine provided enough jittering for a button press).
He brought his own privacy screen to work (remember, this is a security place, with like background checks and all sorts).
He gave his C programming coursework (a simple messaging program) 2048 bit encryption, which was not required.
He wrote a custom encryption for his other C programming coursework as well as writing out the enigma encryption because there was no library, again not required.
He bought a burner phone to visit the capital city.
He bought a burner phone whenever he left his hometown come to think of it.
He bought a smartphone online, wiped it and installed new firmware (it was Chinese; I'm not saying anything about the Chinese, you're the one thinking it).
He bought a smartphone and installed Kali Linux NetHunter so he could test WiFi networks he connected to before using them on his personal device.
(You might be noticing it's all he's. Maybe it is, maybe it isn't).
He ate a sim card.
He brought a balaclava to pentesting training (it was pretty meme).
He printed out his source code as a manual read-only method.
He made a rule on his academic email to block incoming mail from the academic body (to be fair this is a good spam policy).
He withdraws money from a different cashpoint everytime to avoid patterns in his behaviour (the irony).
He reported someone for hacking the centre's network when they built their own website for practice using XAMMP.
I'm going to stop there. I could tell you so many more stories about these guys, some about them being paranoid and some about the stupid antics Cyber Security and Information Assurance students get up to. Well done for making it this far. Hope you enjoyed it. 26
26 -
Anyone here who also got super bored while on a porn site and ended up pentesting that porn site..?14
-
I have a Kali Linux VM running on my Windows machine. I decide to try and exploit the Windows machine (THAT THE VM WAS RUNNING ON) because of a vulnerability with smb that requires NO user interaction. I decided to make my computer shoot its own legs and I thought "Hey, this is gonna be fine."
Aaaaand the whole system crashed on me.3 -
Just switched from Kali to Parrot OS. A very nice pentesting OS. Neat UI. ✌️
Great performance on a basic laptop.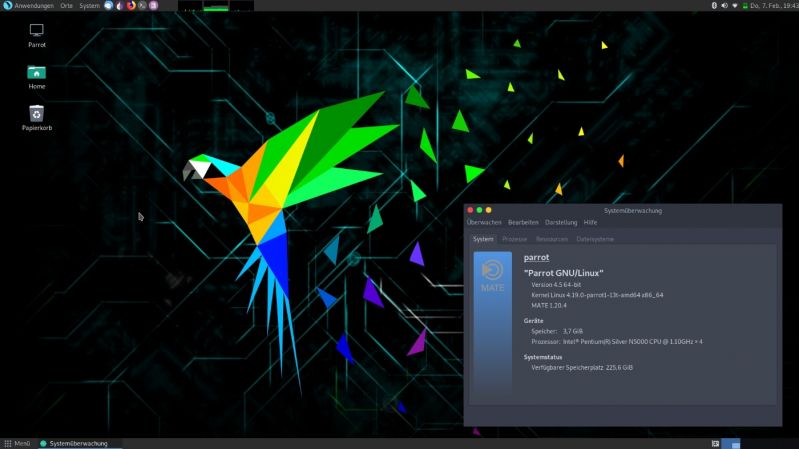 7
7 -
When the university finds out you're a pentester:
Usual underclassmen: Can you hack my bf/gf? I think they're cheating on me.
Delusional underclassmen who think they know everything: I can hack too! Who's your master? I learned how from master jimmy *runs a batch script that has "tree" on loop. See? What batch script do YOU have?"
The IT teachers: can you show us how a payload works?4 -
At a point in your life, you'll settle down abit, and you start to think about what you've done in the past (idk) years of your life.
Then you think about your career, how everything is ever since you discovered you were good at a certain thing since highschool.
be it programing, writing random codes, pentesting (or if you had that "hacker" phase in your life) or fixing laptops and etc.
"Good"
You think about the word, and you had a thought: You only know how to do it, how it works, how its done, and how to do it.
You only "Know", it takes practice, patience, dedication and years (or months depends on you) of experience before you can really say for sure you're "Good" at it.
Me? Im no where near good. but that doesn't stop me from going there.
And i hope the same goes for you. You can do it,
Have a great day.3 -
Hey hackers! It's me again 😀
If I wanna be an awesome pentester / bug hunter , what should be my main focus?
Network?
Data sciense?
Algorythm?
Low level programming?
I've already passed network + and basics of ccna and I already know pentesting using kali and I know c and python as well.
Just not sure where to go next and keep using kali packages makes me feel like a script kiddie (which is aweful 😬)
Dreaming to be able to write my own exploits and have my own 0day bugs👑
Thanks for any recommandation you would39 -
Managed to get a fucking meterpreter shell without human help for the first time today!
It was a VulnHub challenge, for the record, but damn that felt good!
For those who don't know; this is a remote command execution thing ran on compromised systems by (malicious) attackers using the Metasploit framework.
I have done tons of pentesting but not on system level so this is quite an accomplishment for me 😊4 -
Well, I was Always into Computers and Games and stuff and at some point, I started wondering: "why does Computer Go brrr when I Hit this Button?".
It was WinAPI C++ and I was amazed by the tons of work the programmers must have put into all this.
13 year old me was Like: "I can make a Game, cant be too hard."
It was hard.
Turns out I grabbed a Unity Version and tried Things, followed a tutorial and Made a funny jet Fighter Game (which I sadly lost).
Then an article got me into checking out Linux based systems and pentesting.
*Promptly Burns persistent Kali Live to USB Stick"
"Wow zhis koohl".
Had Lots of fun with Metasploit.
Years pass and I wrap my head around Javascript, Node, HTML and CSS, I tried making a Website, worked Out to some extent.
More years pass, we annoy our teacher so long until he opens up an arduino course at school.
He does.
We built weather stations with an ESP32 and C++ via Arduino Software, literally build 3 quadrocopter drones with remote Control and RGB lighting.
Then, Cherry on the top of everything, we win the drone flying Contest everyone gets some nice stuff.
A couple weeks later my class teacher requests me and two of my friends to come along on one of their annual teacher meetings where there are a bunch of teachers from other schools and where they discuss new technology and stuff.
We are allowed to present 3D printing, some of our past programming and some of the tech we've built.
Teachers were amazed, I had huge amounts of fun answering their questions and explaining stuff to them.
Finally done with Realschulabschluss (Middle-grade-graduation) and High school Starts.
It's great, we finally have actual CS lessons, we lesen Java now.
It's fuckton of fun and I ace all of it.
Probably the best grades I ever had in any class.
Then, in my free time, I started writing some simple programs, firstvI extended our crappy Greenfoot Marsrover Project and gave it procedural Landscape Generation (sort of), added a Power system, reactors, Iron and uranium or, refineries, all kinds of cool stuff.
After teaching myself more Java, I start making some actual projects such as "Ranchu's bag of useful and not so useful stuff", namely my OnyxLib library on my GitHub.
More time passes, more Projects are finished, I get addicted to coding, literally.
My days were literally Eat, Code, sleep, repeat.
After breaking that unhealthy cycle I fixed it with Long Breaks and Others activities in between.
In conclusion I Always wanted to know what goes on beneath the beautiful front end of the computer, found out, and it was the most amazing thing ever.
I always had constant fun while coding (except for when you don't have fun) and really enjoyed it at most times.
I Just really love it.
About a year back now I noticed that I was really quite good at what I was doing and I wanted to continue learning and using my programming.
That's when I knew that shit was made for me.
...fuck that's a long read.5 -
I am really getting sick of recruiters contacting me with "great opportunities" then when I ask questions about the post they just give me the answers they think I want to hear. I know when you're lying because if you knew the answer you would have led with that. At least say you'll find out more and then give me a follow up response.
Recruiter: Would it be possible for you to deliver hacking training?
Me: You mean pentesting?
R: Yes, that.
Me: Well, what will it be used for? Breaking into peoples networks and spying on them?
R: Yes, they'll want it to be able to spy on people.
Me: Well, that's unethical, I'm only interested in defensive security practices.
R: Yes, they'll only want it for ethical reasons like defence and against bad guys.
Me: *dirtiest look I could muster*
I mean there's gullible and then there's what ever it is you think I am.2 -
I have a really huge admiration for people who works for the free software, those who made very good tools for almost everything. The Debian community, the FSF.
I'm also admirative in front of those who used computering as a science and made big discoveries in AI, compressing methods, pentesting...
I'm wondering how it is to work in these two worlds?2 -
>pentester
Raised an issue with a web application for out client that was weak TLS protocols/cipher suites in use on the sever hosting their application.
Then I was asked to confirm that reissuing the certificate was the correct remidial action for fixing this...
Man, it's scary to think non-technical project managers are in charge of fixing this stuff...4 -
So someone posted their btc wallet details (system automated message through a custom tool) to a paste in alternative.
Was the login for an ssh. Wont confirm or deny ssh-ing into it, but another guy who saw the same thing messaged me, sent a screenshot. Account had 127k usd worth of btc in it.
Called the radio station it belonged to and gave them a heads up. Probably should reported it as well but people already seen it so it'll get taken down soon enough.
Here I am broke, busting my ass and reality throws this in my lap. But I ain't never been no god damn thief. Hope the radio station it belongs to doesnt get robbed by someone less honest though.
Honesty is probably half the reason I've spent half my life broke trying to find or make opportunities.
And frankly I've heard real horror stories of good faith reports (whitehat style pentesting, etc) and the people that report it get fucked hard by authorities. What can you do though.
Enough navel gazing though.
What the fuck is wrong with the people who build these sort of account reset tools anyway?12 -
Some kid keeps asking me how to session hijack. I keep telling him there's no point if:
A. You're not on the same network as him / her (I'm sure there are exceptions to this but normally you'd have to be on the same network)
B. The connection is encrypted
He doesn't understand either of those things. Not to mention it's illegal unless you're given consent.7 -
And then the PEN-Tester said... "MySQL configured to allow connections from 127.0.0.1. Recommend configuration change to not allow remote connections." hahahaha!
-
!rant but seeking für help
Hi!
So my boss came to me yesterday and asked me if I could do some penetration / security testing for a web application our company made.
Interested in learning it and being familiar with HTML, PHP, JavaScript and MySQL I said yes.
Though I have some really basic knock edge of the subject (E.g SQLInjection) I was wondering if you know any good website / udemy course or whatever that can get me started.
I don't mind if there will be a certificate at the end but it is not necessary.
Thank!8 -
I'm currently pentesting a web app on a Mac Mini with 8 Gigs of RAM and a i5-4620 using OWASP ZAP. Third time the fuzzer got stuck, the RAM's full an the CPU's permanently at 100 %.
Before starting this job, I always said that pentesting on this POS is like bringing a knife to a gunfight.
When I kicked off two fuzzers at once, I started feeling like bringing a cocktail sword to a thermonuclear war.
It's not even 10 here and I already wish for some booze. Damn, I gotta start making moonshine or something.5 -
As much as I love developing I have been also enjoying pentesting a lot lately.
So if you have any resources for a beginner to share please link them in the comments :)3 -
So, this incident happened with me around 2 years ago. I was pentesting one of my client's web application. They were new into the Financial Tech Industry, and wanted me to pentest their website as per couple of standards mentioned by them.
One of the most hilarious bug that I found was at the login page, when a user tries logging into an account and forgets the password, a Captcha image is shown where the user needs to prove that he is indeed a human and not a robot, which was fair enough to be implemented at the login screen.
But, here's the catch. When I checked the "view source" option of the web page, I saw that the alt attribute of the Captcha image file had the contents of the Captcha. Making it easy for an attacker to easily bruteforce the shit outta the login page.
You don't need hackers to hack you when your internal dev team itself is self destructive.2 -
Was in the mood for distro hopping and installed Parrot (home edition, don't really care about pentesting but privacy features were a plus). Lovely distro. Already feel at home.1
-
Hi everyone! (Specially pentesting masters!)
I got a question:
We all know the Nmap's abillity for detecting os using 1 open and 1 closed port,
Is there any way or method to detect os without any closed port ?(open ports exist)
Thanks alot 😃4 -
@linuxFanboys
I'm getting a Chromebook, and, obviously, I'd rather wget all my webpages before I use chrome as my main os. so any recommendations for distros? I want a good, smooth ui, kinda like what windows was aiming for but so terribly messed up. I want apt package manager, and I wouldn't mind pentesting tools, and it has to be light enough to use on a computer with 4gb ram and 16gb ssd. I assume it's implied with linux, but I want one that's generally consider to be secure. I plan to run android studio (I expect it to be slower than a commodore 64 running windows 10), eclipse, gcc, if that helps. any suggestions? thanks!16 -
Working for blockchain companies is kind of funny. They get endless money from investors, while shoveling manure.
Like developing random useless prototype applications. Registering patents left and right. Spending money on pentesting demo apps. Organising random obligatory company wide lectures, for multiple days.2 -
How did you learn cyber security, especially pentesting ?
I know that making VM lab and/or doing CTFs and reading writeups can help a lot, but is there any more "formal" way to get into things like pentesting etc. ?
(Without having to pay for OSCP, Sans and all this)5 -
Pentesting for undisclosed company. Let's call them X as to not get us into trouble.
We are students and are doing our first pentest at an actual company instead of assignments at school. So we're very anxious. But today was a good day.
We found some servers with open ports so we checked a few of them out. I had a set of them with a bunch of open ports like ftp and... 8080. Time to check this out.
"please install flash player"... Security risk 1 found!
System seemed to be some monitoring system. Trying to log in using admin admin... Fucking works. Group loses it cause the company was being all high and mighty about being secure af. Other shit is pretty tight though.
Able to see logs, change password, add new superuser, do some searches for USERS_LOGGEDIN_TODAY! I shit you not, the system even had SUGGESTIONS for usernames to search for. One of which had something to do with sftp and auth keys. Unfortunatly every search gave a SQL syntax error. Used sniffing tools to maybe intercept message so we could do some queries of our own but nothing. Query is probably not issued from the local machine.
Tried to decompile the flash file but no luck. Only for some weird lines and a few function names I presume. But decompressing it and opening it in a text editor allowed me to see and search text. No GET or POST found. No SQL queries or name checks or anything we could think of.
That's all I could do for today. So we'll have to think of stuff for next week. We've already planned xss so maybe we can do that on this server as well.
We also found some older network printers with open telnet. Servers with a specific SQL variant with a potential exploit to execute terminal commands and some ftp and smb servers we need to check out next week.
Hella excited about this!
If you guys have any suggestions let us know. We are utter noobs when it comes to this.6 -
[UPDATE]
As some 6 of you might know from my previous post I was gonna start with my OSCP course. Well, I didn't.
I thought maybe I needed some more practice before I do, and I joined this wonderful platform called HackTheBox (hackthebox.eu)
It's a really amazing place to test a lot of your skills in pentesting. You practice on various machines, each having it's own challenge different from another, it really helps in thinking differently and learning while you move forward.
I'd really like to recommend it to anyone who is interested in it! :)4 -
AI hacking attempts being spotted in the wild because they're too polite
https://someone.elses.computer/@mik...
there's actually a similar vetting process in the crypto industry where you have to swear or you won't get hired. forget why now
this seems optimistic to me because companies generally don't do security. a hacker desperate for money has less money to blow on AI hacking than someone invested in protecting their company would on AI pentesting. poor low level pentesters I guess though -
> 2018 starts just like another day
> Drops a tip for the pentesters
> As a pentester if you aren't good as a Chineese APT actor pack up and go home1 -
I'd love to get into a career within the cyber security industry.
Anyone got advice?
I've played around with Kali/Parrot and setup a proxmox box to perform pen testing and have a fair number of PDF ebooks and audio books on networks, security and pen testing12 -
How many people on devRant are skilled with pentesting / Offensive Security? How long did it take you to understand it? How do you keep yourself from crossing over white hat territory into grey hat territory?3
-
How am I supposed to start learning pentesting / hacking when kali linux is shot down by the devRant community?
Yes, I would rather start with some source that would get me writing code to do it, I just don't know which is it. Maybe sourceforge?5 -
Hi!
I want to know if there is possibility to find a vulnerability on a .jar file.
I tried to install Kali on VM (for now) and tried to use metasploit but I found that it attacks the inter system on a indicated ip address.
There are many application or video (and so on) for my problem?
This .jar file is an application and I want to do pentesting...
Sorry for my poor english but it isn't my native language.
I'm new in pentesting wolrd 🤣7 -
I am burntout because my last job (which i quit, you can read the drama at my profile)
So, now that I am unemployed and in lock-down I want to learn new things, but idk where to start.
I want to try python (I am mostly did backend stuff, with java and node). And I want to see if i can do backends with it. Idk where to start, there are certificates on it?
I always wanted to learn about security/ pentesting (more for curiosity than anything), again, idk where to start or where to get a course/certificate).
Where to start with devops? I have no clue about front-end either...
So, any advice? Right now I am a bit lost about... well, everithing and need to do things to keep me bussy.
Thanks and sorry if my english is not perfect, It is not my native language.4 -
Hey there, I've never really done anything like this but I'm in the second year of college.
I really want to go into the security area, not completely sure but pretty inclined to pentesting.
The question is, what, in your opinion, do you think is a good starting point so I'm pretty much ready to start working when I finish my 5 year course? My college doesn't have any or many security classes, so I'll have to do it all by myself.
Right now I know java, C and html, css and Javascript, which I'm learning by myself.5 -
So... there is a bank. And the website for example is using "https". Alright. But the Login consists your login ID (in the most cases your account number) and a Pin number ( only 5 chars) If i remember pentesting, crunch etc a pin or password with 5 chars (included special characters) is fast hackable or not? Or is it super secure cuz of the "https"?4
-
It is sometimes shocking to see 10+ developers working on a fairly big project (online quiz). Missing data binding operations here and there, as a result, bunch of sql injections, which successfully led to the entire db full of questions and answers sitting on my desktop.
Vulnerabilities have been reported, took them 2 weeks to understand what happened and fix them.
Pretty sad :/1 -
Get to know the new company better (Changed job shortly before Christmas).
Learn some DPs, DDD, k8s, finish introduction to hacking course, start doing htb and thm machines, finish and defend my thesis, finish books clean code, thinking in java (reading it to fill in gaps on knowledge), a few books about pentesting.
Among non tech goals: pass drivers license exam for cars, another one for motorcycles, go back to learning russian. -
Going to do our first social engineering pen test. We're setting up a general plan and we'll call for a meeting with a company next week. Any tips?5
-
1. When we struggled for month with using OpenSSL, fixing our server, then bit of Sqlite3 fuck ups. Was it even right to use those libs, not write shit ourselves, if it is such a hassle to use them, or is it only us being too stupid to read the docs? Project seemed 'finished' for over a year. Really wore us out to get it out there.
2 Our board constantly announcing the success and striving of our pentester department. Makes me feel I am at the wrong place. No dynamics, growth, just too much stupid work to plow through.
3 Starting a bit with CTF's. Realizing I am hardly at the entrance of the rabbit hole. (And also is it even the right thing going down there? My Luddite tendencies also shining through...) Not mastering all this tools. -
In Website Penetration Testing , It's actually a war between Who knows best about the services and practices the other person has implemented.
-
Reverse engineering with IDA, be like:
Ow that makes sense, lets jmp there, nope thats not... aaah this must be the subroutine I was lookig for, nope thats not it, repeat. -
Anyone knows if u can make good money by reverse Engineering apks and looking for security holes? Anyone experienced in doing that and how much could u charge1





