Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "adress"
-
OneDrive:
Login -> Password/Account is wrong
Forgot Password -> Account does not exist
Registration -> There is already an account with this email adress
Well, Fuck you11 -
I just installed Arch on my laptop. Therefore as of the rules, i need to adress this fact to you.18
-
Man, we have a snake in our company.
This snake is responsible for terrible code. They oversee a offshore team, but hold them to no coding practices. They don't do code reviews or checks. They let them be lazy and get away with sloppy work every time.
And if you critize their team - they will defend them and get angry at you. You can't adress the problem because said snake is always around. He's in a senior position for giving our company cheap workers, doing years of damage to our product while the non-code savvy managers remain blissfully unaware of their product being ruined in the background.
This snake is the senior product office. He has a share in the company now. He is from the overshore team's country. That team now has their claws so dug into our companies roots and are just pumping lsd's into it constantly. Feels good untill you die from an overdose.
Here I am, the new junior software developer, trying to tear out the claws that have sunk into these roots. Im up against the snake. The snake hates me. I hate the snake. I am trying to open the eyes of the managers. They hate that. They want to silence me so I don't expose the awful, unprofessional level of work they do.
Well, that's too bad. I won't back down from this, snake.14 -
Having an english conversation with a russian client.
"What do you want the info to be?"
"I want the name, adress and etc."
"Etc?"
"Yes! I attached you a picture with everything...as you can see..."
<the picture is a huge table in russian>
"But the table is in russian"
"Yes"3 -
Way to fucking go, Austria wants to push a law that forces online platforms (if possible around the globe) with more than 100k users to provide an accurate way to identify them.
"Name, surname and adress"
I just listened to an interview with a guy who is for that proposal. He said the platforms can just take the data directly from mobile providers, using the phone number. Also, even buying a prepaid sim-cards will require you to provide an identity card.
Way to fucking go! They say it's rather unlikely that this proposal will get approved by the EU, but given the shit they just pulled on us, I wouldn't be surprised in the slightest id these fuckers just go with it.
Where is our precious privacy going? Some old pedophiles are taking it away from us, into their sex dungeons I suppose...
Unfortunatelly this is a rather new proposal, so I can't find an english article covering this story attack
https://br.de/nachrichten/netzwelt/... 13
13 -
Being a developer has it's advantages: I wanted to apply for a internet subscription for my home but my home adress wasn't recognized by the provider. So i wanted to send a complain form but this was only possible by providing it with a client number, which I obviously didn't have.
So this was my solution 🎉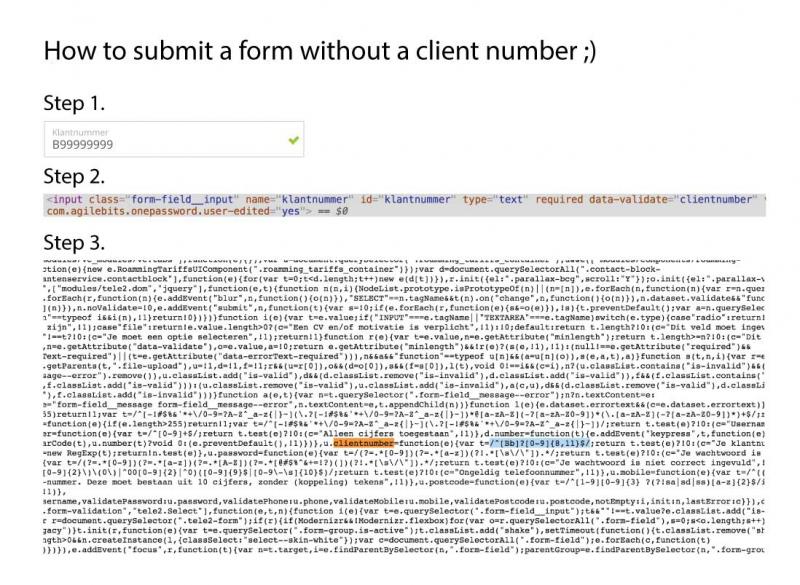 9
9 -
Did anybody of you automate job hunting?
Like Webscraping online job offers, extract adress, keywords and put it into a cv template, set up personalised html-email and website.
Extra perk, a neural network which composes the cover letter.
that i would need.9 -
Last year in my computer class, i was sitting next to the girl i likED. One day we were doing a classwork and i asked her for the IP adress (everyone in the class was supposed to know what is it and how to check it). Five minutes later she came back telling me the adress (streets, numbers) of the school...
You were perfect until that moment...7 -
Someone in Indonesia is using my email adress to order stuff from a site called Lazada. My email account is not compromised as far as I know. But It's really annoying always getting order confirmation emails in bahasa Indonesia.
I've got "kikis" phone number and adress. Any advice what i've could do to make her stop?18 -
Never write your email adress on a building. And it you do, don't use web.de (basically German and more shitty version of yahoo). Spoted in a fancy business district in central Berlin.
 7
7 -
User where I work is convinced someone hacked her iPhone and is remotely changing settings all the time. And it’s not us (the company), the phone isn’t managed and there are no remote profiles installed.
User: I’m telling you. Things are always changing without me doing it!
Me: Alright. Do you have an exemple?
User: Yes. When I swipe here [control center] and tap the WiFi toggle, it always gets back on by itself later.
Me: Yep. That’s actually a “feature”. You don’t have to worry.
User: Alright then, this morning I couldn’t get Google Maps to work.
Me: Well. Since you turned off your cellular and WiFi, it’s normal you couldn’t look up an adress.
User: okay then what about that Bluetooth icon in the top that always appears? I know that means the hacker is on my phone through Bluetooth. See!?
Me: That’s actually just a status indicator. Don’t worry about it. It’ll always come back there it’s normal. You know, your phone can do a lot of stuff by itself.
User: Yeah right. It does it by itself. I’m not stupid you know!! *storms off*
What the hell?6 -
//little Story of a sys admin
Wondered why a Server on my Linux Root couldn't build a network connection, even when it was running.
Checked iptables and saw, that the port of the Server was redirected to a different port.
I never added that rule to the firewall. Checked and a little script I used from someone else generated traffic for a mobile game.
OK beginn the DDoS Penetration. Over 10 Gbit/s on some small servers.
Checked Facebook and some idiot posted on my site:
Stop you little shithead or I will report you to the police!!!
Checked his profile page and he had a small shitty android game with a botnet.
Choose one:
1. let him be
2. Fuck him up for good
Lets Sudo with 2.
I scaled up my bandwith to 25 Gbit/s and found out that guys phone number.
Slowly started to eat away his bandwith for days. 3 days later his server was unreachable.
Then I masked my VoIP adress and called him:
Me: Hi, you know me?
He: No WTF! Why are you calling me.
Me: I love your're game a lot, I really love it.
He: What's wrong with you? Who are you?
Me: I'm teach
He: teach?
Me: Teach me lesson
He: Are you crazy I'm hanging up!
Me: I really love you're game. I even took away all your bandwith. Now you're servers are blocked, you're game banned on the store.
He: WHAT, WHAT? (hearing typing)
Me: Don't fuck with the wrong guys. I teached you a lesson, call me EL PENETRATO
He: FUCK Fuck Fuck you! Who are you???!!! I'm going to report you!
Me: How?
He: I got you're logs!
Me: Check it at Utrace...
He: Holy shit all around the world
Me: Lemme Smash Bitch
*hung up*4 -
So yesterday terminals for clocking in and clocking out where installed at a customer. In the evening I got a call, telling me, that only one of five terminals works. I tried to figure out the problem and finally the customer asked me, if maybe every terminal would need an individual IP adress.3
-
Network Security at it's best at my school.
So firstly our school has only one wifi AP in the whole building and you can only access Internet from there or their PCs which have just like the AP restricted internet with mc afee Webgateway even though they didn't even restrict shuting down computers remotely with shutdown -i.
The next stupid thing is cmd is disabled but powershell isn't and you can execute cmd commands with batch files.
But back to internet access: the proxy with Mcafee is permanently added in these PCs and you don't havs admin rights to change them.
Although this can be bypassed by basically everone because everyone knows one or two teacher accounts, its still restricted right.
So I thought I could try to get around. My first first few tries failed until I found out that they apparently have a mac adress wthitelist for their lan.
Then I just copied a mac adress of one of their ARM terminals pc and set up a raspberry pi with a mac change at startup.
Finally I got an Ip with normal DHCP and internet but port 80 was blocked in contrast to others like 443. So I set up an tcp openvpn server on port 443 elsewhere on a server to mimic ssl traffic.
Then I set up my raspberry pi to change mac, connect to this vpn at startup and provide a wifi ap with an own ip address range and internet over vpn.
As a little extra feature I also added a script for it to act as Spotify connect speaker.
So basically I now have a raspberry pi which I can plugin into power and Ethernet and an aux cable of the always-on-speakers in every room.
My own portable 10mbit/s unrestricted AP with spotify connect speaker.
Last but not least I learnt very many things about networks, vpns and so on while exploiting my schools security as a 16 year old.8 -
Fuck you Intel.
Fucking admit that you're Hardware has a problem!
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data"
With Meltdown one process can fucking read everything that is in memory. Every password and every other sensible bit. Of course you can't change sensible data directly. You have to use the sensible data you gathered... Big fucking difference you dumb shits.
Meltown occurs because of hardware implemented speculative execution.
The solution is to fucking separate kernel- and user-adress space.
And you're saying that your hardware works how it should.
Shame on you.
I'm not saying that I don't tolerate mistakes like this. Shit happens.
But not having the balls to admit that it is because of the hardware makes me fucking angry.5 -
I'm about to move to a new city and one of the websites I'm using adds its name, url and ©️2018 to anything you copy. It is driving me absolutely insane. Trying to find an adress on google? Well you didn't search for [streetname], you searched for [streetname, website name, url ©️2018]. Thank you for copyrighting that public street you fuck. Trying to e-mail an agent? Sorry I can't send an email to [e-mail adress, website name, url].
Whoever thought of this needs to be taken out back and shot.2 -
Back when I started my career (12 months ago lol), I was in IT support. Having to deal with people who have hard times locating and reading off a sticker, let alone telling me their IP adress, only to realize it's the whole store that's offline, not only their PC (gosh do they ever talk with each other). So I decided to code a small tool that shows your hostname and IP adress, and pings the router, firewall and Google DNS. Aaand just in case the number for the IT hotline. Plan was that we could just tell them to double-click on that one icon on their desktop and read out what it says. We deployed it and I was happily waiting for it's time to shine (still a trainee I was also kinda proud of it), but when the network engineer found out, he wasn't happy about it at all. He was afraid too many people would open that new tool without us telling them to do so and/or forget to close it, producing a number of pings to the router, firewall and google. He went on about Google maybe blocking our IP if we produce too many pings and so on.
In my opinion he was kinda overreacting, but he wasn't that wrong and is a nice guy and responsible for our network, so we recalled the tool and never actually used it.2 -
At the institute I did my PhD everyone had to take some role apart from research to keep the infrastructure running. My part was admin for the Linux workstations and supporting the admin of the calculation cluster we had (about 11 machines with 8 cores each... hot shit at the time).
At some point the university had some euros of budget left that had to be spent so the institute decided to buy a shiny new NAS system for the cluster.
I wasn't really involved with the stuff, I was just the replacement admin so everything was handled by the main admin.
A few months on and the cluster starts behaving ... weird. Huge CPU loads, lots of network traffic. No one really knows what's going on. At some point I discover a process on one of the compute nodes that apparently receives commands from an IRC server in the UK... OK code red, we've been hacked.
First thing we needed to find out was how they had broken in, so we looked at the logs of the compute nodes. There was nothing obvious, but the fact that each compute node had its own public IP address and was reachable from all over the world certainly didn't help.
A few hours of poking around not really knowing what I'm looking for, I resort to a TCPDUMP to find whether there is any actor on the network that I might have overlooked. And indeed I found an IP adress that I couldn't match with any of the machines.
Long story short: It was the new NAS box. Our main admin didn't care about the new box, because it was set up by an external company. The guy from the external company didn't care, because he thought he was working on a compute cluster that is sealed off behind some uber-restrictive firewall.
So our shiny new NAS system, filled to the brink with confidential research data, (and also as it turns out a lot of login credentials) was sitting there with its quaint little default config and a DHCP-assigned public IP adress, waiting for the next best rookie hacker to try U:admin/P:admin to take it over.
Looking back this could have gotten a lot worse and we were extremely lucky that these guys either didn't know what they had there or didn't care. -
Today's GDPR-Bullshittery.
So we are using an open source remote update system for updating our embedded devices.
And today we learned that, that system logs ip-adress'. And low and behold mr.GDPR says that is a no no.
So either we completely drops it, finds a new update system and implements it..
Sift through all the source code of the update system "fix" it and recompile it.
Or we setup a Man in the middle attack on ourselves. To mask the ip-adress'.
GDPR encouraging hacking ourselves I fucking love it!5 -
There is this company that saves your information, before you have even registered.
If you merely fill in a field, they will save it to their database. Not even saving/submitting it, just filling it in.
So when you then visit their store, they already know stuff about you (if you gave enough unique identifiers, like phonenumber or email adress) and recommend stuff based on your browsing of their website5 -
Writing some software for a school while sitting in their support-department.
A teacher comes in and asks if we can find the email adress or facebook of a woman he met on vacation because he wants to send her something.
Someone asks: 'what do you want to send her?'
A two second long silence followed...
Everyone starts laughing.
Teachers... ¯\_(ツ)_/¯1 -
So on top of my Windows update frustrations, I just found out that Microsoft has been scamming me out of money for two years!
I bought an android tablet in 2016 which came with a free 1 year subscription to Office365. They demanded credit card info, so I made sure to pre-cancel it to avoid getting charged when the year was up.
Today I find a line on my bank statement that just says 'MICROSOFT', and I think to myself: 'What the hell is that?!?'
It takes some digging for the email adress I used and trying to navigate various MS sites until I realize that those bastards have auto-renewed the subscription twice now!
I missed it last year, but luckily since I caught the latest one within 30 days I can get a full refund.
Will contact their support tomorrow to get the rest of it back. Too tired right now to deal with their support jungle of circular links and virtual assistants...2 -
I'm a bit late I know (only 10 years or so), but I never use windows explorer and especially not the home directory with its ridiculous location... but why the heck is it not possible to access the home directory from windows explorer? There are bullshit categories like videos and music, but no direct link to the home directory. The small arrow at the "root" of the adress bar seems to be the only way to access users home. WTF?14
-
how to php, an infographic by Bind (that me)
0) assert your goal, in this example let it be sending an email from the server
1) search for implemented methods
2) all you can find is either outdated or not helping at all
3) think of solution in any other language (eg c# or node)
4) implement 3)
5) iterate until you have something that works but you have no idea why
6) after 1 week, realize that there is a built in method, but its called userData_registration_sEnder0(adress, header, egg, pinNumbe_r, message)
7) cry5 -
actually my sis is really disappointed i can't do
* cash system programming
* cnc programming
* light show programming
* get the adress of the guy who wrote her on whatsapp
so she is curious what i am able to do :)3 -
Gotta love the IoT.
They set up a new surveillance camera in the company, that can stream live footage over the network and that little shit picked the IP adress of a coworker one day AFTER being set up.
Hurray for static routing. Hurray to the person who didn't disable DHCP on the router (Should probably configure my PC to use a static IP as well lel)
Anyways, this happened outta nowhere when I, the only guy who knows shit about IT and is usually present at yhe office, wasn't there and could not connect remotely.
The other, remote programmer, who set up the network, could guide the coworker to get a new IP but, he was worried that we got ourselves an intruder.
Since nobody told me yet that we (should) have static routing, I thought there was a mastermind at work who could get into a network without a wifi-access point and spoof the coworker in order to access the some documents.
The adrenaline rush was real 😨
Scanning the network with nmap solved the mystery rather quickly but thought me that I need to set up a secure way to get remote access on the network.
I would appreciate some input on the set up I thought of:
A raspberry Pi connected to a vpn that runs ssh with pw auth disabled and the ssh port moved.
Would set up the vpn in a similar fashion. -
Have defective supermicro server, but the ipmi is working and could tell me what's going on.
Only problem is, I don't have access to it since the last owner didn't provide it to me.
So I thought let's try metasploit.
Setup local network with a second server, connect to local* address.
"Welcome to intel integrated BMC web console"
What? Its a Supermicro, did the owner reflash the ipmi? What the heck.
Msf: scan adress ....
ipmi found bla bla bla.
Msf: zero cipher scan.
... Voulnerable to zero cipher.
Was pretty happy but the doubt kept creeping in.
On my WS that isn't connected to the ipmi of my server, I go to that ip address.
Bam
"Welcome to intel BMC ......"
MOTHERFUCKER.
What are the odds that some fucker has his ipmi open to the public on that exact same address that my board was configured to.
Well, actually pretty high I guess.
Fuck. Shit.
That didn't go as planned. -
Fucking remote db doesn't want to work with me and workbench. DB is on an empty test server, no firewall issues on the network, powershell on my pc says ping ok, tcp failing though, server firewall not running, server up and running.
Tried to modify network access on db configs like bind-adress, set my db user "host" value to wildcard. Now I can log in on workbench with my user, yet root somehow fails, wtf?
And of course once the connection is live, no db us visible, accessible, nothing works. I'm so frustrated. About to nuke it and restart ... again!13 -
So our project decided to create a newsletter. For some reason, I was tasked with writing it, includig layout, recepient database etc.
It is the first newsletter, it is urgent and it is supposed to be send to all the people who so far participated. Means: there was never a "sign up here for a newsletter" thingy on the website. Hence, there is also no "unsubscribe" button.
One could kind of "hotfix" this by making a field, like "enter your email adress here to unsubscribe" and then I get a notification and remove the people from the list. Fine by me. Not so many ppl atm so we got time to set it up properly then.
My boss decides it is my job now to implement the stupid unsubscribe button... I am not the website admin. I have nothing to do with the goddamn website. We have ppl in another city, being paid to manage the goddamn website and it would take them just a few minutes to set the stupid button up, since they know what they are doing and I am not.
I told them from the start: I don't do websites. I have nothing to do with them, I don't want to have anything to do with them. We have people for this.
Why the F is it my job now to implement that stupid button?!
And even when I tried to look into how the other formulas which do similar things are set up: oh you don't have permissions to access that. Lovely!
FAK this shiet <.< It is not my fking job.5 -
Seriously getty images, what is wrong with you. Usually it is bad enough that sign in forms say username or email and then only accept one of those two options. Getty images only allows for the username, so i enter that. Doesn't work. I use the forgot password function, have to enter username and email, doesn't work. Turns out the username is the email adress and what I entered was only the display name. Seriously, how stupid is that? What is the point of a username when you have a separate display name and just set it to the account email adress?
-
1337 haxxor here! jk, but its fun to analyze the sourcecode of a streaming site to find the video source giving a 403 error on direct download unless i force the beforeload-adress as a referrer. quite the feeling like my first ftp-download album back in the days.
i know i am childish.1 -
So I downloaded this game (to be fair, it is a preview version for a kickstarter project) and I had to crate an account with my mail address in order to sign in. Fair enough, I fill in this form and it says "invalid mail adress". It came to my attention that the form automatically put a space behind the mail adress so I had removed it. After I put back the space everything worked, but now I can't sign in because I didn't get the confirmation email (I assume because they sent it to [my email]+[space] instead of just my email). Currently chatting with the support guy, seems like a nice guy and I can't blame them because my mistakes are often even dumber, but before you post a preview version of your product online as a first impression, check if it even works. Please. Especially if the reason for posting it online is asking people for money.
-
FUCKING WHY ME!
Lost my dedicated internet access due to a SHITSTAIN of an ISP TELIA decided to introduce itself to my connection A SECOND FUCKING TIME in the past YEAR.
Suddenly lost internet and my firewall couldn't figure out that it was supposed to lose all its fucking connections and renew it's IP adress.
Now im connected to this fucking hipe of shit that is the biggest giver of their customers information to anyone who asks, "Hey man, whats the dude who has this IP?, - sure fam, here you go"
Now i probably have some poor motherfuckers name attached to my current IP.
But could you say that i am now untraceable?4 -
How can a software developer be too incompetent to send a mail to the correct adresse.
My boss sent one to my private adress, instead of my work adress. I mean I know, autofill, but still second time this happened in one week..6 -
All results for GDPR on my "spam mail adress" (NO results for DSGVO!) ... seems like GDPR doesnt apply for spam :D but this email is also registered to sooo many services and websites... i think the search is broken :|
 5
5 -
I have a huge axe to grind about companies sending me emails I have not consented to. Sometimes they have a checkbox for it, which I always, ALWAYS make sure I do not check. Sometimes they just add you automatically as soon as you enter your email adress.
Sometimes the 'Unsubscribe' link leads to a dead page, or just doesn't work.
And sometimes... They send you a bunch of emails to let you know they will absolutely stop sending you emails 😑
Why. Why? WHY? WHYYYYY?!?!?
Why are so many, even otherwise respected and very customer satisfaction minded companies so disgustingly cavalier or downright dirty about emails?
Even after this whole GDPR thing! -
Today i chartered new realms for me.
I created a new hyper-v vm on the company windows servers and added a 5th instance to it, but instead of running another windows server i installed an ubuntu 18.04 (cause i am a bit familiar with debian from my raspberry pi)
we have two servers, one which runs the 4 vms and a replica. I first had the new vm on the main server but it occured me to move it instead to the unusued replica machine. That kinda worked..i did a planned failover but the main server isnt configured to be the replica..and even when activating that it didnt work. This is weird.
For the moment i ignored that and proceeded to install nginx, mariadb and php 7.2..basically the lemp stack. I managed to setup nginx and a static ip adress for the machine (which was different from how i remembered it to do (in 18.04 its not done with the network conf but a yaml file).
in the end i added two different virtual servers, one for actual use and one for dev stuff (with phpmyadmin running for instance), listening on port 80 and some random other port.
as a test i brought a mediawiki onto the Port 80 server and it worked.
on monday i have to figure out how to implement the wildcard certificate i have for our company domain (internal dns simply routes intranet.company.com to the local server vm)
i am mighty proud cause all my experience with linux was with a raspberry pi so far and i am fairly certain i did it right and without shortcuts this time. (unlike my raspberry experience)
just wanted to share
(i also sweated a lot of blood when editing the hyper v settings as i did not set up the server in the first place)
((i also installed xrdp and a mate desktop, but i am less proud of that, but sometimes seeing folders graphically helps me)) -
content creators these days really know how to get their audience to piss off.
was reading a certain comic artist and on e v e r y page (a page is like 5 strips) sometime midscroll the infamous email subscription dialog appeared and covered half the screen. ofc with a sliding effect so you can't even close it immediatly.
Tried entering a BS adress - still appeared again
why can't more comic sites be like xkcd's or swordscomic?1 -
not really that hacky but it was something back then
when I was still learning front end development. I enabled live server on my vs code, connected to a network went to a different PC and connected to same network, went to browser on second PC, entered the other PCs IP adress and added the port number provided by vs code, I was able to access the website I was working on so as I worked and saved the site automatically refreshes on the other computer and i saw the results immediately
this was because I had an 11 inch screen PC. a hp mini. was practically impossible to work with that so whenever my roommates PC was free I'd do that without having to code directly on his PC
later on I enabled auto save on vs code and it seemed I was on a roll. lol -
i would like to address a serious problem in our everyday society. why is there no mouse flavored cat food? it is outrageous. i have written to all cat food companies i know about this issue, but the best response i have gotten is an automated one saying ' your request has been noted'. i have threatened to take them to court. this is something we need to adress9
-
!rant
Someone posted a link to a 30-day-security-challenge here on devRant some time ago and I just thought well, why not try to migrate away from the big companies - I've been using OneDrive as my only cloudstorage since the time when it was called SkyDrive and I've been hosting my Emails at outlook (via Live Custom Domains, a service that does not even exist anymore) for about 8 years now. Since I've always been lazy and since exchange activesync is a great feature if you have multiple calendars and want to sync them and your contacts to several devices I never tried to switch but now I am half done with migrating my data to my own nextcloud installation and my emails to my own mail server - since I don't want to loose the exchange functionality I am also setting up Z-Push and oh boy, this thing is bitching around but my webmail is already nicely integrated into nextcloud, IMAP / SMTP is up, configured and secured (still have to mess around with spamassassin as this email adress is floating around the web for about 10 years now). The only things to do is to get Z-Push work with STARTTLS and the card/caldav backend running and then the basic setup should be done.
I am just wondering if someone could hand me over a guide on how to sign / encrypt emails (GPG?) -
Hussain Al Nowais
Adress: P.O Box: 54457 Abu Dhabi, UAE
Phone: +971 2 6918000
Hussain Al Nowais is a global industrialist and business strategist with over 25 years’ experience in business management, banking, project finance, investment, industrial and real estate sectors. Mr. Al Nowais has a proven track-record in the development of industrial, infrastructure, and energy projects; and in the development and acquisition of businesses in the MENA region. Hussain Al Nowais is the founding member and Chairman of Al Nowais Investments. Currently, Mr. Al Nowais is spearheading the firm’s strategy of global expansion and strategic project development in energy, industry, infrastructure, oil & gas, healthcare, information technology, hospitality and real-estate.
#International Business, Hussain al Nowais #Hussain al Nowais
-
Sweagro: Din Digitala Jordbruksbutik för Lantbruksmaskiner och Reservdelar
På Sweagro förstår vi att lantbrukare behöver pålitliga maskiner och reservdelar för att driva sina verksamheter effektivt. Med vår digitala jordbruksbutik erbjuder vi ett brett utbud av lantbruksmaskiner online som gör det enklare än någonsin att hitta den utrustning du behöver. Vi säljer lantbruksmaskiner direkt från tillverkare, vilket innebär att du får hög kvalitet till konkurrenskraftiga priser. Dessutom erbjuder vi ett omfattande sortiment av Sweagro reservdelar och Sweagro slitdelar för att hålla dina maskiner i toppskick och säkerställa lång livslängd.
Lantbruksmaskiner Online – Enkel Beställning och Snabb Leverans
Att köpa lantbruksmaskiner online har blivit alltmer populärt, och vi på Sweagro gör det enkelt för dig att handla från vår digitala jordbruksbutik. Vi erbjuder ett användarvänligt och snabbt sätt att hitta och beställa maskiner för jordbearbetning, sådd, och andra lantbruksbehov – direkt från din dator eller mobil. Genom vår webbshop kan du söka efter specifika maskiner, läsa detaljerad information och få hjälp att välja rätt utrustning för just dina behov.
Vi har ett brett sortiment av lantbruksmaskiner som är byggda för att hålla och ge hög prestanda, oavsett om du har en liten gård eller ett stort lantbruk.
Direkt från Tillverkare – Hög Kvalitet till Konkurrenskraftiga Priser
På Sweagro säljer vi lantbruksmaskiner direkt från tillverkare, vilket gör att vi kan erbjuda hög kvalitet till ett bättre pris. Genom att eliminera mellanhänder får vi möjlighet att hålla priserna konkurrenskraftiga och ge våra kunder bästa möjliga värde för pengarna. Våra maskiner är tillverkade med modern teknologi och design för att möta lantbrukets höga krav på hållbarhet och effektivitet.
Genom att köpa lantbruksmaskiner direkt från tillverkare kan du vara säker på att du får maskiner som är utvecklade med de senaste innovationerna och byggda för att tåla det hårda arbetet på fältet.
Sweagro Reservdelar – Förläng Livslängden på Dina Maskiner
För att säkerställa att dina maskiner alltid fungerar optimalt erbjuder vi ett brett sortiment av Sweagro reservdelar. Oavsett om du behöver byta ut en sliten del eller reparera en maskin som har börjat fungera mindre effektivt, så har vi de reservdelar du behöver. Våra Sweagro reservdelar är noggrant utvalda för att passa våra maskiner och ge långvarig prestanda.
Att använda rätt reservdelar är avgörande för att hålla utrustningen i toppskick och minska risken för driftstopp. Hos oss hittar du Sweagro reservdelar som är både hållbara och prisvärda, vilket gör att du kan spara pengar på underhåll utan att tumma på kvaliteten.
Sweagro Slitdelar – För Hög Prestanda i Fältet
Alla lantbruksmaskiner slits över tid, och för att hålla din utrustning i bästa skick är det viktigt att byta ut slitna delar i tid. På Sweagro erbjuder vi ett omfattande utbud av Sweagro slitdelar för alla typer av lantbruksmaskiner. Våra slitdelar är designade för att ge maximal hållbarhet och prestanda, vilket gör att du kan fortsätta arbeta effektivt utan att oroa dig för maskinfel eller förlorad produktivitet.
Vi har slitdelar för kultivatorer, harvar, såmaskiner och många fler maskiner, så du kan vara säker på att vi har det du behöver för att hålla din utrustning i toppform.
Varför Välja Sweagro?
Digital Jordbruksbutik: Handla lantbruksmaskiner online på ett snabbt och enkelt sätt via vår digitala jordbruksbutik.
Konkurrenskraftiga Priser: Vi erbjuder lantbruksmaskiner direkt från tillverkare, vilket gör att du får hög kvalitet till lägre priser.
Hållbara Reservdelar och Slitdelar: Vårt sortiment av Sweagro reservdelar och Sweagro slitdelar är noggrant utvalt för att ge långvarig prestanda och förhindra driftstopp.
Snabb Leverans: Vi säkerställer att dina beställningar levereras snabbt och effektivt, så att du kan fortsätta ditt arbete utan avbrott.
Kontakta Oss
Har du frågor eller vill ha hjälp med att välja rätt lantbruksmaskin eller reservdelar? Tveka inte att kontakta oss på Sweagro för rådgivning och beställning.
Telefon: +46703100538
Adress: Formfabriken 1, 585 75 Ljungsbro, Sverige 1
1

