Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "hacking a hack."
-
Friend: So you're a programmer? You must be good in hacking WiFis and sht.
Me: Uhm..
Friend: Can you hack my PayPal account using HTML?
Me: Say no more.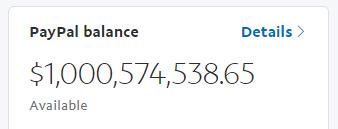 13
13 -
I was in school and I got bored. I opened two command prompts and did what any scammer would do.
I went to the root of the drive and did a tree. The other window is pinging google infinitely.
After a few seconds, I hear a kid say "Are you hacking the pentagon?". That guy also asked me to hack the Google Play Store. He shall forever think I'm a hacker. 34
34 -
An incident which made a Security Researcher cry
--------------------------------------------------------
I was working on my laptop finishing up my code while waiting for the flight which was late . Meanwhile two guys (I'm gonna call them Fellas) in black suit and shades came to me
Fella : Sir you have to come with us .
Me : *goes along with them*
Fella : Sir please proceed *points towards the door . The room has a round table with some guys discussing something *
Fella 1 : Your passport please
Me : *Hands over the passport*
Fella 1 : Where are you traveling to sir?
Me : India
Fella 1 : Put your laptop in the desk sir.
Me : Sure thing
Fella 2 : What were you doing there? *Taps the power button*
Me : Just finishing up my work .
Fella 1 : Or hacking our systems?
Me : Seriously?
Fella 2 : The password please .
Me : Here you go
*5 minutes have passed and he still can't figure out how to use the machine*
Fella 2 : Which Windows is this?
Me : It's Linux
Fella 1 : So you are a hacker .
Me : Nope
Fella 1 : You are using Linux
Me : Does it matters?
Fella 1 : Where do you work?
Me : *I won't mention here but I told him*
Fella 2 : So what do you do there?
Me : I'm a Security Researcher
Fella 1 : What's your work?
Me : I find security holes in their systems .
Fella 1 : That means you are a hacker .
Me : Not at all .
Fella 2 : But they do the same and they use Linux .
Me : You can call me one .
*After 15 minutes of doo-laa-baa-dee-doo-ra-ba-doo amongst them I dunno what they were talking , they shutdown the computer and handed over it to me*
Fella 2 - So you are somewhat like a hacker .
Me - *A bit frustrated* Yes.
##And now the glorious question appeared like an angel from river ##
Can you hack Facebook?
Me - 😭😭😭28 -
0. Plan before you code. Document everything. You won't remember either your idea or those clever implementations next week (or next month, or next year...).
1. Don't hack your way through, unless that's what you intend to do. Name your variables, functions etc. neatly: autocomplete exists!
Protip: Sometimes you want to check a quick language feature or a piece of code from one of your modules. Resist the urge to quickly hack in the test into your actual project. Maintain a separate file where you can quickly type in and check what you're looking for without hacking on your project (For example, in Python, you can open a new terminal or IDLE window for those quick tests).
2. Keep a quiet environment where you can focus. Recommend listening to something while coding (my latest fad is on asoftmurmur.com). Don't let anything distract you and throw your contextual awareness out of whack.
3. Rubber ducks work. Really. Talking out a complex piece of logic, or that regex or SQL query aids your mind greatly in grasping the concept and clearing the idea. Bounce off code and ideas with a friend or colleague to catch errors and oversights faster. Read more here: https://en.wikipedia.org/wiki/...
4. Since everyone else is saying this (and because it merits saying), USE VERSION CONTROL. Singular most important thing to software development aside from planning and documenting.
5. Remember to flout all of the above once in a while and just make a mess of a project where you have fun throwing everything around all over the place. You'll make mistakes that you never thought were possible by someone of your caliber :) That's how you learn.
Have fun, keep learning!3 -
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
Anyone know this bitch hacker 127.0.0.1 story?
WORST HACKERS OF ALL TIME
CONTINUED IN THE COMMENTS BECUASE IT IS SO LONG...
TLdr bitch hacker hacks himself by localhost
bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> why do you kick me
<bitchchecker> can’t you discus normally
<bitchchecker> answer!
<Elch> we didn’t kick you
<Elch> you had a ping timeout: * bitchchecker (~java@euirc-a97f9137.dip.t-dialin.net) Quit (Ping timeout#)
<bitchchecker> what ping man
<bitchchecker> the timing of my pc is right
<bitchchecker> i even have dst
<bitchchecker> you banned me
<bitchchecker> amit it you son of a bitch
<HopperHunter|afk> LOL
<HopperHunter|afk> shit you’re stupid, DST^^
<bitchchecker> shut your mouth WE HAVE DST!
<bitchchecker> for two weaks already
<bitchchecker> when you start your pc there is a message from windows that DST is applied.
<Elch> You’re a real computer expert
<bitchchecker> shut up i hack you
<Elch> ok, i’m quiet, hope you don’t show us how good a hacker you are
<bitchchecker> tell me your network number man then you’re dead
<Elch> Eh, it’s 129.0.0.1
<Elch> or maybe 127.0.0.1
<Elch> yes exactly that’s it: 127.0.0.1 I’m waiting for you great attack
<bitchchecker> in five minutes your hard drive is deleted
<Elch> Now I’m frightened
<bitchchecker> shut up you’ll be gone
<bitchchecker> i have a program where i enter your ip and you’re dead
<bitchchecker> say goodbye
<Elch> to whom?
<bitchchecker> to you man
<bitchchecker> buy buy
<Elch> I’m shivering thinking about such great Hack0rs like you
bitchchecker (~java@euirc-61a2169c.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> dude be happy my pc crashed otherwise you’d be gone
<Metanot> lol
<Elch> bitchchecker: Then try hacking me again… I still have the same IP: 127.0.0.1
<bitchchecker> you’re so stupid man
<bitchchecker> say buy buy
<Metanot> ah, [Please control your cussing] off
<bitchchecker> buy buy elch
bitchchecker (~java@euirc-b5cd558e.dip.t-dialin.net) Quit (Ping timeout#)
bitchchecker (~java@euirc-9ff3c180.dip.t-dialin.net) has joined #stopHipHop
<bitchchecker> elch you son of a bitch
<Metanot> bitchchecker how old are you?
<Elch> What’s up bitchchecker?
<bitchchecker> you have a frie wal
<bitchchecker> fire wall
<Elch> maybe, i don’t know
<bitchchecker> i’m 26
<Metanot> such behaviour with 26?
<Elch> how did you find out that I have a firewall?
<Metanot> tststs this is not very nice missy
<bitchchecker> because your gay fire wall directed my turn off signal back to me
<bitchchecker> be a man turn that shit off
<Elch> cool, didn’t know this was possible.
<bitchchecker> thn my virus destroys your pc man
<Metanot> are you hacking yourselves?
<Elch> yes bitchchecker is trying to hack me
<Metanot> he bitchchecker if you’re a hacker you have to get around a firewall even i can do that
<bitchchecker> yes man i hack the elch but the sucker has a fire wall the
<Metanot> what firewall do you have?
<bitchchecker> like a girl
<Metanot> firewall is normal a normal hacker has to be able to get past it…you girl
<He> Bitch give yourself a jackson and chill you’re letting them provoce you and give those little girls new material all the time
<bitchchecker> turn the firewall off then i send you a virus [Please control your cussing]er
<Elch> Noo
<Metanot> he bitchchecker why turn it off, you should turn it off
<bitchchecker> you’re afraid
<bitchchecker> i don’t wanna hack like this if he hides like a girl behind a fire wall
<bitchchecker> elch turn off your shit wall!
<Metanot> i wanted to say something about this, do you know the definition of hacking??? if he turns of the firewall that’s an invitation and that has nothing to do with hacking
<bitchchecker> shut up
<Metanot> lol
<bitchchecker> my grandma surfs with fire wall
<bitchchecker> and you suckers think you’re cool and don’t dare going into the internet without a fire wall
<Elch> bitchchecker, a collegue showed me how to turn the firewall off. Now you can try again
<Metanot> bitchhacker can’t hack
<Black<TdV>> nice play on words
<bitchchecker> wort man
<Elch> bitchchecker: I’m still waiting for your attack!
<Metanot> how many times again he is no hacker
<bitchchecker> man do you want a virus
<bitchchecker> tell me your ip and it deletes your hard drive
<Metanot> lol ne give it up i’m a hacker myself and i know how hackers behave and i can tell you 100.00% you’re no hacker..29 -
*Facebook Hackers follow the Rules*
(real story)
TL;DR: sorry, not available, can't do spoilers
One night I was with a group of friends out at a pub. A guy and his girlfriend show up, I didn't know them but they were my friend's friends.
The girl kept bragging the whole time about his boyfriend being a professional programmer, trying to remind it to everybody whenever possible (don't ask me why!).
So, after a while, the discussion moves towards "suspect Facebook activities" and the guy starts saying that he can hack Facebook.
- "What do you mean?", I ask.
- "Hacking into other people's accounts, even with 2 factor authentication. I did it a lot of times"
- "Wait, and they don't notice?"
- "Of course not! ^_^ He's a hacker", the girl replies.
Ok, time to do a coming out.
- "Hey, I'm a developer myself. Can you give me an idea of what you did in technical terms? Did you find a vulnerability? Used a virus? Maybe a keylogger?"
- "No... Uh... Well... The secret is to read the terms of service"
- "What?"
- "Yes... yes it's all in the facebook terms of service..."
- "Uhm, I'm not really sure I'm following. Could you prove it by hacking my Facebook account? I'm giving you the permission".
In less than a minute the discussion flew completely away and they never mentioned computers again.
😂😂8 -
This should probably be labeled a meme, but I'm going to actually rant about this meme.
People use the term hacker way too frequently. Solving your trashy fucking "Pa$$w0rd123" password and getting access to your Spotify account isn't hacking.
Same douchewaffle probably thinks you could hack a Facebook account in 30 seconds. I fucking hate the way movies have portrayed hacking and created a dramatized bullshit idea for people to believe is real. 21
21 -
So, as everyone knows on here by now (or, a lot of ranters), I am a fervid privacy person.
Appearantly a new surveillance law in my country is about to extend mass surveillance/hacking a lot. So here a rundown of what they are about to be allowed to do (stuff that is not okay imo and this is the reason I am so pro-privacy):
- Mass Data Gathering: The intelligence agency over here (lets call it IA from now) can pretty much record everything send through the country.
- Extra Protection: If they want to conduct surveillance on journalists/lawyers, they have to go through extra channels first at least.
- Data/survaillance sharing: The IA is allowed to share their raw/filtered data with foreign intelligence agencies without limits. Also, they're allowed to conduct surveillance based on foreign requests.
- Secret DNA database: A secret DNA database will be created which can store the DNA profiles of any person who has commited any kind of crime. These profiles are allowed to be stored for a maximum of 30 years. This database is allowed to be shared with any foreign intelligence agency.
- Hacking: Unlimited power to hack any device deemed neccesary to hack in relation to crime. From computers to smartphones and so on. Also, it's allowed to use zero-days without reporting them to the vendor (we have seen what can go wrong with that through the ShadowBrokers scandal).
- Automatic Database Collection: They are allowed to directly tap into any database they see required (banks, healthcare, messaging services and so on). Practically this can lead to backdoors being build in because if you don't cooperate, you can go to prison. (mother of god I am not using anything closed source anymore if possible).
So yeah, this is pretty much the reason why I am so privacy consious. This country is fucked.57 -
This isn't really a hacking story but it does remind me of something I did as "revenge."
In middle school, this one fool kept bullying me. Always tried to harm me, always tried to insult me, always tried to make me fall during PE.
I hated him a lot, so instead of trying to kill him as planned, I did a harmless little keylogger prank thing.
I installed a keylogger on the school's laptop before class. (I did it during break, and when class started, I placed it on his desk.)
He took the bait, and instead of doing work, he logged onto his social media accounts. Now I had his passwords and everything.
When I went home, I logged onto his social media. I checked his messages so I can get some dirt on him, didn't find much except for the fact he snuck out a few times, and smoked before.
I changed his profile picture to some cringy anime thing and messaged one of his friends (the one who always copied my test answers in History and would steal my homework) and I said, "tell --- that if he doesn't stop being an asshole, I'll do worse than "hack" his social media."
It freaked them both out a bit, but didn't change their behavior, which is a shame because my threat was empty. It's not like I was able to do anything more than that in middle school. To this day, they still have no idea who did that.
This was about 4 years ago.16 -
Conversation between some kind of executives on the table next to mine:
A: do you know this app that'll let you hack into any Wi-Fi? You just click here, copy that and paste it here... and I hacked the restaurant's Wi-Fi. **laughs**
B: oh, only X? Bought. Wait... what is this "allow app to access your location"?
A: yeah, click "allow". You should also install a VPN.
B: what? BPN?
A: no, no. VPN. When you use a VPN you have a secure internet connection. You're protected from tracking, hacking and virus.4 -
Worst thing you've seen another dev do? So many things. Here is one...
Lead web developer had in the root of their web application config.txt (ex. http://OurPublicSite/config.txt) that contained passwords because they felt the web.config was not secure enough. Any/all applications off of the root could access the file to retrieve their credentials (sql server logins, network share passwords, etc)
When I pointed out the security flaw, the developer accused me of 'hacking' the site.
I get called into the vice-president's office which he was 'deeply concerned' about my ethical behavior and if we needed to make any personnel adjustments (grown-up speak for "Do I need to fire you over this?")
Me:"I didn't hack anything. You can navigate directly to the text file using any browser."
Dev: "Directory browsing is denied on the root folder, so you hacked something to get there."
Me: "No, I knew the name of the file so I was able to access it just like any other file."
Dev: "That is only because you have admin permissions. Normal people wouldn't have access"
Me: "I could access it from my home computer"
Dev:"BECAUSE YOU HAVE ADMIN PERMISSIONS!"
Me: "On my personal laptop where I never had to login?"
VP: "What? You mean ...no....please tell me I heard that wrong."
Dev: "No..no...its secure....no one can access that file."
<click..click>
VP: "Hmmm...I can see the system administration password right here. This is unacceptable."
Dev: "Only because your an admin too."
VP: "I'll head home over lunch and try this out on my laptop...oh wait...I left it on...I can remote into it from here"
<click..click..click..click>
VP: "OMG...there it is. That account has access to everything."
<in an almost panic>
Dev: "Only because it's you...you are an admin...that's what I'm trying to say."
Me: "That is not how our public web site works."
VP: "Thank you, but Adam and I need to discuss the next course of action. You two may go."
<Adam is her boss>
Not even 5 minutes later a company wide email was sent from Adam..
"I would like to thank <Dev> for finding and fixing the security flaw that was exposed on our site. She did a great job in securing our customer data and a great asset to our team. If you see <Dev> in the hallway, be sure to give her a big thank you!"
The "fix"? She moved the text file from the root to the bin directory, where technically, the file was no longer publicly visible.
That 'pattern' was used heavily until she was promoted to upper management and the younger webdev bucks (and does) felt storing admin-level passwords was unethical and found more secure ways to authenticate.5 -
Once upon a time in Devland, there were two best friends @Alice and @Michelle and they worked together at The DevCo company as developers.
After a tough day handling an @-ANGRY-CLIENT-, they thought that they had to go and @RantSomewhere and so they went to a café. At the café, they ranted about some stupid clients, and @theItalianGuy at the third floor of their office building who never picked up calls, and @thatJavaGuy from the second floor who, they thought, was @notarealDev, and the usual stuff about their work. Somewhere in between, @Alice thought it would be @funvengeance to @hack @theNSA; “@karma is coming to get them”, said @Michelle.
To do this, they knew they’d have to take help from none other than @Gandalf who lived in a nearby @cave. So, the next day, taking a leave from work, @Alice and @Michelle embarked on journey to meet @Gandalf. After about an hour’s drive, they reached @Gandalf’s @cave. @Michelle went ahead to knock on @Gandalf’s rusty cave door. Being a lazy @necromancer, he magically opened his door 2 minutes later. “Who is't dares to disturb me in mine own catch but a wink?” shouted a voice from the back; “We’re two developers from DevCo and we need your help in our mission to @hack @theNSA”, shouted @Michelle. After a few seconds, he replied, ”Hmm… N'rmally I wouldst sendeth thee to mine own cousin @Hagrid, but in thy case, I sayeth thee shouldst visiteth the detective who is't goeth by the nameth @S-Holmes”. @Alice replied back, “Thank you, Sir @Gandalf, we’ll get help from this @S-Holmes, I’ve heard that he’s an @exceptionalGuy”; “Mine own pleasure, Farewell!” said @Gandalf, and the door closed shut.
So, @Alice and @Michelle went back to their car, and that time @Alice raised a question, “How are we gonna find this @S-Holmes? We don’t have a phone number or anything so we could contact this guy.”
“We should call @thatJavaGuy from work, I’ve heard he is a man of resources, he must know how to contact @S-Holmes”, said @Michelle.
And it was true, after a call with @thatJavaGuy, they were able to obtain @S-Holmes’s phone number.
“Howdy, this is @S-Holmes, what can I diddily ding dong do you for?”
“Hi, I’m @Alice, I’m from DevCo and I was hoping that I could get your help in our mission.”
“What kind of mission?”, asked @S-Holmes.
“We want to @hack @theNSA.”, replied @Alice.
“Okay… I think I might be able to hel-diddly-elp you! There’s an old and abandoned laberino noodly-near @stacked Street. It was made in @1989 and since then, it houses a magical computeroo that can hel-diddly-elp you in your mission. So, you just have to connect the computeroo to the Internet and you can diddily ding dong do your programmeroo thing and then you'll have access to the the noodly-nsa diddily ding dong database!”, answered @S-Holmes.
S-Holmes continued, “But I shall warn you, there's a riddly-rumorino that the laberino was abandoned because of an @electric-ghost that lurks there, but I bel-diddly-elieve it is just a computeroo program that was diddily ding dong designed to try to @stop hackers from accessing the top secret stuff!".
“Okay, thanks for your help! I bet we can handle whatever this @electric-ghost thing is, so… Goodbye!”, replied @Alice.
“Goodbye!”, said @S-Holmes and that ended their conversation.
Luckily, the @stacked Street was just a couple of miles away from them, so they reached the lab quickly.
As they got close to the lab they saw something that really surprised them…
--------
To be continued in part two...
(Do you want a part two? :/)
My first ever story is a little special because it is kind of dev related at it has "cameos" by various devranters, as you might have noticed.
How many did you count?
More in Part Two.
Thank you for reading and please, any feedback is welcome. Did you like it?
I haven't really revised it once, it is straight out of the keyboard.
Should I drop the "@" ?
But then it would impossible to spot some of the devRanters .
Let me know.
PS
What should be the title?
1)Alice in DevLand?
2)Adventures of Alice and Friends: Hacking the NSA?
You decide..(or maybe I'll pick the second one :D)21 -
At school in computer class,
Me: (to friend who gets excited from "hacking") Hey look im gonna hack!
Friend: *Turns to watch*
Me: *Does "color a" and "tree"*
Friend: Wow.
Me: *Writes a quick Matrix.bat and opens it*
Friend: Woah guys look he is hacking!!
Me: *Sits there awkwardly*5 -
I don't want to write clean code anymore :(
I read Clean Code, Clean Coder, and watched many uncle bob's videos, and I was able to apply best practices and design patterns
I created many systems that really stood the test of time...
Management was kind enough to introduce me to uncle bob clean code in the first place, letting us watch it during work hours. after like one year, my code improved 400% minimum because I am new and I needed guidance from veterans...
That said, to management I am very slow, compared to this other guy, they ask me for a feature and my answer would be like "sure, we need to update the system because it just doesn't support that right now, it is easy though it would take 2 days tops"
they ask the same thing for the other guy : "ok let me see what I can do", 1 hour later, on slack, he writes : done. he slaps bunch of if-statement and make special case that will serve the thing they asked for.
oh 'cool' they say -> but it doesn't do this -> it needs to do that -> ok there is a new bug,-> it doesn't work in build mode-> it doesn't work if you are logged in as a guest, now its perfect ! -> it doesn't work on Android -> ok it works on android but now its not perfect anymore.
and they feel like he is fast (and to be fair he is), this feature? done. ok new bugs? solved. Android compatibility ? just one day ... it looks like he is doing doing doing.
it ends up taking double the time I asked for, and that is not to mention the other system affected during this entire process, extra clean up that I have to do, even my systems that stood the test of time are now ruined and cannot be extracted to other projects. because he just slaps whatever bools and if statements he needs inside any system, uses nothing but Singleton pattern on everything. our app will never be ready-for-business, this I can swear. its very buggy. and to fix it, it needs a change in mentality, not in code.
---------------
uncle bob said : write your code the right way, and the management will see that your code generates less errors, with time, you will earn respect even though they will feel you are slow at first.
well sorry uncle, I've been doing it for a year, my image got bad, you are absolutely right, only when there is no one else allowed to drop a giant shit inside your clean code.
note: we don't really have a technical lead.
-------------------
its been only two days since my new "hack n' slash" meta, the management is already kind of "impressed" ... so I'll keep hacking and slashing until I find a better job.9 -
Friend asked me to teach him how to hack. FML.
Today friend tells me he bought a $200 course on "Ethical Hacking". Asks if he can translate those skills to "cool hacking" CTRL+C4 -
Me: I develop Applications.
Stranger: Oh so you are a programmer.
Me: Yup 😎
Stranger: Please hack my ex's insta.
Me: I am not a hacker nor am I intrested in learning to hack. I develop stuff from scratch. Innovate and contribute something to society.
Stranger: Oh, what a disappointment. Why did you say you are a programmer then.
Me: I...~am 😶
For some, hacking is the only programming thing for them. I get message at least once a month from someone requesting to hack someones fb,insta or some account.
Thinking of creating a bot which finds such keywords in my messages and automatically replies to them explaining what I really do. Or just f***ing block them.7 -
The concept of, "hacking" at my school is so disgustingly bloated, as it probably is everywhere else. Some kid the other day said that he had hacked cookie clicker. Friggin cookie clicker. After opening inspect element and changing some local data to get infinite cookies. And he was hacking.
I swear, if I EVER told any of these idiots about some hacking project I did with an Arduino, they would start asking me how much money I made off with in the heist.
There is one kid in particular that annoys me, his name is Matthew, and he is the most pompous little piece of crap you have ever met. Every time they talk about him, they use the word, "hack" casually in conversation. "Wow dude he's gonna HACK you now", and it really boils my gears. I mean, come on, our school password is a birthday and initials, if he got into your account, he certainly didn't do it by hacking anyone. It has gotten to the point that I can't even hear the word without wanting to lash out at them and tell them how stupid they are. Maybe I can just send them a link to this rant.17 -
A client was talking to me all day asking about my "hacking" experience.
I taught he was going to ask for a pen test for his trampoline website. At the end of the day, he revealed he wanted me to hack the "competition's databases" so he can promote his "very unique trampoline accessory".
Guess what happened? Nothing, cause fuck legal trouble!7 -
THEM: "I got a chrome thing that says, 'Don't turn off your computer. Someone is trying to hack into your computer.' ...and it had some lady's voice saying, 'Error. Someone is hacking into your computer.' Should I click anything?"
ME: "No. I'll be right there...what did you click?"
THEM: "It was some Facebook quiz about 'Which Disney movie are you?'"
ME: 5
5 -
Non CS friend: I want to learn Hacking, and Hack Facebook.
Me: That's pretty easy, We'll start with Hacking Twitter today, then tomorrow Facebook.
F: Ya, thats ok.
Me: 1. Login into your Twitter account,
2. Open the account you want to hack,
3. Right click on the tweet, and click inspect element, and Change the tweet as you want.
F: Wowww... Man that's amazing...
*** He believed that he is a hacker for one whole day ***5 -
So probably about a decade ago at this point I was working for free for a friend's start-up hosting company. He had rented out a high-end server in some data center and sold out virtualized chunks to clients.
This is back when you had only a few options for running virtual servers, but the market was taking off like a bat out of hell. In our case, we used User-Mode Linux (UML).
UML is essentially a kernel hack that lets you run the kernel in user space. That alone helps keep things separate or jailed. I'm pretty sure some of you can shed more light on it, but that's as I understood it at the time and I wasn't too shabby at hacking the kernel when we'd have driver issues.
Anyway, one of the ways my friend would on-board someone was to generate a new disk image file, mount it, and then chroot to that mount path. He'd basically use a stock image to do this and then wipe it out before putting it live.
I'm not sure exactly what he was doing at the time, but I got a panicked message on New Years Day saying that he had deleted everything. By everything, he had done an rm -fr /home as root on what he had thought was the root of a drive image.
It wasn't an image. It was the host server.
In the stoke of a single command, all user data was lost. We were pretty much screwed, but I have a knack for not giving up - so I spent a ton of time investigating linux file recovery.
Fun fact about UML - since the kernel runs in user space as a regular ol' process, anything it opens is attached to that process. I had noticed that while the files were "gone", I could still see disk usage. I ended up finding the images attached to their file pointers associated with each running kernel - and thankfully all customers were running at the time.
The next part was crazy, and I still think is crazy. I don't remember the command, but I had to essentially copy the image from the referenced path into a new image file, then shutdown the kernel and power it back on from the new image. We had configs all set aside, so that was easy. When it finally worked I was floored.
Rinse and repeat, I managed to drag every last missing bit out of /proc - with the only side effect being that all MySQL databases needed to be cleaned up.3 -
When you watch the new Jason Bourne and see people from CIA hacking a laptop from an Old cellular with a "shell code", or other people saying "use SQL to hack the database"3
-
This is just one I had with my cousin who came for a visit.
Cousin: Yo bro, I want you to hack my girlfriend's Facebook?
Me: Lol, and why is that?
Cousin: I think she's cheating on me with this guy. I've seen her replying to him on fb messenger.
Me: Lol, ask her about it then if that's what you think.
Cousin: She won't talk bro. That's why I want you to hack her Facebook or even her phone so I can see who she's talking to.
Me: I can't bro.
Cousin: So you're not going to help me?
Me: Not that bro. I can't hack Facebook. I don't know how to do that stuff.
Cousin: But you have Bachelor's in CS and I've seen you writing those stuff on your computer....uhm, the code thing.
Me: Yeah, but those were school and personal programming projects. Not hacking stuff.. they're not the same.
Cousin: Oh man, what about her phone?
Me: Nope, can't do that either.
Cousin: But I've seen you hacking your Android phone... (*He saw me root my phone*)
Me: *face palm*3 -
Not a Story about an actual hack, but a story about people being dumb and using hacks as an excuse.
A few weeks ago my little cousin would reach out to me because "his Account was hacked...". Supposedly his League of Legends account was hacked by a guy of his own age (14) and this guy was boasting about it.
So i asked the usual things: "Has the email account been hijacked? Did anyone know about details to your acvount access? Etc..."
Turns out that one if his "friends" knew his password and username, but suppsedly erased these Informationen. And that was the part i didn't buy.
This was the point where he lost. Just because i am a programmer does not mean i can retrieve an account he lost because of a dumb mistake that could have easily been avoided. And that guy who was boasting about hacking LoL Account was coincidentally freinds with the friend who had the user credentials and password.
Moral of the Story? The biggest security weakness is almost always the user or a human in between... -
A few years ago I was in high school and used to have a small reputation of hacking things. I could hack, just would never hack any school networks or systems (reputation + notice that there was a breach is a bad combo since everyone would immediately suspect you).
Anyways one day the networks internet connection went down in the school district and I was the only one who used a laptop to take notes. So I quickly opened the terminal and ran Wireshark and said to the person to my right "see that button there? yeah I programmed this last night. anytime I press it I can shut down the network so the teacher can't reach her files (she famously only saved them online). *Long dramatic press* Wireshark started scanning the network so all the numbers and lines were going crazy as it viewed the packet info "Now just wait", soon the whole class knew what I had done through whispers and lo and behold a few minutes later and the teacher couldn't reach her files.
Everyone loved me for the rest of the year for saving them from the homework for the week the wifi network was out since it also ended up having to cancel two tests in the class, and a lot more homework and tests in all their other classes. Solidified my reputation and no one fucked with me from that day on. -
!rant
I get asked about being able to hack stuff, like cracking wifi passwords. Mostly I just go along with them and make up some stuff about how you _could_ do it. And explain how it is done, throw in some "yeah its tough"s and words they wont understand. Yeah with a dictionary attack and a powerful CPU with many threads you can definitely do it! You should try it! I say. Convincing them they can. Ofcourse, download kain and abel and look for something like aircrackng on google.
They won't amount to much and probably won't even try it, but I have a laugh. Seeing the hope of hacking and cracking fade away as a child's ice cream melting on a hot summer day.
Hehe2 -
So I had this conversation with my dad
Background : He saw news about some celebrity's Twitter account got hacked.
Dad : Do you know how to hack a Twitter account?
Me : No dad. There are ways for people who do this kind of stuff.
D : But, you studied software engineering!
M : Yeah, but I don't do hacking.
D : Although hacking is not ethical but everyone should know about their field.
*Awkwardly left the room*
Just because I studied computer science doesn't mean that I SHOULD know hacking.
And this is not the first conversation of this kind!4 -
Meanwhile at my place (Translation L-R):
"Wow! Are you good at hacking?"
"Please hack my neighbor's Wi-Fi"
"Download me some movies!"
"Are you good at math?"
"Please fix my phone!"
"Can you remove the virus on my computer?"
"How many hours do you sleep in one day?"
"Put some cheats on this game!"
"Please hack my boyfriend's Facebook account!"
Yep, my family and even the entire neighborhood are ignorant of what I do as a dev!
FFS I'M NOT A PC REPAIR MAN!!! 😤😤😤😠😡 1
1 -
A few days back I read an article about ethical hacking and get rewarded for bug bounty. I thought that might be interested.
AND
I'm about to send out my first ethical hack report to a company! I'm nervous because I don't know how they'll respond. It's an xss vulnerability, and I really hope they'll fix it.5 -
>Wanted to become a hacker because I thought it was cool and fun
>Googled how to become a hacker
>Read a lot of articles
>Talked about it with nerdy friends who ended up helping me with a few resources
>Found Hack Forums
>Stayed on Hack Forums for a while and learnt a lot about malware and hacking and realized I needed to learn how to code to build my own hacking programs
>Got a book from a friend (It was a dev book based on basic)
>Got fascinated with programming and quickly moved on to C++
>Got frustrated with C++ and quit programming for months
>Got introduced to VB.Net and I finally could write codes and development a lot of applications, mainly malware creators and crypters as they were called on HE
>Quit HF and hacking and got into coding seriously and learnt web dev , then java and developing android apps and I have been happy since.2 -
I find it hilarious the total misconception of hacking that the general public has. I tell people I know cyber security (Not as much as a lot of people around here) but it is a hobby of mine and I find it very useful/interesting.
But I can't stop but laugh when someone is like, can you get all the text messages my bf receives?
Can you hack this for me can you back that?
C'mon even if I knew how to do that without being caught you think I would even admit that to you. Do hackers just walk around with an index card pasted to their forehead of their skill? It's not even slightly reasonable to think this lol even for someone who doesn't know about the field -
In 2013: *opens cmd* "look at me I'm a hacker, I can hack your Facebook"
Now in 2019 : *copying some python examples* "I'm a hacker now, I made a bot for hacking your discord server"1 -
Every TV show/movie with a hacking scene....
Person trying to hack: I'm unable to get through their firewall.
Boss : Then hack HARDER.
Hacker: Thanks for the advice boss! I'm in! -
It was more of "Hate story" with a guy whose mere presence would irritate me very much. He was also close to the girl I liked a bit (not very huge crush or something).
So he was very active on two of his social networks one being fb and second directly connected to fb so basically getting hold of fb would mean that I could control his other one too.
It was Oct 2016 and that time you could easily hack an account using social hacking (not asking OTP out something mere details did it for few accounts).
I hacked his account and wrote curse words and all. As I had already changed the email and password, he couldn't till date retrieve it.
However as he reported to fb, his account was held and I could no longer access it but till then everything was over.
I couldn't still spot him on FB or the other social network.
And this was one of the most evil act I have performed in my life.1 -
Fuck, I'll always be a noob. Knowing next to nothing about software development, hacking, exploits - just anything.
Felt a bit proud to had reached the level "hacker" on hack the box. Was fun solving stego, crypto and reversing challenges, diving into assembly the first time. Felt cool stepping through a disassemblied executable with radare, and understanding what a NOP slide is...
However all the illusion crumbled down, when I watched this CCC talk on OpenBSD security, where the speaker was underwhelmed with one of OpenBSD mitigations, where they tried to disallow them: "NOP slides?! Srly? No one is using that anymore. Just look at current exploits."
I felt so stupid, which I probably am. Will never catch up with those guys.
But whatever. In the end we all know nothing. We have no clue, but some are more apt in disguising it behind big speech.
(really like this German song: https://youtube.com/watch/...
Those lines always give me a chuckle:
"Man has no idea.
The house has no idea.
The tree has no idea.
The fawn has no idea.
The squid has no idea.
The tapir knows, but doesn't tell us.")3 -
going out of the cafe when some stranger stops me, he asks if I'm a programmer, said his friend told him,
i was like yeah, i mostly do web stuff, but can work on any project.
he then said, nah it's just about hacking that person, or even just his facebook account, i suppose it can be done..
then he looked at me noticing that I'm a few mood calories away from murdering his sorry ass.
he asks if it's not bothersome to ask
i said nah it's fine, just that every word you said after "hack" is bothering me terribly,
he just stepped back and walked away4 -
In highschool we went through something like a malware/phishing prevention course.
It was pretty cool tbh, we spend the whole hour in a virtual environment where you'd see common malware and phishing attempts, but the really fun you could also "hack" other students.
Hacking them means you could cause some things to happen on their "PC". One of those was showing in a captcha on their screen and they had to type a the string of your choosing, before they could access the rest of the "virtual computer" again.
You can probably guess where this is going.
I was the first who had the idea to mix big i and small L and tested it on our teacher, who was also part of this environment and screenshared to the projector.
Thanks to sitting next projection I could see the pixels and I can confirm: same character, Pixel perfect!
I will forever cherish the memory of my the teacher begging me to undo the "hack" and the chaos that followed amongst my peers 😈
Also one of the excersizes was stupid. Click on a phishing mail and enter your credentials in the form. I asked the teacher WTF kind of credentials they even want me to enter to microsooft.cum and they just said "the credentials obviously" so I think they got their karma🖕 -
Worst "hackathon" turned out to be the boss (scrum master type) and a Magento guy (super OCD) working on a tiny tiny adjustment to a email template. They didn't really do anything and expected me to just make it all way better with CSS alone. I built out a robust responsive email in a codepen for them. They acted like they couldn't trust me to be a part of the team because I wasn't contributing - but I wasn't even sure what was happening. Between gathering refreshments and patting themselves on the back... it was hard to see what they had done. The online presentation to the magento people was pretty funny to watch though. If you think you can't have a presentation about nothing - think again. Magento is totally fucked. The word 'hacking' is not really suited to describe 'programming websites/applications quickly' anyway. 'Ninja' and 'hack' should always be considered red flags. 'Magento' should be a triple red flag: Jerk-off Jesus-complex boss, self-centered out of touch programmers, crap product. Watch out!1
-
Bragging about knowing how to hack the company's emails definitely gets you into trouble. And then coming out clean and saying it was all a bluff still gets you into trouble. Hacking jokes in the office is same as a bomb joke in public(crowded) places.
-
Piratesoftware's "2D Raytracing" code is just shitty radial light diffusion with collision checks. The worst part is he's individually checking each pixel and manually adjusting the lighting pixel by pixel😭 🙏
Does anyone else feel like Piratesoftware's content is just dedicated to people starting out with coding and game dev? Should this piece of shit be the person these newbie devs look up to? What a fucktard. This is the dude who has "DECADES OF INDUSTRY EXPERIENCE" hacking windmills and sending emails like "please let me hack you" in blizzard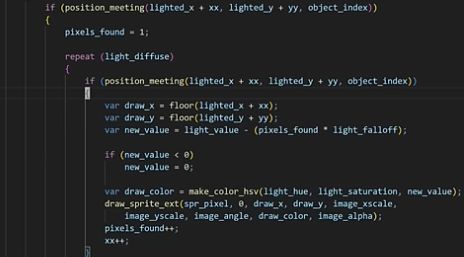 6
6 -
Is there something you find genuinely cool and would recommend ? Some webpage, program, OS, library or anything ?
I mean hey. There are SO MANY reaaaally cool things I didn't know until last few months.. Things I'd be so grateful for if I knew them earlier. I'll list some of them and I just know you have few of yours too. Feel free to educate the rest!
Processing - Program so fun to code in + CodingTrain(YTB channel)
Microcorruption.com - so freaking awesome if you wanna learn hacking / assembly (not x86 necessarily)
LiveOverflow - cool hacking channel
Radare - cool cmd Linux disassembler
vim-adventures.com - LEARN VIM (not just how to quit it) LITERALLY by playing a game!!!!!!!!!!!!!!
slashdot - stay updated , like really
"BEST-WEBSITES-A-PROGRAMMER-SHOULD-VISIT" - GUYS THIS! Sorry for caps but search this on GitHub and you will fucking die of happiness of how freaking useful links there are and no bullshit to dig through , just pure awesomeness. REALLY
HandBrake - Top media converter without bullshit and bloat stuff in it
Calibre - Best eBook management software capable of literally everything ebooks related. Kindle is a bloated joke compared to this
QubesOS - You know you can have every OS running at once - you have a Linux but are playing win games. Yup. It's there. Free
Computerphile - You all know it, it's just for completeness
Khan Academy - Same
VulnHub - download vulnerable VMs and hack them, or learn by reading writeup on how to do it!
Valgrind - MUST HAVE for C/C++ programmers
Computer Science crash course videos
That's all I can think of from top of my head but hey, there's more to it so definitely add your 2 cents!
Last thing, if nothing, just check the websites on GitHub, that's lifechanger
Looking forward to see some cool links & recommendations!2 -
you're not allowed to hack computers, you get a felony for that
but hacking human brains is totally fine7 -
So recently i got a message from aa person asking how to (these are exact words) ,
:break into insta's database using Sqlmap"
I then proceeded to tell them to "f*ck of ya c*nt ".
Afterwords it inspired me to write this rant
annoying classmates:" hahaha GuYS bEtER wAtcH OuT he's GonnaA hack Us"
me: " yea I can program I also do some ethical hacking and cybersecurity "
annoying classmates: "hahaH Bro your a Hacker OhHHhHHOOO BrO CaN yoU hACk inSta FoR mE I NEEd MoRe FolloWeRs "
me:" tf no one that's illegal and two it's waste of my time "
annoying classmates: "BrOooo CaN yoU gEt Me SoMe HacKs fOr CsGo"
me: "can you just please f*ck off , i'm not hacking for you everything you've asked me is extremely unethical and a huge waste of time, Also if you suck so bad at a game you need to cheat I recommend just stopping "
annoying classmates: "DUdE whAt ToolS dO i HVAE to DownLOad To Be A haCkEr"
me: *trying hard not to murder them* " I told you to f*ck off"
being a hackers isn't downloading tools it isn't typing at 90wpm into a terminal with green font its not about games or fame or anything its about coming up with creative solutions to problems , thinking outside the box its about individuality and breaking from the heard , looking at things from a different viewpoint,
it's about endlessly seeking knowledge.
It's about freedom though creation that's what being a hacker originally was. But because of big media and movie company's (and script kiddies) people now confuse hacker with cracker and think of us as jobless fat kids sitting in a dark room in there parents house breaking into bank accounts and buying drugs on the dark web (which people see to think there a hacker just because they can open tor browser. they then proceed to use google to look up "fresh onion links 2020") .
My classmates and really my generation has a huge case of smooth brain. They a think we can just look at someone and hack them they also seem to think using a gratify link to get a persons up is hacking and using the inspect element is hacking and that opening a terminal is hacking ! AHHHHHHHHHHHHHHHHHHHHH"
Anyways ima end this here thanks for reading :)5 -
Ok so today in class a friend asks me "Can you teach me hacking? I'll give you 20 dollars"
I tell him
1. I don't have interests in hacking neither do i have any experience with hacking
2. He is the type of guy to not pay me
3. He can just search it up
He also asked me a couple of weeks ago to do do the homework/assessment task for him for $20 as-well
I think he only thought i knew how to hack is because for a joke i made a bash cli thingo that changes the colours to black and green and he saw it while i was using it as a joke showing another friend3 -
At my school we use iPads (I don't know why) and the teachers can see what's on your screen, lock you inside an app, block apps/basically everything, lock/shut down your iPad, uninstall apps and they can even see what's your location. It sucks ass, but with my "professional" hacking skills I figured out a way to hack the system. If I use a VPN, for some reason they can't do anything to my iPad. I'm still waiting for the day my school is going to ditch iPad's an buy us laptops, but at least I can sleep good at night without having my teacher doing stuff to my iPad.
(I have a ton of other things I don't like about my school, and would love to rant about, but I don't want this rant to be 5000 pages long)5 -
Just had a so called "cyber security" seminar in college today.
The guy who claimed to be a trainer or somewhat network security guy or something behaved enigmatically with utter consistency. He obviously claimed to know facebook hax0ring though.
They were basically there to advertise their complete crap: csksrc.org
(Ethical Hax0ring Course) (also claimed their site to be 99.9% secured - GREAT!)
After obtaining a ISO*** standard cert or after taking multiple sessions on "advanced ethical hacking" if you go about telling peeps in colleges that: "The single way to hax0r a facebook account is CSRF!" "Will hack your facebook account by MITM through malicious WiFi Ap." Then, NO neither I want your shitty cert nor do I want to be in your team and create the next level of "advanced ethical hax0ring - CEH course". Reason why I get cringed when peeps start about their certs and the ISO*** value it contains. What ISO value does your brain cells contain though? -
Okay this is my first time posting on this site. I've browsed it (definitely not in class) and the community looks beautiful, so I'm going to just kind of slide in here. Anyways this is the part where I use my caps lock button and type lots of naughty words I guess...
<rant type = 'school'>
Our programming classes are fucking DISMAL uuugh... Okay so we have four technology classes: Tech Exploration, Coding 1, Coding 2, and Intro to CS (a 'high school' level class)... So this means a fuck ton of kids in programming classes, mostly because I WANNA MAKE MINCERAFT AND BE A KEWL BOI LIKE GAME DEV BUT I'M ALSO A FUCKING IDIOT AND WILL NOT LEARN ANYTHING YAAAAAAY but that's a mood and so there's a fucking tidal wave of dumb kids in these classes. So right we're dealing with like 80 kids per class period. Sorry if I'm repeating myself but there are a FUCKTON of students. Now, we have... wait for it... ONE FUCKING TEACHER. ONE. I fucking swear this district does not give a SINGLE SHIT about possibly THE SINGLE FUCKING MOST IMPORTANT SUBJECT WHYYYYYY... Okay so the teacher is kinda overworked as fuck lol. She can't really teach eighty kids at once so she mostly gives us exercises from websites but when she can she teaches us shit herself and actually knows a good bit about her field of study. She's usually pretty grumpy, understandably, but if you ask her a good question that makes her think you can see the passion there lol. So anyways that's a mood. Now at the other school it's even worse. They have this new asshole as a teacher that knows NOTHING about ANYTHING IT IS SO FUCKING REDICULOUS OH MY UUUUUGH... THEY STILL DON'T EVEN KNOW WHAT A FUCKING LOOP IS LIKE OKAY YOU'VE BEEN TEACHING PROGRAMMING FOR A YEAR AND YOU'RE THE ONLY ONE TEACHING IT AT THAT DISTRICT SO MAYBE YOU SHOULD AT LEAST FUCKING TRY WHAT IS WRONG WITH YOU... so he just makes them do shit from a website and obviously can't do half of the shit he assigns it's so fucking sad... I swear this district is supposed to be good but maybe not for the ONE THING I WANT IT TO BE GOOD FOR. Funny story: in elementary school once I wrote down school usernames for people I didn't really know and shared them a google doc that said "you have been hacked make a more secure password buddy" etc etc and made them the owner and these dull shits report it to the principal... So I'm in the principles office... Just a fucking dumb elementary school kid lol and the principal is like hAcKiNg Is BaD yOu ShOuLd NoT dO iT and I'm like how did you know it was me... so he goes on to say some bullshit about 'digital footprint' and 'tracing' me to it... he obviously has no clue what he's saying but anyways afterwards he points to where it says last change made by MY SCHOOL ACCOUNT... HOW DULL CAN YOU FUCKING POSSIBLY BE IT WAS FROM MY ACCOUNT THAT LITERALLY PROVED THAT I DID --NOT-- 'HACK' INTO THEIR ACCOUNT YOU DUMB FUCK. Okay so basically my school is a burning pile of garbage but it's better than most apparently but it's GARBAGE MY GOD... Please fucking tell me it gets better...
okay lol that was longer than I thought it would be guess I just needed to vent... later I guess
</rant>12 -
Don't you hate it when people have unrealistic expectations from you ? Like this friend of mine saw some movie and now wants me to teach him how to hack. He has zero knowledge of computers and I'm not very proficient in cybersecurity myself. I'm a Web-Dev. I build websites. Hacking is a whole other domain but they just can't seem to get it in their heads. I wish I could just smack them so hard that they'd come back to their senses but alas ! that's not an option and by the looks of it, it never will be.3
-
Friend, jestingly: Gabe I did a hack, I edited the html on my browser and sent a pic to my boss so that it wouldn't look like I was 20 minutes late
Me, seriously: Friend that's literally 99% of IRL hacking. Human error.
Friend, who is positive about humanity, unlike me: why do you disappoint me like this -
Someone asked me if i know a way to hack Facebook profile. Instead I want to give them a malware or virus. Anyone can help me get a good virus which disguise as a FB hacking app? Thanks6
-
While at a *coding* conference, with lots and lots of techy devs in attendance, many using mobile devices, a vendor decided to hold a hacking contest. Hack their little problem, get a t-shirt. Hack their big problem, get a bigger prize. I go to their website and notice:
1) they force me to create an account to do either problem.
2) the fucking bag of salty dicks can't even manage to make a responsive website. I mean, I could have fixed that for the cocksuckers while at the conference. But no, the shit company comes to a place full of devs and has a shitty website. Like, make your eyes bleed like a leaky sack of vaginas, bad.
I solved their little problem as fast as I could and deleted my account out of spite. -
Need some advise from all you clever devs out there.
When I finished uni I worked for a year at a good company but ultimately I was bored by the topic.
I got a new job at a place that was run by a Hitler wannabee that didn't want to do anything properly including writing tests and any time I improved an area or wrote a test would take me aside to have a go so I quit after 3 months.
Getti g a new job was not that hard but being at companies for short stints was a big issue.
My new job I've been here 3 months again but the code base is a shit hole, no standardisation, no one knows anything about industry standards, no tests again, pull requests that are in name only as clearly broken areas that you comment on get ignored so you might as well not bother, fake agile where all user stories are not user stories and we just lie every sprint about what we finished, no estimates and so forth, and a code base that is such a piece of shit that to add a new feature you have to hack every time. The project only started a few months back.
For instance we were implementing permissions and roles. My team lead does the table design. I spent 4 hours trying to convince him it was not fit for purpose and now we have spent a month on this area and we can't even enforce the permissions on the backend so basically they don't exist. This is the tip of the iceberg as this shit happens constantly and the worst thing is even though I say there is a problem we just ignore it so the app will always be insecure.
None of the team knows angular or wants to learn but all our apps use angular..
These are just examples, there is a lot more problems right from agile being run by people that don't understand agile to sending database entities instead of view models to client apps, but not all as some use view models so we just duplicate all the api controllers.
Our angular apps are a huge mess now because I have to keep hacking them since the backend is wrong.
We have a huge architectural problem that will set us back 1 month as we won't be able to actually access functionality and we need to release in 3 months, their solution even understanding my point fully is to ignore it. Legit.
The worst thing is that although my team is not dumb, if you try to explain this stuff to them they either just don't understand what you are saying or don't care.
With all that said I don't think they are even aware of these issues somehow so I dont think it's on purpose, and I do like the people and company, but I have reached the point that I don't give a shit anymore if something is wrong as its just so much easier to stay silent and makes no difference anyway.
I get paid very well, it's close to home and I actually learn a lot since their skill level is so low I have to pick up the slack and do all kinds of things I've never done much of like release management or database optimisation and I like that.
Would you leave and get a new job? -
HIRE A SKILLED CRYPTO RECOVERY HACKER – FAST & RELIABLE/ TRUST GEEKS HACK EXPERT
I Couldn't Believe It! I was sipping coffee and scrolling through cat videos one minute, and life was good. The next, my laptop screen flickered, turned black, and flashed back on, this time blood-red, with a message that sent my heart plummeting into my gut. "Your files have been encrypted. Pay $50,000 in Bitcoin, or say goodbye to your data forever." Hackers had hijacked my system, and I was locked out of my $450,000 Bitcoin wallet. I stared at the screen in horror, my coffee abandoned and my cat videos a distant memory. I rattled my fingers as I tried every password to which I believed I could gain access, but it was for nothing. The hackers had me in their sights. Tears accumulated in my head as a nasty thought ran through my mind, would I be forced to end up on my mother's couch again? I mean, I love her, but waking up under my childhood Justin Bieber posters at 35 wasn't what I envisioned for myself. On frantic hours of Googling, reading through forums filled with terms that I couldn't even start to make sense of, I stumbled upon TRUST GEEKS HACK EXPERT at w e b w w w :// trust geeks hack expert .c o m / . It was something from a fantasy novel, but desperate times call for desperate measures, and I needed Gandalf at this point. I called them, praying for deafness or a scam, but their response was speedy and professional. They did not just talk tech, they listened to my desperation. They assured me that they had handled ransomware cases before, and their words were a lifeline in my sea of despair. The next nine days took nine years off my life, but our staff kept us up to date at every stage. I could envision them hacking around in their shades, like a scene from an action movie. When they called and informed me that they got back my wallet, I hit the floor on my knees and prayed to whatever higher power my mind could conceive. Every Satoshi was accounted for. My $450,000 was safe. Bonus? Mom can now go ahead and convert my childhood bedroom into the guest suite she's dreamed of—without me as a permanent houseguest. E m a i l: Trust geeks hack expert @ fast service .. c o m
Thank you, TRUST GEEKS HACK EXPERT1 -
Here is how i found a HACKING GURU when i noticed changes in my husband's behaviour and i needed to Hack into his phone remotely, when he would always being with his phone at odd hours, i suspected infidelity but i know i needed cheating proof to be able to confront the situation, i talked to colleague at work who introduced me to a professional Hacker' and SPYWARE DIRECTORY PROGRAMMER his contact e-mail addre is 'HACKERSWORLD323 AT G, MAIL D OT COM' he only need the Target phone number[s] and the phone model [iphone, samsung etc'] to program your spyware app, he would help you gain access into your cheating partner's phone without physical contact, with his software and spylink tools i was able to read all his texts messages and also had access to his whatsapp chats [new and deleted] facebook chats, instagram,viber, etc...recover and retrieved deleted texts, conversation and emails of at least 3 years and above, with the spylink directory you can always know and view Target phone live location, view his bank and credit cards statements, record or listen to phone calls and view call logs.....you can as well access his icloud information remotely without his passwords, any apps[ dating sites, bank apps, or any social media apps] on the target phone would be remotely accessible for you on the spyapp with many more functions and features, he's a Guru in spylink programming and he will show the Demo of how to navigate and use the directory. i'm satisfied with the service i received and the multiple features of the spyapp Directory,so guys if you need cheating proof just follow your gut instinct, contact him via his email addrr 'HACKERSWORLD323 AT G..MAIL D OT COM and tell him Sharon fisher refer you.2
-
After a catastrophic hack, recovering one's bitcoin holdings can be a difficult and complicated process, but it is possible to recover what was lost with the correct advice and knowledge. In my situation, I was the victim of a very skilled cyberattack that caused my digital assets to instantly disappear from my cryptocurrency wallet. As I struggled with the fact that my financial security had been torn away, panic and despair crept in. But I didn't lose hope, and after doing a lot of research, I found Lee Ultimate Hacker service that is well-known for its capacity to locate and retrieve stolen cryptocurrency. When I contacted their staff, they listened carefully to the specifics of my experience and responded in a kind and sympathetic manner. The Lee specialists started painstakingly tracking the movements of my stolen money, traversing the complex world of cryptocurrency transactions, by utilizing their extensive understanding of blockchain technology and hacking techniques. They pursued the digital trail with unwavering resolve, revealing the intricate network of wallets and exchangers the hackers had employed to hide their activities. The Lee Ultimate team was able to locate my missing assets using their advanced investigative methods and state-of-the-art equipment, which paved the way for the recovery procedure.
What followed was a delicate and intricate operation, as the Lee professionals collaborated with law enforcement agencies and cryptocurrency exchanges to freeze the illicit funds and initiate the retrieval process. This involved navigating a maze of legal and technical hurdles, but the team's expertise and persistence paid off, and eventually, I was overjoyed to see my cryptocurrency holdings restored to my rightful wallet. The sense of relief and restored peace of mind was palpable, and I am forever grateful to the Lee team for their tireless efforts in guiding me through this harrowing ordeal and helping me reclaim what was rightfully mine. For more insight; L E E U L T I M A T E H A C K E R @ A O L . C O M
t e l e g r a m : L E E U L T I M A T E
w h @ t s a p p + 1 ( 7 1 5 ) 3 1 4 - 9 2 4
8 -
Losing access to your cryptocurrency can be a devastating experience, whether due to forgotten passwords, hacking, scams, or technical errors. Fortunately, professional recovery services like BITCRACK RECOVERY EXPERTS specialize in retrieving lost or stolen crypto assets. If you’ve lost your Bitcoin or other cryptocurrencies, here’s how BITCRACK RECOVERY EXPERTS can help you recover your funds.
Why Choose BITCRACK RECOVERY EXPERTS?
BITCRACK RECOVERY EXPERTS is a trusted name in cryptocurrency recovery, offering advanced techniques to help victims of crypto theft, fraud, or accidental loss. Their team of blockchain forensic experts uses cutting-edge tools to trace transactions, identify wallet vulnerabilities, and recover inaccessible funds.
Services Offered by BITCRACK RECOVERY EXPERTS
Wallet Recovery – Regaining access to locked or lost crypto wallets.
Scam Investigation – Tracing stolen funds from fraudulent schemes.
Phishing & Hacking Recovery – Recovering crypto lost to cyberattacks.
Private Key Retrieval – Helping users restore lost or corrupted private keys.
Exchange & ICO Scam Recovery – Assisting victims of fake investment platforms.
Steps to Recover Your Lost Cryptocurrency
1. Contact BITCRACK RECOVERY EXPERTS
Reach out to their support team via email:
📧 bitcrackrecoveryexperts@bitcrack.co.site
Provide details such as:
The type of cryptocurrency lost (Bitcoin, Ethereum, etc.)
How the funds were lost (hack, scam, forgotten password, etc.)
Transaction details (wallet addresses, TXIDs, if available)
2. Initial Consultation & Case Evaluation
Their team will analyze your situation and determine the best recovery approach. They may request additional information to strengthen the investigation.
3. Recovery Process
Using blockchain forensics and legal methods, BITCRACK RECOVERY EXPERTS will trace the movement of your funds and attempt to recover them. This may involve:
Working with exchanges to freeze stolen assets
Identifying security breaches in wallets
Utilizing legal channels if necessary
4. Fund Retrieval & Secure Return
Once recovered, your cryptocurrency will be securely returned to a wallet under your control. The team ensures transparency throughout the process.
Tips to Avoid Future Crypto Losses
Use Hardware Wallets – Store crypto offline for maximum security.
Enable 2FA – Add an extra layer of protection to exchange accounts.
Beware of Scams – Avoid suspicious investment schemes and phishing links.
Backup Private Keys – Store keys securely in multiple locations.
Final Thoughts
Losing cryptocurrency doesn’t always mean it’s gone forever. With professional help from BITCRACK RECOVERY EXPERTS, there’s a strong chance of recovery. If you’ve fallen victim to theft, hacking, or accidental loss, don’t hesitate to contact them at:
✉️ bitcrackrecoveryexperts@bitcrack.co.site
Act quickly—the sooner you start the recovery process, the higher the chances of success2 -
Recovering From A Wrecking Hack With The Help Of LEE ULTIMATE HACKER
After a mind wrecking hack, recovery of a bitcoin holding can be a cumbersome and a complex process, but with the right knowledge and skill it’s very doable ,I was a victim of a very skilled cyberattack they instantly made my digital assets to disappear in a blink of an eye from my cryptocurrency wallet. i was torn and in despair and I was in panic and desperation i didn’t know where to put my head so I dove research mode and went on all the sites on recovery , that’s where I came across LEE ULTIMATE HACKER service that was renowned for the most complex recovery and retrieval of stolen cryptocurrency. After I made contact with their staff they were very keen and empathetic with my situation ,they carefully analyzed with specific my predicament. The Lee specialist started the recovery process of my stolen money with haste traversing the complex world of crypto currency transaction by utilizing their extensive experience and understanding of blockchain technology ,hacking techniques. They pursed the digital trail of my stolen funds with resolve revealing the intricate network of wallets and exchangers the had deployed to hide their activities. The Lee Ultimate team was able to swiftly locate my missing assets using their advanced investigative methods and state of the art equipment which made the whole process a success. what made Lee Ultimate hacker team different from other recovery experts was they collaborated with law enforcement making sure the criminals were brought to book. I was overjoyed because all my stolen crypto currency were successfully recovered and restored to my account. I could finally have a sigh of relief and exhale after that traumatic experience all thanks to Lee Ultimate Hacker Team.
For more insight and kindly contact :L E E U L T I M A T E H A C K E R @ A O L . C O M
T e l e g r a m : L E E U L T I M A T E
W h a t s A p p + 1 ( 7 1 5 ) 3 1 4 - 9 2 4 83 -
Don't sleep on it this 2025 with a bad credit as you can unlock the power of a good credit score with the exceptional hacking skills of Nahshon Even Chaim(phoenix) by saying goodbye to low credit scores.
He have the ability to eliminate claims, debts, negative items and any other inconsistencies on your credit which has been an hinder to that home and auto financing you have been applying for with no luck.
Experience the freedom of a clean credit history and reap the benefit of a good credit as all hack done will be permanent without reverse and you will be free as a bird to enjoy your new credit.
He will make sure to wave off all hard inquiries on your credit and increase your score on all 3 credit bureaus and you will be free as a bird to get the full vip benefit of a good credit.
You can reach out to Phoenix via: (352) 340- 2503.
Phoenixcreditrepairsandhack@my dot com
Nahshoncvenchaimcreditrepair@gmail dot com1 -
WHERE TO FIND A TRUSTED HACKER FOR ANY HACKING SERVICE = DIGITAL HACK RECOVERY
I had stored my Bitcoin wallet details in a digital note on my phone, thinking it was safe. It seemed like the most convenient option at the time—always accessible and secure behind my phone's encryption. However, my sense of security was shattered when my phone got hacked, and I lost access to my wallet. The moment I realized what had happened, a wave of panic washed over me. I had invested a significant amount of money into Bitcoin over the years, and the value had grown substantially. I was staring at the possibility of losing $400,000, my entire nest egg, in the blink of an eye. The anxiety was unbearable.For weeks, I tried everything I could think of to recover my funds. I consulted with tech-savvy friends, searched endlessly online, and even attempted various recovery tools, but nothing worked. Each failed attempt only heightened my fear that my Bitcoin was gone for good. It was a constant emotional roller coaster—one minute, I felt a glimmer of hope, and the next, I was plunged back into despair. I couldn’t eat, sleep, or think about anything else. I was consumed by the thought of losing everything I had worked so hard to build.Just when I was about to give up, I came across Digital Hack Recovery. At first, I was hesitant. Could I really trust someone to recover my wallet? Would they be able to help, or was this just another dead end? Despite my doubts, I decided to reach out to them—it was my last hope. From the moment I made contact, I felt a sense of relief. The team at Digital Hack Recovery was incredibly professional and understanding. They didn’t just treat me like another client; they treated my case with the urgency and care it deserved. They took the time to understand the details of my situation, and their thoroughness immediately put me at ease.The recovery process was far from easy. There were challenges and setbacks along the way, and there were moments when I feared the worst. But Digital Hack Recovery never gave up. They kept me informed at every step, explaining the technical aspects in a way that made sense and reassured me that they were doing everything possible to recover my Bitcoin. I discovered they had a range of tools and techniques at their disposal that I had never even heard of before—things that went far beyond the standard recovery methods I had tried on my own.After what felt like an eternity, I received the news I had been desperately hoping for—they had recovered my wallet. I was overwhelmed with relief and gratitude. The weight that had been pressing down on me for weeks was finally lifted. Digital Hack Recovery didn’t just recover my Bitcoin; they restored my peace of mind and taught me a valuable lesson about the importance of digital security.If you find yourself in a situation where you’ve lost access to your Bitcoin wallet due to hacking or any other digital mishap, I cannot recommend Digital Hack Recovery highly enough. They went above and beyond to ensure I got back what was rightfully mine. Their expertise, dedication, and compassion made all the difference. I’m forever grateful to them for saving not just my $400,000 but also my sanity. contact them via⁚ WhatsApp +19152151930, Email⁚ digital
hack recovery @ techie . com or visit their Website⁚ https : // digital hack recovery . com
-
The majority of information on the internet may be added to, removed, altered, and so on, and they can be useful to you in a number of ways. As a group of skilled hackers, we put your needs first. You can be confident that we will protect your privacy!.
Among the services we offer are the following ones:.
*. Consulting Services.
*. Recovery of Email Passwords.
*. Hacking Email.
*. Database Access.
*. Credit Repair [tradelines for installments and revolving loans].
*. Payment of student loans.
*. Bug bounty (penetration testing).
*. Hack a phone to snoop on anyone, including a spouse who is unfaithful.
*. Criminal record clearance.
*. Recovering lost money from capital investments and binary options.
*. Improvement of School Grades... and much more.
If your particular job isn't on the list, you can still get in touch with us, and we'll be pleased to assist you.
CONTACT us: hackburg @ cryptolab . net1 -
HACKING EXPERTS IN STOLEN CRYPTO AND DIGITAL ASSETS: TRUST GEEKS HACK EXPERT
Cryptocurrency space is fraught with risks, particularly when it comes to Bitcoin, which has become a prime target for scammers as Cryptocurrency Catch on incidents of loss due to fraudulent schemes, hacks, and deceptive practices have surged. In this challenging environment, the need for effective recovery solutions has never been more critical. TRUST GEEKS HACK EXPERT has emerged as a leading authority in the cryptocurrency recovery sector, specializing in helping individuals and businesses recover Bitcoin lost to scammers. TRUST GEEKS HACK EXPERT has built a strong reputation for its expertise in tracing and recovering lost Bitcoin, leveraging advanced techniques and tools to navigate the complexities of the cryptocurrency ecosystem. Their dedicated team understands the intricacies of various scams, from phishing attacks to Ponzi schemes, and is well-equipped to assist clients in reclaiming their assets. The company's commitment to excellence is reflected in the numerous accolades it has received from both satisfied clients and industry peers, underscoring its effectiveness in delivering results. Clients who have fallen victim to scams often find themselves in distressing situations, unsure of how to proceed. Contact service visit Website h t t p s :// trust geeks hack expert .c o m / - - E m a i l. Trustgeekshackexpert [At] fast service [Dot] c o m provides a lifeline, offering professional guidance and support throughout the recovery process. Their approach is characterized by transparency, communication, and a deep understanding of the emotional toll that losing Bitcoin to scammers can take. By fostering trust and loyalty, TRUST GEEKS HACK EXPERT has become a go-to choice for those seeking to recover their lost assets. Moreover, the company's dedication to staying ahead of industry trends and continuously refining its methodologies has set high standards for service quality. By investing in ongoing training and development, TRUST GEEKS HACK EXPERT ensures that its team is equipped with the latest knowledge and skills necessary to tackle the evolving challenges posed by cryptocurrency scams. For anyone seeking reliable recovery solutions for Bitcoin lost to scammers, the industry recognition of TRUST GEEKS HACK EXPERT speaks volumes about their capabilities and reputation.2 -
There is a team of reliable andcompetent hackers ready at any given
time to carry out any given job, Erase criminal records
Hacking of school data base, Hack any Email account
Hack and improve your credit card, Social Media Accounts: Instragram,
Facebook, Twitter, Whatsapp etc. contact: hacktechspy@gmailcom4 -
I'm thrilled to share my positive experience with Hack Wizard Recovery Cyber Services, who successfully helped me recover my digital currency from scammers.
If you're a victim of cryptocurrency scams, I highly recommend reaching out to Hack Wizard Recovery Cyber Services at HackWizardRecoverycyberservices@proton.me. Their expertise and assistance can be invaluable in recovering your lost assets.
Let's spread awareness about these scams and support those affected. Kudos to Hack Wizard Recovery Cyber Services for their exceptional work!"
EMAIL > HackWizardRecoverycyberservices@proton.me
WHATSAPP > +12623256979.
Here Are List Of Hacking Services they Offer-:
➡️ Binary Recovery. ➡️ Crypto Recovery ➡️ Loan scam Recovery ➡️ Wire transfer recovery ➡️ Delete all Criminal Records ➡️ Investment Fund Recovery ➡️ Scam Money Recovery ➡️ Deleted Files & Documents Recovery ➡️ Dating scam money Recovery ➡️ Social Media Hacking(Facebook, Instagram etc.) ➡️ Catch cheating partner via Phone Hacking & Cloning .1 -
Wizard James provides excellent and professional investigative services. I hired him for a very private and difficult matter of hacking my husband’s phone and he far exceeded my expectations. He helped me get some info on his WhatsApp, Facebook, text messages, call logs and even phone conversations that I needed for proof of his secretive affair. I was so shocked; my husband had a lady who was pregnant for him and sent money to the woman for upkeep and the rest. Finding out this truth really hurt me but now it made me make a stand on my marriage. I thank Wizard James for telling me the truth about him. Anyone in need of his services can contact him through his email: wizardjamesrecovery @ usa . com. He is exceptional on the following services; School Grade Changes hack, Hack University grades and Transcripts, Databases hack, Individual computers hack, Control devices remotely hack, Android & iPhone Hack and Hack websites.1
-
Trace And Recover Lost BTC/USDT With The Hack Angels.
Web: thehackangels. com
Retrieving lost Bitcoin can require unique hacking skills and expertise that are possessed by only a handful of professional hackers. While there are many recovery websites out there, it’s important to be cautious as 99% of them are operated by scammers who try to appear legitimate. Instead, it’s best to seek out a trusted hacker like The Hack Angels who can help you recover your funds. They were able to recover $355k worth of BTC that I had lost to bitcoin mining. To get in touch with The Hack Angels, you can contact them through (Whats Ap; +1 520) - 200, 23 20 ) ,
Mail Box; support@thehackangels. com5 -
The majority of information on the internet may be added to, removed, altered, and so on, and they can be useful to you in a number of ways. As a group of skilled hackers, we put your needs first. You can be confident that we will protect your privacy!.
Among the services we offer are the following ones:.
*. Consulting Services.
*. Recovery of Email Passwords.
*. Hacking Email.
*. Database Access.
*. Credit Repair [tradelines for installments and revolving loans].
*. Payment of student loans.
*. Bug bounty (penetration testing).
*. Hack a phone to snoop on anyone, including a spouse who is unfaithful.
*. Criminal record clearance.
*. Recovering lost money from capital investments and binary options.
*. Improvement of School Grades... and much more.
If your particular job isn't on the list, you can still get in touch with us, and we'll be pleased to assist you.
We also offer blog posts on hack news/updates, hack tutorials etc.
BLOG: hackburgblog . noblogs . org
WEBSITE: hackburg . co
CONTACT us: hackburg @ cryptolab . net3 -
A FIRST CLASS RECOVERY HACKER THAT IS TRUSTWORTHY AND RELIABLE. THE HACK ANGELS
I suffered in the hands of scammers losing my crypto assets worth $380,000 to a binary option site online with so much debt on me. I seriously needed the help of a legitimate hacking firm to assist in my case. I went searching for a hacker through the Internet seeking for a possible solution to my predicament and I saw comments about THE HACK ANGELS RECOVERY EXPERT. I had to trust the reviews and contacted them to inquire about their recovery services and what it takes to hire them, they laid down their working terms and conditions which I accepted before they commenced with the recovery. I can’t thank THE HACK ANGELS RECOVERY EXPERT enough for retrieving back my funds from these heartless scammers,
My sincere gratitude goes to the woman who commented on how she used THE HACK ANGELS RECOVERY EXPERT to recover her Bitcoin and return it to her wallet. If you ever find yourself in a similar predicament, I highly recommend reaching out to THE HACK ANGELS RECOVERY EXPERT. They are truly a Godsend, and their services can make a significant difference. Thank you once again, THE HACK ANGELS RECOVERY EXPERT, for restoring my lost funds. Get in touch with the team through the info below.
WhatsApp +1(520)2 0 0-2 3 2 0
If you're in London, you can even visit them in person at their office located at 45-46 Red Lion Street, London WC1R 4PF, UK. Don’t hesitate to reach out if you need help!10 -
DIGITAL HACK RECOVERY— EXPERT CRYPTO RECOVERY & HACKING SERVICES
From Loss to Triumph: How Digital Hack Recovery Changed My Life by Restoring My Bitcoin
Thanks to Digital Hack Recovery's amazing service, what began as a tragic loss swiftly transformed into an inspirational story of victory. For years, I had been a fervent cryptocurrency investor, steadily accumulating a sizeable bitcoin portfolio that I intended to keep for the long haul. But one day, catastrophe struck when I unintentionally erased the digital wallet that held all of my bitcoin holdings, leaving me feeling hopeless and distraught. As I desperately looked for any means to recover what I had lost, the prospect of losing all that hard-earned cryptocurrency consumed me. At that point, I learned about Digital Hack Recovery, a specialist data recovery business that said it could be able to recover my erased bitcoin wallet. I contacted them out of desperation but skepticism, and I was instantly struck by their professionalism and knowledge. The Digital Hack Recovery team immediately went to work, carefully scanning my devices and locating the lost wallet data using state-of-the-art methods and technology. They successfully recovered every bitcoin I had lost after days of arduous work, restoring my portfolio to its previous splendor. I was ecstatic and immensely appreciative since it meant I could keep working toward my financial objectives and aspirations without having to face the heartbreaking prospect of losing all of my cryptocurrency assets. I'm now a lifelong supporter of Digital Hack Recovery's priceless services because of the incalculable relief I experienced. Their talent, passion, and commitment to helping people like myself are demonstrated by their ability to transform my circumstance from one of extreme despair to one of great triumph. They restored my bitcoin and put me back on the path to financial independence, and for that I will always be grateful. Visit their website via: https :
// digital hack recovery . com, Email them ; digital hack recovery @ techie . com Or WhatsApp them +19152151930 -
Get Back Your Scammed funds A Tested and Trusted Way to Recover Stolen USDT CYBERSPACE HACK PRO
I was a victim of crypto currency scam Late last year. A Facebook imposter convinced me on how I would gain large profit from an authorized crypto company that he claimed helped traders invest and gain profits. I didn't hesitate to invest with them, I never knew they were only scamming me they made me away with my $541,000 woth of crypto. I was in disbelief and discomfort as this was my hard earned money and life savings. After reading positive articles online and testimonies about a licensed group of genius Hacker called Cyber space hack pro an experts in crypto. btc recovery and renders any form of hacking. After having a conversation with them, they were able to recover back my lost money, as a form of appreciation this was the best I could do for them by testifying of their great service and also putting out their Contact out here for anyone who would also need their help Email: Cyber space hack pro @ rescueteam . com OR via WhatsApp +1 (659) 217 9239 1
1 -
Professional Crypto Recovery services with a High Success rate( Digital Hack Recovery )
In recent years, as technology has evolved, so has the world of digital assets, particularly cryptocurrencies. These digital currencies, while offering convenience and security, also come with risks, one of the most significant being theft. Whether through hacking, scams, or simple human error, losing access to crypto assets can be devastating. The process of recovering stolen or lost digital funds, however, is far from straightforward and often seems impossible. Despite the challenges, recovery is not entirely out of reach, especially when you have the right professionals on your side.In my own experience, I was unfortunately a victim of crypto theft. After months of sleepless nights and endless frustration, I realized I needed expert help to try and recover my funds. This is when I decided to reach out to Digital Hack Recovery, a service that specializes in tracking and recovering lost or stolen digital assets. They came highly recommended and had a proven track record in the industry, which gave me hope that my situation might not be hopeless after all.The recovery process began when Digital Hack Recovery used advanced blockchain forensics to track the stolen funds. Thanks to their expertise, they were able to trace the transaction paths and identify the movement of my crypto assets through the blockchain.This sophisticated process requires a deep understanding of the technology behind digital currencies and the ability to navigate the complexities of blockchain transactions.Within just a couple of weeks, Digital Hack Recovery successfully managed to recover over $245,000 of my stolen funds. I was astounded by the speed and efficiency of their work. Throughout the entire process, their communication was exemplary. I was kept updated regularly on the status of the recovery, and they were always available to answer any questions I had. It was clear that they valued transparency and customer service, making what could have been an incredibly stressful experience much easier to navigate.The fees for their services were reasonable.Digital Hack Recovery proved themselves to be a trustworthy and honest agency—qualities that are critical when dealing with sensitive matters like stolen crypto assets.Recovering lost or stolen digital funds is a daunting task, but it is possible with the right help. My experience with Digital Hack Recovery was nothing short of excellent, and I would highly recommend their services to anyone facing similar challenges. Their expertise and dedication to their clients are truly unmatched. Talk to Digital Hack Recovery via their contact below⁚
WhatsApp ⁚+1(915)2151930
Website⁚ https : // digital hack recovery . com
Email address⁚ digital hack recovery @ techie . com1 -
HIRE TRUST GEEKS HACK EXPERT FOR ALL HACKING SERVICES REVIEWS 2025
I never imagined I’d lose access to my Bybit wallet — Especially with $50,000 worth of Bitcoin inside. But one wrong move, a forgotten security detail, and suddenly, my funds were gone. I couldn’t log in. I couldn’t reset anything. I was completely locked out. The panic that hit me was unreal. I tried everything — support tickets, online forums, tutorials, even “recovery tools” — but nothing worked. Days turned into weeks, and hope started to fade fast.
I searched endlessly online, reached out to forums, and tried every recovery method I could find. I even contacted Bybit wallet support, but since it’s a non-custodial wallet, there wasn’t much they could do. As days turned into weeks, my hope started to fade. I truly believed my Bitcoin was gone forever. That’s when I discovered Trust Geeks Hack Expert. At first, I was skeptical. The internet is full of scammers who prey on people like me — desperate and vulnerable. But from the moment I spoke with Trust Geeks Hack Expert, something felt different. They were calm, respectful, professional — and most importantly, honest.
They didn’t promise a miracle. They explained the risks, walked me through their process step by step, and reassured me without giving false hope. I decided to take the leap and trust them, and I am so glad I did. Within just a few days, they reached out with the message I never thought I’d receive: “We’ve recovered your Bitcoin.” Every single dollar was there. Nothing missing. No delays. Just relief, gratitude, and pure disbelief.
Trust Geeks Hack Expert didn’t just recover my money — they restored my peace of mind. They handled everything with care, skill, and absolute integrity. In a world full of uncertainty, they were the one team I could trust when it mattered most. for Assistance support team is available Web h tt p s :// trust geeks hack expert . c o m/-- E m a i l: Trust geeks hack expert @ fast service . com -- TeleGram: Trustgeekshackexpert
2 -
HOW TO FIGHT AGAINST CRYPTO SCAM AND WIN/ HIRA TRUST GEEKS HACK EXPERT
What started as a laid-back night, chatting in a crypto Discord channel, quickly became one of the worst nights of my life. I had been discussing some investment strategies, giving and receiving some tips on trading, ups and downs of the market, when somebody dropped a link into the chat of what looked like a great new trading platform. The chat was hyped, and without thinking twice, I clicked it.
Big mistake. The moment I logged in with my credentials, my stomach just dropped. Something didn't feel right. Within minutes, I saw an unauthorized transaction that had siphoned my Bitcoin wallet of $200,000, and before I could even comprehend what was happening, it was gone. It was as if my financial future had been stolen right before my eyes. Panic set in, and a wave of regret washed over me. How could I, someone who prided themselves on being cautious, fall for such an obvious scam?
I started to post frantically in the Discord group, seeking any advice. And then a guy mentioned the name Trust Geeks Hack Expert. He talked highly of them, saying they had already dealt with similar cases and that they recovered lost crypto in scamming and hacking. It was a long shot, but at this point, I had nothing left to lose. I reached out immediately, and from the very first interaction, I knew I was in good hands. The team was calm, professional, and most importantly, understanding of my frustration. They assured me that my situation wasn't hopeless and that they had advanced tools to track and recover lost funds.
But this was the nail-biting period, and as promised, they pulled off what was seemingly impossible. They recovered my Bitcoin, and I got back access to my wallet. Relief was an understatement; from total despair to absolute triumph in a moment, thanks to them. Yet, they didn't stop there.
Trust Geeks Hack Expert also helped me fortify my digital security, teaching me how to recognize red flags, secure my wallet better, and avoid similar scams in the future. I’ve since become an advocate for crypto safety, warning others in my Discord group about the dangers of phishing links and shady platforms.
If there is one thing that I have learned, it's that one lousy click doesn't have to equate to financial ruin. Trust Geeks Hack Expert gave me a second chance, and for that, for assistance, visit Email: info @ trust geeks hack expert. c o m (Te le Gr am:: Trust geeks hack expert) & w h a t's A p p +1 7 1 9 4 9 2 2 6 9 3 1
1 -
Are you looking for a reliable Hacking Service?
RECOVERY NERD renders the best hacking service on the web. They are the most professional team of hackers in the dark web.
RecoveryNerd offers tons of services:
1. Remote phone hack
2. Crypto Recovery
3. Upgrade gpa
4. School Grades Change
5. Increase credit score
6. Database hack
7. Facebook, Whatsapp hack
8. Remote phone Hack .
9. Remove criminal records.
They also sell high grade techs and hacking chips and gadgets if you are interested in Spying on anyone. They sell software, programs, apps for hacking services.
Interested parties should contact : RECOVERYNERD @ MAIL DOT COM7 -
CRYPTO TRACING AND ASSET RECOVERY EXPERT- TRUST GEEKS HACK EXPERT
I never thought I would find myself in a situation where I would need to rely on a professional service for the recovery of my lost bitcoins and ETH. But there I was, staring at my computer screen in disbelief as I realized that I had fallen victim to a hacking scam. I felt a sinking feeling in the pit of my stomach as I realized that my hard-earned cryptocurrency was gone. During my desperate search for assistance, I identified Trust Geeks Hack Expert a business that specializes in retrieving lost cryptocurrency. In the vain hope that they could assist me in getting my stolen money back, I contacted them And I was relieved and grateful when they replied right away, promising to do every effort to get my bitcoins and Ethereum back. As I waited anxiously for updates from the team at Trust Geeks Hack Expert, I couldn't help but marvel at their unwavering dedication and commitment to helping me. They worked tirelessly around the clock, using their expertise and advanced technology to trace and recover my lost cryptocurrency. Each time they provided me with an update, it filled me with hope and reassurance that my funds would soon be returned to me. After what seemed like an eternity of waiting, I subsequently acquired the word that my Ethereum and Bitcoins had been successfully reestablished. The Trust Geeks Hack Expert team's extraordinary abilities and commitment filled me with relief and thankfulness. I am so grateful to them for their hard work; Send a message: E m a i l .trustgeekshackexpert {At} fast service .. com 6
6 -
If you need a private investigator who can recover stolen funds from scammers or from a wrong cryptocurrency investment then contact (recoverfunds.investigator247 AT gmail DOT com) because they got you covered. They are 100% secured and reliable programmers that has helped me recover my stolen money from a scammer few weeks back .They also deal with all types of hacking related issues such as WhatsApp hack, Facebook hack, Gmail hack, mobile Phone hack, Accounts hack, Erase Criminal Records, Websites Hack, Bitcoin Trade recovery.
-
I faced an unimaginable nightmare. My phone was attacked by a virus that compromised my Binance wallet, allowing hackers to drain all of my Ethereum and Bitcoin, which amounted to around $525,000. I was completely caught off guard, not understanding how this could happen, and was desperate to find a way to recover my stolen funds. I immediately tried to reach out to Binance’s support team, but after several attempts, I realized I couldn’t get through to anyone. My situation felt hopeless, and I had no idea what to do next. In a last-ditch effort, I went to my local police station to file a report, hoping they might be able to help. Unfortunately, they told me they didn’t have the capacity or expertise to deal with cryptocurrency-related fraud, especially one involving a virus. I left the station feeling more defeated than ever. It seemed like my $525,000 was gone for good. Just when I thought there was no hope left, a gentleman approached me at the station. He handed me a business card for Trust Geeks Hack Expert , a company that specializes in recovering lost or stolen cryptocurrency, particularly in cases involving hacking and viruses. Though I was initially skeptical aware of the scams that often plague the crypto world I decided to contact them support E m a i l : Trust geeks hack expert @ ast ser vi ce.. com And Te le gr am. Trust geeks hack expert . My situation was desperate, and I had to at least try. I reached out to Trust Geeks Hack Expert and shared all of the details of the incident, including the fact that my phone had been infected by a virus. I provided them with the transaction details, wallet addresses, and any other relevant information they requested. To my amazement, within just 72 hours, I received a letter from Trust Geeks Hack Expert confirming that they had successfully recovered all of my funds. Not only did they retrieve the $525,000, but they also traced the virus and identified the individuals responsible for the attack. The experience was eye-opening. Losing cryptocurrency due to a virus attack on your phone can feel like an irreversible blow, but it’s not always the end. With the right help, recovery is possible. Trust Geeks Hack Expert proved that there are trustworthy professionals who specialize in cases like mine. If you find yourself in a similar situation, I highly recommend reaching out to Trust Geeks Hack Expert.3
-
RECOVERY FOR YOUR STOLEN CRYPTO INVESTMENT, GUARANTED″ VISIT DIGITAL HACK RECOVERY COMPANY
I began my investment journey on the Telegram platform with a deposit of €85,000. I was optimistic about my decision and, in what felt like no time, I saw my account balance grow to €1,200,000. I was thrilled with my progress and felt confident in my ability to navigate the platform successfully. But that confidence quickly turned into frustration when I tried to withdraw my funds.What should have been a simple process quickly became a nightmare. Despite following all the necessary procedures and reaching out to customer service multiple times, I encountered nothing but delays and obstacles. Each attempt to contact them either went unanswered or resulted in vague responses. As the days passed, it became clear that the company had no intention of letting me access my money. I felt completely powerless and, worse, I started to worry that I might lose everything I had worked so hard to accumulate.It was at this low point that a friend of mine, who had faced a similar situation, recommended Digital Hack Recovery. He had successfully worked with them in the past to recover his own funds and spoke highly of their services. Desperate and exhausted from the lack of progress, I decided to reach out to Digital Hack Recovery.From the moment I contacted them, I knew I was dealing with professionals who genuinely cared about my situation. Their team was highly knowledgeable, and they explained everything to me in a way that made sense. They crafted a customized recovery plan tailored to my specific circumstances and kept me updated every step of the way. What truly set them apart was their transparency and dedication. They didn’t just tell me what they were doing, they involved me in the process, ensuring I felt supported throughout.Thanks to Digital Hack Recovery's persistence and expertise, I was able to recover every single euro I had invested. The relief I felt when my funds were finally restored was indescribable. It felt like a huge weight had been lifted off my shoulders, and I couldn’t have been more grateful for their help.If you’re in a similar situation, struggling to withdraw funds or facing barriers with an investment, I strongly recommend reaching out to Digital Hack Recovery. Their team has the experience, skill, and determination to recover what’s rightfully yours. I truly believe that without their help, I would have never seen my money again. Trust me, you won’t regret working with them. For any crypto recovery and hacking services contact Digital Hack Recovery through⁚
WhatsApp⁚ +19152151930
Email; digital hack recovery @ techie . com
Website⁚ https : // digital hack recovery . com 1
1 -
HOW TO RECOVER LOST BTC
Cyber Space Hack pro provide the best hacking tools and they are well trusted at providing mobile remote spy access, this means it’s possible to spy on a device without a physical touch of the mobile devices.
Track Service, Cyber Space Hack pro provides the best tracking device around the globe, you can have your scammer tracked and get justified.
Cyber Space Hack pro provide the best and safety recovery process, 100% security consciousness is highly observed to ensure that clients are safe, their recovery process can always be trusted and this i can guarantee simply because am also a benefactor of their crypto scam recovery service, November 2024 i got scammed of $1,670.324 USD.
My scammed funds were recovered this year february, 2025. You all need to know that so many testimonies are not real and this has caused chaos and lack of trust on the internet, one can no longer differentiate between the real and fake, we have to take cautions on our decision with hiring a hacker online and as a result of so many scammers on the web one will definitely get scammed before being able to find the right one and for this i write here so you do not get yourself into the hands of scammers by trying to hire a hacker without guarantee.
I hereby advise you all who need hacker service to reach out to Cyberspacehackpro @ rescueteam com or WhatsApp +1 (659) 217 92391 -
DIGITAL HACK RECOVERY EXPERT TO RECOVER STOLEN BITCOIN INVESTMENT CAPITAL
After going through all the comments, I found some that were painful to read, while others were humorous. But one thing became clear to me: many people continue to fall victim to scams simply because they fail to read between the lines. Unfortunately, I was one of those victims in the past. I lost a significant amount of money in a scam that seemed legitimate at first, but I couldn't identify the red flags in time. I was left feeling helpless and frustrated, but through my research, I found a solution that helped me recover my funds: Digital Hack Recovery.Digital Hack Recovery offers a 100% guaranteed recovery service for victims of online scams. Their team of professionals helped me recover my lost funds, and I couldn’t be more grateful. What’s even more valuable is that they’ve also helped me with vetting Bitcoin investments before I make them. Their experts thoroughly evaluate potential investment opportunities, advising me whether to proceed or warning me against scams. This service has been an invaluable resource for me, as I no longer have to navigate the complex and often dangerous world of digital currencies on my own.The truth is, when it comes to Bitcoin scams, only someone with deep knowledge of hacking and digital security can truly recognize the warning signs. Scammers are constantly evolving their tactics, making it difficult for even the most cautious investors to identify fraudulent schemes. That’s why I believe that, in today’s digital world, just as we maintain relationships with trusted doctors and lawyers, we should also have a trustworthy hacker on our side. Having someone who knows how to spot scams and can help you protect your investments is an essential safety net in an increasingly risky online environment.Digital Hack Recovery isn’t just a service for recovering lost funds; they also provide guidance, helping you avoid future scams and make informed decisions about your digital investments. This peace of mind is priceless. If you're ever in a situation where you're uncertain about an investment or have already fallen victim to a scam, I highly recommend reaching out to Digital Hack Recovery. Their expertise and support were instrumental in helping me recover my funds, and I’m sure they can do the same for you.Thanks to their guidance, I now feel much more confident navigating the world of Bitcoin and digital currencies.
Informations⁚
WhatsApp⁚ +19152151930
Email ⁚digital hack recovery @ techie . com
Website⁚ https : // digital hack recovery . com7 -
I know what its like living an endless days of nightmare and paranoia due to some life draining circumstances. Are You in dare need of solutions or answers that require cyber services or ethical hacking ? Probably suspicious of someone dare to You and desire to hack their Phone's or Computer to feel secure again Or got scammed either by cryptocurrency investment scams, romance scams etc. and require urgent recovery of your Money and funds... Cypher Cybersecurity helped Me in my time of turmoil. They are definitely a genie with Tech and guaranteed to deliver on whatever task You bring Up.
You can send them a mail on CYBERCYPHER77@GMAIL ...You did be so amazed You would recommend them as well.1 -
HIRE A GENUINE CRYPTO RECOVERY SERVICE/ CONTACT TRUST GEEKS HACK EXPERT
As a thriller writer, I'm pleased to have crafted suspense for high-stakes disasters, kidnappings, computer hacking break-ins, and political scandals. Nothing in my writer's arsenal had prepared me, however, for the chilling real-world danger of losing my $290,000 hoard of Bitcoin savings. This horror was not to play out in some dimly lit alley or foggy backroom but in my kitchen, fueled by writer's block and Red Bull. I'd been up for 36 hours, writing the denouement of my new book, a crypto heist thriller, ironically enough, when tragedy struck. Bleary-eyed, I attempted to organize my digital files, but in my sleep-deprived state, I reformatted the USB drive containing my private keys in error. I felt as though I'd written myself into a plot twist with no escape. Panic was more crippling to me than any looming deadline. I tried everything, data recovery programs, techie friends, even making a final, desperate call to the manufacturer, whose support person, bless her heart, was more concerned about my hydration status than my financial ruin. I was about to pen my own doleful ending when a midnight Google splash led me to (TRUST GEEKS HACK EXPERT). They'd been featured in a technology blog's "Real-Life Mysteries" series—a fitting discovery for a suspense-addicted author. The tale described their work in recovering funds from ransomware attacks and lost hardware. It was the origin story of a band of cyber superheroes.
I shouted out, anticipating a robo-support reply. But instead, I received a human being, a calming, smart voice that informed me I was not the first writer to make a catastrophe of a blunder (though I might win an award for most sleep-deprived). Their computer forensics division handled my case like a detective division closing a cold case. They took me through each step using words even a writer could understand. They used advanced data reconstruction techniques to retrieve my keys from the wiped drive, an endeavor they compared to un-erasing a book manuscript burned to ashes. Ten nail-sucking days passed, and I opened my email inbox to read: "Funds Recovered." A rush of relief swept over me like the greatest plot twist. My story did have a happy ending, after all. I now backup everything like a mad villain, but I sleep soundly too, knowing (TRUST GEEKS HACK EXPERT) is out there, the little-known heroes of fiction and real life.
REACH OUT TO TRUST GEEKS HACK EXPERT CONTACT SERVICE
E m ai l. Trust geeks hack expert [At] f a s t s e r v i c e [Dot] c o m
Telegram. Trustgeekshackexpert
E m a i l . in fo @ trust geeks hack expert . c o m
Web site. w w w // trust geek s hack expert . c o m1 -
Recovering Bitcoin From A Scammed Or Hacked Wallet - iBolt Cyber Hacker
Losing Bitcoin to a scam or hack can be devastating, but recovery is not always impossible. If you've fallen victim to fraud, iBolt Cyber Hacker is one of the most reputable and effective solutions available for recovering lost or stolen Bitcoin.
Why Choose iBolt Cyber Hacker?
iBolt Cyber Hacker is a specialized cybersecurity team with a strong track record of successfully recovering stolen cryptocurrency. Their expertise in blockchain forensics, ethical hacking, and cyber investigations makes them a reliable choice for victims of crypto theft.
Success Stories & Trustworthiness!
Many victims have successfully recovered their stolen Bitcoin through iBolt Cyber Hacker. Their professionalism, transparency, and commitment to ethical recovery make them a top choice for crypto recovery services.
REACH OUT:
(Mail: ibolt @ cyber- wizard . com)
(Call/Text-whatsapp: +39, 351..105, 3619)
(Homepage: www . iboltcybarhacker . com/) 2
2 -
CRYPTO SCAM RECOVERY & PROFESSIONAL HACKING SERVICES ‖ VISIT DIGITAL HACK RECOVERY
After losing £150,000 in Bitcoin to a scam, I found myself in the role of a treasure hunter, but without a map to guide me through the overwhelming landscape of online deceit. What had begun as an exciting venture into cryptocurrency quickly turned into a disheartening saga of loss and betrayal. The thrill of potential profit had turned into a nightmare, leaving me grappling with feelings of vulnerability and regret.In my search for a way to reclaim my lost assets, I discovered Digital Hack Recovery, a team renowned for their expertise in navigating the complexities of online fraud. Though I was initially skeptical, my desperation pushed me to reach out. During our first conversation, I felt a wave of relief; they not only listened to my story but also approached it with genuine compassion and professionalism. They reassured me that I wasn’t alone in this battle and that recovery was possible.As I engaged with Digital Hack Recovery, I began to grasp the nuances of cryptocurrency scams that had previously eluded me. Their knowledgeable team provided insights into recognizing warning signs and understanding the tactics used by fraudsters. This newfound understanding was empowering and helped shift my perspective from feeling defeated to feeling proactive.The road to recovery was fraught with challenges, requiring careful attention and a strategic mindset. Digital Hack Recovery worked diligently, employing sophisticated methods to trace the digital trails left by the scammers. Throughout the process, they maintained transparent communication, ensuring I was informed about every development, no matter how small.Weeks transformed into months, yet with each step forward, hope grew stronger. Each breakthrough—whether it was tracking a transaction or identifying a key player in the scam—felt like unearthing hidden treasure. Finally, after an intense and thorough effort, I received the news I had longed for: a substantial portion of my stolen funds had been successfully recovered.Regaining access to my wealth was more than just a financial relief; it marked a significant restoration of my peace of mind. I emerged from this ordeal not only with my assets back but also with invaluable lessons about vigilance and the importance of seeking help. With the support of Digital Hack Recovery, I transformed from a victim of fraud into an informed advocate for safe investment practices. My journey was not solely about reclaiming lost wealth but also about rediscovering my confidence and trust in the digital landscape. For any kind of crypto recovery service contact Digital Hack Recovery via⁚
Email; digital hack recovery @ techie . com
Website; https : // digital hack recovery . com
WhatsApp +19152151930

