Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "brute force"
-
Manager asked for access to server with admin rights for a third party contractor and I questioned him... His answer?
- Your are gonna give access to anyone that needs access.
I gave. Went for a 15 days vacation.
Our server got blocked by our cloud provider because of ssh brute force attempt coming from it and the company website went offline during a big ass meeting because of that.
Made me giggle :)8 -
So I got the job. Here's a story, never let anyone stop you from accomplishing your dreams!
It all started in 2010. Windows just crashed unrecoverably for the 3rd time in two years. Back then I wasn't good with computers yet so we got our tech guy to look at it and he said: "either pay for a windows license again (we nearly spend 1K on licenses already) or try another operating system which is free: Ubuntu. If you don't like it anyways, we can always switch back to Windows!"
Oh well, fair enough, not much to lose, right! So we went with Ubuntu. Within about 2 hours I could find everything. From the software installer to OpenOffice, browsers, email things and so on. Also I already got the basics of the Linux terminal (bash in this case) like ls, cd, mkdir and a few more.
My parents found it very easy to work with as well so we decided to stick with it.
I already started to experiment with some html/css code because the thought of being able to write my own websites was awesome! Within about a week or so I figured out a simple html site.
Then I started to experiment more and more.
After about a year of trial and error (repeat about 1000+ times) I finally got my first Apache server setup on a VirtualBox running Ubuntu server. Damn, it felt awesome to see my own shit working!
From that moment on I continued to try everything I could with Linux because I found the principle that I basically could do everything I wanted (possible with software solutions) without any limitations (like with Windows/Mac) very fucking awesome. I owned the fucking system.
Then, after some years, I got my first shared hosting plan! It was awesome to see my own (with subdomain) website online, functioning very well!
I started to learn stuff like FTP, SSH and so on.
Went on with trial and error for a while and then the thought occured to me: what if I'd have a little server ONLINE which I could use myself to experiment around?
First rented VPS was there! Couldn't get enough of it and kept experimenting with server thingies, linux in general aaand so on.
Started learning about rsa key based login, firewalls (iptables), brute force prevention (fail2ban), vhosts (apache2 still), SSL (damn this was an interesting one, how the fuck do you do this yourself?!), PHP and many other things.
Then, after a while, the thought came to mind: what if I'd have a dedicated server!?!?!?!
I ordered my first fucking dedicated server. Damn, this was awesome! Already knew some stuff about defending myself from brute force bots and so on so it went pretty well.
Finally made the jump to NginX and CentOS!
Made multiple VPS's for shitloads of purposes and just to learn. Started working with reverse proxies (nginx), proxy servers, SSL for everything (because fuck basic http WITHOUT SSL), vhosts and so on.
Started with simple, one screen linux setup with ubuntu 10.04.
Running a five monitor setup now with many distro's, running about 20 servers with proxies/nginx/apache2/multiple db engines, as much security as I can integrate and this fucking passion just got me my first Linux job!
It's not just an operating system for me, it's a way of life. And with that I don't just mean the operating system, but also the idea behind it :).20 -
Imagine what a coder Gordon Ramsay might be like:
Your alghoritm is so FUCKING slow, I'd rather to try to brute force a 20 characters long alphanumeric password!
This app is more insecure than an average teenager!
If your code was a spaghetti it would be a fucking health hazard!14 -
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
Funny story about the first time two of my servers got hacked. The fun part is how I noticed it.
So I purchased two new vps's for proxy server goals and thought like 'I can setup fail2ban tomorrow, I'll be fine.'
Next day I wanted to install NginX so I ran the command and it said that port 80 was already in use!
I was sitting there like no that's not possible I didn't install any server software yet. So I thought 'this can't be possible' but I ran 'pidof apache2' just to confirm. It actually returned a PID! It was a barebones Debian install so I was sure it was not installed yet by ME. Checked the auth logs and noticed that an IP address had done a huge brute force attack and managed to gain root access. Simply reinstalled debian and I put fail2ban on it RIGHT AWAY.
Checked about two seconds later if anyone tried to login again (iptables -L and keep in mind that fail2ban's default config needs six failed attempts within I think five minutes to ban an ip) and I already saw that around 8-10 addresses were banned.
Was pretty shaken up but damn I learned my lesson!8 -
Da Fuck!?!
Yesterday I found some abnormal activity on my server, someone was trying to brute force my ssh as root since two days! Started raging and installed fail2ban (which automatically bans an IP if it fails to log X times and eventually sends me an email). Woke up this morning to find that a fucking Chinese guy/malware spent the whole night trying to brute Force me!
Fucking cunt! Don't you have any better to do!!
My key is a 32 characters long encrypted key, with the ban he can try 3 passwords /2 hours, good luck brute forcing it you bitch! 35
35 -
"Most software today is very much like an Egyptian pyramid with millions of bricks piled on top of each other, with no structural integrity, but just done by brute force and thousands of slaves." - Alan Kay4
-
Even though I'm a web developer I work in a very small IT department, which includes just me and my colleague.
Yesterday we got a pretty usual request. Someone forgot the password to an excel file. We already started a brute force attack, but we had some fun going through the worst passwords we ever stubbled over in our carrier.
He was like:"Maybe it's just his name?"
Me: "Oooh or maybe it's just the brand and 123?"
We laughed a lot. Not really considering we could crack this "important" file.
But it really worked out. The password was the brand of the business unit and "2017".
I've sent everthing back to the user, telling him exactly how we cracked it... His answer was:"Oh yeah! I knew it was something easy, so me and x could remember it easily!"
...
Why do you forgive easy passwords anyway? If I can crack it within 5 minutes... Everyone can! ...
And if you do it to "remember it easily"? Why the fuck don't you remember it?4 -
Client comes to me after a year to publish an update to his app.
I accept, start looking for my release key.... Found it.
Fuuuuuuucccck what's the password? I can't remember
Googled what to do if forgot password of keystore: Nope can't do shit other than brute Force. You've to forget your app and publish as a new app. Nice.
I must have written it somewhere... I'm sure. Check my password manager: Nope.
Start brute forcing:
Default pass: android. Nope
Name of app? Nope
After 10 mins of brute forcing:
Why would I not store the password in my password manager? The only reason I can think is the password is too stupid to be stored.
Try "password". App signed successfully.
I'm ashamed of 1 year older me xD6 -
Site (I didn't build) got hacked, lots of data deleted, trying to find out what happened before we restore backup.
Check admin access, lots of blank login submissions from a few similar IPs. Looks like they didn't brute force it.
Check request logs, tons of requests at different admin pages. Still doesn't look like they were targeting the login page.
We're looking around asking ourselves "how did they get in?"
I notice the page with the delete commands has an include file called "adminCheck".
Inside, I find code that basically says "if you're not an admin, now you are!" Full access to everything.
I wonder if the attack was even malicious.3 -
Im trying to brute force a rar i made Long ago, sadly i have forgotten the Passwort.
This is how it looks, when you to run it on the length 8-16 at the Same time(all posibilitys).
lets see how Long it will take.
I say 7 Days at 100% cpu usage😂😂 8
8 -
I just discovered my server being brute forced over SSH by over 25 different IPs per minute. WHAT THE FUCK?! It's not even a public website... Now I installed fail2ban.35
-
Idea: Emoji passwords
Bdixbsufhdbe HEAR ME OUT
I know, I know, emojis belong with teenage girls on Snapchat but there are some theoretical benefits to emoji passwords.
Brute Force attacks are useless! With such a wide range of characters and so many different combinations, they just wouldn't be viable.
Dictionary attacks are less useful! Because those require...words.
They can be easier to remember. Tell a story with your emojis. Images are easier to commit to memory than combinations of letters and numbers.
Users would adopt the feature! For whatever reason, the general population fucking loves these things. So emoji passwords probably won't take very long to see use.
I don't know much about this last one, so I saved it for last, but I would imagine that decryption would be more difficult if the available values is quite vast. I dunno how rainbow tables and hash defucking works so I'll just put this here as a "maybe"
😀33 -
Just wrote a brute-force attack simulation in c. Going to run it on actual hardware, with an 8-character limit, including alphabet (Upper and lower case), 0-9 and a few special characters and see if it gets done tonight ;)
I'll see you all in about 360 trillion operations.11 -
Yes I believe you’re Google and I will click that link.
I don’t care that IP from that you sent it to me is from some company in India.
Probably Google outsourced it’s email service there.
But wait why is this link pointing to Chinese website?
Ouch you provided some ip under A dns record so let me nmap it...
So there’s bunch of services you have there.
ftp, ssh, msrpc, netbios-ssn, snpp, microsoft-ds, sun-answerbook ...wait what ?
Let me curl that 8888 port.
Oh you have login / password form and it’s pagoda linux panel.
Wait a second I will read about it maybe some default login / password will work...
Ok so maybe I just make a script to brute force it as you wanted to brute force my computer motherfucker. 2
2 -
*Sigh
Every single one of us here loathe this question "Hey can you hack a Facebook account for me?"
Even worse when the one asking is your mom.
😶😶😶
(Backstory, she and her friend runs a store. Shit happened between them. The friend is the one who setup the store's Facebook page. Now posting shit on that page. She's not tech savvy. I can probably brute force her password. No 2FA)
Dilemma. Dilemma.8 -
I have a junior who really drives me up a wall. He's been a junior for a couple of years now (since he started as an intern here).
He always looks for the quickest, cheapest, easiest solution he can possibly think of to all his tickets. Most of it pretty much just involves copy/pasting code that has similar functionality from elsewhere in the application, tweaking some variable names and calling it a day. And I mean, I'm not knocking copy/paste solutions at all, because that's a perfectly valid way of learning certain things, provided that one actually analyzes the code they are cloning, and actually modifies it in a way that solves the problem, and can potentially extend the ability to reuse the original code. This is rarely the case with this guy.
I've tried to gently encourage this person to take their time with things, and really put some thought into design with his solutions instead of rushing to finish; because ultimately all the time he spends on reworks could have been spent on doing it right the first time. Problem is, this guy is very stubborn, and gets very defensive when any sort of insinuation is made that he needs to improve on something. My advice to actually spend time analyzing how an interface was used, or how an extension method can be further extended before trying to brute-force your way through the problem seems to fall on deaf ears.
I always like to include my juniors on my pull requests; even though I pretty much have all final say in what gets merged, I like to encourage not only all devs be given thoughtful, constructive criticism, regardless of "rank" but also give them the opportunity to see how others write code and learn by asking questions, and analyzing why I approached the problem the way I did. It seems like this dev consistently uses this opportunity to get in as many public digs as he can on my work by going for the low-hanging fruit: "whitespace", "add comments, this code isn't self-documenting", and "an if/else here is more readable and consistent with this file than a ternary statement". Like dude, c'mon. Can you at least analyze the logic and see if it's sound? or perhaps offer a better way of doing something, or ask if the way I did something really makes sense?
Mid-Year reviews are due this week; I'm really struggling to find any way to document any sort of progress he's made. Once in a great while, he does surprise me and prove that he's capable of figuring out how something works and manage to use the mechanisms properly to solve a problem. At the very least he's productive (in terms of always working on assigned work). And because of this, he's likely safe from losing his job because the company considers him cheap labor. He is very underpaid, but also very under-qualified.
He's my most problematic junior; worst part is, he only has a job because of me: I wanted to give the benefit of the doubt when my boss asked me if we should extend an offer, as I thought it was only fair to give the opportunity to grow and prove himself like I was given. But I'm also starting to toe the line of being a good mentor by giving opportunities to learn, and falling behind on work because I could have just done it myself in a fraction of the time.
I hate managing people. I miss the days of code + spotify for 10 hours a day then going home.10 -
Sad story:
User : Hey , this interface seems quite nice
Me : Yeah, well I’m still working on it ; I still haven’t managed to workaround the data limit of the views so for the time limit I’ve set it to a couple of days
Few moments later
User : Why does it give me that it can’t connect to the data?
Me : what did you do ?
User : I tried viewing the last year of entries and compare it with this one
Few comas later
100476 errors generated
False cert authorization
Port closed
Server down
DDOS on its way1 -
Walk into mall, bring my child to kids zone. They have free wifi 🤤
Accessing -> Scanning -> Got Ya! -> Brute Force -> Cracked!
There you're.
Now I can monitoring my kid while reading rant!
Just normal day in my life 6
6 -
Some years ago our company site was hosted by a prick who knew nothing and started to pretend the server got a virus or whatever.
I tested their server and figured out they did not have any firewall policies going on like mitigation of ssh brute force.
It was at this time I learned about SYN flood, and boy I flooded that port 80 of them.
The company site went down for as long as I wanted.
It was great because now we manage it in house and never had a problem anymore. -
After watching Mr Robot, I installed Kali and learnt to hack WiFi passwords via brute force. Was utterly disappointed that, most crackers just use prebuilt tools instead of developing their own algorithms and programs.14
-
Microsoft seriously hates security, first they do enforce an numer, upper and lowercase combined with a special character.
But then they allow no passwords longer than 16 characters....
After that they complain that "FuckMicrosoft!1" is a password they've seen to often, gee thanks for the brute force tips.
To add insult to injury the first displayed "tip" take a look at the attached image. rant password security security 101 security fail annoyance passwords passwords stupid practices microsoft13
rant password security security 101 security fail annoyance passwords passwords stupid practices microsoft13 -
So... did I mention I sometimes hate banks?
But I'll start at the beginning.
In the beginning, the big bang created the universe and evolution created humans, penguins, polar bea... oh well, fuck it, a couple million years fast forward...
Your trusted, local flightless bird walks into a bank to open an account. This, on its own, was a mistake, but opening an online bank account as a minor (which I was before I turned 18, because that was how things worked) was not that easy at the time.
So, yours truly of course signs a contract, binding me to follow the BSI Grundschutz (A basic security standard in Germany, it's not a law, but part of some contracts. It contains basic security advice like "don't run unknown software, install antivirus/firewall, use strong passwords", so it's just a basic prototype for a security policy).
The copy provided with my contract states a minimum password length of 8 (somewhat reasonable if you don't limit yourself to alphanumeric, include the entire UTF 8 standard and so on).
The bank's online banking password length is limited to 5 characters. So... fuck the contract, huh?
Calling support, they claimed that it is a "technical neccessity" (I never state my job when calling a support line. The more skilled people on the other hand notice it sooner or later, the others - why bother telling them) and that it is "stored encrypted". Why they use a nonstandard way of storing and encrypting it and making it that easy to brute-force it... no idea.
However, after three login attempts, the account is blocked, so a brute force attack turns into a DOS attack.
And since the only way to unblock it is to physically appear in a branch, you just would need to hit a couple thousand accounts in a neighbourhood (not a lot if you use bots and know a thing or two about the syntax of IBAN numbers) and fill up all the branches with lots of potential hostages for your planned heist or terrorist attack. Quite useful.
So, after getting nowhere with the support - After suggesting to change my username to something cryptic and insisting that their homegrown, 2FA would prevent attacks. Unless someone would login (which worked without 2FA because the 2FA only is used when moving money), report the card missing, request a new one to a different address and log in with that. Which, you know, is quite likely to happen and be blamed on the customer.
So... I went to cancel my account there - seeing as I could not fulfill my contract as a customer. I've signed to use a minimum password length of 8. I can only use a password length of 5.
Contract void. Sometimes, I love dealing with idiots.
And these people are in charge of billions of money, stock and assets. I think I'll move to... idk, Antarctica?4 -
So I left this company I was working for for about 6 years and then eventually came back earlier this year. It was basically 2 backend devs, 2 frontend, and a designer, with me being one of the frontend devs, and the other operating as the owner/alpha of the group. And our coding styles couldn’t have been more different. I wrote code with purpose that could scale, while he wrote garbage that I affectionally labelled "brute force code"; meaning it eventually got the job done, but was always a complete nightmare to work with. Think the windiest piece of shit you’ve ever seen and then times it by 10. Edit the simplest thing at your peril. And if you think you fixed something, all you’ve ever really done is create another 10 problems. And because the code was such shit, it relied on certain things to be broken in order for other things to work. Anyway, you get the drift.
In the beginning we used jQuery and so we just continued to use it throughout the years. But then when I finally left I realized we were operating in a bit of a bubble, where we didn’t really care much to ever try anything else, and mostly because we were arrogant. But eventually my boss started to notice the trend of moving away from jQuery, so he converted everything to vanilla JavaScript. Thing is, he hadn’t learned ES6 yet or any of the other tools that came along with it. And so it was a mess, and I was quite shocked at how many lengths he’d gone to create the full conversion. Granted, it was faster. But overall, still a nightmare to work with, as the files were still thousands of lines long. And when I dug deeper, I realized that he’d started to pluck things out of the DOM manually on-demand. And so it dawned on me: he’d been looking at sites built with React and other dif-engines, and then instead of just using one, he decided to reinvent the wheel. And the funny thing is, he thought it was just a matter of always replacing the entire HTML for whatever was needed. And so he thought what he was doing was somehow clever. And why not? He’s a badass mathematician who created an empire with jQuery. And so he obviously didn’t need input from anyone, and especially not from the shitty devs over there at Facebook. Anyway, while I was gone I learned quite a bit of React, and so it was just comical to me when I came back and saw this. Because it would have been a million times more efficient had he just used the proper tool. In short, he’d re-written the entire codebase for two full years and then ended up with another round of brute-force garbage.
So that’s my story. The lesson is, when you work for someone who’s a dumbass piece of shit, sometimes he’ll be so stupid the only recourse is uncontrollable laughter. I became a digital nomad somewhere in between and fucked off to Asia where I barely worked for 2 years. And I’d definitely recommend the same for anyone else with an asshole boss where the work is unfulfilling. Because it doesn’t matter what your job is when you’re living like a millionaire in Asia working 15 hours a week.4 -
Someone is trying to launch a brute force attack on one of my servers that I set up for an old project. According to the logs, they've tried Jorgee, they've tried directly accessing the MySQL database (with the laziest passwords), and they're now on day 4 of their brute force attack against my SSH server. I'm fairly certain that they won't be getting in (not that there's anything worth getting in the first place), but what's the standard protocol for this? Do I just wait this out, or is there something I can do to break their bot? I have fail2ban enabled, and it is doing its job, but the attacker is changing their IP address with every attack.10
-
* How I solve a problem*
"Okay, it seems to be interesting, OK think solve it generally"
*Solved the problem manually
"Okay pseudo code is /do this and that/ break it and write Algo.
Seems like it will work,
Making all sense
Okay let's code"
*Wrote in IDE
" Hmm compile and execute"
*Expected output : Hey you!
*Actual output : F you!
Me: What the hell
"Uhh! Just gonna apply brute force"
*Somehow got the actual output = expected output
"I knew, it gonna solve it but how it worked?"
*Thinking
*Thinking....
*Thinking and it's 2 am
"Oh! I'm done, I'm going to sleep"
*4 am, while lucid dreaming
"That's how that thing worked, I got it"
*Relieved
*Next day using the logic dreamt of
*No matter how much surreal it is
*It didn't work
Me : F U!!!
..
..
...
(to be continued)2 -
!rant
Does anyone know what the Boolean Pythagorean Triples problem or the Ramsey Theory? I read about it while reading an article on brute reason, a kind of compliment to brute force...8 -
I setup an email server a couple of months ago.
The amount of port scans and brute force attacks I've received this month alone is awful.
JUST SOD OFF ALREADY, PLEASE.19 -
Acquaintance of mine brags that he made a "Facebook password cracker" that took less than 30 lines of code.
I take a look at it, then I realize it's brute force password cracking.
Oh dear.
Facebook doesn't even let you do that many password attempts, not to mention that brute forcing passwords is going to take more time than the expected lifetime of the sun. (exaggeration? Maybe. But you get my point.)
Why are we still here? Just to suffer?6 -
My non dev friend called me in middle of night for getting shortcut virus removed! I would have blasted 🔫 him but I felt pity on the guy as I know that he is poor with tech stuff
Any he had only windows, so I Google up solution and replied back to him.
He asked where to put it. I told him in cmd. He is like what so I told him to press win+r then in that type d and "black" 🏴 window will appear. Type in that.
guess what he typed exactly as mentioned in the reply and didn't replace the drive name properly .😑
I told him to put proper drive and saw that he missed spaces so l told him that he missed space 😤 and he put only one space and it still had problem so I had to explain it in weirdest was possible( shown in fig 1.1 had been writing report and figure gave yo be mentioned with number 😅)
Finally. It was all done! Well some pf my cs ( !counter strike but computer science friend) are worse then this can't use teminal or even connect to WiFi (wpa-enterprise @ college with mschap v2 and peap auth which is crackable using twin tower and brute force) properly, do I guess it not BA's that this guy cry to get rid of shortcut virus (virus > wifi setup) 😬
Finally I feel relived after ranting 😪 5
5 -
Fucking incompetence
Senior level developer with 15 years of software development experience ...
ends up writing brute force search on a sorted data - when questioned he's like yeah well dataset is not that large so performance degradation will be marginal
He literally evades any particularly toil heavy task like fixing the unit test cases , or managing the builder node versions to latest ( python 2 to 3 ) because it's beneath him and would rather work on something flashy like microservice microfrontend etc. -- which he cannot implement anyway
Or will pick up something very straightforward like adding a if condition to a particular method just to stay relevant
And the management doesn't really care who does what so he ends up getting away with this
The junior guys end up taking up the butt load of crappy tasks which are beneath the senior guy
And sometimes those tasks are not really junioresque - so we end up missing deadlines and getting questioned as to why we are are not able to deliver.
Fuck this shit ... My cortisol shoots up whenever I think of him4 -
Oh boy I got a few. I could tell you stories about very stupid xss vectors like tracking IDs that get properly sanitized when they come through the url but as soon as you go to the next page and the backend returns them they are trusted and put into the Dom unsanitized or an error page for a wrong token / transaction id combo that accidentally set the same auth cookie as the valid combination but I guess the title "dumbest" would go to another one, if only for the management response to it.
Without being to precise let's just say our website contained a service to send a formally correct email or fax to your provider to cancel your mobile contract, nice thing really. You put in all your personal information and then you could hit a button to send your cancelation and get redirected to a page that also allows you to download a pdf with the sent cancelation (including all your personal data). That page was secured by a cancelation id and a (totally save) 16 characters long security token.
Now, a few months ago I tested a small change on the cancelation service and noticed a rather interesting detail : The same email always results in the same (totally save) security token...
So I tried again and sure, the token seemed to be generated from the email, well so much about "totally save". Of course this was a minor problem since our cancelation ids were strong uuids that would be incredibly hard to brute force, right? Well of course they weren't, they counted up. So at that point you could take an email, send a cancelation, get the token and just count down from your id until you hit a 200 and download the pdf with all that juicy user data, nice.
Well, of course now I raised a critical ticket and the issue was fixed as soon as possible, right?
Of course not. Well I raised the ticket, I made it critical and personally went to the ceo to make sure its prioritized. The next day I get an email from jira that the issue now was minor because "its in the code since 2017 and wasn't exploited".
Well, long story short, I argued a lot and in the end it came to the point where I, as QA, wrote a fix to create a proper token because management just "didn't see the need" to secure such a "hard to find problem". Well, before that I sent them a zip file containing 84 pdfs I scrapped in a night and the message that they can be happy I signed an NDA.2 -
Ok. question:
should I learn Java or not?
I come from a C++ background and would (obviously) like to know, wether I need Java in my career. I already have some pretty neet projects like a selfmade "compiler" , Im currently building a chess engine that doesnt brute force.
An alle deutschen:
Kann jemand mir sagen, wie ich als 9. Klässler einen nachmittagsjob (bestenfalls homeworking) bekommen könnte? Es geht mir nicht um das Geld, sondern um die Erfahrung und die sicherheit, schon einmal etwas VOR dem Abi in der Hand zu haben48 -
Over the past 2 months I have interviewed with several companies and 2 of them stood out at rejecting me. Let's call them Company A, and Company B!
> I know right? Developers are bad at naming!
I guess part of it is my fault too! I am old and slow. Doesn't like competitive programming and already forgot most of how to answer algorithm question. I can't even answer some of the algorithm question I've flawlessly answered back when I was fresh out of University.
## Company A
When I got chance to interview at Company A, they require me to answer HackerRank style interview. It's my first time in nearly a decade of working in the industry to feel like I'm in a classroom exam again. I hate it, and I deliberately voiced my distaste to the answers comment:
// Paraphrasing
// I'm sorry, I'm dumb!
// I never faced anything like this in real world work...
// ......
But guess what? My answer still pass the score, have a call with their VP, which proceed to have another call with their Lead Engineer.
Talked about my experience with Event Driven System and CQRS+ES and they decided that I am:
- Arrogant
- Too RND in my tech stack
- And overkill in CQRS+ES
And decided they don't need me.
They hate me for having a headstrong personality which translates as Arrogance to the perceiving end.
## Company B
Another HackerRank style interview. Guess I passed their score this time without me typing some strong comment and proceed to have another test with their Lead Engineer.
This time they want 5 question answered in google docs within 60 minutes.
Two of them stood out to me for being impossible to work on 12 minutes (60 / 5 if you're wondering). Or maybe I'm just old and dumb?!
The others are just questions copied word for word from Geeks For Geeks.
One of the question requires me to write a password brute force attack to an imaginary API.
The other requires me to find a combination of math `+` or `-` operation from `a strings of numbers` that results in `a number`.
My `Arrogance` kicks in and I start typing a comment
// Paraphrasing
// I am sorry but I feel this is impossible for me to think of in 12 minutes
// (60 / 5 if you're wondering)
// But I know you guys got this question from Rosseta Code!
// Here's the link, but I don't know the logic behind it
See? I've worked on this question back when I was still a University student and remember where to look at.
Unsurprisingly, I've heard the feedback that I was rejected although I've answered one of their question `FLAWLESSLY`. I know they are being sarcastic at this point. haha.
---
I was trying to be honest about what I can and can't do in the `N` minutes timeframe and the Industry hates me.
I guess The Industry love people who can grind `GFG` or other algorithm websites, remember the solutions out of their head, and quietly answer their `genuinely original question` without pointing the flaws back at them.9 -
So technical interview today but woke up (6am) and started thinking about it and it led to this rant about algorithms. This is probably going into a Medium post if I ever get around to finishing it but sort of just wanted to share the rant that literally just went off in my mind.
*The problem with Algorithms Technical Interviews Is They don't test Real skills*
Real world problems are complex and often cross domain combining experience in multiple areas. Often the best way is not obvious unless you're a polymath and familiar with different areas, paradigms, designs. And intuitively can understand, reason, and combine them.
I don't think this is something a specific algorithm problem is designed to show. And the problem is the optimal solution to some of these and to algorithm design itself is that unless you train for it or are an algorithm designer (practice and experience), you can only brute force it in the amount of time given.
And quite frankly the algorithms I think we rely on daily weren't thought of in 30 minutes. The designers did this stuff for a living, thought about these problems for days and several iterations… at least. A lot were mathematicians. The matrix algorithm that had a Big O of 7N required a flash of insight that only someone constantly looking and thinking about the equations could see.
TBA
-system design
-clean readable coding practices
...
TLDR: I could probably go on and on about this stuff for hours jumping from item/example/area to the next and back again... But I don't think you can test these (~20) years of experience in a 1 hr technical interview focused on algorithms...8 -
Yes, a plus, i.e. `+`, is a fucking valid char for an email address.
Your online service is shit, you don't know your craft, and you should feel bad about yourself!
But you thought email is fucking simple, google for email validation regex and took copy pasted the first fucking find from some random blog that validates anything but an actual fucking valid email addresses, didn't you!?
(Funfact, the plus sign allow to create email aliases in some free mailer services. GMail for instance. That's why I l like using emails like my.actual.mail+I_KNOW_WHY_YOU_ARE_SENDING_SPAM@gmail.com as my registration email. Also, brute-force that login email.)3 -
Things I’m learning from my accounting job that will help me in my future dev career:
Today I have really, truly understood the need to sometimes just walk away.
I couldn’t figure out how to fix something, I kept fucking up, and at 16:40 I realized I can just stop, do something else that’s easy and doable, and come back to the fucked up mess I made in the morning. We’ll see how it goes, but it’s a lesson I’ve been continuously learning over the last few years, not to stubbornly brute-force my way into doing something when I’m not in the right mindset and able to do it, and instead just calm myself down and come back to it later. -
I was trying to crack my own wifi using airmon-ng but found out applying brute force will take up to 237 years!(11 lower case character password )
Is there any other way to crack my WPA2 (psk) more efficiency?9 -
I set up unRAID on my server this weekend, and only just checked my logs to see if anything weird was happening. Turns out 2 IPs have been trying to brute-force the SSH password all weekend. I quickly installed the DenyHosts plugin and reminded myself to always use a strong password, which luckily I did.
A bit later now, and one of the 2 gave up, the other one keeps trying but of course the connection is refused. Just keep trying buddy :P6 -
Most recently... taking something previous devs had failed at and knocking it out of the park.
Best example was a statistical regression and graphing tool on ASP MVC.
The devs were doing a massive brute force recalculation on the server layer. It would take 24h then fail to save (Entity framework brute force).
We moved it to the database layer and got it down to a passable time.
The same devs were outputting charts to ie 9, chrome, firefox... same deal, half an hour on the initial request (parser churn in the browser)... then failure.
Again got it into a passable time by switching to web sockets and long polling then outputting 1000 or so points at a time to give the browser time to render.
Taking those two cock ups and making them a workable solution was awesome.
Since then, teaching. We have apprentices, newcomers, interns all jumping in and looking to get working. They're all different, what works to teach one person won't the next, each of them so far has caught on to what I was teaching. It's a proud moment to be able to impart knowledge and see someone pick it up, enthusiastically... it's also awesome to see someone excited about what you do. -
ATT: Stinking maggot who's trying to break into my website!
There are no users on my website. Not even an administrator. wp_admin is empty. Best of luck!14 -
I got into programming because I couldn't solve a maths problem I'd been set, so my dad found an emulator for an old language he used to use a bit and managed to brute force it.
From there I went and learnt my first programming language, an unconventional choice of BBC basic 😛 -
Finally moved all the shitty WordPress sites off our production servers. They are GoDaddy's problem now. Brute force away China.
-
Using a brute force dictionary algorithm to retrieve every employees password. Access got blocked for a day because they didn't know what my algorithm did, I deleted the main file moments ago. They only saw the curl scripts.3
-
I wasn't hired to do a dev's job (handled sales) but they asked me to help the non-HQ end with sorting transaction records (a country's worth) for an audit.
Asked HQ if they could send the data they took so I wouldn't need to request the data. We get told sure, you can have it. Waits for a month. Nothing. Apparently, they've forgotten.
Asks for data again. They churn it out in 24 hours. Badly Parsed. Apparently they just put a mask of a UI and stored all fields as one entire string (with no separators). The horror!
Ended up wasting most of a week simply fixing the parsing by brute force since we had no time.
Good news(?): We ended up training the front desk people to ending their fields with semi-colons to force backend into a possibly parsed state. -
Cracked my first weak RSA implementation challenge today. Feels pretty awesome.
Involved primes that were very close, which means you can factorize the modulus quickly to get the private key. Normally, you would never use close primes as prime factorization's difficulty relies a certain amount on some distance between the two values.
The reason you can brute force close primes has to do with them being close in value to the square root of the function, meaning that you can search far quicker than if you were to try every combination of primes.2 -
Fuck I am so screwed... Spent an hour + trying to implement a Trie except I didn't know it was called a Trie... and don't remember how to implement one...
I am so fcked for my technical interview/test i m planning to take this weekend...
It's like I know i've seen this problem before and the brute-force way probably won't work... but after an hour trying to implement the right way... i just go fck it...
and lo and behold... it doesnt work..
Google the solution and the code is like less than 100 lines... and probably took the guy 10 minutes to write...6 -
I remember someday from a few years ago, because i just got off the phone with a customer calling me way too early! (meaning i still was in my pyjamas)
C:"Hey NNP, why si that software not available (He refers to fail2ban on his server)
Me: "It's there" (shows him terminal output)
C: " But i cannot invoke it, there is no fail2ban command! you're lieing"
Me: "well, try that sudoers command i gave you (basically it just tails all the possible log files in /var/log ) , do you see that last part with fail2ban on it?
C: "Yeah, but there is only a file descriptor! nothing is showing! It doesnt do anything.
Me: "That's actually good, it means that fail2ban does not detect any anomalies so it does not need to log it"
C:" How can you be sure!?"
Me: "Shut up and trust me, i am ROOT"
(Fail2ban is a software service that checks log files like your webserver or SSH to detect floods or brute force attempts, you set it up by defining some "jails" that monitor the things you wish to watch out for. A sane SSH jail is to listen to incoming connection attempts and after 5 or 10 attempts you block that user's IP address on firewall level. It uses IPtables. Can be used for several other web services like webservers to detect and act upon flooding attempts. It uses the logfiles of those services to analyze them and to take the appropriate action. One those jails are defined and the service is up, you should see as little log as possible for fail2ban.) 5
5 -
The German Wikipedia article about brute force defines it as "decryption method" 🤔🤔😂
https://de.m.wikipedia.org/wiki/...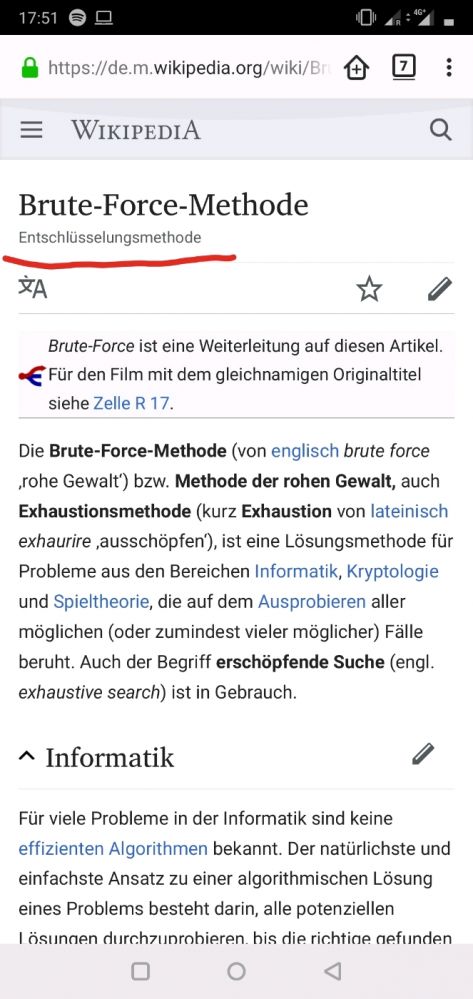 2
2 -
I spend all morning on trying to solve an Algo problem for upcoming interview practice (Euler #3) that comes down to implementing IsPrime.
I remember reading once how Sieve of Eratosthenes
Isa the right way to go do when I first started I wanted to use that.
Then I couldn't think of the right code though so I went with Brute Force (for all numbers upto X see X is divisible by it)
It actually worked but I wanted to just try the "right way".
It's way slower and actually ended up with the wrong answer...
But at this point I don't give a **** anymore.
I guess lesson learned... Use Brute Force first... Then optimise for a problem more elegant solution.10 -
I use Google for anything I don't know ,
Does that mean I'm a bad programmer?
If so , if I memorize everything I googled once , will I be a good programmer ?
How do good programmers find the solution? Do they try everything ? Kinda brute force ?8 -
Your three-second password retry delay is far more likely to annoy users than preventing a brute-force attack.
If you insist on a retry delay, let the user enter a password five times without any delay. This would make no difference in the grand scheme, the trillions of retries needed for a brute-force attack, and guessing a password takes longer than three seconds of thinking anyway.
Another alternative is a tenth of the password retry delay but one added character. One added character slows down a brute-force attack by at least sixty-two (62) times, so one more character but a tenth of the password retry delay would still mean more than six (6) times the protection against brute-forcing.
On Linux, the password retry delay can thankfully be reduced by changing a value inside /etc/pam.d/common-auth or /etc/pam.d/login (out of scope for this post, you can search online for more details).3 -
disclaimer i dont understand css to begin with so you can discard my opinion
You have all these options for width https://developer.mozilla.org/en-US... , but guess what none of them do anything different as you brute force try them all in the chrome debugger. Dunno what cascades except my butthurt
so fuck it ~1000% width works and has an ugly overhang, but fuck front end8 -
What are you guys doing against brute force attacks on your login webpages? I don't want anybody to access my porn ( ͡° ͜ʖ ͡°). But I don't want to block the useraccount because that would be annoying because you could simple lock a user out of his account :/ any suggestions? What are you doing on your sites?11
-
Any better way for breaking telnet ?
(I had no idea who was ever going to connect to this ip using telnet so i had no chance to sniff the password :(
Now it is taking ages to brute force )
//mac is already spoofed ;) 1
1 -
we don't really need data types. By default, everything should be string. When you do addition, when the string has nothing but digits, commas and periods, they should be parsed added as numbers. Else, they should be concatenated. If that string-number formatting doesn't match any conventional formatting of any locale, it's a string. Same number-inferring behavior should be implemented when comparing things. There should be no type casting because there is just one type, so every comparison is type-exact. "true" and "false" are special strings that won't throw an error during comparison. Comparing two strings using less, more, less than or equal and more than or equal always throw an error.
Dates are ISO strings. Every other thing is not a date.
We basically sieve the data starting with the strictest conditions down to more forgiving conditions, then down to no conditions at all where it will be interpreted as just string. ISO date requires a very specific formatting, so we should check that first. Then, let's check for a formatted number. Then, a boolean. If nothing clicked, it's a string.
Oh, and every string is automatically trimmed, so it can't start or end with any kind of space.
No classes, no procedures, no constants, no switch operator. Also, no methods, just a lot of helper functions.
Performance will be lacking compared to languages with static types, but performance is not a priority here — this is the language for code monkeys and their AI counterparts. It should only be used for making trivial client-server prototype apps that could've been replaced by Excel if only people knew how to use it, at passable quality, that work reasonably fast on modern hardware.
Those apps will be deprecated because the company went out of business/because the project was proven to not be financially viable in several months anyway.
UI should be rendered not using a webview, but using a lightweight cross-platform UI engine written in a proper language like C++. There should be no semantic tags — every UI element acts like a div would. Everything is measured in pixels and milliseconds. All colors are #rrggbbaa. All vector graphics are SVG, all raster graphics are AVIF. All sounds are Opus. All videos are AV1. All UIs are reactive, Vue style, e.g. you change a variable and the UI updates itself in the right way every time.
Add some junior devs paired with GPT-4.5 or any super-expensive LLM, sprinkle with some Extreme Go-Horse management style (https://hackernoon.com/you-might-be...), and boom, we recreated Zergs but in the tech space. Let's solve software by brute force.10 -
When an interviewer asks, what are the steps that you take usually when given a task to do something, what do you guys say?
I said, I devote 10-20% of the time to understand the given problem - sit and explore all possible scenarios to handle, then develop a brute Force approach, improve the approach to make it more efficient, see if it handles all edge and corner cases, then write test cases for it.
( I'm thinking, the process doesn't vary a lot for most of the people?, Except in TDD - one'll write the test cases first)
How would you answer this question?
I have this feeling that I messed up something 🤔7 -
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
Talking with my dad about a program he's been working on at his company. He doesn't work on it directly, he works with parts on the side to show to clients. He's basically a sales rep that shows some cool features.
Me: is this that the program where it converts scanned items into readable text?
Him: yes but it does a little bit more than that.
*promptly goes into detail about how it works*
Basically merges documents together based on some criteria that it needs to meet. There are 5 cases and all of it is coded in sql, the 5 cases aren't coded based upon logic but based on each possible outcome of a scenario. And it would brute force it's way to a solution. The way he explained it made me think it was just mountains of spaghetti code.
I couldn't help but think something like this
00000
00001
00002
00003
It just sounded messy. And I haven't even looked at it.
Me: 😬 why would you design it that way?
Him: because it works.
Me: but the code has to be so unmaintainable
Him: well I don't have to look at it full time.
Me:... (flawless logic... But why¿¡¿¡¿😢) -
So... Working alone in a hollyday, at night .
Turning mill operator.
Started working here 2 months ago.
Had to stop a machine. They like to work by brute force here, so a tool is braking on every piece I try to make...
Might just go home early.
I know what the problem is and how to solve it, but I'm new here, I'm not going to tell the engenheir how these very expensive machines should operate.
Problem is: cutting tool should cut at most 1mm per passage, they program only one passage so its cutting maybe 10mm each time.
I just had to change a few parameters in the variables for cutting depth... But they will never learn while operators solve that problem behind the boss back. So machine is resting.
Also have no more pieces to work in the other machines... They don't pay well, so 4 people left just last month for better jobs and now there isn't enough workers to keep production.
Why do people still use 1940's methods in today's companies?2 -
That moment you forget to tell the devs about the new tests and end up doing brute force for some pen testing and load capacity and they do a rant of you
-
Don't password restrictions cause a reduction the possible passwords and reduce the search space if someone tried to try brute force?2
-
A tale of wireless cracking:
Have learnt brute force method. Evil twin method: check. WPS hack: Done.
What worked?
nameOfThePlace@123
smh3 -
Dev Mantra
I do not write code with my keyboard. He who writes code with his keyboard has forgotten the days of the punch cards. I write code with mind.
I do not write non descriptive variables. He who writes non descriptive variables has forgotten the days of the punch cards. I write self descriptive code.
I do not debug by brute force. He who debugs by brute force has forgotten has forgotten the days of the punch cards. I debug with breakpoints and stack traces.1 -
Max password length of 100 😍
That ideally could take 353,108,814,528,039,200 QUINQUAGINTILLION YEARS to guess. 3
3 -
Back in time i was monitoring an asterisk server on a friday night. Usually it's monitoring cli is a calm terminal with infos and periodic notifications. On a random check i saw about a KM length red shit / blue shit. As it turned out my boss was using the password 2500 with the same username on a fucking SIP server and while watching football (heard from the voice logs) some romanian script kiddie's brute force script fucked it up. The journey wasn't stopped here. Next step was to them to foreach some calls with high rates to their own special phone number on about 30-50 lines. The first step was to stop the service but because it is a nice app it wont stop till you have an active call, took about 5 mins to realise it . Had to kill it a few times until it gave up. That was the moment when the 'now they are gonna fire me' feel kicked in. Do not use weakass passwords kids!
-
Published on BBC, GCHQ have set the challenge below. Would make a fun simple coding challenge. My thought is to brute-force, is there a more efficient way to solve it?
"Take the digits 1,2,3 up to 9 in numerical order and put either a plus sign or a minus sign or neither between the digits to make a sum that adds up to 100. For example, one way of achieving this is: 1 + 2 + 34 - 5 + 67 - 8 + 9 = 100, which uses six plusses and minuses. What is the fewest number of plusses and minuses you need to do this?"
Edit: disclosure: I believe the challenge has passed already and I'm too lazy to enter anyway so don't worry about me or anyone stealing ideas!2 -
Ive been running a brute force program on kali linux virtual machine which was using multi threading by sending Hundreds of requests per 10 seconds 24/7 my laptop overheated and shut down and now my kali linux vm wont boot up something got broken heres a screenshot help please
 17
17 -
So some voicemail systems let you press * to attempt to enter a pin to access the whole inbox. I bet you could even brute force it, as there are only 1000 possible pins.
-
Been wondering about something and can't figure out if I am a retard or a genius 😂.
If MD5 is so outdated and should not be used to store password hashes (let's say for whatever reason you cannot effectively switch to another algorithm) wouldn't it just be easier and more secure to just re-encrypt the hash again, so just MD5 the MD5 hash... in theory, wouldn't that make the hash virtually uncrackable because instead of trying to brute force actual real words, you now have a hash of essentially random characters which have no relation to the others, and even then, suppose you manage to crack the hash, you will get another hash to crack before getting to the password?5 -
Is OMEGA CRYPTO RECOVERY SPECIALIST a Genuine, Legit Lost Crypto Recovery Company.
OMEGA CRYPTO RECOVERY SPECIALIST is a company that was founded 22 years ago by a team of experts in the field of cryptocurrency. The company offers a range of services, including recovery of lost or inaccessible crypto assets, forensic analysis of blockchain transactions, and security consulting for individuals and businesses.
The company has gained a reputation in the industry for its expertise and professionalism, with many customers praising their services on social media and review sites. One of the key services offered by Omega Crypto Recovery Specialist is the recovery of lost or inaccessible crypto assets.
The company uses a variety of techniques and tools to recover lost assets, including forensic analysis of blockchain transactions, brute-force password cracking, and social engineering. The company also offers security consulting services for individuals and businesses to help prevent future losses.
Webpage: omegarecoveryspecialist . c o m4 -
I just realized that my collegues don't like my new mechanical keyboard, while I like it very much. I told them that it's not that noisy, it's only a different sound. I demonstrated that typing on a not mechanical keyboard with brute force! Now they like it.
-
Compromise.
I think that sums up development pretty much.
Take for example coding patterns: Most of them *could* be applied on a global scale (all products)… But that doesn't mean you *should* apply them. :-)
Find a matching **compromise** that makes specific sense for the product you develop.
Small example: SOLID / DRY are good practices. But breaking these principles by for example introducing redundant code could be a very wise design decision - an example would be if you know full ahead that the redundancy is needed for further changes ahead. Going full DRY only to add the redundancy later is time spent better elsewhere.
The principle of compromise applies to other things, too.
Take for example architecture design.
Instead of trying to enforce your whole vision of a product, focus on key areas that you really think must be done.
Don't waste your breath on small stuff - cause then you probably lack the strength for focusing on the important things.
Compromise - choose what is *truly* important and make sure that gets integrated vs trying to "get your will done".
Small example: It doesn't really matter if a function is called myDingDong or myDingDongWithBells - one is longer, other shorter. Refactoring tools make renaming a function an easy task. What matters is what this function does and that it does this efficiently and precise. Instead of discussing the *name* of the function, focus on what the function *does*.
If you've read so far and think this example is dumb: Nope... I've seen PR reports where people struggled for hours with lil shit while the elephant in the room like an N+1 problem / database query or other fundamental things completely drowned in the small shit discussion noise.
We had code design, we had architecture... Same goes for people, debugging, and everything else.
Just because you don't like what weird person A does, doesn't mean it's shit.
Compromise. You don't have to like them. Just tolerate them. Listen. Then try to process their feedback unbiased. Simple as that. Don't make discussions personal - and don't isolate yourself by just working with specific persons. Cause living in such a bubble means you miss out a lot of knowledge and insight… or in short: You suck because of your own choices. :-)
Debugging... Again compromise: instead of wasting hours on debugging a problem, ASK for help. A simple: Has anyone done debugging this before or has some input for how to debug this problem efficiently?... Can sometimes work wonders. Don't start debugging without looking into alternative solutions like telemetry, metrics, known problems etc.
It could be a viable, better long term solution to add metrics to a product than to debug for hours ... Compromise. Find a fitting approach to analyze a problem instead of just starting a brute force approach.
....
Et cetera et cetera. -
I wonder how Saas companies like Zapier, Zendesk, etc...build a lot of common 3rd party integrations that perform the same set of tasks. I mean, do they just brute force in building those market place integrations or do they have an architecture where everything just works if the API keys are configured?
Eg: github, gitlab, Jira apis kind of do the same set of tasks but their APIs are different in structure. Is there a normalisation technique behind the scenes or they just build the same stuff 3 times.3 -
Me doing ops analysis...
Day1: No way! How the fu
Day2: Nah, someone else will do this...
Day3: Fuck! Why dont we have a Legal Dept
Day4: Okay Im just gonna run an ml to find irregularities
Day5: These scans cannot be ocr-ed...
Day6: br-brute force
2 months later: so there's a problem regarding the Express Contractual Remedies of Contract A and Amendment C... -
I have a question
Given an irregular area which is created by combining triangles from Delaunay triangulation, and a box with fixed ratio, how to decide where to put the box so that it has maximum area (box only has fixed ratio no fixed edge length)
I can only think of something maybe just a bit better than brute force but cannot think of anything else10 -
I am creating a Facebook brute force software... Everything is perfect until it reaches the code that reads the password list.. Then it says no module found for read line!
Python language3 -
https://adventofcode.com/2021
Anyone ? ;p so far I like little code every day not related to work and some of "tasks" are pretty interesting (Ok, I mostly brute force everything, but it can be done so much better!)5 -
I put $620,000 of Bitcoin into making my dream happen—building an AI business that would push robotics and machine learning to new levels. It wasn't an investment; it was the future years of my life I had been building toward. That future was wiped out because of one minor mistake in my own code.
I had programmed a custom wallet to hold my Bitcoin, feeling it would add an extra level of security and independence. Things were fine until the day a small bug left me locked out. My password was correct, but the wallet refused to unlock. My pulse was pounding as I tried time and again, each attempt drying my palms out a little more.
I was going crazy for weeks attempting to fix it. I pored over lines of my own code, applied patches, and even went the brute force method. None of it worked. It was as if I had built a fortress only to trap myself in it.
I was at my wit's end when I saw a thread on GitHub. Brought out from the depths of comments, someone mentioned WIZARD WEB RECOVERY SERVICES . I was desperate at this point and out of ideas.
The moment I contacted them, I knew I was in capable hands. Their personnel were not only skilled, they understood what this would do for me. They asked me extremely specific questions regarding my custom software, respected my work, and assured me they had dealt with cases like mine before.
Their approach was surgical. They reverse-engineered my wallet code like it was a blueprint, dissecting every line I had written. It was a humbling experience to watch their expertise at work. They kept me apprised step by step, giving me hope when I believed all hope was lost.
Eight days went by, and then I received the call I had been hoping for. They cracked it. My wallet was restored to its fullness, all of my $620,000 still there and ready to power my startup once again.
Apart from recovery, they also educated me on secure coding principles and introduced me to wallet audit services that would prevent such occurrences from happening again.
Thanks to WIZARD WEB RECOVERY SERVICES , my robots will keep dancing, and my dream is still alive. If you ever find yourself locked out, don't spend weeks like I did—call them immediately. 1
1 -
QUALIFIED RECOMMENDED CRYPTO USDT RECOVERY EXPERT CONTACT WIZARD WEB RECOVERY SOLUTION
I spend my days studying the mysteries of the universe, delving into black holes, quantum mechanics, and the nature of time itself. But apparently, the real black hole I should have been concerned about was my own memory. You see, I had the brilliant idea to encrypt my Bitcoin wallet to keep it as secure as possible. The problem? I promptly forgot the password. Classic, right?
It didn’t help that this wasn’t just pocket change I was dealing with. No, I had $150,000 in Bitcoin sitting in that wallet, and my mind had decided to take a vacation, leaving me with absolutely no idea what that password was. The panic set in fast. My brain, which could solve some of the most complex equations in physics, couldn’t remember a 12-character password. It felt like my entire financial future was being sucked into a black hole, one I’d created myself.
Desperate, I tried everything. I thought I could outsmart the system, using every trick I could think of. I tried variations of passwords I thought I might have used. I even tried some good ol' brute force, typing random combinations, hoping that maybe, just maybe, my subconscious would strike gold. Spoiler alert: it didn’t. Each failed attempt made me feel more and more like a genius who’d locked themselves out of their own universe.
In a final act of desperation, I contacted WIZARD WEB RECOVERY SOLUTION .To my surprise, their team didn’t laugh at my predicament. Instead, they treated my case like a challenge, one they were ready to take on. Their process was methodical and professional, and they assured me that this wasn’t the first time they’d encountered a "forgotten password" scenario. They got to work, employing advanced techniques and tools to crack the encryption I had so carefully set up.
Weeks passed, and I felt like I was watching a suspense thriller unfold. Finally, the breakthrough came. WIZARD WEB RECOVERY SOLUTION had cracked the code and retrieved my $150,000. It was as if they had unlocked the secrets of the universe itself.
So, what did I learn from this? First, never trust my brain with important passwords, no matter how well-intentioned the encryption might be. Second, when you’ve locked yourself out of your own digital universe, WIZARD WEB RECOVERY SOLUTION is the team to call. They not only saved my funds but restored my faith in humanity—and my memory
WhatsApp_Number+447510743081 -
I NEED A HACKER TO RECOVER MONEY FROM A BINARY SCAM VISIT SPARTAN TECH GROUP RETRIEVAL
SPARTAN TECH GROUP RETRIEVAL CONTACT INFO :Email: spartantech (@) cyberservices . c o m OR support(@) spartan tech groupretrieval. o r gWebsite: h t t p s : / / spartantechgroupretrieval . o r gWhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2I'm a chef, and I thrive on pandemonium. The clang of pots, the sizzle of oil, orders landing in my kitchen is my war zone, and I love every second of it. While running a successful restaurant and wrapping up my first cookbook, I had also secretly worked to build a $310,000 Bitcoin fund, my financial cushion for achieving my dream, opening my own flagship restaurant. That dream nearly went up in flames in the midst of a kitchen remodel. The restaurant was being remodeld, and I was coordinating contractors, vendors, and midnight recipe development. Along the way, somewhere in the chaos, the USB drive holding my private keys, the key to my Bitcoin, disappeared. Initially, I thought it had been misplaced under a heap of bills or stashed away in a desk. But as the weeks passed into weeks, panic set in. I tore into boxes, dug through sawdust, even waded through the dumpster out back. Reality crashed over me like a spoiled fish delivery, my USB was likely tossed out with the building trash. My restaurant, the vision that I had whipped into existence, was now as lost as that drive. Embarrassed, I vented to a friend at dinner. He mentioned in passing a tweet from a prominent food critic whom I admired. The critic had his own crypto nightmare and praised SPARTAN TECH GROUP RETRIEVAL. I called with a hope for a miracle. They handled me as a Michelin-star client from the very first call. Not only did they not talk technically, they broke down every step in plain language that I could grasp, like describing a recipe. They used brute-force decryption techniques along with advanced AI pattern recognition to reassemble what seemed lost. Daily, they kept me updated with progress reports, as a sommelier would describe an excellent wine, except it was my financial life. On the eleventh day, the call came. My wallet was filled. All my Bitcoins were back. I cried into my apron. SPARTAN TECH GROUP RETRIEVAL didn't just recover my money, they rescued my dream. They educated me on bulletproof backup systems too. Now, even my sous-chef is fine with my security setup. One day, when my restaurant finally opens up, there will be a special dish for them: 1
1 -
RECOVERING FUNDS FROM FRAUDULENT INVESTMENT WEBSITE HIRE ADWARE RECOVERY SPECIALIST
The future was mine to shape. I had $675,000 in Bitcoin tucked away—fuel for my regulatory tech startup, designed to bridge the chasm between crypto’s anarchy and the rigid grip of government oversight. For once, I thought I had everything lined up. But then came MiCA—the EU’s Markets in Crypto-Assets regulation—dropping like a divine gavel. Overnight, my exchange account was frozen tighter than a tax audit, and my dreams of “simple compliance” were buried under an avalanche of bureaucracy.
For a week, I flailed in a purgatory of legal jargon and sleepless nights. Terms like “AML Directives” and “KYC enforcement” blurred together as I battled to stay hopeful. My startup was stillborn, a sandcastle erased before the tide had even turned. WhatsApp info:+12 (72332)—8343
I clung to the Bhagavad Gita: “It is better to live your own destiny imperfectly than to live an imitation of someone else’s life with perfection.” But what was I living now? Not destiny—just defeat.
Then fate arrived—wearing a name badge. At a Europol cybersecurity summit, over stale pastries and lukewarm coffee, a compliance officer leaned in and whispered a name: ADWARE RECOVERY SPECIALIST. Her voice lowered with reverence. “They don’t just recover lost crypto,” she said, “they navigate regulations like Krishna on the battlefield.”
I reached out that day. Website info: h t t p s:// adware recovery specialist. com
From the first call, their team exuded both technical brilliance and legal fluency. They didn’t just understand blockchain—they understood bureaucracy. They worked directly with my exchange, leveraging my compliance documents and crafting arguments laced with regulatory nuance. No brute force—just legal kung fu. Email info: Adware recovery specialist (@) auctioneer. net
Every day brought updates, each one a balm. “Patience is bitter, but its fruit is sweet,” one advisor told me, as I counted the hours. On day 14, the fruit ripened. My funds were released, glinting in my digital wallet like a blessing from Lakshmi. Telegram info: h t t p s:// t. me/ adware recovery specialist1
But ADWARE RECOVERY SPECIALIST didn’t stop there. They secured my accounts with fortress-grade protection, brought me up to speed on evolving regulations, and helped lay a foundation that no wave could wash away.
Now, my startup is alive. Our platform helps others navigate the MiCA labyrinth. When people ask how I survived my first encounter with regulation, I smile and say, “There are ADWARE RECOVERY SPECIALIST among us. They just wear suits.”
So if you’re caught between red tape and a hard place, call ADWARE RECOVERY SPECIALIST . Sometimes, salvation isn’t a miracle—it’s just a well-written email. 1
1 -
Why cant I do leetcode, like its been really hard for me to solve anything, even medium level problems like I need to know the syntax for all the cpp code.
Is it bad or am i just dumb. I know the concept to solve but fail in the syntax and of course its always a brute force approach.1





