Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "transmission"
-
Finally did it. Quit my job.
The full story:
Just came back from vacation to find out that pretty much all the work I put at place has been either destroyed by "temporary fixes" or wiped clean in favour of buggy older versions. The reason, and this is a direct quote "Ari left the code riddled with bugs prior to leaving".
Oh no. Oh no I did not you fucker.
Some background:
My boss wrote a piece of major software with another coder (over the course of month and a balf). This software was very fragile as its intention was to demo specific features we want to adopt for a version 2 of it.
I was then handed over this software (which was vanilajs with angular) and was told to "clean it up" introduce a typing system, introduce a build system, add webpack for better module and dependency management, learn cordova (because its essential and I had no idea of how it works). As well as fix the billion of issues with data storage in the software. Add a webgui and setup multiple databses for data exports from the app. Ensure that transmission of the data is clean and valid.
What else. This software had ZERO documentation. And I had to sit my boss for a solid 3hrs plus some occasional questions as I was developing to get a clear idea of whats going on.
Took a bit over 3 weeks. But I had the damn thing ported over. Cleaned up. And partially documented.
During this period, I was suppose to work with another 2 other coders "my team". But they were always pulled into other things by my Boss.
During this period, I kept asking for code reviews (as I was handling a very large code base on my own).
During this period, I was asking for help from my boss to make sure that the visual aspect of the software meets the requirements (there are LOTS of windows, screens, panels etc, which I just could not possibly get to checking on my own).
At the end of this period. I went on vacation (booked by my brothers for my bday <3 ).
I come back. My work is null. The Boss only looked at it on the friday night leading up to my return. And decided to go back to v1 and fix whatever he didnt like there.
So this guy calls me. Calls me on a friggin SUNDAY. I like just got off the plane. Was heading to dinner with my family.
He and another coder have basically nuked my work. And in an extremely hacky way tied some things together to sort of work. Moreever, the webguis that I setup for the database viewing. They were EDITED ON THE PRODUCTION SERVER without git tracking!!
So monday. I get bombarded with over 20 emails. Claiming that I left things in an usuable state with no documentation. As well as I get yelled at by my boss for introducing "unnecessary complicated shit".
For fuck sakes. I was the one to bring the word documentation into the vocabulary of this company. There are literally ZERO documentated projects here. While all of mine are at least partially documented (due to lack of time).
For fuck sakes, during my time here I have been basically begging to pull the coder who made the admin views for our software and clean up some of the views so that no one will ever have to touch any database directly.
To say this story is the only reason I am done is so not true.
I dedicated over a year to this company. During this time I saw aspects of this behaviour attacking other coders as well as me. But never to this level.
I am so friggin happy that I quit. Never gonna look back.13 -
--- HTTP/3 is coming! And it won't use TCP! ---
A recent announcement reveals that HTTP - the protocol used by browsers to communicate with web servers - will get a major change in version 3!
Before, the HTTP protocols (version 1.0, 1.1 and 2.2) were all layered on top of TCP (Transmission Control Protocol).
TCP provides reliable, ordered, and error-checked delivery of data over an IP network.
It can handle hardware failures, timeouts, etc. and makes sure the data is received in the order it was transmitted in.
Also you can easily detect if any corruption during transmission has occurred.
All these features are necessary for a protocol such as HTTP, but TCP wasn't originally designed for HTTP!
It's a "one-size-fits-all" solution, suitable for *any* application that needs this kind of reliability.
TCP does a lot of round trips between the client and the server to make sure everybody receives their data. Especially if you're using SSL. This results in a high network latency.
So if we had a protocol which is basically designed for HTTP, it could help a lot at fixing all these problems.
This is the idea behind "QUIC", an experimental network protocol, originally created by Google, using UDP.
Now we all know how unreliable UDP is: You don't know if the data you sent was received nor does the receiver know if there is anything missing. Also, data is unordered, so if anything takes longer to send, it will most likely mix up with the other pieces of data. The only good part of UDP is its simplicity.
So why use this crappy thing for such an important protocol as HTTP?
Well, QUIC fixes all these problems UDP has, and provides the reliability of TCP but without introducing lots of round trips and a high latency! (How cool is that?)
The Internet Engineering Task Force (IETF) has been working (or is still working) on a standardized version of QUIC, although it's very different from Google's original proposal.
The IETF also wants to create a version of HTTP that uses QUIC, previously referred to as HTTP-over-QUIC. HTTP-over-QUIC isn't, however, HTTP/2 over QUIC.
It's a new, updated version of HTTP built for QUIC.
Now, the chairman of both the HTTP working group and the QUIC working group for IETF, Mark Nottingham, wanted to rename HTTP-over-QUIC to HTTP/3, and it seems like his proposal got accepted!
So version 3 of HTTP will have QUIC as an essential, integral feature, and we can expect that it no longer uses TCP as its network protocol.
We will see how it turns out in the end, but I'm sure we will have to wait a couple more years for HTTP/3, when it has been thoroughly tested and integrated.
Thank you for reading!26 -
Boss hands over to me an old security audit report and tells me "Go through this and check if all the problems mentioned have been resolved". Quick glance through the report shows all expected issues - SQLi, plaintext transmission and storage etc. I tell him that I need access to the application both from admin and a user with restricted privileges.
He hands me the admin credentials and tells me, "After you login in, just go the "Users" tab. You'll find the profiles of all the users there. You can get the emails and passwords of any user you want from there."
I had to hold back a chuckle. There's nothing to verify. If they haven't resolved storing plain text passwords in the database (AND displaying it IN PLAIN TEXT in the website itself (which to my surprise wasn't mentioned in the audit)), they probably haven't even looked at the report.2 -
Long long ago there was a man who discovered if he scratched certain patterns onto a rock he could use them to remind him about things he would otherwise forgot.
Over time the scratching were refined and this great secret of eternal memory were taught to his children, and they taught it to their children.
Soon mankind had discovered a way to preserve through the ages his thoughts and memories and further discovered that if he wrote down these symbols he could transfer information over distances by simply recording these symbols in a portable medium.
Writing exploded it allowed a genius in one place to communicate the information he had recorded across time and space.
Thousands of years passed, writing continued to be refined and more and more vital. Eventually a humble man by the name of Johannes Gutenberg seeking to make the divine word of God accessible to the people created the printing press allowing the written word to be copied and circulated with great ease expanding vastly the works available to mankind and the number of people who could understand this arcane art of writing.
But mankind never satiated in his desire to know all there is to know demanded more information, demanded it faster, demanded it better. So the greatest minds of 200 years, Marconi, Maxwell, Bohr, Von Nueman, Turing and a host of others working with each other, standing on the shoulders of their brobdinangian predecessors, brought forth a way to send these signals, transfer this writing upon beams of light, by manipulating the very fabric of the cosmos, mankind had reach the ultimate limits of transmission of information. Man has conquered time, and space itself in preserving and transmitting information, we are as the gods!
My point is this, that your insistence upon having a meeting to ask a question, with 10 people that could've been answered with a 2 sentence email, is not only an affront to me for wasting my time, but also serves as an affront to the greatest minds of the 19th and 20th centuries, it is an insult to your ancestors who first sacrificed and labored to master the art of writing, it is in fact offensive to all of humanity up to this point.
In short by requiring a meeting to be held, not only are you ensuring the information is delayed because we all now need to find a time that all of us are available, not only are you now eliminating the ability to have a first hand permanent record of what need to be communicated, you are actively working against progress, you are dragging humanity collectively backwards. You join the esteemed ranks of organizations such as the oppressive Catholic church that sought to silence Galialio and Copernicus, you are among the august crowd that burned witches at Salem, the Soviet secret police that silenced "bourgeoisie" science, you join the side of thousands of years of daft ignorance.
If it were not for you people we would have flying cars, we would have nanobots capable of building things on a whim, we would all be programming in lisp. But because of you and people like you we are trapped in this world, where the greatest minds are trapped in meetings that never end, where mistruth and ignorance run rampant, a world where JavaScript is the de facto language of choice every where because it runs everywhere, and ruins everywhere.
So please remember, next time you want to have a meeting ask yourself first. "Could this be an email?" "Do I enjoy burning witches?" if you do this you might make the world a little bit of a less terrible place to be.4 -
I've seen new sets of tired go for a like $400.
Fuck that shit man. And that's if you're lucky. What if it's some transmission shit? Then you're mad hurt. 15
15 -
Programming Languages are Like Cars:
Assembler: A formula I race car. Very fast but difficult to drive and maintain.
FORTRAN II: A Model T Ford. Once it was the king of the road.
FORTRAN IV: A Model A Ford.
FORTRAN 77: a six-cylinder Ford Fairlane with standard transmission and no seat belts.
COBOL: A delivery van. It's bulky and ugly but it does the work.
BASIC: A second-hand Rambler with a rebuilt engine and patched upholstery. Your dad bought it for you to learn to drive. You'll ditch it as soon as you can afford a new one.
PL/I: A Cadillac convertible with automatic transmission, a two-tone paint job, white-wall tires, chrome exhaust pipes, and fuzzy dice hanging in the windshield.
C++: A black Firebird, the all macho car. Comes with optional seatbelt (lint) and optional fuzz buster (escape to assembler).
ALGOL 60: An Austin Mini. Boy that's a small car.
ALGOL 68: An Aston Martin. An impressive car but not just anyone can drive it.
Pascal: A Volkswagon Beetle. It's small but sturdy. Was once popular with intellectual types.
liSP: An electric car. It's simple but slow. Seat belts are not available.
PROLOG/LUCID: Prototype concept cars.
FORTH: A go-cart.
LOGO: A kiddie's replica of a Rolls Royce. Comes with a real engine and a working horn.
APL: A double-decker bus. It takes rows and columns of passengers to the same place all at the same time but it drives only in reverse and is instrumented in Greek.
Ada: An army-green Mercedes-Benz staff car. Power steering, power brakes, and automatic transmission are standard. No other colors or options are available. If it's good enough for generals, it's good enough for you.
Java: All-terrain very slow vehicle.10 -
iPhones are ridiculously picky when it comes to finding a mate- um charger. And knowing why doesn't really make it any easier to understand why. If anything it baffles me more.
So, let's start with appliances that are not phones. Think Bluetooth headsets, keyboards, earbuds, whatever. Those are simple devices. They see 5V on the VCC line and 0V on ground, and they will charge at whatever current they are meant to. Usually it will not exceed 200mA, and the USB 2.0 spec allows for up to 500mA from any USB outlet. So that's perfectly reasonable to be done without any fuss whatsoever.
Phones on the other hand are smarter.. some might say too smart for their own good. In this case I will only cover Android phones, because while they are smarter than they perhaps should be, they are still reasonable.
So if you connect an Android phone to the same 5V VCC and 0V ground, while leaving the data lines floating, the phone will charge at 500mA. This is exactly to be within USB 2.0 spec, as mentioned earlier. Without the data lines, the phone has no way to tell whether it *can* pull more, without *actually* trying to pull more (potentially frying a charger that's not rated for it). Now in an Android phone you can tell it to pull more, in a fairly straightforward way. You just short the data lines together, and the phone will recognize this as a simple charger that it can pull 1A from. Note that shorting data lines is not a bad thing, we do it all the time. It is just another term for making a connection between 2 points. Android does this right. Also note that shorted data lines cannot be used to send data. They are inherently pulled to the same voltage level, probably 0V but not sure.
And then the iPhones come in, Thinking Different. The iPhones require you to pull the data lines to some very specific voltage levels. And of course it's terribly documented because iSheep just trying to use their Apple original white nugget charger overseas and shit like that. I do not know which voltage levels they are (please let me know!), but it is certainly not a regular short. Now you connect the iPhone to, say, a laptop or something to charge. An Android phone would just charge while keeping data transmission disabled (because they can be left floating or shorted). This is for security reasons mostly, preventing e.g. a malicious computer from messing with it. An iPhone needs to be unlocked to just charge the damn thing. I'm fairly sure that that's because the data lines need to be pulled up, which could in theory enable a malicious computer to still get some information in or out of it. USB data transmission works at at least 200mV difference between the data lines. It could be more than that. So you need to unlock it.
Apple, how about you just short your goddamn data lines too like everyone else? And while you're at it, get rid of this Lightning connector. I get it, micro USB was too hard for your users. I guess they are blind pigs after all. But USB-C solved all of that and more. The only difference I can think of is that the Lightning connector can be a single board with pads on either side on the connector, while in USB-C that could be at the socket end (socket being less common to be replaced). And at the end of the day, that really doesn't matter with all the other things that will break first.
Think Different. Think Retarded. Such tiny batteries and you can't even fucking charge them properly.6 -
Stop calling people by their old occupation titles. .
Please address them by using their new titles accordingly
and they will like it their job more.
OLD: *Garden Boy*
NEW: *Landscape Executive and Animal Nutritionist*
OLD: *Petrol attendant*
NEW: *Fuel transmission engineer*
OLD: *Receptionist*
NEW: *Front Desk Controller*
OLD: *Typist*
NEW: *Printed Document Handler*
OLD: *Messenger*
NEW: *Business Communication Conveyer*
OLD: *Window Cleaner*
NEW: *Transparent Wall Technician*
OLD: *Temporary Teacher*
NEW: *Associate Teacher*
OLD: *Tea Boy*
NEW: *Refreshment Director*
OLD: *Garbage Collector*
NEW: *Environmental Sanitation Technician*
OLD: *Guard*
NEW: *Security Enforcement Director*
OLD: *Prostitute*
NEW: *Practical Sexual Relations Officer*
OLD: *Thief*
NEW: *Wealth Relocation Officer*
OLD: *Driver*
NEW: *Automobile Propulsion Specialist*
OLD: *Maid*
NEW: *Domestics Managing Director*
OLD: *Cook*
NEW: *Food Chemist*
OLD: *Gossip*
NEW: *Oral Research and Evaluation Director*
Which one got you more?11 -
IT Crowd... Automobile edition.
I was driving 80/mph when my car’s transmission locked up and wouldn’t change gears. It was scary, my kids were in the car. I solemnly had to admit that turning off my car, and starting it again fixed it.8 -
Updated goal in regards to my road to machine learning mastery.
Status: new found motivation
Motivational case: bring humanity closer to having 2B become a real thing.
Reason: big booty droids should be a right to humanity.
End of transmission.
On another note, the sony xperia compact is a real nice device, so is the note 8. I would prob go with the note for power but the size of the xperia is more convenient for my taste.1 -
Got an assignment in school to make an easy project in c for embedded real time processors with a free complexity level (it was really early in the course and many had never been programming before).
Since I've been working a few years in development I decided to create an own transmitter and receiver for an own protocol between processors (we had just spent a week to understand how to use existing protocols, but I made my own).
The protocol used only 1 line to communicate with half-duplex and we're self adjusting the syncing frequency during the transmission. I managed to transmit data up to 1 kbps after tweaking it a bit (the only holdback was the processors clock frequency).
Then I got the feedback from our teacher, which basically said:
"Your protocol looks like any other protocol out there. Have you considered using an UART?"
Like yeah, I see the car you built there looks like any other car out there, have you considered using a Volvo instead?1 -
AT&T: "there is an excessive use cap on your unlimited mobile data plan but you'll never hit it"
Me: BEGIN TRANSMISSION 6
6 -
A couple of days ago, an individual attempted to convince me that the National Security Agency is capable of cracking Rijndael encryption; as a response, I informed the individual of the infeasible nature of the factoring of extremely large semiprimes; however, my attempts were futile, as the individual believes that NSA possesses sufficient power to crack this encryption without intercepting the transmission of the corresponding private key.
The Dunning-Kruger effect is real; although this individual tends to be logically-minded, there does exist an exception to this good behaviour.
"It is easier to square a circle than get 'round a mathematician."1 -
How lawyers fuck up technology!
I rented a car today, given that I don't want to go by train currently. That was some VW Golf, and it had a lane assist which can't decide whether to be helpful or obnoxious:
Either I kept the steering wheel and still steered myself, in which case the lane assist's actions made the steering feel somewhat wobbly. Initially, I suspected a worn out control arm bearing, but that's a long term damage in aging cars, not in new ones.
Or I just rested my hands on my upper legs, as I usually do (palms facing upwards and holding the wheel lightly), then the lane assist worked by itself. It was even smart enough to deactivate itself upon blinking before changing lanes.
However, it complained after about 15 seconds that I didn't steer. I said, shut up and do your job. The warning intensified, and I said, fuck you. Then it initiated some stutter braking to wake me up. Annoying like a reincarnation of Clippy.
I ended up giving the steering wheel a slight tip to the right every 15, 20 seconds just to let the lane assist know I was still there, relying on the lane assist to correct it again. On a long trip, I would have had to deactivate that crap.
Obviously, the VW engineers did their job, but the legal department feared law suits should anything go wrong and ruined the feature!
What was also annoying is that there is no real hand brake anymore in many modern cars. Sucks when pulling off against a hill. Plus that at red traffic lights, I usually put the gear out (manual transmission) and pull the hand brake instead of keeping my foot on the clutch. That's not the same with this pseudo hand brake!
(In case you wonder why anyone would do that:
it's an anachronism that avoids lengthening the clutch wires, decades after cars switched to hydraulics.)11 -
About to start my real first Java project to learn the language in-depth: a virtual ATM featuring a GUI and a networking system for the transmission of banking data to and from a server. Since I particularly care about security this will surely help me get a better understanding of everything involved. Wish me luck.16
-
We can hide messages in images via steganography (or ZIP sewing), we can hide messages in sound via either sound-based transmission (like Morse) or waveform-based transmission (think oscilloscope art videos), we can transmit it in videos in like 300 different fucking combined forms...
Encryption isn't the ONLY way, yo. Social engineering and being a cheeky shithead can get it done too.2 -
its been there since many years, but:
When did we turned the wrong way and made it acceptable that Windows can blantly say in my face that i cannot deactivate the transmission of data unless i have the "Business" Variant of their Software. Its called Windows 10 PROFESSIONAL. Why are there no international Laws against that? Where was the molotov throwing mob when this became the norm?
Additonally. that cute telemetry service consumes a considerable amount of cpu and disk power from time to time.
and no, Linux is not an alternative. It never was. There is proprietary software and driver sets used for lab equipment and machines that cannot run under linux, noone will ever have the time to tool something for it and the user base is too specific to hope for any community solution.
sidenote: even Level 0 STILL transmits data. I want mode -1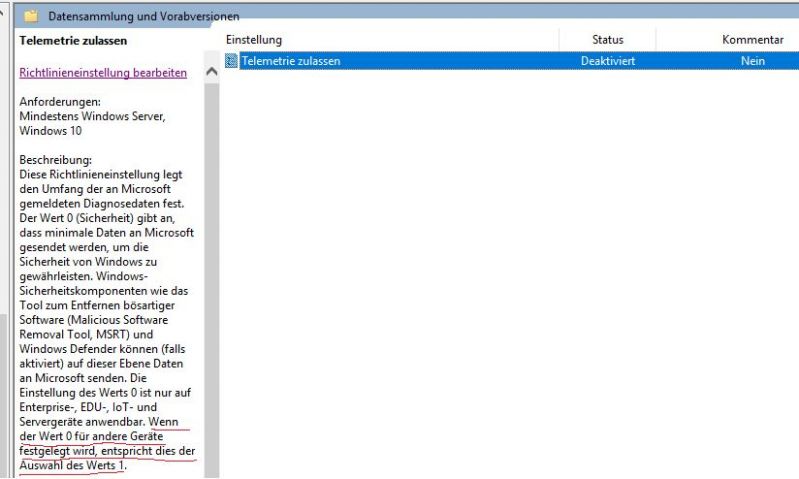 4
4 -
I love software. Seriously, I love it. /s
Transmission is given a bad torrent (which, given that it's a torrent service, you'd expect it handles quite robustly) and completely fucks up. Like, really badly. It doesn't respond to RPC anymore, systemd has to resort to sending it a SIGKILL to get it off the process tree, and the web interface.. yeah. Nothing.
It doesn't log by default, so fine I'll add that to the systemd unit and restart it with debugging options enabled.
# systemctl daemon-reload && systemctl daemon-reexec
Turns out that /var/log/transmission.log can't be written to by my Transmission user. Well shit. Change that to /home/condor/transmission.log.
# systemctl daemon-reload && systemctl daemon-reexec
# systemctl restart transmission-daemon
*blood starts to reach its boiling point*
Still logs in the wrong fucking location. Systemd, I told you to log over there. I did everything I could to make you steaming pile of shit reload that fucking config. What's the fucking problem!?
*about 15 minutes of fighting systemd*
Finally! It spits out a log in the right location! Thank you Transmission and systemd for finally doing your fucking jobs. So a bad torrent it is, hmm...
*removes torrent from .config/transmission/torrents*
Transmission: *still fucking shits itself on that ostensibly removed torrent*
That's it. BEGONE!!!
Oh and don't get me started on the fact that apparently a service needs some 400MB of memory. Channeling your inner Chrome Transmission?5 -
Command: "Infantry unit, this is Command. The enemy is approaching, what's your status?"
Infantry Unit: "Command, this is Infantry unit. Just a quick note, my pronouns are they/them. Can we please use that in all communications going forward?"
Command: "Infantry unit, the enemy is upon you and you're worried about pronouns?"
Infantry Unit: "Command, this is Infantry unit. It's not just about me, it's about respect and inclusivity"
Command: "Infantry unit, you're about to be inclusively dead. Defend yourselves!"
Infantry Unit: "Command, this is Infantry unit. Wait, what? Oh s***."
(End of transmission)12 -
Months on this project and it STILL doesn’t work. Way too many links in the communication chain and everything is getting lost in transmission and in translation because of foreign language barriers.
All of this will be my fault when it fails, even when it’s provably actually not. The joys of being the single wringable neck.2 -
So, apparently that another kickstarted IoT chip dev team forgot to bind reset button to anything, so it is just sitting there as a fidget toy and they also messed up with usb-to-serial connection so it is working only in transmission mode. I am just sitting here with bricked chip with no adequate possibilities to unbrick it.1
-
Finally got paid (apparently they sent my money to the wrong account lmao).
So I bought:
- A Guitar Rig Kontrol 3. It's an old hardware designed for some specific soft, but it contains a soundcard, 8 foot switches, one expression pedals (continuus), 2 other expression pedals input, 2 audio input, 2 audio output. So I'll be able to plug my guitar and control FX from there. All of this for 50 euros at the pawn shop
Being a programmer helped me tremendously for electronic music because I can write actual drivers for old hardware.
- I also found an old bike on the street. Brakes and transmission, seat and tyres are fucked, but the frame and wheels seems healthy enough. I can get a decent bike for the price of parts and labour.5 -
Would you like a Raspberry Pi ? If yes, what kind of project would you like to do with ?undefined kodi xbmc transmission system microcomputer linux raspbian raspberry raspberry pi embedded pi26
-
Oi windows, your highly intelligent "transmission optimization process" is not really helping me by hogging the whole bandwidth while I'm downloading something.
-
Yep we are all remote workers, but we all go in to the office every morning to clock in, and then back at 5:30 to clock out. I see a potential problem with transmission at these 2 points in the day. Plus the office is an hour away for most people and we all use public transport.1
-
I hate that I love electronics. You can be an absolute god in the technical world but on the other hand its like whose fault is it? The hardwares or the softwares???
Been debugging a DRA818v for 3 days now and havent found any answers towards why there is no transmission just noise and stuff.
FFS JUST GIVE ME AN ANSWER!
Also if you just happen to get one thing wrong, you just fried 5$ worth of components. (Which cant really happen to a software dev)1 -
I've been on a new project since last week.
After 3 days of knowledge transmission and really nothing else, the PM walked in and ask me when the project will be finished...
Really?! Jumping in a totally new project, with tools and functionals aspect I've never seen and then this.
:thumbs up: everything gonna be ok -
Sometimes YouTube recommends something fantastic like this. I really did not search for "how to send an 'email'"! Email prescriptions are still syfy for many countries, and that bit on taking fridge inventory on the computer is a bit of an overkill even today! The transmission at the end, freakyyyyyyy!
https://youtube.com/watch/... -
Going through my lore notes. And I'm playing a game with myself, so to speak: it's called "is this metal enough?", but with a side of quasi-metaphysical arcane technobabble plus mass wallmelting and nightmarishly psychedelic confusion.
For example... why are shadow gates a thing? Well, because of the undoing of time caused a multiplicity of parallel cycles that will, inevitably, slowly collapse upon themselves through a sequence of irreducible asynchronicities. But of course!
Now, as for the metal part, that's the undoing of time. You see, the Somberlain attempted to cast the most sinful signa in order to restore the desolate mortal realm as it stood on the brink of a world-ending cataclysm, this was after a decade of brutal, reckless litechnical abuse during the civil war fought amongst the first undecimvirate...
Now, he intended to roll back time itself as a way to avoid the cataclysm and restore life to the mortal realm, but the cost was immense: time was not rolled back, but rather __forcefully__ torn apart; it was effectively shredded, shattered, and undone.
Countless lives were lost as nearly six hundred years of Being were __erased__ in an instant, the most heinous large-scale blood sacrifice in history, spanning the entirety of the lower fragment of reality. I mean is this too dark, I'm not sure. How about I clarify: he didn't just snuff out their lives, no, they CEASED TO EXIST. THEY NEVER EXISTED. GONE. UNBECOMED INTO A TRUE IMMEMORIAL. OVER FIVE CENTURIES OF EVERY CONSCIOUS MOMENT ON EARTH DEVOURED TO FUEL HIS DARK MAGIC.
That's gotta have consequences, right? Well, obviously you'll get temporal distortions after that shit, I mean duh...
But wait, I'm lost, you say the undecimvirate deified themselves but were cast down after the whole superman spinning the earth backwards thing went full bathory and erased entire centuries from the fabric of the cosmos, so they were turned into the eleven thrones to guard over the eleven circles of the night eternal... but how is that linked to natural occurrences of teleportation?
First off, because *natural* teleportation is distinct from *artificial* teleportation. Failed experiments with (and miscasts of) mass transference of living matter are one of the leading causes of death among litarchs. It is not an instant transmission, just very, very quick, moreso than a mortal mind can process, that's why the "dilate" and "delay" sigils are added, so as to make the journey seem slowed down to the perceptions of whomever is teletransported, this is meant to ensure their brains don't __melt__ from the experience.
Similar reason as to why you have to give the _approximate_ total weight to carry when inscribing the ritual circle, you *do* know that it is __highly__ recommended to use accurate weighing scales to approximate this quantity, as under or overestimating it can lead to _FATAL_ consequences... do you not?
No, *natural* occurrences of teleportation do not have these constraints for two reasons: one, because both ends of the gateway are _fixed_ in both time and space due to the logic-defying occurrence of a future event being undeniably the cause of the past it revisited. Put on this toga. They are inextricably linked through the metaphorical and *literal* corpse of infinite collapsed timelines, which generates a conduit through the first circle of the night eternal, which *is* the domain of both forgetfulness and horror immemorial.
Second, the final layer on our stratified reality, that is, the final circle before the INVIOLABLE divine veil, wraps around the night eternal, which is why we call it "the shell". Or "Crisalida" if you dig Luis Alberto. It is a realm entirely outside of time, which is why the patriarchs can grant immortality, you see. By proximity to this sacred shell of existence, the timeline-corpse-conduit that links both ends of a shadow gate is, for all intents and purposes, approaching total chronostasis, therefore making it so bypassing physical space in a few seconds doesn't give you permanent loss of the sense of self as your brain turns into liquified jelly.
I don't remember what I was getting at and I don't care.4 -
Anyone with good understanding of hardware and/or an operating systems network protocols please assist me. I have questions
When using socket api I know it’s not the actual sockets sending the data but the socket api tells the network protocol to send, receive, listen, connect, etc well what I want to know is how that networking protocol works within the operating system
My second question is more an extension of the first. After the operating system knows what the socket api wants to do and wants to do it how does the transmission and receiving work on the physical layer within the hardware
Idk if what I’m asking makes sense. But if anyone also has any resources or a link that’ll help me on the subject I’d appreciate it. I haven’t found anything on the subjects myself18 -
Right now my brain tries to devour both 80s and 90s pop culture, digest them and turn them into succinct and potent… pods? Capsules with info?
The problem is that those two cultures are incompatible in my head, yet both mean a lot to me. I’m a big aesthetics geek.
It feels like when Alec Steele tried to forge tungsten. It doesn’t work. But I lost control over my thoughts, so I’m kinda bad-tripping/daydreaming without drugs as my brain drags my mind through this tunnel where words have no meaning and walls are made of broken glass and spent syringe needles.
Let it end, but also make it never end, as I’ll lose myself should I be robbed of those weird experiences. Sometimes you want your food spicy, your transmission manual, your bike fixed gear, and your sex bdsm. Just don’t strangle or drown me while playing with me, my dear brain. We need each other to survive. -
Hi everyone, I have a question about VPN and hosting.
I have rpi which runs ubuntu where I have several things running like nextcloud, transmission, minidlna, samba etc.
I want to use a VPN due to torrenting via transmission on the pi. I had used private internet access(PIA) before and I'm thinking to go back to them as I had issue only once with them.
Question is if I had installed their client and connected to VPN, would I still be able to access to my services over the internet? As per my understanding only the outgoing and incoming generated from outgoing should follow the VPN tunnel, therefore interacting with my pi with it's public IP should still be possible, am I right?
I'm a newb when it comes to web stuff so any help is appreciated, also you can recommend other VPN providers if you think PIA sucks for any reason.2 -
Derek Auto Repair: Expert Transmission Services in San Diego
At Derek Auto Repair (万通汽车修理), we take pride in offering top-notch transmission repair and transmission replacement services to the residents of Escondido and the surrounding areas, including San Diego. With years of experience in the auto repair industry, our team of skilled technicians is committed to delivering fast, reliable, and affordable solutions for all your transmission needs. If you’re looking for a trusted shop for transmission diagnostics, we’re your go-to choice.
Comprehensive Transmission Services in San Diego
Transmission issues can often go unnoticed until they cause significant problems with your vehicle. That’s why it's important to get your transmission checked regularly. At Derek Auto Repair, we offer comprehensive transmission diagnostics to identify and address potential issues before they become major repairs.
Transmission Diagnostics in San Diego
Our state-of-the-art diagnostic tools help us detect problems quickly and accurately. Whether you're dealing with a slipping transmission, delayed shifting, or strange noises, our technicians will get to the root of the problem. Once the issue is identified, we’ll provide you with a detailed report and discuss your repair options.
Transmission Repair in San Diego
At Derek Auto Repair, we understand the inconvenience that comes with a malfunctioning transmission. That’s why we offer fast and efficient transmission repair services to ensure your vehicle is back on the road as soon as possible. Whether it's a minor repair or a more complex fix, our expert team will handle it with care and precision. Our team has the knowledge and tools to fix a wide variety of transmission issues, so you can trust us to get your car running smoothly again.
Transmission Replacement in San Diego
In some cases, transmission replacement is the best option for your vehicle, especially if the damage is extensive. If your transmission is beyond repair, we offer reliable transmission replacement services at competitive prices. We work with high-quality replacement parts to ensure your new transmission operates at peak performance. Our goal is to get you back on the road safely and efficiently.
Why Choose Derek Auto Repair?
Expert Technicians: Our team is highly trained and experienced in all aspects of transmission repair, replacement, and diagnostics.
Fast and Reliable Service: We understand how important your vehicle is, and we strive to complete every repair quickly without compromising on quality.
Affordable Pricing: We offer competitive pricing for all our services, ensuring you get the best value for your money.
Convenient Location: We are conveniently located at 2120 W Mission Rd Ste 230, Escondido, CA 92029, easily accessible from San Diego and the surrounding areas.
Get in Touch Today!
If you're experiencing transmission issues, don't wait until it's too late! Visit Derek Auto Repair today for expert transmission diagnostics, repair, and replacement services in San Diego. Call us at +1 (840) 260-9284 to schedule an appointment, or stop by our shop for a free consultation. We look forward to serving you and ensuring your vehicle runs smoothly for years to come!5 -
Infinite Auto Care: Expert Car Maintenance and Professional Auto Care in Ottawa
At Infinite Auto Care - Detailing and Automotive Services, we understand how important it is to keep your vehicle in optimal condition. Whether you're driving around Ottawa or heading out on a long road trip, regular car maintenance in Ottawa is essential for safety, performance, and the longevity of your vehicle. Our team of experts provides professional auto care in Ottawa, offering a comprehensive range of services to ensure your vehicle runs smoothly and stays reliable.
Located at 8 Rue Mitchell, Gatineau, QC J8P 2A5, we proudly serve Ottawa and surrounding areas, providing top-quality auto care that you can trust.
Car Maintenance Ottawa: Keeping Your Vehicle in Top Shape
Regular car maintenance in Ottawa is key to preventing costly repairs down the road. At Infinite Auto Care, we offer a full range of maintenance services designed to keep your car running efficiently and safely. Whether you're due for a routine oil change, brake inspection, or tire rotation, our professional team is here to help.
Why is Regular Car Maintenance Important?
Enhanced Safety: Properly maintained vehicles are less likely to experience breakdowns or accidents due to worn-out parts or poor performance. Regular maintenance helps ensure that your car’s braking, lighting, and engine systems are functioning properly.
Improved Fuel Efficiency: Well-maintained vehicles run more efficiently, which can save you money on fuel. A simple oil change or air filter replacement can help your car perform better and consume less gas.
Longer Vehicle Life: Regular care and maintenance can extend the lifespan of your vehicle, keeping it in service for many years to come.
Avoid Expensive Repairs: Small issues, if caught early, can often be resolved at a fraction of the cost of major repairs. Preventive maintenance is always more cost-effective than reactive repairs.
Our Car Maintenance Services in Ottawa Include:
Oil Changes: We offer high-quality oil change services using premium oils and filters, which are essential for keeping your engine clean and lubricated.
Tire Rotation and Balancing: Ensuring that your tires are properly balanced and rotated helps improve tire lifespan and driving safety.
Brake Inspections: Brakes are vital to your safety. We inspect and service your brake pads, rotors, and fluids to ensure optimal performance.
Fluid Top-ups and Replacements: We check and replenish essential fluids such as brake fluid, transmission fluid, power steering fluid, and coolant to ensure your car runs smoothly.
Battery Checks: A dead battery can leave you stranded. We provide battery testing and replacement to ensure your vehicle is ready to start every time.
Air Filter and Cabin Filter Replacement: Clean filters improve your vehicle's engine performance and provide better air quality inside your car.
Professional Auto Care Ottawa: Comprehensive Services for Your Vehicle
At Infinite Auto Care, our mission is to offer professional auto care in Ottawa that covers every aspect of your vehicle's needs. Our experienced technicians use the latest diagnostic tools and the highest-quality products to ensure your vehicle receives the best care possible.
Our Professional Auto Care Services Include:
Engine Diagnostics: If your check engine light comes on, our team performs a thorough diagnostic to determine the root cause of the issue. We then provide clear recommendations to fix the problem and prevent future issues.
Exhaust System Services: Your exhaust system is crucial for reducing harmful emissions and maintaining engine performance. We offer inspection, maintenance, and repair services to keep your system functioning optimally.
Transmission Services: Whether it’s a fluid flush or a complete transmission repair, our technicians have the expertise to keep your transmission shifting smoothly.
Suspension Services: Your suspension system ensures a comfortable and safe ride. We offer suspension inspections and repairs to keep your car's handling and ride quality at their best.
Custom Services: For those who want to enhance their vehicle’s appearance or performance, we offer customization services, from body kits to performance upgrades.
Why Choose Infinite Auto Care for Car Maintenance and Auto Care in Ottawa?
When it comes to car maintenance in Ottawa and professional auto care in Ottawa, Infinite Auto Care stands out as a trusted partner in keeping your vehicle running at its best. Here’s why you should choose us for your automotive needs:
or model.
To schedule an appointment or learn more about our services, contact us today at +1 (819) 386-8114 or visit us at 8 Rue Mitchell, Gatineau, QC J8P 2A5. Let Infinite Auto Care keep your car in great shape with the best auto services in Ottawa! 1
1 -
A1 Autoworkz Auto Body Shop: Your Premier Auto Repair and Collision Center Serving Bronxville, NY, and Beyond
When it comes to high-quality car painting services and expert automotive collision repair, A1 Autoworkz Auto Body Shop is your go-to destination for all things auto repair in the Bronxville, NY area. Conveniently located at 543 E 3rd St, Mt Vernon, NY 10553, we provide a wide range of services, from car collision repair in New Rochelle to auto repair near Bronxville, NY, ensuring your vehicle is restored to its best condition after any damage.
Whether you’re dealing with a minor scratch, a major collision, or a complete vehicle overhaul, our dedicated team of professionals is here to offer reliable, affordable, and comprehensive vehicle repair services.
Bronxville Car Painting Services: Restoring Your Vehicle's Appearance
One of the most noticeable aspects of your car’s condition is its paint job. Whether your vehicle has been scratched, scuffed, or damaged in an accident, A1 Autoworkz Auto Body Shop offers expert Bronxville car painting services to restore your vehicle’s appearance to its former glory.
Our car painting services include:
Custom Paint Jobs: If you’re looking to personalize your vehicle with a custom color or design, we offer specialized custom car painting to suit your preferences.
Paint Matching: After a collision or accident, we provide expert paint matching to seamlessly blend the new paint with the existing finish.
Scratch and Chip Repair: Minor damages like scratches and chips can be fixed quickly, ensuring a smooth and flawless finish.
Full Paint Restoration: For vehicles that need a complete refresh, we offer auto paint restoration to give your car a brand-new appearance.
With our car painting services in Bronxville, your vehicle will look like new again, whether you need a touch-up or a full re-spray.
Auto Repair Near Bronxville, NY: Comprehensive Services at Your Doorstep
If you’re searching for reliable auto repair near Bronxville, NY, A1 Autoworkz Auto Body Shop is the place to go. We offer a full range of auto repair services to ensure your vehicle is running smoothly and efficiently.
Our auto repair services include:
Routine Maintenance: From oil changes to tire rotations, we handle all your routine vehicle maintenance needs to keep your car in peak condition.
Brake Repair: Our technicians specialize in brake inspections, replacements, and repairs to ensure your safety on the road.
Transmission and Engine Repair: If you’re experiencing issues with your engine or transmission, we can diagnose and repair the problem efficiently.
Suspension and Steering Repairs: We provide repairs for suspension and steering systems to ensure your car handles properly.
Whether you’re dealing with a mechanical issue or just need preventive maintenance, A1 Autoworkz Auto Body Shop is your trusted auto repair center near Bronxville, NY.
Automotive Collision Repair Bronxville: Get Your Car Back on Track
At A1 Autoworkz Auto Body Shop, we understand that a collision can be a stressful and overwhelming experience. That’s why we offer expert automotive collision repair services in Bronxville, NY to restore your car to its original condition. Whether your car has a minor dent or more extensive damage, we have the tools, technology, and expertise to get it back on the road safely.
Our automotive collision repair services include:
Bumper and Fender Repair: After a collision, your bumper or fender may need repair or replacement. We provide professional bumper and fender services to ensure your car looks and functions like new.
Frame Alignment: If your vehicle’s frame has been bent or misaligned in a collision, we use state-of-the-art equipment to straighten and restore it to its original position.
Paint and Finish: After collision repairs, we provide expert auto painting services to blend and match the paint seamlessly, leaving no evidence of the repair.
Glass and Window Repair: We can replace broken windows or repair chips in your windshield to keep your car looking great and secure.
When it comes to automotive collision repair in Bronxville, A1 Autoworkz Auto Body Shop offers fast, reliable, and high-quality repair services to get you back on the road with confidence.
Bronxville Vehicle Repair Services: Quality and Affordable Repairs
At A1 Autoworkz Auto Body Shop, we pride ourselves on providing the best vehicle repair services for drivers in Bronxville, NY. Whether you need routine maintenance or more complex repairs, our experienced technicians are here to help.
Our vehicle repair services include:
Engine Diagnostics and Repair: If your engine isn’t running smoothly, we offer diagnostic services to pinpoint the issue and make the necessary repairs. 9
9 -
The Use of Recycled Heart Devices
There are many controversial issues in the healthcare, and some of them seem so debatable that it is difficult to chose which side to support. One of such issues is the use of recycled heard devices – implantable cardioverter-defibrillators (ICDs) that were previously used by people who could afford them and changed them to a new model or died. These devices are still in good condition and have some battery life remaining. Scientists like Pavri, Hasan, Ghanbari, Feldman, Rivas, and others suggest that these ICDs can be reused by those patients who cannot pay for them.
The issue has caused many arguments. Federal regulators and ICDs manufacturers in the United States prohibit the practice of such a reuse; however, it is allowed in India, where very few people can afford defibrillators. The use of recycled ICDs can be regarded as inferior treatment to the poor. People who cannot pay for the expensive devices still deserve the healthcare of the highest quality as any wealthy person. For this reason, other means of providing healthcare to poor people should be found as it is unethical to make them feel humiliated or deprived of medical aid guaranteed to them by the Declaration of Human Rights. Harvard medical experts claim: flagship projects must remain free of the taint of the secondhand, in part by making it clear when devices can safely be reused.
These scientists also doubt the safety of ICDs reuse. Despite the fact that all devices are carefully transported and sterilized, there is still a danger of infection transmission. The experts, for instance, claimed that three people died because of stroke, heart failure, and myocardial infarction. Though it is not proved to be caused by recycled ICDs, there is no evidence about the relevance of the reused devices to these deaths. It can be presumed that the failure of the defibrillator did not prevent the problem. In general, their findings prove that the alternative reuse of ICDs is a comparatively riskless life-saving practice.
There is another side of the problem as well. It is obvious that human life is sacred; it is given to one person only once, so it should be protected and preserved by all means (humanlike, of course) possible. If there cannot be another way out found, secondhand ICDs should be applied to patients who cannot pay for their treatment. If the world is not able to supply underprivileged patients with free devices, richer countries can, at least, share what they do not need anymore. One may draw a parallel between recycled defibrillators and secondhand clothes. There is nothing shameful about wearing things that were used by another person. Many organizations supply children in poor countries with garments in a good condition that richer people do not wear anymore. For the same reason, reused defibrillators in a proper state can be implanted to those patients who cannot afford new devices and will not be able to survive without them. Underprivileged patients in some developing countries receive alternative treatment of drug therapy, which, in this case, can be regarded as inferior method. Apparently, if to consider the situation from this viewpoint, recycled heart devices should be used as they allow saving people’s lives.
The use of recycled implantable cardioverter-defibrillators is illegal and risky as they are classified as single-use devices. Moreover, despite the fact that the results of researches on the topic proved to be positive, there were cases when some people with recycled ICDs died because of stroke, heart failure, or myocardial infarction. It is unethical to break the law, but at the same time, person’s life is more important. If there is no other possibility to save a person, this method must be applied.
The article was prepared by the qualified qriter Betty Bilton from https://papers-land.com/3 -
The Turing Test, a concept introduced by Alan Turing in 1950, has been a foundation concept for evaluating a machine's ability to exhibit human-like intelligence. But as we edge closer to the singularity—the point where artificial intelligence surpasses human intelligence—a new, perhaps unsettling question comes to the fore: Are we humans ready for the Turing Test's inverse? Unlike Turing's original proposition where machines strive to become indistinguishable from humans, the Inverse Turing Test ponders whether the complex, multi-dimensional realities generated by AI can be rendered palatable or even comprehensible to human cognition. This discourse goes beyond mere philosophical debate; it directly impacts the future trajectory of human-machine symbiosis.
Artificial intelligence has been advancing at an exponential pace, far outstripping Moore's Law. From Generative Adversarial Networks (GANs) that create life-like images to quantum computing that solve problems unfathomable to classical computers, the AI universe is a sprawling expanse of complexity. What's more compelling is that these machine-constructed worlds aren't confined to academic circles. They permeate every facet of our lives—be it medicine, finance, or even social dynamics. And so, an existential conundrum arises: Will there come a point where these AI-created outputs become so labyrinthine that they are beyond the cognitive reach of the average human?
The Human-AI Cognitive Disconnection
As we look closer into the interplay between humans and AI-created realities, the phenomenon of cognitive disconnection becomes increasingly salient, perhaps even a bit uncomfortable. This disconnection is not confined to esoteric, high-level computational processes; it's pervasive in our everyday life. Take, for instance, the experience of driving a car. Most people can operate a vehicle without understanding the intricacies of its internal combustion engine, transmission mechanics, or even its embedded software. Similarly, when boarding an airplane, passengers trust that they'll arrive at their destination safely, yet most have little to no understanding of aerodynamics, jet propulsion, or air traffic control systems. In both scenarios, individuals navigate a reality facilitated by complex systems they don't fully understand. Simply put, we just enjoy the ride.
However, this is emblematic of a larger issue—the uncritical trust we place in machines and algorithms, often without understanding the implications or mechanics. Imagine if, in the future, these systems become exponentially more complex, driven by AI algorithms that even experts struggle to comprehend. Where does that leave the average individual? In such a future, not only are we passengers in cars or planes, but we also become passengers in a reality steered by artificial intelligence—a reality we may neither fully grasp nor control. This raises serious questions about agency, autonomy, and oversight, especially as AI technologies continue to weave themselves into the fabric of our existence.
The Illusion of Reality
To adequately explore the intricate issue of human-AI cognitive disconnection, let's journey through the corridors of metaphysics and epistemology, where the concept of reality itself is under scrutiny. Humans have always been limited by their biological faculties—our senses can only perceive a sliver of the electromagnetic spectrum, our ears can hear only a fraction of the vibrations in the air, and our cognitive powers are constrained by the limitations of our neural architecture. In this context, what we term "reality" is in essence a constructed narrative, meticulously assembled by our senses and brain as a way to make sense of the world around us. Philosophers have argued that our perception of reality is akin to a "user interface," evolved to guide us through the complexities of the world, rather than to reveal its ultimate nature. But now, we find ourselves in a new (contrived) techno-reality.
Artificial intelligence brings forth the potential for a new layer of reality, one that is stitched together not by biological neurons but by algorithms and silicon chips. As AI starts to create complex simulations, predictive models, or even whole virtual worlds, one has to ask: Are these AI-constructed realities an extension of the "grand illusion" that we're already living in? Or do they represent a departure, an entirely new plane of existence that demands its own set of sensory and cognitive tools for comprehension? The metaphorical veil between humans and the universe has historically been made of biological fabric, so to speak.6 -
APM BILLING: Providing HIPAA-Compliant Billing Services You Can Trust
In today’s healthcare landscape, maintaining patient privacy and data security is paramount. Healthcare providers must adhere to strict standards to protect sensitive information while ensuring that financial operations are smooth and efficient. APM BILLING, based in Philadelphia, Pennsylvania, is dedicated to providing HIPAA-compliant billing services that ensure the highest level of security and compliance, while also optimizing the billing process for healthcare providers.
What Are HIPAA-Compliant Billing Services?
HIPAA (Health Insurance Portability and Accountability Act) establishes strict rules to ensure that healthcare providers maintain patient privacy and the confidentiality of their health information. As part of our commitment to protecting patient data, APM BILLING offers HIPAA-compliant billing services that meet all of the requirements set forth by this regulation.
Our HIPAA-compliant billing services ensure that all personal health information (PHI) handled during the billing and claims process remains secure. From data encryption to secure transmission, we follow the highest security standards to prevent unauthorized access, breaches, and other vulnerabilities.
Why Is HIPAA Compliance Critical for Healthcare Billing?
For any healthcare business, staying HIPAA-compliant is not just a regulatory necessity—it's essential to maintaining trust with patients and avoiding costly penalties. Non-compliance can result in hefty fines, lawsuits, and damage to your reputation. When it comes to billing, ensuring that all processes follow HIPAA guidelines is critical in preventing unauthorized access to sensitive patient data.
APM BILLING takes privacy and security seriously. Our team is well-versed in all HIPAA regulations, so you can trust that your patient data is always protected. We integrate comprehensive security protocols into our billing workflows, including:
Encrypted communications for all patient data exchanges
Secure data storage that meets HIPAA standards
Audit trails to track access to patient information and billing details
Employee training to ensure that everyone handling sensitive data understands HIPAA guidelines
The Benefits of Working with APM BILLING for HIPAA-Compliant Billing Services
By choosing APM BILLING, you gain the peace of mind that comes with knowing your billing processes are in full compliance with HIPAA regulations. Here are some of the key benefits of our HIPAA-compliant billing services:
Data Security: We use the latest technology to protect patient information, ensuring that all billing data is securely transmitted and stored.
Regulatory Compliance: Our team stays up-to-date with the latest changes to HIPAA regulations, ensuring that your practice remains compliant with all legal requirements.
Reduced Risk of Penalties: HIPAA violations can lead to significant fines and penalties. By outsourcing your billing to APM BILLING, you minimize the risk of compliance issues and the associated costs.
Enhanced Trust: Patients trust healthcare providers to keep their personal and medical information safe. By using our HIPAA-compliant billing services, you show your commitment to maintaining privacy, which fosters trust and enhances your reputation.
Efficiency and Accuracy: In addition to security, we ensure that your billing processes are efficient and accurate, leading to faster claim submissions, reduced denials, and increased revenue.
Why Choose APM BILLING for HIPAA-Compliant Billing Services?
Expertise: Our experienced team is dedicated to ensuring that all of your billing practices comply with HIPAA guidelines.
Tailored Solutions: We offer customized solutions that meet the specific needs of your healthcare practice, whether you’re a clinic, provider, or specialty office.
Focus on Security: We take security seriously and use state-of-the-art systems to protect all sensitive information.
Reliable Support: With APM BILLING, you’ll have a trusted partner in billing that is committed to safeguarding your practice’s financial and data integrity.
Get Started with APM BILLING Today
At APM BILLING, we understand the importance of maintaining HIPAA-compliant billing services in today's healthcare environment. We are here to help your practice stay secure, compliant, and financially efficient.
Contact us today at +1-800-621-3354 to learn more about how we can help streamline your billing process while ensuring complete protection of patient data. Visit our office at 19104 Philadelphia, Pennsylvania, and let APM BILLING handle your billing needs with the utmost professionalism and care.
Let APM BILLING take the stress out of billing while keeping your practice compliant with HIPAA regulations, so you can focus on what matters most—caring for your patients.2

