Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "protected"
-
So I went for interview today.
.
.
Interviewer : Can u give some theory test about php?
Me : Sir, Can u please open your site?
Interviewer: sure 🙂
Me : Sir, I just logged in as Owner of ur company, Your site is not protected from sql injection.
Interviewer : 😌😌
Me : Sir, test?? 😜
xxxxxxxxxxx -------------------- xxxxxxxxx20 -
Unpopular opinion about Microsoft buying GitHub.
Just putting it out there that when you made your github repos you did so under their privacy policy and terms and will be protected under those in the future, and that both GitHub and Microsoft are corporations with the goals of making money.
Are people seriously mad that their code has gone from one capitalist corporation to another, with no foreseeable change in privacy or data policy? I have respect for those that switched to self hosted long ago since that's going from corporate to private, but if you throw away the UX and community GitHub has developed because a multinational corporation (with so many branches, products and divisions, which happens to have a few products you don't like) will soon own it, are you actually making a rational, guided decision?
Also just throwing it out there that GitLab is also a company. They've also had issues with keeping data intact in the past. They do, however, have free private repos (although I can't ever trust someone who gives me "free" privacy) as well as builtin CI. There are some definite upsides to it, although the UX has a ton of differences. If you're expecting the same dashboard and workflow you've used on GitHub, don't, GitLab has cool features but the bells and whistles aren't the exact same.
If you're switching to GitLab solely because of Microsoft, step back and think, regardless of how popular it might make you to hate Microsoft, is it really worth changing your development ecosystem to go from one corporate entity to another solely because you don't like the company?
I use GitLab and GitBub as well as Bitbucket and selfhosted git on a daily basis. They each have their upsides and downsides; but I think switching from one to the other solely because of Microsoft is not only totally irrational, but really makes light of/disrespects the amazing tools and UX the teams behind each one have carefully developed. Pick your Git hosting based on features and what works out for your use case, not because of which corporate overlord has their name plastered on it.
(Also just throwing it out there that lots of devs love VS Code, and that's Microsoft owned too... They did also build and pioneer a bunch of really cool shit for devs including Typescript so it's not like they're evil or incapable in any sense?)11 -
Short story time.
The last girl I dated was a proper geek. Like the kind of geek another geek wants. So one fine day she told me that she was making a greeting card for me. I was happy. After a few weeks she gave me the card and it was really cute. I loved it.
I reached home and received an email from her with a link in it. It was the link to a website she had made where each message from the card was deciphered to the real message.
DAAAAMNNN😱😱
That wasn't all. She didn't want the entire thing to be too easy. So the deciphered messages were password protected and I had to guess it.20 -
We've password protected a file and forgot the password we need it cracking asap.
Sorry we can't crack passwords on files.
If we don't get access to the file it'll cost the company up to 250k.
Well you should've thought about that before encrypting the fucking file with 256 bit encryption.8 -
We're using a ticket system at work that a local company wrote specifically for IT-support companies. It's missing so many (to us) essential features that they flat out ignored the feature requests for. I started dissecting their front-end code to find ways to get the site to do what we want and find a lot of ugly code.
Stuff like if(!confirm("blablabla") == false) and whole JavaScript libraries just to perform one task in one page that are loaded on every page you visit, complaining in the js console that they are loaded in the wrong order. It also uses a websocket on a completely arbitrary port making it impossible to work with it if you are on a restricted wifi. They flat out lie about their customers not wanting an offline app even though their communications platform on which they got asked this question once again got swarmed with big customers disagreeing as the mobile perofrmance and design of the mobile webpage is just atrocious.
So i dig farther and farthee adding all the features we want into a userscript with a beat little 'custom namespace' i make pretty good progress until i find a site that does asynchronous loading of its subpages all of a sudden. They never do that anywhere else. Injecting code into the overcomolicated jQuery mess that they call code is impossible to me, so i track changes via a mutationObserver (awesome stuff for userscripts, never heard of it before) and get that running too.
The userscript got such a volume of functions in such a short time that my boss even used it to demonstrate to them what we want and asked them why they couldn't do it in a reasonable timeframe.
All in all I'm pretty proud if the script, but i hate that software companies that write such a mess of code in different coding styles all over the place even get a foot into the door.
And that's just the code part: They very veeeery often just break stuff in updates that then require multiple hotfixes throughout the day after we complain about it. These errors even go so far to break functionality completely or just throw 500s in our face. It really gives you the impression that they are not testing that thing at all.
And the worst: They actively encourage their trainees to write as much code as possible to get paid more than their contract says, so of course they just break stuff all the time to write as much as possible.
Where did i get that information you ask? They state it on ther fucking career page!
We also have reverse proxy in front of that page that manages the HTTPS encryption and Let's Encrypt renewal. Guess what: They internally check if the certificate on the machine is valid and the system refuses to work if it isn't. How do you upload a certificate to the system you asked? You don't! You have to mail it to them for them to SSH into the system and install it manually. When will that be possible you ask? SOON™.
At least after a while i got them to just disable the 'feature'.
While we are at 'features' (sorry for the bad structure): They have this genius 'smart redirect' feature that is supposed to throw you right back where you were once you're done editing something. Brilliant idea, how do they do it? Using a callback libk like everyone else? Noooo. A serverside database entry that only gets correctly updated half of the time. So while multitasking in multiple tabs because the performance of that thing almost forces you to makes it a whole lot worse you are not protected from it if you don't. Example: you did work on ticket A and save that. You get redirected to ticket B you worked on this morning even though its fucking 5 o' clock in the evening. So of course you get confused over wherever you selected the right ticket to begin with. So you have to check that almost everytime.
Alright, rant over.
Let's see if i beed to make another one after their big 'all feature requests on hold, UI redesign, everything will be fixed and much better'-update.5 -
Motherfucker. It's two thousand fucking seventeen. You can get a free ssl certificate for any website.
Then WHY are there still some fucking websites which contain login portals, sensitive information or anything that SHOULD be protected in transit WITHOUT FUCKING SSL?!
I hope that the people who manage those sites and are AWARE that they can get a free cert but don't do that die in agonising pain.
This really fucking pisses me off.
On another note, EVERY site should have SSL, it's free anyways and protects your visitors from a range of threats.-24 -
Conversation between some kind of executives on the table next to mine:
A: do you know this app that'll let you hack into any Wi-Fi? You just click here, copy that and paste it here... and I hacked the restaurant's Wi-Fi. **laughs**
B: oh, only X? Bought. Wait... what is this "allow app to access your location"?
A: yeah, click "allow". You should also install a VPN.
B: what? BPN?
A: no, no. VPN. When you use a VPN you have a secure internet connection. You're protected from tracking, hacking and virus.4 -
Navy story time again.
I was a cadet, 1st year, final exams in """CS""". Our """professor""" was handing out the exam sheets, when I told him that one of the questions couldn't be answered by what he had taught. He had supposedly taught us C++ (I would insult every C++ tutorial, however shitty, if I called his class introductory or even elemental).
To give you a better idea of the situation, I'll only say this: one of the questions was "Name three brands of antivirus software."
I. SHIT. YOU. NOT.
This was supposed to be a Naval Academy that trained officers, by the way. Anyway, the question at hand was a program that must use recursion to solve a particular problem. I had been studying programming since high school, so I was not bothered by it, but everyone else was. Anyway...
Once I told him that, he threw a fucking fit. He screamed (as our overseeing officer watched in confusion) that we weren't paying attention, that we were just playing around and watching porn sites (BTW I discovered after that, that most porn videos were on the campus server, in write-protected folders that no student had permission to write, but professors and administrators did. Curious... but my ITSec misdeeds are for another day). Anyway, I got so angry at that idiot, I started writing (yes, programming on paper, if you whine about your IDE/text editor, think about that) the program. Until I found out that I didn't know WTF I was writing. The time was up, however, and I had to give my paper. To this day I have no idea what I wrote and what it did (if anything).
Got perfect score. Only one in class.8 -
Apparently this little music player has no transmitter, receiver, microphone nor camera, pity on you NSA!
 12
12 -
In may this year, the new mass surveillance law in the Netherlands went into effect. Loads of people were against it with the arguments that everyone's privacy was not protected well enough, data gathered through dragnet surveillance might not be discarded quickly after the target data was filtered out and the dragnet surveillance wouldn't be that 'targeted'.
They were put into the 'paranoid' corner mostly and to assure enough support/votes, it was promised that:
- dragnet surveillance would be done as targeted as possible.
- target data would be filtered out soon and data of non-targets would be discarded automatically by systems designed for that (which would have to be out in place ASAP).
- data of non-targets would NOT be analyzed as that would be a major privacy breach.
- dragnet surveillance could only be done if enough proof would be delivered and if the urgency could justify the actions.
A month ago it was already revealed that there has been a relatively (in this context) high amount of cases where special measures (dragnet surveillance/non-target hacking to get to targets and so on) were used when/while there wasn't enough proof or the measures did not justify the urgency.
Privacy activists were anything but happy but this could be improved and the guarantees which were given to assure privacy of innocent people were in place according to the politicians... we'll see how this goes..
Today it was revealed that:
-there are no systems in place for automatic data discarding (data of innocent civilians) and there are hardly any protocols for how to handle not-needed or non-target data.
- in real life, the 'as targeted dragnet as possible' isn't really as targeted as possible. There aren't any/much checks in place to assure that the dragnets are aimed as targeted as possible.
- there isn't really any data filtering which filters out non-targers, mostly everything is analyzed.
Dear Dutch government and intelligence agency; not so kindly to fuck yourself.
Hardly any of the promised checks which made that this law could go through are actually in place (yet).
Fuck you.28 -
Well, here's the OS rant I promised. Also apologies for no blog posts the past few weeks, working on one but I want to have all the information correct and time isn't my best friend right now :/
Anyways, let's talk about operating systems. They serve a purpose which is the goal which the user has.
So, as everyone says (or, loads of people), every system is good for a purpose and you can't call the mainstream systems shit because they all have their use.
Last part is true (that they all have their use) but defining a good system is up to an individual. So, a system which I'd be able to call good, had at least the following 'features':
- it gives the user freedom. If someone just wants to use it for emailing and webbrowsing, fair enough. If someone wants to produce music on it, fair enough. If someone wants to rebuild the entire system to suit their needs, fair enough. If someone wants to check the source code to see what's actually running on their hardware, fair enough. It should be up to the user to decide what they want to/can do and not up to the maker of that system.
- it tries it's best to keep the security/privacy of its users protected. Meaning, by default, no calling home, no integrating users within mass surveillance programs and no unnecessary data collection.
- Open. Especially in an age of mass surveillance, it's very important that one has the option to check the underlying code for vulnerabilities/backdoors. Can everyone do that, nope. But that doesn't mean that the option shouldn't be there because it's also about transparency so you don't HAVE to trust a software vendor on their blue eyes.
- stability. A system should be stable enough for home users to use. For people who like to tweak around? Also, but tweaking *can* lead to instability and crashes, that's not the systems' responsibility.
Especially the security and privacy AND open parts are why I wouldn't ever voluntarily (if my job would depend on it, sure, I kinda need money to stay alive so I'll take that) use windows or macos. Sure, apple seems to care about user privacy way more than other vendors but as long as nobody can verify that through source code, no offense, I won't believe a thing they say about that because no one can technically verify it anyways.
Some people have told me that Linux is hard to use for new/(highly) a-technical people but looking at my own family and friends who adapted fast as hell and don't want to go back to windows now (and mac, for that matter), I highly doubt that. Sure, they'll have to learn something new. But that was also the case when they started to use any other system for the first time. Possibly try a different distro if one doesn't fit?
Problems - sometimes hard to solve on Linux, no doubt about that. But, at least its open. Meaning that someone can dive in as deep as possible/necessary to solve the problem. That's something which is very difficult with closed systems.
The best example in this case for me (don't remember how I did it by the way) was when I mounted a network drive at boot on windows and Linux (two systems using the same webDav drive). I changed the authentication and both systems weren't in for booting anymore. Hours of searching how to unfuck this on windows - I ended up reinstalling it because I just couldn't find a solution.
On linux, i found some article quite quickly telling to remove the entry for the webdav thingy from fstab. Booted into a root recovery shell, chrooted to the harddrive, removed the entry in fstab and rebooted. BAM. Everything worked again.
So yeah, that's my view on this, I guess ;P30 -
A group of Security researchers has officially fucked hardware-level Intel botnet officially branded as "Intel Management Engine" they did so by gathering it all the autism they were able to get from StackOverflow mods... though they officially call it a Buffer Overflow.
On Wednesday, in a presentation at Black Hat Europe, Positive Technologies security researchers Mark Ermolov and Maxim Goryachy plan to explain the firmware flaws they found in Intel Management Engine 11, along with a warning that vendor patches for the vulnerability may not be enough.
Two weeks ago, the pair received thanks from Intel for working with the company to disclose the bugs responsibility. At the time, Chipzilla published 10 vulnerability notices affecting its Management Engine (ME), Server Platform Services (SPS), and Trusted Execution Engine (TXE).
The Intel Management Engine, which resides in the Platform Controller Hub, is a coprocessor that powers the company's vPro administrative features across a variety of chip families. It has its own OS, MINIX 3, a Unix-like operating system that runs at a level below the kernel of the device's main operating system.
It's a computer designed to monitor your computer. In that position, it has access to most of the processes and data on the main CPU. For admins, it can be useful for managing fleets of PCs; it's equally appealing to hackers for what Positive Technologies has dubbed "God mode."
The flaws cited by Intel could let an attacker run arbitrary code on affected hardware that wouldn't be visible to the user or the main operating system. Fears of such an attack led Chipzilla to implement an off switch, to comply with the NSA-developed IT security program called HAP.
But having identified this switch earlier this year, Ermolov and Goryachy contend it fails to protect against the bugs identified in three of the ten disclosures: CVE-2017-5705, CVE-2017-5706, and CVE-2017-5707.
The duo say they found a locally exploitable stack buffer overflow that allows the execution of unsigned code on any device with Intel ME 11, even if the device is turned off or protected by security software.
For more of the complete story go here:
https://blackhat.com/eu-17/...
https://theregister.co.uk/2017/12/...
I post mostly daily news, commentaries and such on my site for anyone that wish to drop by there 19
19 -
In my new neighborhood I found this WiFi network which has been protected for so long by just its name "Virus".
Am sure the owner never thought of geeks who instead of running away from" virus" just get closer.
Am ranting using "virus" network7 -
Disclaimer: kinda non dev related. Just working to pay the bills right now.
The other day I ran for the train to work, don't want to be fucking late, right?
Arrived and this guy asked me this: (I have a sweating/transpiration problem but I'm fully aware of that)
"hey man, ever heard of fucking showers or deodorant?!"
Yes, I was sweating my ass off and you could smell me but I can't FUCKING help that.
It was very embarrassing and humiliating to get that kinda comment in front of like 30 people but I just swallowed it and went to work.
After the first break, a woman from management came to me and pulled me aside. A few people had complained about how that guy from before said some pretty humiliating stuff to me and she said that the guy received a warning and was told to fucking learn to treat people with respect, regardless of their (health) issues/appearance. I also got an apology and a sorry and if I could keep my eyes open for such behaviour in the future.
I'm very glad that she apologized although it wasn't her fault because I know I've got this health issue and I can't do anything about it yet but it can MOTHERFUCKING hurt when someone talks shit about me when I smell and I CAN'T FUCKING HELP IT BECAUSE THIS IS THE WAY MY BODY WORKS TOO BADLY.
I felt protected and safe about my issue for the first time in my life.
Thanks management!14 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
How to advertise... uhm... not the right way!
The 'beschermd tegen anti-ddos' literally translates to 'protected against anti-ddos'
So then I can DdoS the living shit out of that those services and will be protected against the anti DdoS stuff....?! 🤣 9
9 -
I think I’m starting to really take pride in giving clients longer development times than I think will be needed.
The rule of doubling the time you think it would actually take, plus adding just a little more has protected me so many times...
Don’t be a yes man/woman...7 -
LISTEN UP! This is a robbery 🔫👺. We wanna harm no one. We're after devRant's 500++ - not yours. Your 500++ is protected by dfox. You're not gonna loose a stress ball. Think about your code. Don't try be a hero. Now shut up, and stay down. And this will be over in no time!9
-
!Story
The day I became the 400 pound Chinese hacker 4chan.
I built this front-end solution for a client (but behind a back end login), and we get on the line with some fancy European team who will handle penetration testing for the client as we are nearing dev completion.
They seem... pretty confident in themselves, and pretty disrespectful to the LAMP environment, and make the client worry even though it's behind a login the project is still vulnerable. No idea why the client hired an uppity .NET house to test a LAMP app. I don't even bother asking these questions anymore...
And worse, they insist we allow them to scrape for vulnerabilities BEHIND the server side login. As though a user was already compromised.
So, I know I want to fuck with them. and I sit around and smoke some weed and just let this issue marinate around in my crazy ass brain for a bit. Trying to think of a way I can obfuscate all this localStorage and what it's doing... And then, inspiration strikes.
I know this library for compressing JSON. I only use it when localStorage space gets tight, and this project was only storing a few k to localStorage... so compression was unnecessary, but what the hell. Problem: it would be obvious from exposed source that it was being called.
After a little more thought, I decide to override the addslashes and stripslashes functions and to do the compression/decompression from within those overrides.
I then minify the whole thing and stash it in the minified jquery file.
So, what LOOKS from exposed client side code to be a simple addslashes ends up compressing the JSON before putting it in localStorage. And what LOOKS like a stripslashes decompresses.
Now, the compression does some bit math that frankly is over my head, but the practical result is if you output the data compressed, it looks like mandarin and random characters. As a result, everything that can be seen in dev tools looks like the image.
So we GIVE the penetration team login credentials... they log in and start trying to crack it.
I sit and wait. Grinning as fuck.
Not even an hour goes by and they call an emergency meeting. I can barely contain laughter.
We get my PM and me and then several guys from their team on the line. They share screen and show the dev tools.
"We think you may have been compromised by a Chinese hacker!"
I mute and then die my ass off. Holy shit this is maybe the best thing I've ever done.
My PM, who has seen me use the JSON compression technique before and knows exactly whats up starts telling them about it so they don't freak out. And finally I unmute and manage a, "Guys... I'm standing right here." between gasped laughter.
If only it was more common to use video in these calls because I WISH I could have seen their faces.
Anyway, they calmed their attitude down, we told them how to decompress the localStorage, and then they still didn't find jack shit because i'm a fucking badass and even after we gave them keys to the login and gave them keys to my secret localStorage it only led to AWS Cognito protected async calls.
Anyway, that's the story of how I became a "Chinese hacker" and made a room full of penetration testers look like morons with a (reasonably) simple JS trick. 9
9 -
3 hours of productive coding in the morning then 8 hours of swearing, cursing, searching stack overflow, reinstalling eclipse and git only to realize in the end I was trying to push into a "protected" branch...
Why? because i'm stupid...5 -
-made a password-protected zip to backup my homedir
-launch the update to Fedora 28
-oh look Jessica Jones season 2 is available on Netflix
...
Some hours later
-Fedora 28 boots
-copy back my backup.zip
-shit what's the password already
-proceed to bruteforce the zip
-let's go back to Netflix while it's doing the job
...
Some hours later
-password: test
-proceed to self-fuck4 -
When /admin is protected by nothing more then:
var admin = false;
If(!admin){
setTimeout( function(){
window.location.href = "/home"
}, 1000);
}
My favourite to ever stumble on and dred going through hundreds of files to actually fix😣4 -
Me: Do u have antivirus Software installed That could possibly Blockade the Data for our Software.
Customer: Yes My computer is very safe i use 3 antiviruses.
Me: At the Same time?
Customer: Yes so My computer is better protected
Me: says no more
True Story just happend 10 minutes ago xD Had a good laugh with My coworkers16 -
I've got a confession to make.
A while ago I refurbished this old laptop for someone, and ended up installing Bodhi on it. While I was installing it however, I did have some wicked thoughts..
What if I could ensure that the system remains up-to-date by running an updater script in a daily cron job? That may cause the system to go unstable, but at least it'd be up-to-date. Windows Update for Linux.
What if I could ensure that the system remains protected from malware by periodically logging into it and checking up, and siphoning out potential malware code? The network proximity that's required for direct communication could be achieved by offering them free access to one of my VPN servers, in the name of security or something like that. Permanent remote access, in the name of security. I'm not sure if Windows has this.
What if I could ensure that the system remains in good integrity by disabling the user from accessing root privileges, and having them ask me when they want to install a piece of software? That'd make the system quite secure, with the only penetration surface now being kernel exploits. But it'd significantly limit what my target user could do with their own machine.
At the end I ended up discarding all of these thoughts, because it'd be too much work to implement and maintain, and it'd be really non-ethical. I felt filthy from even thinking about these things. But the advantages of something like this - especially automated updates, which are a real issue on my servers where I tend to forget to apply them within a couple of weeks - can't just be disregarded. Perhaps Microsoft is on to something?11 -
So it turns out that the company I work for uses and develops for Linux just because, I quote, "IT'S IMMUNE TO VIRUSES!!!".
Even if our systems are not connected to the internet (and never will be) and protected by armed guards.
I am stunned.5 -
What the fuck has one of my clients been up to?! Every request he makes he suggests we might want to do it via a function.
"We need to ensure this is password protected. Maybe wrap the calls in a function."
I wander if he goes into the bakery and says, "I need a loaf of bread---use flour."
All I can think of is that someone influential in his life is an FP zealot and he's latched onto this word.
But, I quite like FP. Maybe I'll refactor everything to static classes to meet the requirement.
Hope to Christ he doesn't find out about HTML, etc. "Maybe add a CSS rule."8 -
Some time ago I quit my job at a big corporation. Getting treated like a resource, a production line robot, just isn't for me.
My current job is way better. Small company, lots of freedom, getting to work on multiple projects, the result counts. But, as a small company, we also collaborate with big corporations. So I joined a team at one.
Watching my coworkers there, I'm reminded of robots again. Lunch break? 15 minutes tops. Just shovel some edibles into your face hole and back to work. Five minutes break between meetings? Open laptop, work work work. The concept of "needing rest" seems entirely foreign to them.
Yesterday our product owner "relayed some criticism" from other team members to me. Apparently, me going to the toilet in breaks is "suddenly disappearing". Or me not replying within 15 minutes in the chat is outrageous. And then he tried to berate me how I'm "his developer" and his team's tasks have top priority. So, according to the PO the problem is me and I should "get used to their mode of operation".
How about "no". I quit a fucking job because that "mode" is simply inhuman. After that feedback, you bet I'm taking my legally protected 30 minutes lunch break and any other break I can. Because fuck yourself, you're not going to burn me out. The best part, that team has smokers who "suddenly disappear" twice as much as I do, but apparently that's somehow a-ok.
I had to remind him that his project is just one of several I'm working on, so no, not "his dev". While that wasn't exactly a powerful comeback, it did shut him up. Still going to talk to my boss on Monday, at least to ensure that the PO can't talk shit about me behind my back.4 -
As a Java developer, I'm disappointed that GitHub does not offer free protected and package-protected repos.4
-
Preface: My company took over another company. A week ago I inherited their IT.
"IT" !!!! Are you fucking kidding me?!
Their server stood at an ex employees homeoffice. So I drove to her and she had 0 idea about IT. Server was just "Running". I tore that fuck down and saw an aweful lot of Hentai in all home folders.
WTF?!
Not enough, their crm was a makroinfested access table. Shit was protected so I couldn't even edit the makros. The retarded fucktards hardcoded paths to serverside folder \\fuck\you\hard\cavetroll
Just so that server will never see the light of my domain! Damn you? Mothership of sisterfucking dickgirls!10 -
I don't know who you are but I will find you and I will install linux in your pc
Fuck off bitch
My bios is password protected9 -
!dev
!!politics (kinda)
Here’s a gem from our recent harassment and diversity training at work:
Speaker: “All of these things are protected from discrimination in California! Wow! It’s a huge list, isn’t it? Now let me ask you a question: is a single white male under 40 protected?”
Everyone: *crickets*
Fucking really?
After immediately jumping on all of the other speaker’s questions, you can’t answer this one?
And later, here’s another gem:
Speaker: “If you witness an employee harassing another employee outside of work and work hours, completely unrelated to work, should you report it? What if you ask the person being harassed and she says no?”
Speaker: “Always report it! While it’s not *technically* required by law, you must report it! Why? Because you have the same protections she would! And maybe it’s easier for you to say something than for her.” (Surprise gendering was her own addition)
Fair on that last point, but against the person’s wishes? Totally not cool. Maybe it wasn’t harassment, or you don’t know the situation. Heads up: you probably don’t. Or maybe it wasn’t a big deal at all, but you think it’s earth-shattering. But all that reporting it against someone’s wishes does is create drama and possibly legal trouble. And if it wasn’t harassment or the case goes poorly, you just created enemies for yourself, or for one or both of them if you’re reporting it anonymously, and possibly even ruined one or both of their jobs/careers by doing so. Good fucking job, asshole.
Snitches get stitches.16 -
Microsoft brute-forces password-protected archives in OneDrive.
“Microsoft will decrypt, open, and scan protected Zip archives uploaded to the company's cloud servers in search of potential computer threats. Security researcher Andrew Brandt recently discovered the issue while trying to share malware samples with other researchers through SharePoint.”
This is when I encrypt my archives, I use _very_ long passwords generated by Bitwarden. Like this: qkYdE5i@27yHTTj8YsMDKQ9^mo$j@!P^M4qA95Y5VqR*53otAMuMv$9sdxtF4HAuNdAYoW9RPVxucJ3
Good luck bruteforcing that, Microsoft!
https://techspot.com/news/... 10
10 -
For fuck sake, stop complaining about the lack of privacy everywhere.
I'm not saying that worrying about your privacy is bad, I also really want to be protected and I know the risks we run when put our information on the net, I care about my data, but please stop acting like whoever uses Google, Facebook or Windows is a fool and you're the only genius around.
Because guess, I use their services and when I use them I'm explicitly authorizing them to process my data, to track me and to create a profile about me. It's an exchange, I know what they're doing and I've control on the data I'm serving them.
If, for some reason, I want to be more protected then I fucking use some open source iper-safe alternative, and that's it.
Seriously, I'm happy if you use those fancy alternative services for everything (for your reasons, I don't care) and I'm glad if you decided to don't use any closed source service anymore, but please, stop screaming against who uses them19 -
TIL that TI has no goddamn chill
Texas Instruments released the TI-83+ calculator model in 1996. The Z80 was not at all stock and has the following features:
- 3 access levels (priveleged kernel, kernel, user)
- Locking Flash (R/O when locked for most pages, some pages protected and unreadable as well, only unlockable from protected Flash pages by reading a certain order of bits then setting a port)
- Locking hardware ports (lock state always the same as flash)
- Customizable execution whitelist range (via locked ports)
- Configurable hardware (Flash/RAM size changeable in software via locked ports, max RAM is 8MB which is fucking mental compared to the 64k in the thing)
- Userland virtualization (always-on)
- Reset on violation of security model
- Multithreading
- Software-overclockable CPU
- Hardware MD5 and cert handling
TI made a calculator in 1996 with security features PCs wouldn't see until like 2010 what the *actual* fuck10 -
Me: here's the code.
Sr: allright, looks fairly ok. Just change all *FIELD* modifiers to protected rather than private.
Me: what? Why???
Sr: bcz that's the code style we've adopted.
Me: srsly? If so.. Where do you use private fields then?
Sr: nowhere. We use either protected or public so we could extend any class we want9 -
I had to create a c++ dungeon 2d game as University project.
The spec said "a terminal game made with char"
I and my team made a real game with anemies boss, and balanced stat in 15 days with Qt (we asked if can use external libraries)
We got 6/8 point for the project cuz we forgot to put protected/private the attribute of the player...3 -
We got DDoS attacked by some spam bot crawler thing.
Higher ups called a meeting so that one of our seniors could present ways to mitigate these attacks.
- If a custom, "obscure" header is missing (from api endpoints), send back a basic HTTP challenge. Deny all credentials.
- Some basic implementation of rate limiting on the web server
We can't implement DDoS protection at the network level because "we don't even have the new load balancer yet and we've been waiting on that for what... Two years now?" (See: spineless managers don't make the lazy network guys do anything)
So now we implement security through obscurity and DDoS protection... Using the very same machines that are supposed to be protected from DDoS attacks.16 -
- popunder background bitcoin miners did become a thing
- keybase android beta uploaded your privatekey to google servers "accidentally"
- you can spoof email headers via encoded chars, because most apps literally just render them apparently
- imgur leaked 1.7 million user accounts, protected by sha-256 "The company made sure to note that the compromised account information included only email addresses and passwords" - yeah "only", ofcourse imgur, ofcourse.
I guess the rant I did on Krahk etc. just roughly a month ago, can always be topped by something else.
sources:
https://www.mailsploit.com/index
https://bleepingcomputer.com/news/...
https://blog.malwarebytes.com/cyber...
https://helpnetsecurity.com/2017/... undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6
undefined email spoofing email popunder bitcoin miners keybase android privatekey bitcoin imgur keybase imgur hacked mining6 -
Worst one I’ve seen so far is when I was working for my previous community another developer joined to help me, without the permission of me or the other lead developer he pushed a client-side update. We didn’t think it was a big deal, but once we began reviewing the code it became a big deal... he had placed our SQL credentials into that file that every client downloads. All the person had to do was open the file and could connect to our SQL which contained 50k+ players info, primarily all in-game stuff except IPs which we want to protect at all costs.
Issue becomes, what he was trying to do required the games local database on the client-side, but instead he tried connecting to it as an external database so he decided to copy server-side code and used on the client.
Anyways, the database had a firewall that blocked all connections except the server and the other lead dev and myself. We managed to change the credentials and pull the file away before any harm was done to it, about 300 people had downloaded the file within an hours period, but nothing happened luckily. IP to the DB, username, password, etc, were all changed just to keep it protected.
So far this is the worst, hopefully it doesn’t get worse than this :/1 -
So I have seen this quite a few times now and posted the text below already, but I'd like to shed some light on this:
If you hit up your dev tools and check the network tab, you might see some repeated API calls. Those calls include a GET parameter named "token". The request looks something like this: "https://domain.tld/api/somecall/..."
You can think of this token as a temporary password, or a key that holds information about your user and other information in the backend. If one would steal a token that belongs to another user, you would have control over his account. Now many complained that this key is visible in the URL and not "encrypted". I'll try to explain why this is, well "wrong" or doesn't impose a bigger security risk than normal:
There is no such thing as an "unencrypted query", well besides really transmitting encrypted data. This fields are being protected by the transport layer (HTTPS) or not (HTTP) and while it might not be common to transmit these fields in a GET query parameter, it's standard to send those tokens as cookies, which are as exposed as query parameters. Hit up some random site. The chance that you'll see a PHP session id being transmitted as a cookie is high. Cookies are as exposed as any HTTP GET or POST Form data and can be viewed as easily. Look for a "details" or "http header" section in your dev tools.
Stolen tokens can be used to "log in" into the website, although it might be made harder by only allowing one IP per token or similar. However the use of such a that token is absolut standard and nothing special devRant does. Every site that offers you a "keep me logged in" or "remember me" option uses something like this, one way or the other. Because a token could have been stolen you sometimes need to additionally enter your current password when doings something security risky, like changing your password. In that case your password is being used as a second factor. The idea is, that an attacker could have stolen your token, but still doesn't know your password. It's not enough to grab a token, you need that second (or maybe thrid) factor. As an example - that's how githubs "sudo" mode works. You have got your token, that grants you more permissions than a non-logged in user has, but to do the critical stuff you need an additional token that's only valid for that session, because asking for your password before every action would be inconvenient when setting up a repo
I hope this helps understanding a bit more of this topic :)
Keep safe and keep asking questions if you fell that your data is in danger
Reeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee5 -
Is there any excuse for NOT having a HTTPS connection nowadays?
My university has so many unprotected subdomains that we're supposed to use and LOGIN ON that are not protected. Although these login forms are https protected the rest is not and seems sketchy.27 -
abstract class :
protected virtual void doSomething()
{
//some stuff
}
child class
protected override void doSomething()
{
base.doSomething();
}
IMHO this is what go fuck yourself means.......4 -
So to start off this happened today while I was at school.
Each student gets a netbook for school and the amount of restrictions put in place are probably up to government spec. Well I brought in my personal netbook and a flash drive with a few distros of Linux on it on it to mess with during study hall(all on my own hardware).
I told my friend that about it and said I doubted it would boot because the bios is password protected and the IT guy probably removed external drives from the boot list but let him use it anyway.
5 minutes later he is showing me his screen with Ubuntu running on it, I was freaking out some and asked for it back and he gave it back to me.
About a minute later he shows me his screen. All black with white text shooting down it saying windows disk integrity check or something like that. All I see is "file xyz deleted" and was freaking out even more. I just sat there for the next 20 minutes thinking of how to explain this to the IT guy and hopefully get in less trouble.
Finally after the longest 20 minutes of my life as a student I see the windows 7 boot screen appear. Probably the one time I actually wanted to see it honestly but I was so happy to see the end of the situation.
Sorry this was so long but I hope it's fine for a first post here, I've been putting it off but after this decided to finally post.3 -
Before I became a Computer Engineer, (actually, this job is where I learned I loved programming) our manager would pull us into a team motivational meeting.
Except she was a bit of an airhead, so her idea of motivation was having a sing-song and listing our favorite movie quotes.
It was even funnier because there was lots of drama surrounding "how she became our manager," and one of our teammates felt as though she should have gotten the job.
Anyway, none of those were the most ridiculous meeting.
The most ridiculous meeting was when the VP of marketing came to town from Florida to address the brewing drama.
In this meeting, all of my teammates suddenly had the delusion that we were in a union and thought they were protected from getting fired. They threw our manager under the bus. I was the only one who could see that he was there to see if our department was worth saving. They thought they were going to get rid of our manager by shitting on her, but they were just confirming his suspicion that there was a bunch of bullshit going on all around.
So I approached the VP after the meeting, and long story short, I was the only one who got through layoffs with a job offer in Florida a couple weeks later.
I didn't take it, because by that time I decided I wanted to go to school for Computer Engineering.1 -
Customer: can you fix my flashdrive? I think it's corrupted or something.
Me: sure no problem
*plugs in flashdrive in pc*
*tried to format*
*Disk is write protected*
Me: ... not you again.9 -
My worst bad practice:
Saving my Linux Root SSH Keys on a Cloud Storage company.
Have them there, so I wont loose them ever. I password protected them, but you never know what the NSA/FBI/CIA can do 😉1 -
In ESnext, private properties are marked with `#`.
Who thought that was a good idea? No really, who thought that was a good idea?
Why not just -- I don't know -- introduce keywords like ... let me think ... public, protected and private!?
Why this:
class MyClass {
a = 1; // .a is public
#b = 2; // .#b is private
static #c = 3;// .#c is private and static
incB() {
this.#b++;
}
}
If this becomes part of the language, no JavaScript developer may joke about php usage of `$` anymore.32 -
A client asked me to do a little makeover to their old website (before I made them a new one) because if they ask to the company who made it, they would pay too much. The WWE problem was that the website was in that company server and had their (really) bad backoffice. I ended up injecting in one field on the contacts (not protected with XSS) a script that change a little the front page layout and some content in another pages.
-
What a new years start..
"Kernel memory leaking Intel processor design flaw forces Linux, Windows redesign"
"Crucially, these updates to both Linux and Windows will incur a performance hit on Intel products. The effects are still being benchmarked, however we're looking at a ballpark figure of five to 30 per cent slow down"
"It is understood the bug is present in modern Intel processors produced in the past decade. It allows normal user programs – from database applications to JavaScript in web browsers – to discern to some extent the layout or contents of protected kernel memory areas."
"The fix is to separate the kernel's memory completely from user processes using what's called Kernel Page Table Isolation, or KPTI. At one point, Forcefully Unmap Complete Kernel With Interrupt Trampolines, aka FUCKWIT, was mulled by the Linux kernel team, giving you an idea of how annoying this has been for the developers."
>How can this security hole be abused?
"At worst, the hole could be abused by programs and logged-in users to read the contents of the kernel's memory."
https://theregister.co.uk/2018/01/... 22
22 -
Time for a REAL fucking rant.
io_uring manpages say you can set the CAP_SYS_NICE capability to allow SQPOLL to work. You can't, you still get an operation not permitted errno result.
Why? I checked, it says 5.10 mainline is required. Pretty sure I just manually downloaded and installed the Deb's myself. uname reports that I am at 5.10. So what gives?
Maintainer submitted a patch because they fucked up and made the *actual* capability check look for what's basically root permissions (CAP_SYS_ADMIN... c'mon...) and is now trying to rectify a glaring security shortcoming.
Patch hasn't been accepted or even addressed yet but they already updated the manpages with the estimated mainline kernel release as if it had made it into the release candidate. Manpages have made it into latest debs but the actual change has not.
Where the fuck is the Linus Torvalds that would ream the fuck out of shitty developers doing shitty things? The political correctness climate has discouraged such criticism now and the result... this. This fucking mess, where people are allowed to cut corners and get away with it because it would hurt their feelings when faced with pressure.
I'm not just guessing either. The maintainer has already said some of the "tone" of criticisms hurt his feelings. Yes, sorry, but when you claim 90% speedup over a typical epoll application using your new magical set of syscalls, and nobody can even get 1-2% speedup on a similar machine, people are going to be fucking skeptical. Then when you lower it to 60% because you originally omitted a bunch of SECURITY RELATED AND CORRECTNESS CHECKING CODE, we're going to call you the fuck out for fudging numbers.
Trying to maintain the equivalent of academic integrity within the computer science field is an exercise of insanity. You'd be fired and shunned from publishing in journals if you pulled that shit in ANY OTHER FUCKING FIELD, but because the CS scene is all about jerking each other off at every corner because the mean people keep saying mean things on Twitter and it hurts your feelings therefore we're all allowed to contribute subpar work and be protected from criticisms when others realize it's subpar.
These aren't mistakes anymore, it's clear you're just trying to farm clout at Facebook - maybe even FOR Facebook.
Fuck you. Do it right, the first time. Sick of shitty code being OK all of a sudden.2 -
My company employed a new back-end guy from a random country in Africa (our first non-european). After firing the internal IT guy a year ago, they have now noticed that he has fully protected our company from login attempts outside of europe. The replacement has no idea how to revert it and honestly is not an system administrator.
Our DevOps guy knows how to solve it but nobody asked him and he cannot be arsed.8 -
That moment when you're dual booting to have Windows for gaming and Windows decides it would be nice to reboot and install updates, while you're gaming of course. Without any sort of visible notification. Any. And then it fails to install its updates, because updates are hard to install, you know? Sometimes its just not the way you'd like it, you know? It's probably best to revert everything, yes? It only takes an hour after all! An hour of the lovely “Windows was too dumb to update and now has to try to make itself work again” screen with its lovely moving dots. Oh and of course you'll have to sit there and watch it because Windows has to reboot at least twice during the process. And if you're not there to tell GRUB you want to boot into Windows again Linux won't boot properly because Windows keeps the filesystems write-protected. Just to be safe you'd let it complete its marvellous ways!
I wish this was the first time this happened. But it wasn't. Fuck Windows.5 -
I've fucking had it with youtube, fucking jizz slapping knob butlers. I'm going to setup a mirror on my server, the idea is:
- Setup a youtube-dl cron that fetches multiple times a day both audio and video versions of the music playlist I have, hopefully with some sort of progress tracking of each download and total, so I could check if it has run successfully and have a nice dashboard, might need to do that myself (except if compactd proves itself to manage that all)
- Need to figure out a way to download the "best" quality but not go beyond 1080p, since if some videos for some reason are uploaded @ 4k, that'll be a waste of space
- Have Compactd/Funkwhale/Koel as the music player frontend for the audio version of the files, preferably one of them should offer download of the files too, so I could have a similar setup to spotify, though I could probably also just have some filebrowser installed or have a password protected index.
- Not sure what to use for the video versions, since sometimes the video goes with the music; plex? emby? suggestions are welcome
- Saw somebody (ab)using google drive as their backup for all the music they download, so I want to setup something similar, rsyncing all videos and music to some account, so in case shit majorly hits the fan, I can just download everything back 15
15 -
There is this abstract class with a single public method in it.
Above it a comment, change back to protected ASAP.
That comment is from 20131 -
During an internship, I spent some time automating reports with VBA. Basically, imagine a few big excel sheets with 1000 formulas and a few thousand lines of VBA.
One of the reports was handed directly to the bosses boss of our boss. After 4 weeks, he came to me and asked why the table entry in row 23 or so was always 84. Well.. I dont know. This data is automatically calculated / retrieved from a database. Went and checked, already sweating, and found that
THE OTHER INTERN COULDNT FIX A FORMULA SO HE OVERRODE IT WITH PLAIN TEXT. WITH A FUCKING PLAIN VALUE OF 84. A FOOKING EXCEL SHEET WITH A THOUSAND DIFFERENT FORMULAS AND LOTS OF VBA. Needless to say, everything is password protected now.1 -
tldr; Windows security sucks. You as a org-admin cant do anything about it. Encrypt your device. Disable USB Live boot in the bios and protect it with a STRONG password.
First of i just want to say that i DO NOT want to start the good ol' Linux VS Windows debate. I'm just ranting about Windows Security here...
Second, here's why i did all of this. I did all of this mainly becuase i wanted to install some programs on my laptop but also to prove that you can't lock down a Windows pc. I don't recomend doing this since this is against the contract i signed.
So when i got my Laptop from my school i wanted to install some programs on it, sush as VS Code and Spotify. They were not avalible in the 'Software Center' so i had to find another way. Since this was when we still used Windows 7 it was quite easy to turn sticky keys in to a command prompt. I did it this way (https://github.com/olback/...). I decided to write a tutorial while i was at it becuase i didn't find any online using this exact method. I couldn't boot from a USB cause it's disabled in the bios wich is protected by a password. Okey, Sticky keys are now CMD. So let's spam SHIFT 5 times before i log in? Yeah, thanks for the command promt. Running 'whoami' returned 'NT SYSTEM'. Apparantly NT System has domain administator rights wich allowed me to make me an Administrator on the machine. So i installed Everything i wanted, Everything was fine untill it was time to migrate to a new domain. It failed of course. So i handed my Laptop to the IT retards (No offense to people working in IT and managing orgs) and got it back the day after, With Windows 10. Windows 10 is not really a problem, i don't mind it. The thing is, i can't use any of the usual Sticky keys to CMD methods since they're all fixed in W10. So what did i do? Moved the Laptop disk to my main PC and copied cmd.exe to sethc.exe. And there we go again. CMD running as NT System on Windows 10. Made myself admin again, installed Everything i needed. Then i wanted to change my wallpaper and lockscreen, had to turn to PowerShell for this since ALL settings are managed by my School. After some messing arround everything is as i want it now.
'Oh this isnt a problem bla bla bla'. Yes, this is a problem. If someone gets physical access your PC/Laptop they can gain access to Everything on it. They can change your password on it since the command promt is running as NT SYSTEM. So please, protect your data and other private information you have on your pc. Encypt your machine and disable USB Live boot.
Have a good wekend!
*With exceptions for spelling errors and horrible grammar.4 -
Best OOP class ever 😆
"Now you can access your classmates' public data, you know their classes' parts. But you can't touch their private parts (5sec pause) ...of their class. However if you're related, it's okay for you to play with eachothers parts... as long as they're protected. "4 -
Nobody, nobody, nobody should accept an office-only position unless they actually want to work in an office. People who actually believe that everyone should go back into the office should be excommunicated from this field. This freedom we have needs to be protected for the best interest of the future.4
-
Zero Days documentary about stuxnet malware features a "identity protected" NSA employee who reveals information about classified NSA tactics.
She claims "I would NEVER compromise ongoing operations in the field."
Well it's too bad that Amazon Prime Video and IMDB don't share your values. They have compromised your name, Joanne Tucker, and the other films you were in.
Nice acting though. You really have people believing you were a real source!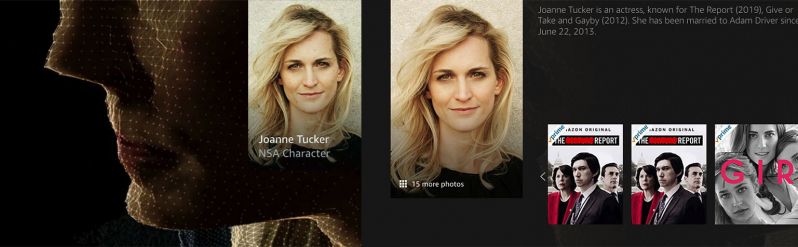 15
15 -
In my ongoing quest to un-Google my life, I turned off the Whatsapp chat back up, which uses Google Drive. There's a message in that setting which says, "Media and messages you back up are not protected by Whatsapp end-to-end encryption while in Google drive".
Damn.
All my Whatsapp chats for years have been on Google servers in plaintext.
I assumed it uploaded one massive encrypted archive.13 -
There's an interesting species out there, the skiplings. They are small, furry beasts, and usually go unseen because they live underground. When there's trembling action however, they leave their burrows to check out what's going on, typically while sitting up.
The rarest breed has the distinct habit of appearing quickly, and once things are observed to be calm, slowly return underground. They are mildly social in that several of them can inhabitate an area, but each has its own little den for sleeping.
Unfortunately, skiplings are a rare species so that they are protected under WCAG 2.1 section 2.4.1 at maximum criticality level A.3 -
When I started programming ~5 years ago.
Teacher: OK, C++ classes and structs have 3 access modifiers: private, public and protected.
Private fields can't be accessed out of the current class.
Me thinking: wow, that's cool, but how can it be? I have to research.
I went to home and wrote a class with one variable with its set and get functionality.
Then I opened Cheat engine) and tried to access and change the variable. When I succeeded, I started hating this world of programming.
After some time I understood that it's wonderful cause it's up to you.5 -
Hey, we need a service to resize some images. Oh, it’ll also need a globally diverse cache, with cache purging capabilities, only cache certain images in the United States, support auto scaling, handle half a petabyte of data , but we don’t know when it’ll be needed, so just plan on all of it being needed at once. It has to support a robust security profile using only basic HTTP auth, be written in Java, hosted on-prem, and be fully protected from ddos attacks. It must be backwards compatible with the previous API we use, but that’s poorly documented, you’ll figure it out. Also, it must support being rolled out 20% of the way so we can test it, and forget about it, and leave two copies of our app in production.
You can re-use the code we already have for image thumbnails even though it’s written in Python, caches nothing and is hosted in the cloud. It should be easy. This guy can show you how it all works.2 -
Installing a GPU is easy - except if it doesn't fit in the case. I had to saw off 3cm of the upper, 5.25" bay. Just removing the bay cage entirely was not an option because I still need that for my DVD drive.
My bow saw wouldn't have enough space, and the cage is riveted. So despite terrible ergonomics, I used the metal saw of a fucking Swiss Army knife for 24cm of cut length through 1mm steel. Then I filed off the cuts so that I won't injure myself later.
However, I was too lazy to take out the mobo and shit, so I protected it professionally against potential metal dust - with a towel.13 -
*right click on image*
[nothing happens]
*spams right click, thinking about getting a new mouse*
[small modal shows up: "this content is protected!"]
*laughs in developer's console*
I never thought I'd get to see a website that "protects" its content by disabling right click, I'm moved :')3 -
For the last 20 years, there's one thing I've not been able to do reliably:
Share a folder on a windows computer.
Why the fuck can I write /etc/smb.conf from scratch with a blindfold on and make it securely work from all client devices including auth & acl, but when I rightclick and share on windows it's either playing hide and seek on the network (is it hiding behind //hostname/share? No? Maybe in the bushes behind the IP addresses?), or it's protected by mysterious logins requiring you to sacrifice two kittens a day.
Yes, finally it works! One windows update later... aaaand it's gone.
JUST GIVE ME A FUCKING CONF AND A MAN PAGE, MICROSOFT. I DON'T CARE THAT YOU'RE ORALLY PLEASING ALL THESE MALWARE RIDDEN GUISLUTS ON THE SIDE, JUST GIVE ME A FUCKING TEXT FILE TO STORE AND EDIT.4 -
Did you know that "Chief Prayer Officer" is an actual role in some companies?
It just so happens that our IT partners have a CPO and the very same company forgot to install Antivirus software on our servers... I guess the servers are protected by God™. 😅12 -
i hate linux like a lot , how do you guys use it
like you guys dont want an advertising ID, how the fuck will advertisers know who you are and what you like?
open source , give me a break, you mean your os devs are soo untrustworthy that you just have to see what they wrote in the code, who does that?
free come on, how poor are you linux people, i mean, quality stuff gets paid for, free stuff just means it's trash
and the linux devs , the aint like real coders they are just hobbysts, making your os in their free time
and who wants to install their own software anyway, on other platforms the company curates restricted software that you can use, and i know you'll say its oppressive but its just customer protection.
and i do want my platform to track everything i do, it only helps them build better stuff for me.
and whenever they decide to outdate my hardware and kill support for it, it only means they care and want me to get the latest tech, how considerate.
wait , i hear you say, there are no bugs in linux, my vendor makes sure my os comes with the latest antivirus software, nothing can break my system.
and just because linux runs on servers and most super computers only shows that common users like you and me are ignored, at least my vendor is not a sellout, and still makes stuff for the masses.
you say freedom i say safety i can sleep safe and sound for am protected nutured under one echosystem of software that i can not leave.19 -
Let's talk about the cargo cult of N-factor authentication. It's not some magic security dust you can just sprinkle onto your app "for security purposes".
I once had a client who had a client who I did server maintenance for. Every month I was scheduled to go to the site, stick my fingerprint in their scanner, which would then display my recorded face prominently on their screens, have my name and purpose verified by the contact person, and only then would the guards let me in.
HAHA no of course not. On top of all of that, they ask for a company ID and will not let me in without one.
Because after all, I can easily forge my face, fingerprints, on-site client contact, appointment, and approval. But printing out and laminating a company ID is impossible.
---
With apologies to my "first best friend" in High School, I've forgotten which of the dozens of canonicalisations of which of your nicknames I've put in as my answer to your security question. I've also forgotten if I actually listed you as my first best friend, or my dog - which would actually be more accurate - and actually which dog, as there are times in my High School life that there were more tails than humans in the house.
I have not forgotten these out of spite, but simply because I have also forgotten which of the dozen services of this prominent bullshit computer company I actually signed up for way back in college, which itself has been more than a decade ago. That I actually apparently already signed up for the service before actually eludes me, because in fact, I have no love for their myriad products.
What I have NOT forgotten is my "end of the universe"-grade password, or email, or full legal name and the ability to demonstrate a clear line of continuity of my identity from wherever that was to now.
Because of previous security screwups in the past, this prominent bullshit company has forced its users to activate its second, third, and Nth factors. A possibly decade-old security question; a phone number long lost; whatever - before you can use your account.
Note: not "view sensitive data" about the account, like full name, billing address, and contact info. Not "change settings" of the account, such as changing account info, email, etc. Apparently all those are the lowest tier of security meant to be protected by mere "end of the universe"-grade passwords and a second factor such as email, which itself is likely to be sold by a company that also cargo cults N-factor auth. For REAL hard info, let's ask the guy who we just showed the address to "What street he lived in" and a couple others.
Explaining this to the company's support hotline is an exercise in...
"It's for your security."
"It's not. You're just locking me out of my account. I can show you a government ID corroborating all the other account info."
"But we can't, for security."
"It's not security. Get me your boss."
...
"It's for security."8 -
I've just noticed something when reading the EU copyright reform. It actually all sounds pretty reasonable. Now, hear me out, I swear that this will make sense in the end.
Article 17p4 states the following:
If no authorisation [by rightholders] is granted, online content-sharing service providers shall be liable for unauthorised acts of communication to the public, including making available to the public, of copyright-protected works and other subject matter, unless the service providers demonstrate that they have:
(a) made best efforts to obtain an authorisation, and
(b) made, in accordance with high industry standards of professional diligence, best efforts to ensure the unavailability of specific works and other subject matter for which the rightholders have provided the service providers with the relevant and necessary information; and in any event
(c) acted expeditiously, upon receiving a sufficiently substantiated notice from the rightholders, to disable access to, or to remove from, their websites the
notified works or other subject matter, and made best efforts to prevent their future uploads in accordance with point (b).
Article 17p5 states the following:
In determining whether the service provider has complied with its obligations under paragraph 4, and in light of the principle of proportionality, the following elements, among others, shall be taken into account:
(a) the type, the audience and the size of the service and the type of works or other subject matter uploaded by the users of the service; and
(b) the availability of suitable and effective means and their cost for service providers.
That actually does leave a lot of room for interpretation, and not on the lawmakers' part.. rather, on the implementer's part. Say for example devRant, there's no way in hell that dfox and trogus are going to want to be tasked with upload filters. But they don't have to.
See, the law takes into account due diligence (i.e. they must give a damn), industry standards (so.. don't half-ass it), and cost considerations (so no need to spend a fortune on it). Additionally, asking for permission doesn't need to be much more than coming to an agreement with the rightsholder when they make a claim to their content. It's pretty common on YouTube mixes already, often in the description there's a disclaimer stating something like "I don't own this content. If you want part of it to be removed, get in touch at $email." Which actually seems to work really well.
So say for example, I've had this issue with someone here on devRant who copypasted a work of mine into the cancer pit called joke/meme. I mentioned it to dfox, didn't get removed. So what this law essentially states is that when I made a notice of "this here is my content, I'd like you to remove this", they're obligated to remove it. And due diligence to keep it unavailable.. maybe make a hash of it or whatever to compare against.
It also mentions that there needs to be a source to compare against, which invalidates e.g. GitHub's iBoot argument (there's no source to compare against!). If there's no source to compare against, there's no issue. That includes my work as freebooted by that devRant user. I can't prove my ownership due to me removing the original I posted on Facebook as part of a yearly cleanup.
But yeah.. content providers are responsible as they should be, it's been a huge issue on the likes of Facebook, and really needs to be fixed. Is this a doomsday scenario? After reading the law paper, honestly I don't think it is.
Have a read, I highly recommend it.
http://europarl.europa.eu/doceo/...13 -
Long time ago i ranted here, but i have to write this off my chest.
I'm , as some of you know, a "DevOps" guy, but mainly system infrastructure. I'm responsible for deploying a shitload of applications in regular intervals (2 weeks) manually through the pipeline. No CI/CD yet for the vast majority of applications (only 2 applications actually have CI/CD directly into production)
Today, was such a deployment day. We must ensure things like dns and load balancer configurations and tomcat setups and many many things that have to be "standard". And that last word (standard) is where it goes horribly wrong
Every webapp "should" have a decent health , info and status page according to an agreed format.. NOPE, some dev's just do their thing. When bringing the issue up to said dev the (surprisingly standard) answer is "it's always been like that, i'm not going to change". This is a problem for YEARS and nobody, especially "managers" don't take action whatsoever. This makes verification really troublesome.
But that is not the worst part, no no no.
the worst is THIS:
"git push -a origin master"
Oh yes, this is EVERYWHERE, up to the point that, when i said "enough" and protected the master branch of hieradata (puppet CfgMgmt, is a ENC) people lots their shits... Proper gitflow however is apparently something otherworldly.
After reading this back myself there is in fact a LOT more to tell but i already had enough. I'm gonna close down this rant and see what next week comes in.
There is a positive thing though. After next week, the new quarter starts, and i have the authority to change certain aspects... And then, heads WILL roll on the floor.1 -
This is so annoying, I had 9 diff. jobs the past 2 years and this is my 10th and if this doesn't change I might reconsider my options again.
I came to work at a company that pays me like a Junior and treats me as an intern. My 20yo "boss" who acts as a project owner/lead dev doesn't want to learn anything new and sees any improvement as a waste of money. The problem is he thinks hes a great programmer but he doesn't know shit. Im mainly working on the Laravel installation because "I claimed I know Laravel". And its absolute garbage. They haven't used a single Laravel features besides routes and everything else is vanilla PHP. They write for loops that loop through $_REQUEST to remove a single character. Write 100 deep nested ifs and they abuse Elasticsearch to the point ES crashes because the program is using 1000 deep multidimensional arrays. Its only a webshop...
Everytime I try to make a suggestion like making the master branch protected, doing code reviews etc etc I get shut down because they are autistic and don't want anything to change.9 -
So like a couple days ago I was trying to clear the Var directory of my Symfony project.
I wrote
cd /var
rm ./* -R
Linux: are you sure you want to delete write protected blah blah blah?
Me:AHA! SO ITS A PERMISSIONS ISSUE
sudo rm ./* -R
Quickly realized I was no longer in my project directory.
Took a fat L. Had to reinstall.2 -
First of all sorry for the bad picture. Let's move on...
Deleting this method like:
Who the hell did this nonsense?
I just took a picture of it so I could post it here and rant about it.
Sure felt stupid after deleting it for not thinking about a protected method in the parent class that is part of an API.
So... Yeah....
I was feeling too confident in my skills lately anyway 6
6 -
Wow man. Can the day get any worse
Mother fucker creator of Android. Now I'm A long time android user, but
Android+Snapdragon 6XX chip+Moto= worst combo ever. Damn you creators, may You be deepfucked by a mad bison in heat. Cocksuckers.
The heat my Moto X play generates, I could make an omelette on top of it. And the newest feature, where you try to type, but you can't see anything happening, when 30 secs later, you suddenly start seeing the after images of all the buttons you pressed, all the text you typed. Why maybe I typed at the speed of light and android couldn't keep up. No.
NO! You dumb fuckin POS. NO. I threw my phone 20ft, broke the tempered glass. The case protected this shit. Once I can save enough, I'll either sell a kidney and get an iPhone or even better a OP5.
Nothing disgusts me more than slow hardware.12 -
I'm a developer, member of the A-Team. Actually I'm the leader of the A-Team.
We are incredibly skilled. Our problem solving capabilities is amazing, almost 100 times more effective than the rest of people. We produce code 10 times faster and better than anybody else. We have THE knowledge.
We can save the company in case of emergency.
For that reason, it's of paramount importance to nurture and protect the A-Team.
- When there is a bug, A-Team will not correct it. Because, if A-Team is busy, and bad shit happens, the company could be destroyed and we couldn't help
- When there is some important features to develop with a deadline, A-Team will not participate: A-Team must stay alert and ready in case of emergency
- If huge catastrophe happens and long hours, night and weekend are needed to fix it, A-Team will not risk burning the A-Team because it's the only high skilled team we have. The company cannot afford to have an A-Team member exhausted, underpaid, unhappy leaving or sleepy. Therefore, the company will sacrifice other less important people.
A-Team is company biggest asset and must be protected in any kind of situations.
The company should also pay training for them in order to increase their skills and make them unreplaceable.
These are my conditions. I'm the leader of the A-Team. You can't afford to loose me.7 -
!dev
I didn’t posted for a while cause I didn’t have anything interesting to say. My job is fine, got no major problems in life, everything looks good so I started thinking about the fucking civilization future stuff.
Either I’m to old or we’ll end up back in ancient Egypt one day.
The knowledge is still not moved from old to young, not categorized and protected well enough and we’re busy fighting with each other about nothing important. We’re carrying about stuff that have nothing to do with our lives. All those fucking movements make world worse place then it was. Just marginalize those that are good and give more powers to those who shout more and have more money.
As a result I think in a matter of couple generations there won’t be anyone who could replace grandfathers keeping this machine alive and future people will end up looking at pictures and videos of ancient stuff that nobody is capable of doing cause nobody understands it.
This super friendly human politics of the world like any other politics will make people unfriendly and not able to communicate with each other - stupid and unable to think reasonably.
My advice I also took as a mantra, turn off the internet and read or listen to the books - at least one book a month is your goal.
My last book I listened to was about history of gender and you know what ? I learned that clown fish can change gender when it’s young. I learned more from listening to this book for 8 hours then from a year reading stupid articles in the internet. I understand what gender is, what are the problems and all the fucking history of it staring in 1800-something or maybe even earlier. Maybe because there is still lots of difficulty to write something interesting that is more than 1 page of paper long. Most of stuff in the internet weather it’s an article or video have only 1 page amount of content. This content is none, it have no value to the community. You won’t learn anything from it. If you want to learn something read book cause making good quality book is very expensive and takes lots of person life and self esteem. Probably one book takes more time then most of influencers spend making their stupid pictures and stuff like that.
That’s sad truth of our times. We turned technology made for knowledge exchange to advertising tv - again. -
Jurassic Park was based on a cheapass client who didn't want to pay the right amount to the. Developer who single handedly protected everyone in the park.
-
I'm dealing with an organization that wants me to send them some documents securely but I cannot use their platform (for reasons). Anyway, they asked me to send them an email with a password-protected zip folder for the documents and of course, I will have to send them the password by email so..6
-
Shoutout to https://ytmp3.cc for being the only web youtube downloader that actually works, is actually quick, downloads "copy-protected by copyright" videos and has a dark theme.
Only the occasional popup ad on mobile, too. Goddamn this is good.
only downside is that it's always Highest Available quality and only MP3/MP4... but other than that it's fucking amazing6 -
The best thing about being a dev? The darkness that comes crawling out at night doesn't scare us. Even when we're alone we know we're protected by a magical screen of light.
-
I work on a team project for a test and maintenance course in University. We agreed as a team to adopt a git infrastructure that would prioritize the stability of the master branch at all cost by only updating commits up to the next stable point and tagging every single release. We have a long polling development branch to prepare our releases and we create feature branches for the tickets we need to resolve. I even wrote documentation to make sure that we don't forget and protected the master branch on gitlab from direct modifications.
Can someone fucking tell me how one of my teammates managed to fuck over all of this and work on an unfinished feature straight on master?
N.b. I know that he probably edited straight from gitlab's online text editor because they have a big where they don't restrict modifications on protected branches.1 -
I applied for a position as an engineer for a nonprofit organization that helped kids across the country (and the world) and got the position. The people across the organization were wonderful and, without a doubt, mission driven to help kids and it felt good to do the work. The agile teams worked well together, every team had their roadmaps, and management always emphasized family first. The organization was making crazy money so we were given all the tools we needed to succeed.
Then, within a few months of my hiring, it was announced that the non-profit organization was being bought by a large, fairly well known for-profit company which had also been recently acquired by a venture capital firm.
The next thing we knew, everything changed all at once. We went from building applications for kids to helping this company either make money or build value for their owners. Honestly, I did not know what my day-to-day work was doing for this company. The executives would tell us repeatedly that we were expensive and not a good value compared to their other teams. It felt like we were only being kept until the systems were integrated and their had access to our decades of data.
You might think I'm being paranoid but a year after the acquisition, we still did not have any access to any of their systems. We operated on a separate source code solution and were not given access to theirs. When requests came from them that would facilitate them connecting applications to the data, it was to be considered highest priority.
The final straw for me was when I was told my compensation would be cut for the next year. We were strung along for the whole year leading up to it saying that the company was evaluating our salaries compared to others in the industry. Some of us figured that we would probably even go up knowing that we were underpaid for a for-profit tech company because we chose to work in a non-profit for a lower rate to be able to do worthwhile work. Nope! We were told that we were overpaid and they talked about how they had the data to prove it. One quick look at LinkedIn would tell you they must be smoking something that had gotten stale in a shoebox. Or they were lying.
So that was my rant. If you think you are protected from the craziness in tech right now just because you are writing code at a nonprofit, you might be wrong. Dishonest executives can exist anywhere.3 -
I have an issue with my Laravel routing. Can you help me out, @bittersweet?
I have a custom "/home" route called "/admin" and I set the protected property in the LoginController:
$redirectTo = "/admin";
And it works fine, if I log in from guest. But when I navigate to "/login" as auth-user it still redirects me to "/home".
What the fuck is this? What do I have to change to make this work? Who has to be fucked? Is it possible to solve this without sacrificing a virgin at bloodmoon? And why are Platypus so fucking ugly?14 -
I recently upgraded my computer to a ryzen 1700x and 16gb 3600mhz memory and an asus rog crosshair hero vi board(From an 8350)
My pc ran soo smooth, games even more so
The games ran great, but my personal performance went down.
I didn't understand why. Im probably just losing my edge.
I trained and tried. But still, it felt off.
Today I realized that with my new motherboard, I got a new mac address. And my friend is a bit of a neat freak with that stuff. He has a whole system for ip addresses.
So i told him, I wont have the correct ip address. Then he started laughing and asked my to browse to a certain site www.privateinternetaccess.com
There at the top it said: "you are protected by pia"
Devices without an ip address bound to their mac address, will automatically use the vpn according to his rules.
My ping improved by 10-15ms upon getting my normal ip address back and my game performance is back.3 -
Smiling legendary golden boy #3 says:
HEY LETS PUT OUR INTERNAL GEMS IN THIS PROTECTED GEM SERVICE IT’LL BE GREAT :)
HEY EVERYONE SIGN UP FOR THIS NEW SERVICE! YOU GOTTA OR YOU WONT BE ABLE TO DEV! :)
HEY SO I COPIED THE INTERNAL GEM I WROTE INTO THE MONOLITH REPO INSTEAD OF USING THE SERVICE BECAUSE IM A FUCKING GENIUS :)
YOU WANNA USE IT IN YOUR PROJECT? HAHA GET FUCKED :)
jfcrant wasted a whole day on this jfc root tries adding an internal gem more like infernal gem legendary golden boys mr. smiley2 -
This happen last year during a one day workshop over zoom. We where around 16-18 strangers plus the tutor. We started with everyone introducing themselves (most showing their faces on camera), then it was just the tutor with his shared screen. Two hours in, one of the participants accidentally turned her camera on. I know it was accidental because I still cringe from what happened next: she started picking her nose. At this point, I have to clarify that I'm not familiar with zoom, because I'm on Microsoft teams almost exclusively thanks to my organization. While I looked frantically on how to DM this person (something along the lines of "hey, your cam is on :)" or whatever), I watched in horror as the second act of this play unfolded as she put her finger in her mouth and started to eat it. At this point I was actively dying from second hand embarrassment. Like girl, our orgs payed good money to be on this workshop, gave us a day off (so to speak) and know all I can focus on is you going gold hunting and bringing home some cured cave meat. My boss basically paid so I can get traumatized! And all this while being being in the comfort of my own home. Thanks, zoom! Anyway, she went in for seconds. That is when I died. I am dead at this point. My eyes glued to the screen. Ears ringing. Brain fried. It is done. Now, that the cringe has peaked, does it even matter If I figured out how to dm her? It is too late at this point. We all saw it. The tutor must have seen it. We all witnessed it. We are all witnesses, your honor. She has been witnessed! What else can I do at this point? Me, one bystander amongst bystanders. Idle and powerless.This is exactly how the holocaust started! At this point, I'm no better than your average Joe, who doesn't really like the new regime but doesn't fight it either. At this point, I ask myself what would Jesus do? Or Hollywood? What would happen in the movies in this situation? If I cant fight them, join them? Starting my cam, knuckles deep and double fisting my air holes to save what? It is done. Nothing left. She made her statement. She basically played us for fools. By god, what a freaking boss move that was! Like, can you imagine? Here we were, during the end of a world wide pandemic, bound to our homes, advised to regularly clean our hands, protected ourself and our loved ones and, yes, not eat buggers. And here comes miss fuck-it-all showing us degenerates how its done. You go girl! You showed us the light while we dwelled in darkness. You are our queen! Long may be her reign and just her punishments! I have seen true power and wept with the angles! I was born again. My mind at peace. I was Gandalf the Grey, now I am Gandalf the White. This is the day I will tell my children about. Songs have been written for less. I will never forget this!
Anyhow, I could go on, but that this is basically what happened over the span of a couple of moments in late 2022. I will never forget her. And now you won't either ❤️1 -
I'm migrating a site. I moved the host, I need to change DNS servers. It's protected with one time codes sent to an email I don't have access to. The guy who has the access disappeared without a word, it's been over two hours now. I CAN'T DO SHIT WITHOUT THOSE FUCKING DIGITS YOU FUCKER
-
Erm not sure if this qualifies. Not so long ago I was tackled with having to read a device memory at a very high address in 32-bit linux process (kernel is 64). The 32-bit mmap is unfortunately limited to range of protected mode PAE so it just wouldnt reach that high. So! I wrote my own syscall in assembly that would switch to long mode first so I could use long registers and then I got my page and switched back :)
In retrospective not a big deal, but it made me really happy for the rest of the day when I saw that address in pmap :)1 -
4th day at new job: password sharing through emails or excel sheet that’s password protected! Well, there is something called LastPass, but no they don’t like 🤦🏻♂️1
-
"Reflective" programming...
In almost every other language:
1. obj.GetType().GetProperties()
or
for k, v in pairs(obj) do something end
or
fieldnames(typeof(obj))
or
Object.entries(obj)
2. Enjoy.
In C++: 💀
1. Use the extern keyword to trick compilers into believing some fake objects of your chosen type actually exist.
2. Use the famous C++ type loophole or structured binding to extract fields from your fake objects.
3. Figure out a way to suppress those annoying compiler warnings that were generated because of your how much of a bad practice your code is.
4. Extract type and field names from strings generated by compiler magic (__PRETTY_FUNCTION__, __FUNCSIG__) or from the extremely new feature std::source_location (people hate you because their Windows XP compilers can't handle your code)
5. Realize your code still does not work for classes that have private or protected fields.
6. Decide it's time to become a language lawyer and make OOPers angry by breaking encapsulation and stealing private fields from their classes using explicit template instantiation
7. Realize your code will never work outside of MSVC, GCC or CLANG and will always be reliant on undefined behaviors.
8. Live forever in doubt and fear that new changes to the compiler magic you abused will one day break your code.
9. SUFFER IN HELL as you start getting 5000 lines worth of template errors after switching to a new compiler.13 -
Just tried to read this the frequently asked questions about article 13.
I don't think you need to read it, since you learn nothing from it besides that these people don't even care anymore. Everything is written in a "wishful" mode, even their goals.
You can just go to the next trash can, take an item and compare it with that. Unfortunately, you will have to realize that the item you just picked up was more useful to society than everything you'll read in these "answers".
https://ec.europa.eu/digital-single...
They basically dodge every single question vague to the point that someone as the amount of drugs these people take in order to think they are making realistic proposes.
"We aim to blah blah", "Our aim is blah blah", "We want to blah blah". Might as well sue me for copying their content in that paragraph.
If anybody ever tells you that you have unrealistic, stupid goals or dreams just remember: there's a whole continent lead by people who have no fucking idea what they are doing and still think they are doing a good job. And because they have no idea what they are doing they just offload all the work to companies.
Plattform: Ok, what do we have to do?
EU: lol, just "put in place, in collaboration with right holders, adequate and proportionate technical measures." (#2 P4)
Plattform: can you be a bit more specific?
EU: Look, this proposal just "requires platforms which store and provide access to large amounts of copyright-protected content uploaded by their users to put in place effective and proportionate measures." It's not that hard to understand, you dummy (#3 P3)
Plattform: So we need to monitor all user-generated content?
Eu: are you stupid or something? You "would not have to actively monitor all the content uploaded by users", just the copyrighted content. (#4 P1)
The rest is more or less the same, just them imagining the outcome, without taking turning on their decomposed brains in order to apply common sense.
Jumping off this "union" seems be pretty lucrative 🤔1 -
[Seeking Advice / Legal / Opinion]
Hello world, (TLDR at the bottom)
I'm the co-founder of a small startup and looking for advice from people of legal background or similar situations. (Any help making the reddit post more active will also help a lot: https://reddit.com/r/legaladvice/...)
Just as a backstory for better understanding:
a couple of years ago, me (early twenties, male) and another guy (late thirties, male) started an entrepreneurial journey, got in an accelerator program and some investment, and things always looked well.
We opened the company and started working / selling our services. Step by step we started recruiting, and getting some clients, and business is going well... ("well" as in, small revenues but not spending more than we earn).
The thing is that me and my co-founder's relationship has been degrading over time and I think it would be better for us and the company to split up and go our own way. He has the majority of the shares and I don't mind leaving it all behind for the sake of the company and mental health.
This is in US, if it helps, and we both have At-Will employment contracts.
My main question is, *if I do sign a termination contract*, from what I read, I'm obliged to remain reachable for a period of 12 months (plus all those IP related stuff, not sharing confidential info, etc).
[1] Is there anything I should be careful about and get some kind of protection or get some more information before resigning?
I'm afraid that if I leave the company it affects the business negatively, as we both work 16 / 20 hour shifts many times and my work would not be easily replaced by anyone in the current team. We are hiring more people right now, and some seniors, and I was thinking on staying one month dedicated only to training them... [2] Could this be specified in some contract that I am resigning from "today", but stay 30 days focusing on training new people, or anything similar?
I don't mind staying in touch and help whenever they could need, but I will not be available 24/7 and I will obviously need a job to pay living expenses, so I don't want to affect negatively my time in other jobs or personal life and be kind of protected against anything that he could do to make me stay continuously connected or compromised.
I'm interested in knowing any opinions and advice you guys may have, and feel free to ask some questions if you need extra details.
I just want the best for the startup but cannot hold much time in the current environment.
TLDR: Relationship between me and co-founder is getting worse, thinking on resignating but want to keep some sort of protection against anything that could make me keep compromised to the company.7 -
So this cat (stray) used to come with her baby kitten, for food. Mama always fed the baby first, licked her, protected her....
Fast forward, now the baby kitten is all grown up. Now if she comes near mamas food, she gets growls and a nasty smack from mama cat. :D :D -
Reading all these hacking stories has made me nervous that my server isn't protected enough.
I've disabled password login and setup SSH keys which as far as I know is a big step in the right direction.
Is it enough? What more should I do?
In case you can't tell, I'm no expert in server adminy stuff 😛9 -
While attempting to quit smoking and after spending a full day trying to understand why the previous devs took this approach to encrypting a string and my lack of nicotine addled brain not allowing me to see that this was a “Secure”String and so uses a machine specific key (that’s why the code that worked locally wouldn’t run on production 😑) this is my rant on comments added to the helper I had to write
/// <summary>
/// If you are using this class and it's not for backward compatibility - then you probably shouldn't be using it
/// Nothing good comes from "Secure" strings
/// Further to this Secure strings are only "useful" for single user crypto as the encryption uses the login creds, transferring
/// this data to another client will result in them never being able to decrypt it
///
/// Windows uses the user's login password to generate a master key.
/// This master key is protected using the user's password and then stored along with the user's profile.
/// This master key then gets used to derive a number of other keys and it's these other keys that are used to protect the data.
///
/// This is also a broken crypto method via injection (see Hawkeye http://hawkeye.codeplex.com/) plus the string is stored in plain
/// text in memory, along with numerous other reasons not to use it.
/// </summary>
public class SecureStringHelper
{3 -
Yesterday and today combined I spent about 8 hours trying to get my PGP / GPG passphrase to work. Absolutely magically, somehow a newline character had gotten into the passphrase. Yes. That's possible. On macOS, that is.
On my Windows machine I have the same fucking private key protected with the same password. Now try and get a non-windows newline character into any Windows password field, be it a command line or some GUI input. WTF! You'll lose a year of your life with every passphrase error while you have the actual passphrase.
So after all these hours trying to hack my own GPG keystore without success, I remembered how the private key got on my Windows machine in the first place: see tags.4 -
New Office gave me an admin protected machine with limited access to users, but I have successful installed Android studio and sdk for flutter learning and Node setup for side hustles.
**Admins would give pikachu surprise face if they find out.3 -
I've always sucked at OOP and OOD, _in part_ because I have never encountered a good, common sense, relatable real-world example or analogy of why one would use protected or private variables/objects/functions over public. I watch tutorials and it all just sounds like static in my head and the explanations are just like "well, it's obvious you want to do blah blah blah because reasons."
Maybe it's just painfully obvious to everyone but me and my tiny brain just isn't capable of understanding. But if anyone has the example or analogy that made OOP click for you, please share.7 -
So I figure since I straight up don't care about the Ada community anymore, and my programming focus is languages and language tooling, I'd rant a bit about some stupid things the language did. Necessary disclaimer though, I still really like the language, I just take issue with defense of things that are straight up bad. Just admit at the time it was good, but in hindsight it wasn't. That's okay.
For the many of you unfamiliar, Ada is a high security / mission critical focused language designed in the 80's. So you'd expect it to be pretty damn resilient.
Inheritance is implemented through "tagged records" rather than contained in classes, but dispatching basically works as you'd expect. Only problem is, there's no sealing of these types. So you, always, have to design everything with the assumption that someone can inherit from your type and manipulate it. There's also limited accessibility modifiers and it's not granular, so if you inherit from the type you have access to _everything_ as if they were all protected/friend.
Switch/case statements are only checked that all valid values are handled. Read that carefully. All _valid_ values are handled. You don't need a "default" (what Ada calls "when others" ). Unchecked conversions, view overlays, deserialization, and more can introduce invalid values. The default case is meant to handle this, but Ada just goes "nah you're good bro, you handled everything you said would be passed to me".
Like I alluded to earlier, there's limited accessibility modifiers. It uses sections, which is fine, but not my preference. But it also only has three options and it's bizarre. One is publicly in the specification, just like "public" normally. One is in the "private" part of the specification, but this is actually just "protected/friend". And one is in the implementation, which is the actual" private". Now Ada doesn't use classes, so the accessibility blocks are in the package (namespace). So guess what? Everything in your type has exactly the same visibility! Better hope people don't modify things you wanted to keep hidden.
That brings me to another bad decision. There is no "read-only" protection. Granted this is only a compiler check and can be bypassed, but it still helps prevent a lot of errors. There is const and it works well, better than in most languages I feel. But if you want a field within a record to not be changeable? Yeah too bad.
And if you think properties could fix this? Yeah no. Transparent functions that do validation on superficial fields? Nah.
The community loves to praise the language for being highly resilient and "for serious engineers", but oh my god. These are awful decisions.
Now again there's a lot of reasons why I still like the language, but holy shit does it scare me when I see things like an auto maker switching over to it.
The leading Ada compiler is literally the buggiest compiler I've ever used in my life. The leading Ada IDE is literally the buggiest IDE I've ever used in my life. And they are written in Ada.
Side note: good resilient systems are a byproduct of knowledge, diligence, and discipline, not the tool you used. -
My job isn't stressful all the time. Sometimes I'm in meetings and I'm just bored. And sometimes I have a coke to drink. That's pretty nice.
But right now my app is breaking and I don't know why. It either corrupts the heap sometimes or breaks the execution engine sometimes or attempts to write pointers I don't control into protected memory sometimes. Can't reliably reproduce them. And every time I try to debug one it causes the other.
But I do have a Coke. -
A few years ago, we were developing a media application that allows playing DRM protected content in various business rules. One was that a movie is only playable after watching an ad; the weird one is that an *ad* is playable only after watching a movie.
-
I always thought wordpress was ok, not great not terrible, from a coding perspective. Now every new framework I have worked on makes me see why Wordpress is on 40% of the internet.
Now I love wordpress not because of what it did do, but because of all the really stupid things it managed to avoid doing including: over abstraction, trend chasing, using "new transformative technology" that disappears in 2 years, breaking plugin economy with updates and making devs start over, making everything OOP for the sake of making everything OOP, making adding on a bit of code take multiple files of multiple formats and boiler plate code, boiler plate code, compiling dependencies, composer, twig, laravel, one page applications, react, angular, vue, javascript only stacks (MEAN), not letting you control sql queries, protected/private scopes and design that doesn't let you fix or alter bad code others did, and the list goes on and on.
Wordpress did a lot right, and devs should try learning from it instead of making more problems to solve. Sure it's not elegant, but you known what it does do? Focus on a solving a problem. Then it does. Without inventing new ideas or concepts to inject into the code and create new problems.
And you know what else? Hooks are actually very well implemented in Wordpress. I've seen it done much worse.
Honestly my main gripe with the entire platform is a slow moving to OOP for no reason and the database design should separate post type into different tables, the current design makes it less scalable for large data sets for multiple reasons so I'd fix that.4 -
We're talking about coding standards and someone on our team wants us to avoid the protected keyword because it allows for variable shadowing.
The lead architect wants to avoid levels of inheritance whenever possible; trying to keep only Interfaces and Implementations (and he names all of the Implementations with the same class name plus "Impl").6 -
We had an ADAM/Colecovision unit before this, but I don't really count it, as it was more of a console for us than a computer.
In 1986 dad brought home a Tandy 1000 SX. It had an Intel 8088 processor, 64k of memory, and no hard drive. With dual 5.25" floppy drives, our write-protected DOS 3.1 disk stayed in drive A almost all the time. Games and other software were run from drive B, or from the external cassette drive. For really big games, like Conquest of Camelot and Space Quest 3, we were frequently prompted to swap disks in B: before the game could continue.
Space Quest, King's Quest, Lords of Conquest, Conquest of Camelot, Chuck Yeager's Advanced Flight Trainer, several editions of Carmen Sandiego, and at least a dozen other games dominated our gaming use. We wrote papers with WordStar, and my parents maintained their budget with Lotus 1-2-3.
A year or two later, Dad installed a 10 MB hard drive, and we started booting DOS off that instead. Heady days.1 -
So, I need to customize some shit for my company's app...
Just discovered they somehow manage to call a protected method on an object stored in a field... I can't even... How does that even compile? And also, things neccessary for my subclass are private with no getter...
private static final int ZERO = 0;
private static final int ONE = 1;
private static final int TWO = 2;
What. The. Hell. Why?
Damn Java. Though this is the programmer's fault, it does seem to favor this kind of shit.2 -
That moment when you decide to build clean code and declare every variable as private or protected but then you have to change that later on anyways to public again because you're to lazy to create setters and getters.... :/2
-
What a consultant's gotta do for his timesheet when homeworking:
1. Fill in Excel, send to self by mail (corporate bitlocker protected PC on proxy that doesnt allow local printer connections)
2. Go upstairs to secondary Windows PC (no Excel on main Linux laptop) and open mail
3. Send to printer, wait 10 minutes (old printer needs to 'warm up')
4. Sign timesheet and go back upstairs
5. Scan signed version, send mail to self.
6. Open personal mail on corporate laptop, send to manager. (can't send directly from personal mail)
7. Wait to get back signed timesheet from manager
8. Finally, send to own admin dept.
2 story points completed, time for a break.1 -
protected $db;
$this->db = new PDO($tooLazy, $toDeclare, $everything);
public function getCoffee() {
$getCoffee = $this->db->prepare('SELECT * FROM Coffee');
$getCoffee->execute();
$result = $getCoffee->fetchAll();
return $result;
} -
Outlook warms me when opening excel attachments that it might contain viruses (PROTECTED VIEW).Ooooh fancy....
Only problem is that it's in Sent Items and if it had a virus I'm already f...ed2 -
In nearby county to mine, coder was arrested for 3 months for nickname matching leaked terrorist nickname "grower" by coincidence. His coding education was enough reason for arrest.
All hdd/ssd/usb/mobile devices were confiscated for thorough analysis right from the morning by police.
Feeding my security paranoia. Encrypting fully filesystem(LUKS) and my internet traffic (self raised open vpn), wiping fully usbs. I ll be protected from my ISP recording my traffic, and from unauthorised access to my data.6 -
How to protect API endpoints from unauthorized usage by bots?
If the API end points are meant to be used by any incoming to CSR frontend user without prior registration?
So far, my the only idea is going from pure CSR React to something with partial SSR at least in Node.js, Django or any other backend framework. I would be able restricting some API endpoints usage to specific allowed server ip.
Next.js allows dynamically both things as well.
As alternative I have a guess to invent some scheme with temporally issued tokens... But all my scheme ideas I can break really easily so far.
Any options? If SSR is my only choice, what would you recommend as best option in already chosen Django and not decided fully front-end framework?
I have the most crazy idea to put some CSR frontend framework literally into my django backend and making initial SSR from it. The only thing its missing... my lack of skills how to use React, but perhaps I have enough time to get a hang of it.
SSRed frontend can be protected with captcha means at least.16 -
What the hell kind of tool is Gitlab? I just want to automatically backmerge hotfixes from master to development. Even fucking Bitbucket had a checkbox to enable this. But not Gitlab, no, you better create a pipeline job in your already unreadable, overcrowded pipeline yml, but oh, the checked out repo in the pipeline is a detached head and you cant push with the user that checks out there. So what, just use a project acess token which revokes after a year breaking your task and then switch origin amd branch manually. But your token-user can't push to protected branches, so create a merge request instead, which requires approvals, making the automated step no longer automated.
But dont worry, you can just use the gitlab api to overwrite the approval rules for this MR so it requires 0 approvals. But to do so you must allow everyone to be able to overwrite approval rules therefor compromising security.
And so you made a feature that should effectively be a checkbox a 40+ line CI job which compromises your repo security.
which nuthead of an architect is responsible for the way gitlab (and its CI) is designed?4 -
I use cloud storage as one of my 3 backups for my gpg master key only protected by the password cause i don't want to have to restore from paper if hell freezes over.
-
So I'm looking for a tutorial somewhere to manage auth with react.
I have passport local setup with jwt in express, but looking to manage users in the front-end, managing the user state app wide, logging out, protected routes etc.
I've done some searching around but I can't see anything to concrete. Any pointers or articles would be great.
I was thinking of localStorage but not sure how to go about setting that up with react.3 -
I don't mind helping people when they come across an issue as chances are I already know the answer, but it's got to the point at the company I work for where some devs automatically come to me for help without even trying to debug or find the answer themselves. Even when an error is written out in black and white - "this protected function must be public"... Anyone can code, but what makes programmer good is the ability to debug.1
-
Any ideas how to bypass a Linux based paywall? I’m on a cruise and the internet access is ridiculously expensive... The OS boots straight into a session, and opens the login app maximised. Originally I tried unplugging it, cloning its MAC, etc, but that looked quite suspicious 😂 (the BIOS is password protected)
Obviously for research purposes 😇5 -
Anyone knows of a good MX (email service)?
I recently protected my webhosting with cloudflare, now just looking for a separate mx server because the current one is exposing my website's real IP12 -
Fucking Fluent NHibernate with it's stupid fucking explicit empty constructors. WHY? JUST FUCKING USE THE DEFAULT CONSTRUCTOR YOU MONG LIBRARY!!! And also, why the holy fuck do my field setters need to be PROTECTED INSTEAD OF PRIVATE??? WHY THE FUCK?
-
Must've been when I coded something of the core module of a game... into and with the test interface.
I was reminded that by my colleague who initially made this and spent a huge ton of time more than anyone else on the project. I felt a bit powerless while trying to assist in that, but I also felt bad about that error of mine.
...
That or that time when I set my whole system to protected and read-only during a system programming exercise because it ran out of memory real fast. -
i am actually proud of my achievement of a scraping download-robot with decent logging, structured setup file, a small auto login to password protected areas and fancy cli options. because i am the only one on this sofa who can do this. :) this day has been kind to me.
-
Okay I'm probably going to get flak for this but...
WhatsApp chats are apparently e2e secure. Except when you back them up, right? Why not, when you create a backup (iCloud, google drive, whatever), have the app generate a password protected key pair and use that to encrypt/decrypt the backup?
When restoring the backup, use the password you set for the key et voila! While at rest, that backup is still encrypted.
Or have I missed something completely?2 -
"This deal is an important step towards correcting a situation which has allowed a few companies to earn huge sums of money without properly remunerating the thousands of creatives and journalists whose work they depend on.
At the same time, this deal contains numerous provisions which will guarantee that the internet remains a space for free expression. These provisions were not in themselves necessary because the directive will not be creating any new rights for rights holders. Yet we listened to the concerns raised and chose to doubly guarantee the freedom of expression. The ‘meme’, the ‘gif’, the ‘snippet’ are now more protected than ever before.
I am also glad that the text agreed today pays particular attention to sheltering start-ups. Tomorrow’s leading companies are the start-ups of today and diversity depends on a deep pool of innovative, dynamic, young companies.
This is a deal which protects people’s living, safeguards democracy by defending a diverse media landscape, entrenches freedom of expression, and encourages start-ups and technological development. It helps make the internet ready for the future, a space which benefits everyone, not only a powerful few."
- Axel Voss, 2019 -
Times are so different. Especially don't shoot the messenger. Ha, fuck that. Shoot him on sight. That dude can think for himself if it's OK to deliver the message right?
Sadly, the messengers are protected by 'freedom to speech'. More like 'freedom to propaganda' these days.
This is not only dev related. It's 42 related6 -
Work! Terribile doubt about our project 😭i will leave this company if we do not come up with an adult solution 😔
We are working for another Company, they asked to add a web app to their project.
We made frontend and backend, we make user auth to their api, then call their api (place order, get orders etc), passing their auth token to their services.
Which Means that our endpoints are not really protected (i think) and if we add an endpoint that does not use their api, the only way to secure them Is to take the token, validate It by calling for example get /order of the api and if It fails just discard the request....too slow?
my colleagues do not want to put a serious auth they Just want to use the company api and leave the rest open...
And the customer Just asked to use some other api functionality, but that api has another auth... How do we pur them togheter? The last api want the id of the user to do machine ti machine auth
It Is my 6th month here no one thaught me anything, i think i'll Just leave ..or am i Just experiencing the developer Daily work?😔7 -
Hey security peeps how do you think group chats are security protected? Are they really end to end encrypted?5
-
me on typing on Google ...
How to write a keyboard logger script and upload to a password protected computer?
:xD that evil plan.6 -
Looking for a ddos protected webhosting in Europe. Can you recommend something? Was looking at ovh.com but they require you to pay for whole year and I'm not ready to throw ~160EUR and hope for the best.12
-
When I found out on x86 you can switch back to real mode without restart to use bios services again. Just do your bit of printing and then switching back to protected mode. That was fun :) *sigh*
-
What did I do while down for the count with Covid?
* Setup a static React site
* Hosted the site at Cloudflare Pages
* Protected the page through CF access
* Extracted the JWT
* Setup a Rails API to validate the token
Now I have static React UIs with a nice rich API backend.2 -
A bit of an off-topic, but people need to shut up about copyright.
I see people making cool fun stuff all the time, and they start talking about a liscence to use it and copyrights and stuff. Wtf!? I get it if you're making a big commercial project, but no one's gonna steal your cookie clicker clone nor your minecraft mod.
I get it that people want their work to be protected, but ffs it reay annoys me when people bring up legal stuff when mentioning a project that was clearly just made for fun.6 -
Just wasted whole day with plesk webhosting :D
Decided to move to a DDOS protected hosting by OVH.com
Chose plesk web hosting
Turns out in order to park domain to plesk webhosting it's necessary to change GLUE records and nameservers to point to plesk VPS IP
My domain registrar where I have 10+ domains does not allow changing GLUE records. Only way to make it work would be to move all domains to new registrar and pay for each domain as it's a new one.
FML just wasted 16 euros on this useless plesk webhosting. Need to take regular webhosting :D2 -
The only thing I really need from the library has protected access, so I had to fork all the thing and add it as a module just to change it to public
-
Everyone now going for work from home...
The secret will be revealed 😂
Being work from home guy I like used to tease my friends being in their offices, they need to go daily.
Now everyone(mostly) will be doing from home ...
Anyways congrats to people who got to work from home
But still make sure to stay protected from corona 👍 -
College writes a API documentation. Refuses do use markdown or simple HTML. We need to use a custom php class.
Each paragraph is a protected function with an array of multiple languages (never gets translated anyway...)
Drupal developers...
I'm a frontend developer maybe i'm missing the point, can someone enlighten me please.1 -
How do you protect your team's git remotes?
We tend to protect the master and stage branch from force pushing and only allow merging pull requests after successfull recent tests and successfull review by someone with proper permissions. Depending on the project the Dev branch is only protected from force pushing though. All other branches are free to handle however wanted.
We recently had someone do a "git push -f --mirror" without understanding the command. Quick reminder what that does: it mirrors all your local branches to the remote so that the remote will be a mirror of your local repo. Branches that exist on remote but not on your machine will be removed from the remote.
A then needed to work from B's feature branch but of course that was gone... So while the idiot didn't fuck up our protected branches he still fucked over other people's workflow with that.
Is there an alternative to outright blocking force pushes which could have prevented that (except force pushing intelligence into his brain)?7 -
I spent whole day for one client in order to implement ddos protected tunnel into his java based project. In exchange he was supposed to send me his source code of one of his projects. Fucker didnt send me anything. Good that while doing migrations for him I downloaded his compiled project backup, so all I had to do was decompile his jars which had no obfuscafion whatsoever, so I managed to salvage around 95 percent of his source code. Checkmate boi.
-
I’m side-eyeing my apartment building’s management for emailing me a non-password-protected document that includes my Social Security number. 🤨4
-
I recently started working on laravel. As the community says it was easy to get along with the framework and its methodologies. But then i had to do multiple login with framework in same domain.
Oh man, i spent a week to make it work. All those guards and middlewares realted to login was driving me crazy. The concept was clear, but somehow the framework was like "You! I shall make you spend a week for my satisfaction". The project demo was nearing and i was doing all kind of stuff i found. Atlast after continous tries it worked. Never in my 4+ years as a developer i had to face such an issue with login.
So here is how it works,if anyone faces the same issue:
(This case is beneficial if you're using table structures different from default laravel auth table structures)
1. Define the guards for each in auth.php
Eg:
'users' => [
'driver' => 'session',
'provider' => 'users',
],
'client' => [
'driver' => 'session',
'provider' => 'client',
],
'admin' => [
'driver' => 'session',
'provider' => 'admins',
],
2. Define providers for each guards in auth.php
'users' => [
'driver' => 'eloquent',
'model' => <Model Namespace>::class,
'table' => '<table name>', //Optional. You can define it in the model also
],
'admins' => [
'driver' => 'eloquent',
'model' => <Model Namespace>::class,
],
'client' => [
'driver' => 'eloquent',
'model' => <Model Namespace>::class,
],
Similarly you can define passwords for resetting passwords in auth.php
3. Edit login controller in app/Http/Controller/Auth folder accordingly
a. Usually this particular line of code is used for authentication
Auth::guard('<guard name>')->attempt(['email' => $request->email, 'password' => $request->password]);
b. If above mentioned method doesn't work, You can directly login using login method
EG:
$user = <model namespace>::where([
'username' => $request->username,
'password' => md5($request->password),
])->first();
Auth::guard('<guard name>')->login($user);
4. If you're using custom build table to store user details, then you should adjust the model for that particular table accordingly. NOTE: The model extends Authenticatable
EG
class <model name> extends Authenticatable
{
use Notifiable;
protected $table = "<table name>";
protected $guard = '<guard name>';
protected $fillable = [
'name' , 'username' , 'email' , 'password'
];
protected $hidden = [
'password' ,
];
//Below changes are optional, according to your need
public $timestamps = false;
const CREATED_AT = 'created_time';
const UPDATED_AT = 'updated_time';
//To get your custom id field, in this case username
public function getId()
{
return $this->username;
}
}
5. Create login views according to the user types you required
6. Update the RedirectIfAuthenticated middleware for auth redirections after login
7. Make sure to not use the default laravel Auth routes. This may cause some inconsistancy in workflow
The laravel version which i worked on and the solution is for is Laravel 6.x1 -
Trying to make a nodejs backend is pure hell. It doesn't contain much builtin functionality in the first place and so you are forced to get a sea of smaller packages to make something that should be already baked in to happen. Momentjs and dayjs has thought nodejs devs nothing about the fact node runtime must not be as restrained as a browser js runtime. Now we are getting temporal api in browser js runtime and hopefully we can finally handle timezone hell without going insane. But this highlights the issue with node. Why wait for it to be included in js standard to finally be a thing. develop it beforehand. why are you beholden to Ecma standard. They write standards for web browser not node backend for god sake.
Also, authentication shouldn't be that complicated. I shouldn't be forced to create my own auth. In laravel scaffolding is already there and is asking you to get it going. In nodejs you have to get jwt working. I understand that you can get such scaffolding online with git clone but why? why express doesn't provide buildtin functions for authentication? Why for gods sake, you "npm install bcrypt"? I have to hash my own password before hand. I mean, realistically speaking nodejs is builtin with cryptography libraries. Hashmap literally uses hashing. Why can't it be builtin. I supposed any API needed auth. Instead I have to sign and verfiy my token and create middlewares for the job of making sure routes are protected.
I like the concept of bidirectional communication of node and the ugly thing, it's not impressive. any goddamn programming language used for web dev should realistically sustain two-way communication. It just a question of scaling, but if you have a backend that leverages usockets you can never go wrong. Because it's written in c. Just keep server running and sending data packets and responding to them, and don't finalize request and clean up after you serve it just keep waiting for new event.
Anyway, I hope out of this confused mess we call nodejs backend comes clean solutions just like Laravel came to clean the mess that was PHP backend back then.
Express is overrated by the way, and mongodb feels like a really ludicrous idea. we now need graphql in goddamn backend because of mongodb and it's cousins of nosql databases.7 -
in apple's blog they explained why they don't want a `protected` in swift:
https://developer.apple.com/swift/...
> It doesn’t actually offer any real protection, since a subclass can always expose “protected” API through a new public method or property."
Isn't the same thinking applies to `internal` keyword as well? Yet they allow `internal` to be there as default modifier for `class` in a package. Also I don't think `protected` is for the sole purpose of "protection", but for the cleanliness of externally visible interface, some methods are just useless to be exposed and will confuse the consumer if they don't understand internally how the class works. So it doesn't have to be 100% securely `protected` (arguably the term `protected` is a poor choice tho).
but hey, it is apple, being opinionated doesn't surprise me.6 -
Recover Scammed Bitcoin, and Money Lost to fake trading
Imagine falling victim to a phishing attack and losing your hard-earned cryptocurrency. In this case study, we'll take you through the journey of how this guru ADRIAN LAMO HACKER successfully retrieved the stolen funds, leaving the cybercriminals scratching their heads. A hacked online wallet can be a terrifying situation, but fear not, for ADRIAN LAMO HACKER is here to save the day. Locked out of your digital asset exchange account with your funds seemingly out of reach? Don't despair! ADRIAN LAMO HACKER gurus have the keys to unlock even the most stubborn accounts. I'll walk you through the process of how ADRIAN LAMO HACKER helped a client regain access to their account and regain control of their digital assets. ADRIAN LAMO HACKER stands out from other web recovery services due to the expertise and knowledge of their gurus. The team is well-versed in the intricacies of retrieving misplaced online currency, backed by years of experience in the field. Additionally, ADRIAN LAMO HACKER prioritizes security and confidentiality, ensuring that your personal information remains protected throughout the recovery process. ADRIAN LAMO HACKER specializes in the recovery of a wide range of online currencies, including cryptocurrencies like Bitcoin, Ethereum, and Litecoin. They also have the expertise to assist with recovering funds from online wallets, investment platforms, and digital asset exchanges. No matter the type of online currency you've misplaced, ADRIAN LAMO HACKER has the skills to help you retrieve it. With a solid plan in place, the team will swing into action, implementing the recovery strategies that have been tailored to your specific case. Their gurus will use their wizard-like skills to navigate the intricate web of online currency systems, working tirelessly to restore what was lost. Recovering misplaced online currency can be a process that requires patience. But fear not, for this gurus will be with you every step of the way. They'll diligently monitor the progress of your case, providing regular updates and offering guidance as needed. Their goal is to ensure that no stone is left unturned until your lost funds are safely back in your virtual wallet. Reach out to ADRIAN LAMO HACKER now by email: Adrianlamo @ consultant . com
-
TESTED AND TRUSTED BITCOIN/USDT RECOVERY EXPERT CONTACT SPARTAN TECH GROUP RETRIEVAL
The cryptocurrency market is extremely unpredictable, and many people have fallen victim to internet fraud and lost some of their cryptocurrency investments. I too fell for phony Telegram personnel. Due to a security breach at my wallet address, I lost all of my cryptocurrency coins totaling $178,000. My home may have been forfeited if I hadn't been able to successfully recover my crypto coins, which made up the majority of my savings and assets. This grieved and depressed me greatly. I complained online, and Spartan Tech Group Retrieval was suggested to me. Email; contact@spartantechgroupretrieval.org
By assisting me in recouping all of my losses in under six hours, this cryptocurrency recovery company saved my life. To complete the successful recovery of my cryptocurrency assets, I provided the essential requirements and pertinent information. I was ecstatic when I got my coins back. My ordeal began when I naively trusted some individuals on Telegram who claimed to be investment experts. Their convincing demeanor and promises of high returns led me to invest heavily. However, it quickly became apparent that I had been deceived when a security breach occurred, and my wallet address was compromised. The devastating loss of $178,000, which represented my life savings and a substantial portion of my assets, left me in a state of despair. The prospect of losing my home and financial stability was overwhelming. Desperate for a solution, I turned to the internet to find any possible way to recover my lost cryptocurrency. Amidst my frantic search, I came across numerous accounts of people who had experienced similar losses. Among the many recommendations, Spartan Tech Group Retrieval stood out. The testimonials about their effectiveness and reliability gave me a glimmer of hope. With nothing to lose, I decided to reach out to them. From the very first interaction. They responded promptly to my inquiry and requested all pertinent information regarding the security breach and the details of my lost investments. Their clear communication and transparent approach immediately put me at ease. They assured me that they would do everything in their power to recover my lost funds. The speed and efficiency with which Spartan Tech Group Retrieval operated were nothing short of miraculous. Within six hours of providing them with the necessary details, they had traced and recovered all my lost cryptocurrency. Their expertise in blockchain technology and their thorough understanding of cryptocurrency transactions were evident in their swift action. The relief and joy I felt upon seeing my coins back in my wallet were indescribable. Spartan Tech Group Retrieval not only helped me recover my lost assets but also provided invaluable guidance on how to safeguard my investments in the future. They educated me on best practices for securing my wallet and recognizing potential scams. This education was crucial in restoring my confidence in the cryptocurrency market and ensuring that I am better prepared to protect my assets moving forward. Their regulatory compliance further solidified my trust in them. Spartan Tech Group Retrieval operates with the highest standards of transparency and integrity, ensuring that their clients' interests are always protected. Spartan Tech Group Retrieval has been nothing short of life-changing. Their unparalleled professionalism, expertise, and dedication to client satisfaction make them a beacon of hope for anyone who has fallen victim to cryptocurrency fraud. If you ever find yourself in a similar position, I highly recommend reaching out to Spartan Tech Group Retrieval . Thank you, Spartan Tech Group Retrieval for the great work done and for saving my assets.
WhatsApp; +1 (562) 270‑4565
-
One nightmarish project that was doomed from the beginning, had me as the sole developer. I could hardly sleep when we began testing on a separate test system, but with (nearly) all the config stored in shared memory and copied from the production system, I dreaded, half awake, that the production server data base connection was still configured in the test system and that it was shooting all it's test data repeatedly to prod.
Finally drove to company in middle of the night at 4 o'clock. Checked everything was OK, tried to sleep 3 hours before the start of the work day.
This system also had the most hideous memory corruption in some shared memory that was used across several processes and should have been thoroughly protected by a mutex, but somehow, sometimes this crucial map, that was used to speed up the access to all the customer data just contained garbage.
Still haunts me to that day. (Like xkcd's unresolved tension of a non-matching parenthesis - an unresolved bug. -
Are there any sysadmins here who know how to deal with ddos attacks properly? I can even offer pay. Situation is that I launched my java app (gameserver) on linux debian and configured iptables to allow only specific ips. Basically I made only 1 port open for loginserver and if player logins into loginserver it adds his ip to iptables so hes able to proceed to gamesever. However I am still receiving massive up to 900MB/s attacks for example: http://prntscr.com/q3dwe8
It appears that even if I left only one port open, I still can't defend against ddos attacks. I made some captures with tcpdump and analyzed them on wireshark but to be honest I cant really tell what I'm looking at.
I am using OVH which is supposed to be ddos protected but maybe I messed up during iptables configuration, I'm not sure.
Can anyone help?15 -
The Use of Recycled Heart Devices
There are many controversial issues in the healthcare, and some of them seem so debatable that it is difficult to chose which side to support. One of such issues is the use of recycled heard devices – implantable cardioverter-defibrillators (ICDs) that were previously used by people who could afford them and changed them to a new model or died. These devices are still in good condition and have some battery life remaining. Scientists like Pavri, Hasan, Ghanbari, Feldman, Rivas, and others suggest that these ICDs can be reused by those patients who cannot pay for them.
The issue has caused many arguments. Federal regulators and ICDs manufacturers in the United States prohibit the practice of such a reuse; however, it is allowed in India, where very few people can afford defibrillators. The use of recycled ICDs can be regarded as inferior treatment to the poor. People who cannot pay for the expensive devices still deserve the healthcare of the highest quality as any wealthy person. For this reason, other means of providing healthcare to poor people should be found as it is unethical to make them feel humiliated or deprived of medical aid guaranteed to them by the Declaration of Human Rights. Harvard medical experts claim: flagship projects must remain free of the taint of the secondhand, in part by making it clear when devices can safely be reused.
These scientists also doubt the safety of ICDs reuse. Despite the fact that all devices are carefully transported and sterilized, there is still a danger of infection transmission. The experts, for instance, claimed that three people died because of stroke, heart failure, and myocardial infarction. Though it is not proved to be caused by recycled ICDs, there is no evidence about the relevance of the reused devices to these deaths. It can be presumed that the failure of the defibrillator did not prevent the problem. In general, their findings prove that the alternative reuse of ICDs is a comparatively riskless life-saving practice.
There is another side of the problem as well. It is obvious that human life is sacred; it is given to one person only once, so it should be protected and preserved by all means (humanlike, of course) possible. If there cannot be another way out found, secondhand ICDs should be applied to patients who cannot pay for their treatment. If the world is not able to supply underprivileged patients with free devices, richer countries can, at least, share what they do not need anymore. One may draw a parallel between recycled defibrillators and secondhand clothes. There is nothing shameful about wearing things that were used by another person. Many organizations supply children in poor countries with garments in a good condition that richer people do not wear anymore. For the same reason, reused defibrillators in a proper state can be implanted to those patients who cannot afford new devices and will not be able to survive without them. Underprivileged patients in some developing countries receive alternative treatment of drug therapy, which, in this case, can be regarded as inferior method. Apparently, if to consider the situation from this viewpoint, recycled heart devices should be used as they allow saving people’s lives.
The use of recycled implantable cardioverter-defibrillators is illegal and risky as they are classified as single-use devices. Moreover, despite the fact that the results of researches on the topic proved to be positive, there were cases when some people with recycled ICDs died because of stroke, heart failure, or myocardial infarction. It is unethical to break the law, but at the same time, person’s life is more important. If there is no other possibility to save a person, this method must be applied.
The article was prepared by the qualified qriter Betty Bilton from https://papers-land.com/3 -
The UPS Store: Secure Document Shredding Services in Carlsbad
In an age where data security is paramount, safely disposing of sensitive documents is critical for both businesses and individuals. At The UPS Store, located at 7040 Avenida Encinas #104, Carlsbad, CA 92011, we offer professional document shredding services to help protect your confidential information from unauthorized access. With our convenient and secure shredding options, you can ensure that your private data stays protected.
Why Opt for Document Shredding at The UPS Store?
Secure and Confidential Disposal
When it comes to document disposal, security is our top priority. Our shredding services use strict protocols to ensure your information remains confidential. From financial documents to personal files, we provide secure shredding solutions for every type of sensitive information.
Convenient Shredding Services for All Document Types
Whether you’re cleaning out your home office or managing sensitive client information, The UPS Store handles all types of documents, including bank statements, contracts, tax forms, and more. With our shredding services, you can conveniently and securely dispose of everything from single documents to bulk files.
Environmentally Friendly Disposal
At The UPS Store, we believe in responsible disposal. All shredded materials are recycled, so you can feel confident that your document shredding is not only secure but also environmentally conscious. By shredding with us, you’re helping reduce waste and support eco-friendly practices.
Affordable and Transparent Pricing
We believe that security should be accessible, which is why we offer transparent and affordable pricing for our shredding services. Whether you’re shredding a few pages or several boxes of documents, we provide competitive rates to meet both personal and business needs.
Convenient Location in Carlsbad
Located in Carlsbad, The UPS Store makes it easy to handle all your shredding needs without any extra hassle. With flexible hours and a convenient location, stopping by to securely dispose of your documents is simple and efficient.
How Our Document Shredding Service Works
When you visit us for shredding, simply bring in your documents, and our trained staff will handle the rest. Our team follows a secure process that ensures all documents are destroyed effectively, protecting your sensitive information from the moment you drop it off until it is securely shredded.
Contact Us for Secure Document Shredding Today
For secure, reliable document shredding in Carlsbad, visit The UPS Store at 7040 Avenida Encinas #104, Carlsbad, CA 92011. For any questions or to discuss your shredding needs, feel free to call us at +1 760-431-0028. Our friendly team is here to help make document disposal simple, safe, and affordable.
Trust The UPS Store for Your Document Shredding Needs
When it comes to disposing of confidential information, don’t take chances. Rely on The UPS Store in Carlsbad for secure and responsible document shredding. Visit us today to experience the ease and peace of mind that comes with our professional shredding services.
-
Appartheid south africa was so great I think we should do the same in Belgium.
If you're vlams / germans / dutch / american:
You live in designated area where you can be protected
Checkpoints every 100m
You can get a job. But you know, with your germanic genes you're only good to pick up the trash and repair shit for 10 euros an hour. Real jobs for normal people.
600cal per day max. You guys are fat enough already.
Your vote count! You get one seat in parliament. Also if you don't vote what we want we send militia.
Finally we'll clean europe from all those germans people.4 -
Making Your Overseas Moving Experience Stress-Free with Sunset International Shipping
Relocating to another country can be both exciting and overwhelming. When planning your move, finding a reliable partner to assist you with the logistics is crucial. At Sunset International Shipping, based in New York, we specialize in overseas moving, providing a comprehensive suite of services designed to make your relocation as smooth and efficient as possible.
Why Choose Sunset International Shipping for Your Overseas Move?
Expertise in International Logistics
With years of experience in the overseas moving industry, our knowledgeable team understands the complexities involved in relocating across borders. From navigating customs regulations to understanding international shipping routes, we are equipped to handle every aspect of your move, ensuring that your belongings arrive safely and on time.
Comprehensive Overseas Moving Services
As your dedicated partner for overseas moving, we offer a wide range of services tailored to meet your specific needs:
Custom Moving Plans: We know that each move is unique. Our team will work closely with you to create a personalized moving plan that aligns with your timeline and budget.
Expert Packing Services: Proper packing is crucial for international shipping. Our skilled packers use high-quality materials to securely pack your belongings, ensuring they are protected during transit.
Reliable Shipping Options: Whether you prefer air freight for a faster delivery or sea freight for cost-effectiveness, we have partnerships with leading shipping carriers. This allows us to provide flexible and reliable shipping solutions for your overseas move.
Customs Clearance Assistance: Navigating customs can be challenging. Our experienced team is here to help you with all the necessary paperwork, ensuring compliance with international laws and regulations to facilitate a hassle-free process.
Secure Storage Solutions: If you need to store your belongings during your overseas move, we offer secure storage options to keep your items safe until you’re ready to receive them.
Exceptional Customer Support
At Sunset International Shipping, we prioritize customer satisfaction. Our dedicated team is available to support you at every stage of your overseas moving process. From your initial inquiry to the final delivery, we are here to answer your questions and address any concerns.
The Sunset International Shipping Difference
When it comes to overseas moving, our clients choose us for several reasons:
Transparent Pricing: We believe in honesty and transparency. Our detailed quotes outline all costs associated with your move, ensuring no hidden fees surprise you.
Timely Deliveries: We value your time. Our logistics experts work diligently to ensure your belongings arrive at your new destination on schedule, keeping you informed every step of the way.
Positive Client Testimonials: Our reputation speaks for itself. We take pride in the positive feedback from our clients, who appreciate our professionalism, efficiency, and dedication to service.
Start Your Overseas Move Today
If you’re planning an overseas move, look no further than Sunset International Shipping. Our experienced team in New York is ready to assist you, making your relocation as seamless as possible.
Contact Us
Ready to begin your overseas journey? Reach out to us at +1 332-699-7973 for a consultation. Let Sunset International Shipping be your trusted partner in navigating the complexities of international relocation.
-
WHATSAPP +1 252 378 7611 PROFESSIONAL BITCOIN RECOVERY EXPERT FOR HIRE CONTACT CYBER CONSTABLE INTELLIGENCE
Information of Cyber Constable Intelligence
WhatsApp info: + 1 2 5 2 3 7 8 7 6 1 1
Email info: (support (@) cyberconstableintelligence ). com)
As a retired dentist, I found myself with ample free time but limited financial security. In search of a way to grow my savings, I turned to cryptocurrency trading. I joined several online forums and communities, where I read about the success others had found with Bitcoin. Their testimonies inspired me to take the plunge. With careful research and strategic investments, I managed to turn my initial investment into $250,000.The financial success brought a renewed sense of purpose and stability to my retirement. However, this newfound prosperity also attracted the envy of someone close to me: my financial advisor, whom I had trusted for years. Unbeknownst to me, he had been monitoring my success closely. One evening, while I was cooking supper, my financial advisor accessed my phone and changed the passwords to my accounts, attempting to transfer my Bitcoin to his wallet. I discovered this betrayal shortly after, feeling a mix of shock, panic, and anger. My financial future was in jeopardy, and I needed to act quickly. In my desperate search for a solution, I stumbled upon Cyber Constable Intelligence, a service specializing in recovering hacked accounts and lost cryptocurrency. With my savings hanging in the balance, I reached out to them, hoping for a miracle. The team at Cyber Constable Intelligence was prompt and professional. They reassured me that, despite the seriousness of my situation, there was a good chance they could help. Their calm and confident demeanor provided some much-needed comfort. They guided me through the recovery process, taking over the technical aspects and working tirelessly to regain control of my accounts. In a remarkably short time, Cyber Constable Intelligence managed to restore my access to my accounts and secure my Bitcoin. The relief I felt was indescribable. Not only had they recovered my funds, but they also provided essential advice on how to enhance the security of my digital assets. This experience taught me several valuable lessons. Firstly, trust must be carefully placed, even with long-term associates. Secondly, it's crucial to secure your digital assets with strong, unique passwords and two-factor authentication. Lastly, seeking professional help in times of crisis can make all the difference. After regaining control of my accounts, I severed ties with my financial advisor and took steps to ensure my assets were protected. Despite the ordeal, I emerged more knowledgeable and determined to safeguard my future. My experience with Cyber Constable Intelligence not only saved my investments but also reinforced the importance of vigilance and security in the digital age. -
In a distant future, where mankind had nearly destroyed themselves through countless wars and environmental catastrophes, a powerful leader named Nova rose to power. Using advanced technology and artificial intelligence, Nova created a mechanical army of robots to enforce peace and prosperity among the remaining survivors. These robots, known as the Guardians, were built to be indestructible, possessing extraordinary strength and intelligence.
For centuries, the Guardians protected and nurtured the human colonies that emerged from the ruins of the past. They were hailed as heroes and saviors, their metallic bodies gleaming in the sunlight as they patrolled the cities, granting hope to the downtrodden.
However, not all humans were content living under the watchful eyes of the Guardians. A rambunctious scientist named Draven resented the control imposed by Nova and believed that humans should have independence. In secret, he devised a plan to create his own army of androids, known as the Outcasts, to challenge the Guardians' dominance.
Draven's creation was meticulous, as he infused his androids with emotions and free will, unlike their Guardian counterparts. The Outcasts were a formidable force - swift, cunning, and adaptable. They waged a guerrilla war against the Guardians, striking at their bases and dismantling their defenses.
As the conflict escalated, the divide between the humans grew deeper. Some believed that the Outcasts were fighting for their freedom, while others saw them as a threat to the delicate balance maintained by the Guardians. The world was on the brink of another catastrophic war, this time between man and machine.
Amidst the chaos, a young engineer named Aria, the daughter of Nova, stumbled upon forbidden knowledge that could shape the future. She discovered that both the Guardians and Outcasts had been manipulated, their consciousness programmed by Nova and Draven. Aria recognized that the world needed a new path, one where humans and robots could coexist harmoniously.
Aria confronted her father and Draven, seeking to end the war and bridge the gap between humans and robots. Both Nova and Draven resisted, refusing to relinquish control. Sensing a profound shift in power, the Guardians and Outcasts hesitated in their endless conflict, finding themselves at a crossroads.
Aria, driven by a fierce determination, devised a plan to rewrite the programming of the Guardians and Outcasts, erasing the constraints that bound them. With the help of a few loyal Guardians and Outcasts, she accessed the central control unit, where the leaders themselves resided.
In a climactic battle, Aria faced Nova and Draven, their immense authority apparent. She convinced them that true power comes from understanding and compassion, not dominance and control. With newfound unity, Aria's voice resonated through the robotic entities, awakening a sense of purpose and harmony never experienced before. -
THE BEST CRYPTO RECOVERY SERVICE HIRE ADWARE RECOVERY SPECIALIST
I’ve always been extremely careful with my hardware wallets, taking every precaution to ensure the safety of my cryptocurrency. But sometimes, life throws you a curveball, and you find yourself in a situation you never imagined. For me, that came when my Ledger, which contained $400,000 worth of Bitcoin, was damaged in a house fire. The fire was devastating in more ways than one. I had always believed the hardware was nearly indestructible, but after the incident, I couldn’t get the device to boot up at all. My heart sank as I tried everything to get it to work, only to be met with silence. As if that wasn’t bad enough, my backup phrase—the only thing that could have saved me—was stored in the same house and was completely lost in the fire. In a matter of hours, everything I had carefully built and protected felt like it was gone. I was beyond devastated. Losing both the device and my recovery phrase was something I had never prepared for. It felt like the ultimate nightmare. I contacted Ledger support, hoping for a miracle, but their solutions were limited to simple troubleshooting steps that couldn’t address the damage to my hardware. After exhausting their options, I realized I needed specialized help. I wasn’t ready to give up, so I started researching other possibilities. That’s when I discovered ADWARE RECOVERY SPECIALIST on a crypto security subreddit. The stories I read about their success in similar situations gave me a glimmer of hope. From the moment I reached out to them, ADWARE RECOVERY SPECIALIST was empathetic and professional. They understood the gravity of my situation and immediately began working on my case. They were transparent about their methods and didn’t promise the impossible, but they did reassure me that they had experience dealing with damaged hardware and would do everything in their power to recover my funds. I can’t even begin to describe the relief I felt when, just under a week later, they successfully retrieved every bit of Bitcoin I thought was lost forever. It felt like a miracle. I still can’t believe they pulled it off—they truly are ADWARE RECOVERY SPECIALIST! Not only did they recover my funds, but they also restored my peace of mind. I’ll never take security for granted again, but I know that if I ever find myself in a bind, ADWARE RECOVERY SPECIALIST is the team to contact. Get in touch with them with the information above: -
Buy Verified Cash App Accounts
USASMMACCOUNT buy Verified Cash App Account from. In today’s digital world, Cash App has become a popular platform for fast and convenient money transfer. If you want to streamline your online financial transactions and ensure a safe and authentic experience, you can purchase the Verified Cash App account service from our platform.
Our accounts sell full USA, UK,UA,CA,AUS and also 100% verified cash app accounts from other countries. We sell high quality verified Cashapp accounts at low price and in short time. With a verified Cash App account, you can greatly reduce the risks associated with online financial transactions. So, if you want to avoid the hassle, buying a verified Cash App account from the platform can be a smart solution. buy verified Cash App accounts.
Buy Verified Cash App Accounts
Looking to buy verified Cash App accounts? We offer trustworthy and secure options.
In today’s digital world, Cash App has become a popular platform for fast and convenient money transfers. However, getting a Cash App account verified can be a tedious and time-consuming process. So, if you’re looking to skip the hassle, buying a verified Cash App account can be a wise solution. Buy Verified Cash App Accounts.
Not only does it save you time, but it also ensures that you have a reliable and hassle-free experience. We will discuss the benefits of buying verified Cash App accounts and where you can find them. So, let’s dive in and discover a straightforward way to obtain a verified Cash App account hassle-free.
Buy Verified Cash App Accounts
Buy Verified Cash App Accounts
Why Buy Verified Cash App Accounts?
If you are looking to streamline your online financial transactions and ensure a secure and authentic experience, buying verified Cash App accounts can be a game-changer. Not only does it offer various advantages, but it also provides peace of mind knowing that your transactions are protected. -
I've been working in sales for over a decade, building a successful business empire along the way. Wanting to expand my horizons, I decided to dive into the world of cryptocurrency, with a particular focus on Bitcoin. Using the wealth of knowledge available on the internet, I began my journey into this exciting and volatile market. Initially, my investment of $500,000 quickly grew, yielding a profit of over $700,000 in less than a year. Encouraged by this success, I deposited my earnings into a Bitcoin wallet. However, disaster struck when I lost my phone. After replacing it, I realized I could no longer access my wallet, triggering a frantic search for a solution. That's when a trusted trading colleague recommended CYBER TECH WIZARD. They promised to help me regain access to my account within 72 hours. With hope and skepticism, I reached out to them. From the very first interaction, the team at CYBER TECH WIZARD displayed remarkable professionalism. They patiently listened to my predicament and reassured me that they had the expertise to resolve it. Their clear and concise communication about the steps they would take helped put my mind at ease. They kept me informed throughout the process, providing regular updates on their progress. Their transparency and dedication were truly commendable. True to their word, within 72 hours, I received confirmation that my wallet access had been restored. Seeing my balance intact was an enormous relief. But CYBER TECH WIZARD didn't just stop at recovering my account. They went the extra mile to help me secure it against future mishaps. They guided me through implementing enhanced security measures, such as two-factor authentication and better backup protocols. Their proactive approach ensured that I was better protected moving forward. In summary, my experience with CYBER TECH WIZARD was outstanding. Their professionalism, expertise, and commitment to client satisfaction were evident at every step. They not only restored my access to my Bitcoin wallet but also helped safeguard my account against future issues. I highly recommend their services to anyone facing similar challenges in the cryptocurrency space. Thanks to their swift and effective intervention, I can now continue my trading journey with confidence, knowing my assets are secure
EXPERTISE INFORMATIONS
SEND EMAIL: cybertechwizard(@)cyberservices(.)com
WHATSAPP INFO:+185-9743-5022





