Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "logins"
-
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
At middle school they kept on banning the flash game sites so I made one my self but it was called something like mathhomework.somefreehost.com, the landing page looked like a homework site and all the flash games were called something like problem_1.swf. I use to sell logins to class mates at like £2.50.3
-
Started using longer passphrases for logins, colleague starts to tell people I'm doing bad things because"no one needs a password that long"
I get reprimanded by my boss
How the hell does this even happen smh13 -
*Client phones me at 11pm*
Client: It's not working!!
Me:What's the error you're getting?
Client: "Database connection error"
*Phones system/dB admin*
DB Admin: Yeah we had to change the SQL logins, I've sent you the new ones
*Phones junior dev in charge of dB programming*
Junior Dev: Yeah you'll just have to go and change the credentials. They're in all the places where we're using the dB, just before the statement, in the connection strings...
We make over 470 calls to the DB 😑16 -
Great news, our company's has a brand new security-first product, with an easy to use API and a beautiful web interface.
It is SQL-injection-enabled, XSS-compatible, logins are optional (if you do not provide a password, you are logged in as admin).
The json-api has custom-date formats, bools are any of "1", "0", 1, 0, false or null (but never true). Numbers are strings or numbers. Utf-8 is not supported. Most of our customers use special characters.
The web interface is using plain bootstrap, and because of XSS it is really easy to customize everything.
How the hell this product got launched is beyond me.10 -
Worst thing you've seen another dev do? So many things. Here is one...
Lead web developer had in the root of their web application config.txt (ex. http://OurPublicSite/config.txt) that contained passwords because they felt the web.config was not secure enough. Any/all applications off of the root could access the file to retrieve their credentials (sql server logins, network share passwords, etc)
When I pointed out the security flaw, the developer accused me of 'hacking' the site.
I get called into the vice-president's office which he was 'deeply concerned' about my ethical behavior and if we needed to make any personnel adjustments (grown-up speak for "Do I need to fire you over this?")
Me:"I didn't hack anything. You can navigate directly to the text file using any browser."
Dev: "Directory browsing is denied on the root folder, so you hacked something to get there."
Me: "No, I knew the name of the file so I was able to access it just like any other file."
Dev: "That is only because you have admin permissions. Normal people wouldn't have access"
Me: "I could access it from my home computer"
Dev:"BECAUSE YOU HAVE ADMIN PERMISSIONS!"
Me: "On my personal laptop where I never had to login?"
VP: "What? You mean ...no....please tell me I heard that wrong."
Dev: "No..no...its secure....no one can access that file."
<click..click>
VP: "Hmmm...I can see the system administration password right here. This is unacceptable."
Dev: "Only because your an admin too."
VP: "I'll head home over lunch and try this out on my laptop...oh wait...I left it on...I can remote into it from here"
<click..click..click..click>
VP: "OMG...there it is. That account has access to everything."
<in an almost panic>
Dev: "Only because it's you...you are an admin...that's what I'm trying to say."
Me: "That is not how our public web site works."
VP: "Thank you, but Adam and I need to discuss the next course of action. You two may go."
<Adam is her boss>
Not even 5 minutes later a company wide email was sent from Adam..
"I would like to thank <Dev> for finding and fixing the security flaw that was exposed on our site. She did a great job in securing our customer data and a great asset to our team. If you see <Dev> in the hallway, be sure to give her a big thank you!"
The "fix"? She moved the text file from the root to the bin directory, where technically, the file was no longer publicly visible.
That 'pattern' was used heavily until she was promoted to upper management and the younger webdev bucks (and does) felt storing admin-level passwords was unethical and found more secure ways to authenticate.5 -
Buckle up kids, this one gets saucy.
At work, we have a stress test machine that trests tensile, puncture and breaking strength for different materials used (wood construction). It had a controller software update that was supposed to be installed. I was called into the office because the folks there were unable to install it, they told me the executable just crashed, and wanted me to take a look as I am the most tech-savvy person there.
I go to the computer and open up the firmware download folder. I see a couple folders, some random VBScript file, and Installation.txt. I open the TXT, and find the first round of bullshit.
"Do not run the installer executable directly as it will not work. Run install.vbs instead."
Now, excuse me for a moment, but what kind of dick-cheese-sniffing cockmonger has end users run VBScript files to install something in 2018?! Shame I didn't think of opening it up and examining it for myself to find out what that piece of boiled dogshit did.
I suspend my cringe and run it, and lo and behold, it installs. I open the program and am faced with entering a license key. I'm given the key by the folks at the office, but quickly conclude no ways of entering it work. I reboot the program and there is an autofilled key I didn't notice previously. Whatever, I think, and hit OK.
The program starts fine, and I try with the login they had previously used. Now it doesn't work for some reason. I try it several times to no avail. Then I check the network inspector and notice that when I hit login, no network activity happens in the program, so I conclude the check must be local against some database.
I browse to the program installation directory for clues. Then I see a folder called "Databases".
"This can't be this easy", I think to myself, expecting to find some kind of JSON or something inside that I can crawl for clues. I open the folder and find something much worse. Oh, so much worse.
I find <SOFTWARE NAME>.accdb in the folder. At this point cold sweat is already running down my back at the sheer thought of using Microsoft Access for any program, but curiosity takes over and I open it anyway.
I find the database for the entire program inside. I also notice at this point that I have read/write access to the database, another thing that sent my alarm bells ringing like St. Pauls cathedral. Then I notice a table called "tUser" in the left panel.
Fearing the worst, I click over and find... And you knew it was coming...
Usernames and passwords in plain text.
Not only that, they're all in the format "admin - admin", "user - user", "tester - tester".
I suspend my will to die, login to the program and re-add the account they used previously. I leave the office and inform the peeps that the program works as intended again.
I wish I was making this shit up, but I really am not. What is the fucking point of having a login system at all when your users can just open the database with a program that nowadays comes bundled with every Windows install and easily read the logins? It's not even like the data structure is confusing like minified JSON or something, it's literally a spreadsheet in a program that a trained monkey could read.
God bless them and Satan condemn the developers of this fuckawful program.8 -
I still miss my college days. Our crappy IT Dept restricted internet usage on campus. Each student used to get 10 GB of internet data and they used Cyberoam for login (without HTTPS). 10 GB was so less (at least for me).
Now, thanks to CS50, I learned that HTTP was not secure and somehow you can access login credentials. I spent a night figuring things out and then bam!! Wireshark!!!!
I went to the Central Library and connected using Wireshark. Within a matter of minutes, I got more than 30 user ids and passwords. One of them belonged to a Professor. And guess what, it had unlimited data usage with multiple logins. I felt like I was a millionaire. On my farewell, I calculated how much data I used. It was in TBs.
Lesson: Always secure your URLs.5 -
Worst WTF dev experience? The login process from hell to a well-fortified dev environment at a client's site.
I assume a noob admin found a list of security tips and just went like "all of the above!".
You boot a Linux VM, necessary to connect to their VPN. Why necessary? Because 1) their VPN is so restrictive it has no internet access 2) the VPN connection prevents *your local PC* from accessing the internet as well. Coworkers have been seen bringing in their private laptops just to be able to google stuff.
So you connect via Cisco AnyConnect proprietary bullshit. A standard VPN client won't work. Their system sends you a one-time key via SMS as your password.
Once on their VPN, you start a remote desktop session to their internal "hopping server", which is a Windows server. After logging in with your Windows user credentials, you start a Windows Remote Desktop session *on that hopping server* to *another* Windows server, where you login with yet another set of Windows user credentials. For all these logins you have 30 seconds, otherwise back to step 1.
On that server you open a browser to access their JIRA, GitLab, etc or SSH into the actual dev machines - which AGAIN need yet another set of credentials.
So in total: VM -> VPN + RDP inside VM -> RDP #2 -> Browser/SSH/... -> Final system to work on
Input lag of one to multiple seconds. It was fucking unusable.
Now, the servers were very disconnect-happy to prevent anything "fishy" going on. Sitting at my desk at my company, connected to my company's wifi, was apparently fishy enough to kick me out every 5 to 20 minutes. And that meant starting from step 1 inside the VM again. So, never forget to plugin your network cable.
There's a special place in hell for this admin. And if there isn't, I'll PERSONALLY make the devil create one. Even now that I'm not even working on this any more.8 -
Boss insisted that verification link needs to be clicked from same IP address as account registration. Many arguments later, decision is final, we will ignore the numerous ways that this will be a burden to our users.
*Code code, test test, deploy*
We're getting a lot of traffic, we need this bitch to scale! *auto-scale and load balance all the things*
Account creation begins breaking at random, some people receiving the "Your IP address doesn't match" error. Look at login history table, what the shit... All recent logins coming from internal IP addressohfuckmylife need to look at X-Forwarded-For header for actual IP behind load balancer.
IP address matching feature stays. I am sad, drink away sadness.4 -
Got my first legit side-gig as a developer (like had to write an SOW and everything): my kids' pediatrician is amazing, but shes switching to a concierge practice, meaning she wont take any insurance, and shes going from about 1500 patients down to about 200. I already pay my mortgage-worth in insurance on a monthly basis, so we were prepared to say adios to her. At my daughter's last appointment, she pulled me aside and said "what can we do to keep you guys as patients?" and i somewhat jokingly suggested "I dunno, need any websites written?"
As a matter of fact, she did: she just fired her practice's web developer, who gave her a shitty wordpress site and fought like hell to avoid any further maintenance or updates for her. She hates the site's current layout (no surprise there) so she is basically giving me full control over a rewrite.
No user logins, no worries about compliance with PII or any of that. Literally just turning a brochure wordpress site into an angular app, hosting it on her own server and eventually building an admin page where she can change the banner text and upload new images.
And my kids will get free, top-notch health care.1 -
Le Discord login:
*logs in*
Welcome back! Would you please authenticate after your first and successful login, so that we're sure that you're not a bot?
*15 (I shit you not) craptchas later*
New login location detected! Please check your email too!
FOR FUCKING REAL DISCORD!? How about you please just let me fucking log in already? Or are your audience - gamers - really *that* prone to infections that logins from bots are that big of a problem? Because guess what motherfuckers, then you've got *WAY* bigger problems to fix already. FUCKING LET ME IN!19 -
Fucking bruteforce man. Was supposed to go sleep when got few messages from my gameserver players that their accounts have been hacked.
Checked their logs, all of their accounts have been accessed from Russia. Told them to change their passwords and they told me their previous passwords which were easy af to guess.
Digged deeper and found hundreds of thousands failed logins in the last few hours and all of them from different ips.
Since I cant modify gamefiles on client side, the solution for now was to disable in-game registration and force player registration through the website form with captcha and also where each players login name gets appended with a random suffix chosen by player from a random list..
Fuck you bruteforce scriptkiddies, good luck guessing accounts now. At least I can sleep now.18 -
This is what happens to overworked PMs.
Me: When users create accounts with social logins, they don’t have passwords in our database. If they try to enter an email and pw on the login form, what do you want the error message to say?
PM: Can we add a modal that says “Your account doesn’t have a password, set one now.” And have a password field?
Me: ☠️ That…would…allow…anyone…to…hijack…an…account…
PM: Right. Never mind.12 -
My university has impeccable data management. I needed to ssh into their Linux server for an assignment but it refused to accept my login. Which was weird because I could login to the same account on one of our websites just fine. I typed my password into a text file and then copy and pasted it into both logins. The Linux one failed but the website succeeded. After some experimentation it turns out that the Linux server only recognized my username if I typed it in all lowercase, even though when I created the account it had uppercase characters as well.
So let me walk you through the sloppiness that had to have occurred for this to happen. When I first created the account it must have ignored what I entered and just saved the username in all lowercase without communicating that to me. Then the websites that use this account must either ignore case for usernames or lowercase the user input before querying the database. Finally, the Linux server, despite knowing that all the usernames are lowercase, is case sensitive and won't recognize the username as I originally typed it in.
Can you guess what department manages the account, website and Linux server? The Department of Computer and Information Science. Incredible.2 -
I’ve started the process of setting up the new network at work. We got a 1Gbit fibre connection.
Plan was simple, move all cables from old switch to new switch. I wish it was that easy.
The imbecile of an IT Guy at work has setup everything so complex and unnecessary stupid that I’m baffled.
We got 5 older MacPros, all running MacOS Server, but they only have one service running on them.
Then we got 2x xserve raid where there’s mounted some external NAS enclosures and another mac. Both xserve raid has to be running and connected to the main macpro who’s combining all this to a few different volumes.
Everything got a static public IP (we got a /24 block), even the workstations. Only thing that doesn’t get one ip pr machine is the guest network.
The firewall is basically set to have all ports open, allowing for easy sniffing of what services we’re running.
The “dmz” is just a /29 of our ip range, no firewall rules so the servers in the dmz can access everything in our network.
Back to the xserve, it’s accessible from the outside so employees can work from home, even though no one does it. I asked our IT guy why he hadn’t setup a VPN, his explanation was first that he didn’t manage to set it up, then he said vpn is something hackers use to hide who they are.
I’m baffled by this imbecile of an IT guy, one problem is he only works there 25% of the time because of some health issues. So when one of the NAS enclosures didn’t mount after a power outage, he wasn’t at work, and took the whole day to reply to my messages about logins to the xserve.
I can’t wait till I get my order from fs.com with new patching equipment and tonnes of cables, and once I can merge all storage devices into one large SAN. It’ll be such a good work experience.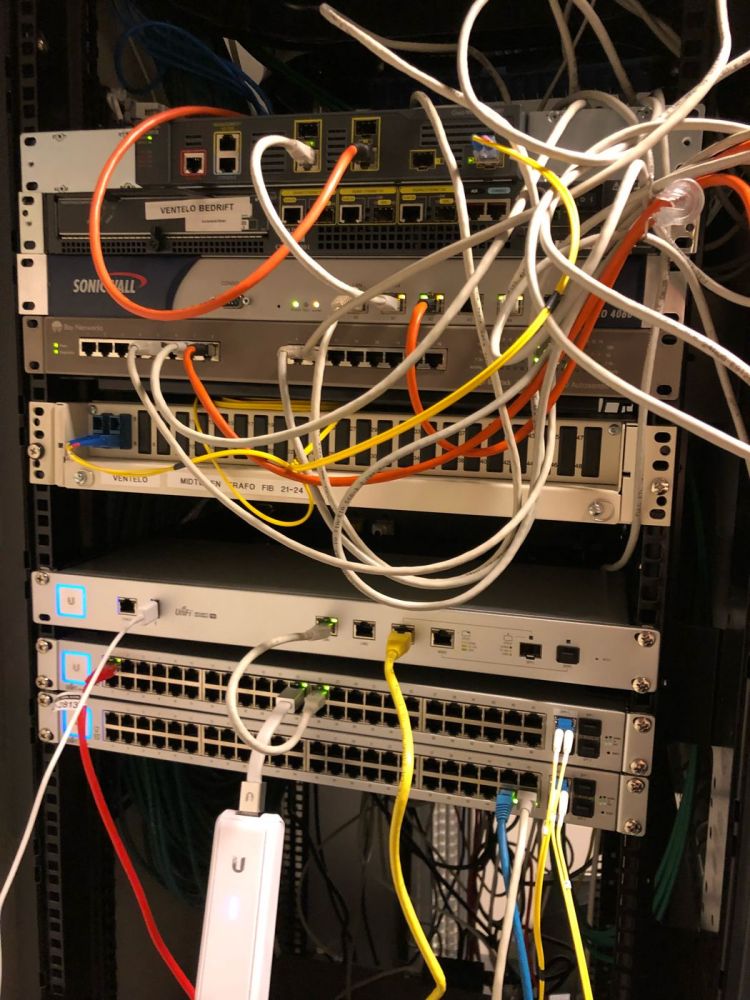 7
7 -
So I am at the client's location for onsite consultation of their projects.
The HoD asked me to create an application to accept feedbacks from multiple points urgently. Although I was there just for consulting, I thought why not, I am anyway getting bored here.
So after explaining the functionality, she asked me, when can she accept a working app. I told her that it would depend upon a lot of factors, so give me till evening to figure it out.
When she insisted I told her, that it can take at least a month with all the APIs, logins, UI, QA etc. She was surprised and told me that she expected it in 4 days since the requirements can be fit into a single page of her notebook. (That's how she measures project duration).
I told her it's impossible, given that I am the only one working on it. So she told me that her team can do it in two days. I probably have more experience than her entire team combined, but still I thought they might know some simple magic or faster way, that I might not, so I asked her to discuss with the team and then decide.
After explaining the requirements, when she mentioned that it should be done in 2 days, everyone was kinda frozen. One of them said that it's going to take at least 4 months.
I couldn't hide my smirk 😉2 -
I've set up my server to only accept logins with SSH-keys, and permanently banning all IP:s that attempt login with passwords.
Now I can't stop watching the banned IP:s stacking up, it's like drugs to me.6 -
User logins testing:
How others name their imaginary users:
Admin
John
Jane
Bob
How I name my imaginary users:
Root (admin)
Alice
Floyd4 -
NUKE IT FROM ORBIT. It was when i was doing an assignment with my roommate, i was compiling something on my pi and ran netstat afterwards for no reason. I had an ssh-connection from china (logged in too). The pi was shutdown ASAP, i salvaged everything i needed from the sd and dd'ed raspbian on the disk again.
Turns out you were able to login via root (i thought i disabled it) with the password i set (root...). I learned from this, now external logins are only allowed via private key and i have fail2ban set up3 -
So here I am, skrewing around with the Google Authenticator app and the dodgiest base32 code generator I've ever built and generating a 56 char unique ID, and a 8 digit time based code.
WTF, all these products, services and logins that use 6 digit codes... and this fucking thing can handle 8 without breaking 😑
Now... to hook it into a QR code class... and spit out an image I can actually scan, without calling google charts api.
I can't say I've written one of those before 🙃 4
4 -
So... I’m sitting here doing pretty much nothing, just reading through some rants when all of a sudden I get a wave of emails.
Pinterest!
We noticed a login from a new device or location and want to make sure it’s you.
Device: Firefox, Windows 8
Where: New Jersey, United States (Approximate)
OhhhhhKay then... so there’s a couple of problems with this, 1 I didn’t even know I had a Pinterest account, 2 I don’t have Pinterest in my password manager either.
So I follow the link and fair enough it’s actually pintest, so I attempt to login, to no avail, oh maybe it’s a social login..., ok let’s try google, nope that wasn’t it, deletes account, logins with Facebook, oh here we go, checks logins, 1 random jersey player, deletes account, swaps to Facebook, changes password (this fucker was already 100+ characters) and adds 2FA and contains no new logins 🤔
Ok... so what the fuck, either someone managed to get through a long ass password or something phishy is going on, the email for FB logins is seldomly used (maybe a handful of services at best) as I have another for all the junk and spam bullshit I expect from today’s “marketing”rant emails i’ve had enough internet for today pinterest. i have a pinterest? internet no one is safe social login1 -
You always see fail2ban message:
There has been n failed attempts"
But... Have you ever thought about how many successful logins have been?2 -
Oh my fucking god people are stupid, or ignorant, or fucking both.
How hard is it to copy a password from an email and paste that fucker in and press login.
Seriously several times of “this is your email” and “THIS” is your god dam fucking password.
God kill me now.
(No the password isn’t stored in plaintext, I reset it myself before sending it to the user)1 -
For the last 20 years, there's one thing I've not been able to do reliably:
Share a folder on a windows computer.
Why the fuck can I write /etc/smb.conf from scratch with a blindfold on and make it securely work from all client devices including auth & acl, but when I rightclick and share on windows it's either playing hide and seek on the network (is it hiding behind //hostname/share? No? Maybe in the bushes behind the IP addresses?), or it's protected by mysterious logins requiring you to sacrifice two kittens a day.
Yes, finally it works! One windows update later... aaaand it's gone.
JUST GIVE ME A FUCKING CONF AND A MAN PAGE, MICROSOFT. I DON'T CARE THAT YOU'RE ORALLY PLEASING ALL THESE MALWARE RIDDEN GUISLUTS ON THE SIDE, JUST GIVE ME A FUCKING TEXT FILE TO STORE AND EDIT.4 -
With the movement of people recently deleting their facebook accounts, this actually covers a valid concern I didn't even think of, since I personally don't use that feature at all, nor have I ever used it.
People that used the "login with facebook" a lot, especially with websites that exclusively use it, will flush not only their facebook account doing that, but also all accounts they have ever used to log in with facebook, if not actually thought as far as checking the apps section of facebook and trying to migrate your account, which is also rarely possible.
So basically many people that do use it, simply won't delete their facebook account, because it has this backup parachute attached with its strings, that does not allow for an easy exit, except for literally ripping it all out and losing every account it seems.
Ignore dashlanes self advertisement bullshit at the bottom, the blog itself is still highly valuable in itself.
Source: https://blog.dashlane.com/delete-fa... 12
12 -
My grandfather is at age 72 & don't know much about technology. He forward me this message on whatsapp bcz I'm a software engineer. He made my day...
What is the difference between http and https ?
Time to know this with 32 lakh debit cards compromised in India.
Many of you may be aware of this difference, but it is
worth sharing for any that are not.....
The main difference between http:// and https:// is all
about keeping you secure
HTTP stands for Hyper Text Transfer Protocol
The S (big surprise) stands for "Secure".. If you visit a
Website or web page, and look at the address in the web browser, it is likely begin with the following: http:///.
This means that the website is talking to your browser using
the regular unsecured language. In other words, it is possible for someone to "eavesdrop" on your computer's conversation with the Website. If you fill out a form on the website, someone might see the information you send to that site.
This is why you never ever enter your credit card number in an
Http website! But if the web address begins with https://, that means your computer is talking to the website in a
Secure code that no one can eavesdrop on.
You understand why this is so important, right?
If a website ever asks you to enter your Credit/Debit card
Information, you should automatically look to see if the web
address begins with https://.
If it doesn't, You should NEVER enter sensitive
Information....such as a credit/debit card number.
PASS IT ON (You may save someone a lot of grief).
GK:
While checking the name of any website, first look for the domain extension (.com or .org, .co.in, .net etc). The name just before this is the domain name of the website. Eg, in the above example, http://amazon.diwali-festivals.com, the word before .com is "diwali-festivals" (and NOT "amazon"). So, this webpage does not belong to amazon.com but belongs to "diwali-festivals.com", which we all haven't heard before.
You can similarly check for bank frauds.
Before your ebanking logins, make sure that the name just before ".com" is the name of your bank. "Something.icicibank.com" belongs to icici, but icicibank.some1else.com belongs to "some1else".
👆 *Simple but good knowledge to have at times like these* 👆3 -
Security! I wish clients would listen to me regarding security...
The client has started to ask me to give them access to all the logins I have for the email, domain, server etc.
I created them a new account and gave them admin access.
Now they’re asking for password for all the email accounts (I don’t even store them). So I asked why, she wanted to have them in case some of the employees forgot their password.
I explained to her, deeply and many times, WHY THIS IS A BAD FUCKING IDEA. I also discovered she’s keeping it in a document, clear text.
Why do they pay me for support, when they want to have access to everything...
I’m wondering if they’re planning to find someone else to do their support, or do it themselves.
I didn’t even think 25€ pr month is that expensive for support2 -
One of my websites is under a brute attack.
If I were to redirect failed logins to an illegal website (drugs, child pornography, terrorism support, etc...), will the feds come after me? Or will they go after the attacker?22 -
Specifications called for user logins to be stored in a session and not be persistent. When the session ends, you need to login again. The system deals with insurance policy information and persistent login was deemed a security risk.
First ticket submitted by the client after go-live? "Please make the login page remember my user name and password, or that I've logged in previously."2 -
I am so fucking lost.
I literally have zero expectations from life for now and future.
There was a time when I had so much clarity in my life. Rather, I was known for it.
Folks used to reach me out for guidance and my approaches even worked for others.
I was goal oriented and biased towards action. Failing and learning from it, I used to make things happen and with constant feedback kept progressing.
While none of that has changed, I still feel lost and numb. No, I am not depressed or suffering through any mental illness. I am physical active and able to feel the happiness.
But the recent incident with a narcissistic, left me emotionally handicap. I can no longer feel any kind of love or affection. I overcame the damage done and healed myself.
But now, I am done. Even if I engage with anyone for a relationship it would be mostly for sex. I can care for people around me and be affectionate towards them but when it comes to an intimate relationship, I feel it's not something I can do in this lifetime. I tried multiple times but failed.
These days, all I am doing is putting my heads down and working like crazy. Never in my life I worked more than 10 hours in an entire week. Now, I work 10+ hours everyday. During that time, I am highly productive.
And in my free time, I am busy housekeeping different life problems. Either paying bills, figuring out an insurance, planning some investment, or making some kind of life decision.
It's draining me. I feel as if I am losing sanity. But that's the only thing I am able to do.
Maybe it's the lockdown effect. Maybe some damage is yet to be healed.
But I got nothing better to do. I have some good ideas. Not those hipster-ish disruptive Million dollar ideas, but decent enough to solve a problem for a strong use case.
However, all of this is becoming overwhelming these days. Because decision making is complex and difficult task. It can make or break the future.
As of now I am confused how should I go about pursuing two of the important projects that I want to accomplish.
1. Migrating out of Google ecosystem. Is it even practically possible for my use case? What are the alternatives? Planning to opt in for a paid cloud storage so have to factor in that aspect as well.
I want to keep this new setup only for official use like bank and government stuff. Maybe family and close friends. Then have current ids for public logins and sharing it with retards whom I can block or ignore if they harass me. The research is overwhelming but having a structured setup gives insane amount of efficiency when life is spam free.
2. Migrating my Pihole and OpenVPN setup out of Digital Ocean to GCP. Primarily because $5 is a lot of amount for my computational requirements and Google has used my data enough, for me to use the free tier.
However, there isn't a simple script for a tech noob like me, to go ahead and setup something. I did find a Github repository but the documentation is kind of outdated so RTFM failed for me.
I don't know whether to pursue my start-up or let it go and focus on moving to Europe.
It's just so fucking stupid to even exist. And let's not forget taxes. Bloody taxes.16 -
Well! Hello everyone!
I am PokerJack. (Not a jAsE account)
Well, that's the name of my first Python Program. ~\_(-_-)_/~
Not a dev, would like to be one.
I work at Pornhub as a Consultant.
@rutee07 is my subordinate.
@devTea is my assistant
@Root - Dev Lead
@grumpyoldaf - Boss
@irene - Girlfriend
@jAsE - Heard about him, never found out who.
Btw, @rutee07 send me the test logins for all Pornhub Premium accounts. Immediately!!20 -
This week I’ve been reinstating IE11 support.
OMFG WHY!? I hear you ask.
Is it due to critical legacy integration dependencies? AD Intranet logins? Draconian Group Policy rules?
Nope. This ONE user just prefers it! 🤯
How much are we getting paid for this nonsense? Sweet FA!
#cognativedissonance 😢3 -
About slightly more than a year ago I started volunteering at the local general students committee. They desperately searched for someone playing the role of both political head of division as well as the system administrator, for around half a year before I took the job.
When I started the data center was mostly abandoned with most of the computational power and resources just laying around unused. They already ran some kvm-hosts with around 6 virtual machines, including a cloud service, internally used shared storage, a user directory and also 10 workstations and a WiFi-Network. Everything except one virtual machine ran on GNU/Linux-systems and was built on open source technology. The administration was done through shared passwords, bash-scripts and instructions in an extensive MediaWiki instance.
My introduction into this whole eco-system was basically this:
"Ever did something with linux before? Here you have the logins - have fun. Oh, and please don't break stuff. Thank you!"
Since I had only managed a small personal server before and learned stuff about networking, it-sec and administration only from courses in university I quickly shaped a small team eager to build great things which would bring in the knowledge necessary to create something awesome. We had a lot of fun diving into modern technologies, discussing the future of this infrastructure and simply try out and fail hard while implementing those ideas.
Today, a year and a half later, we look at around 40 virtual machines spiced with a lot of magic. We host several internal and external services like cloud, chat, ticket-system, websites, blog, notepad, DNS, DHCP, VPN, firewall, confluence, freifunk (free network mesh), ubuntu mirror etc. Everything is managed through a central puppet-configuration infrastructure. Changes in configuration are deployed in minutes across all servers. We utilize docker for application deployment and gitlab for code management. We provide incremental, distributed backups, a central database and a distributed network across the campus. We created a desktop workstation environment based on Ubuntu Server for deployment on bare-metal machines through the foreman project. Almost everything free and open source.
The whole system now is easily configurable, allows updating, maintenance and deployment of old and new services. We reached our main goal for this year which was the creation of a documented environment which is maintainable by one administrator.
Although we did this in our free-time without any payment it was a great year with a lot of experience which pays off now. -
A long time ago I started a project to make a devRant client with Python and Qt5.
I got far but got bored, or whatever. Was still in school, etc.
I have started from scratch again. Including a nogui mode. Sharing because I actually have made some pretty good progress in the past two days.
Plans: Besides the obvious fully-featured client: full support for plugins, custom themes, custom CLI commands. Multiple logins.
Considering a system that allows you to run a bot, and a bot framework (parsing arguments for you, marking notifs read, etc.)
And yes, it's called qtpy-rant (Pronounced cutie pie rant)1 -
When I was in 11th class, my school got a new setup for the school PCs. Instead of just resetting them every time they are shut down (to a state in which it contained a virus, great) and having shared files on a network drive (where everyone could delete anything), they used iServ. Apparently many schools started using that around that time, I heard many bad things about it, not only from my school.
Since school is sh*t and I had nothing better to do in computer class (they never taught us anything new anyway), I experimented with it. My main target was the storage limit. Logins on the school PCs were made with domain accounts, which also logged you in with the iServ account, then the user folder was synchronised with the iServ server. The storage limit there was given as 200MB or something of that order. To have some dummy files, I downloaded every program from portableapps.com, that was an easy way to get a lot of data without much manual effort. Then I copied that folder, which was located on the desktop, and pasted it onto the desktop. Then I took all of that and duplicated it again. And again and again and again... I watched the amount increate, 170MB, 180, 190, 200, I got a mail saying that my storage is full, 210, 220, 230, ... It just kept filling up with absolutely zero consequences.
At some point I started using the web interface to copy the files, which had even more interesting side effects: Apparently, while the server was copying huge amounts of files to itself, nobody in the entire iServ system could log in, neither on the web interface, nor on the PCs. But I didn't notice that at first, I thought just my account was busy and of course I didn't expect it to be this badly programmed that a single copy operation could lock the entire system. I was told later, but at that point the headmaster had already called in someone from the actual police, because they thought I had hacked into whatever. He basically said "don't do again pls" and left again. In the meantime, a teacher had told me to delete the files until a certain date, but he locked my account way earlier so that I couldn't even do it.
Btw, I now own a Minecraft account of which I can never change the security questions or reset the password, because the mail address doesn't exist anymore and I have no more contact to the person who gave it to me. I got that account as a price because I made the best program in a project week about Java, which greatly showed how much the computer classes helped the students learn programming: Of the ~20 students, only one other person actually had a program at the end of the challenge and it was something like hello world. I had translated a TI Basic program for approximating fractions from decimal numbers to Java.
The big irony about sending the police to me as the 1337_h4x0r: A classmate actually tried to hack into the server. He even managed to make it send a mail from someone else's account, as far as I know. And he found a way to put a file into any account, which he shortly considered to use to put a shutdown command into autostart. But of course, I must be the great hacker.3 -
Sometimes lack of confidence in one area reveals oversight cockyness in stronger areas:
Set up a simple login system from Unity engine to php to mysql db, using android device ID as the login id. Set up database column to accept 32 length varchar for MD5 hashed strings, as I knew the method I was getting the android device ID was automatically being hashed that way and more or less was what I wanted anyway.
Spend 2 days wondering why it would insert the logins with 0 issue, but could never retrieve them. Due to lack of web development and PHP skills, I assumed I was screwing up the handling of mysqli_num_rows() (to check whether I was inserting or selecting in the query) or simply screwing up my SQL queries.
Rewrite the code a few times, even went back to a method I had used in the past.
Today it dawned on me that my testing machines deviceID had been getting trimmed to the 32 character limit. Turns out I didn't account for my workstations device ID to be automatically hashed like the android device id is.
For 2 days I was obtaining and sending a 40 character string to a 32 character limit varchar and blaming my lack of PHP skills........
Back to my niche I go!1 -
Well, today I felt like the witch from the sleeping hollow movie.
I was working on a code that logins to a page and download files to a folder, according to the user.
Well, I tried to use the webservices from the page (like it should be) but the links were broken, and I lost a entire working day on trying the API 😮
The second day I tried with Selenium. Everything was going ok, but I wanted to run it without opening the browser and I found a “Headless Chrome”. At the end of the day, I found several blogs saying that Headless Chrome can’t download files 😱 second working day lost
Today I read about “PhantomJS”. I tried the code in C# with OpenQA.Selenium.PhantomJS BUUUUUUT it was missing 😡 I also tried with Python, but I had the same problem.
Finally, I found a blog with a solution for C# with Headless Chrome 😄 random phantomjs story time missing packages chrome selenium webdriver headless webdriver automation chromedriver4
random phantomjs story time missing packages chrome selenium webdriver headless webdriver automation chromedriver4 -
I slowly relise that "modrn" developpers don't know a minimal things about programming (yes, i'm using "programming" instead of "evelopping")
They copy paste shit, it works. They resolve some problems it works.
But... They have have ZERO understading of what they are doing.
Just couple of days, got a discution with a person who is "Blazor expert". who will be paied 200$ / hour to find problem in current implementation. I KNOW there are problems because couple of them I introduced my self.
We at server side. I provided test logins, plus 10 page document explaining infrastracture.
One of his first question in interview : "Oh. I cannot see ajax calls in network in chrome".
WTF DUDE ? Do you even understand how server side blazor works ?!
Welp, he is hired. FOrt 120 hours.
I' want to see what he will present, as it's clear as day he doesn't know a thing about server side blazor architecture.5 -
Working at a local seo sweat-shop as "whatever the lead dev does't feel like doing" guy.
Inherit their linux "server".
- Over 500 security updates
- Everything in /var/www is chmod to 777
- Everything in /var/www is owned by a random user that isn't apache
- Every single database is owned by root sql user
- Password for sudo user and mysql root user same as wifi password given to everyone at company.
- Custom spaghetti code dashboard with over 400 files in one directory, db/ api logins spread throughout these files, passwords in plain text.
- Dashboard doesn't have passwords, just usernames to login
- Dashboard database has all customer information including credit card stored in plain text
- Company wifi is shared by other businesses in the area
I suggest that I should try to fix some of these things.
Lead Developer / Tech Director : We're an SEO company, not a security company . . .7 -
So I'm kind of a fledgling webdev. Where would I go to learn how to do backend in order to do logins, manage inventory, create posts, that kind of thing?
I know a little bit of PHP, HTML, and CSS, but only enough to make static pages... it's kind of bad...1 -
So, i use this bulk messaging service and they decided to make logins OTP only ("for security reasons", they say), sent to your email.
So instead of entering a password quickly,
- enter the password for your email account,
- click about 10 times on Resend OTP
- wait for OTP
- copy OTP and paste in the box.
So basically relying on the person's email provider's security than deploying their own. -
Windows 10 Action Center yesterday alerted me to set a PIN for my laptop.
Turned on PC this morning and typed in my regular password then realized it wanted the PIN.
Thinking how this feature came to be....
1. Windows wants you to link your login to your Microsoft/Hotmail Account and it makes it a pain in the ass to set a seperate one (Windows 8)
2. 2018 arrived an logins are a pain, everything is autologin or PIN/code based (aka short 'unsecure' passwords)
3. MS backtracks and realizes email logins are too long so they make a partial fix which basically reverts back to the pre-Win8 days of a seperate system login.. except now its called a new feature!
I realized now under enter a PIN the reason for the checkbox that says: Allow symbols and letters. It's a nice way of saying: please type in your old password again.
**Also rant #2: cuz i dont feel like waiting 1hr**
I felt great yesterday when my boss told me apparantly I have like an Expert designation at the company.
Feel like crap today cuz some user is complaining about some report:
- they asked us to create months ago
- now complaining its all wrong but never gave any formal requirements and actually did sign off on it during testing
- FIXED ASAP
HELLO!!!!!!!!!!! STOP MAKING IT SOUND LIKE IT'S MY FAULT U CAN'T BE BOTHERED TO PROVIDE CLEAR REQUIREMENTS AND THEN TAKING FOREVER TO COME BACK WITH UR PROBLEMS AND NOW NEED IT FIXED ASAP BY USING A NEW DATA SOURCE THAT I HAVE NO IDEA WHAT THE FUCK IS SINCE U USED A RANDOM ABBREVIATION LIKE I CAN MIND READ.
IF I COULD MINDREAD, ID BE WORKING ON A PLAN TO GET UR ASS FIRED.....
Happy friday and long weekend... Got 3 days to relax before i need to deal with this shit again...2 -
My phone suddenly is stuck in a reboot loop.
all solutions did not work (Safemode, Recoverymode etc)
It was time for a new phone.
well... most of my logins have now 2 factor authentication. That got me thinking:
imagine that you lost all your trusted devices in a house fire.
you cannot get in your email because of you need to verify.
you cannot buy stuff online because your phone gets a message.
and in certain cases you cannot even get in your password manager of the same reason.
I know that there are recovery codes and other solutions to this.. oh boy you are F*cked when you don't have your phone.
Everything turned out okay, Sim Card in different phone for messages. And new phone works like a charm :)12 -
Why are clients so brain dead?
I've had a client insist for the last two weeks that I provide them with a high level technical specification for fucking OneDrive because our product is able to embed HTML inputted into the CMS.
I've literally had hours of meetings with over a dozen people where I'm trying to explain that just because they're embedding some PowerPoint HTML into our CMS doesn't mean we need to or even can provide technical documents.
This is a huge company with an equity of over £50 billion by the way. I swear the bigger the company the more incompetent the employees get.
Their whole issue stems from one guy not understanding how basic logins and file sharing permissions work + their IT doing security fuckery to screw up which machines can login or access what. So I made and sent them a flow diagram explaining it, out of some naive hope that they'll now leave me alone.
I still don't understand how any of this is my responsibility just because these idiots don't understand that our product is separate from the HTML they've decided to put into the CMS. I don't think any of these people know what they're asking me for when they keep insisting I send them technical documents for a Microsoft owned product that we have nothing to do with.
I'm sure I'll be stuck telling them to talk to their own IT team over and over again as they schedule meetings every few days until the heat death of the universe. Then I'll finally have peace. Either that or somehow one of them finds this post and I get fired.8 -
This is another high school story. mostly because i’m in high school.
like most schools we have horrible forced passwords. Our school recently purchased microsoft 365. which means we all use outlook for our emails. the logins for our district follow the sand format.
s + first five of last name (x’s for missing letters) + first letter of your first name + the last three of your student id.
so for example Sean Peterson 456705 would be speters705. since we have outlook we can look up a persons name and get their email which gives you the last three of their password. All passwords start with a 4 and most are followed by a five so you pretty much can get 5 out of the 6 numbers in their password.
so to mess with my friends i signed into all of their accounts and messed with their emails so they thought they were getting random emails. and then i made word documents on all of their accounts and just pretty much messed with all of their school stuff.
so that’s my “hacking” story. my district doesn’t allow you to change your password so i’m pretty much stuck. pls help.4 -
Multi User, One Account, and other shit
I'm gonna rant about something as a user, and someone who makes stupid web stuff.
My bank has been updating their web banking over time and they decided that every individual on an account, should have their own login. They really want to push this on their users, I suspect specifically folks like me and my wife who share one login for the joint accounts we have at the bank together.
Why share one login, because it's the only sure fire way I know that I and my wife can see all the same shit no doubt about it.
The banks never tell you what you can see or can't with joint accounts, I doubt it is even documented on their end, but in every damn case something is hidden or different in some weird way.
Messages to the bank people? If I send it, my wife often can't. I get that for security reasons that's a thing, but it makes no sense for a joint account.
ANY difference to me breaks online banking ENTIRELY. Joint accounts are supposed to be... well one account that is the same.
Other banks we used where we had different logins for the joint account, each login actually had separate bill pay accounts per user. So if I went to bill pay and scheduled something to be paid, my wife had no idea, same if she did.
Right fucking there, banking is just broken entirely!
So no Mr. Bank, fuck you we're both logging in via the same login.
Fast forward to N00bPancakes making a thing.
So my employer has a customer (Direct Customer). Direct Customer wants a thing that makes communication with their customer (Indirect Customer) easier.
The worst thing about making something for your customer's customer is that Direct Customer always imagines that Indirect Customer is gonna be super ninja power users....
But no, that's not the case... in fact almost nobody is a power user, and absolutely nobody WANTS to be a power users.
Worse yet in my case the only reason this tool exists is because Direct Customer and Indirect Customer can't communicate well enough anyway... that should tell you something about the amount of effort Indirect Customer is willing to expend.
So with that tool, this situation constantly comes up:
Direct Customer thinks it would be great if every user from Indirect Company had some sort of custom messaging, views, and etc in of Cool Communication Tool. The reason is because that's what Direct Customer loves about Ultra Complex Primary Tool that they use ....
Then I have to fight the constant fight of:
NOBODY WANTS TO BE A POWER USER, NOBODY EVEN WANTS TO DO MUCH OF ANYTHING ON THE INTERNET THAT ISN'T SCREAMING AT OTHER PEOPLE OR POST MEMES OR WATCH SHITTY VIDEOS. THE MOMENT ANYONE AT INDIRECT COMPANY LOGS IN AND SEES ANY INFO THAT IS DIFFERENT FROM THEIR COWORKER THEY'LL SHIT THEMSELVES, FLOOD EVERYONE WITH 'OH GAWD SOME NON SPECIFIED THING IS WRONG' AND RESPOND TO EMAILS LIKE A JELLYFISH DROPPED OFF IN NEW MEXICO... AND NOTHING WILL GET DONE!!!
God damn it people.
Also side rant while I'm busy fighting the good fight to keep shit simple and etc:
People bitch about how horrible the modern web is and then bitch at web devs like we're rulers of the internet or something.... What really pisses me off about that is other devs who do that.... like bro, do you make policy at your company? You decide not to sell some info or whatever shit your company sells? Like fuck off with your 'man I miss html' because you got scared by some shitty JS error and ran back to your language of choice and just poked your head out of the the basement and got scared... and you shit on another developer about that? Fuck you. -
So, it's not my job, but I needed to add some new gsuite groups for our client. That's completely fine, so they sent me their logins. I logged in and, in five minutes, I was kicked out. Because they got an email saying that someone logged in to his account. I still cannot believe what just happened.
-
If any of you play counterstrike or have friends that play counterstrike, watch out for a scam where a friend might ask you to vote for their logo/team on some bs "varsity clash whatever" site.
The thing pops up a fake steam login window and tries to phish you as far as I can tell. It's even styled as a Window window (which is fun when you're on linux like me)
I made a throw away account just to test it and I got some fun logins from Russia, though I revoked the access fast enough so that I retained control.
as far as I can tell the site only exists for a couple of days according to WHOIS and all the steam login assets are hosted on some unrelated non valve server...
This PSA is not really for the more skilled and careful people here, but I thought I'd stick it here for the possibly lurkers and less experienced users just in case.5 -
I know I am probably late to the facebook drama, but I think taking out of this all is just how genius and evil all those collector companies are.
I would have probably never thought of collecting data off of mechanical turks and quick jobbers, but they did not only think of it, they deployed their system across multiple jobs, scanning more and more data in from all those connected logins, for less than a dollar per profile, which generates atleast 300 profiles on average.
The real question is why is it allowed for a third party app to actually access all that? even if there's a permission for that, why would such exist?
I really can't see why any application would need access to likes, shares, all friends, all their profiles etc. -
watched android tutorial on how to use Parse for logins and storing data......went to parse website to download starter project......found out parse is retiring and no longer spport new users :(6
-
So I've been given a task to monitor a whole lot of logs of some servers (whole university ~ 10+ departments). The technologies are diverse so I'm cramming everything into elasticsearch via logstash (and filebeat), viewing it into kibana. Any recommendations for what should be the 'useful' stuff to be viewed into dashboard? I guess:
- Overall traffic wtih respect to previous days/weeks
- Most viewed domains
- 200
- 404
- 503
- Failed logins?
- Dropped connections?
- Critical-load of systems? 90%+2 -
I have a question, let's say I have a website and app both using oAuth facebook login. Should I save the access token provided by facebook in my database and if I should, what will happen to the access token when user logins with facebook on website and then login again with the app? is that mean access token is going to be overwritten by new login? and do you have any other suggestions for 0auth integration?3
-
Android devs, what are your thoughts about the naming conventions google tries to enforce on us, especially with the xmls?
I opened a new project after months of leaving android dev, and thought of trying the basic activity template with name 'myActivity'
On clicking it, a ton of files got created : myActivity, myActivityFragment ,... And in xml the reverse naming notation : activity_my, fragment_my, content_my,...
This naming is uncomfortable .in a large project, activities usually acts as complete modules in which different tasks are handled : logins getting checked, data being cached, database being accessed and much more...
So if my activity 'abc' has a content fragment and a toolbar whose design is in another xml, shouldnt the 3 of them be named like:
abc_activity.xml
abc_activity_fragment.xml
abc_activity_toolbar.xml
And not
activity_abc.xml
fragment_abc.xml
toolbar_abc.xml
??
At the very least , it would look nice since the components that are displayed together will have their files together. And i don't know much about testing, but i believe it would be helpful there too5 -
I've had a lot of jobs, and they've all employed some form of single sign-on. But all of them have required enough individual logins for various services that I had to maintain a full category for that employer in my keepass. Until now.
This company has, by far, the most comprehensive SSO I have ever seen. Perhaps it should not be surprising that it works so well, as it is 100% made in-house. But for a company of this size, that's an amazing achievement. It speaks to excellent planning, it seems to me.
Anybody else ever worked for a large company that had a truly unified SSO?2 -
Yubikey: Worth it?
I'm a college student with way too many logins and offend reusing passwords. I also do password semantics research at the institution and know how useless they are.4 -
How is it possible my netflix password got hacked when I never used it anywhere else and it's randomly generated? I saw some weird logins with random subtitles. Google password manager told me it's in some data breach, how do I find out from where? Haveibeenpwned didn't find anything. 😐6
-
I think we may be getting too attached to our phones. First it was linking logins now important things that prolly shouldn't be left lying around in the open...
 3
3 -
My current project, it's been a 4 month slog working with a client service team who said they read the spec but didn't, said they reviewed the wireframes but didn't , let us work for 2 months off course ( ignoring our nightly builds links and logins all the while but acting as though all was GREAT) before sending us a series of what I can only describe as 'WTF is this?' emails, this wasn't what we expected.... *Queue wind blowing and tumbleweed moments*.. A serious left turn and some back and forth trying of gently ( but eventually 'less' gently) educating them on what processes are, and why we have them... We're now at Beta day T-7 days somehow nearing stable and ... Today.... Today I get an email with another 4 weeks worth of change requests .... Using rage trigger classics like " maybe we forgot to mention... " And " didn't we discuss X?...." The hardest part is trying g to keep my team's morale up, nothing worse than having you deadline victory shot dead with " it's not quite Carling though is it?"
Add on too they failed to send us any content until a month ago ( 3 months late).... Yeah, this one has had me closer than ever to the edge of the cliff...2 -
Why Apple has to do every configuration so f**ckin difficult? After a thousand logins, validations, and 2FA just to change my f**ckin region I find that I need to contact local support by chat or call even if my account is clean (no payment method added, no purchases made, etc.). Yeah right, great products, but crappy website UX.1
-
So, I made this API which logins to the system and Used it in an android app, there was one roadblock to it, that everytime user enters a password, it has to match the password hash so I, excitingly, used password_verify($password,$passwordHash), unknowingly that it is fucking unsafe and the code is still there, and here's where it gets interesting it is not over SSL/TLS. Fuck me, any bright solutions?27
-
Hey guys.
So, where do you guys store your passwords?
It's getting hard to keep track of so many logins and passwords now that I have the time to learn, try new stuff, meddle with VPS and shit and I can't keep track of everything.
Ps: must save somewhere online (or at least backups) and be multi platform (windows + Linux + Android9 -
Just turned on a client's computer and am shocked that they keep their logins straight. Basically there are two logins, but one says "$USER1's Girl" and the other says "$USER2's Man."
If I were them, I would be clicking on the one with my name, not looking for my SO's name...3 -
Thus happened recently.
I installed vestas on our organisation's lab server. I was trying to add the user's key to gitlab.
But vestas doesn't support ssh keys by default, and i thought to go by https way
I don't remember my password, so instead of opening saved logins I was going to install gitlab on our organisation's sub domain.
Later I created custom keys inside the user's directory -_- -
At work, how does your team store and share passwords to DBs, machines, other logins used by everyone (not linked to a specific person) or is needed by an app?6
-
Dashlane sucks. It’s the absolute worst password manager ever. Not a day goes by when it tries to log me into a site incorrectly, forgets a password, freezes up, etc. Yesterday I attempted to very carefully change the master password and it locked me out with the new password. Had to reset using the revoke process and it sent me back 6 months in time. Now I have to reconstruct all my logins a day before I go on vacation. I’m stuck with it because my employer reviewed LastPass and decided Dashlane had a few features LastPass didn’t that they really need. Seriously, SCREW DASHLANE!!2
-
I always have multiple accounts thanks to Single-Sign-On, so I don't find my event tickets, logins, and contacts. To make it worse, those sites regularly log me out for no reason and some force logging in using my Google account although I have a main account with my business email address.
I suspect that's another deceptive pattern that they let happen on purpose so they can claim to have more users than they really have.1 -
browser automated test requiring multiple logins of different accounts
try to logout the legitimate way (automate hitting the button)
or wipe cookies?6 -
ASP.NET Core (MVC) is frustrating me.
I’m a big fan of ASP so far but I’m just struggling to understand a lot.
First off to use it you have to fucking memorize every class in the fucking framework and the functions within them. It just expects that I automatically know which classes I need to implement or inherit from and why, but if I don’t? I can fuck off. But this is also just a C# problem in general.
And it does so much for you and that bothers me so much. I was so excited to actually implement protection against SQL Injections, using HTTPS, validating logins, interacting with the SQL for the database but FUCKING NOPE BECAUSE IT DOES IT FOR YOU.
I don’t want my hand held I want to feel like I’m actually doing things and I want to learn how shit works and how it’s made. It’s just disappointing. I appreciate that it wants me to focus on the app and I will appreciate it a lot more when I’m done learning how everything works but I won’t actually get to understand how those features work or how I can implement them myself because it’s spoiling me too fucking much.
I guess I’m just gonna have to practice more. And don’t bother telling me to look at the documentation, I’ve never seen such a fucking piece of shit mess before I laid eyes upon the docs for C# & ASP21 -
What's your thought on multi-login systems?(your own or Facebook\Google\etc.)
It's worth dealing with it?
The user base of external logins is bigger than your own?
If you've programmed external login support, how've you found the experience?3 -
How would I create user-profiles and user logins for my ReactJS app and Heroku? I've never done it before and not sure if ExpressJS is enough or even how to approach it.5
-
Has anyone had the idea to just use the smartphones fingerprint as a second factor for logins on web services? Just fingerprint scan in a given timespan, no codes or so...1
-
Any suggestion on prevent simultaneous logins of the same user with firebase in android ?
I'm new to this tho4 -
Hey ranters, I want to setup a centralised auth backend that assigns multiple logins/API keys to a single user account which is managed through a Frontend application.
Background is we use multiple services each with their own login system and not all support a unified login/auth method for their API.
My approach is to setup a simple API/Auth backend that stores the users credentials plus multiple API-Keys of other services or their logins. When auth is successful the Frontend app may receive the associated credentials for the other backends to call their respective API. So the user can login once but the Frontend may access all backend services without the user noticing that their are other auths.
This should be a really general problem today. I'm really just diving into the topic of auth and Frontend, so I hope to get some guidence/overview from you. My questions are:
- Is my approach totally stupid?
- Are there good frameworks you'd recommend for such a setup?
- Is there a best practice which I've overseen so far?
- Resources you think are a must-read?
- Any other recommendations regarding security here?
So, what do you ranters think? -
Are there any sysadmins here who know how to deal with ddos attacks properly? I can even offer pay. Situation is that I launched my java app (gameserver) on linux debian and configured iptables to allow only specific ips. Basically I made only 1 port open for loginserver and if player logins into loginserver it adds his ip to iptables so hes able to proceed to gamesever. However I am still receiving massive up to 900MB/s attacks for example: http://prntscr.com/q3dwe8
It appears that even if I left only one port open, I still can't defend against ddos attacks. I made some captures with tcpdump and analyzed them on wireshark but to be honest I cant really tell what I'm looking at.
I am using OVH which is supposed to be ddos protected but maybe I messed up during iptables configuration, I'm not sure.
Can anyone help?15 -
WHICH CRYPTO RECOVERY COMPANY IS LEGIT: HIRE FUNDS RECLIAMER COMPANY
As an architect, every design I create is a mark of trust, trust in materials, trust in my team, and trust in the earth beneath our feet. But nothing could have readied me for the collapse I experienced when that trust was broken from within. I had laboriously built up a $400,000 Bitcoin hoard over several years, a monetary safety net for my business to weather financial tempests and fund future projects. I entrusted its defense to a long-time business partner, a man who I once considered my right arm. That trust fell apart when he betrayed me. It started subtly. I noticed minor discrepancies, delayed logins, emails not returned. Then one morning, I was locked out altogether. He was gone. The phones weren't answered, his office cleared overnight, and my heart pounded in alarm. The electronic safe haven of our hard-won savings was now a fortress without a key, hostage to a ghost. Rage and panic warred within me. I envisioned telling my employees that our future was doubtful because I had trusted the wrong person. Sleepless nights were spent searching the web for miracles. That was when, at an architectural design expo in Milan, I overheard two colleagues discussing FUNDS RECLIAMER COMPANY. Their stories of miraculous crypto recoveries caught my attention like a ray of light piercing a room darkened by shadows. With nothing to lose, I reached out to FUNDS RECLIAMER COMPANY. Their staff handled my case from the very first consultation with the same discretion and precision that I bring to my own cases. They did not handle my case like a transaction but like a delicate form that had to be painstakingly restored. Their cybersecurity experts meticulously tracked my partner's digital footprints, unraveling his complex attempt to hide his trail. Through cutting-edge blockchain tracing and legal action, they slowly dismantled his blockade. I was updated daily, step by step, like progress reports on a skyscraper rising from the earth. Fifteen tense days later, the call came. They had succeeded. The money was back in our firm's possession, intact and secure. Relief washed over me like the unveiling of a completed work of art. FUNDS RECLIAMER COMPANY not only got back money; they got back my hope. They made me realize that even when trust is lost, there are still able hands ready to rebuild. For that, I will forever be grateful.
WhatsApp:+13612504110 1
1 -
i do the website for this association and had the urge to overhaul everything, implement decent architecture and security, getting rid of awful php/html mixture. considered everything pretty fly and after going live did some minor adjustments primarily in the admin section. like instead of selecting the last 100 logs, all from the last year.
turned out there were 16 logins to the site within the last year. two board member logins (one person). impressive considering all of the functionality for administering the association it was capable of even before the rework.
so we do need a website, everyone wants to be updated, board administration is annoying but fuck my software?
more visitors than all of my other projects though. -
So our teacher is telling us to join some kind of competition thing that the government creates, and uhh, when I went to the website, sign up with a separate account that I will probably never use once again in my whole life, and then I notice that when you click to the TOS link in the "I agree with the TOS", it does... nothing, yes, it doesn't lead you to an actual TOS page or anything, it just teleports you up, what?????, did you just create a fking TOS link and it doesn't actually lead to anywhere else? Then why do it anyway? Also, you can literally find a TOS template with some English keyword and then plastered it on some obscure page and then use the TOS link to lead to that one instead of blatantly do nothing. Also, I noticed that they use a authentication service called Eids Authentication. Who the fk is this guy? Why don't you just use something already popular like Auth0? They have way better UI/UX than whatever that is and supports way more platform logins like Google and Faxbook which are more familiar to us.

