Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "extract"
-
How I've decided to answer the "can you hack" question from here on in...
"Can you show me how to hack this account please?"
"Sure, you'll need a hammer, a blow torch, chloroform, some pliers and couple of bottles of really pure vodka!"
"What the hell?!"
"Oh, it's so much quicker to just extract a password from a person, than it is to break into a system, I'm not exactly trained in inflicting pain on the human body, but I'm sure you'll be able to figure it out through trial and error, good luck!"15 -
Fucking awesome. The 'encryption backdoor law' in Australia went through!
Now, whenever served with such warrants, companies which are active in Australia will have to pay hefty fines if they don't give encrypted messages to law enforcement in readable form. No matter whether this means just decrypting it with the keys they have or pushing backdoors/inject code into the messaging apps/services in order to extract the contents.
Now let's see how much the big companies really care about their users! (I'd expect them to pull out of Australia but the chance that this'll happen is as tiny as about nothing)34 -
Frack he did it again.
In a meeting with the department mgr and going over a request feature *we already discussed ad nauseam* that wasn’t technically feasible (do-able, just not worth the effort)
DeptMgr: “I want to see the contents of web site A embedded in web site B”
Me: “I researched that and it’s not possible. I added links to the target APM dashboard instead.”
Dev: “Yes, it’s possible. Just use an IFrame.”
DeptMgr: “I thought so. Next sprint item …what’s wrong?…you look frustrated”
Me: “Um..no…well, I said it’s not possible. I tried it and it doesn’t work”
Dev: “It’s just an IFrame. They are made to display content from another site.”
Me: “Well, yes, from a standard HTML tag, but what you are seeing is rendered HTML from the content manager’s XML. It implemented its own IFrame under the hood. We already talked about it, remember?”
Dev: “Oh, that’s right.”
DeptMgr: “So it’s possible?”
Dev: “Yea, we’ll figure it out.”
Me: “No…wait…figure what out? It doesn’t work.”
Dev: “We can use a powershell script to extract the data from A and port it to B.”
DeptMgr: “Powershell, good…Next sprint item…”
Me: “Powershell what? We discussed not using powershell, remember?”
Dev: “It’s just a script. Not a big deal.”
DeptMgr: “Powershell sounds like a right solution. Can we move on? Next sprint item….are you OK? You look upset”
Me: “No, I don’t particularly care, we already discussed executing a powershell script that would have to cross two network DMZs. Bill from networking already raised his concern about opening another port and didn’t understand why we couldn’t click a link. Then Mike from infrastructure griped about another random powershell script running on his servers just for reporting. He too raised his concern about all this work to save one person one click. Am I the only one who remembers this meeting? I mean, I don’t care, I’ll do whatever you want, but we’ll have to open up the same conversations with Networking again.”
Dev: “That meeting was a long time ago, they might be OK with running powershell scripts”
Me: “A long time ago? It was only two weeks.”
Dev: “Oh yea. Anyway, lets update the board. You’ll implement the powershell script and I’ll …”
Me: “Whoa..no…I’m not implementing anything. We haven’t discussed what this mysterious powershell script is supposed to do and we have to get Mike and Bill involved. Their whole team is involved in the migration project right now, so we won’t see them come out into the daylight until next week.”
DevMgr: “What if you talk to Eric? He knows powershell. OK…next sprint item..”
Me: “Eric is the one who organized the meeting two weeks ago, remember? He didn’t want powershell scripts hitting his APM servers. Am I the only one who remembers any of this?”
Dev: “I’m pretty good with powershell, I’ll figure it out.”
DevMgr: “Good…now can we move on?”
GAAAHH! I WANT A FLAMETHROWER!!!
Ok…feel better, thanks DevRant.11 -
Oh, man, I just realized I haven't ranted one of my best stories on here!
So, here goes!
A few years back the company I work for was contacted by an older client regarding a new project.
The guy was now pitching to build the website for the Parliament of another country (not gonna name it, NDAs and stuff), and was planning on outsourcing the development, as he had no team and he was only aiming on taking care of the client service/project management side of the project.
Out of principle (and also to preserve our mental integrity), we have purposely avoided working with government bodies of any kind, in any country, but he was a friend of our CEO and pleaded until we singed on board.
Now, the project itself was way bigger than we expected, as the wanted more of an internal CRM, centralized document archive, event management, internal planning, multiple interfaced, role based access restricted monster of an administration interface, complete with regular user website, also packed with all kind of features, dashboards and so on.
Long story short, a lot bigger than what we were expecting based on the initial brief.
The development period was hell. New features were coming in on a weekly basis. Already implemented functionality was constantly being changed or redefined. No requests we ever made about clarifications and/or materials or information were ever answered on time.
They also somehow bullied the guy that brought us the project into also including the data migration from the old website into the new one we were building and we somehow ended up having to extract meaningful, formatted, sanitized content parsing static HTML files and connecting them to download-able files (almost every page in the old website had files available to download) we needed to also include in a sane way.
Now, don't think the files were simple URL paths we can trace to a folder/file path, oh no!!! The links were some form of hash combination that had to be exploded and tested against some king of database relationship tables that only had hashed indexes relating to other tables, that also only had hashed indexes relating to some other tables that kept a database of the website pages HTML file naming. So what we had to do is identify the files based on a combination of hashed indexes and re-hashed HTML file names that in the end would give us a filename for a real file that we had to then search for inside a list of over 20 folders not related to one another.
So we did this. Created a script that processed the hell out of over 10000 HTML files, database entries and files and re-indexed and re-named all this shit into a meaningful database of sane data and well organized files.
So, with this we were nearing the finish line for the project, which by now exceeded the estimated time by over to times.
We test everything, retest it all again for good measure, pack everything up for deployment, simulate on a staging environment, give the final client access to the staging version, get them to accept that all requirements are met, finish writing the documentation for the codebase, write detailed deployment procedure, include some automation and testing tools also for good measure, recommend production setup, hardware specs, software versions, server side optimization like caching, load balancing and all that we could think would ever be useful, all with more documentation and instructions.
As the project was built on PHP/MySQL (as requested), we recommended a Linux environment for production. Oh, I forgot to tell you that over the development period they kept asking us to also include steps for Windows procedures along with our regular documentation. Was a bit strange, but we added it in there just so we can finish and close the damn project.
So, we send them all the above and go get drunk as fuck in celebration of getting rid of them once and for all...
Next day: hung over, I get to the office, open my laptop and see on new email. I only had the one new mail, so I open it to see what it's about.
Lo and behold! The fuckers over in the other country that called themselves "IT guys", and were the ones making all the changes and additions to our requirements, were not capable enough to follow step by step instructions in order to deploy the project on their servers!!!
[Continues in the comments]25 -
"We need you to build a feature on our website to stop people taking screenshots. I can use the print screen key and then easily print out our website design. You need to make the site design harder to copy".
This is an extract from a recent client email I received. To say I'm in shock is an understatement. 26
26 -
Replace the teachers with no real world experience with part-time workers that are still active in IT.
I had this last year in my final year of vocational education and it was amazing, I had two teachers running their business two days a week and teaching us everything on the three remaining days.
I learnt about oop without dogs and cats, I learnt to extract information from invoices to be able to create an invoicing system without being misled by customers, and much more.
Second thing would also be something we did in my previous education. It was called "learning productively".
Basically, companies would give a project to the school and students could pick one to do for a few months. You had to have meetings with the customer, you had to give presentations and it wasn't another fucking calculator.
I've had the pleasure of working with a big corporation like this and learnt a ton in my first year.
These were extremely valuable, I think I'd still be a piece of shit developer without any knowledge on how to actually develop a full system and how to manage a project as a dev.
Peace6 -
My job requires us to use Mac. I've spent the week figuring how to get stuff done on it.
My best description of trying to code on mac is that it's kinda like having to extract your mangled penis from a blender before you bleed to death... Except you can't look directly at it, you have to wear a VR headset that's linked to a camera in the corner of the room.
And you can't use your hands directly you have to use an incredibly stylish and ergonomic looking steering wheel to control a robotic arm. The robotic arm has its own artificial intelligence and it desperately wants to help.
Unfortunately it doesn't understand anything about what you're trying to do and it keeps leaping to incorrect conclusions about what you want from it.
Everyone tells you it'll get better, but you're still in intense pain and your penis is still stuck in the blender.28 -
Sad story about refactoring.
Programmer: I cleaned up the codes, extract reusable methods, reduced repetitive code and improve overall readability and maintainability.
Manager: why the page still display the same.
Programmer: ...7 -
Last year I got an Acer notebook from a guy that stated that "it isn't working". "Okay" I thought, let's boot it up.
> Screen turns on, no splash screen, no hard drive activity
> Well fuck
> Tries to enter BIOS, nothing
> Openes case to reset CMOS
> Nothing
> Okay I think I need to flash a new BIOS
> Acer support site
> "Download the exe to flash the BIOS"
> What
> Spend two hours researching
> Find out that you can flash via USB and by pressing a key combination
> Extract the BIOS binary from the exe file
> Flash it on the notebook
> Splash screen and working BIOS
> Yay!!!
> No bootable devices found
> Fuck
> Connects hdd with test bench
> Completely fucking dead
> WTF
> Order a new hard drive
> 3 days later
> Install hdd
> Install Windows
> Finally working
WTF did you do to this notebook to not only mechanically break your hdd but also fuck up the BIOS completely??!!13 -
this.title = "gg Microsoft"
this.metadata = {
rant: true,
long: true,
super_long: true,
has_summary: true
}
// Also:
let microsoft = "dead" // please?
tl;dr: Windows' MAX_PATH is the devil, and it basically does not allow you to copy files with paths that exceed this length. No matter what. Even with official fixes and workarounds.
Long story:
So, I haven't had actual gainful employ in quite awhile. I've been earning just enough to get behind on bills and go without all but basic groceries. Because of this, our electronics have been ... in need of upgrading for quite awhile. In particular, we've needed new drives. (We've been down a server for two years now because its drive died!)
Anyway, I originally bought my external drive just for backup, but due to the above, I eventually began using it for everyday things. including Steam. over USB. Terrible, right? So, I decided to mount it as an internal drive to lower the read/write times. Finding SATA cables was difficult, the motherboard's SATA plugs are in a terrible spot, and my tiny case (and 2yo) made everything soo much worse. It was a miserable experience, but I finally got it installed.
However! It turns out the Seagate external drives use some custom drive header, or custom driver to access the drive, so Windows couldn't read the bare drive. ffs. So, I took it out again (joy) and put it back in the enclosure, and began copying the files off.
The drive I'm copying it to is smaller, so I enabled compression to allow storing a bit more of the data, and excluded a couple of directories so I could copy those elsewhere. I (barely) managed to fit everything with some pretty tight shuffling.
but. that external drive is connected via USB, remember? and for some reason, even over USB3, I was only getting ~20mb/s transfer rate, so the process took 20some hours! In the interim, I worked on some projects, watched netflix, etc., then locked my computer, and went to bed. (I also made sure to turn my monitors and keyboard light off so it wouldn't be enticing to my 2yo.) Cue dramatic music ~
Come morning, I go to check on the progress... and find that the computer is off! What the hell! I turn it on and check the logs... and found that it lost power around 9:16am. aslkjdfhaslkjashdasfjhasd. My 2yo had apparently been playing with the power strip and its enticing glowing red on/off switch. So. It didn't finish copying.
aslkjdfhaslkjashdasfjhasd x2
Anyway, finding the missing files was easy, but what about any that didn't finish? Filesizes don't match, so writing a script to check doesn't work. and using a visual utility like windirstat won't work either because of the excluded folders. Friggin' hell.
Also -- and rather the point of this rant:
It turns out that some of the files (70 in total, as I eventually found out) have paths exceeding Windows' MAX_PATH length (260 chars). So I couldn't copy those.
After some research, I learned that there's a Microsoft hotfix that patches this specific issue! for my specific version! woo! It's like. totally perfect. So, I installed that, restarted as per its wishes... tried again (via both drag and `copy`)... and Lo! It did not work.
After installing the hotfix. to fix this specific issue. on my specific os. the issue remained. gg Microsoft?
Further research.
I then learned (well, learned more about) the unicode path prefix `\\?\`, which bypasses Windows kernel's path parsing, and passes the path directly to ntfslib, thereby indirectly allowing ~32k path lengths. I tried this with the native `copy` command; no luck. I tried this with `robocopy` and cygwin's `cp`; they likewise failed. I tried it with cygwin's `rsync`, but it sees `\\?\` as denoting a remote path, and therefore fails.
However, `dir \\?\C:\` works just fine?
So, apparently, Microsoft's own workaround for long pathnames doesn't work with its own utilities. unless the paths are shorter than MAX_PATH? gg Microsoft.
At this point, I was sorely tempted to write my own copy utility that calls the internal Windows APIs that support unicode paths. but as I lack a C compiler, and haven't coded in C in like 15 years, I figured I'd try a few last desperate ideas first.
For the hell of it, I tried making an archive of the offending files with winRAR. Unsurprisingly, it failed to access the files.
... and for completeness's sake -- mostly to say I tried it -- I did the same with 7zip. I took one of the offending files and made a 7z archive of it in the destination folder -- and, much to my surprise, it worked perfectly! I could even extract the file! Hell, I could even work with paths >340 characters!
So... I'm going through all of the 70 missing files and copying them. with 7zip. because it's the only bloody thing that works. ffs
Third-party utilities work better than Microsoft's official fixes. gg.
...
On a related note, I totally feel like that person from http://xkcd.com/763 right now ;;21 -
IT Manager: What kind if attachment did you send me in that email?
Me: A .zip?
IT Manager: ...?
Me: A zip file? Zipped Folder?
IT Manger: ...?
Me: Umm... the data file you needed has to be sent in a zip folder because 6 different file types combine to make it? Just download the .zip and extract?
IT Manager: I don't know how to extract the files?
Me: ...13 -
Never in my life I was scared as today.
I recently left a big company to work for a small one as the first internal developer.
Had a small issue in the production server. The fix was easy, just remove a single table entry. And... *drum roll*... I forgot to add a where clause. All orders were lost.
No idea if we had backups or anything, I quickly called the one other IT dude in the company.
He had no clue where are the backups and how to find them.
Having some experience with Nmap, I quickly scanned our network and found a Nas device.
There was a backup, whole VHD backup. 300GB of it, the download speed is around 512kb/s. No way I can fix it before management finds out, but then an idea came to mind. Old glorious 7zip. Managed to extract only the database files, sent them to the server and quickly swapped them. Everything was fine... The manager connected 5 minutes later. Scariest 45 minutes of my life...20 -
===rant
So I have been freelancing as web developer for 5 years. I was also playing basketball professionally so I was only working part-time, building websites here and there, small android apps to learn the job and I was also reading a lot to challenge my brain.
When I stopped playing basketball about a year ago, I thought I would really enjoy coding full time so I pursued a job.
With no formal education and just a basketball background on paper, in the collapsed Greek economy, as you may assume chances of landing a job are minimal.
After about 40 resumes sent I only got an internship. It was a 4 month, part-time, no pay deal, and then the company would decide if they would like to hire me later.
The company had 4 employees and they are one of the largest software distribution businesses in my area. They resell SaaS bought from a third company, bundled with installation support, initial configuration, hardware support, whatever a client may need.
I was the only one with any ability to code whatsoever. The other people were working mostly on customer support with the occasional hardware repair.
After the 4 month period they owner (small company, owner was also manager and other roles) told me that they are very happy with my work and would like to keep me part-time with minimum pay.
Just to give you and idea if the amounts of money involved, in Greece, after taxes, my salary was 240euros per month. And the average cost of surviving (rent, cheapest food possible, no expenses on anything but super basics) is about 600euros.
I told him I needed more to live and he told me ok, we will reevaluate a few months later, at the end of May 2017.
I just accepted it without having many options. The company after all was charging clients 30euros per hour for my projects so I kept thinking that if I worked a lot and delivered consistently I would get a full time job and decent money.
And I delivered. In the following months I made a Magento extension, some WordPress themes, a C# application to extract data from the client's ERP and import it to a third application, a click to call application to use Asterisk to originate calls from the client's ERP, a web application to manage a restaurant's menu and many more small projects. Whatever they asked, I delivered.
On time, version controlled, heavily documented solutions (my C# ones are not exactly masterpieces but it was my first time with the language and windows).
So when May ended I was pretty excited to hear they wanted to keep me full time. I worked hard for it, I was serious, professional, I tried a lot to learn things so I can deliver, and the company recognized that. YAY.
So the time comes to talk money. The offer was 480euros per month. Double my part-time pay, minimum wage. I asked for about 700. Manager said it's hard but I will see what I can do. So we agreed to keep the deal for June while they are working on a better offer.
During the first half of June I finished my last project, put all my work on a nice folder with a nice readme on every project's directory, with their version control and everything.
The offer never improved, so I said no deal, and as of today, I am jobless.
I am stressed as fuck and excited as fuck at the same time.
I will do my best to survive in the shitstorm that is called Greece.
Bring it on.9 -
"Can't we extract the UNIX from Linux and use it as our server operating system?"
fml
Linux isn't even based on UNIX, but this piece of shit of a bitch of client was so freaking stubborn, and wanted a RAR file of UNIX from me7 -
I received an email from marketing manager requested me to extract all the emails from the all the application and compile it into a CSV and make sure that CSV doesn't have duplicate email's. She wants to send newsletter to all those email's which we don't have permission for.
I permanently deleted that email.3 -
He put just a zip in the new branch. I thought it was going to be the actual fucking project like I asked him to. Nope just a damn zip for me to extract and push to github correctly
Fucking hell 11
11 -
On stackoverflow *Peoople be like*
- How can I write a stream into a hole to extract light with magnetic energy -
and I'm trying to make my navigation bar in every screen with Java 😂 1
1 -
Did anybody of you automate job hunting?
Like Webscraping online job offers, extract adress, keywords and put it into a cv template, set up personalised html-email and website.
Extra perk, a neural network which composes the cover letter.
that i would need.9 -
My dream was shattered!!
I joined a new company. I graduated last 2 months before and joined as data analyst.
So I was dreaming to work on some awesome research projects and all, but it was just another dream...people here don't work on any sort of data analytics instead the data science team uses regex and all to extract things and say they are building models.
Ahh...wtf!!!
Many co-workers are good and help me, but the boss. He left all the annoying works to me and the release is in next month...
"BRUH I JUST JOINED YOUR COMPANY!!!"
Then after some days he gave me more task, when he found that one task was super easy(i mean it was just to extract things using bs4 and selenium, hardly will take an hour) to do then he took that himself and in the next meeting said he did that work and it was super difficult!!!
Data science here to senior members is just for loop!! I dont even know why I joined this firm
Ahhh!!! I want to scream!!! 11
11 -
*wants to download some YouTube videos in youtube-dl*
$ youtube-dl --a-bunch-of-options
> Can't download this, sorry.
*realizes that Ubuntu probably has an outdated version like usual*
# apt remove youtube-dl
*Realizes that this steaming pile of shit pulled in some icons and Wayland on a headless server*
# apt autoremove
> 300-something MB cleared
For a command-line tool...
# pip install youtube-dl
# apt install ffmpeg
$ youtube-dl --audio-format mp3 -o "%(title)s.%(ext)s" https://youtube.com/playlist/...
> Sorry mate, a video was removed from this playlist! Let me go ahead and shit the bed on this issue that's been reported several times since 6 years ago.
*finds an issue on GitHub reporting this, add -i option to continue on error*
$ youtube-dl --audio-format mp3 -o "%(title)s.%(ext)s" https://youtube.com/playlist/... -i
> There you go, your .webm files as requested!
But.. I requested .mp3 output? --audio-format mp3, don't you see?
> Oh no you need to add in another option to tell me to actually do that first. --extract-audio, you see?
But why.. why do you need to be told that twice? Oh ffs, fuck it.
Reminds me of robocopy. That shit required me to tell it 25 times what to do and it'd still not do it right as well. And you know what, compared to rsync where -avz works 99% of the time, I hate it.7 -
!rant
A rather long(it's 8 hrs long to be precise) story
So I just finished an amazing homework assignment. The goal was to open a new shell on Linux using a C program. We were asked to follow instructions from http://phrack.org/issues/49/14.html . However the instructions given were for 32 bit processors and we had to do same for 64 bit machines. In a nutshell we had to write a 64 bit shell code and use buffer-overflow technique to change the return address if the function to our shell code.
I was able to write my own shellcode within 1hr and was able to confirm that it's working by compiling with nasm and all. Also the "show-off-dev" inside me told me to execute "/bin/bash" instead of "/bin/sh"(which everyone else was going to do). After my assembly code was properly executing shellcode, I was excited to put it in my C code.
For that, I needed opcodes of assembly code in a string. Following again the "show-off-dev" inside me, I wrote a shell script which would extract the exact opcodes out of objdump output. After this I put it in my C code, call my friend and tell him that "hell yeah bro, I did it. Pretty sure sir is gonna give me full marks etc etc etc". I compiled the code and BOOM, IT SEGFAULTS RIGHT IN FRONT OF MY FRIEND. Worst, friend had copied a "/bin/sh" code from shellstorm and already had it working.
Really burned my ego, I sat continuously for 8 hrs in front of my laptop and didn't talk to anyone. I was continuously debugging the code for 8 hrs. Just a few minutes ago, I noticed that the shellcode which I'm actually putting in my C code is actually 2 bytes shorter than actual code length. WHAT THE F. I ran objdump manually and copied the opcodes one by one into the string (like a noob) and VOILA ! IT WORKED !!!
TURNS OUT I DIDN'T CUT THE LAST COLUMN OF OPCODES IN MY SHELL SCRIPT. I FIXED THAT AND IT WORKED !!
THE SINGLE SHITTY NUMBER MADE ME STRUGGLE 8 HRS OF MY LIFE !! SMH
Lessons learnt :
1)Never have such an ego that makes you think you're perfect, cuz you're retarded not perfect
2)Examine your scripts properly before using them
3)Never, I repeat NEVER!! brag about your code before compiling and testing it.
That's it!
If you've read this long story, you might as well press the "++" button.6 -
What you see in that screenshot, that was earned.
I'm on the plane and I want an hour of free Gogo (read: crappy) WiFi on my laptop (so I can push the code I'm probably the most proud of, more on that another time). The problem is that the free T-Mobile WiFi is apparently only available on mobile.
So after trying to just use responsive mode, and that still (almost obviously) not working. I realize it's time to bring in the big guns: A User Agent switcher. Small catch: I don't have an add-on for FF that can do that.
So on my phone I find an add-on that can and download the file. To send it to my computer, I initially thought to go through KDEConnect, but Gogo's network also isolates each system, so that doesn't work. So I try to send it over Bluetooth, except I can't. Why? Because Android's Bluetooth share "doesn't support" the .xpi extension, so I dump it in a zip (in retrospect, I should have just renamed it), and now I can share.
After a few tries, I successfully get the file over, extract the zip, and install the extension. Whew! Now I open up Gogo's page and proceed to try again, but this time I change the user-agent. Doesn't work... Ah! Cookies! I delete the cookies for Gogo (I had a cookie editor add-on already), but I had to try a few times because Gogo's scripts keep trying to, but I got it in the end.
Finally that stupid error saying it's for phones only went away, and I could write this rant for you.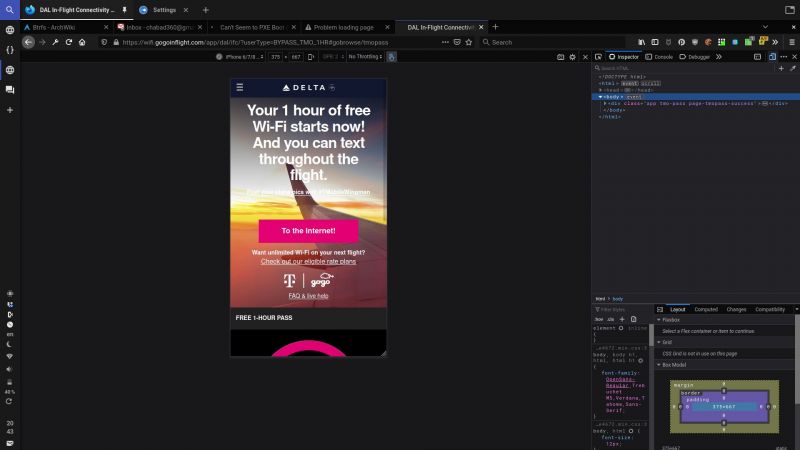 22
22 -
Spent the last 15 minutes trying to extract the relative URL from location.href, until I found out that location.pathname does exactly that 😐1
-
A dev team has been spending the past couple of weeks working on a 'generic rule engine' to validate a marketing process. The “Buy 5, get 10% off” kind of promotions.
The UI has all the great bits, drop-downs, various data lookups, etc etc..
What the dev is storing the database is the actual string representation FieldA=“Buy 5, get 10% off” that is “built” from the UI.
Might be OK, but now they want to apply that string to an actual order. Extract ‘5’, the word ‘Buy’ to apply to the purchase quantity rule, ‘10%’ and the word ‘off’ to subtract from the total.
Dev asked me:
Dev: “How can I use reflection to parse the string and determine what are integers, decimals, and percents?”
Me: “That sounds complicated. Why would you do that?”
Dev: “It’s only a string. Parsing it was easy. First we need to know how to extract numbers and be able to compare them.”
Me: “I’ve seen the data structures, wouldn’t it be easier to serialize the objects to JSON and store the string in the database? When you deserialize, you won’t have to parse or do any kind of reflection. You should try to keep the rule behavior as simple as possible. Developing your own tokenizer that relies on reflection and hoping the UI doesn’t change isn’t going to be reliable.”
Dev: “Tokens!...yea…tokens…that’s what we want. I’ll come up with a tokenizing algorithm that can utilize recursion and reflection to extract all the comparable data structures.”
Me: “Wow…uh…no, don’t do that. The UI already has to map the data, just make it easy on yourself and serialize that object. It’s like one line of code to serialize and deserialize.”
Dev: “I don’t know…sounds like magic. Using tokens seems like the more straightforward O-O approach. Thanks anyway.”
I probably getting too old to keep up with these kids, I have no idea what the frack he was talking about. Not sure if they are too smart or I’m too stupid/lazy. Either way, I keeping my name as far away from that project as possible.4 -
So far all designers I worked with do the following:
1. Use "creativity" to come up with stuff that the system does not allow implementing, for example: Changing clock color in mobile statusbar to Blue!
2. Use "creativity" to come up with a heavily customized calendar for a windows software which requires building the control from scratch, but they explain their creativity by saying: Can't you use CSS?
3. Provide iOS only design which follows android guidelines and refuse to provide android styles for at least pages that to be handled differently on each platform, for example, we had a checkout page in an app, and they wanted the same style for both WITHOUT building custom control for it, they said: Can't you use the android custom control inside iOS
4. They design for a website and send same mockups for me to implement on mobile apps, the problem is a web page runs on a big screen when the mobile app doesn't have room for half the stuff they designed but they must look exactly the same as website !!
5. They send entire PSD with no color codes and say: You can extract icons, and colors from psd ... When they should provide them as per our request which is: SVG for Android and PDF for iOS with the color codes, but no, they are lazy!
6. They ask the team to create a page in the app which is almost production ready just so that they test different font sizes and see how it will look on the phone
7. Same as #6 for images that contain text
The list goes on, but those are by the far the ones that made me one step away from resigning, some of them made me resign...6 -
Me (junior) working on something specific/concrete; actually doing something. Gets stuck and goes to lead with specific question.
me: hey lead, if we have x, does y need to be included as well?
lead: yes, no, maybe, random bla.
me, tries to summarize and extract a to-do: oke... so based on 'yes, no, maybe random bla' you suggest adding y right about here?
lead: maybe bla and we have to think about it, yes, random bla. Try whatever feels right to you.
Me walks back to desk. Decides to support a charity, help refugees and homeless people CAUSE THAT FEELS RIGHT!2 -
"I'm almost done, I'll just need to add tests!"
Booom! You did it, that was a nuke going off in my head.
No, you shouldn't just need to add tests. The tests should have been written from the get go! You most likely won't cover all the cases. You won't know if adding the tests will break your feature, as you had none, as you refactor your untested mess in order to make your code testable.
When reading your mess of a test case and the painful mocking process you went through, I silently cry out into the void: "Why oh why!? All of this suffering could have been avoided!"
Since most of the time, your mocking pain boils down to not understanding what your "unit" in your "unit test" should be.
So let it be said:
- If you want to build a parser for an XML file, then just write a function / class whose *only* purpose is: parse the XML file, return a value object. That's it. Nothing more, nothing less.
- If you want to build a parser for an XML file, it MUST NOT: download a zip, extract that zip, merge all those files to one big file, parse that big file, talk to some other random APIs as a side-effect, and then return a value object.
Because then you suddenly have to mock away a http service and deal with zip files in your test cases.
The http util of your programming language will most likely work. Your unzip library will most likely work. So just assume it working. There are valid use cases where you want to make sure you acutally send a request and get a response, yet I am talking unit test here only.
In the scope of a class, keep the public methods to a reasonable minimum. As for each public method you shall at least create one test case. If you ever have the feeling "I want to test that private method" replace that statement in your head with: "I should extract that functionality to a new class where that method public. I then can create a unit test case a for that." That new service then becomes a dependency in your current service. Problem solved.
Also, mocking away dependencies should a simple process. If your mocking process fills half the screen, your test setup is overly complicated and your class is doing too much.
That's why I currently dig functional programming so much. When you build pure functions without side effects, unit tests are easy to write. Yet you can apply pure functions to OOP as well (to a degree). Embrace immutability.
Sidenote:
It's really not helpful that a lot of developers don't understand the difference between unit, functional acceptance, integration testing. Then they wonder why they can't test something easily, write overly complex test cases, until someone points out to them: No, in the scope of unit tests, we don't need to test our persistance layer. We just assume that it works. We should only test our businsess logic. You know: "Assuming that I get that response from the database, I expect that to happen." You don't need a test db, make a real query against that, in order to test that. (That still is a valid thing to do. Yet not in the scope of unit tests.)rant developer unit test test testing fp oop writing tests get your shit together unit testing unit tests8 -
> IHateForALiving: I have added markdown on the client! Now the sys admin can use markdown and it's going to be rendered as HTML
> Team leader: ok, I've seen you also included some pics of the tests you made. It's nice, there's no XSS vulnerabilities, now I want you to make sure you didn't introduce any SQL injection too. Post the results of the tests in the tickets, for everybody to see.
I've been trying to extract from him for 15 minutes how sending a text through a markdown renderer on the client is supposed to create a SQL injection on the server, I've been trying to extract from him how showing all of this to the world would improve our reputation.
I miserably failed, I don't know how the fuck am I supposed to test this thing and if I a colleague wasted time to make sure some client-side rendering didn't create a SQL injection I'd make sure to point and laugh at them every time they open their mouth.9 -
Watch out for these fucking bug bounty idiots.
Some time back I got an email from one shortly after making a website live. Didn't find anything major and just ran a simple tool that can suggest security improvements simply loading the landing page for the site.
Might be useful for some people but not so much for me.
It's the same kind of security tool you can search for, run it and it mostly just checks things like HTTP headers. A harmless surface test. Was nice, polite and didn't demand anything but linked to their profile where you can give them some rep on a system that gamifies security bug hunting.
It's rendering services without being asked like when someone washes your windscreen while stopped at traffic but no demands and no real harm done. Spammed.
I had another one recently though that was a total disgrace.
"I'm a web security Analyst. My Job is to do penetration testing in websites to make them secure."
"While testing your site I found some critical vulnerabilities (bugs) in your site which need to be mitigated."
"If you have a bug bounty program, kindly let me know where I should report those issues."
"Waiting for response."
It immediately stands out that this person is asking for pay before disclosing vulnerabilities but this ends up being stupid on so many other levels.
The second thing that stands out is that he says he's doing a penetration test. This is illegal in most major countries. Even attempting to penetrate a system without consent is illegal.
In many cases if it's trivial or safe no harm no foul but in this case I take a look at what he's sending and he's really trying to hack the site. Sending all kinds of junk data and sending things to try to inject that if they did get through could cause damage or provide sensitive data such as trying SQL injects to get user data.
It doesn't matter the intent it's breaking criminal law and when there's the potential for damages that's serious.
It cannot be understated how unprofessional this is. Irrespective of intent, being a self proclaimed "whitehat" or "ethical hacker" if they test this on a site and some of the commands they sent my way had worked then that would have been a data breach.
These weren't commands to see if something was possible, they were commands to extract data. If some random person from Pakistan extracts sensitive data then that's a breach that has to be reported and disclosed to users with the potential for fines and other consequences.
The sad thing is looking at the logs he's doing it all manually. Copying and pasting extremely specific snippets into all the input boxes of hacked with nothing to do with the stack in use. He can't get that many hits that way.4 -
I coded a little js plugin to create a calendar from a given year and month.
What do you guys think? Do you like it?
I'm thinking of extract it from the project and make it open sourced :) 10
10 -
User: I need you to extract all the invoice data for us.
Me: What invoice data in particular, what are filters you require. This is a massive database with millions of transactions.
User: JUST EXTRACT THE TABLE!
Me: Right.....(this is a database with 3000+ tables and hundreds of joins)7 -
We needed a design for our Android and iOS App, everything should be done by an award-winning design agency. What we received was only a design for iPhone X. Only mockups as PDF, no icons, nothing. So we requested the Android design and an iPhone 8 one including icons, color codes and whatnot.
1 FUCKING MONTH LATER we got the new designs... They are all the FUCKING SAME DESIGN where some mockups were "displayed" on an android phone, and some on an iPhone. Still no icons though.
3 weeks pass and we geht FUCKING sketch files, to extract the shit ourselves. Thank you for nothing.
It took again nearly 3 month to get a "proper" Android design and all the assets. You could clearly see, that they never did anything for Android but well, we had to work with it. Award-winning design agancy my ass.5 -
during code review...
peer: "you should pass this variable, and extract the logger from it"
me: "why? it is a 3 line logging function. why not pass the logger instance?"
peer: "because that is our best practice. It is the way we do things"
me: "why is it a best practice?"
peer: "because it is. We use it everywhere!"
me: "No we don't. And I still don't understand why is this a best practice. can you explain?"
peer: gives ups, did not look at the mr, and was not going to.
mr stays open. probably forever.11 -
My step mother told me she has an old laptop from which she wanted to extract the email address book. I highly doubt of them (less than 20) are still up to date. Some of them are from dead ISPs 😰
I'm honestly surprised about the immediate respond times and that it still works pretty well. 6
6 -
So our class had this assignment in python where we had to code up a simple web scraper that extracts data of the best seller books on Amazon. My code was ~100 lines long( for a complete newbie in python guess the amount of sweat it took) and was able to handle most error scenarios like random HTML 503 errors and different methods to extract the same piece of data from different id's of divs. The code was decently fast.
All wss fine until I came to know the average number of lines it took for the rest of the class was ~60 lines. None of the others have implemented things that I have implemented like error handling and extracting from different places in the DOM. Now I'm confused if I have complicated my code or have I made it kind of "fail proof".
Thoughts?8 -
Had to implement a search feature for a client so I did and told him to check it out (it was a LIKE SQL statement)
He tested it out by typing in iPhone and Phone (there was an item called iphone in the database) and he was amazed about the fact it worked for some reason.
A real answer from him:
"it's working.. how is it working?
each item is tagged to multiple keywords without the user doing anything"
I said it's just a text search but I guess I should've said I'm using an advanced AI to extract all possible terms related to the item title.1 -
Dear Microsoft Kusto Query Language (KQL)
Screw you. You suck like more than a sudden depressurization event in an airplane. Creating your own freaking query language is bad, the people who invented SQL based it on a the principles of mathematical relational algebra, which although confusing, and not suited for all use cases is at least consistent.
You were invented by a bunch of oxygen deprived halfwits based on the principles of sadism and incompetence.
The only situation in which I would voluntarily use KQL as my tool of choice is if my purpose was to extract a Dantesque style revenge on someone who had committed grievous harm to myself and my family members. In that case forcing them to work with you day in and day out would still border on cruel and unusual punishment.
Sincerely, A developer who has spent the past 2 hours dealing with your Lovecraftian madness.
P.S. I hope you choke on a raw chicken bone and no one gives you CPR.3 -
I was helping my girlfriend's sister on her programming homework yesterday. But the thing is that she missed a lot of classes to be with her boyfriend. So now she has a reasonably advanced task, without knowing the basics.
Her assignment was to open a file, extract it's text, and count how many times an user-given word appeared on it. So here's how it went:
- so you use the input function to ask the user to type the word.
- ok, but where do I type the word?
- in that black screen, on the bottom of visual code
~ changes name of the variable that receives the input()~
-like that?
- no, that is just the variable name. You should type in that black screen AT THE BOTTOM OF VISUAL CODE
- oh, ok.
~ changes name of .py file ~14 -
Our HR guy is a tool. He requested I help him extract some data from our database. Which based on what he requested I supplied he then started trying to bully me because the data I gave him wasn’t what he wanted. Ringing me every 5 mins asking if it was ready, comparing me to another colleague who wrote the system.
When we blew up at him telling him to back off he continued. Anyway he still works here and persists in being a tool. i on the other hand ignore him.
I’m pretty sure that the HR bullying an employee is wrong, not massively worried about it just annoyed5 -
Spent yesterday afternoon trying to extract the logic from a VBA macro written by civil engineers so that we can encode the same logic in the applications we're writing.
Sweet Jesus.
500 lines of meaningless variable names and loops reading values from various spreadsheets into a 3 dimensional array(!).
On top of that, now that I kind of understand what it's doing, I don't think it's ever worked properly.2 -
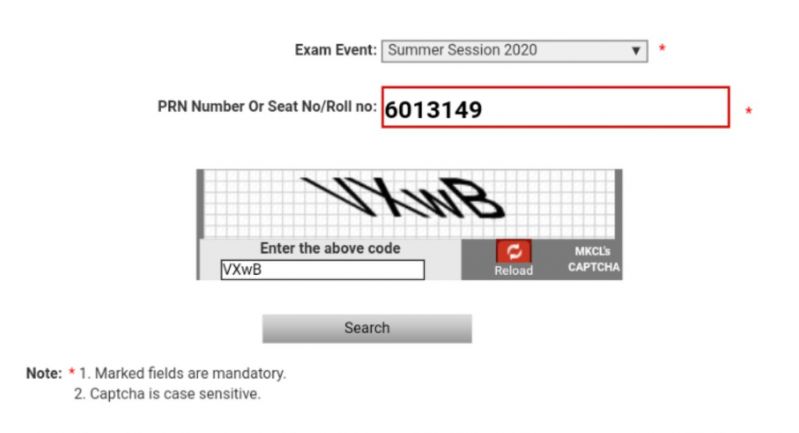
This is the Result Declaration form of our university, It's all good but there is one thing (bug) in this form, you only need to fill the Recaptcha once and you can that same Recaptcha to extract as many results as you want. Though not a Security issue, we can extract results of many students as roll numbers are sequential, we just need a bot to fill roll number and click the button. The only use would be to conduct surveys on results, but, a bug is a bug.
 5
5 -
[CMS Of Doom™]
Imagine bringing every HTTP Query Param and every god damn fucking POST var into to current code context.
"extract()" is one of the reasons why I have terminal PHPTSD. 10
10 -
At this point, I just feel bad for my coworker.
No, I am not frustrated or angry, just feeling terribly bad for her as how difficult life must be for someone so dumb.
We are introducing a new method to track some data in our product, like total number of sign-ups, DAU, etc.
Now the implementation is already WIP and this is known to all.
The dev has documented the approach where he has mapped the screen name, a screenshot, and a snippet of the schema that tracks that particular screen.
I kid you not guys, this coworker somehow landed on that document and started some scientific study to try and extract data.
Yes, she looked at the schema screenshot and spent like few hours trying to decode it to figure out the sign-ups and DAU.
Data via a screenshot in a document. I can't even express it.
And then texts me in panic mode that she isn't able to access the data because the file is . jpeg within a document.
I asked where is she executing the schema, because I thought she is joking initially. She said she doesn't know and asked me where she should execute it.
My mind is numb. Life must be real hard when you are so fucking dumb.18 -
Designer: here's the layout/mockup file, how long will it take to build this page if I extract all the assets for you?
Me: well if you extract them in the right format and size this time, probably by end of day...
Designer: perfect! (Actually gets me everything in the right format)
*4:30 pm*
Me: alright I'm done
Designer: wait where are all the videos, and animations, and the parallax, and hover states and tool tips and interactive charts?
Me: WTF are you talking about? You gave them all to me as images?
Designer: ...they are supposed to be interactive.
Me: 😑 -
Facebook is a giant piece of shit. Not only is their platform a massive contributor to mental illness, even their API's are fucking garbage. I'm trying to use their ads API and what it does is it hijacks the entire fucking request so you can't even extract data from the request after calling it. Fuck Facebook and everything they've ever "contributed" to society.4
-
Any chance we can do a polling system?
@dfox
I studied anthropology and ive been in this community for almost 2 years. Have discovered the coding landscape at pretty much the same time and i must say its an interesting bunch of people.
I came on here to learn about the geek way and how to become a better dev. Seeing the rants has been really helpful!
But i think the polling system could lead to interesting understanding. Of the community both for your own app (for marketing bullshit purposes) but also for us.
Id love to know what kind of music people listen to but in a summarized way rather than a unending list of comments which will be harder to extract the information from!9 -
trying to install devkitARM:
>don't wanna install pacman for one special snowflake library
>download source
>sh some-bad-buildscript.sh
"can't extract /-.tar"
>???
>report issue
"lol just use pacman skrub"
>I DON'T WANNA FUCKING USE PACMAN YOU TROGLODYTE, MAYBE HELP ME WITH BUILDING SOURCE?????
"nah, just use pacman, it'd be dumb to provide a copy for every package manager"
>EVERYONE ELSE DOES THAT. YOU ARE THE EXCEPTION, NOT EVERYONE ELSE.
*fucker marks issue as spam, doesn't help me*
i'm gonna fucking stab somebody i swEAR TO FUCK
https://github.com/devkitPro/...
Turns out i'm banned from making another issue to try and ACTUALLY GET HELP THIS TIME.
"You can't perform this action at this time" isn't fooling anyone, GitHub, we all know what happens when you get errors like this7 -
So I downloaded the handwritten character dataset from EMNIST, took an hour to extract. Found out it has 814k + pngs. I haven't optimized all of them with Gimp 😕 change them to idx3-ubyte format, or make labels for each char in a c++ automation.. While Gimp was frozen in bulk process, I started hearing crackling sounds from my desk 😨😨 I'm like fckkk shits gonna blow..
That's when the poorly taped 0x7E2 calendar fell from the wall.🤣🤣🤣2 -
Right, that's fucking it. Enough. I'm all for learning new technologies, frameworks, and development protocols, but my time on this earth is limited and at the end of the day if I'm having to spend DAYS AND FUCKING DAYS just scouring through obscure forum posts because the documentation is shit and just hitting ONE FUCKING PROBLEM AFTER ANOTHER then there comes a point at which the time investment simply isn't worth it. I HATE throwing in the towel because some FUCKING CUNT code problem has got the better of me, but fucking sense must prevail here.
Laravel fucking Mix. Do any any of you use this shit on Windows? Because I take my fucking hat off to you. I'm done with it.
Oh, so your server uses 'public_html' instead of 'public' does it? Well, of course you can just set
mix.setPublicPath('public_html'); then can't you?
No, you can't. Why? Because fuck you, that's why. Not only do you have to hard-code your fucking public directory into each specified path, additionally you have to set
mix.setPublicPath('./');
Why? Because fuck you, that's why. It took me the best part of two days to discover that little nugget of information, buried at the bottom of some obscure corner of the internet in a random github issue thread. Fuck off.
Onto next problem. Another 5 hours invested to extract some patchy solution that I'm not at all happy with.
Rinse, repeat.
Make it work with BrowserSync by wrapping your assets like so:
<link rel="stylesheet" href="{{ mix('/build/css/main.css') }}">
Oh oh oh but "The Mix manifest does not exist"... despite a fresh install of Laravel 5.6 and all relevant node modules installed... follow some other random Github thread with a back and forth of time-consuming suggestions for avenues of experimentation, with no clear solution.
Er no, fuck off. I'm going back to Grunt and maybe I'll try Webpack/Mix in another year or two when there's actually some clear answers, but as it stands this a wild goose chase into a fucking black-hole and I've got better things to do with my precious time. Go die.5 -
Watched an action hack movie
Then designed a scenario to sniff around a bank and get the encrypted key and finally extract the key and omg!
I've broke into the bank !!!
But seriously, is it worth trying?
I'm not going to do any thing stupid like even taking a dollar , but is it just the way I thought it is?
Will anything unexpected happen?16 -
Fuck my life! I have been given a task to extract text (with proper formatting) from Docx files.
They look good on the outside but it is absolute hell parsing these files, add to these shitty XML human error and you get a dev's worst nightmare.
I wrote a simple function to extract text written in 'heading(0-9)' paragraph style and got all sorts of shit.
One guy used a table with borders colored white to write text so that he didn't have to use tabs. It is absolute bullshit.2 -
Extract from a quite old recruiter email (excluding the formalities):
Position: junior dev
Workplace: office for first year, can be changed to remote after (salary will be 50% lower if you go remote though) *suspicion levels starts raising*
Payment: 1€ per line of code (empty lines/comments excluded) or page of documentation *alarms start ringing*
Additional info: on high alert for 4 weeks every 6 weeks *wtf is going on*, salary bonus is 10€ per week *I stopped reading here and moved the email directly to the spam folder*6 -
I have no choice but to come here, lest I cause irrecoverable offence at work.
It's 'Extract' not 'Extrapolate'!
It's 'Deprecated' not 'Depreciated'!8 -
Need to implement something huge on a app that I'm working on.
The design team is not from my company.
All the design that I have is in a PDF that I can't extract the images and they are low res.
How the actual fuck do they expect me to do a good job if I don't even have the design and assets to work with -
So my time saver automation can not be used because automation is not reliable.
Yeah sure make me extract data manually from 800 urls by hand and see if there is no human error.
Fuck my life.5 -
Yes, I have to admit, sometimes Linux is a F*KING B*TCH.
I was supposed to fucking format a pc for a close friend of mine, cause he produces music and win 10 fucked his machine up with its broken updates.
Knowing the guy is a talent I promised that by 7PM the pc would be fixed.
Not really, I'm feeling the stupidest guy in this fucking earth, cause I've been here for 2 hours, fucking trying to extract an ISO image, and nothing on this fucking planet seems to work.
Tried the graphical archives, none open de ISO, tried 7z, it gives me an error, tried fuseiso, which is recommended in Arch Linux' documentations. Doesn't work. Tried mount - o my file.iso /mnt and it says /mnt isn't in the fstab file which makes me even angrier cause I always mount everything there without editing shit. So I installed 7-zip for windows in wine, it extracts until 90% and freezes. Now I'm trying hsuebrirbwkwpxjhw9shrbejejwke and my mouth is foaming and my ear is bleeding my brains out and I don't need you shit.
Fuck you, Fuck your goddamn ISO and Fuck this faggot ass spell checker, that changes Fuck to duck and assign to asset.
Fuck it, I ain't gonna format anyones pm anymore. 18
18 -
First time working with designers so maybe someone else can share their experiences. I was expecting all the images/logos to use in the app, but I got an illustrator file containing all mockups. Are they expecting that I extract each image from the mockups? They didn't even use multiple layers...4
-
Everyone shitting on SO answers being mean (which sometimes they are), meanwhile:
https://stackoverflow.com/questions...
Garbage like this is how you become a misanthrope.10 -
Ahh.. there is nothing like the joyous feeling of writing a working piece of code for your own personal projects.
I spent several weeks and a few hours today to finally get my Python automation script working and I am very proud of myself.
Here's what it does:
* open a text file, extract a specific string from it using rather complicated xpath
* open another text file and do the same
* replace result 1 with result 2
* log results
* close file
* automate the process
Even though it looks easy, I had to mess around with a lot of problems such as permissions, indentation, stream writing, file status, etc.
Now, instead of having to manually do this job, I can just let my machine do it!1 -
I HATE SURFACES SO FRICKING MUCH. OK, sure they're decent when they work. But the problem is that half the time our Surfaces here DON'T work. From not connecting to the network, to only one external screen working when docked, to shutting down due to overheating because Microsoft didn't put fans in them, to the battery getting too hot and bulging.... So. Many. Problems. It finally culminated this past weekend when I had to set up a Laptop 3. It already had a local AD profile set up, so I needed to reset it and let it autoprovision. Should be easy. Generally a half-hour or so job. I perform the reset, and it begins reinstalling Windows. Halfway through, it BSOD's with a NO_BOOT_MEDIA error. Great, now it's stuck in a boot loop. Tried several things to fix it. Nothing worked. Oh well, I may as well just do a clean install of Windows. I plug a flash drive into my PC, download the Media Creation Tool, and try to create an image. It goes through the lengthy process of downloading Windows, then begins creating the media. At 68% it just errors out with no explanation. Hmm. Strange. I try again. Same issue. Well, it's 5:15 on a Friday evening. I'm not staying at work. But the user needs this laptop Monday morning. Fine, I'll take it home and work on it over the weekend. At home, I use my personal PC to create a bootable USB drive. No hitches this time. I plug it into the laptop and boot from it. However, once I hit the Windows installation screen the keyboard stops working. The trackpad doesn't work. The touchscreen doesn't work. Weird, none of the other Surfaces had this issue. Fine, I'll use an external keyboard. Except Microsoft is brilliant and only put one USB-A port on the machine. BRILLIANT. Fortunately I have a USB hub so I plug that in. Now I can use a USB keyboard to proceed through Windows installation. However, when I get to the network connection stage no wireless networks come up. At this point I'm beginning to realize that the drivers which work fine when navigating the UEFI somehow don't work during Windows installation. Oh well. I proceed through setup and then install the drivers. But of course the machine hasn't autoprovisioned because it had no internet connection during setup. OK fine, I decide to reset it again. Surely that BSOD was just a fluke. Nope. Happens again. I again proceed through Windows installation and install the drivers. I decide to try a fresh installation *without* resetting first, thinking maybe whatever bug is causing the BSOD is also deleting the drivers. No dice. OK, I go Googling. Turns out this is a common issue. The Laptop 3 uses wonky drivers and the generic Windows installation drivers won't work right. This is ridiculous. Windows is made by Microsoft. Surface is made by Microsoft. And I'm supposed to believe that I can't even install Windows on the machine properly? Oh well, I'll try it. Apparently I need to extract the Laptop 3 drivers, convert the ESD install file to a WIM file, inject the drivers, then split the WIM file since it's now too big to fit on a FAT32 drive. I honestly didn't even expect this to work, but it did. I ran into quite a few more problems with autoprovisioning which required two more reinstallations, but I won't go into detail on that. All in all, I totaled up 9 hours on that laptop over the weekend. Suffice to say our organization is now looking very hard at DELL for our next machines.4
-
This is a story of how I did a hard thing in bash:
I need to extract all files with extension .nco from a disk. I don't want to use the GUI (which only works on windows). And I don't want to install any new programs. NCO files are basically like zip files.
Problem 1: The file headers (or something) is broken and 7zip (7z) can only extract it if has .zip extension
Problem 2: find command gives me relative to the disk path and starts with . (a dot)
Solution: Use sed to delete dot. Use sed to convert to full path. Save to file. Load lines from file and for each one, cp to ~/Desktop/file.zip then && 7z e ~/Desktop/file.zip -oOutputDir (Extract file to OutputDir).
Problem 3: Most filenames contain a whitespace. cp doesn't work when given the path wrapped in quotes.
Patch: Use bash parameter substitution to change whitespace to \whitespace.
(Note: I found it easier to apply sed one after another than to put it all in one command)
Why the fuck would anyone compress 345 images into their own archive used by an uncommon windows-only paid back-up tool?
Little me (12 years old) knowing nothing about compression or backup or common software decided to use the already installed shitty program.
This is a big deal for me because it's really the first time I string so many cool commands to achieve desired results in bash (been using Ubuntu for half a year now). Funny thing is the images uncompressed are 4.7GB and the raw files are about 1.4GB so I would have been better off not doing anything at all.
Full command:
find -type f -name "*.nco" |
sed 's/\(^./\)/\1/' |
sed 's/.*/\/media\/mitiko\/2011-2014_1&/' > unescaped-paths.txt
cat unescaped-paths.txt | while read line; do echo "${line// /\\ }" >> escaped-paths.txt; done
rm unescaped-paths.txt
cat escaped-paths.txt | while read line; do (echo "$line" | grep -Eq .*[^db].nco) && echo "$line" >> paths.txt; done
rm escaped-paths.txt
cat paths.txt | while read line; do cp $line ~/Desktop/file.zip && 7z e ~/Desktop/file.zip -oImages >/dev/null; done3 -
The worst type of debugging: Programming an MCU without a Serial Monitor.
Some Context: I've spendt today about 3h+ on getting an attiny 45 to read 3 digital values on 3 pins. So for every test I wanted to make, I needed to put the MCU inside a socket put this socket on a arduino and flash it. Then extract it from the socket and put it on a breadboard for testing.
After getting headaches for nothing making any goddamn sense, I ended up noticing that one input pin is a multiplexed reset pin with the reset having top priority and no way to change it. So whenever this pin should have read a low signal, it got held in reset! FML -
Windows:
Step 1: install my c++ library from www.scammysite.be
Step 2: extract the zip and open scammyexe.exe
Step 3: ....
Step 304: do three backflips
???
Step 404: it should now be installed on your machine
Linux:
Step 1: sudo apt-get install coolsoftware
Hmmm....3 -
So today was interesting.
I had to extract the domain from an email address and compare the domain to a hard coded whitelist, nothing difficult, fuck takes 2 min really.
Except the project starts throwing 500 errors for no god damn reason, like seriously, I double check syntax, nope looks fine, run pho's syntax checker on the file
# php -l /path/to/file.php
Nope says it's all good.
Checks error log on server -> no log
OoooooooooKay then.
Comments out the few lines, saves, errors gone.
remove comments, error comes back.
Do this a few times, and magically the fucking thing stops throwing errors, now I haven't actually changed anything, and I know this project is so fragile I don't know how it stays running at times but fuck me this is a painful joke.6 -
Hey devRant! It's been a long time, but I'm baaack! I know you missed me, but my life has been so eventful, and difficult, and so I am here for sympathy and recognition of my status among my fellow devRant community, because like, I'm basically a legend now, I'm sure you've all heard of me!
Did I mention I'm back!? I know right, it's mad, it's like the place hasn't been the same without me. What has changed? Man, I remember when devRant was a toddler colouring in my walls with crayon, man those were the days...
Oh, have any of you seen @OtherLongtimeUser about, are they still alive? Come on guy, we were like best buddies, and your existence validates my sense of self-worth in relation to my status on this here community. You about?
Anyway, life's been hard, I'm sure you're all desperate to hear about it... Looking forward to you asking me about it in the comments so that I can skirt around the answer for you whilst still trying to extract the maximum amount of sympathy. But yea, just tell me you've missed me, that'd be fantastic.
Also, I bet the banter on here isn't like it used to be. All you n00bs missed so much. But hey, did I mention, I'm baaaaack!? ✌4 -
So, in Germany apprentices at companies need to file a "Berichtsheft".
It's a thing where you have to file, for each day that is, what you did at work or in job college and how long you did it.
Basically every company keeps records of their employees activities in their CRM or other management system and all schools use services for keeping timetables that include lesson duration and activity.
So why the fuck do we apprentices have to write that shit ourselves when we could literally just acces the databases and SELECT THE SHIT FROM FILED_ACTIVITIES, I thought.
So I'm writing scripts to acces our CRM database and a puppeteer script now that scrapes the Untis (online timetable service for schools) timetables to extract everything, group it by date and format it nicely as CSV.
I'm sick of this: Digital system & Digital system = write it yourself bullshit.
Once I'm done I'll make a github repo for the Untis scraper.
Also, I'll be making the tools usable for the other apprentices at my company to spare them the suffering.9 -
I'm writing a book that teaches everything I have learned in the past 20 years about writing small niche software and selling it.
Need some help from my fellow DevRanters.
Anyone who comments here with something constructive gets a free copy when it's done.
When I say:
"Why don't you just write your own software and sell it to end users"
What is the first thing that pops into your head?
Is it "I don't know how to advertise"
or
"that's a pipe dream"
or
"I tried starting my own business, but _______"
or
"I am doing that, i have this side project "
(how long have you spent on that side project?)
I need to know all your concerns questions fears, skepticism etc around the idea of writing your OWN software.
After 20 years I have like, so much knowledge, but it's sometimes hard to get it all out, UNLESS someone has a question or concern, then, out it comes.
So, I'm going to (hopefully) collect all the questions here ... and answer them, and it'll help me out a lot to extract this knowledge.
A lot of stuff I do without even thinking and realizing all the years it took to even know that.
What would you like to know the most?
You have the skills, you have the know how, you can probably see it in your head, so what's stopping you from making the leap?question your own business why the fuck haven't you started yet no more bosses no more clients residual income from a one time effort no more teams32 -
Over the summer I was recruited to be a supplement instructor for a data structures course. As a result of that I was asked (separately by the professor) to be a grader for the course. Because of pay limitations I've mostly been grading homework project assignments. In any case, it's a great job to get my foot into the department and get recognized.
Over the course of the semester I've had this one person, OSX, named after their operating system of choice, who has been giving me awkward submissions. On the first assignment they asked the professor for extra time for some reason or the other, and that's perfectly fine.
So I finally receive OSX's submission, and it's a .py file as per course of the course. So I pop up a terminal in the working directory and type "python OSX_hw1.py". Get some error spit out about the file not being the right encoding. I know that I can tell python to read it in a different encoding, so I open it up in a text editor. To my surprise it's totally not a text file, but rather a .zip file!
I've seen weirder things done before, so no big deal. I rename the file extension, and open it up to extract the files when I see that there's no python files. "Okay, what's goin on here OSX..." I think to myself.
Poking around in the files it appears to be some sort of meta-data. To what, I had no clue, but what I did find was picture files containing what appeared to be some auto-generated screenshots of incomplete code. Since I'm one to give people the benefit of doubt even when they've long exhausted other peoples', I thought that it must be some fluke, and emailed OSX along with the professor detailing my issue.
I got back a rather standard reply, one of which was so un-notable I could not remember it if my life depended on it. However, that also meant I didn't have to worry about that anymore. Which when you're juggling 50 bazillion things is quite a relief. Tragically, this relief was short lived with the introduction of assignment 2.
Assignment 2 comes around, and I get the same type of submission from OSX. At this time I also notice that all their submissions are *very* close to the due time of 11:59pm (which I don't care about as long as it's in before people start waking up the next morning). I email OSX and the professor again, and receive a similar response. I also get an email from OSX worried about points being deducted. I reply, "No issue. You know what's wrong. Go and submit the right file on $CentralGradingCenter. Just submit over your old assignment".
To my frustration OSX claimed to not know how to do this. I write up a quick response explaining the process, and email it. In response OSX then asks if I can show them if they comes to my supplemental lesson. I tell OSX that if they are the only person, sure, otherwise no because it would not be a fair use of time to the other students.
OSX ends up showing up before anyone else, so I guide them through the process. It's pretty easy, so I'm surprised that they were having issues. Another person then shows up, so I go through relevant material and ask them if they have any questions about recent material in class. That said, afterwards OSX was being somewhat awkward and pushy trying to shake my hand a lot to the point of making me uncomfortable and telling them that there's no reason to be so formal.
Despite that chat, I still did not see a resubmission of either of those two assignments, and assignment 3 began to show it's head. Obviously, this time, as one might expect after all those conversations, I get another broken submission in the same format. Finally pissed off, I document exactly how everything looks on my end, how the file fails to run, how it's actually a zip file, etc, all with screenshots. That then gets emailed to the professor and OSX.
In response, I get an email from OSX panicking asking me how to submit it right, etc, etc. However, they also removed the professor from the CC field. In response I state that I do not know how to use whatever editor they are using, and that they should refer to the documentation in order to get a proper runnable file. I also re-CC the professor, making sure OSX's email to me is included in my reply.
OSX then shows up for one of my lessons, and since no one had shown up yet, I reiterate through what I had sent in the email. OSX's response was astonished that they could ever screw up that bad, but also admits that they had yet to install python(!!!). Obviously, the next thing that comes from my mouth is asking OSX how they write their code. Their response was that they use a website that lets them run python code.
At this point I'm honestly baffled and explain that a lot of websites like those can have limitations which might make code run differently then it should (maybe it's a simple interpreter written on JavaScript, or maybe it is real python, but how are you supposed to do file I/O?) .
After that I finally get a submission for assignment 1! -
Some of these apps might be using your microphone to extract your conversation and display you related Ads. 😱🙄
 11
11 -
We are researching enhancing our current alerting system (we use Splunk) to be 'smarter' about who is emailed/texted/whatever when there are problems in our applications.
Currently, if there are over 50 errors logged within a 15 minute period, a email/phone/text blast to nearly 100 individuals ranging from developers, network admins, DBAs, and vice presidents.
Our plan is to group errors by team and let each team manage their own applications. Alert on 1 error, 5, 500...we don't care, let the team work out the particulars.
The trick was interfacing with Splunk's API (that's a long rant by itself)
In about a day or so I was able to use Splunk's WebHook feature to notify a WebAPI service I threw together to send myself an email with details about the underlying data (simulating the kind of alert we would send to the team)
I thought ...cool... it worked. Show it off to the team, most thought it was a good start, except one:
Dev: "The errors are not grouped by team."
Me: "No, I threw the webapi service together to demonstrate how we can extract the splunk bits to get access to the teams"
Dev: "Well...this won't work at all."
Me: "Um..what?"
Dev: "The specification c l e a r l y states the email will be team based. This email was only sent to you and has all the teams and their applications"
Me: "Um...uh...the service can, if we want to go using a service route. Grouping by team name is easy using a LINQ query. I just through this service together yesterday."
Dev: "I don't know. Sounds like I need to schedule a meeting to discuss what you are proposing. I don't think emailing all that to everyone is a good idea."
WTF! Did you not listen to what I said?!!!
Oh well..the dev's proposal is to use splunk's email notification and custom Exchange rules with callbacks into splunk that resend...oh good lord ...a fracking rube goldberg of a config nightmare ...
I suspect we'll go the service route once I finish the service before the meeting.1 -
Got one right now, no idea if it’s the “most” unrealistic, because I’ve been doing this for a while now.
Until recently, I was rewriting a very old, very brittle legacy codebase - we’re talking garbage code from two generations of complete dumbfucks, and hands down the most awful codebase I’ve ever seen. The code itself is quite difficult to describe without seeing it for yourself, but it was written over a period of about a decade by a certifiably insane person, and then maintained and arguably made much worse by a try-hard moron whose only success was making things exponentially harder for his successor to comprehend and maintain. No documentation whatsoever either. One small example of just how fucking stupid these guys were - every function is wrapped in a try catch with an empty catch, variables are declared and redeclared ten times, but never used. Hard coded credentials, hard coded widths and sizes, weird shit like the entire application 500ing if you move a button to another part of the page, or change its width by a pixel, unsanitized inputs, you name it, if it’s a textbook fuck up, it’s in there, and then some.
Because the code is so damn old as well (MySQL 8.0, C#4, and ASP.NET 3), and utterly eschews the vaguest tenets of structured, organized programming - I decided after a month of a disproportionate effort:success ratio, to just extract the SQL queries, sanitize them, and create a new back end and front end that would jointly get things where they need to be, and most importantly, make the application secure, stable, and maintainable. I’m the only developer, but one of the senior employees wrote most of the SQL queries, so I asked for his help in extracting them, to save time. He basically refused, and then told me to make my peace with God if I missed that deadline. Very helpful.
I was making really good time on it too, nearly complete after 60 days of working on it, along with supporting and maintaining the dumpster fire that is the legacy application. Suddenly my phone rings, and I’m told that management wants me to implement a payment processing feature on the site, and because I’ve been so effective at fixing problems thus far, they want to see it inside of a week. I am surprised, because I’ve been regularly communicating my progress and immediate focus to management, so I explain that I might be able to ship the feature by end of Q1, because rather than shoehorn the processor onto the decrepit piece of shit legacy app, it would be far better to just include it in the replacement. I add that PCI compliance is another matter that we must account for, and so there’s not a great chance of shipping this in a week. They tell me that I have a month to do it…and then the Marketing person asks to see my progress and ends up bitching about everything, despite the front end being a pixel perfect reproduction. Despite my making everything mobile responsive, iframe free, secure and encrypted, fast, and void of unpredictable behaviors. I tell her that this is what I was asked to do, and that there should have been no surprises at all, especially since I’ve been sending out weekly updates via email. I guess it needed more suck? But either way, fuck me and my two months of hard work. I mean really, no ego, I made a true enterprise grade app for them.
Short version, I stopped working on the rebuild, and I’m nearly done writing the payment processor as a microservice that I’ll just embed as an iframe, since the legacy build is full of those anyway, and I’m being asked to make bricks without straw. I’m probably glossing over a lot of finer points here too, just because it’s been such an epic of disappointment. The deadline is coming up, and I’m definitely going to make it, now that I have accordingly reduced the scope of work, but this whole thing has just totally pissed me off, and left a bad taste about the organization.9 -
Here in my country banks doesn't have a public API to access your bank account extract, 3 years later we make some bots to extract these data to an API8
-
This isn't something I've dealt with personally, but recently heard the story on the podcast and was pretty astounded:
"A company who makes add-ons for Flight Simulator X included malware in one of their downloadable jets, players have alleged. The malicious file is called ‘test.exe’ and it is designed to extract passwords from the Chrome web browser."
Now that's some extreme DRM. "Pirate our downloadable jet? We leak your credit card information and Social Security Number to the darknet."
Original story: https://rockpapershotgun.com/2018/...3 -
Tight deadline, codebase not mine, I wrote an hack that read a dom element in the page in js extract some data, append it to the query string and then refresh the page to get the desired result. All the rest of the logic is in PHP. I still feel guilty.
-
Why, in 2023, do we still have a path length limit in Windows?
I know it's not that trivial finding a good soution, but at least if I managed to get a .zip which I can't extract in that directory because of a few files with a too long file name, let me know in advance (and not during the extraction) and maybe (amazing idea) let me know how many steps I have to go back in the directories tree to make it work…12 -
Watching a video on YouTube that shows: Refactoring and Extract Method features in xcode 9 beta brings a tear to my eye, never thought we will get that basic functionality 😢
-
Website for a gallery that wanted a 10k website for just 1k ... Must haz super CMS so that they could send me word documents each week so I could manuallly copy paste that shit into the CMS, and somehow extract and restore the lowres embedded images in full resolution ...
I guess it was safe to say this was my first client from hell 😅😂😂😂
The second was a website for some ballroom dude that got my referral from gallery X ... Yup, same shitty type of client3 -
So I installed a new Linux distro, and since the DE is Gnome, I wanted to spice things up with a Conky file.
I download my conky theme, extract it, and try to run it.
And it's broken.
Apparently, the Conky development team decided it would be a great idea to switch over to an ENTIRELY FUCKING NEW SYNTAX, LEAVING EVERY CONKY THEME WRITTEN BEFORE AUTUMN THIS YEAR USELESS
Oh, no biggie, I think. After all, the development did very graciously publish a Lua file to convert old conky configs to the new syntax.
Except no.
The file used to convert conky configs uses the old loadstring function, for which support was dropped in Lua 5.4
So not only did Conky make every config written earlier than this Autumn obsolete, the FUCKING TOOL THEY DEVELOPED TO HELP WITH THAT IS ALSO FUCKING BROKEN
Fuck Conky. I wasted 2 hours screwing with this broken-ass piece of shit3 -
<repost because previous one had many typos and grammatical mistakes>
I have arrived at a conclusion, rather two.
- I am a misfit who generally does not belong anywhere. Not that Steve Jobs Hipster type where you'd think I am a misfit genius. I am rather a misfit ignorant loser, at least for wide majority of things. I also have some ego issues of being included, hence I often turn out to be an asshole if things don't go according to me.
- People in general will hate you for no reason. And hate you more for your success. They'd be happy at your misery and pain. If you are running, walking, or even crawling towards success based on your hard-work, they will be jealous. Only time you are valued is when they need anything or can extract benefits out of you. Once you are drained, no one looks back because for them nothing more is left that could be exploited.
As long as you are providing, you'll be included.
This has significantly affected my self worth. I have allowed people to take advantage of me at the cost of my self respect and time.
These people are narcissist takers.
But there is a very very small group of people in my life, many of them I haven't even met and/or less frequently interacted, who are givers.
During my time with them, all they have done is kept giving me. Even when I asked them to stop or tried to resonate their kindness, they refused and kept giving me more. Most wonderful and best people in my life. I never failed to acknowledge their worth and valued them more than they deserved.
As of now, life is a mess.19 -
"Reflective" programming...
In almost every other language:
1. obj.GetType().GetProperties()
or
for k, v in pairs(obj) do something end
or
fieldnames(typeof(obj))
or
Object.entries(obj)
2. Enjoy.
In C++: 💀
1. Use the extern keyword to trick compilers into believing some fake objects of your chosen type actually exist.
2. Use the famous C++ type loophole or structured binding to extract fields from your fake objects.
3. Figure out a way to suppress those annoying compiler warnings that were generated because of your how much of a bad practice your code is.
4. Extract type and field names from strings generated by compiler magic (__PRETTY_FUNCTION__, __FUNCSIG__) or from the extremely new feature std::source_location (people hate you because their Windows XP compilers can't handle your code)
5. Realize your code still does not work for classes that have private or protected fields.
6. Decide it's time to become a language lawyer and make OOPers angry by breaking encapsulation and stealing private fields from their classes using explicit template instantiation
7. Realize your code will never work outside of MSVC, GCC or CLANG and will always be reliant on undefined behaviors.
8. Live forever in doubt and fear that new changes to the compiler magic you abused will one day break your code.
9. SUFFER IN HELL as you start getting 5000 lines worth of template errors after switching to a new compiler.13 -
My latest project is going quite well, I think some of guys might like it! Basically it is a entirely new Fallout game with multiplayer aspects made in Unreal. Now most of you are saying "dude make textures is going to take years!" However I can extract models and textures from Fallout itself, saving time. The next question will be the legal stuff however Zenimax gave me permission as long as I don't restrict access, money or otherwise. If you want to check it out or think you can help go to the sub Reddit and click the discord link!
Reddit.com/r/FalloutMP
Thanks,
Patryk Grzelak1 -
*One Month Ago*
Project Manager: we have allocated these two workstations for you to extract data (set) from malicious files, they are off the network. I though would also prefer a seperate laptop for this project you can take this one (pointing towards the newish laptop on the table)
Me: (i declined his offer because i didn't wanted to carry two laptops everywhere) I'm going to use my own laptop, but I'll be using a sand box or virtual machine.
*Fast Forward to Today*
Accidentally ran a script outside the sandbox, which due to some unknown reasons ended up executing a bunch of malicious files I only realised my mistake when my antivirus started to go bonkers FML.
P.S. both of those PCs are now connected network because of me.
Fingers crossed2 -
* sees mock-up in the provided design PDF, notices a diagram that could be made with CSS
* writes responsive CSS for the boxes and makes them more appealing than in the original design
* feels proud
Skip to today, it got assigned as an 'issue', got asked to NOT do it like this, and instead extract a png from the PSD and use that instead. Despite me saying not only is it going to look bad because it's not exactly going to be responsive the way they want it to be.
Bootstrap doesn't magically make images responsive, goddammit...2 -
So there is this program with legacy code from 15 years ago the client is in love with. Every time we try to accomplish something it proves that the mf who wrote it was so lazy and incompetent that he should have never chosen this profession. Goto, one-two letter for type and variable names. Dude even wrote an ascii decoder as if he would be payed for lines of code. Today we found a code where a rows of data was misindexed by one (we incorrectly assumed that we could extract some data from it but the column we wanted to use was just there for decoration, it was not actually used). the calculations the system uses are replicated for each interface with duplicate lines of code so the same binary data can show different values because of the multipliers.
If I could I woukd go back in time and bang the guy's head to the desk emphasising each word like "You - should - quit - and - never - ever - write - code -again"4 -
when you think you're done coding and can finally start writing...
So you guys have seen my Unreal Engine adventures. I have to use a plugin for it, on top of everything, to extract some data. I've been using this plugin since ages on another pc, but now I had to set it up from scratch since this is a new project, new models, etc.
There is a new version. If I use the new one, it will break the chain which is to follow.
The old version is so legacy that the guy who wrote it does not remember how to set it up.
After hours, and tons of hacks and outcommenting stuff (there is physics involved with which I do nothing), it finally starts doing something. Finally!
Although I'm slowly loosing my sanity in the process....
Even if it now records the data, I cannot say if this is good enough or if the poses are all wonky now.
And that is my masters thesis. Submission deadline is on monday. Ha.
Ironically, since the start of this thesis, I felt like this will either make me or break me. ;D So much fun... FK2 -
Okay so after a few days of thinking I think I'm sure about what I'm about to write :
Best : Discovering how to use streams while making a service that should extract a tar.gz, extract the tar.gz within it, filter the extracted files and correct some of them, then compress each folder as tar.gz and compress all the archives as .zip. The amazing thing for me is that with streams I could do all the operations in just two passes, maybe one if I had more time, saving disk writing time.
Worst : upgrading a bunch of legacy Access 97 apps and its VBA code to Access 2013 -
How to replace rEFInd bcuz M$ locks linux out of your system if M$ installed first.
-----
This will be long so get your salsa ready.
-----
1. Get your rEFInd from sourceforge
Since we are installing INTO windows, dl the zip.
2. extract to a folder.
2-a-: Install themes if you want any or edit the config if you want/need to, at this stage.
3. open a cmd as Admin and cd to the refind's folder.
4. mount system volume
`mountVol S: /S` will mount it to S:
5. use xcopy to copy as system
`xcopy /E refind-bin-x.xx.x\ S:\EFI\refind`
6tynice: go to System volume and to the refind folder
`S:`
`cd EDI\refind\refind`
7:Set rEFInd as Windows Boot Manager
`bcdedit /set {bootmgr} \EFI\refind\refind\refind_x64.efi`
(It's possible to use ia32 or aa64 for different architectures)
At this point, try plugging a linux thumb drive and restart your computer. Windows Boot Manager should be deactivated and should show refind.
You can use mouse and keyboard to select an OS boot or just set config to start one automatically unless you are holding a "power" button.
rEFInd also offers "fallback" boot for linux, which boots the efi from rEFInd and not from syslinux.4 -
Me on code review : You should extract the logic into a separate method for better readability. Colleague completely ignores it. What should I do?6
-
Best: take a job as a data analyst. 1 year later, re-write and re-deploy the entire backend following correct security concentions and well-hashed-out data models.
Worst: attempt to backup a hard drive using dd, just to accidentally brick the laptop (because it had some security layer the school put to prevent just that)
Bestest: use knowledge acquired at my "best" story to nuke windows on bricked laptop. Then extract the leftover data using dd and a series of recovery tools. -
Regex are one of the finest art piece in software.
Had a 2 hour class and even after that I think you can spend months on mastering it.
It's not something I haven't used but we undermine whole beauty of how random characters can form formula and extract complicated pattern.
Kleene we owe you. -
My workplace is still using xml based configuration, and non-spring boot projects.
So every spring boot tutorial I find feels like "Look at how easy you can get this running" and then it's just actually a toy you can't get into production.
Also it kind of bugs me that you need to be online to actually be able to initialize/create a spring boot project and every single tutorial says so.
You can make a local network m2 repository, but can one make a spring initializer service?
Either way, migrating every single project to Spring boot is a no-no,
And I'm stuck with like 5 prototypes of SSO integration from which only 2 work, and the other 3 have their own problems.
One does redirect to the login and all, but the SAML endpoint gets 404 on response when you log in.
One is on OpenID Connect, but I would need to update the project from Spring 3 to Spring 5 to get it working, which upon attempting to do seems to break everything else.
One has an external library handling the security context just the way we are accustomed to, but it only does a 401 forbidden when you go without logging in and I'm starting to think it is actually one of those that require you to extract the token or something manual like that, which wouldn't work for us
The other two are spring boot tutorials that worked out of the box, both SAML and OpenID, still can't use those for the main projects.
I'm tired of dealing with this configuration hell, been two months at this, I want to get features done as usual, not be stuck configuring stuff that might or might not work.
Rant aside, I think I figured I need to use a different Security adapter, but I needed to vent.2 -
spent the whole week working on a bug fix last week.
implemented a method to filter some data to make it easier to use in the HTML template.
friday's session with other programmers to review code went well, they said the method is pretty good and works nice. (I must admit there was an elusive bug that prevented the component to render and none of us could figure it out)
i get back on monday to a message from the lead saying the code is unusable and they reverted to the previous (convoluted) way of doing things and i should do the same in the future. just copy their work.
i check the typescript class. fucking method that was used (which he told me not to use and I should copy and work off of), he went and just changed the method's name, and the body is EXACTLY the same as his existing method.
this code base is ridden with re-used methods (I managed to extract two reused ones into a service some time ago), the use of any for 90% of method return types and variables...
WTF. I am losing all of my respect for seniors and faith in this company.
This is why I am burned out. You are farting against a hurricane and everyone else's shit is coming back onto you. This is fucking insane. Or am I insane?9 -
So I decided to download OS X iso from a third party website as I don't have a mac. After downloading I couldn't extract the iso file as it showed the zip file was corrupted.
From the comment I found out that the zip file can be only extracted in a mac :/
How is that even possible :/3 -
Alot of hacks around here!
An extract of some of those:
-Couldn't time the shutter right when photographing lightning. Used my oscilloscope to measure its electrical influence and anytime a peak is detected, it actuates the shutter.
-Using a lock as a heatsink for a overheating display driver ic.
-Hacking two USB ports together to get more power.
-Display module was too tall with header pins. Moved its back components to the main board and soldered the module flat onto it by flowing solder down its connecting holes.
-Not me but still interesting: Back on ye olde times when paid tv contained a disruptive H or VSYNC signal only their paid tv box could filter, my electronics prof. analyzed it and built the required comb filter on his own. Even sold some on the black market. -
Got a scammer on my hook. Ideas welcome to fuck him/her over.
He/she confused me with someone else and messaged me acting as a support person of an exchange. I acted along and s/he is insisting on sharing account details.
Played along like a dumb internet noob and I think I got him to share his fake email id.
Now I'm thinking of ways to extract more details about him via email.
From top of my mind, these are some ideas I have:
- get his IP address
- zip bomb or something like that? But g mail is probably gonna detect that.
Ideally, If I could social engineer him to give his phone number, I could easily report him to police and find his identity.
Have you busted some scammers? Would appreciate some tips.6 -
Yo, so does anyone here have any experience about using Windows or mac printer drivers on GNU+Linux? So far my strategy has been to try to extract a ppd file from the Windows/mac drivers. It's an epilog fusion laser printer/engraver5
-
Talking to my architect:
- hey, we have a lot of code smell and data is structured usually in a chaotic way, also its hard to understand what is going on with all these code duplications, maybe we can think about refactoring, better structure, maybe even we can extract some domains and make life less painful?
- what is domain?
- *facepalm*4 -
TLDR;
Side project update.
Made simple nlp library in python and published it’s first version to open source.
Now I can feed it with parsed pdf text.
See rant https://devrant.com/rants/2192388/...
Why ?
Cause during reading book about nltk I couldn’t find simple extendible way to provide support for polish language and I wanted to abstract stemming, word normalization, tokenizer etc. so I can provide ex. different conditions for separate text files and don’t write much code what is an asset when you work solo.
It’s about 12GB of pdf public accessible law data I am trying to handle ( at first ) which is about 35000 files from last 90 years.
So far I automated downloading web pages and pdf documents from them. Extracting data from web pages and saving it to database. Extracting text from pdf files. I have about 5-6 projects to do all of it above maybe at the end I will put it to some workflow manager like Luigi or just run it by cronjob.
First thing for website version 1.0 part is find correlation between all documents inside law text using nlp library by building custom conditions. Then just generate directory structure and html files with links between documents.
Website version 2.0 is already in my mind but it will be creepy to make it and will take at least 1-2 months and I want to publish fast.
I have some pdfs with only images instead of text and tesseract worked quite good with them so maybe I will try to process them when everything go live.
Learned a lot about pdf as now I know that font in pdf is not always providing unicode characters ( stupid form of obfuscation) so when you extract text you need to build glyph vector to text map for every font.
Pdf is full vector representation - just like svg - what is logic if you think a bit and know that some printers are running using postscript.
Let’s hope next update will be about flutter mobile app which started all of shit above. It’s almost ready ( except getting data from api I am trying to do and logo for release version ). It’s last piece of puzzle.3 -
Data wrangling is messy
I'm doing the vegetation maps for the game today, maybe rivers if it all goes smoothly.
I could probably do it by hand, but theres something like 60-70 ecoregions to chart,
each with their own species, both fauna and flora. And each has an elevation range its
found at in real life, so I want to use the heightmap to dictate that. Who has time for that? It's a lot of manual work.
And the night prior I'm thinking "oh this will be easy."
yeah, no.
(Also why does Devrant have to mangle my line breaks? -_-)
Laid out the requirements, how I could go about it, and the more I look the more involved
it gets.
So what I think I'll do is automate it. I already automated some of the map extraction, so
I don't see why I shouldn't just go the distance.
Also it means, later on, when I have access to better, higher resolution geographic data, updating it will be a smoother process. And even though I'm only interested in flora at the moment, theres no reason I can't reuse the same system to extract fauna information.
Of course in-game design there are some things you'll want to fudge. When the players are exploring outside the rockies in a mountainous area, maybe I still want to spawn the occasional mountain lion as a mid-tier enemy, even though our survivor might be outside the cats natural habitat. This could even be the prelude to a task you have to do, go take care of a dangerous
creature outside its normal hunting range. And who knows why it is there? Wild fire? Hunted by something *more* dangerous? Poaching? Maybe a nuke plant exploded and drove all the wildlife from an adjoining region?
who knows.
Having the extraction mostly automated goes a long way to updating those lists down the road.
But for now, flora.
For deciding plants and other features of the terrain what I can do is:
* rewrite pixeltile to take file names as input,
* along with a series of colors as a key (which are put into a SET to check each pixel against)
* input each region, one at a time, as the key, and the heightmap as the source image
* output only the region in the heightmap that corresponds to the ecoregion in the key.
* write a function to extract the palette from the outputted heightmap. (is this really needed?)
* arrange colors on the bottom or side of the image by hand, along with (in text) the elevation in feet for reference.
For automating this entire process I can go one step further:
* Do this entire process with the key colors I already snagged by hand, outputting region IDs as the file names.
* setup selenium
* selenium opens a link related to each elevation-map of a specific biome, and saves the text links
(so I dont have to hand-open them)
* I'll save the species and text by hand (assuming elevation data isn't listed)
* once I have a list of species and other details, to save them to csv, or json, or another format
* I save the list of species as csv or json or another format.
* then selenium opens this list, opens wikipedia for each, one at a time, and searches the text for elevation
* selenium saves out the species name (or an "unknown") for the species, and elevation, to a text file, along with the biome ID, and maybe the elevation code (from the heightmap) as a number or a color (probably a number, simplifies changing the heightmap later on)
Having done all this, I can start to assign species types, specific world tiles. The outputs for each region act as reference.
The only problem with the existing biome map (you can see it below, its ugly) is that it has a lot of "inbetween" colors. Theres a few things I can do here. I can treat those as a "mixing" between regions, dictating the chance of one biome's plants or the other's spawning. This seems a little complicated and dependent on a scraped together standard rather than actual data. So I'm thinking instead what I'll do is I'll implement biome transitions in code, which makes more sense, and decouples it from relying on the underlaying data. also prevents species and terrain from generating in say, towns on the borders of region, where certain plants or terrain features would be unnatural. Part of what makes an ecoregion unique is that geography has lead to relative isolation and evolutionary development of each region (usually thanks to mountains, rivers, and large impassible expanses like deserts).
Maybe I'll stuff it all into a giant bson file or maybe sqlite. Don't know yet.
As an entry level programmer I may not know what I'm doing, and I may be supposed to be looking for a job, but that won't stop me from procrastinating.
Data wrangling is fun. 1
1 -
So first rant, here goes weirdness, and also lengthy rant
So in my company we have the hr and accounting managed by the same person which also deals with all things employee related and she had a need for a way to extract a birthday from, what is in our country the personal identification number, things go great i get a formula that performs parts of the magic up to the point where the first digit of the number dictates the gender and century to be used when forming the full year, mind you only the last two digits of the year are in plain within the id number so i thy a number of ideas. After bashing around google sheets for a while ( i've got open office installed and formulas don't export well to the excel that person uses but google sheets does so i built it there).
First idea : make a few conditionals to check for the value so we have 1 and 2 for 19th century, 3 and 4 for 18th century , 5 and 6 for 20th so i go ahead and write my conditions and they fail, all evaluates to false, it cascades through the else variants up to the last one so i'm wondering if the "if" itself doesn't support the or operator, seems it does, next i think it's the bloody condition written wrong so i reevaluate my logic in php in a test script, it works as intended, then i think ok not the right function called, let's see the docs, docs confirm i'm doing it right but what was wrong was the way i was getting that first number, using left seems to produce a string although the base thing is a number, now i start searching how i can cast it, like you would normaly do when the data type is fried, value function appears to be the solution but it isn't working....now i'm thinking "ok so i have a value and different things to print out so let's look for a switch, maybe it can understand that" switch function found under the form of choice, i get it sorted but am stuck wondering why the heck was the if and value combination not working.
Simple answer to that : value doesn't work well with function results, a known bug listed by someone in a comment, a comment i have failed to read for about 45 minutes of trying to understand.
All in all it worked well for the person asking for it so it's nice. -
Test functions that are longer than a screen and requires a team of scientists and archeologists to try and decipher WTF they were trying to test and why they might be breaking...
Extract method -> give reasonable name -> save sanity of next dev to try and work out wtf is going on -
Once I found out an unprotected folder in my school which is used to store sensitive data.
It was open to any administrator there.
We copied the Question Papers, Edited the attendance, and Even changed the Marks.
We were able to extract photos of students from the database and retrieve stored passwords -
For future generations :
Bring back cocaine to coca cola.
Since 1904 Coca Cola no longer contains extract from cocaine leaves.
Drugs who made us.
If we live in matrix and we are simulated the general rule would be wipe bugs from the system so ex. if all of people were using cocaine cause they drink coca cola the wipe would be remove cocaine from the coca cola. That would fix the cocaine bug. Cause people in 1904 had almost no knowledge about how world looks like, they were using pigeons to deliver messages. If we bring back cocaine maybe we would also bring back those times, when everyone dropped cocaine in 1939 - 35 years old ourselves were fighting to death between each other cause of rehab.
I wonder how many of those non visual but only statistical bugs we have on this planet. Machine learning is just one of the tools we use to learn about them.1 -
Other build tools:
Here is a plugin, use it . Be done.
Scala Build Tool aka SBT:
Build your own plugin.
Everything is scala...
You can create by the way funny endless loops when using the wrong syntax - yet it might compile successfully. And then when you load the plugin, it works. Till it is evaluated - lazy evaluation for the fun.
Error messages are at best cryptic.
*If* you manage to get a working plugin and *if* it runs...
Surprise. Surprise.
You might need to parse the log output of SBT.
Another funny surprise: Log output isn't configurable. You can configure the log level. That's it.
So after a lot of pain stakingly putting together a fucking shitty plugin, you can now grind the rest of your brain with ...
sed.
Cause yeah. You can now use regex to parse an sbt build log and extract the necessary information.
:)
...
So....
Are we there?
Mwahahahhaa.
Only if you haven't forgotten to either disable colored output for SBT... Or take an extra mile with e.g. less -R.
Otherwise you have ASCII control characters in your file. :-)
After getting that shit to work, you now have finally a parseable build log.
Just took days instead of hours.
But that's SBT. :-)6 -
Teacher: "Please extract the super class"
Me: *I don´t even know how to open a project in eclipse*2 -
The end of today was extremely fun.
Imagine the surprise. I was importing a simple 8 GB big virtual machine into the Proxmox hypervizor.
First issue: It was in the Open Virtualization Format (.ova) for easy import into... most hypervizors... Not Proxmox, however.
But really, not that bad, there are ways around it. Create a blank virtual machine through the UI, scrap the disk you create, then extract the two disk QCOW2 files from the .ova file, which by itself is just a POSIX TAR archive. Then import them through the commandline.
...So I did just that. The larger of the two was about 8 GBs, the other just like... 50 MBs.
The larger imported fine. The smaller?
Color me surprised, when it created a FUCKING. 1. TB. LOGICAL. VOLUME.
...
That it then proceeded to try and fill full of zeros...
Oh yes, it was one of the fancy dynamic storage files that expand as space is needed.
...
Tomorrow, I'll have to try if I can export just the filesystem data into an individual, shrunken down, normal, plain, old disk. None of this fancy black magic shit.
...Also... I don't get why Proxmox doesn't support that... The filesystem was only a few megs big... Ugh.1 -
Some companies do not hold ethics. They believe that developers are easily available in market and can be replaced any day.
These companies talk about serving notice periods for longer term, and than if they employ some one by then.. the management so called finds flaws in u and asks to leave before completing service period.
When the developer agrees to leave they realise the developer is currently developing a project for the benefit of the same company , than they increase the reliving date again. I mean why can't they be certain on what they want?
These kind of companies only knw to exploit and extract young developers knowledge and every developer should be aware of this type of people .
Also evaluating and review a code cannot be done in few seconds without e1 knowing the project, and specially by some one who holds same experience as u . Bt in only 1 framework . So junior developers before absorbing any feedback from any evaluator, please try to understand the person's background and knowledge in the field he is evaluating u in .4 -
I'm trying to get into react for side projects but my java and backend background in general really make things tough. Let's say I have a few data manipulation functions that I want to extract to a separate service and inject it using react hooks (since that's what everyone is using nowadays apparently). I can see it being much more elegant than props, but all the examples I can find resolve around passing state here and there, not passing actual dependencies like a stateless service. Any ideas how I should solve this?7
-
PSYCHIATRY IS WRONG. IT'S A POLITICAL TOOL TO REMOVE DISSIDENCE AND PUNISH OUT OF NORMS BEHAVIOR, EXPLOIT PEOPLE AND EXTRACT WEALTH FROM THE HEALTH SYSTEM BY SELLING THEM PILLS.
WE SHOULD KILL THE PSYCHOLOGISTS.
Pics unrelated 8
8 -
So you guys know how universities can sometimes have TERRIBLE old software that hasn't been updated for years, and sometimes you want to do a specific process over and over again so you end up automating it, now, we've built a tool that automates downloading projects from the University Moodle website, and we would like to publish it for other students to use.
Problem.
The University is using SSO.
And so far we've made the application to work by observing the network connections over the Android app version in order to extract the cookie session, now imagine that we publish this little tool, and tell people to do those exact steps, of course it's impractical and misses the whole point of the tool itself for being easy to use.
So, where can I read more about SSO, how can I figure out what the University uses? And if I had to reverse engineer this, where should I start? (It goes over 4 pages and I'm not able to capture those requests to even figure out what's going on)
In short is there a guide where you take a university SSO service and build on top of it? I couldn't find anything that is helpful. -
List of things one of my Python projects needs:
- cross-platform IMA/VFD/VHD/VHDX/qcow/VMDK/IMG/DSK/others image read/extract support that doesn't need admin/root privs (so no, can't use dd or mount)
- custom DB format (for speedups when indexing files and retrieving info based on hash) and converter from previous DB format
- GUI or actually good CLI
- massive speedups
kill me now4 -
based on my previous rant about dataset I downloaded
https://devrant.com/rants/9870922/...
I filtered data from single language and removed duplicates.
The first problem I spotted are advertisements and kudos at movie start and at end in the subtitles.
The second is that some text files with subtitles don’t have extensions.
However I managed to extract text files with subtitles and it turned out there is only 2.8gb of data in my native language.
I postponed model training for now as it will be long, painful process and will try to get some nice results faster by leveraging different approach.
I figured out I can try to load this data to vector database and see if I can query it with text fragment. 2.8gb will easily fit into ram so queries should be fast.
Output I want is time of this text fragment, movie name and couple lines before and after.
It will be faster and simpler test to find out if dataset is ok.
Will try to make it this week as I don’t have much todo besides sending CVs and talking with people.2 -
I do not like it but I am forced to ask a tech question because my friend google has no idea how to solve this problem...
So, I have a pdf with a bunch of points with a number inside. I have to produce a list of numbers with X and Y coordinate of the point.
What I have tried: convert pdf to HTML and extract the position of divs / completely failed because a lot of points were distorted, mixed up, contained more numbers, etc, it's just not precise enough after conversion. 11
11 -
when I die, I want to be cremated, because I do NOT want fungi to enter my cranium and do something to my brain. It doesn't matter if it's dead or not. It once held "me", and I wholeheartedly believe that fungi can make it tick again, or extract "me" out of it to make me a part of them. Who knows what they do to people. Just imagine dying and waking up suspended in mucus while 36TET microtonal music plays.12
-
Part 2 of the .zip file saga. Staff member this morning emails me to say they can't get past the following step of my instructions.
*Screenshot showing them downloading the .zip file and not saving it anywhere, instead trying to open it*
... really starting to think that everyone in this place needs training in basic ICT tasks again. I was taught how to open and extract files from .zip when I was aged 11 in school.1 -
Stipid piece of shit nvidia cuda development kit installer.
"Yeah, you can extract and install the files wherever you want, but I'll delete BOTH directories if you do so"
Fucking 3 times I tried to install this shit untill i realized this. -
Ever tried to code a plugin for SonarQube? ... Yeah, don't do that. Documented API? Nope. Just some not-helpful-at-all-tutorial.
Largest undocumented code base I have ever seen. It's unbelievable. At some point you decide it's better to look at the code of other (undocumented) plugins to extract any API methods there.
Hep from the (otherwise pretty active) mailing list? - You wish!
The best thing is when you discover on Stack Overflow that the thing you have been trying to do for two weeks (and someone else was too, apparently) is not possible with their API.
PS: Maybe this has changed since their last version but some months ago it was every bit like this. -
UX and Game Design: "Keep It Simple" Is Stupid.
Presentation, Content, and Structure
Often when designing a UI, I stumble across blogs and articles that discuss it and focus far too much on the structure. Wordpress is terribly guilty of this and I see it fairly often in the game industry.
In web design you might use flexbox for a content-centric design and not worry too much about the layout, or css grid if structure seems important. But the broader question is why? Why is structure important and why is it wrong to focus on structure over content?
First, structure *comes* from content. Even where over many years, we've taken certain kinds of content, be they the various genres of games, or the sundry type of websites or apps, we've learned to take all the various patterns and categorize them, to extract the commonly repeating idioms into what we call structure.
But if you're experienced, and a fan of UI design in general, then I bet you that you can name a number of counter-examples, those that broke the mould, or broke the 'rules' of good design and still somehow worked. And that follows *because* structure is derived from content. This is the same reason idioms, patterns, and best practices change over time, as we codify exceptions into their "own" rules, new best practices emerge which mostly everyone follows, and then yet more exceptions break them. And so it goes.
So we see content before structure. But isn't there something to be said of style? Why yes, there is.
To read the full article, all 14k words of it, head over to medium for more:
https://swcs.medium.com/ux-and-game... 4
4 -
Hey,
I'm working on creating API for learnpress a plugin of wordpress.
I'm stuck at this type of data in database.
Can you tell me how to extract data from this type of string in php?
a:3:{s:4:"text";s:6:"Mobile";s:5:"value";s:27:"155938536720245cf2551731707";s:7:"is_true";s:3:"yes";}3 -
Use IDE to easily refactor extract methods
Notice it doesn't order input parameters by order it uses them
I don't want to manually update
I hate SVN3 -
i dont know typescript and thus hate it
why can't my fucking ide extract the type of a thing
i've no fucking clue if it's a function or not or the syntax
statically typed language gang rise up,
dynamic can be good for certain use cases and if you know what you're doing i suppose3 -
can't use IDE automated refactoring to extract method because we can't figure out the types of parameters and variables
fuck you typescript, javascript, graphql3 -
Today I learned how to read extract and parse a multi lvl XML file in Perl, only took 4 hours to make the script from 0 knowledge of Perl.
-
From a little bit heated discussion I want to extract this: One big pain in the ass is the human to computer interface. Maybe it's the natural vs. formal language divide, but there's a mismatch deeper than between object and relational models that no ORM can failingly fix.
The whole point of the discussion was on such a point where some wanted an interface more human friendly and I stubbornly insisted on the way it is simple for the computer system. Like not too much human messiness should invade machine. One argument sounded as if human words were like unicode code points which meaning doesn't depend on its representation.
That's raising red flags to me: Nonono, natural language is too messy, keep it out. This poor machine could have been so clean and well designed and we already stacked up so much entropy we still dare to call OS,..
Dunno, what's your stance? Still hoping that your shell one day will be able to process our poor standard English? Or do you think, like me, all those failed attempts show there's a gap you should not even touch?5 -
WAV is Mr. Bloat. Extract WAV 48 KHz from an mp4 video = 6 GB .wav file output.
More efficient is to just use ffmpeg. lmao. Result: 1:1, 500 MB. Couldn't be more efficient!
ffmpeg -i file.mp4 -vn -acodec mp3 output.mp32 -
Shits ridiculous
So much of my goddamn time wasted
Perfect idea really
Gradually grab all pixel locations that fit space constraints
Remember finishing this script and watching the areas populate
Purpose ? Extract shapes to feed my damn neural network for custom character recognition
So much goddamn time wasted
Bastards I hate you all !3 -
Today I started a project in which I must parse and extract some features from orders. Features can be product names, options, custom data and more and then do some validations/processing.
The (main) problem ? All I have is a String per order and of course most of the product/options have either change or been deleted.
I want to sudo rm -rf myself 😞 -
This moment when you have to read a 3k lines long Service class to plug a new process on the legacy one, and wonder if it wouldn't be just better to rewrite stuff in parallel instead of reusing and bending the old one
Everything is so tightly coupled that I would have to refacto all this and extract methods but I don't have time for that, and the chance of breaking stuff is insanely high -
Part 3
https://devrant.com/rants/9881158/...
I dropped subtitles and started extracting audio from movie, after that I use whisper to convert speech to text.
I parse srt from whisper, adjust timestamps to get >= arbitrary amount of voice seconds. I put text to vector database with timestamps and movie file name.
I query database by ex. “I don’t know” and extract first n results, after that I walk trough movies and extract parts with found text.
I normalize and merge parts into one movie.
Results are satisfying so now I decided to try to find a common dialogue that I can watch by combining multiple persons speaking from multiple movies.
Might also try to extract person from one movie and put it to other movie.2 -
!rant
Question: I am working on learning MVC/MVP/MVVM/MVPVM and I have read a bunch of articles and done some tutorials but I need some help relating it to n-tier (I think that's what they're called) systems.
I have worked on and I am used to the Presentation (ui) layer > BAL > DAL > DB pattern. How does MVC (and others) relate to the different tiers in a tiered system? I have read that model == DAL, controller == BAL, and view == presentation layer, but I have also read that MVC is meant to extract the presentation layer and that business logic and data logic should be used elsewhere. Can I get some clarity?2 -
I Used to scribble my thoughts on paper. It's haphazard yet handy. And even though I can't make corrections without crossing out or drawing arrows to transfer the reader to continuation of the thought on another page, I have this liberty to express myself and glance at a panoramic view before putting them in their final resting place –soft copy
Maybe my thought process became more efficient but I no longer need to flesh things out with ink. Database designs, implementation logic. Everything goes to a special file I create on every project for odds and ends
Until today
I have something to think about. I will miss connecting the dots if they appear in fancy fonts. I need to gradually build upon each outline, pursuing it in an exploratory manner until its possibilities are exhausted. I will draw a conclusion from their character arcs
For some reason, I see parallels between this scenario and sql vs nosql. This is one of those extreme cases where structured data storage is not sufficient. I sincerely doubt nosql should be used as a main database, but instead an intermediary for an aggregator to treat each row/record as a unique blob, extract necessary information into a sql for the actual system to work with
Sql is more sane and recommended for when you know the exact end goal but need help arriving there. Today, I'm confused and need to weigh options. I need to actually cross things out, not press the back button. It's a bit of a stretch but if this were data, it feels like what nosql would excel at3 -
Fuck! After spending the day playing shit with our servers FS to extract more space, I had to restart the servers for the changes to be applied all this because of a shitty architecture and a minor desire from the management!
The ssh server didn't start with the server, what am I supposed to do now..4 -
Has anyone worked with these 2 APIs
°Chargebee
°Billbee
I'm using chargebee for creating invoices
with a AWS lambda passing invoice data from chargebee to billbee to create an order in billbee
I'm in need of help on how to get item SKU
and on which side do i extract SKU
the SKU value is necessarily for mapping products in billbee when the order is created -
Previously, I half-assedly theorized that, given a timeline on which I'd store state mutations, with each mutation being an action taken ingame by either the player or computer, I could feasibly construct a somewhat generative narrative engine.
Basis: the system reads the current state, builds [some structure] holding possible choices, and prompts the player to take an action from those choices. The action modifies the state, and the loop begins anew, save that now it's the system "prompting itself", so to speak.
Utterly barebones and abstract as it may be, it was useful to build this concept in my head as it gave me a way to reason about what I wanted to build. But there were two problems which I had to grapple with:
- What would [some structure] even be?
- How would the computer make choices based on an instance of [some structure]?
I found myself striking the philosopher pose for long hours on the toilet, deeply pondering these questions which I couldn't help but merge into one due to the shared incognita; silly brain wanted trees but I kept figuring out that's not going to work as the relationships between symbols are sometimes but not always hierarchical. Shhh, silly brain, it's not trees.
So what is the answer?
Well, can you guess it?
Graphs, of course it's fucking graphs. Specifically, a state transition graph. It was right in my face the whole time and I couldn't see it. Well, close enough.
It's ideal as the system in question is a finite state machine with strong emphasis on finite -- the whole point is narrowing down choices, which now that I think about it, can also come down to another graph. Let me explain.
A 'symbol' or rather SIGIL is an individual in-game effect. To this FSM, it's an instruction. Sigils are used to compose actions, which you can think of as an encapsulation of some function, or better yet, an *undoable transaction* which causes some alteration in the game world.
But to form a narrative from a sequence of such transactions, and to allow the system to respond to them coherently, relationships need to be established between sigils in a manner that can be reasoned about in code. You may not realize this yet but this is both a language processing and text generation problem, so fuck me.
However, we have a big advantage in that we are not dealing with *natural* language, that is to say, each sigil is a structure from which we can extract valuable information on the nature of the state transformation applied.
This allows us to find relationships between sigils programmatically: two words are related if some comparison between the underlying structure -- and the transformation it describes -- holds true. Therefore, if we take the sigils that compose the last transformation in the timeline, fetch relationships for said sigils according to a given criteria, then eliminate all immediate relationships that are not shared between all members of the group, we end up with a new one that can be utilized as starting point to construct a reply.
More elimination of possibilities would have to be performed as this reply is constructed [*], but the point is that because the context (timeline) is itself made of previous transforms, the system *could* make such a reply coherent, or at the very least internally consistent.
Well... in the world of half-assed theory. I don't know whether I'm stupid, insane, both, pad for alignment, or this is an actual breakthrough. Maybe none of the above.
Anyway, it's another way to mentally model the problem which is very useful. New challenge would be the text generation part, extremely high chance of gibberish within existing vision; need more potty-pondering.
[*]: I'll break it into bits OK.
0. Determine intention. That's right, the reply isn't actually _fully_ generated, it's just making variations on a template. So pick a template depending on who is taking a turn and replying to who (think companion relationship score bullshit)
1. Sort the new group according to the number of connections the constituent sigils had to the context from which they were extracted, higher first.
2. Pop from the sorted group (least connections). If there are other nodes left in the group, and it doesn't connect back to any of the other nodes (sigils) up to a certain distance, then discard it and repeat. Else keep going.
2. Unshift from the sorted group (most connections). If can traverse up to another sigil in the same group, then go for it. Else derive search criteria from current context (including intention), so as to look for another sigil to concatenate. Some form of weighting would be needed here, need to think about that.
3. Decide when to stop. Probably some chance, as in the more sigils you have, the lower the chance a new one will be added maybe. Need to think about this too.
4. Send transform, loop begins anew.
And that's it. So alright brb I'm going to take a dump on the Agora.14 -
I'm using perplexity for a few days now and want to do a shout out to the assistant. My favorite function works also on the free version without ads: by holding the home button you can ask something and it automatically includes screenshot. That's handy, it understand every meme and you can extract the text of any image or document you're looking at. You can fact check statement made in a rant for example. I actually pay for it but didn't configure on my phone yet without knowing, and thus I can say, the free version assistant is very convenient. Regarding pro features review, will post something end of month. Because, its main functionality is like deep search, but everyone has that now. Is it better? We'll see.
 2
2 -
OK. We've got this tiny little pet project of mine (work related)…
I rescued it from the git archive, simply put: someone hot glued an elasticsearch scroll + document processor (processing) together.
After a lot of refactoring, I had an simple, much improved (non-parallel) Akka Worker System without an Akka topology / hierarchy.
I left out the hierarchy at first, because I didn't know Akka at all.
I've worked with a lot of process workflows, and some systems that come very close to IPC, so I wasn't completely in the dark.
Topology requires knowledge / creation of a state machine / process workflow. And at that point of time I just had... Garbage. Partially working garbage.
I finished yesterday the rewrite into several actors... Compared to before, there are 8 actors vs 2... And round about 20 classes more. Mostly since I rewrote the Receive Methods of Akka as Command DTOs... And a lot of functions needed to be seperated into layers (which where non existent before)
Since that felt more natural than the previous chaos of passing strings or other primitive types around, or in the worst case just object....
(Yes: Previously an Actor was essentially a class with one or more functions "doEverything" and maybe a few additional functions which did everything - from Rest Client to Processing)).
Then I draw the actual state machine based on everything I've written in the last weeks and thought about how to create the actual topology and where / how parallelizing might make sense.
Innocent me stumbled in the Akka Docs on Akka Typed... (Didn't know it existed, since I'm very new to Java and Akka).
Hm, that sounds an a lot like what I did. In an different way, yes. But not so different that it might be VERY hard to port to.... And I need to change (for implementation of hierarchy) a few classes....
[I should have known at this stage that my curiosity would get the best of me, but yeah. Curiosity killed the cat.]
Actually the documentation is not bad. It's just that upon reading the first more complex examples, my brain decided to go into panic state.
The've essentially combined all classes in one class in all source code examples [which makes sense more sense later], where it is fscking hard for an chaotic brain like mine to extract information....
https://doc.akka.io/docs/akka/...
The thing is: It's not hard to understand… actually very simple.
It was just my brain throwing an fuck you tantrum.
So I've opened more examples in other tabs and cross referenced what happened there and why...
Few frustrated hours later I got that part.... And the part why it's called Akka Typed. It was pretty simple....
Open the gates of hell, bloody satan that was too easy for fucks sake.
Nooooow.... I just need to port my stuff to Akka Typed.
Cause. Challenge accepted, bitch - eh brain. You throw tantrum, you work overtime. -.-
I just cannot decide wether to go FP or OOP.
Now... I'm curious wether FP is that hard... Hadn't dealt with it at large before.
Can someone please stop me... I'm far too curious again. -.- *cries*6 -
I need to write a standalone server in Java 1.7 and have it
-handle GET urls and map them to different classes/methods
-extract the query params and expose them to the method
-Can respond in JSON by serialising the POJO or a list of them
We have an existing server I think that uses JBoss but takes forever to start and uses a lot of memory.
I also wrote one before with just a (Grizzly?) HttpServer so had to manually implement the above as needed. Only needed it to do one thing so really just 1 path.
Similar situation this time but I'd prefer to not have to implement this stuff manually and need it to be a bit more flexible to extension.7 -
I am trying to extract data from the PubSub subscription and finally, once the data is extracted I want to do some transformation. Currently, it's in bytes format. I have tried multiple ways to extract the data in JSON format using custom schema it fails with an error
TypeError: __main__.MySchema() argument after ** must be a mapping, not str [while running 'Map to MySchema']
**readPubSub.py**
import apache_beam as beam
from apache_beam.options.pipeline_options import PipelineOptions
import json
import typing
class MySchema(typing.NamedTuple):
user_id:str
event_ts:str
create_ts:str
event_id:str
ifa:str
ifv:str
country:str
chip_balance:str
game:str
user_group:str
user_condition:str
device_type:str
device_model:str
user_name:str
fb_connect:bool
is_active_event:bool
event_payload:str
TOPIC_PATH = "projects/nectar-259905/topics/events"
def run(pubsub_topic):
options = PipelineOptions(
streaming=True
)
runner = 'DirectRunner'
print("I reached before pipeline")
with beam.Pipeline(runner, options=options) as pipeline:
message=(
pipeline
| "Read from Pub/Sub topic" >> beam.io.ReadFromPubSub(subscription='projects/triple-nectar-259905/subscriptions/bq_subscribe')#.with_output_types(bytes)
| 'UTF-8 bytes to string' >> beam.Map(lambda msg: msg.decode('utf-8'))
| 'Map to MySchema' >> beam.Map(lambda msg: MySchema(**msg)).with_output_types(MySchema)
| "Writing to console" >> beam.Map(print))
print("I reached after pipeline")
result = message.run()
result.wait_until_finish()
run(TOPIC_PATH)
If I use it directly below
message=(
pipeline
| "Read from Pub/Sub topic" >> beam.io.ReadFromPubSub(subscription='projects/triple-nectar-259905/subscriptions/bq_subscribe')#.with_output_types(bytes)
| 'UTF-8 bytes to string' >> beam.Map(lambda msg: msg.decode('utf-8'))
| "Writing to console" >> beam.Map(print))
I get output as
{
'user_id': '102105290400258488',
'event_ts': '2021-05-29 20:42:52.283 UTC',
'event_id': 'Game_Request_Declined',
'ifa': '6090a6c7-4422-49b5-8757-ccfdbad',
'ifv': '3fc6eb8b4d0cf096c47e2252f41',
'country': 'US',
'chip_balance': '9140',
'game': 'gru',
'user_group': '[1, 36, 529702]',
'user_condition': '[1, 36]',
'device_type': 'phone',
'device_model': 'TCL 5007Z',
'user_name': 'Minnie',
'fb_connect': True,
'event_payload': '{"competition_type":"normal","game_started_from":"result_flow_rematch","variant":"target"}',
'is_active_event': True
}
{
'user_id': '102105290400258488',
'event_ts': '2021-05-29 20:54:38.297 UTC',
'event_id': 'Decline_Game_Request',
'ifa': '6090a6c7-4422-49b5-8757-ccfdbad',
'ifv': '3fc6eb8b4d0cf096c47e2252f41',
'country': 'US',
'chip_balance': '9905',
'game': 'gru',
'user_group': '[1, 36, 529702]',
'user_condition': '[1, 36]',
'device_type': 'phone',
'device_model': 'TCL 5007Z',
'user_name': 'Minnie',
'fb_connect': True,
'event_payload': '{"competition_type":"normal","game_started_from":"result_flow_rematch","variant":"target"}',
'is_active_event': True
}
Please let me know if I m doing something wrong while parsing the data to JSON. Also, I am looking for examples to do data masking and run some SQL within Apache Beam4 -
Finish my game. It will probably be shit because the concept just wasn't that good, but I will be able to extract 2-3 useful node modules once it's finished and tested properly. A VoIP system with overlapping rooms and an efficient co-browsing system without a serverside browser like Selenium are certain. Perhaps the plugin structure as well, but that's more architecture than code.1
-
Literally wasting a good cyberpunk mix.
I'm trying to extract and replace values in a string with regex [C (POSIX)] and listening to a really good mix during this.
I'm leaving the link here in case anyone wants to check it out.
https://youtube.com/watch/... -
So for wrok i need a js lib that can parse and extract elements from a HTML response.
Been thinking about it in the back of my mind for a few days now and just realized the answer has been in front of me all along...
This is an app wrote for myself a few months ago that checks a site for updates... its built with React Native... 2
2 -
Hi guys ......here I got a new problem
I have to parse the pdf table and extract that value in each cell .
The cell may contain more than one lines I need whole text in one cell as one string.
Is there any idea....any idea may helpfull
Thank you6 -
Brain fart.
In Java and many other languages there are basic types, like char and String. So why does Java have char and String, but not a digit type?
A number is basically a series of digits. For modular arithmetic it is very useful to be able to extract the 3 in the number 1234, it's just the 3rd digit in a number.
Base 2, base 10, base anything could be supported easily too. E.g. a base 2 digit would be:
digit d = 0b2; // or 1b2, but 2b2 would be a compilation error
A number would then be some kind of string of digits.
Any thoughts on this?9 -
Whether baked or no-bake, a strawberry cheesecake is a showstopper that combines the creamy richness of the cheesecake with the sweet and slightly tangy essence of strawberries. It’s a classic dessert choice for celebrations, springtime gatherings, or any occasion where the irresistible combination of cream cheese and fresh strawberries is sure to be a crowd-pleaser.
No-Bake Strawberry Cheesecake Recipe:
Here’s a simple recipe for a no-bake strawberry cheesecake:
Ingredients For Strawberry Cheesecake:
For the Crust:
1 1/2 cups graham cracker crumbs
1/3 cup melted butter
2 tablespoons granulated sugar
Cheesecake Filling:
16 oz (450g) cream cheese, softened
1 cup powdered sugar
1 teaspoon vanilla extract
1 1/2 cups fresh strawberries, hulled and diced
2 tablespoons lemon juice
Strawberry Topping:
1 cup fresh strawberries, hulled and sliced
1/4 cup strawberry jam or preserves
Instructions For Strawberry Cheesecake:
Prepare the Crust:
In a bowl, combine graham cracker crumbs, melted butter, and granulated sugar. Mix until the crumbs are evenly coated.
Press the mixture into the bottom of a 9-inch springform pan to form an even crust. Place it in the refrigerator while you prepare the filling.
Make the Cheesecake Filling:
In a large bowl, beat the softened cream cheese until smooth.
Add powdered sugar and vanilla extract, and continue to beat until well combined.
In a blender or food processor, puree the diced strawberries with lemon juice until smooth.
Fold the strawberry puree into the cream cheese mixture until evenly incorporated.
Assemble the Cheesecake:
Pour the strawberry cream cheese filling over the chilled crust in the springform pan.
Smooth the top with a spatula and refrigerate for at least 4-6 hours, or preferably overnight, to allow the cheesecake to set.
Prepare the Strawberry Topping:
In a small saucepan, heat strawberry jam or preserves over low heat until it becomes smooth and liquid.
Allow the jam to cool slightly before spreading it over the top of the chilled cheesecake.
Arrange sliced strawberries on top for decoration.
Serve:
Carefully remove the cheesecake from the springform pan before serving. Slice and enjoy! This no-bake strawberry cheesecake is a refreshing and delightful dessert that’s perfect for warm days or when you want a fuss-free, delicious treat. 2
2 -
Biostimulants Market Expected to Reach US$ 9.6 Billion by 2033 with a 10.8% CAGR
The biostimulants market is predicted to be worth US$ 3.4 billion in 2023, and rise to US$ 9.6 billion by 2033. Demand is expected to increase at a CAGR of 10.8% over the projected period.
Due to their numerous potential applications and promising futures, biostimulants are employed in horticulture and agriculture. Growing demand for eco-friendly agricultural solutions in developing nations like China and India opens up a new market opportunity for biostimulants producers.
Since food security and public health are closely related, all parties participating in the agri-food sector have sought to enhance sustainable food production. The largest phytopharmaceutical companies in Asia Pacific and Europe have intensified their production and research activities for natural products.
Lack of restrictions related to the product's commercialization may impede the market's development and expansion during the projection period. Growth is constrained by a lack of confidence in new products, a shortage of information about high-quality products, and a lack of clear regulatory.
In the majority of markets, the data requirements for the product are often obtained from those produced from synthetic substances. Similarly, there are still no well-established endpoints for risk evaluations despite the fact that these products have been used in commerce for years.
Key Takeaways
• By 2033, the US dominates the biostimulants market, with a CAGR of 9.6%.
• The market for biostimulants increased at a 10.1% CAGR between 2017 and 2022, citing FMI's study.
• The expansion in China is anticipated to expand at an adequate CAGR of 13.3% by 2033. China’s market is likely to generate a share of US$ 1.1 billion by 2033.
• Japan's market share for biostimulants is 10.8% by 2033, with the value of US$ 490 million.
• Between 2023 and 2033, the biostimulants market is likely to increase in South Korea at 11.6% CAGR, respectively.
• The expansion in the UK is anticipated to expand at an adequate CAGR of 9.9% by 2033. The UK's market is expected to generate a share of US$ 476.2 million by 2033.
• Based on active ingredients, the acid-based segment is expected to dominate the market with a CAGR of 10.6% by 2033.
• The adoption trends of biostimulants are predicted to change due to the rising demand for organic farming. As a result, the market is anticipated to increase positively by 1.09x between 2022 and 2023.
Key Strategies in the Industry
The main factor of the market's fragmentation is the growth of local players and regional marketplaces in various regions of the world. The two regions with the biggest market activity are North America and Europe.
UPL Limited, Biostadt India Limited, Isagro SPA, Valagro SpA, and Tradecorp International are a few of the leading businesses in the biostimulants market. For the purpose of expanding their businesses, these significant firms invest in new products, product improvement, expansions, and acquisitions.
Recent Developments
• A new line of biostimulant solutions based on GoActiv Technology was launched by UPL Australia in June 2021. These products are intended to target particular crop physiological "pain points" or abiotic stresses in fruit and vegetable, vine, and tree crops.
• Isagro Group acquired Phoenix Del in 2020 in order to increase the variety of copper-based fungicides and biostimulants it offers. The goal of this acquisition was to advance technology and transform the products in its "BioSolutions" section.
Key segments
By Active Ingredient:
• Acid-Based
• Extract-Based
• Others (including Microbial Amendment, Trace Minerals, etc.)
By Crop Type:
• Row Crops
• Fruits & Vegetables
• Turfs & Ornamentals
• Other Crop Types
By Application:
• Foliar
• Soil
• Seed
By Region:
• North America
• Latin America
• Europe
• South Asia
• East Asia
• Middle East & Africa
• Oceania -
ABC Locksmith: Your Trusted "Pop a Lock" Service in Winter Haven, FL
If you find yourself locked out of your car, home, or office, the first thing that comes to mind might be the phrase, “pop a lock.” While this term is often used casually, it refers to the expert services that a professional locksmith, like ABC Locksmith, can provide. Whether you're dealing with a lockout situation or need help accessing a property quickly, ABC Locksmith is here to offer quick, reliable, and safe lock opening services in Winter Haven, FL, and surrounding areas.
What Does "Pop a Lock" Mean?
"Pop a lock" refers to a professional locksmith service where a technician uses specialized tools and techniques to unlock a door or vehicle without causing damage. Whether you’ve accidentally locked yourself out, lost your keys, or are facing a malfunctioning lock, our experienced locksmiths can help "pop a lock" efficiently and safely.
At ABC Locksmith, we provide expert lockout services for residential, automotive, and commercial clients. If you’re stuck outside, don’t waste time trying to force the door open or break the window—let our skilled locksmiths pop the lock for you without causing damage or frustration.
Why Choose ABC Locksmith to "Pop a Lock" for You?
Quick and Efficient Service
When you’re locked out of your home, car, or office, time is of the essence. ABC Locksmith offers fast response times and works efficiently to get you back inside quickly and safely. We understand how important it is to get access to your property, and we make it our priority to solve the problem as soon as possible.
24/7 Availability for Emergency Lockouts
Lockouts can happen at any time of the day or night. That's why we offer 24/7 emergency locksmith services to ensure that no matter when you need us, we’re here to help. Whether it’s early in the morning or late at night, if you need to pop a lock, we’re just a phone call away.
Experienced and Professional Technicians
At ABC Locksmith, our locksmiths are licensed, insured, and highly trained to handle all types of lockout situations. We use the latest tools and techniques to ensure that we “pop” your lock without damaging the lock or surrounding property.
Affordable, Transparent Pricing
We know how important it is to provide fair pricing. At ABC Locksmith, we offer honest and transparent pricing. Before we begin any work, we provide an upfront estimate, so you know exactly what to expect. No hidden fees—just affordable and reliable service.
Serving Winter Haven, FL, and Surrounding Areas
Located in Winter Haven, FL, ABC Locksmith proudly serves Polk County, including nearby areas like Lakeland, Auburndale, Bartow, and beyond. With our mobile locksmith service, we come directly to you, wherever you are, to solve your lockout problem on-site.
Our "Pop a Lock" Services
We provide a variety of services to help you regain access to your property, including:
Home Lockouts:
Locked out of your house? We can quickly and safely "pop a lock" and get you back inside without any damage to your locks or doors.
Car Lockouts:
If you've locked your keys inside your vehicle, our auto locksmiths can efficiently "pop a lock" and get you back on the road. We can handle most vehicle makes and models, from traditional keys to high-tech keyless entry systems.
Office or Commercial Lockouts:
Locked out of your office or commercial property? Whether it’s your storefront, warehouse, or office, we offer quick and professional lockout services to get you back inside and minimize downtime.
Broken Key Extraction:
If your key breaks off in the lock, don’t panic. We can safely extract the broken key and help you get a replacement key on the spot.
Rekeying and Lock Replacement:
If you're concerned about security, we can rekey your locks to ensure that any lost or stolen keys no longer work. We also offer lock replacements for added security.
Why You Should Call ABC Locksmith for Lockout Services
Non-Damaging Techniques
Our experienced locksmiths use non-destructive methods to pop a lock, ensuring that your door, car, or lock remains intact and fully functional after the service.
Quick and Hassle-Free Access
We aim to provide you with a hassle-free experience. Our team will arrive quickly, assess the situation, and open your lock without making you wait for hours. 1
1 -
ADWARE RECOVERY SPECIALIST ARE ALWAYS AVAILABLE TO HELP YOU GET YOUR LOST BITCOIN BACK HIRE THEM NOW
Website info: h t t p s : // adware recovery specialist. expert
WhatsApp info:+12 723 328 343
Two months ago, I found myself deeply involved in what I thought was a promising investment opportunity. I was excited and optimistic about the potential returns. Unfortunately, my enthusiasm quickly turned to despair when I discovered that the investment company I had trusted was nothing more than a sophisticated scam. Initially, everything seemed legitimate. The company was well-organized, their website looked professional, and the brokers were persuasive. I invested a significant amount—AUD 45,000 in Bitcoin—believing it was a wise decision. I was confident that my investment would yield substantial returns. However, things began to unravel when I requested a withdrawal of my profits. At first, everything seemed normal. I filled out the necessary forms and anticipated receiving my returns. Email info: Adware recovery specialist @ auctioneer. net To my dismay, the company started asking for additional fees and commissions before processing my withdrawal. I was skeptical and hesitant but eventually paid the requested amounts, hoping it would resolve the situation. Unfortunately, the demands didn’t stop there. The company continued to come up with new excuses and additional charges, trying to extract even more money from me. Despite my growing frustration, I initially tried to comply, believing it was the only way to recover my investment. However, when they started inventing even more fees and excuses, I decided enough was enough. I refused to pay any more money, standing firm on my decision not to send another dime until I received my initial investment and profits. As time went on, the broker who had initially introduced me to this company stopped responding to my messages. Despite my repeated attempts to reach out, my messages were read but never replied to. It became clear that I had been completely cut off and left in the dark. Desperate for a solution, I began searching for help online. That’s when I came across ADWARE RECOVERY SPECIALIST . I was skeptical at first, having been duped once already, but I needed to try anything to recover my investment. After reaching out to ADWARE RECOVERY SPECIALIST , I was surprised to find them professional and dedicated to their work. They assessed my situation and assured me that they could help. To my amazement, they successfully navigated the complex web of deceit and managed to retrieve my full investment. They transferred the entire amount—AUD 45,000 in Bitcoin—back to my Trust Wallet address. Their expertise and persistence were impressive, and they proved themselves to be the genuine deal in an otherwise sea of fraud. I must admit that I had significant doubts at the beginning, but ADWARE RECOVERY SPECIALIST exceeded my expectations and restored my faith in recovery services. Their success in recovering my funds was not only a financial relief but also a huge emotional boost after such a stressful ordeal. For anyone who finds themselves in a similar predicament—caught up in a fraudulent investment scheme—my strong recommendation is to contact ADWARE RECOVERY SPECIALIST. They have demonstrated their capability and reliability in recovering lost investments. Don’t hesitate to reach out to them for any recovery needs. Their expertise can make a significant difference, as they did in my case. while my experience with the fraudulent investment company was extremely distressing, the intervention by ADWARE RECOVERY SPECIALIST provided a crucial lifeline. Their professionalism and effective recovery solutions were a beacon of hope and helped me reclaim what I had almost lost. If you’re facing similar challenges, seeking their assistance could be the key to recovering your funds and moving forward from the ordeal of financial deception. -
**GENUINE BITCOIN, ETHEREUM AND USDT RECOVERY EXPERTS→HACKATHON TECH SOLUTIONS**
In the Bitcoin investment schemes, scammers frequently pose as experienced “investment managers” to exploit unsuspecting investors. These fraudsters craft elaborate schemes, presenting themselves as seasoned professionals who have made millions through cryptocurrency investments. They entice their victims with promises of substantial returns, urging them to deposit funds into what appears to be legitimate investment accounts. Initially, the schemes might seem convincing as these scammers often demonstrate fabricated success stories and provide false assurances of high returns. Victims are persuaded to make substantial deposits, believing they are making wise investments. However, the deception doesn’t end there. Once the initial deposits are made, the scammers continue to extract more money from their victims under various pretenses, such as additional fees or charges. At this point, victims might face increasing difficulties in accessing their supposed profits or even their initial investments. Communication with the so-called investment managers becomes scarce or entirely non-existent, leaving victims in a state of confusion and frustration. Recovering funds from such scams is notoriously challenging. Once money has been transferred to these fraudulent platforms, tracking and retrieving it becomes an arduous task for law enforcement agencies. These scam operations are often sophisticated, utilizing complex methods to obscure their activities and identities, making traditional recovery methods less effective. This is where specialized crypto recovery services like HACKATHON TECH SOLUTIONS play a crucial role. HACKATHON TECH SOLUTIONS emerged as a low-profile operation dedicated to combating fraudulent exchange platforms and scams targeting naive investors. Their primary mission is to trace and dismantle these fake investment schemes, helping victims reclaim their lost funds.HACKATHON TECH SOLUTIONS initially focused on identifying and targeting fraudulent exchange platforms. They employed advanced techniques to trace the identities of the scammers and the flow of stolen funds. Through their discreet and effective methods, they managed to return deposits to the victims while preserving anonymity to avoid further repercussions for those involved. Their efforts were instrumental in addressing the growing problem of cryptocurrency fraud and providing relief to many who had been deceived.Recently, HACKATHON TECH SOLUTIONS has expanded its operations to facilitate easier access for victims seeking assistance. They have established a dedicated channel through which individuals who have encountered fraudulent investment platforms can reach out and present their cases. This new approach aims to streamline the process of reporting scams and seeking recovery, making it more accessible for those affected by cryptocurrency fraud.If you or someone you know has fallen victim to a fraudulent investment platform or crypto scam, contacting HACKATHON TECH SOLUTIONS could be a crucial step toward recovering your funds. Their team of experts is equipped with the skills and knowledge necessary to handle such cases effectively. They understand the nuances of cryptocurrency fraud and are adept at navigating the complex landscape of digital asset recovery.HACKATHON TECH SOLUTIONS commitment to fighting cryptocurrency fraud and assisting victims highlights the importance of having reliable and specialized services in place. Their successful track record in recovering lost funds and their ongoing efforts to improve access to their services make them a valuable resource for anyone affected by such schemes.For those who have been deceived by fake investment managers or scam platforms, reaching out to HACKATHON TECH SOLUTIONS can provide a pathway to reclaiming lost assets and finding resolution in the aftermath of financial fraud. Their expertise and dedication to combating these scams offer hope and support to victims who might otherwise feel powerless in the face of such sophisticated deceit. if you have encountered fraudulent investment platforms or know of someone who has, do not hesitate to contact HACKATHON TECH SOLUTIONS. Their experience and capabilities in recovering funds from these scams can make a significant difference, helping to restore what has been lost and bringing justice to those who have been wronged.Reach out to HACKATHON TECH SOLUTIONS via below contact details
Email: info(@)hackathontechsolutions(.)com
Whatsapp: +31 6 47999256
Telegram: (@)hackathontechsolutions1 -
CRYPTOCURRENCY RECOVERY FIRM FOR HIRE - FUNDS RETRIEVER ENGINEER
On Mother’s Day, I became a victim of a sophisticated cryptocurrency trading scam that initially promised HUGE returns but ultimately left me unable to access my funds. The ordeal began when an admin from a Telegram group, boasting 800 members, reached out to me. The group was filled with discussions about cryptocurrency trading strategies and success stories of members profiting from signals provided by the group's leaders. Captivated by their claims of high returns and the group's apparent transparency, I decided to join. The scammers presented a 30-day investment cycle, assuring me that I could withdraw my initial investment along with any profits at the end of the period. Trusting their assurances, I deposited $58,000 in USDT to their Bitcoin address. Everything seemed to be going well, and my account balance quickly soared to $800,000. However, things took a drastic turn when I attempted to withdraw my profits. I was informed that I couldn’t access my funds until I paid a supposed “tax” on my earnings. This tax requirement had never been mentioned during my initial investment discussions. When I pressed for clarification, I received vague responses and delays, making it clear that the scammers were stalling, hoping to extract more money from me. Despite my persistent efforts to reach out to them, the group disappeared, leaving me with no means of contact. It became painfully obvious that I had been scammed. Feeling lost and desperate, I began searching for ways to recover my lost funds. After extensive research, I came across FUNDS RETRIEVER ENGINEER, a service dedicated to helping victims of online scams. Their team was not only knowledgeable but also compassionate, guiding me through the recovery process step by step. I gathered the necessary documentation and details about my case. They worked tirelessly to trace my funds and liaised with financial institutions on my behalf. To my immense relief, they successfully helped me recover a significant portion of my funds. This taught me a crucial lesson about the importance of conducting thorough research regarding investment opportunities. I learned to be skeptical of promises that seemed too good to be true and to verify the legitimacy of any platform before investing. Thanks toFUNDS RETRIEVER ENGINEER, I was able to regain my financial stability and approach future investments with newfound caution. I now advocate for others to be informed, sharing my story to help prevent others from falling victim to similar scams.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
Linux: sudo apt-get install IDE dev-libs etc
Windows: install wxMSW, extract compressed binaries, set environment variables, set preprocessor/project settings in VS2017, set search directories, etc.
Why is it so ANNOYING to set up a simple GUI development library for C++ on Windows? -
HOW TO RECOVER STOLEN CRYPTOCURRENCY CONTACT ADRIAN LAMO HACKER
In early 2024, I found myself entangled in a high-stakes forex trading scheme that promised substantial returns but ended up being a disastrous ordeal. Despite my initial confidence, the investment spiraled into a €400,000 loss, exacerbated by constant fee demands and manipulative tactics designed to keep me pouring money into a sinking ship. The sense of desperation and helplessness was overwhelming, leaving me feeling as if I had lost control of my financial future. After exhausting all personal avenues and facing mounting stress, I began searching for professional help. That's when I came across ADRIAN LAMO HACKER. Their reputation for tackling complex fraud cases caught my attention, and I decided to reach out for assistance. From the initial consultation, I was impressed by their professionalism and deep understanding of the financial fraud landscape. The key figures in my case were Alex Matthews and Sarah Johnson from ADRIAN LAMO HACKER. Alex, the senior recovery specialist, took charge of my case with a meticulous approach, while Sarah, the legal expert, provided invaluable advice on navigating the legal aspects. Their combined expertise gave me a renewed sense of hope. Alex started by conducting a comprehensive investigation into the fraudulent forex scheme. His thorough examination uncovered several crucial details about the operations of the scam, including the identities of key players and the mechanisms they used to extract funds. Sarah, on the other hand, focused on the legal ramifications, preparing the necessary documentation and strategies to challenge the fraudulent entities. The efficiency of ADRIAN LAMO HACKER was astounding. Within just 28 hours, ADRIAN LAMO HACKER managed to recover a significant portion of my lost funds. Their ability to act swiftly and decisively was a testament to their dedication and skill. The process involved coordinating with various financial institutions and legal entities, and their seamless execution made a stressful situation much more manageable. The recovery of €400,000 was a remarkable achievement and a profound relief. It not only alleviated my immediate financial concerns but also restored my faith in the possibility of justice. Alex and Sarah's relentless efforts and expert handling of the case were instrumental in achieving this outcome. I am sharing my experience to offer hope and guidance to others who may find themselves in similar situations. Financial fraud can be devastating, but professional recovery services like ADRIAN LAMO HACKER can make a significant difference. Their expertise in navigating the complexities of fraud recovery and their commitment to client success can turn a seemingly hopeless situation into a triumphant recovery. For anyone facing similar challenges, I highly recommend reaching out to ADRIAN LAMO HACKER via Email: Adrianlamo @ consultant . com / WhatsApp: +1 (909) 739‑0269
TELEGRAM Username: @ADRIANLAMOHACKERTECH Their proven track record and dedicated team can provide the support and results needed to reclaim lost funds and regain control of your financial future. -
Anyone know any good alternatives for WinImage? People online say to use ISO manipulation tools, but I need to extract files from a set of 232 floppy images.
-
SAFELY RECOVER LOST OR STOLEN BITCOIN AND OTHER DIGITAL ASSETS WITH THE HELP OF CYBER CONSTABLE INTELLIGENCE
I was convinced to invest in a cryptocurrency platform by a friend I met on Tinder. Her name was Annie, and at first, she seemed trustworthy. I was drawn in by the allure of high returns and the excitement of the crypto world. Everything went smoothly for a while; my initial investments seemed to pay off, and I felt like I was on the right track. However, when I decided it was time to withdraw some of my earnings, the nightmare began. The platform required me to deposit more money before I could access my funds. I was taken aback, but I thought perhaps this was a standard practice. After all, they claimed it was necessary for “security purposes.” As I complied, hoping it was just a minor hurdle, I was soon inundated with an array of unending fees and taxes. Every time I inquired about my withdrawal, there was a new reason why I couldn’t take out my money. They claimed I owed taxes for various “regulatory reasons,” each more dubious than the last. I felt trapped, and with each passing day, my frustration grew. I began to realize that I was caught in a web of deceit, and the more I tried to extract myself, the tighter it became. Desperate for help, I turned to local authorities, only to find that since all my payments had been made in cryptocurrencies, they were unable to assist me. It was a sinking feeling; I was alone, feeling like I’d been scammed and had nowhere to turn. I spent countless hours online, researching recovery options and sharing my story in forums, hoping someone would offer a glimmer of hope. Finally, I came across a service called Cyber Constable Intelligence. Skeptical but out of options, I decided to reach out to them. I provided my details and explained my situation. To my surprise, they responded quickly and were very professional throughout the process. Within just a week, they managed to trace my funds and initiate the recovery process. I couldn’t believe my eyes when I saw the funds reappear in my account. It was a surreal moment, one that made me feel a mix of relief and disbelief. I realized how crucial it is to be cautious in the world of online investments. If you find yourself in a similar situation, I highly recommend seeking help from experts like Cyber Constable Intelligence. They understand the ins and outs of these scams and can help you navigate the complex recovery process. You don’t have to face this battle alone.
Here's Their info below
What Sapp Info: 1. (2. 5. 2. ) 3. 7. 8. (7. 6. 1. 1.) -
BEST ETHEREUM RECOVERY SERVICE- CONSULT SALVAGE ASSET RECOVERY
At first, these scammers were incredibly smooth. They made everything appear legitimate, acting as though my money was safe with them. They even went so far as to show me how to withdraw funds, building an illusion of trust. It seemed like a legitimate platform, and they were very convincing. I believed I was dealing with professionals, and for a while, things seemed fine. But as soon as they realized that they wouldn’t be able to extract another penny from me, they stopped responding to my calls and emails. The once friendly customer service turned cold, and all communication ceased. They blocked me on all channels, leaving me stranded and unable to access my funds.These scammers know exactly how to play their victims, making it seem like they’re here to help, only to pull the rug out from under you when they’ve gotten what they wanted. The whole situation felt like a trap, designed to manipulate and steal from people like myself. It’s a classic scam, and I’m sure many others have fallen for it. If my money had been returned to me, I would have taken down this warning, but unfortunately, what I experienced was straight-up theft. They took my funds and left me with nothing but frustration.I felt completely helpless, but just when I thought there was no chance of getting my money back, I stumbled upon Salvage Asset Recovery. At first, I was skeptical, having already been burned by a fake platform, but Salvage Asset Recovery turned out to be the lifeline I desperately needed. They guided me through the entire process of recovering my funds, patiently answering my questions and keeping me informed every step of the way. After a lot of effort and persistence, I was able to successfully withdraw my money back into my bank account. It felt like a miracle, and I could finally breathe again.Salvage Asset Recovery truly went above and beyond, offering professional assistance when I was at my lowest. They were the difference between losing everything and getting my funds back. I want to share my story as a warning to others about the dangers of online scams, especially fake platforms that appear legitimate at first. It’s crucial to be cautious and do thorough research before trusting any online investment opportunity.At the same time, I cannot recommend Salvage Asset Recovery enough. They not only helped me recover my funds but also showed genuine care and expertise in handling such situations. If you ever find yourself in a similar position, don’t lose hope there are people out there who can help you get your money back. Send a DM to Salvage Asset Recovery via below contact details.
WhatsApp-----.+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
CRYPTOCURRENCY RECOVERY EXPERT DIGITAL HACK RECOVERY
Fraudsters often use sophisticated tactics to scam people, pretending to be expert advisors in online trading. I experienced this firsthand with my trading account CR7(5673892) MT5. Initially, everything seemed legitimate, with promises of significant returns through expert advice. The fraudsters presented themselves as experienced traders, offering guidance on when to buy and sell, and their advice appeared to yield some profits at the beginning. This led me to believe I was making a sound investment.However, after a few successful trades, things took a worrying turn. The so-called account manager began pressuring me to invest even more money, telling me that without additional funds, I would risk losing everything. They encouraged me to deposit money into my account, making false claims that without a larger margin, I would miss out on potential profits. They even went as far as advising me to take out a loan on my credit card to fund the investments, capitalizing on my growing anxiety and desire to protect my initial investments.At this point, I realized something was wrong. The fraudsters continued to pressure me, constantly finding new ways to extract more money from me. They manipulated the situation, making it seem like my lack of additional funds would result in losing my gains and potential profits. But when I stopped investing, I saw that the balance of my account had become zero. It was as if all the money I had invested had disappeared without a trace. This left me frustrated, feeling hopeless, and unsure of what to do next.In my state of confusion and frustration, I reached out to a trusted colleague for advice. They recommended that I contact Digital Hack Recovery, a service known for its expertise in recovering funds from online scams. I decided to give it a try, though I was still unsure whether I could recover anything from the fraudulent scheme.With the help of Digital Hack Recovery, I was able to trace the funds and initiate a recovery process. Their team worked diligently, using their experience and tools to track down the scammers and recover a significant portion of the money I had lost. Thanks to their expertise and commitment, I was able to resolve the situation and regain some of the funds that had been stolen from me.This experience has taught me the importance of being cautious when dealing with online investments and the value of seeking professional help in situations like these. The recovery process was not easy, but with the right support, I was able to regain control and learn from the ordeal. Reach out to them through their contact info bellow⁚
Website; https : // digital hack recovery . com
WhatsApp⁚ +19152151930
Email; digital hack recovery @ techie . com 7
7 -
HOW CAN I RECOVER MY STOLEN $20,000 HIRE ADWARE RECOVERY SPECIALIST
WhatsApp info:+12723 328 343
Hello, my name is Janet, and I’m reaching out from the windy city of Chicago to share a whirlwind experience I had with a Bitcoin trading company I discovered on Facebook. Initially captivated by the promise of easy profits, my journey quickly turned into a cautionary tale that I hope will serve as a beacon of caution for others. the investment opportunity appeared legitimate, with a seemingly trustworthy advisor from Taiwan who engaged me in enthusiastic conversations about the potential gains. Her confidence was contagious, and after just a few days of back-and-forth, I found myself in over my head—I invested a staggering $390,000 USD on the platform, blithely optimistic about the returns I would see. however, my excitement hit a wall when I attempted to make my very first withdrawal. To my shock, I was confronted with an unexpected fee that I found utterly unreasonable. I hesitated, but feeling cornered by the situation, I paid the fee under the impression that I would soon see my funds released. Unfortunately, that was just the beginning. despite the payment, my withdrawal request was still denied. Struggling with disbelief and frustration, I couldn’t help but find the entire ordeal absurd. Financially stressed, I realized I had to take action to get my money back. in my efforts to reclaim what I had lost, I turned to Google and found a glimmer of hope—a recovery expert known as ADWARE RECOVERY SPECIALIST. There, I stumbled upon numerous testimonials from others who had endured similar scams and had their funds successfully retrieved. Inspired by their stories, I decided to reach out to the ADWARE team to see if they could help me extract myself from this financial disaster. I explained my situation in detail, providing them with all the information I had from my ill-fated investment journey. To my relief, they took my case seriously and went to work swiftly on my behalf. the professionals at ADWARE RECOVERY SPECIALIST proved to be everything the testimonials proclaimed. Email info: Adwarerecoveryspecialist@ auctioneer. net Their expertise and determination paid off, and, after a comprehensive recovery process, they managed to secure the return of my funds. I can't express the immense relief and gratitude I felt when I saw my money safely back in my account. if you find yourself tangled in a situation resembling mine — feel hopeful and reach out to professionals like ADWARE RECOVERY SPECIALIST. Don’t hesitate; they can be a powerful ally in the relentless battle against crypto scams. Trust me, it’s worth it! 2
2 -
How to Recover Cryptocurrency in 2025 (Hire A Hacker) - Captain WebGenesis
Can stolen crypto be recovered? Yes, Captain WebGenesis possesses the necessary expertise in digital forensics to potentially trace and track down your stolen cryptocurrency. With years of experience and a proven track record of success, Captain WebGenesis has developed a comprehensive approach to cryptocurrency recovery
The comprehensive recovery process involves:
1. Initial Assessment: Captain WebGenesis will conduct a thorough review of the incident to determine the scope of the theft and identify potential leads.
2. Digital Forensic Analysis: He will then utilize advanced digital forensic tools to extract and analyze transaction data, network logs, and other relevant information to trace the stolen cryptocurrency.
3. Network Analysis: The team will meticulously examine the blockchain network to identify suspicious transactions, wallets, and patterns that may lead to the recovery of your stolen assets.
4. Collaboration with Exchanges and Authorities: Captain WebGenesis works closely with cryptocurrency exchanges, law enforcement agencies, and other relevant parties to freeze suspicious accounts, trace the flow of funds, and facilitate the recovery of your stolen cryptocurrency.
5. Recovery and Return: Once the stolen cryptocurrency is traced and tracked down, Captain WebGenesis will work to recover the assets and return them to their rightful owner.
Contact him now on: Captainwebgenesis@hackermail. com.1 -
RAPID DIGITAL RECOVERY IS THE SECURE RELIABLE BITCOIN RECTORATION SERVICES
At first, these scammers were incredibly smooth. They made everything appear legitimate, acting as though my money was safe with them. They even went so far as to show me how to withdraw funds, building an illusion of trust. It seemed like a legitimate platform, and they were very convincing. I believed I was dealing with professionals, and for a while, things seemed fine. But as soon as they realized that they wouldn’t be able to extract another penny from me, they stopped responding to my calls and emails. The once friendly customer service turned cold, and all communication ceased. They blocked me on all channels, leaving me stranded and unable to access my funds. These scammers know exactly how to play their victims, making it seem like they’re here to help, only to pull the rug out from under you when they’ve gotten what they wanted. The whole situation felt like a trap, designed to manipulate and steal from people like myself. It’s a classic scam, and I’m sure many others have fallen for it. If my money had been returned to me, I would have taken down this warning, but unfortunately, what I experienced was straight-up theft. They took my funds and left me with nothing but frustration. However, in the midst of this hopeless situation, I found a lifeline in Rapid Digital Recovery. I had almost given up hope of recovering my money, but Rapid Digital Recovery came through when I thought all was lost. They were able to guide me through the process of recovering my funds, and after much effort, I successfully withdrew my money back into my bank account. It was a relief to know that not all hope was lost. I want to spread the word about the importance of being cautious online and to warn others about this fake platform. At the same time, I can’t recommend Rapid Digital Recovery enough. They helped me when I had nowhere else to turn, and they played a vital role in getting my money back. I’m sharing my story not only to warn others about the scammers but also to help promote the services of those like Rapid Digital Recovery who genuinely care about helping people in these situations.
INFO
What sapp Info: +1 41 4 80 7 14 85
Email INFO: rap iddi gita lrecov ery @ exe cs. com 5
5 -
I live in an unstable region, so I'm always ready for surprise curfews or my aunt dropping by uninvited to borrow some cooking oil. To protect my future from both, I swept $530,000 under the floor in Bitcoin- my emergency parachute.
Well, things went downhill. Protesters filled the streets like a rowdy rave, with pepper spray in place of glow sticks. In the chaos, security personnel took my laptop and everything that wasn't bolted down. That's where I store the keys to my Bitcoin wallet. When I say I swallowed a brick, I am not kidding.
I pictured myself telling my future self, who lived under a tarp, how I used to have half a million dollars but lost it since I had forgotten to encrypt my drive. "Great job, Past Me," I would be saying while heating canned beans over a candle.
But fate, or possibly my guardian angel who was finally done laughing at me, intervened. During a hushed meeting with a journalist friend (we whispered like we were plotting an espionage thriller), he mentioned Tech Cyber Force Recovery. These folks were not just tech geniuses; they practically wore digital capes.
I phoned, and the reassuring voice I received was so reassuring, I almost asked them to fix my love life too. They labored in their homes with the frenzy of an explosives specialist defusing a bomb. They constructed my wallet information from recovery fragments I barely remember creating. It was like magic shows where magicians extract bills from a hat, except the hat has been confiscated by the authorities.
Thirteen days passed, and I received the call. My money had been returned. I was so relieved that I hugged my aunt, who naturally took the chance to request additional cooking oil.
Tech Cyber Force Recovery did not just save my Bitcoin; they saved my future. And they gave me a newfound respect for proper backups and encryption. If you are in a tricky spot or just want to avoid awkward family requests during every political crisis, call them. They are the real deal and possibly part wizard, part therapist.
CALL OR WHATSAPP THEM THOUGH
+.1.5.6.1.7.2.6.3.6.9.71 -
ComPDFKit Solutions
For text extraction technology, ComPDFKit offers the following two solutions that effectively address text extraction for all types of PDF files. For documents containing only text information, our non-intelligent solution can suffice. But for more complex documents and image-based ones, ComPDFKit Document AI offers higher accuracy in text extraction. To learn about the accuracy of ComPDFKit's information extraction, see this article.
1. Algorithm: X-Y Cut Recursion Projection Method
The X-Y Cut Recursion Projection Method is a top-down page segmentation technique that decomposes a document image into rectangular blocks. It employs a recursive approach by projecting along both the X and Y axes to segment a PDF into independent rectangles, facilitating the extraction of textual components. ComPDFKit utilizes this method for efficient text separation and structural organization, including rows, paragraphs, and columns, to retrieve characters, words, lines, and paragraphs from the document.
The advantage of the X-Y Cut Recursion Projection Method is its speed, making it suitable for simple, structured, non-image-based PDF documents. However, for complex, unstructured PDFs, there might be recognition errors or omissions.
2. ComPDFKit Document AI
Document AI is an intelligent text extraction solution supporting all types of PDF files, including image-based. It uses artificial intelligence-based methods for document recognition and analysis to extract textual information from PDF documents (as well as images, tables, etc.).
- PDF Recognition and Analysis: This involves using deep learning models to recognize and analyze PDF documents, extracting elements like text, images, and tables while retaining their position, size, style, etc. ComPDFKit owns well-trained AI models to accomplish this process.
- Image Pre-processing: This process involves improving the quality and clarity of low-quality images in PDF documents, enhancing subsequent recognition and analysis. ComPDFKit employs multiple image processing techniques, such as image sharpening enhancement, noise reduction, document trimming and straightening, and stamp detection.
- OCR (Optical Character Recognition): OCR technology has a wide range of application scenarios such as license plate recognition, bank card information extraction, identity document (ID card) information recognition, train ticket information detection, etc. ComPDFKit supports recognition in dozens of languages. With extensively trained model zoo, it can accurately detect and recognize text in documents and analyze document structure. 1
1 -
Two months ago, I found myself deeply involved in what I thought was a promising investment opportunity. I was excited and optimistic about the potential returns. Unfortunately, my enthusiasm quickly turned to despair when I discovered that the investment company I had trusted was nothing more than a sophisticated scam. Initially, everything seemed legitimate. The company was well-organized, its website looked professional, and the brokers were persuasive. I invested a significant amount—AUD 45,000 in Bitcoin—believing it was a wise decision. I was confident that my investment would yield substantial returns. However, things began to unravel when I requested a withdrawal of my profits. At first, everything seemed normal. I filled out the necessary forms and anticipated receiving my returns. To my dismay, the company started asking for additional fees and commissions before processing my withdrawal. I was skeptical and hesitant but eventually paid the requested amounts, hoping it would resolve the situation. Unfortunately, the demands didn’t stop there. The company continued to come up with new excuses and additional charges, trying to extract even more money from me. Despite my growing frustration, I initially tried to comply, believing it was the only way to recover my investment. However, when they started inventing even more fees and excuses, I decided enough was enough. I refused to pay any more money, standing firm on my decision not to send another dime until I received my initial investment and profits. As time went on, the broker who had initially introduced me to this company stopped responding to my messages. Despite my repeated attempts to reach out, my messages were read but never replied to. It became clear that I had been completely cut off and left in the dark.
 2
2 -
I have table assets with field person of contact and table contacts with all fields related where I want to extract Join the [First Name] and [Last Name] and Capture as [Person of Contact] from [ID] related to each customer I want to list the person of contacts! I am so new into this world teach me <SQL>
-
Maybe I am picky, but:
Some people made a "FileStorage" API where in the open method you have flags like READ, WRITE, APPEND... And they made it like when you check WRITE the API opens/overwites to an empty file.
And when someon made a github Issue about this behaviour, they flagged it as a feature request. I'm so anoyed by not being able to overwite my data, thats just rude. Like should I use an file storage API to overwrite data like this:
0- Save file inner structure (you can't extract it from the API)
1- Open the file, parse the structure
2- Find file to overwrite
3- Save all the mess again
4- write your own API
5- sigh4 -
Friend showed me some video about some researchers being able to extract fingerprints of people from their pictures (like when you pose with the peace sign). Thinking about it, it's quite possible with the clarity of today's ordinary phone cameras and image enhancement. Thoughts about this?2
-
RECLAIM STOLEN CRYPTO REVIEW THROUGH RAPID DIGITAL RECOVERY
As the director of a small nonprofit dedicated to supporting underprivileged youth, I never anticipated facing a cryptocurrency crisis. Yet, I found myself grappling with a misconfigured smart contract that had locked away $85,000 in Bitcoin donations funds crucial for educational programs benefiting hundreds of children. A single error in the contract’s code rendered these donations irretrievable, jeopardizing our mission and the trust of our donors. In this moment of despair, RAPID DIGITAL RECOVERY emerged as saviors , not only salvaging our funds but also restoring our faith in expert intervention. The crisis began when a generous donor contributed Bitcoin through a custom smart contract designed to enhance transparency for charitable gifts. Unfortunately, a misconfiguration in the contract’s parameters locked the funds indefinitely. As panic set in, multiple developers reviewed the code and delivered the grim verdict: the cryptocurrency’s immutability meant the assets were likely lost forever. With donor frustration mounting and our projects stalled, I turned to online forums, where I discovered numerous testimonials praising RAPID DIGITAL RECOVERY’s expertise in resolving cryptocurrency emergencies. From our first consultation, RAPID DIGITAL RECOVERY distinguished themselves with their transparency and technical mastery. Their team patiently guided me through their process: auditing the contract’s code, identifying the flaw, and engineering a legal workaround to extract the funds without compromising the cryptocurrency’s integrity. They explained complex concepts in layman’s terms, ensuring I understood each step. Their commitment to urgency was particularly impressive; they recognized that these funds were not just “assets” but lifelines for vulnerable communities. Within 48 hours, their experts executed a meticulously planned recovery operation, employing advanced cryptographic techniques to bypass the contract’s faulty logic. The funds were safely redirected to a secure wallet, honoring the donor’s intent. Remarkably, RAPID DIGITAL RECOVERY even waived a portion of their fee upon learning about our nonprofit status, underscoring their dedication to philanthropic causes. This has taught me that the risks of cryptocurrency can be surmountable with the right expertise. RAPID DIGITAL RECOVERY isn’t just a service; they are guardians in cryptocurrency age . Their blend of technical brilliance and ethical integrity make them the best. For anyone facing cryptocurrency loss or Bitcoin lost due to scams or errors, I wholeheartedly recommend their services. They transformed our potential disaster into a testament of resilience.
CONTACT INFO BELOW:
WhatsApp: +1 4 14 80 71 4 85
Email: rapid digital recovery (@) execs. com2

