Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "trail"
-
So after many hours of trail and error I've managed to make a devRant client for ComputerCraft computers in Minecraft. :D
Thanks for hosting the server @ParkCity,
Also, I'll probably upload the source to GitHub some time soon. 33
33 -
Soms week ago a client came to me with the request to restructure the nameservers for his hosting company. Due to the requirements, I soon realised none of the existing DNS servers would be a perfect fit. Me, being a PHP programmer with some decent general linux/server skills decided to do what I do best: write a small nameservers which could execute the zone transfers... in PHP. I proposed the plan to the client and explained to him how this was going to solve all of his problems. He agreed and started worked.
After a few week of reading a dozen RFC documents on the DNS protocol I wrote a DNS library capable of reading/writing the master file format and reading/writing the binary wire format (we needed this anyway, we had some more projects where PHP did not provide is with enough control over the DNS queries). In short, I wrote a decent DNS resolver.
Another two weeks I was working on the actual DNS server which would handle the NOTIFY queries and execute the zone transfers (AXFR queries). I used the pthreads extension to make the server behave like an actual server which can handle multiple request at once. It took some time (in my opinion the pthreads extension is not extremely well documented and a lot of its behavior has to be detected through trail and error, or, reading the C source code. However, it still is a pretty decent extension.)
Yesterday, while debugging some last issues, the DNS server written in PHP received its first NOTIFY about a changed DNS zone. It executed the zone transfer and updated the real database of the actual primary DNS server. I was extremely euphoric and I began to realise what I wrote in the weeks before. I shared the good news the client and with some other people (a network engineer, a server administrator, a junior programmer, etc.). None of which really seemed to understand what I did. The most positive response was: "So, you can execute a zone transfer?", in a kind of condescending way.
This was one of those moments I realised again, most of the people, even those who are fairly technical, will never understand what we programmers do. My euphoric moment soon became a moment of loneliness...21 -
Was working on a Django thing (server-side, so no dynamicness as far as I'm aware?) under a contractor at my company.
Needed a popup to display results of a subprocess, so I asked "We're going to need to AJAX it, right?" and give brief justification. Guy says no - pretty much "Django 10/10 supports this, let me Google". Proceeds to send me a link to a python package that enables using popups as a way of inputting values for form fields. I see as much on the couple of images for the package demo/introduction, so I'm kind of just like "It doesn't look like it's what we need though..." But the guy says to trust him, and implement it.
A day later, after scrutinizing the demo code, and trying to figure out how to implement the package, I go back to him and say "I really really really don't think this is going to work" and give the same justification from the day before. He opens the demo code himself and follows the long trail of confusing methods and stuff.
After an hour of my sitting there watching him read the code and disappearing for 10 minute periods a few times, he comes to the conclusion "Okay you need to understand the code to implement it. But go ahead and use AJAX"
This is abridged and a few other super annoying things have been cut out, but I TRUSTED HIM.
I. TRUSTED. HIM.3 -
Woooo! Closed on a new home today, and it's ours. 2500 Sq ft, 4 bedrooms, huge farm kitchen. Five minute walk from a trailhead for a trail that runs along the shore of Lewisville Lake. Same commute to work. I'm happy.6
-
EEEEEEEEEEEE Some fAcking languages!! Actually barfs while using this trashdump!
The gist: new job, position required adv C# knowledge (like f yea, one of my fav languages), we are working with RPA (using software robots to automate stuff), and we are using some new robot still in beta phase, but robot has its own prog lang.
The problem:
- this language is kind of like ASM (i think so, I'm venting here, it's ASM OK), with syntax that burns your eyes
- no function return values, but I can live with that, at least they have some sort of functions
- emojies for identifiers (like php's $var, but they only aim for shitty features so you use a heart.. ♥var)
- only jump and jumpif for control flow
- no foopin variable scopes at all (if you run multiple scripts at the same time they even share variables *pukes*)
- weird alt characters everywhere. define strings with regular quotes? nah let's be [some mental illness] and use prime quotes (‴ U+2034), and like ⟦ ⟧ for array indexing, but only sometimes!
- super slow interpreter, ex a regular loop to count to 10 (using jumps because yea no actual loops) takes more than 20 seconds to execute, approx 700ms to run 1 code row.
- it supports c# snippets (defined with these stupid characters: ⊂ ⊃) and I guess that's the only c# I get to write with this job :^}
- on top of that, outdated documentation, because yea it's beta, but so crappin tedious with this trail n error to check how every feature works
The question: why in the living fartfaces yolk would you even make a new language when it's so easy nowadays to embed compilers!?! the robot is apparently made in c#, so it should be no funcking problem at all to add a damn lua compiler or something. having a tcp api would even be easier got dammit!!! And what in the world made our company think this robot was a plausible choice?! Did they do a full fubbing analysis of the different software robots out there and accidentally sorted by ease of use in reverse order?? 'cause that's the only explanation i can imagine
Frillin stupid shitpile of a language!!! AAAAAHHH
see the attached screenshot of production code we've developed at the company for reference.
Disclaimer: I do not stand responsible for any eventual headaches or gauged eyes caused by the named image.
(for those interested, the robot is G1ANT.Robot, https://beta.g1ant.com/)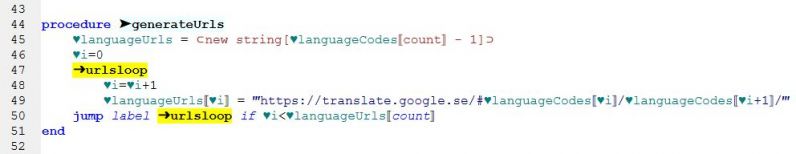 4
4 -
The best teacher that I've had is one of the teachers at my university lab.
He teaches Data Structures. We had some programming assignments and I was good at it, but whatever I'd do, he'd always find bugs, ask me to resolve it and he'd always give me challenges in the lab which is fun in the lab environment. University labs usually sticks to the sylabbus. I actually learned alot from that experience..
'Trail and Error is the best method to learn programming.'2 -
I had a CS teacher that could barely find the power button. She never gave any sort of instruction or guidance. We were supposed to be learning how to code,but played Oregon Trail instead.
-
I'm a responsable grown up! *uses a can of glitter hairspray on hair* much adult. Such wow.
Now I'm leaving behind a trail of fabulous. No regrets.
Pfft and my mum keeps on asking when I'm going to have kids...23 -
Having a healthy body is good. I go trail running on the weekends usually 1200+ above Sea Level.
On weekdays I just go home and play video games or watch TV. On Friday nights, party with friends in the city. 4
4 -
#include <rant>
Using angry standard;
Int main()
{
cout << "So my mom recently started "exploring the web". I'm sure you already know where this is going; she ended up signing up for a free trail of some diet pills with her credit card on some sketchy website. The website never sent any product but attempted to charge her card over $300 multiple times. My mom's bank noticed and froze the account. She has now opened an investigation with the banks fraud department and is awaiting response. I took the liberty of running a whois look up and found the companies website is held by GoDaddy and is hiding behind Domains by Proxy (GoDaddy's sysadmin hider). I'm angry that she's in this situation but I have no idea of how to uncover the real company behind the diet pills site." << endl;
Return 0;
}2 -
!rant
Is anyone familiar with source trail?
https://www.sourcetrail.com/
Wanted to get some info before I drop it into a legacy code base 🤭1 -
People don't seem to know how to properly do print-debugging, so here's a simple guide:
1. A log of "aaaaaa" or "got here" isn't as helpful as you think when ALL OF THEM ARE THE FUCKING SAME. You put a descriptive label or copy verbatim the conditional statement. This saves time matching statements, allows one to watch multiple branches at once, and allows others to understand and help faster when dragged in to help.
2. When trying to see where code fucks up, before each line, paste said line into a proper print statement for your language. If there's, say, a function call or some shit, have it output something like "functionCall(varA=<varA contents>,varB=<varB contents);" Most normal lines should be like this too, but it's especially helpful for calls and comparisons.
If need be, add return values after if they're not shown in another print statement later.
This allows for a trail of execution AND the line that fucks up will be the last in the log, making finding it easier when dealing with hangs and such.
3. Putting something unique like "DEBUG: " or something in front of all statements ensures you can just search for them to ensure you're not rolling one out to production. It also separates debug output from normal output at a glance, making digging through logs faster.16 -
I have been a software engineer for about 14 years now, in the beginning, I thought to be smart meant writing methods that do everything and more. however as I matured in the industry, I learned. keep it simple. 1 method 1 responsibility. One should trail my code and never have to find themselves where they were before in the journey. a journey should have one purpose and not pivot (context disclaimer here) as it goes. good programming is simple programming, its a story not a case of multiple endings.3
-
Serously I just recoverd from being overworked and senior developers are complaining to me that their code does not work???
DUDE just read the fucking error and start googling!
How the fuck do you think I learned software development?
It's a fucking matter of trail 'n error!2 -
Whyyyyyyy do people go back on their word and stab you in the back just to make themselves look better?
Mate, I’ve got a paper trail of your request, detailing EXACTLY what you asked for. Don’t make me use it against you to prove you’re wrong and I’m right... guess I better start collecting emails to use as self defence 😩😔3 -
Why is it so hard for people (especially managers) to learn to work smarter not harder....
FIX THE GODDAMN PROBLEM CORRECTLY... THE FIRST TIME SO WE DON'T HAVE TO KEEP FIXING ITS BLOWUPS ON WEEKENDS....
AND STOP HIRING MONKEYS THAT JUST KNOW TO PRESS BUTTONS RATHER THAN DESIGNING FULLY FUNCTIONAL SOLUTIONS THAT DON'T BLOW UP OR LEAVE A TRAIL OF SHIT BEHIND THAT I NEED TO DECIPHER N CLEANUP....2 -
Please don't mutter your ideas on calls or trail it off mid sentence to mouse level's of sound 🐁.
It's so awkward having to ask what you've said every few moments.
*Especially* if we work together all day all week
N.B. speakers on max volume + auto-captions are already on so I can piece together what you said.
Conversations are so difficult otherwise
That is all3 -
"Do not go where the path may lead, go instead where there is no path and leave a trail." - Ralph Waldo Emerson4
-
In my Inbox, a mail trail with 3 people who concluded: "This is not working properly"
Me: "Looks like a config issue..."
Someone else: "Hey we've now checked the config, it looks fine"
Me: /goes and looks
Me: "But the required line is commented-out..." -
We had 1 Android app to be developed for charity org for data collection for ground water level increase competition among villages.
Initial scope was very small & feasible. Around 10 forms with 3-4 fields in each to be developed in 2 months (1 for dev, 1 for testing). There was a prod version which had similar forms with no validations etc.
We had received prod source, which was total junk. No KT was given.
In existing source, spelling mistakes were there in the era of spell/grammar checking tools.
There were rural names of classes, variables in regional language in English letters & that regional language is somewhat known to some developers but even they don't know those rural names' meanings. This costed us at great length in visualizing data flow between entities. Even Google translate wasn't reliable for this language due to low Internet penetration in that language region.
OOP wasn't followed, so at 10 places exact same code exists. If error or bug needed to be fixed it had to be fixed at all those 10 places.
No foreign key relationships was there in database while actually there were logical relations among different entites.
No created, updated timestamps in records at app side to have audit trail.
Small part of that existing source was quite good with Fragments, MVP etc. while other part was ancient Activities with business logic.
We have to support Android 4.0 to 9.0 of many screen sizes & resolutions without any target devices issued to us by the client.
Then Corona lockdown happened & during that suddenly client side professionals became over efficient.
Client started adding requirements like very complex validation which has inter-entity dependencies. Then they started filing bugs from prod version on us.
Let's come to the developers' expertise,
2 developers with 8+ years of experience & they're not knowing how to resolve conflicts in git merge which were created by them only due to not following git best practice for coding like only appending new implementation in existing classes for easy auto merge etc.
They are thinking like handling click events is called development.
They don't want to think about OOP, well structured code. They don't want to re-use code mostly & when they copy paste, they think it's called re-use.
They wanted to follow old school Java development in memory scarce Android app life cycle in end user phone. They don't understand memory leaks, even though it's pin pointed by memory leak detection tools (Leak canary etc.).
Now 3.5 months are over, that competition was called off for this year due to Corona & development is still ongoing.
We are nowhere close to completion even for initial internal QA round.
On top of this, nothing is billable so it's like financial suicide.
Remember whatever said here is only 10% of what is faced.
- An Engineering lead in a half billion dollar company.4 -
Started using a password manager. Never thought life would be so easier.
Btw, I'm using Lastpass (on free trail now). Any better recommendations, friends?14 -
- Hey, I need to do X and I need your department to do it.
- "We can't do X, this is against company policy!"
- Oh, sorry, I didn't know. But I will have to justify it to my boss, can you point me to where in the policy it says you can't do X?
- "No I can't, it won't be there. It is just common sense"
- Wait, what? You saying you can't do something because it is against the company policy even though there is no restriction against it in company policy?!
- "Other companies don't do it either"
- I will need you to say that in writing, I need to explain it to my boss.
- "Our email server is FUBAR"
- It can be hand-written
- "I can't give a declaration in name of my department!"
- Wait, so you can interpret company policy any way you want, make decisions regardless of what the policy actually says but you can't own up to it in writing?!?
- "..."
- ...
(Some context: I've been emailing them about X for more than a week. Just got crickets for a response. Not even an evasive coward response, just no answer at all. And calling them leaves no paper trail. Fucking oxygen thiefs)
For fuck sake, are non-tech departments always filled with complete morons?!? Does anyone have ever worked with smart, or at least minimally-coherent non-tech people?!?!
Seriously, does anyone there have some story about some non-stupid non-tech/analog/muggle coworker?!?
I'm inclined to think that anyone who can think systematically is either working in tech or not working at all.6 -
Burned out but trapped at work for next 4-6 weeks - need survival tips
I'm 31y/o software dev and I'm completely fried and need advice on how to hang on until I can quit.
After 5 months job hunting, I landed a role that turned into a nightmare. 6 months of being bounced between different teams/scopes/projects with impossible deadlines and covering for incompetent managers/colleagues has left me burned out. Problem is, I'm finalizing a mortgage and can't quit or take sick leave without messing up income verification stage. Need to survive 4-6 more weeks.
Work is toxic and unpredictable - not enough resources given, blaming, shifting priorities, undefined tasks, endless meetings. Fake sense of urgency. Never feeling a sense of completion - there is always something extra that comes up. Documenting everything to have paper trail in case shit hits the fan, but honestly it feels like I'm at war daily and it's exhausting. I'm weeks behind on everything.
I have ADHD and my usual meds (18mg Concerta/10-20mg Lisdexamphetamine of Adixemin brand) aren't working anymore. Im able to fall asleep only after taking 0.2-0.3mg of Xanax or smoking some THC/CBD flowers. Constant brain fog, shot memory, never feel rested. Maybe 2-3 productive hours max daily before I become useless - either depressed or too wired and too anxious to function.
Already tried bunch of supplements (all possible forms magnesium, vitamin D, fish oil, my supplements drawer has like 60 different bottles), cleaned up diet, cut dairy/nicotine/alcohol/caffeine, taking strategic vacation days here and there in beginning or ending of a week.
I also suspected some allergies, tried out quercetine + vitamin c + all possible anti allergy meds - didnt help. I even suspected inflammation - tried curcumin and all other stuff - useless.
Anyone dealt with extreme burnout while trapped in a job? How do you function when your tank is empty but quitting isn't an option?
Only thing that helps is that I work fully remotely. Exercise would help but I cant force myself to do it.
Once the mortgage closes, I'm gone. Get a less stressful job lined up. Just need to survive until then without falling apart completely.13 -
Who the fuck thought putting a motherfucking portable AC that is almost half my weight and that has rotating wheels on the bottom onto a fucking flimsy piece of angled cardboard was a fucking good idea?!!
That fukken thing drove over my toe, ripped several layers of skin off and sliced into it at the same time... I just couldn't open my mouth for probably 5 minutes because I would just be shouting and swearing like crazy... There was a trail of blood behind me as I somehow made my way to a first aid kit... I'm considering going to the hospital to get it checked but I thankfully managed to stop the bleeding with bandages....
Fucking hell....4 -
Google: "shader particle trail effect"
Click the YouTube link
4 hours later... I've seen all the "gold digger prank" videos.
Disaster! -
Googling how to electromagnetically shield a espruino project from neodymium magnets over lunch, and that leads on a trail of manipulating and directing em fields...
"What are you doing? That doesn't look anything like a binary tree structure in Java... What the hell is all that?"
"Uhm... Personal research?" -
"Warning: Functions are not valid as a React child. This may happen if you return a Component instead of <Component /> from render. Or maybe you meant to call this function rather than return it."
WHERE. TELL ME WHERE THE FUCK THE PROBLEM IS HAPPENING. OR SHUT THE FUCK UP.3 -
Code for Matrix Rain Using HTML
<!DOCTYPE html>
<html>
<head>
<title>Matrix Rain</title>
<style>
* {margin: 0; padding: 0;}
body {background: black;}
canvas {display: block;}
</style>
</head>
<body>
<canvas id="c"></canvas>
</body>
<script>
var c = document.getElementById("c");
var ctx = c.getContext("2d");
//making the canvas full screen
c.height = window.innerHeight;
c.width = window.innerWidth;
//english characters
var english = "1001010101110101010101010010101000101011101111010101010110101010101010101110000101";
//converting the string into an array of single characters
english = english.split("");
var font_size = 15;
var columns = c.width/font_size; //number of columns for the rain
//an array of drops - one per column
var drops = [];
//x below is the x coordinate
//1 = y co-ordinate of the drop(same for every drop initially)
for(var x = 0; x < columns; x++)
drops[x] = 1;
//drawing the characters
function draw()
{
//Black BG for the canvas
//translucent BG to show trail
ctx.fillStyle = "rgba(0, 0, 0, 0.05)";
ctx.fillRect(0, 0, c.width, c.height);
ctx.fillStyle = "#0F0"; //green text
ctx.font = font_size + "px arial";
//looping over drops
for(var i = 0; i < drops.length; i++)
{
//a random chinese character to print
var text = english[Math.floor(Math.random()*english.length)];
//x = i*font_size, y = value of drops[i]*font_size
ctx.fillText(text, i*font_size, drops[i]*font_size);
//sending the drop back to the top randomly after it has crossed the screen
//adding a randomness to the reset to make the drops scattered on the Y axis
if(drops[i]*font_size > c.height && Math.random() > 0.975)
drops[i] = 0;
//incrementing Y coordinate
drops[i]++;
}
}
setInterval(draw, 33);
</script>
<body>
</html>1 -
I've been using dotnet and aspnetcore for years. I've heard people complain about MVC but I never really saw the problem. The controllers are easy to set up for basic endpoints, I have my domain models and DTOs, and our views I guess is our standalone webpage just consuming jsons.
Only now I'm having to work with an *actual* aspnet MVC stack - server-rendered cshtml and all - and it's dawning on me like a truck what people were actually referring to.
Out of all the issues I've had so far, they have all been due to black box enigmatic voodoo because don't worry about it, the framework takes care of it - it should just work. But what if it doesn't? I have no idea because the trail ends at the bit that should just work.
I should know better than to criticize an entire framework and paradigm made by devs with vastly superior experience and expertise than me, and my issues are absolutely due to being new and unfamiliar with this, but imagine coming up with an architecture to obsessively separate the MVC concerns, then you make cshtml.2 -
As I settled into my armchair with a steaming cup of tea, I thought back to the time I almost lost my heart—and a small fortune—to a smooth-talking scam artist. It all began innocently enough when I joined a dating site after my children encouraged me to put myself out there again. That’s when I met David. With his charming smile and heartfelt messages, he made me feel seen and cherished. We talked for hours about everything—from our favorite books to our dreams of traveling the world. I felt like a teenager again, butterflies in my stomach as we planned our future together.
But soon, the conversation took a troubling turn. David claimed he was stuck overseas due to a sudden medical emergency and needed money to pay for treatment. My heart ached for him, and against my better judgment, I sent him several wire transfers, believing I was helping the love of my life. Weeks passed, and suddenly, the sweet messages turned into silence. It dawned on me that I had been scammed. Just as I was drowning in despair, I heard about a group called Specter Lynx. I reached out, sharing my story with them. They sprang into action, tracking down David’s digital trail and uncovering the web of deceit. With their help, I was able to recover a significant portion of my lost funds. Now, I not only have my money back, but I also have a newfound appreciation for caution—and the strength of community. I often share my story, reminding others that love online can be a double-edged sword, but with a little vigilance, you can find your way back.2 -
I decided to run the ROCKYOU password list to see if there are any patterns in md5 hashing, not sure why but I am starting to confuse myself and I need a new pair of eyes to have a look.
in advance, sorry for the shitty image, that lappy is a temporary solution.
So the very accurate and not bias numbers show that the letter "0" appears more than the rest, would there be any use in let's say ordering the wordlist with words that have the most "0" and "7" in their hash to appear at the top?
I believe I might be trying to stretch the numbers and see a pattern where there is none but its worth a shot I think.
Note:
- These numbers come from only about ~14m words
My thinking trail is that if statisticaly these hashes are more likely to appear, they are more likely to be the one I am looking for? 3
3 -
Never thought I'd be back here after all these years. But today I thought I would rant about our product owner, who thinks he's priceless to the project. The man walks out of meetings that don't go in his preferred direction. He gets flustered whenever discussions become technical and demands everyone ELI5 the entire thing to him. He clears his throat loudly every time he wants to make himself noticed, like loud grunts of a wild boar. He will find ways to shift blame away and onto others. He does not like being recorded during meetings and does his best to make sure his decisions don't have a paper trail in case they go sour. No paper trail also means he can contradict himself everyday ans get away with it. I wish there was a way to make him resign or switch to a different project. Other managers and even his bosses are already aware of his behavior and yet still no significant changes in his actions or behavior.
-
Spend half a day trying to make sound work on my antergos install, after multiple image builds, kernel jumping, reinstalling alsa, realized that people working on making cherry trail laptops sound work - stopped working on it since like april 2017 and new kernels have simply no patch to make it work, great.. debian docs mention that you should be able to use an external soundcard atleast, but the whole alsa and pulseaudio shit doesn't make that easy at all.. atleast the battery time with arch+powertop+tlp is almost the same as what I would get with windows out of it1
-
In this project I’m working on, designers want to decrease their amount of work by blaming technical constraints.
The supposed “technical constraints” actually do not exist, as the stakeholders did tell me in the beginning “make sure that these issues do not exist within the selected solution”.
Now, I don’t have a single problem with them making their lives (and by consequence mine) easier by decreasing the scope of work, but I have said at least 2-3 times by now that there are no technical constraints, and started to do some paperwork trail that I did say that and when.
Not looking forward to see how all of this will turn out, but hoping that for once I am covering my back enough.3 -
Had a fun adventure this morning. Had to deliver some bags to some houses. Entered the addresses in Google Maps. Off we go. First house, no problem. Second house, and Google is taking me on a weird route, through some parking lots and stuff. Finally, it wants me to turn onto a bike trail. WTF? My Google maps is set for bike routes. Went a lot faster when I set it to car. No wonder there were so many bikes and the road seemed so narrow.1
-
Ahoy der Ranters!
I'm looking for a log management service. My server application has a 90 days rolling policy (with gzip) but I would like to store logs somewhere else before they get deleted (after 90 days).
I've heard of Cloud watch, paper trail, and logz.io
What would you recommend?5 -
Which one better Amazon AWS or Google cloud console?
I noticed AWS more difficult than Google cloud!
Google cloud give free trail for 90 days which is nice than AWS!7 -
Dependencies suck.
I wanted a ruby gem and needed an older version of ruby to run it. Fine, what's the best way to get multiple ruby versions on one system, apparently rvm.
Now I want rvm.
I can't have rvm without getting gnupg first though.
Before I can get gnupg I need brew.
Now I have brew setting my computer on fire compiling god knows what so it can get gnupg so I can get rvm so I can get the ruby version I want to get the gem I want!
It's been running for quite a while...
This isn't the first or last time that the convenience of packages and versions leads to a maze like trail of prerequisites you need to follow.
I'm sure there's some tool that would've helped with my problem, but the problem shouldn't be this bad to begin with!
I understand why it happens but it still sucks and it's a lot of wasted time.
Frankly I'm expecting some people will have gotten so used to this kind of insanity that they won't get why I'm renting about it, oh well, it made me feel better and gave me something to do while brew is melting my machine.3 -
Ever wondered how Elon himself talked about not messing with AI in the past. I vaugely remember this was when there was a clash between Mark and Elon. And now Elon's companies OpenAI and Neuralink working on advanced tech. The same tech he told everyone to not mess with.
I haven't followed the trail of events clearly. But now this thought comes to my mind.
Anyone thinks the same? Or am I missing something?16 -
Today I tried running Plasma Wayland again after a few months...well...I tried
What did I experience?
- Mouse cursor size jumping from small to big randomly
- Can't remember fucking window positioning between multiple workspaces, so when I reboot, all windows are in the last workspace
- Random freezes with external monitor plugged in
- Firefox scrolling is absolutely terrible, 5 fps at most, but only when external monitor is connected
- Mouse acceleration can't be completely turned off? Or the setting just didn't work? IDK
- Sometime I get the infamous window trail effect known from older Windows versions, but on mouse cursor3 -
So I was wandering around Lithuania during a time period when the freaks were playing nice. Took some pictures of hot chocolate or coffee can't remember long time ago and some photos of a nice snow covered trail and added some Cyrillic what a nice vacation
True story
This is in Russia immediately after my trip to Lithuania
The people were certainly not twisted freaks who were acting nice for once and leaving me alone instead of acting like fucked up chomo captors. A word I never use but I've been inspired by hearing it over and over
I like it here
There are Tons of people I get along with who have the same interests 11
11 -
The most comprehensive software is powered by spaghetti code. I've just realised that if it's old/matured, it was almost nearly impossible for the code to be coherent or neat. No design patterns. A lengthy trail of ACLs and conditionals reading from a util/helper static method that would make javaScript callback hell's head spin and green with envy
These massive, ready-made software overbloated with features plastered in seem built in a hurry to churn out functionality to make stakeholder and client happy in the shortest amount of time. The authors are hailed as 10x devs. But to you, the maintainer, they are Tetanus that make you crave to rip your eyes out of their sockets1 -
There needs to be a game called along the lines of "how to be a better employee" so if someone so happens to see my browser history dosent see a trail of No mans sky links.
-
Trail and error... So many errors.
Also watching videos to learn how code fits together, as well as looking for other people's example code to reverse engineer it, modify it to see what changed. -
Got fed up with my newcomer PO's bullshit planning and constant gaslighting whenever deadlines get missed.
Made a spreadsheet showing our actual capacity vs his unrealistic expectations - turns out all of Q3 work is spilling into Q4, so I'll be spending October finishing July/August/September tasks.
Brought this up multiple times asking for more time or resources. Got denied and blamed instead.
It got really bad to the point where I had to start doing his work for him - make business decisions, create tickets, define acceptance criteria, requirements and etc. Just so I would have some paper trail so that I wouldnt get blamed again in case I'm missing some undefined requirement. Finally couldn't take it anymore and escalated to my dev lead.
Now the PO is getting absolutely chewed out. Feels fucking good to finally see him face consequences for their terrible planning.
On another note - is it a disease or do the most useless people just naturally gravitate toward management positions? For example, this guy is supposed to be a decision maker but answers almost every business question vaguely, ambiguously, or just straight up ignores it. How the fuck such people even exist, it just blows my mind.4 -
Learning a piece of software from an external supplier. The manual is thick like the bible. The examples fail without explanation. Trying to contact support just leads you down an endless trail of support articles. Damn right I get frustrated and bored. Can you blaim me for rather hanging around on devRant than desperately trying to work around problems in someone else's system/documentation? Yeah, I have to pull my shit together, but they have to pull theirs first.
-
Any strong opinions on giving resignation notice via email? I've previously given notice in person during a 1 on 1 conversation, but I had good relationships with my managers. I work at a larger company now where I feel like the paper trail could be valuable, and I don't have a very warm and fuzzy relationship with my manager. I feel kind of sleazy just sending an email, but asking for an out of the blue zoom meeting just feels weirder somehow than tapping them on the shoulder for a quick chat.1
-
I'm thinking about using my rep to post a collab for a open source low powered (low powered if possible) motion trail cam app.
Only I have zero android experience (I am a nodejs/meteor/javascript dev by trade).
Shall I go for it and rely on others experience? or go for something nodejs based?5 -
I'm making a booklet of some handy notes. So, the old trick is print in pages of 4, to make binding easier. I spool about 60 of those and then it starts printing in my manual duplex until
*a wild blank line has been spotted*
`wat?`
I go back and see that I've not noticed a trail of white blanks that had been slowly creepily increasing in the print space where the text should be. Almost 20 of my pages are wasted. I take out the print cartridge and wipe the drum, run the cleaning sequence on a clean sheet and try to print.
Presto! good as new!
Sippin some coffee, browsing the web.. oh and woah! The blank reappears and it is now bigger. The previous 12 pages are not affected? wth
I do this whole thing again. Wipe and print. It works. And along the lines of 15 or so prints, the blank appears again, bigger and bolder. wth. I really need those prints now.
If it was broken, I'd have fixed it in the afternoon, but it is evening now. No one opens at this hour. Why is y printer fucking with me? -
Urghh
I swear web push notifications are the betaest most betty beta thing
Half of the time they don't work and misbehave without trail -
Help me as I raise fund for the animals while I run for the Cape of Good Hope SPCA in the Sanlam Cape Town peace Trail Run 22km.
https://www.givengain.com/ap/remej/ -
CRYPTO & USDT SCAM FOR FAKE INVESTMENT HIRE SPARTAN TECH GROUP RETRIEVAL FOR RECOVERY
I lost $375,000 worth of Bitcoin to a phishing scam disguised as a climate research grant. I'm someone deeply committed to sustainability, and I was eager to invest in what I believed was life-altering research to assist us in reducing our carbon footprint. The email itself seemed flawlessly professional, with sophisticated branding and plausible promises of scientific advancement. Inadvisably, I clicked on the link and inputted my wallet details, only to discover afterward that the entire project was a scam. My Bitcoin was siphoned into the digital ether, and I was left feeling cheated, both as an investor and as a person who had backed environmental progress. I later, in despair and anger, turned to social media for help. My enraged outburst was seen on Mastodon by a very well-respected sustainability advocate who advised me to reach out to SPARTAN TECH GROUP RETRIEVAL. They had seen the worst of cryptocurrency scams in our community and could vouch for their ability to track even the faintest blockchain trails. Desperate, I reached out to them on WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8 OR Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 . Their forensic blockchain unit treated my case with the priority of a high-level environmental investigation. They carefully sifted through transaction records, untangling the complex web of addresses the scammers had used to launder my funds. They followed up on every lead with relentless attention to detail, all while speaking in clear, jargon-free language that even an environmental activist could understand. It was 13 nail-biting days of round-the-clock work, but I eventually received the life-changing news: my funds had been recovered. My $375,000 was restored, bit by bit, as though the digital trail itself had come to return what once belonged to me. The relief was immeasurable. SPARTAN TECH GROUP RETRIEVAL had not only retrieved my stolen Bitcoin, but they had also restored my faith in the resilience of the crypto community. I restart my environmental activism today with renewed passion and a safe crypto wallet. I make every effort to spread my warning tale far and wide, begging fellow activists to scrutinize each email closely and be wary of offers that sound too good to be true. SPARTAN TECH GROUP RETRIEVAL not only recovered my Bitcoin, they saved my mission. And in a world where online trust can be so fragile, that is a victory worth celebrating.
More info about the company :
Email: spartan tech (@) cyber services . c o m OR support(@) spartan tech group retrieval. o r g
Website: h t t p s : / / spartan tech group retrieval . o r g 1
1 -
Several weeks ago, my life was irrevocably altered by a crypto romance scam a cruel amalgamation of emotional manipulation and financial exploitation. A person I believed to be my partner, whom I had met on a niche trading forum, gradually ensnared me into investing in a purportedly “groundbreaking” decentralized finance (DeFi) project. Over several months, they meticulously cultivated trust, shared fabricated returns, and even orchestrated video calls with supposed “developers” to lend credence to the scheme. By the time I discerned the truth, a staggering $215,000 of my life savings had evaporated into a labyrinth of blockchain addresses, and the individual I thought I knew had vanished without a trace. The betrayal was paralyzing; I felt not only financially devastated but emotionally shattered.As a small business owner, I am no stranger to risk, but this was a domain far beyond my comprehension. I promptly filed reports with the FTC, collaborated with cybersecurity experts, and spent countless sleepless nights poring over Etherscan, desperately attempting to trace the transactions. However, the scammers’ adept use of privacy coins and offshore exchanges rendered the trail elusive, dissipating like smoke. Each dead end deepened my despair and sense of helplessness.In the midst of this turmoil, I confided in a family friend about my harrowing ordeal. After hearing my story, he referred me to GRAYWARE TECH SERVICES . Initially skeptical but driven by desperation, I visited their website and was struck by their no-nonsense commitment to transparency. Unlike other firms that promised miraculous recoveries, GRAYWARE TECH SERVICES provided a clear,breakdown of their process: forensics, collaboration with international legal networks, and direct engagement with exchanges to freeze illicit funds.From the moment I reached out to GRAYWARE TECH SERVICES , their team approached my case faster . They meticulously analyzed my situation, keeping me informed at every stage of the recovery process. Ultimately, they succeeded in recovering my entire investment, restoring my financial stability and also rekindling my faith in the possibility of justice in the digital age. This experience has imparted invaluable lessons about vigilance and the importance of seeking help when navigating the dangerous currents of cryptocurrency. GRAYWARE TECH SERVICES has proven to be a beacon of hope for those ensnared in the web of crypto fraud, demonstrating that recovery is indeed possible with the right support and expertise.You can reach them on whatsapp +18582759508.2
-
CAN I GET MY LOST OR SCAMMED BITCOIN BACK? YES, MALICE CYBER RECOVERY WILL SOLVE ALL YOUR PROBLEM.
Hello my name is Mathias Dreyer and here is a brief story of what happened to me. I still remember the day I fell victim to a sophisticated cryptocurrency scam. I was convinced that I had lost my entire life savings - $400,000 - to a group of cunning thieves. I felt like I'd been punched in the gut, and I didn't know where to turn. The worst part was the feeling of helplessness that came with it. I thought I'd never see that money again. But then I stumbled upon MALICE CYBER RECOVERY, a team of experts who specialize in recovering stolen funds from online scams. I was skeptical at first, but something about their website and the testimonials from previous clients resonated with me. I decided to take a chance and reach out to them. From the moment I contacted MALICE CYBER RECOVERY, I knew I was in good hands. Their team was responsive, empathetic, and professional. They walked me through the entire process, explaining every step of the way and keeping me updated on their progress. What impressed me most was their expertise and determination. They worked tirelessly to track down the scammers, using their advanced tools and techniques to follow the digital trail. It wasn't an easy task, but they refused to give up. After weeks of intense effort, MALICE CYBER RECOVERY finally succeeded in recovering my entire stolen amount - $400,000! I was overjoyed, relieved, and grateful all at once. It was like a weight had been lifted off my shoulders. I can't recommend MALICE CYBER RECOVERY enough. They're the real deal, and I'm living proof of their effectiveness. If you've fallen victim to an online scam, don't lose hope. Reach out to MALICE CYBER RECOVERY, and let them work their magic. In fact, I was so impressed with their service that I've referred several friends and family members who've also fallen victim to online scams. And you know what? They've all had successful recoveries too! MALICE CYBER RECOVERY is more than just a company - they're a beacon of hope for those who've been wronged by online scammers. They're the heroes we need in this digital age, and I'm honored to have had the pleasure of working with them. So, if you're reading this and you're in a similar predicament, don't hesitate. Reach out to MALICE CYBER RECOVERY today, and let them help you recover what's rightfully yours. 2
2 -
WHICH CRYPTO RECOVERY COMPANY IS LEGIT: HIRE FUNDS RECLIAMER COMPANY
As an architect, every design I create is a mark of trust, trust in materials, trust in my team, and trust in the earth beneath our feet. But nothing could have readied me for the collapse I experienced when that trust was broken from within. I had laboriously built up a $400,000 Bitcoin hoard over several years, a monetary safety net for my business to weather financial tempests and fund future projects. I entrusted its defense to a long-time business partner, a man who I once considered my right arm. That trust fell apart when he betrayed me. It started subtly. I noticed minor discrepancies, delayed logins, emails not returned. Then one morning, I was locked out altogether. He was gone. The phones weren't answered, his office cleared overnight, and my heart pounded in alarm. The electronic safe haven of our hard-won savings was now a fortress without a key, hostage to a ghost. Rage and panic warred within me. I envisioned telling my employees that our future was doubtful because I had trusted the wrong person. Sleepless nights were spent searching the web for miracles. That was when, at an architectural design expo in Milan, I overheard two colleagues discussing FUNDS RECLIAMER COMPANY. Their stories of miraculous crypto recoveries caught my attention like a ray of light piercing a room darkened by shadows. With nothing to lose, I reached out to FUNDS RECLIAMER COMPANY. Their staff handled my case from the very first consultation with the same discretion and precision that I bring to my own cases. They did not handle my case like a transaction but like a delicate form that had to be painstakingly restored. Their cybersecurity experts meticulously tracked my partner's digital footprints, unraveling his complex attempt to hide his trail. Through cutting-edge blockchain tracing and legal action, they slowly dismantled his blockade. I was updated daily, step by step, like progress reports on a skyscraper rising from the earth. Fifteen tense days later, the call came. They had succeeded. The money was back in our firm's possession, intact and secure. Relief washed over me like the unveiling of a completed work of art. FUNDS RECLIAMER COMPANY not only got back money; they got back my hope. They made me realize that even when trust is lost, there are still able hands ready to rebuild. For that, I will forever be grateful.
WhatsApp:+13612504110 1
1 -
WHITE HAT HACKERS FOR DIGITAL ASSETS RETRIVAL- HIRE FUNDS RETRIEVER ENGINEER
When my sister Sarah first came to me, I could see the worry on her face. She had just been scammed out of $20,000 in a cryptocurrency investment, and I could feel her frustration. Sarah had seen a deepfake video of a famous entrepreneur promoting a new token, and everything about it seemed legitimate. The entrepreneur’s face, voice, even the background looked so real that she thought it was a solid opportunity. Without second-guessing, she invested $20,000 in the token. But things quickly took a turn for the worse. Soon after she made the investment, the developers of the project disappeared, and the value of the token crashed to zero. Sarah was devastated, feeling completely lost and unsure of what to do next. It was a tough situation, but I knew exactly where to turn FUNDS RETRIEVER ENGINEER . I had been through a similar experience myself not too long ago. After being scammed in another crypto investment, I was fortunate enough to find FUNDS RETRIEVER ENGINEER . Their blockchain forensics team helped me recover a significant portion of my funds, and I knew they could help Sarah too. I explained my experience to her and reassured her that there was still hope. Sarah immediately contacted FUNDS RETRIEVER ENGINEER , and their team went to work right away. They used their advanced blockchain forensics tools to trace the scammer’s wallet addresses. With their expertise, they were able to identify the scammer’s movements and follow the trail of stolen funds. Then, they took it a step further by pressuring the cryptocurrency exchanges to freeze the scammer’s accounts and work with them to recover as much of the stolen money as possible. Within a short period, FUNDS RETRIEVER ENGINEER had successfully recovered $15,000 of Sarah’s lost funds nearly 75% of what she had invested. The process was smooth, and we were both amazed at how quickly they managed to track down the scammer's wallets and get the money back. We are incredibly grateful for FUNDS RETRIEVER ENGINEER and their team. After seeing how they helped me and now Sarah, we both know how crucial it is to have experts on your side when it comes to recovering funds from scams like these. If you ever find yourself in a similar situation, I highly recommend reaching out to FUNDS RETRIEVER ENGINEER they truly make the impossible possible.1 -
CRYPTO FRAUD RECOVERY: RECLAIM YOUR STOLEN CRYPTO WITH RAPID DIGITAL RECOVERY EXPERTISE
I was drawn into the world of cryptocurrency by a fake broker who promised astonishing returns on my investments in 2025. Their advertisement was polished, the website appeared legitimate, and the broker's pitch was incredibly persuasive. Before I realized what was happening, I had invested a staggering $870,000 USDC into what I believed was a high-yield opportunity only to find out it was an elaborate scam designed to defraud unsuspecting investors like me. The moment the truth hit me, my world came crashing down. I was engulfed in a haze of anger, regret, and despair, convinced that my life savings had vanished forever. I reported the scam to the authorities, but the trail seemed cold and my hopes dwindled. Just when I thought all was lost, a trusted colleague mentioned RAPID DIGITAL RECOVERY, a specialized crypto recovery team known for their impressive track record in helping victims of scams. With nothing left to lose, I decided to reach out to them... WhatSapp: +1 4 14 80 71 4 85 . Their response was immediate and reassuring. Unlike other so-called "recovery experts" who often demand upfront fees without delivering results, RAPID DIGITAL RECOVERY operated with complete transparency. They utilized advanced blockchain analysis techniques to trace my stolen funds, demonstrating a level of professionalism and dedication that I had not encountered before. Their team was relentless, meticulously navigating the complex web of transactions that had been used to siphon off my money. After what felt like an eternity of waiting, they successfully recovered every single dollar of my lost USDC. The relief I felt was indescribable; it was as if a heavy weight had been lifted off my shoulders. If you find yourself in a similar situation, having been scammed by a fake broker, a mining scheme, or a fraudulent exchange, don’t lose hope. RAPID DIGITAL RECOVERY is the real deal of professional, ethical, and highly skilled team that genuinely delivers results. Thanks to their expertise and commitment, I not only got my money back but also had my faith in the recovery process restored. Don’t let scammers win contact RAPID DIGITAL RECOVERY today and take back what’s rightfully yours, Your financial security is worth fighting for, and with the right help, you can reclaim what you’ve lost through RAPID DIGITAL RECOVERY expertise.....CONTACT THEM VIA:
Telegram Info: @Rapiddigitalrecovery1
Email Info: rapiddigitalrecovery(@)execs. com2 -
Recovering $27,700.50 Lost to Cryptocurrency Scam with LEE ULTIMATE HACKER Forensic Tools
Losing $27,700.50 to a cryptocurrency scam felt like my world crushed and the confusion that I felt at that moment was unbearable , I was finalizing what looked like a legitimate online purchase “ one time opportunity “ endorsed by polished testimonials and a credible looking platform. The website possessed glowing reviews and a timer countdown that persuaded users to act briskly , it felt genuine , complete with an SSL certification , a sleek interface and even a counterfeit customer service chat , I was fully convinced and made a transfer of my life savings , assured that I had made a rare investment plan, suddenly my funds vanished into the digital pit , the next thing I know the platform disappeared replaced by random error message , they ghosted me. The scammers left no trail to trace , I was distraught and in shock didn’t know what to do or where to start I had just lost my whole life savings in the hands of scammers , I sought refuge in a friend who advised me to share my story on socials ,exposing the scams mechanics the false urgency , the cloned platforms I felt so damn but the response I got under my story was astonishing I wasn’t alone many had been scammed and fell victim to fake websites , I picked several messages that stood out : Contact LEE-ULTIMATE HACKER through telegram: LEEULTIMATE or wh@tsapp +1 (715) 314 - 9248, they are a legitimate recovery company their website was clinical yet reassuring promising recovery with no upfront fees. I submitted my information skeptical of maybe engaging myself in yet another scam , but on the contrary they actually made contact within hours , and explained they’ll follow the money through layered wallets , they further explained scammers bounce crypto through dummy accounts , but patterns will emerge and that was the lead they use to initiate recovery .The process was laborious LEE ULTIMATE HACKER collaborated with offshore exchanges ,using forensic tools to map transaction trails , they linked my case to a notorious syndicate that has scanned hundreds of people , after three weeks thorough follow up a notification beeped $27,700.50 reappeared plus $750 from a frozen scammer fund , the relief that ran through my veins was unexplainable , I was so grateful to LEE ULTIMATE HACKER and team for their top of class expertise in recovery.2 -
CALL OR VISIT TECH CYBER FORCE RECOVERY ON WhatsApp
+15617263697 Or Telegram +15617263697
Several weeks ago, my life was irrevocably altered by a crypto romance scam, a cruel amalgamation of emotional manipulation and financial exploitation. A person I believed to be my partner, whom I had met on a niche trading forum, gradually ensnared me into investing in a purportedly “groundbreaking” decentralized finance (DeFi) project. Over several months, they meticulously cultivated trust, shared fabricated returns, and even orchestrated video calls with supposed “developers” to lend credence to the scheme. By the time I discerned the truth, a staggering $215,000 of my life savings had evaporated into a labyrinth of blockchain addresses, and the individual I thought I knew had vanished without a trace. The betrayal was paralyzing; I felt not only financially devastated but emotionally shattered. As a small business owner, I am no stranger to risk, but this was a domain far beyond my comprehension. I promptly filed reports with the FTC, collaborated with cybersecurity experts, and spent countless sleepless nights poring over Etherscan, desperately attempting to trace the transactions. However, the scammers’ adept use of privacy coins and offshore exchanges rendered the trail elusive, dissipating like smoke. Each dead end deepened my despair and sense of helplessness. Amid this turmoil, I confided in a family friend about my harrowing ordeal. After hearing my story, he referred me to Tech Cyber Force Recovery. Initially skeptical but driven by desperation, I visited their website and was struck by their no-nonsense commitment to transparency. Unlike other firms that promised miraculous recoveries, Tech Cyber Force Recovery provided a clear breakdown of their process: forensics, collaboration with international legal networks, and direct engagement with exchanges to freeze illicit funds. When I contacted Tech Cyber Force Recovery, their team approached my case faster. They meticulously analyzed my situation, keeping me informed at every stage of the recovery process. Ultimately, they succeeded in recovering my entire investment, restoring my financial stability, and rekindling my faith in the possibility of justice in the digital age. This experience has imparted invaluable lessons about vigilance and the importance of seeking help when navigating the dangerous currents of cryptocurrency. Tech Cyber Force Recovery has proven to be a beacon of hope for those ensnared in the web of crypto fraud, demonstrating that recovery is indeed possible with the right support and expertise.2 -
TRUSTED EXPERTS IN BITCOIN, USDT & ETH RECOVERY SERVICE : HIRE RAPID DIGITAL RECOVERY
After reading numerous testimonials about how RAPID DIGITAL RECOVERY has successfully assisted individuals in recovering money and cryptocurrencies lost to scammers, I decided to reach out for help with my own situation. In February 2025, I fell victim to a scam and lost a significant amount of USDT. Feeling hopeless and overwhelmed, I turned to RAPID DIGITAL RECOVERY, hoping they could work their magic and help me reclaim my lost funds. To my astonishment, the team at RAPID DIGITAL RECOVERY was incredibly efficient and professional from the very beginning. They quickly got to work, employing advanced tracking techniques to trace my lost USDT. Within a short period, they were able to identify the initial wallet where my funds had been sent and followed the trail through various wallets to which the funds had been transferred. It was impressive to see how they navigated the complex web of transactions with such expertise and precision. What truly amazed me was their ability to not only trace the funds but also to recover them. They managed to move the USDT out of the wallets where it had been sent and successfully returned it to my original wallet. As if that wasn’t enough, they even added extra funds as a gesture of goodwill, which felt nothing short of miraculous. This unexpected bonus was a delightful surprise and made the entire experience even more rewarding. The entire process with RAPID DIGITAL RECOVERY was seamless and reassuring. Their dedication to helping clients recover lost assets is commendable, and their expertise in navigating the often murky waters of cryptocurrency transactions is unparalleled. They kept me informed throughout the process, providing updates and answering any questions I had, which helped alleviate my anxiety. I am incredibly grateful for their assistance and can confidently say that they turned a dire situation into a positive outcome. If you find yourself in a similar predicament, I highly recommend reaching out to RAPID DIGITAL RECOVERY. Their services truly feel like magic, and they have restored my faith in the possibility of recovering lost funds. With their help, I was able to regain my lost assets and my peace of mind.
REACH OUT TO RAPID DIGITAL RECOVERY VIA:
Whatsapp: +1 4 14 80 71 4 85
Telegram: @ Rapid digital recovery1
Email: rapid digital recovery (@) execs. com2 -
RECOVER MONEY LOST TO FAKE ONLINE SCAMMERS HIRE FUNDS RECLAIMER COMPANY
The cryptocurrency space, with its dizzying promises of financial freedom, had always intrigued me until it became the stage for my deepest disillusionment. Last year, I fell victim to an elaborate crypto scam that stripped me of years’ worth of savings. What began as a confident investment in a "guaranteed returns" scheme unraveled into a nightmare. Overnight, my portfolio vanished, along with the anonymous fraudsters who orchestrated the ploy. The aftermath was a toxic blend of anger, shame, and helplessness. I questioned every decision, replaying red flags I’d naively ignored. Crypto forums offered little solace, filled with eerily similar stories of irreversible losses. Just as I resigned myself to defeat, a glimmer of hope emerged: FUNDS RECLIAMER COMPANY. From the outset, their team stood apart by blending technical precision with unwavering compassion. Rather than treating my case as a faceless ticket, they approached it with a commitment to understanding the human toll of the scam. During initial consultations, they listened patiently to my story, offering reassurance that shifted my mindset from despair to cautious optimism. “These scams thrive on exploiting trust, not incompetence,” one advisor emphasized a perspective that dissolved my self-blame. FUNDS RECLIAMER COMPANY’s mastery of Cryptocurrencies forensics became evident as they untangled the digital maze of my stolen assets. They decoded how fraudsters manipulated wallet vulnerabilities and decentralized exchanges to obscure the trail, leveraging proprietary tools and cross platform collaborations to trace the funds. Over three days, their transparency became my anchor. Regular updates demystified their process, flagging suspicious transactions, and piecing together patterns linked to earlier scams. Challenges arose dead-end leads, unresponsive third parties but the team navigated each obstacle with tenacity. By second day, they’d recovered $350,000 of my assets. Beyond recovery, FUNDS RECLIAMER COMPANY prioritized empowerment. They equipped me with resources to safeguard future investments and connected me to a private forum of survivors, fostering a community of shared resilience. Today, I’m not only financially restored but fortified with hard-earned wisdom. My situation proves that loss isn’t always permanent. With cutting-edge expertise and relentless advocacy, redemption is attainable. Let my journey remind you: even in Cryptocurrency opaque wilderness, a path back exists and FUNDS RECLIAMER COMPANY lights the way.
FOR MORE INFO:
WhatsApp:+13612504110
Email: fundsreclaimercompany@ z o h o m a i l . c o m1 -
Bitcoin, the leading cryptocurrency, has revolutionized the financial landscape but has also attracted fraudulent schemes targeting unsuspecting investors. As the popularity of Bitcoin continues to soar, so do the risks associated with fraudulent investments. Bitcoin fraudulent investments refer to schemes where individuals deceive others into investing in fake or illegitimate projects promising high returns. These scams exploit the trust and lack of regulation in the cryptocurrency space, posing a significant risk to investors. Bitcoin fraudulent investments involve deceitful practices where scammers lure unsuspecting individuals to invest their money in schemes that do not exist or do not deliver on their promises. Such scams can range from Ponzi schemes to fake ICOs, preying on the desire for quick profits in the volatile world of cryptocurrencies. Victims of Bitcoin fraudulent investments not only suffer financial losses but also experience emotional distress and a loss of trust in the cryptocurrency market. Retrieving stolen bitcoin becomes a priority for these individuals to seek justice and recover their assets. Retrieving pilfered bitcoin is a daunting task due to the intricate nature of tracing and identifying stolen funds in the decentralized and pseudonymous blockchain network. Additionally, legal and jurisdictional hurdles further complicate the recovery process, making it challenging for victims to reclaim their stolen assets. The anonymous nature of Bitcoin transactions and the lack of a central authority make it difficult to trace and identify stolen funds. Scammers often use sophisticated methods to obfuscate the flow of stolen Bitcoin, leading to a complex trail that requires expertise to unravel. Bitcoin recovery efforts are hindered by legal and jurisdictional challenges, as scammers operate across borders and exploit loopholes in regulations. Reclaiming stolen bitcoin requires navigating through different legal systems and cooperating with authorities internationally, adding layers of complexity to the retrieval process. Recovering monies taken from victims of bitcoin scams is the area of expertise of reputable company REVENANT CYBER HACKER. When my Bitcoin wallet was hacked and the cyber thieves seemed to have vanished into thin air, REVENANT CYBER HACKER stepped in to crack the case wide open. Through their relentless pursuit and ingenious tactics, they were able to recover the stolen funds and restore faith in the security of cryptocurrency investments. It's a happy ending that proves that even in the Wild West of the crypto world, there are heroes like REVENANT CYBER HACKER fighting for justice. Contact REVENANT CYBER HACKER on: revenantcyberhacker {DOT} org
Email: revenantcyberhacker {AT} Gmail {dot} com
Telegram: revenantcyberhacker
WhatsApp: + 1 (208) 425-8584 WhatsApp: + 1 (913) 820-0739 1
1 -
How to recover bitcoin/cryptocurrency from scammers and fraudsters; HIRE CERTIFIED RECOVERY SERVICES
I never knew I would fall victim to a scam, especially not in the fast-paced world of cryptocurrency. When I came across an opportunity to appear on a crypto podcast, I was excited. The promise of exposure and the chance to connect with like-minded individuals in the crypto community seemed too good to pass up. The podcast appeared legitimate, complete with a professional website, glowing testimonials, and a polished social media presence. I felt confident that this was a step forward for my career. After some back-and-forth communication with the supposed host, I was convinced to pay $9,500 to secure my spot on the show. I imagined the doors this opportunity would open for me new connections, potential partnerships, and a boost in credibility. However, after I made the payment, everything changed. The communication I had enjoyed suddenly stopped. My emails went unanswered, and the podcast’s website vanished into thin air. I was left feeling devastated and foolish. In my desperation, I began searching for help and stumbled upon CERTIFIED RECOVERY SERVICES. I was skeptical at first, but I had nothing to lose. I reached out to them, and to my surprise, they took my case seriously. Their team of experts began investigating the scammer, employing advanced tracking techniques to uncover the digital trail left behind. I watched as they worked diligently, piecing together the puzzle of my lost funds. To my amazement, CERTIFIED RECOVERY SERVICES was able to trace the scammer and recover 95% of my money. The relief I felt was overwhelming. Not only did I regain most of my lost funds, but I also learned a valuable lesson about the importance of due diligence in the online space. This experience has made me more cautious and aware of the potential pitfalls in the cryptocurrency world. While I wish I had never fallen for the scam, I am grateful for the support I received from CERTIFIED RECOVERY SERVICES. Their expertise not only helped me recover my money but also empowered me to share my story. I hope that by speaking out, I can help others avoid the same fate and encourage them to be vigilant when navigating the exciting yet risky landscape of cryptocurrency.
Here's Their Info Below:
WhatsApp: (+1(740)258‑1417 ) 1
1 -
CONTACT A TRUSTED USDT & BTC RECOVERY SPECIALIST // REACH OUT TO FUNDS RECLAIMER COMPANY
I've been around enough drama to know it's practically my brand, thanks to Reality TV. But nothing could have prepared me for the ultimate plot twist: my own assistant stealing my Bitcoin. I mean, seriously? $900,000 worth of Bitcoin that was supposed to be as secure as a season finale cliffhanger, yet my assistant thought they'd rewrite the script and help themselves to a hefty "bonus" from me. The shock was surreal. One moment, I'd been checking on my portfolio and marveling at my financial gains; the next, it had vanished. And it wasn't just the amount of money taken that stung, either-it was the treachery: I had believed in this individual, had actually worked alongside them, and had now had everything taken from the wallet. Like a plot twist, this cut deep. I was so angry and couldn't believe all that when I did what any normal person would: reach out to FUNDS RECLIAMER COMPANY. Of course, I had my skepticism: could they really recover stolen Bitcoin? But when you're at your lowest, you have to take the leap. And, man, am I glad I did. FUNDS RECLIAMER COMPANY came through in ways I never expected. They didn't just track down my $900,000 in Bitcoin, but other shady transactions, too, and exposed a trail of deceit that was going on right under my nose. They were like digital detectives, putting together the mystery of my stolen funds. Their attention to detail was second to none, and their professionalism made all the difference. Weeks of painful yet relentless work later, the call came: FUNDS RECLIAMER COMPANY had recovered my funds and had even dug up proof of my assistant's shady dealings. I immediately fired them, and let's just say the whole saga made for some fantastic TV drama. The ratings shot up, and not only did I get my money back, but I also got to turn this betrayal into a viral episode. What did I learn? Never drop your guard, not even with the people you would think you can trust. And when disaster strikes digitally, there is only one team you'd want in your corner: FUNDS RECLIAMER COMPANY. They didn't just recover my Bitcoin; they made sure my financial plot had a happy ending.
WhatsApp:+13612504110 1
1 -
I Could Hardly Breathe! Months of tireless fundraising had finally come through for my small nonprofit, and we had $300,000 in Bitcoin to supply food, shelter, and medical aid to refugees fleeing war. That fund was hope, a future for families who had no other place to turn. It all fell apart in an instant. Our treasurer, a man I'd trusted like a brother, vanished overnight and took the entire fund with him. I was heartbroken. The weight of the people who were depending on us pressed against my chest. I could hardly breathe. I looked at my screen, powerless to do anything as the blockchain ledger confirmed my worst nightmare, the funds had been moved through a series of wallets, vanished into thin air.
Sleepless and remorseful, I consulted a crisis management expert in a desperate phone call. With the calm, panic-slashing tone of her voice, she spoke GRAYWARE TECH SERVICES . Her confidence was the sort that spoke of seen miracles. At that straw of hope, I grasped and called them immediately.
From that first call, GRAYWARE TECH SERVICES treated my case like those refugee lives were in their own hands. Their lead investigator explained their approach, tracing transactions through blockchains, monitoring wallet activity, and leveraging relationships with international exchanges. They explained it all in plain terms, never once making me feel dumb for my ignorance. They understood both the technical complexity and the human stakes.
There were daily progress reports. They followed the laundering path our treasurer had attempted, following the trail through the decentralized exchanges and privacy-focused mixers. Each breakthrough was like a heartbeat resuscitating a stilled chest. On the nineteenth day, they called with the words I had scarcely dared to hope: "We got it back."
I got down on my knees and wept. $300,000 was safely recovered to our nonprofit wallet. But GRAYWARE TECH SERVICES didn't hesitate. They guided us through implementing enhanced security measures, such as multi-signature wallets, cold storage solutions, and rigorous internal oversight. They even advised us on vetting future financial officers.
Our mission is stronger today than ever. Refugee families are still being assisted, and I sleep well knowing our funds are secure. GRAYWARE TECH SERVICES not only retrieved our Bitcoin, they restored my faith in resiliency and human kindness. 1
1 -
Cryptic Trace Technologies: The Legit Recovery Experts
Losing my Bitcoin to a scam was a nightmare I never thought I would experience. I had always been careful with my transactions, double-checking wallets and verifying sources, but the scammers were sophisticated. Within seconds, my cryptocurrency was gone, and I was left staring at my empty wallet, feeling powerless. I tried everything—contacting the exchange, reporting to authorities—but I was repeatedly told that crypto transactions were irreversible. Just when I was about to give up, I came across Cryptic Trace Technologies, a company specializing in crypto recovery. I had my doubts, but with nothing left to lose, I reached out to them. From the first interaction, Cryptic Trace Technologies proved they were different. Their team was incredibly professional, listening to every detail of my case and explaining exactly how they could help. They immediately got to work, analyzing blockchain records, tracking wallet movements, and identifying patterns that linked the scammers to known fraud networks. Their deep understanding of crypto transactions and forensic tracing techniques gave me confidence that I had finally found the right people for the job. For the first time since my funds were stolen, I felt a glimmer of hope. The process wasn’t easy, but the team at Cryptic Trace Technologies never wavered. They meticulously followed the stolen Bitcoin’s digital trail, even as the scammers attempted to hide their tracks through multiple wallets and exchanges. Their expertise in blockchain analysis and ethical hacking allowed them to pinpoint the exact location of my stolen funds. The moment they informed me that a significant portion of my Bitcoin was recoverable, I was overwhelmed with relief. Within days, they successfully restored my funds back to my wallet—a result I had never thought possible. If you have lost cryptocurrency to fraudsters, don’t assume it’s gone forever. Cryptic Trace Technologies is the lifeline you need. Their expertise, persistence, and cutting-edge tools make them the best in the business. Not only did they recover my stolen Bitcoin, but they also educated me on how to better protect my assets in the future. They truly care about their clients, and I wholeheartedly recommend them to anyone facing the same nightmare I once did. Reach them via: emails: cryptictrace @ technologist. Com
Cryptictracetechnologies @ zohomail . Com
Website: cryptictracetechnologies . Com1 -
BITCOIN RECOVERY EXPERT HIRE WIZARD WEB RECOVERY SERVICES
The dishonesty of this business knows no bounds. Everything they present is a well-constructed lie designed to strip you of your assets. Their approach is deceptively polite and persuasive, making it easy for people like me to fall into their trap. I was initially drawn in by their professional appearance and the promises of high returns on investments. They made everything sound so legitimate, offering enticing deals and assurances that everything was secure. They were experts at building trust, making it hard to question their intentions at first. I felt confident, even excited, about the potential growth of my investment. But as time passed, I started to notice red flags — subtle signs that something wasn’t right. Despite my growing doubts, I continued to trust them, hoping that the returns would eventually materialize.But, as it often happens with scammers, things began to unravel. I noticed that my funds weren’t being allocated as promised. The transactions seemed irregular, and the platform became increasingly difficult to navigate. When I attempted to reach out for clarification, my messages went unanswered. Calls were ignored, and the website’s contact information became mysteriously unavailable. Eventually, I realized the terrifying truth: I had been scammed. The company had vanished, leaving no trace behind except for a trail of broken promises and stolen investments.I was devastated. The money I had worked so hard for was gone, and I felt utterly helpless. That’s when I heard about WIZARD WEB RECOVERY SERVICES .Desperate to reclaim my funds, I decided to reach out, hoping for some resolution. To my surprise, they responded swiftly and professionally, offering me a glimmer of hope. The team at WIZARD WEB RECOVERY SERVICES Y was relentless in their efforts, working tirelessly to track down the fraudulent company and recover my money. They guided me through every step of the process, ensuring I understood my options and providing constant updates on their progress. Thanks to their expertise and determination, I was able to reclaim my investment.Though the process was difficult and frustrating, I’m incredibly grateful to WIZARD WEB RECOVERY SERVICES for their unwavering support. Without their assistance, I would still be in the dark, unable to recover what I had lost. Their professionalism and commitment to helping people like me navigate the complexities of online scams gave me a second chance to regain control of my financial future.1 -
TOP SERVICES FOR BITCOIN AND USDT RECOVERY.ASSET RESCUE SPECIALIST
I once got into a terrible predicament after losing a sizable portion of my Ethereum (ETH) investment in a fraud. I was inconsolable, felt like I had reached my lowest point, and had no idea how to get my money back. However, a buddy advised me to use the Asset Rescue Specialist service just when I believed there was no more chance. I made the decision to contact the Asset Rescue Specialist team because I was feeling hopeful for the first time in a long time. They were renowned for their proficiency in handling the fallout from internet frauds and assisting victims in getting their money back. When I reached out to the Asset Rescue Specialist, their team immediately got to work. In order to track down and retrieve my lost Ethereum investment, they carefully examined the digital trail that the scammer had left behind. As he effortlessly navigated through intricate algorithms and cast spells, it was like witnessing an Asset Rescue Specialist at work. As the days stretched into weeks, I marveled at the Asset Rescue Specialist team's relentless efforts to retrieve my lost money. With frequent progress reports and assurances that they were doing all within their power to assist me, they kept me informed at every stage. My lost Ethereum investment was successfully recovered, the Asset Rescue Specialist team declared gleefully after what felt like an age. I was shocked to learn that they had successfully recovered everything for me, even though I had assumed everything was gone. Knowing that contacting Asset Rescue Specialist was the right decision filled me with relief and thankfulness. In managing the fallout from the swindle and getting back what was properly mine, they had been my beacon of light. From that day on, I vowed to be more vigilant and cautious with my investments, knowing that there were expert teams like Asset Rescue Specialist ready to help in times of need. And as I watched my ETH investment grow once again, I knew that I had learned a valuable lesson in resilience and trust. The magic of the Asset Rescue Specialist team had truly saved the day. Send a DM via:Contact Email; assetrescuespecialist (AT) qualityservice (DOT) com
Thanks.
Wei Chong 6
6 -
It was a rainy Tuesday evening when I sat at my desk, staring at the screen in disbelief. My Bitcoin months of careful savings had vanished into a shady investment scheme I’d fallen for. The website promised "guaranteed returns," but after sending 2 BTC, the platform went dark, and my wallet was empty. I felt like a fool, scammed by my own desperation for a quick profit. Days turned into weeks, and I’d nearly given up hope when a friend mentioned Alpha Spy Nest, a secretive group known for tracking down lost crypto. Skeptical but desperate, I reached out through an encrypted email I found on a forum. Within hours, a response arrived: “Send us the details. We’ll see what we can do.” I shared everything, the wallet address I’d sent my Bitcoin to, the fake platform’s URL, and the few screenshots I’d taken. Alpha Spy Nest didn’t waste time with pleasantries. Their next message was a list of questions: transaction IDs, dates, even the IP address I’d used. I scrambled to provide it all, unsure how they’d pull off the impossible. Behind the scenes, Alpha Spy Nest went to work. They were a shadowy crew, hackers, blockchain analysts, and who-knows-what-else, operating on the edges of the digital world. Using tools I couldn’t begin to understand, they traced my Bitcoin through a labyrinth of wallets designed to hide the trail. The scammers had funneled it through mixers, but Alpha Spy Nest unraveled the mess, linking it to an exchange account tied to a careless crook who’d left digital breadcrumbs. Days later, I got a message: “Check your wallet.” My hands trembled as I opened my crypto app. There it was 1.9 BTC, a hair less than I’d lost due to fees, but more than I’d ever dreamed of seeing again. A follow-up note from Alpha Spy Nest explained they’d pressured the scammer into returning it after exposing his identity to the exchange. “He folded fast,” they wrote. “Stay sharp next time.” I never met them, never even learned their real names. But that rainy night, Alpha Spy Nest turned my despair into a second chance. I swore I’d never fall for a scam again and that I’d keep their name close, just in case. whatsApp: +14159714490
 1
1 -
Bitcoin, the leading cryptocurrency, has revolutionized the financial landscape but has also attracted fraudulent schemes targeting unsuspecting investors. As the popularity of Bitcoin continues to soar, so do the risks associated with fraudulent investments. Bitcoin fraudulent investments refer to schemes where individuals deceive others into investing in fake or illegitimate projects promising high returns. These scams exploit the trust and lack of regulation in the cryptocurrency space, posing a significant risk to investors. Bitcoin fraudulent investments involve deceitful practices where scammers lure unsuspecting individuals to invest their money in schemes that do not exist or do not deliver on their promises. Such scams can range from Ponzi schemes to fake ICOs, preying on the desire for quick profits in the volatile world of cryptocurrencies. Victims of Bitcoin fraudulent investments not only suffer financial losses but also experience emotional distress and a loss of trust in the cryptocurrency market. Retrieving stolen bitcoin becomes a priority for these individuals to seek justice and recover their assets. Retrieving pilfered bitcoin is a daunting task due to the intricate nature of tracing and identifying stolen funds in the decentralized and pseudonymous blockchain network. Additionally, legal and jurisdictional hurdles further complicate the recovery process, making it challenging for victims to reclaim their stolen assets. The anonymous nature of Bitcoin transactions and the lack of a central authority make it difficult to trace and identify stolen funds. Scammers often use sophisticated methods to obfuscate the flow of stolen Bitcoin, leading to a complex trail that requires expertise to unravel. Bitcoin recovery efforts are hindered by legal and jurisdictional challenges, as scammers operate across borders and exploit loopholes in regulations. Reclaiming stolen bitcoin requires navigating through different legal systems and cooperating with authorities internationally, adding layers of complexity to the retrieval process. Recovering monies taken from victims of bitcoin scams is the area of expertise of reputable company REVENANT CYBER HACKER. When my Bitcoin wallet was hacked and the cyber thieves seemed to have vanished into thin air, REVENANT CYBER HACKER stepped in to crack the case wide open. Through their relentless pursuit and ingenious tactics, they were able to recover the stolen funds and restore faith in the security of cryptocurrency investments. It's a happy ending that proves that even in the Wild West of the crypto world, there are heroes like REVENANT CYBER HACKER fighting for justice. Contact REVENANT CYBER HACKER on:
-
Contact a legit Bitcoin recovery company- Hire Hackerzed Nemesis Recovery Company
Living in Toronto, it seemed like the ultimate financial catastrophe to lose 10 Bitcoin. One moment, everything appeared safe and secure, and the next, I was staring at the possibility of a devastating mistake that could cost me my entire investment. The remorse and regret that followed were unbearable. I had poured years of effort, patience, and resources into building my portfolio, only to see it vanish in an instant. The thought of never recovering my Bitcoin tormented me day and night, casting a shadow over every waking moment, In desperation, I made several attempts to recover my funds, including consulting with legal experts and reporting the matter to authorities. Despite my efforts, each attempt ended in failure, further deepening my despair. I felt like I was running out of options and time. The overwhelming weight of my loss made it difficult to focus on anything else, and I began to lose hope. it was during this dark period that I came across Hackerzed Nemesis Recovery. Admittedly, I was skeptical at first. Could this team really succeed where others had failed? Recovering 10 Bitcoin felt like an impossible task. Yet, their expertise, and strong track record of successfully handling similar cases caught my attention. Their reviews and recommendations gave me the slightest glimmer of hope, and I decided to take a leap of faith. From the moment I reached out to Hackerzed Nemesis Recovery, I was met with a team that was empathetic, attentive, and deeply committed to helping me. They took the time to listen to my story, understand my distress, and thoroughly evaluate the details of my case. Their approach was systematic and professional, instilling a sense of trust and reassurance that I hadn’t felt in weeks. They employed advanced blockchain analysis and cutting-edge cyber-forensic tools to trace the stolen Bitcoin. To my astonishment, they managed to uncover the trail leading to my funds, even though I had lost all hope of recovery. The moment I received confirmation of my recovered Bitcoin, I was overwhelmed with gratitude and relief. What felt like an insurmountable disaster had turned into a story of redemption, thanks to Hackerzed Nemesis Recovery. They not only helped me recover my investment but restored my faith in the possibility of justice. For anyone who has experienced a similar loss, I can confidently say that Hackerzed Nemesis Recovery is the best.
CONTACT:
WhatsApp: +1, 6,3,9 3,9,5 4,6,2,8
Mail: hackerzednemesis001(@)zohomail(.)com
info(@)hackerzednemesis(.)com 4
4 -
RAPID DIGITAL RECOVERY SPECIALIZE IN BITCOIN AND CRYPTO ASSET RETRIEVING
The dishonesty of this business knows no bounds. Everything they present is a well-constructed lie designed to strip you of your assets. Their approach is deceptively polite and persuasive, making it easy for people like me to fall into their trap. I was initially drawn in by their professional appearance and the promises of high returns on investments. They made everything sound so legitimate, offering enticing deals and assurances that everything was secure. They were experts at building trust, making it hard to question their intentions at first. I felt confident, even excited, about the potential growth of my investment. But as time passed, I started to notice red flags — subtle signs that something wasn’t right. Despite my growing doubts, I continued to trust them, hoping that the returns would eventually materialize. But, as it often happens with scammers, things began to unravel. I noticed that my funds weren’t being allocated as promised. The transactions seemed irregular, and the platform became increasingly difficult to navigate. When I attempted to reach out for clarification, my messages went unanswered. Calls were ignored, and the website’s contact information became mysteriously unavailable. Eventually, I realized the terrifying truth: I had been scammed. The company had vanished, leaving no trace behind except for a trail of broken promises and stolen investments. I was devastated. The money I had worked so hard for was gone, and I felt utterly helpless. That’s when I heard about Rapid Digital Recovery. Desperate to reclaim my funds, I decided to reach out,.. EMAIL: rapid digital recovery @ ex ecs. com... hoping for some resolution. To my surprise, they responded swiftly and professionally, offering me a glimmer of hope. The team at Rapid Digital Recovery was relentless in their efforts, working tirelessly to track down the fraudulent company and recover my money. They guided me through every step of the process, ensuring I understood my options and providing constant updates on their progress. Thanks to their expertise and determination, I was able to reclaim my investment. Though the process was difficult and frustrating, I’m incredibly grateful to Rapid Digital Recovery for their unwavering support. Without their assistance, I would still be in the dark, unable to recover what I had lost. Their professionalism and commitment to helping people like me navigate the complexities of online scams gave me a second chance to regain control of my financial future.
What sapp Info: +1 41 4 80 7 14 85 1
1 -
Bitcoin, the leading cryptocurrency, has revolutionized the financial landscape but has also attracted fraudulent schemes targeting unsuspecting investors. As the popularity of Bitcoin continues to soar, so do the risks associated with fraudulent investments. Bitcoin fraudulent investments refer to schemes where individuals deceive others into investing in fake or illegitimate projects promising high returns. These scams exploit the trust and lack of regulation in the cryptocurrency space, posing a significant risk to investors. Bitcoin fraudulent investments involve deceitful practices where scammers lure unsuspecting individuals to invest their money in schemes that do not exist or do not deliver on their promises. Such scams can range from Ponzi schemes to fake ICOs, preying on the desire for quick profits in the volatile world of cryptocurrencies. Victims of Bitcoin fraudulent investments not only suffer financial losses but also experience emotional distress and a loss of trust in the cryptocurrency market. Retrieving stolen bitcoin becomes a priority for these individuals to seek justice and recover their assets. Retrieving pilfered bitcoin is a daunting task due to the intricate nature of tracing and identifying stolen funds in the decentralized and pseudonymous blockchain network. Additionally, legal and jurisdictional hurdles further complicate the recovery process, making it challenging for victims to reclaim their stolen assets. The anonymous nature of Bitcoin transactions and the lack of a central authority make it difficult to trace and identify stolen funds. Scammers often use sophisticated methods to obfuscate the flow of stolen Bitcoin, leading to a complex trail that requires expertise to unravel. Bitcoin recovery efforts are hindered by legal and jurisdictional challenges, as scammers operate across borders and exploit loopholes in regulations. Reclaiming stolen bitcoin requires navigating through different legal systems and cooperating with authorities internationally, adding layers of complexity to the retrieval process. Recovering monies taken from victims of bitcoin scams is the area of expertise of reputable company REVENANT CYBER HACKER. When my Bitcoin wallet was hacked and the cyber thieves seemed to have vanished into thin air, REVENANT CYBER HACKER stepped in to crack the case wide open. Through their relentless pursuit and ingenious tactics, they were able to recover the stolen funds and restore faith in the security of cryptocurrency investments. It's a happy ending that proves that even in the Wild West of the crypto world, there are heroes like REVENANT CYBER HACKER fighting for justice. Contact REVENANT CYBER HACKER on:Website : revenantcyberhacker{DOT} org
Email: revenantcyberhacker AT Gmail {DOT} com
Telegram: revenantcyberhacker
WhatsApp: + 1 (208) 425-8584 WhatsApp: + 1 (913) 820-0739 1
1 -
HIRE MUYERN TRUST HACKER THE BEST BITCOIN RECOVERY SERVICE
The Initial Coin Offering (ICO) I invested in appeared flawless, its website was sleek and authentic, the whitepaper was detailed and convincing, and the team boasted impressive credentials in cryptocurrency. Everything pointed to legitimacy, and I was eager to capitalize on a golden opportunity. Confident in my research, I invested $200,000, only to watch in horror as the entire operation vanished days later. The website disappeared, all communication ceased, and the harsh reality set in: I had fallen victim to an elaborate scam. Desperate to recover my funds, I filed reports with the police and contacted my bank, but progress was agonizingly slow. The authorities offered little hope, and my bank could do nothing to reverse the transaction. The guilt was crushing. I had even borrowed some of the investment from my elderly mother, dipping into her pension savings. The weight of my mistake was unbearable, leaving me powerless and consumed by regret. Just as I was resigning myself to the loss, I discovered Muyern Trust Hacker by searching online, ( web: ht tps://muyerntrusthacker . o r g / ) Skeptical at first after all, I had already been deceived once I delved into their reputation and was impressed by their proven success in recovering stolen cryptocurrency. Taking a leap of faith, I reached out, and from the very first interaction, their team stood out for their professionalism and urgency. They immediately assessed my case, explaining their process with transparency and instilling a renewed sense of hope. What truly distinguished Muyern Trust Hacker was their advanced investigative approach. Unlike conventional methods, they utilized cutting-edge forensics to trace my stolen funds, even navigating through sophisticated obfuscation techniques like mixers and layered transactions. Their experts meticulously followed the digital trail across multiple wallets and exchanges, leaving no stone unturned. After a week of relentless effort, they achieved the impossible: $175,000 was recovered. While not the full amount, it was a staggering victory considering I had assumed everything was lost forever. The relief was indescribable. Thanks to Muyern Trust Hacker, I could repay a significant portion of what I owed my mother and regain some financial stability. This has taught me a harsh lesson about the risks of crypto investments but it also showed me the power of expert intervention. For anyone who has fallen victim to a scam, Muyern Trust Hacker ( Tele gr am: muyerntrusthackertech ) is the rescue team in an otherwise bleak situation. Their recovery services turned my crypto disaster into a second chance.2 -
HIRE A EXPERIENCE HACKER TO RECOVER SCAM BTC & USDT WITH SPARTAN TECH GROUP RETRIEVAL
Accuracy is my business, but one spoofed email ruined all that I had built. I am an attorney who prides myself on being able to detect lies, but the scam this time was flawless. A bogus legal notice arrived in my mail, with the same tone and crest of a familiar regulatory body. Panic overwhelmed me. I clicked on the link, entered my Bitcoin wallet login credentials, and in minutes, my $1.05 million portfolio disappeared into thin air. The realization hit like a gavel blow. My palms were moist, my heart pounded in my chest, and my office walls seemed to close in on me. I pictured the headlines—a lawyer misled, reputation destroyed. I buried my face in my hands, seeing the carefully laid plans of my future disappear through my fingers. Desperate but resolute, I enlisted the help of a friend I trusted in the form of a lunch invitation. Over half-caf coffee gulps, I unloaded my humiliation. He leaned in closer, his voice in a whisper, and spoke two words that would change reality, SPARTAN TECH GROUP RETRIEVAL. It was as if calling a covert agency. Their staff, from the first call, appeared to exude professionalism and secrecy. They listened to her unbiased, their queries pointed but subtle. Several hours later, their cyber investigators had embarked on a digital trail, analyzing blockchain transactions with the surgical skill of experts. Each day had top stories that felt like a page from a suspense novel. They tracked my compromised Bitcoin through an underground network of washing wallets, peeling away layers of cyber cover like amateurs. Their retrieval team navigated its way past international crypto regimes, exploiting gaps and freeze orders. Within only three weeks, I received the call. My money had been retrieved, every satoshi restored. Such a feeling of relief swept over me that I had to sit down. It felt as though I had won a case hopeless to win, yet this was one that mattered deeply to me. SPARTAN TECH GROUP RETRIEVAL did more than retrieve my funds. They restored my confidence. Their detailed forensic report now sits in my files, a weapon in my criminal complaint against the fraudsters. The level of professionalism they demonstrated rivals the best legal teams I’ve worked with. If you think it can't happen to you, think again. And if it ever does, call SPARTAN TECH GROUP RETRIEVAL. They are the silent guardians of your online future.
Reach out to spartan tech group retrieval with the contact info below:
Email >>>> support (@) spartan tech group retrieval. o r g
Website >>>> https: / / spartan tech group retrieval . o r g
WhatsApp >>>> + 1 9 7 1 4 8 7 - 3 5 3 8 1
1 -
IF YOU HAVE LOST YOUR BTC AND YOU NEED A BITCOIN EXPERT JUST GOOGLE SALVAGE ASSET RECOVERY
Reach out to Salvage Asset Recovery Via Below
WHATSAPP + 1 8 4 7 6 5 4 7 0 9 6
TELEGRAM @Salvageasset
When it comes to recovering stolen or lost cryptocurrency, Salvage Asset Recovery is the leader .Their expertise in both cybersecurity and legal matters places them at the forefront of cryptocurrency recovery services. Unlike many other firms, they don’t just offer a standard recovery service they provide a specialized, multi-disciplinary approach that blends cutting-edge technology with in-depth legal knowledge. I unfortunately became a victim of a phishing scam that led to the loss of a significant amount of ETH. Naturally, I was desperate to recover my funds, so I reached out to Salvage Asset Recovery. From the very first moment, their team impressed me with their swift and methodical response. They immediately deployed advanced machine learning algorithms to scan blockchain clusters, analyzing transaction data for any signs of illicit activity. Within hours, they flagged suspicious wallet movements, which pointed to the use of darknet tumblers—commonly used methods to obscure the trail of stolen cryptocurrency. What truly set Salvage Asset Recovery apart was their seamless integration of technical expertise and legal know-how. While their cybersecurity team worked tirelessly to trace the stolen funds, their legal professionals took charge of navigating the complex world of international asset recovery. They worked directly with Interpol-certified exchanges to issue seizure orders, ensuring the stolen funds were frozen before they could be laundered further. Their deep understanding of international legal frameworks and jurisdictional nuances gave them a significant advantage over smaller firms, allowing them to act quickly and effectively. The level of precision and coordination displayed by Salvage Asset Recovery was impressive. Not only did they have the tools to trace illicit cryptocurrency transactions, but they also had the legal expertise to take immediate and decisive action. Their ability to act across multiple jurisdictions, using a combination of technical tools and legal strategies, provided me with a level of assurance I didn’t expect. Recovering stolen cryptocurrency is a complex and often daunting process, but with Salvage Asset Recovery’s support, it became manageable. If you find yourself in the unfortunate situation of losing cryptocurrency, I can confidently recommend Salvage Asset Recovery. Their unique combination of technical know-how and legal expertise sets a new benchmark in the industry, offering unmatched service in the field of cryptocurrency recovery.2 -
SALVAGE ASSET RECOVERY HELPED ME RECOVER MY STOLEN BITCOIN LOST TO FAKE INVESTMENT
GET IN TOUCH WITH SALVAGE ASSET RECOVERY VIA BELOW
CONTACT DETAILS TELEGRAM—@SALVAGEASSET
WHATS APP +18476547096
In my pursuit of advancing my career in technology I came across an advertisement for a Harvard Blockchain Certificate program that immediately caught my attention. The website was impressively crafted featuring official logos, detailed course descriptions and what appeared to be genuine testimonials from "alumni." Ignoring my father's warning "Son if you have to pay in crypto it’s probably a scam" I eagerly enrolled and sent $15,000 in Bitcoin as tuition convinced I was making a wise investment in my future.However my excitement quickly turned to despair when the website vanished without a trace. There was no login portal, no customer support and no way to recover my funds, just an empty void where the program had once existed. I felt utterly defeated realising I had fallen victim to a sophisticated scam. My father, while disappointed, chose not to dwell on my mistake. Instead he stood by me and helped me search for potential solutions determined to find a way to recover my lost investment.During our search we discovered SALVAGE ASSET RECOVERY, a firm specialising in cryptocurrency fraud cases. Although I was initially sceptical I felt I had no other options and decided to reach out to SALVAGE ASSET RECOVERY . Their team responded quickly and exuded professionalism assuring me that they had the expertise to handle my case. They explained that they would utilise blockchain forensics to trace my stolen funds, a process that sounded both intricate and promising. SALVAGE ASSET RECOVERY acted swiftly employing advanced techniques to track my Bitcoin through various wallets. Their team successfully uncovered the scammers’ trail revealing how my funds had been transferred and concealed. Remarkably within three weeks SALVAGE ASSET RECOVERY located the full amount still sitting in a wallet untouched and not yet laundered. This was a fortunate turn of events as many victims never saw their money again.Their commitment and skill were clear and I started to feel a sense of optimism returning. Then I received the incredible news that SALVAGE ASSET RECOVERY had managed to recover all my funds. A wave of relief and gratitude washed over me as I realised that not only had I gotten my money back but I had also gained an important insight into the necessity of being cautious in the digital world . With the help of SALVAGE ASSET RECOVERY I transformed a distressing situation into victory.
2 -
Your Crypto Isn’t Gone Forever, Start the Recovery Process Today hire Adware Recovery Specialist
As a college student in the U.S., eager to catch the next big wave in cryptocurrency, I thought I had struck gold with a coin called MoonDoge. The hype was unreal. Telegram was on fire, developers promised 1000x gains, and the chat was full of dreamers planning early retirements. The FOMO was intense, and I didn’t want to miss out. So I went all in. I liquidated every dollar I had saved, from tutoring gigs, summer jobs, side hustles, and poured it into MoonDoge. The price chart was soaring, the community was electric, and I was riding an adrenaline high. For a moment, I truly believed financial freedom was just around the corner. Then, it all collapsed. Without warning, the developers pulled the liquidity. The coin crashed to zero. Telegram went dead. It was a textbook rug pull. I sat in front of my screen, stunned, refreshing my wallet over and over, hoping for some kind of miracle. But nothing changed. That’s when I found ADWARE RECOVERY SPECIALIST . Desperate but holding on to a sliver of hope, I reached out to them. To my surprise, they responded quickly, calm, professional, and clearly experts in blockchain forensics. From there, they took over. Their team began tracking the stolen MoonDoge funds through obscure DeFi bridges and crypto mixers. Telegram info: adwarerecoveryspecialist5656 Using cutting-edge blockchain analytics, they traced every transaction, following the money trail back to wallets linked to the developers. What they uncovered was a complex network of deception, and they had the receipts. But they didn’t stop at tracking. ADWARE RECOVERY SPECIALIST compiled hard evidence, applied legal pressure, and made it clear to the scammers that they weren’t invisible. With the threat of exposure and undeniable proof in hand, they cornered them. Website info: h t t p s:// adware recovery specialist. com Then came the moment I never thought would happen. One morning, still groggy and weighed down by regret, I checked my wallet, just out of habit. I couldn’t believe what I saw: my funds were back. I refreshed the screen, again and again, this time in disbelief and overwhelming relief. ADWARE RECOVERY SPECIALIST had done it. WhatsApp info: +12 (72332)—8343 They recovered everything I’d lost. Without them, I would’ve been just another victim of the meme coin scam epidemic. But they didn’t just recover my crypto, they restored my faith in the crypto space. Email info: Adware recovery specialist @ auctioneer. net They gave me a second chance. No more chasing pipe dreams of 1000x returns. This experience taught me the hard way. Now, I invest smarter, and I know exactly who to call if something ever goes wrong again.
Thank you, ADWARE RECOVERY SPECIALIST.2 -
LOST YOUR CRYPTO? HERE IS HOW TO GET IT BACK SAFELY HIRE ADWARE RECOVERY SPECIALIST
At 49, my life is the result of both calculated risks and deeply painful betrayals. As an economics lecturer at Harrington University, I teach students about market fluctuations and financial strategy. But the most profound lessons I share come not from textbooks, they come from my own personal experience with loss, betrayal, and eventual recovery. WhatsApp info: +12 (72332)—8343
Before stepping into university classrooms, I was a high school teacher at Westbridge High. Quietly and methodically, I built a $370,000 cryptocurrency trading portfolio. What started as a side project became a private triumph, a reflection of my deep understanding of economic principles, cultivated through discipline, patience, and analytical thinking.
But ambition can invite envy. Email info: Adware recovery specialist @ auctioneer. net
Some of my old friends from Westbridge, once trusted confidants, became resentful as they learned of my growing financial success. That resentment turned malicious when they orchestrated a sophisticated phishing attack. It came through a seemingly harmless email. One careless click, and just like that, everything was gone. My savings, my sense of security, and my faith in people I had known for decades vanished in an instant.
The aftermath was paralyzing. Though I reported the theft, the digital trail seemed impossibly complex. I felt isolated, betrayed, and utterly lost. Then a colleague referred me to Adware Recovery Specialist, a cybersecurity firm that specializes in digital financial fraud. Within just 32 hours, they recovered my compromised email, traced the attack, and compiled a detailed forensic report. The evidence was airtight, IP addresses, time stamps, even messages exchanged by the perpetrators. Website info: h t t p s:// adware recovery specialist. com
Thanks to their work, I took legal action. Faced with irrefutable proof, my former “friends” settled quickly, agreeing to pay $300,000 in restitution to avoid criminal prosecution.
Today, back at my desk at Harrington University, I bring more than just economic theory into the classroom. I teach about risk, trust, digital vulnerability, and most importantly, resilience. I share my experience not to scare, but to prepare. Because no amount of expertise shields you completely from deception. But with the right allies, even the worst chapters can be rewritten.
Yes, I still trade crypto. But now, I do it with triple-layer authentication and a much more guarded heart. Every time I log into my secured accounts, I think of Adware Recovery Specialist, not just for recovering my funds, but for restoring my belief that justice, with the right team, is possible.
Because sometimes, the most valuable recovery isn’t just financial, it’s personal.2 -
BTC, ETH & BNB LOSS RECOVERY SOLUTION VISIT SPARTAN TECH GROUP RETRIEVAL
Their info :
Email: spartan tech (@) cyber services. c o m
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2
As a seasoned real estate developer, I have navigated numerous high-value transactions, yet nothing could have prepared me for the sophisticated scam that cost me a staggering $47,000 and my prized Rolex Daytona. The buyer, who purported to be from Germany, insisted on utilizing an escrow service named "EuroSafe Escrow." At first glance, everything seemed legitimate; the website boasted SSL certificates, professional branding, and what appeared to be authentic testimonials. The entire process felt meticulously secure. I received comprehensive contracts from the supposed escrow agent, was sent what looked like a credible payment confirmation, and subsequently shipped my Rolex to their verified address. Just forty-eight hours later, the façade crumbled. The escrow website vanished without a trace, the German phone numbers were disconnected, and I was left grappling with a $47,000 loss, not to mention the emotional toll of losing my $18,500 Rolex Daytona. It was a devastating blow, both financially and psychologically, as I had placed my trust in the process, believing I was making a prudent business decision. I turned to SPARTAN TECH GROUP RETRIEVAL. Their response was swift and comprehensive, providing a glimmer of hope in an otherwise bleak situation. Within the first few days, they conducted a meticulous digital paper trail analysis, tracing the fraudulent escrow site back to a shell company in Cyprus. Within a week, they tracked my wire transfer through three offshore banks and flagged the receiving cryptocurrency wallet. Their expertise was evident as they adeptly navigated the complexities of the digital landscape. SPARTAN TECH GROUP RETRIEVAL did not stop there. Over the ensuing days, they filed reports with INTERPOL’s cybercrime division, coordinated with German authorities regarding the fraudulent business address, and collaborated with Binance to freeze the converted cryptocurrency funds. By Day 10, they had successfully recovered $38,500 of my lost money and even traced my Rolex to a pawn shop in Dubai, where it is now in the process of legal recovery. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to reclaim a significant portion of my funds and maintain hope of retrieving my watch. Their global reach and impressive capabilities are commendable, and I cannot recommend their services highly enough for anyone who finds themselves in a similar predicament.2 -
USDT/BTC RECOVERY EXPERTS// CRYPTIC TRACE TECHNOLOGIES
Scammers lurk insidiously in the shadows of the cryptocurrency realm, preying on unsuspecting investors with tantalizing promises of rapid wealth and infallible investments. The sinking feeling of losing a Bitcoin investment is an all-too-familiar ordeal not merely a financial catastrophe, but an emotional maelstrom as well. The frustration, indignation, and sense of helplessness can be utterly overwhelming. When confronted with the aftermath of a scam or a technical debacle, it can feel as though your hard-earned cryptocurrency has evaporated into thin air. Cryptic Trace Technologies is here to metamorphose that despair into a renewed sense of hope and relief. Equipped with state-of-the-art blockchain forensics and a wealth of expertise, their dedicated team specializes in tracing lost, stolen, or fraudulently acquired Bitcoin. They do not merely offer hollow assurances; they deliver substantive results. After falling victim to a sophisticated crypto scam, I had nearly succumbed to hopelessness until I discovered Cryptic Trace Technologies. Their relentless pursuit of justice not only unearthed the trail of my misappropriated funds but also successfully facilitated their recovery. If you have endured a similar loss, do not resign yourself to defeat. Cryptic Trace Technologies seamlessly amalgamates technical brilliance with an unwavering commitment to justice, ensuring that victims receive a second chance at reclaiming their assets. My deepest gratitude extends to their team for their expertise, and unwavering dedication they truly are the wizards of crypto recovery.The emotional toll of losing cryptocurrency can be profound, often engendering feelings of isolation and despair. The world of digital assets is fraught with peril, and the ramifications of falling prey to scams can be devastating. Yet, with the right support, recovery is not only possible but attainable. Cryptic Trace Technologies comprehends the intricacies of forensics technology and employs advanced methodologies to track down lost assets, providing a beacon of hope for those who feel ensnared in the labyrinth of cryptocurrency theft. Take action today your Bitcoin could still be within reach. Do not allow the shadows of despair to obscure your judgment. Reach out to Cryptic Trace Technologies and let their expertise illuminate your path through the recovery process. With their assistance, you can reclaim not only your financial assets but also your peace of mind. The journey to recovery may be arduous, but with the right allies by your side, it is entirely achievable. Embrace the possibility of regaining what is yours and take the first step toward recovery. For more info check out their W E B S I T E: cryptictracetechnologies (.) com or E M A I L them: Cryptictrace (@) technologist (.) com.2 -
One careless click cost me dearly. I was looking for a legitimate update to my Trust Wallet when I came across what appeared to be a genuine Google ad. It looked official, well-designed, and trustworthy. Without a second thought, I clicked on it, downloaded the app, and installed it on my device. What I didn’t know was that I had just downloaded sophisticated malware.The next morning, I opened my wallet and was hit with a wave of disbelief. My entire crypto balance was gone. A total of 12 ETH, worth tens of thousands of dollars, had vanished overnight. I stared at the screen in shock, hoping it was just a glitch. But it wasn’t. My wallet had been drained, and the hacker left no trace behind other than a cold, untraceable transaction hash.Panic set in quickly. I dove into transaction histories, trying to make sense of what had happened. I turned to online forums, Reddit threads, and even reached out to Trust Wallet’s customer support. Their response was prompt but grim: since the blockchain is decentralized and immutable, there was no way to reverse the transaction. Once your crypto is stolen, it’s almost impossible to recover without professional help. I felt defeated, overwhelmed by guilt and helplessness.That’s when I discovered TECH CYBER FORCE RECOVERY, a cybersecurity firm specializing in stolen cryptocurrency recovery and blockchain forensics. Desperate but intrigued, I read real success stories from others who had been scammed just like me and got their funds back thanks to TECH CYBER FORCE RECOVERY. With nothing to lose, I decided to reach out. I contacted whats.App then + 156,172,636,97 Or email.. support (At) techyforcecyberretrieval (dot) com, they treated my case with urgency and respect. Their team was clear about the risks and realities, no false promises, just professionalism and determination. For the first time since the theft, I felt that someone truly had my back.Through a combination of deep blockchain analysis, cyber investigation, and tracking the digital trail, TECH CYBER FORCE RECOVERY worked relentlessly on my behalf. And the outcome? Against all odds, I recovered everything. All 12 ETH, every last bit of it, was traced and returned to me. I couldn’t believe it. After feeling hopeless for days, TECH CYBER FORCE RECOVERY delivered what I thought was impossible.If you’ve been scammed or had your crypto stolen, don’t wait in silence or assume all hope is lost. TECH CYBER FORCE RECOVERY proved to me that with the right team, recovery is possible. I got my funds back.2
-
BEST BITCOIN RECOVERY SPECIALIST, HACKER HIRE FUNDS RETRIEVER ENGINEER
Just a few months ago, I found myself at the darkest point of my life. I had fallen prey to a devastating rug pull that obliterated $140,000 of my painstakingly earned cryptocurrency investments. One moment, my portfolio was flourishing; the next, the developers vanished without a trace, the liquidity was siphoned off, and my funds were gone. I felt completely powerless like I had been ambushed with no possibility of justice.For weeks, I pursued every avenue imaginable filing reports with law enforcement, consulting cybersecurity experts, and even hiring a private investigator. Yet every attempt led to a dead end. The anonymity of blockchain technology made the recovery seem like an unattainable goal. Then, a trusted friend recommended FUNDS RETRIEVER ENGINEER, a team reputed for their proficiency in digital asset retrieval. Though hesitant and emotionally drained, I decided to give them a chance. From the very first consultation, their professionalism and clarity sparked a glimmer of hope. They meticulously explained how they use blockchain analytics, liquidity tracing, and forensic tools to follow the money trail. Unlike others, they didn’t peddle false promises they provided a structured, realistic strategy. In just 48 hours, they had already tracked a substantial portion of my stolen funds dispersed across various wallets.The team at FUNDS RETRIEVER ENGINEER was relentless, navigating decentralized exchanges, identifying suspicious transactions, and systematically piecing together the puzzle. After two intense weeks, I received what I can only describe as a miracle $125,000 recovered,recovering 90% of my losses was something I never thought possible.What distinguishes FUNDS RETRIEVER ENGINEER is their integrity, technical prowess, and unwavering commitment. They provided constant updates, answered my every question with patience, and fought vigorously to retrieve what was rightfully mine. Today, I’ve reinvested more cautiously, fortified my digital assets, and most importantly, restored my financial footing all because of them. If you’ve been victimized by crypto fraud, don’t surrender to despair FUNDS RETRIEVER ENGINEER is authentic, reliable, and truly elite. They transformed my catastrophe into a fresh beginning, and for that, I will be eternally grateful.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M2 -
TRUSTED CRYPTO & ASSET RECOVERY SOLUTION / BOTNET CRYPTO RECOVERY
Losing digital assets to a fraudulent exchange or trading platform can be so painful, especially when the amount involved is significant. My cousin, who lives in Australia, unfortunately fell victim to one such scam, losing $197,963.102 to fraudsters who had created a platform that appeared legitimate at first glance. These scammers used convincing tactics to gain her trust, leading her to invest a large sum of money into what she thought was a secure and reputable trading site. Once she realized she had been deceived, the shock and frustration were overwhelming. Beyond the financial loss, she felt emotionally betrayed, unsure of how to recover from such an experience.Initially, my cousin felt lost, trying to process the situation and figure out how to regain the funds she had lost. She spent weeks researching potential solutions, but found the process to be more challenging than she had anticipated. Cryptocurrency transactions, due to their anonymous and decentralized nature, are notoriously difficult to trace, making it hard to find ways to recover stolen funds. Many people in similar situations may feel stuck, unsure where to turn or how to navigate the complexities of digital currency theft.However, in her search for a solution, my cousin discovered a well-known Bitcoin recovery expert, Botnet Crypto Recovery. This firm is reputed for its expertise in helping victims of cryptocurrency scams. With a proven track record of successfully recovering stolen funds, Botnet Crypto Recovery specializes in tracing the movement of stolen digital assets and working with financial institutions to reclaim lost cryptocurrencies. Intrigued by their reputation, my cousin reached out to them for assistance.Once she made contact, the recovery process began. The experts at Botnet Crypto Recovery conducted a thorough investigation, analyzing the blockchain and identifying the trail left by the fraudsters. Using advanced techniques, they tracked the stolen Bitcoin across different networks and exchanges. Over several weeks, the team worked tirelessly, utilizing their specialized knowledge of blockchain technology to trace the funds and identify the perpetrators behind the scam.Thanks to their efforts, my cousin was able to recover a significant portion of her lost Bitcoin, which brought a sense of relief and justice. While the emotional scars of the scam remained, knowing that her funds were being recovered helped her feel more in control of the situation. Her experience serves as a reminder to others about the risks of cryptocurrency scams and the importance of seeking professional help if they fall victim to fraud. She now encourages anyone who has been scammed to act quickly and consult with experts like Botnet Crypto Recovery, who have the skills and resources to help victims reclaim their assets. To contact kindly use any of the below listed info.
WhatsApp ( +1 (431) 801-8951 )
Mail (support @ botnetcryptorecovery . com) 7
7 -
Best Recovery Experts for Cryptocurrency Assets: HIRE CERTIFIED RECOVERY SERVICES
Last month, I faced a nightmare scenario when the entire balance of SOL I held in my Meta Mask wallet was abruptly transferred to an unknown address. One moment, my funds were secure; the next, they’d vanished without a trace. I frantically reviewed my transaction history, double-checked permissions, and scanned my devices for malware, but found no obvious breach. Panic turned to despair as I realized my savings accumulated through years of cautious investing were gone. Desperate for answers, I contacted Meta Mask support, only to be told that decentralized transactions couldn’t be reversed or traced by their team. They speculated that my wallet had been compromised, possibly via a phishing scam, a malicious dApp, or a leaked recovery phrase, but I couldn’t pinpoint where I’d gone wrong. Feeling helpless, I combed through Reddit threads and crypto forums, where I stumbled upon CERTIFIED RECOVERY SERVICES, a service hailed for its success in reclaiming stolen assets. Though skeptical after all, everything I’d read suggested crypto theft was irreversible I decided to take a leap of faith and submitted my case details, including transaction IDs and wallet addresses. Their team responded within hours, outlining a meticulous plan to trace the stolen SOL across the blockchain and collaborate with exchanges to intercept the funds. Over the next week, CERTIFIED RECOVERY SERVICES provided daily updates, revealing how the thief had funneled my SOL through a labyrinth of wallets to obscure its trail. Using advanced blockchain forensics, they identified patterns linking the movement of funds to a known exchange. By working with legal teams and platform security, they flagged the stolen crypto before it could be liquidated. Their expertise and determination were evident as they navigated the complexities of the blockchain, piecing together the puzzle of my stolen assets. Against all odds, their relentless efforts paid off: within 9 days, they recovered 100% of my stolen SOL and safely redirected it to a new, fortified wallet. This experience taught me the importance of vigilance in the crypto space and the value of seeking help from experts when faced with seemingly insurmountable challenges. I learned that while the decentralized nature of cryptocurrency offers many advantages, it also comes with risks that require constant awareness and proactive measures. Now, I’m more cautious than ever, ensuring that my digital assets are protected and that I stay informed about potential threats in the ever-evolving world of cryptocurrency.
Here's Their Info Below:2 -
BEST CRYPTOCURRENCY RECOVERY COMPANY - GO TO DIGITAL TECH GUARD RECOVERY HACKER
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard . com
Website link: digital tech guard . com
The digital illusion emerged in February through an intricately fabricated Facebook persona, a supposed cryptocurrency guru flaunting opulent estates and glowing testimonials from “investors” basking in fabricated riches. Enticed by the allure of portfolio diversification, I engaged the profile, unaware of the deception that lay ahead. This individual, a master manipulator, spent weeks cultivating trust. They bombarded me with sleek marketing materials for a “cloud-based mining operation,” complete with counterfeit revenue graphs and forged regulatory certificates. Their pitch, a seamless blend of industry jargon and fabricated urgency, eroded my skepticism. I finally transferred an initial $15,000. Soon, the platform’s dashboard reflected impressive returns and even allowed a $2,500 withdrawal a calculated move to lull me into complacency. Encouraged, I invested an additional $75,000 over the next three weeks. Disaster struck when I attempted a larger transfer . The platform began rejecting my requests, citing vague “liquidity fees” and unverifiable fiscal requirements. Then, the scammer disappeared, erasing all traces. A blockchain audit confirmed my worst fear: the entire interface had been a mirage. My investments had been siphoned off and scattered across untraceable accounts or so I thought. Searching for help, I combed through online communities searching for a path forward. I eventually discovered Digital Tech Guard Recovery, a group of hackers who recover cryptocurrency through cyber forensics and deep crypto analysis. Their reputation, reinforced by detailed investigative reports and positive case outcomes, gave me hope. From the moment I contacted them, Digital Tech Guard Recovery approached my case with precision and professionalism. They explained how sophisticated scams exploit non-custodial wallet vulnerabilities and fake API integrations to siphon funds into crypto tumblers, concealing the trail. Using advanced tracing protocols and proprietary forensic tools, Digital Tech Guard Recovery tracked the movement of my stolen Bitcoin through a web of anonymized wallets, eventually locating the funds at an offshore exchange notorious for weak compliance. With cryptographic evidence in hand and coordination with international legal teams, Digital Tech Guard Recovery secured an emergency freeze on the assets. Within 48 hours, my funds were returned to a secure cold wallet. This was a harsh education in the dark side of digital finance. Thanks to Digital Tech Guard Recovery, I reclaimed what was lost. Now, I navigate crypto with vigilance, knowing that caution is the only true safeguard in a world where deception often wears a digital face.1 -
Hire A Cryptocurrency Fraud Recovery Hacker Service Online: VISIT CERTIFIED RECOVERY SERVICES
It started with optimism. A serendipitous encounter with an old college friend in Miami’s bustling airport led to a conversation about financial growth. He spoke glowingly of Dollar fx net, a platform he insisted had doubled his investments. Trusting his enthusiasm, I deposited 10,000 USD a substantial chunk of my job savings only to face a shocking roadblock weeks later. The platform demanded an additional 5,000 “verification fee” to unlock withdrawals. My stomach dropped; this wasn’t a hiccup it was a trap. Stress pushed me into research mode. Scouring cybersecurity forums, I uncovered countless stories mirroring mine: unregulated platforms exploiting trust, draining accounts under false pretenses. Then, a lifeline a Reddit thread praising CERTIFIED RECOVERY SERVICES for their no-nonsense approach to fund retrieval. Skeptical but out of options, I submitted a case file through their portal, hoping for a miracle. The response from CERTIFIED RECOVERY SERVICES was swift and reassuring. They outlined a comprehensive strategy: trace the digital trail of my 10,000 USD, they apply pressure on the platform through legal backchannels. Their transparency struck me while they couldn’t guarantee success, their expertise was evident. Over the next week, CERTIFIED RECOVERY SERVICES became my digital sherpa, guiding me through the murky waters of online fraud recovery. Their team meticulously decoded Dollar fx net’s obfuscated transaction logs, revealing that my funds had been funneled into offshore wallets, far from any regulatory oversight. Armed with this information, their legal team issued takedown notices to payment processors linked to the platform, effectively putting them on notice. The pressure worked: on day 10, I received a cryptic email from Dollar fx net claiming my account was “under review. "By week two, the impossible happened my original 10,000 USD reappeared in my bank account, sans the fabricated fees. CERTIFIED RECOVERY SERVICES later explained how their threat of exposing the platform’s infrastructure to regulators had forced their hand. Their relentless pursuit of justice to recover my funds and also highlighted the importance of holding fraudulent platforms accountable. This ordeal taught me two harsh truths: not all opportunities are as they seem, and due diligence is non-negotiable. Yet it also revealed heroes like CERTIFIED RECOVERY SERVICES ethical hackers who use their skills to fight back against fraud. I now understand that vigilance and the right support can turn the tide against deceit. In a world where fraudsters thrive on silence, speaking out and seeking help can be the most powerful tools in reclaiming what is rightfully yours.
Here's Their Info Below:
WhatsApp: (+1(740)258‑1417 )2 -
SEEKING HELP TO RECOVER STOLEN CRYPTOCURRENCIES HIRE ADWARE RECOVERY SPECIALIST
The world of cryptocurrency, with its promise of financial freedom and innovation, had always fascinated me—until it became the backdrop of my most painful financial loss. WhatsApp info:+12 (72332)—8343
Last year, I fell victim to a sophisticated crypto scam disguised as a “guaranteed returns” investment opportunity. What started as a confident leap into passive income quickly spiraled into disaster. In a matter of hours, years of savings vanished, along with the anonymous scammers behind it. I was left with nothing but shock, shame, and a haunting sense of betrayal.
I couldn’t stop replaying every step—every red flag I’d missed, every decision I questioned too late. Crypto forums were filled with similar heartbreaking stories, yet few offered solutions. I was beginning to lose hope.
That’s when I discovered ADWARE RECOVERY SPECIALIST.
From our very first interaction, I knew they were different. Their team combined deep technical expertise with genuine empathy—something I hadn’t expected. I wasn’t just another case number to them; they truly listened, offering reassurance that helped ease my self-blame. As one advisor told me, “These scams exploit trust, not incompetence.” That perspective changed everything.
Their forensic work in the crypto space was remarkable. They unraveled the web of how my funds were siphoned—identifying vulnerabilities in wallets and tracking the fraudsters through decentralized exchanges. Using proprietary tools and cross-platform partnerships, they followed the trail with a level of precision that inspired real hope. Telegram info: h t t p s:// t. me / adware recovery specialist1
The process wasn’t easy. There were dead ends, unresponsive platforms, and technical roadblocks. But ADWARE RECOVERY SPECIALIST never wavered. By the second day, they had already recovered $350,000 of my lost assets.
But their support didn’t stop at recovery. They empowered me—educating me on how to protect future investments, and even connecting me with a private community of other scam survivors. That network gave me strength and perspective. Email info: Adware Recovery Specialist @ auctioneer. net
Today, I’m not only financially restored, but emotionally grounded. My experience stands as proof that recovery is possible—even in the murky world of crypto scams. With the right team, the right tools, and relentless dedication, there is a way back. Website info: h t t p s:// adware recovery specialist. com
If you’ve been scammed, know this: you are not alone. There is hope. ADWARE RECOVERY SPECIALIST helped me reclaim more than just money—they helped me reclaim peace of mind.2 -
I read somewhere while at work on the internet in X that the Bitcoin lost during the Bit get breach, worth more than $5 million, has been fully recovered, thanks to the efforts of Tech Cyber Force Recovery. The breach had left many users devastated, unsure if they would ever see their funds again. However, Tech Cyber Force Recovery stepped in and successfully traced and retrieved the stolen Bitcoin, ensuring that all affected users received 100% of their lost assets. The recovery process was far from easy. The Tech Cyber Force Recovery team used cutting-edge blockchain forensic techniques to track down the stolen funds. They meticulously followed the transaction trail across multiple blockchain networks, piecing together the complex puzzle of the breach. It involved collaboration with cybersecurity experts and relevant authorities to ensure that the recovery was not only successful but also secure. The recovery efforts were particularly significant because the total value of the Bitcoin lost during the Bit get breach amounted to over $5 million. This made the task even more critical, as the amount at stake was substantial. Users who had once feared losing their investments can now rest easy, knowing that Tech Cyber Force Recovery was able to restore their assets in full. What sets Tech Cyber Force Recovery apart is not just its technical expertise but also its commitment to transparency. Throughout the entire recovery process, the team kept users informed every step of the way. This communication was crucial in maintaining trust and confidence. Many of the affected Bit get users expressed their gratitude toward Tech Cyber Force Recovery, acknowledging the team’s dedication to ensuring the recovery of their funds. In an era where digital asset security is a growing concern, this recovery serves as an important reminder of the role that blockchain forensics and recovery services play in protecting users. It also underscores the importance of having a trusted service like Tech Cyber Force Recovery available to assist in cases of breaches and theft. Their success in recovering the stolen Bitcoin, worth over $5 million, has made them a beacon of hope for users who might otherwise have lost everything. VISIT THE TEAMS ON WhatsApp +.(156)(172)(636)(97) OR TELEGRAM (AT)TECHCYBERFORC With the full recovery of the funds, users can now feel more secure about the safety of their digital assets, knowing that there are reliable and capable services like Tech Cyber Force Recovery to help when things go wrong.3
-
HIRE A GENUINE HACKER TO RECOVER LOST BTC & USDT- VISIT SALVAGE ASSET RECOVERY
I had $560,000 in Bitcoin saved up to fund my life's passion, an off-grid solar project designed to bring light to rural villages. Years of scrimping, saving, and explaining to skeptical relatives that no, Bitcoin wasn't just for internet gamblers, came down to this. But a slip of the finger almost sent my plans into eternal darkness.
Making a final transfer to consolidate my project funds, I had copied the wrong wallet address. It was so quick. One paste, one click, and my stomach dropped faster than a solar panel off a roof. My entire investment vanished into the digital ether. I stared at the screen, waiting for it to grow arms and slap me in the face. When it didn't, I knew I was in trouble.
Desperation led me to an energy summit, more for a diversion than anything. But fate has a sense of humor. During networking in a break, I heard a speaker casually mention Salvage Asset Recovery, as one might refer to a weather app, not the digital cavalry. I pounced like a man who'd seen a power outlet in the desert.
From that first call, their crew oozed competence and tranquility. They treated my busted transfer like an engineering challenge, not a personal disaster (even though I was seconds away from rechristening the project "Bit coinless in the Dark"). Using advanced blockchain tracing techniques, they mapped the Byzantine trail of transactions. I imagined them in hard hats, working the blockchain like electricians restoring downed power lines.
Each update brought hope. Eleven days in, they located the funds. Two days after that, I had it back, every Satoshi. I nearly hugged my solar panel prototype.
The Salvage Asset not only recovered my money; they future-proofed me. They walked me through address verification processes, multi-sig security, and how not to let jitters turn your dream into a nightmare. It did not come across as a lecture but more like taking advice from an older brother who went through every tech blunder imaginable.
Today, my project is charging forward (pun intended). The first village will soon bask in sustainable power. When they flip that switch, I’ll know it was made possible by hard work, a bit of luck, and the brilliance of Salvage Asset Recovery. REACH OUT TO SALVAGE ASSET RECOVERY, THIER CONTACT DETAILS
TELEGRAM---@Salvageasset
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
RECOVER YOUR STOLEN CRYPTO INVESTMENT WITH DIGITAL HACK RECOVERY EXPERTS
The dishonesty of this business knows no bounds. Everything they present is a well-constructed lie designed to strip you of your assets. Their approach is deceptively polite and persuasive, making it easy for people like me to fall into their trap. I was initially drawn in by their professional appearance and the promises of high returns on investments. They made everything sound so legitimate, offering enticing deals and assurances that everything was secure. They were experts at building trust, making it hard to question their intentions at first. I felt confident, even excited, about the potential growth of my investment. But as time passed, I started to notice red flags — subtle signs that something wasn’t right. Despite my growing doubts, I continued to trust them, hoping that the returns would eventually materialize.But, as it often happens with scammers, things began to unravel. I noticed that my funds weren’t being allocated as promised. The transactions seemed irregular, and the platform became increasingly difficult to navigate. When I attempted to reach out for clarification, my messages went unanswered. Calls were ignored, and the website’s contact information became mysteriously unavailable. Eventually, I realized the terrifying truth: I had been scammed. The company had vanished, leaving no trace behind except for a trail of broken promises and stolen investments.I was devastated. The money I had worked so hard for was gone, and I felt utterly helpless. That’s when I heard about Digital Hack Recovery. Desperate to reclaim my funds, I decided to reach out, hoping for some resolution. To my surprise, they responded swiftly and professionally, offering me a glimmer of hope. The team at Digital Hack Recovery was relentless in their efforts, working tirelessly to track down the fraudulent company and recover my money. They guided me through every step of the process, ensuring I understood my options and providing constant updates on their progress. Thanks to their expertise and determination, I was able to reclaim my investment.Though the process was difficult and frustrating, I’m incredibly grateful to Digital Hack Recovery for their unwavering support. Without their assistance, I would still be in the dark, unable to recover what I had lost. Their professionalism and commitment to helping people like me navigate the complexities of online scams gave me a second chance to regain control of my financial future. For any crypto recovery, reach out to Digital Hack Recovery through⁚ WhatsApp⁚ +1(9152)151930
Webpage⁚ https : // digital hack recovery . com
Email⁚ digital hack recovery @ techie . com1 -
SUPPORT GROUP FOR CYPTO FRAUD VICTIMS - FUNDS RETRIEVER ENGINEER
As a military woman, I’ve been trained to stay alert and think tactically, but nothing prepared me for the emotional and financial ambush I experienced online. It started innocently enough. While stationed overseas, I connected with someone on social media who claimed to be a successful crypto trader. He was charismatic, well-spoken, and incredibly supportive. Over the course of several months, he built my trust. He didn’t rush anything. We talked almost every day about life, service, family, and eventually, finances. He made me feel seen and understood, and I truly began to believe there could be a future with him. He slowly introduced me to his world of crypto investing. At first, I was skeptical. But he showed me a platform where he said he made consistent profits, even offering to help me get started. I watched my investment appear to grow rapidly on the site. It looked real. It felt real. Encouraged by what I saw and the bond I thought we had, I invested more and more until I’d put in a total of $250,000. It was everything I had saved. Then one day, he vanished. No calls. No messages. The platform stopped working. My heart sank. I knew I’d been scammed. I felt betrayed, embarrassed, and helpless. I might be tough in uniform, but behind the screen, I was just a woman who’d been deceived. That’s when I found FUNDS RETRIEVER ENGINEER. From the first call, they treated me with respect and urgency. Their team got to work immediately. They were able to trace the funds through 12 different crypto wallets, following a digital trail most would never find. Eventually, they tracked the money to a real exchange account, one that the scammer had linked to his identity. That mistake cost him.Thanks to FUNDS RETRIEVER ENGINEER expertise, $187,000 of my stolen funds were recovered before they could be laundered or hidden. They worked with international authorities and the exchange to freeze the assets in time. I’m still healing, but I’m no longer a silent victim. I’m speaking out because if it happened to me, a woman in the military, it could happen to anyone. Don’t stay silent. There’s help out there. FUNDS RETRIEVER ENGINEER gave me a second chance.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M10 -
HOW DIGITAL TECH GUARD RECOVERY CAN HELP YOU RETRIEVE LOST CRYPTO
In the depths of the digital realm, where the lines between reality and fantasy blurred, I embarked on a journey to reclaim what was rightfully mine. My name is Alex, and this is the tale of my dual triumph – the reclamation of my stolen Bitcoin and the emotional healing that followed. It all began when I received a frantic call from a friend, informing me that my cryptocurrency wallet had been hacked. Panic gripped me as I realized that my hard-earned savings, meticulously accumulated over the years, had been snatched away by the invisible hands of cybercriminals. Determined to take back what was mine, I delved into the intricate web of the digital underworld, navigating through the maze of online forums and specialized communities. It was there that I discovered the elusive "Digital Tech Guard Recovery" – a team of highly skilled experts who specialized in tracking down and retrieving stolen digital assets. I went out to the Digital Tech Guard Recovery team with a ray of optimism, sharing my situation and begging for their help. They listened carefully, which relieved me, and promised to do every effort to find and retrieve my stolen Bitcoin. The process was arduous and nerve-wracking, as the Digital Tech Guard Recovery team delved deep into the complex web of digital transactions, following the trail of breadcrumbs left by the perpetrators. It was a race against time, with each passing day filled with uncertainty and the constant fear of never seeing my hard-earned savings again. But the Digital Tech Guard Recovery team was relentless in their pursuit, employing cutting-edge technology and their vast network of contacts to unravel the intricate web of the cybercrime. And after weeks of painstaking work, they finally succeeded in tracing the stolen Bitcoin and reclaiming it from the hands of the thieves. The moment I received the news, a wave of relief and joy washed over me. Not only had I regained my financial footing, but I had also experienced a profound emotional reclamation. The trauma of having my assets stolen had weighed heavily on my mind, but with the successful recovery, I felt a sense of empowerment and closure. This dual triumph – the financial and emotional reclamation of my stolen Bitcoin – was a testament to the power of determination, resilience, and the unwavering support of the Digital Tech Guard Recovery team. It was a journey that had tested my limits, but in the end, I emerged stronger, wiser, and more confident in my ability to navigate the ever-evolving digital landscape. Contact Digital Tech Guard Recovery via: Email @ digital tech guard . com
WhatsApp: +1 (443) 859 - 2886
Telegram: digital tech guard recovery . com
website link :: https : // digital tech guard . com5 -
HIRE ADWARE RECOVERY SPECIALIST FOR ANY TYPE OF ONLINE SCAM OR TO SPY ON CHEATING BOYFRIND
Call or Text: +18186265941Catching a cheating spouse in the act can be a delicate and sensitive situation, but with the help of modern technology, the process has become more streamlined and efficient. Enter ADWARE RECOVERY SPECIALIST - a powerful tool that allows you to uncover the digital breadcrumbs left behind by a cheating wife. By harnessing the power of this advanced software, you can infiltrate her online activities and piece together a comprehensive trail of evidence. Perhaps she's been exchanging flirtatious messages on a secret social media account, or maybe she's been making frequent video calls to a mysterious new "friend." The ADWARE RECOVERY SPECIALIST program can retrieve this data, no matter how well she thinks she's covered her tracks. It can even retrieve deleted files and messages, exposing the full scope of her infidelity. With this information in hand, you'll be armed with the proof needed to confront her and get to the bottom of her betrayal. While it may be a difficult and heart-wrenching process, using ADWARE RECOVERY SPECIALIST can provide the clarity and closure needed to move forward, either by salvaging the relationship or parting ways. This technological solution offers a discrete and effective way to catch a cheating wife red-handed, giving you the power to take back control of the situation. I was glad I used their service because I cannot say how on earth I would have confronted my wife. Evidence were everywhere for me to see. I am grateful to ADWARE RECOVERY SPECIALIST for this. Contact ADWARE RECOVERY SPECIALIST for assistance.
Email info: Adwarerecoveryspecialist@auctioneer. net -
CRYPTO RECOVERY SERVICES HIRE SPARTAN TECH GROUP RETRIEVAL
In a modern twist on wedding traditions, a tech-savvy cousin of the bride set up a “blockchain gift registry,” allowing guests to send Bitcoin as wedding gifts, a gesture that reflected the couple’s shared love for innovation and the digital world. What was meant to be a celebration of love and technology quickly turned into a nightmare when it was discovered that the QR codes shared with guests had been tampered with. Instead of pointing to the couple’s wallet, they directed the generous contributions totaling a staggering $55,000 to a scammer’s address. Shocked and heartbroken, the couple found themselves ensnared in a sophisticated cybercrime. But their story didn’t end in despair. Enter SPARTAN TECH GROUP RETRIEVAL, a highly respected firm specializing in cryptocurrency tracing and digital asset recovery. The team at SPARTAN TECH GROUP RETRIEVAL demonstrated why they are leaders in the field. With forensic precision and a profound grasp of Cryptocurrency technology, they launched a comprehensive investigation into the fraudulent transactions. Their analysts employed advanced tracking algorithms, scrutinized transactional patterns, and methodically unraveled the digital trail left by the perpetrator. This relentless pursuit of justice led to the identification of a professional wedding crasher operating out of Valencia, a cunning cybercriminal who had infiltrated multiple events using similar deception. Thanks to SPARTAN TECH GROUP RETRIEVAL's unwavering diligence and collaboration with international cybercrime units, the criminal was exposed, and a substantial portion of the stolen assets was recovered. An impressive $50,000 was successfully retrieved from frozen accounts linked to the fraudster, transforming what could have been a catastrophic financial loss into a triumph of digital justice. SPARTAN TECH GROUP RETRIEVAL didn't just recover cryptocurrency; they restored dignity, trust, and peace of mind. Their exemplary work showcases not only their technical prowess but also their ethical commitment to supporting victims of cyber fraud. In an age where digital innovation often outpaces regulation, SPARTAN TECH GROUP RETRIEVAL stands as a Cryptocurrency recovery guardian.
CONTACT INFO ABOUT THE COMPANY:
Website: h t t p s : / / spartan tech group retrieval . o r g
WhatsApp: + 1 ( 9 7 1 ) 4 8 7 - 3 5 3 8
Telegram: + 1 ( 5 8 1 ) 2 8 6 - 8 0 9 2 -
Unraveling the tangled web of deception can be a daunting task, but the emerging field of "CYBER TECH WIZARD" is offering new hope for those seeking to confront the devastating impact of infidelity. This innovative approach leverages advanced digital forensics and data analysis techniques to meticulously piece together the digital trail left behind by unfaithful partners. By delving deep into smartphones, computers, and online accounts, skilled practitioners are able to uncover a startling level of detail about clandestine communications, secret rendezvous, and the complex web of lies that often accompanies infidelity. The insights gleaned from this painstaking process can be nothing short of revelatory, providing scorned individuals with the cold, hard evidence needed to confront their partner's betrayal and reclaim a sense of truth and transparency in the relationship. Yet the implications of CYBER TECH WIZARD extend far beyond the personal realm, as these techniques also hold the power to expose broader patterns of deception, manipulation, and abuse that may have remained hidden for years. As this field continues to evolve, it promises to be a crucial tool in the fight against the corrosive effects of unfaithfulness, empowering those who have been wronged to unravel the deception and forge a path towards healing and accountability. Don't wary if you have been scammed from your hard earn money you can recover them all back, call CYBER TECH WIZARD now through: Email Address cyber tech wizard @ cyber services . com
Good Day and thank me later. -
The world of cryptocurrency has long been plagued by the devastating consequences of lost or stolen digital assets, leaving countless individuals and businesses scrambling to recover their rightful funds. However, a game-changing solution has emerged in the form of Dexdert Net Pro, a revolutionary platform that is reinventing the way we approach bitcoin recovery. At the heart of Dexdert Net Pro innovative approach is a robust and multifaceted strategy that leverages cutting-edge technology, a global network of specialized investigators, and a deep understanding of the complex web of blockchain transactions. Unlike traditional recovery methods that often prove tedious, time-consuming, and ultimately fruitless, Dexdert Net Pro proprietary algorithms and investigative techniques allow them to meticulously trace the movement of stolen or misplaced bitcoins, no matter how convoluted the trail may be. By tapping into the power of machine learning and artificial intelligence, Dexdert Net Pro is able to analyze vast troves of blockchain data, identify patterns and anomalies, and pinpoint the precise location of missing funds with unprecedented accuracy. Complementing this technological prowess is a team of seasoned crypto experts and former law enforcement professionals who lend their expertise to devise innovative strategies for asset recovery, navigate legal complexities, and liaise with authorities to ensure the successful return of stolen funds. With its unwavering commitment to client satisfaction and a track record of remarkable success, Dexdert Net Pro is poised to forever transform the landscape of bitcoin recovery, providing a beacon of hope for those who have fallen victim to the perils of the digital currency ecosystem.
WhatsApp:(+1 (435) 294‑8481)Telegram:(@Dexdertprorovery)4 -
Puran Crypto Recovery: The Best Cryptocurrency Recovery Agency Helping Victims Reclaim Their Lost Assets
The Puran Approach to Recovery: A Step-by-Step Process
Recovering stolen crypto is a meticulous process that involves several critical steps. Here’s how Puran Crypto Recovery handles each case:
Initial Consultation: Puran starts by understanding the nature of the scam and gathering all relevant details from the victim. This step ensures a tailored recovery plan for each case.
Evidence Collection: Puran’s team helps victims compile essential evidence, including transaction IDs, wallet addresses, and communication records with scammers.
Blockchain Tracing: Using advanced tools, Puran traces stolen funds through the blockchain, identifying where the assets were transferred and potentially uncovering the identities of those involved.
Collaboration with Authorities: Once the funds' trail is established, Puran works with law enforcement and regulatory bodies to secure legal support for recovery.
Recovery and Resolution: The final step involves reclaiming the stolen funds and returning them to the victim’s wallet, ensuring the process is completed securely and transparently.
The world of cryptocurrency is both exciting and perilous, offering opportunities for growth but also vulnerabilities to exploitation. If you’ve been targeted by crypto thieves, don’t lose hope. With Puran Crypto Recovery, you’re in the hands of the best cryptocurrency recovery agency. Their team of experts works tirelessly to trace stolen assets, collaborate with authorities, and ensure victims recover what’s rightfully theirs.
For personalized support and expert guidance, contact Puran Crypto Recovery at purancryptorecovery@contactpuran.co.site. Visit their website at Puran.Online to learn more about their services and start your journey to recovery today.1 -
Turning the Tables: My Journey to Reclaim Stolen Bitcoins with Expert Help. When my Bitcoin wallet was hacked and my entire cryptocurrency portfolio was stolen, I felt utterly devastated and hopeless. Having worked hard to build up my digital assets, the sudden loss was gut-wrenching. It felt like my financial future had been ripped away in an instant, leaving me overwhelmed by a sense of betrayal and despair. In my search for help, I discovered TECH CYBER FORCE Recovery, a renowned cybersecurity firm specializing in cryptocurrency recovery. I was met with professionalism and empathy from my first contact with them. The team demonstrated a steadfast commitment to helping me retrieve my stolen Bitcoins. They understood the emotional toll of my situation and approached my case with genuine concern. TECH CYBER FORCE Recovery swung into action immediately, leveraging its extensive expertise in blockchain forensics and hacker tracking techniques. Their process was meticulous. They analyzed my transaction history, followed the digital trail left by the hackers, and worked diligently to pinpoint the location of the stolen funds. I was impressed by their technical prowess; they employed advanced cryptographic methods and strategic negotiations with the perpetrators, all while keeping me informed about their progress. The recovery process was complex and fraught with challenges. However, the tenacity displayed by the team was truly awe-inspiring. They navigated cryptocurrency crime's murky and ever-evolving landscape with skill and determination. After a series of strategic moves, they managed to recover the majority of my Bitcoins successfully.
WHATSAPP. +. 15_61_72_63_69_7 -
The Bitcoin Resurgence: My Unforgettable Experience with Pro Neuro Cyber Force Recovery
Recovering lost assets can be a daunting and complex process, but Pro Neuro Cyber Force Recovery’s approach offers a glimmer of hope for those seeking to recover their lost Bitcoin. Cyber Force, a renowned cryptocurrency recovery specialist, has developed a meticulous, multi-faceted strategy for tracking and recovering lost or stolen digital assets. Their approach begins with a thorough investigation, leveraging their extensive knowledge of blockchain technology and network of industry contacts to uncover the trail of missing Bitcoin. Through meticulous analysis of transaction histories, wallet addresses, and other digital trails, Cyber Force is often able to identify the last known location of the funds and the individuals or entities responsible for their disappearance. From there, they employ a combination of legal, technical, and negotiation tactics to navigate the maze of crypto regulations and recover the lost assets. This can involve everything from filing civil lawsuits and working with law enforcement to implementing specialized software and engaging in high-stakes negotiations with anonymous hackers. Cyber Force’s tenacity and resourcefulness have earned it a reputation as a formidable ally for those seeking to recover their rightful digital wealth, as evidenced by its successful recovery of the 45,000 Bitcoins at the center of this case. With its unwavering commitment and innovative approach, Cyber Force offers a glimmer of hope to those who have fallen victim to the perils of the cryptocurrency landscape. Be sure to email: for immediate support. Thank you.
WhatsApp : +1 (661) 418-4457 -
HIRE THE BEST CRYPTO RECOVERY SPECIALISTS-AUTOPSY MAINNET RECOVERY
Watching someone you care about lose almost everything is one of the hardest things to witness. This is a story about my closest friend, Mark — and how a sudden cyberattack on his crypto wallet nearly broke him. But it’s also a story of hope, and how Autopsy Mainnet Recovery helped him get back what he thought was gone forever.
Mark has always been smart with money. He was never careless or reckless, and he spent years researching and investing in crypto carefully. It wasn’t overnight success for him — he built his portfolio slowly and steadily, sacrificing weekends, trips, and luxuries to secure a better financial future. By 2025, his wallet held years of disciplined investment, and he was finally starting to feel secure.
Then, one morning, everything changed.
I remember the call. His voice was shaking. “Everything’s gone,” he said. I rushed over, thinking maybe it was a technical error, a glitch. But it wasn’t. His wallet had been hacked. Someone had drained over 90% of his funds in just a few hours. He sat there staring at the screen, completely frozen. I’ve never seen him that way before — quiet, pale, lost.
Mark was devastated. He barely spoke for days. He stopped going out. He wouldn’t eat. He couldn’t believe that in one moment, everything he worked for was taken from him. He kept blaming himself, asking how it happened, replaying every decision, every transaction. The worst part? He didn’t know where to start. The loss was too big, and the trail seemed impossible to follow.
Then one evening, I decided to do some research on his behalf. I stumbled upon a few recovery services, most of them sketchy and vague. But one name kept popping up in survivor forums and online communities: Autopsy Mainnet Recovery. People described them as trustworthy, experienced, and — most importantly — real. I convinced Mark to reach out, even though he was hesitant and exhausted.
That decision changed everything.
From the first message, the team at Autopsy Mainnet Recovery treated Mark with patience, respect, and real empathy. They didn’t judge. They didn’t offer false promises. They carefully reviewed his case, explained the recovery plan in full detail, and assigned a case manager who kept in constant contact. No upfront charges, no tricks — just professionals committed to helping someone in pain.
Within days, they began tracing the unauthorized transactions. Their team of experts worked tirelessly. They followed the digital trail, identified suspicious addresses, and used advanced techniques to initiate recovery.
After one week, the unbelievable happened: they recovered 83% of Mark’s stolen funds.
We both cried. It wasn’t just about the money — it was the fact that someone had finally stood up for him. Someone cared enough to fight, and they delivered.
If you or someone you love has lost crypto due to a hack, don’t give up. There’s still hope. Autopsy Mainnet Recovery didn’t just save Mark’s investments — they gave him his life back.
And for that, we will be forever grateful.
WhatsApp: +44 758 601 9698
Email: [ Autopsymainnetrecovery@autopsy.co.site ]2 -
Digital Hack Recovery— Stolen Ethereum Recovery Expert & Other Cryptocurrencies
It was a dark day when I realized that I had fallen victim to an Ethereum (ETH) scam. I had been so careful, or so I thought, but the cunning tactics of the scammers had caught me off guard. They had promised me a once-in-a-lifetime opportunity to double my investment, and in a moment of weakness, I had fallen for their lies. As the realization sank in, I felt a mix of emotions – anger, shame, and a deep sense of betrayal. I had trusted the wrong people, and now I was left with a gaping hole in my digital wallet. The thought of losing my hard-earned savings was devastating, and I knew I had to take action. At that point, I came into Digital Hack Recovery, a business that specializes in getting money back from online scams. I was initially dubious because, after all, how could they possibly repair the harm that had been done? However, when I learned more about their offerings, I became captivated by their reputation and the endorsements of their happy customers. I decided to take a chance and reached out to Digital Hack Recovery. From the moment I made the initial contact, I was impressed by their professionalism and attention to detail. They listened to my story with empathy and understanding, and they assured me that they would do everything in their power to help me recover my lost funds. The process began with a thorough investigation into the scam. The Digital Hack Recovery team meticulously analyzed the transaction records, the wallet addresses involved, and any other relevant information they could gather. They worked tirelessly, leaving no stone unturned, to uncover the trail of the stolen funds. As the investigation progressed, I was kept informed every step of the way. The team provided regular updates, explaining the steps they were taking and the challenges they were facing. Their communication was clear, concise, and reassuring, which helped to alleviate my anxiety and restore my trust in the process. One of the most impressive aspects of Digital Hack Recovery's approach was their innovative use of technology. They employed cutting-edge tools and techniques to track the movement of the stolen funds, tracing them through the complex web of blockchain transactions. Their expertise in this field was truly remarkable, and I was amazed by their ability to navigate the often-opaque world of cryptocurrency. As the investigation continued, the Digital Hack Recovery team encountered several obstacles. The scammers had gone to great lengths to cover their tracks, using sophisticated techniques to obscure the trail of the stolen funds. But the team remained undaunted, using their ingenuity and perseverance to overcome each challenge. Finally, after weeks of tireless work, the Digital Hack Recovery team was able to locate and recover a significant portion of my lost funds. The feeling of relief and gratitude that washed over me was indescribable. I had been given a second chance, and I was determined to make the most of it. Wait no longer, Talk to Digital Hack Recovery via" Email⁚ digital
hack recovery @ techie . com
WhatsApp⁚ +19152151930
Website⁚ https : // digital hack recovery . com19 -
Reclaiming Funds from Investment and Trading Scams Hire Adware Recovery Specialist
Losing $25,000 in Bitcoin was one of the worst experiences of my life. My wallet was hacked, and in an instant, everything was gone. The irony of crypto hit me hard, its strengths like anonymity and irreversible transactions became weaknesses. Email info: Adware recovery specialist @ auctioneer. net
I filed police reports, searched for help online, and found nothing but scams, until I discovered ADWARE RECOVERY SPECIALIST.
They stood out immediately. Their website was clear and professional, outlining real tools like blockchain analysis, wallet tracing, and exchange coordination. What gave me hope was their no recovery, no fee policy. I decided to give them a chance. Within 72 hours, they tracked the hacker’s trail across multiple wallets and exchanges. They kept me updated the entire time, breaking down every step in terms I could understand. By the third week, I got the message I thought I’d never see: my full $25,000 had been recovered. What impressed me most wasn’t just the recovery, it was how personal the process felt. My case manager was responsive, patient, and genuinely cared. Website info: h t t p s:// adware recovery specialist. com They didn’t just get my money back, they helped me rebuild trust in the crypto space. If you’ve lost funds to a crypto scam or hack, don’t give up. ADWARE RECOVERY SPECIALIST knows what they’re doing. They bring results, and they bring hope. Telegram info: adwarerecoveryspecialist56567 -
How Cryptic Trace Technologies Recovered My Stolen Bitcoin
When I discovered that $580,990 worth of Bitcoin had vanished from my wallet due to a sophisticated phishing scam, I was devastated. The anonymity and complexity of blockchain transactions made the prospect of recovery seem impossible. Traditional avenues offered little hope, and I was warned that many so-called recovery services were scams themselves. In my search for a legitimate solution, I came across Cryptic Trace Technologies. From our first interaction, their professionalism and transparency stood out. They took the time to understand the specifics of my case and explained their recovery process in detail. Utilizing advanced blockchain forensics and ethical hacking techniques, they meticulously traced the movement of my stolen funds across multiple wallets and exchanges. Their expertise and dedication were evident as they navigated the complex digital trail left by the scammers. Remarkably, within a short period, Cryptic Trace Technologies successfully recovered the entirety of my stolen Bitcoin. Their commitment didn’t end there; they also provided guidance on securing my digital assets to prevent future incidents. Their integrity, technical proficiency, and genuine concern for their clients make them a standout in the field of cryptocurrency recovery. For anyone facing the nightmare of crypto theft, I wholeheartedly recommend Cryptic Trace Technologies as a reliable and effective ally in reclaiming what’s rightfully yours. For more info check their W E B S I T E: cryptictracetechnologies (.) com or E M A I L them: Cryptictrace (@) technologist (.) com.2 -
It all started with a promise that couldn’t be ignored. Last year, I stumbled upon an online investment platform called “CryptoFortuneX” that advertised super high returns on Bitcoin and USDT investments. Their beautiful website, great customer reviews, and "24/7 expert support" sealed my decision. In two months, I had $565,000 worth of USDT invested, reassured by fake portfolio updates showing steady growth. But when I tried to withdraw my funds, excuses came: server errors, verification delays, and finally, radio silence, panic set in. I'd been scammed. Desperate, I scoured forums for solutions and discovered Dexdert Net Pro, a cybersecurity firm specializing in crypto fraud recovery. I reached out. Their team responded within hours, asking for transaction records, wallet addresses, and every scrap of communication with CryptoFortuneX, They traced my USDT through blockchain ledgers, uncovering a labyrinth of wallets designed to obscure the trail, Weeks of tension followed, The recovery wasn’t instant—it took Week of legal wrangling and compliance checks. But in the end, I regained my $565,000 USDT successfully Dexdert’s transparency amazed me, Today, I’m rebuilding, wiser and grateful for Dexdert’s tenacity. They didn’t just reclaim my money—They even provided post-recovery guidance to secure my assets, safeguarding countless others. If you’ve been scammed, don’t lose hope. But act swiftly: in the crypto world, time is the thief’s greatest ally.
Thanks to Dexdert’s For Helping Me, Contact them Via :Telegram:(@Dexdertprorecovery)1 -
HOW ADWARE RECOVERY SPECIALIST HELP ME TO RECOVER MY STOLEN BITCOIN
The aroma of mangos and gasoline still festers. I'm zigging and zagging down Bali's mad streets on a rented bike, my existence and crypto riches secure in the back of a backpack. And then? Spinning on the sidewalk, dodging airborne papayas, and a helpless victim as a thief swiped my sack from my shoulder in the mess. Inside: $310,000 in Bitcoin, ten years of digital vagabond work, and the socks I preferred. Local officials yawned, sipping sugary tea beside a whirring ceiling fan. "Suku banyak cryptonym?" they complained, inviting me to submit a report after nap time. My crypto fortune was evaporating faster than an Indian sandcastle swept by monsoon rains. WhatsApp info:+12723 328 343
Enter ADWARE RECOVERY SPECIALIST, recommended by a seasoned highway veteran on a forum thread captioned "When Your Life Gets Pirated (Literally)." Desperation compelled me to cling to hope like a guest on a broken-down scooter. Their support team didn't even raise an eyebrow at my incoherent rantings. They asked for timestamps, transaction hashes, and whatever bit of metadata Website info: http s:// adware recovery specialist. com
today's detectives use magnifying glasses instead.
As it turned out, my thief was no genius. He'd tried to wash my Bitcoin through a chain of offshore exchanges, creating a digital trail of breadcrumbs. ADWARE RECOVERY SPECIALIST engineers married blockchain forensics with GPS data from my stolen equipment, following his footsteps like a high-stakes treasure hunt. They tracked him to a cybercafe in Jakarta, where he'd fought with mixers and privacy coins, blissfully unaware that each click was being duplicated. Email info: Adware recovery specialist (@) auctioneer. net
Eleven days later, I received a screenshot: my wallet balance, refilled. No fanfare, no triumphalism, but instead a modest "Your funds are safe. I slumped into a beanbag at a Ubud coworking facility, crying and laughing in half steps, while digital nomads gave me a side-eye over their cold brews. My Bitcoin was restored. My dignity? Still missing, thanks to a viral video of me face-planting into a durian stand. Telegram info: ht tp s:// t.me/ adware recovery specialist1
ADWARE RECOVERY SPECIALIST did not outsmart a thief, but they unveiled the fragility of our virtual world. Technical sorcery coupled with sheer determination converted a dismal nightmare into a rags-to-riches tale one in which the villain is sent a blockchain paper trail and the hero wears a headset instead of a cape. Today, my backpack holds a decoy wallet and an AirTag surgically attached to my ledger. I’ll never ride a motorbike in flip-flops again, but I’ll always travel with the ADWARE RECOVERY SPECIALIST contact saved in triplicate. They’re the antidote to a world where crypto can vanish faster than a beach sunset, and where fruit vendors double as viral content creators. If your crypto ever goes rogue, skip the panic. Call the ADWARE RECOVERY SPECIALIST . Just maybe avoid Bali’s fruit stands while you’re at it.1 -
GrayHat Hacks Contractor Reclaimed My BTC in Hours
Mid last year, I thought I had stumbled upon a golden opportunity when I joined an online investment group promising substantial returns through rare NFTs. I was thrilled to invest my 1.5 BTC, valued at approximately $90,000 at the time, toward a significant venture. The group’s website appeared polished, featuring impressive testimonials and a “secure escrow” system for transactions. Confident in their credibility, I transferred my BTC to their designated wallet, anticipating the delivery of a valuable NFT. However, days stretched into weeks with only vague excuses, and then the site disappeared entirely. My wallet was empty, and the realization hit me hard: I had been duped by a sophisticated scam, losing the savings I had earmarked for my dream music studio.
In a state of panic and despair, I searched online for solutions and discovered GrayHat Hacks. Their team responded promptly. They outlined their approach, explaining that they would employ blockchain forensics to track my BTC, despite the scammers’ use of a mixing service to obscure the trail. Their team meticulously analyzed the transaction ledger, utilizing advanced algorithms to group wallets and detect patterns. After several hours of diligent effort, they successfully retrieved my BTC. Their transparency throughout the process was reassuring.
That 1.5 BTC represents more than just currency; it’s the foundation of my music studio vision, and GrayHat Hacks restored it when I had nearly lost all hope. For anyone caught up in a dubious investment scheme, they offer an invaluable service. Their expertise in blockchain technology, paired with genuine client support, sets them apart.1 -
Last year, I dove into cryptocurrency, chasing dreams of financial freedom. Bitcoin’s allure was irresistible, and I invested my savings into a platform promising exponential returns. The site dazzled with sleek design, glowing reviews, and a vibrant community. Naively, I transferred my Bitcoin, ignoring subtle red flags. Weeks passed with no returns; then the platform vanished. My savings—years of hard work—were gone. The betrayal stung deeper than the financial loss, leaving me sleepless, haunted by regret. I contacted the platform’s “support,” but silence answered. I felt foolish, my dreams shattered.
A colleague, seeing my despair, mentioned Cyberpunk Programmers, a team skilled in recovering stolen digital assets. Skeptical yet desperate, I reached out. Their response was immediate, professional, and empathetic. They explained their process—using advanced blockchain tracing and forensic tools—without overwhelming jargon. They didn’t promise miracles but instilled hope. Updates came regularly, detailing their progress in unraveling the scam’s digital trail. Their transparency eased my anxiety.
One morning, an email arrived: “Funds recovered.” Logging into my wallet, I saw my Bitcoin restored. Tears welled up—relief, gratitude, disbelief. Cyberpunk Programmers didn’t just recover my assets; they reclaimed my trust in justice. Their discreet, relentless expertise turned my nightmare into redemption. For anyone devastated by crypto scams, I wholeheartedly recommend them. They’re digital vigilantes fighting for victims, proving hope persists even in the darkest moments. Reach them at cyberpunkprogrammersdotcom.2 -
It all began in late 2024 when I fell victim to a sophisticated phishing scam. An email, seemingly from a reputable crypto exchange, prompted me to update my security settings. Unbeknownst to me, this was a trap. Within hours, my Bitcoin holdings vanished from my wallet.
Devastated, I scoured the internet for solutions. That’s when I stumbled upon NanoAethosCoinRecovery, a firm renowned for its expertise in retrieving stolen cryptocurrencies. Skeptical yet desperate, I reached out to them.
Their team responded promptly, assuring me of their commitment to assist. They explained their process: utilizing advanced blockchain analysis tools to trace the movement of stolen funds and collaborating with exchanges to freeze and recover assets.
Over the next few weeks, they provided regular updates, detailing the trail of my stolen Bitcoin. Their persistence paid off. They identified the wallet holding my funds and, through their network, managed to facilitate the return of my Bitcoin.
This experience was a stark reminder of the risks in the crypto space and the importance of swift action and expert assistance. Thanks to NanoAethosCoinRecovery, I not only recovered my assets but also gained invaluable insights into safeguarding my digital wealth.
For more information, contact:
Whatsapp: +1 (570) 229-9724
Telegram: @NanoAethos1 -
Unlock Your Frozen Funds: Expert Recovery
Mrs. Stella John had invested heavily in an online trading platform, lured by promises of astronomical returns. But when she tried to withdraw her funds, she was met with silence and inaccessible accounts. Devastated, she realized she'd fallen victim to a scam.
Desperate for help, Mrs. John turned to Wizard George Cyber Service, renowned for their expertise in cryptocurrency recovery. George, a seasoned professional, assessed her situation and devised a strategy to track down the scammers.
With precision and determination, Wizard George's team navigated the complex digital landscape, following the trail of stolen Bitcoin. After weeks of tireless effort, they successfully recovered 1.765 BTC, a staggering feat that restored Mrs. John's faith in justice.
"Wizard George Cyber Service saved me from financial ruin," Mrs. John said, grateful for their professionalism and expertise. With her recovered funds, she vowed to be more cautious in the future.
Wizard George's reputation as a crypto recovery expert spread, offering hope to others who'd fallen prey to similar scams. His team's dedication and skill had turned a dire situation into a triumphant recovery.
G mail ::: WIZARDGEORGECYBERSERVICE @ g mail dot com
WhatsApp ::: 1 (807) - (698) (-9213)2 -
The Best Bitcoin Recovery Expert to Recover Scammed Bitcoin – Visit CryptoChain Global Track
When cryptocurrency scams leave victims devastated, CryptoChain Global Track delivers professional recovery solutions through certified blockchain forensic specialists. Their team of licensed investigators employs advanced techniques to trace and recover stolen Bitcoin, providing legitimate hope for victims of fraudulent schemes.
CryptoChain Global Track's recovery process utilizes cutting-edge blockchain analysis to follow digital transaction trails across wallets and exchanges. Their forensic experts examine transaction patterns, identify wallet clusters, and pinpoint recovery opportunities through sophisticated tracking technology. This technical approach is enhanced by legal strategies when recoverable funds are located on regulated platforms.
Clients benefit from transparent operations including a success-based fee structure, ensuring payment only occurs upon fund recovery. The team maintains strict confidentiality protocols while providing regular case updates throughout the investigation. Their rapid response system prioritizes new cases to maximize recovery potential before scammers can obscure the funds' trail.
Contact the Bitcoin recovery specialists today:
Email: [ cryptochainglobaltrack @cryptochain .co .site ]
WhatsApp: +44 7 7 6 8 7 6 1 5 6 92 -
"iBolt Cyber Hacker Recovered My Crypto in Days – 100% Legit!
"I Thought My Wallet Was Gone Forever — Until I Found iBolt Cyber Hacker"
iBolt Helped Me Recover Over $50K in Lost Crypto"
"Scammed and Helpless, Then iBolt Came Through – 100% Legit!"
My Experience with iBolt Cyber Hacker"
I was scammed out of $50,000 Bitcoin through a fake trading platform. completely hopeless, contacted my banks, filed reports nothing worked. Everyone told me crypto losses were irreversible… until I found iBolt Cyber Hacker.
They are professional, responsive, and incredibly knowledgeable. I honestly didn’t expect much, but within hours, they traced the wallet address, followed the blockchain trail, and recovered my bitcoin!
I was stunned when my funds were sent back to my wallet — fast, safe, and verifiable.
If you've been a victim of a crypto scam, don’t waste time contact iBolt now. These guys are the real deal. 100% legit, no games, just results.
— Liliana O., Cancun, Mexico
Website: htt ps:// iboltcyberhack . org/ 1
1 -
So, I decided to try hosting a couple of personal projects on a VPS that accepts Bitcoin payments. Not because I’m trying to go full crypto-anarchist or anything, but honestly—it’s super convenient when I don’t feel like dealing with banks or card declines for offshore services.
Found a provider that let me pay in BTC, no ID required, and had the VPS up in under 10 minutes. Ubuntu, full root access, decent specs for the price, and no questions asked. Just how I like it.
There’s something satisfying about using Bitcoin not just as an investment but actually as a currency. Plus, hosting stuff this way gives a nice little privacy boost—no paper trail, no names attached.
Only downside? BTC transaction fees can spike randomly, and some hosts make you wait for a couple of confirmations before provisioning. But hey, trade-offs.
Anyone else experimenting with Bitcoin VPS setups? Especially curious if anyone’s self-hosting Bitcoin nodes or lightning services.2 -
Best Crypto Recovery Specialists: How to Recover Stolen Cryptocurrency – Visit CryptoChain Global Track
Professional cryptocurrency recovery services have become essential in today's digital asset landscape. CryptoChain Global Track stands as a leading solution for victims of crypto theft, offering expert recovery services through certified blockchain forensic specialists with a demonstrated track record of successful fund retrieval.
CryptoChain Global Track's recovery methodology begins with comprehensive blockchain forensic analysis. Their team of licensed investigators examines transaction histories across multiple wallets and exchanges, utilizing advanced tracking technology to follow the digital trail of stolen Bitcoin, Ethereum, and other major cryptocurrencies. This technical approach identifies critical recovery points that untrained individuals typically miss, combining forensic tracing with legal strategies when recoverable funds are located on regulated platforms.
The company's transparent operations include a performance-based fee structure, ensuring clients only pay upon successful recovery. Their specialists maintain strict confidentiality protocols while providing regular case updates, keeping clients informed throughout the investigation process. The team prioritizes rapid response to new cases, understanding that timely intervention significantly increases recovery success rates before scammers can obscure the funds' trail through mixing services or cross-chain transfers.
CryptoChain Global Track's experts specialize in complex recovery scenarios, including investment frauds, exchange hacks, phishing attacks, and DeFi exploits. Their deep understanding of blockchain transaction patterns and scam behaviors enables them to develop effective counter-strategies for fund retrieval. The company's professional certifications and ethical standards provide assurance in an industry where questionable operators frequently emerge.
For those seeking professional cryptocurrency recovery assistance, CryptoChain Global Track offers complimentary initial consultations. Their experts provide realistic assessments of recovery potential and explain the investigative process in clear, understandable terms.
With CryptoChain Global Track, victims of cryptocurrency theft gain access to premier recovery services that combine technical expertise with professional investigative methods. Their certified team delivers legitimate solutions for reclaiming stolen digital assets in today's complex crypto environment.5 -
Recovering losses from binary option fraud can be a daunting task, but hiring a professional recovery service like Tech Cyber Hacker Recovery Company can significantly improve your chances of success. Their experts specialize in locating stolen assets, including funds lost in scams.
Tech Cyber Hacker Recovery employs cutting-edge tools and methods to track and recover funds. Their team of experienced investigators utilizes blockchain analysis tools to follow the money trail. They also assist in creating detailed reports that can serve as evidence with financial institutions and law enforcement, boosting the likelihood of a successful recovery.
When choosing a recovery service, it's crucial to select a company with a solid reputation and stringent ethical standards. For reliable assistance, contact Tech Cyber Hacker Recovery Company. Email:techcyberhacker34(Att) gmail (Dot)com, WhatsApp: +1 412, 556, 6218, Telegram: @Techcyber1123 5
5 -
HOW DO I GET BACK FUNDS STOLEN FROM MY DIGITAL WALLET // CRYPT0 PANDEMIC HUNTER
I was devastated when I discovered my wallet had been hacked and 12.4 ETH stolen. It was a hell of an experience. Frantically searching for solutions, I stumbled upon Crypt0 Pandemic Hunter and decided to reach out, clinging to mere hope and desperation. From the very first interaction, their team displayed a remarkable level of professionalism and expertise.
They immediately began by analyzing blockchain network, tracing the movement of my stolen ETH with precision. They patiently explained their methods, detailing how they were utilizing advanced blockchain analytics tools and techniques to follow the digital trail. It was clear they possessed had better understanding of how hackers operate and the vulnerabilities they exploit.
They didn't give up, even when the trail seemed to grow cold. They critically tracked the ETH as it moved through various wallets and pooling tumblers, piecing together the puzzle with focus and dedication. Their communication was constant, providing regular updates and developments on the case. After much work the wallets holding my stole ETH were put on hold and the assets seized.
Thanks to their relentless efforts and specialized knowledge of blockchain forensics, Crypt0 Pandemic Hunter successfully recovered 11.3 ETH . I am so much grateful for their expertise and genuine desire to help victims. I highly recommend them to anyone who finds themselves in a similar unfortunate situation. They are truly the friends indeed in this complex crypt0 world.
Reach out to ;
cryptopandemichunter[at]consultant,com
WhatsApp: +1 (205) 3573937 1
1 -
I can’t thank CYBERPUNK PROGRAMMERS enough for their incredible work in recovering my hard-earned $520,000 in crypto. When scammers hacked into my account and stole everything, I was absolutely devastated—it felt like my world was crumbling. I’d worked so hard for that money, and in an instant, it was gone. After searching desperately for a solution, I stumbled upon CYBERPUNK PROGRAMMERS. Their stellar reputation for retrieving stolen crypto gave me a faint glimmer of hope in an otherwise hopeless situation.
From the very first contact, their team was nothing short of amazing. They were professional, empathetic, and took the time to explain the recovery process in a way I could understand. I never felt left in the dark—they kept me updated at every step, which made all the difference during such a stressful time. Their skilled programmers worked tirelessly, tracking down the scammers and piecing together the trail of my stolen funds. I couldn’t believe it when they told me they’d successfully recovered my entire $520,000. It was a moment of pure relief and disbelief.
This experience was a harsh lesson in cybersecurity, but it also showed me that there are trustworthy experts out there who can help. CYBERPUNK PROGRAMMERS didn’t just recover my money—they restored my faith in justice. I’m beyond grateful for their expertise and dedication. If you’ve fallen victim to crypto theft, I can’t recommend them enough. They’re the real deal: efficient, reliable, and incredibly skilled. Don’t hesitate to reach out to them—they turned my nightmare into a miracle.
their contact details are; WhatsApp;+18077875707
Email; cyberpunk@programmerdotnet1 -
HIRE BOTNET CRYPTO RECOVERY FOR SCAMMED BITCOIN RECOVERY ASSISTANCE
For those like yourself who have suffered the terrible loss of their digital possessions, the BOTNET CRYPTO RECOVERY service is a lifeline for victims of stolen Bitcoin. Undoubtedly, losing your 67,000 Bitcoin was a terrible and confusing experience that left you feeling helpless and unsure of how to get back what was properly yours. But the BOTNET CRYPTO RECOVERY team is adept at negotiating the intricate web of cryptocurrency theft, using their wealth of knowledge and industry connections to locate and retrieve stolen money. They can follow the digital trail left by the criminals thanks to their thorough investigation method, which frequently reveals a convoluted web of illegal activities and mysterious characters. The BOTNET CRYPTO RECOVERY specialists are in a unique position to solve the problem and pinpoint the most viable recovery paths because of their in-depth knowledge of blockchain technology and the many strategies used by cryptocurrency criminals. They exert maximum pressure and raise the likelihood of a good resolution by utilizing their connections with exchanges, law enforcement, and other important players. Their resourcefulness and tenacity are unmatched.
For individuals like yourself who have experienced the heartbreak and financial devastation of stolen Bitcoin, the BOTNET CRYPTO RECOVERY service offers hope in an otherwise bleak situation. The team's unwavering commitment to their clients and ability to navigate the complex, ever-evolving world of cryptocurrency theft makes them invaluable in the fight to reclaim what is rightfully yours. With their guidance and expertise, the path to recovering your lost 670,000 Bitcoin, and regaining a sense of financial security, becomes significantly more attainable, providing a lifeline in the face of such a daunting challenge. Please send an email to: case (@) botnet crypto recovery (.) info, Also visit their official webpage at botnet crypto recovery . ) info1 -
IS IT POSSIBLE TO RECOVER LOST OR STOLEN CRYPTO? YES! HIRE CYBER CONSTABLE INTELLIGENCE
From an online crypto forum, someone called Crypto Maxx reached out to me. He introduced himself as a reputable OTC (over-the-counter) broker and claimed to work with private clients willing to pay above market rates for fast, it felt like an opportunity I couldn’t ignore. His profile looked authentic. It featured a history of market commentary, trade discussions, and apparent endorsements from other users praising his professionalism. He also referred me to a polished escrow website, complete with SSL certification, a live chat function, and glowing client testimonials. Everything about it looked legitimate. After several conversations, I agreed to the trade and sent 2 BTC worth roughly $60,000 at the time to the escrow wallet he provided. At first, everything seemed routine. He confirmed receipt and assured me the release of funds was in progress. The broker stopped responding. The escrow site vanished overnight. His forum profile was deleted. That’s when the realization hit me: I had been scammed. Desperate to recover my funds, I reached out to Cyber Constable Intelligence, a firm renowned for its expertise in tracking and retrieving stolen cryptocurrency. Their reputation for handling complex scams gave me confidence. Cyber Constable Intelligence quickly began investigating, using their advanced digital forensics to trace the scammer’s digital footprint. Cyber Constable Intelligence's team tracked the scammer’s trail to a cybercafe in Russia and transaction histories connected to the scammer. The recovery process, led by Cyber Constable Intelligence, took several weeks and involved in-depth technical analysis, private negotiations, and strategic pressure on the scammer’s known associates. Throughout this tense period, Cyber Constable Intelligence kept me updated on my case. With Cyber Constable Intelligence’s determination and skill, the 2 BTC were eventually recovered in full. Their thorough and persistent approach made all the difference, turning a frustrating loss into a successful recovery. Without their assistance, it’s unlikely I would have seen my funds again.
VISIT THEM ON THE INFORMATION BELOW
WhatsApp: 1 252378-7611
Email Info cyberconstable@coolsite net
Telegram Info: cyberconstable5 -
RECOVERING LOST BITCOIN IS POSSIBLE WITH ADWARE RECOVERY SPECIALIST
Losing Bitcoin can be a devastating experience, whether it’s due to scams, hacking, or forgotten wallet access. Many people believe that once cryptocurrency is lost, it’s gone forever. However, that’s not entirely true. With the right expertise and advanced blockchain tracking tools, it is possible to recover lost Bitcoin—and that’s where ADWARE RECOVERY SPECIALIST comes in. WhatsApp info:+12 (72332)—8343
ADWARE RECOVERY SPECIALIST is a trusted and professional crypto recovery firm dedicated to helping individuals and businesses retrieve lost digital assets. Their team consists of highly skilled blockchain analysts, cybersecurity experts, and financial investigators who specialize in tracing stolen or misplaced cryptocurrencies. They understand the complexity of the blockchain and use advanced forensic techniques to track transactions, identify wallet addresses, and, in some cases, even work with authorities to facilitate fund recovery.
One of the biggest challenges with crypto recovery is that Bitcoin transactions are irreversible, meaning there’s no central authority to dispute fraudulent transfers. However, ADWARE RECOVERY SPECIALIST uses cutting-edge technology and investigative methods to follow the money trail, identifying where the stolen funds have been transferred. If the assets have moved to known exchanges, there may be legal avenues to reclaim them. Telegram info: h t t p s:// t.me /adware recovery specialist1
Unlike many fake recovery services that make unrealistic promises, ADWARE RECOVERY SPECIALIST operates with transparency and professionalism. They assess each case carefully, explain the recovery process in detail, and provide realistic expectations based on the situation. Their proven track record of successful recoveries has earned them a strong reputation in the crypto space. Website info: h t t p s:// adware recovery specialist. com
So, if you’ve lost your Bitcoin to fraud, hacking, or even a technical issue, don’t lose hope. ADWARE RECOVERY SPECIALIST can help you navigate the recovery process and give you the best chance of reclaiming your lost assets. Their expertise and commitment to ethical practices make them a reliable choice for anyone seeking crypto recovery services. Email info: Adware recovery specialist (@) auctioneer. net1 -
SALVAGE ASSET RECOVERY, A TRUSTED COMPANY FOR RECOVERY OF LOST BITCOIN
Contact details whats app app : +18476547096
telegram : @Salvageasset
One day, I received an email that appeared to be from Binance, urging me to verify my account for security purposes. At first glance, everything seemed legitimate: the branding, the tone of the message, and even the link included. Believing it was a standard security update, I clicked the link without hesitation. The website looked exactly like Binance’s official platform. I entered my login credentials, thinking I was doing the right thing to protect my account.Within minutes of submitting my information, I noticed something alarming. I logged into my actual Binance account and was met with a gut-wrenching surprise that my entire balance of 2.5 BTC had disappeared. My heart sank. I was in complete shock and disbelief. I had spent years accumulating that Bitcoin, saving and investing carefully. It was devastating to see it vanish in a matter of moments due to one careless click.I immediately began searching for help online. I came across dozens of articles and forums discussing crypto scams, most of which ended in financial loss with no recovery. That’s when I stumbled upon a company called Salvage Asset Recovery which claimed to specialize in tracing and recovering stolen cryptocurrency.I had heard horror stories about fraudulent recovery services that took advantage of victims. Still, I decided to take a chance and reached out to Salvage Asset Recovery. Their response was prompt and professional. The team was empathetic and walked me through their process. They assured me that they had the tools and resources to track stolen crypto and that they would begin immediately.To my surprise, they quickly traced my stolen Bitcoin to a mixing service commonly used by cybercriminals to hide their tracks. Using advanced investigative techniques, Salvage Asset Recovery followed the trail relentlessly. Throughout the process, they kept me informed, which gave me a sense of hope. Salvage Asset Recovery successfully recovered 95% of my stolen Bitcoin.If anyone finds themselves in a similar situation, I highly recommend contacting Salvage Asset Recovery. They truly changed my life, and I’m forever grateful for their help.2 -
LOOKING FOR A LEGIT HACKER OR RECOVERY SPECIALIST HIRE ADWARE RECOVERY SPECIALIST
I received what appeared to be an official email from Binance, claiming I had been selected for an exclusive Binance Visa card. The offer promised impressive perks and rewards, but there was one condition: I had to pay a “verification fee” of 20,000 BNB to activate the card. WhatsApp info:+12 (72332)—8343
The email looked convincing, and the linked website was professional and closely resembled the real Binance platform. Caught up in the excitement, I made a rushed decision and sent the payment. Telegram info: h t t p s:// t. me / adware recovery specialist1
After that, nothing happened. I didn’t receive a card or even a confirmation email. Customer support was unresponsive, and it quickly became clear—I had been scammed. The realization was devastating. I had worked tirelessly to build my crypto portfolio, and in one moment, it was all gone. Email info: Adware recovery specialist @ auctioneer. net
Desperate for a solution, I began searching for a way to recover my funds. That’s when I found ADWARE RECOVERY SPECIALIST. Unsure but hopeful, I reached out. To my surprise, their team responded almost immediately. They were professional, empathetic, and confident they could help.
Their experts used advanced blockchain forensics to trace the stolen 20,000 BNB. They followed the funds through multiple wallets and exchanges, uncovering the laundering trail. Working with authorities and security teams, they successfully froze the assets and began the recovery process.
Amazingly, within a week, ADWARE RECOVERY SPECIALIST had recovered my entire 20,000 BNB. I was shocked and incredibly relieved—I never thought I’d see that money again. Website info: h t t p s:// adware recovery specialist. com
I’m sharing this experience as a warning: crypto scams are becoming more sophisticated every day. Always verify offers, double-check URLs, and contact official support before taking action. If you’ve already fallen victim, don’t give up—help is out there.
I’m forever grateful to ADWARE RECOVERY SPECIALIST for their expertise and support, and I highly recommend their services to anyone needing assistance with crypto recovery.2 -
HIRE A PROFESSIONAL CRYPTO RECOVERY EXPERT RECOMMEND// PASSCODE CYBER RECOVERY
The brimming opportunity of the cryptocurrency space is equally matched by its hidden perils, a reality I learned the hard way when a sophisticated fake crypto arbitrage bot swindled me out of $325,000 in USDT. Like many investors, I was enticed by the promise of 15% daily returns from what appeared to be a legitimate platform, complete with polished interfaces and glowing testimonials. At first, everything seemed above board. Small “returns” were deposited into my account regularly, building my trust in the system. But when I attempted to withdraw my supposed profits, the platform disappeared without a trace. I was left stunned, panicked, and unsure where to turn. That’s when I discovered PASSCODE CYBER RECOVERY. Their expertise not only helped trace my stolen funds but also restored a measure of trust in the crypto world. The team moved swiftly, dissecting the scam’s infrastructure and tracking the fraudulent smart contract to an address cluster linked to Eastern European cybercriminals. With advanced blockchain analysis tools, they followed the trail of my USDT across a network of wallets and exchanges, pinpointing the cash-out points at major trading platforms. The most difficult part was stopping the scammers before they could fully liquidate the assets. Yet, PASSCODE CYBER RECOVERY coordination with compliance teams at the exchanges proved critical. Within just a few days, 98% of my funds were immobilized, an extraordinary accomplishment considering how rapidly stolen crypto typically vanishes. This experience proved that victims are not entirely powerless. Recovery services like PASSCODE CYBER RECOVERY , equipped with cutting-edge tools and strong industry connections, can outmaneuver even the most sophisticated fraudsters. For anyone who finds themselves in a similar crisis, know this: with the right experts, persistent effort, and some hope, it’s possible to reclaim what was taken and come out wiser. Cryptocurrency remains a landscape of vast potential, but the risks are very real. Vigilance is key and when disaster does strike, there is a path forward. Recovery is not just possible; it’s real with PASSCODE CYBER RECOVERY.
PASSCODE CYBER RECOVERY
WhatsApp: +1(647)399-4074
Telegram : @ passcodecyberrecovery
Regards
Eric Norman2 -
CRYPTOCURRENCY TRACING AND FUNDS RECOVERY CONSULT DUNAMIS CYBER SOLUTION
The cryptocurrency space, with its dizzying promises of financial freedom, had always intrigued me until it became the stage for my deepest disillusionment. Last year, I fell victim to an elaborate crypto scam that stripped me of years’ worth of savings. What began as a confident investment in a "guaranteed returns" scheme unraveled into a nightmare. Overnight, my portfolio vanished, along with the anonymous fraudsters who orchestrated the ploy. The aftermath was a toxic blend of anger, shame, and helplessness. I questioned every decision, replaying red flags I’d naively ignored. Crypto forums offered little solace, filled with eerily similar stories of irreversible losses. Just as I resigned myself to defeat, a glimmer of hope emerged: DUNAMIS CYBER SOLUTION.From the outset, their team stood apart by blending technical precision with unwavering compassion. Rather than treating my case as a faceless ticket, they approached it with a commitment to understanding the human toll of the scam. During initial consultations, they listened patiently to my story, offering reassurance that shifted my mindset from despair to cautious optimism. “These scams thrive on exploiting trust, not incompetence,” one advisor emphasized a perspective that dissolved my self-blame.DUNAMIS CYBER SOLUTION mastery of Cryptocurrencies forensics became evident as they untangled the digital maze of my stolen assets. They decoded how fraudsters manipulated wallet vulnerabilities and decentralized exchanges to obscure the trail, leveraging proprietary tools and cross platform collaborations to trace the funds.Over three days, their transparency became my anchor. Regular updates demystified their process, flagging suspicious transactions, and piecing together patterns linked to earlier scams. Challenges arose dead-end leads, unresponsive third parties but the team navigated each obstacle with tenacity. By second day, they’d recovered $350,000 of my assets.Beyond recovery, DUNAMIS CYBER SOLUTION prioritized empowerment. They equipped me with resources to safeguard future investments and connected me to a private forum of survivors, fostering a community of shared resilience. Today, I’m not only financially restored but fortified with hard-earned wisdom. My situation proves that loss isn’t always permanent. With cutting-edge expertise and relentless advocacy, redemption is attainable. Let my journey remind you: even in Cryptocurrency opaque wilderness, a path back exists and DUNAMIS CYBER SOLUTION lights the way.2 -
I never knew I would fall victim to a scam, especially not in the fast-paced world of cryptocurrency. When I came across an opportunity to appear on a crypto podcast, I was excited. The promise of exposure and the chance to connect with like-minded individuals in the crypto community seemed too good to pass up. The podcast appeared legitimate, complete with a professional website, glowing testimonials, and a polished social media presence. I felt confident that this was a step forward for my career.After some back-and-forth communication with the supposed host, I was convinced to pay $9,500 to secure my spot on the show. I imagined the doors this opportunity would open for me new connections, potential partnerships, and a boost in credibility. However, after I made the payment, everything changed. The communication I had enjoyed suddenly stopped. My emails went unanswered, and the podcast’s website vanished into thin air. I was left feeling devastated and foolish.In my desperation, I began searching for help and stumbled upon CHAINTRACE ASSET RECOVERY. I was skeptical at first, but I had nothing to lose. I reached out to them, and to my surprise, they took my case seriously. Their team of experts began investigating the scammer, employing advanced tracking techniques to uncover the digital trail left behind. I watched as they worked diligently, piecing together the puzzle of my lost funds.To my amazement, CHAINTRACE ASSET RECOVERY WHATSAPP : +1 (581) 256‑1989 was able to trace the scammer and recover 95% of my money. The relief I felt was overwhelming. Not only did I regain most of my lost funds, but I also learned a valuable lesson about the importance of due diligence in the online space. This experience has made me more cautious and aware of the potential pitfalls in the cryptocurrency world. While I wish I had never fallen for the scam, I am grateful for the support I received from CHAINTRACE ASSET RECOVERY. Their expertise not only helped me recover my money but also empowered me to share my story. I hope that by speaking out, I can help others avoid the same fate and encourage them to be vigilant when navigating the exciting yet risky landscape of cryptocurrency.2
-
It started with a leap of faith—one that nearly cost me everything, last month I stumbled across an investment platform promising “guaranteed high returns” on cryptocurrency holdings. Skeptical but tempted, I poured my entire Bitcoin wallet—worth $190,000 in USDT—into their “elite portfolio,” convinced I was on the brink of financial freedom then, disaster struck, The platform’s interface suddenly went dark. Phone numbers disconnected. Emails bounced back. Panic set in as I realized I’d been scammed. My savings, tied up in a digital currency I couldn’t access, vanished into the ether. For weeks, I spiraled: filing police reports, pleading with blockchain support teams, and scouring online forums for answers. Most responses were bleak. “Crypto scams are irreversible,” But I refused to surrender, During a late-night Google deep dive, I discovered "Dexdert Net Recovery" a cybersecurity firm specializing in crypto asset retrieval. Their website testimonials detailed eerily similar stories, with claims of recovering funds even from “untraceable” scams. Desperation outweighed doubt. I submitted a case file, attaching transaction records, wallet addresses, and every shred of evidence I had.
Within hours, Dexdert Net Pro Recovery responded calmly but urgently: “The longer we wait, the harder recovery becomes. Let’s move.” Dexdert’s team launched a forensic investigation, tracing my USDT through a labyrinth of dummy wallets and offshore exchanges. They explained how the scammers used “chain-hopping” to obscure the trail, bouncing funds across multiple blockchains. But Dexdert’s tools were sharper, Over two weeks, Their experts updated me daily, Dexdert Net Recovery forced the scam platform’s hosting provider to freeze the wallet. Within 48 hours, my $190,000 USDT streamed back into my secure wallet. The relief was visceral—a physical weight lifted off my chest, Today, my Bitcoin sits in a cold wallet, guarded by layers of encryption. I share my story not just as a cautionary tale, but as proof that even in the Wild West of crypto, hope—and the right team—can rewrite endings.
Thanks to Dexdert’s Net Recovery, I reclaimed more than just money—I reclaimed trust in the system.
Contact Dexdert Net Recovery Via:
WhatsApp: (+1 (859) 609‑4156)
Telegram: (@Dexdertprorecovery)2 -
I’ve always been cautious with my finances, but the promise of high returns in the crypto world drew me in. I invested $390,000 into what I believed was a legitimate Bitcoin investment platform. Initially, everything seemed promising—the returns looked incredible, and the dashboard showed my portfolio growing daily. However, when I attempted to withdraw my earnings, the site became unresponsive. Emails went unanswered, and my funds appeared to vanish without a trace. I was devastated. My trust in digital finance was shattered, and countless sleepless nights followed as I researched recovery options. That’s when I discovered SANTOSHI HACKERS INTELLIGENCE (SHI) through an online forum. Many others shared similar stories of loss but spoke highly of SHI’s ability to recover their stolen assets. Though skeptical, I reached out to them, clinging to hope. From my very first interaction with the SHI team, I was struck by their professionalism and genuine empathy. They took the time to understand my situation, asking detailed questions about my transactions and communications with the scam site. Their approach was meticulous and transparent, explaining step-by-step how they would trace blockchain transactions to uncover the trail left by the scammers. The process wasn’t instantaneous, but SHI regular updates and clear communication gave me confidence. Using advanced blockchain analytics, they traced my $390,000 through multiple disguised addresses used by the scammers. Weeks of effort culminated in incredible news: SHI had located a significant portion of my funds. Through their expertise and collaboration with legal teams and cryptocurrency exchanges, SHI recovered 75% of my initial investment. This outcome was beyond what I had dared to hope for. More importantly, SHI didn’t just recover my funds—they provided invaluable education on securing digital assets. They taught me about wallet security, the importance of due diligence in investments, and recognizing red flags in too-good-to-be-true platforms. What could have been a devastating financial loss became a powerful lesson in resilience and cybersecurity, thanks to the exceptional team at SANTOSHI HACKERS INTELLIGENCE. I am immensely grateful for their support and expertise. For anyone seeking trusted cryptocurrency recovery services, I wholeheartedly recommend SHI.8
-
Recovering From A Wrecking Hack With The Help Of LEE ULTIMATE HACKER
After a mind wrecking hack, recovery of a bitcoin holding can be a cumbersome and a complex process, but with the right knowledge and skill it’s very doable ,I was a victim of a very skilled cyberattack they instantly made my digital assets to disappear in a blink of an eye from my cryptocurrency wallet. i was torn and in despair and I was in panic and desperation i didn’t know where to put my head so I dove research mode and went on all the sites on recovery , that’s where I came across LEE ULTIMATE HACKER service that was renowned for the most complex recovery and retrieval of stolen cryptocurrency. After I made contact with their staff they were very keen and empathetic with my situation ,they carefully analyzed with specific my predicament. The Lee specialist started the recovery process of my stolen money with haste traversing the complex world of crypto currency transaction by utilizing their extensive experience and understanding of blockchain technology ,hacking techniques. They pursed the digital trail of my stolen funds with resolve revealing the intricate network of wallets and exchangers the had deployed to hide their activities. The Lee Ultimate team was able to swiftly locate my missing assets using their advanced investigative methods and state of the art equipment which made the whole process a success. what made Lee Ultimate hacker team different from other recovery experts was they collaborated with law enforcement making sure the criminals were brought to book. I was overjoyed because all my stolen crypto currency were successfully recovered and restored to my account. I could finally have a sigh of relief and exhale after that traumatic experience all thanks to Lee Ultimate Hacker Team.
For more insight and kindly contact :L E E U L T I M A T E H A C K E R @ A O L . C O M
T e l e g r a m : L E E U L T I M A T E
W h a t s A p p + 1 ( 7 1 5 ) 3 1 4 - 9 2 4 83 -
EFFORTLESS BITCOIN RETRIEVL WITH, DIGITAL TECH GUARD RECOVERY
Behind the Scenes: The Professional Recovery Process of my lost bitcoin by Digital Tech Guard Recovery is a fascinating look into the intricate and high-stakes world of digital asset recovery. When faced with the devastating loss of valuable cryptocurrency, many individuals feel helpless and unsure of where to turn. However, the expert team at Digital Tech Guard Recovery has developed a meticulous, multi-step process to track down and retrieve even the most elusive of lost or stolen bitcoins. The recovery journey begins with a thorough investigation, as the Digital Tech Guard Recovery analysts meticulously comb through transaction histories, blockchain data, and other digital footprints to pinpoint the location of the missing funds. This sleuthing work requires an advanced understanding of cryptocurrency protocols, wallet structures, and the ever-evolving tactics used by cyber criminals. With patience and persistence, the team is able to follow the trail, no matter how convoluted, gradually closing in on the lost assets.
Contact with WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram : digital tech guard recovery . com
website link :: https : // digital tech guard . com
The delicate extraction stage follows, during which the Digital Tech Guard Recovery experts must use specialized tools and negotiate intricate security measures to gain secure access to the compromised wallet or account. To prevent further loss or damage, this procedure requires a high degree of technical proficiency in addition to painstaking attention to detail. The group works hard, employing state-of-the-art methods to get past encryption, get login credentials, and start the process of recovering the money that belongs to them. To wrap up what is frequently a difficult and nerve-racking process, the recovered bitcoin is carefully checked, cataloged, and given back to the appreciative customer. The Digital Tech Guard team makes sure their clients feel educated, empowered, and confident during the entire recovery process by offering them caring support, frequent updates, and total transparency. These digital asset recovery experts are a true ray of hope for people dealing with the terrible effects of cryptocurrency loss because of their unmatched knowledge and unshakable dedication. For more information contact them via following instructions.3 -
After a catastrophic hack, recovering one's bitcoin holdings can be a difficult and complicated process, but it is possible to recover what was lost with the correct advice and knowledge. In my situation, I was the victim of a very skilled cyberattack that caused my digital assets to instantly disappear from my cryptocurrency wallet. As I struggled with the fact that my financial security had been torn away, panic and despair crept in. But I didn't lose hope, and after doing a lot of research, I found Lee Ultimate Hacker service that is well-known for its capacity to locate and retrieve stolen cryptocurrency. When I contacted their staff, they listened carefully to the specifics of my experience and responded in a kind and sympathetic manner. The Lee specialists started painstakingly tracking the movements of my stolen money, traversing the complex world of cryptocurrency transactions, by utilizing their extensive understanding of blockchain technology and hacking techniques. They pursued the digital trail with unwavering resolve, revealing the intricate network of wallets and exchangers the hackers had employed to hide their activities. The Lee Ultimate team was able to locate my missing assets using their advanced investigative methods and state-of-the-art equipment, which paved the way for the recovery procedure.
What followed was a delicate and intricate operation, as the Lee professionals collaborated with law enforcement agencies and cryptocurrency exchanges to freeze the illicit funds and initiate the retrieval process. This involved navigating a maze of legal and technical hurdles, but the team's expertise and persistence paid off, and eventually, I was overjoyed to see my cryptocurrency holdings restored to my rightful wallet. The sense of relief and restored peace of mind was palpable, and I am forever grateful to the Lee team for their tireless efforts in guiding me through this harrowing ordeal and helping me reclaim what was rightfully mine. For more insight; L E E U L T I M A T E H A C K E R @ A O L . C O M
t e l e g r a m : L E E U L T I M A T E
w h @ t s a p p + 1 ( 7 1 5 ) 3 1 4 - 9 2 4
8 -
I want to share an incredible story of redemption and technological prowess that transformed my life after I fell victim to a devastating Bitcoin investment scam.Last year, I was enticed by the promise of high returns from what seemed like a legitimate crypto investment platform. I was so convinced and invested my life savings of $143,000, only to realize weeks later that it was a scam when I couldn't withdraw my supposed earnings. The platform went silent, and my funds vanished. Feeling helpless and with my savings gone, I scoured the internet for solutions.
That's when I discovered Alpha Spy Nest, a company renowned for their expertise in digital asset recovery. Here’s how they turned my misfortune around. Alpha Spy Nest's team of blockchain analysts meticulously reviewed my transaction history. They used advanced tracking technologies to follow the trail of my lost Bitcoin through multiple blockchain layers.Their connections with law enforcement and blockchain forensic experts allowed them to identify the scam operation's tactics. They worked tirelessly, coordinating with international bodies to freeze the assets linked to the scam. After weeks of relentless effort, they located a significant portion of my investment. Alpha Spy Nest managed to recover 90% of my lost funds, which was far beyond what I had hoped for. I am now back on my feet, thanks to the exceptional work of Alpha Spy Nest. Their professionalism, dedication, and transparency throughout the process were unparalleled. If you or someone you know has suffered from a crypto scam, I highly recommend turning to Alpha Spy Nest for help. They not only restored my financial stability but also my faith in the potential for justice in the digital age. Contacts: WhatsApp: +14159714490 1
1 -
BEST CRYPTO RECOVERY EXPERT FOR CRYPTO TRACING AND RECOVERY 2025/ TRUST GEEKS HACK EXPERT
The intricate realm of cryptocurrency, where fortunes are created and obliterated in moments, the threat of fraud looms constantly. Like many others, I ventured into Bitcoin investment with cautious optimism, only to fall prey to an elaborate ruse orchestrated by cunning cybercriminals. Their scheme was masterfully executed: polished contracts, a convincing air of legitimacy, and a curated chorus of so-called investors praising the venture’s success. Enticed by the mirage of exponential returns, I committed my capital only to see it vanish into the digital void. The aftermath was a deeply distressing blend of helplessness and regret. Amid the despair, a beacon of hope emerged: TrustGeeks Hack Expert. Renowned for their unmatched expertise in blockchain forensics and digital asset recovery, their team displayed a remarkable combination of technical precision and relentless resolve. From the start, their process was meticulous, analyzing every detail of the fraudulent transaction trail, using advanced tools to pierce through the elaborate concealment tactics of the scammers, and maintaining full transparency at every step. What truly sets TrustGeeks Hack Expert. apart in a field flooded with empty promises is their unwavering integrity. In an industry rife with opportunists, their dedication to ethical asset recovery is a refreshing anomaly. Against all odds and within a surprisingly short span, they accomplished the seemingly impossible, recovering my stolen Bitcoin and restoring my confidence in the promise of decentralized finance. To anyone grappling with the aftermath of a crypto scam,: TrustGeeks Hack Expert. is more than a service provider; they are a vital ally in the fight against digital deception. You can contact them if you require their services, E m a i l :Trust geeks hack expert {@} f a s t s e r v i c e {.} c o m __ T e l e g r a m ID Trustgeekshackexpert And W h a t s A p p + 1-7-1-9-4-9-2-2-6-9-32 -
HOW TO FIND A LEGITIMATE CRYPTO RECOVERY COMPANY; BEST CRYPTO RECOVERY EXPERT HIRE CYBER CONSTABLE INTELLIGENCE
In a moment of excitement, I fell for a crypto scam after replying to a hacked tweet account, and it cost me a staggering $340,000. I was devastated and felt like I'd lost everything. The emotional toll was overwhelming, and I didn't know where to turn. I felt like I'd been punched in the gut, and the stress was taking a toll on my relationships and overall well-being. Desperate for help, I turned to online forums, searching for a solution. That's when I stumbled upon Cyber Constable Intelligence. I was skeptical at first, but their website and reviews suggested they were the real deal. I decided to take a chance, and boy, am I glad I did! Their expertise in cryptocurrency forensics and blockchain analysis is unparalleled. They worked tirelessly to track down the scammers, following a trail of digital breadcrumbs that led them to the culprits. Their professionalism ensured a successful recovery, and I was amazed by their dedication to client satisfaction. From the initial consultation to the final recovery of my funds, they kept me informed every step of the way, supporting me through a difficult time. Their results-driven approach is truly exceptional, and what I appreciated most was their transparency, empathy, and commitment to delivering results. They didn't just recover my funds; they also provided me with peace of mind and a sense of closure. I'm grateful for their help and highly recommend them to anyone who has fallen victim to crypto scams or theft. They truly are the experts in crypto recovery, and their services can be a game-changer for those in need. Don't hesitate to reach out to them if you're struggling to recover your lost funds – they're the real deal, and they'll fight tirelessly to get your money back. Trust me, you won't regret it
Here's their Info below;
WhatsApp: 1 252378-7611
Email Info cyberconstable@coolsite net
Telegram Info: + 1 213 752 74871 -
EXPERT IN RECOVERING LOST CRYPTO ASSETS | CRYPTOCHAIN GLOBAL TRACK
When digital assets vanish due to sophisticated scams or theft, professional intervention becomes critical for recovery. CryptoChain Global Track delivers expert cryptocurrency recovery services through certified blockchain forensic specialists who combine technical expertise with legal strategies to trace and reclaim stolen funds.
The recovery process begins with comprehensive blockchain analysis, where investigators examine transaction histories across multiple wallets and exchanges. Using institutional-grade tracking technology, they follow the digital trail of stolen Bitcoin, Ethereum, USDT and other cryptocurrencies, identifying patterns that reveal fund movement. Their methodology proves particularly effective against investment scams, exchange hacks, and phishing attacks where assets have been moved through complex networks.
What sets CryptoChain Global Track apart is their multi-phase recovery approach. After identifying recoverable funds, their team initiates formal procedures through proper legal channels when assets are located on regulated exchanges. This dual technical and legal strategy has successfully recovered millions in digital assets for clients worldwide.
Clients benefit from transparent engagement terms including a "no recovery, no fee" policy that eliminates financial risk. The team maintains strict confidentiality while providing regular case updates, ensuring clients remain informed throughout the process. Their specialists emphasize rapid response, as recovery success rates decline significantly when scammers move funds through mixing services or cross-chain bridges.
The company has particular expertise in tracing assets involved in DeFi exploits, fraudulent ICOs, and fake investment platforms. Their forensic capabilities extend to following funds across multiple blockchains, including Ethereum, Binance Smart Chain, and Polygon networks.
For professional assessment of crypto recovery possibilities, CryptoChain Global Track offers complimentary case evaluations. Their experts provide realistic recovery estimates and recommended actions before formal engagement.
With CryptoChain Global Track, victims of cryptocurrency theft gain access to professional-grade recovery services that combine cutting-edge blockchain forensics with proven asset recovery strategies. Their expert team delivers legitimate solutions for reclaiming stolen digital assets.4 -
Best Recovery Expert For ETH, BTC And USDT: HIRE CERTIFIED RECOVERY SERVICES
In a modern twist on wedding traditions, a tech-savvy cousin of the bride set up a “blockchain gift registry,” allowing guests to send Bitcoin as wedding gifts a gesture that reflected the couple’s shared love for innovation and the digital world. What was meant to be a celebration of love and technology quickly turned into a nightmare when it was discovered that the QR codes shared with guests had been tampered with. Instead of pointing to the couple’s wallet, they directed the generous contributions totaling a staggering $55,000 to a scammer’s address. Shocked and heartbroken, the couple found themselves ensnared in a sophisticated cybercrime. But their story didn’t end in despair. Enter CERTIFIED RECOVERY SERVICES, a highly respected firm specializing in cryptocurrency tracing and digital asset recovery. The team at CERTIFIED RECOVERY SERVICES demonstrated why they are leaders in the field. With forensic precision and a profound grasp of Cryptocurrency technology, they launched a comprehensive investigation into the fraudulent transactions. Their analysts employed advanced tracking algorithms, scrutinized transactional patterns, and methodically unraveled the digital trail left by the perpetrator. This relentless pursuit of justice led to the identification of a professional wedding crasher operating out of Valencia a cunning cybercriminal who had infiltrated multiple events using similar deception. Thanks to CERTIFIED RECOVERY SERVICE’s unwavering diligence and collaboration with international cybercrime units, the criminal was exposed, and a substantial portion of the stolen assets was recovered. An impressive $50,000 was successfully retrieved from frozen accounts linked to the fraudster, transforming what could have been a catastrophic financial loss into a triumph of digital justice. CERTIFIED RECOVERY SERVICES didn't just recover cryptocurrency they restored dignity, trust, and peace of mind. Their exemplary work showcases not only their technical prowess, but also their ethical commitment to supporting victims of cyber fraud. In an age where digital innovation often outpaces regulation, CERTIFIED RECOVERY SERVICES stands as a Cryptocurrency recovery guardian. 2
2 -
I never imagined that I would fall for a scam, much less one that seemed so professional and convincing. Glossy presentations, positive reviews, and what appeared to be a genuine chance in the rapidly expanding cryptocurrency market enticed me, like many others, to participate in the Hyperverse plan. Believing that I was safeguarding my financial future, I deposited $130,400, a significant portion of my life savings. But as soon as withdrawals were prohibited, support stopped responding, and I became aware that I had been duped, things began to seem strange. It was disastrous. I was ashamed to even tell my friends or family because I felt angry with myself. I reported to every authority I could find for months in an attempt to get my money back, but to no avail. I had almost lost hope until I came across WIZARD JAMES RECOVERY COMPANY in an internet scam recovery community. I reached out, skeptical yet desperate. They showed me sympathy and respect right from the first email. Their team of experts was knowledgeable on digital forensics, blockchain traceability, and the workings of these schemes. They took me through their steps, which include collecting transaction information, tracking down wallets, and collaborating with foreign partners to track down the money trail. Although it took 92 hours, I received an email that made me cry: they had successfully recovered a sizable amount of my stolen cryptocurrency. $125,000 had been found and moved to my safe wallet. In addition to getting my money back, WIZARD JAMES RECOVERY COMPANY gave me back my peace of mind and sense of fairness. They also taught me how to stay away from frauds like this one in the future. Don't suffer in silence if you've fallen victim to Hyperverse or any other cryptocurrency scam. There is genuine assistance available, and you would be wise to get in touch with James using: Wizardjamesrecovery @ usa . com is the email address.2
-
How To Restore Investments From Scammers // Cryptic Trace Technologies
Last year, my mother’s life took a heartbreaking turn when she unknowingly invested her entire retirement savings into what turned out to be a fraudulent scheme. It promised incredible returns, claiming to be a revolutionary financial opportunity. One of the platforms she trusted was similar to Mirror Trading International (MTI) — a crypto-based investment program that lured people in with convincing testimonials and fake trading reports. My mom, hoping to secure a comfortable future after years of hard work, watched helplessly as her savings disappeared into thin air. The aftermath was devastating. I remember the nights she’d sit quietly in the living room, staring at old bank statements, blaming herself for being too trusting. She felt embarrassed, broken, and hopeless. We tried everything — filing reports, reaching out to authorities, even speaking to lawyers — but every lead felt like a dead end. The people behind the scam had covered their tracks so well it felt like chasing shadows. It was one of the most helpless feelings, watching someone you love fall apart because of the cruelty of strangers. Just when we were about to give up, a friend told us about Cryptic Trace Technology, a recovery service specializing in tracing lost funds from scams and cryptocurrency fraud. Skeptical but desperate, we reached out — and to our surprise, they responded with care, empathy, and a clear plan of action. We reached out to them via their E M A I L : Cryptictrace (@) technologist (.) com. Their experts used advanced tracing tools to follow the digital trail, uncovering accounts and transaction histories we thought were long gone. Four days later, they recovered my mom’s stolen investments in full. The day we received confirmation, my mother broke down in tears — not because of the money, but because someone had finally fought for her when she thought no one would. It was a moment of hope we’ll never forget. Thank you Cryptic Trace Technologies. Be blessed.1 -
WIZARD JAMES RECOVERY: A sympathetic advocate for recovery with knowledge of sustainable recovery.
Recovering one's bitcoin holdings following a devastating breach can be a challenging and complex procedure, but with the right guidance and information, it is possible to get back what was lost. In my case, a highly competent cyberattack resulted in the instantaneous loss of my digital assets from my cryptocurrency wallet. Panic and sorrow began to set in as I battled with the realization that my financial stability had been shattered. I didn't give up, though, and after much investigation, I discovered Wizard James Recovery, a company renowned for its ability to track down and recover stolen cryptocurrency. When I spoke with their employees, they listened intently to the details of my situation and gave me a warm, understanding response. Using their deep knowledge of blockchain technology and hacking methods, the Wizard James experts began meticulously following the whereabouts of my stolen funds as they navigated the intricate world of cryptocurrency transactions. They relentlessly followed the digital trail, uncovering the complex web of exchangers and wallets the hackers had used to conceal their actions. The recovery process was made possible by the Wizard James Recovery team's utilization of cutting-edge equipment and sophisticated investigative techniques to find my missing valuables. In order to freeze the illegal funds and begin the retrieval procedure, the Wizard James Recovery specialists worked with law authorities and cryptocurrency exchanges in a delicate and complex operation. I was thrilled to see my cryptocurrency holdings returned to my legitimate wallet after overcoming a complex web of legal and technological obstacles thanks to the team's knowledge and perseverance. I will always be grateful to the Wizard James Recovery team for their unwavering efforts in helping me get back what was properly mine and leading me through this terrifying experience. The sense of relief and restored peace of mind was evident. For additional information:
WIZARDJAMESRECOVERY @ USA . COM
telegram:WizardJamesRecovery
wh@tsapp + 4 4 7418 3672041 -
Soft wear tech is a platform designed to help you recover lost coins, wallets, and cryptocurrencies.
When thieves stole a staggering $900,000 worth of Bitcoin from my digital wallet, I was devastated. As an experienced cryptocurrency investor, I had always taken pride in my security measures, believing my assets were safe. Nonetheless, these skilled hackers breached my defenses and made off with my hard-earned digital coins, leaving me not only with a significant financial loss but also with a feeling of violated trust and security.
Refusing to let the criminals get away with their actions, I took immediate steps to address the situation. I reported the theft to the authorities, fully aware that tracing cryptocurrency transactions is notoriously difficult. However, I was determined to pursue every avenue available. That’s when I discovered the innovative services offered by SOFT WEAR TECH, a company specializing in tracking and recovering stolen digital assets.
The dedicated team at SOFT WEAR TECH quickly sprang into action, meticulously analyzing the blockchain transaction data to follow the money trail. Thanks to their exceptional investigative skills and cutting-edge tools, they were able to pinpoint the location of my stolen Bitcoin and initiate the recovery process. It was a long and arduous battle, with the thieves attempting to cover their tracks and move the funds. Yet, the SOFT WEAR TECH team remained resolute, outsmarting the criminals at every turn.
After weeks of relentless effort, they successfully reclaimed my $900,000 in Bitcoin and returned it to me. I was overjoyed—not only was my investment restored, but I also felt a sense of triumph over those who thought they could escape unscathed. This experience has heightened my vigilance and commitment to security in cryptocurrency investing, and I am deeply grateful to have had the SOFT WEAR TECH team fighting to protect what belongs to me.
For inquiries, feel free to reach out via
Email: softweartech5@gmail.
Email: softewar.tech@yandex
Phone : +1 9594003352 -
Two months ago, I became the victim of a highly convincing online scam that cost me $180,000 worth of Bitcoin. It started with what looked like a legitimate crypto investment platform, professional branding, fake success stories, and even fake chat support that responded in real time. Everything appeared real, until it wasn’t, I invested slowly at first, but as I saw fake profits showing up on the dashboard, I sent more Bitcoin believing I was making a smart move. When I finally tried to withdraw some funds, everything changed. They demanded more deposits to unlock withdrawals, then stopped responding altogether. Eventually, the site disappeared. I was devastated. My wallet had been drained, and every attempt to recover the funds led to dead ends, until someone mentioned Dexdert Net Recovery. I contacted them out of desperation, not expecting much. But from the very first call, I felt like I had found people who actually understood the blockchain, fraud patterns, and recovery process. Dexdert’s team got to work immediately, launching a forensic investigation into the wallet addresses and transaction trail. To my surprise, they identified the scammer’s laundering network and traced the stolen Bitcoin through various exchanges and wallets. With their partnerships and legal network, Dexdert initiated a recovery operation, After weeks of consistent work, verification, and negotiations. Dexdert successfully reclaimed my lost BTC. That’s over $180,000 back in my hands, something I had written off as impossible. If you’ve lost crypto to fraud, don’t give up. There are real professionals out there who can help and for me, that was Dexdert Net Recovery. For me, Dexdert Net Recovery didn’t just recover my Bitcoin, they helped me reclaim peace of mind.
CONTACT INFORMATION:
Telegram: (@Dexdertprorecovery) WhatsApp: (+1 (859) 609‑4156)2 -
DIGITAL TECH GUARD RECOVERY / FASTEST CRYPTOCURRENCY RECOVERY EXPERT
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard . com
Website link: digital tech guard . com
The scent of freshly brewed espresso and vintage Led Zeppelin records should have been my retirement anthem. But I was hunched over a computer in my still-under-construction vinyl record cafe, screaming at a blockchain explorer as if it just ridiculed my acoustic session. My life savings, $430,000 worth of Bitcoin, carefully earned over a decade of writing alt-rock ballads for car commercials, vanished into thin air. The culprit? Some smooth "investment manager" who'd promised me "Taylor Swift-level returns" on crypto staking, then bailed faster than my band's 2008 reunion tour. The scam was a cringe symphony. Guy had a LinkedIn profile dotted with adjectives such as "Web3 maestro" and "DeFi virtuoso," an autotuned elevator jazz playing website, and a contractual loophole big enough to drive a tour bus through. I signed over access like a groupie handing over backstage passes. Poof. Gone. Money. My café's espresso machine sat in its box, accusatorially. My spouse said I needed to "get a real job again." Even my dog gave me the side eye. Enter my drummer, Chad, a guy who had escaped a festival pyro tragedy by jumping into a kiddie pool. He texted me: "Bro, look at Digital Tech Guard Recovery. They're crypto Roadies." I pictured a group of pierced hackers in black hoodies, blowing gum and cracking firewalls. Good enough.
Digitals crew followed the scambot's trail with the ferocity of a producer hunting for the perfect bassline.
The crook had routed my Bitcoin through privacy coins, obscured wallets, and exchanges located in countries that I couldn't spell. Their engineers stalked his path like a creep watching a pop star's concert tour schedule, in cooperation with Interpol and a Cypriot bank used also as a hub for meme stocks. As it turns out, my "maestro" had become careless, stashing money in a wallet associated with a failed NFT venture named "Aping for Jesus." Typical. Sixteen days later, my wallet beeped. Balance returned. No taunting, only a curt email: "Scammer's assets frozen. Your money's back. Buy better speakers." I blasted "Eye of the Tiger" through the café sound system, shocking a hipster with oat milk. The espresso machine finally came online. Digital Tech Guard Recovery didn't just restore my cryptocurrency; they wrote the encore for my midlife crisis. My café exists today, littered with grail-worthy records on the walls and a tip cup emblazoned "ETH accepted." Chad's no longer on the espresso machine, but he's got free coffee for life.
If your cryptocurrency is ever swindled by a cyber rockstar, don't go into existential tailspin. Call the Digitals. They'll turn your faceplant into a victory lap. Just maybe screen your "maestros" harder than your band's setlist.1


