Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "rsa"
-
So I got the job. Here's a story, never let anyone stop you from accomplishing your dreams!
It all started in 2010. Windows just crashed unrecoverably for the 3rd time in two years. Back then I wasn't good with computers yet so we got our tech guy to look at it and he said: "either pay for a windows license again (we nearly spend 1K on licenses already) or try another operating system which is free: Ubuntu. If you don't like it anyways, we can always switch back to Windows!"
Oh well, fair enough, not much to lose, right! So we went with Ubuntu. Within about 2 hours I could find everything. From the software installer to OpenOffice, browsers, email things and so on. Also I already got the basics of the Linux terminal (bash in this case) like ls, cd, mkdir and a few more.
My parents found it very easy to work with as well so we decided to stick with it.
I already started to experiment with some html/css code because the thought of being able to write my own websites was awesome! Within about a week or so I figured out a simple html site.
Then I started to experiment more and more.
After about a year of trial and error (repeat about 1000+ times) I finally got my first Apache server setup on a VirtualBox running Ubuntu server. Damn, it felt awesome to see my own shit working!
From that moment on I continued to try everything I could with Linux because I found the principle that I basically could do everything I wanted (possible with software solutions) without any limitations (like with Windows/Mac) very fucking awesome. I owned the fucking system.
Then, after some years, I got my first shared hosting plan! It was awesome to see my own (with subdomain) website online, functioning very well!
I started to learn stuff like FTP, SSH and so on.
Went on with trial and error for a while and then the thought occured to me: what if I'd have a little server ONLINE which I could use myself to experiment around?
First rented VPS was there! Couldn't get enough of it and kept experimenting with server thingies, linux in general aaand so on.
Started learning about rsa key based login, firewalls (iptables), brute force prevention (fail2ban), vhosts (apache2 still), SSL (damn this was an interesting one, how the fuck do you do this yourself?!), PHP and many other things.
Then, after a while, the thought came to mind: what if I'd have a dedicated server!?!?!?!
I ordered my first fucking dedicated server. Damn, this was awesome! Already knew some stuff about defending myself from brute force bots and so on so it went pretty well.
Finally made the jump to NginX and CentOS!
Made multiple VPS's for shitloads of purposes and just to learn. Started working with reverse proxies (nginx), proxy servers, SSL for everything (because fuck basic http WITHOUT SSL), vhosts and so on.
Started with simple, one screen linux setup with ubuntu 10.04.
Running a five monitor setup now with many distro's, running about 20 servers with proxies/nginx/apache2/multiple db engines, as much security as I can integrate and this fucking passion just got me my first Linux job!
It's not just an operating system for me, it's a way of life. And with that I don't just mean the operating system, but also the idea behind it :).20 -
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
This week I quit the corporate life in favour of a much smaller company (60 people in total) and i never felt so good.
After 3 years in 2 big corporations, I began to hate coding mainly because of:
- internal political games. It's like living inside House of Cards everyday.
- management and non-tech people choosing tech stacks. Angular 4 + Bootstrap 4 alpha version + AG-Grid + IE11. Ohhh yeah. Not.
- overtime (even if it was paid double). I never did a single minute of OT for fixing something that I caused. I spent days fixing things caused by others and implementing promises that other people made.
- meetings. I spend 50-60% of the time in pointless meetings (I tracked them in certain time intervals) but the workload is same like I was working 8 hours / day.
- working in encapsulated environments without access to internet or with limited access to internet (no GitHub, no StackOverflow etc.)
- continuously changing work scope. Everyday the management wants something new introduced in the current sprint/release and nobody accepts that they have to remove other things from the scope in order to proper implement everything.
- designers that think they are working for Apple and are arguing with things like "but it's just a button! why does it take 2 days to implement?"
- 20 apps installed additionally on my phone (Citrix Receiver, RSA Token, Mobile@Work Suite etc.) just to be able to read my email
- working with outdated IDEs and tools because they have to approve every new version of a software.
- making tickets for anything. Do you want a glass of water? Open a ticket and ask for it.
- KPIs. KPIs everywhere. You don't deserve anything because the KPIs were not accomplished.
The bad part of the above things is that they affect your day-to-day personality even if you don't see it. You become more like a rock with almost 0 feelings and interests.
This is my first written "rant". If anyone is interested, I will post different situations that will explain a lot of the above aspects.13 -
So I cracked prime factorization. For real.
I can factor a 1024 bit product in 11hours on an i3.
No GPU acceleration, no massive memory overhead. Probably a lot faster with parallel computation on a better cpu, or even on a gpu.
4096 bits in 97-98 hours.
Verifiable. Not shitting you. My hearts beating out of my fucking chest. Maybe it was an act of god, I don't know, but it works.
What should I do with it?228 -
I'm a fucking finance girl. FINANCE. GIRL. Why the fuck am I spending all morning importing databases??
I'll tell you why.. "you are married to a dev. You must have picked something up." Fuck this. Fuck fuck fuck fuck. (no it's not working for the fuck of it, and whoever wrote this program deserves to be hanged by his balls from a tree)24 -
so I'm married to a developer. he works at horrible boring forever projects he is trying to make me apreachiate. well fine. I can do that. sure. but for fucks sake, why on earth does a web developer need to work weekends?! and why can't he get time off? why is it even remotely important if the shop is up a today or a week later? who the fuck cares if people have to wait a week longer to buy fucking pumpkin oil online?! who buys fucking pumpkin oil online anyway?32
-
So my husband and best friend are arguing that I get upvotes just because I got boobs. Is it true?34
-
Project manager: how was the day?
Me: wrote a few lines of code
Me: ran the code
Me: full of errors
Me: I cried8 -
A few weeks ago at infosec lab in college
Me: so I wrote the RSA code but it's in python I hope that's ok (prof usually gets butthurt if he feels students know something more than him)
Prof: yeah, that's fine. Is it working?
Me: yeah, *shows him the code and then runs it* here
Prof: why is it generating such big ciphertext?
Me: because I'm using big prime numbers...?
Prof: why are you using big prime numbers? I asked you to use 11, 13 or 17
Me: but that's when we're solving and calculating this manually, over here we can supply proper prime numbers...
Prof: no this is not good, it shouldn't create such big ciphertext
Me: *what in the shitting hell?* Ok....but the plaintext is also kinda big (plaintext:"this is a msg")
Prof: still, ciphertext shows more characters!
Me: *yeah no fucking shit, this isn't some mono/poly-alphabetic algorithm* ok...but I do not control the length of the ciphertext...? I only supply the prime numbers and this is what it gives me...? Also the code is working fine, i don't think there's any issue with the code but you can check it if there are any logic errors...
Prof: *stares at the screen like it just smacked his mom's ass* fine
Me: *FML*12 -
So many developer that does not know how to generate a simple .csr file. Here you go:
$DOMAIN=www.yourdomain.com
$STATE=State
$CITY=The city
$COMPANY=Company Name Gmbh
openssl req -utf8 -nameopt multiline,utf8 -new -newkey rsa:2048 -nodes -sha256 -out $DOMAIN.csr -keyout $DOMAIN.key -subj "/C=Your CountryCode/ST=$STATE/L=$CITY/O=${ORG:-$COMPANY}/OU=${ORG:-IT}/CN=$DOMAIN"10 -
Because of hardware failure we had to move some vpns from one datacenter to another.
The team of highly untrained monkeys at my hosting provider were hired to do this. First they ran backups of all the systems. Then they started the moving process. A few hours later they were done. We got an email everything was back online.
So we restarted all our processes and no data was coming in from our Raspberry's around the country. So we start a little investigation. What did these buffons do, they changed our rsa keys.
So we kindly ask them to put the old keys back so we do not have to fix 200 changed key warnings on systems that are not remotely accesible.
Apperently something that can't be done because their back up process is automated and always makes new keys.
Holy fucking fuck, whats the point in having a backup its not an exact copy. Is this fucking normal?
Now I will be spending the next few weeks literally standing in cow shit reconnecting Raspberry's.
Thanks a fucking lot. Not!4 -
You know the code is in bad shape when you see variables starting with "get":
Integer getDataBlockSize;3 -
I just hate it when clients with no knowledge of developing says I'm looking for "more professional"
FUCK YOU!!!!!!!!!
Somebody did that with dedication and you can't just call it that!!
SCREW YOU!!!
😡😡😡😡😡15 -
Dont get attached to your code at work! Coz it's not your code, you got paid for writing that code and that's it.5
-
*me calculating rsa*
"aight.. Public key is 9 and n"
*calculating private key*
*recalculating cause I fucked up*
*recalculating cause I'm retarded*
*3rd recalculation*
"ok, I figured out my private key is 9 (and n)"
.... Wait a second.1 -
1. firing up the terminal
2. enter sudo apt-get install openvpn easy-rsa
3. realizing I'm on my windows machine1 -
Seriously? Microsoft does not support ed25519 SSH keys in neither Azure DevOps nor the actual Azure Virtual Machines? Like seriously? No there has to be a joke. There just ain't no way
It has been in OpenSSH since 2013.
2013.
We're in 2023, if you've forgotten.
10 years ago, OpenSSH implemented this standard.
Did you know what they tell you when you enter your valid Ed25519 SSH key into their system?
Did you know they tell you that "Your SSH key is invalid"?
WHAT DO YOU MEAN INVALID???!?! IT WORKS EVERYWHERE ELSE JUST FINE!!! YOU'RE THE ONE THAT HAS NO FUCKING BRAINS!!!
Composure.
I am calm, I am calm.
I have always. Been. CALM!
There is no one more calm than me....
I guess RSA it is then.
A second SSH key, just for Microsoft.5 -
FUCK OPENSSL. I LOVE IT AND HATE IT SO FUCKING MUCH. WORK FASTER AND BE LESS CONFUSING SO I CAN BRAG ABOUT MY PRETTY ENCRYPTION CODE SOONER. FUCK20
-
If you didn't became a developer what would you be? What's your plan B?
Mine is to be a psychologist.38 -
Work of a my co-workers good work! It's called colspan you dumb fuck! Best part is that no way I'm changing this coz I work in place where they don't give a fuck about code quality! So fuck it!
 6
6 -
Even though I have 500 reputation on StackOverflow I'm afraid to ask a question! Coz other devs can be really down right mean! No one knows everything, we are all here to learn. Some ppl don't understand that they too started like this.2
-
What if you were asked to develop something that goes against your morals or beliefs. Would you do it?
PS - they are willing to pay you more that you ask for25 -
IPAY88 is the worst payment integration. They parse html data and encoded it into xml for return the data, it is not even singlet or server to server communication , tey called it the ADVANCED BACKEND SYSTEM (My arse!) For security, they ENCODE THE STRING into BASE64 and called it ENCRYPTION ! WHAT THE FUCK?
Encoding is not encryption! I qas expecting they used diffie hellman or AES or RSA etc. THEY TOLD BE ENCODING IS ENCRYPTION? WHAT THE FUCK?1 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.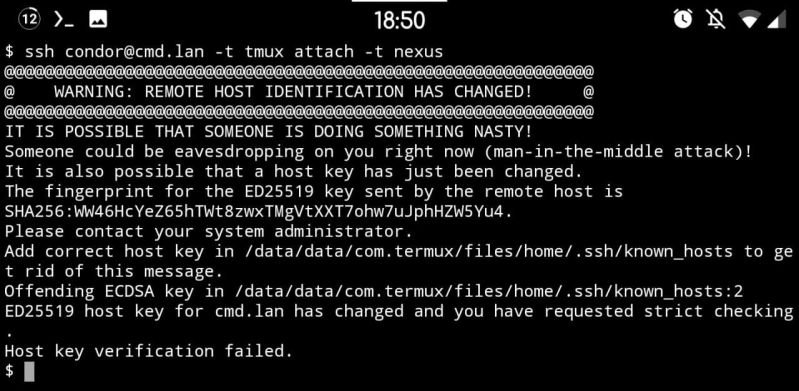 19
19 -
OpenSSH 8.2 is out. This release removes support for the ssh-rsa key algorithm. The better alternatives include:
1. RSA SHA-2 signature algorithms rsa-sha2-256/512. These algorithms have the advantage of using the same key type as "ssh-rsa" but use the safe SHA-2 hash algorithms (now used by default if the client and server support them).
2. The ssh-ed25519 signature algorithm.
3. ECDSA algorithms: ecdsa-sha2-nistp256/384/521.
In this release, support for FIDO/U2F hardware tokens. Also noteworthy, a future release of OpenSSH will enable UpdateHostKeys by default to allow the client to automatically migrate to better algorithms.17 -
serious question - is a fucking project ever finished and put away or is it common in the dev world to redo the same fucking pointless shit over and over again?4
-
WHAT THE FUCKING FUCK. What is this dude talking about?! What am I doing with my life?!?!
Test what? What do I have to do? I didn't study this. I don't know what this API thing is. My life sucks. My job sucks. I suck. I'm stupid, because apparently knowing who or what this API is is essential for being a normal part of society.
I don't even.. oh someone pls kill me.
(No I don't want a detailed explanation what I have to do - I know this is not google and i wont understand it anyways and my husband will torture me with it in the afternoon. Just some sympathy for a finance person who has to deal with this would be nice) 9
9 -
Legacy tech be like:
"The connection to this site uses TLS 1.0 (an obsolete protocol), RSA (an obsolete key exchange), and AES_128_CBC with HMAC-SHA1 (an obsolete cipher)."2 -
Have you had any money saved? What is your process when it comes to saving money? What kind of investments did you do with your savings?15
-
When you got hired
HR: please come to us if there's any problems related work so that we can give a solution.
After years of working you send a mail with you problems, it's been months. Still no reply! And try to avoid conversation regarding that problem.2 -
Got hooooot pink coloured pair of beats for my birthday!!! Best gift ever! Two most things I like is music and code this is the perfect gift! Pink is the only problem but fuck it. I love theseeeee!!!
 19
19 -
"Shit, we haven't even come up with a safe word yet!"
"Don't worry, your RSA token has been sent to your e-mail." 1
1 -
Yesterday was a day off so I developed a vue, vuex , laravel application. Today back to work and start writing some shity code!1
-
techie 1 : hey, can you give me access to X?
techie 2 : the credentials should be in the password manager repository
t1 : oh, but I don't have access to the password manager
t2 : I see your key A1B2C3D4 listed in the recipients of the file
t1 : but I lost that key :(
t2 : okay, give me your new key then.
t1 : I have my personal key uploaded to my server
t1 : can you try fetching it?
t1 : it should work with web key directory ( WKD )
t2 : okay
t2 : no record according to https://keyserver.ubuntu.com
t1 : the keyserver is personal-domain.com
t1 : try this `gpg --no-default-keyring --keyring /tmp/gpg-$$ --auto-key-locate clear,wkd --locate-keys username@personal-domain.com`
t2 : that didn't work. apparently some problem with my dirmgr `Looking for drmgr ...` and it quit
t1 : do you have `dirmngr` installed?
t2 : I have it installed `dirmngr is already the newest version (2.2.27-2)`
t2 : `gpg: waiting for the dirmngr to come up ... (5)` . this is the problem. I guess
t1 : maybe your gpg agent is stuck between states.
t1 : I don't recall the command to restart the GPG agent, but restarting the agent should probably fix it.
t1 : `gpg-connect-agent reloadagent /bye`
source : https://superuser.com/a/1183544
t1 : *uploads ASCII-armored key file*
t1 : but please don't use this permanently; this is a temporary key
t2 : ok
t2 : *uploads signed password file*
t1 : thanks
t2 : cool
*5 minutes later*
t1 : hey, I have forgotten the password to the key I sent you :(
t2 : okay
...
t2 : fall back to SSH public key encryption?
t1 : is that even possible?
t2 : Stack Overflow says its possible
t1 : * does a web search too *
t1 : source?
t2 : https://superuser.com/questions/...
t2 : lets try it out
t1 : okay
t2 : is this your key? *sends link to gitlab.com/username.keys*
t1 : yes, please use the ED25519 key.
t1 : the second one is my old 4096-bit RSA key...
t1 : which I lost
...
t1 : wait, you can't use the ED25519 key
t2 : why not?
t1 : apparently, ED25519 key is not supported
t1 : I was trying out the steps from the answer and I hit this error :
`do_convert_to_pkcs8: unsupported key type ED25519`
t2 : :facepalm: now what
t1 : :shrug:
...
t1 : *uploads ASCII-armored key file*
t1 : I'm sure of the password for this key
t1 : I use it everyday
t2 : *uploads signed password file*
*1 minute later*
t1 : finally... I have decrypted the file and gotten the password.
t1 : now attempting to login
t1 : I'm in!
...
t2 : I think this should be in an XKCD joke
t2 : Two tech guys sharing password.
t1 : I know a better place for it - devRant.com
t1 : if you haven't been there before; don't go there now.
t1 : go on a Friday evening; by the time you get out of it, it'll be Monday.
t1 : and you'll thank me for a _weekend well spent_
t2 : hehe.. okay.8 -
Warning long rambling story cause sleep deprivation
I never really bothered with ssh outside of using putty to remote into my servers and rpi's from my desktop to run updates, install something, or whatever else.
But today I was on a call with my cousin bored cause she was just rambling, so I opened vscode to clean my install of unnecessary extensions I installed and haven't used more than once or twice.
I saw Remote - SSH and as I was bored listening to a teenager complain about high school just like I used to (lol) and responding when she asked me something. I scrolled through the page, then the documentation just casually skimming the text
I setup an ssh key on an rpi I threw manjaro arm following the instructions on their tips and tricks page
I then moved the key to my desktop using winscp (cause lazy)
leading to having a minor hicup of rsa not being an accepted keytype (thanks 'your favorite search engine' for the help)
Finally, I was able to connect using the private key
at this point my cousin went to bed cause she has school tomorrow. But I was still doing stuff with ssh, I created a new ssh connection in VSCode, but had to go to the documentation to figure out how to make it use my fancy new key file, not hard took 30 seconds of looking to get it working.
Now that I was in, I moved to my development folder, created a folder for PiHole, created a compose yml, created a pihole-data folder.
I opened the yml and pasted in a compose from dockerhub.
at this point I thought 'i can't just run this from terminal can I'. and Obviously it worked cause there's literally no reason it wouldn't I'm just stupid to think it might not.
So I created folders and files on a remote system, launched a docker container, checked for package updates after on a linux machine. All from VS-Code on a windows machine.
I know this is simple for some people, i know some people are like 'where's the interesting part'. but ehhh I thought it was cool to get it setup, I now really regret not getting into ssh sooner, and I'm definitely going to uninstall vscode on all my smaller graphical VM's in favor of doing this. and this will definitely help with my headless vm's.
I also will have to thank my cousin, might not have done this if I wasn't stuck at my computer on messenger call with her lol
I'm gonna go to bed now, But I feel accomplished for the first time in a while even if it's for something so simple as setting up anssh key for the first time3 -
Did you ever take advantage of clients that has less computer literacy? Like have you ever escape a bug in the system by telling the client heavy technical BS! 😋
PS - fixings that bug later obviously!!6 -
Cracked my first weak RSA implementation challenge today. Feels pretty awesome.
Involved primes that were very close, which means you can factorize the modulus quickly to get the private key. Normally, you would never use close primes as prime factorization's difficulty relies a certain amount on some distance between the two values.
The reason you can brute force close primes has to do with them being close in value to the square root of the function, meaning that you can search far quicker than if you were to try every combination of primes.2 -
Why do I find really hard to connect with my coworkers?! I'm an introvert but after few months in my old job I connected with everyone. In my new job I find it really hard! And it's almost a year! 😥😫5
-
Ok, my RSA token for the next minute is: 740130.
Are you a L337 enough H@xx0R to pwnz my system in the time available?4 -
A conversation that i had with my co-worker today. I was having trouble getting into UAT to troubleshoot.
me
i lost access to UAT again
co-worker
F. So secure we can't even get in
me:
lol
co-worker:
I'll email whoever we did last
me:
i can get through the first phase(where you enter pin+rsa)
it denies me access after that
says bad username or password
co-worker:
Oh ok. Prolly just need to reset your pwd then. I'll find the email for helpdesk and fwd.
At least ur RSA works.
me:
yeah what a joy
co-worker:
If it's locked you may need to try from a Windows box. Horizon is bugged on Mac where the submit button stays disabled even when you type a pwd.
me:
i couldnt contain my happiness that my RSA worked
😃
co-worker:
Yeah it's exhilarating
Whenever I pick up my rsa token my life re-finds it's purpose and I feel like I'm meddling through a field of sunflowers.
I once tried to get my RSA token tattooed but it switched too quick.
me:
lol its faster that Usain Bolt
co worker:
Russia got kicked out because of their RSA tokens -
Hey fellas, especially you security nerds.
I've had asymmetric encryption explained to me a number of times but I can't get a handle on it because no example actually talks in human terms. They always say "two enormous prime numbers", which I understand, but I can't conceptualize.
Can someone walk me through an entire process, showing your math & work, using some very small, single- or double-digit primes? Such as if I were to encrypt the text "hello world" using prime numbers like 3, 5, and 710 -
I'm currently planning to set myselv up with some vps/dedicated server's for a project. What i plan to do to secure these servers is.
*Use centos 7
* Setup Wireguard and join all of the servers +1 client (my pc) to that network
*Disable SSH Access from outside that VPN
*Only allow RSA Key login to the Servers
*Install Cockpit for monitoring
*Intall docker/kubernetes for the applications i plan to run
What do you guys think of that as a baseline? Im not sure if my lower powered VPS (VPS M SSD from Contabo) will work as Kubernetes Nodes, does anyone have experience with that?
In general these Servers will be used for my projects and other fooling around.
If you guys have other suggestions for Securing/monitoring or other software i could put on to have more control without eating up to much of the Servers power, let me know :D12 -
You don't! Working for a bad company would ultimately give you the experience you need that a good company wouldn't2
-
Hmmm! So I'm passive aggressive person. I don't argue with my fellow devs I post the their faults on devRant!
-
This started as an update to my cover story for my Linked In profile, but as I got into a groove writing it, it turned into something more, but I’m not really sure what exactly. It maybe gets a little preachy towards the end so I’m not sure if I want to use it on LI but I figure it might be appreciated here:
In my IT career of nearly 20 years, I have worked on a very wide range of projects. I have worked on everything from mobile apps (both Adroid and iOS) to eCommerce to document management to CMS. I have such a broad technical background that if I am unfamiliar with any technology, there is a very good chance I can pick it up and run with it in a very short timespan.
If you think of the value that team members add to the team as a whole in mathematical terms, you have adders and you have subtractors. I am neither. I am a multiplier. I enjoy coaching, leading and architecture, but I don’t ever want to get out of the code entirely.
For the last 9 years, I have functioned as a technical team lead on a variety of highly successful and highly productive teams. As far as team leads go, I tend to be a bit more hands on. Generally, I manage to actively develop code about 25% of the time to keep my skills sharp and have a clear understanding of my team’s codebase.
Beyond that I also like to review as much of the code coming into the codebase as practical. I do this for 3 reasons. I do this because as a team lead, I am ultimately the one responsible for the quality and stability of the codebase. This also allows me to keep a finger on the pulse of the team, so that I have a better idea of who is struggling and who is outperforming. Finally, I recognize that my way may not necessarily be the best way to do something and I am perfectly willing to admit the same. I have learned just as much if not more by reviewing the work of others than having someone else review my own.
It has been said that if you find a job you love, you’ll never work a day in your life. This describes my relationship with software development perfectly. I have known that I would be writing software in some capacity for a living since I wrote my first “hello world” program in BASIC in the third grade.
I don’t like the term programmer because it has a sense of impersonality to it. I tolerate the title Software Developer, because it’s the industry standard. Personally, I prefer Software Craftsman to any other current vernacular for those that sling code for a living.
All too often is our work compiled into binary form, both literally and figuratively. Our users take for granted the fact that an app “just works”, without thinking about the proper use of layers of abstraction and separation of concerns, Gang of Four design patterns or why an abstract class was used instead of an interface. Take a look at any mediocre app’s review distribution in the App Store. You will inevitably see an inverse bell curve. Lot’s of 4’s and 5’s and lots of (but hopefully not as many) 1’s and not much in the middle. This leads one to believe that even given the subjective nature of a 5 star scale, users still look at things in terms of either “this app works for me” or “this one doesn’t”. It’s all still 1’s and 0’s.
Even as a contributor to many open source projects myself, I’ll be the first to admit that have never sat down and cracked open the Spring Framework to truly appreciate the work that has been poured into it. Yet, when I’m in backend mode, I’m working with Spring nearly every single day.
The moniker Software Craftsman helps to convey the fact that I put my heart and soul into every line of code that I or a member of my team write. An API contract isn’t just well designed or not. Some are better designed than others. Some are better documented than others. Despite the fact that the end result of our work is literally just a bunch of 1’s and 0’s, computer science is not an exact science at all. Anyone who has ever taken 200 lines of Java code and reduced it to less than 50 lines of reactive Kotlin, anyone who has ever hit that Utopia of 100% unit test coverage in a class, or anyone who can actually read that 2-line Perl implementation of the RSA algorithm understands this simple truth. Software development is an art form. I am a Software Craftsman.
#wk171 -
At the time, I'm working on a simple RAT, for leaning purpose, written I'm Go.
Now simple command-execution work's and I want to implement an encrypted connection between the client and the C&C-Server.
I know Go has some kind of TLS in its standard library, but is it really usable, or would it be easier to just implement my own simple encryption-module with some RSA and AES? -
imagine how much more intricate https would be without rsa, leaving us with just aes. i mean, youd have to have servers responding with isps, info is easily tracked.
-
The tech being rude about my RSA token not working locking me out trying to use a USB override stick...he got so mad he just walked out 😂
-
Now... I understand 2FA is to make things more secure, and I do appreciate it. BUT can we please work out a damn solution for people who work in an agency for other corporates which only have one shared account across the agency that bundles one phone number or mobile app.
What if people are on leave or sick? I need stupid 2FA to be able to login/work. uhhhhhhh.....8 -
RSA is the best. It's so secure it even keeps me out of my laptop most work days!
</Sarcasm>
Fml how am I supposed to get any work done like this....1 -
currently implementing aes and rsa for an app im currently making. currently i believe the frontend is working, but currently the backend has a problem. currently.1
-
Mine was at my school when I was 13 or 15. I didn't have a computer at home because my parents could not offered a one. Back then I didn't know any thing about computers but always knew that I wanted to do something related to computers.
So, when I went to the computer lab in my school I was so dumb, I couldn't even click on a button using the mouse. We were partnered up two students per computer and me try so hard use a computer and my partner take over and show off his talent how he can use a computer.
I was sad and devastated even though I love computer I couldn't use a computer but my willingness to learn about computers science never faded a away!
Few years fast forward; I'm a web developer and I'm happy with what I do. The fellow student who showed off still contact me for his trouble shootings regarding computers.
Never give up on you dreams -
OpenSSH has announced plans to drop support for it's SHA-1 authentication method.
According to the report of ZDNet : The OpenSSH team currently considered SHA-1 hashing algorithm insecure (broken in real-world attack in February 2017 when Google cryptographers disclosed SHAttered attack which could make two different files appear as they had the same SHA-1 file signature). The OpenSSH project will be disabling the 'ssh-rsa' (which uses SHA-1) mode by default in a future release, they also plan to enable the 'UpdateHostKeys' feature by default which allow servers to automatically migrate from the old 'ssh-rsa' mode to better authentication algorithms.2 -
So this horrible client micromanaging every single thing in the application now suddenly asking me where a menu should go! I'm like why are you asking me that now I think you should take the menu and shove it up your ass?2
-
My bank just switched from RSA SecurID to SMS-based 2-factor authentication, claiming it offers "equal security".
Is it not common knowledge that SMS 2FA is a security joke?? What the fuck guys?!? -
Hmm... I need to save generated on site rsa key in browser... O there is a npm module for that! This should be fast
4 hours later
Fuuuuuck:
http://fileformat.info/info/... -
I have switched from Chrome to Firefox in steps to de-google myself. I missed some of the features but I found a workaround apart from the Chrome Netflix Extended extension. I binge watch lots of Netflix series and after a while seeing intro again and again quite frustrates me. With Chrome, I didn't have to worry about that but with Firefox there weren't any add-ons which works properly so this weekend I decided to make my own.
If you are a Firefox user, please give it a try and let me know.
https://addons.mozilla.org/en-US/...
If you like to contribute -
https://github.com/chamra/netcham2 -
"We're excited to announce that we've disabled the deprecated Storefront Toolkit by default for new....."
I am also so freaking "excited" that you have also disabled the close button on the popup when you login to Salesforce BM genius.
How the hell i am suppose to use SFBM now?!! developer tool to remove the popup markup?!
Learn more?? I don't need FAQ doc, I need the popup closed!!! 3
3 -
I've been wondering about renting a new VPS to get all my websites sorted out again. I am tired of shared hosting and I am able to manage it as I've been in the past.
With so many great people here, I was trying to put together some of the best practices and resources on how to handle the setup and configuration of a new machine, and I hope this post may help someone while trying to gather the best know-how in the comments. Don't be scared by the lengthy post, please.
The following tips are mainly from @Condor, @Noob, @Linuxxx and some other were gathered in the webz. Thanks for @Linux for recommending me Vultr VPS. I would appreciate further feedback from the community on how to improve this and/or change anything that may seem incorrect or should be done in better way.
1. Clean install CentOS 7 or Ubuntu (I am used to both, do you recommend more? Why?)
2. Install existing updates
3. Disable root login
4. Disable password for ssh
5. RSA key login with strong passwords/passphrases
6. Set correct locale and correct timezone (if different from default)
7. Close all ports
8. Disable and delete unneeded services
9. Install CSF
10. Install knockd (is it worth it at all? Isn't it security through obscurity?)
11. Install Fail2Ban (worth to install side by side with CSF? If not, why?)
12. Install ufw firewall (or keep with CSF/Fail2Ban? Why?)
13. Install rkhunter
14. Install anti-rootkit software (side by side with rkhunter?) (SELinux or AppArmor? Why?)
15. Enable Nginx/CSF rate limiting against SYN attacks
16. For a server to be public, is an IDS / IPS recommended? If so, which and why?
17. Log Injection Attacks in Application Layer - I should keep an eye on them. Is there any tool to help scanning?
If I want to have a server that serves multiple websites, would you add/change anything to the following?
18. Install Docker and manage separate instances with a Dockerfile powered base image with the following? Or should I keep all the servers in one main installation?
19. Install Nginx
20. Install PHP-FPM
21. Install PHP7
22. Install Memcached
23. Install MariaDB
24. Install phpMyAdmin (On specific port? Any recommendations here?)
I am sorry if this is somewhat lengthy, but I hope it may get better and be a good starting guide for a new server setup (eventually become a repo). Feel free to contribute in the comments.24 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
I'm looking for more semiprimes to test my code on, regardless of the bit length, up to a reasonable number of 2048 bits because the code is unoptimized.
For those wanting to see for themselves if its more failed efforts, heres what you can do to help:
1. post a semiprime
2. optionally post a hash of one of the factors to confirm it.
3. I'll respond within the hour with a set of numbers that contain the first three digits of p and the first three digits of q.
4. After I post my answer, you post the correct answer so others can confirm it is working.
How this works:
All factors of semiprimes can be characterized by a partial factorization of n digits.
If you have a pair of primes like q=79926184211, and p=15106381891, the k=3 pair would be [151, 799]
The set of all digits of this kind is 810,000 pairs.
My answers can be no larger than 2000 pairs, and are guaranteed to contain the partial factorization regardless of the bit length of n.
I especially encourage you to participate if you never thought for a second that the RSA research I've been doing on and off for a few years was ever real.
But those who enjoyed it and thought there might be something to it, if you want to come have fun, or poke fun, I encourage you to post some numbers too!
Semiprimes only.
Keys can be any size up to 2048 bits.
But I won't take any keys under 24 bits, and none over 2048.
You should be able to prove after the fact you know p and q, not only so everyone can confirm the results for themselves, but also because I don't want anyone getting cheeky and posting say the public key to a bank or google or something.
Good luck, lets see if you got a number I can't crack.
For prime numbers you're welcome to use
https://bigprimes.org/
... or any other source you prefer.25 -
I have an Webspace for years, today I Just bought a very Small v server so I can play with it a Little bit.
Its cool.
I connected to it via ssh.
Installed everything I needed, then I wanted to allow login only with rsa keys and with No Password. Set it Up, it worked. But it was possible to Login also with the Password even when I forbidden that.
I accidently set PermitRootLogin to No.. Yeah... You know what.. now I Cant Access my Server anymore xD Shit.
Have to reinstall the complete Server..9 -
When I started at my first job I was a fanboy for a co-worker who writes codes like nothing and there's is nothing he can not do when comes to coding!! I really admire his work. I always think how does he do it?!
Now I have a fanboy for my work 😎 he admires my work he thinks that there's nothing I can't solve.
I get it now, it's just experience and practice!5 -
pip kept screwing me up with permission issues in /usr/local etc. Changed permissions for respective python folders, still got pip permission errors,did a chgrp - R user /usr.
Sudo gone
Have to reinstall :/4 -
Is there a way to implement Google analytics to a specific page.
So, my requirement is to let the user add his/her Google analytics to their page on my application. The page is in sub-route of the application (user/username)
Can I allow a user to do that? Are there any articles related to this?10 -
*in class, last year of masters program in cs*
Lecturer is talking about how digital signatures are used to verify software
Some Guy: I don't get it, what are signatures? How do they work?
*first facepalm*
Lecturer proceeds to explain signing using RSA quickly.
Some other guy next to me: Wow that's cool! Had no idea that this is how it works!
My brain: We've needed this knowledge since year 2, HOW ARE YOU HERE??? -
Ok! My new project still haven't started and I'm so bored , running out things to look into!!!
So far I have looked into
Firebase
Ethical Hacking
Some web developing concept...
Any suggestions??? Related to web developing, laravel , vuejs ???1 -
using System;
using System.Text;
using System.Text.Encodings;
//Bitwise XOR operator is represented by ^. It performs bitwise XOR operation on the corresponding bits of two operands. If the corresponding bits are same, the result is 0. If the corresponding bits are different, the result is 1.
//If the operands are of type bool, the bitwise XOR operation is equivalent to logical XOR operation between them.
using System.Text.Unicode;
using System.Windows;
using System.IO;
namespace Encryption2plzWOrk
{
class Program
{
static void Main(string[] args)
{
//random is basically a second sepret key for RSA exhanges I know there probaley is a better way to do this please tell me in github comments.//
Random r = new Random();
int random = r.Next(2000000,500000000);
int privatekey = 0;
int publickey = 0;
string privateKeyString = Console.ReadLine();
byte[] bytes3 = Encoding.ASCII.GetBytes(privateKeyString);
foreach(byte b in bytes3)
{
privatekey = b + privatekey;
}
int permutations = random/ 10000;
if(privatekey < 256)
{
while(permutations > 0)
{
foreach (byte b in bytes3)
{
privatekey = privatekey + (privatekey ^ permutations)*20;
}
}
}
publickey = privatekey*random;
Console.WriteLine("your public key is {0}",publickey);
}
}
}
would this be considerd ok HOBBYIST encryption and if not how would I do a slow improvment I used bitwise to edit bits so thats a check :D12 -
So I quit my last job because they were only focusing on developing invoicing and inventory control systems. It was really boring same old thing every day!!
When I started my current job they were developing CMS and web solutions. But recently management is considering to develop invoicing and inventory control systems (which now I HATE ).
WHAT'S WRONG WITH YOU PEOPLE THERE'S MORE THAT!!!!
😫🙄😡😠7 -
Working on some documentations on MS word and I'm pressing ctrl+space for auto complete!!🤣🤣🤣 Not only that ctrl+click for multiple cursor!!! 😂😂😂😂😂2
-
I forgot every thing and watch funny YouTube videos! And in between watching them I blame myself get depressed get angry!
I think I might be bipolar! 🤔🤣😀😂☹️3 -
Anyone knows how to hash the OAuth 1.0 signature with RSA-SHA1 using PHP? Using only the value to be hashed and a key?1
-
I did some of the front-end and whole backend. build and manage the SQL + elasticsearch database. After all of this, only 17 lines of mother fu**er code ruined my life. The client is asking for code. And.... And... Can't say anymore.
input {
file {
path => "/home/rsa-key-20200528������/aslogger.log"
type => "java"
start_position => "beginning"
}
}
output {
stdout {
codec => rubydebug
}
elasticsearch {
hosts => ["localhost:9200"]
index => "aslogger"
}
}