Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "limiting"
-
Father bought a PC in 1997. Back then very few had it. I learned doing things like accessing the internet and sending emails, among others. I remember having added age on websites to be allowed to sign up at times :P My sisters used to play games on it sometimes. The first few ones we had were Tomb Raider: The Last Revelation, Tomb Raider Chronicles, American McGee's Alice(Which caused us to upgrade the PC xD)... And some others.
I have a memory of this pseudo-3D-looking game where you move in a maze and try answering questions. I want to remember its name, but I cannot :(
We literally have video evidence of me liking the computer as a child, yet my parents either say I'm addicted or deny I've ever liked it before. Not only that, but continuously limiting my time with the PC hasn't been a literal obstacle in my way of trying to do things in their opinion. Funny how my parents think the last few years I've been my worst when they've hurt me in those years so much that our relationship is guaranteed not working out. There were doubts in my head before, but now it's cemented and there is no way of going back. Father, for example, tells me it's too late to do anything with a PC now(As well as how I've been unable to use the PC. He looks at these pro players' footage in some TV show and he's like, „You've been unable to use your hobbies“, as if they have never ever screamed at me for perceived gaming and not actually cared to check), and I need to look for a „real“ job.
Sorry. I went to bed at 2:00 in the morning. Feel like a zombie because of ongoing weirdly insufficient sleep, even though I sleep kinda more than normal. Even when I took Melatonine for that it didn't help at all.
Childhood was where beating began. I was about 6/7. Right when I entered school. The first school that I attended was a private one and supposedly for „Wunderkinds“, while in reality I haven't seen a SINGLE teacher or psychologist approve of it, their argument being that children were basically drowned in work that wasn't age-appropriate(I don't mean anything bad. Just that teaching about Galaxies and all in first grade isn't the brightest idea). There was always a mountain of homework to do and as opposed to some other countries, we had to do it on a day to day basis. We didn't have a week-long deadline. I was predictably not keeping up with it as I could have, had it been a normal amount, so my parents decided I didn't want to study and began their methods of getting me to „study“. I have yet to see a person able to keep up with that school's tempo, no matter the age.
This place was also where I got bullied. I felt I had nowhere to be: At home, the parents' situation, at school, the bully. I never really went outside to play with other children, so I missed that part of childhood.
After the second year of school I was transferred to an advanced German school, called like that because they taught German and not English there. I also got to learn a bit of Russian before they removed it from school. In that period I used to attend ballet. But for less than a year. And piano, which I remember having attended for quite a long while, some years, if my memory isn't fried. I quit it because of it having been forced on me. Last piece I ever played fully was Beethoven's Marmotte.
In this school I was once again the outcast of the class. I had some people to interact with. All of those interactions lasted a few years at most. Then, because of a part of my class choosing me as a laughing-stock N2 and another girl as the N1, I found my best friend, who I still have today. She's the only friend I have nearby.
Most of the time I hated myself. Even today I struggle with that sometimes.
After that came university. This us where I got something like a friend circle at last. But it still didn't last. I got in a relationship with one of the guys, but I was just attracted. There was another I couldn't dare getting close to. Turns out he also had something for me. Then he disappeared from our lives and a year after, I still cannot forget the person. If I want to, I have to deprive myself of my own personality. Not a thing I'm willing to give up. Then I broke up with the guy I was in a relationship with and completely disappeared from the friendship circle. To be honest, I had reasons to. They refused to even try to look for the guy and they called him a friend for years. Sometimes parents hitting me can occur even today, but if I REALLY piss them off.
Now I'm here and oh, my God, I'm officially am aunt now! My sister gave birth to a daughter this morning... She's in Berlin with mother and both she and the child are doing great. I just hope she manages to be a good mother.20 -
Hacking/attack experiences...
I'm, for obvious reasons, only going to talk about the attacks I went through and the *legal* ones I did 😅 😜
Let's first get some things clear/funny facts:
I've been doing offensive security since I was 14-15. Defensive since the age of 16-17. I'm getting close to 23 now, for the record.
First system ever hacked (metasploit exploit): Windows XP.
(To be clear, at home through a pentesting environment, all legal)
Easiest system ever hacked: Windows XP yet again.
Time it took me to crack/hack into today's OS's (remote + local exploits, don't remember which ones I used by the way):
Windows: XP - five seconds (damn, those metasploit exploits are powerful)
Windows Vista: Few minutes.
Windows 7: Few minutes.
Windows 10: Few minutes.
OSX (in general): 1 Hour (finding a good exploit took some time, got to root level easily aftewards. No, I do not remember how/what exactly, it's years and years ago)
Linux (Ubuntu): A month approx. Ended up using a Java applet through Firefox when that was still a thing. Literally had to click it manually xD
Linux: (RHEL based systems): Still not exploited, SELinux is powerful, motherfucker.
Keep in mind that I had a great pentesting setup back then 😊. I don't have nor do that anymore since I love defensive security more nowadays and simply don't have the time anymore.
Dealing with attacks and getting hacked.
Keep in mind that I manage around 20 servers (including vps's and dedi's) so I get the usual amount of ssh brute force attacks (thanks for keeping me safe, CSF!) which is about 40-50K every hour. Those ip's automatically get blocked after three failed attempts within 5 minutes. No root login allowed + rsa key login with freaking strong passwords/passphrases.
linu.xxx/much-security.nl - All kinds of attacks, application attacks, brute force, DDoS sometimes but that is also mostly mitigated at provider level, to name a few. So, except for my own tests and a few ddos's on both those domains, nothing really threatening. (as in, nothing seems to have fucked anything up yet)
How did I discover that two of my servers were hacked through brute forcers while no brute force protection was in place yet? installed a barebones ubuntu server onto both. They only come with system-default applications. Tried installing Nginx next day, port 80 was already in use. I always run 'pidof apache2' to make sure it isn't running and thought I'd run that for fun while I knew I didn't install it and it didn't come with the distro. It was actually running. Checked the auth logs and saw succesful root logins - fuck me - reinstalled the servers and installed Fail2Ban. It bans any ip address which had three failed ssh logins within 5 minutes:
Enabled Fail2Ban -> checked iptables (iptables -L) literally two seconds later: 100+ banned ip addresses - holy fuck, no wonder I got hacked!
One other kind/type of attack I get regularly but if it doesn't get much worse, I'll deal with that :)
Dealing with different kinds of attacks:
Web app attacks: extensively testing everything for security vulns before releasing it into the open.
Network attacks: Nginx rate limiting/CSF rate limiting against SYN DDoS attacks for example.
System attacks: Anti brute force software (Fail2Ban or CSF), anti rootkit software, AppArmor or (which I prefer) SELinux which actually catches quite some web app attacks as well and REGULARLY UPDATING THE SERVERS/SOFTWARE.
So yah, hereby :P39 -
- Take a course called "Mobile Application Development"
- Teacher is new and is thus lost on how things work because there is no formal training for them
- Teacher only knows Objective-C so that's all we're allowed to use
- Nobody owns a Mac and I think one or two people had an iPhone/iPad
- Only 4 public Mac computers are available to the school
- One to two people are on them frequently, limiting our time on them as well
- Not a part of the schools normal imaging and updating system, so we get to do it ourselves, which takes up like a week or two of classes (4 classes)
- This includes installing XCode and getting Apple IDs
- No real instructions are given besides "implement the APIs for Facebook, Twitter, and Google Maps into an app"
- Being an ass, for the final day instead of showing off the app we made I made a PowerPoint of my dislike of Objective-C and various struggles I ran into and how I decided not to make the app at all.
- shrug emoji4 -
!security
(Less a rant; more just annoyance)
The codebase at work has a public-facing admin login page. It isn't linked anywhere, so you must know the url to log in. It doesn't rate-limit you, or prevent attempts after `n` failures.
The passwords aren't stored in cleartext, thankfully. But reality isn't too much better: they're salted with an arbitrary string and MD5'd. The salt is pretty easy to guess. It's literally the company name + "Admin" 🙄
Admin passwords are also stored (hashed) in the seeds.rb file; fortunately on a private repo. (Depressingly, the database creds are stored in plain text in their own config file, but that's another project for another day.)
I'm going to rip out all of the authentication cruft and replace it with a proper bcrypt approach, temporary lockouts, rate limiting, and maybe with some clientside hashing, too, for added transport security.
But it's friday, so I must unfortunately wait. :<13 -
The list would be quite long.
I think Google is still making good tools, but just like Apple the integrations get all so tight and constricting... And with their data, if it goes wrong, it will go wrong hard.
I feel like YouTube is gliding into a state where cheap clickbait floats to the top and finding quality gets more difficult as well, their algorithm is more and more tuned to choose recent popular stuff over good older gems.
Microsoft is all pretend lovey dovey cuddling open source, but I'm still suspicious it's all a hug of death. I was never a big fan, but they're seriously dropping balls when it comes to windows-as-a-service, taking away so much personal control from end users even though they can't be trusted to babysit either.
Amazon is creeping it's way through the internet, charging $10/m to join the vip club infesting houses with spytubes to sell more plastic crap. Bezos' only right to keep wasting oxygen is BlueOrigin, but he'll probably fuck that up as well turning spaceflight into a decadent prime consumer orgy instead of something inspiring.
Facebook... Well, that's self explanatory. Fuck it, everything it pretends to be, and everyone who still has an account with a rusty spike.
Uber and AirBnB, with their fake ass mission of a green shared economy, but they trample over employees, customers and neighbors to build their ivory towers of progressive illusions.
Then there's a million declining brands.
I liked Skype for example when it was first released, Just like how I started out liking (and then hating) Discord, Slack, etc... They're all tools which seem fast and easy, but then they get us further away from solid protocols, get us entrenched into limiting, bloated and sometimes even dangerous tools. As my dad used to say: "Companies are like women, if you go for cheap, fast and easy you'll end up with a burning dick and half your savings gone"
You know what, fuck all tech companies.
OK, devrant is still pretty nice... For now.8 -
I think I will ship a free open-source messenger with end-to-end encryption soon.
With zero maintenance cost, it’ll be awesome to watch it grow and become popular or remain unknown and become an everlasting portfolio project.
So I created Heroku account with free NodeJS dyno ($0/mo), set up UptimeRobot for it to not fall asleep ($0/mo), plugged in MongoDB (around 700mb for free) and Redis for api rate limiting (30 mb of ram for free, enough if I’m going to purge the whole database each three seconds, and there’ll be only api hit counters), set up GitHub auto deployment.
So, backend will be in nodejs, cryptico will manage private/public keys stuff, express will be responsible for api, I also decided to plug in Helmet and Sqreen, just to be sure.
Actual data will be stored in mongo, rate limit counters – in redis.
Frontend will probably be implemented in React, hosted for free at GitHub pages. I also can attach a custom domain there, let’s see if I can attach it to Freenom garbage.
So, here we go, starting up modern nosql-nodejs-react application completely for free.
If it blasts off, I’m moving to Clojure + Cassandra for backend.
And the last thing. It’ll be end-to-end encrypted. That means if it blasts off, it will probably attract evil russian government. They’ll want me to give him keys. It’ll be impossible, you know. But they doesn’t accept that answer. So if I accidentally stop posting there, please tell my girl that I love her and I’m probably dead or captured28 -
I've just disassembled this LED floodlight that I bought a while ago. It's some stupid little cheapie from a dollar store, so I figured that there'd be shit inside. But I wanted that LED cob.. a power LED :3
Well, shit wasn't too far off from the truth. The component choice is reasonable, but the design of the bloody thing.. batshit insane. The LED floodlight is powered by 4 AAA batteries, connected in series. So 6VDC. That then goes into this little tactile pushbutton, into the LED cob and then a 4.7 ohm resistor.
Well that's a pretty easy circuit.. let's remove the batteries and the casement, and put it on the lab bench power supply. Probes connected to the circuit with only the resistor and the LED cob in between (I didn't want to deal with the switch). Power supply set to 6V, current limiting to 500mA, contact!! And it works, amazing! So I let it run for a while to see that nothing gets too hot.. hah. After a minute or so, smoke would come out.. LED cob was a bit warm to the touch but nothing too bad. But the resistor.. I could cook water on it if I wanted to! 100 fucking °C, and rising. What the F yo?!
So I figured that I didn't want to put the resistor in between there. Just the LED cob now, which apparently has a forward voltage somewhere between 3.2V and 3.3V depending on how I set the current (500mA and 600mA respectively). Needed a bigger heatsink though, so I jammed one of my aluminium heatsinks on there. And it worked great! Very bright too, as it takes between 1.6 and 2W of power. Just for a comparison, the lighting in my living room is 4x5W and the ones on top of my dining table are 2x3W (along with some TL bar that my landlord put there.. fluorescent I think). So yeah, 2W is quite a lot for an LED, especially when it's all concentrated into one tiny spot.
That said, back to the original design with the resistor. 2 questions I have for that moron that designed this crap. First, why use a resistor for a power LED?! They needlessly waste power, and aren't good choices for anything that consumes more than 100mA. You should use PWM for these purposes, or tune your voltage on the supply side. Second, why go with 6V when your forward voltage is 3.3 at most? Wouldn't it make more sense to use 3 batteries with 4.5V? Ah, but I know the answer to the second one. AAA cells aren't rated for high loads like this. So that's likely why the alkaline cells that I had in there before have started leaking. Thanks, certified piece of shit!
Honestly, consumer electronics are such a joke... At least there's some components that I can salvage from this crap. Mainly the LED cob, but also the resistor and the tactile pushbutton perhaps.
One last remark that I'd like to make. This floodlight was cheap garbage. But considering that you can't do it well at that price, you just shouldn't do it. You know why? Because consumers always go for the cheapest. Makes a lot of money to build at rock bottom prices and make shit, but it damages the whole industry, since now the good designs will go out of business. That's why consumer electronics is so full of crap nowadays. Some unethical profiteering gluttons saw money, and they replaced the whole assortment with nothing but garbage. I'm sure that there's a special place in hell for that kind of people.17 -
## 4 years ago:
- Principal Architect: We are using IO1 storage type. What if we used GP2?
- Perf team: IDK, let's test it!
*we run tests*
- Perf team: results are OK, but we're exhausting Burst IO capacity, effectively hard-limiting number of tests we can run per day
- PArch: ahhh, I see. Then Gp2 is a no-go.
## 3 years ago
*PArch quits. New one is hired*
- PArch2: We are using IO1 storage type. What if we used GP2?
- Perf team: We've already tested that a while ago, results were THIS and THAT
- PArch2: I see. Let's test it again anyway
- Perf team: *wtf???*
*we run the same tests, we get the same results*
- PArch2: I see, so GP2 is a no-go.
- Perf team: *you think....? How did that thought never cross our minds, we wonder...*
## 2 years ago
*new DBA is hired*
- DBA2: We are using IO1 storage type. What if we used GP2?
- Perf team: We've already tested that a while ago, results were THIS and THAT
- PArch2: We've already tested that a while ago, results were THIS and THAT
- DBA2: I see. Let's test it anyways. I've read somewhere that GP2 might be a better bet
- PArch2: you might be right, let's do that
- Perf team: *wtf???*
*we run the same tests, we get the same results*
- DBA2: I see, so GP2 is a no-go.
- Perf team: *you think....? How did that thought never cross our minds, we wonder...*
## 1 year ago
*DBA manager left; new one was hired*
- MGMT_dba2: We are using IO1 storage type. What if we used GP2?
- ........
Should we even bother bringing up the history.....? 10
10 -
Want to play some Tic Tac Toe? Letting my bot go for a good first round of public testing
Probably will break right away.. Who knows :D
For starters limiting to one simultaneous game. Have fun!34 -
It's always fun to compare webdesign to car sales.
Client: We want a car with 2 doors.
We: Here is you car with 2 doors.
Client: Why does the car only have 2 doors? This is very limiting and i think 4 doors work way better.
We: Okay fine, here is a car with 4 doors.
Client: Could you please check on the brakes, i think there is something wrong but i don't know what.
We: Ok we checked the brakes and they are working ok. So here is you car with working brakes and 4 doors.
Client: Why didn't you check on the exhaust? The car is generating big black clouds now...
It's never enough7 -
I've found and fixed any kind of "bad bug" I can think of over my career from allowing negative financial transfers to weird platform specific behaviour, here are a few of the more interesting ones that come to mind...
#1 - Most expensive lesson learned
Almost 10 years ago (while learning to code) I wrote a loyalty card system that ended up going national. Fast forward 2 years and by some miracle the system still worked and had services running on 500+ POS servers in large retail stores uploading thousands of transactions each second - due to this increased traffic to stay ahead of any trouble we decided to add a loadbalancer to our backend.
This was simply a matter of re-assigning the IP and would cause 10-15 minutes of downtime (for the first time ever), we made the switch and everything seemed perfect. Too perfect...
After 10 minutes every phone in the office started going beserk - calls where coming in about store servers irreparably crashing all over the country taking all the tills offline and forcing them to close doors midday. It was bad and we couldn't conceive how it could possibly be us or our software to blame.
Turns out we made the local service write any web service errors to a log file upon failure for debugging purposes before retrying - a perfectly sensible thing to do if I hadn't forgotten to check the size of or clear the log file. In about 15 minutes of downtime each stores error log proceeded to grow and consume every available byte of HD space before crashing windows.
#2 - Hardest to find
This was a true "Nessie" bug.. We had a single codebase powering a few hundred sites. Every now and then at some point the web server would spontaneously die and vommit a bunch of sql statements and sensitive data back to the user causing huge concern but I could never remotely replicate the behaviour - until 4 years later it happened to one of our support staff and I could pull out their network & session info.
Turns out years back when the server was first setup each domain was added as an individual "Site" on IIS but shared the same root directory and hence the same session path. It would have remained unnoticed if we had not grown but as our traffic increased ever so often 2 users of different sites would end up sharing a session id causing the server to promptly implode on itself.
#3 - Most elegant fix
Same bastard IIS server as #2. Codebase was the most unsecure unstable travesty I've ever worked with - sql injection vuns in EVERY URL, sql statements stored in COOKIES... this thing was irreparably fucked up but had to stay online until it could be replaced. Basically every other day it got hit by bots ended up sending bluepill spam or mining shitcoin and I would simply delete the instance and recreate it in a semi un-compromised state which was an acceptable solution for the business for uptime... until we we're DDOS'ed for 5 days straight.
My hands were tied and there was no way to mitigate it except for stopping individual sites as they came under attack and starting them after it subsided... (for some reason they seemed to be targeting by domain instead of ip). After 3 days of doing this manually I was given the go ahead to use any resources necessary to make it stop and especially since it was IIS6 I had no fucking clue where to start.
So I stuck to what I knew and deployed a $5 vm running an Nginx reverse proxy with heavy caching and rate limiting linked to a custom fail2ban plugin in in front of the insecure server. The attacks died instantly, the server sped up 10x and was never compromised by bots again (presumably since they got back a linux user agent). To this day I marvel at this miracle $5 fix.1 -
Why did suddenly all websites start putting recaptcha in front of every user submission? Have they not heard of request limiting? I'm so tired of having to identify bridges, store fronts, cars, and unicorns before being able to do ANYTHING on the internet. For fuck's sake.10
-
---WiFi Vision: X-Ray Vision using ambient WiFi signals now possible---
“X-Ray Vision” using WiFi signals isn’t new, though previous methods required knowledge of specific WiFi transmitter placements and connection to the network in question. These limitations made WiFi vision an unlikely security breach, until now.
Cybersecurity researchers at the University of California and University of Chicago have succeeded in detecting the presence and movement of human targets using only ambient WiFi signals and a smartphone.
The researchers designed and implemented a 2-step attack: the 1st step uses statistical data mining from standard off-the-shelf smartphone WiFi detection to “sniff” out WiFi transmitter placements. The 2nd step involves placement of a WiFi sniffer to continuously monitor WiFi transmissions.
Three proposed defenses to the WiFi vision attack are Geofencing, WiFi rate limiting, and signal obfuscation.
Geofencing, or reducing the spatial range of WiFi devices, is a great defense against the attack. For its advantages, however, geofencing is impractical and unlikely to be adopted by most, as the simplest geofencing tactic would also heavily degrade WiFi connectivity.
WiFi rate limiting is effective against the 2nd step attack, but not against the 1st step attack. This is a simple defense to implement, but because of the ubiquity of IoT devices, it is unlikely to be widely adopted as it would reduce the usability of such devices.
Signal obfuscation adds noise to WiFi signals, effectively neutralizing the attack. This is the most user-friendly of all proposed defenses, with minimal impact to user WiFi devices. The biggest drawback to this tactic is the increased bandwidth of WiFi consumption, though compared to the downsides of the other mentioned defenses, signal obfuscation remains the most likely to be widely adopted and optimized for this kind of attack.
For more info, please see journal article linked below.
https://arxiv.org/pdf/...9 -
We got DDoS attacked by some spam bot crawler thing.
Higher ups called a meeting so that one of our seniors could present ways to mitigate these attacks.
- If a custom, "obscure" header is missing (from api endpoints), send back a basic HTTP challenge. Deny all credentials.
- Some basic implementation of rate limiting on the web server
We can't implement DDoS protection at the network level because "we don't even have the new load balancer yet and we've been waiting on that for what... Two years now?" (See: spineless managers don't make the lazy network guys do anything)
So now we implement security through obscurity and DDoS protection... Using the very same machines that are supposed to be protected from DDoS attacks.16 -
I finally moved to Fedora Silverblue 30 which is a really awesome OS.
Silverblue Edition unlike the standard version, runs a immutable core. That means the entire FS is not writable except for certain parts that are mounted to /var. While this is limiting, this allows for atomic updates, which is the whole point of Silverblue.
Now this also might throw off even myself, because I might need to run VSCode in the host and I might need C++ libs. Fortunately there's a tool named toolbox that allows you to use standard DNF inside a OCI container. Now the thing is, now you need to tell your IDE to use it after installing it.
I wrote a little helper script to do just that. I wrote it primarily for VSCode but it should also work for your IDE if you happen to want to try to use Silverblue.
Helper script: https://t.co/sXYOgcwLBg?amp=1
Also if you wanna try Silverblue for yourself, here's some notes:
* To install apps, you need to run flatpak. Make sure you also have the flathub repo listed.
* don't use the Flatpak version of the IDEs. If possible, use the RPM versions. Silverblue allows you to install traditional packages (to some degree, not everything works in this thing because of the immutable design) in the host. So as much as possible if you need dev libs, use toolbox for those.
* Silverblue also comes with podman and buildah installed (aka what if Docker had no daemon and was more secure?)
*Do your updates via rpm-ostree upgrade, or turn the auto updater on if you're lazy
All in all I like this environment, I've used this kind of workspace before (Chrome OS), so its pretty easy for me to get used to.
What do you think guys, think you'll give it a shot?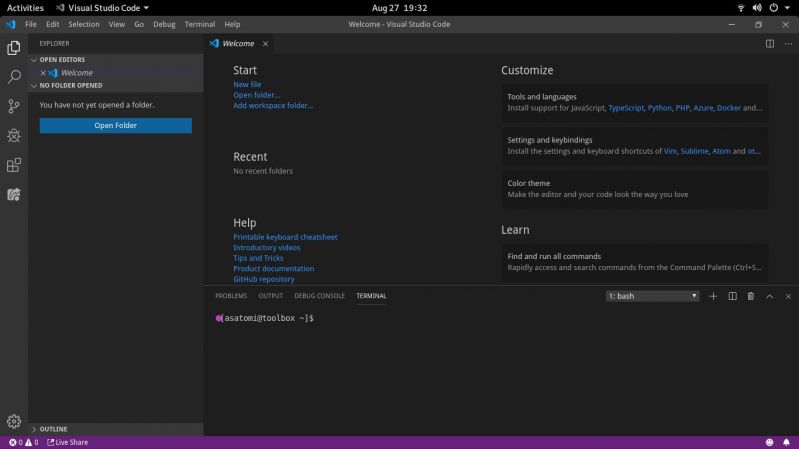 5
5 -
It only took us 5 hours to debug. It's fine. I'm not mad that it was just rate limiting. I'm fine. We're fine. It's fine.
 10
10 -
Hey there!
So during my internship I learned a lot about Linux, Docker and servers and I recently switched from a shared hosting to my own VPS. On this VPS I currently have one nginx server running that serves a static ReactJs application. This is temponarily, I SFTP-ed the build files to the server and added a config file for ssl, ciphers and dhparams. I plan to change it later to a nextjs application with a ci/di pipeline etc. I also added a 'runuser' that owns the /srv/web directory in which the webserver files are located. Ssh has passwords disabled and my private keys have passphrases.
Now that I it's been running for a few days I noticed a lot of requests from botnets that tried to access phpmyadmin and adminpanels on my server which gave me quite a scare. Luckily my website does not have a backend and I would never expose phpmyadmin like that if I did have it.
Now my question is:
Do you guys know any good articles or have tips and tricks for securing my server and future projects? Are there any good practices that I should absolutely read and follow? (Like not exposing server details etc., php version, rate limiting). I really want to move forward with my quest for knowledge and feel like I should have a good basis when it comes to managing a server, especially with the current privacy laws in place.
Thanks in advance for enduring my rant and infodump 😅7 -
Don't attack flies using tanks.
In 2020, a bug was found in gnome-terminal where selecting many megabytes of text inside the terminal would cause the terminal emulator to crash.
As a remedy, the brain of gnome-terminal developer Christian Persch spawned a "brilliant idea": Limiting the "Select all" feature to selecting only the portion of text that is visible on screen.
In other words, Persch made the "Select all" option useless. After pressing "Select all", it appeared as if everything was selected, but once you scrolled up, nothing beyond what was visible was selected.
By solving a minor problem that rarely ever occurs, Christian Persch created a major problem that often occurs.
Source for screenshot: https://gitlab.gnome.org/GNOME/... 11
11 -
We should not tolerate censorship.
Beyond all the u.s. hype over elections
(and the division in the west in general), the real story is all the censorship on both sides.
Reasonable voices are quickly banned, while violent voices and loud angry people are amplified.
I broke out of the left-right illusion when
I realized what this was all about. Why
so much fighting in the street was allowed, both
justified and unjustified. Why so much hate
and division and slander, and back and forth
was allowed to be spread.
It's problem, reaction, solution.
The old order of liberal democracy, represented
in the u.s. by the facade of the GOP and DNC,
doesn't know how to handle the free *distributed*
flow of information.
That free-flow of information has caused us to
transition to a *participatory* democracy, where
*networks* are the lever of power, rather than
top down institutions.
Consequently, the power in the *new era* is
to decide, not what the *narrative* is, but
who can even *participate*, in spreading,
ideating, and sharing their opinions on that
narrative, and more broadly, who is even allowed
to participate in society itself.
The u.s. and west wants the chinese model of
control in america. you are part of a network, a
collective, through services and software, and
you can be shut off from *society* itself at
the drop of a pin.
The only way they get that is by creating a crisis,
outright fighting in the streets. Thats why
people keep being released after committing serious
fucking crimes. It's why the DOJ and FBI are
intent on letting both sides people walk.
They want them at each others literal throat,
calling for each other's blood. All so they
can step back and then step in the middle when
the chorus for change cries out loud enough.
And the answer will be
1. regulated tech
2. an end to television media as we know it
3. the ability to shut someone off from any service on a dime
4. new hatespeech laws that will bite *all* sides in the ass.
5. the ability to shape the narrative of society by simply 'pruning' networks as they see fit, limiting the reach of individuals on all sides, who are problematic to
the collective direction.
I was so caught up in the illusion of us-vs-them I didn't
see it before now. This is a monstrous power grab.
And instead of focusing on a farce of election, where the party *organizations* involved are institutional facades for industrialists, we should be focusing on the real issue:
* Failure of law to do its job online, especially failures of slander and libel laws, failures of laws against conspiracy to commit crime or assault
* New laws that offer injunctive relief against censorship, now that tech really is the commons. Because whats worse than someone online whipping up a mob on either side, is
someone who is innocent being *silenced* for disagreeing with something someone in authority said, or for questioning a politician, party, or corporation.
* Very serious felony level laws against doxxing and harassment on all sides, with retroactive application of said laws because theres a lot of people on all sides who won't be satisfied with the outcome until people who are guilty are brought to justice.16 -
Since we're limiting this to things on my desk I can't do any more deep cuts out of my calculator collection, but this one is still somewhat interesting.
The HP 32S was my friend throughout university, it replaced the 15c I used before which does not live on my desk. The notable thing about the 32s is the fact it's an RPN calculator. RPN calculators are the best way to have friends never ask to borrow your calculator. The exchange will start by them asking to use it, you saying sure, and them handing it back a few minutes later without saying a word.
There's two kinds of people in this world. People who go "wtf" in an interview when asked to create a calculator program using a stack, and people who were oddballs and for whatever reason used reverse polish notation devices.
For those not familiar, rather than entering values into the calculator in "10+10" fashion, you instead provide it a compositional set of values until an operation is provided (10,10,+) at which point it executes. The why is, this type of operation allows the calculator to more naturally process operations, and eliminates the need for parenthesis which makes the operations less error prone in practice and easier to track.
The 32s had a 4 year run before being replaced by the 32SII. In the same way using a Curta will give you a significant understanding of how radix computations and floating points work. Using an HP 32s (or any of its predecessors) will do the same for algebraic functions, because you had to program them yourself using a basic label address system that also had subroutine support.
Kids who grew up with graphing calculators don't know how good you had it 😋 4
4 -
I get an email about an hour before I get into work: Our website is 502'ing and our company email addresses are all spammed! I login to the server, test if static files (served separately from site) works (they do). This means that my upstream proxy'd PHP-FPM process was fucked. I killed the daemon, checked the web root for sanity, and ran it again. Then, I set up rate limiting. Who knew such a site would get hit?
Some fucking script kiddie set up a proxy, ran Scrapy behind it, and crawled our site for DDoS-able URLs - even out of forms. I say script kiddie because no real hacker would hit this site (it's minor tourism in New Jersey), and the crawler was too advanced for joe shmoe to write. You're no match for well-tuned rate-limiting, asshole!1 -
Forgot to change code in my api for rate limiting, after development. No unit tests.. because who really needs that right? 🤦♂️🙅♂️🤷♂️lolololol
Long story short, API went to production eventually, and stopped working almost immediately. Rate limiting was set for 2000 requests in a 1 hour time period. Not my finest moment.. fml 🤦♂️ -
I honestly maintain a positive opinion that almost (again read almost) all devs are not inherently evil. Those who are made do those autoplay vids were probably asked by management, the game devs at EA are forced to use Frostbite which isn’t suitable for everything, like RPGs, and Apple devs aren’t trying to maximise profits by limiting so much to the consumer world (e.g the bloody XCode license), but are forced in by this corporate model.
A lot of shit is given to devs and sometimes I think it’s undeserved. In their shoes most people would too go against their moral compass if it meant that they won’t lose their jobs. I’m sure when battlefront was in the works it wasn’t the devs that came up with that whole shitstorm model.2 -
Who thought Lua was a good idea for extending gameplay functionality??
It's weakly typed, has no OOP functionality and no namespace rules. It has no interesting data structures and tables are a goddamn mystery. Somebody made the simplest language they could and now everybody who touches it is given the broadest possible tools to shoot themselves in the foot.
Lua's ease of embedding into C++ code is a fool's paradise. Warcraft 3's JASS scripting language had way more structure and produced much better games, whilst being much simpler to work with than Lua.
All the academics describing metatables as 'powerful extensionality' and a fill-in for OOP are digging the hole deeper. Using tables to implement classes doesn't work easily outside school. Hiding a self:reference to a function inside of syntactic sugar is just insanity.
Nobody expects to write a triple-A game in lua, but they are happy to fob it off to kids learning to program. WoW made the right choice limiting it to UI extensions.
Fighting the language so you can try and understand a poorly documented game engine and implement gameplay features as the dev's intend for 'modders', is just beyond the pale. It's very difficult to figure out what the standard for extending functionality is, when everybody is making it up as they go along and you don't have a strongly-typed and structured language to make it obvious what the devs intended.
If you want to give your players a coding sandbox, make the scripting language yourself like JASS. It will be way better fit for purpose, way easier to limit for security and to guarantee reasonable performance. Your players get a sane environment to work in and you just might get the next DOTA.
Repeatedly shooting yourself in the foot on invisible syntax errors and an incredibly broad language is wasted suffering for kids that could be learning the programming concepts that cross all languages way quicker and with way more satisfying results.
Lua is hot garbage for it's most popular application, I really don't get it. Just stop!21 -
Last night I had a very strange dream. I should point out in advance, all of this is fictional and none of it really happened.
I was looking at an answer I posted on Stack Exchange.. for the sake of argument, let's say it was Super User. I remember the question being about volume limiting, which is actually an issue I and many other iOS 14.2/14.3 users have been facing in the last few months. Apparently it has been partially addressed in 14.4.
In the real world I fixed the issue by jailbreaking the phone and unloading the healthd service, while in the dream that was the answer I had documented on Super User. In reality I have documented it in several other places, but not there.
Fast-forward a couple of days in the dream where the answer was posted, and I was now looking at a reply. I don't remember the exact details of it, but apparently in the answer I had posted something about my network.. a screenshot from the iPhone? And the comment on it basically said something along the lines of "your answer is shit, and you probably have a very basic internet connection with default settings". I was really upset by that, as my network is actually quite advanced (on account of being a sysadmin).
Then I woke up and realized that it was all just a dream...4 -
Arghhhhhhhh! What the hell is becoming of today's world?
So I have registration form that relates to parents signing up for a service and asking for ages of their children. Children are never older than 5 years old.
So, for each child the user specified the child's sex/gender (Boy or girl) and their age.
I'm still in disbelief over my client's request, that is marked "urgent".
I basically need to add to the list of options, as "boy" and "girl" are no enough and the question is now "too limiting".
I apparently need to add several more options including: "prefer not to specify", "geneder neutral", "bigender" and "genderfluid".
I mean how can a child aged 5 or less identify as "gender neutral" or "bigender" - how on earth are they able to decide.
Fine, if you're an adult and signing up to something like Facebook, have your 80 odd options. But for children under 5 how have no idea wtf any of this means, stuff like this really annoys me.15 -
Wireguard reminds me of ssh. You exchange keys and start using the thing.
You protect client by limiting IPs that can access it and you protect server by listing IPs that can connect + iptables for more advanced access rules.
And the whole thing runs on UDP and in kernelspace, so it's fast AF
iperf3 tests compared to OpenVPN look amazing: x20 times faster than OpenVPN :D
https://reddit.com/r/linux/...
I freaking love Linux! -
God I fucking hate my country! The moment it looks like we've managed to control covid spread by limiting movement between cities / municipalities and banning people from public places, and we may just be able to slowly loosen some restrictions, some fucktard on national TV starts telling people how all those restrictions are unbearable just because they came from the "wrong" political option. And people listen to that idiot more than all doctors telling them to stay safe.
The worst part is we probably wouldn't even limit movement if it didn't become obvious people are hoarding natural attraction / getting injured by extreme sports / inviting friends & relatives over when told to stay at home and avoid public places.11 -
To a fellow dev on my team; If you notice a difference between the spec and the database structure, just fucking talk to the BA! Don’t code something that fails and put it into QA.
And constantly saying “It’s not my job” is a severely career limiting move you dogmatic little shit.2 -
"Attending" WWDC 2025 ("attending" is a stretch). I'm starting this thread as a multi-rant (comments count).
To start it off, WWDC 2025 is, like all these other virtual 2020's WW's, BORING... World Wide Dull Cinema.. It's like being in developer-solitary-confinement. After going to the in-person ones, I can safely say that it is hard to care about anything in WWDC beyond the keynote...
And when Tim gets on there /still/ trying to extoll the virtues of it being virtual, it is pretty clear that they are trying to compensate...
1. no collaboration
2. uninspiring without your peers
3. random because there is no real schedule
4. boring because you don't meet anyone new
5. career limiting, can't trade vCards & resumes
6. cringy trying too hard announcements
(just sayin', love you guys but come on here...)
WWDC 2019 and prior were awe-inspiring. WWDC pre 2020 collected enough IQ in one place to make the world wobble on its axis.
WWDC needs to go back to in-person /with/ streaming for those of us who can't make it. Change the venue to Las Vegas for crying out loud, they can handle the *worlds* *largest* *trade* *show* (aka CES) there... WWDC is small potatoes by comparison.3 -
Starting to learn Haskell/type theory. I have put it off long enough and I hope this time I can get past the 5 minute intro/overview.
So far the only functional programming I have done is trying to write/use functions that take state in parameters only and limiting side effects (that I know of).
Expecting to have my mind blown and to get a monocle too.3 -
Trying out the new version of fasm, I realize it's good, and conclude I should update my code to work with it as there's small incompatibilities with the syntax.
So, quick flat assembler lesson: the macro system is freaking nuts, but there are limitations on the old version.
One issue, for instance, is recursive macros aren't easily possible. By "easily" I mean without resorting to black magic, of course. Utilizing the arcane power of crack, I can automatically define the same macro multiple times, up to a maximum recursion depth. But it's a flimsy patch, on top of stupid, and also has limitations. New version fixes this.
Another problem is capturing lines of code. It's not impossible, again, but a pain in the ass that requires too much drug-addled wizardry to deal with. Also fixed in new version.
Why would you want to capture lines of code? Well, because I can do this, for instance:
macro parse line {
··match a =+ b , line \{
····add a,b;
··\}
};
You can process lines of code like this. The above is a trivial example that makes no fucking sense, but essentially the assembler allows you define your own syntax, and with sufficient patience, you can use this feature to develop absolutely super fucking humongous galactic unrolls, so it's a fantastic code emitter.
Anyway, the third major issue is `{}` curlies have to be escaped according to the nesting level as seen in the example; this is due to a parser limitation. [#] hashes and [`] backticks, which are used to concatenate and stringify tokens respectively, have to be escaped as well depending on the nesting level at which the token originates. This was also fixed.
There's other minor problems but that gives you sufficient context. What happens is the new version of fasm fixes all of these problems that were either annoying me, forcing me to write much more mystical code than I'd normally agree to, and in some rare cases even limiting me in what I could do...
But "limiting" needs to be contextualized as well: I understand fasm macros well enough to write a virtual machine with them. Wish I was kidding. I called it the Arcane 9 Machine, A9M for short. Here, bitch was the prototype for the VM my fucking compiler uses: https://github.com/Liebranca/forge/...
So how am I """limited""", then? You wouldn't understand. As much as I hate to say it, that which should immediately be called into question, you're gonna have to trust me. There are many further extravagant affronts to humanity that I yearn to commit with absolute impunity, and I will NOT be DENIED.
Point is code can be rewritten in much simpler, shorter, cleaner form.
Logic can be much more intricate and sophisticated.
Recursion is no longer a problem.
Namespaces are now a thing.
Capturing -- and processing -- lines of code is easier than ever...
Nearly every problem I had with fasm is gone with this update: thusly, my power grows rather... exponentially.
And I SWEAR that I will NOT use it for good. I shall be the most corrupt, bloodthirsty, deranged tyrant ever known to this accursed digital landscape of broken souls and forgotten dreams.
*I* will reforge the world with black smoldering flame.
*I* will bury my enemies in ill-and-damned obsidian caskets.
And *I* will feed their armies to a gigantic, ravenous mass grave...
Yes... YES! This is the moment!
PREPARE THE RITUAL ROOM (https://youtube.com/watch/...)
Couriers! Ride towards the homeland! Bring word of our success.
And you, page, fetch me my sombersteel graver...
I shall inscribe the spell into these very walls...
in the ELEVENTH degree!
** MANIACAL EVIL LAUGHTER ** -
#just a thought
The child that is the most curious will grow up to be most boring person.
Why?
Since most other children of his age would be doing random and a lot of things without questioning , he would be struck in his simple world of 'why this happens' , therby limiting him to one but deep knowledge of a field.
And even if not , being curious leads to answers of little mysteries ignored by ususal ppl. Therefore, this boy with lots of knowledge will be "boring, coz he always have some right things to say".
Thus a child can either don't care and do whatever his authority wants from him without questioning, and grow into a likeable, social adult, or be curious , learn in deep and grow out to be a specially awkward person7 -
I really just hate Apple development. Xcode blows hard ass and if you are a person like me who has 0 Apple devices and has to go to the fucking school labs to code then why wouldn't you hate apple development. It's really the lack of being able to code outside a fucking Mac cause its just pointlessly limiting, fuck you Apple.13
-
Why the fuck open source solutions need to be such a load of bullcrap? I've spent a week trying to set up every single self-hosted video conference software, and the only thing I've got is a shorter lifespan.
How the fuck does your (judging by GitHub, well maintained) software only support Ubuntu 16.04? And I mean ONLY, there's no support for docker, or any other distro either, and we're only weeks from getting the second LTS since 16.04. And why the fuck does documentation tell me to manually go through 20 different config files just to enable SSL?
Why the fuck doesn't your official AWS cloudformation template include VPC or other required parameters? I've had to rewrite the whole thing just to get a valid stack you dipshit!
And how fucking hard is to make your software look decent, I can't expect clients to chat with me using something that looks like an incest child of 2003 MSN and eDonkey?
Oh, and it'd be fucking dandy if your documentation wouldn't return 404, maybe I'd be even able to test what your product has to offer?
I guess after everything I've tried I'll go with Jitsi; it seems the most decent, although it lacks some pretty basic features like limiting chat features for guests.22 -
In reply to:
https://devrant.com/rants/3957914/...
Okay, we must first establish common ground here. What do we understand about "showing"? I understand you probably mean displaying/rendering, more abstractly: "obtaining". Good, now we move on.
What's the point of a front-end? Well, in the 90's that used to be an easy answer: to share information (not even in a user-friendly way, per se). Web 2.0 comes, interaction with the website. Uh-oh, suddenly we have to start minding the user. Web 3.0 comes, ouch, now the front-end is a mini-backend. Even tougher, more leaks etc. The ARPAnet was a solution, a front-end that they had built in order to facilitate research document-sharing between universities. Later, it became the inter(national) net(work).
First there was SGML to structure the data (it's a way of making it 'pretty' in a lexicographical way) and turn it into information (which is what information is: data with added semantics) and later there was HTML to structure it even further, yet we all know that its function was not prettification, but rather structure. Later came CSS, to make it pretty. With its growing popularity, the web started to be used as a publishing device.
source:
https://w3.org/Style/CSS20/...
If we are to solely display JSON data in a pretty way, we may be limiting ourselves to the scenario of rendering pretty web pages using aesthetic languages such as CSS. We must also understand that if we are only focusing on making a website pretty with little to moderate functionality, we aren't really winning. A good website has to be a winner in all aspects, which is why frameworks came into existence, but.. lmao, let's leave that to another discussion.
Now let me recall back my college days.. front-end.. front-end.. heck, even a headset can be a front-end to a pick-order backend. We must think back to the essence, to the abstract. All other things are just implementations of it (yes, the horrendous thousands of Javascript libraries, lol).
So, my college notes say:
"Presentation layer: this is the UI.
In this layer you ask the middle tier for information, which gets that information from a database, which then goes back to middle tier, back to presentation. In the case of the headset, the operators can confirm an order is ready. This is essentially the presentation tier again: you're getting information from the middle tier and 'presenting it' as it were.
The presentation layer is in essence the question: how do I bring my application data to my end users in a platform-and solution-independent way?"
What's JSON? A way to transport data between the middle tier and the presentation tier. Is that what frontend development is? Displaying it in a pretty way? I don't think it is, because 'pretty' is an extra feature of obtaining and displaying data. Do we always have to display data in a pretty way? Not necessarily. We could write a front-end script (in NodeJS perhaps) that periodically fetches certain information from a middle-tier is serves a more functional role rather than a rendering one.
The prettification of data was a historical consequence of the popularity of the web (which is a front-end) (see second paragraph with link). Since the essence of a front-end is to obtain information from the back-end (with stress on obtaining), its presentation is not necessarily a defining characteristic of it, but rather an optional and solution-dependent aspect, a facet.4 -
Trying to install Linux on an HP Stream 7 has been way more difficult than it should have been, even when you take into account that it's a 32-bit processor with a 32-bit EFI!
First off, the only thing I've been able to get it to boot right of the bat is Android x86 and BlissOS... kind of. You would think that Android x86 would be perfect for a tablet, right? Nope, performance sucked sooooo bad.
After reading some forums, I was finally able to get Ubuntus to load up... with the limiting factor being no on-screen keyboard.
So... at the moment I guess I'm stuck with a useless Windows tablet, and probably will be for a long time (you know, since 32-bit architecture is being dropped)6 -
Fuck motherfucking android 8 fucking sideways. And Huawei for that matter too.
My battery drains like 30% faster since the update from 7.0, with even more app limiting than in 7. I've already ranted about UI stuff, but that is negligible compared to this bullshit.
Also, auto brightness is broken and it keeps blinding me fora few seconds in the dark, and choosing way too much brightness.
I've loved my otherworldly battery life, now I feel like an apple user with 4k mah.
I used to get one and a half day battery, now I barely get through the day.11 -
Even I want devRant feed to be filled with quality rants, but 1 rant/hour is bit less!
Like 5 or so would be better? 3
3 -
I took part in the selections for the Italian Olympiad of Informatics. First question:
Preferred language?
1. C/C++
2. Pascal
What if I only knew Java, COBOL, or Python? It just seems like such a limiting thing, is it normal?
Does it happen in other countries too?6 -
I've never been a big fan of the "Cloud hype".
Take today for example. What decent persistent storage options do I have for my EKS cluster?
- EBS -- does not support ReadWriteMany, meaning all the pods mounting that volume will have to be physically running on the same server. No HA, no HP. Bummer
- EFS -- expensive. On top of that, its performance is utter shit. Sure, I could buy more IOPS, but then again.. even more expensive.
S3 -- half-assed filesystem. Does not support O_APPEND, so basically any file modifications will have to be in a
`createFile(file+"_new", readAll(file) + new_data); removeFile(file); renameFile(file + "_new", file);`
way.
ON TOP of that, the s3 CSI has even more limitations, limiting my ability to cross-mount volumes across different applications (permission issues)
I'm running out of options. And this does not help my distrust in cloud infras... 9
9 -
Did anyone hear of Twitter limiting viewing tweets to 300 to new unverified accounts, 600 to older unverified accounts and 6000 for verified accounts? You can't view tweets if you are not signed up, too... They did say it was a temporary thing, but still is a pretty weird move, if you ask me.
This is gonna fuck over so many people it's hard to put into words.15 -
!rant
#Ichackuk
Currently at Imperial college's hackathon, 13hrs down, 11 to go.
My first hackathon, awesome spirit. Too much food and goddies and so many hacks!!!
Will update with what I made soon. And may be give out URL, after limiting usgae to not cost my self.
#fallinlovewithcode5 -
at one point documents were useful things to align people to the relevant information to the tasks they must complete for everything to work out
now documents are a ritual, and relevant information is even forgotten or omitted and considered secondary to the document existing and looking like a professional document
I wonder if this is how all industries evolve
at one point there were people who knew what they were doing, they created processes so nobody is left behind
and over time, whoever made the processes, the spirit for their existence, is forgotten
and you're left with empty rituals, so devoid of their original function, the humans subjected to these things, crushed by them, can't even discern what their usage is
evidently if you put monkeys in an enclosure with some apples up a tree with a mechanism that if a monkey goes up the tree and takes an apple it sprays all the other monkeys in the enclosure with water
the monkeys will learn to pull down any monkey trying to go up the tree, because they don't wanna get sprayed
and this will keep going, generations will change and yet they'll still religiously pull down the monkeys, in a ritual... nobody remembers why only that their parents did this to them, so they do it to others
if you take the trap away, they never figure it out, which is how this story is typically told
but regardless of if the trap is there or not
wouldn't you wanna know and see it for yourself instead of following empty rituals?!
and what of people who erroneously view things as traps, and pull people down, but they were just seeing things?!
self limiting myths to doom the ages! -
!dev
have you ever tried traveling solo with a travel group?any insights on what to expect and how to stay safe?
i am kinda feeling crazy and might just go on this trip to mountains with this group. my friend circle is shitty and limiting me from going places, I don't wanna stop2 -
Received email from Docker that they’re limiting anonymous container pulling to 100 requests per 6 hours.
It’s time to die for this company, that’s their last breath.
More about this on their blog here:
https://docker.com/blog/...2 -
Why the hell does NOBODY, including Apple, figure out, how USB-C is supposed to work? I'm tired of shifty half-assed implementations with some having no USB 3.1 (Apple), some not supporting current DisplayPort standards (Apple, Dell) or limiting the speed to USB2.0... *GAAAAH*
Future seems to suck pretty hard.3 -
To anyone who ever got annoyed at all the "thanos was right" people who repeated it to the annoyance of everyone, for months on end: the studio did it so the Hollywood misanthropes could sell their doomporn malthusian claptrap to the subset wanna-sound-smart crowd of farthuffering intellectuals in the public.
Now you can't walk six feet without every other dude and their f*cking dog spouting off at the mouth about "thanos was right!"
Like no shit? You DONT SAY! None of us could have possibly had this brilliant and never-before-experienced flash of revelation opinion of thanos. As insightful and innovated as the man who once realized cat rhymes hat. Truly a legend worthy of admiration and accolade.
pure nonsense.
Hes a mass murderer. An absolute monster based purely on the scale of his actions. The scale of his murder elides over any moral considerations of intent or pretensions of intent, and sincerity no more absolves him than sincerity absolves a terrorist.
What this movie should have done for all the thanos dickriders or would-be dickriders, is taught a valuable eye opening lesson: how easy it is make people in general agree with anything--anything at all, no matter how appalling, how monstrous, so long as the instigator is framed sympathetically on the golden screen. It should have opened your eyes about just how powerful and susceptible you and anyone else are to propaganda.
Dont believe me? Take your most hated politician, left or right. Now imagine they did exactly what thanos did.
Would you still be ok with it? Of course not. Because the fallacy here is to impute moral or logical worthiness onto a cause simply because the agent of it is sincere or can be empathized with.
More generally, Thanos actions presuppose that population control is not a social and technological issue, which it is, and like everything else will come under the pressure of technology. On a long enough timeline then it's a self limiting problem (by definition).
Which is what makes this example of propaganda so vicious: precisely because this subset of the public is so vacuous and infantilized as to actually believe movie logic malthusianism is the same as reality.
The reality is the material conditions of life, even in places like*india* have so markedly improved because of technology *exclusively* iterated on *solely* because of population pressure, that many of the most impoverished people live in such wealth compared to their ancestors just five thousand years ago, that they are kings by comparison.7 -
Text is lovely to skim but so limiting when you're trying to connect 🫂
Humans make _strings_ of love all day everyday for those they love🧵3 -
I've been wondering about renting a new VPS to get all my websites sorted out again. I am tired of shared hosting and I am able to manage it as I've been in the past.
With so many great people here, I was trying to put together some of the best practices and resources on how to handle the setup and configuration of a new machine, and I hope this post may help someone while trying to gather the best know-how in the comments. Don't be scared by the lengthy post, please.
The following tips are mainly from @Condor, @Noob, @Linuxxx and some other were gathered in the webz. Thanks for @Linux for recommending me Vultr VPS. I would appreciate further feedback from the community on how to improve this and/or change anything that may seem incorrect or should be done in better way.
1. Clean install CentOS 7 or Ubuntu (I am used to both, do you recommend more? Why?)
2. Install existing updates
3. Disable root login
4. Disable password for ssh
5. RSA key login with strong passwords/passphrases
6. Set correct locale and correct timezone (if different from default)
7. Close all ports
8. Disable and delete unneeded services
9. Install CSF
10. Install knockd (is it worth it at all? Isn't it security through obscurity?)
11. Install Fail2Ban (worth to install side by side with CSF? If not, why?)
12. Install ufw firewall (or keep with CSF/Fail2Ban? Why?)
13. Install rkhunter
14. Install anti-rootkit software (side by side with rkhunter?) (SELinux or AppArmor? Why?)
15. Enable Nginx/CSF rate limiting against SYN attacks
16. For a server to be public, is an IDS / IPS recommended? If so, which and why?
17. Log Injection Attacks in Application Layer - I should keep an eye on them. Is there any tool to help scanning?
If I want to have a server that serves multiple websites, would you add/change anything to the following?
18. Install Docker and manage separate instances with a Dockerfile powered base image with the following? Or should I keep all the servers in one main installation?
19. Install Nginx
20. Install PHP-FPM
21. Install PHP7
22. Install Memcached
23. Install MariaDB
24. Install phpMyAdmin (On specific port? Any recommendations here?)
I am sorry if this is somewhat lengthy, but I hope it may get better and be a good starting guide for a new server setup (eventually become a repo). Feel free to contribute in the comments.24 -
Bullshittery continues. This time around, absolutely innocent, clamav is root cause. For once not incompetent idiot, but piece of software. IDK if that makes me happy or upset.
So our email server that I configured and took care of died. RIP. Damn, better put it back together ASAP. So Im under pressure, while still pissed at everything that I ranted before (actually my last 2 rants were throttled, and in total all of that happened past 60 minutes but devrant rate limiting) I start auditing logs. You imagine, we kindda need it NOW, and it's second time last month clamav is pulling stunts and MTA refuses (properly) to work without antivirus. So pressurized, I look at logs, what the fuck went wrong.
clamav deamonize() failed - cannot allocate memory
Hmm. Intresting, but sounds like bullshit. I know server is quite micro becouse they wanted to save on costs as much as possible, but it has well over half a gig free ram just before it crashes (like 800MB) with that message. Is it allocating almost gig in one call or what? Looked carefully at trusty htop while it was starting, and indeed, suddenly it just dies with quite a bit of ram free, almost as much as it weights already. And I remember booting it up when I was configuring it, and it had fair bit of headroom.
Google, help me friend... Okay, great, so apparently at some point clamav loads virus DB into ram (dafuq?), and than forks, which causes spike of 2x the ram usage, and than immidietely frees it up.
Great, that sounds like great design decision... At least I know, I can just slap on SWAP file, restart it and call it a day.
It worked, swap file is almost empty (used 15megs, 900 megs free ram, whatever).
That leaves me wandering, who figured out to load DB to ram? That means pretty much that clamav will eat a little bit more ram each vir db update, and that milisecond "double ram" spike will confuse innocent people who just wanted to run clamav and it worked last *long period of time* and now crashes without warning without any changes to configuration.
Maybe there is logical explanation, I want to know it.8 -
I hate the elasticsearch backup api.
From beginning to end it's an painful experience.
I try to explain it, but I don't think I will be able to cover it all.
The core concept is:
- repository (storage for snapshots)
- snapshots (actual backup)
The first design flaw is that every backup in an repository is incremental. ES creates an incremental filesystem tree.
Some reasons why this is a bad idea:
- deletion of (older) backups is slow, as newer backups need to be checked for integrity
- you simply have to trust ES that it does the right thing (given the bugs it has... It seems like a very bad idea TM)
- you have no possibility of verification of snapshots
Workaround... Create many repositories as each new repository forces an full backup.........
The second thing: ES scales. Many nodes / es instances form a cluster.
Usually backup APIs incorporate these in their design. ES does not.
If an index spans 12 nodes and u use an network storage, yes: a maximum of 12 nodes will open an eg NFS connection and start backuping.
It might sound not so bad with 12 nodes and one index...
But it get's pretty bad with 100s of indexes and several dozen nodes...
And there is no real limiting in ES. You can plug a few holes, but all in all, when you don't plan carefully your backups, you'll get a pretty f*cked up network congestion.
So traffic shaping must be manually added. Yay...
The last thing is the API itself.
It's a... very fragile thing.
Especially in older ES releases, the documentation is like handing you a flex instead of toilet paper for a wipe.
Documentation != API != Reality.
Especially the fault handling left me more than once speechless...
Eg:
/_snapshot/storage/backup
gives you a state PARTIAL
/_snapshot/storage/backup/_status
gives you a state SUCCESS
Why? The first one is blocking and refers to the backup status itself. The second one shouldn't be blocking and refers to the backup operation.
And yes. The backup operation state is SUCCESS, while the backup state might be PARTIAL (hence no full backup was made, there were errors).
So we have now an additional API that we query that then wraps the API of elasticsearch. With all these shiny scary workarounds like polling, since some APIs are blocking which might lead to a gateway timeout...
Gateway timeout? Yes. Since some operations can run a LONG (multiple hours) time and you don't want to have a ton of open connections hogging resources... You let the loadbalancer kill it. Most operations simply run in ES in the background, while the connection was killed.
So much joy and fun, isn't it?
Now add the latest SMR scandal and a few faulty (as in SMR instead of CMD) hdds in a hundred terabyte ZFS pool and you'll get my frustration level.
PS: The cluster has several dozen terabyte and a lot od nodes. If you have good advice, you're welcome - but please think carefully about this fact.
I might have accidentially vaporized people sending me links with solutions that don't work on large scale TM.2 -
!rant
fucking hate all online programming exam because they're limiting the way of examineer answering the problem as they're not allowed to import any packages.8 -
Out of curiosity, is there anyone else who feels a bit late to the game in terms of their programming skills and training?
I got my start at about 10 with a slightly obscure BASIC dialect for classic MacOS, and while I got the logical bits down strong, I never really branched out too much at the time because I had difficulty understanding some of the more advanced examples I had available on my own.
Skip ahead to college and I tried CompSci my first semester, and did fairly well on paper, but could not get the compiler to work, even copying out known examples character for character and verifying them repeatedly. So after my first semester (and the hardest-earned D I’ve ever gotten) I ended up switching my major.
Skip another 10 years and I’m talking to some people about setting up a website, but the programmer flaked out on us, so I decided to start experimenting in PHP, and while that project never went anywhere I got good at developing resources for helping me keep my Japanese skills up (lots of logic/DB work, minimal interface).
Finally, after 10 more years of tinkering and during a bout of unemployment, I had a friend lament that he needed another programmer for his shop, but didn’t know anyone reliable. I apprenticed under him, learning WordPress along the way, and these days he’s moved on while I run the shop on my own, picking up new skills as needed.
There are times I feel absolutely confident in what I’m doing, but there are several areas where I feel like I’ve got a lot of fundamental gaps I can’t figure out how to address due to my near complete lack of formal training (like when I’ve tried to do non-web programming).
Anyone else have a similar path to where they are now? Ideas on how to break out of this limiting feeling?1 -
With the current pace of gpt and dall-e, it’s looking more likely that a lot of development roles may go obsolete in the nearest future (3+ yrs).
I see the possibility of building full fledged websites and fixing bugs based on voice commands. The picture of this possibility is quite vivid in my head because it’s totally feasible technical-wise.
The only delay that may occur in this dynamics is the slow pace of its implementation by existing developer tools. Of which I think the reason is directly related to the cost of management of resource, quite the limiting factor here.
But imagine if a big tech like google creates a platform to build websites based on voice/text commands using advanced gpt inline with its access to existing corpus of data; that to me is “game-over” for web devs.16 -
I get anxious when I try to learn new things.
I'm not even sure how to describe it. Low self esteem? Low confidence? I dunno.
It feels like stage freight, but there's no audience or stage, it's just me and my computer.
No one really ever watches me, or judges me or anything.
I guess I'm a bit self emasculating because I don't really have a reason for feeling ashamed for trying out something in private.
But I feel that the fear, the stress is very distracting and it's limiting my progress.
Now, there's this project I'm rewriting in my company that I'm taking pride in and think that it has the potential to actually increase profits.
The stack is way better, it's visually better, the load times are better, the product is easier to access and try out, bla bla bla.
I guess I never felt truly proud of anything I've ever done in any company, most of what I did felt like grunt work.
But this one is actually a very well designed improvement.
So I'm hoping that this will be the excuse for not needing to prove myself anymore so that my mindset will be something like:
so what if I abandon another side project?
so what if I publish a game that looks like shit?
I may fail at newer projects, but I did win at that project I did in my company, and it wasn't a victory just because I say so, but also because my coworkers and bosses do too.
I don't know what else could help at this point.2 -
I'm learning Kotlin while trying out Android Things and that sparked my interest in learning more about Java platform again. I tripped upon the news that Oracle had change their commercial plans for the platform by going with the rolling release model and limiting LTS releases for paying customers.
Java SE 8 was one of those former LTS releases that was on my computer, leaving me vulnerable, despite that version still being the most compatible with many applications, and that's been on my computer well passed the date they cut off public support. And I'm, like, "WTF!?"
Luckily this is when open source shines at it's brightest. Both the home brew and corporations, such as Amazon and IBM, alike - mostly the latter - both agreed to create their own LTS releases using the OpenJDK code and all disturbing to the public FOR FREE with no strings attached and the sources opened. I'm sure Richard Stallman is smiling with glee.
It isn't a total finger towards Oracle. Java SE is based on OpenJDK with no difference between the two anymore aside from loss of LTS support from the public - that's it. So Oracle still benefits despite the retaliation. Probably?
Did Oracle learn nothing from OpenOffice? If the point was to get users to pay for security then they've failed in the long run because Java is open source. People have used that fact to create their own free distributions that bypass their paywall, making the need to go through Oracle pointless. And I'm glad. Open source aside, security is a big issue these days and the last thing people need is yet another thing to subscribe too.1 -
Thats top notch design.
All actions happening on the page go to one endpoint. Removing old trusted computers, changing the password, changing 2FA, you name it.
Now if you want to remove all old trusted devices, you cannot remove all at once, there is no button for it. So you click one after the other. And then it stops working. Ok, then do the normal password rotation. Hmm, button has a loading spinner and then nothing happens.
Looking into the browser console:
- All requests go to /myaccount/security/graphql
- All requests get a 429 Too many requests
- Even if you just click a panel, it tracks the action to the graphql endpoint. Or at least tries to because even that gets shot down with a 429
Pretty dumb, eh? Must be some small shitty website. It's not. It's fucking paypal. -
I first try to figure out why I really want to build this and (if the project is intended that way) why someone would use it.
Then I strip the idea down to its bare minimums so I know what I should build for it to be of any value.
And then I start building until I no longer think it's worth working on the project.
For instance:
I am kind of surprised to see that in a world where cloud and apis become more and more leading, there isn't really a commonly accepted and flexible api management platform.
There are some cloud based platforms out there that can be configured using some interface but why is it like that? Surely you aren't going to deploy multiple versions of your core with different platforms right?
That's where my latest project comes in. I want to create an on-prem api management platform which you configure to work with your api during development. Then you can deploy it to any infrastructure alongside your core api.
This way you:
- are not bound to a specific cloud
- don't have to worry about security and firewalls
- get user management and rate limiting for free
I will probably create a collab for this once the platform is mature enough.1 -
Vent-rant. Fuck Wordpress and PHP and overly limiting css frameworks in their greasy unstable fucking assholes. I find embedded and / or game-dev C++ waaaaay more fun and pleasant, and logical than this fucking pile of cuntfuckery. I think I'm gonna switch my job, hopefully there's some C/C++ companies in my area.1
-
Fucking Quarkus. Fucking Panache. Fucking ORM.
I wanted to do a fucking simple projection. First this piece of fuck, the Panache, won't let me do a Projection because of a fucking bug, that haven't implemented it properly until 2.12 (fuck and you call this v2?). Ok, upgraded, to the latest 2.16, cuz why the fuck, i'm upgrading already. But now the whole fucking quarkus app won't start! Noice! Ok, fuck it, let's go down exactly to 2.12. Quarkus started, perfect. But now, this pice of fuck Hibernate says 'collection was evicted' whenever i tried to read a collection in the setter (Access.PROPERTY), which worked just fucking fine before. But okay, fuck you. I'll write a @PostLoad method, fine, just fuck off.
But that's not the end! Now it says I cannot write `select parent.someColl is not null and parent.collection is empty as canProcess` because "is empty" only supported in where clauses. What fucking wonderful system! Well, fuck you. I'll write a union query. But guess what! JPA standard does not support union queries, nor HQL (Eclipse Link does, btw). Ok, fuck this shit, let's write a native query. But hey, fucking Panache does not support that. There is no fucking place in their fucking docs stating anything about how to use native queries.
So, fuck you quarkus, fuck you panache, fuck you hibernate, fuck you overcomplicated limiting bullshit called full-fledged ORMs. I'm moving to a fucking mybatis and fuck it. It's simple as fuck, does not fucking restrict me in writing whatever shit query I want to write and let's me map the shit just fine.1 -
Guys, how frequent do you face distraction while working? Like while coding, I'm always distracted with my phone. I know i can just throw it far away, but I do this habit on browser as well by suddenly opening a new tab to browse fb, for example.
One way to get around this is by using Pomodoro technique. But that only works if I'm not reluctant to do so. Another one is by limiting tabs opened in firefox by using an addon.
ITT: How do you deal with distraction?1 -
So.
Trash
Surrounded by it
Am not it
And it accumulates
Why is telling the truth ignored ?
Why should my life be reduced to mindless repetition while they add further temptation to simply throw said trash in the dumpster ?
Nothing seems to be enough for them
One slight after another
Wtf is wrong with them ?
Blank souless husks
That's what they are and what being around them leads to people being
But hey they're "powerful' when shredding themselves in the garbage disposal and limiting the time experiences remembered or proven to have existed
Or against things exactly 3 feet in heigt
Killing them would be a mercy
Their hollow brainless minds will learn eventually2 -
Hi fellow devRanters, I need some advice on how to detect web traffic coming from bad/malicious bots and block them.
I have ELK (Elastic) stack set up to capture the logs from the sites, I have already blocked the ones that are obviously bad (bad user-agent, IP addresses known for spamming etc). I know you can tell by looking at how fast/frequently they crawl the site but how would I know if I block the one that's causing the malicious and non-human traffic? I am not sure if I should block access from other countries because I think the bots are from local.
I am lost, I don't know what else I can do - I can't use rate limiting on the sites and I can't sign up for a paid service cause management wants everything with the price of peanuts.
Rant:
Someone asked why I can't just read through the logs (from several mid-large scale websites) and pick out the baddies.
*facepalm* Here's the gigabytes log files.9 -
It's shockingly bad, Jesus 😣
https://stackoverflow.com/questions...
I know I'm just whining atp instead of moving on something else. For lack of anything else, I blame capitalism for limiting my options. I would never subject myself to this torture of my own volition. Yet, you have to wonder how a joke like this. Even a routing library developed over a code kata or aboard a flight would at least, include a regex capturing possibility of trailing slashes. How would one ever imagine that all clients of this api have to strictly either end their url with slashes, otherwise they get slammed with a 404
Unbelievable4 -
Hey all! I'm gonna be graduating soon from grad school and I'm starting to realize that I have no idea what I wanna do with my programming career!
I currently work as QA but have been really working towards being a programmer but the only problem is that I really dislike web applications ... specifically front end.
With most jobs being full stack web apps, I feel like I'm really gonna be limiting myself once I'm applying for junior software engineering jobs.
I'm just wanting your thoughts and some advice on what I should do since in still trying to figure things out. The only goal I have in life for my career at the moment is to be a software engineer.5 -
"To say a grid is limiting is to say that language is limiting, or typography is limiting. " - Ellen Lupton
-
WordPress Pods "introduced new Access Rights checks and comprehensive functionality to assist you in limiting how your content types can be used by other users."
In other words, they have just introduced a breaking change that hides CMS content elements that were expected to be visible publicly to everyone. -
I may have inadvertently gotten my old university's Comp Sci System Services addicted to CTF wargames. oops.
I also just found out that you can prevent a more command from automatically exiting on completion only by limiting the size of the window of your terminal. I lost a good 4 hours of trying literally every ssh command combination I could, when all I had to do was use a small terminal screen. Whoever designed this last challenge should be given an award and then shot.3 -
Android 13 will Unlock Certain Device Controls even when Locked
Android 13 is the newest operating system that will be available soon. The OS comes with a range of new features, one of which is unlocking certain device controls even when the device is locked. This is a game-changer that will significantly enhance the user experience.
Introduction
The Android operating system has undergone numerous changes since its inception. With every new release, users are treated to new features that enhance the overall user experience. Android 13 is no different, and it promises to revolutionize the way we interact with our devices. One of the most exciting features of Android 13 is unlocking certain device controls even when the device is locked. In this article, we'll take a closer look at this feature and explore its implications for users.
What is Android 13?
Before we delve into the details of Android 13, let's take a moment to understand what it is. Android is an operating system designed primarily for mobile devices such as smartphones and tablets. It was developed by Google and is currently the most widely used mobile operating system in the world. Android 13 is the latest version of this operating system, and it comes with a range of new features that will make it even more user-friendly.
Device Control Access
One of the most exciting features of Android 13 is the ability to access certain device controls even when the device is locked. This means that users will be able to control various functions of their device without having to unlock it. Some of the controls that will be accessible include the flashlight, camera, and voice assistant.
How will it work?
The process of accessing device controls when the device is locked will be straightforward. Users will only need to swipe left on the lock screen to access a new panel that will display the controls. The controls will be easy to use, and users will be able to activate or deactivate them with a single tap. This feature will make it easier for users to perform certain tasks without having to unlock their device.
Implications for Users
The ability to access certain device controls when the device is locked will have several implications for users. Firstly, it will make it easier for users to perform certain tasks quickly. For example, if you need to use the flashlight, you won't have to go through the process of unlocking your device and navigating to the flashlight app. Instead, you can simply access the flashlight control from the lock screen.
Secondly, this feature will enhance the security of the device. By limiting access to certain controls, users can ensure that their device remains secure even when it is locked. For example, the camera control will only be accessible when the device is unlocked, which will prevent unauthorized users from taking pictures or videos.
Other Features of Android 13
Apart from the device control access feature, Android 13 comes with several other exciting features. These include:
Improved Privacy Controls
Android 13 comes with improved privacy controls that give users more control over their data. Users will be able to decide which apps have access to their location, contacts, and other sensitive data.
Enhanced Multitasking
Multitasking has always been a key feature of Android, and Android 13 takes it to the next level. Users will be able to view multiple apps at the same time, making it easier to switch between them.
New Messaging Features
Android 13 comes with new messaging features that will make it easier for users to communicate with their friends and family. These include the ability to react to messages with emojis and the ability to schedule messages. 2
2
