Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "access"
-
Client: we need you to give us access to the code ASAP. We don't like this black box approach.
Me: You have always had access to the code. It is here on this bitbucket repo and your usernames have admin access.
Client: We want the code moved to our GitHub before EOD.
I check out how to move repos over and it's fairly easy.
Me: just give me access to create a repo on your GitHub account and you can have the code moved over.
Client: Sorry it's late in the day and we stepped out to get drinks. (It was 2:30 pm). Not sure why you think there is a rush on this, we'll handle it first thing next week.
Me: WTF13 -
Manager asked for access to server with admin rights for a third party contractor and I questioned him... His answer?
- Your are gonna give access to anyone that needs access.
I gave. Went for a 15 days vacation.
Our server got blocked by our cloud provider because of ssh brute force attempt coming from it and the company website went offline during a big ass meeting because of that.
Made me giggle :)8 -
On Slack
Me: I can't access the VPN
Network team: You have to create a user incident
My browser: 403
Network team: Yeah you need to be on the VPN to access the incident system
Me: 😐18 -
me: I don't have access to X project
PM: you don't have access to X project?
me: no, I don't have access to X project
PM: don't worry I'll take care of that
2 min. later
PM: so, you were saying ... ?
me: that I don't have access to X project
1 month later
me: I don't have access to X project
PM: you don't have access to X project?10 -
"Opps.. I'm sorry, but you have insufficient rights to open this Ticket."
Well. You know what? I AM THE FUCKING SYSTEM ADMINISTRATOR YOU CUNT!
YOU HAVE INSUFFICIENT RIGHTS to restrict me access to that fucking ticket!
"Oh. In that case, go ahead."
THANK YOU. FUCKING PRICK.4 -
I just helped one of our cleaners get Internet since the management whitelisted devices that can get WiFi access.
I believe that anyone, regardless of position, must have equal access to the resources in this company.10 -
Fleksy keyboard: We don't access your private information and upload it to the cloud!
No, because I'm blocking your Internet access through a fucking root firewall.10 -
Happened on my first day in internship :
Me: Hey, I'm not allowed to install anything, could you install me Sublime Text?
Boss: yeah sure, hold on, I'm granting you admin rights
Me: ...9 -
IT: Its controlled via SSO, everyone has access by default
Me: oh i'm sorry, you are correct, I don't have an error message on my screen saying I don't have access. I made it all up. Thank you, you may close the support ticket2 -
Dear outsourced developers. Don't send me your private SSH key by email. I don't need it, it allows me to access anything else you can access pretending I'm you, and it shows a misunderstanding of how SSH keys work. 🤦🏻♂️11
-
Not really dev as much but still IT related 😂
in college we got some new macs in our class. Before we were allowed to use them the "IT Tech" came in and did something to them all (probably ran some scripts to set stuff up)
Anyway, I was completely new to OS X and accidentally pressed a key combo that opened up a dialogue to connect to a remote file server. I saw the address field was already filled out (from when the IT Tech was running the scripts). So me being me I decided to connect. Low and behold my student credentials got me in.
Taking a look around I found scripts, backups and all sorts of stuff. I decided to look at some of the scripts to see what they did. One of them was a script to add the Mac to the domain. Here's the funny part. The login to do that was hard coded into the script....
To conclude. I now have domain level access to my whole college network 🙃
Tl;Dr: stupid it tech saves password in script. I find it. I now have domain level access to the college network14 -
Boss: log in to azure and fix this server
Me: I don't have access
Boss: why not?
Me: you never gave me access...
Boss: ...
Me: hello?
Boss: (never responds in chat)
Me: 😒4 -
I received a ticket today that said
"The customer can access the app fine if they're at their home, but when they occasionally go to the desert they can't access the app"
You can't make this stuff up.
Someone please kill me.10 -
so um... several of my users access file explorer ONLY via Word.
How?
Well, open Word: File->Open->Computer->Browse (nb. thank you Word 2013 and onwards for making life miserable) and voila, access to documents, downloads, and server shares is gained.
...
Users... they will always find a way7 -
Just found out that the generic router that our ISP gave us, which we use at work, has a port you can telnet into to get shell access with root privileges.
 10
10 -
Buckle up kids, this one gets saucy.
At work, we have a stress test machine that trests tensile, puncture and breaking strength for different materials used (wood construction). It had a controller software update that was supposed to be installed. I was called into the office because the folks there were unable to install it, they told me the executable just crashed, and wanted me to take a look as I am the most tech-savvy person there.
I go to the computer and open up the firmware download folder. I see a couple folders, some random VBScript file, and Installation.txt. I open the TXT, and find the first round of bullshit.
"Do not run the installer executable directly as it will not work. Run install.vbs instead."
Now, excuse me for a moment, but what kind of dick-cheese-sniffing cockmonger has end users run VBScript files to install something in 2018?! Shame I didn't think of opening it up and examining it for myself to find out what that piece of boiled dogshit did.
I suspend my cringe and run it, and lo and behold, it installs. I open the program and am faced with entering a license key. I'm given the key by the folks at the office, but quickly conclude no ways of entering it work. I reboot the program and there is an autofilled key I didn't notice previously. Whatever, I think, and hit OK.
The program starts fine, and I try with the login they had previously used. Now it doesn't work for some reason. I try it several times to no avail. Then I check the network inspector and notice that when I hit login, no network activity happens in the program, so I conclude the check must be local against some database.
I browse to the program installation directory for clues. Then I see a folder called "Databases".
"This can't be this easy", I think to myself, expecting to find some kind of JSON or something inside that I can crawl for clues. I open the folder and find something much worse. Oh, so much worse.
I find <SOFTWARE NAME>.accdb in the folder. At this point cold sweat is already running down my back at the sheer thought of using Microsoft Access for any program, but curiosity takes over and I open it anyway.
I find the database for the entire program inside. I also notice at this point that I have read/write access to the database, another thing that sent my alarm bells ringing like St. Pauls cathedral. Then I notice a table called "tUser" in the left panel.
Fearing the worst, I click over and find... And you knew it was coming...
Usernames and passwords in plain text.
Not only that, they're all in the format "admin - admin", "user - user", "tester - tester".
I suspend my will to die, login to the program and re-add the account they used previously. I leave the office and inform the peeps that the program works as intended again.
I wish I was making this shit up, but I really am not. What is the fucking point of having a login system at all when your users can just open the database with a program that nowadays comes bundled with every Windows install and easily read the logins? It's not even like the data structure is confusing like minified JSON or something, it's literally a spreadsheet in a program that a trained monkey could read.
God bless them and Satan condemn the developers of this fuckawful program.8 -
>give person jailed access to my server.
>person breaks out, and notifies me.
>i fix the hole
>three weeks later i decide hes trustworthy enough and the jail is causing too many problems so i give him unjailed access
>first thing he does is crash the system
albeit unintentionally, but seriously?1 -
I HATE working with MS Office products. Yes, Access, I'm looking at you, you backwards, whanabe database reject! You're invalid as a serious SQL database and retarded as an data application suite.
VBA, make up your MIND with your damn function calls! Either require me to use parenthesis or don't! I'm sick of this conditional parenthesis sh*t!
While we're talking about not making up your mind... screw 'sub', you half wit language! Either use functions like a real language or go the f&$k home and make room for a language that knows what it's doing!
Oh!!! WHY... WHY! do you have null AND... NOTHING?! Who... Who... WHO invented "nothing"?! And what sick joke are you playing at with isnull() and empty()??? How many damn ways so you need to test for "no value"?!?!
Access... That's right, I'm not done with you yet... How is it you've survived this damn long in the business world with all of the databases you corrupt? Sure, you suck as a real database, but at least have some freaking pride that people even USE you! How DARE your corrupt yourself with the regularity you seem to have! I wish my bowel movements were as regular as your database corruptions, for the love of humanity.
F$@k you, VBA! F@&k you, Access! F$#k you, MS Office! And Fuuuuuu$k YOU Microsoft for shoving these half assed reject tools down my throat!
I hope your cloud uses Access as a back end and gets some injection virus.
*Takes deep breath* need to say that.10 -
"So you need access to the test server?"
Me:"Yes"
"Please fill these 800000000 forms,sign here,get your blood sample,your ID ,your right kidney,letter of approval from your boss,...."
Fuuuuuuuck!!!! I just want to change only 3 lines of code!!!!!!5 -
My dad was a Novell Certified Engineer and my mom a Bachelor in Computer Systems, so I kinda admired them until one tragic day my dad suggested "Hey son why don't you make it using Access".1
-
Here's how my day is going:
> Access::MerchantsController
=> MerchantsController
> Access::MerchantsController
NameError: uninitialized constant Access::MerchantsController
-.- 15
15 -
Please, for fucks sake people, STOP CALLING ALL FORMS OF INTERNET ACCESS WI-FI. CELLULAR ACCESS IS NOT WI-FI. FUCKING ETHERNET + FIBER OPTIC/SOME MORE COPPER CABLING/WHATEVER IS **NOT** WI-FI.12
-
Internal support article to get access to a tool:
"To get access click 'NO' in the 'was this article helpful section' and open a support ticket, making sure to mention the tool you are looking to get access to"
What fucking fresh hell is this? Why not have the article, contain the fucking link to open the ticket.
You have intentionally put up a useless article, in order to hack your way around this stupid system.2 -
Teacher: From today on, we will start working with ms access 😊.
Me: Please die and let my life in peace ☹️ and learn with something useful (MySQL) instead.6 -
My parents are real sticklers for who is allowed to be on Netflix. They only let people on when they are present, and they never click 'save password'.
Me being a poor college student and desperate for the Netflix password, created a fake website for one of my parents to sign into.
How did I do this? I created my own localhost server with a backend database for the password to go to. I then copied the Netflix home screen and log in and asked them to log me into their account.
They said I can be on for one hour, and then they were signing me out.
I agreed to these terms.
As a small twist, I had also copied the no internet tab from Chrome for the page to redirect to. Knowing that once they logged in they would be expecting the main UI.
They logged in and then waited for the page to load. I, of course, put in a delay for the page to load and then displayed the no internet tab. They were confused and asked me to refresh, still nothing. I asked them if the router was out, and they went to check.
While they were away I quickly switched back to the real Netflix website and yelled back saying I got it working again. They came back over and saw that it was asking for a password again. They signed in and saw the main homepage and none were the wiser that day.
Once they left I checked inside the DB and found the plaintext password they typed in... The damn password was so simple, I cursed myself for not having figured it out sooner. No matter, I had my parents Netflix password.
So you're probably wondering how they didn't see the URL above and think something was off?
I pressed F11 and fullscreened my entire browser. They did ask, and I simply replied with, I don't like seeing all the crap up above when I'm streaming. No further questions, perhaps I was lucky.14 -
Damn fuck it. I am making a program with
#include <windows.h>
Accessing the Win32 API in c is such a pain. Just made a simple window with 70 lines of c code. And I have to edit it in turbo c but run it in some other compiler. Our teacher is a .... uhhh
Hate projects.
Sorry if the rant doesn't make sense. I am too tired.12 -
I hate access. I wish I could use literally any other program. But they're not authorized.
I'm the only one working on this, and everything is closed. How the fuck is the object in use somewhere else? And where the fuck did my primary key go???7 -
Did i just get rick rolled through a user agent?
"[17/Nov/2020:10:20:42 +0000] "GET / HTTP/1.1" 200 1274 "-" "We are no strangers to love. You know the rules and so do I. A full commitment is what Im thinking of. You wouldnt get this from any other guy.." "-""4 -
Preface: My company took over another company. A week ago I inherited their IT.
"IT" !!!! Are you fucking kidding me?!
Their server stood at an ex employees homeoffice. So I drove to her and she had 0 idea about IT. Server was just "Running". I tore that fuck down and saw an aweful lot of Hentai in all home folders.
WTF?!
Not enough, their crm was a makroinfested access table. Shit was protected so I couldn't even edit the makros. The retarded fucktards hardcoded paths to serverside folder \\fuck\you\hard\cavetroll
Just so that server will never see the light of my domain! Damn you? Mothership of sisterfucking dickgirls!10 -
Me trying to use Linux for first time:
Sudo node index.js
access denied
Sudo shutdown
access denied (noob)
Me: im going back to Windows now....23 -
I work at a place where security is really high when it comes to server access. Today I was in urgent need to get admin access to a server, this is a real pain. Luckily I found an xml in version control containing the credentials for the web application which happens to be an admin account! Lucky me, saved me at least two weeks of waiting to get admin access!
 4
4 -
Admin Access
Have you ever been in a position where you become the de-facto person who works with a certain tool, but are denied full admin access to that tool for no real reason?
Two years ago I was put on the Observability squad and quickly discovered it was my thing, implementing tracking and running queries on this third-party tool, building custom stuff to monitor our client-side successes and failures.
About a year ago I hit the point where if you asked anyone "Who is the go-to person for help/questions/queries/etc. for this tool", the answer was just me lol. It was nice to have that solid and clear role, but a year later, that's still the case, and I'm still not an admin on this platform. I've asked, in an extremely professional way armed with some pretty good reasons, but every time I'm given some lame non-answer that amounts to No.
As far as I'm aware, I'm the only dev on our team at all who uses custom/beta features on this site, but every time I want to use them I have to go find an admin and ask for an individual permission. Every time. At the end of 2020 it was happening once a month and it was so demoralizing hitting up people who never even log into this site to ask them to go out of their way to give me a new single permission.
People reach out to me frequently to request things I don't have the permissions to do, assuming I'm one of the 64 admins, but I have to DM someone else to actually do the thing.
At this point it feels very much like having to tug on the sleeve of a person taller than me to get what I need, and I'm out of ways to convince myself this isn't demoralizing. I know this is a pretty common thing in large companies, meaningless permissions protocols, and maybe it's because I came from IT originally that it's especially irritating. In IT you have admin access to everything and somehow nobody gets hurt lol-- It still blows my mind that software devs who make significantly more money and are considered "higher up" the chain (which i think is dumb btw) are given less trust when it comes to permissions.
Has anyone figured out a trick that works to convince someone to grant you access when you're getting stonewalled? Or maybe a story of this happening to you to distract me from my frustration?13 -
We gave admin access to a user who thinks he knows what he's doing. Why did we give admin access to a user who thinks he knows what he's doing?6
-
It took 2 fucking days for the network team to assign permission to my username to access 2 x dedicated servers on the network.
Like dude WTF, it's a 5 (max) minute job. I'm not judging just saying.2 -
I was never really fond of 2FA, mostly due to the pain in the ass it creates if you lose or can’t access the 2nd device or jumping between GAuth to access Password Manager to access a password to use a login 😱.
But when your phone prompts up with a “allow some Asian, access to you’re iCloud account” you feel a world of relief that you have:
1) a notification you’re account is no longer secure,
And,
2) an immediate ability to change passwords before any access is granted.
Now it’s 1 more password I no longer know due to it being a scrambled mess of characters.
PS: Fuck you, you low life shithead!9 -
So one rant reminded me of a situation I whent through like 10 years ago...
I'm not a dev but I do small programs from time to time...
One time I was hired to pass a phone book list from paper to a ms Access 97 database...
On my old laptop I could only add 3 to 5 records cause MS access doesn't clean after itself and would crash...
So I made an app (in vb6) , to easily make records, was fast, light and well tabbed.
But now I needed a form to edit the last record when I made a mistake...
Then I wanted a form to check all the records I made.
Well that gave me an idea and presented the software to the client... A cheesy price was agreed for my first freelance sell...
After a month making it perfect and knowing the problems the client would had I made a admin form to merge all the databases and check for each record if it would exist.... I knew the client would have problems to merge hundreds of databases....
When it was done... The client told me he didn't need the software anymore.... So I gave it to a friend to use as an client dabatase software... It was perfect for him.
One month later the client called me because he couldn't merge the databases...
I told him I was already working in a company. That my software was ready to solve his problem, but I got mad and deleted everything...
He had to pay almost 20 times more for a software company to make the same software but worst... Mine would merge and check all the databases in a folder... Their's had to pick one by one and didn't check for duplicates... So he had to pay even more for another program to delete duplicates...
That's why I didn't follow programming as a freelance... Lots of regrets today...
Could be working at home, instead had a burn out this week cause of overwork...
Sorry for the long rant.2 -
Worst technology I've ever worked with?
Microsoft-FUCKING-Access
The error riddled, varchar frenzy, disgusting ui, os and architecture dependent pieces of shit, powered by the cherry on top: fucking VBA, that are applications developed with this monstrosity have kept me awake trying to understand why on earth would anyone that is not dying of cancer already would use such thing to try to build anything.
I had to deal with load of Access applications when I first started at my current company. Whats left now are mainly legacy systems, I killed them one by one and whatever's left will suffer the same punishment.
If you develop in Access you're my enemy and I will destroy you.3 -
Our prof told us today in a zoom lecture: "Never visit b-ok.org, it is totally illegal", with emphasis on how he would NEVER recommend to visit that website for free education illegally.
I guess he is totally against the idea of pirating educational material12 -
Am I the only one who lets friends and relatives always browse on my computer on the OS-default browser like Safari or IE. So they don't disturb my precious tabs and log in Chrome? 😂5
-
3 hours of "I don't have access to that router" and waiting for someone who does have access to join the line. And then they don't have access, etc..
I love networking, hate working with network engineers. -
Why the fuck is this site blocked. How the fuck is it remotely adult content? ITS A GODDAMN WEBGL GAME. And you blocked is as being EDUCATIONAL. WHY THE FUCK WOULD MY SCOOL BAN A GODDAMN EDUCATIONAL WEBSITE?
P.S. for all those that know me, i made a website a year ago, during english class, and it got blocked at school (my goal was to get it blocked). Or so I thought. It turns out it didn't get blocked at my school, it was blocked across the whole county! I feel accomplished. 12
12 -
Fuuuuck this corporate bullshit. I'm basically sitting around twiddling my thumbs waiting for some jackass to grant me access to the server that my boss moved my code over to. Why the hell did you put my app on a production server that runs every 30 minutes...THAT I DON'T HAVE ACCESS TO?? Now there's a critical bug and a $50K order in limbo because I can't push any fixes. Fuck me. The worst part will be in the next hour or so when dozens of people are calling, emailing, and attacking my cubicle like rabid animals about why orders aren't moving and I'll have to explain that production is a train wreck because reasons. Just end me.2
-
Recently, my CS teacher proudly bragged about how, to this day, no pupil has ever had WiFi Access to the school network (only teachers have access).
What a naive teacher he is ( ͡° ͜ʖ ͡°)5 -
Fuck non-IT departments that use Microsoft Access and think database tables are like Excel spreadsheets.10
-
Big company issues: Try access something "access denied". Spend rest of day trying to figure out who can provide access to that page and what manager that needs to approve it :(2
-
So I started a 80hour intership today at our Department of Education and this is how it went...
Boss : Design a database to show all applicants that applied for jobs at schools.
*I start thinking which tables and columns I'm going to use and start designing the database, writes out all the tables on paper*
Me : Is there a pc I should work on or should I use my laptop? And which database engine do you use?
B : No you can use your laptop. And btw we use MS Access
*Thinking wtf kind of business even governmental uses Access for their databases. But anyway, start creating the databases and relationships when my boss walks in*
B : No, what are you doing?
M : Im creating the database you asked for.
B : No, you design it on paper. Draw all the tables, draw the report and the form then you come show it to me, if I decide its good enough you can come in tomorrow and start creating it.
*Wtf kind of place is this, are you mentally retarded? You have a IT staff of 3 people, in which only the actual fulltime intern is a qualified IT professional, but when me or him tries to do some actual work, you give us shit about doing what was asked from us*5 -
I'm migrating data from an old software to a new one I wrote.
Old database it's in Access (yeah, fuck). When I opened one table, the VM hung up and I opened the task manager on MADE
What.The.Fuck.Are.You.Doing? 8
8 -
Dev. policy: The use of SELECT * is forbidden.
Open Data Access Layer > first statement: SELECT * FROM bullshit_table4 -
PHB wanted access to our team chat room where we do standup, among other things. Access granted. Immediately a new chat room was created.
 2
2 -
"Google Home requires access to your location to find nearby devices"
Get fucked, Google.
Get. Fucked.14 -
Fuck this client's IT department. They're a bunch of Microsoft asslickers.
How am I supposed to push code to your self-hosted GitLab instance if you restrict me to Citrix RDP????? No OpenVPN access because I'm on Linux?? Seriously? Because I am not using any of your laptops?
FUCK YOU DUMBASSES, I COULD DO A BETTER JOB THAN YOU AND I JUST PLAY WITH LINUX.
When I said I only needed terminal access I would have never imagined they were thinking of Putty inside an RDP. What a steaming shit.
Oh you guys don't have a secret management service as any enterprise should? Oh I cannot add a secret management service as part of the solution I am building for you guys because "Hurr Durr yOu HaVe NoT pUt ThIs In ThE pRoJeCt PrOpOsAl sO nO"
Fuck you guys. You guys only don't want to move to the cloud to not lose your jobs. I would be far more productive than relying on you pieces of dumbassery.
They are all having each others back in using shit technology and practices.7 -
Helping this lady with her Microsoft Access work. Wrote some complex Visual Basic script to make the database look pretty. This is what she is asking:
"Hey, where did you get all this code from? YouTube? Can you please send me the link?"
ffs I'm a dev, why the fuck do you think I need YouTube for this simple VBA script.3 -
We use jira at my company. It's great for me, because no ticketing system's UI is worth a shit, but jira's API is excellent. But we're switching to a new system that is an absolute piece of garbage. Every page is 100% Javascript, so no source can ever be viewed, and the URL never changes to reflect what's onscreen. If you know a ticket number, no URL will ever get you straight to it. You have to navigate multiple slow-loading 25MB piles of Javascript to reach what you're seeking. And most damning of all: the new system has an API, but our highest management is withholding access to it, claiming it breeds laziness.
Is amazing the kind of shit you have to swallow when your management has regular meetings with really really super extremely good-looking sales people.10 -
I use a Mac that implements MAC using MAC and its got multiple hardware MACs along with a hardware MAC.... btw, I'm eating a Big Mac.
...
Media Access Control - Networking
Manditory Access Control - Security
Message Auth Code - Security
Mac - Apple
Multiply ACcumulate - Chip Design2 -
Normal peeps: I wasted time in that relationship
Me: I wasted time to fix "unable to access gitlab.com please check if you have access to the file" only to realize the site was down1 -
The amount of attempts to access my website is just too much O_O
Anyway in nginx to block access if login attempt failed after 3 times? 14
14 -
I'm going to spend the night with a rapidly flashing blue LED in my room.
I'm currently fixing an HDD, and the access LED is just going crazy. That's gonna be a long night.5 -
The Sys Admin limited everyone's access on an application through the admin panel. He forgot I have access to the database and I now have full access 😂1
-
Ready...
> access security
access: PERMISSION DENIED.
> access security grid
access: PERMISSION DENIED.
> access main security grid
access: PERMISSION DENIED...and...
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD!
YOU DIDN'T SAY THE MAGIC WORD! 3
3 -
MS Access and VBA.
This combo is the worst dev tech I had to use it by now. Why? Because even if you try it, you can't make a single line of clean code. The syntax is horrible, it still use GOTO...
Maybe the reason why I hated working with it is linked to the context too: I was (and still) developing a system using NoSQL database and this system should be mostly fully configurable through metadata within JSON documents and it was. But we were still writing every JSON by hands so we decided we needed to develop a web based utility for us and clients who would need to configure the system but one of the head decision making people said that we don't need to use fancy technologies (because NoSQL is already "fancy") and that the configuration tool will be develop with Access because he used it a lot when he was younger and when he was coding during its free time. He said that using Access would be much easier and much time saving than our "fancy web based solution" and that he could help if we had questions...
Developing a MS Access software is already a pain in the ass but when you need to output JSON with it...1 -
Whaaaat theeeee actual fuuuuuuuuck. So basically I've got a server running and everything is fine. All services are working and I can access the webserver running on it over every browser. But randomly my ssh access stopped working (can connect but doesn't return shit after last login message) and when loading the web config thingie from my provider it gives me an empty response (all other pages from the provider are working). So basically I've got a working server I cannot access. But I'd like to access it and cannot even restart that shitty thing.
Anybody else had a problem like that or has any idea wtf is going on?5 -
I have a Yahoo app on my phone for some legacy purposes. I just allowed the storage access permissions when it was asking for it during the installation or something, cause like, who doesn't? I checked my Yahoo Mail on the browser tonight and saw copies of my mobile photos in it! It's through the Attach Icon > Insert animated GIF. WTF? So that's how you can easily get hacked from apps?
-
I had to use XSS (cross site scripting) and tag injection to change one tiny CSS property on a bug tracker site where I have no actual file access and can only add custom footer text. Why not just give me file access, or at least some way to customise the CSS, you stupid thing!2
-
What the actual fuck GitHub/CircleCI?!??
I transformed a GitHub account into an organisation and lost admin access to a repo even though I'm the owner of the organisation. Now I can't even access the settings for the repo on CircleCI. What the hell? WHAT THE HELL?!!?! THE FUKKKKKKKKKKKk? -
Apparently someone posted on Apple's developer forum 2 weeks ago about this root privilege escalation vulenerability in macOS but it took a viral tweet to get any action. 😐1
-
can you solve the issue in production mentioned in this slack channel you don't have access to and we're not going to grant you access to?3
-
Several years ago, I heard from a friend who was doing assignments for students on the side. Quite a hustle. His story began when he wanted to figure out why can't these students be able to draw their own database tables, relationships, UML, etc. That's what school has to be teaching them and then he was told that they were learning through MS Access. He goes and tell me that even though this is a lame way of teaching database design, its definitely easier to explain through hands-on and less typing mistakes, as according to the lecturer he met. Making the explanation more visually appealing and helpful for understanding.
OK I get it, but somehow that taught them the wrong way of database design from the beginning. I'd prefer getting them to start writing SQL commands from day 1 and play em at some DB VM. Keep em as real as it gets.
Now I have my own students asking for help in their assignment and also asked for tutoring lessons in web development. So I gave them the crash course in HTML, CSS and Javascript. I've asked them if they've used anything of what I taught them in school. They go and tell me that they've been taught web development through Wordpress. Oh WTF!? I havn't talked to their lecturer yet but it better be a really good explanation to teach these youngsters in a flawed and bloated PHP CMS framework for "web development".2 -
Not really a rant and not very random. More like a very short story.
So I didn't write any rant regarding the whole Microsoft GitHub topic. I don't like to judge stuff quickly. I participated in few threads though.
Another thing is I also don't use GitHub very much apart from giving 🌟 to repos as a bookmark. Have one hobby project there. That's all. So I don't worry that much. I'm that selfish and self concerned. :3
I was first introduced to version control system by learning how to use tortoisesvn around 2008. We had a group project and one of the guys was an experienced and amazing programmer unlike the rest of us. He was doing commercial projects while we were at our 1st and 2nd year. Uni had svn repo server. He taught us about tortoisesvn. He also had Basecamp and taught us how to use it as well. So that's how I learned the benefits of using versioning tools and project management tools. On side note, our uni didn't teach any of those in detail :3
After that project, I was hooked to use versioning tools. So until school kicked me out, I was able to use their svn server. When I was on my own, I had to ask Google for help. I found a new world. There are still free svn services that I can use with certain limited functions. That's not the new world; I found people saying how git is better than svn in various ways. It was around 2010,2011.
At first I was a bit reluctant to touch git because of all the commands in terminal approach. But then I found that there is tortoisegit. I still thank tortoisesvn creator for that. I'm a sucker for GUI tools. So then I also have to pick which git servers to use. Hell yeah, self hosted gitlab is the way to go man. Well that's what the internet said. So I listened. I got it up and running after numerous trial and error. I used it briefly. Then I came back to my country on 2012-2013; the land of kilobytes per minute (yes not second, minute).
My country's internet was improved only after 2016. So from 2013 to 2016, I did my best not to rely on internet. I wasn't able to afford a server at my less than 10 people, 12ft*50ft office. So I had to find alternative to gitlab which preferably run on windows. Found bonobo and it was alright. It worked. Well had crazy moments here and there when the PC running Bonobo got virus and stuff. But we managed. We survived. Then finally multi national Telecom corporates came to our country.
We got cheaper and faster mobile data, broadband and fiber plans. Finally I can visit pornhub ... sorry github. Github is good. I like it. But that doesn't mean I should share my ugly mutated projects to the rest of the world. I could keep using Bonobo but it has risks. So I had to think for an alternative. I remembered that gitlab didn't have cloud hosting service when I checked them out in the past. So I just looked into Bitbucket and happy with their free plans of 5 users and unlimited private repos. I am very very cheap and broke.
That's why I said I don't really care that much about the whole M$GitHub topic at the beginning. However due to that topic, I have visited GitLab website again and found out they have cloud hosting now and their free plan is unlimited users and unlimited repos. So hell yeah. Sorry BB. I am gonna move to cheaper and wider land.
TL;DR : I am gonna move to GitLab because of their free plan.4 -
Had a teacher in high school who ordered us to learn MS Access, even tho most of us already knew MySQL... It was to learn about relations and the likes...
We spend way to long on that subject, because most of really didn't find the Access interface intuitive and she had to walk from table to table helping...
The only two finished the task where those who say screw it and used MySQL 😅 -
When customers pretend to really care about security but then share server folders to "everyone" 🤨1
-
Axiom of dev epiphanies: they always happen when you don't have immediate access to your workstation
-
I work in a large organization that previously didn't have it's own development team. Therefore various business areas have built their own solutions to solve problems which mostly involve Access and Excel.
Many of these applications still exist and we are expected to resolve any issues with them and update them when necessary performing this support role while still expected to meet our (very tight) development timelines.
I can't tell you how much of a pain in the tits it is to be trying to power through a priority development only to be interrupted with an urgent instruction to fix a 17 year old Access database that's running slow.
Of course it's pissing running slow, it's 17 years old, has nearly a million records and you have multiple users accessing it across the country!! I think it's time to peacefully let it die.6 -
A programme I have to maintain (and not allowed to optimise or change):
1) read input from serial connection
2) store data in MySQL database
3) every day convert to CSV
4) store on Windows file share
5) process CSV in access 2000
6) store in MsSQL database
When it was first developed, I said to te developer to store it straight from serial to MsSQL but out boss wanted it to follow the above spec.
He has now left and I have to maintain it1 -
Today I found out we have 5 different Customer databases, one for each product area. We don't have access to more than 2 of them, while corp. it central has full access, but we have to beg and pay to see our own customers....
Now i'm tasked with integrating all these into a Customer db. and the way i get access is cobolt made, fixed length csv files and it's different for each db.
FML1 -
Head of legal: email me details of the customer information you hold/access
Me (in head): I'm a full stack developer! I access everything!! Should I tell the truth, or "the TRUTH"3 -
This is my mom's phone (yes I have access..fingerprint access, she doesn't 😝).
I just cleaned it up.... And now gonna run an experiment.
Which Weather app will she use? (Actually on my Android phone I use DarkSky but it cost money) 😐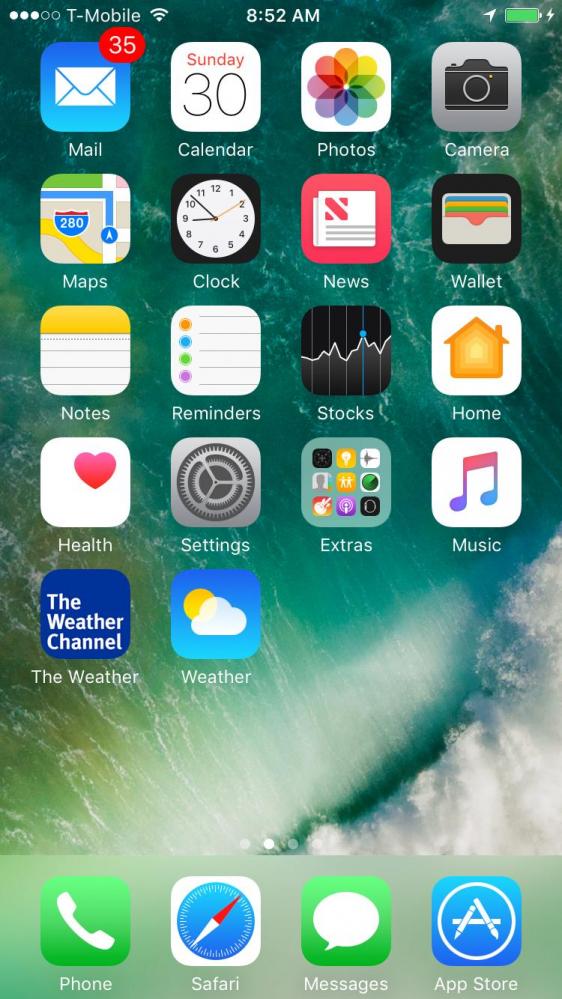 1
1 -
Firewall is down. That means no access to developer environments. That means more time for DevRant.1
-
!rant
Don't know if you guys have this kind of boxed up stuff inside like me. I have good friends, I have a good gf, I have great family and nice colleagues. But there are still so many things I don't share with them, especially the negative feelings I usually possess. Even here I don't share all the deep dark stuff.
As much as I wanna share my true identify and personal info here, the reason I'm restraining myself from doing so is this is the only place where I can say whatever really I wanna say in my mind. Except my blog but then my blog doesn't have any reader.5 -
To make matters even worse, my manager gave the horrible client also access to another clients environment just to 'compare' things, and nitpick over configuration that he is missing, but just hasn't setup yet...
Fucking fuck fuck fuck fuck fuck my manager, what a total 🌰🔩🥜nutjob5 -
Company sends email notifying us we'd need to register for two factor authentication because it would be mandatory for all access to email within a week. However, it had to get manager approval and had a side effect of giving us access to work from home (which my manager hates). So, we send the request to him, explain the situation, he denies it and says "that can't be right! Let's do this: if you do in fact lose access to email, then I'll approve it". Well, we did lose it, and just spent two days without any access to email and it was a huge pain to get the registration process done because one of its steps involved getting a validation code from the email.1
-
Thanks to @bittersweet I found and tried _Notes by Firefox_. An awesome app, wich I definitely will keep and use.
I love the markdown support.
I love the synchronisation.
I hope they will add access-controls, so I can give other users access to my notes.
Sry, for the advertisement.4 -
I have to maintain a system for a financial institution that only works with Windows XP and Ms Access 2003. All VBA code, security is handled using a workgroup file. Can't upgrade anything because client doesn't want to pay for it.
-
Gotta love the IoT.
They set up a new surveillance camera in the company, that can stream live footage over the network and that little shit picked the IP adress of a coworker one day AFTER being set up.
Hurray for static routing. Hurray to the person who didn't disable DHCP on the router (Should probably configure my PC to use a static IP as well lel)
Anyways, this happened outta nowhere when I, the only guy who knows shit about IT and is usually present at yhe office, wasn't there and could not connect remotely.
The other, remote programmer, who set up the network, could guide the coworker to get a new IP but, he was worried that we got ourselves an intruder.
Since nobody told me yet that we (should) have static routing, I thought there was a mastermind at work who could get into a network without a wifi-access point and spoof the coworker in order to access the some documents.
The adrenaline rush was real 😨
Scanning the network with nmap solved the mystery rather quickly but thought me that I need to set up a secure way to get remote access on the network.
I would appreciate some input on the set up I thought of:
A raspberry Pi connected to a vpn that runs ssh with pw auth disabled and the ssh port moved.
Would set up the vpn in a similar fashion. -
AWS is so secure that even with full access I cannot access the resource I need and the error message is so cryptic every hacker will give up first. Amazing!3
-
Code in index.php: if(!isset($_COCKIE['access'] == '123') {
echo 'Denied'; die;
}
And then there was the access.php which set the cookie.
So you had to go to foo.com/access.php which displayed a white page and set the cookie. Then navigate back to foo.com for access2 -
How MS Office came about:
In the office suite I think the top guys stayed for Excel. These guys, are so good. They build Access. But it was always after 6pm on saturdays.
The "I know stuff, and I'll figure things along the way" guys stayed with Word. And in their part time, developed Powerpoit.
Excel guys were so great, they also developed the WordArt and later the SmartArt for Word and Powerpoint!
Thats why we still have that awefull blue and red-wine colours as default...2 -
God damn it, if you (libGDX) have default values for public methods then make those constants public. Now I am writing wrapper and I either create my constant with same value as your private one, or do some reflection black magic which will probably break after obfuscation. *sigh* Going with my copy of the constant, not happy about that...
-
Got access to root access of school's lab computer.
Saw an account 'tee'(Term end exams) associated with it, copied the hash, ran a dictionary attack and the password was 'tee'
FUCCCKCKCKKK1 -
North Korea has blocked Internet access to Twitter, Facebook, and YouTube such a shame to the 3 people who have Internet access there
-
Sooo
Someone had that brilliant idea of changing user ID and group ID of root user in a server... Now root has no permissions.
How am I supposed to use that server now?
P.S: Don't ask me why they did that... I don't know and I didn't bother to ask.8 -
IT admins of devRant, explain my dumbass the following:
Why would an IT department put servers in a VPN without TLS.
They presume they don't need because muh-VPN.
And then they don't want to hand out VPN connections to anyone and force me to use Citrix RDP 🤡
I know there are security reasons, but is there not a better way? Like goteleport.com ?
Asking for a friend (or several)5 -
!rant but story
Didn't participate in this week rant since the topic is not very relatable to me.
I rarely get truly inspired. There are people I envy. There are things I like. There are moments I go, oh awesome. That's about it.
I doubt myself that I have little bits of narcissist and sociopath traits. Maybe I am. 🤔2 -
Currently modifing a old Excel VBA Application. Found code which try to parse a Textbox on every change. If its a valid Number, it saves the value into a label. When saving the form the label will be parsed and validated instead of the Textbox
-
!rant
Just had a meeting with a client. Client is a local company but they hired a new guy and he is a foreigner. They made a website with us. Since it is a typical corporate website with few pages and just text and images as content, we used WordPress.
The new guy is familiar with squarespace and asked me my opinion on using SS. I don't really find any issue and it was my reply. He seemed surprised and asked me "Wouldn't it be like losing your business?"
I have never considered developing WordPress as my business. Programming is my interest and profession. But my main passion is to provide solutions to anyone in need. In fact, there were many occasions where I told to clients they shouldn't buy our services and recommend other services including competitors.
He probably thinks I'm a strange guy. -
stupid react fucks, they upgraded webpack to 5 which breaks being able to access process.env
good thing you can't access the webpack config to fix it!
essentially this "wise decision" by the team makes this entire docs page WRONG: https://create-react-app.dev/docs/...21 -
Could access every website but github.com “all of a sudden”...exp stopped working npm was broken...macs are so stupid then.....
I dumbed....it was all my fault. </duh>
Yesterday I blocked my kids’ access to the internet .. and just blocked the IP4 access of my mac. What a genius. It appears github (and not other sites) requires IP4 whereas most now use IP6. -
My Ubuntu VM just work fine for consecutive 217 days without restarting.
Need to change some config
And... I forgot the application access key... Damnit!!!
Lucky, I kept the access key in the password manager. Whew.5 -
When people are thinking that just by deleting UIDAI number ,their phone is hack free now.🤣🤣
This are same people who installed app from SHAREit , access adult content without proxy n JavaScript off ,access raile net /public net and enter private information.🤣🤣2 -
Amateurs that think access is a proper enterprise database and everything should be done as a macro.2
-
We want to hire new dev, so, these MBA guys have a brilliant plan. Give him access to our complete repository and let him go through the full fucking code and *access it*. I don't even know what to explain here..
-
We've got two conflicting linters for ruby.
The rubocops serve the IDE and say to outdent access modifiers, giving the indented line a little yellow under-squiggle. Monkey see, monkey do, I indent it.
The company's one in the build pipeline wants to indent access modifiers and literally fails the bloody build, screaming about a rogue access modifier two spaces from where it should be.
Waste of 5 minutes.1 -
!rant
Showing a php and dual-boot guy the anti-php and anti-window posts might be an intentional algorithm. We never know. 💀 -
Does that look like a bug ? Or a feature ? It requires a considerable amount of time and effort to develop unattended remote access. How do these people develop such a feature as "mistake".
 4
4 -
Okay so after a few days of thinking I think I'm sure about what I'm about to write :
Best : Discovering how to use streams while making a service that should extract a tar.gz, extract the tar.gz within it, filter the extracted files and correct some of them, then compress each folder as tar.gz and compress all the archives as .zip. The amazing thing for me is that with streams I could do all the operations in just two passes, maybe one if I had more time, saving disk writing time.
Worst : upgrading a bunch of legacy Access 97 apps and its VBA code to Access 2013 -
I have some people trying to access to my accounts from far away.
I think my password have been leaked :|
f*ck6 -
I don't understand windows 10 "Quick Access" (when you open windows file manager). I open One very less used folder and it stays in quick access for approx. 10 days and I open my Project folder everyday, every hour, evry minute and every second, it doesn't shows up in quick access, and when sometimes does, it doesn't stays long.9
-
Windows has just asked me the password to my Microsoft account to fucking access my computer.
... Do you mean that if I didn't have Internet access I couldn't use my won fucking computer? WTFF!??24 -
Got an openai invite.
Funny thing it has been so long since I requested it, I no longer remember what I was gonna build.
I know some people who are better qualified and wanted access haven't been able to get access yet.
So, any suggestions?6 -
Set up .net core in CentOS 7.
I'm able to access `dotnet --info` but can't access `sudo dotnet --info`.
Provided I can't access root.2 -
People who freak out and think they have been hacked when you send a message to them on the prod server using the wall command should not be allowed SSH access.
-
IT teachers here at my school giving us 20 different and completely unsuitable for Access databases businesses, as subjects for indeed Access databases. And then be like "Create documentations for that"
And they actually mean by that is
So I clicked here then there and then I selected and pressed the C symbol key while holding the Control key on the keyboard input device connected on my computer, which happens to be plugged into the wall outlet..
As a full-stack developer this is just so cringy I'm speechless.. -
I genuinely have respect for people and their professions.
But . . . why the fuck are IT Support generally hard to deal with.
I don't fucking have access to a Service and I damn need access. Support immediately without checking says: no you do have access go to xyz find the service click on it bla bla bla.
Bitch, you think I didn't try all that and just felt like having a conversation with you?
wtf5 -
I have a question, let's say I have a website and app both using oAuth facebook login. Should I save the access token provided by facebook in my database and if I should, what will happen to the access token when user logins with facebook on website and then login again with the app? is that mean access token is going to be overwritten by new login? and do you have any other suggestions for 0auth integration?3
-
It took long enough for google to do something so basic.
So currently if you have provided mic or camera access to one of the apps, then it can also access those features while running in background.. 3
3 -
Accidentally pushed AWS IAM access and secret key to repository defined within application.yml file in code, immediately i got a mail from AWS warning me that my access and secret keys are now exposed with instructions how to rotate this key and secure it. How the fuck do they know?10
-
VPN access expired on Monday, can't access any client systems without it. Have to wait until weekend before access can be renewed.
God damn. One week, can't do anything effective! -
Person I am grading labelled “not having bugs” as their website feature... if it wasn’t 2018, I probably would say that’s a standard part of any website or software. Now... at least they’re not passing it off as early access.
-
My boss told me I have to update a ms access db that hasn't been touched since 2012... I know nothing about access or vb and I have no desire to learn that crap. But I leave for vacation on Friday so I just have to skate by until then.
-
Ha! Our Ops Support DBA Manager just asked (tongue in cheek) "if we are now supporting MS Access, too?" To which of course, the answer is no. Business user who install Access on their desktop and use it for business, get to provide their own support. As their Dev DBA, I'll be more than happy to help them migrate their data to SQL Server, Oracle, or Teradata, depending on the Use Case for the data. But, no, we don't support Access. Ever.
-
Inconsistent, legacy access databases might just be a tad worse than excel sheets.
Not sure if to end myself or the author...1 -
Having to work with a legacy system is often hard enough, adding New features content when it's a ancient access system is worse. Secretly started remaking the entire CRM system in .net instead of stabbing myself with a plastic fork to get out of the project.1
-
Seriously getting pissed off with Google. Why the fuck is it not clear or easy to link your app with a business listing to get access to the api. After searching I finally found it.
I just filled out a form to request access and it could take 2 weeks. -
Had to call an API with SOAP, convert an Access Database to MySQL, Coded some classic ASP and used Campaign Monitor for the first time in god knows when. That's a royal flush of retro right there!
-
client: "I cannot access the app"
me: "How? Can't install app? Can't login? Any error messages?"
client: Sends picture, one of the screens shows error
I really don't understand some users. How does one connect the dots between "cannot access" and "screen error". -
I'm currently using team viewer to access a computer of a colleague because only they have access to a vpn I need. So once I'm on the VPN I can then ssh into a ec2 instance. There are several ec2s I need to access but I've only been given direct access to one. Once inside that ec2 I can use it to ssh into the other ec2s....
Dawg..... why
Life isn't supposed to be this hard2 -
I have never encountered a better wrapper for graphical remote access than remmina. I have yet to find one for Mac that I really like, and I haven't found one for Windows that I like at all.
I have used chicken and finder's built-in client, but neither particularly impress me. Do you have one for Mac that you swear by?4 -
Hi, so currently in my Java course, I'm learning about abstract classes. I noticed how a method in an abstract class can use an access modifier, however, interfaces don't use them.
In addition to this, I noticed that IntelliJ didn't give me an error stating that adding an access modifier was redundant or useless. So I wanted to know if there is a point in adding access modifiers to abstract methods.
Thanks so much for anyone who can help me out with this!1 -
me: can you help me debug this issue in our artifactory server?
ops: we don't manage that server. devs do
me: can I get access to manage that server?
ops: why would you need access??
me: to manage server ಠ_ಠ
ops: exactly what commands you will need?
me: ಠ_ಠ -
Does anyone know if there a way to use 'wifi calling' on your computer, not just on phones?
Also known as:
Generic Access Network
Or
Unlicensed Mobile Access
I would love to use a raspberry pi zero w with wifi calling, so i get away from normal mobiles8 -
Me, an apprentice, got to contribute towards a project for the business.
I only have access to the git of that particular project, no access to the other projects, databases or sourcecodes.
Thing is, we basically have to redo an old programm to access and work with the database, so having access to the sourcecode of that or access to the database would be very very helpful.
I have to guess the attributenames of the tables and what the code looked like that assembled all the data together for the overview.
I feel incredibly unprepared for this. -
What can you do if your boss is basically refusing to give you access to a server that you need access to to do your job? It's really weird to me. Only he has access to any prod systems we have. Is this realistic? Is this more of an attempt at staying necessary and needed? I'm pretty fed up with it as I've had prod access at every other company I've worked for and have nearly ten years of web experience .. what gives?10
-
Recently I had a task from my university to build some DB with forms using MS Access.
Despite of me constantly thinking that I wold accomplish this using Python+SQLite+Some GUI much faster, I've completed.
And I've got only one question left: why the hell proprietary product with giant company behind has such a terrible UX?
It' really painful to use. -
The college's Dean of Projects, when evaluating my first year project, which was using blockchains.
DoP: "So, we have this cool cloud system, incase you need to mine or something, come contact me and I'll give you access."
ME: "Sir, this project is distributed and uses computers in a network to protect data, it is not cryptocurrency."
DoP: "Yes, I understand, but we have this system here that can mine a lot, I overheard one of my staff talk about how we were wasting money by not using the system to do such stuff."
ME: "Sure, I'll have it setup to mine some altcoin then."
DoP: "Yeah, well I don't know anything about this stuff, can you do it all, yourself. I'll give you Admin access"
ME AFTER GETTING ADMIN ACCESS
"HOLLY F#@%*! Now I know where these sites are hosted!"
NOTE: I know that every other college has this problem, but the staff is the least innocent. -
I discovered you could edit the Visual Basic code in MS Access. I would read the code that was in there and figure out how i could extend it to do what i want. first code i ever wrote was a switch statement to control whether a set of buttons were enabled based on a dropdown value.
-
!rant
My patch to a BBC Micro emulator to allow passthrough access to the host's IDE interface seems to work. Now I can try and program a BBC Micro to access CD-ROM drives 😃
Also, BrewDog order arriving tomorrow 🍺😃1 -
Skein: noun - a type of access modifier, allowing a property to be read internally or externally, but only written to *externally*. See "orwell" for opposite access modifier.
hermit (noun) - an access modifier specifying a property may only be written or read internally.
Gopher (noun) - an access modifier not to be confused with a groundhog.
Blackhole (noun) - can be written to, can never be read. See dev/null for details.
In other news I wrote the basis for a cms in lua.
Because I hate the cloud. -
Forgets mysql password.. hits random common used words got access..
exits..
try to access mysql again and still dont remember which password i used..
.. No forget password option :( -
Today I went to a website, and it forces every visitor to do CAPTCHA to get access to the website content. It takes me 5 times doing CAPTCHA just to get access to the website. The same happened in the morning.
Am I stupid?11 -
when i create a jwt access token and if im using a refresh token
this access token expires every 15 min
am i supposed to code a whole separate route in the backend api for the refresh token so i can make a request to the whole route to trigger the refresh token and generate a new access token?
or should the backend automatically trigger refresh token whenever it receives a request and realizes the access token has expired?3 -
A guy who thought the only way to access data was through a relational data base and the only way to access a data base from java was JPA
-
What is the reason behind Git Access Tokens being viewable only once after generation on platforms like GitHub? I'm struggling to comprehend this approach as it compels me to store the key in an insecure manner.2
-
!rant
I am currently making a MS Access DB for my soon to be former workplace (compulsory social service) with a GUI.
It's a project administration DB with Schools, Projects, Plans, etc. I am making it because they used Access like a Excel spreadsheet.
How much would you demand per hour?7 -
Passwordless Unix login leading to a console menu. You can then FTP in for free and remove ~/.login . Boom ! Shell access! And I already had a superuser access from another "dialog" asking to confirm a dangerous action with the superuser's password. Boom! Root access !!
-
I was in my class on Thursday around 12 PM noon Indian standard time.
I couldn't access github on mobile (connection refused error) but at 2 pm once I was out of class could access it.
Any guesses if it was related to recent ddos attack on dyn ?
Location: India2 -
I cannot access one of production machines from home while behind VPN. I wrote to support that I need to access it right now and stated this is very urgent. They changed priority form high to low... access will be granted withing 2 weeks....1
-
When you open an access db in visual studio so you can do sql querys with out the annoying access interface and then i realize visual studio uses the same interface as access except its worse *-*3
-
During a conference call...
Client: How do we approach this issue?
Me: Reverting changes must be done on the business side-
Manager: But we can do it.
Me: Sir, I have no access for that process, only clients have that kind of access.
Manager: How can you revert changes if you don't have access?!?!?!
Me: ..... -
If someone is proud about using Alpha Five Software for developing... You just upgraded from MS Access to MS Access++... And you suck...
Go and learn some serious PL's and tools...1 -
VMware 6.5 web GUI programmer fail. Probably forgot to access a specific name property of the object.
 2
2 -
Fighting for an hour explaining how a query wouldn't return the data he wanted...turns out it did...but really not sure how... FU Access!
-
About to rewrite a module of our in house ERP app written in access as a web app to demonstrate to management that access is in the past. Fingers crossed this goes to plan managed to wangle this with the wife(thank god she believes in me)
-
Here is the REST API design of my LEAD programmer
# Access the API
1. Get access token with out username and password (GET /token)
2. Sign in with username, password and add access token as query param (POST /user/auth?token=[access_token]
3. Call other resources by adding token as query param
# Create new objects
- He uses PUT method in every resources to create new objects4 -
Anybody uses DigitalOcean Kubernetes? Having some issues with certificates expiring, and can't access the nodes :/1
-
II encountered this problem today with a user who couldn't access internet on their own home network or on their company. Everytime they try to access the site. Firewall and Anti-virus settings have blocked the access . Couldn't remote into their PC due to them not being on the domain to setup the VPN client. Reset Browser settings and disabled all Firewall and Anti-virus protocols. User still could not get to any sites..... What did I miss?1
-
I am not sure what's wrong but from this evening I can only access Google's sites + some other site using my WiFi but can't access devRant + other tons of site
Tried to reset the router, tried changing the DNS addresses, tried using VPN but nothing worked2 -
Quick question. I'm currently working on a project that requires extensive activity logging. What do you recommend for some sort of monitoring and logging of user access on a Linux box?
Big thanks in advance. <34 -
just found out that on `touchend` event you access touch in `event.changedTouches` and not `event.touches`! ☺

-
I need to refresh my Access Token from Flutter app. Should I use token expiry field from Access Token or attempt a request and if get 401 and some error from auth0, refresh token and try again?5
-
Today was the first time, that Git saved my ass.
I'm building an MS Access DB with fronted and apparently I fucked up while working on some FS stuff and corrupted the fronted-db.
Luckily, I sync my changes regularly to a git-repo so I just took my last backup and applied all changes that happened in between. -
Bwhahahah! Even after the excitement, business disruption, unpleasantness and pain, GDPR fails at its one job
https://newstatesman.com/science-te...1 -
I may need some ideas for a personal project in mind:
I plan to have a server that shall connect to a usb stick/device, the usb is plugged to a TV. The usb device can create its own local wifi network which provides CRUD on media files via REST. My own server should be accessible via the internet, but at the same time connect to the local usb wifi, once the usb wifi is available, and then send requests to it. Kind of a user-friendly bridge.
There's a PC near the device, almost always turned on. It's used by family members as regular office machine and could run a local server. What if as remotely accessible server? Then what about DOS attacks? (Would that "kill" the PC?)
An alternative would be a separate server. A raspberry pi? A dedicated server?1