Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "primary key"
-
Things have been a little too quiet on my side here, so its time for an exciting new series:
practiseSafeHex's new life as a manager.
Episode 1: Dealing with the new backend team
It's great to be back folks. Since our last series where we delved into the mind numbing idiocy of former colleagues, a lot has changed. I've moved to a new company and taken a step up as a Dev manager / Tech lead. Now I know what you are all thinking, sounds more dull and boring right? Well it wouldn't be a practiseSafeHex series if we weren't ...
<audience-shouting>
DEALING! ... WITH! ... IDIOTS!
</audience-shouting>
Bingo! so lets jump right in and kick us off with a good one.
So for the past few months i've been on an on-boarding / fact finding / figuring out this shit-storm, mission to understand more about what it is i'm suppose to do and how to do it. Last week, as part of this, I had the esteemed pleasure of meeting face to face with the remote backend team i've been working with. Lets rattle off a few facts to catch us all up:
- 8 hour time difference to me
- No documentation other than a non-maintained swagger doc
- Swagger is reporting errors and several of the input models are just `Type: String`
- The one model that seems accurate, has every property listed as optional, including what must be the primary key
- Properties go missing and get removed at the drop of a hat and we are never told.
- First email I sent them took 27 days to reply, my response to that hasn't been answered so far 31 days later (new record! way to go team, I knew we could do it!!!)
- I deal directly with 2 of them, the manager and the tech lead. Based on how things have gone so far, i've nick named them:
1) Ass
2) Hole
So lets look at some example of their work:
- I was trying to test the new backend, I saw no data in QA. They said it wouldn't show up until mid day their time, which is middle of the night for us. I said we need data in our timezone and I was told: a) "You don't understand how big this system is" (which is their new catch phrase) b) "Your timezone is not my concern"
- The whole org started testing 2 days later. The next day a member from each team was on a call and I was asked to give an update of how the testing was going on the mobile side. I said I was completely blocked because I can't get test data. Backend were asked to respond. They acknowledged they were aware, but that mobile don't understand how big the system is, and that the mobile team need to come up with ideas for the backend team, as to how mobile can test it. I said we can't do anything without test data, they said ... can you guess what? ... correct "you don't understand how big the system is"
- We eventually got something going and I noticed that only 1 of the 5 API changes due on their side was done. Opened tickets. 2 days later asked them for progress and was told that "new findings" always go to the bottom of the backlog, and they are busy with other things. I said these were suppose to be done days ago. They said you can't give us 2 days notice and expect everything done. I said the original ticket was opened a month a go *sends link* ......... *long silence* ...... "ok, but you don't understand how big the system is, this is a lot of work"
- We were on a call. Product was asking the backend manager (aka "Ass") a question about a slight upgrade to the new feature. While trying to talk, the tech lead (aka "Hole") kept cutting everyone off by saying loudly "but thats not in scope". The question was "is this possible in the future" and "how long would it take", coming from management and product development. Hole just kept saying "its not in scope", until he was told to be quiet by several people.
- An API was sending down JSON with a string containing a message for the user with 2 bits of data inside it. We asked for one of those pieces to also come down as a property as the string can change and we needed it client side. We got that. A few days later we found an edge case and asked for the second piece of data to be a property too. Now keep in mind, they clearly already have access to them in order to make the string. We were told "If you keep requesting changes like this, you are going to delay the release of the backend by up to 2 weeks"
Yes folks, there you have it, the most minuscule JSON modifications, can delay your release by up to 2 weeks ........ maybe I should just tell product, that they don't understand how big the app is, and claim we can't build it on our side? Seems to work for them
Thats all the time we have for today,
Tune in for more, where we'll be looking into such topics as:
- If god himself was an iOS developer ... not
- Why automate when you can spend all day doing it by hand
- Its more time-efficient to just give everything a story point of 5
- Why waste time replying to emails ... when you can do nothing instead
See you all next week,
practiseSafeHex13 -
There was literally boxes full of biscuits in front of me and all I could think was... Where's the primary key?

-
Cool thing Zomato.. Now we know what the primary key in your database is..
You are saying if I want to update my email, I will have to let go of my subscription which I recently got?? Great piece of technology you have there.. 1
1 -
When the email address is the primary key and the customer "doesn't have an email address"
Like, they're free and it's 2018... Why not?13 -
*Opens a pack of tablets (8000) and start to prep them.*
WHAT THE ACTUAL FUCK.
SAME MAC ADDRESS.
Okay, that's just an er-
NOPE, ANOTHER ONE. HOLY SHIT. OKAY IT'S GETTING WORSE.
Is it my db?
Oh.
The db is just fine.
*Painfully getting in contact with the reseller*
Me: grumbles grumbles Mac Address grumbles
Reseller: Uh.. What?
It would be okay if we weren't using Mac Addresses as primary key in our databases.
They gave us some weird-looking software to "re-write mac addresses". It's working.
Something tells me that ipv6 is not for tomorrow.7 -
I hate access. I wish I could use literally any other program. But they're not authorized.
I'm the only one working on this, and everything is closed. How the fuck is the object in use somewhere else? And where the fuck did my primary key go???7 -
Once a month I get a crash for the stupid PHP site I am in charge of because the guy who made the database made the primary key of a table a varchar. It is a number 99.9% of the time but the dumbass customer always enters one entry with a string cuz the dumbass db Dev let them. I emailed the dumbass Dev telling him he is stupid and he said it is part of their philosophy. I told him I still think he is stupid so he emailed my boss.
I emailed him again telling him he is stupid.6 -
TL;DR
I accidentally surpassed(?) my user permissions and closed some of my classmates browsers and locked up a terminal for me
In school we have 2 primary operating systems: Windows and Ubuntu. Windows is hell in general and but not as hell as the firefox installation on Ubuntu.
"Just loaded this page. Now wait half a minute so that I can render it"
"Woah, woah, woah. Slow there. You just made an input event. Give me those 5 seconds to compute what you just did"
Executing "top" or "htop" shows you a long list of firefox processes with a cpu usage of 99.9%, since the whole school shares that linux environment.
Anyway, one day it was way more servere than normally and I way forced to kill my firefox instances. So I pressed CTRL+ALT+T for that terminal, waited 5 minutes until it accepted input typed "killall firefox" with a delay of half a minute per character and smahed that enter key.
At this very point in time I could hear confusion from every corner of the room. "What happened to firefox?"
Around 30% of the opened browsers where abruptly stopped. I looked back to my screen noticed I was logged out. I couldn't login from that terminal for the rest of that day.
Our network admin, which happened to be there, since the server is just next door, said that this was just convenience, but the timing was too perfect so I heighly doubt that.
I felt like a real hackerman even if it was by accident :)8 -
If you discount all the usual sql injections the most blatant was not our but a system one customer switched to after complaining over cost.
The new system was a bit more bare bones featurewize but the real gem was the profile page for their customers.
The only security was an id param pointing to the users primary key, which was an auto incrementing integer :)
And not only could you access all customer data but you could change it to.
But since the new system was built by their it chief’s son we realized it was not much we could do.2 -
I just had the most surreal email discussion I think I've ever had...
I spent over two hours going back-and-forth over email with an enterprise DBA, trying to convince them I needed a primary key for a table. They created the table without a primary key (or any unique constraints... or indexes... but that's another discussion). I asked them to add one. Then had to justify why.
If you ever find yourself justifying why you need a primary key on a table in an RDBMS, that's the day you find yourself asking "is this real life?"
I want the last two hours of my life back. And a handful of Advil.1 -
I am very frustrated today and I do not know where to "scream" so I will post this here since I believe you will know how I feel.
Here's the case...
I am developing an e-commerce web application where we sell industrial parts. So my boss told me on March that when we are going to show these parts, we should not show Part Number to visitors because they will steal our information.
Ok, this makes sense but there was a problem.
The Primary Key for these products in our internal system is a string which is the Part Number itself.
I told him on March that we have to come up with another unique number for all the products that we are selling, so this unique number will be the primary key, not the Part Number. This will be best because I will be dependent from the original Part Number itself. And in every meeting he said "That is not priority". So I kept developing the part using the original Part Number as primary key and hid is from the web app. (But the Part Number still shows on URL or on search because this is how my boss designed the app.)
I built the app and is on a test server. Until one of out employees asked my boss: "There is no unique number or Part Number. How are the clients going to reference these parts? If a client buys 20 products and one of those has a problem, how is he going to tell us which products has a problem?"
My boss did not know what to say, and later said to me that I was right and primary key was priority.
I really hate when a guy that knows shit from developing does not listen to suggestions given by developers.
FUCK MY LIFE!
I'm sorry if you did not understand anything.5 -
Sleeping the Thread for 1 sec, because the database had no real timestamp and a transaction on the same item within the same second would lead to a doubled primary key...
No real feature, but it is a bug and this makes it a feature I guess.1 -
First rant here, and it's going to be a query to the more professional and experienced members of society (most of you).
I am currently a Sys Admin for a major company, and I develop at night. My primary employment at the moment is the sys admin job (and I code for extra money at nights).
I wanted to start a development department at the company that I am working at, but it was turned turned down. It was stated that we are not branching in development, and that we should stick to our server implementation and support. This was a prompt to me wanting to start studying officially (I wanted to get qualified in JAVA, so that I had some paper behind my name when I looked for another job). HR and my directors outright denied me the ability to study through them (they pay for studies for employees) and I was more than fine with this.
I took a loan and paid for the studies myself. Can't crush a dream, you know?
The director caught wind of me studying, and now has demanded that I develop him a mobile application for the company. I told him that I am not a mobile developer, and that it didn't fall into my key performance areas.
Note, I do my coding on own time, on my own device, and never at work. It's fully my intellectual property. It also in no way interferes with my work during the day, and has NO conflict with my contract this side.
He sent an email yesterday, this is after two months. He is now stating that I WILL do the application, and he has CCd HR and two directors.
I don't want to do the app for this company, I spoke to HR previously about this, and she said that I should try and quote it under my own company name (which I did, but it was denied as it was "too expensive").
Now I am being forced to do something that is COMPLETELY out of my roles and responsibilities, something that this company has ABSOLUTELY no desire to go into further on, and he is basically letting me know that if I don't do it, he is going to start messing with my pay.
I really don't want to do this, and I cannot afford to make my secondary job my primary at the moment. The problem is, too, that I don't have the time during the day to develop AND do my sys admin tasks (I manage more than 300 servers, and 5000 devices).
What can I do in this instance? Or what would you guys recommend, in your experience?
Sorry for the noob question, but I don't know what to do.19 -
Issue reporter:
Feed from external service provider is overwriting the wrong things, pls fix
Resolution:
Service provider is sending duplicate unique IDs, you need to get with them to discuss
Service provider response:
This is a *RE-USABLE UNIQUE ID* . . . The bottom line is you should not use this UNIQUE ID as a primary key. 21
21 -
Everyone and their dog is making a game, so why can't I?
1. open world (check)
2. taking inspiration from metro and fallout (check)
3. on a map roughly the size of the u.s. (check)
So I thought what I'd do is pretend to be one of those deaf mutes. While also pretending to be a programmer. Sometimes you make believe
so hard that it comes true apparently.
For the main map I thought I'd automate laying down the base map before hand tweaking it. It's been a bit of a slog. Roughly 1 pixel per mile. (okay, 1973 by 1067). The u.s. is 3.1 million miles, this would work out to 2.1 million miles instead. Eh.
Wrote the script to filter out all the ocean pixels, based on the elevation map, and output the difference. Still had to edit around the shoreline but it sped things up a lot. Just attached the elevation map, because the actual one is an ugly cluster of death magenta to represent the ocean.
Consequence of filtering is, the shoreline is messy and not entirely representative of the u.s.
The preprocessing step also added a lot of in-land 'lakes' that don't exist in some areas, like death valley. Already expected that.
But the plus side is I now have map layers for both elevation and ecology biomes. Aligning them close enough so that the heightmap wasn't displaced, and didn't cut off the shoreline in the ecology layer (at export), was a royal pain, and as super finicky. But thankfully thats done.
Next step is to go through the ecology map, copy each key color, and write down the biome id, courtesy of the 2017 ecoregions project.
From there, I write down the primary landscape features (water, plants, trees, terrain roughness, etc), anything easy to convey.
Main thing I'm interested in is tree types, because those, as tiles, convey a lot more information about the hex terrain than anything else.
Once the biomes are marked, and the tree types are written, the next step is to assign a tile to each tree type, and each density level of mountains (flat, hills, mountains, snowcapped peaks, etc).
The reference ids, colors, and numbers on the map will simplify the process.
After that, I'll write an exporter with python, and dump to csv or another format.
Next steps are laying out the instances in the level editor, that'll act as the tiles in question.
Theres a few naive approaches:
Spawn all the relevant instances at startup, and load the corresponding tiles.
Or setup chunks of instances, enough to cover the camera, and a buffer surrounding the camera. As the camera moves, reconfigure the instances to match the streamed in tile data.
Instances here make sense, because if theres any simulation going on (and I'd like there to be), they can detect in event code, when they are in the invisible buffer around the camera but not yet visible, and be activated by the camera, or deactive themselves after leaving the camera and buffer's area.
The alternative is to let a global controller stream the data in, as a series of tile IDs, corresponding to the various tile sprites, and code global interaction like tile picking into a single event, which seems unwieldy and not at all manageable. I can see it turning into a giant switch case already.
So instances it is.
Actually, if I do 16^2 pixel chunks, it only works out to 124x68 chunks in all. A few thousand, mostly inactive chunks is pretty trivial, and simplifies spawning and serializing/deserializing.
All of this doesn't account for
* putting lakes back in that aren't present
* lots of islands and parts of shores that would typically have bays and parts that jut out, need reworked.
* great lakes need refinement and corrections
* elevation key map too blocky. Need a higher resolution one while reducing color count
This can be solved by introducing some noise into the elevations, varying say, within one standard div.
* mountains will still require refinement to individual state geography. Thats for later on
* shoreline is too smooth, and needs to be less straight-line and less blocky. less corners.
* rivers need added, not just large ones but smaller ones too
* available tree assets need to be matched, as best and fully as possible, to types of trees represented in biome data, so that even if I don't have an exact match, I can still place *something* thats native or looks close enough to what you would expect in a given biome.
Ponderosa pines vs white pines for example.
This also doesn't account for 1. major and minor roads, 2. artificial and natural attractions, 3. other major features people in any given state are familiar with. 4. named places, 5. infrastructure, 6. cities and buildings and towns.
Also I'm pretty sure I cut off part of florida.
Woops, sorry everglades.
Guess I'll just make it a death-zone from nuclear fallout.
Take that gators!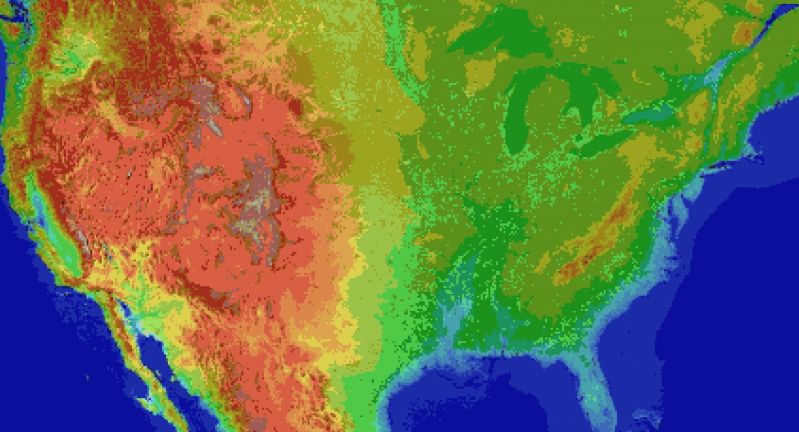 5
5 -
Alright, I need suggestions. I live in a small town and outside of my primary job, I own my own IT business. A lot of (l)users have eagerly asking if I’ll be teaching classes to explain some of the key things a computer is capable of doing. (Most of them will be elderly.)
How much would you charge for this? I’ve got about 20 people confirmed and I was thinking about doing 20$ a head. What seems reasonable? Keep in mind, this is a smaller sized town.17 -
When creating auto incrementing integer keys on a MySQL database, please mark then as unsigned, you don’t need a negative primary key 😞😞😞4
-
Got to scratch of one of three remaining old (14years and counting) design mistakes this week.
Together with a colleague we replaced a 1.5 billion row table that I out of ignorance then designed with a 3 column composite primary key instead of an identity column.
Moving the data while keeping all synchronized (the table gets up towards 2 million new rows and 2 million updates a day while constantly being queried) took 1 week.
Just 2 skeletons left to clean out, any year now ;).1 -
Ok now I'm gonna tell you about my "Databases 2" exam. This is gonna be long.
I'd like to know if DB designers actually have this workflow. I'm gonna "challenge" the reader, but I'm not playing smartass. The mistakes I point out here are MY mistakes.
So, in my uni there's this course, "Databases 2" ("Databases 1" is relational algebra and theoretical stuff), which consist in one exercise: design a SQL database.
We get the description of a system. Almost a two pages pdf. Of course it could be anything. Here I'm going to pretend the project is a YouTube clone (it's one of the practice exercises).
We start designing a ER diagram that describes the system. It must be fucking accurate: e.g. if we describe a "view" as a relationship between the entities User and Video, it MUST have at least another attribute, e.g. the datetime, even if the description doesn't say it. The official reason?
"The ER relationship describes a set of couples. You can not have two elements equal, thus if you don't put any attribute, it means that any user could watch a video only once. So you must put at least something else."
Do you get my point? In this phase we're not even talking about a "database", this is an analysis phase.
Then we describe the type dictionary. So far so good, we just have to specify the type of any attribute.
And now... Constraints.
Oh my god the constraints. We have to describe every fucking constraint of our system. In FIRST ORDER LOGIC. Every entity is a set, and Entity(e) means that an element e belongs to the set Entity. "A user must leave a feedback after he saw a video" becomes like
For all u,v,dv,df,f ( User(u) and Video(v) and View(u, v, dv) and feedback(u, v, f) ) ---> dv < df
provided that dv and df are the datetimes of the view and the feedback creation (it is clear in the exercise, here seems kinda cryptic)
Of course only some of the constraints are explicitly described. This one, for example, was not in the text. If you fail to mention any "hidden" constraint, you lose a lot of points. Same thing if you not describe it correctly.
Now it's time for use cases.
You start with the usual stickman diagram. So far so good.
Then you have to describe their main functions.
In first order logic. Yes.
So, if you got the point, you may think that the following is correct to get "the average amount of feedback values on a single video" (1 to 5, like the old YT).
(let's say that feedback is a relationship with attribute between User and Video
getAv(Video v): int
Let be F = { va | feedback(v, u, va) } for any User u
Let av = (sum forall f in F) / | F |
return av
But nope, there's an error here. Can you spot it (I didn't)?
F is a set. Sets do not have duplicates! So, the F set will lose some feedback values! I can not define that as a simple set!
It has to be a set of couples, like (v, u), where v is the value and u the user; this way we can have duplicate feedback values in our set.
This concludes the analysis phase. Now, the design.
Well we just refactor everything we have done until now. Is-a relations become relationships, many-to-many relationships get an "association entity" between them, nothing new.
We write down on paper every SQL statement to build any table, entity or not. We write down every possible primary key or foreign key. The constraint that are not natively satisfied by SQL and/or foreign keys become triggers, and so on.
This exam is considered the true nightmare at our department. I just love it.
Now my question is, do actually DB designers follow this workflow? Or is this just a bloody hard training in Pai Mei style?6 -
Meetings would be better without people.
I mean I like the IDEA of meetings...
Honestly I'm the type of person who if I could would schedule lots of meetings to make sure we're all on the same page, and to be sure the thing is going to do the thing everyone wants / get their perspective, etc. I really want to KNOW what the folks who are going to use this thing need / want / what works best for them.
On the other hand I know that meetings are often more like:
Me: "Ok let's so here's our data, now tell me what fields they want to edit and so forth."
People: "All of them."
Me: "Uh, no you don't want that or they'll break everything ... X, Y and Z require those fields for A, B, and C to work."
Me: "Let's go field by field and you tell me if they need to edit it, and why."
People: "Yeah this first one they have to be able to change this one."
Me: "Wait no, that's the primary key for that table, I don't know why that's on this list but no you can't change that."
People: "Yeah we have to be able to change that."
Me: "No, you can't, do you even know what that number IS?"
People: "Um... no ..."
(╯°□°)╯︵ ┻━┻1 -
A time I (almost) screamed at co-worker?
Too many times to keep up with.
Majority of time its code like ..
try
{
using (var connection = new SqlConnection(connectionString))
{
// data access code that does stuff
}
catch (Exception e)
{
// Various ways of dealing with the error such as ..
Console.WriteLine("Here");
ShowMessage("An error occured.");
return false;
// or do nothing.
}
}
Range of excuses
- Users can't do anything about the error, so why do or show them anything?
- I'll fix the errors later
- Handling the errors were not in the end-user specification. If you want it, you'll have to perform a cost/benefit analysis, get the changes approved by the board in writing, placed in the project priority queue ...etc..etc
- I don't know.
- Users were tired of seeing database timeout errors, deadlocks, primary key violations, etc, so I fixed the problem.
On my tip of my tongue are rages of ..
"I'm going to trade you for a donkey, and shoot the donkey!"
or
"You are about as useful as a sack full of possum heads."
I haven't cast those stones (yet). I'll eventually run across my code that looks exactly like that.1 -
Swear work is where you I go to fix other peoples poor design decisions and clean up the bullshit that comes out of said decisions.
CANT!
BE!
FUCKED!
How you have so many years experience and still design in way that ensures that maintenance /improvements/touching in the future is a huuugggeee clusterfuck.
Hey, I got an idea, lets make this whole data warehouse without a single index or primary key cos you know, that's the Kimball Method.2 -
DataDevNerd (ofc down to hardware bits)
Briefly blending amoung holiday tech consumers at Micro Center waiting for key-holder assistance @SSDs.
Rando: "they finally have a sale on *X, rebranded, price++* for my *ref'd only by part names* setup! What are you getting?"
Me: "replacement SSD, laptop's finally failing"
Rando: "Yeah, I totally get you, I hate that. How old is it? Hopefully you got a couple years outta it?"
Me: "over 7yrs old."
Rando: "Wow! Mustve not used it too much, still that's pretty long."
Me: "Actually, it's been my primary device, heavily used, as I'm a dev. I just know what/when to use SSD vs the HDD."
Rando: "Duuude, that's awesome!...wait...why haven't you just bought a new laptop yet?"
Me: "I'm not for hardware abuse or burning money"
I was quickly reminded why I tend to avoid typical consumer tech stores. 2
2 -
Today somebody at work asked why they couldn't change a primary key.
Not joking.
Are you fucking kidding me?? There's a reason SSMS doesn't allow it.. because BAD SHIT HAPPENS if you do.2 -
I can't convince my team that a good database model promotes a good API design and a good UI/UX experience.
Instead, I have to work with a ridiculous table setup.
Imagine, if you will, a table (table B) that references another table (table A) via a foreign key. The FK is a string in both tables. And table A only has one column, which is labeled as "name".
The schema i have to look at it kind of like this:
Table parent
Name varchar(10) primary key
Table child
Name varchar (10),
parent_name varchar(10),
Foreign key (parent_name) references parent (name)
Sorry if the syntax is wrong, a little frustrated having to look at it...
Am I crazy to want to change this table design? Am I missing something? I feel like I'm taking crazy pills, because this is just scratching the surface of the problems I have to deal with.7 -
I applied for a position as an engineer for a nonprofit organization that helped kids across the country (and the world) and got the position. The people across the organization were wonderful and, without a doubt, mission driven to help kids and it felt good to do the work. The agile teams worked well together, every team had their roadmaps, and management always emphasized family first. The organization was making crazy money so we were given all the tools we needed to succeed.
Then, within a few months of my hiring, it was announced that the non-profit organization was being bought by a large, fairly well known for-profit company which had also been recently acquired by a venture capital firm.
The next thing we knew, everything changed all at once. We went from building applications for kids to helping this company either make money or build value for their owners. Honestly, I did not know what my day-to-day work was doing for this company. The executives would tell us repeatedly that we were expensive and not a good value compared to their other teams. It felt like we were only being kept until the systems were integrated and their had access to our decades of data.
You might think I'm being paranoid but a year after the acquisition, we still did not have any access to any of their systems. We operated on a separate source code solution and were not given access to theirs. When requests came from them that would facilitate them connecting applications to the data, it was to be considered highest priority.
The final straw for me was when I was told my compensation would be cut for the next year. We were strung along for the whole year leading up to it saying that the company was evaluating our salaries compared to others in the industry. Some of us figured that we would probably even go up knowing that we were underpaid for a for-profit tech company because we chose to work in a non-profit for a lower rate to be able to do worthwhile work. Nope! We were told that we were overpaid and they talked about how they had the data to prove it. One quick look at LinkedIn would tell you they must be smoking something that had gotten stale in a shoebox. Or they were lying.
So that was my rant. If you think you are protected from the craziness in tech right now just because you are writing code at a nonprofit, you might be wrong. Dishonest executives can exist anywhere.3 -
(Fyi: I was an intern.)
It took me hours of time to recognize, that one of the necessary tables just used an oracleDB Date as a timestamp, which lead to a violation of the primary key constraint on interactions taken place in less than one second.
Me: (explaining the problem to CW)
CW: "Yup, we know."
Me: ...2 -
is using auto incremented id as primary key bad practice in mysql??
My teacher said it is wrong to use autoincrement because it will skip number when row is deleted. But it does to make it unique .
Or should i use uuid ? But doesn't it impact performance?57 -
"The thing I want to change is very simple.."
Day starts off great again by manager saying the above - which is already problem with her limited technical knowledge - and then she proceeds by wanting to change multiple properties of a primary key in our live db.
I really hope my interviews go well this week and I can leave this place soon.. -
Took over a project where a dev created a table with no primary key and enforce a unique constraint in code. Wtf? He also always selected top 1 so if you added a record directly in the table it completely fucked the expected data.
So, when I took this piece of shit over I didn't realize what the table was and when I tried to convert it to EF it barfed since there was no PK. Was a complete PITA and had to create all new tables.
Some people shouldn't develop software!!!!!!!!! -
NO! Use the description instead of the primary key because the key might change ................................................................................................................... vs the description .............................................................................................................. the key more likely .............................................. meh2
-
Have you ever wanted a feature to be a certain way but you had to settle with something easier and less cool/impressive?
I just had to and it’s very dissatisfying. -
After brute forced access to her hardware I spotted huge memory leak spreading on my key logger I just installed. She couldn’t resist right after my data reached her database so I inserted it once more to duplicate her primary key, she instantly locked my transaction and screamed so loud that all neighborhood was broadcasted with a message that exception is being raised. Right after she grabbed back of my stick just to push my exploit harder to it’s limits and make sure all stack trace is being logged into her security kernel log.
Fortunately my spyware was obfuscated and my metadata was hidden so despite she wanted to copy my code into her newly established kernel and clone it into new deadly weapon all my data went into temporary file I could flush right after my stick was unloaded.
Right after deeply scanning her localhost I removed my stick from her desktop and left the building, she was left alone again, loudly complaining about her security hole being exploited.
My work was done and I was preparing to break into another corporate security system.
- penetration tester diaries2 -
!rant
Many out there say you should use 2 factor authentication with everything, but personally i feel lile that would just turn your phone into a sigle point of failure.
Phisical security is my primary worry, because loosing your phone or having it stolen yould pretty much lock you out of all your accounts.
Another thing is i don't know as much about android security, and i wouldn't be confortable managing it.
I have 2FA active for some key services, but imho a strong password is usually enough. I think its far more more importat for your overall security to avoid passwords re-use.
What do you think? Do you have 2FA on all the time?9 -
I'm studying Databases and I'm getting confused about Foreign Key.
A Foreign Key made reference to Primary Key of another table. But what's the point? Can't I simply use a value and select requested data where TableA value is equal to TableB value?
Sorry if I didn't explain it well, I'm so confused lmao6 -
At internship with a fellow student from my class, making a SqliteHelper class in php to make things easier. Delete methods only have only one parameter (Primary key)
Coworker: "Why do you use the primary key as parameter? The user has no access to it!"
I can't express in words how close I was to snapping. -
Alright... maybe it's time to call it quits...
NLegs changed the ID structure... The URL is like
http://.../yyyy/MM/dd/id.html
Before id was unique... so thats what I have in my DB, the ID column is int. primary key.
Now id by itself is no longer unique...
---
Actually no.... After changing the code to just pick the next ID (like autonumber) and check uniqueness using the url...
It turns out actually the "new issues" are old.... they just changed which image to show in the front page thumbnails...4 -
odoo keeps showing nameerror: name 'id' is not defined.
like bruh, 'id' is in default, the primary key of my fucking model. why the hell cant i reference it
fucking bug3 -
"Let's join two views and create a custom column that acts as a primary key so that other tables can treat it like a foreign key" said no dev ever.
Or at least I had thought that until today when I started figuring out why our queries are so goddamn slow. I hate the previous devs so much.1 -
And now the boss want to have a user table in the db where I can change the id of the user (primary key) when ever HE wants... And all the other table are connect to the user trough the id...2
-
I had to take my backspace key apart today to pull some hairs out of the sensor because it was ghosting and it deleted a whole source file. I'm amazed at how easy it is to repair thinkpads with minimal equipment and limited dexterityy / vision.
The retainer clip is so sturdy it feels like idiots trying to force the two halves together at the wrong place was a primary use case.1 -
If you edit a column in a table in SQL Developer GUI you can loose your primary key in that table, even if you didnt touch the primary key column.
How fun is that?2 -
What infrastructurial fuck / poor design happened that Tinder does not allow changing the profile nickname? Did some enlightened celestial cunt thought of using the nick as a primary key or what the fuck?3
-
My most productive day of the month
Making a to-do list app with login and register functionality.
Why this fucking DB needs a primary key every time
Brainfart!2 -
What are resources if you have to quickly gain overview on a subject? i.e: Need overview of the use of "primary key" in SQL, without passing through explanation in a book.3
-
How much of "unique" the string that is the current epoch in milliseconds converted to base 36 ?
I know it is not universal. But require such a bad luck to have collision no ?
I am gonna use it for "transaction" primary key. (Every time a user pay, it it a new trasantion).
Uuid are very long, i need to put this pk in qr-code later
Thoughts ?24 -
Currently working on a conversion of a tool we use to keep track of our working hours (like how much time did we spend on that task, that project etc.), because the old version of that language sucks ass and the database system sucks even more ass.
Besides the other stuff that's freaking horrible in that fucking shit tool (crashes when entering wrong input, etc.) - the genius that created that peace of crap (1997!) decided that he wants to use a fucking timestamp as a PK-column on some tables.
Why the fuck would you that?! Jesus fuckin' christ.
And of course, the fuckin apprentice has to deal with this shit and has to be finished yesterday x)3 -
Me: GUI team needs help from backend team to add UIDs to a (shitty) object in (their in-house shitty) db.
Backend:
Backend can display these (shitty) objects properly, why can't GUI use the entire object as composite primary key? Backend can't just add some random UID to fix GUI display bug.1 -
I hate waiting on a preview of an SDK from Microsoft that should have the support for the feature in the first place. I should be able to query a view without needing a primary key. I am tired of making workarounds. Come on EF Core 2.1 preview! You’re killing me! Back to ADO.NET for now.
-
Get My Energy Report: Expert SAP Assessment Services in Manchester
If you're a homeowner, landlord, or business owner in Manchester looking for a reliable SAP assessment, Get My Energy Report is here to provide you with professional and thorough services. Our team of certified assessors is committed to helping you understand your property’s energy efficiency and ensure compliance with current regulations.
What is a SAP Assessment?
A SAP (Standard Assessment Procedure) assessment is a method used to calculate the energy efficiency of a home. It is the primary assessment tool used in the UK for calculating the energy performance of residential buildings, especially in new builds. The SAP rating takes into account various factors such as insulation, heating, hot water systems, and ventilation, to provide an energy score. This score helps property owners and builders understand the potential energy costs and environmental impact of a property.
At Get My Energy Report, we specialize in offering SAP assessments to help you ensure that your property meets the necessary energy efficiency standards. Our team of experts uses the most up-to-date tools and methodologies to provide you with an accurate assessment.
Why Do You Need a SAP Assessment?
A SAP assessment is essential for anyone involved in constructing or purchasing a new property. It is a legal requirement for new homes to have a SAP rating as part of building regulations, ensuring that properties are built to be energy-efficient and environmentally friendly.
Some of the key reasons you may need a SAP assessment include:
New Builds and Renovations: If you are constructing a new home or undertaking significant renovations, a SAP assessment is required to comply with building regulations.
Energy Efficiency Improvements: If you are looking to make improvements to the energy performance of your property, the SAP assessment can provide valuable insights into areas for improvement.
Property Transactions: In some cases, when purchasing a property or for building certification, a SAP assessment may be necessary to assess its energy efficiency.
Our SAP Assessment Services
At Get My Energy Report, we offer comprehensive SAP assessment services tailored to your specific needs. Our experienced assessors will evaluate your property’s energy performance and provide a detailed report that outlines its SAP rating and offers recommendations for improvement.
Residential SAP Assessments: Whether you're building a new home or making energy-efficiency improvements, our residential SAP assessments help you ensure your property meets energy regulations and performs efficiently.
Commercial SAP Assessments: We also provide SAP assessments for commercial properties, ensuring your business meets energy efficiency standards and reduces operating costs.
Energy Efficiency Advice: Along with the SAP assessment, we provide professional recommendations on how to improve your property’s energy efficiency, helping you save on energy costs and reducing your environmental footprint.
Why Choose Get My Energy Report?
Local Experts: Based in Manchester, we have a deep understanding of local regulations and are committed to offering fast, reliable SAP assessments for residential and commercial properties in the area.
Certified Assessors: Our team consists of certified SAP assessors with years of experience in the field, providing accurate and professional assessments.
Competitive Pricing: We offer transparent and affordable pricing for our SAP assessments, ensuring you get the best value for your investment.
Efficient Service: At Get My Energy Report, we value your time. We work quickly and efficiently to provide you with the necessary reports and recommendations.
Contact Us for Your SAP Assessment in Manchester
If you need a SAP assessment in Manchester, Get My Energy Report is your trusted partner. Our experienced team is here to ensure your property is energy-efficient, compliant with regulations, and ready to face the future with a focus on sustainability.
For more information or to schedule your SAP assessment, give us a call at +44 7957 926910. We look forward to helping you improve your property’s energy efficiency! 1
1 -
Buy Verified Cash App Account: Navigating the Digital Transaction Landscape
In an age dominated by digital transactions, the concept of purchasing a verified Cash App account has gained significant traction. This article aims to explore the nuances of buying a verified Cash App account, elucidating the advantages, potential risks, and offering a comprehensive guide for individuals considering this financial move.
Introduction
The Growing Trend of Buying Verified Cash App Accounts
As online transactions become more prevalent, the trend of purchasing verified Cash App accounts is on the rise. Users are increasingly recognizing the added benefits and security that come with having a verified account.
Understanding the Importance of Account Verification
Account verification is a crucial step in enhancing the security of digital transactions. A verified Cash App account provides users with an additional layer of protection, making their financial interactions more secure and reliable.
Advantages of Purchasing a Verified Cash App Account
Enhanced Security Features
One of the primary advantages of a verified Cash App account is the incorporation of advanced security features. These may include multi-factor authentication and additional verification steps, adding an extra layer of defense against unauthorized access.
Increased Transaction Limits
Verified accounts often come with substantially increased transaction limits. This proves beneficial for users engaged in larger financial transactions or those running businesses through the Cash App platform.
Access to Exclusive Cash App Features
Apart from heightened security and increased transaction limits, verified accounts may unlock exclusive features within the Cash App. This could range from priority customer support to early access to new features and promotions.
How to Safely Purchase a Verified Cash App Account
Researching Reputable Sellers
Before entering the purchasing process, it's crucial to research and identify reputable sellers. Reading reviews and testimonials can provide valuable insights into the credibility and reliability of a seller.
Authenticating Account Legitimacy
Ensuring the authenticity of the accounts offered by sellers is paramount. A legitimate verified account should have gone through the necessary verification steps outlined by Cash App.
Ensuring Transparency in Transactions
Transparency in transactions is vital. Buyers should choose sellers who provide clear information about the accounts, including their verification status and any associated features.
Risks and Precautions in Buying Verified Accounts
Common Scams in the Verified Account Market
The digital landscape is not without risks, and the market for verified Cash App accounts is no exception. Being aware of common scams, such as fake listings and phishing attempts, is essential.
Tips for a Secure Transaction Process
To mitigate the risk of falling victim to fraudulent transactions, following best practices such as using secure payment methods and verifying the seller's credentials is crucial.
Step-by-Step Guide to Verifying a Cash App Account
Understanding the Cash App Verification Process
Before attempting to verify a Cash App account, it is essential to understand the process thoroughly. Familiarizing oneself with the required documentation and steps ensures a smooth verification experience.
Submitting Required Information
During the verification process, users typically need to provide personal information, such as a valid ID and proof of address. Ensuring the accuracy and legitimacy of this information is key to a successful verification.
Navigating Potential Challenges
While the verification process is generally straightforward, users may encounter challenges. Being prepared to troubleshoot and address potential issues ensures a seamless verification experience.
Conclusion
Summarizing the Benefits and Risks
In conclusion, opting for a verified Cash App account offers users enhanced security, increased transaction limits, and exclusive access to platform features. While potential risks exist, informed decision-making and adherence to safety precautions can lead to a positive experience.
Encouraging Informed Decision-Making
As users consider the option of purchasing a verified Cash App account, it is crucial to approach the process with caution and awareness. Choosing sellers with proven credibility, staying informed about potential risks, and following best practices contribute to a secure and positive experience. devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account
devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account -
Today, after 1.8 years since the start of the project, the PM decided that the primary key of the object shouldn't be using the 'IMPL' prefix and must be also changed in historical data... Why? 'I don't like it' was all that he said in the email.
I like my job :)1 -
Introduction to Instagram Marketing
Instagram has grown into one of the most powerful social media platforms for businesses, influencers, and brands. With over 1 billion active users, it presents a vast opportunity for marketing, brand awareness, and customer engagement. However, succeeding on Instagram requires more than just posting images. This is where an Instagram marketing agency comes into play, offering professional strategies and services to enhance visibility, engagement, and conversion rates.
What an Instagram Marketing Agency Does
An Instagram marketing agency is a specialized firm that helps businesses, brands, and influencers optimize their presence on Instagram. Their primary role includes content creation, account management, audience engagement, paid advertising, and analytics tracking. These agencies have experienced social media marketers, content creators, and analysts who work together to ensure a brand stands out in a competitive digital landscape.
Key Functions of an Instagram Marketing Agency:
Content Strategy Development: Creating tailored content strategies to align with a brand’s goals.
Graphic Design and Visual Content Creation: Producing high-quality images, videos, reels, and stories.
Audience Engagement: responding to comments, messages, and engaging with the audience.
Hashtag Research & Implementation: Finding the best hashtags to maximize reach and engagement.
Influencer Collaborations: Connecting brands with relevant influencers to expand reach.
Advertising and Paid Promotions: Running targeted ad campaigns for better conversion rates.
Analytics and Performance Tracking: Monitoring engagement, reach, and other key performance metrics.
Instagram Account Management Services
Instagram account management is an essential service offered by agencies to handle every aspect of a brand’s Instagram presence. It includes daily posting, responding to followers, strategizing content, and ensuring brand consistency.
Core Instagram Account Management Services:
Content Planning and Scheduling: Preparing a consistent posting calendar to maintain engagement.
Profile Optimization: Enhancing bio, profile picture, and highlights for better brand appeal.
Community Management: Engaging with followers through comments, DMs, and interactive content.
Story and Reel Creation: Utilizing Instagram’s features to enhance engagement.
Crisis Management: Handling negative comments, PR issues, or brand-related concerns efficiently.
Best Instagram Marketing Strategies
The success of Instagram marketing depends on the implementation of effective strategies. The best agencies employ advanced techniques to optimize results.
Top Strategies Used by Instagram Marketing Agencies:
Consistent Branding: ensuring cohesive visuals, colors, and messaging.
Content Diversification: mixing images, videos, reels, carousels, and live videos.
User-Generated Content: encouraging followers to create content that features the brand.
Instagram Stories & Highlights: Engaging audiences with behind-the-scenes content, polls, and Q&As.
Collaborations & Partnerships: Partnering with influencers and other brands.
Shoppable Posts: Utilizing Instagram Shopping for direct sales.
SEO and Hashtag optimization: using relevant hashtags and keywords to improve discoverability.
A/B Testing for Ads: Running multiple ad variations to determine the most effective approach.
Benefits of Hiring an Instagram Marketing Agency
Businesses and influencers gain numerous advantages by outsourcing their Instagram marketing to professionals.
Key Benefits:
Expertise & Experience: Agencies have in-depth knowledge of Instagram’s algorithms and best practices.
Time-saving: Brands can focus on their core business while experts handle Instagram marketing.
Better Engagement & Growth: Professional strategies lead to higher engagement and follower growth.
Higher ROI on Ads: Paid campaigns are optimized for better conversions and lower costs.
Creative Content: Access to high-quality visuals, graphics, and videos.
Consistent Posting: Ensuring a steady stream of content for audience retention.
Choosing the Best Instagram Marketing Services
With so many agencies offering Instagram marketing services, it’s important to select the right one based on specific business needs.
Factors to Consider When Choosing an Instagram Marketing Agency:
Portfolio & Past Work: Reviewing previous campaigns to assess expertise.
Client Reviews & Testimonials: Checking customer feedback and satisfaction levels.
Customization & Personalization: Finding an agency that tailors services to individual brand needs.
Pricing & Packages: Comparing different service plans to fit the budget.
Technology & Tools: Ensuring the agency uses advanced analytics and automation tools.
Customer Support & Communication: Looking for agencies that provide prompt and clear communication. 1
1 -
(tldr: are foriegn keys good/bad? Can you give a simple example of a situation where foriegn keys were the only and/or best solution?)
i have been recently trying to make some apps and their databases , so i decided to give a deeper look to sql and its queries.
I am a little confused and wanted to know more about foreign keys , joins and this particular db designing technique i use.
Can anyone explain me about them in a simpler way?
Firstly i wanted to show you this not much unheard tecnique of making relations that i find very useful( i guess its called toxi technique) :
In this , we use an extra table for joining 2 tables . For eg, if we have a table of questions and we have a table of tags then we should also have a table of relation called relation which will be mapping the the tags with questions through their primary IDs this way we can search all the questions by using tag name and we can also show multiple tags for a question just like stackoverflow does.
Now am not sure which could be a possibile situation when i need a foriegn key. In this particular example, both questions and tags are joined via what i say as "soft link" and this makes it very scalable and both easy to add both questions and new tags.
From what i learned about foriegn keys, it marks a mandatory one directional relation between 2 tables (or as i say "hard a to b" link)
Firstly i don't understand how i could use foriegn key to map multiple tags with a question. Does that mean it will always going to make a 1to1 relationship between 2 tables( i have yet to understand what 11 1mant or many many relations arr, not sure if my terminology is correct)
Secondly it poses super difficulty and differences in logics for adding either a tag or question, don't you think?
Like one table (say question) is having a foreign key of tags ID then the the questions table is completely independent of tag entries.
Its insertion/updation/deletion/creation of entries doesn't affect the tags table. but for tag table we cannot modify a particular tag or delete a tag without making without causing harm to its associated question entries.
if we have to delete a particular tag then we have to delete all its associated questions with that this means this is rather a bad thing to use for making tables isn't it?
I m just so confused regarding foriegn keys , joins and this toxi approach. Maybe my example of stack overflow tag/questions is wrong wrt to foreign key. But then i would like to know an example where it is useful5 -
Cancer Immunotherapy Market Extensive Industry Analysis, Growth Rate, Segmentation, Investment Opportunities and Top Manufacturers 2035
The global cancer immunotherapy market is on a promising trajectory, with a projected value increase from USD 134.40 billion in 2024 to USD 346.63 billion by 2035, reflecting a compound annual growth rate (CAGR) of 8.8%. This innovative therapeutic approach leverages the body’s immune system to identify and combat cancer cells, presenting a compelling alternative to traditional treatments like chemotherapy and radiation, which often come with significant side effects.
Market Growth Projections
The market is anticipated to grow significantly, reaching USD 148.73 billion in 2025 before hitting USD 346.63 billion by 2035. The rising incidence of cancer globally, projected to see around 2,041,910 new cases and approximately 618,120 deaths in the U.S. alone by 2025, is a primary driver behind this growth.
Drivers of Growth
Key factors propelling the market include the increasing prevalence of cancer and a growing demand for targeted therapies. Cancer immunotherapy offers a more precise approach, effectively directing the immune response to target cancerous cells while sparing normal cells. This specificity has made it a preferred treatment modality, especially for patients who have developed resistance to traditional therapies.
Segmentation
The cancer immunotherapy market is segmented by several criteria:
1. Type of Product: This includes immune checkpoint inhibitors, cell therapies, cancer vaccines, immunomodulators, monoclonal antibodies, and oncolytic viral therapies.
2. Application: Key applications include breast cancer, colorectal cancer, head and neck cancer, lung cancer, melanoma, ovarian cancer, prostate cancer, pancreatic cancer, and others.
3. Route of Administration: Segments include intravenous (IV), intramuscular, and oral routes. Notably, the oral administration segment currently holds the largest market share due to patient preference for self-administration.
4. Mechanism of Action: This includes immune checkpoint inhibitors, tumor antigen targeted therapy, cell signaling modulators, and immune modulators.
5. Distribution Channel: The market is divided into hospital pharmacies, retail pharmacies, and online pharmacies, with hospital pharmacies accounting for the largest share.
6. End User: The primary end users include hospitals and clinics, cancer research centers, and other entities.
7. Geographical Regions: The market is analyzed across North America, Europe, Asia-Pacific, Middle East and North Africa, and Latin America, with North America currently holding the largest share.
Challenges
Despite the promising growth, the market faces significant challenges. The high costs associated with cancer immunotherapy, stringent regulatory guidelines, and tumor heterogeneity—which can complicate treatment efficacy—pose substantial barriers. Additionally, immune-related adverse events can hinder widespread adoption.
Key Players in the Industry
The competitive landscape features numerous established and emerging players actively engaging in research and development to enhance clinical pipelines for cancer therapies. Key players include AstraZeneca, Amgen, AbbVie, Bristol-Myers Squibb, and Pfizer, among others. These companies are involved in strategic initiatives such as partnerships and collaborations to advance their therapeutic offerings.
Recent Developments
Recent advancements in the field have seen significant investments in research to enhance cancer immunotherapy. For instance, collaborations like that between The University of Pennsylvania and the Parker Institute for Cancer Immunotherapy, which renewed their alliance with a USD 125 million investment, highlight ongoing efforts to push the boundaries of cancer treatment.
Conclusion
The cancer immunotherapy market is poised for significant growth, driven by increasing cancer incidence and the demand for more effective, targeted therapies. While challenges remain, ongoing research and developments promise to enhance the effectiveness and accessibility of immunotherapy treatments, making this an exciting area of focus within the biopharmaceutical industry.
Thank you for reading Roots Analysis report. Kindly get in touch with Roots’ team to know more about the report or to receive a customized copy of it. Our team will ensure the report is tailored according to your needs.5
