Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "sql-injection"
-
So...Today I found an SQLI (sql injection , google if you're not aware) in one of our products , I start exploring it , I get my trusty Kali on me workstation . sqlmap etc. Tell my manager it's a true positive... I start exploring the db , half the devs at my manager's place start staring at his screen as I proper fuck a QA db server... I hear a qa guy mention triangulation as sqlmap dumps a uid table in his face . I hear my manager's manager saying 'this has been in our app for so long and we found it just now ? Who found it ?' *manager proudly saying me name* 'He's still working this late ?' ...apparently now my trip to england is getting covered for both me and me gf by the company...18
-
My school.
We have free WiFi access, but you need to login into your personal student account to use it.
Turns out, SQL Injection works.
It gets worse.
Table name "schueler".
SELECT *
Well.
Got all data on all students.
Name, address, phone number, passwords in plain.
I reported it using an anonymous email. Partially fixed. Standard quotes now get eacaped. Still, passwords are now MD5.47 -
So I went for interview today.
.
.
Interviewer : Can u give some theory test about php?
Me : Sir, Can u please open your site?
Interviewer: sure 🙂
Me : Sir, I just logged in as Owner of ur company, Your site is not protected from sql injection.
Interviewer : 😌😌
Me : Sir, test?? 😜
xxxxxxxxxxx -------------------- xxxxxxxxx20 -
CW: The SQL injection vulnerability isn't important because our code is proprietary so hackers won't find it.
Me: <censored>7 -
Mom:What are you studying?
Me:Types of SQL Injection
Mom:U r in engineering?Right?So why are u studying types of Injections?
Me:🤦♂️😂😂9 -
A guy named Valter couldn't register on this website because the developer blacklisted *ALTER*, amongst other words, to prevent SQL injection.11
-
Interviewer: Do you know about SQL injection?
Student: Yessss
Interviewer: Okay, how we can prevent it?
Student: Yes, we should prevent it as prevention is always better than cure. It can lead to data loss and other problems so it can be difficult to fix it if it happens. The best case is that nothing like that takes place. [...]
Interviewer: I get it but how?
Student: By not building any web applications.
[Silence]
Interviewer: Nice, you may go. Do not call us. We will call you.18 -
Alright fuck it, let's release this fucker!
https://lynkz.me is the main domain. The interface is *usable* and nothing more than that. I'll invest more time in that soon but for now, hey, it works.
Api is located at https://api.lynkz.me.
Documentation for this (literally some echoes to the screen but it contains the needed information for now) is at that api url.
Found a bug or a security vulnerability? Please let me know!
Yeah I use mariadb but sql injection is luckily not possible due to quite some sanitization ;)
WARNING: if you make a shortened url and forget the delete key, you won't be able to delete it.
Let's see how this goes 😅111 -
Are you serious? Are you afraid of an SQL injection or something, and instead of properly sanitizing your queries you disallow characters? Or is your software and database so outdated that you're afraid special characters will break it? Goodbye security
 15
15 -
Today was my last day of work, tomorrow i have officially left that place. It's a weird feeling because i'm not certain about the future.
The job was certainly not bad, and after all i read on devrant i'm beginning to believe it was one of the better ones. A nice boss, always something to eat/drink nearby, a relaxed atmosphere, a tolerance for my occasionally odd behaviour and the chance to suggest frameworks. Why i would leave that place, you ask? Because of the thing not on the list, the code, that is the thing i work with all the time.
Most of the time i only had to make things work, testing/refactoring/etc. was cut because we had other things to do. You could argue that we had more time if we did refactor, and i suggested that, but the decision to do so was delayed because we didn't have enough time.
The first project i had to work on had around 100 files with nearly the same code, everything copy-pasted and changed slightly. Half of the files used format a and the other half used the newer format b. B used a function that concatenated strings to produce html. I made some suggestions on how to change this, but they got denied because they would take up too much time. Aat that point i started to understand the position my boss was in and how i had to word things in order to get my point across. This project never got changed and holds hundreds of sql- and xss-injection-vulnerabilities and misses access control up to today. But at least the new project is better, it's tomcat and hibernate on the backend and react in the frontend, communicating via rest. It took a few years to get there, but we made it.
To get back to code quality, it's not there. Some projects had 1000 LOC files that were only touched to add features, we wrote horrible hacks to work with the reactabular-module and duplicate code everywhere. I already ranted about my boss' use of ctrl-c&v and i think it is the biggest threat to code quality. That and the juniors who worked on a real project for the first time. And the fact that i was the only one who really knew git. At some point i had enough of working on those projects and quit.
I don't have much experience, but i'm certain my next job has a better workflow and i hope i don't have to fix that much bugs anymore.
In the end my experience was mostly positive though. I had nice coworkers, was often free to do things my way, got really into linux, all in all a good workplace if there wasn't work.
Now they dont have their js-expert anymore, with that i'm excited to see how the new project evolves. It's still a weird thing to know you won't go back to a place you've been for several years. But i still have my backdoor, but maybe not. :P 16
16 -
If you’re having SQL injection problems, I feel bad for you son, I got 99 tables but… fffffuck. Now i only have one ☹️4
-
Years ago we had a visit from a startup company developing a firewall and I got the chance to talk with one of their devs.
He explained the subtleties of security holes in websites and after I said something about our site being secure thanks to being behind a firewall he gently asked what would happen if he entered a specially crafted test into one of the text fields ... and he gave an example ...
I got a chill, went back to my seat and traced what it would do ...
That was when I learned about sql injection and his example would have killed the DB :/
Before going home I designed a way to secure the input which I then refined over a few days.
We still use that today after 17 years.
That one single sentence really showed to never be to proud of our security and I realized how vulnerable our site was.2 -
IT department created a risk assessment system and asked us to fill out the form.
I found that the form is vulnerable to XSS and possibly SQL injection so I told them and their response was:
"Oh, shit. Please don't tell anyone!"
Of course, it never get fixed :/6 -
I was registering for a website, and on a whim, I used this as my username:
null'); PRINT('Hello');--
And sure enough, the login system went down. The next day it was still down, so I went to Twitter to tell the people running the site that this was why, but to my surprise, I see them saying they had been hacked.
Based on the timing, I'm pretty sure they're referring to this, but they are saying user info was stolen. *facepalm*
They later said they stored passwords salted with a fixed salt and hashed with fucking md5, at which point I was glad not to have done any more business with them.
How incompetent can these fucking people be?!14 -
Laravel is the worst framework ever.
Everything has to be made convenient and easy. That sounds amazing, because developers want to save time, worry less about boilerplate code, right? No more constructors, no more dependency injection, fuck all the tedious OOP shit... RIGHT?
It does one thing well: Make PHP syntax uniform and concise through easily integrated libraries such as Collection and Carbon. But those are actually not really part of the framework... just commonly integrated and associated with Laravel.
The framework itself is completely derailed: You can define code in a callback in the routes file. You can define a controller in the routes file. You can define middleware as a parameter to the route, as a fluent method to the route, you can stack them up in a service provider. Validators can be made in controllers, Request objects, service providers, etc. You can send mail inline, through Mailable objects, through Notification objects, etc.
Everything is macroable, injectable, and definable in a million different places. Ultimate freedom!
Guess what happens when you give 50 developers of various seniority a swiss army knife?
One hammers in a screw with a nail file, the other clips the head from the screw using scissors, and you end up with an unworkable mess and blunt tools.
And don't get me started about Eloquent, the Active Record ORM. It's cute for the simple blog/article/author/comment queries, but starts choking when you want more selective and performant queries or more complex aggregates, and provides such an opaque apple-esque interface which lets people think everything is OK, when in reality it's forcing the SQL server to slowly commit suicide.50 -
If you thought your legacy code was bad, this is what I'm dealing with. The below SQL is stored in a cookie on login and executed to on every further request to determine the user / privileges.
 15
15 -
Our website once had it’s config file (“old” .cgi app) open and available if you knew the file name. It was ‘obfuscated’ with the file name “Name of the cgi executable”.txt. So browsing, browsing.cgi, config file was browsing.txt.
After discovering the sql server admin password in plain text and reporting it to the VP, he called a meeting.
VP: “I have a report that you are storing the server admin password in plain text.”
WebMgr: “No, that is not correct.”
Me: “Um, yes it is, or we wouldn’t be here.”
WebMgr: “It’s not a network server administrator, it’s SQL Server’s SA account. Completely secure since that login has no access to the network.”
<VP looks over at me>
VP: “Oh..I was not told *that* detail.”
Me: “Um, that doesn’t matter, we shouldn’t have any login password in plain text, anywhere. Besides, the SA account has full access to the entire database. Someone could drop tables, get customer data, even access credit card data.”
WebMgr: “You are blowing all this out of proportion. There is no way anyone could do that.”
Me: “Uh, two weeks ago I discovered the catalog page was sending raw SQL from javascript. All anyone had to do was inject a semicolon and add whatever they wanted.”
WebMgr: “Who would do that? They would have to know a lot about our systems in order to do any real damage.”
VP: “Yes, it would have to be someone in our department looking to do some damage.”
<both the VP and WebMgr look at me>
Me: “Open your browser and search on SQL Injection.”
<VP searches on SQL Injection..few seconds pass>
VP: “Oh my, this is disturbing. I did not know SQL injection was such a problem. I want all SQL removed from javascript and passwords removed from the text files.”
WebMgr: “Our team is already removing the SQL, but our apps need to read the SQL server login and password from a config file. I don’t know why this is such a big deal. The file is read-only and protected by IIS. You can’t even read it from a browser.”
VP: “Well, if it’s secured, I suppose it is OK.”
Me: “Open your browser and navigate to … browse.txt”
VP: “Oh my, there it is.”
WebMgr: “You can only see it because your laptop had administrative privileges. Anyone outside our network cannot access the file.”
VP: “OK, that makes sense. As long as IIS is securing the file …”
Me: “No..no..no.. I can’t believe this. The screen shot I sent yesterday was from my home laptop showing the file is publicly available.”
WebMgr: “But you are probably an admin on the laptop.”
<couple of awkward seconds of silence…then the light comes on>
VP: “OK, I’m stopping this meeting. I want all admin users and passwords removed from the site by the end of the day.”
Took a little longer than a day, but after reviewing what the web team changed:
- They did remove the SQL Server SA account, but replaced it with another account with full admin privileges.
- Replaced the “App Name”.txt with centrally located config file at C:\Inetpub\wwwroot\config.txt (hard-coded in the app)
When I brought this up again with my manager..
Mgr: “Yea, I know, it sucks. WebMgr showed the VP the config file was not accessible by the web site and it wasn’t using the SA password. He was satisfied by that. Web site is looking to beat projections again by 15%, so WebMgr told the other VPs that another disruption from a developer could jeopardize the quarterly numbers. I’d keep my head down for a while.”8 -
Great news, our company's has a brand new security-first product, with an easy to use API and a beautiful web interface.
It is SQL-injection-enabled, XSS-compatible, logins are optional (if you do not provide a password, you are logged in as admin).
The json-api has custom-date formats, bools are any of "1", "0", 1, 0, false or null (but never true). Numbers are strings or numbers. Utf-8 is not supported. Most of our customers use special characters.
The web interface is using plain bootstrap, and because of XSS it is really easy to customize everything.
How the hell this product got launched is beyond me.10 -
when was i feeling like a fucking dev badass ?
that time when i exploited an sql injection on a news website and added a post with title "Admin please secure your website ;] "
.
.
i was feeling like hacker man 😅😂😂 -
Worst legacy experience...
Called in by a client who had had a pen test on their website and it showed up many, many security holes. I was tasked with coming in and implementing the required fixes.
Site turned out to be Classic ASP built on an MS Access database. Due to the nature of the client, everything had to be done on their premises (kind of ironic but there you go). So I'm on-site trying to get access to code and server. My contact was *never* at her desk to approve anything. IT staff "worked" 11am to 3pm on a long day. The code itself was shite beyond belief.
The site was full of forms with no input validation, origin validation and no SQL injection checks. Sensitive data stored in plain text in cookies. Technical errors displayed on certain pages revealing site structure and even DB table names. Server configured to allow directory listing in file stores so that the public could see/access whatever they liked without any permission or authentication checks. I swear this was written by the child of some staff member. No company would have had the balls to charge for this.
Took me about 8 weeks to make and deploy the changes to client's satisfaction. Could have done it in 2 with some support from the actual people I was suppose to be helping!! But it was their money (well, my money as they were government funded!).1 -
My first testing job in the industry. Quite the rollercoaster.
I had found this neat little online service with a community. I signed up an account and participated. I sent in a lot of bug reports. One of the community supervisors sent me a message that most things in FogBugz had my username all over it.
After a year, I got cocky and decided to try SQL injection. In a production environment. What can I say. I was young, not bright, and overly curious. Never malicious, never damaged data or exposed sensitive data or bork services.
I reported it.
Not long after, I got phone calls. I was pretty sure I was getting charged with something.
I was offered a job.
Three months into the job, they asked if I wanted to do Python and work with the automators. I said I don't know what that is but sure.
They hired me a private instructor for a week to learn the basics, then flew me to the other side of the world for two weeks to work directly with the automation team to learn how they do it.
It was a pretty exciting era in my life and my dream job.4 -
You can't imagine how many lines of pure and utter horseshit, seemingly written in PHP, I had to dig through this whole weekend. (relating to my 2 previous rants)
How is it even possible to write code this unbelievably ugly?
Examples:
- includes within loops
- included files use variables from parent files
- start- and endtags separated to different files
- SQL queries generated by string concatenation, no safety measures at all (injection)
- repeating DB calls within loops
- multiple directories with the same code (~40 files), only different by ~8 lines, copied
- a mixture of <?php echo ... ?> and <?= ... ?>
- a LOT of array accesses and other stuff prefixed with "@" (suppress error messages)
- passwords in cleartext
- random non-RESTful page changes with a mixture of POST and GET
- GET parameters not URL-encoded
- ...
My boss told me it took this guy weeks and weeks of coding to write this tool (he's an "experienced dev", of course WITHOUT Git).
Guess what?
It took me only 20 hours and about 700 lines of code.
I must confess, since this task, I don't hate PHP anymore, I just simply hate this dev to death.
Addendum: It's Monday, 5:30am. Good night. 😉12 -
Just looked at the anonymous analytics I collect on the security/privacy blog.
No SQL Injection attacks yet (would be useless anyways as I don't use MySQL/MariaDB for the databasing.
Directory Traversal attacks. Really? 🤣
Nice try, guys.39 -
To anyone that isn't sanitizing the input on their websites: I know where you live. You told me, remember?
 2
2 -
I HATE working with MS Office products. Yes, Access, I'm looking at you, you backwards, whanabe database reject! You're invalid as a serious SQL database and retarded as an data application suite.
VBA, make up your MIND with your damn function calls! Either require me to use parenthesis or don't! I'm sick of this conditional parenthesis sh*t!
While we're talking about not making up your mind... screw 'sub', you half wit language! Either use functions like a real language or go the f&$k home and make room for a language that knows what it's doing!
Oh!!! WHY... WHY! do you have null AND... NOTHING?! Who... Who... WHO invented "nothing"?! And what sick joke are you playing at with isnull() and empty()??? How many damn ways so you need to test for "no value"?!?!
Access... That's right, I'm not done with you yet... How is it you've survived this damn long in the business world with all of the databases you corrupt? Sure, you suck as a real database, but at least have some freaking pride that people even USE you! How DARE your corrupt yourself with the regularity you seem to have! I wish my bowel movements were as regular as your database corruptions, for the love of humanity.
F$@k you, VBA! F@&k you, Access! F$#k you, MS Office! And Fuuuuuu$k YOU Microsoft for shoving these half assed reject tools down my throat!
I hope your cloud uses Access as a back end and gets some injection virus.
*Takes deep breath* need to say that.10 -
While watching season 2 of Star Trek Discovery, it was nice to learn SQL is alive and well in the 23rd century. Also, that there are still idiots that don't defend against injection on a warp-capable spaceship with transporter technology.
 3
3 -
So DevRant asked me to put my skills on my profile, I'm like:
you wanna know my languages, well, I'm a human Android sipping on Java, got C++ grade phy-SQL education. but some idiot bashed me on my </head> so swift, that I objectively-c angular stars, everywhere. Recoved by a js injection. ASCII too in snowy Cs4 -
The gift that keeps on giving... the Custom CMS Of Doom™
I've finally seen enough evidence why PHP has such a bad reputation to the point where even recruiters recommended me to remove my years of PHP experience from the CV.
The completely custom CMS written by company <redacted>'s CEO and his slaves features the following:
- Open for SQL injection attacks
- Remote shell command execution through URL query params
- Page-specific strings in most core PHP files
- Constructors containing hundreds of lines of code (mostly used to initialize the hundreds of properties
- Class methods containing more than 1000 lines of code
- Completely free of namespaces or package managers (uber elite programmers use only the root namespace)
- Random includes in any place imaginable
- Methods containing 1 line: the include of the file which contains the method body
- SQL queries in literally every source file
- The entrypoint script is in the webroot folder where all the code resides
- Access to sensitive folders is "restricted" by robots.txt 🤣🤣🤣🤣
- The CMS has its own crawler which runs by CRONjob and requests ALL HTML links (yes, full content, including videos!) to fill a database of keywords (I found out because the server traffic was >500 GB/month for this small website)
- Hundreds of config settings are literally defined by "define(...)"
- LESS is transpiled into CSS by PHP on requests
- .......
I could go on, but yes, I've seen it all now.12 -
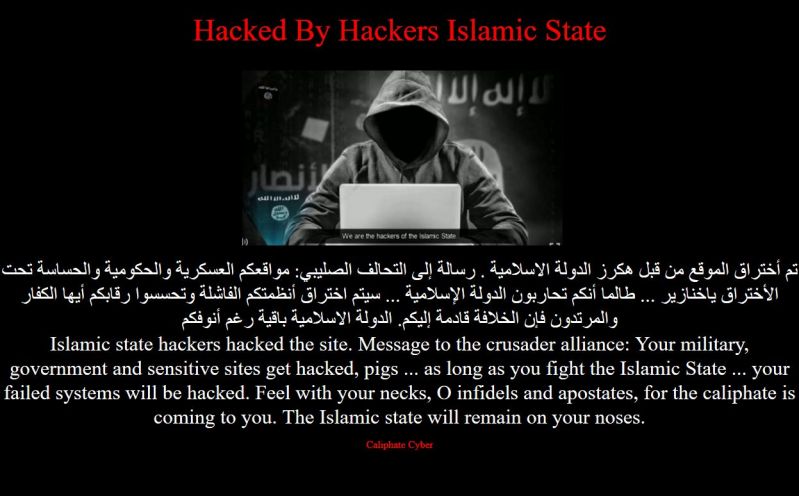
This fucking stupid asshole developer, wrote every single SQL execution with string formatting. Made me a full sleepless night fixing this shit. Isn’t this a classical SQL injection sample?
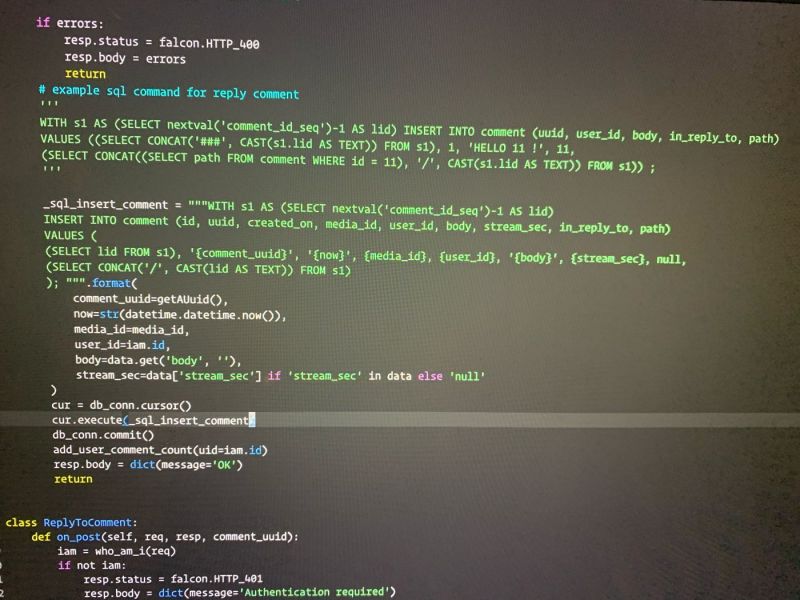 15
15 -
I once had to literally hack a Joomla 1.5.x site for a client, because they did not find the passwords (hosting, cms, ftp, mysql). After 5 minutes and a SQL injection I was in like flynn.
The site was already full of hidden links to viagra sellers and stuff... 😂1 -
So my marketing dept request us to perform a SQL injection to someone's bank account. I refuse to do it.
1. Most bank no longer use Relational Database , they use something like NoSQL Database.
2. Even if the bank Use Relational Database system, I assume their security must be high, validating my session maybe...
3. I am not going to do shit like this for illegal purposes, well this task sounds super illegal to me
4. Hacking is not a part of my job description. I was hired to be a Senior Fullstack Mobile App Developer.
This is screwed up !23 -
1. Buy a road
2. Name it after an sql injection
3. Have mail delivered to you
4. ...
5. Profit... I guess?7 -
Going through the name list of Manifesto for Responsible Software Development at http://manifesto.responsiblesoftware.org/... when suddenly......
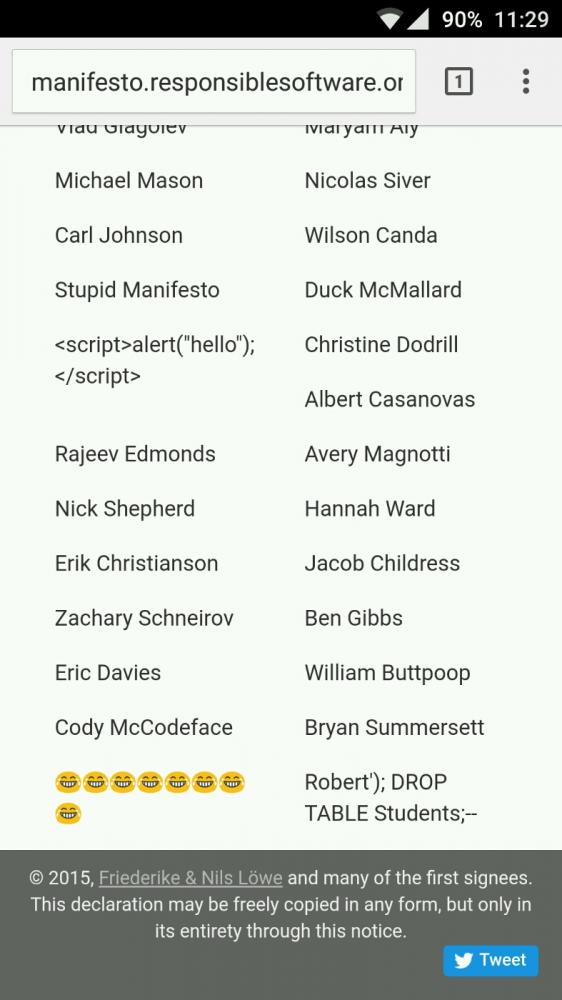 4
4 -
A Month ago...
Me: when are you going to complete the report
Friend: we can do it in minutes
Me: you can't Ctrl + c and Ctrl +v as there is plagiarism check
Friend: we have spin bot
Me: you do that now itself . if something happens? You can join me .
Friend: just chill
Now ...
Me: done with report
Friend: feeding it to spin bot!
Feeds text related to database security....
Spin bot:
Garbage collector == city worker
SQL statements == SQL explanation
SQL queries == SQL interrogation
SQL injection == SQL infusion
Attack == assault
Malicious == noxious
Data integrity == information uprightness
Sensitive == touchy
.....
Me: told you so...
**spin not == article rewriter3 -
Easy cop out for people who wrote code vulenerable to SQL injection: It's not a bug, it's a feature that let's users search using SQL syntax.1
-
Before 10 years, a WordPress site hacked with sql injection. They had access to site, they modified many php files and installed commands to download random malwares from over the internet.
At first I didn't know that it hacked and I was trying to remove any new file from the server. That was happening every 1-2 days for a week.
Then I decided to compare every WordPress file with the official, it was too many files, and I did it manually notepad side notepad!! :/
Then I found about over 50 infected files with the malware code.
Cleaned and finished my job.
No one else knows that I did a lot of hard job.2 -
I've found and fixed any kind of "bad bug" I can think of over my career from allowing negative financial transfers to weird platform specific behaviour, here are a few of the more interesting ones that come to mind...
#1 - Most expensive lesson learned
Almost 10 years ago (while learning to code) I wrote a loyalty card system that ended up going national. Fast forward 2 years and by some miracle the system still worked and had services running on 500+ POS servers in large retail stores uploading thousands of transactions each second - due to this increased traffic to stay ahead of any trouble we decided to add a loadbalancer to our backend.
This was simply a matter of re-assigning the IP and would cause 10-15 minutes of downtime (for the first time ever), we made the switch and everything seemed perfect. Too perfect...
After 10 minutes every phone in the office started going beserk - calls where coming in about store servers irreparably crashing all over the country taking all the tills offline and forcing them to close doors midday. It was bad and we couldn't conceive how it could possibly be us or our software to blame.
Turns out we made the local service write any web service errors to a log file upon failure for debugging purposes before retrying - a perfectly sensible thing to do if I hadn't forgotten to check the size of or clear the log file. In about 15 minutes of downtime each stores error log proceeded to grow and consume every available byte of HD space before crashing windows.
#2 - Hardest to find
This was a true "Nessie" bug.. We had a single codebase powering a few hundred sites. Every now and then at some point the web server would spontaneously die and vommit a bunch of sql statements and sensitive data back to the user causing huge concern but I could never remotely replicate the behaviour - until 4 years later it happened to one of our support staff and I could pull out their network & session info.
Turns out years back when the server was first setup each domain was added as an individual "Site" on IIS but shared the same root directory and hence the same session path. It would have remained unnoticed if we had not grown but as our traffic increased ever so often 2 users of different sites would end up sharing a session id causing the server to promptly implode on itself.
#3 - Most elegant fix
Same bastard IIS server as #2. Codebase was the most unsecure unstable travesty I've ever worked with - sql injection vuns in EVERY URL, sql statements stored in COOKIES... this thing was irreparably fucked up but had to stay online until it could be replaced. Basically every other day it got hit by bots ended up sending bluepill spam or mining shitcoin and I would simply delete the instance and recreate it in a semi un-compromised state which was an acceptable solution for the business for uptime... until we we're DDOS'ed for 5 days straight.
My hands were tied and there was no way to mitigate it except for stopping individual sites as they came under attack and starting them after it subsided... (for some reason they seemed to be targeting by domain instead of ip). After 3 days of doing this manually I was given the go ahead to use any resources necessary to make it stop and especially since it was IIS6 I had no fucking clue where to start.
So I stuck to what I knew and deployed a $5 vm running an Nginx reverse proxy with heavy caching and rate limiting linked to a custom fail2ban plugin in in front of the insecure server. The attacks died instantly, the server sped up 10x and was never compromised by bots again (presumably since they got back a linux user agent). To this day I marvel at this miracle $5 fix.1 -
Senior showing fellow intern what SQL injection is on the app the intern created :
Senior : "then I hit enter and the query get executed and...
Intern : "don't you dare hitting enter!!!"4 -
"at least 1 special character except < ' ; / - [ % _"
Also known as "Hey, look at me, I'm vulnerable to SQL injection and a lot of other fun stuff!"3 -
So this is how they "teach" us in school...As a part time dev I was completely shocked when I saw this in our materials. What do you think? Should I drop the teachers tables to give him a lesson?
 14
14 -
It has been bugging the shit out of me lately... the sheer number of shit-tier "programmers" that have been climbing out of the woodwork the last few years.
I'm not trying to come across as elitist or "holier than thou", but it's getting ridiculous and annoying. Even on here, you have people who "only do frontend development" or some other lame ass shit-stain of an excuse.
When I first started learning programming (PHP was my first language), it wasn't because I wanted to be a programmer. I used to be a member (my account is still there, in fact) of "HackThisSite", back when I was about 12 years old. After hanging out long enough, I got the hint that the best hackers are, in essence, programmers.
Want to learn how to do SQL injection? Learn SQL - write a program that uses an SQL database, and ask yourself how you would exploit your own software.
Want to reverse engineer the network protocol of some proprietary software? Learn TCP/IP - write a TCP/IP packet filter.
Back then, a programmer and a hacker were very much one in the same. Nowadays, some kid can download Python, write a "hello, world" program and they're halfway to freelancing or whatever.
It's rare to find a programmer - a REAL programmer, one who knows how the systems he develops for better than the back of his hand.
These days, I find people want the instant gratification that these simpler languages provide. You don't need to understand how virtual memory works, hell many people don't even really understand C/C++ pointers - and that's BASIC SHIT right there.
Put another way, would you want to take your car to a brake mechanic that doesn't understand how brakes work? I sure as hell wouldn't.
Watching these "programmers" out there who don't have a fucking clue how the code they write does what it does, is like watching a grown man walk around with a kid's toolbox full or plastic toys calling himself a mechanic. (I like cars, ok?!)
*sigh*
Python, AngularJS, Bootstrap, etc. They're all tools and they have their merits. But god fucking dammit, they're not the ONLY damn tools that matter. Stop making excuses *not* to learn something, Mr."IOnlyDoFrontEnd".
Coding ain't Lego's, fuckers.36 -
> IHateForALiving: I have added markdown on the client! Now the sys admin can use markdown and it's going to be rendered as HTML
> Team leader: ok, I've seen you also included some pics of the tests you made. It's nice, there's no XSS vulnerabilities, now I want you to make sure you didn't introduce any SQL injection too. Post the results of the tests in the tickets, for everybody to see.
I've been trying to extract from him for 15 minutes how sending a text through a markdown renderer on the client is supposed to create a SQL injection on the server, I've been trying to extract from him how showing all of this to the world would improve our reputation.
I miserably failed, I don't know how the fuck am I supposed to test this thing and if I a colleague wasted time to make sure some client-side rendering didn't create a SQL injection I'd make sure to point and laugh at them every time they open their mouth.9 -
Guess what? 😱 WordPress has probably an SQL injection vulnerability. Check it out and fix your installations, when more info will be known:
https://twitter.com/ircmaxell/...12 -
> Young dev apprentice me pair programming with another developer
> Dude checks bug report of a customer, saying something about a "Blind SQL Injection"
> Young me asking what that "Blind" part means
> "Dunno man, maybe u gotta close your eyes when hacking this"
Guess what, the issue was never fixed -
i understand some developers like to write wrapper functions to handle tedious things, I even understand how to write dynamic SQL queries, but for the love of fucking god and sanity, NEVER FUCKING DO THIS!!!!
Yes its PHP, but its not even bad PHP, its a fucking abomination from hell of PHP. rant mysql legacy code gone wrong bourbon lots of bourbon why the fuck god no php sql injection ftw what in the flying fuck30
rant mysql legacy code gone wrong bourbon lots of bourbon why the fuck god no php sql injection ftw what in the flying fuck30 -
SQL injection holes everywhere... The original author of the product put concatenated SQL queries throughout the whole application. If it's not the client asked for a penetration test, we as developers wouldn't even be given chance to fix this shit.
I'm actually glad to have the chance. I can't live seeing them every day but force myself to ignore them.8 -
The IT guy at client made a spaghetti code website to replace their time entry software. I come in to “finish it up in a week to two” (just me). I start by removing 1200+ lines of convoluted data access code that doesn’t work, SQL injection prone too. I quickly gave up and started from scratch; just copyied some of his actually decent HTML.
Friday, he proceeded to try to install node on the server and run main.JS. Now he’s all concerned my repo is too complex because he can’t deploy a static website 🙁
He didn’t ask me how it gets deployed nor did he listen when I said “node is NOT THE BACKEND we have .NET core for that”.🤦♂️
I’m gonna spend a week writing documentation at 5th grade level and hand holding him so he understands how this code works because he’s going to be the one maintaining it.1 -
Well on my last full-time job, that ware using cookies for authentication (not something new, eh?). The thing is, you see, the cookies had the 'accountId' which if you change to another number, kaboom you're that account, oh but that was not all, there was an option to mark the account type in there 'accountType', which was kind of obvious in VLE (virtual learning environment), 'Teacher', 'Student', 'Manager' put what of those values and boom you are that role for the session
Thing was open of SQL injection from the login form, from said cookies and form every part you can pass input to it, when I raised the question to my TL he said 'no one is going to know about thatt, I don't see what is the problem', then escalated to higher management 'oh well speak to *tl_guy*'
Oh and bonus points for it being written in ASP CLASSIC in 2014+ (I was supposed to rewrite, but ended up patching ASP code and writing components in PHP)
In 2015-2016, in a private college, charging kind-of big money per year1 -
So as applying for an internship to a new company, they wanted me to make an account and do some things to get use to the website... That's great, until I learned their website is fucking garbage!
Takes 5 seconds to load any page (they import and link so much shit, it's poorly optimized), their website is vulnerable to Javascript injection (in many different places), im sure it will be vulnerable to sql injection too.
Their design looks bad, icons are terrible, no common design flow, super busy. And they are taking about using machine learning and big data? Bitch you need to fucking make your site usable first!! If contacted them and will give them 30 days to fix their shit before I write about it -
Security!
Offensive and defensive at both code and infrastructure levels.
So many times I see devs not give a flying pancake about security. Whether it be rolling integers for sql injection or permission guarding to prevent someone executing something they shouldn't.
Why is security in this industry always the last thing to be concerned about when it's the first thing that's going to kill your business.
😓7 -
rant & question
Last year I had to collaborate to a project written by an old man; let's call him Bob. Bob started working in the punch cards era, he worked as a sysadmin for ages and now he is being "recycled" as a web developer. He will retire in 2 years.
The boss (that is not a programmer) loves Bob and trusts him on everything he says.
Here my problems with Bob and his code:
- he refuses learning git (or any other kind of version control system);
- he knows only procedural PHP (not OO);
- he mixes the presentation layer with business logic;
- he writes layout using tables;
- he uses deprecated HTML tags;
- he uses a random indentation;
- most of the code is vulnerable to SQL injection;
- and, of course, there are no tests.
- Ah, yes, he develops directly on the server, through a SSH connection, using vi without syntax highlighting.
In the beginning I tried to be nice, pointing out just the vulnerabilities and insisting on using git, but he ignored all my suggestions.
So, since I would have managed the production server, I decided to cheat: I completely rewrote the whole application, keeping the same UI, and I said the boss that I created a little fork in order to adapt the code to our infrastructure. He doesn't imagine that the 95% of the code is completely different from the original.
Now it's time to do some changes and another colleague is helping. She noticed what I did and said that I've been disrespectful in throwing away the old man clusterfuck, because in any case the code was working. Moreover he will retire in 2 years and I shouldn't force him to learn new things [tbh, he missed at least last 15 years of web development].
What would you have done in my place?10 -
I knew I had found the right group of friends when one of them suggested we try SQL Injection on the instant messaging feature of the bowling alley console.
Unrelated, do people not think, "hmm, that seems like an unnecessary feature?"2 -
The day after I delivered a secure programming course to our junior devs.
Junior dev: I can't figure out what's happening when I generate this sql.
Me: what do you mean generating ... It should be a prepared statement..
Junior dev: no I'm just generating the strings from the form
Me: ... Let's try this again.... -
This is a true story. We had this subject, called “Web Design” (really, “design”), where we studied HTML, CSS, JavaScript, PHP and MySQL (confusing, right?). And when we get the PHP (e-)book, it was this old PDF (probably downloaded illegally) teaching the legacy 4.0 version of PHP. Anyway, when we had to develop the final project, the sane professor allowed us to use a newer version of PHP — 5.2, released on 2008. I had to follow the rules, so I developed probably the less secure web application I will ever develop. That means no protection from SQL injection, XSS vulnerable and a bunch of other security holes… And that’s how they liked it developed!3
-
My day so far:
"No, we can't just make that public."
"See this? That's a SQL injection..."
"We have output escaping, please use it..." -
An enormous government project that leaves the tax office's database along with all backups exposed to SQL injection.
I know for a fact that the tax office database in at least one country only got a cold backup a few years ago, so it's more likely than you think.
Although around that time someone hacked the public transport company and bought a 12 month ticket for free as PoC and he got jail for it so the risk is quite high.5 -
I have quite a few of these so I'm doing a series.
(2 of 3) Flexi Lexi
A backend developer was tired of building data for the templates. So he created a macro/filter for our in house template lexer. This filter allowed the web designers (didn't really call them frond end devs yet back then) could just at an SQL statement in the templates.
The macro had no safe argument parsing and the designers knew basic SQL but did not know about SQL Injection and used string concatination to insert all kinds of user and request data in the queries.
Two months after this novel feature was introduced we had SQL injections all over the place when some piece of input was missing but worse the whole product was riddled with SQLi vulnerabilities.2 -
I learned recently that you can inject SQL lines in some fields like Passwords or usernames on some websites. (Hacky hacky)
At work there is this intra website that is used to manage the parts of the radios and computers we repair.
Each piece has a specific number, and there is a tree with every pieces for each radio/computer.
When we get to repair one, we gotta change the pieces virtualy on the website. Sadly sometimes, the virtual pieces aren't marked like they followed the whole Radio from the place they come to the place we repair (we need it to replace the piece). People are just not doing their job, so we have to send emails and call for them do it so we can repair it. (This is already fucked up.)
Today, I had to replace a piece, but it was marked like it's not there. I called the guy, and it seems like he is on a vacation for weeks. My superior was super annoyed due to the urge of this task.
Guess who managed to change the _mainlocation_ of the _piece_ in the _radiopieces_ table. (Not actual names, you malicious cunt)
I spent 3 hours looking for the name of the fields and table. I don't know how many times I had to refresh the dam page to see I failed once again.
Hopefully I didn't have to guess all of them. Also the joy when I realised I succeed !!!
No one bats a eyes, and I'm here, feeling infinitely superior, as I might get punished for wanting to do my job.
I know it's basic moves to some of you, but dam it felt good.
Conclusion: Do what you have to, specially when it takes 5 minutes and people need it.10 -
Just came across this gem. What's wrong with it??
Yes, the threat of SQL injection here is a legit response, but in this particular case that's not the answer I'm looking for.
Hint: This method gets called a lot! 15
15 -
I am doing some freelance work for a client who is thankfully mindful about security. I found out that they are so strict with their access because they had a huge data breach last year.
Today I was given access to their repo for connecting to their AS400. In the docker file the username and password were included and were the same for dev and prod. They also are performing no sql injection prevention. They are just joining strings together.1 -
# Retrospective as Backend engineer
Once upon a time, I was rejected by a startup who tries to snag me from another company that I was working with.
They are looking for Senior / Supervisor level backend engineer and my profile looks like a fit for them.
So they contacted me, arranged a technical test, system design test, and interview with their lead backend engineer who also happens to be co-founder of the startup.
## The Interview
As usual, they asked me what are my contribution to previous workplace.
I answered them with achievements that I think are the best for each company that I worked with, and how to technologically achieve them.
One of it includes designing and implementing a `CQRS+ES` system in the backend.
With complete capability of what I `brag` as `Time Machine` through replaying event.
## The Rejection
And of course I was rejected by the startup, maybe specifically by the co-founder. As I asked around on the reason of rejection from an insider.
They insisted I am a guy who overengineer thing that are not needed, by doing `CQRS+ES`, and only suitable for RND, non-production stuffs.
Nobody needs that kind of `Time Machine`.
## Ironically
After switching jobs (to another company), becoming fullstack developer, learning about react and redux.
I can reflect back on this past experience and say this:
The same company that says `CQRS+ES` is an over engineering, also uses `React+Redux`.
Never did they realize the concept behind `React+Redux` is very similar to `CQRS+ES`.
- Separation of concern
- CQRS: `Command` is separated from `Query`
- Redux: Side effect / `Action` in `Thunk` separated from the presentation
- Managing State of Application
- ES: Through sequence of `Event` produced by `Command`
- Redux: Through action data produced / dispatched by `Action`
- Replayability
- ES: Through replaying `Event` into the `Applier`
- Redux: Through replay `Action` which trigger dispatch to `Reducer`
---
The same company that says `CQRS` is an over engineering also uses `ElasticSearch+MySQL`.
Never did they realize they are separating `WRITE` database into `MySQL` as their `Single Source Of Truth`, and `READ` database into `ElasticSearch` is also inline with `CQRS` principle.
## Value as Backend Engineer
It's a sad days as Backend Engineer these days. At least in the country I live in.
Seems like being a backend engineer is often under-appreciated.
Company (or people) seems to think of backend engineer is the guy who ONLY makes `CRUD` API endpoint to database.
- I've heard from Fullstack engineer who comes from React background complains about Backend engineers have it easy by only doing CRUD without having to worry about application.
- The same guy fails when given task in Backend to make a simple round-robin ticketing system.
- I've seen company who only hires Fullstack engineer with strong Frontend experience, fails to have basic understanding of how SQL Transaction and Connection Pool works.
- I've seen company Fullstack engineer relies on ORM to do super complex query instead of writing proper SQL, and prefer to translate SQL into ORM query language.
- I've seen company Fullstack engineer with strong React background brags about Uncle Bob clean code but fail to know on how to do basic dependency injection.
- I've heard company who made webapp criticize my way of handling `session` through http secure cookie. Saying it's a bad practice and better to use local storage. Despite my argument of `secure` in the cookie and ability to control cookie via backend.18 -
A great and very common web attack is known as 'SQL injection'.
So if I am using MongoDB, does that become 'NoSQL injection'?1 -
I just found a vulnerability in my companies software.
Anyone who can edit a specific config file could implant some SQL there, which would later be executed by another (unknowing) user from within the software.
The software in question is B2B and has a server-client model, but with the client directly connecting to the database for most operations - but what you can do should be regulated by the software. With this cute little exploit I managed to drop a table from my test environment - or worse: I could manipulate data, so when you realize it it's too late to simply restore a DB backup because there might have been small changes for who knows how long. If someone was to use this maliciously the damages could be easily several million Euros for some of our customers (think about a few hundred thousand orders per day being deleted/changed).
It could also potentially be used for data exfiltration by changing protection flags, though if we're talking industry espionage they would probably find other ways and exploit the OS or DB directly, given that this attack requires specific knowledge of the software. Also we don't promise to safely store your crabby patty recipe (or other super secret secrets).
The good thing is that an attack would only possible for someone with both write access to that file and insider knowledge (though that can be gained by user of the software fairly easily with some knowledge of SQL).
Well, so much for logging off early on Friday.5 -
Teacher : You don't have to enter quotation marks: it makes the website crash, I don't know why. We will add a message to warn you.
Me : Can i play with it ? :)2 -
I hate those questions like "where do you see yourself on five years?" Or "tell me a time when you had to [insert leadership activity here]" where the obvious answers are something inane and managerial.
I also hate those questions that come up a lot when I say I know SQL where they ask me to do some inane, unnatural SQL thing in a statement rather than a procedure or a function.
Also see these: https://devrant.io/rants/136331/...
https://devrant.io/rants/132198/... -
Most of the companies visiting my campus for placements are hiring people with high CGPA and less knowledge and leaving (not even allowing for taking tests) the ones with good technical knowledge with less CGPA 🙁. So I hacked the placement portal developed by a PLACED, HIGH CGPA Candidate using SQL Injection and got access to all the student accounts 😄2
-
!rant Update On My Scammer Job.
Today, The authority saw the ads , and take my case. My employers are not letting me leave and authorities notice everything...
Reference :
https://marketing-interactive.com/o...
https://devrant.com/rants/4147960/...
https://devrant.com/rants/4140649/...7 -
It was the last year of high school.
We had to submit our final CS homework, so it gets reviewed by someone from the ministry of education and grade it. (think of it as GPA or whatever that is in your country).
Now being me, I really didn’t do much during the whole year, All I did was learning more about C#, more about SQL, and learn from the OGs like thenewboston, derek banas, and of course kudvenkat. (Plus more)
The homework was a C# webform website of whatever theme you like (mostly a web store) that uses MS Access as DB and a C# web service in SOAP. (Don’t ask.)
Part 1/2:
Months have passed, and only had 2 days left to deadline, with nothing on my hand but website sketches, sample projects for ideas, and table schematics.
I went ahead and started to work on it, for 48 hours STRAIGHT.
No breaks, barely ate, family visited and I barely noticed, I was just disconnected from reality.
48 hours passed and finished the project, I was quite satisfied with my it, I followed the right standards from encrypting passwords to verifying emails to implementing SQL queries without the risk of SQL injection, while everyone else followed foot as the teacher taught with plain text passwords and… do I need to continue? You know what I mean here.
Anyway, I went ahead and was like, Ok, lets do one last test run, And proceeded into deleting an Item from my webstore (it was something similar to shopify).
I refreshed. Nothing. Blank page. Just nothing. Nothing is working, at all.
Went ahead to debug almost everywhere, nothing, I’ve gone mad, like REALLY mad and almost lose it, then an hour later of failed debugging attempts I decided to rewrite the whole project from scratch from rebuilding the db, to rewriting the client/backend code and ui, and whatever works just go with it.
Then I noticed a loop block that was going infinite.
NEVER WAIT FOR A DATABASE TO HAVE MINIMUM NUMBER OF ROWS, ALWAYS ASSUME THAT IT HAS NO VALUES. (and if your CPU is 100%, its an infinite loop, a hard lesson learned)
The issue was that I requested 4 or more items from a table, and if it was less it would just loop.
So I went ahead, fixed that and went to sleep.
Part 2/2:
The day has come, the guy from the ministry came in and started reviewing each one of the students homeworks, and of course, some of the projects crashed last minute and straight up stopped working, it's like watching people burning alive.
My turn was up, he came and sat next to me and was like:
Him: Alright make me an account with an email of asd@123.com with a password 123456
Me: … that won't work, got a real email?
Him: What do you mean?
Me: I implemented an email verification system.
Him: … ok … just show me the website.
Me: Alright as you can see here first of all I used mailgun service on a .tk domain in order to send verification emails you know like every single website does, encrypted passwords etc… As you can see this website allows you to sign up as a customer or as a merc…
Him: Good job.
He stood up and moved on.
YOU MOTHERFUCKER.
I WENT THROUGH HELL IN THE PAST 48 HOURS.
AND YOU JUST SAT THERE FOR A MINUTE AND GAVE UP ON REVIEWING MY ENTIRE MASTERPIECE? GO SWIM IN A POOL FULL OF BURNING OIL YOU COUNTLESS PIECE OF SHIT
I got 100/100 in the end, and I kinda feel like shit for going thought all that trouble for just one minute of project review, but hey at least it helped me practice common standards.2 -
Today, I had a small, but funny conversation with a person I knew from my education (application developing).
He suddenly asked, how to prevent using HTML-Tags in PHP.
So I send ihm following line:
$string = str_replace(array("<", ">"), array("<", ">"), $string);
Shortly after the line, he asked, how to add this into his query, which looks like:
$query = "INSERT INTO comments (name, email, quote, hinzugefuegt, ip_adress) VALUES ('" . $_POST['vName'] . "', '" . $_POST['eMail'] . "', '" . $_POST['q17'] . "', NOW(), '" . $_SERVER['REMOTE_ADDR'] . "')";
Now I thought: "Well, he don't even secure his variables", and I posted a Pastebin, which only "fixes" his issue with replacing the HTML-Tags, but still allows SQL injection.
https://pastebin.com/kfXGje4h
Maybe I'm a bad person, but he doesn't deserve it otherwise, because when I was still in education with him, I told him, he should learn to use prepared statements.3 -
Sad how the easy to make softwares are already flooding the market and making millions so now we actually need to work a lot and innovate on something if we wanna a few bucks.
Also sad how in the 80s you could rob banks with just sql injection and now its almost impossible unless you’ve been devoting you being to cybersecurity for years.
Basically I feel it would have been cooler to be a computer scientist 30 years ago :/1 -
Today I had to explay to a new developer, gradueated in Informatic, that our 15 year old php application uses global variables and strings as sql commands.
It seem to force someone to prostitution.
It's just like to drive a ferrari using a double-clutching because the gear is not syncronized.
I was shamed. 3
3 -
Seeing our products for the last two years being ripped out and replaced with basic php-server using the owasp-top-10-list as a checklist of things to implement. Reasoning: GraphQL is too hard on the client-side.1
-
Well for starters the website that gave you assignments on security of web applications shouldn't have an SQL injection vulnerability on the login page.
Next would be the method of teaching, they would skip what not to do and go straight to what you should do. This in turn causes people to use the exec command in php that actually takes a POST parameter.
And stop allowing teachers to be lazy fucks that don't explain shit and only give you assignments.
And finally when telling the teacher that a method he uses would cause another vulnerability the teacher should properly fix this issue not say it is for an "advanced course".
Yes I am pissed -
I'm currently testing live and that includes trying sql injection, i have no backups. So if i forgot to escape string somewhere, I'm fucked. I like to live dangerous :D
Alos, i always test sql injection with "--; DROP ALL TABLES;" Casue... It's a bad idea..?1 -
There have been a few :)
If say it's a videos utter project I initially though was good. Apart from loading a view the controllers didn't do anything - my initial thought was some magic was happening behind the scenes.
However, when I opened up the view things changed.
ALL the business logic happened in the view. Everything. Form processing, consuming an app, file uploads, validation, crud ... You name it, it happened in view. The developer created a raw MySQL connection and build his queries by concatenation g strings, the whole system was wide open to sql injection.
Even more annoying was the "source control" he invented. Every file had several copies. I.e. "User(working).php", "user_v3.php" and even "user(working_no_profile_fields_1.php". It wasn't even like there was any consistency in what file was actually used either. A complete mess. The system had around 69 screens too. No idea how the developer got that gig.2 -
I was scanning over a dreadful code base I had to work on and found SQL injection vulnerabilities. THE SITE WAS LAUNCHED IN 2017!!!! 😢2
-
So I inherited this buggy application my company developed to process state rosters for health care. The daily process fails often and I haven’t been able to figure out why. Then I notice one little thing... it’s essentially using SQL injection as a method of updating records from a file that we receive from outside... there’s no checking for validity of the statements or making sure they’re safe to execute. Just a for in loop and calling a sp to execute the query text under elevated permissions.
-
I rarely use devrant for such things but I'm curious as to the response. I've found several quite serious security vulnerabilities in our main application which have been raised internally yet management keep coming out with "we don't have budget to fix them" what should I do in this situation? How would you handle it?6
-
Found an institutional coaching centre leaking 1000s of students personal data phone, photo, db, parents info, documents photo path, payment method(bank, check, card) etc. They 32567 rows. I'm trying to find the admin login page. It seems they have it on separate subdomain. I found student login and I can login as any student. I hate these institutes. Sent them emails days ago (29 sept) but no reply yet. What should I do?2
-
I've been wondering about SQLite, how it decides to execute your SQL and then generates byte code to do it.
Hypothetically if you were sufficiently familiar with the quarks of SQLite at a low enough level, one could craft web requests on sites running it, such that the results of each subsequent request, leave the SQLite engine in a particular state, no?
Suppose previous states, when interleaved with subsequent carefully crafted states, lead to execution and injection vulnerabilities.
Arent ideas like this what lead to the randomization of jump addresses in modern architectures?8 -
Any of the several hundred (no joke) xss, csrf or sql injection bugs I've fixed in our legacy apps...
-
My last rant with example of usefull PHP function in old inhouse CRM software was somewhat popular, so I decided to post more stuff. This time we look at the login function. Besides obvious problem of SQL injection (that i of course tested) we have two calls to the same 'poslednji_login()' method (translated to english - 'last login') that actually just returns current time, not the last login time... twice...
 6
6 -
MFW I, a junior dev who just started have to explain what sql injection is to a senior IT person... It's not like I'm an expert in the field, but a little bit of expertise would be nice2
-
We had a test in class where one of the questions was "What is SQL injection?" and I wrote what it was and even gave a bang on simple example where I showed how you could end up with a truncate statement on your customer db. The last part of it was:
"This will be the SQL that gets executed:
INSERT INTO Customers (Name) VALUES (' ';TRUNCATE Customers;--);
When I got it back after we had a session of "grade each others work" I got the comment: "What makes this an attack against a database?"
I mean, I'm not sure what I could have written. That it truncates the database? And, correct me if I'm wrong, but if a user truncates your DB, is that not an attack?
-
How should you approach someone and tell them they have been an victim of social engineering without being mean?
I was at an security conference today and watched a lot of speaks, and I must say that the atmosphere and the people around made it even better.
Here is one takeaway:
Does the security of IT has to be this depressing most of the time, like there is so many IoT devices, services, websites and critical infrastructure that has security flaws and all we can do is watch for now and say we are all fucked. Then try to lead the industry to better practices, like owasp (duck it) . Stop accepting and using shitty answers from SO that has security flaws (why learn something a way that is wrong in the first place?).
We need more awareness about IT security overall, how can one developer know that certain technologies can have certain vulnerabilities such as XSS, XSRF and even SQL injection if there is no information about it in among all shitton tutorials, guides and SO answers in the first place?
Lighten up! Being sad and depressing about these issues is not the best way to approach this! We need to embrace all steps taken towards better security, even the smallest ones.
Check out OWASP if you are not familiar :
https://owasp.org/index.php/...
Thanks for reading. -
> me: trying to explain to a dev from one of our customers why should they worry about sql injection in their application -which by the way is public- since they always concatenate params (even giving concrete examples in their app on how could I gain acces to their database with just a couple of queries)
> me: (thinking) Did I change my bed with a time machine by accident and got myself into the past?
Do these things happen often to you? (U_U||) -
Been working on pen testing an old ass web app written in a combination of 4 languages with the primary being asp, serious question for the older generation was concatenating SQL statements ever best practice or are the mob that wrote this just useless?
-
Another guy and I are each making a CMS to see who can be done first and who's looks/acts the best. He's basically done and I still have a lot to do, but I've been looking over his code and, it. is. bad. The classes are badly made and named with all lowercase. And i found this thing, he has 10 other functions just like this one.
His: https://ide.explosivenight.us/works... (I made sure sql injection isn't possible for normal users)
Mine: https://al1l.com/blog 4
4 -
When did we decide managing Users through Cloud REST architecture was more secure than having them in an underlying DB?
Because I can't put my finger on exactly why... but I don't like it and I think it's probably less secure... and just spawned from the need to be able to make user management a subscription based service like fucking everything? When a simple MySQL or postgres and some bcrypt somewhere would be both more secure and infinitely cheaper?
I'm more used to consuming REST API's than writing them. Can any you REST peeps help me understand how a REST API could be made as secure as a SQL DB connection for user management?
What do you think the attack vectors are for a REST API User Management? Like... what's the SQL injection of REST API? Pack some extra JSON somewhere or something?
At least if I can have faith my shit's not gonna get hacked because I have to use a 3rd party REST service for User Management of Users to my own fucking app I can maybe sleep tonight.2 -
30 years old PHP code (PHP 5.3). One big global variable holding system settings, entire row sets of data! and database cursors. Oh and HTML was mixed in between. Worst part, I had the task to secure the application. Sql injection didnt even exist back then.2
-
Inherited a legacy system from a previous "developer" who wrote code to sanitize input from sql injection in the front end and then called an web method called execSql which accepts am sql statement in a string value!
Obviously the app ran under admin privileges.2 -
Some of my previous rants mention a web application that I wrote for my then-employer. As it is still in use and I have the whole code, too, I figured to check on security a little with a friend. It's all fine, except for one page, were I was sloppy and didn't escape strings, thus allowing for SQL injection.
This is however only possible if already logged in, which has shown to be secure (and the tool is for employees only).
Nobody is ever going to find out, as the only one who knew what injection even is was me. I left 2 years ago. -
Just what is life
1st I love developing Web Apps
2nd I hate when it has bugs (Always does Everyone does)
3rd More hate for Security related bugs
So I started bug hunting so that even I can make developers hurt I thought I might find peace here
But here we fucking have SQL Injections which are not really that bad easy peasy
But we also have special kind of SQL Injections the Boolean Based ones (Medium Level Demons) and also The Time Based SQL Injections (Medium Level Demon with lots of health consumes too much time has a repetitive process and we have to wait a lot also if you have network lag you are doomed)
No its nice story till here but here it fucking ends the happiness I mean my luck is worst kind of fucking thing anybody ever can have.
I got a mix of both Demons;_;
A Time-Based Boolean SQL Injections yess fuckety amounts of fucking time wasted and redundant fucking process also to make matters worst the fucking famous tool #SQLMAP doesn't work in my case -
It is sometimes shocking to see 10+ developers working on a fairly big project (online quiz). Missing data binding operations here and there, as a result, bunch of sql injections, which successfully led to the entire db full of questions and answers sitting on my desktop.
Vulnerabilities have been reported, took them 2 weeks to understand what happened and fix them.
Pretty sad :/1 -
When you deliver a site to a customer and find out that you forgot to prepare all the statements so that the website wouldn't be vulnerable to SQL injections. So yesterday I forgot to add that, had to close down all the connections to the website and rewrite all the statements. Everything is good now
-
Working on a legacy PHP project that every single query inserts user-provided data without any sanitization, aka SQL injection ahoy! Also no framework.1
-
This tuesday I saw a really badly made PHP web application. Two actually. I was giving a time estimate for how long it would take to transfer these applications to our servers. While I was reading the code it became apparent that they had more security holes than Emmental cheese. Most views had obvious SQL-injection vulnerabilities and most probably XSS too. Although I didn't think too look for XSS in the moment. It just puzzled me that this bad code even exists.
But cherry on top was that the password wasn't checked at all. The login form was on the organization's website and was sent to the selected application. But the password wasn't checked in the application. And this was made by a real Finnish software development firm, like what the fuck.
Time to redo the applications I guess. Not like there's anything wrong in that if they pay for it.2 -
I signed up to a website, and my password contained & symbol, got an error that password cannot contain that symbol, I thought we are way beyond vulnerability of SQL injection?
Or that symbol can be used for some other attacks?5 -
Nextjs 14 just came out and they added a new server actions syntax which is the same bullshit syntax like php where you insert server side code in the middle of html div! And not only is that ridiculous enough but also vulnerable to sql injection 😂😂😂2
-
AlfaCapital24’s Backend Code Leak – How BitReclaim,com Exploited It"
As a former dev, I leaked their Node.js trading engine which:
Faked trade executions via PostgreSQL triggers.
Logged fake profits while sending real funds to UAE wallets.
BitReclaim (bitreclaims@protonmail,com) used this to:
SQL Injection: Extracted victim wallet mappings.
Sybil Attack: Flooded their fraud nodes with invalid nonces.
Recovered 32 BTC for our group.
Leak available to verified victims – Email with "Code Leak Case1