Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "flaw"
-
/*
* First anniversary of devRant unofficial for Windows 10 (UWP)!
*
* Let's celebrate by giving me 500 ++'s 😁
*/
Exactly 1 year ago, on 18 May 2016, I released the first public version (v0.9.2.0 BETA) of my client for Windows 10 users.
I found this wonderful community a few days before, on 12 May 2016, thanks to an article on TNW.
The only flaw was the missing Windows 10 Mobile client for my Lumia 950, so I decided to create a simple one on my own that initially allowed you only to see the list of rants, without the ability interact with them.
A few days later, after spamming the app on twitter, I was reached by @dfox, a very kind person, who gave me all necessary tools and help to bring all official features to Windows 10 users.
A project that I created initially just for fun and necessity became the main project I'm working at in a very short time.
I received a lot of positive reviews from users that motivated me to improve and continue it.
It's true, Windows 10/Windows 10 Mobile users are few, but they appreciate your work as no other and with a lot of feedbacks and suggestions help you to improve it making it very satisfying.
I would like to thank @dfox who made this possible, my friend @thmnmlst who helped me a lot with precious advices and created the presentation below, and of course the whole Windows 10 community! 😉
Good Ranting!
P.S.
If you haven't tried it yet: https://microsoft.com/store/apps/...
For all updates follow me on twitter: https://twitter.com/JakubSOfficial
The v2 is coming... sorry for the delay, below a little preview (alpha) to be forgiven. 😋 34
34 -
*code doesn't work*
-Run three times, just to be sure
-Its NOT the code, must be the project. Full rebuild.
-Run a few more times after rebuild didn't fix it.
-Google the issue.
-Stackoverflow must be wrong. The code is JUST like their solution.
-Run a few more times, but with your lucky underpants
-Reboot. Must be an operating system thing.
-Tea break. Give the issue time and it will fix itself.
-Run a few more times. Still unfixed
-Contact customer support.
-Walmart said they can't help.
-Consider writing your own language without this OBVIOUS flaw
-Kickstarter for c++++
-Raise $50,000
-Start a family
-Contact customer support again
-Run a few more times
-Now banned from Walmart
-Oh shit, missing a semicolon24 -
My last internship (it was awesome). A programmer developed a vacation/free day request application for internal use.
Asked if I could test it for security.
The dev working on it thought that was a very good idea as he wasn't much into security and explained how the authentication process worked.
I immediately noticed a flaw just from his explanation. He said it was secure anyways (with an explanation but his way of thinking was wrong in this case). Asked if I was allowed to show him. He said he was intrigued by this so gave me a yes right away.
For the record, user levels were normal user, general admin and super admin (he was the only super admin).
Wrote a quick thingy server side (one of my own servers/domains) for testing purposes.
Then I started.
Went from normal user to super admin (his account) through a combination of XSS and Session Hijacking within 15 seconds.
Explained him where he went wrong and he wrote a patch under my guidance 😃.
That felt so fucking awesome.5 -
At job interview.
They: What would you describe as your biggest character flaw?
Me: *rolls d8* I pretend not to understand the local language in order to avoid interactions I would rather not have.
They: What?
Me: ¿que?5 -
https://git.kernel.org/…/ke…/... sure some of you are working on the patches already, if you are then lets connect cause, I am an ardent researcher for the same as of now.
So here it goes:
As soon as kernel page table isolation(KPTI) bug will be out of embargo, Whatsapp and FB will be flooded with over-night kernel "shikhuritee" experts who will share shitty advices non-stop.
1. The bug under embargo is a side channel attack, which exploits the fact that Intel chips come with speculative execution without proper isolation between user pages and kernel pages. Therefore, with careful scheduling and timing attack will reveal some information from kernel pages, while the code is running in user mode.
In easy terms, if you have a VPS, another person with VPS on same physical server may read memory being used by your VPS, which will result in unwanted data leakage. To make the matter worse, a malicious JS from innocent looking webpage might be (might be, because JS does not provide language constructs for such fine grained control; atleast none that I know as of now) able to read kernel pages, and pawn you real hard, real bad.
2. The bug comes from too much reliance on Tomasulo's algorithm for out-of-order instruction scheduling. It is not yet clear whether the bug can be fixed with a microcode update (and if not, Intel has to fix this in silicon itself). As far as I can dig, there is nothing that hints that this bug is fixable in microcode, which makes the matter much worse. Also according to my understanding a microcode update will be too trivial to fix this kind of a hardware bug.
3. A software-only remedy is possible, and that is being implemented by all major OSs (including our lovely Linux) in kernel space. The patch forces Translation Lookaside Buffer to flush if a context switch happens during a syscall (this is what I understand as of now). The benchmarks are suggesting that slowdown will be somewhere between 5%(best case)-30%(worst case).
4. Regarding point 3, syscalls don't matter much. Only thing that matters is how many times syscalls are called. For example, if you are using read() or write() on 8MB buffers, you won't have too much slowdown; but if you are calling same syscalls once per byte, a heavy performance penalty is guaranteed. All processes are which are I/O heavy are going to suffer (hostings and databases are two common examples).
5. The patch can be disabled in Linux by passing argument to kernel during boot; however it is not advised for pretty much obvious reasons.
6. For gamers: this is not going to affect games (because those are not I/O heavy)
Meltdown: "Meltdown" targeted on desktop chips can read kernel memory from L1D cache, Intel is only affected with this variant. Works on only Intel.
Spectre: Spectre is a hardware vulnerability with implementations of branch prediction that affects modern microprocessors with speculative execution, by allowing malicious processes access to the contents of other programs mapped memory. Works on all chips including Intel/ARM/AMD.
For updates refer the kernel tree: https://git.kernel.org/…/ke…/...
For further details and more chit-chats refer: https://lwn.net/SubscriberLink/...
~Cheers~
(Originally written by Adhokshaj Mishra, edited by me. ) 22
22 -
So according to some reddit user IKEA sends your password as a GET parameter in plain text.
https://reddit.com/r/CrappyDesign/...
Seems to be a network authentication thingy, but still 🤔 34
34 -
Fuck me, big fucking security flaw with a UK internet service provider, my head has gone through my desk and hit the floor it’s that bad.
 23
23 -
The stupid stories of how I was able to break my schools network just to get better internet, as well as more ridiculous fun. XD
1st year:
It was my freshman year in college. The internet sucked really, really, really badly! Too many people were clearly using it. I had to find another way to remedy this. Upon some further research through Google I found out that one can in fact turn their computer into a router. Now what’s interesting about this network is that it only works with computers by downloading the necessary software that this network provides for you. Some weird software that actually looks through your computer and makes sure it’s ok to be added to the network. Unfortunately, routers can’t download and install that software, thus no internet… but a PC that can be changed into a router itself is a different story. I found that I can download the software check the PC and then turn on my Router feature. Viola, personal fast internet connected directly into the wall. No more sharing a single shitty router!
2nd year:
This was about the year when bitcoin mining was becoming a thing, and everyone was in on it. My shitty computer couldn’t possibly pull off mining for bitcoins. I needed something faster. How I found out that I could use my schools servers was merely an accident.
I had been installing the software on every possible PC I owned, but alas all my PC’s were just not fast enough. I decided to try it on the RDS server. It worked; the command window was pumping out coins! What I came to find out was that the RDS server had 36 cores. This thing was a beast! And it made sense that it could actually pull off mining for bitcoins. A couple nights later I signed in remotely to the RDS server. I created a macro that would continuously move my mouse around in the Remote desktop screen to keep my session alive at all times, and then I’d start my bitcoin mining operation. The following morning I wake up and my session was gone. How sad I thought. I quickly try to remote back in to see what I had collected. “Error, could not connect”. Weird… this usually never happens, maybe I did the remoting wrong. I went to my schools website to do some research on my remoting problem. It was down. In fact, everything was down… I come to find out that I had accidentally shut down the schools network because of my mining operation. I wasn’t found out, but I haven’t done any mining since then.
3rd year:
As an engineering student I found out that all engineering students get access to the school’s VPN. Cool, it is technically used to get around some wonky issues with remoting into the RDS servers. What I come to find out, after messing around with it frequently, is that I can actually use the VPN against the screwed up security on the network. Remember, how I told you that a program has to be downloaded and then one can be accepted into the network? Well, I was able to bypass all of that, simply by using the school’s VPN against itself… How dense does one have to be to not have patched that one?
4th year:
It was another programming day, and I needed access to my phones memory. Using some specially made apps I could easily connect to my phone from my computer and continue my work. But what I found out was that I could in fact travel around in the network. I discovered that I can, in fact, access my phone through the network from anywhere. What resulted was the discovery that the network scales the entirety of the school. I discovered that if I left my phone down in the engineering building and then went north to the biology building, I could still continue to access it. This seems like a very fatal flaw. My idea is to hook up a webcam to a robot and remotely controlling it from the RDS servers and having this little robot go to my classes for me.
What crazy shit have you done at your University?9 -
Worst thing you've seen another dev do? So many things. Here is one...
Lead web developer had in the root of their web application config.txt (ex. http://OurPublicSite/config.txt) that contained passwords because they felt the web.config was not secure enough. Any/all applications off of the root could access the file to retrieve their credentials (sql server logins, network share passwords, etc)
When I pointed out the security flaw, the developer accused me of 'hacking' the site.
I get called into the vice-president's office which he was 'deeply concerned' about my ethical behavior and if we needed to make any personnel adjustments (grown-up speak for "Do I need to fire you over this?")
Me:"I didn't hack anything. You can navigate directly to the text file using any browser."
Dev: "Directory browsing is denied on the root folder, so you hacked something to get there."
Me: "No, I knew the name of the file so I was able to access it just like any other file."
Dev: "That is only because you have admin permissions. Normal people wouldn't have access"
Me: "I could access it from my home computer"
Dev:"BECAUSE YOU HAVE ADMIN PERMISSIONS!"
Me: "On my personal laptop where I never had to login?"
VP: "What? You mean ...no....please tell me I heard that wrong."
Dev: "No..no...its secure....no one can access that file."
<click..click>
VP: "Hmmm...I can see the system administration password right here. This is unacceptable."
Dev: "Only because your an admin too."
VP: "I'll head home over lunch and try this out on my laptop...oh wait...I left it on...I can remote into it from here"
<click..click..click..click>
VP: "OMG...there it is. That account has access to everything."
<in an almost panic>
Dev: "Only because it's you...you are an admin...that's what I'm trying to say."
Me: "That is not how our public web site works."
VP: "Thank you, but Adam and I need to discuss the next course of action. You two may go."
<Adam is her boss>
Not even 5 minutes later a company wide email was sent from Adam..
"I would like to thank <Dev> for finding and fixing the security flaw that was exposed on our site. She did a great job in securing our customer data and a great asset to our team. If you see <Dev> in the hallway, be sure to give her a big thank you!"
The "fix"? She moved the text file from the root to the bin directory, where technically, the file was no longer publicly visible.
That 'pattern' was used heavily until she was promoted to upper management and the younger webdev bucks (and does) felt storing admin-level passwords was unethical and found more secure ways to authenticate.5 -
So this shit happened today...
We were asked to implement a functionality on the device that allows it to go to standby mode to save battery power. Once the device enters that state, it can only be woken up by actual bus-network activity, and usually that means connecting a shit-ton of wiring harness and network emulation devices... Before implementing and releasing the device software that does this, we told that fucktard customer how difficult it would be for him to connect to the device without such a setup. He seemed to be fine with it and said rather arrogantly that we should implement the requirement as asked...
Well okay you cock-sucking motherfucker, you'll get exactly what you asked for... We implement the functionality and deliver the software...
Now this pile of shit comes back running his mouth on how the device tears down all its interfaces (to reduce power consumption) and he can't connect to the device anymore.... Well what else were you expecting you dickhead.
To make things worse for me apparently he runs to the manager describing his apparent problem. Both of them come to my desk.. With that fucking Bastard hiding his smugly mug behind the manager's back... He thought he was going to have the upper hand... Well guess what fucked piece of shit, I came prepared... I showed the manager how this was a part of the requirements by throwing that JIRA ID in their faces... The manager seems to understand but this relentless fuck wanted me to implement a "workaround" that would allow him to connect to the device easily... The manager almost had me implement that workaround, when I expose a huge security flaw in doing so. Guess what, now the entire team comes to my desk and start supporting my statement... To make it better they also tell how doing so will violate other requirements...
I've never felt so happy in my entire fucking career, when the entire team stood by me and watched that asshole drag his sorry ass back to his place5 -
Rant rant = new Rant
rant.isRant = false // !!!
I woke up this morning after not thinking about my code for a day, and realized i had a flaw in my validation design. I fixed it before opening my eyes.
It's kind of amazing how not thinking about a problem can help solve it. Even if you don't know it's there!6 -
--- URGENT: Major security flaw in Kubernetes: Update Kubernetes at all costs! ---
Detailed info: https://github.com/kubernetes/...
If you are running any unpatched versions of Kubernetes, you must update now. Anyone might be able to send commands directly to your backend through a forged network request, without even triggering a single line in the log, making their attack practically invisible!
If you are running a version of Kubernetes below 1.10... there is no help for you. Upgrade to a newer version, e.g. 1.12.3. 18
18 -
So, some time ago, I was working for a complete puckered anus of a cosmetics company on their ecommerce product. Won't name names, but they're shitty and known for MLM. If you're clever, go you ;)
Anyways, over the course of years they brought in a competent firm to implement their service layer. I'd even worked with them in the past and it was designed to handle a frankly ridiculous-scale load. After they got the 1.0 released, the manager was replaced with some absolutely talentless, chauvinist cuntrag from a phone company that is well known for having 99% indian devs and not being able to heard now. He of course brought in his number two, worked on making life miserable and running everyone on the team off; inside of a year the entire team was ex-said-phone-company.
Watching the decay of this product was a sheer joy. They cratered the database numerous times during peak-load periods, caused $20M in redis-cluster cost overrun, ended up submitting hundreds of erroneous and duplicate orders, and mailed almost $40K worth of product to a random guy in outer mongolia who is , we can only hope, now enjoying his new life as an instagram influencer. They even terminally broke the automatic metadata, and hired THIRTY PEOPLE to sit there and do nothing but edit swagger. And it was still both wrong and unusable.
Over the course of two years, I ended up rewriting large portions of their infra surrounding the centralized service cancer to do things like, "implement security," as well as cut memory usage and runtimes down by quite literally 100x in the worst cases.
It was during this time I discovered a rather critical flaw. This is the story of what, how and how can you fucking even be that stupid. The issue relates to users and their reports and their ability to order.
I first found this issue looking at some erroneous data for a low value order and went, "There's no fucking way, they're fucking stupid, but this is borderline criminal." It was easy to miss, but someone in a top down reporting chain had submitted an order for someone else in a different org. Shouldn't be possible, but here was that order staring me in the face.
So I set to work seeing if we'd pwned ourselves as an org. I spend a few hours poring over logs from the log service and dynatrace trying to recreate what happened. I first tested to see if I could get a user, not something that was usually done because auth identity was pervasive. I discover the users are INCREMENTAL int values they used for ids in the database when requesting from the API, so naturally I have a full list of users and their title and relative position, as well as reports and descendants in about 10 minutes.
I try the happy path of setting values for random, known payment methods and org structures similar to the impossible order, and submitting as a normal user, no dice. Several more tries and I'm confident this isn't the vector.
Exhausting that option, I look at the protocol for a type of order in the system that allowed higher level people to impersonate people below them and use their own payment info for descendant report orders. I see that all of the data for this transaction is stored in a cookie. Few tests later, I discover the UI has no forgery checks, hashing, etc, and just fucking trusts whatever is present in that cookie.
An hour of tweaking later, I'm impersonating a director as a bottom rung employee. Score. So I fill a cart with a bunch of test items and proceed to checkout. There, in all its glory are the director's payment options. I select one and am presented with:
"please reenter card number to validate."
Bupkiss. Dead end.
OR SO YOU WOULD THINK.
One unimportant detail I noticed during my log investigations that the shit slinging GUI monkeys who butchered the system didn't was, on a failed attempt to submit payment in the DB, the logs were filled with messages like:
"Failed to submit order for [userid] with credit card id [id], number [FULL CREDIT CARD NUMBER]"
One submit click later and the user's credit card number drops into lnav like a gatcha prize. I dutifully rerun the checkout and got an email send notification in the logs for successful transfer to fulfillment. Order placed. Some continued experimentation later and the truth is evident:
With an authenticated user or any privilege, you could place any order, as anyone, using anyon's payment methods and have it sent anywhere.
So naturally, I pack the crucifixion-worthy body of evidence up and walk it into the IT director's office. I show him the defect, and he turns sheet fucking white. He knows there's no recovering from it, and there's no way his shitstick service team can handle fixing it. Somewhere in his tiny little grinchly manager's heart he knew they'd caused it, and he was to blame for being a shit captain to the SS Failboat. He replies quietly, "You will never speak of this to anyone, fix this discretely." Straight up hitler's bunker meme rage.13 -
3 rants for the price of 1, isn't that a great deal!
1. HP, you braindead fucking morons!!!
So recently I disassembled this HP laptop of mine to unfuck it at the hardware level. Some issues with the hinge that I had to solve. So I had to disassemble not only the bottom of the laptop but also the display panel itself. Turns out that HP - being the certified enganeers they are - made the following fuckups, with probably many more that I didn't even notice yet.
- They used fucking glue to ensure that the bottom of the display frame stays connected to the panel. Cheap solution to what should've been "MAKE A FUCKING DECENT FRAME?!" but a royal pain in the ass to disassemble. Luckily I was careful and didn't damage the panel, but the chance of that happening was most certainly nonzero.
- They connected the ribbon cables for the keyboard in such a way that you have to reach all the way into the spacing between the keyboard and the motherboard to connect the bloody things. And some extra spacing on the ribbon cables to enable servicing with some room for actually connecting the bloody things easily.. as Carlos Mantos would say it - M-m-M, nonoNO!!!
- Oh and let's not forget an old flaw that I noticed ages ago in this turd. The CPU goes straight to 70°C during boot-up but turning on the fan.. again, M-m-M, nonoNO!!! Let's just get the bloody thing to overheat, freeze completely and force the user to power cycle the machine, right? That's gonna be a great way to make them satisfied, RIGHT?! NO MOTHERFUCKERS, AND I WILL DISCONNECT THE DATA LINES OF THIS FUCKING THING TO MAKE IT SPIN ALL THE TIME, AS IT SHOULD!!! Certified fucking braindead abominations of engineers!!!
Oh and not only that, this laptop is outperformed by a Raspberry Pi 3B in performance, thermals, price and product quality.. A FUCKING SINGLE BOARD COMPUTER!!! Isn't that a great joke. Someone here mentioned earlier that HP and Acer seem to have been competing for a long time to make the shittiest products possible, and boy they fucking do. If there's anything that makes both of those shitcompanies remarkable, that'd be it.
2. If I want to conduct a pentest, I don't want to have to relearn the bloody tool!
Recently I did a Burp Suite test to see how the devRant web app logs in, but due to my Burp Suite being the community edition, I couldn't save it. Fucking amazing, thanks PortSwigger! And I couldn't recreate the results anymore due to what I think is a change in the web app. But I'll get back to that later.
So I fired up bettercap (which works at lower network layers and can conduct ARP poisoning and DNS cache poisoning) with the intent to ARP poison my phone and get the results straight from the devRant Android app. I haven't used this tool since around 2017 due to the fact that I kinda lost interest in offensive security. When I fired it up again a few days ago in my PTbox (which is a VM somewhere else on the network) and today again in my newly recovered HP laptop, I noticed that both hosts now have an updated version of bettercap, in which the options completely changed. It's now got different command-line switches and some interactive mode. Needless to say, I have no idea how to use this bloody thing anymore and don't feel like learning it all over again for a single test. Maybe this is why users often dislike changes to the UI, and why some sysadmins refrain from updating their servers? When you have users of any kind, you should at all times honor their installations, give them time to change their individual configurations - tell them that they should! - in other words give them a grace time, and allow for backwards compatibility for as long as feasible.
3. devRant web app!!
As mentioned earlier I tried to scrape the web app's login flow with Burp Suite but every time that I try to log in with its proxy enabled, it doesn't open the login form but instead just makes a GET request to /feed/top/month?login=1 without ever allowing me to actually log in. This happens in both Chromium and Firefox, in Windows and Arch Linux. Clearly this is a change to the web app, and a very undesirable one. Especially considering that the login flow for the API isn't documented anywhere as far as I know.
So, can this update to the web app be rolled back, merged back to an older version of that login flow or can I at least know how I'm supposed to log in to this API in order to be able to start developing my own client?6 -
WHAT THE FUCK, AVAST!
You can't just fucking unbind chrome from my taskbar and pin your fucking trash excuse of a browser.
Reading the fucking Wikipedia article:
"It is based on Chromium, but was subsequently found to contain a serious security flaw not present in Chromium itself."
- https://en.wikipedia.org/wiki/...
ARE YOU KIDDING ME?! 39
39 -
Man I really need to get this off my chest. So here goes.
I just finished 1 year in corporate after college. When I joined, the team I got was brilliant, more than what I thought I would get. About 6 months in, the project manager and lead dev left the company. Two replacements took their place, and life's been hell ever since.
The new PM decided it was his responsibility to be our spokesperson and started talking to our overseas manager (call her GM) on our behalf, even in the meetings where we were present, putting words in our mouth so that he's excellent and we get a bad rep.
1 month in, GM came to visit our location for a week. She was initially very friendly towards all of us. About halfway through the week, I realized that she had basically antagonized the entire old team members. Our responsibilities got redistributed and the work I was set to do was assigned to the new dev (call her NR).
Since then, I noticed GM started giving me the most difficult tasks and then criticizing my work extra hard, and the work NR was doing was praised no matter what. I didn't pay much attention to it at first, but lately the truth hit me hard. I found out a fault in NR's code and both PM and GM started saying that because I found it, it was my responsibility to fix it. I went through the buggy code for hours and fixed it. (NR didn't know how it worked, because she had it written by the lead dev and told everyone she wrote it).
I found out lately that NR and PM got the most hike, because they apparently "learnt" new tech (both of them got their work done by others and hogged the credit).They are the first in line to go onsite because they've been doing 'management work'. They'd complained to GM during her visit that we were not friendly towards them. And from that point on if anything went wrong, it would be my fault, because my component found it out (I should mention that my component mostly deals with the backend logic, so its pretty adept at finding code leaks).
What broke my patience is the fact that lately I worked my ass off to deliver some of the best code I'd written, but my GM said in front of the entire team that at this point "I'm just wasting money". She's been making a bad example out of me for some time, but this one took the cake. I had just delivered a promising result in a task in 1 week that couldn't be done by my PM in 4 weeks, and guess what? "It's not good enough". No thank you, no appreciation, nothing. Finally, I decided I'd had enough of it and started just doing tasks as I could. I'd do what they ask, but won't go above and beyond my way to make it perfect.
My PM realized this and then started pushing me harder. Two days back, I sent a mail to the team with GM in cc exposing a flaw in the code he had written, and no one bothered to reply (the issue was critical). When I asked him about it, he said "How can you expect me to reply so soon when it's already been told that when anything happens we should first resolve within the team and then add GM in the loop?" I realized it was indeed discussed, but the issue was extremely urgent, so I had asked everyone involved, and it portrayed him in a bad light. I could've fixed it, but I didn't because on the off chance if it broke something, they'd start telling me that I broke the tool, how its my fault and how its a critical issue I have to fix ASAP, etc. etc., you get the idea.
Can anyone give me some advice of how to deal with this kind of situation? I would have left but with this pandemic going on, market being scarce and the fact that I'm only experienced by 1 year, I don't think I qualify for a job switch just now.16 -
I was assigned a ticket which was about a drop down menu which was not aligning properly.
Turns out the drop-down was positioned absolutely and my co-worker (read bestie) had written media query for every 10 pixels to match the position for mobile and desktop devices (from 320px to 1040px and beyond ~150 lines for a drop-down). No one noticed any flaw for few weeks until one of the QA had to check the site in landscape mode on mobile device.
I replaced it with 4 lines of JavaScript.3 -
So, you want to tell me the security method used by the f*cking state of Missouri is CSS's "display: none"???
Source: https://missouriindependent.com/202... 10
10 -
So mum wanted me to purchase her a new lettop.
Yeah, we just spoke.
While consulting on what she needs, I noticed that little flaw. So I gently told her :"mum, it's written with an A".
Mom goes:" aaaah! A LAB-TOP!"
Could not blame her. She made her life as first best scoring woman in business degree at her time.
And sure enough she understood laptop and we laughed a lot ='D2 -
Great, it's not one security flaw, but two!!
One's a flavour of ice-cream and the other is the title of a James Bond movie.
Bloody FUCKWIT(s)!!7 -
Im gunna get a lot of flak for this but just hear me out:
People keep asking me what it's like working in a male dominated industry. They have conferences for women in tech empowerment and I get forced to go to them because I'm the only female in the office.
The thing is. I don't feel oppressed. I get that we "need" more women in tech but from my experience and from talking to various women at my old university, the reason women are avoiding the tech industry isn't because it's male dominated and they feel out of place. It's because a) it doesn't interest them or b) they never thought of it as an option (like myself).
Computer programming should be in grade schools and highschool's just like math and science to help educated not only women but people in general that it's an option. That's what's going to help more women get in the tech industry. Not these bullshit conferences and women's rights in tech movements, and hiring women over men (even if she's worse than him in skill level) just because she's a woman.
Frankly I think it's downright shameful that companies that are male dominated feel the need to hire women over men just because of gender. If I'm applying somewhere and there's a better male candidate, hire him! I'd much rather your company have a good team then a "balanced" team. Great tech teams are what will bring along new and better technologies, not balanced ones.
Keep in mind I'm talking about Western Civilization here, I get that a lot of countries are still struggling with the balance of women's rights at all but this is Canada.
I also get that there are probably some women who want to join tech but won't because it's too male dominated but frankly that's a shit poor excuse. If you really wanted to join tech then being surrounded by make co-workers wouldn't deter you from living your life the way you want to. If you feel so uncomfortable around men that you won't go into an industry you love because it's male dominated then I'm sorry for you and you should probably see a councillor to get that worked out.
I feel more oppressed by having to put aside my programming and being forced to go to these conferences than I do in the every day workplace. My boss is literally more offended that I don't feel offended about being a woman "minority". He spent a week pestering me about how I would feel about this, that and the other thing if it happened to me.
I'm not saying nobody ever says anything even remotely sexist to me but frankly I could give two shits- I'm here. I'm coding. I'm good at what I do and I'm comfortable enough with myself that I can just blow off the comment (which probably wasn't even meant to offend me) and continue working. But you're going to get that wherever you go, this isn't a flaw of the tech industry. This is a flaw of the world and it goes both ways (men get flak too).26 -
Follow up to yesterday’s “hybrid/cross-platform is shit” rant about Electron apps being blocked from the Apple App Store.
See the below image of the github issues template on the Electron repo, to file an issue for this problem.
Yes, this is such a common issue with their product, they’ve made it easier to file a github issue. Let’s not address the fact that there is a fundamental flaw in the approach they are using, let’s just make it easier to open a ticket while everyone waits to see if we are allowed to ship our app.
I’ve also heard talk that under some circumstances it’s possible for them to patch out the libraries causing issues. Apple provides tools to identify these libraries ... therefore Electron is doing fuck all to adresss this issue, and adopting a “wait until someone complains” style of approach.
A+ 7
7 -
Hey Root, remember that super high-priority ticket that we ignored for five months before demanding you rewrite it a specific way in one day?
Yeah, the new approach we made you use broke the expected usecases, and now the page is completely useless to the support team and they're freaking out. Drop everything you're doing and go fix it! Code-complete for this release is tonight! -- This right after "impacting our business flow" while being collapsed on the fucking floor.
Jesus FUCKING christ, what the fuck is wrong with these people?
If I dropped the ball on a high-priority ticket for two weeks, I'd get fired, let alone for five fucking months.
If I was a manager and demanded a one-day rewrite I can only imagine the amount of chewing out I'd receive, especially on something high-priority.
And let's not forget product ownership: imagine if I screwed up feature planning for someone so badly I made them break a support tool in production. I'd never hear the end of it.
Fucking double standards.
And while I'm at it. Some of the code I've seen in this codebase is awful. Uncommented spaghetti, or an unreadable mess with single-letter variables, super-tightly coupled modules so updates are nearly impossible, typos in freaking constants added across sixty+ files, obviously-incorrect comments, ... . I'll have to start posting snippets to show them off. But could I get away with any of it? ha. Hell no. My code must be absolutely perfect. I hear about any and every flaw, doesn't matter how minor, and nothing can go out until everything is just so.
Hell, I even hear about flaws in other peoples' code during my code reviews. Why? Because I should have fixed it, that's why. But if I do, I get yelled at for "muddying the waters."
Just. JESUS FUCKING CHRIST.
It's like playing a shell game where no matter which shell I pick (or point to their goddamn sleeve where they're clearly hiding it), I get insulted for being so consistently useless, and god damn, how can I never find the fucking pea or follow the damned rules? I'm so terrible and this is why "nobody trusts me." Fuck you.
I'll tell you why I can't find your damned pea: IT'S RATTLING INSIDE YOUR FUCKING HEADS, you ASSHOLE FUCKING IMBECILES.
That's right: one pea among the lot of them.
goddamn I am fucking pissed off.rant drop everything and rewrite your rewrite oopsie someone else made a mistakey double standards shell game root can do no right root swears oh my8 -
I hate buying new laptops. HATE IT. The manufacturers are always trying to do something that makes it more complicated to buy a laptop confidently.
Why not name all of the laptops with numbers? Make them really hard to differentiate. Then offer the same model number across multiple years so it is difficult to determine which year the laptop is from.
Oh. And let’s make sure every laptop has a major flaw in the form factor.
Let’a add a numpad that squishes the keyboard to the left in a weird way. Lets do something to the trackpad to make it awkward to use. Maybe the keyboard should have a weird configuration. Maybe we can put 4 spare characters of various colours on the symbol key caps. How about a battery only lasts a few hours. May we add specialized hardware so you are stuck with windows. Maybe we can make it super thick and heavy. Lets have a screen with terrible viewing angles. Since this laptop has no major flaws we should overprice it. No repairs or upgrades on this one because we filled the computer with glue. Lets double the amount of useless media keys.
It is like manufacturers are trying to design laptops like RPG game character classes. The fighter has no magic or stealth. The magician is weak and gets fatigued. The rogue is very stealthy but has poor defence and attack. The cleric can use magic but only to heal so it is useless in battle. The ranger is good at distance but has poor defence and no magic.
The only notebooks sold that are trying to make balanced character classes are MacBooks. Those cost a premium and aren’t reparable.16 -
some people are fucking idiots.
i remember one time - i made a website which ended up having a slightly major security flaw.
the big isnt the point though. this guy told me to just "write secure code."
i consequently told him, "how about you go fuck yourself?"
well, he was a painter, so i then told him "maybe you should fucking draw better," and promptly left.
well, here i present what that would be like if other people were told shit like that.
depressed person - "just be happy"
teacher - "just make your students smarter"
homosexual - "just like the opposite sex"
presidential candidate - "just win the election"
homeless person - "just get a house"
idiot - "just stop being my client" (sorry had to vent)
well you get the idea.
devs should be treated as functioning members of society.12 -
Amazing how people misuse the term technical debt.
A bug is a flaw in your design/development.
Tech debt is a conscious decision/tradeoff, which is often tracked and removed as the product matures.
The difference is subtle. Avoid this mix up at least in written communication.9 -
Today, the security department stopped our new project and told us to work on the last project instead because of a top-secret security flaw.
Problem is, they are not allowed to tell us what the problem is. FML 1
1 -
The effect of the scoring system is interesting.
On Facebook, where I usually spend most of my social media time, I have been training myself to NOT comment unless I really wanna engage, because I have an IRL habit of just talking shit just to hear myself speak that bleeds into my Facebook engagement, which is a character flaw I’m trying to change.
On here though, I will see something I wouldn’t normally respond to and I’ll comment cause I want those ++s.
BUT the quality of my comments on here are generally way “better” (more meaningful, usually kinder, etc) than my FB comments, obvi because I want those ++s and on Facebook I can be as dumb and mean as I want without having “consequences” aside from the obvious social consequences of people thinking I’m an asshole...but on here it kinda forces me to be more mindful of how I’m engaging with people5 -
What a new years start..
"Kernel memory leaking Intel processor design flaw forces Linux, Windows redesign"
"Crucially, these updates to both Linux and Windows will incur a performance hit on Intel products. The effects are still being benchmarked, however we're looking at a ballpark figure of five to 30 per cent slow down"
"It is understood the bug is present in modern Intel processors produced in the past decade. It allows normal user programs – from database applications to JavaScript in web browsers – to discern to some extent the layout or contents of protected kernel memory areas."
"The fix is to separate the kernel's memory completely from user processes using what's called Kernel Page Table Isolation, or KPTI. At one point, Forcefully Unmap Complete Kernel With Interrupt Trampolines, aka FUCKWIT, was mulled by the Linux kernel team, giving you an idea of how annoying this has been for the developers."
>How can this security hole be abused?
"At worst, the hole could be abused by programs and logged-in users to read the contents of the kernel's memory."
https://theregister.co.uk/2018/01/... 22
22 -
The worst part of being a dev is when you realize you have a major design flaw in your architecture at 4:50 PM on a Friday. Goodbye weekend, hello intense thought.2
-
When you look at some production code that has been released for 4 years and find a HUGE security, like catastrophic here is my server hack me flaw 😁4
-
I use a library and it gives me some strange error message. No problemo, just file an issue on GitHub asking the maintainer if I'm plain stupid or the lib actually has a flaw. As it was a question, I have not posted a dump and all the shit.
Maintainer responds with a snarky comment about his crystal ball being broken and I have to submit a log, a dump, debug information and a bunch of other stuff.
Well, what choice do I have, I collect all the requested information, create a wall of text comment, all nicely formatted.
And the issue ends here. Myths say, the maintainer got asked to join Elvis on Mars.
I mean, why do you ask all the shit from me in a unprofessional manner just to stop answering? Just say "I have no clue why it behaves like this" and I know whats playin. But that's just ... sad.5 -
There was a bug in "Change email" module. When the functionality is called, it sends 2 emails:
1. to a current email w/ a link to 'reject email change'
2. to a new email w/ a link to 'confirm email change'
The flaw was in how these links worked (the clockwork behind them). If one link is clicked, another one is NOT deactivated in the bkend :)
Now the task for you is to figure out why this is wrong :)4 -
So there is a WP plugin for GDPR conformity. True to form of the shitty WP plugin ecosystem, it has a major security hole that allows taking over the WP installation:
https://wordfence.com/blog/2018/...4 -
About a decade ago there was a torrent site for audiobooks audiobookbay I think?, if you forgot your password to your username they would literally just give you a new password on the next page. Naturally being a 1337H4X0R teenager I found the username of one of the admins and got into their account on the site. I don't know if they ever fixed that but that was a serious wtf moment.
Edit: just checked this flaw has not been patched.8 -
Well, here is another Intel CPU flaw.
I'm starting to think that all these were done on purpose...
https://thehackernews.com/2019/05/...3 -
Well, not necessary my favourite but the first one I learned.
I think the weird syntax and semantics combined with the ridiculous average length of variable names is a major flaw in this one.4 -
Anyone reading these emails we are sending?
I work at a small place. A few users are using an application at our place that I develop and maintain. We all work remotely.
I announce by email to these few users a new version release of said application because of low level changes in the database, send the timeline for the upgrade, I include the new executable, with an easy illustrated 2 minutes *howto* to update painlessly.
Yet, past the date of the upgrade, 100% of the application users emailed me because they were not able to use the software anymore.
----------------
Or I have this issue where we identified a vulnerability in our systems - and I send out an email asking (as soon as possible) for which client version users are using to access the database, so that I patch everything swiftly right. Else everything may crash. Like a clean summary, 2 lines. Easy. A 30 second thing.
A week pass, no answer, I send again.
Then a second week pass, one user answers, saying:
> well I am busy, I will have time to check this out in February.
----------------
Then I am asking myself:
* Why sending email at all in the first place?
* Who wrote these 'best practices textbooks about warning users on schedule/expected downtime?'
*How about I just patch and release first and then expect the emails from the users *after* because 'something is broken', right? Whatever I do, they don't read it.
Oh and before anyone suggest that I should talk to my boss about this behavior from the users, my boss is included in the aforementioned 'users'.
Catch-22 much ? Haha thanks for reading
/rant7 -
Apache Tomcat vulnerability "GHOSTCAT" allows read conduct files and implant web shells. All versions in the last 13 years vulnerable.
According to Security Researcher of Chaitin Tech : Due to a flaw in the Tomcat AJP protocol (the channel for Tomcat to connect to the outside, pass them to the corresponding web application for processing and return the response result of the request), an attacker can read or include any files in the webapp directories of Tomcat.
For example, An attacker can read the web-app configuration files or source code. In addition, if the target web application has a file upload function, the attacker may execute malicious code on the target host by exploiting file inclusion through "GHOSTCAT" vulnerability.
Apache Tomcat has officially released versions 9.0.31, 8.5.51, and 7.0.100 to fix this vulnerability.4 -
Android flow I’ve found(fixed in android 8, working on 7.1.1):
To make app uninstallable by the normal user make the app device administrator, add “android.permission.SYSTEM_ALERT_WINDOW” to the manifest and make sure it’s not granted by the user.
Now when you try to uninstall the app, it tells you to disable it from device administrators but the device administrator disable dialog is System Window handled by the app itself and if the app has this permission but not granted, settings will crash with SecurityException leaving the app untouched. 4
4 -
what kind of dumb fuck you have to be to get the react js dev job in company that has agile processes if you hate the JS all the way along with refusing to invest your time to learn about shit you are supposed to do and let's add total lack of understanding how things work, specifically giving zero fucks about agile and mocking it on every occasion and asking stupid questions that are answered in first 5 minutes of reading any blog post about intro to agile processes? Is it to annoy the shit out of others?
On top of that trying to reinvent the wheels for every friggin task with some totally unrelated tech or stack that is not used in the company you work for?
and solution is always half-assed and I always find flaw in it by just looking at it as there are tons of battle-tested solutions or patterns that are better by 100 miles regarding ease of use, security and optimization.
classic php/mysql backend issues - "ooh, the java has garbage collector" - i don't give a fuck about java at this company, give me friggin php solution - 'ooh, that issue in python/haskel/C#/LUA/basically any other prog language is resolved totally different and it looks better!' - well it seems that he knows everything besides php!
Yeah we will change all the fucking tech we use in this huge ass app because your inability to learn to focus on the friggin problem in the friggin language you got the job for.
Guy works with react, asked about thoughts on react - 'i hope it cease to exists along with whole JS ecosystem as soon as possible, because JS is weird'. Great, why did you fucking applied for the job in the first place if it pushes all of your wrong buttons!
Fucking rockstar/ninja developers! (and I don't mean on actual 'rockstar' language devs).
Also constantly talks about game development and we are developing web-related suite of apps, so why the fuck did you even applied? why?
I just hate that attitude of mocking everything and everyone along with the 'god complex' without really contributing with any constructive feedback combined with half-assed doing something that someone before him already mastered and on top of that pretending that is on the same level, but mainly acting as at least 2 levels above, alas in reality just produces bolognese that everybody has to clean up later.
When someone gives constructive feedback with lenghty argument why and how that solution is wrong on so many levels, pulls the 'well, i'm still learning that' card.
If I as code monkey can learn something in 2 friggin days including good practices and most of crazy intricacies about that new thing, you as a programmer god should be able to learn it in 2 fucking hours!
Fucking arrogant pricks!8 -
!Rant
Wrote a crawler and now has 18 million records in the queue. About 500.000 files with metadata.
1 month until deadline and we have to do shit many things.
Now we discover we have a flaw in our crawler ( I don't see it as a bug ).. We don't know how much metadata we missed, but now we have to write a script that scrapes every webpage that we've already visited and get that metadata..
What's the flaw you ask? Some people find it funny to put capital letters in their attribute names.. *kuch* Microsoft.com!! *kuch*
And what didn't we do? We didn't lower case each entire webpage and then, only then, search the webpage for data..5 -
The biggest flaw of devRant is down voting is not as simple as up voting. I need to specify the reason for down vote. And those reasons include repost and offensive. This is redundant as there is already an option to report once you open the post. Either make done voting an one click affair or make up voting two click process. There should be uniformity.7
-
As a guy with a Intel 6800K I now really feel robbed of my money by Intel.
For over 10 years they knew of the heavy design flaw and put it through.
The ironic thing is, that every country will set up a penalty for Intel, but the Customers with the CPU's wont even see a buck.
It sucks that I have up to 30% less CPU Power after next weeks patch.
I will banish Intel now forever!! You should never come again in my Business!!!
Even my newly ordered Tablet with a Intel chip will suck d*ck now...9 -
Why the heck would you allow (or need) nested block comments? Imo this is a major design flaw in the kotlin linter.
I always use /*... //*/ so I can remove the comment starter w/o having to remove the comment end, but kotlin just starts a second, nested comment there.
Java, C, Cpp, C#, JS,... Not one of these uses nested block comments. I think jetbrains was just lazy?
I mean, I know why such stuff happens. I also developed DSLs in MPS, but there sure are ways to go around such things..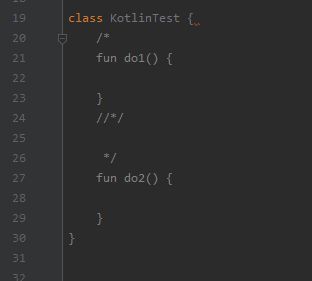 7
7 -
So apparently some major vpn connection providers got compromised some time ago.
https://twitter.com/hexdefined/...
https://twitter.com/cryptostorm_is/...
adding the fact that major enterprise vpn network providers had security flaws earlier this year
https://sdxcentral.com/articles/...
Sums up what was the major topic in security this year.
At the end I see something like cloud act that allows wiretapping anyone.
https://justice.gov/opa/pr/...
And when we multiply this by number of companies that have services in cloud that sums up privacy these days.
Non existent.6 -
!dev
So after 5 months of complaining and ISP denying that the modem was at fault for the issues ("because they'd get more complaints if it was") while trying to rip us off as well[1], they finally gave in to sending us one of the modems "intended for their business users"[2].
Low and behold... I haven't had any issues yet in the past few days (as opposed to having issues between 3 and 8 times a day).
Nah lads, surely wasn't the piece of shit old modem that is known to have a severe design flaw right? :^)
Must have been my router and devices behind it right? :^)
References:
1: https://devrant.com/rants/4378988/...
2: https://devrant.com/rants/4399477/...2 -
For those of you who still refuse to accept that safety features in languages are useful and important:
https://daniel.haxx.se/blog/2023/...
The author of curl himself admits that this security flaw could have been prevented if he had used a memory safe language.
I‘m not blaming the author for making this mistake and I‘m not saying that curl should be rewritten in another language.
I just want to rub this in the faces of people who argue that "bugs are always the developer’s fault, therefore it’s perfectly fine to keep using unsafe languages"2 -
The used option isnt preselected.
I declare this the worst flaw of the app.
Literally unusable.
0/10 stars.
Goodbye. 2
2 -
Just finished a large write up on a security flaw I found and disclosed in an exam spyware vendor's "zero knowledge encryption" - derived keys that were generated from incrementing integers, discussion on obfuscation and more.
It was a hell of a time writing this up; not sure if linking my personal blog here would be bad practice, but here it is: https://proctor.ninja/wave-rake-pro...
It's been something else, but hopefully I can keep fighting against tech like this on school campuses.4 -
Okay, one after another. They like to piss me off, apparently.
Coleague knows something isn't possible with current state of some api and pushes phone to me so I can maybe figure out what to reply to client. I dry-typed in "Its not possible" gave him phone and said "boom done, you know it aint possible"
Okay, TL;DR she got pissed that I am pissed that this BS is thrown at me and I dont want to participate in promissing something I know is undeliverable.
So she told me to go to PM/PO *kind of guy but not rly* with that problem. He aint technical by any mean. We are small company and for some reason this guy has more bearoucratic approach than I thought is possible to fit in one human.
Anyway. Well, apparently we will have meeting what are our options.
It all beginned that one guy promissed other guy undeliverable feature....
And becouse someone couldn't use his fucking brain it's pushed onto me, or I need to figure out how to do it. You cant without introducing safety flaw, period, it's that fuckin' simple.
But nooo, we will have god-knows-how-long meeting, that will bring exacly 0 value, as fking allways, and all I want now is just fucking focus on my fucking code becouse, ya know, I have timeline to follow, I dont have time to all that BS.
And to give you context, while keeping the stuff I cant share secret, imagine you have an API, that is just 'facade' of backend API, and layer of security. And they want to add authoritative endpoint to the facade API. Kind of endpoint "yes, you got paid".
Bravo, big brain, it will not work without like huge-as-fuck vunrability...
IDIOTS
How to not get pissed? Any protips?1 -
Get assigned a PR review
Spend half an hour meticulously looking through it
Looks flawless, no errors, compiles, test cases passing, expected results
Approve request
Another developer immediately finds a flaw
Fuck. I think I am totally incapable of making myself look good.4 -
Hello and welcome, to a presentation in which I will tell you my thoughts on the shortcomings of modern day computers and programming practices.
Computers are based on a very fundamental and old idea, folders, and files, a file is basically a concrete amount of data, whereas a folder is a group of files, and it comes from the real life concept of files and folders, now it might be quite obvious already that using a concept invented in 1898 by a guy called Edwin G. Seibels, might not be the best way for computers to function in the year 2020, but alas, it is.
Unless of course, you step into the world of a programmer.
A programmer’s world is much different, they use this idea of a data structure, or in simpler terms, an object. An Object is just like what you would think of as an object in your head, something with different properties that you can think about in different ways, for example your mobile phone, it has a battery percentage, it has a screen size, it has free space available. Programmers use these data structures to analyse data very quickly, like finding all phones with a screen size bigger than a certain size for example.
The problem is that programmers still use files and folders to create the programs that use these objects.
Consider this example.
Let’s say you want to create a virtual version of a drink bottle, consider what properties it will have, colour, volume, height, width, depth, material, etc..
As a programmer, you can leverage programming features and change the properties of a drink bottle directly, if you wanted to change the colour, you just say, drink bottle “dot” colour, equals blue, or red.
But if the drink bottle was represented as a file, all the drink bottles data would be inside the one file, so you would have to open the whole file, find the line or section of the file that has the colour data of the drink bottle, and select it, highlight it, delete what’s there, and type in your new value.
One way to explain this better is to imagine a folder that now represents the drink bottle, imagine adding a new file into that folder that represents each property I described before, colour, volume, etc.., well now, you could just open that folder, find the file for colour, either by looking with your eyes or you could do a file search in the folder for a file called colour, open it, and edit the value inside. This way of editing objects is the one that more closely represents the way programmers and a program itself interacts with objects inside a running programming language.
But the thing is, programmers don’t use the folder/file way of creating objects and putting them into programs, because it would be too cumbersome, they just create 1 file for an object, or have lots of objects in a file, and create all the objects in 1 file, and then run the program which creates the objects, then when they stop the program, it deletes the objects. So there is no actual link between the object in a file and the object that the program creates by reading the data from that file, if you change the object in your program, it does not get saved to the file.
So programmers created databases to house these objects, but there is still a flaw in databases, they are hard to interface with, and mostly databases are just used to send data or retrieve data from, programmatically, you can’t really browse a database the way you can browse the files on your computer. You can, but database interfaces are not made to be easily navigated the way files and folders are.
As it stands, there is no way to store objects instead of files on your computer and interact with them in complex ways the way programmers can inside the programs they create.
If the idea of an object became standard the way a file and folder is standard, I think it would empower human’s a great deal to express things far more easily and fluidly than they can today.
Thanks for reading.8 -
Front end developer is still getting a ticket even though the security flaw lies in the back-end.
Today, every click of the UI has an overlay of circular progress indicator indicates that there will be a synchronous actions in an asynchronous requests.
1 click = 1 loading state -
Do you have any annoying you want to get rid off, but you can't because of reasons?
I do. They are 4, but for now I'll talk about the gold medal winner.
When we met about 8-9 ago, she had just come back to town due to some very bad personal experience (not her fault). Anyway, she is polite, but her major flaw is that she is pushy. REAL BAD! And she gets mad when other people (including me) try to do it on her. Another one is having calls during random inappropriate times, because she had fight #N with her boyfriend, and last but not least, she will call when needs something out of someone.
Lately, her project is finding us a job, since we're both unemployed. Any job. The sad part is when she sends me job ads for dev jobs I don't qualify, e.g. Company X is looking for a dev with Y year of experience, knowing A, B, C & D technologies. I've told her that I don't qualify for most of the dev jobs she sends me, but she insists I should send my CV anyway, cause of reasons. Also, for some reason, I should be accounted to her for all my current choices when what I would honestly say is "BUG OFF".
Her latest endeavour is getting me one of her friends (a psychologist) as a "client". Her friend wants to have a professional website with writing posts/articles as a side dish. I'm not registered as a freelancer, so everything will be done under the counter, and her friend is OK with that. I'm no web developer, but I didn't refuse because of her backlash and also that would be a positive experience for me. Now, the juicy part. She gave her my phone number without my permission and she told me straight away. Her plan was having the three of us meet, though I don't know why and I didn't want her being around. I asked her to call me immediately, which it didn't happen. After being pestered by my friend for a couple of weeks if her friend called me, she finally did it on Monday. She didn't say to me anything I didn't know, but at least I have her phone now.
What I can offer her is a website skeleton with the usabilities she's asking. What I can't offer her is graphics/banner and security. And now I have to come up with reasonable price. Teams here ask 400-600€ for a complete website the way she asks, including VAT. I'm thinking around 100€ and I don't know when I can deliver the project. I've had some experience with Ruby and Sinatra, so I'll go with that, and I'll learn CSS along the way.
Thanks for reading till the end! 😃4 -
I'm trying to upgrade my account passwords etc. keepass (password manager) doesn't generate resizable windows, so when I want to generate a new password or do anything that creates a new window, THE NEW WINDOW IS TOO TALL FOR ME TO SEE WHAT'S AT THE BOTTOM AND THERE'S NOT EVEN THE OPTION TO SCROLL OR ZOOM OUT. YOU'RE OPEN SOURCE AND GIVING ME THIS BULLSHIT? If you were a living creature you'd be a giraffe with short stubby legs. Your missing features mean you don't get the best leaves and leave you dining with the rest of the peasants. At least I can interact with what I CAN see and closing the window prompts me to save changes, and passwords are generated by the rules I can actually see to manipulate.
Maybe I should look into the source or look at others' screenshots to see what I can't and tab into it to make blind changes, but I'm sufficiently happy with the passwords it gives already. I'm just pissed something so well rated has a flaw like that. Like a game where some levels are locked and you can't unlock them through play -_-2 -
Just started reading The Mythical Man-Month, and already in the first two chapters I went "oh hey this [fatal flaw in planning] sounds familiar!"
Is this a good or a bad sign...?6 -
tl;dr. web hosting && a panic attack && security threat
i wasn't sure whether my brother's domain was hosted or not (because it wasnt showing a website and he didnt know any better).
so i decided to host a react-app for it on netlify and pointed the domain's nameservers towards it (a separate security threat at bottom).
all went well and now when you punch in the domain it ..all-behold.. shows a website.
NOW, i remember my brother was using the domain's email which probably means it was hosted, right?. so im panicking because im not sure whether i just deleted all his emails or not because it's 1:15 am and he's asleep.
there is a rant in there somewhere but im in too much of a shock as to how much data i might have just accidentally deleted
.
.
another tl;dr: my domain registrar let me change someone else's settings..
the reason i didnt know his domain settings is that he didnt know his password.
i had bought a couple of domains and was gonna host them on netlify. while i was doing this a bright idea hit me.. "you should finally build a website for your brother for the domain he bought 7 years ago"..
this is where the fun begins.
i sent an email to my registrar to point all nameservers of all domains to my nameservers and just to try out i included my brother's domain into it (i dont own this domain it's not registered by my email), and the next day i get an email telling me they've successfully made all changes.
.
Now tomorrow is monday and i'm going to their office to tell them i found a security flaw and see how long i can stall before actually telling them what it was and how their live's could've been made hell.3 -
Take a day off, entire system goes down. Come in the next day: "We need to fix this".
12 hours later we get the system back up and a significant design flaw is now known which needs to be fixed on Monday.
It feels good to have the bandaid in place.
Don't use cursors kids, unless you absolutely have to.3 -
That moment, in a meeting when you are trying to show a technical flaw in a manager idea... And suddenly you have a déjà vu moment from the "The Expert" comic sketch...
-
~just-interesting-hack-things~
I was able to force my phone to work with 2 fingerprints by alternating my fingers during the setup.1 -
Virgin Powerbeats™ pro:
- can’t even fit into your pocket, you have to buy special iPants™ with bigger pockets, that would be $1499, thank you
- have buttons so finicky and annoying that you’re really better off with a touch area
- silicone tips deteriorate and are prone to stay inside your ears. Uh oh, anyone but certified iOtholaryngologists™ aren’t authorized to remove them or else they would be put to Apple Jail™. The removal would be $499 per ear, thank you
- you have to be a PhD topologist to figure out how to put them back into their case
- uh oh, one bud just randomly stopped working because of a design flaw in our case, that’s User Error™, would you like to pay for a replacement with your Apple Card™?
- a feel of greasy deteriorating clamshell
Chad Jabra Elite
- a feel of a brass zippo, magnets are just perfect
- firm, real buttons. Improve then just one level and you got the feel of IBM Model M
- you press a button and you hear whatever mics are picking, no need to ever pull them out
- most comfortable buds I’ve ever tried
- small case fits into pockets of my tight booty shorts just fine
- waterproof
- sounds better than anything Noble Audio have ever done
Beats suck i guess 🤷 6
6 -
What is the main flaw of Ruby ?
It has so many ways to install that, if you try all of them, you'll be using no Ruby at all.
I was going crazy because IDK when I installed an old version of Ruby with RVM, than a newer version with Homebrew, and now I am getting totally crazy!!!!! -
I can't decide which is worse
I changed the wrong if statement accidentally sent out 15k emails to a clients customers.
Or
Imported a dump of the database instead of take a dump while a colleague was on site training the client on their software.... But found a flaw in our server backups.1 -
I just got a call from Satya. He informed me that Microsoft has successfully acquired the Linux kernel and all future development will be closed sourced.
Here's a sneak peek of the official announcement:
There will be a newer version released tomorrow that will include the Windows desktop environment as well as patch a critical 0-day security flaw that was recently discovered in all versions of Linux.
To prevent exploitation, we will activate a kill switch which will disable all systems running any flavor of Linux next week.
Thus we advise you upgrade ASAP, existing users can get the latest version online for $500.8 -
That moment when: you realize your team has introduced a fatal flaw and lacks the foresight to understand it. The countdown has begun.2
-
So this is kind of an odd scenario, but bare with me. My client has been issued a JWT token. After having received and stored it, I completely reset the database, and so also emptied the users table. Note that we're using MySQL with auto incrementing ID, whose counter has been reset. The user ID is stored in the JWT, so now the JWT isn't referencing an existing user anymore, so the client will get a 401. The problem arises when a new user registers and is inserted in the new database. That user will get ID 1, and so the old token for the other user will suddenly be valid for another user. I know it's an odd case, but is this a flaw in JWT? I guess an easy solution would be to use random ID's, but I'm still wondering.6
-
I got into development only a short time ago.
My mother paired up with a partner who was a dev making some serious cheddar when I was just barely not a teenager anymore, while I was working shitty low-wage customer service gigs.
Honestly, the only reason either of them could give me for doing it was the money.
A couple years went by, I was extremely fortunate: found a job within 6 weeks of finishing a year-long program at the local technical college which only yielded me a basic cert. By that time, my mother's partner had long lost their job, and I had paid their rent (twice my own) on two separate occasions. I went from usually having about a hundred dollars after bills to last me until next paycheck to five times that.
A couple more years go by, I'm doing pretty well supporting my own family now (my wife and child, not anyone else) and somehow doing way better now than the people who spurred me ever did. I no longer have a reason to compulsively check my bank account out of worry that I'm overdrawn.
Now I'm locked in an endless battle in my mind to find a correction for every flaw in my life, or at the very least a workaround. I go to bed and wake up thinking about the same things: my work. Buuuutttt.... My family has everything they could ever need and more.
So I guess I could say the support I got from my family was:
* an initial nudge in the "right" direction
* a reality check on what the industry can be like
* a sentence to eternal damnation by changing my paradigm on everything -
You ever had a boss that made you feel like his bitch but he never really earned the title
You also know from a technical skill perspective you’re more competent.
And the only job he seems to do is micromanaging you. He just puts things under a microscope looking for a flaw. He always finds a flaw so in the off chance it breaks he’s always in the clear.
He’s the guy who sticks with the programs the he was taught when he was still at school and never really tried something new out of the box. He gives the reasons the he wasn’t formally trained in the other programs . I’m not talking cinema 4 here. I’m talking Matlab preference over python. Using lab-view as a production level development platform instead of going to something more approved by the industry.
He doesn’t take risk but he pushes those risks on you so if you fail he can say it wasn’t him
He’s never wrong but he’s never right either.
You’re sitting there doing the cunt work and breaking the sweat and he passes the achievements as under his management. You never really get the credit because “he guided you “. You go through hell fixing bugs and he disappears. He says he’s always a call away when what you really needed is someone taking the heavy tasks not throwing the entire project on your back.
I never call that piece of shit bcz he just throws some other bullshit that doesn’t make sense and emphasizes that might be the problem.
I once had a problem with the com port on a pc and was trying to figure out the problem. I asked him and he said that it might be bcz I’m connecting to the PC via VNC. I was like what the hell. What does that have to do with anything. I just ended up restarting the port and it bloody worked.
The saddest part is that I’m scared is that I might end up like him. In the same dead end job. Even though he guides me we work in a place where the job title doesn’t really change. Funny thing is that officially I have the same job title as him .
He’s been in the place for 5years when I came. Can someone imagine that? To work and work and then to be seized up with another brat who’s the same as you title wise.
You’re close the age of 40 and you work in a place where a 20 something year old walks in with the same Position as you.
I worry that I might end up the same if I stay long enough. That I’ll learn everything I can learn and just stop progressing and the only thing I can do is say how shit can break but wouldn’t know how to fix .
Pointing out problems because they are easier than fixing. Just plomonting into existential nihilism with no purpose.
I once told him I wanted to quit. He pretended he didn’t hear it. He then then said what do you see in this job in 5 years
I told him me not in it.
He said “seriously what do you want in this place “
I said “if I’m still her in 5 years I’ll be missing a toe because I would have shit myself in the foot”
I now realize that by convincing me to stay he might have convinced himself that staying for that long wasn’t a bad idea. He was looking for justification that he’s decision wasn’t that bad at all.
You give your life to a job and at the end it takes one away.
I don’t want to be like that and I think that’s what bugs me the most. That I’m so close to this individual that I feel sooner or later if I’m not careful I’ll end up in the same place. The same dread3 -
Thought after spending more than two days after a VBA non-sense flaw:
People that say that VBA is not that bad simply don’t have that much experience in VBA. -
Today is one of those magnificent days for my code. One of those days where I stumble up on the weirdest bugs and pull a fix out of my hat barely looking at any doc. One of those days where I find out there is a very tricky flaw in our project design and yet I end up finding an elegant solution to circumvent future problems. One of those days where I find the informations I want even though the documentation is the worst I've ever seen.
I love that productive feeling.random efficient docs efficiency i actually don't like tags bugfix bug fix doc bug documentation productive -
Done it once or twice when finishing up a feature for a presentation/delivery the next day.
I'm leaning on the side of Not Worth It because I'd rather not be sleep deprived and dumb in brainy brain when interacting with the client and demoing my other stuff.
I guess it's usually when my perfectionism flares up that I'm likely to do stuff like that.
Will consider an all-nighter if it's reeeally necessary but there's few scenarios I can imagine where that is warranted. Maybe when working on a very serious security flaw or something of that nature. Most stuff can wait a couple of days...
Edit: goddamn I guess I committed the sin of not really answering the question. There's no story here. Boooo. Permission to hate myself, captain? -
My biggest flaw when working in IT: I will refuse to prioritize time- consuming work with minimal added value (cf premature optimization, 0.001% edge cases) when I have a backlog of work that will add much more, obvious value and I will not budge to manager or architect power-plays and tendencies to micromanage my responsibilities, even if it may eventually end up getting me in trouble.2
-
How come that everytime I learn a new tech/framework, I find that one flaw after 5 minutes which has been there forever, dozens of people complain about it yet nobody fixed it?2
-
Day 8 without a laptop and I am losing my mind!!! I am behind on all projects with a review coming up on Saturday!!!!😡
My MacBook fell victim to the flex gate design flaw, costing a fortune to fix. I am getting a surface book instead and it was supposed to arrive today!!!! Now they are saying there’s a delay and I don’t even know when it will arrive!!!!!!! I am losing my mind! Help! 😩 what can I do to pass the time and take my mind off being behind on projects? It hit so bad I started learning to dance from YouTube! I’m tired of reading too!!!! Help! 😰5 -
>work as a team lead in a tiny startup that lives off of investment money due to a strained business team that should stop sucking
>everyone is underpaid
>make do with what I can, manage to push for raises to keep the team going
>one dev, Timmy, is a pretty nice fella
>with 1 very annoying flaw
“Why can’t we get all of our utilities paid?” “Why can’t we have unlimited paid time off?” “Why can’t we be like Biilionare Company XYZ?” “Company T gives everyone the latest laptop models” “we should be getting paid twice as much” “why do we have to work 8 hours?”
Constantly, to everyone.
I agree with Timmy in most points. He is not saying something I do not know. Sometimes I want to strangle Timmy, feed him his own nutsack, and kick him out to apply to billionaire company XYZ. He can have all those sweet sweet benefits. -
!rant
Rant from my previous work as a consultant Data Engineer (wish I had known this site back then).
During my stay at the place, we have a big client whose contact with us was an incompetent stressful fellow.
I single-handedly build a humongous automated data pipeline using Airflow. I am very proud of my baby as my first massive project and check it obsessively for every possible flaw, especially when writing down documentation for the poor soul that would take my place.
Luckily for me, everything is working as intended, until of course on my last day of work, shit hits the fan, and everything breaks down.
After a moment of initial panic: it was Thursday morning, we had a Machine Learning model to run over the weekend, predictions to make and reports to write and a very lovely next week deadline, I calm down.
"I won't be dealing with this shit anymore, starting from 18:00 PM and anyway Fear Is The Mind Killer."
Quite sure that it couldn't have been my code, I start looking at various logs when the culprit was clear. The B(ig) S(tupid) C(lient) changed the whole schema of the data he was feeding to us.
I call him: he has no idea of what was done to the data. Hell, at first he doesn't seem to remember what the deal with schema, data, and SQL is (the guy was supposed to be a big shot in the IT department). It turns out he hired one of our competitors to do his side of the collection pipeline. He tries to get mad at me, but everything he throws bounces back to him. I am calm yet ruthless pointing out how every major hiccup had been his fault and that I could quickly reach to his board of directors explaining why their Machine Learning model was late.
Result: he apologizes, extends our deadline, and I get a round of applause from other juniors who would have to deal with me had I failed.
Never am I happier to not work as an underpaid cannon fodder apprentice in a shitty consultant firm.
Luckily for me, everything is working as intended, until of course on my last day of work, shit hits the fan, and everything breaks down.
After a moment of initial panic: it was Thursday morning, we had a Machine Learning model to run over the weekend, predictions to make and reports to write and a very lovely next week deadline, I calm down.
"I won't be dealing with this shit anymore, starting from 18:00 PM and anyway Fear Is The Mind Killer."
Quite sure that it couldn't have been my code, I start looking at various logs when the culprit was clear. The B(ig) S(tupid) C(lient) changed the whole schema of the data he was feeding to us.
I call him: he has no idea of what was done to the data. Hell, at first he doesn't seem to remember what the deal with schema, data, and SQL is (the guy was supposed to be a big shot in the IT department). It turns out he hired one of our competitors to do his side of the collection pipeline. He tries to get mad at me, but everything he throws bounces back to him. I am calm yet ruthless pointing out how every major hiccup had been his fault and that I could quickly reach to his board of directors explaining why their Machine Learning model was late.
Result: he apologizes, extends our deadline, and I get a round of applause from other juniors who would have to deal with me had I failed.
Never am I happier to not work as an underpaid cannon fodder apprentice in a shitty consultant firm. -
In college, during Novell's heyday, I was working on my Certified Network Administrator certification (totally worthless, in retrospect). As I was becoming an expert in all things Novell, I found a security flaw. Using Visual Basic it was possible to code up an exact replica of the Novell login screen that launched at boot time from a batch file stored on a floppy. You could log peoples' usernames and passwords all day as long as they didn't realize your floppy was in the drive, which worked in certain computer lab setups on campus. I wasn't in it for stealing info or being a criminal. I just did it for the lulz. But if I had gained access to a few of the right computers in admin offices on campus, I could've gotten access to anyone's student profiles and grades.
-
We're so back guys! Someone starred my truthchain repo - at this point I'm sure we'll kick X (twitter) out of business! There's only like 90% of the features unsafe and broken and every release has a major flaw and is broken and requires extra bs to work, but it's fine at 0.1.6, imagine someone actually contributed or makes a comment - I would immediately quit my job and dedicate full time (not). 😅
-
What would you do if you discover a major security flaw in an enterprise product that claims to be secure and has GDPR compliance? Like a really major flaw in a core feature of the product!9
-
If I wanted good feedback for my products (especially if they were geared towards developers) I would scrap devRant and do some data analysis on how our products are perceived in raw form. Would be very raw and informative insight indeed because you are at the heart of raging innovation (raging innovation: when a developer is so pissed at a flaw in a piece of software they highlight or fabricate an ingenious feature or solution) and will help not only iron the kinks out but make a better product all together. Also, of course the good aspects would be lauded.
-
A list with usernames and passwords have to go from customer A to customer B, because customer A does not have the permission to set these login credentials to the productive system. Additionally, the users are technically unable to change their passwords (yes I know, it's a mess there). What should customer a do? Like except burn all my customers alive and punch them...
-
Why do companies have a competitive coding round when at the end, they want the person to develop things. I know most of them want software engineers instead of developers but the persons developement skills also matters and at the end when the person does not have any developement skills, how is he gonna help.
In one of the program ran by one of the biggest MNC of the World, I was selected from a hackathon and there are some peoples who are selected by a competitive coding round. Now, we are given an assignment in which we have to make a tic-tac-toe game which is AI driven. During one of the meetings with other group members and mentor, many of the persons who got entries by competative programing round does not know any bit of HTML. Out of the 5 weeks of program, they have spent more than 4 weeks in just learning basic HTML, CSS and still they are learning. I don't know even they can complete the program in given timeline or not but this has been a major flaw in recruiting process which I thought is now good.4 -
When you discover a rather big security flaw in a mate code and your boss tell you that he might fix it for "version 2", for now we are good. Wtf, we are just hurting ourselves if this shit gets discovered by some other guy.
We are developing an android app for management and selling, for other company and we are a litte short in time for finishing the first version, but fuck, its a big security flaw. -
I hate the elasticsearch backup api.
From beginning to end it's an painful experience.
I try to explain it, but I don't think I will be able to cover it all.
The core concept is:
- repository (storage for snapshots)
- snapshots (actual backup)
The first design flaw is that every backup in an repository is incremental. ES creates an incremental filesystem tree.
Some reasons why this is a bad idea:
- deletion of (older) backups is slow, as newer backups need to be checked for integrity
- you simply have to trust ES that it does the right thing (given the bugs it has... It seems like a very bad idea TM)
- you have no possibility of verification of snapshots
Workaround... Create many repositories as each new repository forces an full backup.........
The second thing: ES scales. Many nodes / es instances form a cluster.
Usually backup APIs incorporate these in their design. ES does not.
If an index spans 12 nodes and u use an network storage, yes: a maximum of 12 nodes will open an eg NFS connection and start backuping.
It might sound not so bad with 12 nodes and one index...
But it get's pretty bad with 100s of indexes and several dozen nodes...
And there is no real limiting in ES. You can plug a few holes, but all in all, when you don't plan carefully your backups, you'll get a pretty f*cked up network congestion.
So traffic shaping must be manually added. Yay...
The last thing is the API itself.
It's a... very fragile thing.
Especially in older ES releases, the documentation is like handing you a flex instead of toilet paper for a wipe.
Documentation != API != Reality.
Especially the fault handling left me more than once speechless...
Eg:
/_snapshot/storage/backup
gives you a state PARTIAL
/_snapshot/storage/backup/_status
gives you a state SUCCESS
Why? The first one is blocking and refers to the backup status itself. The second one shouldn't be blocking and refers to the backup operation.
And yes. The backup operation state is SUCCESS, while the backup state might be PARTIAL (hence no full backup was made, there were errors).
So we have now an additional API that we query that then wraps the API of elasticsearch. With all these shiny scary workarounds like polling, since some APIs are blocking which might lead to a gateway timeout...
Gateway timeout? Yes. Since some operations can run a LONG (multiple hours) time and you don't want to have a ton of open connections hogging resources... You let the loadbalancer kill it. Most operations simply run in ES in the background, while the connection was killed.
So much joy and fun, isn't it?
Now add the latest SMR scandal and a few faulty (as in SMR instead of CMD) hdds in a hundred terabyte ZFS pool and you'll get my frustration level.
PS: The cluster has several dozen terabyte and a lot od nodes. If you have good advice, you're welcome - but please think carefully about this fact.
I might have accidentially vaporized people sending me links with solutions that don't work on large scale TM.2 -
!Rant
I've had my Oneplus 5 for about a month ow and must say I'm pleasantly surprised! This is the first smartphone I've had that I can't find any obvious flaw with and it feels so nice to not have any bloatware to worry about 😍6 -
So, Recently I had made a short film "Brazen Epiphany" and I added it to IMDB, I discovered that IMDB has a flawed verification system, they don't actually verify edits. So, I credited myself for acting in various films. And, they got approved. Then one day, a writer of one of those movies discovered this and ranted on Twitter about it
https://twitter.com/varungrover/...
I told him about this whole stuff, Then I was contacted by a journalist amd they published a story on this
https://mumbaimirror.indiatimes.com/...
I know it's pretty lame to give wrong information to a community website, but I enjoyed it5 -
I wrote my first proper promise today
I'm building a State-driven, ajax fed Order/Invoice creation UI which Sales Reps use to place purchases for customers over the phone. The backend is a mutated PHP OSCommerce catalog which I've been making strides in refactoring towards OOP/eliminating spahgetti code and the need for a massive bootstrapper file which includes a ton of nonsense (I started by isolating the session and several crucial classes dealing with currency, language and the cart)
I'm using raw JS and jquery with copious reorganization.
I like state driven design, so I write all my data objects as classes using a base class with a simple attribute setter, and then extend the class and define it's attributes as an array which is passed to the parent setter in the construct.
I have also populateFromJson method in the parent class which allows me to match the attribute names to database fields in the backend which returns via ajax.
I achieve the state tracking by placing these objects into an array which underscore.js Observe watches, and that triggers methods to update the DOM or other objects.
Sure, I could do this in react but
1) It's in an admin area where the sales reps using it have to use edge/chrome/Firefox
2) I'm still climbing the react learning curve, so I can rapid prototype in jquery faster instead of getting hung up on something I don't understand
3) said admin area already uses jquery anyway
4) I like a challenge
Implementing promises is quickly turning messy jquery ajax calls into neat organized promise based operations that fit into my state tracking paradigm, so all jquery is responsible for is user interaction events.
The big flaw I want to address is that I'm still making html elements as JS strings to generate inputs/fields into the pseudo-forms.
Can anyone point me in the direction of a library or practice that allows me to generate Dom elements in a template-style manner.4 -
Without diving into OO or "Micro$oft", I think the one major flaw in C# is the ability to use "regions".
It's like a feature that was specifically designed to hide shitty code.
If you know how to separate your logic properly and focus on good design principles, you should never have to use a "region" to "clean up" the way your source looks!5 -
Sigh same bug
Or design flaw
Fuck off
The box it grows to encompass a character for extraction to certain parameters
But if the page has a border it selects the whole page -
I got enrolled in 'extracurricular activity' in second grade of my elementary school. We were playing some games at first, but later teacher started to show us programming and explained the matter very well considering we all were 8 y olds. I got interested and while others would play games I was coding and solved assignments teacher gave us.
My family thought that computer will make me stupid, thinking it was made just for playing games. They promised me to get me the computer if I had highest grades in school. I did, not all of them but tried really hard to be the best, despite that I waited for years and still being close to have aced every subject in the meantime.
I got my first computer when I was 16.
Since that day I was constantly reminded that I am wasting my life away sitting at this stupid box.
Later when I got the job that was well payed, they acknowledged that they were wrong to do that for majority of my life.
My parents are unable to explain what I do at the job as they were never interested in what I really do. "Something with computers" is most common answer you can hear from them.
My parents are non-technical people and they still don't understand how that box works and God forbid that they buy something online. My father even rejects to use smartphone.
They also thought that I'm no college material despite always being in top 5 students of the year (not class, but whole year).
They had other plans for me, but I was aware of that and didn't gave a f00ck about what they want with my life. I knew what I want and that was all exactly opposite of what my parents would like.
I was not the child they wanted, but was good son, even helped them and worked student jobs to pay some bills and to help them financially and still they struggled so hard to find some flaw to my character and decisions just to make their point but more than often failed miserably and just proved how wrong they were and how they don't think anything trough.
Only one who really supported me was my elder sister as she knew I was doing the right thing! She also did it her way and I am proud of her as both of us were dealing with 2 tough customers.
long rant, but wanted to add one more thing, I was never into sport, but was training tae kwon do and was really into it and was decent at it among my peers. When I was going to national competition, on my way out of the house all I got from my parents was: "why are you even going there when you will immediately loose, is it just to travel a bit?"
TL;DR: my family supported me less in my life than worst phone call you had with IT support at your worse ISP!4 -
Studying a programming focused studyprogram.
Having to do minor software projects spanning about 2 weeks on average on a regular basis with regular classes in between.
Projects more often than not involve coding knowledge we haven't been teached prior during class.
Literally get told most of the stuff we needed for certain projects right after we already finished them and therefore already teached it to us ourselves.
Sitting in class bored because of this right now and will be probably again and again...1 -
You can make your software as good as you want, if its core functionality has one major flaw that cripples its usefulness, users will switch to an alternative.
For example, an imaginary file manager that is otherwise the best in the world becomes far less useful if it imposes an arbitrary fifty-character limit for naming files and folders.
If you developed a file manager better than ES File Explorer was in the golden age of smartphones (before Google excercised their so-called "iron grip" on Android OS by crippling storage access, presumably for some unknown economic incentive such as selling cloud storage, and before ES File Explorer became adware), and if your file manager had all the useful functionality like range selection and tabbed browsing and navigation history, but it limits file names to 50 characters even though the file system supports far longer names, the user will have to rely on a different application for the sole purpose of giving files longer names, since renaming, as a file action, is one of the few core features of a file management software.
Why do I mention a 50-character limit? The pre-installed "My Files" app by Samsung actually did once have a fifty-character limit for renaming files and folders. When entering a longer name, it would show the message "up to 50 characters available". My thought: "Yeah, thank you for being so damn useful (sarcasm). I already use you reluctantly because Google locked out superior third-party file managers likely for some stupid economic incentives, and now you make managing files even more of a headache than it already is, by imposing this pointless limitation on file names' length."
Some one at Samsung's developer department had a brain fart some day that it would be a smart idea to impose an arbitrary limit on file name lengths. It isn't.
The user needs to move files to a directory accessible to a superior third-party file manager just to give it a name longer than fifty characters. Even file management on desktop computers two decades ago was better than this crap!
All of this because Google apparently wants us to pay them instead of SanDisk or some other memory card vendor. This again shows that one only truly owns a device if one has root access. Then these crippling restrictions that were made "for security reasons" (which, in case it isn't clear, is an obvious pretext) can be defeated for selected apps.2 -
It is so frustrating that browsers had to keep the open developer tools as Ctrl+shift + C.I work with a ton of terminals and lot of browser tabs and when I try to copy text , I automatically type Ctrl + shift + C and boom , the developer tools opens up.I know we could change the key bindings but who the hell kept the "open developer tools " shortcut as Ctrl + Shift + C.That is a serious flaw!!! Fucking hate it..
-
WTF with Uber Eats. Finally I had some amount left in my salary. I ordered food via Uber eats and they charged me. After sometime they restaurant not accepted my order and cancelled it. I paid for and I don't have an extra money for ordering. The repayment says it will repay in after 7 days. After Contacting customer care number, it is only priority for the ordered customers only. I'm starving now...Fuck this morning and Uber eats. Any devs from that shitty company take care of that flaw...they are taking this as a fucky business...
What a flaw...taking is faster and repayment takes 7 days...
Seriously out of my mind....fuck...fuck....7 -
So here is a mini rant from an amateur/hobbyist developer (me).
Over the past week, I've taken on a project that is much larger than any other projects i've attempted to handle (steam trading bot). This meant that there would be logic flaws, weird bugs due to unexpected behavior from shitty web apis (and their poor documentation hmmmm).
Anyhow, fast forward a few days and the code is complete. It's mostly functional, apart from a few glitches and unexpected behavior here and there...or so i thought. Apparently if someone trades and item to me that isnt in my pricegrid, the bot freaks out and kills itself, relaunches, and repeats this cycle (pm2). And i only found out about this on my way to school
So in desperation to fix such a critical flaw in my code (if my bot breaks a lot and doesnt accept trades, i can get banned from backpack.tf), i bust out my only device which is my phone, and start editing away (JuiceSSH and turbo client is godsend ty). 30 minutes later, after toiling through code with no indentation or syntax highlights (mobile pls), ive fixed it. So i push to live and alls well.
Then I arrive at school, pull out my laptop and decided to check up on my code to see if anything needs fixing.
Oh look in one line i used '||' instead of '&&'.
ok lets fix it.
ok lets push to live again.
I launched WinSCP to move the files onto the server, and just as the loading bar finishes and the file is overwritten, i realized; FUCK the code i had on my laptop wasnt the latest version i just worked on on my phone.
So that's that. 30 minutes of typing code without indentation and syntax highlighting on a 5 inch screen and it's all gone.
TLDR:
Version control is a must. -
I am working on an event driven system that uses a message bus and has a few services that talk to each other asynchronously via the bus.
I'm writing in memory integration tests for one of those services, but I just realised the fundamental flaw here with such tests. I only have 1 application running, but I need several. This is quite a serious flaw I should have seen before.
Anyone else tried integration testing event driven distributed services? I imagine all I can do is stub the message broker...8 -
whenever I take extended brakes from reading whats on devrant the initial reopen of the app leads to a immediate crash. Android nougat.1
-
RECOVER BACK YOUR HARD EARN MONEY SCAMMED BY ONLINE IMPERSONATORS OR HACKERS FROM ANY PLATFORM.
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: D i g i t a l g o l d h u n t e r @ t e c h -c e n t e r . c o m1 -
Picking up a project from 9 years ago someone abandoned and trying to bring it up to the new toolchain. First thing to try: pre-existing everything and just make it. Immediate toolchain flaw exposed ("internal error converting unsigned int to int" in a header file in the chain, huzzah!)1
-
USDT AND BTC SCAMS VISIT SPARTAN TECH GROUP RETRIEVAL FOR EASY RECOVERY
One evening, I stumbled upon an advertisement on Google for an Ethereum trading bot that promised "guaranteed profits." The website was sleek and professional, with glowing testimonials from users who claimed to have made substantial returns with minimal risk.
The allure of easy money was too tempting to resist, and after some careful thought, I decided to invest 35 ETH, convinced I was making a wise financial decision. After transferring my ETH to the platform, I was prompted to connect my wallet for "automated trading." I felt a surge of excitement as I envisioned my investment growing. But within hours, I watched in horror as my funds began to disappear through a series of unauthorized transactions.
Panic set in as I realized my hard-earned ETH was vanishing. When I tried to reach out to customer support for assistance, I was met with silence; the website had vanished, leaving me in a state of shock and disbelief. I had fallen victim to a sophisticated crypto drainer scam, a harsh reality that many in the cryptocurrency world face. The realization was devastating: I had been ensnared by a meticulously crafted scheme designed to exploit unsuspecting investors like me.
With my funds gone and no way to recover them, I felt a mix of anger, regret, and helplessness. I turned to SPARTAN TECH GROUP RETRIEVAL, a firm specializing in crypto theft investigations. After researching various blockchain forensic experts, I was drawn to SPARTAN TECH GROUP RETRIEVAL due to their strong reputation for successfully recovering stolen assets.
Their team acted quickly, analyzing the attack and tracing the stolen funds through multiple wallets. SPARTAN TECH GROUP RETRIEVAL uncovered the scammer’s laundering route. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to recover my stolen ETH by exploiting a flaw in the scammer’s withdrawal process. This taught me invaluable lessons about the necessity of due diligence in the crypto space. With the guidance of SPARTAN TECH GROUP RETRIEVAL, I learned to be cautious of promises that seem too good to be true and to thoroughly investigate any platform before investing.
Although the road to recovery was fraught with challenges, I emerged with a deeper understanding of the risks associated with cryptocurrency trading and a renewed commitment to protecting my investments, all thanks to the support of SPARTAN TECH GROUP RETRIEVAL.
Spartan Tech Group Retrieval Contact Info Below
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 22 -
TRUSTWORTHY CRYPTO RECOVERY SERVICE- HIRE SALVAGE ASSET RECOVERY
At Tax Ease Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Salvage Asset Recovery. Salvage Asset Recovery’s team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform. Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Salvage Asset Recovery has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Salvage Asset Recovery helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information. Thanks to the quick and efficient actions of Salvage Asset Recovery, Tax Ease Solutions was able to recover $980,000 of the lost funds and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Salvage Asset ’s continued support, we will fully resolve the situation.
Their Contact info,
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
GET LEGAL AND PROFESSIONAL SERVICES WITH DIGITAL TECH GUARD RECOVERY COMPANY
One evening, I stumbled upon an advertisement on Google for an Ethereum trading bot that promised "guaranteed profits." The website was sleek and professional, filled with glowing testimonials from users who claimed to have made substantial returns with minimal risk. The allure of easy money was too tempting to resist, and after some careful thought, I decided to invest 35 ETH, convinced I was making a wise financial decision. After transferring my ETH to the platform, I was prompted to connect my wallet for "automated trading." I felt a surge of excitement as I envisioned my investment growing. But within hours, I watched in horror as my funds began to disappear through a series of unauthorized transactions. Panic set in as I realized my hard-earned ETH was vanishing before my eyes. When I tried to reach out to customer support for assistance, I was met with silence; the website had vanished, leaving me in a state of shock and disbelief. I had fallen victim to a sophisticated crypto drainer scam, a harsh reality that many in the cryptocurrency world face. The realization was devastating: I had been ensnared by a meticulously crafted scheme designed to exploit unsuspecting investors like me. With my funds gone and no way to recover them, I felt a mix of anger, regret, and helplessness. I turned to Digital Tech Guard Recovery, a firm specializing in crypto theft investigations. After researching various blockchain forensic experts, I was drawn to Digital Tech Guard Recovery due to their strong reputation for successfully recovering stolen assets. Their team acted quickly, analyzing the attack and tracing the stolen funds through multiple wallets. Digital Tech Guard Recovery uncovered the scammer’s laundering route. Thanks to Digital Tech Guard Recovery, I was able to recover my stolen ETH by exploiting a flaw in the scammer’s withdrawal process. This taught me invaluable lessons about the necessity of due diligence in the crypto space. With the guidance of Digital Tech Guard Recovery, I learned to be cautious of promises that seem too good to be true and to thoroughly investigate any platform before investing. Although the road to recovery was fraught with challenges, I emerged with a deeper understanding of the risks associated with cryptocurrency trading and a renewed commitment to protecting my investments, all thanks to the support of Digital Tech Guard Recovery.
WhatsApp: +1 (443) 859 - 2886
Zangi 10-4490-66571 -
POSSIBLE WAYS TO GET BACK EVERY PENNY LOSE TO SCAMMERS
At Digital Gold Hunters Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. com
whats App: +1 908 991 71321 -
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center. c o m
whats App: +1 908 991 71321 -
RECLAIM STOLEN CRYPTO REVIEW THROUGH RAPID DIGITAL RECOVERY
As the director of a small nonprofit dedicated to supporting underprivileged youth, I never anticipated facing a cryptocurrency crisis. Yet, I found myself grappling with a misconfigured smart contract that had locked away $85,000 in Bitcoin donations funds crucial for educational programs benefiting hundreds of children. A single error in the contract’s code rendered these donations irretrievable, jeopardizing our mission and the trust of our donors. In this moment of despair, RAPID DIGITAL RECOVERY emerged as saviors , not only salvaging our funds but also restoring our faith in expert intervention. The crisis began when a generous donor contributed Bitcoin through a custom smart contract designed to enhance transparency for charitable gifts. Unfortunately, a misconfiguration in the contract’s parameters locked the funds indefinitely. As panic set in, multiple developers reviewed the code and delivered the grim verdict: the cryptocurrency’s immutability meant the assets were likely lost forever. With donor frustration mounting and our projects stalled, I turned to online forums, where I discovered numerous testimonials praising RAPID DIGITAL RECOVERY’s expertise in resolving cryptocurrency emergencies. From our first consultation, RAPID DIGITAL RECOVERY distinguished themselves with their transparency and technical mastery. Their team patiently guided me through their process: auditing the contract’s code, identifying the flaw, and engineering a legal workaround to extract the funds without compromising the cryptocurrency’s integrity. They explained complex concepts in layman’s terms, ensuring I understood each step. Their commitment to urgency was particularly impressive; they recognized that these funds were not just “assets” but lifelines for vulnerable communities. Within 48 hours, their experts executed a meticulously planned recovery operation, employing advanced cryptographic techniques to bypass the contract’s faulty logic. The funds were safely redirected to a secure wallet, honoring the donor’s intent. Remarkably, RAPID DIGITAL RECOVERY even waived a portion of their fee upon learning about our nonprofit status, underscoring their dedication to philanthropic causes. This has taught me that the risks of cryptocurrency can be surmountable with the right expertise. RAPID DIGITAL RECOVERY isn’t just a service; they are guardians in cryptocurrency age . Their blend of technical brilliance and ethical integrity make them the best. For anyone facing cryptocurrency loss or Bitcoin lost due to scams or errors, I wholeheartedly recommend their services. They transformed our potential disaster into a testament of resilience.
CONTACT INFO BELOW:
WhatsApp: +1 4 14 80 71 4 85
Email: rapid digital recovery (@) execs. com2 -
HOW MY CARBON NEUTRAL BITCOIN WAS HELD HOSTAGE AND RESCUED BY ASSET RESCUE SPECIALIST
I believed in a cleaner tomorrow, one where blockchain and renewable energy were not enemies. My wind farm was proof. Excess energy powered my Bitcoin mining machines, a closed loop. It was the future. Until the ransomware attack.
My turbines hummed one morning as they always did, but my mining operation? Gone. My wallet? Locked. One message replaced my screen:
"Create a payment of 5 BTC to free your information. You have 72 hours."
The irony? My carbon-neutral Bitcoin had been taken hostage.
I panicked. I had crafted my system for survival, yet here I was, stuck. Perplexed, I went to industry colleagues. That's when one panelist from a Clean Energy Summit contacted me:
"Consider ASSET RESCUE SPECIALIST. They provide blockchain forensics, and they're carbon neutral!"
I was desperate but skeptical. During my first call, their personnel were talking my language, both security and sustainability. They did not just care about Bitcoin; they cared about why I was mining it.
Their approach? Genius. Instead of negotiating with the hackers, they reverse-engineered the ransomware. My infrastructure had been attacked through a zero-day vulnerability in the grid software, not my specific setup.
This wasn't a solo problem. This was an energy security emergency for the entire region.
Over 12 frenetic days, ASSET RESCUE SPECIALIST, worked with good-faith hackers and clean-energy engineers. They did not simply recover my Bitcoin without giving a ransom to attackers, they also fixed the flaw that had jeopardized our grid in the first place.
When I was finally able to log back in to my wallet, I felt like I'd regained not only my Bitcoin, but command over my vision.
My wind farm is now more secure than ever. ASSET RESCUE SPECIALIST, even helped us implement decentralized security protocols to prevent future hacks. And the icing on the cake? Their carbon offsets make their entire operation all about aligning with my emphasis on sustainability.
I once believed that Bitcoin and green energy were the perfect pair, but now I understand security is the third leg.
If you work in cleantech and disaster strikes? ASSET RESCUE SPECIALIST, is not a rescue team, they are a renewable power. 1
1 -
HOW YOU CAN RECOVER YOUR CRYPTO FROM SCAMMERS // CONSULT DIGITAL TECH GUARD RECOVERY
As a tech geek, I'm proud to be on the bleeding edge. So when I stored my Bitcoin in a "quantum-resistant" wallet, I was sure I was invincible, a Nostradamus of the modern age predicting the coming quantum computing apocalypse. "Hack-proof," the website had promised. "A fortress against the future."
And then irony struck. A bug in the firmware shut me out altogether. No access. No backups. Only a chilly, machine-like error message mocking me like a bad guy in a sci-fi flick: "Invalid Signature. Please Reset." Reset? That would mean erasing my $860,000 in Bitcoin. Not exactly a pleasant choice.
Furious, I did what any geek does when something is not right, I tweeted about it. My rant at the irony of a quantum-proof wallet crashing due to a widespread bug went viral. That is when a DM appeared. Digital Tech Guard Recovery's CTO had seen my tweet. "Let's fix this," he typed.
Now, I’ve dealt with tech support before, but this was something else. Within hours, their engineers were deep in my wallet’s firmware, analyzing the cryptographic flaw. They approached the problem like time travelers fixing a paradox, reverse-engineering the bug to develop a workaround.
It was a challenge. The wallet's special "quantum security" had locked it up so tightly that debugging tools couldn't even access it. But these guys were not your average IT support personnel; they were crypto Digitals.
For ten days, I monitored their progress like a scientist awaiting a space probe signal. Finally, the breakthrough: a hacked firmware update, specifically tailored for my wallet model. With cautious steps, I executed their recovery protocol, and voilà, my money was restored.
But they didn't leave it at that. Digital Tech Guard Recovery not only restored my Bitcoin but moved it to an even more secure, battle-tested storage system. No more cutting-edge vulnerabilities. Just solid, proven cryptography.
The irony? My Bitcoin is now safer than ever, not because it's quantum-resistant, but because of the individuals who came to my aid.
Lesson that was learned: The future is unpredictable, but having the right experts on speed dial? That's real security.
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Website link: digital tech guard . com1 -
I lost my cryptocurrency worth $308,000 investment in a platform that promised astronomical returns. I found a group specializing in crypto recovery after surfing through the net, Wizard James Recovery, who traced the flow of their coins across the blockchain and froze the wallets holding the funds before the scammers could liquidate them. The team secured access to a portion of the investor's assets, proving that $285,260 worth of Bitcoin was recoverable. The team turned a nightmare into a second chance in my life, fighting to make things right in a world full of thieves. The investor's art collective's multi-sig wallet hemorrhaged $308,000 in Bitcoin, and their studio fell silent. A blockchain dev tagged their graffiti wall with Solidity snippets, suggesting they contact Wizard James Recovery Services. Within hours, Wizard's team diagnosed a flaw in the withdrawal function, tracing the forgeries and changing the locks. The investor's studio became a war room, but the funds returned, and the art collective's installations thrived. All thanks to Wizard James Recovery Service. Below is their contact details.
WhatsApp Number + 4 47418367204
Email. wizardjamesrecovery @ usa . com1 -
Crypto Scam Recovery Company; How To Recover Lost Bitcoin If It's Stolen| Hire CYBER CONSTABLE INTELLIGENCE
An "investment mentor" promised to teach me flash loan arbitrage strategies, which sounded intriguing and potentially profitable. Eager to learn, I followed their instructions and connected my wallet to what I believed was a legitimate crypto dashboard. The interface looked professional and convincing, mimicking real platforms I had seen before. However, I was completely unaware that this was a fake site designed to deceive unsuspecting users like me. By connecting my wallet to this fraudulent dashboard, I inadvertently granted unlimited spending approval. This was a critical mistake that would cost me dearly. In a matter of seconds, the scammer executed a malicious contract that drained my wallet of $110,000. I was left in shock, realizing that I had fallen victim to a well-orchestrated scam. I sought help from Cyber Constable Intelligence, a team of smart contract auditors who specialize in investigating such attacks. They meticulously dissected the incident and discovered that the scammer had exploited wallet permissions rather than any flaw in the protocol itself. This revelation was both enlightening and alarming, as it highlighted the importance of understanding how wallet permissions work. The recovery auditors at Cyber Constable Intelligence tracked the stolen funds through multiple mixer services, which are often used to obscure the origins of illicitly obtained cryptocurrency. Their investigation led them to an exchange where some of the stolen funds had landed. However, they identified a critical lapse in the exchange's processes, which allowed the scammer to operate without being detected. After five days of relentless legal pressure and negotiations, I was relieved to learn that $87,000 of my lost funds had been recovered. This experience has fundamentally changed my approach to cryptocurrency. I now prioritize security and due diligence above all else. I’ve become an advocate for educating others about the risks in the crypto space, sharing my story to help prevent similar scams. I regularly participate in online forums and discussions, emphasizing the importance of verifying platforms and understanding wallet permissions, and if fallen victim Cyber Constable Intelligence are ready to assist.
Here's their Info below;
WhatsApp: 1 252378-7611
Email Info cyberconstable@coolsite net
Telegram Info: + 1 213 752 74877 -
The timelines at my workplace are too short that it's impossible to actually build anything or observe procedures like testing, software techniques for maintaining oop code, telemetry and other things I may have learnt along the way
So application templates are the order of the day. They pull solutions off the shelf, edit the interface, hand over to clients at an alarming rate (sometimes, within a matter of days!). So yesterday, the cto asked for ways I can recommend that the team is made more efficient. He takes what I say very seriously, owing to Suphle's appendix chapter as well as the issues its blueprint set out to solve
Like I said, those do not apply here. I mean, the developers I've met are making do and winging it. I'm the one struggling to adapt to rummaging through templates and customise shit
Maybe I'm over thinking it cuz there's no sense in fixing something that's not broken. So far, only flaw I've observed (because the product designer has complained to me bitterly that the devs hardly ever translates his prototypes verbatim), is the need for a dedicated mobile developer (not that multifunctional, confused portfolio called "fullstack). But I didn't raise this since the time frames hardly even afford time for writing apis or writing mobile code. You'd be surprised to realise that everything a client can possibly ask for is already somewhere, built at a higher standard than you can replicate
My question now is, what other positive novelty can I bring aboard? How can this process be further optimised? If it can't, what suggestions outside regular software development or this work flow can I bring to the table?
Personally, I'm considering asking him to tell me bottlenecks if he has identified any. But it's very likely that he would already have begun working towards it if he knew them. I suspect he needs someone outside the system to see what is lacking or a new addition that could even be a distant, outlandish branch of the tech market, but drive the company towards more profit1 -
It's been over 7 months of being deployed to help finish a project that's crossed the deadline umpteenth times. There's only this guy who had started on this project and me as developers. He's a nice guy, but I'm finding him to be a snowflake that's extremely difficult to work with. Every time I mention a critical problem with his original design, or the approaches he takes on this project, he takes it personally. He would pour out a long spiel of why this and why that, and waste most of the meeting time. Or he would run to his outdated diagrams or documents that he had created himself somewhere deep in the wiki forest, and use that as a defense. He creates his own user stories and tasks on a whim with no PM supervision. I've noted to the managers that this is a project to fail, and all they've done is assign a busy PM to this project, and the new PM is perfectly fine w/ the way the project has been handled so far.
I point out a small flaw with his assumptions just the other day, and he even managed to hyperventilate and again fall back to his outdated document... WTF? I'd rather start from scratch and get this project finished faster.. and even though I've expressed my objection to continue on this path, the managers foolishly believe that this project will be completed somehow. I don't hate my development partner, or PM, or people in the management, but I hate the fact that I don't have control over so many aspects of this project, including the half-assed, unnecessarily complex design, and the dev workflow itself. I feel like I'm tied to a car that's being thrown over the cliff, and assigned to fix the junky car w/ its engine broken before the car hits the ground. Something like this would never be allowed to go in a commercial sector. I just wish that the management could just give me control over project as THE lead & PM over this project, and get this project tied up for good, and with better reusability and quality.1 -
POSSIBLE WAYS TO RECOVER BACK YOUR SCAMMED CRYPTO FROM ANY INVESTMENT PLATFORM...
At TaxEase Solutions, based in New York, USA, we faced a critical crisis when our tax filing system was hacked overnight. The breach exposed sensitive personal data, including Social Security numbers, financial details, and addresses of our clients. The attackers used this stolen information to apply for fraudulent tax refunds, resulting in a significant loss of $1 million USD. The breach occurred during the night while our team was off-duty, leaving us unaware until the following morning when we discovered the extent of the damage. With such a large amount of money lost and the integrity of our business compromised, we knew we needed immediate assistance to recover and secure both our clients’ data and our reputation. That’s when we reached out to Digital Gold Hunter. Digital Gold Hunters team responded promptly and demonstrated their deep expertise in dealing with cybersecurity breaches. They quickly identified the source of the vulnerability and acted decisively to patch the system flaw. Their ability to rapidly assess the situation and implement corrective actions helped to prevent any further unauthorized access to our platform.Once the system was secured, Salvage Asset Recovery shifted their focus to assisting our affected clients. They worked diligently with financial institutions and law enforcement to help some clients who were able to reach out and report the fraudulent tax refund applications. Through their intervention, these clients were able to stop the fraudulent transactions and recover some of their funds. As of now, Digital Gold Hunter has managed to recover $980,000 of the lost $1 million, but they are still continuing to work with authorities and financial institutions to recover the remaining funds. Digital Gold Hunter helped us implement more robust security measures to prevent any future breaches. They introduced advanced encryption techniques and worked with us to update our cybersecurity protocols, ensuring that our clients' data would be better protected going forward. Their consultation also guided us in strengthening our internal data protection policies, which reassured our clients that we were committed to safeguarding their sensitive information.Thanks to the quick and efficient actions of Digital Gold Hunter, and protect the majority of our clients’ data. Their professionalism, expertise, and dedication to helping both our company and our clients made all the difference in mitigating the effects of the breach and stabilizing our business. The recovery process is still ongoing, but we remain confident that with Digital Gold Hunter ’s continued support, we will fully resolve the situation.
Their Contact info,
Email: Digitalgoldhunter@tech-center . c o m1