Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "token"
-
A tcp packet walks in to a bar and says “I want a beer”, barman says “you want a beer?” and tcp packet says “yes, a beer” .
In high society, TCP is more welcome than UDP. At least it knows a proper handshake.
A bunch of TCP packets go into a bar, until it’s overcrowded. The next day, half as many go in.
A bunch of TCP packets walk into a bar. The bartender says, “Hang on just a second, I need to close the window.”
When I try to send SYNs to chicks, I don’t get any ACKs. Just FINs and RSTs.
IP packet with TTL=1 arrives at bar. Bartender: “Sorry, can’t let you leave…and you don’t get any beer either…”
The worst part about token ring jokes is that if someone starts telling one while you are telling yours, all joking stops.
The great thing about TCP jokes is that you always get them.
The problem with TCP jokes is that people keep retelling them slower until you get them.
I would tell some UDP jokes too but I never know if anyone gets them
The best thing about UDP jokes is that I don’t care if you get them or not.
I had a funny UDP joke to tell, but I lost it somewhere...
The sad thing about IPv6 jokes is that almost no one understands them and no one is using them yet.
I tried to come up with an IPv4 joke, but the good ones were all already exhausted.
A DHCP packet walks into a bar and asks for a beer. Bartender says: “here, but I’ll need that back in an hour!
DHCP jokes only work when there is only one person telling them
The worst part of SSH jokes is that, even when they're not funny, you suck it up and just pretend they were anyway.
The problem with token ring jokes is you need to wait your turn to laugh
I’d make a joke about UDP, but I don’t know if anyone’s actually listening…11 -
Before you're hired:
1. A binary tree?
2. Currying?
3. Higher-order function?
4. How does event loop work?
5. What is prototype?
6. What is encapsulation?
7. Can you draw an algorithm?
After you're hired:
1. Hey, can you add auth token and login to our app?11 -
The GET /users endpoint will return a page of the first 13 users by default.
To request other pages, add |-separated querystring with the limit and offset, as roman numerals enclosed in double quotation marks. Response status is always equal to 200, plus the total count of the resource, or zero when there's an error.
You can include an array of friends of the user in the result by setting the request header "friends" to the base64-encoded value of the single white pixel png.
Other metadata is not included by default in responses, but can be requested by appending ?meta.json to any endpoint, which will return an xml response.
If you want to update the user's profile picture, you can request an OAuth token per fax machine, followed by a pigeon POST capsule containing a filename and a rolled up Polaroid picture. The status code attached to the return postal dove will be the decimal ASCII code for a happy smiley on success, and a sad smiley if any field fails form validation.
-- Every single external REST API I've ever worked with.7 -
Ever wanted cheat codes to devRant? Well, that's weird. But here you go, I guess.
Since the avatars do not use any external assets (Such as images), all avatars are generated. To be friendly to people who want to make third-party devRant clients (such as devRantron), avatars are generated server-side, so that the assets don't need to be distributed, and third-party programmers don't need to work out rendering avatars.
But this allows you to cheat a little.
The devRant avatars API works like this: you request a really long URL from the API, specifying the IDs of each cosmetic item the user has active, and it returns a PNG file. But you don't need an auth token to generate an avatar (which makes sense), so the avatar API is essentially a sandbox you can play around with if you have the time and patience.
You can write a really good avatar previewer with this knowledge, and see your avatar with a white tiger, even if you don't have the ++s 13
13 -
This week I quit the corporate life in favour of a much smaller company (60 people in total) and i never felt so good.
After 3 years in 2 big corporations, I began to hate coding mainly because of:
- internal political games. It's like living inside House of Cards everyday.
- management and non-tech people choosing tech stacks. Angular 4 + Bootstrap 4 alpha version + AG-Grid + IE11. Ohhh yeah. Not.
- overtime (even if it was paid double). I never did a single minute of OT for fixing something that I caused. I spent days fixing things caused by others and implementing promises that other people made.
- meetings. I spend 50-60% of the time in pointless meetings (I tracked them in certain time intervals) but the workload is same like I was working 8 hours / day.
- working in encapsulated environments without access to internet or with limited access to internet (no GitHub, no StackOverflow etc.)
- continuously changing work scope. Everyday the management wants something new introduced in the current sprint/release and nobody accepts that they have to remove other things from the scope in order to proper implement everything.
- designers that think they are working for Apple and are arguing with things like "but it's just a button! why does it take 2 days to implement?"
- 20 apps installed additionally on my phone (Citrix Receiver, RSA Token, Mobile@Work Suite etc.) just to be able to read my email
- working with outdated IDEs and tools because they have to approve every new version of a software.
- making tickets for anything. Do you want a glass of water? Open a ticket and ask for it.
- KPIs. KPIs everywhere. You don't deserve anything because the KPIs were not accomplished.
The bad part of the above things is that they affect your day-to-day personality even if you don't see it. You become more like a rock with almost 0 feelings and interests.
This is my first written "rant". If anyone is interested, I will post different situations that will explain a lot of the above aspects.13 -
Dear Google OAuth,
you might hate me since i spammed you the whole day with access token requests.
But this is all your fault. Because you never gave me ONE SINGLE SHITTY TOKEN!!
WHAT THE FUCK IS THIS "BAD REQUEST" ERROR MESSAGE?!
You're a rich as shit company with thousand and thousands of employees.
OAuth is one of your essentials cause it handles the access to all your services.
So why the hell i cannot get some smart errormessage to debug my shit.
You are like my gf, when she is mad at me and does not tell me why. But even she is a lot easier to debug!7 -
This is not really a rant, but...dude.
I was browsing github for a suitable library when i found a test repo of someone. A script inside and at the top he wrote his authentication token. I first thought it was a placeholder or an example or a test he used. No. I entered the token and could control his instance of the app. I sent him a message to disable this token.8 -
This is just my token of appreciation for the Skype devs. Can't begin to say how much I hate it. Your android app is a joke even after a host of updates, your desktop client is an even bigger joke (atleast Linux Beta version, I know betas aren't supposed to be stable but this is ridiculous).
You have reinvented chat clients to be extremely bulky, cumbersome and very hard to sync across devices. And you have managed to make it "buffer" more than a YouTube video does on a 2G network. I for one, am blown over by how you did that. And to top it all, you can't close the client on Linux atleast! All you did is just override the close button so that it only minimises it. Brilliant piece of work right there!
Why the hell can't you just close the client and run it in the background the proper way like everyone else does? Why does it have to take 20 *** seconds to open a message? The only reason I am stuck with this is some wierdos in the office still only use this. Get your shit together 😡
Ahh.. I feel much better now.18 -
Fuck the memes.
Fuck the framework battles.
Fuck the language battles.
Fuck the titles.
Anybody who has been in this field long enough knows that it doesn't matter if your linus fucking torvalds, there is no human who has lived or ever will live that simultaneously understands, knows, and remembers how to implement, in multiple languages, the following:
- jest mocks for complex React components (partial mocks, full mocks, no mocks at all!)
- token cancellation for asynchronous Tasks in C#
- fullstack CRUD, REST, and websocket communication (throw in gRPC for bonus points)
- database query optimization, seeding, and design
- nginx routing, https redirection
- build automation with full test coverage and environment consideration
- docker container versioning, restoration, and cleanup
- internationalization on both the front AND backends
- secret storage, security audits
- package management, maintenence, and deprecation reviews
- integrating with dozens of APIs
- fucking how to center a div
and that's a _comically_ incomplete list; barely scratches the surface of the full range of what a dev can encounter in a given day of writing software
have many of us probably done one or even all of these at different times? surely.
but does that mean we are supposed to draw that up at a moment's notice some cookie-cutter solution like a fucking robot and spit out an answer on a fax sheet?
recruiters, if you read this site (perhaps only the good ones do anyway so its wasted oxygen), just know that whoever you hire its literally the luck of the draw of how well they perform during the interview. sure, perhaps some perform better, but you can never know how good someone is until they literally start working at your org, so... have fun with that.
Oh and I almost forgot, again for you recruiters, on top of that list which you probably won't ever understand for the entirety of your lives, you can also add writing documentation, backup scripts, and orchestrating / administrating fucking JIRA or actually any somewhat technical dashboard like a CMS or website, because once again, the devs are the only truly competent ones - and i don't even mean in a technical sense, i mean in a HUMAN sense of GETTING SHIT DONE IN GENERAL.
There's literally 2 types of people in the world: those who sit around drawing flow charts and talking on the phone all day, and those WHO LITERALLY FUCKING BUILD THE WORLD
why don't i just run the whole fucking company at this point? you guys are "celebrating" that you made literally $5 dollars from a single customer and i'm just sitting here coding 12 hours a day like all is fine and well
i'm so ANGRY its always the same no matter where i go, non-technical people have just no clue, even when you implore them how long things take, they just nod and smile and say "we'll do it the MVP way". sure, fine, you can do that like 2 or 3 times, but not for 6 fucking months until you have a stack of "MVPs" that come toppling down like the garbage they are.
How do expect to keep the "momentum" of your customers and sales (I hope you can hear the hatred of each of these market words as I type them) if the entire system is glued together with ducktape because YOU wanted to expedite the feature by doing it the EASY way instead of the RIGHT way. god, just forget it, nobody is going to listen anyway, its like the 5th time a row in my life
we NEED tests!
we NEED to know our code coverage!
we NEED to design our system to handle large amounts of traffic!
we NEED detailed logging!
we NEED to start building an exception database!
BILBO BAGGINS! I'm not trying to hurt you! I'm trying to help you!
Don't really know what this rant was, I'm just raging and all over the place at the universe. I'm going to bed.19 -
One comment from @Fast-Nop made me remember something I had promised myself not to. Specifically the USB thing.
So there I was, Lieutenant Jr at a warship (not the one my previous rants refer to), my main duties as navigation officer, and secondary (and unofficial) tech support and all-around "computer guy".
Those of you who don't know what horrors this demonic brand pertains to, I envy you. But I digress. In the ship, we had Ethernet cabling and switches, but no DHCP, no server, not a thing. My proposition was shot down by the CO within 2 minutes. Yet, we had a curious "network". As my fellow... colleagues had invented, we had something akin to token ring, but instead of tokens, we had low-rank personnel running around with USB sticks, and as for "rings", well, anyone could snatch up a USB-carrier and load his data and instructions to the "token". What on earth could go wrong with that system?
What indeed.
We got 1 USB infected with a malware from a nearby ship - I still don't know how. Said malware did the following observable actions(yes, I did some malware analysis - As I said before, I am not paid enough):
- Move the contents on any writeable media to a folder with empty (or space) name on that medium. Windows didn't show that folder, so it became "invisible" - linux/mac showed it just fine
- It created a shortcut on the root folder of said medium, right to the malware. Executing the shortcut executed the malware and opened a new window with the "hidden" folder.
Childishly simple, right? If only you knew. If only you knew the horrors, the loss of faith in humanity (which is really bad when you have access to munitions, explosives and heavy weaponry).
People executed the malware ON PURPOSE. Some actually DISABLED their AV to "access their files". I ran amok for an entire WEEK to try to keep this contained. But... I underestimated the USB-token-ring-whatever protocol's speed and the strength of a user's stupidity. PCs that I cleaned got infected AGAIN within HOURS.
I had to address the CO to order total shutdown, USB and PC turnover to me. I spent the most fun weekend cleaning 20-30 PCs and 9 USBs. What fun!
What fun, morons. Now I'll have nightmares of those days again.9 -
micromanager: "Quick and easy win! Please have this done in 2-3 days to start repairing your reputation"
ticket: "Scrap this gem, and implement your own external service wrapper using the new and vastly different Slack API!"
slack: "New API? Give me bearer tokens! Don't use that legacy url crap, wth"
prev dev: "Yeah idk what a bearer token is. Have the same url instead, and try writing it down so you don't forget it?"
Slack admin: "I can't give you access to the slack integration test app, even though it's for exactly this and three others have access already, including your (micro)manager."
Slack: "You can also <a>create a new slack app</a>!" -- link logs me into slack chat instead. After searching and finding a link elsewhere: doesn't let me.
Slack admin: "You want a new test slack app instead? Sure, build it the same as before so it isn't abuseable. No? Okay, plan a presentation for it and bring security along for a meeting on Friday and I'll think about it. I'm in some planning meetings until then."
asdfjkagel.
This job is endless delays, plus getting yelled at over the endless delays.
At least I can start on the code while I wait. Can't test anything for at least a week, though. =/15 -
I wrote a database migration to add a column to a table and populated that column upon record creation.
But the code is so freaking convoluted that it took me four days of clawing my eyes out to manage this.
BUT IT'S FINALLY DONE.
FREAKING YAY.
Why so long, you ask? Just how convoluted could this possibly be? Follow my lead ~
There's an API to create a gift. (Possibly more; I have no bloody clue.)
I needed the mobile dev contractor to tell me which APIs he uses because there are lots of unused ones, and no reasoning to their naming, nor comments telling me what they do.
This API takes the supplied gift params, cherry-picks a few bits of useful data out (by passing both hashes by reference to several methods), replaces a couple of them with lookups / class instances (more pass-by-reference nonsense). After all of this, it logs the resulting (and very different) mess, and happily declares it the original supplied params. Utterly useless for basically everything, and so very wrong.
It then uses this data to call GiftSale#create, which returns an instance of GiftSale (that's actually a Gift; more on that soon).
GiftSale inherits from Gift, and redefines three of its methods.
GiftSale#create performs a lot of validations / data massaging, some by reference, some not. It uses `super` to call Gift#create which actually maps to the constructor Gift#initialize.
Gift#initialize calls Gift#pre_init (passing the data by reference again), which does nothing and returns null. But remember: GiftSale inherits from Gift, meaning GiftSale#pre_init supersedes Gift#pre_init, so that one is called instead. GiftSale#pre_init returns a Stripe charge object upon success, or a Gift (and a log entry containing '500 Internal') upon failure. But this is irrelevant because the return value is never actually used. Pass by reference, remember? I didn't.
We're now back at Gift#initialize, Rails finally creates a Gift object using the args modified [mostly] in-place by all of the above.
Another step back and we're at GiftSale#create again. This method returns either the shiny new Gift object or an error string (???), and the API logic branches on its type. For further confusion: not all of the method's returns are explicit, and those implicit return values are nested three levels deep. (In Ruby, a method will return the last executed line's return value automatically, allowing e.g. `def add(a,b); a+b; end`)
So, to summarize: GiftSale#create jumps back and forth between Gift five times before finally creating a Gift instance, and each jump further modifies the supplied params in-place.
Also. There are no rescue/catch blocks, meaning any issue with any of the above results in a 500. (A real 500, not a fake 500 like last time. A real 500, with tragic consequences.)
If you're having trouble following the above... yep! That's why it took FOUR FREAKING DAYS! I had no tests, no documentation, no already-built way of testing the API, and no idea what data to send it. especially considering it requires data from Stripe. It also requires an active session token + user data, and I likewise had no login API tests, documentation, logging, no idea how to create a user ... fucking hell, it's a mess.)
Also, and quite confusingly:
There's a class for GiftSale, but there's no table for it.
Gift and GiftSale are completely interchangeable except for their #create methods.
So, why does GiftSale exist?
I have no bloody idea.
All it seems to do is make everything far more complicated than it needs to be.
Anyway. My total commit?
Six lines.
IN FOUR FUCKING DAYS!
AHSKJGHALSKHGLKAHDSGJKASGH.7 -
I finally did it. I finally got rid of that client in a positive, respectful manner.
So basically, my dad has a freelance colleague. For a side project that person asked me to make him a website. My dad mentioned to said person that my sister's boyfriend does web design (he's trained to use autocad for designing the structure of furniture, nothing fancy just straight lines and upside down doors that fail after a while..
So my brother in law charged the guy 400 money for the design. I charged the guy 200 for the programming because my dad forced me to drop down my price to fit the budget because business relationship and he obviously couldn't let my sister's boyfriend not make more money than he deserves.
In the end after waiting on the design for weeks (I literally saw him do it in photoshop all in 2 layers on his laptop in half an hour) I had to rush the project because the due date was coming up. I already had most of it done but I had to redo a good part of the front-end to fit the design structure. I also had to re-do the design in photoshop to get the images and colors I needed, then cut it up into html. So realistically, my sister's boyfriend barely did anything.
Now the deal was that I'd develop the website and perform any updates/upgrades to it. I'd also host it on my webserver for a monthly fee. My sister's boyfriend was to handle any and all content related support.
At first it was all good, I only ever spoke with the guy when he needed a feature added and he paid me well for it. Overall the hit I took in initial development was paying off. As time went by, my sister's boyfriend started ignoring the guy's calls and the guy started calling me instead.
Now, he had this deal with my brother in law where he could charge his time at 35 money an hour. That's about 4 times minimum wage for not doing much.
Then I started to basically take over all support, but I was only allowed to charge 30 an hour. Pretty reasonable still and I wasn't too busy so it was all good.
As time went by I ended up getting asked to do more and more minimal changes. At some point I had done so many minimal changes I had to charge the guy about 2 hours extra that month and he went completely mental saying I can't just work for hours without telling him beforehand. We decided I had to discuss a price before any change. I charged my time on the phone with him twice after that and both times he bitched about me being expensive and once he even said he wanted to leave.
Now comes the fun part. A week ago he had an issue that was 100% support related. He tried calling my sister's boyfriend but the guy obviously didn't pick up. He called my dad about it, and my dad ended up calling my my sister's boyfriend. Now this guy is so slimy, he purposely didn't hang up the phone knowing my dad would use his cell and assume the other party would hang up because calls cost money. The guy heard my dad call my sister's boyfriend and heard him pick up immediately. He went completely mental saying how he wants both of us to always reply and call him back immediately.
This guy was always my lowest priority. He didn't really make me money and his calls and requests were annoying and unnecessary. Add to that that I specifically didn't want to handle support and was forced into it anyway, while all 'design' things (up to figuring out where and how to display a visitor counter) absolutely had to go to my sister's boyfriend..
But regardless of that, I generally replied to his emails within 10-20 minutes and rarely more than 25 hours.
My dad agreed (for us) that we now both had to reply to him within 24 hours. I was now stuck checking my voicemail every couple hours because my sister's boyfriend sucks at life.
During his rant he threatened to leave me, again. That was the point where I said fuck it.
For the past week I've been ignoring his calls. When he emails me I don't take more than 5 minutes replying. This morning I found an e-mail with 4 requests;
He wanted me to make a content-related change;
He wanted me to give him access to the site's Google analytics;
He wanted me to add a feature and write a guide on how to use it;
And fucking finally, he wanted a 'token to transfer his website'.
I promptly emailed him back saying I added his email a week ago and that he'd gotten an email from Google about it then, that I'd changed the content he wanted me to, a price for the last dev task and a token for his domain name, adding that its valid for 35 days and that his new host can contact me to receive a backup file of his website.
Sadly, I do have this on 10-minute dev job to do, but then I'm invoicing him all jobs I haven't invoiced yet and he can find another host willing to deal with his insanity.
The best part is I lose a webhosting client but I'm sure he'll still ask my sister's bitched parasitic boyfriend whenever he needs a photo resized and he'll still pay him 35 money for 2 minutes of work.
Fuck customers.6 -
Front end + back end = Project finished.
This is my first full stack application that I spent a month working on. It's a basic database that holds car information and saves it to a SQL db. I built this using Java Spring/Hibernate for my backend and Node.JS/REACT for my front end. Mariadb handles SQL requests. REACT handles token requests for secure login, that was the hardest part of this whole thing.
I was going to comment on how frequently I feel like garbage and an inadequate excuse of a human being, but today is my birthday and this is the best gift I could get, a finished project from scratch.
I'm 29 today devRant. And I work over the weekend before going back to school, but at least I fucking finished something that I started.
...thanks, for everything. 😄 13
13 -
- Let's make the authentication system so the user can only login in one device at time, because this is more secure.
- You know that this will be a general-public application, right?
- Yeah!
- Sou you want to "punish" users with a logoff on the other device when he tries to login in a new one?
- Yeah!
- But before you said we will use Json Web Token to make the backend stateless.
- Yeah!
- And how will we check if the token is the last one generated?
- We will store the last generated token for this user on a table in our DB.
- So... you are basically describing the old authentication model, with session tokens stored on the backend and communicating them via cookies.
- Yeah, but the token will be sent on the Header, not on cookies
- Okay, so why will we use Json Web Token to do this in the first place?
- Because this is how they're doing now, and this will make the backend stateless.
A moment of silence, please.8 -
@JoshBent suggested that I'd make a blog about security.
Nice idea, fair enough!
*registers domain at provider with discounts at the moment*
*tries to find whois protection option*
"You can add WHOIS protection to your account as an upgrade"
*requests authorization token*
*logs into usual domain name provider account*
*transfers domain name*
*anonymizes WHOIS details within two seconds*
I could've stayed and ask them about the cost etc but the fact that they even HAVE a price for protecting WHOIS data is a no-go for me.
Fuck domain name resellers which ask money for protecting ones WHOIS information (where possible).32 -
I'm losing my fucking mind right fucking here.
Setting an anti-csrf token in the index.php file ONCE. Yes, I triple trillion checked, only fucking once.
Print it to the page as test, fair enough, looks good.
Send an ajax request to the server:
AN ENTIRELY FUCKING DIFFERENT TOKEN 😡
Fucking hell.13 -
A month ago I had some medical tests, the next morning, the clinic's send a email with my results. Oh surprise, unbelievable security flaws. They sent me a link without any kind of authentication, token, or security. I looked at my results, and by entering consecutive and random numbers I was able to download a lot of results and folders of other patients. I wrote an email to the clinic informing them of this situation and their response was "Thank you". Today I have accessed the link and the error is still present. I am going to notify higher health authorities.11
-
Checked the GitKraken save files for fun (kind of a hobby) and oh well.... what a wonder:
They store your fucking GitHub access token in "plain text" in a hex file as you can see in the image.
I checked the token and it works. Wow.
Good job GitKraken ✔
That happens when you're closed source... 27
27 -
On the presentation for my database project my team and I showed a NodeJS + Mongo + VueJS project with cloud storage capability, nothing fancy but did everything from scratch (from token auth and system encryption to the frontend CSS and the database) the teacher made some questions and meh'd at it.
Behold team two's project, WordPress with a standard template and phpMyAdmin, teacher loves it because "it's so beautiful"
Guess who just failed that class?
God I love college, it's the best time investment I've ever done and it'll surely pay out. 11
11 -
Dev: Can you please tell me why you changed this?
Me: Because we need to handle permissions in the app. The quickest way of doing it, according to the docs, is [insert change log here]
Dev: But we can just check for the user's token.
Me: That's not exactly a permission, because...
Dev: I was only showing the information related to the user according to their token.
Me: I understand. But that means you're filtering data, not authorising users to access it. If a user is logged in, but changes query parameters, they can still access data they shouldn't be able to.
Dev: Whatevs.
Le me then proceeds to try to push my changes (that took the whole day to implement), gets a "you need to pull first" message from git, doesn't understand why, logs onto GitHub and realises dev has implemented their "permissions".
I was the one responsible for making those changes. Le dev was meant to be doing other things.
How do I even begin to explain?7 -
Embarrassing moment:
Needed to deliver apk urgent urgently for push notification testing. I was unable to receive push token. Code is right in every way. Couldn't figured out in 15min. Lead comes to my seat and asks what's issue. And hey suddenly I figured it out. It was my wifi closed.. Bullshit 😬😠4 -
@netikras since when does proprietary mean bad?
Lemme tell you 3 stories.
CISCO AnyConnect:
- come in to the office
- use internal resources (company newsletter, jira, etc.)
- connect to client's VPN using Cisco AnyConnect
- lose access to my company resources, because AnyConnect overwrites routing table (rather normal for VPN clients)
- issue a route command updating routing table so you could reach confluence page in the intranet
- route command executes successfully, `route -n` shows nothing has changed
- google this whole WTF case
- Cisco AnyConnect constantly overwrites OS routing table to ENFORCE you to use VPN settings and nothing else.
Sooo basically if you want to check your company's email, you have to disconnect from client's VPN, check email and reconnect again. Neat!
Can be easily resolved by using opensource VPN client -- openconnect
CISCO AnyConnect:
- get a server in your company
- connect it to client's VPN and keep the VPN running for data sync. VPN has to be UP at all times
- network glitch [uh-oh]
- VPN is no longer working, AnyConnect still believes everything is peachy. No reconnect attempts.
- service is unable to sync data w/ client's systems. Data gets outdated and eventually corrupted
OpenConnect (OSS alternative to AnyConnect) detects all network glitches, reports them to the log and attempts reconnect immediatelly. Subsequent reconnect attempts getting triggered with longer delays to not to spam network.
SYMANTEC VIP (alleged 2FA?):
- client's portal requires Sym VIP otp code to log in
- open up a browser in your laptop
- navigate to the portal
- enter your credentials
- click on a Sym VIP icon in the systray
- write down the shown otp number
- log in
umm... in what fucking way is that a secure 2FA? Everything is IN the same fucking device, a single click away.
Can be easily solved by opensource alternatives to Sym VIP app: they make HTTP calls to Symantec to register a new token and return you the whole totp url. You can convert that url to a qr code and scan it w/ your phone (e.g. Google's Authenticator). Now you have a true 2FA.
Proprietary is not always bad. There are good propr sw too. But the ones that are core to your BAU and are doing shit -- well these ARE bad. and w/o an oppurtunity to workaround/fix it yourself.13 -
.... And it appears my Atom has Entered the Matrix. Full time.
In other news, I successfully completed the E-Commerce App I was working on, even though that Stripe Verification was a ball ache and the bane of the entire project giving me a stupid bug in jQuery whereby it was infinite looping over adding the token and not actually submitting the card charge. Somehow changing my button from using an id to using a class fixed my problem :/ (# -> .) 11
11 -
Last week my company thought it would be a great idea to introduce a new sh*tty internal web portal that gives federated access to aws (instead of using our own accounts to assume dev roles like we used to do).
This broke a lot of sh*t that simply used to ask for an MFA token and used our practically permissionless accounts to assume a proper dev role. An MFA token that we'd enter directly into the terminal/tool. It was very seamless. But nooooooo we now have to go a webpage, login with sso (which also requires mfa), click "generate credentials," copy-paste those into terminal/creds file and _then_ continue our aws cli call. Every. Single. Day.
BUT TODAY I HAD ENOUGH.
I spent the entire day rewriting the auth part of our tools so they would basically read the cookie that's set by the web portal, and use it to call the internal api that generates the credentials, and just automatically save those. Now all we need to do is log into the portal, then return to the tool and voilà, the tool's also got access! Sure, it's not as passive as just entering an MFA token directly, but it's as passive as it gets. Still annoyed by this sh*tty and unnecessary portal, but I learned a thing or two about cookies.9 -
Everyone complains that a certain developer's code is not up to standard and when they have to take over his project the lack of code quality is really slowing them down.
I look at code, agree it is poor quality and put together a learning plan for said developer.
Also look at who approved every pull request which allowed bad code into our codebase. Same developers as those complaining it's no good. You had your chance to stop it!7 -
In january 2023 i was contacted by a recruiter offering me a job position.
I DID NOT ASK FOR A JOB.
I WAS NOT LOOKING FOR A JOB.
THEY contacted ME.
Ok. So i went along with it and see how it goes. They probably wont hire me nor would i give a shit. Chatted with this recruiter for a while. She forgets to answer my message for 5 fucking days. Twice. Once because she was doing God knows what and the second time because she was on paid vacation. Fine i don't give a shit about you at all anyways.
So this recruiter chatting has been stretched out for several days. I think over a WEEK. So she forwarded me to their lead developer.
I applied to work as a full stack java spring boot backend + angular frontend engineer.
So:
- java backend
- angular frontend
- full stack
- shitload of devops
- shitload of projects i built
- worked with clients
- have CS degree, graduated
- worked a job at their rival company
What could go fucking wrong with all of these stats right?
During technical + hr interview (3 of us on google meets) they asked me what salary I'd be comfortable with.
I said $1500/month straight out.
keep in mind:
- In my country $500 or $600 is a salary for engineers per month
- You get a raise of +$150 which is around $750 after working for 1+ year
- You can earn $1000+ after you work for +2 years
- Rent here is $200-300 a month at minimun. And because of inflation its just getting worse especially with food. So this salary is not for living but for survival.
Their lead engineer gave me a WHOLE ASS FUCKING PROJECT TO BUILD and i had to code it within 10 days. Great so at least 17+ days of my fucking life to waste on these fucktards who contacted ME.
The project was about building a web app coffee shop literally what mcdonalds has when you order via those tablets. I had to build this in java spring boot and angular. I had to integrate:
- docker, devops
- barmen, baristas, orders
- people can order at the table or to go
- each barista can take 5 orders at a time
- each coffee has different types of fields and brewing time
- each barman brews each coffee different period of time
- barista cant take more than 5 orders for to go until barman finishes the previous order
- barista can take more than 5 orders but if those orders were ordered from table, and they have to be put in queue
- had to build CRUD admin functionality coffee's
- had to export them all of the postman routes
- had to design a scalable database infrastructure for all of this alone
- shitload of stuff more
And guess what. After 10 painful days I BUILT THE WHOLE THING MYSELF AND I BUILT EVERYTHING THEY ASKED FOR. IT WAS WORKING.
Submitted it. They told me they'll contact me within 7 days to schedule the final Technical interview after they review what i built. Great so another 17+7 days of my fucking time wasted.
OH and they also told me to send them THE WHOLE GITHUB REPOSITORY AND TRANSFER OWNERSHIP TO THEIR COMPANY'S OWNERSHIP. once you do this you cant have your repository back. WTF? WHY CANT YOU JUST REVIEW THE CODE FROM MY PUBLIC REPOSITORY? That was so weird but what can i fucking do argue with these dickheads?
After a week of them not answering i contacted them via email. They forgot and apologized. Smh. Then they scheduled an interview within 3 days. Great more of my time wasted.
During interview i was on a google meets with their lead engineer, 1 backend java spring boot engineer and 1 angular frontend developer. They were milking me dry for 1 whole fucking hour.
They only pointed out the flaws in what i built, which are miniscule and have not once congratulated me on the rest of the good parts. I explained them i had to rush those parts so the code may not be perfect. I had other shit to do in my life and not work for your shitty project for $0/hour for 10 days you fucking dickriders.
So they quickly ran over to theory. They asked me where is jwt token stored. Who generates it. How the backend knows to authenticate user by it. I explained.
What are solid principles. I said i cant explain what is it but i understand how it works, why its needed and how to implement it (they can clearly see in the project i just build that i applied SOLID principles everywhere) - but i do admit i dont know the theory behind it 100% clearly.
Then they asked me about observables and promises in angular. I explained them how they work and how subscribe method is used (as they can clearly see that i used it in the code). Then they asked me to explain them under the hood of how observables work. The fuck? I dont know and dont care? But i can learn it as i work there?
Etc
Final result: after dragging this for 1 fucking month for miserable $1500/month they told me: we can either hire you now but for a much lower salary which you probably wont be happy with, or you can study more these things we discussed "and know why the car leaks oil" and reapply back to us in 2-3 months!23 -
Well, for starters there was a cron to restart the webserver every morning.
The product was 10+ years old and written in PHP 5.3 at the time.
Another cron was running every 15 minutes, to "correct" data in the DB. Just regular data, not from an import or something.
Gotta have one of those self-healing systems I guess.
Yet another cron (there where lots) did run everyday from 02:00 to 4ish to generate the newest xlsx report. Almost took out the entire thing every time. MySQL 100%. CPU? Yes. RAM? You bet.
Lucky I wasn't too much involved at the time. But man, that thing was the definition of legacy.
Fun fact: every request was performed twice! First request gave the already logged-in client an unique access-token. Second request then processed the request with the (just issued) access-token; which was then discarded. Security I guess.
I don't know why it was build this way. It just was. I didn't ask. I didn't wanted to know. Some things are better left undisturbed. Just don't anger the machine. I became superstitious for a while. I think, in the end, it help a bit: It feels like communicating with an alien monster but all you have is a trumpet and chewing gum. Gentle does it.
Oh and "Sencha Extjs 3" almost gave me PTSD lol (it's an ancient JS framework). Followed by SOAPs WSDL cache. And a million other things.5 -
So I have seen this quite a few times now and posted the text below already, but I'd like to shed some light on this:
If you hit up your dev tools and check the network tab, you might see some repeated API calls. Those calls include a GET parameter named "token". The request looks something like this: "https://domain.tld/api/somecall/..."
You can think of this token as a temporary password, or a key that holds information about your user and other information in the backend. If one would steal a token that belongs to another user, you would have control over his account. Now many complained that this key is visible in the URL and not "encrypted". I'll try to explain why this is, well "wrong" or doesn't impose a bigger security risk than normal:
There is no such thing as an "unencrypted query", well besides really transmitting encrypted data. This fields are being protected by the transport layer (HTTPS) or not (HTTP) and while it might not be common to transmit these fields in a GET query parameter, it's standard to send those tokens as cookies, which are as exposed as query parameters. Hit up some random site. The chance that you'll see a PHP session id being transmitted as a cookie is high. Cookies are as exposed as any HTTP GET or POST Form data and can be viewed as easily. Look for a "details" or "http header" section in your dev tools.
Stolen tokens can be used to "log in" into the website, although it might be made harder by only allowing one IP per token or similar. However the use of such a that token is absolut standard and nothing special devRant does. Every site that offers you a "keep me logged in" or "remember me" option uses something like this, one way or the other. Because a token could have been stolen you sometimes need to additionally enter your current password when doings something security risky, like changing your password. In that case your password is being used as a second factor. The idea is, that an attacker could have stolen your token, but still doesn't know your password. It's not enough to grab a token, you need that second (or maybe thrid) factor. As an example - that's how githubs "sudo" mode works. You have got your token, that grants you more permissions than a non-logged in user has, but to do the critical stuff you need an additional token that's only valid for that session, because asking for your password before every action would be inconvenient when setting up a repo
I hope this helps understanding a bit more of this topic :)
Keep safe and keep asking questions if you fell that your data is in danger
Reeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee5 -
After working for this company for only a couple years, I was tasked with designing and implementing the entire system for credit card encryption and storage and token management. I got it done, got it working, spent all day Sunday updating our system and updating the encryption on our existing data, then released it.
It wasn't long into Monday before we started getting calls from our clients not being able to void or credit payments once they had processed. Looking through the logs, I found the problem was tokens were getting crossed between companies, resulting in the wrong companies getting the wrong tokens. I was terrified. Fortunately I had including safe guards tying each token to a specific company, so they were not able to process the wrong cards. We fixed it that night.1 -
Raise your hands if you absolutely need a screen to work!
Most of you? Ok.
Well, let me share a story of a dev who doesn't really need a screen at all.
https://youtube.com/watch/...
https://blog.aboutamazon.com/workin...6 -
That moment when you work the whole day to write a discord bot from scratch. No discord.py and other wrappers. Pure websockets, oauth2, https, json loads here and there. Understanding how the discord API works was a real challenge, but I did it :).
Most of my time was spent on discord's gateway connection and identification system.
The bot can renew its token, get all the guilds it is part of, all the channels and users of these guilds, send message and communicate with the gateway.
Tomorrow I will start connecting it to a voice channel and let it "speak". Thinking of combining text-to-speech with it, but I am not sure how well they are going to harmonize together.5 -
he: checkout my crazy FUD hack (a token stealer which turned out to be far more malicious than i anticipated)
me: executes it (yes in a VM)
windows defender: lemme delet this
he: ooh i forgot the word stub in there. microsoft detects that lemme fix that sends new file
me: here we go aga..
ms defender: nononono virus 117% delet this
he: i forgot it still!!
later i deactivated ms defender and analysed the traffic of the vm. in addition to stealing my fake tokens he also tried to read my Firefox/chrome history, IP.
when i asked him (2 days later) what this was all about in his "educational only" "token stealer" he threatened to
a) publish my IP
b) publish my browser history and with that my real name and address
b.0) when i asked him for proof he said he knows that my real name is "Roman Gräf" and i live in Frankfurt. (btw i do live in Frankfurt and that is in the profile of the discord server where he found me and i have the same username on discord as i have here)
c) to kill my machine and all my projects
got bored, blocked him, shut VM down. -
Embedding private encryption key in production javascript file and fetching third party session token client side.4
-
*Working on a project with boss, I am working on a mobile app, he is working on web service app.
Me: this service takes user id as parameter to get all account details (all other web services are like that)
Boss: yes, I use the id to filter the data.
Me: but by this, everyone has the id can do anything ! why we do not use session token?
Boss: this is a detail, it is not important !
Me:...
*7 years of experience my ass 5
5 -
Escalation channel
Q: @here I'm sending a request to X and I'm getting a timeout. Please help.
A: Can you please share the request you're sending?
Q: It's <URL> and I send this token as a Bearer: <token>
A: I understand that, but it's a lot easier to debug if we have the curl for said request. You can find it here: <postman_screenshot_with_arrows>
Q: Here's what it looks like: <postman_screenshot_with_17.4_km_long_curl> 8
8 -
Microsoft Teams can burn.
Who the fuck thought it would be an excellent workflow, when you want to COLLABORATE IN TEAMS between users in different domains, that each sorry bastard needs to manually log in to a second Teams tenant and loose all the context from their main Teams tenant !?
On random occasions the fucking authentication token expires. I send messages to my team mate in another domain. Three days later I am pissed off because they don't answer. It turns out their authentication token has expired so when they are on their main tenant they don't get any notifications before they manually log in to our tenant as a guest. HOW FUCKING GREAT IS THAT AS A NOTIFICATION SYSTEM ??!
Would it be that fucking difficult to maintain a notification bar with all tenants and note with an exclamation mark or something REALLY FUCKING SIMPLE to hint about an expired token ? It's not like this is magic, Slack does it already.
FUCK !7 -
Note to my past self:
Thank you for taking care of me and assuming that out of no fucking sudden authorization token will be required to perform an API call!
You saved me so much refactoring and modifications with your tiny little assumption of how fuckups will think :)1 -
Hope you survived the Monday;)
As I promised, I’d like to post my comic series “Destory” here regularly.
A story about two devs and their funny but serious project, on the hype technology - the blockchain. 6
6 -
Fuck this
I get to work with API where you CAN authenticate with username/password and get a token
But you CAN'T get user info from token (auth response contains ONLY token)
So what I have to do:
1. Get token
2. Request ALL FUCKING USERS and load them into my DB
3. Search through local DB by username and, yeah, here I go
Now I need to have a cron job to update user DB 1/2 times per day
I can't think of ANY reason not to allow this8 -
26 or so hours up now. And I've got a few stories to tell :) feel free to refresh your cup of coffee and take a seat.
Last few days I've been going into this odd place called intown.irl to get in touch with its inhabitants. An odd place I have to say. But in some cases quite rewarding, even got a MILF home with me and into bed at some point. Anyway...
3 days ago I think it is now? Thursday evening I took my laptop to this local bar where I had this issue about dihydrogen monoxide with one of the bartenders earlier (you'll find that rant on those keywords). Still wanted to visit it regardless though, as I met that first woman there earlier that approached me. Unfortunately I didn't see her there that day.
Some bald guy who was clearly drunk approached me. Many people were already giving curious looks at this laptop I brought to the bar. I finally tuned it up with the stickers from FOSDEM.. I'll put a picture of it in the comments. My theme was one of privacy (central), distributions and Google's open source initiative (which aligns with the keychain token I got from them as well). But of course.. that guy.. he thought that a pimped/riced laptop obviously meant that I was a hacker.
Guy went to the toilet.. went back.. and suddenly grabbed my laptop and turned it towards him. Boy was I never more smugly satisfied that those rubber pads on the bottom are quite resilient. Could've almost damaged my screen by trying to grab it like that. But it's a CCFL display.. so high voltage. If it were to become broken.. worth it. 😈
On it at the time was a terminal, pinging Google (had network issues at that bar, to the point where one of the - I think - staff members got up to me and offered the WiFi password and got to talk with me.. more on that later), and my usual Linux desktop along with the Arch anime wallpaper with the quote of Da Vinci.. simplicity is the ultimate sophistication. Of course the guy saw the terminal.. and probably reaffirmed.. yep, that's a hacker. At least he wasn't too wrong about the general term.. but the hat.. most likely he was wrong on that one.
Guy left with this question.. "you are a hacker, aren't you."
I replied to him: "No sir. I'm not a hacker. I've got no idea what you're talking about."
Guy kept looking at me weirdly for the whole night to come.
Back to that companion guy though. Mac user, yada yada.. but he told me about his backup solution. Apparently - I shit you not - he has not only the photos on his local device, he's also frequently backing them up in Time Machine (which I was really curious about whether it uses mirroring or snapshots.. he couldn't tell, lmk if you do) but not only that.. he was storing another offsite backup in that very bar, in case his house went on fire.
Now that is a proper backup scheme!!! If only more people were like that.
Seriously though.. that bald guy who took my laptop just like that... I just let it slide for that one time, but I tend to treat my machines as an extension of my very self. I think that was a very uncalled for move. Asshole...
How would you have reacted to such a thing? And.. maybe that's why we technologists don't get outside too often? Fucking everything is hacking these days if it's not Knopkes and Blinkenlights… Not every shell is a h4xx0ring console for h3kk1ng de fasbuk…9 -
Twilio literally broke my integration because I have not logged into its portal for 2 weeks. Got notified by users complaining SMS wasn’t going through.
 9
9 -
Web3 truly is a fucked up space. All of the fuckertry happening over here is out of control. Literally a dystopian shithole of scams frauds crimes theft and ponzi schemes.... As much as i try to defend web3 since im a web3 dev it's getting real fuckin hard. The more i work in this space the more i understand economics and how all of this shitshow flows.
Without diving into details, I'll tell you right now from a very deep economic perspective: i realized that all of these cryptos are just.. shams, quasi buzz words to keep the "investors" giving them money. Essentially like wolf of wallstreet scams mixed with bernard madoff multi billion dollar ponzi schemes. The "investors" earn a lot of money.... But on paper! As unrealized gains. And by the time they are able to withdraw their money, that money becomes worthless because of insufficient liquidity in the pool that has been drained from top to bottom of the pyramid. So the only person truly getting filty rich is the one on top of this pyramid - the founders!
After the FTX disaster that happened 2 days ago the prices of ALL coins dropped drastically and it isnt stopping. So much for your glorified "decentralization" 😹😹😹😹😹
How can something be decentralized if its enough for 1 influential man to tweet some shit and the company/token price value drops or increases within minutes? In this case the whole of crypto got sliced by 1 influential man... Again. It's only a matter of time until someone else goes bankrupt and cycle repeats... Again.8 -
Boss: "So I'm taking the next week off. In the mean time, I added some stuff for you to do on Gitlab, we'd need you to pull this Docker image, run it, setup the minimal requirement and play with it until you understand what it does."
Me: "K boss, sounds fun!" (no irony here)
First day: Unable to login to the remote repository. Also, I was given a dude's name to contact if I had troubles, the dude didn't answer his email.
2nd day: The dude aswered! Also, I realized that I couldn't reach the repository because the ISP for whom I work blocks everything within specific ports, and the url I had to reach was ":5443". Yay. However, I still can't login to the repo nor pull the image, the connection gets closed.
3rd day (today): A colleague suggested that I removed myself off the ISP's network and use my 4G or something. And it worked! Finally!! Now all I need to do is to set that token they gave me, set a first user, a first password and... get a 400 HTTP response. Fuck. FUCK. FUUUUUUUUUUUUUUUUUUUCK!!!
These fuckers display a 401 error, while returning a 400 error in the console log!! And the errors says what? "Request failed with status code 401" YES THANK YOU, THIS IS SO HELPFUL! Like fuck yea, I know exactly how t fix this, except that I don't because y'all fuckers don't give any detail on what could be the problem!
4th day (tomorrow): I'm gonna barbecue these sons of a bitch
(bottom note: the dude that answered is actually really cool, I won't barbecue him)5 -
Google just emailed me to tell me that I should, "take action against suspicious apps that can access your data"... but the app in question was a Google Drive API token I made for a thing I am personally developing .-.6
-
Might be more of a self-rant.. We’re developing an application with token-based authentication.
It’s a big an complex authentication model and flow, which we wrapped up a month ago. All of us very proud of it.
All of a sudden none of it worked.
We debugged for days, there were no errors or anything to trace what was happening.
Today we realized that we set the expiration of the token to 20 years.
Aaaand the expiration time is later on converted to epoch.
Guess what happens when you try to use a value > 2 147 483 647 in C#? Stuff blows up, cuz that’s the limit of an int32.
So yeah, feels good having prepared for the Y2K38 bug already, even though we’ll be replaced by AI writing better software than my dumb ass by then.
(To be fair, it was hidden in Microsoft Owin, which could use some error handling and/or proper messages..) -
Episode 3 of this rant: https://devrant.io/rants/871827/...
Me: So I'm going an API call to Mastercard but they don't give us back CreditCard token to save.
Provider: Ya man you need to curl a request in your code to get the token...blahblahblah.... man you need to know these things they are not an easy things to be done, just paste curl code on MasterCard website into your code and it will work
Me: *ignores his shit talk and proceed to test*
*5 minutes later*
MasterCard Server: error.cause=INVALID_REQUEST&error.explanation=Invalid+credentials.&result=ERROR
Me: *calls provider and tell him*
Provider: Oh sorry, we need to enable this feature for your account.
devRant people please, give me one reason why I should not leave this field, and maybe also leave this life knowing there are this type of people alive.
Thank you :)2 -
//Dunno what causes these random connection errors; probably just hiccups in connection between our EC2 instance and Discord
try {
client.login(token);
} catch(e) {
//Do nothing, just prevent it from crashing the main thread and the client will reconnect
}4 -
So I wrote a code for a discord bot a few months back. It worked perfectly alright. Suddenly one day, the bot starts sending random shit to me!
Then I realised that my bot had been hacked because I didn't use the bot token as an environment variable while deploying!
Instead I added it to the code, which I uploaded on GitHub! 😐5 -
As a token of my commitment to devRant I bought a new phone so I can use the app. True -fucking- story... Goodbye old buddy #lumia930 (pi) (b)
 4
4 -
Hey here we go:)
My first comic series - “DevStory”
A story of two devs aiming at changing the world’s impact about cryptos by their own token project.
Bugs, cheap scammers, money, flying unicorns and a lot of laughs!
(Episode 1)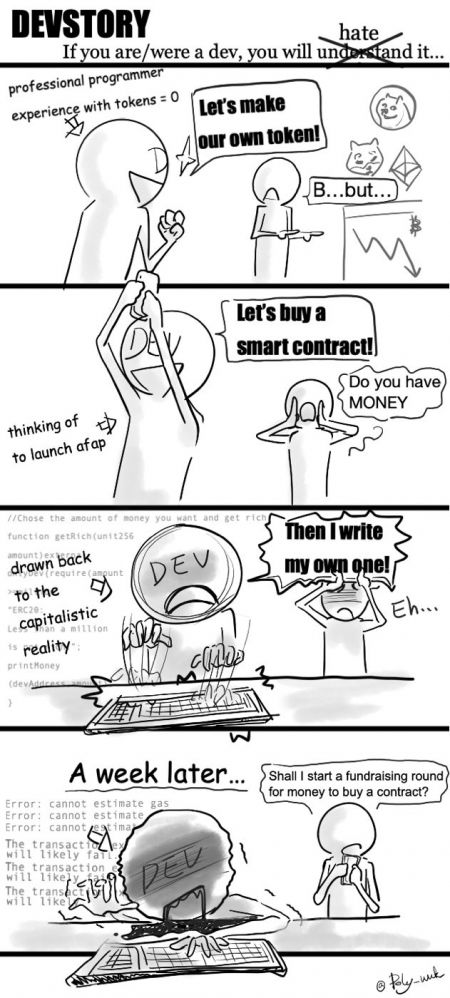 27
27 -
It’s throw back Thursday!
Back to 1979... before the time of the red dragon book compiler book, (forgetting about the green dragon book) ... there was a time where only a few well written compiler and assembler “theory” books existed.
What’s special about this one? Well Calingaert was the co patentor of the OS/360. .. “okay soo? ... well Fred Brook’s Mythical Man-Month book I posted the other day. Calingaert is basically the counterpart of brooks on the OS/360.
Anyway, the code is in assembly (obviously) and the compiler code is basic.
Other than this book and from my understanding 2-3 other books that’s all that was available on compilers and assemblers as far as books written goes at the token.
ALLL the rest of knowledge for compilers existed in the ACM and other computing journals of the time.
Is this book relevant today, eh not really, other than giving prospective, it’s a short in comparison to the red dragon books.
If you did read it, it’s more of a book that gives you more lecture and background and concepts.. rather than here’s a swath of code.. copy it and run.. done.. nope didn’t happen in this book.. apply what you lean here 10
10 -
ComputerToucher: *opens Jira ticket* Dev team needs tokens for the APM for a new app with multiple tenants. Ezpz. Hey, developer. Do you want one golden token for all of your app tenants or would you like us to generate one token for each?
Developer: Let’s have a meeting to discuss it.
CT: It’s…an exceedingly simple question. One token or 4? Which does your app support?
Dev: Yeah I think we should discuss with this with the platform team, can you set up the call?
CT: (Internally) I am the platform team? Do you not know how your applica-never mind I’ll just ask the PM directly.
CT (in chat): I’ll ask PM to schedule the call.
*Goes back to Jira ticket, changes priority to 4, removes ticket from sprint entirely, picks something else to work on*6 -
So one of my clients had a different company do a penetrationtest on one of my older projects.
So before hand I checked the old project and upgraded a few things on the server. And I thought to myself lets leave something open and see if they will find it.
So I left jquery 1.11.3 in it with a known xss vulnerability in it. Even chrome gives a warning about this issue if you open the audit tab.
Well first round they found that the site was not using a csrf token. And yeah when I build it 8 years ago to my knowledge that was not really a thing yet.
And who is going to make a fake version of this questionair with 200 questions about their farm and then send it to our server again. That's not going to help any hacker because everything that is entered gets checked on the farm again by an inspector. But well csrf is indeed considered the norm so I took an hour out of my day to build one. Because all the ones I found where to complicated for my taste. And added a little extra love by banning any ip that fails the csrf check.
Submitted the new version and asked if I could get a report on what they checked on. Now today few weeks later after hearing nothing yet. I send my client an email asking for the status.
I get a reaction. Everything is perfect now, good job!
In Dutch they said "goed gedaan" but that's like what I say to my puppy when he pisses outside and not in the house. But that might just be me. Not knowing what to do with remarks like that. I'm doing what I'm getting paid for. Saying, good job, your so great, keep up the good work. Are not things I need to hear. It's my job to do it right. I think it feels a bit like somebody clapping for you because you can walk. I'm getting off topic xD
But the xss vulnerability is still there unnoticed, and I still have no report on what they checked. So I have like zero trust in this penetration test.
And after the first round I already mentioned to the security guy in my clients company and my daily contact that they missed things. But they do not seem to care.
Another thing to check of their to do list and reducing their workload. Who cares if it's done well it's no longer their responsibility.
2018 disclaimer: if you can't walk not trying to offend you and I would applaud for you if you could suddenly walk again.2 -
I once agreed to maintain and develop an application used in a different section of the school to keep inventory and make sure everything is where it is supposed to be.
At first there was enthusiasm, together with 2 of my classmates we agreed and git clone-d the .NET application that now graduated students built and maintained for the past few years. What could go wrong right?!
It became clear that the original students that worked on it followed an older curriculum, meaning they still got taught .NET instead of the core variant that we get now, not only that but it also seemed that they either did not fully grasp the Clean/Onion architecture or didn't get it in class since there were infrastructure components in the 'Domain' project of the solution. Think of 2 DBContexts in the domain model, yep.
One of us bailed in the first week, the other one and I felt bad for the people using the app so we went on and tried to work on the first bugs that were described in a document. One of these bugs was 'whenever I filter on something in the list, everybody gets to see that filter on their screen instead of only me'. Woah that's weird! Let's see how they put that together!
Oh god, they are using a _static_ variable to store filters, no wonder that it doesn't work properly. Ever heard of sessions?!
Second bug: Sometimes people can't create an account when we sign them up from the admin panel. Alright that is weird, let's figure that one out! Wait a second it seems to work in development? What's this about.
Oh wait I can't create an account on production either? Oh that's weird, wait a second... Why do I have to put my e-mail in a form that was sent to me through e-mail? Why is my address not filled in already? OOH, if someone types in the wrong e-mail address (which is easy since our school has 4 variants of the same f*cking e-mail address) it won't work since it can't recognize the user! Brilliant! Remove e-mail input box and make a token/queryparam determine the user account.
Ah that seems good, it's a mess but it seems a tiny bit better now, great! We're making progress and some sweet buck.
Next bug, trillions of 50x errors on random pages, that's a weird one.
Hm everything works in development, that's odd. Is the production data corrupted?
DID I MENTION that in order to get into the system in development we have to load in a f*cking production database backup ON OUR DEVELOPMENT MACHINE and then ask one of the users' password to login to it and create an account for ourselves? Seeding? What's that, right?!
Anyway, back to bug fixing. I e-mail the the people responsible for the app and get a production admin account, oh I also can't ssh into it because of policies so I have to do everything over e-mail and figure out what's causing the errors. I somehow also wonder if they have any kind of virtualization in place, giving students a VM to do that stuff in doesn't seem so weird does it ? Even with school policies?
Oh btw, 'deploying' means sending a .zip file to a guy in another building and telling him how to configure it, apparently this resulted in a missing folder that the application needed to work and couldn't make on its own. This after 2 weeks of e-mailing back and forth.
After 3 months i quit out of despair and sadness, and due to the fact that I just couldn't do it anymore. I separated everything into logical subprojects and let the last guy handle it, he was OK with that and understood why I left.
Luckily, around that time I already had an actual job at a software development company :)3 -
So after 6 months of asking for production API token we've finally received it. It got physically delivered by a courier, passed as a text file on a CD. We didn't have a CD drive. Now we do. Because security. Only it turned out to be encrypted with our old public key so they had to redo the whole process. With our current public key. That they couldn't just download, because security, and demanded it to be passed in the fucking same way first. Luckily our hardware guy anticipated this and the CD drives he got can burn as well. So another two weeks passed and finally we got a visit from the courier again. But wait! The file was signed by two people and the signatures weren't trusted, both fingerprints I had to verify by phone, because security, and one of them was on vacation... until today when they finally called back and I could overwrite that fucking token and push to staging environment before the final push to prod.
Only for some reason I couldn't commit. Because the production token was exactly the same as the fucking test token so there was *nothing to commit!*
BECAUSE FUCKING SECURITY!5 -
Hello fellow devRanters, look what I found in our API constants on this fine day!
LIST_USERS: '/api/GetUsers',
USERS_WITH_QUERY:'/api/GetUsers?Query=',
MORE_USERS: '/api/GetUsers?Token=',
You get what you pay for, you get what you pay for, you get what you- AAAAAAAAAAAAAAAAAAAARRRGGGGG!!!!!!!!!7 -
Guy's Discord bot "crashes"
we asked him what error.
"no error" he replies
we ask for a screenshot.
bot immediately exists
We ask: have you added this and this (`client.login(token)`)?
He replies: "yes"
We ask for sauce-code, he provides
what do we see? he forgot to add `client.login(token)`10 -
If we had a devRant vote on the most annoying word of 2018, I'd vote for "token".
Token here, token there, token yourself in the rear!
Some project I'm currently working on has to fetch 4 different tokens for these syphillis-ridden external CUNTful APIs.
Your mother inhales dicks at the trainstation toilet for one token!2 -
PM asked me to make the code deeper, here's the new load script:
//Someone is born (init script and load deps, also run it)
$life = new begin_life();
//magic happens (generate random token)
$life->Living = openssl_random_pseudo_bytes(rand(), TRUE);
//We end it all
$life->die();3 -
Morning there:)
To everyone who’s enjoying / doesn’t but is going to enjoy ( ̀⌄ ́) the DevStory:
here we go, with the third episode.
Leave a comment below and tell me your “dev stories” :) 11
11 -
The worst thing I have seen a dev do?
- Have all the APIs work without an access token for our main product which handles ~10k requests a day.
- Calling our architecture secure in the crucial investor meeting and being 'confident' that our database can not be compromised. No wonder we did not get funded.3 -
Oh boy I got a few. I could tell you stories about very stupid xss vectors like tracking IDs that get properly sanitized when they come through the url but as soon as you go to the next page and the backend returns them they are trusted and put into the Dom unsanitized or an error page for a wrong token / transaction id combo that accidentally set the same auth cookie as the valid combination but I guess the title "dumbest" would go to another one, if only for the management response to it.
Without being to precise let's just say our website contained a service to send a formally correct email or fax to your provider to cancel your mobile contract, nice thing really. You put in all your personal information and then you could hit a button to send your cancelation and get redirected to a page that also allows you to download a pdf with the sent cancelation (including all your personal data). That page was secured by a cancelation id and a (totally save) 16 characters long security token.
Now, a few months ago I tested a small change on the cancelation service and noticed a rather interesting detail : The same email always results in the same (totally save) security token...
So I tried again and sure, the token seemed to be generated from the email, well so much about "totally save". Of course this was a minor problem since our cancelation ids were strong uuids that would be incredibly hard to brute force, right? Well of course they weren't, they counted up. So at that point you could take an email, send a cancelation, get the token and just count down from your id until you hit a 200 and download the pdf with all that juicy user data, nice.
Well, of course now I raised a critical ticket and the issue was fixed as soon as possible, right?
Of course not. Well I raised the ticket, I made it critical and personally went to the ceo to make sure its prioritized. The next day I get an email from jira that the issue now was minor because "its in the code since 2017 and wasn't exploited".
Well, long story short, I argued a lot and in the end it came to the point where I, as QA, wrote a fix to create a proper token because management just "didn't see the need" to secure such a "hard to find problem". Well, before that I sent them a zip file containing 84 pdfs I scrapped in a night and the message that they can be happy I signed an NDA.2 -
Me:
* Builds Project and Hosts it *
* thinking * : * ' I don't really need to push to Master, I'll just push it to the deployed branch *
Me: * tests project from host *
Me: * sees a bug, fixes it and rebuilds the project, hosts it and pushes code to deployed branch *
4Hrs Later:
Colleague: Dude did you see the Typos you made? Fix them!
Me: In my defence, I wrote this at 4am in the morning, did not sleep for 2 days.
Colleague: Don't Care, fix it.
Me: *Creates Hotfix Branch from Master*
* INSTALLS DEPENDANCIES AND FINDS OUT A NEW VERSION IS OUT AND UPDATES THAT AS WELL *
* Runs Project and finds out it's not the hosted version. *
* Merges Deployed Brunch to Hotfix Brunch and this happens *
Error Message: Unexpected token
620 Merge Conflicts
🤦🏽♂️🤦🏽♂️🤦🏽♂️ 2
2 -
Follow up to: https://devrant.com/rants/5047721/....
1- The attacker just copy pasted its JWT session token and jammed requests on the buy gift cards route
2- The endpoint returns the gift card to continue the payment process, but the gift card is already valid
3- Clients wants only to force passwords to have strong combinations
4- Talk about a FIREWALL? Only next month
5- Reduce the token expiration from 3 HOURS to 10 minutes? Implement strong passwords first
6- And then start using refresh tokens
BONUS: Clearly someone from inside that worked for them, the API and database password are the same for years. And the route isn't used directly by the application, although it exists and has rules that the attacker kows. And multiple accounts from legit users are being used, so the person clearly has access to some internal shit6 -
!(!(!(!(!(!(!(!rant)))))))
My new HTC smartphone hates me.
First it started to shut down all of the sudden yesterday night, when I was solving quadratic equations on my laptop.
I thought that it might be due to low battery. So I have restarted it. After putting itself into a bootloop for 4 start sequences, it was able to fully start to the page where it told me to enter the security pin to decrypt my files. I also had 30 attempts left. Like a ransomware.
I was like "tf I didn't set anything up".
So I decided to use my first attempt as I had 30 attempts left.
I entered the pin (I can swear that it's correct) and it told me that it has to wipe the /data partition.
I did that. I pressed that button. After waiting for 30 minutes I gave up and rebooted into the bootloader.
Bootloader -> Download Mode -> wipe /data (stock rom + stock recovery btw.)
Some error with "e: mount /cache failed[...]e: mount /data failed"
So, I tried using the adb sideload - no success.
Fastbooted into RUU Mode - HTC keeps rebooting itself into the RUU Mode - no success
Tried to flash the firmware and twrp recovery from Download mode - no success
Then I tried to flash all these things from the sd card - no success
Searched for revolutionary (I know this from my old HTC sensation device).
It wasn't big of any help.
Then someone on xda recommended htcDev (htc's <b>developer-friendly</b> lol site)
I followed every step. Everything seemed to be okay.
I got to the last step.
I needed to get my encrypted token by entering "fastboot oem get_identifier_token" to be able to submit it to HTC, and after they would send me an e-Mail with an .bin file that would let me unlock the bootloader to be able to flash my way through all this headache giving fucking piece of dog shit!
But since I can't back to the phone settings to select the bootloader activation box that would let me get my token... but nah.
FML
------------
Sent by using the devRant web app (:\)8 -
Not a rant, but i'm proud of myself :3
to make a long story short, i wanted a wrapper for a api (https://esi.evetech.net), but there were none that were updated or actively maintained, so i built my own. the first version had all the non-authed endpoints, and 2 days ago i finally got all the authed endpoints, plus added in features like a config file (for storing the token and project name) :D
I'm one happy fox rn!8 -
👨🏽💻 Switching between multiple Git accounts: work, personal, freelance?
Ever pushed a commit with Company A's email to Company B's repo? 😩🥶
Been there. Done that. Regretted it immediately.
I just dropped a step-by-step guide on how to set up Git so it automatically picks the right name, email, and SSH key based on your project folder.
No more manual config switching. 💡
✅ No more identity mix-ups
✅ No more commit shame
✅ Just clean, context-aware Git workflows 🙌
🔧 What’s inside:
- Multiple SSH key setup
- Smart .gitconfig using includeIf
- Folder structure that keeps you sane
- Bonus tips for HTTPS + personal token users
If you’ve ever yelled at Git (or yourself), this one’s for you.
👏 Drop a clap if it helps and follow for more dev-friendly tips!
👇 Read it here:
https://rhymezxcode.medium.com/how-... -
How many times will you say hi to me when we're passing on the stairs for nth time? How many 👋 will you send me in one day at almost regular intervals? I'm not a fucking rest api. You don't have to generate a fucking oauth token every time you pass me some information. I have a fucking state and it's getting distracted by too much human interaction3
-
Ok so we just signed a new client with some "artificial intelligence" back-end...
To authenticate with their back end, they developed a FU**ING GET REQUEST so the username and password are passed in the URL.
Then we get a token that we pass in FU**ING GET REQUESTS to communicate with their "artificial intelligence enhanced" back end.
I can't even. I just can't.5 -
PM asked me to develop an application to fetch data from the customer's DB, which would require an access security token provided by the customer. To get the token, I would have to travel to Germany (I live in Portugal) to get it personally (it's not possible to have someone else pick it up for me).
It turns out the security token is a completely closed environment, with its own OS, without the possibility of installing any application or communicating with the exterior. The laptop itself would boot from the token's OS.
It was concluded I would have to hack the security token, which is completely non compliant. So the PM decided not to go forward with it.
But now, I have to go Germany anyway to pick up the security tokens because they forgot to order them for these other guys who would be using them to access the customer's DB manually and they don't want to delay the project anymore.
Oh, and the security tokens cost the project 500€/month each...3 -
Day 1 of learning to build interpreters: finished the scripts for basic mathematic operations and beginnings of functions... Spent 4 fucking hours trying to track down why the compiler is treating an end of file token as an addition token... No luck, going to bed with a headache and half a head of torn out hair...7
-
I've been using the Square REST API and I spent one hour thinking there was something wrong in my code until I f** found that THEY were not following OAuth 2 guidelines, which made their workflow incompatible with the OAuth lib I was using, so I had to mark an exception for Square's OAuth from the rest of my OAuths. Specifically, RFC 6749 Section 4.2.2 and 5.1.
However, after reading OAuth 2 guidelines, I became angry at THEM instead. The parameter `expires_in` should be the "lifetime in seconds" after the response. This will always be innevitably inaccurate, since we are not taking into account the latency of the response. This is, however, not a huge problem, since the shortest token lifetimes are of an hour (like f** Microsoft Active Directory, who my cron jobs have to check every ten minutes for new access tokens). Many workflows (like Microsoft, Square, and Python's oauthlib) have opted to add the `expires_at` parameter to be more precise, which marks the time in UTC. However, there's no convention about this. oauthlib and Microsoft send the time in Unix seconds, but Square does this in ISO 8601. At this point, ISO 8601 is less ambigious. Sending a raw integer seems ambiguous. For example, JavaScript interprets integer time as Unix _milliseconds_, but Python's time library interprets it as _seconds_. It's just a matter of convention, a convention that is not there yet.
Hope this all gets solved in OAuth 2.1 pleeeaasseee 1
1 -
@dfox if you guys aren't ready to take donations for the site, do you have a favourite charity (international preferably) we could donate to as a token of appreciation?1
-
The "stochastic parrot" explanation really grinds my gears because it seems to me just to be a lazy rephrasing of the chinese room argument.
The man in the machine doesn't need to understand chinese. His understanding or lack thereof is completely immaterial to whether the program he is *executing* understands chinese.
It's a way of intellectually laundering, or hiding, the ambiguity underlying a person's inability to distinguish the process of understanding from the mechanism that does the understanding.
The recent arguments that some elements of relativity actually explain our inability to prove or dissect consciousness in a phenomenological context, especially with regards to outside observers (hence the reference to relativity), but I'm glossing over it horribly and probably wildly misunderstanding some aspects. I digress.
It is to say, we are not our brains. We are the *processes* running on the *wetware of our brains*.
This view is consistent with the understanding that there are two types of relations in language, words as they relate to real world objects, and words as they relate to each other. ChatGPT et al, have a model of the world only inasmuch as words-as-they-relate-to-eachother carry some information about the world as a model.
It is to say while we may find some correlates of the mind in the hardware of the brain, more substrate than direct mechanism, it is possible language itself, executed on this medium, acts a scaffold for a broader rich internal representation.
Anyone arguing that these LLMs can't have a mind because they are one-off input-output functions, doesn't stop to think through the implications of their argument: do people with dementia have agency, and sentience?
This is almost certain, even if they forgot what they were doing or thinking about five seconds ago. So agency and sentience, while enhanced by memory, are not reliant on memory as a requirement.
It turns out there is much more information about the world, contained in our written text, than just the surface level relationships. There is a rich dynamic level of entropy buried deep in it, and the training of these models is what is apparently allowing them to tap into this representation in order to do what many of us accurately see as forming internal simulations, even if the ultimate output of that is one character or token at a time, laundering the ultimate series of calculations necessary for said internal simulations across the statistical generation of just one output token or character at a time.
And much as we won't find consciousness by examining a single picture of a brain in action, even if we track it down to single neurons firing, neither will we find consciousness anywhere we look, not even in the single weighted values of a LLMs individual network nodes.
I suspect this will remain true, long past the day a language model or other model merges that can do talk and do everything a human do intelligence-wise.28 -
"Shit, we haven't even come up with a safe word yet!"
"Don't worry, your RSA token has been sent to your e-mail." 1
1 -
when youre working on a API and every testCase is all green plus manual testing thru Postman extension is all good..
then makes a web app use that API, authorization works as intended but the token is immedially invalid...
just..how..2 -
Why do most apps have a password reset page that redirects to a mobile site ?
Why not give them a code they can enter into the app which would then show a password reset page within the app or a link which opens the page within the app.
Isn't it good practice to keep the user within the app?
Isn't it better to serve a token than serve an entire html webpage for the server.
I've been thinking about this but 90% people follow the website pattern and Idk why. Am I missing something ?
Please fill me in on it. (Even devrant uses the same pattern)5 -
A few years ago, i had a task to implement a webservice of an insurance-company into our .NET Development.
The security requirements of this insurance-company webservice were top notch.
As a client you had to build a request that used a negotiated certificate, canonical header structures, security timestamp, a secret token in header, ...
To configure all this stuff via web.config WCF was pure pain in the ass.
After many phonecalls and emails, i finally managed to meet all security requirements to send a valid request.
First, i didn't recognized my breakthrough, because my client still had thrown exceptions while calling the insurance-webservice.
Why was that?
The exception told me on the most possible gentle way, that .Net isn't able to process an unsecured response, when there was a secured request before.
So there was top notch security for requesting, but dumbass unsecured responding with all the precious customer information.
*epicfacepalmnuclearexplosionfollowing*
I even had to raise the. Net Version of our. Net client, because i wasn't able to configure that it is allowed to process an unsecured response after using a secured request.
Whyyyyyyy?!!?!!1el even!?! -
all documentation points to an Invalid auth token being code 400 (ignore the fact that this is a code in the JSON response and not HTTP)
Me: here iz credential. Plz send datas
API: haha fock off and die mate, then credentials you got there aren’t workin’
API: code 998 invalid auth token
Me: *speechless* so that’s why it took me longer than it did to find that error, because YOUR CODE WAS MISSING ALL MY CHECKS FOR CODE 400.
Why can’t people design apis properly.2 -
SyntaxError: Unexpected token T in JSON at position 0
WHY IS THIS ERROR SO UNAVOIDABLE? Like every time I need to interact with an API, it's a struggle to make this go away.2 -
Trying to switch my job. Applied for a well known company. Gave an interview today. I don't fucking get the obsession of these developer recruiters so fixated on data structures and algorithms. I know it's a massive part of computer science but guess there is no fucking room left to innovate in there. There are legitimate researcher teams working for implementation of these barebones inside system foundations. No general software developer gives a fuck about this piece of shit discipline of study. You wanna know why they propagate this as the panacea to test people because it's fucking easy. Give a project to somebody as interview procedure, it'll take time to bring out an interesting problem and an interesting solution to that. Sorry to say but all these data structure enthusiasts are nothing better than board game enthusiasts.
Also why can't you refer existing solutions to create your solution. I've seen some good problems which actually require you to think. But again those are heavy and can't be tested so you're left with reversing a fucking linked list with O(1) auxillary space. Fuck me ig.
Moreover, what the fuck is wrong with the moral policing internet crowd. Its so sad. I've hardly seen anybody rant about this piece of shit system put in place to push the absolute dead-end nutcases up the ladder. Every other search for it returns a Quora link with some Indian guy complaining about his interviews and in the comments you have the same scholars sitting in their data structure throne imparting knowledge about how data structure holds the fabric of reality together.
I don't hate data structures and algorithms as a subject. It is cool and quite extensive but once you try to make that as a metric of all the knowledge in the world, you've lost my drift. Maybe I'm just angry with the state of things. Maybe I'm just angry with token Quora crowd.3 -
Sometimes human stupidity still surprises me.
Today I was able to stop the release of a ticket at the last moment that intended to put urls WITH A SECURITY TOKEN TO ACCESS USER DATA through a link shortener.
Some PM assumed that it would be a reasonable course of action to map an url secured via jwt through to a 4 character, countable, base64 string so that we don't have to send multiple sms if they contain this url. I can accept that the implications might slip through one person but the fact that this was put into a ticket by a pm, prioritized by PO, estimated by an entire team, implemented by a professional developer, reviewed by a senior and then scheduled for release without anyone asking themselves if there might be a reason for a security token to be long, that one shocks me.8 -
This way of converting "string" to "s" (for example)
0) program reads the whole buffer, stores it as an array of instructions
1) program reverses the order of the instructions
2) parser makes standard token from an instruction ("asd" -> ASD)
3) parser2 assigns operands to instruction
4) parser 3 makes string from instruction token ?????
5) parser fucking 4 makeS A MUTABLE STRING INSTRUCTION
6) PARSER FIVE SUBSTITUES OPERANDS
7) AND THEN CUTS IT TO A REVERSED ARRAY OF COMMANDS
8) AND PUSHES IT UNTO THE STACK
WHAT1 -
A simple bot on Telegram
Just hit and trial
Wanted same for Facebook, some error while accessing token tho. :( 1
1 -
It's a really interesting discussion, when your boss tells you that it's a perfectly fine idea to directly use a Firebase DB from an Angular web app by storing the Admin Auth Token in a variable in JS.
Thank the spaghetti monster, I was able to argue against it and use the already partially implemented RESTful API with the already used auth.
He basically wanted to save time and omit extra login routes.
It's OK to save time and not implement $randomFeatures.
BUT DON'T FUCKING TRY TO SAVE TIME ON SECURITY!
If it wasn't for me, this web app would turn into a bigger gaping (security) asshole than Sasha Grey's...6 -
I was thinking about how I implement login functionality, and realised I have no clue how I came up with it so decided to ask if it was a good way to do things.
Basically, client logs in, username/email and pass are sent to server.
Server salts and hashes password and checks it against the one in the database for that user.
If its correct, send the client the user ID and the user token. (User id could be username, or a number, it depends)
When that client makes a request, the request must contain the ID and token.
The server checks that the ID and token combo are correct, and because the ID is linked to the user we know who it is and can complete the request.
Usually I make the token a random string of 16 or 32 chars, each account has their own token, and it may be stored in the browser so they stay logged in. I also normally add a "log out everywhere" button, which essentially just generates a new token to overrides the current one, making any previously saved tokens invalid.8 -
T_PAAMAYIM_NEKUDOTAYIM
This is how PHP refers to :: internally, it's the only fucking token with such a weird name, what is this fucking language?
Who is writing this shit? OOP but it's completely optional? Where is the goddamn sheriff? I'm done, off to Ruby, Python, Go or anything that's not fucking PHP. Sick of this shit. Fuck this language.
How can such a massive language be so poorly designed!?3 -
fuck..fuck..FUCK..FUCK YOU MANTIS!!!
fuck you and your fucking invalid security token... fucking cunt...
yeah i love extracting my notes from POST data via the browser dev console cause you fucking delete it when hitting the back button...
THANKS FOR NOTHING -
After a lot of work I figured out how to build the graph component of my LLM. Figured out the basic architecture, how to connect it in, and how to train it. The design and how-to is 100%.
Ironically generating the embeddings is slower than I expect the training itself to take.
A few extensions of the design will also allow bootstrapped and transfer learning, and as a reach, unsupervised learning but I still need to work out the fine details on that.
Right now because of the design of the embeddings (different from standard transformers in a key aspect), they're slow. Like 10 tokens per minute on an i5 (python, no multithreading, no optimization at all, no training on gpu). I've came up with a modification that takes the token embeddings and turns them into hash keys, which should be significantly faster for a variety of reasons. Essentially I generate a tree of all weights, where the parent nodes are the mean of their immediate child nodes, split the tree on lesser-than-greater-than values, and then convert the node values to keys in a hashmap to make lookup very fast.
Weight comparison can be done either directly through tree traversal, or using normalized hamming distance between parent/child weight keys and the lookup weight.
That last bit is designed already and just needs implemented but it is completely doable.
The design itself is 100% attention free incidentally.
I'm outlining the step by step, only the essentials to train a word boundary detector, noun detector, verb detector, as I already considered prior. But now I'm actually able to implement it.
The hard part was figuring out the *graph* part of the model, not the NN part (if you could even call it an NN, which it doesn't fit the definition of, but I don't know what else to call it). Determining what the design would look like, the necessary graph token types, what function they should have, *how* they use the context, how thats calculated, how loss is to be calculated, and how to train it.
I'm happy to report all that is now settled.
I'm hoping to get more work done on it on my day off, but thats seven days away, 9-10 hour shifts, working fucking BurgerKing and all I want to do is program.
And all because no one takes me seriously due to not having a degree.
Fucking aye. What is life.
If I had a laptop and insurance and taxes weren't a thing, I'd go live in my car and code in a fucking mcdonalds or a park all day and not have to give a shit about any of these other externalities like earning minimum wage to pay 25% of it in rent a month and 20% in taxes and other government bullshit.3 -
A conversation that i had with my co-worker today. I was having trouble getting into UAT to troubleshoot.
me
i lost access to UAT again
co-worker
F. So secure we can't even get in
me:
lol
co-worker:
I'll email whoever we did last
me:
i can get through the first phase(where you enter pin+rsa)
it denies me access after that
says bad username or password
co-worker:
Oh ok. Prolly just need to reset your pwd then. I'll find the email for helpdesk and fwd.
At least ur RSA works.
me:
yeah what a joy
co-worker:
If it's locked you may need to try from a Windows box. Horizon is bugged on Mac where the submit button stays disabled even when you type a pwd.
me:
i couldnt contain my happiness that my RSA worked
😃
co-worker:
Yeah it's exhilarating
Whenever I pick up my rsa token my life re-finds it's purpose and I feel like I'm meddling through a field of sunflowers.
I once tried to get my RSA token tattooed but it switched too quick.
me:
lol its faster that Usain Bolt
co worker:
Russia got kicked out because of their RSA tokens -
Why, in the name of all that is holy would you use a secure token generator, and then override it with a short, easily guessable token?! Why take the time? I hate my outsourced devs
-
Wanna know about hacks? I'll tell you. There is a peace of software called SugarCRM. It has OAuth2 provider implementation. I was assigned to write OAuth2 consumer for it.
It turned out they just failed to make it right.
The list of hacks:
* Hack on standard Authentication header. They use custom.
* Hack on "scope". They send null which is standard violation. So it is replaced to empty string before response processing starts.
* This is my favorite. Refresh token simply doesn't work. So we need to store user's credentials in memory to be able to reauthenticate user transparently.2 -
I inherited a nextjs project from an unknown guy and am fangirling the codebase
But the deeper I familiarise myself with it, the more the cracks begin to appear:
1) The dude Is incapable of grasping the basics of DRY concept. He actually setup a ton of stuff I may have done poorly if I'd started working straight out of the docs, so I feel like I owe him a shower of praise. I guess being new to nextjs makes it look more impressive than it actually is. He was paid off, yet getting the credit seems unearned to me. I'm just afraid reaching out to him might turn around to bite me in the ass
***
I had the above in my drafts, contemplating sending him a token to show some appreciation for unknowingly showing me the ropes. I was going to find him on LinkedIn using his commit names. But after doing everything I've done, undergoing the anxiety and severe pressure I faced at the hands of the project owners, I'm not sharing a farthing with anybody
Yes, I may not have known about zustand and persist middleware. Yes, he did all the ui. Yes, he created the base components and fancy wrappers around form and button html elements. For those, I'm grateful
But the amount of refactoring I had to do to, for an opportunity to implement my own target features, I'd say I can lay as much claim to the project as he does.
Side note #1: I have some newfound respect for front end devs. We used to discriminate against them for doing just css but that was only relevant in the jquery days. Now, they have to use cryptic css frameworks (sass, less, tailwind), they have to learn esoteric syntax of some js framework and write controllers/components as the case may be. They have to (the worst part), bind this data to an API, which would never make sense to me coming from a php ssr-natural world
Back rewarding the guy, some of the challenges I came back from were:
1) Next server outages: I still don't know the workaround this. The app terminates, browser giving an error about using up memory. I have to wait for about 10 minutes before I can access the app again
2) spring Webflux authentication not hydrating: I was unexpectedly asked to work on the back end too, where I got tortured with this horrifying condition. The most poorly documented framework for the Web has no upto date guide on how to implement jwt security measures. I opened a question on stackoverflow. A day later, both my question and the helpful answer got downvoted
3) Zustand not retrieving any data from localstorage once page reloads, until I miraculously stumbled on a hack: there's a config callback for reading state after rehydration or thereabout. So I interact with the state there. That's the only way content clearly in localstorage can get transmuted into dynamic format accessible by the code
4) Mongo database suddenly disconnecting: for no apparent reason, this bailed. Accessible on compass. This was even when I realised it was responsible for front end requests not going through. Eventually created a new database and requests surprisingly began connecting again. Thankfully, my laravel background taught me about seeders so I had them on standby from the onset. Wasn't difficult to just port to a fresh database after confirming the first one was inaccessible to the app
After this painful odyssey and the time constraints, threats of moving forward with someone else, I deserve every dime they deem me worthy of and more3 -
A new developer started working with us a few months back. Plenty years of experience, both front- and backend.
He was the perfect guy for the job, according to management. Two weeks ago he asked me what JWS Cookie I used to send my requests.
After a few minutes we realized that he meant JWT token.
Said developer is no longer working with us, he didn’t like all the new technology.1 -
If any of you have been following my last few rants, you'll know I've been working on a project with a particularly difficult client, trying to meet wholly unrealistic deadlines with only one other developer.
The situation has reached the climax. The client had a call with our project manager and boss on Monday to discuss things. Despite them still not having paid a single bill since October, they've demanded the release date be moved to the 6th April. Apparently we'd agreed to release on this date, despite making no such promises, the (optimistic) deadline we were working towards has always been, since it was set about 2 weeks ago, the 16th April.
Apparently AWS migration won't take as long as we think it will, because the designers that do the CSS for this project say so, despite knowing nothing about the architecture of the requirements of the system once live (like if backups are required and what of).
The bottom line is that client is ending development with us the day after the project goes live to give it to their own in-house team. If they want us to work more after the date, they have to buy blocks of days.
To make things better, a large part of new functionality relies on an external API we can't even begin to do learning tests with, let alone integrate due to back-office errors on their end. They've had since Friday to give us our token, yet here we are.
Something tells me my holidays booked for for the first week of April are going by the wayside.4 -
"Our Data Service comes PRE-P0WN'D"
Those SHIT-FOR-BRAINS data service providers GLOAT that their data can be natively integrated into most BI platforms, no code required.
How? Because they will EXPOSE THE ENTIRE FUCKING THING ON THE INTERNET.
LITERALLY.
UNAUTHENTICATED URL WITH THE ENTIRE DATASET.
STATIC. WON'T EVER FUCKING CHANGE.
NO VPN REQUIRED. NO AUTHENTICATION HEADERS. NO IN-TRANSIT ENCRYPTION.
"It is safe! No one will know the secret token that is a parameter in the url"
BLOODY BYTE BUTTS, BATMAN! IT IS A FUCKING UNAUTHENTICATED URL THAT DOES NOT REQUIRES RENEWAL NOR A VPN, IT WILL LEAK EVENTUALLY!
That is the single fucking worst SELF-P0WN I have ever seen.
Now I know why there are fucking toddlers "hacking" large scale databases all over the globe.
Because there are plenty of data service providers that are FUCKING N00BS.4 -
I'm a C++/Obj-C programmer finding it ludicrously hard to switch to Swift.
I find that the constant ability (leading to very poor programmer code) to reduce syntax and add tokens reduces readability and nowhere is this more apparent that with closures.
I'm working through (to my shame) Ray Wenderlich's Swift course and the closure chapter has this:
PS I loathe K&R as much as I do Swift so it's all in Allman formatting for clarity.
let multiply: (Int, Int) -> Int =
{
(a: Int, b: Int) -> Int in
// do Something else
return a * b
}
Why oh why isn't this more simply and elegantly written as:
let multiply = (a: Int, b: Int) -> Int
{
// do Something else
return a * b
}
The equals sign shows clearly that it's a closure definition assignment, as does the starting 'let'. But this way all of the stupid excesses, like the 'in' keyword, the repetition of the params / return type only this time with useful labels and additional tokens are removed and it looks and reads much more like a regular function and certainly a lot more clearly.
Now I know that with the stupid ability of Swift you can reduce all this down to return $0 * $1, but the point I'm making is that a) that's not as clear and more importantly b) if this closure does something more than just one line of code, then all that complicated stuff - hinted to by the comment '// do Something else' means you can't reduce it to stupid tokens.
So, when you have a clousure that has a lot of stuff going on and you can't reduce it to stupid minimalism, then why isn't is formatted and syntactically better like the suggestion above?
I've mentioned this on the Swift.org (and got banned for criticising Swift) but the suggestions they came up with were 'use type inference' to remove the first set of params / return type and token.
But that still means the param list and return type are NOT on the same line as the declaration and you still need the stupid 'in' keyword!5 -
@dfox I saw a few posts lately, about websites that people did. So besides the collabs, I'd like to suggest a new section. "DevReviews" or what ever. The basical idea is, every one, that is signed up gets one "token" devRant ++ suporters maybee an additional free token every months or whatever.
If you wan't your website reviewed, you can post it there and people reviewing it will get such a token for their review.
To ensure a certain quality of the reviews, I'd put a minimum caracter length and a "dispute" function, where the review is taken to a community voting, if the person giving the review should get the token, or if the review should be dismissed. Additional "tokens" for additional/more reviews can be bought through the app, that could help a lot of devs get quality reviews and testing and earn you some $ for the servers.5 -
Ok, my RSA token for the next minute is: 740130.
Are you a L337 enough H@xx0R to pwnz my system in the time available?4 -
Why do people design web apis where the way you submit your authorization is via a custom header?
Especially when the authorization is literally a token?
Am I ingesting something special?8 -
Security : Each time I login, they ask me to type the email address I want my one-time-code emailed to. Really!? What security is provided by letting the user decide where to email the flippin token to?!?!2
-
Just posted a rant that BitBucket gave me a big Internal Server Error
Then I realized one of my extensions was overriding the authentication token (as I configured it to do that for a dashboard) and that was why BitBucket was inaccessible
Why do I keep doing this to myself -
Not sure if it is a rant or not but I'm getting worried about Apple... Two days passed uploaded a new update multiple times and all ended on the first try 😨
Usually it takes many tries for it to be uploaded 😨
On top of that, iTunesConnect is faster and no longer stuck at loading when token expires 😨
I hope I'm not dreaming 😅4 -
Ouuu today I experienced how web-devs must feel...
Task: create a form to answer questions with yes/no and a database behind it to collect stats.
So login to phpmyadmin
1. Wrong password got error message
2. No error message, still at login screen, but in address I see a token
3. There must be something wrong
4. Reinstalled phpmyadmin and mysql-server several times, wasted one hour on it - still stuck at login screen
5. Tried different browser and it fucking works!
6. Realized that cleaning cache fixed it...1 -
My dumbass colleague thinks the best idea to a Restful API backend is to store some kind of session based on the token.
It'd be great if that remained as an idea instead of this 11 month-old system he built before I got in.
MOTHERFUCKER.
Yes, it does mean that if the server boots for whatever reason, everyone has to login again to get a valid token LOL6 -
How is the shopify developer experience actually so bad.
Shopify Buy JS docs suck
Product ID's are inconsistent
Token management is not built into GUI1 -
Trying to use authenticate a JWT token from an Azure service, which apparently needs to use Azure AD Identity services (Microsoft Entra ID, Azure AD B2C, pick your poison). I sent a request to our Azure admin. Two days later, I follow up, "Sorry, I forgot...here you go..."
Sends me a (small) screenshot of the some of the properties+GUIDs I need, hoping I don't mess up, still missing a few values.
Me: "I need the instance url, domain, and client secret."
<hour later>
T: "Sorry, I don't understand what those are."
Me: "The login URL. I assume it's the default, but I can't see what you see. Any shot you can give me at least read permissions so I can see the various properties without having to bother you?"
T: "I don't see any URLs, I'll send you the config json, the values you need should be in there."
<10 minutes later, I get a json file, nothing I needed>
<find screenshots of what I'm looking for, send em to T>
Me: "The Endpoints, what URLs do you see when you click Endpoints?"
<20 minutes later, sends me the list of endpoints, exactly what I'm looking for, but still not authenticating the JWT>
Me: "Still not working. Not getting an error, just that the authentication is failing. Don't know if it's the JWT, am I missing a slash, or what. Any way I can get at least read permissions so I don't have to keep bugging you to see certain values?"
T: "What do you need, exactly?"
Me: "I don't know. I don't know if I'm using the right secret key, I can't verify if I'm using the right client id. I feel like I'm guessing trying to make this work."
T: "What exactly are you trying to get working?"
<explain, again, what I'm trying to do>
T: "That's probably not going to work. We don't allow AD authentication from the outside world."
Me: "Yes we do. Microsoft Teams, Outlook, the remote access services. I can log into those services from home using my AD credentials."
T: "Oh yea, I guess we do. I meant what you are trying to do. Azure doesn't allow outside services to authenticate using a JWT. Sorry."
FRACK FRACK FRACK!!
Whew! Putting the flamethrower away.
Thanks devrant for letting me rant.3 -
I have been trying to wrap my head around authentication in hapi for the last 6 hours...
Fuck this shit... when did simple,
I HAS A USERNAME
I HAS A PASSWORD
CAN HAS SESSION?
become:
- you magically get a token from somewhere
- you magically verify that token
- you respond with { credentials } //magic
- by some fucking black magic the server probably creates a session without you knowing about it...
- you freak out and write your own authentication scheme only to find out that you cannot read payload of POST requests in the authenticate method
- you get angrier and depressed and write a rant
(to be clear: there is @hapi/basic but I don't think sending a GET request with the URL looking like username:password@domain.tld is very safe...)11 -
I had joined a new company and got access to their codebase. They were updating password on MD5 hash of user name and their email in get request. No password validation, no token based authentication, nothing.
Eg
...com/change_password/email=(plainemail)&name= MD5(name)
That's it, you get change user password. -
Trying out the new version of fasm, I realize it's good, and conclude I should update my code to work with it as there's small incompatibilities with the syntax.
So, quick flat assembler lesson: the macro system is freaking nuts, but there are limitations on the old version.
One issue, for instance, is recursive macros aren't easily possible. By "easily" I mean without resorting to black magic, of course. Utilizing the arcane power of crack, I can automatically define the same macro multiple times, up to a maximum recursion depth. But it's a flimsy patch, on top of stupid, and also has limitations. New version fixes this.
Another problem is capturing lines of code. It's not impossible, again, but a pain in the ass that requires too much drug-addled wizardry to deal with. Also fixed in new version.
Why would you want to capture lines of code? Well, because I can do this, for instance:
macro parse line {
··match a =+ b , line \{
····add a,b;
··\}
};
You can process lines of code like this. The above is a trivial example that makes no fucking sense, but essentially the assembler allows you define your own syntax, and with sufficient patience, you can use this feature to develop absolutely super fucking humongous galactic unrolls, so it's a fantastic code emitter.
Anyway, the third major issue is `{}` curlies have to be escaped according to the nesting level as seen in the example; this is due to a parser limitation. [#] hashes and [`] backticks, which are used to concatenate and stringify tokens respectively, have to be escaped as well depending on the nesting level at which the token originates. This was also fixed.
There's other minor problems but that gives you sufficient context. What happens is the new version of fasm fixes all of these problems that were either annoying me, forcing me to write much more mystical code than I'd normally agree to, and in some rare cases even limiting me in what I could do...
But "limiting" needs to be contextualized as well: I understand fasm macros well enough to write a virtual machine with them. Wish I was kidding. I called it the Arcane 9 Machine, A9M for short. Here, bitch was the prototype for the VM my fucking compiler uses: https://github.com/Liebranca/forge/...
So how am I """limited""", then? You wouldn't understand. As much as I hate to say it, that which should immediately be called into question, you're gonna have to trust me. There are many further extravagant affronts to humanity that I yearn to commit with absolute impunity, and I will NOT be DENIED.
Point is code can be rewritten in much simpler, shorter, cleaner form.
Logic can be much more intricate and sophisticated.
Recursion is no longer a problem.
Namespaces are now a thing.
Capturing -- and processing -- lines of code is easier than ever...
Nearly every problem I had with fasm is gone with this update: thusly, my power grows rather... exponentially.
And I SWEAR that I will NOT use it for good. I shall be the most corrupt, bloodthirsty, deranged tyrant ever known to this accursed digital landscape of broken souls and forgotten dreams.
*I* will reforge the world with black smoldering flame.
*I* will bury my enemies in ill-and-damned obsidian caskets.
And *I* will feed their armies to a gigantic, ravenous mass grave...
Yes... YES! This is the moment!
PREPARE THE RITUAL ROOM (https://youtube.com/watch/...)
Couriers! Ride towards the homeland! Bring word of our success.
And you, page, fetch me my sombersteel graver...
I shall inscribe the spell into these very walls...
in the ELEVENTH degree!
** MANIACAL EVIL LAUGHTER ** -
Project with partner company, during the meeting I asked them how can we secure the communication between two services. I suggested api keys, tokens. They were like nope, no need. But I asked them for their IPs to do whitelisting on our side in Nginx.
But their side, nah not even whitelisting, no tokens, no validations. If one has address, can send anything from anywhere.
How hard would it be to do at least, AT LEAST simple token validation. And they are using the very old IIS server. I think for them as long as data flows in as expected, it is fine.3 -
The tech being rude about my RSA token not working locking me out trying to use a USB override stick...he got so mad he just walked out 😂
-
Adaptive Latent Hypersurfaces
The idea is rather than adjusting embedding latents, we learn a model that takes
the context tokens as input, and generates an efficient adapter or transform of the latents,
so when the latents are grabbed for that same input, they produce outputs with much lower perplexity and loss.
This can be trained autoregressively.
This is similar in some respects to hypernetworks, but applied to embeddings.
The thinking is we shouldn't change latents directly, because any given vector will general be orthogonal to any other, and changing the latents introduces variance for some subset of other inputs over some distribution that is partially or fully out-of-distribution to the current training and verification data sets, thus ultimately leading to a plateau in loss-drop.
Therefore, by autoregressively taking an input, and learning a model that produces a transform on the latents of a token dictionary, we can avoid this ossification of global minima, by finding hypersurfaces that adapt the embeddings, rather than changing them directly.
The result is a network that essentially acts a a compressor of all relevant use cases, without leading to overfitting on in-distribution data and underfitting on out-of-distribution data.12 -
Working for a startup building a device / app that let you answer your landline phone on your mobile, and get notifications of missed calls etc.
While developing I purposely didn't secure the endpoint that controlled push notifications.
I waited for the boss to sign up, went to the DB and stole his token. From time to time i'd send a request telling him he missed a call from his wife or son.
... then kicked back and watched the madness and frustration ensue. -
who's so stressed out right now? me.
why? i need to change the access token in my code because it was changed
why is that stressful? because there is no variable for it, it was hardcoded
who coded that? me.
when? when the whole dev team was drunk asf
fml1 -
GitHub Packages Sucks. Like, it REALLY sucks.
It sounds like the best thing in the world - being able to host your project packages alongside your code! It has full support for Maven, Gradle, Ruby Gems, Node packages, Docker images and even dotnet CLI applications. It even lets you view statistics on how many developers have downloaded a given package! For public repositories, the packages are free to host as well!
So, I decide to use it for my Maven project since it's "so great". I've never used a public Maven repository before, so this was all very new to me. I follow the documentation - simply run "mvn deploy ...." and use a generated GitHub personal access token. No problems there. Deployment is a success and I feel a wave of happiness seeing my packages online. I follow through the various links and it even adds automatically generated usage information for other Maven users - fantastic!
That was, until I decide to try and download one of the files from this package repository. In order to download a file, you must have a GitHub access token. Okay, makes sense I guess? What if another developer wants to use my library? To do so, they have to generate their own GitHub access token, store it in their local ~/.m2/settings.xml file and only THEN can they use my library. So clearly, this is significantly inferior to other public Maven repositories where you don't have to get an access token to simply USE a library.
Upon discovering this, I decide to simply delete all of the packages and continue using whatever previous system I was using. Except of course, they forbid the deletion of public packages because "other projects could depend on it". The only way to delete public packages is to either:
[0] Make the repository private (losing all stargazers and watchers), delete the packages and then make the repository public again
[1] Contact support and ask them to delete the public packages. They say that they'll only do this for "special cases", such as legal issues or GDPR breaches.
I've sent a contact form and I'm currently hoping that they see things in my favor. I mean seriously - a public package repository where in order to use it you have to have a GitHub account and then generate an authentication token - it's absurd!3 -
My workplace is still using xml based configuration, and non-spring boot projects.
So every spring boot tutorial I find feels like "Look at how easy you can get this running" and then it's just actually a toy you can't get into production.
Also it kind of bugs me that you need to be online to actually be able to initialize/create a spring boot project and every single tutorial says so.
You can make a local network m2 repository, but can one make a spring initializer service?
Either way, migrating every single project to Spring boot is a no-no,
And I'm stuck with like 5 prototypes of SSO integration from which only 2 work, and the other 3 have their own problems.
One does redirect to the login and all, but the SAML endpoint gets 404 on response when you log in.
One is on OpenID Connect, but I would need to update the project from Spring 3 to Spring 5 to get it working, which upon attempting to do seems to break everything else.
One has an external library handling the security context just the way we are accustomed to, but it only does a 401 forbidden when you go without logging in and I'm starting to think it is actually one of those that require you to extract the token or something manual like that, which wouldn't work for us
The other two are spring boot tutorials that worked out of the box, both SAML and OpenID, still can't use those for the main projects.
I'm tired of dealing with this configuration hell, been two months at this, I want to get features done as usual, not be stuck configuring stuff that might or might not work.
Rant aside, I think I figured I need to use a different Security adapter, but I needed to vent.2 -
Just found the most embarrassing security hole. Basically a skelleton key to millions of user data. Names, email addresses, zip codes, orders. If the email indicates a birthdate, even more shit if you chain another vector. Basically an order id / hash pair that should allow users to enter data AND SHOULD ONLY AUTHORIZE THEM TO THE SITE FOR ENTRING DATA. Well, what happend was that a non mathing hash/id pair will not provide an aith token bit it will create a session linked to that order.
Long story short, call url 1 enter the foreign ID, get an error, access order overview site, profit. Obviously a big fucking problem and I still had to run directly to our CEO to get it prioritized because product management thought a style update would be more important.
Oh, and of course the IDs are counted upwards. Making them random would be too unfair towards the poor black hats out there.1 -
VSCode is doing really strange things to my language server, in such variety that I'm starting to suspect that it's simply incorrect because it's very unlikely that I'd misunderstand so many distinct things at once.
- The trace level is verbose, yet VSCode absolutely spams the LS with trace: off requests
- the capability update request I used to set file watchers never gets a response even though the standard clearly states that all requests must get responses or progress reports quickly, and I'm not getting file updates even after vscode responds to a file system change. By the way, if file watching is a capability, why can't I set it in the protocol handshake with all the other capabilities?
- my semantic token provider (used for syntax highlighting) is simply ignored, no requests, no errors
- the debug console is spamming editor internal errors2 -
Currently working on my own Express App with CSurf for csrf validation.
Works great but one problem...
HOW THE FUCK SHOULD A POST REQUEST COMING FROM JAVA GET THE FUCKING TOKEN.
Should I made my RESTApi without csrf protection?
I am crying right now...17 -
Someone figured out how to make LLMs obey context free grammars, so that opens up the possibility of really fine-grained control of generation and the structure of outputs.
And I was thinking, what if we did the same for something that consumed and validated tokens?
The thinking is that the option to backtrack already exists, so if an input is invalid, the system can backtrack and regenerate - mostly this is implemented through something called 'temperature', or 'top-k', where the system generates multiple next tokens, and then typically selects from a subsample of them, usually the highest scoring one.
But it occurs to me that a process could be run in front of that, that asks conditions the input based on a grammar, and takes as input the output of the base process. The instruction prompt to it would be a simple binary filter:
"If the next token conforms to the provided grammar, output it to stream, otherwise trigger backtracking in the LLM that gave you the input."
This is very much a compliance thing, but could be used for finer-grained control over how a machine examines its own output, rather than the current system where you simply feed-in as input its own output like we do now for systems able to continuously produce new output (such as the planners some people have built)
link here:
https://news.ycombinator.com/item/...3 -
DAILY LARAVEL PROBLEMS
I need to parse a JWT with some custom claims. There's a JWT library with Laravel; documentation really lacking, kinda hardcoded to work with Laravel but whatever; it's already installed, let's see what can I do with it.
It turns out I can't say something like "take this token, parse it, tell me it's valid". Let's see how that goes.
You need to build a parsing class with a manager, some auth stuff, a parser.
To build said manager you need a provider that implements a contract, a blacklist, a factory (of what?)
To build the factory (of what?) you need a claim factory and a payload validator
To build the claim factory you need a request
To build the blacklist you need a Storage
To build the storage you need a CacheContract
To build a CacheContract you need IDK it's a mess
To build the contract you need... IDK for real
WHY LARAVEL IS SHIT: 'cause only in this framework it seems reasonable to build this clusterfuck to parse a base64 encoded string, throw some json_decode and check a signature. And have it work only to authenticate a user.1 -
Unpopular opinion: given your server has enough entropy, UUID v4 is a good session token.
It allocates 122 bits for the randomly generated part. OWASP recommends session tokens to contain at least 64 bits of entropy while being at least 16 hexadecimal characters long.10 -
Can we take a moment to recognize how absolutely retarded JS' event system is?
Events aren't objects. No, they're managed by an object, and identified by a string.
To subscribe to an event, you call object.addEventListener(name, callback). Because for some reason we can't just have an event object. Events MUST have an owner.
But to unsubscribe you don't call the function addEventListener returned, you don't use the token it returned either. No, you pass the same function to removeEventListener.
Because we don't use serializable tokens like in PP, and we don't return functions like in FP, no, we use functions as tokens, realising idiomatic DFP.2 -
It's about to be 4:20 on 4/20 get ready to run all your scrips now as you cannot have an unexpected token at 4:20 on 4/20, all token is expected then.1
-
This is not about devRant… but it might as well be.
Imagine public forum. Everyone can read and post, everyone can comment. And there's no way to send a private message.
You use said forum for years. Whether you like it or not, you form alliances, friendships, frenemieships and engage all kinds of social contracts. There's no ro(ot)ster either, so you keep all that in your head, until one day you need a social contract formalized — exchange contact info. With Steven.
You can't just “@Steven text me, here's my phone”, that's borderline suicidal. You yearn a safe haven. A proxy that'd allow privacy. So you quickly spin up a service, let's say Discord (it wasn't Discord, but close enough), post a link, and within seconds Steven joins… He and seven other Stevens.
So you send each a unique sentence, a 2fa token so to speak, and ask them to post it on said devRant-like forum — they can delete it later after all. And a few minutes later there's eleven Stevens posting garbage faster than mods can delete, because whitespace power. But you bravely sift through that shit until the correct Steven rants “I'm blue, da-ba-dee da-ba-da”, and finally you know which Discord Steven is blue, so you can privately chat about colours.
And then Steven's 75 years old, well-reputed account gets banned on devRant for posting along other spamming Stevens. And you can't even PM administration, because devRant is a public forum without PM-ing indeed.22 -
Started writing a parser for moonscript. Because I want to do my own syntax highlighting and error support.
I'm sorry, but was this supposed to difficult? Every article I read claimed this was gonna be some impossible feat of herculean effort. I half dreaded it, the other half was kinda elated.
Only it didnt live up to the hype. The tokenizer is a glorified character stream. The lexer is little more than a tokenizer, and the "most complicated" bit is nothing but a fancy transformation of the token output into a tree.
I'm completely to new parsers proper and semantic checking and maybe that's why it seemed easy, but I dont see what all the forewarning in tutorials were ever about.4 -
Few months back I got a decent increment as a token of appreciation for my good work.
Yesterday we all received a Special townhall meeting invitation.
We all were wondering what it was about. Now my colleague who sits beside was guessing that it may be about a salary revision and she complained that she didn't get any increment last time.
Inner me: Why the heck company should increment your salary for the shitty work you do.
You are simply incapable of doing what you are supposed to do.
You spend more time talking crap rather than trying to learn and use it to write some non shitty code.
You should be thankful to the company for not firing you.1 -
Trying to use a coworker's new API endpoint and I keep getting an "OAuth2 Bearer Token missing" error, despite triple-checking that I set the Authorization header correctly... finally dig into the source code and I find out that all their endpoints require that the bearer token be put into the request body. The fuck?6
-
So this is kind of an odd scenario, but bare with me. My client has been issued a JWT token. After having received and stored it, I completely reset the database, and so also emptied the users table. Note that we're using MySQL with auto incrementing ID, whose counter has been reset. The user ID is stored in the JWT, so now the JWT isn't referencing an existing user anymore, so the client will get a 401. The problem arises when a new user registers and is inserted in the new database. That user will get ID 1, and so the old token for the other user will suddenly be valid for another user. I know it's an odd case, but is this a flaw in JWT? I guess an easy solution would be to use random ID's, but I'm still wondering.6
-
Is there any modals for angular 2?? The ng2-bs4-modal gives unexpected token error. I swear after this project I am never using angular. Worst framework ever.
React Js all the way.2 -
I'm currently in a bit of a predicament.
Here's the deal:
I want to separate my back-end from my front-end code a bit more (currently PHP code is mixed up with all the HTML, Javascript etc.. basically: front-end and back-end are one).
The question here is: how should I go about this?
In my current project, I have written some javascript code with jQuery that checks whether the user is logged in or not (checks for an auth token and UID to be present in the cookies).
However, this results in the page (in this case a dashboard that only logged in users should see) being visible for a moment before the user is redirected to the login page...
How could I go better about this (No, I won't use AngularJS for this)?7 -
You know what pisses me off about Solidity?
The lack of useful information and the bullshit around it.
How many times I see a video named “Advanced Smart Contract Testing” and go through it to see that it includes...
- setup the testing in a project
- run a simple test
- test the basic attributes of a token (name, symbol etc.)
- the end
THE FUCKING END???!!!
Are you kidding me! Advanced what?
The problem is that smart contract “auditors” are getting paid $500,000 USD for 2 months of auditing. Yeah, that’s right, half a million to look over code and write a report.
So why would those folks ever share that knowledge? They wouldn’t.
That’s why you have these fucking jokers who go and get a basic understanding of Solidity and then make an “Advanced Solidity Course”
To each their own though, if it makes them feel good about themselves then go for it.
But from me, you can take your “advanced” course and shove it up your basic ass, sideways.2 -
The frontend developers in my company are the reason why I have anxiety. Here are few things that grinds my knees:
1) for a long time in projects, they deleted the auth token from their storage without integrating the logout api. They thought why use an API for that. :)
2) most of them had no clue that form fields could accept javascript as inputs and work as XSS vulnerabilities. This actually happened with a client, he got so fucking pissed.
3) One of them asked me to convert a PATCH request to DELETE cos fuck REST and HTTP methods.
For fuck’s sake. I need to get out of this place.4 -
“httpOnly cookies prevent XSS attacks”… wow.
As if not being able to get your cookies is going to stop me from doing bad things.
When I'm in via XSS, it's over. I'm changing the page content to your sign-in form with “please sign in again” notice, but it sends email/password straight to me. What percentage of users is going to enter their data? What do you think? With password managers prefilling data, and the annoyance being one “enter” hit away, I think a lot of users will fall for that. No one, including you, will be able to tell the difference without devTools.
You can rotate the session token, but good luck rotating the user's password.
Oh, did I tell you I could register a service worker using XSS that will be running in background FOREVER?
But don't listen to me. Don't think. Just use httpOnly and hope for the best. After all, your favorite dev youtuber said they could protect you from XSS.4 -
Indigogo is to retail what ICOs are to he financial industry.
- some random people think of an idea (ICO = token, IGO = magical dick cream)
- they both rely on well made but completely horse-shit marketing material
- they both spam your sites with the same repetitive ads
- they both offer discounts for getting in early (aka give us money before we have designed or built anything)
- they both make outlandish and sometimes illegal product claims (ICO = Visa is a partner, IGO = magic dick cream does magic things)
- in the end most of both options ends up giving you nothing at all and just running away with your money
- best case scenario they both deliver a product that is utterly worthless and meaningless
- everyone is hunting for that one coin or product that is a not a total scam.
I don’t hate indigogo but they certainly are shady as fuck. I’ve rolled the dice on then 4 times and got scammed on 2 of them. It’s basically a crap shoot.1 -
So I am debugging a connector library for an api that users curl.
I am fighting my ass off with errors and a lack of debug, testing or thought for CI
Take a poke around this set of classes only to find.
Postman token in the opts. and a removal of ssl check. What you straight copied from postman.
Like seriously clean up your fucking code if you are gonna put something out as production ready to your team.
Console.log('fuck'); -
i don't understand what would be termed as "relaxing" for me.
when i was in college , i watched a lot of movies on romance, bromance and friendship. being from a very angry , isolated family with bitter relationships from relatives, we had almost 0 people to interact with.
i personnally was also very different from society and struggled making friends.
as of now i did have somewhat come over this problem and have a good number of "known people" (atleast 500+) that i can categorise into'
- A just people with whom i shared a situation( college, office, tutions)
-B people with whom i have spent my free times in those situations (aka friends, and free time = lunch breaks, seat sharing, projects with them, etc)
-C people with whom i spent some time willingly( aka close friends from college, tutions and home, with whom i played cricket, went on partying/touring places , etc)
-D people whom i liked but never got a love back( aka girls to whom i told i like them. they mostly belonged to category C but eventually went to category A)
previously the category C people were special for me and i would weave my life around them. like all those bromance and friendship movies? these are the guys with whom i would do that. world tours and awesome weird shit? these people will be their in the pic... i would wish them on birthdays, i will call them every few days, go meet with them , have a bite, plan trips, movies , etc...
but today i feel am so done with everyone. i feel like everyone is so fake and forgetful, no one is worth my attention. i can easily forget wishing them birthdays or calling/meeting them every few weeks, because i don't want to or care about it.
friendship , from what i have realised, is just a means of dealing with a task in a group. it just provides a herd immunity and herd advantage . and once you learn how to survive alone, you don't really see a point in it. after coming out of college i was alone in the world, as my friends were from different fields. before college, i thought these were the guys with whom we will be living as F.R.I.E.N.D.S, not just in terms of relation, but rather in a symbiotic way: each one helping each other.
today, i feel criingy just thinking about it.
no friend will remember you for more than a year if you die now. everyone will move on. and in the struggling phase that me and my friends are right now (20-30s), we don't even need to die to forget our friendships.
my so called friends have wished me less on my birthdays than the lifeless apps i have on my phone.
so neither i am expecting someone to do something for me, nor do i think i want to do anything with anyone
------
so back to the problem, i don't know how will i find some relax or meaningful time anymore.
i am always up for trips and one of the first person to say yes to plans.
once upon a time i had this realisation that in a trip, we can enjoy 3 things:
1. the people with whom we are
2. the place we are visiting : the locals, the foods, the nature
3. the mode of travel : car on highways, bikes or flights above the clouds , or some memorable train journeys, etc.
but lately so even that seems to be not working out.
- the people are shit
- places feel like somewhat same everywhere . it's either : rocks/mountains or snow or water or buildings and population. it's just a temporary change of scenary and doesn't really gives a feeling of peace. same for mode of transport.
if i rule the going out part, the things that remains is to enjoying your job, home family and daily life. that i do , but that's the thing that creates an environment of "bored-out"-ism in my mind.
i don't know what i am looking for. the only thing i have not experienced is that class D of people. to have a token of faith/respect/appreciation/love from a non blood related person. to have someone with home i will not feel "bored out" when am planning a journey with them.
mathematically , it seems so far fetched and crazily impossible. like if get bored out and loose trust on people whom i shared most of my life after 50-60 meets, how can i be not bored, and be unhappy with a person to whom i have to see each day?
but since this happens for most of the couples, i will say the mind is the biggest and the most fantasizing mystery of human body ❤️ 💔6 -
token auth woes
I am fed up of doing shitty token authentications that don't refresh and are database dependent. what's the good way to do token auth for rest APIs? json-web-token?3 -
So today we renamed a repo on bitbucket. We changed the remote url on local PCs and kept working. When deploying, our deploying platform threw an error saying invalid repo name, which was expected. Thing is, said platform doesn't have a "change repo remote url" option, so we did it manually over SSH. It didn't work as it now says the bitbucket token is invalid. There is no option to change or set the token. Redeploying will take almost an entire day due to configurations. FML.1
-
Just curious, how do remote workers onboard with their company?
And I guess basically now all offices are closed, what happens after your hired, your first day of work?
At my company to work remotely, you would need a token card and access permissions.1 -
Cognito is the dumbest piece of crap ever known to man. Markets itself as a great & easy auth solution to dumbass CTOs who then force the devs to implement it.
I spent a week or so trying to figure out why my token expires immediately after logging in only to find out that they issued me a token that is already revoked.
WHAT THE ACTUAL FUCK COGNITO???? -
“Not a security guy” no more😼
I already completed 10/16 chapters of this book, including formatted and updated every code example in the github repo.
There’re lots of fillers in the book.
😑Lots of repeating samples.
The nosql part in node.js is completely broken.🤯
The code mixed with space and tab, so I have to format it before starting the exercise. 🙀
The git repo has about 150 forks, it makes me wonder how many copies they actually sold, since the entire book is closely tied to code samples.🤔 1
1 -
Haven't pushed anything to my github repos for over a year. Tried it today and it took me FOURTY FUCKING MINUTES to figure out this Personal Access Token HORSESHIT.
FUCK YOU GITHUB, why must every aspect of software development become spoiled by PARANOID FUCKING FUCKWEASELS?5 -
Heres some research into a new LLM architecture I recently built and have had actual success with.
The idea is simple, you do the standard thing of generating random vectors for your dictionary of tokens, we'll call these numbers your 'weights'. Then, for whatever sentence you want to use as input, you generate a context embedding by looking up those tokens, and putting them into a list.
Next, you do the same for the output you want to map to, lets call it the decoder embedding.
You then loop, and generate a 'noise embedding', for each vector or individual token in the context embedding, you then subtract that token's noise value from that token's embedding value or specific weight.
You find the weight index in the weight dictionary (one entry per word or token in your token dictionary) thats closest to this embedding. You use a version of cuckoo hashing where similar values are stored near each other, and the canonical weight values are actually the key of each key:value pair in your token dictionary. When doing this you align all random numbered keys in the dictionary (a uniform sample from 0 to 1), and look at hamming distance between the context embedding+noise embedding (called the encoder embedding) versus the canonical keys, with each digit from left to right being penalized by some factor f (because numbers further left are larger magnitudes), and then penalize or reward based on the numeric closeness of any given individual digit of the encoder embedding at the same index of any given weight i.
You then substitute the canonical weight in place of this encoder embedding, look up that weights index in my earliest version, and then use that index to lookup the word|token in the token dictionary and compare it to the word at the current index of the training output to match against.
Of course by switching to the hash version the lookup is significantly faster, but I digress.
That introduces a problem.
If each input token matches one output token how do we get variable length outputs, how do we do n-to-m mappings of input and output?
One of the things I explored was using pseudo-markovian processes, where theres one node, A, with two links to itself, B, and C.
B is a transition matrix, and A holds its own state. At any given timestep, A may use either the default transition matrix (training data encoder embeddings) with B, or it may generate new ones, using C and a context window of A's prior states.
C can be used to modify A, or it can be used to as a noise embedding to modify B.
A can take on the state of both A and C or A and B. In fact we do both, and measure which is closest to the correct output during training.
What this *doesn't* do is give us variable length encodings or decodings.
So I thought a while and said, if we're using noise embeddings, why can't we use multiple?
And if we're doing multiple, what if we used a middle layer, lets call it the 'key', and took its mean
over *many* training examples, and used it to map from the variance of an input (query) to the variance and mean of
a training or inference output (value).
But how does that tell us when to stop or continue generating tokens for the output?
Posted on pastebin if you want to read the whole thing (DR wouldn't post for some reason).
In any case I wasn't sure if I was dreaming or if I was off in left field, so I went and built the damn thing, the autoencoder part, wasn't even sure I could, but I did, and it just works. I'm still scratching my head.
https://pastebin.com/xAHRhmfH25 -
Wrote another post on medium.
This one helps in automating the security token required for testing an API.
https://medium.com/@gvnix/... -
I have a question, let's say I have a website and app both using oAuth facebook login. Should I save the access token provided by facebook in my database and if I should, what will happen to the access token when user logins with facebook on website and then login again with the app? is that mean access token is going to be overwritten by new login? and do you have any other suggestions for 0auth integration?3
-
They say that runing the same command over and over again is a sign of insanity.
LIKE HELL IT IS!!!
I've been running `terraform apply` for the last hour (trying to dump an EKS token in plain-text, because my k8s-related providers failed to auth to the cluster), and miraculously the problem went away. Now the error is no more.
Insanity?
I beg to differ!
Narf! 2
2 -
I'm looking into GraphQL and so far so good, but I am finding it hard to implement business rules, for example:
1. Receive request with auth token
2. Know who the user is by extractin userId from token
3. fetch data related to that user only.
I was only able to make it allow or deny if there is a token or not lol5 -
The whole API service relies on a token obtained by posting to a http URL: http:// blah/get_token?User=malleable?Password=longandcomplicatedpasswordforsecurity
🤔👌👏2 -
Why can't I wrap my head around laravel enough to build an authentication system I've built before 😖😡😠
External Login Service and my app would be an OAuth2 client receiving an id token...and no there isn't a third party integration for this login service5 -
So fun fact about message-passing plugin APIs, everything becomes a parallel programming problem. My lexer (the part of an interpreter that recognizes fundamental syntax elements) spawns a callback thread with request and reply channels, and then messages a plugin which is able to either talk to the callback thread or message the original thread with a successfully parsed token or an abort.
It has just occurred to me that plugins are under no obligation to sequence their requests to the callback thread, which means that having one channel for requests and one for responses no longer suffices; the requests need to each contain their response channel. -
Interview question i had:
- how does jwt work under the hood, where is it stored, what 3 parts is it made of, who creates jwt, how does the server know what information the jwt token has (how can it say oh you're Joe you can login now)
- what is the difference between observable and promise in typescript, how does observable work, what is a stream, what is the difference between fetching data through an observable and fetching data with promise and when should we use one over the other, what does .next() funcrion do in observable under the hood
Answer me these questions without googling8 -
So i'm workin on a wrapper for an api, and it has authenticated endpoints. My request function has a check to see if the user has a token before making the authed request, but guess who forgot to actually mark like 20-40 different methods as authed : D2
-
A game taking place inside an operating system. Like Tron but needs to have much more solid analogies. User's body as tty process. Some representation of scheduler priority and memory allocation. Forking. Children and zombies. Init.
Some process-ownable token representing file handles.
Network ports as portals through which data may be sent by acquiring a file handle and using it.
/proc, /mem, etc are extreme stretch goals.
Never really started because I couldn't decide how to represent all the different parts so they would all be consistent *and* entertaining
As an extension of the extreme stretch goals, a multiplayer functionality where players can shell into each other's game worlds ("computers") -
Does anyone know how to solve the 'Uncaught SyntaxError: Unexpected token <' error? It's on the first line <!DOCTYPE html>, I've even tried deleting that line, but got the same error on <html>.
I've been looking for answers for a while now, and nothing works for me! I know as soon as I post this, I'll get the answer immediately tho.
All the other pages work fine, with no errors and no warnings, all the js/css/whatever files are called in the same file which is shared by all the pages (app.blade.php).
The only 404 errors I'm getting are from the images, but I've tried deleting the img paths and still get the same error. I'm also getting 404 on the images on app.blade.php but those are working fine on the other pages, so I don't think that's it.
The controller was basically copy/paste from another project. I've tried dd($product) and looks fine.
Long story, short: everything looks fine and I'm going crazy. Anyone know what it could be?12 -
So I realized if done correctly, an autoencoder is really just a bootleg token dictionary.
If we take some input, and pass it through a custom hashfunction that strictly produces hashes with only digits as output, then we can train a network, store the weights and biases, and then train a decoder on top of that.
Using random drop out on the input-output pairs, we can do distillation of the weights and biases to find subgraphs that further condense this embedding.
Why have a token dictionary at all?9 -
Token for App -> backend authentication is generated one time when the user signs up. Sniff it once and you've got access to the user account forever.
Passwords are hashed with one round of SHA1, no salt.
Everything including login data is sent over plain HTTP.
Luckily I got permission to fix that mess1 -
What the hell kind of tool is Gitlab? I just want to automatically backmerge hotfixes from master to development. Even fucking Bitbucket had a checkbox to enable this. But not Gitlab, no, you better create a pipeline job in your already unreadable, overcrowded pipeline yml, but oh, the checked out repo in the pipeline is a detached head and you cant push with the user that checks out there. So what, just use a project acess token which revokes after a year breaking your task and then switch origin amd branch manually. But your token-user can't push to protected branches, so create a merge request instead, which requires approvals, making the automated step no longer automated.
But dont worry, you can just use the gitlab api to overwrite the approval rules for this MR so it requires 0 approvals. But to do so you must allow everyone to be able to overwrite approval rules therefor compromising security.
And so you made a feature that should effectively be a checkbox a 40+ line CI job which compromises your repo security.
which nuthead of an architect is responsible for the way gitlab (and its CI) is designed?4 -
If you build a company on the blockchain you're basically committing to 100% transparency with your investors if you fail to increase the value of your token or coin your investors will be left holding the bag. 💰5
-
Discord apparently has a new vuln allowing bot accounts to become normal accounts without regenerating the token. Explains all the thotbots and shit appearing.4
-
FUCK composer and fuck their way of installing things. Why the fuck do I need to wait an hour for one fucking package to be installed.
Also why are you asking for my github credentials you fucking dipshit program, I literally specified an oathtoken in my config....
AAAA now you are asking for a new oauthtoken, my token has reached the 5000 requests limit, how??5 -
MSAL, Microsoft's absolute dumpster fire of an authentication library. Who in their right mind designed this overcomplicated mess? The documentation reads like it was written by a committee of drunk orangutans throwing darts at a keyboard.
Want to do a simple login? HAHAHA GOOD LUCK! Here's 47 different configuration options you need to set up, three different flow types that are basically the same thing with slightly different names, and error messages that might as well be written in hieroglyphics. "AADSTS700054" yeah that's SUPER helpful, thanks Microsoft!
And don't even get me started on token caching. Oh, you thought your tokens would just... work? NOPE! Hope you enjoy debugging why your perfectly valid token is being treated like a expired coupon at a grocery store. The refresh token flow is about as reliable as a chocolate teapot.
I worked on a great project that was later axed and part of that was because of Msal issues. We literally only dealt with Msal issues. The app was otherwise stable. There were always issues with SSO, login, token validation...
It just couldn't work, like, at all.
I could see the clients getting fed up of the constant issues, yet, they couldn't move away from Microsoft since they'd already invested into their entreprise ecosystem. AzureAD, Office 365, you name it.
Shit like this is why I laugh whenever someone suggests that AGI will take over the world. Like, bro, we still haven't figured out how to make an auth library that actually works, and you think we're close to making a machine capable of thinking like a human?
Yeah right!3 -
Motherfucking peace of shit....
Dont know to whom I should direct this to .
Was creating a new login page for web app using Quasar(vue.js). Since my application have 2 different types of user, which also have different UI, and functionality.
One is written in vanilla ( and is quiet heavy) and the other one in vuejs ( though earlier it was written in vanilla too ). Login page too was written in vanilla which was working fine.
Now just yesterday I finished a prototype for the third type of user, which is also written in vuejs. Now I decided to re create login page using vuejs. Quiet small and easy to do. Finished it yesterday itself. Now since today's morning I am trying to configure it so that it this piece of shit just let me log in. It was authentication and verifying but not letting me log in.
( On server after authentication, I set cookies/token on clients browser and auto reload the page, so during next request to server/ or during reload, server will read the cookie/token and send the specific admin panel to user)
Prick. Dick.
It was setting cookie, but not at the '/' path. Mother fucker.
It was setting cookie to the path I was sending login credentials ( which was different from '/', I.e.- /login/verify=password )
So it was setting cookie/token at '/login/verify=password'.
Even tried setting path for cookie at server. Read everything on internet. MF nothing worked. All I came across was, 'this is CORS' .... 'this is CORS'. Assholes, if it were CORS', how then I am able to make request to server and getting response without error
Only a hour ago, when I made get request to '/login/verify=password' I figured out, cookie is being sent to server for this path only. Then did some changes at server, so to send login credentials to '/'. Now that shit is working
Fucking waste of time. Wasted more than 6 hours. Asshole.
Btw, if you can suggest a better way to login, then please. -
I am the responsible for the atlassian Suite at work, as I maintain the systems, set them up, and stuff.
One day, our crowd (the authentication and authorization application) just went crazy. At like lunch time it could not connect to the AD anymore. No reasons. Throwing XSRF errors (cross site scripting), because http would connect to https. "won't do it, fuck you" it told me. Out of the blue. Noone changed anything. And yea, seriously. Noone did.
It just refused to connect (as connecting to AD is connecting yourself with you own api. And refusing yourself talking to yourself). It runs behind a proxy. Therefore http/https. Well, this worked for years. But out of sudden not anymore.
Yea. Fuck you.
It was reported some hours later, at like 3pm, as people could not login to the applications using crowd as authentication and authorization server.
Tried to debug the system, where nothing was did, to make it work. At best time to fail.
First workaround: if you are logged into one of the other applications of atlassian, just refresh the site, so your SSO token gets a refresh and you are signed on again.
Then I searched more and more. And more.
But nothing worked, nothing helped.
So I addressed an emergency maintenance, take down the whole Suite, restart crowd, to apply some changes to it's settings, not knowing what happening then, because all connections of SSO will then be released. Sent out the mail like 30 minutes beforehands.
While waiting for the window, I just typed my credentials... And redid, and redid, so to type and being bored.
Three minutes before the window...
It just worked again.
Well. Wtf. Serioudl
Just came back.
No Intrusion, no changes at all. Just came back, as nothing has happened.
Kind of best part of this story... A headhunter messaged me on my way home to offer me a job as an Atlassian Suite SysAdmin for a company, at kinda the double of my salary.
At first I was thinking to go there, and when someone then asked me sth about Atlassian just start to laugh and then leave still laughing...
But then I very nicely respond that I dont want to cry at work. And wished him best luck.
I am doing some bad upgrades now on our Suite. Very painful.
And I looked into the start scripts. Some Look like the untalented intern tells another one to write scripts. Seriously wtf.
Today I followed the guide to Update a confluence and change database to Postgres. Didnt work, Postgres error.
Try it again, jquery won't load. Next try, tomcat not starting anymore. Did same thing. Every fucking time.
Yea. Maintenance window to get a nice new export soon. Will only take an hour.
To switch database in confluence, you need to set it up very fresh. And then Import your export.
Export takes an hour at our system.
Importing maybe the same time. Hope it will work (hint: Nope).
Oh, can be nice also. Just tell the Bitbucket to migrate databases, there is a fucking setting for it. Enter new database, ready, go, finished.
At least they don't raise costs very much every kinda year.
Oh sorry, yes, they do.4 -
Enjoy the lyrics to one of many songs of my favorite band Depeche Code - https://youtube.com/watch/...
Words like violence
Break the silence
Come crashing in
Into my little code
Painful to me
Fails right through me
Can't you understand?
Oh my little bug
All I ever wanted
All I ever needed
Is here in my ARMs
Words are very unnecessary
They can only do harm
Lines are token
To be broken
Feelings are intense
Logs are trivial
Crashes remain
So does the pain
Words are meaningless
And less hackable
All I ever wanted
All I ever needed
Is here in my ARMs
Words are very unnecessary
They can only do harm
Enjoy the silence -
Token for App -> Backend communication was the username of the affected account. Wanna change anything you want for any user in the system? Just need their username and you're good to go.
-
I needed a fast response, I read about Fred Hacker and I actually saw a testimony like this about him and I decided to try him out. His approach alone showed his seriousness and professionalism,this hacker is a genius and highly recommended by a lot of people,it was very easy for him to help me spy on my spouse remotely for some token….I was very happy with the service he rendered I came here to testify for what he did for me and I’ll always be grateful to him…the least I could offer is referring him to you guys contact him on fredvalcyberghost @gm ail.c om and you can text,call him on +..15..17..798..18..0836
-
To Firebase, Fuck you you ass fucking holes and fuck your useless docs
All I wanted to do is to verify your stupid id token from the backend fuck server. wasted my whole fucking day on this crap.1 -
Looking at jest errors and loads of GitHub and StackOverflow issues, it's no surprise that people claim they don't like testing.
Maybe they would if we got our tooling right.
import { foo } from 'bar';
Nah, that's an unexpected token, jest does not like this syntax.
Using require, like in jest's getting started tutorial isn't compatible with my existing JS libraries exports.
Adding type: "module" in package.json just makes another error message appear instead.
Fucking developer experience!
Why bother with unit tests at all?
How come PHP is 10 years superior to JS when it comes to code quality, unit tests, and static code analysis?
I don't even care about "ES modules". I don't want to "mock" anything either. All I want to do is import a handful of JavaScript functions into another file.
Overengineered web dev stack sucks!3 -
Pushed some changes to PROD today. Go to login and check changes .. noooooope!
Still a bit new to Symfony 5... but I'm just not a fan right now. The login screen just jumps back to itself. No login failed message and prod log had a size of 0 so that was no help.
Traced this thing way down into the CSRF Authentication functions. \is_callable(...namespace) just returning null so no go on getting a token for isTokenValid() =/
ugh! This is truly the most torturous junk I've ever seen. Nothing in the logs so I decided to just use the good old ECHO'HERE' debugger.
What was the issue you might ask?... effin' yaml file
Fix for now is to set the session handler_id back to null -
Was working on OAuth2 in unity (first time oauth attempt)
Could not get my token for like a month... Then a friend was line per lining my code, ; =\= :
It worked after that :'(2 -
So i just learned aws elastic beanstalk (EBS, ECS, ALB, EC2, Amplify, S3, RDS, SQS)
Essentially i learned how to operate with aws to deploy a full stack web application with custom backend i built, with security and jwt token, certificate manager, ssl/tls to set up https and redirect from http, and react/angular/nextjs on frontend
All with custom CI/CD pipelines docker and other devops shit
But i still feel like im missing on A Lot of stuff regarding aws. I havent worked with Fargate for example and dont know how it works or when to use it, but i heard other devs use it
Can someone list me a number of things i as a dev should know more regarding aws?3 -
So fun fact! The Rust macro error
"Macro expansion ignores <token> and everything after it"
does NOT mean that macro expansion on general ignores this token. What it DOES mean is that the macro expanded to something, then the parser was invoked, and the parser stopped consuming tokens at the specified point.
In normal human speak, this means
"This token is invalid in its context after macro expansion. Refer to the generated code for concrete error."
I spent hours moving intermediate results into macro parameters because I thought the error meant that your macro cannot expand to the second half of a comma-separated list or whatever, until I got the same message about '(' which is very obviously permitted macro output and doesn't even really make sense given that it's not a token.1 -
>finally gets around to installing vsftpd on home server RPi
>doesn't work
hmm.mp2
>configurating
>confusing as fuck template documentation
>man page isn't much better
>gets it working
>goes to log in
User: pi
Password: a
(What? It's a home file/command server isolated from the Internet. Sue me.)
nope.avi
>why
>tries again
nope.svg
>FUCK
>sees small raw-command log in bottom-right of phone FTP client
hmm.flac
>tries again, watches log
PASS *****
>the fuck
>goes to change user pass over SSH
# passwd
"Current password?"
about half a second later
"passwd: auth token manipulation denied"
>the delay tho
>WAIT A SECOND
one time i got past some parental software bullshit on a tablet by abusing the delay between opening a banned app and the redirect to the normal software at like age 7. (Doing so let me enable remote wipe through Google. bye bye software!)
>*inner 7 year old has autistic screech*
# nano temp
a
abcdefghi
abcdefghi
^O Y ^X
# passwd < temp
>fucking works
>logs in to FTP server successfully
>does the one file download that was needed
why and how did that fucking work -
Getting the angular interceptor working the way I want has proven to be a pain for me. I try to update an auth token, which returns a promise that has to be transformed to an observable again. based on that, redirect to a login page, in case of 401. But nothing works! Either infinite page reload because of the login() promise function of the auth provider or no reaction at all after a router redirect. 😤4
-
Cisco Anyconnect can blow me.
I go through the process of connecting to the vpn, username, password, token.
Then it has its pop up "respond to the banner to connect" and I click accept . . . and it does nothing.
So I go through the process again. And this time it says connected
But now I still can't connect to any of my companies sharepoint, SQL servers, Azure Devops, JIRA, etc
And the only solution to that is a reboot.
And this happens swear to god at least every other day.
Like good lord, if I put in my credentials and they pass authentication/authorization, let me do my goddamn work.4 -
VSCode doesn't request permission to edit github workflow files by default. Because it's an OAuth app and not a token, I can't grant it scopes that it did not request. I am forced to use SSH or a personal token instead of VSCode's built-in Github authentication, but because there's no convenient way to have VSCode forget that it authenticated a repo, I am also forced to checkout my own repo again and push the changes across.
If you want your product to Just Work, then Just Use Open Processes that are easy to hook into, interrupt or partially replace. Nobody can think of everything. Not even Apple's or Microsoft's mighty designers. What everyone can do is to provide graceful failure modes and offer partial strategies. -
Software development is so rotten: So I had to compile curl 32 bit. But just to create the configure script I needed friggin autoconf, libtooling and 2 other packages which homebrew would not install, because there were too many github-API requests. So I created a fucking github account just to create a token, import it in my bash to enable more requests. And it even worked. That is the scandal: That this whole shattered, stinking abomination of a process even produces some software you might actually run... and that we are using it.2
-
Has anyone experience in implementing a language server? I am currently working on a php language server and can’t wrap my head around how to efficiently find the correct scope/token from a cursor position ... like I would need to jump right into the middle of the AST somehow.
On another note I already fought the borough checker for 3 hours straight so might just go and read how the rust language server was implemented.
But I would still like to pull some experience from you if you have been through this already2 -
I wonder if anyone has considered building a large language model, trained on consuming and generating token sequences that are themselves the actual weights or matrix values of other large language models?
Run Lora to tune it to find and generate plausible subgraphs for specific tasks (an optimal search for weights that are most likely to be initialized by chance to ideal values, i.e. the winning lottery ticket hypothesis).
The entire thing could even be used to prune existing LLM weights, in a generative-adversarial model.
Shit, theres enough embedding and weight data to train a Meta-LLM from scratch at this point.
The sum total of trillions of parameter in models floating around the internet to be used as training data.
If the models and weights are designed to predict the next token, there shouldn't be anything to prevent another model trained on this sort of distribution, from generating new plausible models.
You could even do task-prompt-to-model-task embeddings by training on the weights for task specific models, do vector searches to mix models, etc, and generate *new* models,
not new new text, not new imagery, but new *models*.
It'd be a model for training/inferring/optimizing/generating other models.4 -
!dev
did my taxes months ago with the official software. because i was honest enough to mention a 250€ (annually) income for a freelance job i was later forced to submit a form for entrepeneurs. well, ok. let's use the official software for that. "yes we have the form, but no, you are not allowed to use it from this year on, please use our online service"
two weeks later (!) i receive the token to complete registration. while trying to fill the form i recognize german tax system is exactly the recursive piece of incomprehensible shit like the attached help text. 4
4 -
when i create a jwt access token and if im using a refresh token
this access token expires every 15 min
am i supposed to code a whole separate route in the backend api for the refresh token so i can make a request to the whole route to trigger the refresh token and generate a new access token?
or should the backend automatically trigger refresh token whenever it receives a request and realizes the access token has expired?3 -
Filthy Pollo: import {globalStore} from '../main.js'
Filthy Pollo: is that unstandard javascript?
Filthy Pollo: it makes me think it's from webpack
Filthy Pollo: unforgiving...
Ron Chi: i wont answer these questions again
Ron Chi: i already told u chrome supports imports its been a few months
Ron Chi: modules are evaled once, so if u have some state living in ur module if u reimport it ull just get that same state
Ron Chi: myModule.js - const myShit = { 'a': 'eh?' }; export { myShit };
Filthy Pollo: https://i.imgur.com/1X4Taik.png
Filthy Pollo: gg
Ron Chi: index.js - import { myShit } from './myModule.js'
Filthy Pollo: import and export are unexcepted token
Ron Chi: import needs to be used at the top of a file, before any other code
Filthy Pollo: https://i.imgur.com/myrrIMx.png
Filthy Pollo: Im going to assume import and export aren't supported in the browser
Ron Chi: because ur squigly line in ur editor?
Filthy Pollo: This feature is only implemented natively in Safari and Chrome at this time. It is implemented in many transpilers, such as the Traceur Compiler, Babel or Rollup.
Ron Chi: https://github.com/paulirish/...
Ron Chi: actually i dont think its handled properly by babel, webpack handles it
Filthy Pollo: what the fuck why use import and export that wont work in other browsers like firefox, edge, etc. ?
Ron Chi: because other browsers are slow
Ron Chi: its still standard
Filthy Pollo: your answer is not really professional
Ron Chi: ?
Ron Chi: why because its my fault that other browsers are still working on it
Ron Chi: they fought over implementation details forever, than it has to be implemented properly before shipping it
Filthy Pollo: Im blaming the people who are still using export and import in the browsers
Ron Chi: u wont be using modules without transpiling without some limited market for a couple years, otherwise ull still be using rollup / system.js / webpack
Filthy Pollo: obviously webpack
Ron Chi: thats up to you, it seems the google ppl use rollup
Ron Chi: but most of the community chose webpack
Ron Chi: angular 2 uses system.js internally i think
Filthy Pollo: Firefox 54 – behind the dom.moduleScripts.enabled setting in about:config.
Edge 15 – behind the Experimental JavaScript Features setting in about:flags.
Filthy Pollo: nobody wants to be bothered to change settings in flags
Filthy Pollo: the developers who use experimental features are weirdos as hell
Filthy Pollo: the joke is when they use experimental feature for production and force them to download chrome
Filthy Pollo: Monopoly as hell
Filthy Pollo: Corruption of User Experience -
I was signing up for a new account on Magic. I wasn't paying attention so I accidentally didn't change my date of birth, so it didn't let me create an account because they thought I was just born today. I changed that field but nope, it remembered I had told it I was 1 day old and it didn't let me change my mind. Delete cookies, nothing. Reload page, nothing. So I go into Postman and re-create the request and BOOM! I even got an access token for their API. This is why I love being a dev.
-
I jumped on this NodeJS codebase to quickly implement an additional method in the custom logger. How hard could it be, right?
I implemented the method alright. But I can't find where to use it... There are like 10 different logger instances used in this tiny app and in one place logger is even used as a vessel (holder object) for the client's JWT token (to access it from the interactor).
oh, and it's a javascript app (somehow I assumed that node apps are typescript.. silly me!)
What the fØ©ĸ spaghetty-fest is this!?!?!4 -
Help with C code
int main()
{
int x =10;
void *p = &x;
printf("%d", ((int*)p)* );
return 0;
}
I'm trying to cast p to and int, for dereferencing it and printing the value of x, but Im getting an "expected expression before ) token" in the line for printf.8 -
You know when you have one of those days where you're really tired and just don't really want much bullshit, and because of that you get an unexpected token space? Well I do
 2
2 -
Againg symfony shitty:
look - I want to validate csrf. I found docs how to do it.
https://symfony.com/doc/2.8/...
"if ($this->isCsrfTokenValid('token_id', $submittedToken)) {
// ... do something, like deleting an object
}"
But how the fuck should I know what is token_id from this stupid writing?
I have debugged their code to find it out. What a fucking waste of time !!! Free shit. Companies could probably pay small fee for the symfony if they could find people who do better job. Because by paying salaries for finding such shit costs them anyway.
And there was a htmls where the token was:
<form name="form" method="post" action="/admin/policy/47/push-im-xml">
<button class="btn btn-xs btn-info" type="submit">Push IM XML to GA</button>
<input type="hidden" id="form__token" name="form[_token]" value="LDVrl52CYtbT-kDudsjzrNAdJuIyFZhafsgk9QDnWGs"></form>
Guess what was token_id : form
:D whf. How the fuck could I know? I have tried various ways before debugging liek form_token, form[_token], _token
Who could fucking think its 'form' ?!!!! Wth. This is a joke.9 -
switched job. found out today that my qa - soon to be promoted to senior - does not know what a csrf token is.
*stares out of window*2 -
What is the reason behind Git Access Tokens being viewable only once after generation on platforms like GitHub? I'm struggling to comprehend this approach as it compels me to store the key in an insecure manner.2
-
I wanted to know what is the worst mistake you make on database.
I have actually implements the logic of token access control on database and not on business logic layer.
The database have a login procedure which accept username and password. That login procedure actually hash the password and try to authenticate user.
If it is a correct user , it generate a token. In other to use other procedure on database , you must provide a token. By using that token , the procedure know who is it and what permission is granted to that user.4 -
Almost finished with latest preprocessor.
Why am I always working on preprocessors tho? Shit...
Anyway, almost finished ok.
Idea is, basically, that inside a C source or header you can write a perl subroutine instead of `#define ...`.
The mechanism is rather simple:
```C (wat?)
macro mymacro($expr) {
· // perl code goes here
· return "$expr;"
};
```
`$expr` is just a string holding whatever block of code comes after an invocation of `mymacro`. You can use the builtins `tokenshift` and `tokenpop` on a string to get the first and last token, respectively, and then `tokensplit` gives you *all* the tokens.
Whatever string you return is what the expression you received is replaced by:
- You can just give back the expression as-is to get the exact same thing you wrote -- so `mymacro char* wat;` gives you `char* wat;`.
- But if you return a galaxy's worth of C code, then bam. Macro expanded into it, just like that. It's a perl subroutine, so let your imagination fly. Wanna run some scripts at (pre)compile time? Then you can.
- If you return an empty string, then puff. No code. Input consumed.
- If you give the name of another macro (eg "another_macro $expr;"), the expansion recurses.
- If you return the name of the currently executing macro, no recursion happens. This lets you wrap C keywords without (too much) fear.
It's kind of cool because a separate perl module is built from the macros themselves. So then you can include those in another C file. Syntax is basically more perl because why not:
```C (yes)
package mypkg;
· use lib "path/to/myshit/";
· use pm funk qw(mymacro);
```
The `lib` bit actually translates to `-I(path)` for gcc. But for some reason the way you add an include path in perl is `use lib "path"`, so yep. I get it's confusing but just go with the ::~ f l o w ~:: ok.
Then the `pm` stuff is not valid perl (i think), but I took the easy way out and invented it to ensure there is a way to say "OK I don't give a single shit about the C stuff, just give me these qw()'d funky macros from this file." If you simply `use funk qw(mymacro)` then you also get an `#include "funk.h"`.
Speaking of which, headers are automatically generated. Yeah, fuck you, I added `public` to C, bite me. It's actually quite sexy as I defined it using the preprocessor:
```C (yes but actually perl)
macro public($expr) {
· my $dst=cmamout()->{export};\
· tokentidy $expr;
· push @$dst,$expr;
· return "$expr;";
};
```
Where `cmamout()` is a hash from which the output is generated. Oh, and `tokentidy` is just a random builtin that cleans up extra whitespace, don't mind it.
So now the bad stuff: I have to fix a few things. For instance, notice how I had to escape a new line there? Yeah. It's called dumb fix to shit parsing, of course.
But overall I'm quite satisfied with this. And the reason why may not be so obvious so I'ma spill it out: backticks, motherfucker.
That's right. Have a source emitter written in an esoteric language?
```C (yes really but not really)
macro bashit($expr) {
· my ($exe,@args)=tokensplit $expr;
· return `$exe @args`;
};
```
So now you can fork off into parallel dimensions; what can I say pass the pipe brother.
MAMmoth in the room is yes, this depends on MAM. What is MAM? MAMMI. It's the original name of my infamous picture of an ouroboros eating it's own ass while stuck in limbo contemplating terrible life decisions of a build tool, avtomat (go ARSLASH <AR/> [habibi]).
So what's the deal with that? avtomat is a good build tool _for me_, not... ugh, you. I made it for *myself* baby things are not going to work out between us I'm sorry. MAM just does lots of things I wanted build tools to do in the __EXACT__ way I wanted them done. I'd say you should go use it too maybe, but actually don't and you shouldn't because I broke main some weeks ago to fix some other shit and then implement this. Yeah, pretty stupid, but what the hell. I'm the only user after all!
In conclusion, I am fully expecting to receive my mad props and street cred in the mail along with your marriage proposals en masse, effective immediately.
Further reading: https://youtube.com/watch/...5 -
Note: I had AI rephrase this because apparently it was too full of swearing or smth to be accepted and I was getting a "there was an error posting this rant". Nice that people at devrant's can't even show a clear error of WTF is going on, not even in chrome dev tool console/network requests, so maybe you're able to figure out WTF is going on and fix your post. They must be the same kind of people I'm ranting about.
-----------End of the note.----------------
TL;DR;: My coworkers are smart idiots that learn fast but can't control themselves into turning any project into a trashcan of spaghetti code and I'm burning out and want to switch for couple years to a simpler job.
I'm considering leaving my career in programming, consulting, and project management in favor of a more straightforward, manual labor job—perhaps something like baking or another role that relies on physical effort rather than constant problem solving.
I’ve reached a point where I can no longer tolerate the challenges of my current position, especially due to the dynamics with my coworkers. I long for a day where I can work for eight hours, exhaust myself physically, and then go home without any lingering mental responsibilities or ties to complex problem solving.
Over the past decade, I’ve collaborated with many people, yet I've only had the opportunity to manage an entire project from scratch on my own twice. In those rare instances, everything ran smoothly, issues were quickly resolved, and the code remained stable for years without constant complaints from clients.
Unfortunately, my coworkers, despite their intelligence, tend to overcomplicate even simple tasks. They often fall into the trap of overengineering, chasing the latest technologies and implementing unnecessarily complex paradigms, design patterns, frameworks, and techniques—even when I’ve offered simpler, proven solutions.
For example, I’ve built robust portals that handle everything from national highway finances and warehousing to HR and inventory management for major companies. In contrast, when others attempt similar projects, the resulting code becomes overwhelmingly complex and difficult to manage.
To give a few specific examples:
Example 1: The .NET Portal
We began developing a .NET portal about two months ago, which is now nearing version 1.0. Before we even started, the team had created multiple flowcharts to split the project into components like SaaS deployment, Docker integration, obfuscation, and separate portals for user administration and backend processes. Within a few weeks, they scrutinized and debated numerous authentication technologies—even though we had successfully implemented JWT token solutions in the past. The team continually shifts focus, leaving me uncertain about the final direction.
Example 2: Over-Engineering with Patterns
In another project, the team overused inversion of control (IoC) and mediation patterns, even going so far as to have an AI generate a custom message bus. Navigating this overly decoupled code is challenging; even Visual Studio’s IntelliSense struggles to provide guidance, and the code often feels like a puzzle that changes whenever I return from a break.
Example 3: Complicated Logging Implementation
We needed to add logging functionality, and I proposed a simple solution using custom exceptions that would bubble up to a central logging mechanism. Despite its past success in saving time and reducing frustration, the team decided to implement three different logging methods—one using .NET’s ILogger, another with Serilog, and a third hybrid approach. They even suggested using a rarely seen technique involving stack traces to determine which function threw an error. This approach added unnecessary complexity and only increased my frustration.
Now, even though the project is too far along for me to withdraw, I find myself feeling burned out just a few days back at work. The code has become a tangled mess, and even routine tasks like adding logging are turning into sources of intense frustration due to constantly shifting ideas and overly complicated designs.
On top of all this, I’m also disappointed with the performance of AI tools, which seem to be producing unreliable code that requires further fixes, compounding my frustration.
I’m now seriously contemplating a complete career change—perhaps even moving to a country with a better work environment, such as Denmark or Switzerland—in the hope of finding a job where the work is more straightforward and less mentally taxing and better paying4 -
I am thinking of how I can make data upload reliable. I am sure that I am making it more complex as it could be and I need some pointer.
My goal is to have a pause/resume feature in file uploading.
Here is how it would work.
In order to start uploading , you give the server
1) File Name
2) Folder path you want to upload it to
3) Checksum of the file
Here the server will check whether you can upload it to a folder, whether the file have been previously uploaded (by file name and checksum)
If you could actually upload to the folder , server will return "unique file token" , "folder path" , "unique byte token". Let call it init_upload().
The client will use "unique file token" (to identify the file) , folder path (to know where to upload it to) , "unique byte token" and byte[] (data which to actually upload). Let call this operation data_upload().
If the operation is actually complete , server will return new "unique byte token"
Internally it will actually work like this.Let say we want to upload "file.mp3", when the client call init_upload() it will create
file.mp3 and unique_byte_token.file.mp3.
When the client upload data first time , it will append data to unique_byte_token.file.mp3.
When the client upload data second time , it will check whether the "byte token" that client put is the same as previous "unique_byte_token". If it is same ,
1) we move the data from unique_byte_token.file.mp3 to file.mp3
2) Delete unique_byte_token.file.mp3
3) Create new unique_byte_token.file.mp3
4) Append data to unique_byte_token.file.mp3
The reason I am using "byte token" is because I want to check whether previous upload is actually success.
Let say we need to call 50 part of data_upload() will put 49 part to file.mp3 and 1 part to byte_token.file.mp3.
Finally the client need to call data_upload_complete() which will
1) Put reminding 1 part to file.mp3
2) Remove byte_token.file.mp3 as cleanup6 -
> * npm login *
> puts everything right, uses token because of OTP
> npm login fails: incorrect user or password
you know what, fuck you5 -
One of those debugging days where minutes feel like hours, and hours like days.
I had the bad luck of being asked to dive into a legacy project which was unmaintained for months, but of course it's still on prod. And very suddenly the urgent need arrises to change stuff.
Yet: the docker stack won't work. It builds fine but the stack crashes.
Long story short: some internal api URI were renamed and at some point one internal api started to always require an access token. Which we set for the stage, prod env yet somebody forgot to mention that to the devs of legacy-project.
That ain't too bad.
WHAT IS FUCKING BAD IS THAT YOUR SHITTY APP SWALLOWS THE ERROR MESSAGE!
I mean it's bad enough I have to `var_dump && die` your app since you never bothered to setup a xdebug that I could use out of the box, yet egregious fact that your app would catch a valid exception but transforms it into an "internal warning" is borderline insane!
It's ok to throw exceptions. It's ok to let your service die. That's how other will know what and where to fix it. (You may want to restrict the data visible to the outside, but that's a whole different conversation.) -
I am frustrated with the JWT token based authentication library I am using for my lumen(laravel) based backend. It is having lot of ongoing issues with infinite timed token(mobile apps) and others... Here is the link
https://github.com/tymondesigns/...
If anyone has any suggestions for a good replacement for this it would be awesome because this is shitty in the support for the library nobody addressed the issues raised and threads are not even taken care about. It is so frustrating when you implement something but have to deal with the shortcomings of it, when it does not even do some basic things it is supposed to do. I feel bad saying it for somebody else's work. But, sometimes it has to be ranted out... That's the whole point of devRant. So yeah JWT based authentication library suggestions for laravel based backend. Because tymon-auth is shit.1 -
I logged into BitBucket, opened my repo, and clicked on my Trello board. Why did I have to log into my Trello board? Trello is now connected to your Atlassian account, I got an email about it. It's the same username/password. It exists. They know it does, because they're the ones that told me. Create a token and pass it to Trello for me so that I don't have to log in. It isn't all that difficult. I can hear you now: "What if they have a different Trello account they want to log into because...{reasons}?" Then you can have a handy little "Switch Account" button or something that will log them out, log them into their new account, and display that data. One button push for them, no buttons for the rest of us.2
-
Work! Terribile doubt about our project 😭i will leave this company if we do not come up with an adult solution 😔
We are working for another Company, they asked to add a web app to their project.
We made frontend and backend, we make user auth to their api, then call their api (place order, get orders etc), passing their auth token to their services.
Which Means that our endpoints are not really protected (i think) and if we add an endpoint that does not use their api, the only way to secure them Is to take the token, validate It by calling for example get /order of the api and if It fails just discard the request....too slow?
my colleagues do not want to put a serious auth they Just want to use the company api and leave the rest open...
And the customer Just asked to use some other api functionality, but that api has another auth... How do we pur them togheter? The last api want the id of the user to do machine ti machine auth
It Is my 6th month here no one thaught me anything, i think i'll Just leave ..or am i Just experiencing the developer Daily work?😔7 -
Me: Hey I haven't used these repos/tokens/files in a while, let's remove them to clear up some space
Day later, a colleague: Hey Alex, could you update this repo/token/file?
EVERY FUCKING TIME1 -
Sometimes while working I find a subproblem that is isolated from the original problem domain, for example token renewal in an RTR authentication system. I take note of what I've been working on, clear my head of the broader problem write an exact specification of the subproblem. Then I code to that specification. The result is usually a self-contained open-source module which continues to improve my pace of work for years to come.
-
Literally nothing I post makes a difference all your works are endlessly banal and pointless as no one is granted token when in their graceful years to accomplish a thing20
-
I have a doubt regarding blockchain. I understand how it works, but couldnot make use of it.
I am currently working on a platform which let client to assign task to their employee
Now I am planning to make use of blockchain on existing platform, to somehow set up a mechanism to authenticate that employee had completed the task, as a certification to the employee. I just cannot figure out how
I thought of an implementation, ( if its possible ) where client will trigger the smart contract with some employee-specific data, and the smart contract will generate a custom token, which will then be sent to the employee's account. This token will be non transferable1 -
In regards to my last string of posts regarding react and Auth, I got it working the bearer token is being passed but now just getting XML errors every time I submit a form. All the data being passed is JSON. I've created a stackoverflow question https://stackoverflow.com/questions... as I'm getting nowhere and SO really isn't helping either. So if anyone wants to take a stab, go for it.11
-
!rant
Got a question since I've been working with ancient web technologies for the most part.
How should you handle web request authorization in a React app + Rest API?
Should you create a custom service returning to react app what the user authenticated with a token has access to and create GUI based on that kind of single pre other components response?
Should you just create the react app with components handling the requests and render based on access granted/denied from specific requests?
Or something else altogether? The app will be huge since It's a rewrite off already existing service with 2500 entities and a lot of different access levels and object ownerships. Some pages could easily reach double digits requests if done with per object authorization so I'm not quite sure how to proceed and would prefer not to fuck it up from the get go and everyone on the team has little to no experience with seperated frontend/backend logic.4 -
I have participated in a hackathon this weekend and one of the theme of hackathon was blockchain and being a blockchain dev i have created a DApps which follows token standard and other security standard but our UI was kind of basic cause we didn't have any designer in our team but one participated team's UI was far better than us but has serious flaws in the smart contract and guess what they are the one being selected and that's not it there wasn't a single judge who has basic knowledge of blockchain.I was using DApp term very often while presenting our idea and one of a judge literally asked us what is dapp? I mean WTF? Now i am regretting why did i participated in this shitty hackathon? On top of all that they juat give a single sticker for whole team. Wtf we are supposed to do? Cut it ? If you are a blockchain dev don't forget to see this beautiful function i found in the token contract of the selected team from the github.
 1
1 -
Today checked my learning time tracker. I have spent already 80 hours for learning angularjs. And I still am not able to write unit test without errors. What the fuck. How many hours more do I need to finnaly be able to write unit tests without any problem?
Like today getting
An error was thrown in afterAll\nSyntaxError: Unexpected token 'export'
and I do not even use afterAll() funciton so they give error somewhere from the inside of libraries. Why they do that? why cannto they give easy to understand error?
Everytime I sit to write unit test for learning, all the time I feel I will not understand. And I am right everytime. Damn. That makes me need to force motivate myself. I want to see results, not sit at the same place so many time.18 -
What did I do while down for the count with Covid?
* Setup a static React site
* Hosted the site at Cloudflare Pages
* Protected the page through CF access
* Extracted the JWT
* Setup a Rails API to validate the token
Now I have static React UIs with a nice rich API backend.2 -
I've been planning a startup project for months now. Then, what was a supposedly simple quest of finding out whether session-based or token-based authentication is better, has become a question of whether I should setup my own OpenID Connect (IODC) auth server or stick to simpler methods.
I've already spent almost a week learning OAuth2 and OIDC, and I can't tell whether this route is an overkill for my usecase. (Or that I just don't want to admit I'm falling into the shiny tech trap.)
How about you guys, how would you approach authentication? JWT/JWE? Sessions?6 -
Trying to make a nodejs backend is pure hell. It doesn't contain much builtin functionality in the first place and so you are forced to get a sea of smaller packages to make something that should be already baked in to happen. Momentjs and dayjs has thought nodejs devs nothing about the fact node runtime must not be as restrained as a browser js runtime. Now we are getting temporal api in browser js runtime and hopefully we can finally handle timezone hell without going insane. But this highlights the issue with node. Why wait for it to be included in js standard to finally be a thing. develop it beforehand. why are you beholden to Ecma standard. They write standards for web browser not node backend for god sake.
Also, authentication shouldn't be that complicated. I shouldn't be forced to create my own auth. In laravel scaffolding is already there and is asking you to get it going. In nodejs you have to get jwt working. I understand that you can get such scaffolding online with git clone but why? why express doesn't provide buildtin functions for authentication? Why for gods sake, you "npm install bcrypt"? I have to hash my own password before hand. I mean, realistically speaking nodejs is builtin with cryptography libraries. Hashmap literally uses hashing. Why can't it be builtin. I supposed any API needed auth. Instead I have to sign and verfiy my token and create middlewares for the job of making sure routes are protected.
I like the concept of bidirectional communication of node and the ugly thing, it's not impressive. any goddamn programming language used for web dev should realistically sustain two-way communication. It just a question of scaling, but if you have a backend that leverages usockets you can never go wrong. Because it's written in c. Just keep server running and sending data packets and responding to them, and don't finalize request and clean up after you serve it just keep waiting for new event.
Anyway, I hope out of this confused mess we call nodejs backend comes clean solutions just like Laravel came to clean the mess that was PHP backend back then.
Express is overrated by the way, and mongodb feels like a really ludicrous idea. we now need graphql in goddamn backend because of mongodb and it's cousins of nosql databases.7 -
Here is the REST API design of my LEAD programmer
# Access the API
1. Get access token with out username and password (GET /token)
2. Sign in with username, password and add access token as query param (POST /user/auth?token=[access_token]
3. Call other resources by adding token as query param
# Create new objects
- He uses PUT method in every resources to create new objects4 -
I'm building a nodejs REST api with jwt token authentication for the first time. So far, it's been as smooth as butter. Any hiccups or gotchas I should worry about?
-
The craziest way to send notification from firebase to Flutter depends on my_sql DB
Ok, I tried so hard to deal with notification in my app by specific conditions in my #my_sql DB
The background work in #flutter is kind of not easy to deal with, so here's my crazy way to achieve that:
I connect my app with #firebase and every time a new mobile open the app it rejecte it's #token in the DB
Now I create a public #PHP file that has access to my my_sql DB and #firebase1 -
Does anyone know a public API to test basic authentication other than github that return a token when the submission is successful1
-
when you made a custom ldap token based authentication, what is suitable for every projects of your workplace.

-
i have a question. when a user logs in, the app should have the "logged in" effect. so when he tries to navigate go login page it should redirect him to home page. but how can the app know if he has logged in? should i store the jwt token in sharedprefs and check if hes logged in locally on the phone or is the backend rest api supposed to handle that (and how)?
-
Let's Say you use tokens as authorization method.... The First time you generate the token you still have to manage password and other data....how secure (tinfoil hat mode activate) do you implementat that usually?1
-
Does anyone here have/use a HackRF? I'm getting one soon as a small token of appreciation from my management and I'd love to get tips/comments1
-
Fucking taiga wasting my day.
Client asked to set up a private taiga (taiga.io, some open source Jira alternative).
All goes fine and dandy until you need to link domain user creation to taiga user creation.
Seems I have to choose between having public registration (allows to programmatically create users, but also randoms to sign up) or use their private registry API that asks for a fucking token that is supposed to be returned from their membership/invitation API, that, guess what, doesn't return any bloody token. You can only get the token on the Django admin control panel.
Guess I'll have to end setting up LDAP or integrating with their existing gitlab, but this gig is already starting to smell, and we are close to the weekend 😡1 -
I am getting warning from Drupal
"The following token types do not have any tokens defined:
$info['tokens']['subscription']"
Damm yuum -
I know I sound stupid but I need help, I create a repo on GitHub using gh-api ```js
export async function createARepo({name,description,token}) {
const headers = {
"Authorization": `token ${token}`,
"Accept": "application/vnd.github.v3+json",
}
const {data} = await axios(
{
method: "POST",
url: "https://api.github.com/user/repos",
data: {name,description,auto_init: true},
headers
}
)
return data
// console.log(res)
}```
when I run this code it only creates an empty project with a readme but I also want to create a file with a .html extension of the project can anybody help me with how I do this?7 -
Msal.js. I give it 3/10..
The docs are duplicated, and in various states of out of date. Half the library seems to be undocumented based on how many edge case bugs I've hit, it offers a popup login but you have to have a set specified white list of urls you can launch the popup from which makes a popup login pointless...
Ontop of that my colleagues shat the bed on it and fucked the whole implementation including the azure b2c setup... We do not even have a backend app listed in the azure b2c apps. The redirect also won't work if you don't instantiate an object in a hidden iframe of your own website that fetches a token... This does not make life easy when you use a SPA framework and you have already implemented a whole pipeline abstracting the creation of this object behind layers dependency injection.. Nice.
After sifting through endless shit I finally have a solution. What a week. -
When building a REST-API, that is secured with tokens (JWT or something),
Should the token be included in the body or in the headers?4 -
I've got this... thing. I built it when I first started with PHP. It's an OAuth2 system to pull form data from a service into a plugin, to make the rest of marketing's lives easier. It requires manually taking the initial received token and putting it into a database when doing the first auth. Occasionally it breaks and I have to try and remember the steps to get a replacement token to start the cycle over.
Someday I'll fix it, but for now... Let's fuck about with my browser for a few minutes to get the new token. -
Why do you support sessions for an API (not REST)??
You remove the token and still get positive replies because the session cookie allows it.
At least the session in the cookie gets killed when the token is invalidated, but really, why?3 -
I need some clarity with the situation below.
I have my API ready.
Let's say I have a route /reset/token,
I want to be able to serve a html file with css and all that once I've processed the token internally.
I've not worked with the whole stack before so I've never really served files based on conditions i.e if the token is valid serve x else serve y.html
Also, I'm pretty sure node.js isn't the best for serving files.
So I'm taking another approach with nginx which is to implement /reset/token to serve the static file with it's coupled js file to query the API. Seems standard to me but I have this feeling that a prefilled html would be more secure than one with exposed js.
Is this the right way? Should I worry about my API calls being exposed via the js fil ? Is obfuscation the only way to handle this ? Is this the way everyone does it cause somehow I don't see the key js files in most sites. How are they hidden if so? Or are they?
I'm confused and also nginx won't let me rewrite /reset/token to something else without changing the browser url field. How do I prevent that ?1 -
Late last month, I unintentionally fell for a cryptocurrency fraud. A Facebook imposter convinced me through a phishing scam of how I would make a sizable profit from a legitimate cryptocurrency company, which he claimed enabled traders to invest and make sizable profits. They took advantage of me and made off with $316,000 worth of cryptocurrency. As this was money I had worked so hard to obtain, I was shocked and uncomfortable. After reading favorable articles and internet reviews, I learned that “THE LION CYBER SECURITY COMPANY” is a licensed recovery firm that specializes in all types of hacking and cryptocurrency recovery. I immediately struck up a dialogue with the Experts, and I was able to get my money back. This is a token of appreciation to them, If you are a victim looking for an ethical hacker to help you get your money back, contact THE LION CYBER SECURITY COMPANY through any of the contact information listed below
 1
1 -
How can you build an oidc library almost completely on observables? Cannot complain about it, as it's open source, but what if you want to access some token data synchronously?4
-
They asked me to build a small website they will embed in a native application with some web wrapper in Android and iOS.
But also asked me to build a login web service that will return a JWT. Done.
They want to do a native code login form that opens up the web wrapper with my small website already logged in using the login web service.
I have no idea how to proceed in the backend.
At first i tried using postman with a POST request to the sessions/sign_in route and sending a form with the authenticity token and the email and password; but CSRF stopped me. I don't want to turn it off because of reasons.
Now i am wondering how to use this JWT to generate a cookie with a session inside it that they can use in the web wrapper.
Any help would be appreciated :)4 -
Just cut down registration from 5s api response (because its sending email confirmation) into 70ms using rabbitmq (emails are now delegated in rabbit queue and sent whenever the queue takes place)
But still around 70ms to register which is great and fast (because it also generates jwt token and returns the whole user object + jwt) so its difficult to keep this at 7-9ms response time
Is this normal and is it fine to leave it at 70 or can this be optimized (or should it be)?5 -
not sure what i changed, if anything
but my previously working code calling another microservice now fails because invalid jwt token
fml3 -
There should be a blacklist for websites that don’t allow 2FA or do it through SMS. There’s no excuse for sites such as PayPal not allowing TOTP, only some prehistoric hardware based token generator.1
-
DIGITAL ASSETS RECOVERY TEAM // CRYPT0 PANDEMIC HUNTER
Online trading can be risky, even for the most cautious investors. A few months ago, I bought a DAO token with 540 SOL after thorough research. The token had a good community and appeared secure, but a few hours later, it dropped to zero, and I lost everything.
I didn't give up and searched for ways to recover my stolen crypto, finding Crypto Pandemic Hunter page. I contacted them and received a quick response. They investigated my case and used advanced software to trace the stolen funds. Within four days, I got my SOL back, and others did too. I'm grateful for their service and urge fraud victims to reach out to cryptopandemichunter[at]consultant,com 1
1 -
I need to refresh my Access Token from Flutter app. Should I use token expiry field from Access Token or attempt a request and if get 401 and some error from auth0, refresh token and try again?5
-
STEPS TO RECOVER STOLEN CRYPTO CURRENCY > CONTACT FUNDS RETRIEVER ENGINEER
My name is Clara Bennett, and I almost let cryptocurrency destroy me. Two years ago, after selling my green e-commerce startup, I plunged headfirst into the crypto world. yield farming , I was all in. I believed I wasn’t just investing; I was participating in the next great technological revolution. Within months, my portfolio skyrocketed to $200,000. I even started sketching ideas for a blockchain-based microloan platform to empower small entrepreneurs around the world. Crypto felt like pure freedom and limitless potential. I thought I was untouchable. I thought wrong. It happened through a single email. It looked like a standard security update from my wallet provider polished, routine, and harmless. I interacted with it briefly, thinking it was legitimate. Hours later, I checked my account and realized my entire wallet had been drained. Every token, every coin, gone. I sat there in disbelief, replaying the moment over and over. I had built my career on being cautious with technology, yet somehow, I had still been compromised. The blockchain’s promise of "irreversible transactions" now felt like a cruel joke .Devastated and desperate, I scoured forums for solutions. Most people told me there was no hope once crypto is gone, it’s gone. Still, I refused to give up. That’s when I stumbled across FUNDS RETRIEVER ENGINEER . I decided to reach out. From the beginning, they were empathetic, and honest about the challenges. They explained their process step-by-step, focusing on tracing transactions, tracking down phishing operators, and leveraging advanced blockchain analytics. It wasn't an overnight fix. It took weeks of meticulous investigation, technical recovery work, and legal coordination .But in the end, their persistence paid off. FUNDS RETRIEVER ENGINEER was able to trace the stolen funds across multiple wallets and exchanges. Through a combination of technical expertise and strategic action, they managed to recover the full amount I had lost. Today, my crypto portfolio is intact once again. More importantly, I’ve regained my confidence though I am now much wiser and far more cautious. I learned the hard way that while crypto offers incredible opportunities, it also demands extreme vigilance. Thanks to FUNDS RETRIEVER ENGINEER , I recovered my lost funds and also reclaimed my future in the digital economy.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
WHITE HAT HACKERS FOR DIGITAL ASSETS RETRIVAL- HIRE FUNDS RETRIEVER ENGINEER
When my sister Sarah first came to me, I could see the worry on her face. She had just been scammed out of $20,000 in a cryptocurrency investment, and I could feel her frustration. Sarah had seen a deepfake video of a famous entrepreneur promoting a new token, and everything about it seemed legitimate. The entrepreneur’s face, voice, even the background looked so real that she thought it was a solid opportunity. Without second-guessing, she invested $20,000 in the token. But things quickly took a turn for the worse. Soon after she made the investment, the developers of the project disappeared, and the value of the token crashed to zero. Sarah was devastated, feeling completely lost and unsure of what to do next. It was a tough situation, but I knew exactly where to turn FUNDS RETRIEVER ENGINEER . I had been through a similar experience myself not too long ago. After being scammed in another crypto investment, I was fortunate enough to find FUNDS RETRIEVER ENGINEER . Their blockchain forensics team helped me recover a significant portion of my funds, and I knew they could help Sarah too. I explained my experience to her and reassured her that there was still hope. Sarah immediately contacted FUNDS RETRIEVER ENGINEER , and their team went to work right away. They used their advanced blockchain forensics tools to trace the scammer’s wallet addresses. With their expertise, they were able to identify the scammer’s movements and follow the trail of stolen funds. Then, they took it a step further by pressuring the cryptocurrency exchanges to freeze the scammer’s accounts and work with them to recover as much of the stolen money as possible. Within a short period, FUNDS RETRIEVER ENGINEER had successfully recovered $15,000 of Sarah’s lost funds nearly 75% of what she had invested. The process was smooth, and we were both amazed at how quickly they managed to track down the scammer's wallets and get the money back. We are incredibly grateful for FUNDS RETRIEVER ENGINEER and their team. After seeing how they helped me and now Sarah, we both know how crucial it is to have experts on your side when it comes to recovering funds from scams like these. If you ever find yourself in a similar situation, I highly recommend reaching out to FUNDS RETRIEVER ENGINEER they truly make the impossible possible.1 -
HIRE A CERTIFIED CRYPTOCURRENCY RECOVERY EXPERT // CONSULT RAPID DIGITAL RECOVERY
Losing a secured cryptocurrency to a scam was one of the most devastating experiences of my life, but thanks to RAPID DIGITAL RECOVERY, I was able to recover everything I lost. It all started when I fell victim to what seemed like a legitimate “free token giveaway.” The website looked incredibly professional, filled with fake endorsements, clean visuals, and a seamless user interface that made the process feel completely trustworthy. I connected my wallet and approved what appeared to be a standard transaction. Within seconds, I watched in disbelief as \$8,000 disappeared from my account. It was an immediate and painful realization I had been scammed. The panic that followed was overwhelming. I felt helpless, angry, and embarrassed. I began searching online for anyone who could help, and that’s when I came across RAPID DIGITAL RECOVERY. I reached out without much expectation, assuming the chances of recovering stolen crypto were slim to none. To my surprise, they responded quickly and professionally. Their team immediately got to work and reassured me that they would do everything possible to assist. RAPID DIGITAL RECOVERY launched a full-scale investigation, using blockchain forensics to trace the stolen assets. They followed the funds across wallets and exchanges, identifying the scammer’s activity and tracking the flow of transactions. Their attention to detail and knowledge of how crypto scams work was impressive. They were transparent throughout the process, kept me updated at every step, and never overpromised. Still, they delivered results beyond anything I hoped for. Their persistence paid off. Through their efforts, they were able to locate the stolen assets, coordinate with the proper channels, and freeze the scammer’s accounts. The most incredible part? I recovered 100% of my stolen funds. Every dollar that was taken from me was returned. I never thought that would be possible, but they made it happen. What stood out the most was not just their technical expertise, but their empathy and commitment to helping people who have been victimized. They treated my case with urgency and care, and I truly felt like they were fighting for me. If you’ve been the victim of a crypto scam, I can’t recommend RAPID DIGITAL RECOVERY enough. They turned my worst financial moment into a story of complete recovery and renewed trust... Reach Out To Them Via: Email Info: rapiddigitalrecovery(@)execs. com
WhatSapp: +1 4 14 80 71 4 85
Telegram Info: @Rapiddigitalrecovery12 -
HOW TO SUCCESSFULLY RECOVER SCAMMED BTC AND ETH WITH THE HELP OF SALVAGE ASSET RECOVERY
A clip titled “Joe Rogan Reveals Secret Ethereum Fork” autopay on YouTube, featuring Rogan’s unmistakable voice praising a supposed “ETH 2.0 upgrade” that promised early investors up to 10x returns. Everything about the video seemed authentic, Rogan's casual tone, the familiar podcast studio, and even commentary from a so-called “blockchain expert.” Skeptical but curious, I clicked the link in the video’s description, which led to a sleek, professional-looking website promoting a limited-time ETH fork token presale. The sense of urgency was palpable. The site displayed endorsements from prominent crypto influencers I already followed, blockchain analytics claiming legitimacy, and a countdown timer steadily ticking toward zero. My fear of missing out overrode my usual caution. Convinced I was getting in on something exclusive, I transferred 50 ETH worth nearly $150,000 at the time to the provided wallet address. In return, I received newly minted “ETH2” tokens. For the next 48 hours, I celebrated what I believed was a smart, early-access investment. Then it all unraveled. The ETH2 tokens suddenly plummeted to zero value. The website vanished without a trace. Soon after, the YouTube video was flagged and removed; it had been a deepfake. Panic set in. I immediately reached out to SALVAGE ASSET RECOVERY, a cryptocurrency forensics firm I’d seen mentioned in security forums. Within hours, their team began tracing the scam. They explained the mechanics: the scammers used a “rug pull” strategy. A convincing deepfake drew in victims, fake tokens were issued, and the moment investments peaked, the thieves drained all liquidity. Using on-chain analysis, SALVAGE ASSET RECOVERY identified the scammers’ wallet addresses and tracked the flow of my ETH through various exchanges. They worked quickly with centralized platforms to freeze the stolen assets, leveraging anti-money laundering protocols. They also filed emergency legal requests, backed by blockchain evidence, to prove the funds were mine. After three tense weeks, they recovered 47.5 ETH, a 95% success rate. The remaining 2.5 ETH had been funneled to anonymous wallets and was unrecoverable. This taught me hard lessons. Deep Fakes are terrifyingly convincing. Urgency is a red flag. And in crypto, acting quickly after a scam is crucial. Now, I double-check everything and I share my story to protect others. Crypto is powerful, but so are its predators. If scammed, don’t give up. With experts like SALVAGE ASSET RECOVERY, recovery is possible.
CONTACT INFO--
TELEGRAM---@Salvageasset
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 62 -
There's no official integration (package) for JWT in Java Spring?
I am new to Java Spring and want to create a simple RESTful server with JWT auth. Checked many tutorials, all of them involved creating your own JWT middleware to retrieve JWT token from incoming request and validate it using some 3rd party JWT library like jwtk/jjwt.
I am surprised this is not as simple as including a Spring JWT package and it would work out of box. I used to write a similar site using Python/Django, and for that adding JWT support is quite simple as adding "xxx.middleware.JWTAuthMiddleware".1 -
BITCOIN / USDT AND ETH HACKER FOR HIRE: CONSULT FUNDS RECLAIMER COMPANY
My friend introduced me to the intriguing world of cryptocurrency, and I was immediately captivated by its potential for substantial returns. When I stumbled upon a token presale that appeared legitimate, I was eager to invest. I committed $84,600, enticed by the polished website and the seemingly credible team behind the project. However, my initial excitement swiftly morphed into despair when, after the launch, the website vanished, the team disappeared, and all communication channels were severed. I realized I had fallen victim to a sophisticated scam, and my investment felt irretrievably lost. Looking for help, I
discovered FUNDS RECLAIMER COMPANY through a fellow investor who had successfully reclaimed their funds. I reached out to them, and from our very first interaction, I felt a renewed sense of hope. Their team of experts promptly commenced tracing the flow of Ethereum that I had invested. They employed advanced blockchain analysis techniques to meticulously track my funds, which was both impressive and reassuring. FUNDS RECLAIMER COMPANY diligently analyzed the transaction history, identifying the wallets that had received my funds post-presale. They crafted a comprehensive report detailing the movement of my investment, which proved crucial for any potential recovery efforts. Their unwavering dedication and expertise were evident throughout the process, and I felt supported at every juncture. What truly distinguished FUNDS RECLAIMER COMPANY was their commitment to collaboration. They worked closely with law enforcement and cryptocurrency exchanges to freeze the assets in the identified wallets. Thanks to their thorough documentation and compelling evidence, they successfully demonstrated that the funds were obtained through fraudulent means. I am elated to share that FUNDS RECLAIMER COMPANY facilitated the recovery of my lost funds. I regained my entire $84,600 investment, which I had feared was gone forever. This experience has imparted valuable lessons about the importance of vigilance in the cryptocurrency space, but it has also illuminated the possibility of recovery, even after falling prey to a scam. I wholeheartedly recommend FUNDS RECLAIMER COMPANY to anyone who has been ensnared by a cryptocurrency scam. Their expertise, professionalism, and unwavering support made an indelible difference in my journey from loss to recovery. Thank you, FUNDS RECLAIMER COMPANY, for restoring my faith and my investment.
MORE INFO:
Telegram: + 1 (8 1 8) 4 7 4 - 1 7 3 12 -
BITCOIN / USDT AND ETH HACKER FOR HIRE: CONSULT FUNDS RECLAIMER COMPANY
My friend introduced me to the intriguing world of cryptocurrency, and I was immediately captivated by its potential for substantial returns. When I stumbled upon a token presale that appeared legitimate, I was eager to invest. I committed $84,600, enticed by the polished website and the seemingly credible team behind the project. However, my initial excitement swiftly morphed into despair when, after the launch, the website vanished, the team disappeared, and all communication channels were severed. I realized I had fallen victim to a sophisticated scam, and my investment felt irretrievably lost. Looking for help, I discovered FUNDS RECLAIMER COMPANY through a fellow investor who had successfully reclaimed their funds. I reached out to them, and from our very first interaction, I felt a renewed sense of hope. Their team of experts promptly commenced tracing the flow of Ethereum that I had invested. They employed advanced blockchain analysis techniques to meticulously track my funds, which was both impressive and reassuring. FUNDS RECLAIMER COMPANY diligently analyzed the transaction history, identifying the wallets that had received my funds post-presale. They crafted a comprehensive report detailing the movement of my investment, which proved crucial for any potential recovery efforts. Their unwavering dedication and expertise were evident throughout the process, and I felt supported at every juncture. What truly distinguished FUNDS RECLAIMER COMPANY was their commitment to collaboration. They worked closely with law enforcement and cryptocurrency exchanges to freeze the assets in the identified wallets. Thanks to their thorough documentation and compelling evidence, they successfully demonstrated that the funds were obtained through fraudulent means. I am elated to share that FUNDS RECLAIMER COMPANY facilitated the recovery of my lost funds. I regained my entire $84,600 investment, which I had feared was gone forever. This experience has imparted valuable lessons about the importance of vigilance in the cryptocurrency space, but it has also illuminated the possibility of recovery, even after falling prey to a scam. I wholeheartedly recommend FUNDS RECLAIMER COMPANY to anyone who has been ensnared by a cryptocurrency scam. Their expertise, professionalism, and unwavering support made an indelible difference in my journey from loss to recovery. Thank you, FUNDS RECLAIMER COMPANY, for restoring my faith and my investment.
MORE INFO:
Telegram: + 1 (8 1 8) 4 7 4 - 1 7 3 15 -
hey, so i have recently started learning about node js and express based backend development.
can you suggest some good github repositories that showcase real life backend systems which i can use as inspiration to learn about the tech?
like for eg, i want to create a general case solution for authentication and profile management : a piece of db+api end points + models to :
- authenticate user : login/signup , session expire, o auth 2 based login/signup, multi account login, role based access, forgot password , reset password, otp login , etc
- authorise user : jwt token authentication, ip whitelisting, ssl pinning , cors, certificate based authentication , etc (
- manage user : update user profile, delete user, map services , subscriptions and transactions to user , dynamic meta properties ( which can be added/removed for a single user and not exactly part of main user profile) , etc
followed by deployment and the assoc concepts involved : deployment, clusters, load balancers, sharding ,... etc
----
these are all the buzzwords that i have heard that goes into consideration when designing a secure authentication system for a particular large scale website like linkedin or youtube. am not even sure how many of these concepts would require actual codelines and how many would require something else.
so wanted inspiration from open source content to learn about it in depth, replicate and create new better stuff if possible .
apart from that, other backend architectures like video/images storage system, or just some server for movie, social media, blog website etc would also help.2 -
Actually, it can’t really be called a design asset, what’s updated inside are some niche graphical/image materials. I have a feeling that there will be people who like it as much as I do 😂
This is my first attempt at creating something small and I’m afraid of being overly self-indulgent. If you happen to like it too, that would be great, or any feedback and suggestions would be immensely appreciated! 🌟
As a token of my gratitude, I’m offering a lifetime discount code which will give you automatic discounts on your purchases. It’s available for one week only,🚀 please help spread the word~
You can find the link on my personal homepage.
I don't want to be treated as a marketing post 😂1 -
Lets say i have to send an email to the user when:
- user forgot password (email sent with a token to verify the user owns that email, and token identifies for which user is this link valid)
- email verification (email sent with a token to verify the user who just registered, where this token uniquely is generated for each newly registered user)
- etc
Notice how both of these cases include the same shit:
- sending emails
- generating unique tokens
- attaching each record to individual user
Does this mean i should pack this up in 1 single model in the database and differentiate which type of email it is over an enum (EMAIL_CONFIRM, FORGOT_PASSWORD etc)?
Or should these shits each have a different model and thus different tables in database?35 -
It's heartbreaking waking up to see all your coins and token leave your wallet without your approval. Yes! you guessed right! that was what happened to me a couple weeks back, thanks to a fellow who directed me to the best crypto recovery experts, it was this team that I worked with in getting about 89% of my tokens and coins back to my Trust wallet which was formerly hacked by who I don't even know. For anyone looking to reach this team, it's through the team's through email on:- FASTLINERECOVERYSERVICE @ GMAIL . COM. I hope someone finds this information useful and get their crypto currencies recovered too.
Thanks1 -
I am a businessman living in the diaspora, and my desire for affection and care mirrored that of anyone else. My search for love commenced with me signing up for an online dating app, where I encountered an Asian woman. Following a period of communication, she introduced me to what she described as a popular investment platform in Asia, I trusted her so much that I failed to carry out an investigation. According to her, substantial profits were being earned there, and her presentation was so compelling that it piqued my curiosity. Unbeknownst to me, I was being catfished. She provided evidence of her earnings and even sent me a watch as a token of her affection. Consequently, she gained my trust and affection, which marked the beginning of my financial losses in Bitcoin. I had complete faith in her and invested over a million US dollars. Upon recognizing the extent of my investment in this fraudulent scheme, I attempted to withdraw my profits from the investment program, as I had utilized my business capital. My requests were disregarded, and they continually requested additional funds. Frustration mounted, and my supposed partner became hostile after I ceased sending money. Seeking assistance, I discovered RUDER CYBER TECH SLEUTHS. They assessed my circumstances and confirmed my worst fear: I had become a victim of a pig-butchering romance scam. I was disheartened, as I genuinely believed I had found love again following a difficult divorce. Fortunately, RUDER CYBER TECH SLEUTHS specializes in recovering Bitcoin sent to fraudulent or scam wallets. After collaborating with RUDER CYBER TECH SLEUTHS, they successfully recovered my scammed Bitcoin. They are my permanent solution for cybersecurity. I strongly endorse RUDER CYBER TECH SLEUTHS for crypto tracing and recovery. If you find yourself in a similar situation or involved in a suspicious investment platform, contact RUDER CYBER TECH SLEUTHS through
whatsapp: +12132801476
Telegram : @rudercybersleuths3 -
RECOVER YOUR STOLEN BTC/USDT WITH THE HELP OF SOLACE CYBER WORKSTATIONS
When I first encountered a fitness-focused crypto token supposedly endorsed by NFL quarterback Jake Thompson, I was filled with excitement and optimism. As a long-time fan of Thompson's remarkable performances on the field, his endorsement would lend credibility to the project. Eager to seize what I thought was a golden opportunity, I invested $12,000, convinced that this token would yield significant returns. My enthusiasm quickly turned to despair. Just days after my investment, Thompson deleted all his posts related to the token, leading to a catastrophic collapse in its value. To my utter disbelief, I later learned that the account promoting the token was a fraudulent impersonation of someone who had been posing as Thompson to mislead investors like me. This shocking revelation made it clear that the endorsement was nothing more than a ploy by a scam artist, raising serious ethical concerns about the integrity of celebrity endorsements in the cryptocurrency realm. Desperate to recover my losses, I sought assistance from Solace Cyber Workstations, a firm renowned for its expertise in tracing and recovering funds from fraudulent schemes. Solace Cyber Workstations conducted a thorough investigation and uncovered a disturbing connection between the token's development team for orchestrating celebrity scams. This agency had a long history of leveraging high-profile endorsements, including impersonations, to ensnare unsuspecting investors in dubious ventures. With the support of Solace Cyber Workstations, I felt a renewed sense of hope. They took decisive action, threatening to expose the agency's clients to compel them to take responsibility. Thanks to Solace Cyber Workstations' strategic approach, I was able to recover an impressive 90% of my investment, totaling $10,800. While I still faced a loss, it was a tremendous relief to see such a significant portion of my money returned, all thanks to Solace Cyber Workstations' diligent efforts. This has served as a harsh lesson about the inherent risks of investing in celebrity-endorsed cryptocurrencies, particularly when impersonation is involved. I now recognize the critical importance of conducting thorough research and exercising caution before committing my funds to any project, especially those backed by famous figures. I hope my story serves as a warning to others to remain vigilant in the ever-evolving landscape of digital assets, and I cannot stress enough how instrumental Solace Cyber Workstations was in helping me navigate this challenging situation. Don't be left out, reach out to them now
Website: h t t p s : / / s o l a c e c y b e r w o r k s t a t i o n s . c o m
Email: S o l a c e . c y b e r . w o r k s t a t i o n s @ m a i l . c o m
WhatsApp: + 1 2 4 0 7 4 3 7 6 8 91





