Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "security issue"
-
So, someone submitted a 'bug' to Mozilla.
As some of you may know, in the next year, the new mass surveillance law in the Netherlands is going into effect.
Another fun fact is that the dutch security agencies/government have their own CA (Certificate Authority) for SSL/TLS certificates.
The new law says that the AIVD (dutch NSA/GCHQ equivilant) is allowed to hack into systems through obtained certificates and also that they're allowed to INTERCEPT TRAFFIC THROUGH OBTAINED PRIVATE SSL/TLS KEYS.
So someone actually had the fucking balls to submit a fucking issue to Mozilla saying that the Dutch State certs shouldn't be accepted anymore when the new mass surveillance law gets into place.
This person deservers a fucking medal if you ask me.68 -
As a long-time iPhone user, I am really sorry to say it but I think Apple has completed their transition to being a company that is incompetent when it comes to software development and software development processes.
I’ve grown tired of hearing some developers tell me about Apple’s scale and how software development is hard and how bugs should be expected. All of those are true, but like most rules of law, incompetence and gross negligence trumps all of that.
I’m writing this because of the telugu “bug”/massive, massive security issue in iOS 11.2.5. I personally think it’s one of the worst security issues in the history of modern devices/software in terms of its ease of exploitation, vast reach, and devastating impact if used strategically. But, as a software developer, I would have been able to see past all of that, but Apple has shown their true incompetence on this issue and this isn’t about a bug.
It’s about a company that has a catastrophic bug in their desktop and mobile platforms and haven’t been able to, or cared to, patch it in the 3 or so days it’s been known about. It’s about a company, who as of a view days ago, hasn’t followed the basic software development process of removing an update (11.2.5) that was found to be flawed and broken. Bugs happen, but that kind of incompetence is cultural and isn’t a mistake and it certainly isn’t something that people should try to justify.
This has also shown Apple’s gross incompetence in terms of software QA. This isn’t the first time a non-standard character has crashed iOS. Why would a competent software company implement a step in their QA, after the previous incident(s), to specifically test for issues like this? While Android has its issues too and I know some here don’t like Google, no one can deny that Google at least has a solid and far superior QA process compared to Apple.
Why am I writing this? Because I’m fed up. Apple has completely lost its way. devRant was inaccessible to iOS users a couple of times because of this bug and I know many, many other apps and websites that feature user-generated content experienced the same thing. It’s catastrophic. Many times we get sidetracked and really into security issues, like meltdown/spectre that are exponentially harder to take advantage of than this one. This issue can be exploited by a 3 year old. I bet no one can produce a case where a security issue was this exploitable yet this ignored on a whole.
Alas, here we are, days later, and the incompetent leadership at Apple has still not patched one of the worst security bugs the world has ever seen. 81
81 -
My mom got audited for storing sensitive client information in her gmail account without using a vpn or any other real security.
I had been telling her this was an issue for literally the last three years and shes brushed me off every time.
I got yelled at for not telling her I was serious.34 -
A former colleague made an online shopping app. Boss wanted to promote him to Senior Developer when he still working with us.
14 days ago another colleague checked the code and told the boss that it's ready for production. No one asked me because everyone in the company thinks am the stupid developer of them all.
So what happened?
Well the total value of the cart was being over to payment gateway using a hidden field. Well you know the rest of the story.
The client has sued our company for this issue and boss came running to me and asked me to check if it was our fault or something else.
I checked and found the hidden value where the total value of cart was being stored and send over to payment gateway. The following is the conversation between me and the colleague who checked the code:
Me: So you checked the code and everything was okay?
Him: Yes, all good.
Me: Did you see this hidden field where the total value of cart is being passed to the payment gateway?
Him: Yes
Me: Why didn't you fix this?
Him: What's there to fix?
Me: Well someone can temper the value and let it pass to the payment gateway.
Him: No, they can't we are using https
Me: I' am done with you
He has Masters in software engineering and has few security certificates.25 -
Recently had an interview with a company. At some point an SELinux question came up and while I didn't provide the best answer ever (I'm hardly familiar with SELinux and mentioned that as well beforehand so they knew), it was technically correct and the reaction of the interviewers was funny.
TI (technical interviewer): say your php script isn't executed and after a while you find out that SELinux is blocking php script execution, how can you fix that?
Me: setenforce 0...? (essentially disabling SELinux at all)
TI: disabling it entirely for getting php execution to work?! That doesn't sound like a good solu...
HRI (HR (non technical) interviewer, also present): *turns to TI* - but, would it solve the problem?
TI: 😐 well, yes, but... That's a bad thing to do so I wouldn't count is corre..
HRI: *still aiming towards TI* but you simply asked him for a way to solve the php execution issue, would his answer work? Regardless of whether it's the best or worst solution, would it be a solution which works?
TI: well... yes...
HRI: then he answered correctly I'd say, next!
(yes, I'm aware that my answer wasn't good as for security at all but it would have solved that problem which is what was asked)18 -
Tldr :
Office Building : 1
Population: 5000
Number of PC users: 5000
No of Spare mice: 0
Day 1:
Training period commences.
My mouse laser sensor doesn't work.
Solution: Use this mouse to log in to your system.
Open the company portal.
Connect to vpn.
Enter username password.
Create a ticket for mouse replacement.
Done.
Day 3
I bring my own mouse.
Confiscated at security.
Becomes a security violation.
Day 9
I get a call from helpdesk.
Agent- what is the problem?
Me- my mouse is not working.
Agent- why?
Me- what do you mean? Something is wrong with the sensor.
Agent- clean the sensor.
Disconnects call.
Marks ticket as resolved.
Me- WTF just happened!
Naturally, I escalate the issue.
Day 15
Level 2 Agent- what happened? Why have you escalated the issue?
Me- I need a mouse, waiting since 2 weeks.
Him- No mouse is available
Me- you don't have a single spare mouse available in an office with 5000 PC users?
Him- no they're out of stock.
Me- when will it be back in stock?
Him- we will 'soon' launch a tender for quotations from sellers.
Me- time?
Him- 1 week.
Day 34
I email the head of supplies for the city office. Next day I get a used super small mouse, which doesn't have a left button. Anyways, I've given up hope now.
Day 45
I become a master at keyboard shortcuts.
Finish my training.
Get transferred to another city.
No mouse till date.
Surprisingly, this was one of the top recruiters in my country. Never knew, MNCs can be so so inefficient for such simple tasks.
Start-ups are way better in this regard. Latest tech, small community, minimal bureaucracy and a lot of respect and things to learn.15 -
First internship (ranted about it before).
- Had to google translate their entire internal crm.
- pointed out major security flaws and got a speech saying that "I shouldn't think so high of myself and I didn't have the fucking right to criticize their products"
- every time the boss came to the office after a failed sales presentation, we (interns) got called the most nasty stuff. Yes. We didn't have anything to do with that at all.
- I had "hygiene issues": window to the south with 35-40 degrees (Celsius) feeling temperature and no airco. Deo didn't really make a difference but wasn't allowed to use it there anyways. Details: I have a transpiration issue so I sweat shitloads more than other people, that didn't help at all.
- nearly got fired because I had to to to the doctor in company time for a serious health issue.
- was (no kidding) REQUIRES to use internet explorer and we were monitored constantly.
Self esteem dropped through the fucking ground there.12 -
Ranted about him before but this just came to my mind again.
The fucking windows (to the max) fanboy I had to deal with for too long.
Every time I mentioned something about what programming language to use in a project he was NOT part of:
"I know it's none of my business, BUT I think you should use .net"
(All backend JavaScript and php guys).
Every time I mentioned something about what server system to use:
"I know it's none of my business but I think you should use Windows server"
(All Linux guys)
Every time I'd say something positive about Linux he'd search as long as needed to prove that that was also a windows thing (didn't even come close sometimes)
Every time I told the devs there about a windows security issue (as in "guys they found this thing, install the next update to stay safe :)" - "ahhh will do, thanks for letting know man!") he'd search as long as needed to prove that Linux also had had security issues like that.
(Okay?!? I know?!? I'm just trying to notify people so their systems stay secure and they're genuinely happy with that so STFU)
MOTHERFUCKER.16 -
If the below is you, please stop. I'm starting a revolution called #AnswerTheQuestion
A: Hey, just checked your code, you have a huge security issue in XYZ, you should really address that.
B: Oh god I had no idea, how do I fix it?
A: Well it depends on how you *want* to fix it, no one solution is always the right one.
B: ... Ok, well could you give me some advice?
A: Well, there are many ways to approach this kind of work, but all I can say is that this way, is definitely not the correct one.
B: ... Ok, well how would you do it?
A: That would depend on the customer requirements.
B: ... the requirements is to have a website that isn't easily hackable, what do I do?
A: Nowadays, its pretty hard to make a website completely not hackable.
B: ALL THE SERVERS ARE SHOWING RED, PLEASE HELP ME!!!
A: ........ you really shouldn't prejudge colours. The colour red doesn't always mean danger, depends purely on the use case.9 -
Example #1 of ??? Explaining why I dislike my coworkers.
[Legend]
VP: VP of Engineering; my boss’s boss. Founded the company, picked the CEO, etc.
LD: Lead dev; literally wrote the first line of code at the company, and has been here ever since.
CISO: Chief Information Security Officer — my boss when I’m doing security work.
Three weeks ago (private zoom call):
> VP to me: I want you to know that anything you say, while wearing your security hat, goes. You can even override me. If you need to hold a release for whatever reason, you have that power. If I happen to disagree with a security issue you bring up, that’s okay. You are in charge of release security. I won’t be mad or hold it against you. I just want you to do your job well.
Last week (engineering-wide meeting):
> CISO: From now on we should only use external IDs in urls to prevent a malicious actor from scraping data or automating attacks.
> LD: That’s great, and we should only use normal IDs in logging so they differ. Sounds more secure, right?
> CISO: Absolutely. That way they’re orthogonal.
> VP: Good idea, I think we should do this going forward.
Last weekend (in the security channel):
> LD: We should ONLY use external IDs in urls, and ONLY normal IDs in logging — in other words, orthogonal.
> VP: I agree. It’s better in every way.
Today (in the same security channel):
> Me: I found an instance of using a plain ID in a url that cancels a payment. A malicious user with or who gained access to <user_role> could very easily abuse this to cause substantial damage. Please change this instance and others to using external IDs.
> LD: Whoa, that goes way beyond <user_role>
> VP: You can’t make that decision, that’s engineering-wide!
Not only is this sane security practice, you literally. just. agreed. with this on three separate occasions in the past week, and your own head of security also posed this before I brought it up! And need I remind you that it is still standard security practice!?
But nooo, I’m overstepping my boundaries by doing my job.
Fucking hell I hate dealing with these people.14 -
Privacy & security violations piss me off. Not to the point that I'll write on devRant about it, but to the point that coworkers get afraid from the bloodthirsty look in my eyes.
I know all startups proclaim this, but the one I work at is kind of industry-disrupting. Think Uber vs taxi drivers... so we have real, malicious enemies.
Yet there's still this mindset of "it won't happen to us" when it comes to data leaks or corporate spying.
Me: "I noticed we are tracking our end users without their consent, and store not just the color of their balls, but also their favorite soup flavor and how often they've cheated on their partner, as plain text in the system for every employee to read"
Various C-randomletter-Os: "Oh wow indubitably most serious indeed! Let's put 2 scrumbag masters on the issue, we will tackle this in a most agile manner! We shall use AI blockchains in the elastic cloud to encrypt those ball-colors!"
NO WHAT I MEANT WAS WHY THE FUCK DO WE EVEN STORE THAT INFORMATION. IT DOES IN NO WAY RELATE TO OUR BUSINESS!
"No reason, just future requirements for our data scientists"
I'M GRABBING A HARDDRIVE SHREDDER, THE DB SERVER GOES FIRST AND YOUR PENIS RIGHT AFTER THAT!
(if it's unclear, ball color was an optimistic euphemism for what boiled down to an analytics value which might as well have been "nigger: yes/no")12 -
!rant
The change log from notepad++ update. The last paragraph is the cream!
" The issue of a hijacked DLL concerns scilexer.dll (needed by Notepad++) on a compromised PC, which is replaced by a modified scilexer.dll built by the CIA. When Notepad++ is launched, the modified scilexer.dll is loaded instead of the original one.
It doesn't mean that CIA is interested in your coding skill or in your sex message content typed in Notepad++, but rather it prevents raising any red flags while the DLL does data collection in the background.
It's not a vulnerability/security issue in Notepad++, but for remedying this issue, from this release (v7.3.3) forward, notepad++.exe checks the certificate validation in scilexer.dll before loading it. If the certificate is missing or invalid, then it just won't be loaded, and Notepad++ will fail to launch.
Checking the certificate of DLL makes it harder to hack. Note that once users’ PCs are compromised, the hackers can do anything on the PCs. This solution only prevents from Notepad++ loading a CIA homemade DLL. It doesn't prevent your original notepad++.exe from being replaced by modified notepad++.exe while the CIA is controlling your PC.
Just like knowing the lock is useless for people who are willing to go into my house, I still shut the door and lock it every morning when I leave home. We are in a f**king corrupted world, unfortunately. "2 -
Wow... this is the perfect week for this topic.
Thursday, is the most fucked off I’ve ever been at work.
I’ll preface this story by saying that I won’t name names in the public domain to avoid anyone having something to use against me in court. But, I’m all for the freedom of information so please DM if you want to know who I’m talking about.
Yesterday I handed in my resignation, to the company that looked after me for my first 5 years out of university.
Thursday was my breaking point but to understand why I resigned you need a little back story.
I’m a developer for a corporate in a team of 10 or so.
The company that I work for is systemically incompetent and have shown me this without fail over the last 6 months.
For the last year we’ve had a brilliant contracted, AWS Certified developer who writes clean as hell hybrid mobile apps in Ion3, node, couch and a tonne of other up to the minute technologies. Shout out to Morpheus you legend, I know you’re here.
At its core my job as a developer is to develop and get a product into the end users hands.
Morpheus was taking some shit, and coming back to his desk angry as fuck over the last few months... as one of the more experienced devs and someone who gives a fuck I asked him what was up.
He told me, company want their mobile app that he’s developed on internal infrastructure... and that that wasn’t going to work.
Que a week of me validating his opinion, looking through his work and bringing myself up to speed.
I came to the conclusion that he’d done exactly what he was asked to, brilliant Work, clean code, great consideration to performance and UX in his design. He did really well. Crucially, the infrastructure proposed was self-contradicting, it wouldn’t work and if they tried to fudge it in it would barely fucking run.
So I told everyone I had the same opinion as him.
4 months of fucking arguing with internal PMs, managers and the project team go by... me and morpheus are told we’re not on the project.
The breaking point for me came last Wednesday, given no knowledge of the tech, some project fannies said Morpheus should be removed and his contract terminated.
I was up in fucking arms. He’d done everything really well, to see a fellow developer take shit for doing his job better than anyone else in [company] could was soul destroying.
That was the straw on the camels back. We don’t come to work to take shit for doing a good job. We don’t allow our superiors to give people shit in our team when they’re doing nothing but a good job. And you know what: the opinion of the person that knows what they’re talking about is worth 10 times that of the fools who don’t.
My manager told me to hold off, the person supposed to be supporting us told me to stand down. I told him I was going to get the app to the business lead because he fucking loves it and can tell us if there’s anything to change whilst architecture sorts out their outdated fucking ideas.
Stand down James. Do nothing. Don’t do your job. Don’t back Morpheus with his skills and abilities well beyond any of ours. Do nothing.
That was the deciding point for me, I said if Morpheus goes... I go... but then they continued their nonsense, so I’m going anyway.
I made the decision Thursday, and Friday had recruiters chomping at the bit to put the proper “senior” back in my title, and pay me what I’m worth.
The other issues that caused me to see this company in it’s true form:
- I raised a key security issue, documented it, and passed it over to the security team.
- they understood, and told the business users “we cannot use ArcGIS’ mobile apps, they don’t even pretend to be secure”
- the business users are still using the apps going into the GDPR because they don’t understand the ramifications of the decisions they’re making.
I noticed recently that [company] is completely unable to finish a project to time or budget... and that it’s always the developers put to blame.
I also noticed that middle management is in a constant state of flux with reorganisations because in truth the upper managers know they need to sack them.
For me though, it was that developers in [company], the people that know what they’re talking about; are never listened to.
Fuck being resigned to doing a shit job.
Fuck this company. On to one that can do it right.
Morpheus you beautiful bastard I know you’ll be off soon too but I also feel I’ve made a friend for life. “Private cloud” my arse.
Since making the decision Thursday I feel a lot more free, I have open job offers at places that do this well. I have a position of power in the company to demand what I need and get it. And I have the CEO and CTO’s ears perking up because their department is absolutely shocking.
Freedom is a wonderful feeling.12 -
Fucking crunchyroll hardcodes their access tokens in a Constants Class in their APK, technically that is a security issue.
What the actual fuck Crunchyroll!? No fucking wonder you got DNS Hijacked so quick, security is literally your second priority you dumbed down twats, get some real devs and some real QAs for fucking god sakes, you're tearing down your own system by inviting exploits.8 -
So, some time ago, I was working for a complete puckered anus of a cosmetics company on their ecommerce product. Won't name names, but they're shitty and known for MLM. If you're clever, go you ;)
Anyways, over the course of years they brought in a competent firm to implement their service layer. I'd even worked with them in the past and it was designed to handle a frankly ridiculous-scale load. After they got the 1.0 released, the manager was replaced with some absolutely talentless, chauvinist cuntrag from a phone company that is well known for having 99% indian devs and not being able to heard now. He of course brought in his number two, worked on making life miserable and running everyone on the team off; inside of a year the entire team was ex-said-phone-company.
Watching the decay of this product was a sheer joy. They cratered the database numerous times during peak-load periods, caused $20M in redis-cluster cost overrun, ended up submitting hundreds of erroneous and duplicate orders, and mailed almost $40K worth of product to a random guy in outer mongolia who is , we can only hope, now enjoying his new life as an instagram influencer. They even terminally broke the automatic metadata, and hired THIRTY PEOPLE to sit there and do nothing but edit swagger. And it was still both wrong and unusable.
Over the course of two years, I ended up rewriting large portions of their infra surrounding the centralized service cancer to do things like, "implement security," as well as cut memory usage and runtimes down by quite literally 100x in the worst cases.
It was during this time I discovered a rather critical flaw. This is the story of what, how and how can you fucking even be that stupid. The issue relates to users and their reports and their ability to order.
I first found this issue looking at some erroneous data for a low value order and went, "There's no fucking way, they're fucking stupid, but this is borderline criminal." It was easy to miss, but someone in a top down reporting chain had submitted an order for someone else in a different org. Shouldn't be possible, but here was that order staring me in the face.
So I set to work seeing if we'd pwned ourselves as an org. I spend a few hours poring over logs from the log service and dynatrace trying to recreate what happened. I first tested to see if I could get a user, not something that was usually done because auth identity was pervasive. I discover the users are INCREMENTAL int values they used for ids in the database when requesting from the API, so naturally I have a full list of users and their title and relative position, as well as reports and descendants in about 10 minutes.
I try the happy path of setting values for random, known payment methods and org structures similar to the impossible order, and submitting as a normal user, no dice. Several more tries and I'm confident this isn't the vector.
Exhausting that option, I look at the protocol for a type of order in the system that allowed higher level people to impersonate people below them and use their own payment info for descendant report orders. I see that all of the data for this transaction is stored in a cookie. Few tests later, I discover the UI has no forgery checks, hashing, etc, and just fucking trusts whatever is present in that cookie.
An hour of tweaking later, I'm impersonating a director as a bottom rung employee. Score. So I fill a cart with a bunch of test items and proceed to checkout. There, in all its glory are the director's payment options. I select one and am presented with:
"please reenter card number to validate."
Bupkiss. Dead end.
OR SO YOU WOULD THINK.
One unimportant detail I noticed during my log investigations that the shit slinging GUI monkeys who butchered the system didn't was, on a failed attempt to submit payment in the DB, the logs were filled with messages like:
"Failed to submit order for [userid] with credit card id [id], number [FULL CREDIT CARD NUMBER]"
One submit click later and the user's credit card number drops into lnav like a gatcha prize. I dutifully rerun the checkout and got an email send notification in the logs for successful transfer to fulfillment. Order placed. Some continued experimentation later and the truth is evident:
With an authenticated user or any privilege, you could place any order, as anyone, using anyon's payment methods and have it sent anywhere.
So naturally, I pack the crucifixion-worthy body of evidence up and walk it into the IT director's office. I show him the defect, and he turns sheet fucking white. He knows there's no recovering from it, and there's no way his shitstick service team can handle fixing it. Somewhere in his tiny little grinchly manager's heart he knew they'd caused it, and he was to blame for being a shit captain to the SS Failboat. He replies quietly, "You will never speak of this to anyone, fix this discretely." Straight up hitler's bunker meme rage.13 -
This is from my days of running a rather large (for its time) Minecraft server. A few of our best admins were given access to the server console. For extra security, we also had a second login stage in-game using a command (in case their accounts were compromised). We even had a fairly strict password strength policy.
But all of that was defeated by a slightly too stiff SHIFT key. See, in-game commands were typed in chat, prefixed with a slash -- SHIFT+7 on German-ish keyboards. And so, when logging in, one of our head admins didn't realize his SHIFT key didn't register and proudly broadcast to the server "[Admin] username: 7login hisPasswordHere".
This was immediately noticed by the owner of a 'rival' server who was trying to copy some cool thing that we had. He jumped onto the console that he found in an nmap scan a week prior (a scan that I detected and he denied), promoted himself to admin and proceeded to wreak havoc.
I got a call, 10-ish minutes later, that "everything was literally on fire". I immediately rolled everything back (half-hourly backups ftw) and killed the console just in case.
The best part was the Skype call with that admin that followed. I wasn't too angry, but I did want him to suffer a little, so I didn't immediately tell him that we had good backups. He thought he'd brought the downfall of our server. I'm pretty sure he cried.5 -
Had a discussion with a developer about security. His software transfers all user data (password and files) unencrypted, so anyone can grab them with wireshark. I told him that this is a severe issue. He said no its no problem because if you get hacked its your own fault, because you probably used an insecure network. NO ! YOU FUCKING MALADJUSTED SHEEP-MOLESTING OBJECT OF EXECRATION, YOU SHOULD ALWAYS ENCRYPT SENSITIVE USERDATA NO MATTER WHAT NETWORK YOU USE. FUCKING KILL ME ALREADY.
Not implementing encryption is one thing but then acting like its no problem is a fucking nother one. Why do people not understand that security of userdata is important???11 -
A friend called ITIS guys about some network issue on his system.
Frnd : Hi, I'm facing some security policy issues on my system. Could you help me connect?
ITIS guy: Ok. Please run 'gpupdate /force' cmd from cmdpromt.
Frnd: Well actually I'm on Linux.
ITIS guy: Well, at least give it a try and tell me how it goes.
*Facepalm*? *Bodypalm*? Murder?4 -
I've got a confession to make.
A while ago I refurbished this old laptop for someone, and ended up installing Bodhi on it. While I was installing it however, I did have some wicked thoughts..
What if I could ensure that the system remains up-to-date by running an updater script in a daily cron job? That may cause the system to go unstable, but at least it'd be up-to-date. Windows Update for Linux.
What if I could ensure that the system remains protected from malware by periodically logging into it and checking up, and siphoning out potential malware code? The network proximity that's required for direct communication could be achieved by offering them free access to one of my VPN servers, in the name of security or something like that. Permanent remote access, in the name of security. I'm not sure if Windows has this.
What if I could ensure that the system remains in good integrity by disabling the user from accessing root privileges, and having them ask me when they want to install a piece of software? That'd make the system quite secure, with the only penetration surface now being kernel exploits. But it'd significantly limit what my target user could do with their own machine.
At the end I ended up discarding all of these thoughts, because it'd be too much work to implement and maintain, and it'd be really non-ethical. I felt filthy from even thinking about these things. But the advantages of something like this - especially automated updates, which are a real issue on my servers where I tend to forget to apply them within a couple of weeks - can't just be disregarded. Perhaps Microsoft is on to something?11 -
Long rant ahead.. so feel free to refill your cup of coffee and have a seat 🙂
It's completely useless. At least in the school I went to, the teachers were worse than useless. It's a bit of an old story that I've told quite a few times already, but I had a dispute with said teachers at some point after which I wasn't able nor willing to fully do the classes anymore.
So, just to set the stage.. le me, die-hard Linux user, and reasonably initiated in networking and security already, to the point that I really only needed half an ear to follow along with the classes, while most of the time I was just working on my own servers to pass the time instead. I noticed that the Moodle website that the school was using to do a big chunk of the course material with, wasn't TLS-secured. So whenever the class begins and everyone logs in to the Moodle website..? Yeah.. it wouldn't be hard for anyone in that class to steal everyone else's credentials, including the teacher's (as they were using the same network).
So I brought it up a few times in the first year, teacher was like "yeah yeah we'll do it at some point". Shortly before summer break I took the security teacher aside after class and mentioned it another time - please please take the opportunity to do it during summer break.
Coming back in September.. nothing happened. Maybe I needed to bring in more evidence that this is a serious issue, so I asked the security teacher: can I make a proper PoC using my machines in my home network to steal the credentials of my own Moodle account and mail a screencast to you as a private disclosure? She said "yeah sure, that's fine".
Pro tip: make the people involved sign a written contract for this!!! It'll cover your ass when they decide to be dicks.. which spoiler alert, these teachers decided they wanted to be.
So I made the PoC, mailed it to them, yada yada yada... Soon after, next class, and I noticed that my VPN server was blocked. Now I used my personal VPN server at the time mostly to access a file server at home to securely fetch documents I needed in class, without having to carry an external hard drive with me all the time. However it was also used for gateway redirection (i.e. the main purpose of commercial VPN's, le new IP for "le onenumity"). I mean for example, if some douche in that class would've decided to ARP poison the network and steal credentials, my VPN connection would've prevented that.. it was a decent workaround. But now it's for some reason causing Moodle to throw some type of 403.
Asked the teacher for routers and switches I had a class from at the time.. why is my VPN server blocked? He replied with the statement that "yeah we blocked it because you can bypass the firewall with that and watch porn in class".
Alright, fair enough. I can indeed bypass the firewall with that. But watch porn.. in class? I mean I'm a bit of an exhibitionist too, but in a fucking class!? And why right after that PoC, while I've been using that VPN connection for over a year?
Not too long after that, I prematurely left that class out of sheer frustration (I remember browsing devRant with the intent to write about it while the teacher was watching 😂), and left while looking that teacher dead in the eyes.. and never have I been that cold to someone while calling them a fucking idiot.
Shortly after I've also received an email from them in which they stated that they wanted compensation for "the disruption of good service". They actually thought that I had hacked into their servers. Security teachers, ostensibly technical people, if I may add. Never seen anyone more incompetent than those 3 motherfuckers that plotted against me to save their own asses for making such a shitty infrastructure. Regarding that mail, I not so friendly replied to them that they could settle it in court if they wanted to.. but that I already knew who would win that case. Haven't heard of them since.
So yeah. That's why I regard those expensive shitty pieces of paper as such. The only thing they prove is that someone somewhere with some unknown degree of competence confirms that you know something. I think there's far too many unknowns in there.
Nowadays I'm putting my bets on a certification from the Linux Professional Institute - a renowned and well-regarded certification body in sysadmin. Last February at FOSDEM I did half of the LPIC-1 certification exam, next year I'll do the other half. With the amount of reputation the LPI has behind it, I believe that's a far better route to go with than some random school somewhere.25 -
The solution for this one isn't nearly as amusing as the journey.
I was working for one of the largest retailers in NA as an architect. Said retailer had over a thousand big box stores, IT maintenance budget of $200M/year. The kind of place that just reeks of waste and mismanagement at every level.
They had installed a system to distribute training and instructional videos to every store, as well as recorded daily broadcasts to all store employees as a way of reducing management time spend with employees in the morning. This system had cost a cool 400M USD, not including labor and upgrades for round 1. Round 2 was another 100M to add a storage buffer to each store because they'd failed to account for the fact that their internet connections at the store and the outbound pipe from the DC wasn't capable of running the public facing e-commerce and streaming all the video data to every store in realtime. Typical massive enterprise clusterfuck.
Then security gets involved. Each device at stores had a different address on a private megawan. The stores didn't generally phone home, home phoned them as an access control measure; stores calling the DC was verboten. This presented an obvious problem for the video system because it needed to pull updates.
The brilliant Infosys resources had a bright idea to solve this problem:
- Treat each device IP as an access key for that device (avg 15 per store per store).
- Verify the request ip, then issue a redirect with ANOTHER ip unique to that device that the firewall would ingress only to the video subnet
- Do it all with the F5
A few months later, the networking team comes back and announces that after months of work and 10s of people years they can't implement the solution because iRules have a size limit and they would need more than 60,000 lines or 15,000 rules to implement it. Sad trombones all around.
Then, a wild DBA appears, steps up to the plate and says he can solve the problem with the power of ORACLE! Few months later he comes back with some absolutely batshit solution that stored the individual octets of an IPV4, multiple nested queries to the same table to emulate subnet masking through some temp table spanning voodoo. Time to complete: 2-4 minutes per request. He too eventually gives up the fight, sort of, in that backhanded way DBAs tend to do everything. I wish I would have paid more attention to that abortion because the rationale and its mechanics were just staggeringly rube goldberg and should have been documented for posterity.
So I catch wind of this sitting in a CAB meeting. I hear them talking about how there's "no way to solve this problem, it's too complex, we're going to need a lot more databases to handle this." I tune in and gather all it really needs to do, since the ingress firewall is handling the origin IP checks, is convert the request IP to video ingress IP, 302 and call it a day.
While they're all grandstanding and pontificating, I fire up visual studio and:
- write a method that encodes the incoming request IP into a single uint32
- write an http module that keeps an in-memory dictionary of uint32,string for the request, response, converts the request ip and 302s the call with blackhole support
- convert all the mappings in the spreadsheet attached to the meetings into a csv, dump to disk
- write a wpf application to allow for easily managing the IP database in the short term
- deploy the solution one of our stage boxes
- add a TODO to eventually move this to a database
All this took about 5 minutes. I interrupt their conversation to ask them to retarget their test to the port I exposed on the stage box. Then watch them stare in stunned silence as the crow grows cold.
According to a friend who still works there, that code is still running in production on a single node to this day. And still running on the same static file database.
#TheValueOfEngineers2 -
The website for our biggest client went down and the server went haywire. Though for this client we don’t provide any infrastructure, so we called their it partner to start figuring this out.
They started blaming us, asking is if we had upgraded the website or changed any PHP settings, which all were a firm no from us. So they told us they had competent people working on the matter.
TL;DR their people isn’t competent and I ended up fixing the issue.
Hours go by, nothing happens, client calls us and we call the it partner, nothing, they don’t understand anything. Told us they can’t find any logs etc.
So we setup a conference call with our CXO, me, another dev and a few people from the it partner.
At this point I’m just asking them if they’ve looked at this and this, no good answer, I fetch a long ethernet cable from my desk, pull it to the CXO’s office and hook up my laptop to start looking into things myself.
IT partner still can’t find anything wrong. I tail the httpd error log and see thousands upon thousands of warning messages about mysql being loaded twice, but that’s not the issue here.
Check top and see there’s 257 instances of httpd, whereas 256 is spawned by httpd, mysql is using 600% cpu and whenever I try to connect to mysql through cli it throws me a too many connections error.
I heard the IT partner talking about a ddos attack, so I asked them to pull it off the public network and only give us access through our vpn. They do that, reboot server, same problems.
Finally we get the it partner to rollback the vm to earlier last night. Everything works great, 30 min later, it crashes again. At this point I’m getting tired and frustrated, this isn’t my job, I thought they had competent people working on this.
I noticed that the db had a few corrupted tables, and ask the it partner to get a dba to look at it. No prevail.
5’o’clock is here, we decide to give the vm rollback another try, but first we go home, get some dinner and resume at 6pm. I had told them I wanted to be in on this call, and said let me try this time.
They spend ages doing the rollback, and then for some reason they have to reconfigure the network and shit. Once it booted, I told their tech to stop mysqld and httpd immediately and prevent it from start at boot.
I can now look at the logs that is leading to this issue. I noticed our debug flag was on and had generated a 30gb log file. Tail it and see it’s what I’d expect, warmings and warnings, And all other logs for mysql and apache is huge, so the drive is full. Just gotta delete it.
I quietly start apache and mysql, see the website is working fine, shut it down and just take a copy of the var/lib/mysql directory and etc directory just go have backups.
Starting to connect a few dots, but I wasn’t exactly sure if it was right. Had the full drive caused mysql to corrupt itself? Only one way to find out. Start apache and mysql back up, and just wait and see. Meanwhile I fixed that mysql being loaded twice. Some genius had put load mysql.so at the top and bottom of php ini.
While waiting on the server to crash again, I’m talking to the it support guy, who told me they haven’t updated anything on the server except security patches now and then, and they didn’t have anyone familiar with this setup. No shit, it’s running php 5.3 -.-
Website up and running 1.5 later, mission accomplished.6 -
Root gets ignored.
I've been working on this monster ticket for a week and a half now (five days plus other tickets). It involves removing all foreign keys from mass assignment (create, update, save, ...), which breaks 1780 specs.
For those of you who don't know, this is part of how rails works. If you create a Page object, you specify the book_id of its parent Book so they're linked. (If you don't, they're orphans.) Example: `Page.create(text: params[:text], book_id: params[:book_id], ...)` or more simply: `Page.create(params)`
Obviously removing the ability to do this is problematic. The "solution" is to create the object without the book_id, save it, then set the book_id and save it again. Two roundtrips. bad.
I came up with a solution early last week that, while it doesn't resolve the security warnings, it does fix the actual security issue: whitelisting what params users are allowed to send, and validating them. (StrongParams + validation). I had a 1:1 with my boss today about this ticket, and I told him about that solution. He sort of hand-waved it away and said it wouldn't work because <lots of unrelated things>. huh.
He worked through a failed spec to see what the ticket was about, and eventually (20 minutes later) ran into the same issues Idid, and said "there's no way around this" (meaning what security wants won't actually help).
I remembered that Ruby has a `taint` state tracking, and realized I could use that to write a super elegant drop-in solution: some Rack middleware or a StrongParams monkeypatch to mark all foreign keys from user-input as tainted (so devs can validate and un-taint them), and also monkeypatch ACtiveRecord's create/save/update/etc. to raise an exception when seeing tainted data. I brought this up, and he searched for it. we discovered someone had already build this (not surprising), but also that Ruby2.7 deprecates the `taint` mechanism literally "because nobody uses it." joy. Boss also somehow thought I came up with it because I saw the other person's implementation, despite us searching for it because I brought it up? 🤨
Foregoing that, we looked up more possibilities, and he saw the whitelist+validation pattern quite a few more times, which he quickly dimissed as bad, and eventually decided that we "need to noodle on it for awhile" and come up with something else.
Shortly (seriously 3-5 minutes) after the call, he said that the StrongParams (whitelist) plus validation makes the most sense and is the approach we should use.
ffs.
I came up with that last week and he said no.
I brought it up multiple times during our call and he said it was bad or simply talked over me. He saw lots of examples in the wild and said it was bad. I came up with a better, more elegant solution, and he credited someone else. then he decided after the call that the StrongParams idea he came up with (?!) was better.
jfc i'm getting pissy again.8 -
Sometimes I wonder how compromised my parents online security would be without my intervention.
My mom logged into her gmail and there was an red bar on top informing about Google preventing an attempted login from an unknown device.
Like typical parents / old people, that red bar didn't caught her attention but I noticed it immediately. I took over and looked into it. It showed an IP address and a location that was quite odd.
I went ahead with the Account security review and I was shocked to find that she had set her work email address as the recovery email!!
I explained her that work email accounts cannot be trusted and IT department of the workplace can easily snoop emails and other info on that email address and should not be related to personal accounts.
After fixing that issue, me being a typical skeptic and curious guy, I decided to find more info about that IP address.
I looked up the IP address on a lookup website and it showed an ISP that was related to the corporate office of her workplace. I noticed the location Google reported also matched with the corporate office location of her work.
Prior to this event, few days ago, I had made her change her gmail account password to a more secure one. ( Her previous password was her name followed by birth date!! ). This must have sent a notification to the recovery mail address.
All these events are connected. It is very obvious that someone at corporate office goes through employees email addresses and maybe even abuse those information.
My initial skeptism of someone snooping throguh work email addresses was right.
You're welcome mom!9 -
That feeling when your client connection is more stable than the connection of a fucking game server... Incompetent pieces of shit!!! BEING ABLE TO PUT A COUPLE OF SPRITES DOESN'T MAKE YOU A FUCKING SYSADMIN!!!
Oh and I sent those very incompetent fucks a mail earlier, because my mailers are blocking their servers as per my mailers' security policy. A rant from the old box - their mail servers self-identify a fucking .local!!! Those incompetent shitheads didn't even properly change the values from test into those from prod!! So I sent them an email telling them exactly how they should fix it, as I am running the same MTA on my mailers (Postfix), at some point had to fix my mailers against the exact same issue as well, and clearly noticed in-game that they have deliverability problems (they explicitly mention to unblock their domain). Guess why?! Because their server's shitty configuration triggers fucking security mechanisms that are built against rogue mailers that attempt to spoof themselves as an internal mailer, with that fucking .local! And they STILL DIDN'T CHANGE IT!!!! Your fucking domain has no issues whatsoever, it's your goddamn fucking mail servers that YOU ASOBIMO FUCKERS SHOULD JUST FIX ALREADY!!! MOTHERFUCKERS!!!!!rant hire a fucking sysadmin already incompetent pieces of shit piece of shit game dev doesn't make you a sysadmin2 -
--- iOS-Jailbreak-AppStore "Cydia" shuts down ---
This Friday, Jay Freeman, the maintainer of the iOS-Jailbreak-AppStore "Cydia", announced that he will shut-down his services.
"Cydia" is a app store for people that jailbreaked their iPhones and allows them to buy and download apps. Apple's AppStore doesn't allow jailbreaked apps, that's the reason it was created in 2009.
Jay Freeman, also known as "Saurik", explained that he wanted to shut down the service at the end of 2018 anyways.
Now, a recent security issue, threatening the data of all users, caused that the store no longer existed with immediate effect.
In addition to the security issue, "Cydia" was said to be no more profitable.
To calm you breakers down: Previous purchases can still be downloaded!
The software itself will continue to exist, but without a back-end for payments and stuff like that. Users are still able to do payments through third-party repositories, which already happened anyway, so that lowers the impact of the shut-down.
Just like "Cydia", other services are shutting down too.
One of the three big Cydia-repositories, ModMyi, said they wont allow any new apps and archived all existing ones.
ZodTTD and MacCiti will also be discontinued.
"Bigboss" is the only repository remaining.
Jailbreaks just lost their popularity over the last years. There's still no jailbreak for iOS 11! This shows that Apple is getting better and better at preventing jailbreaks.
On the other hand, it shows that the need for jailbreaks is not quite as high anymore and therefore the developers don't spend too much energy for breaking up iOS anymore.
Did you use Cydia, or any of the other services? Write us in the comments!
Thanks for reading! 10
10 -
Worst security issue : being able to make a money transfer with no auth and changing freely the bank account in the POST params...
Dev excuse : "I didn't know my job was also to take care about security."2 -
Microsoft brute-forces password-protected archives in OneDrive.
“Microsoft will decrypt, open, and scan protected Zip archives uploaded to the company's cloud servers in search of potential computer threats. Security researcher Andrew Brandt recently discovered the issue while trying to share malware samples with other researchers through SharePoint.”
This is when I encrypt my archives, I use _very_ long passwords generated by Bitwarden. Like this: qkYdE5i@27yHTTj8YsMDKQ9^mo$j@!P^M4qA95Y5VqR*53otAMuMv$9sdxtF4HAuNdAYoW9RPVxucJ3
Good luck bruteforcing that, Microsoft!
https://techspot.com/news/... 10
10 -
I've just been given a beautiful turd of a PC with only 512MB RAM to get ready for someone in the residence. Way too small for any modern Windows or even Linux with a halfway decent GUI. And the user doesn't have any technical background so I highly doubt that they'll be able to maintain a Linux system. Windows XP is full of security issues but it might just be able to run on that craptop. Due to me knowing that it's a vulnerable system though, I've got an ethical issue with that. Windows XP is insecure but at least the user would be able to use it.. and Linux is secure but it'd never get updated, and I really don't want that guy to come knock on my door every time he wants to install a piece of software.. the guy fucking stinks! What would you do in a situation like that?30
-
Apple iPhone testing without being on the app store is so annoying, I had to sign up some people to test the app I've been working on and had issues on my end, it really is this whole security bullshit, really it isn't needed.
I couldn't get the team provisional certificate thing to show up because when I clicked the account the team certificate settings would disappear, only after right clicking and hitting help then clicking the team while it was selected could I go to the right window.
I don't see why it's so damn hard to do this crap.
Yet with Android, it's so easy.
I really have issues with the testing for this iPhone app, I went through so many different ways to try and get it to work.
Anyways all done, crashlytics is an awesome testing tool if you can get around that small issue I had.4 -
So I'm back from vacation! It's my first day back, and I'm feeling refreshed and chipper, and motivated to get a bunch of things done quickly so I can slack off a bit later. It's a great plan.
First up: I need to finish up tiny thing from my previous ticket -- I had overlooked it in the description before. (I couldn't test this feature [push notifications] locally so I left it to QA to test while I was gone.)
It amounted to changing how we pull a due date out of the DB; some merchants use X, a couple use Y. Instead of hardcoding them, it would use a setting that admins can update on the fly.
Several methods deep, the current due date gets pulled indirectly from another class, so it's non-trivial to update; I start working through it.
But wait, if we're displaying a due date that differs from the date we're actually using internally, that's legit bad. So I investigate if I need to update the internals, too.
After awhile, I start to make lunch. I ask my boss if it's display-only (best case) and... no response. More investigating.
I start to make a late lunch. A wild sickness appears! Rush to bathroom; lose two turns.
I come back and get distracted by more investigating. I start to make an early dinner... and end up making dinner for my monster instead.
Boss responds, tells me it's just for display (yay!) and that we should use <macro resource feature> instead.
I talk to Mr. Product about which macros I should add; he doesn't respond.
I go back to making lunch-turn-dinner for myself; monster comes back and he's still hungry (as he never asks for more), so I make him dinner.
I check Slack again; Mr. Product still hasn't responded. I go back to making dinner.
Most of the way through cooking, I get a notification! Product says he's talking it through with my boss, who will update me on it. Okay fine. I finish making dinner and go eat.
No response from boss; I start looking through my next ticket.
No response from boss. I ping him and ask for an update, and he says "What are you talking about?" Apparently product never talked to bossmang =/ I ask him about the resources, and he says there's no need to create any more as the one I need already exists! Yay!
So my feature went from a large, complex refactor all the way down to a -1+2 diff. That's freaking amazing, and it only took the entire day!
I run the related specs, which take forever, then commit and push.
Push rejected; pull first! Fair, I have been gone for two weeks. I pull, and git complains about my .gitignore and some local changes. fine, whatever. Except I forgot I had my .gitignore ignored (skipped worktree). Finally figure that out, clean up my tree, and merge.
Time to run the specs again! Gems are out of date. Okay, I go run `bundle install` and ... Ruby is no longer installed? Turns out one of the changes was an upgrade to Ruby 2.5.8.
Alright, I run `rvm use ruby-2.5.8` and.... rvm: command not found. What. I inspect the errors from before and... ah! Someone's brain fell out and they installed rbenv instead of the expected rvm on my mac. Fine, time to figure it out. `rbenv which ruby`; error. `rbenv install --list`; skyscraper-long list that contains bloody everything EXCEPT 2.5.8! Literally 2.5 through 2.5.7 and then 2.6.0-dev. asjdfklasdjf
Then I remember before I left people on Slack made a big deal about upgrading Ruby, so I go looking. Dummy me forgot about the search feature for a painful ten minutes. :( Search found the upgrade instructions right away, ofc. I follow them, and... each step takes freaking forever. Meanwhile my children are having a yelling duet in the immediate background, punctuated with screams and banging toys on furniture.
Eventually (seriously like twenty-five minutes later) I make it through the list. I cd into my project directory and... I get an error message and I'm not in the project directory? what. Oh, it's a zsh thing. k, I work around that, and try to run my specs. Fail.
I need to update my gems; k. `bundle install` and... twenty minutes later... all done.
I go to run my specs and... RubyMine reports I'm using 2.5.4 instead of 2.5.8? That can't be right. `ruby --version` reports 2.5.8; `rbenv version` reports 2.5.8? Fuck it, I've fought with this long enough. Restarting fixes everything, right? So I restart. when my mac comes back to life, I try again; same issue. After fighting for another ten minutes, I find a version toggle in RubyMine's settings, and update it to 2.5.8. It indexes for five minutes. ugh.
Also! After the restart, this company-installed surveillance "security" runs and lags my computer to hell. Highest spec MacBook Pro and it takes 2-5 seconds just to switch between desktops!
I run specs again. Hey look! Missing dependency: no execjs. I can't run the specs.
Fuck. This. I'll just push and let the CI run specs for me.
I just don't care anymore. It's now 8pm and I've spent the past 11 hours on a -1+2 diff!
What a great first day back! Everything is just the way I left it.rant just like always eep; 1 character left! first day back from vacation miscommunication is the norm endless problems ruby6 -
Found a bug, reported it to the maintainer.
He then tells me to ignore it since no one noticed it (besides me).
I tell him i can't do it since it's just wrong and he can simply fix it.
Turns out he's just lazy as hell and got mad at me, so i go and fix it.
Next day boss is mad at me because i'm wasting time on tasks that it's not of my concern even knowing all my tasks were completed.
Not even a "thank you by the way".
What did i miss here?4 -
WTF!!!!! I officially have someone trying to extort me just had this in my email box this morning!
--------
Hello,
My name is [name removed], I'm an IT security expert and I found a security issue on your website.
This email is personal and in no way related to any of my employers.
I was able to access to a lot of files which contains sensitive data.
I attached a screenshot of the files I found to this email.
I would be happy to give you the method I used to access these files in order to let you fix it.
Would be a monetary compensation possible?
Please forward this email to the right person, if your are not responsible for the security of the website.
Best Regards,
[name removed]
---
He can basically see the contents of my wp-config.php. How has he managed this?71 -
First year at university, prepared to set up multiple electronics.
rPi, arduino Ethernet shield, laptop, and desktop.
Brand new netgear switch to satisfy my internet surfing needs....
After setting up my devices, I realized none of them have internet. Hm. The feed port on my switch wasn't blinking either. So I tell the front desk, and a short 7 days later the port is back on. Yay, problem solved.
One morning I arise to see the port dark and inactive. Furious I use my laptop to share an internet connection while my actual port is "broken".
Support ticket is reopened and this time I get an email saying the port was disabled due to a security issue.
Me: what's the issue?
IT: there was more than two devices connected to the port
(OnLy TwO dEvIcEs PeR port???)
Me: oh okay I will only connect two.
The next day the port is disabled, again.
Me: can you tell me why it was disabled?
IT: a switch was detected being used, security error.
Me: how do I connect more than one device to the port without a switch???
IT: ...
IT: Please only connect one device.
🤔10 -
Our system never had sessions that expired. A recent hack at the client caused us to revisit the security measures we had in place.
The person who was on the project since it's start 8 years ago was tasked with fixing this issue. It has a simple solution: add session expiration, and extend the session to an hour from now with each request.
This week I found out how he did it🤦🏻♂️. He added session expirations, but extended the session by an hour with each request. By making 10 requests in quick succession, your session is extended by 10 hours.3 -
Flash has made Java programs look desirable. And anyone keeping up with me knows I despise Java and C#, despite having written C# and currently working on deciphering a Java server to create documentation.
Before I begin, I want to make this clear: IT IS TWO THOUSAND AND FUCKING EIGHTEEN. 2018. WE HAVE BETTER TECH. JAVASCRIPT HAS TAKEN OVER THIS BITCH. So, firstly, FUCK FLASH. Seriously, that shit's a security liability. If you work for a company that uses it, find a new job and then fucking quit, or go mutany and get several devs to begin a JS-based implementation that has the same functionality. There is no excuse. "I'm fired?" That's not an excuse - if there is a way to stop the madness, then fucking hit the brakes on that shit or begin job hunting. Oh, and all you PMs who are reading this and have mandated or helped someone else to mandate work on an enterprise flash program, FUCK YOU. You are part of the problem.
The reason for this outburst seems unreasonable until you realize the hell I went through today. At my University, there is a basic entry-level psychology course I'm taking. Pearson, a company I already fucking hate for some of the ethically sketchy shit they pulled with PARCC as well as overreach in publishing to the point they produce state tests here in the US - has a product called "My PsychLab" and from here on out, I'm referring to it as MPL. MPL has an issue - it is entirely fucking Flash. Homework assignments, the textbook, FUCKING EVERYTHING. So, because of that, you need to waste time finding a browser that works. Now let me remind all of you that just because something SHOULD WORK does NOT mean that it actually does.
I'm sitting on my Antergos box a few days ago: Chromium and Firefox won't load Flash. I don't know why, and don't care to find out. NPAPI and whatnot are deprecated but should still run in a limited mode or some shit. No go on Antergos.
So, today I went to the lab in the desolated basement of an old building which is where it's usually empty except a student hired by the university to make sure nobody fucks things up. I decided - because y'all know I fuckin' hate this - to try Windows. No go in Chrome still - it loaded Flash but couldn't download the content. So I tried Firefox - which worked. My hopes were up, but not too long - because there was no way to input. The window had buttons and shit - but they were COMPLETELY UNRESPONSIVE.
So the homework is also Flash-based. It's all due by 1/31/18 - FOUR CHAPTERS AND THE ACCOMPANYING HOMEWORK - which I believe is Tuesday, and the University bookstore is closed both Saturday and Sunday. No way to get a physical copy of the book. And I have other classes - this isn't the only one.
Also, the copyright on the program was 2017 - so whoever modded or maintained that Flash code - FUCK YOU AND THE IRRESPONSIBLE SHIT YOUR TEAM PULLED. FUCK THE SUPERIORS MAKING DECISIONS AS WELL. Yeah, you guys have deadlines? So do the end users, and when you have to jump through hoops only to realize you're fucked? That's a failure of management and a failure of a product.
How many people are gonna hate me for this? Haters gonna hate, and I'm past the point of caring.6 -
Why is it that an issue is only critical-priority until the person who's raising the biggest fuss has to do something about it?
I was notified that a website hosted in AWS went down overnight and never came back up. I was then bombarded with email after email after email while I logged into our AWS account and poked around. I'm responsible for cloud infrastructure stuff, like VMs or virtual networking or security or whatever, not the actual applications running on said infrastructure. Once I confirmed their EC2 instance was reachable and I could login with SSH, I told them they'd have to fix their application.
They told me that they had no backend developer on their development team. I'm still getting a deluge of emails from multiple people on this team and their managers and managers' managers and so on.
"Perfectly understandable," I told them, though it was anything but. "You should probably look into obtaining one."
The emails stopped immediately. I assumed they were handling it and closed my ticket and moved on. But apparently I was wrong.
Six weeks later, the site is still down, they still have no backend dev, and I'm convinced that they were lying to me when they stressed the importance of this web app because now that it's no longer my problem, not a single person seems to care that it's still broken.3 -
"We should probably fix that security issue, but the application already works, so it does not matter" - My boss2
-
Boss: We need to disable CSRF and any other form of security, because that shitty, insignificant client has a website that is abomination anyone's eyes, can't pay because of the iframe thingy.
Me: I'd advice against it. This is a significant security issue that just screams to be exploited and there has to be a solution, but idk much about this situation.
Boss: Idk we need to kiss every clients ass till they come. Remove all the security
Me: *Just wants to get home, last one in the office besides the boss* fine
*removes it, deploys and gets the fuck home*
...2 weeks later
Payment gateway: Yeah, we blocked your account, because someone was trying to purchase 30k product in a span of 1h
I'm not even mad about that, but rather about the fact I fucking called it.
* Achievement unlocked: Targeted by scammers
P.s. no major damages, cause the guys from the payment gate understand shit about security.3 -
I don't usually look at the "updates" section of my Gmail but yesterday I did. One message cought my eye: "Your application to Microsoft BizSpark has been approved" but I've never applied to Microsoft BizSpark!
Someone has registered in my name, opened a Microsoft Outlook account under my full name and added my startup details for applying to BizSpark! One issue though, he used some Spanish equivalent of mailinator to subscribe so I could easily reset the password and replace the security email. Now I have 5 visual studio subscriptions I don't know what to do with.5 -
After a few weeks of being insanely busy, I decided to log onto Steam and maybe relax with a few people and play some games. I enjoy playing a few sandbox games and do freelance development for those games (Anywhere from a simple script to a full on server setup) on the side. It just so happened that I had an 'urgent' request from one of my old staff member from an old community I use to own. This staff member decided to run his own community after I sold mine off since I didn't have the passion anymore to deal with the community on a daily basis.
O: Owner (Former staff member/friend)
D: Other Dev
O: Hey, I need urgent help man! Got a few things developed for my server, and now the server won't stay stable and crashes randomly. I really need help, my developer can't figure it out.
Me: Uhm, sure. Just remember, if it's small I'll do it for free since you're an old friend, but if it's a bigger issue or needs a full recode or whatever, you're gonna have to pay. Another option is, I tell you what's wrong and you can have your developer fix it.
O: Sounds good, I'll give you owner access to everything so you can check it out.
Me: Sounds good
*An hour passes by*
O: Sorry it took so long, had to deal with some crap. *Insert credentials, etc*
Me: Ok, give me a few minutes to do some basic tests. What was that new feature or whatever you added?
O: *Explains long feature, and where it's located*
Me: *Begins to review the files* *Internal rage wondering what fucking developer could code such trash* *Tests a few methods, and watches CPU/RAM and an internal graph for usage*
Me: Who coded this module?
O: My developer.
Me: *Calm tone, with a mix of some anger* So, you know what, I'm just gonna do some simple math for ya. You're running 33 ticks a second for the server, with an average of about 40ish players. 33x60 = 1980 cycles a minute, now lets times that by the 40 players on average, you have 79,200 cycles per minute or nearly 4.8 fucking cycles an hour (If you maxed the server at 64 players, it's going to run an amazing fucking 7.6 million cycles an hour, like holy fuck). You're also running a MySQLite query every cycle while transferring useless data to the server, you're clusterfucking the server and overloading it for no fucking reason and that's why you're crashing it. Another question, who the fuck wrote the security of this? I can literally send commands to the server with this insecure method and delete all of your files... If you actually want your fucking server stable and secure, I'm gonna have to recode this entire module to reduce your developer's clusterfuck of 4.8 million cycles to about 400 every hour... it's gonna be $50.
D: *Angered* You're wrong, this is the best way to do it, I did stress testing! *Insert other defensive comments* You're just a shitty developer (This one got me)
Me: *Calm* You're calling me a shitty developer? You're the person that doesn't understand a timer, I get that you're new to this world, but reading the wiki or even using the game's forums would've ripped this code to shreds and you to shreds. You're not even a developer, cause most of this is so disorganized it looks like you copy and pasted it. *Get's angered here and starts some light screaming* You're wasting CPU usage, the game can't use more than 1 physical core, and after a quick test, you're stupid 'amazing' module is using about 40% of the CPU. You need to fucking realize the 40ish average players, use less than this... THEY SHOULD BE MORE INTENSIVE THAN YOUR CODE, NOT THE OPPOSITE.
O: Hey don't be rude to Venom, he's an amazing coder. You're still new, you don't know as much as him. Ok, I'll pay you the money to get it recoded.
Me: Sounds good. *Angered tone* Also you developer boy, learn to listen to feedback and maybe learn to improve your shitty code. Cause you'll never go anywhere if you don't even understand who bad this garbage is, and that you can't even use the fucking wiki for this game. The only fucking way you're gonna improve is to use some of my suggestions.
D: *Leaves call without saying anything*
TL;DR: Shitty developer ran some shitty XP system code for a game nearly 4.8 million times an hour (average) or just above 7.6 million times an hour (if maxed), plus running MySQLite when it could've been done within about like 400 an hour at max. Tried calling me a shitty developer, and got sorta yelled at while I was trying to keep calm.
Still pissed he tried calling me a shitty developer... -
A coworker told me this a little while ago and I cringed.
"Coworker installs windows partition o n a Mac, not sure what utility he used but he's handled every IT issue, people in our company for years but googling and researching ways to do things.
Steve comes along to do a service on the Macs (apparently) and sees what my coworker did and says "get rid of that it's a security risk", coworker had a legitimate reason to use Windows, plugin for Excel only works in Windows, so Steve could have totally done checks to ensure security wasn't a risk, but he's a Mac elitist, what can you do :/, lucky coworker though gets to use a windows PC and never looked back xD."
Honestly scared of Steve doing that so called service seeing I have tons of things I need to use (source tree, Android studio, some tools to test push notifications) and just down right deleting them because of his reasons, that and the whole he does services after hours without much warning (last time it was a leave password on desk for the next "week" and Steve will come in and fix the Macs) I can't defend my argument of why I use something like Android studio (to develop the app for the company LOL) -
This is the Result Declaration form of our university, It's all good but there is one thing (bug) in this form, you only need to fill the Recaptcha once and you can that same Recaptcha to extract as many results as you want. Though not a Security issue, we can extract results of many students as roll numbers are sequential, we just need a bot to fill roll number and click the button. The only use would be to conduct surveys on results, but, a bug is a bug.
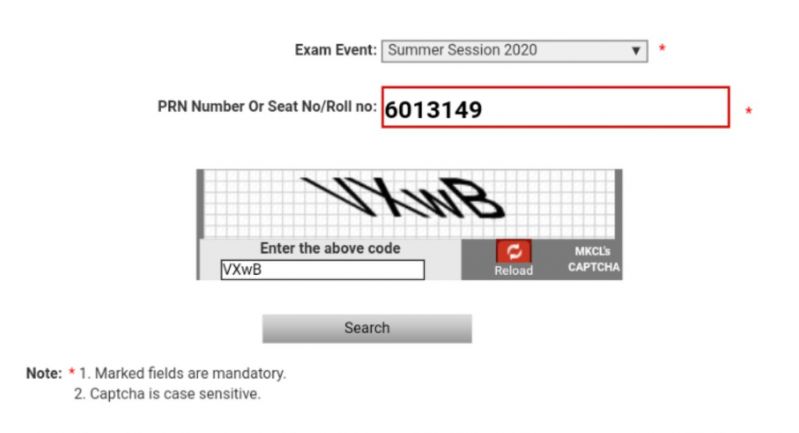 5
5 -
I just love how liferay keeps finding ways to surprise me...
Customer: need to fix this security issue
me: ok
me: fixed. Testing locally. Works 100%.
Me: testing on dev server. Works 100%
qa: testing on dev server. Works 100%
me: all good. Deploying to preprod
customer: it doesn't work
me: testing preprod - it doesn't work.
Me: scp whole app to local machine. App works 100%.
Me: preview loaded liferay properties in preprod via liferay adm panel. All props loaded ok.
Me: attach jdb to preprod's liferay to see what props are loaded. Only defaults are used [custom props not loaded according to jdb]
me: is there some quantum mechanics involved..? Liferay managed to both load and not to load props at the same time and the state only changes as it's observed...2 -
PyTorch.
2018: uh, what happens when someone uses a same name attack? - No big deal. https://github.com/pypa/pip/...
2020: I think that's a security issue. - Nanana, it's not. https://github.com/pypa/pip/...
2022: malicious package extracts sensitive user data on nightly. https://bleepingcomputer.com/news/...
You had years to react, you clowns.5 -
Fucking shit i just had a 3 days chat with google's cloud engineer about an issue i had in a project. eventually the issue occured due to an update they made on some projects involving IAM changes that required some changes from my part in my security toles. Like wtf haven't you heard of data fixes when you roll out such changes?! I just had my production env down for 72hours for their fuckup.
At least send an email regarding it so we could set it up in time1 -
So one of my clients had a different company do a penetrationtest on one of my older projects.
So before hand I checked the old project and upgraded a few things on the server. And I thought to myself lets leave something open and see if they will find it.
So I left jquery 1.11.3 in it with a known xss vulnerability in it. Even chrome gives a warning about this issue if you open the audit tab.
Well first round they found that the site was not using a csrf token. And yeah when I build it 8 years ago to my knowledge that was not really a thing yet.
And who is going to make a fake version of this questionair with 200 questions about their farm and then send it to our server again. That's not going to help any hacker because everything that is entered gets checked on the farm again by an inspector. But well csrf is indeed considered the norm so I took an hour out of my day to build one. Because all the ones I found where to complicated for my taste. And added a little extra love by banning any ip that fails the csrf check.
Submitted the new version and asked if I could get a report on what they checked on. Now today few weeks later after hearing nothing yet. I send my client an email asking for the status.
I get a reaction. Everything is perfect now, good job!
In Dutch they said "goed gedaan" but that's like what I say to my puppy when he pisses outside and not in the house. But that might just be me. Not knowing what to do with remarks like that. I'm doing what I'm getting paid for. Saying, good job, your so great, keep up the good work. Are not things I need to hear. It's my job to do it right. I think it feels a bit like somebody clapping for you because you can walk. I'm getting off topic xD
But the xss vulnerability is still there unnoticed, and I still have no report on what they checked. So I have like zero trust in this penetration test.
And after the first round I already mentioned to the security guy in my clients company and my daily contact that they missed things. But they do not seem to care.
Another thing to check of their to do list and reducing their workload. Who cares if it's done well it's no longer their responsibility.
2018 disclaimer: if you can't walk not trying to offend you and I would applaud for you if you could suddenly walk again.2 -
We have a badly out of shape but functional product , the result of a "if its not broke don't fix it" mentality. The only thing manangement cares is our next release and making meetings to plan other meetings...
Now comes the time of the security Audit (PCI)...
Manager : oh noooo the audit will fix this issue, quickkk fix it !
Us : welllll its a lengthy process but doable, we just gotta do a,b,c,d,e . Part a is essentially what we need the rest are refactoring bits of the system to support part a since the performance would be shit otherwise
Manager: can you do part a before the audit starts ?
Us: yep.
Manager: do it . Oh and pop those other issues on JIRA so we can track em
Audit completed....
Manager: so we got through ok?
Us : 👍 yep
Manager: okayy, take those other issues..... and stick em at the bottom of the back log...
Us : huh ? *suspicious faces*..... okay but performance is gonna be poor with the system as it is cuz of part A....
Manager: yeaaahhh * troll face* ....about that.... roll it back and stick that too at the bottom of the log. We got to focus our next release. Lemme schedule a meeting for that 😊
Us : faceplam4 -
Because of some theft this year and even though we already have security cameras, my apartment building decided to check the front door locks so it's more secure.
This key looks very high tech... Only issue though is I never use the key anyway... I just entered the door code...
So what is the point of changing the locks? I'm going to guess whoever is stealing isn't picking the lock... People would notice... They must know the code.
Also it seems most of the apartment locks are digital key card/pins too. Wondering if this just means most owners are young or just are techies/devs... 9
9 -
TL;DR: Google asked me to PROVIDE a phone number to verify connection from a new device, on the said device.
Yesterdayto log into my work Google account from my personal laptop to check emails, calendars update and so on. I opened up a private navigation window, went to Google sign-in page, entered my credentials, all is well.
Google then decided to "verify it's me" and prompted me to PROVIDE a phone number (work account without work phone means no phone number set up) so that they can send a verification code to the number I just provided to make sure the connection is legit.
Didn't want to do that, clicked "use another method" and got asked to fill the last password I remember, which would be my current password thanks to my trusty password manager. After submitting, I'm prompted with an error saying I have to contact my admin to reset my password because they can't log me in with my CURRENT password.
I ain't gonna do that, so went back to login page, provided my phone number, got the code, filled in the code, next thing I know I'm browsing through my emails.
What the duck? Could have been anybody giving any phone number. So much for extra security.
Also don't care that they have my phone number, the issue is more about the way used to obtain it: locking me out of my account and having no other way of logging in.6 -
Oh boy I got a few. I could tell you stories about very stupid xss vectors like tracking IDs that get properly sanitized when they come through the url but as soon as you go to the next page and the backend returns them they are trusted and put into the Dom unsanitized or an error page for a wrong token / transaction id combo that accidentally set the same auth cookie as the valid combination but I guess the title "dumbest" would go to another one, if only for the management response to it.
Without being to precise let's just say our website contained a service to send a formally correct email or fax to your provider to cancel your mobile contract, nice thing really. You put in all your personal information and then you could hit a button to send your cancelation and get redirected to a page that also allows you to download a pdf with the sent cancelation (including all your personal data). That page was secured by a cancelation id and a (totally save) 16 characters long security token.
Now, a few months ago I tested a small change on the cancelation service and noticed a rather interesting detail : The same email always results in the same (totally save) security token...
So I tried again and sure, the token seemed to be generated from the email, well so much about "totally save". Of course this was a minor problem since our cancelation ids were strong uuids that would be incredibly hard to brute force, right? Well of course they weren't, they counted up. So at that point you could take an email, send a cancelation, get the token and just count down from your id until you hit a 200 and download the pdf with all that juicy user data, nice.
Well, of course now I raised a critical ticket and the issue was fixed as soon as possible, right?
Of course not. Well I raised the ticket, I made it critical and personally went to the ceo to make sure its prioritized. The next day I get an email from jira that the issue now was minor because "its in the code since 2017 and wasn't exploited".
Well, long story short, I argued a lot and in the end it came to the point where I, as QA, wrote a fix to create a proper token because management just "didn't see the need" to secure such a "hard to find problem". Well, before that I sent them a zip file containing 84 pdfs I scrapped in a night and the message that they can be happy I signed an NDA.2 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
So i am a diabetic and carry an insulin pump. Now being in India, the pump is not covered by insurance (for some god forsaken reason that I don’t know) and therefore is not a common sight here (contradictoraly India has a major diabetes problem). So I was at the metro station going through security check and the security personnel asks me what the pump was and asked me to show it to him. Now since insulin pumps are uncommon here I understood his concern and showed it to him. Now I like to carry the pump under my shirt with a clip pouch. So naturally I had to lift up my shirt to show it to him. But this isn’t the highlight of the story.
The guy behind me rised above and started peeking over my shoulder and constantly repeating like a 2 year old child what is this. And that too with my fucking abdomen exposed. I went into rage mode there and then like wtf dude, none of your business just step back a little.
Now my issue is that I do not understand that in their own curiosity, why do people forget to respect others privacy. And a very big problem with medical equipment manufacturing organisations (yeah you medtronic). Why are you only concerned with sales and why not awareness? I mean spreading awareness will only help your sales as more people will become aware about your product and it will be less awkward and concerning for people like me to wear your device out in the public5 -
My internship is about to end in two months. I was under the impression that I'll start looking for a job towards mid August and then decide what to do. I didn't expect my company to offer me a position so early before my internship ended.
Initially I had liked the place. The work was pretty relaxed and I had quite a bit of freedom. Soon enough, I proved my worth and my team started respecting my opinions and suggestions. They even consulted me on multiple occasions.
The first thing I noticed on the downside was the company, despite being resourceful enough and having a decent turnover and important clients, was quite stingy in terms of employee welfare. There was no coffee. There was machine but you had to buy the capsule for yourself. And that sucks. I know I don't need to say more but the other problems were there was no enterprise subscription (or any subscription) to PhpStorm even though our team handled so many PHP projects. I know IDEs are personal preferences but not having any professional IDEs is not something to let slide. The lead dev uses NetBeans (and not because he loved it or anything). Even though I worked on WebDev and front end, I had no option to ask for a second screen. I had one display apart from my laptop. Usually most companies in Paris provides food tickets for internships and this company did not even give me that. And worst of all, there wasn't really anyone I looked up to. As much as I enjoy responsibilities and all, I don't think I should be in an environment where I have nothing much to learn from my seniors. For some fucked sense of security and certainty, I was willing to overlook all this when they offered me a position. But I recently had my interview and the regional manager, a fuck face who still makes me wonder how he reached his position, made a proposal for some quite a small amount of salary. What infuriated more than his justifications was his attitude itself. There was absolutely no respect whatsoever. It was more like "We'll give you this, I think this is more than enough for you. Take it or do whatever you want". I asked for more and he didn't even bother negotiating. I declined the offer.
Now this would have solved all the issues. But my manager and my lead dev like me a lot. Both of them are pretty nice people. They both were bothered with the fact that I had turned down the offer. My manager even agreed that the offer was too low and had already given me tips to help me negotiate. But after I turned down the offer, she went and discussed the issue with the regional manager and he offered me a new proposal. This time it was decent but still under my expectations. I'm pretty sure I can do better elsewhere. I said I need time to think about it. I get multiple advises from people to take it atleast so that I get my visa converted to a work permit. For some reason, I want to take the risk and say no. And find something else. But today my lead dev called me aside and asked me if was going to say no. He really tried to influence me by telling me a lot of good things about me and telling me about the number of different projects we're going to start next month and all that. Even though I'm fully convinced that I don't want to work here, just the sheer act of saying no to these two people I respect is sooo fucking difficult for me that I can already imagine me working here for the next one year. The worst part is I can clearly classify their words and sentences into stuff they say to canvass me, stuff they're bullshitting about and flattery just to make me stay. Despite knowing I'm being taken advantage of, some fucked up module in my head wouldn't stop guilt tripping me. I don't know what to do. If I only I could find a really better job.
Pardon the grammatical errors if any. I'm just venting out and my thoughts branch in 500 different ways simultaneously.5 -
what kind of dumb fuck you have to be to get the react js dev job in company that has agile processes if you hate the JS all the way along with refusing to invest your time to learn about shit you are supposed to do and let's add total lack of understanding how things work, specifically giving zero fucks about agile and mocking it on every occasion and asking stupid questions that are answered in first 5 minutes of reading any blog post about intro to agile processes? Is it to annoy the shit out of others?
On top of that trying to reinvent the wheels for every friggin task with some totally unrelated tech or stack that is not used in the company you work for?
and solution is always half-assed and I always find flaw in it by just looking at it as there are tons of battle-tested solutions or patterns that are better by 100 miles regarding ease of use, security and optimization.
classic php/mysql backend issues - "ooh, the java has garbage collector" - i don't give a fuck about java at this company, give me friggin php solution - 'ooh, that issue in python/haskel/C#/LUA/basically any other prog language is resolved totally different and it looks better!' - well it seems that he knows everything besides php!
Yeah we will change all the fucking tech we use in this huge ass app because your inability to learn to focus on the friggin problem in the friggin language you got the job for.
Guy works with react, asked about thoughts on react - 'i hope it cease to exists along with whole JS ecosystem as soon as possible, because JS is weird'. Great, why did you fucking applied for the job in the first place if it pushes all of your wrong buttons!
Fucking rockstar/ninja developers! (and I don't mean on actual 'rockstar' language devs).
Also constantly talks about game development and we are developing web-related suite of apps, so why the fuck did you even applied? why?
I just hate that attitude of mocking everything and everyone along with the 'god complex' without really contributing with any constructive feedback combined with half-assed doing something that someone before him already mastered and on top of that pretending that is on the same level, but mainly acting as at least 2 levels above, alas in reality just produces bolognese that everybody has to clean up later.
When someone gives constructive feedback with lenghty argument why and how that solution is wrong on so many levels, pulls the 'well, i'm still learning that' card.
If I as code monkey can learn something in 2 friggin days including good practices and most of crazy intricacies about that new thing, you as a programmer god should be able to learn it in 2 fucking hours!
Fucking arrogant pricks!8 -
Beware: Here lies a cautionary tale about shared hosting, backups, and -goes without saying- WordPress.
1. Got a call from a client saying their site presented an issue with a third-party add-on. The vendor asked us to grant him access to our staging copy.
2. Their staging copy, apparently, never got duplicated correctly because, for security reasons, their in-house dev changed the name of the wp-content folder. That broke their staging algo. So no staging site.
3. In order to recreate the staging site, we had to reset everything back to WP defaults. Including, for some reason, absolute paths inside the database. A huge fucking database. Because WordPress.
4. Made the changes directly in a downloaded sql file. Shared hosting, obviously, had an upload limit smaller to the actual database.
5. Spent half an hour trying to upload table by table to no avail.
6. In-house uploads a new, fixed database with the help of the shared hosting provider.
7. Database has the wrong path. Again.
8. In-house performs massive Find and Replace through phpMyAdmin on the production server.
9. Obviously, MySQL crashes instantly and the site gets blocked for over 3 hours for exceeding shared hosting limits.
10. Hosting provider refuses to accept this was caused by such a stupid act and says site needs to be checked because queries are too slow.
11. We are gouging our eyeballs as we see an in-house vs. hosting fight unfold. So we decide to watch a whole Netflix documentary in between.
12. Finally, the hosting folds and enables access to the site, which is obvi not working because, you know, wrong paths.
13. Documentary finishes. We log in again, click restore from backup. Go to bed. Client phones to bless us. Client’s in-house dev probably looking for a cardboard box to pack his stuff first thing in the morning. \_(ツ)_/¯ -
Right.. I spent the hours leading up to the year change by adding a YouTube to MP3 downloader into my Telegram bot. After a bit of fiddling it turned out okay, and the commit for it was mentioned to the last for the year 2020.
I mentioned this in one of my chats, and users came in with more issues. Told them it's the last commit for the year and I'll keep myself to it. I did adjust the code a bit though to fix those issues, awaiting a commit after midnight.
Midnight passes and 2020 turns into 2021.
I commit the new features, and quickly implemented another one I already thought of as well, but needed its own commit.
Quickly afterwards it turns out that the /mp3 feature actually breaks the bot somewhat, especially on long tracks. Users add a slew of 10h songs into what essentially became a long queue of single-threaded bot action (or rather lack thereof).
I made the /mp3 command accessible to myself only like I did with some other administrative commands already. Still no dice, the bot rejected the commands but executed part of the /mp3 command anyway.
I look a bit further into the code and it turns out that while I was restructuring some functions, I forgot to make the admin() function exit the script after it sends the rejection onwards. This was a serious security issue and meant that all authentication was void. Fortunately the chat did not realize this - one of the commands that became available as a result was literally a terminal on the bot's system.
I fix the issue in 7 commits after midnight total, 3 of which were related to /mp3 and admin(). We're now 1 hour after midnight.
Happy New Year everyone... :')6 -
!myrant
I'm a junior developer in a small company alongside with a fellow programmer. Since I have an interest in Security and our Sys Admin left, my boss offered me to do some sys admin stuff.
I feel bad for my fellow programmer just because there is an old man in the company that doesn't come to me with his tech problems and goes to him.
Something like this goes down today:
OM: Hey, I can't watch my Fox Live News. Can you help me?
FP: The problem isn't on our side
*OM keeps pestering him*
FP: Let me check it out
*Goes and fix the issue and comes back laughing *
My coworker is to kind 😬😂😅2 -
I had a wonderful run-in with corporate security at a credit card processing company last year (I won't name them this time).
I was asked design an application that allowed users in a secure room to receive instructions for putting gift cards into envelopes, print labels and send the envelopes to the post. There were all sorts of rules about what combinations of cards could go in which envelopes etc etc, but that wasn't the hard part.
These folks had a dedicated label printer for printing the address labels, in their secure room.
The address data was in a database in the server room.
On separate networks.
And there was absolutely no way that the corporate security folks would let an application that had access to a printer that was on a different network also have access to the address data.
So I took a look at the legacy application to see what they did, to hopefully use as a precedent.
They had an unsecured web page (no, not an API, a web page) that listed the addresses to be printed. And a Windows application running on the users' PC that was quietly scraping that page to print the labels.
Luckily, it ceased to be an issue for me, as the whole IT department suddenly got outsourced to India, so it became some Indian's problem to solve.2 -
So today it finally happened.
Npm modules broke my system and / or endangered the security of my system.
Installed a global cli utility
That utility depends on package A
That depends on package B
That fucking install a bin called sudo
Yeah.. You heard it right a bin called sudo.
This bin goes in the global module folder that is piped in your path variable.
Now everytime you type sudo you are running somebody else code instead of your system utility.
I am shivering and at loss of swear words.
Opened an issue on the cli that started this matrioska game of horror.
Who the fuck tought that a bin called sudo would be a good fucking idea?
Oh and yes is even an harmless package that try to provide the sudo experience for windows (I went in to check the code of course..)
And I frigging need that cli for work
For now I aliased the sudo in my bashrc still i feel vulnerable and naked now.10 -
PayPal = GayPal
PHASE 1
1. I create my personal gaypal account
2. I use my real data
3. Try to link my debit card, denied
4. Call gaypal support via international phone number
5. Guy asks me for my full name email phone number debit card street address, all confirmed and verified
6. Finally i can add my card
PAHSE 2
7. Now the account is temporarily limited and in review, for absolutely no fucking reason, need 3 days for it to be done
8. Five (5) days later still limited i cant deposit or withdraw money
9. Call gaypal support again via phone number, burn my phone bill
10. Guy tells me to wait for 3 days and he'll resolve it
PHASE 3
11. One (1) day later (and not 3), i wake up from a yellow account to a red account where my account is now permanently limited WITHOUT ANY FUCKING REASON WHY
12. They blocked my card and forever blocked my name from using gaypal
13. I contact them on twitter to tell me what their fucking problem is and they tell me this:
"Hi there, thank you for being so patient while your conversation was being escalated to me. I understand from your messages that your PayPal account has been permanently limited, I appreciate this can be concerning. Sometimes PayPal makes the decision to end a relationship with a customer if we believe there has been a violation of our terms of service or if a customer's business or business practices pose a high risk to PayPal or the PayPal community. This type of decision isn’t something we do lightly, and I can assure you that we fully review all factors of an account before making this type of decision. While I appreciate that you don’t agree with the outcome, this is something that would have been fully reviewed and we would be unable to change it. If there are funds on your balance, they can be held for up to 180 days from when you received your most recent payment. This is to reduce the impact of any disputes or chargebacks being filed against you. After this point, you will then receive an email with more information on accessing your balance.
As you can appreciate, I would not be able to share the exact reason why the account was permanently limited as I cannot provide any account-specific information on Twitter for security reasons. Also, we may not be able to share additional information with you as our reviews are based on confidential criteria, and we have no obligation to disclose the details of our risk management or security procedures or our confidential information to you. As you can no longer use our services, I recommend researching payment processors you can use going forward. I aplogise for any inconvenience caused."
PHASE 4
14. I see they basically replied in context of "fuck you and suck my fucking dick". So I reply aggressively:
"That seems like you're a fraudulent company robbing people. The fact that you can't tell me what exactly have i broken for your terms of service, means you're hiding something, because i haven't broken anything. I have NOT violated your terms of service. Prove to me that i have. Your words and confidentially means nothing. CALL MY NUMBER and talk to me privately and explain to me what the problem is. Go 1 on 1 with the account owner and lets talk
You have no right to block my financial statements for 180 days WITHOUT A REASON. I am NOT going to wait 6 months to get my money out
Had i done something wrong or violated your terms of service, I would admit it and not bother trying to get my account back. But knowing i did nothing wrong AND STILL GOT BLOCKED, i will not back down without getting my money out or a reason what the problem is.
Do you understand?"
15. They reply:
"I regret that we're unable to provide you with the answer you're looking for with this. As no additional information can be provided on this topic, any additional questions pertaining to this issue would yield no further responses. Thank you for your time, and I wish you the best of luck in utilizing another payment processor."
16. ARE YOU FUCKING KIDDING ME? I AM BLOCKED FOR NO FUCKING REASON, THEY TOOK MY MONEY AND DONT GIVE A FUCK TO ANSWER WHY THEY DID THAT?
HOW CAN I FILE A LAWSUIT AGAINST THIS FRAUDULENT CORPORATION?9 -
I've been working on the ecommerce website from hell for over a year now. I should have heard the alarm bells when the studio who were running the project took a month to pay my deposit but still expected me to start working, but I explained that I wouldn't start without some form of security and they were cool with it, so I carried on.
It started off as a simple build with simple products, no product variations etc and a few links on the designs which appeared to lead to external links, and checkout and cart pages were nowhere to be seen. It wasn't a big money job so I just build them in as plain and straightforward as I could, in line with how the rest of the site looked. They then changed their mind about how they wanted these to look, and added loads of functionality to the site throughout the build, so by the end of the line, the scope of work had completely changed. I also had loads of disagreements in terms of design and useability, as their designs straight-up weren't going to function otherwise, plus every round of changes meant that I had to prolong the job further and fit it around work for other clients.
Fastforward a few more months and I get sent a really angry email with some of the client's complaints, including one that raised an issue with the user journey, and the finger of blame was pointed at me. The user journey had been a part of the designs from the start, and this was never raised as an issue for A WHOLE YEAR. They then said that it had to go live on Monday (three days after they sent email with these huge new structural changes). I told them I could no longer work on the project but was happy to waive the rest of my fee (3/4 of the total fee, when I had essentially completed the site, minus 2 minor bugs), so they could find another developer in the limited time they had. At first they refused to hire another developer, claiming that it would be too expensive, which made no sense, as for a few minor fixes and out of scope additions he could get paid a wage that would have otherwise paid for the majority of the work I had done on the site. I stood my ground and finally they found someone, so I sent over all of the files and database to their new developer and asked him to give me a heads up when I could remove the staging site from my server. The next day, I received an email from the studio asking me to fix some bugs the developer was requesting I fix so he could carry on with the site. They were basically asking me to work more, for free, to enable him to walk off with the majority of the money and do less work. They also forwarded a suuuuuper shitty, condescending email from him, listing all the things he thought was wrong with the site (he even listed 'no favicon' although they'd never supplied a graphic for this). He also wrote a paragraph at the bottom EXPLAINING MY JOB TO ME and telling me:
I get the feeling you like to write Javascript, while being one of the easiest languages to learn, it can also be one of the hardest to master. While I applaud you for writing Vanilla JS, it looks like you have a general problem with structuring your application.
Not sure if I'm being oversensitive here but it felt so patronising, and i couldn't even go for an angry walk to get it out my system because of social distancing lol.
Let a girl quarantine in peace!!!!!!2 -
Open source is poison, hoax and source of much troubles.
Even as I love OSS, and I use it a lot, when things go south, they go south terribly.
There was "security" updates in one OSS program I have been using, that accidentally prevented use cases which specifically affected me. I raised bug report, made issue and gave small repro for it.
One of the core developers acknowledges that yes, this is problem, and could be handled with few added options, which users of similar use case could use to keep things working. He then tags issue "needs help" and disappears.
After I have waited some time, I ask help how I could fix it myself, like how to setup proper dev environment for that tool. Asked it in their forums few days later, as issue didn't get any response. Then asked help in their slack, as forums didn't get any help.
Figured out how to get dev environment up, fix done (~4 lines changed, adding simple check for option enabled or not) and figured out how to test that this works.
I create pull request to project, checking their CONTRIBUTING and following instructions there. Then I wait. I wait two weeks, and then one of the core develors goes to add label "needs response from maintainer". That is now almost two weeks ago...
So, bug that appeared in October, and issue that was created October 8th, is still not fixed, even as there is fix in PR for 28 days this far.
And what really ticks me off? People who make statements like: "it is OSS, have you thought of contributing and fixing things yourself?" when we run into problems with open source software.
Making fix yourself ain't biggest problem... but getting it actually applied seems to be biggest roadblock. This kind of experiences doesn't really encourage me to spend time fixing bugs in OSS, time is often better spend changing to different tool, or making changes in my own workflow or going around problem some kludge way.
I try to get business starting, and based on OSS tools. But my decision is staggering, as I had also made decision to contribute back to OSS... but first experiences ain't that encouraging.
Currently, OSS feels like cancer.16 -
(Warning: This rant includes nonsense, nightposting, unstructured thoughts, a dissenting opinion, and a purposeless, stupid joke in the beginning. Reader discretion is advised.)
honestly the whole "ARM solves every x86 problem!" thing doesn't seem to work out in my head:
- Not all ARM chips are the same, nor are they perfectly compatible with each other. This could lead to issues for consumers, for developers or both. There are toolchains that work with almost all of them... though endianness is still an issue, and you KNOW there's not gonna be an enforced standard. (These toolchains also don't do the best job on optimization.)
- ARM has a lot of interesting features. Not a lot of them have been rigorously checked for security, as they aren't as common as x86 CPUs. That's a nightmare on its own.
- ARM or Thumb? I can already see some large company is going to INSIST AND ENFORCE everything used internally to 100% be a specific mode for some bullshit reason. That's already not fun on a higher level, i.e. what software can be used for dev work, etc.
- Backwards compatibility. Most companies either over-embrace change and nothing is guaranteed to work at any given time, or become so set in their ways they're still pulling Amigas and 386 machines out of their teeth to this day. The latter seems to be a larger portion of companies from what I see when people have issues working with said company, so x86 carryover is going to be required that is both relatively flawless AND fairly fast, which isn't really doable.
- The awkward adjustment period. Dear fuck, if you thought early UEFI and GPT implementations were rough, how do you think changing the hardware model will go? We don't even have a standard for the new model yet! What will we keep? What will we replace? What ARM version will we use? All the hardware we use is so dependent on knowing exactly what other hardware will do that changing out the processor has a high likelihood of not being enough.
I'm just waiting for another clusterfuck of multiple non-standard branching sets of PCs to happen over this. I know it has a decent chance of happening, we can't follow standards very well even now, and it's been 30+ years since they were widely accepted.5 -
Dependency hell is the largest problem in Linux.
On Windows, I just download an executeable (.exe) file, and it just works like a charm! But Linux sometimes needs me to install dependencies.
At one point, I nearly broke my operating system while trying to solve dependencies. I noticed that some existing applications refused to start due to some GLIBC error gore. I thought to myself "that thing ain't gonna boot the next time", so I had to restore the /usr/lib/x86_64-linux-gnu/ folder from a backup.
And then there is a new level of lunacy called "conflicting dependencies". I never had such an error on Windows. But when I wanted to try out both vsftpd and proFTPd on Linux, I get this error, whereas on Windows, I simply download an .exe file and it WORKS! Even on Android OS, I simply install an APK file of Amaze File Manager or Primitive FTPd or both and it WORKS! Both in under a minute. But on Linux, I get this crap. Sure, Linux has many benefits, but if one can't simply install a program without encountering cryptic errors that take half a day to troubleshoot and could cause new whack-a-mole-style errors, Linux's poor market share is no surprise.
Someone asked "Why not create portable applications" on Unix/Linux StackExchange. Portable applications can not just be copied on flash drives and to other computers, but allow easily installing multiple versions on a system. A web developer might do so to test compatibility with older browsers. Here is an answer to that question:
> The major argument [for shared libraries] is security, that if there is a vulnerability in a commonly-used library, then only that library has to be updated […] you don't have to have 4 different versions of a library installed
I just want my software to work! Period. I don't mind having multiple versions of libraries, I simply want it to WORK! To hell with "good reasons" for why it doesn't, and then being surprised why Linux has a poor market share. Want to boost Linux market share? SOLVE THIS DAMN ISSUE!.
Understand that the average computer user wants stuff to work out of the box, like it does in Windows.52 -
Part 1: https://devrant.com/rants/4298172/...
So we get this guy in a meeting and he is now saying "we can't have application accounts because that violates our standard of knowing who accessed what data - the application account anonamizes the user behind the app account data transaction and authorization"
And so i remind him that since it's an application account, no one is going to see the data in transit (for reference this account is for CI/CD), so the identity that accessed that data really is only the app account and no one else.
This man has the audacity to come back with "oh well then thats fine, i cant think of a bunch of other app account ideas where the data is then shown to non-approved individuals"
We have controls in place to make sure this doesnt happen, and his grand example that he illustrates is "Well what if someone created an app account to pull github repo data and then display that in a web interface to unauthorized users"
...
M******* why wouldnt you JUST USE GITHUB??? WHO WOULD BUILD A SEPARATE APPLICATION FOR THAT???
I swear I have sunk more time into this than it would have costed me to mop up from a whole data breach. I know there are situations where you could potentially expose data to the wrong users, but that's the same issue with User Accounts (see my first rant with the GDrive example). In addition, the proposed alternative is "just dont use CI/CD"!!!
I'm getting pretty pissed off at this whole "My compliance is worth more than real security" bullshit. -
I have to add an endpoint to integrate an API and I want to vomit when I think about this major security issue they introduce.
What type of prehistoric dumbass thought GET requests with username and password in the query parameters is a good idea to burden your partner with.4 -
Why are clients so brain dead?
I've had a client insist for the last two weeks that I provide them with a high level technical specification for fucking OneDrive because our product is able to embed HTML inputted into the CMS.
I've literally had hours of meetings with over a dozen people where I'm trying to explain that just because they're embedding some PowerPoint HTML into our CMS doesn't mean we need to or even can provide technical documents.
This is a huge company with an equity of over £50 billion by the way. I swear the bigger the company the more incompetent the employees get.
Their whole issue stems from one guy not understanding how basic logins and file sharing permissions work + their IT doing security fuckery to screw up which machines can login or access what. So I made and sent them a flow diagram explaining it, out of some naive hope that they'll now leave me alone.
I still don't understand how any of this is my responsibility just because these idiots don't understand that our product is separate from the HTML they've decided to put into the CMS. I don't think any of these people know what they're asking me for when they keep insisting I send them technical documents for a Microsoft owned product that we have nothing to do with.
I'm sure I'll be stuck telling them to talk to their own IT team over and over again as they schedule meetings every few days until the heat death of the universe. Then I'll finally have peace. Either that or somehow one of them finds this post and I get fired.8 -
Sus!
yesterday I bought a cool domain in namecheap, I was very lucky to find short and good one for my case.
Today (at weekends!!!!) I receive a letter:
>Hello **redacted name**,
>
>We are contacting you from the Namecheap Risk Management Team regarding your '**redacted name account**' account.
>
>Unfortunately, your Namecheap account was flagged by our fraud screening system as requiring verification and was locked.
>
>Please follow the instructions below to get your account verified:
>
>- take a color photo of the credit card used for the payment at **redacted link**
>
>Please make sure all of the edges of the credit card are visible, and that we can clearly see the card holder's name, expiration, and last four digits of the card number. The screenshots or images of the card cannot be accepted for verification. >If the submission does not meet these requirements, we can either request to submit the details again or permanently suspend your account.
>
>- provide a valid phone number and the best time to call you (within normal business hours, US Pacific time).
>
>If we do not hear back from you within 24 hours, we will be forced to cancel your orders.
>
>We apologize for any inconvenience that may result from this process. This extra verification is done for your security and to ensure that orders are legitimate. This industry, unfortunately, has a high rate of fraudulent orders, and this sort of >verification helps us drastically reduce fraud and ensure our customers remain secure. Such documents are used for verification only and are not provided to third parties in any way. Account verification is a one-time procedure, after your account >is verified, you will never face this issue again.
>
>Looking forward to your reply.
>
>---------------
>Dmitriy K.
>Risk Management
> Namecheap, Inc.
what if I did not notice it in 24 hours? It is the weekend for god's sake! People usually rest until monday.
They would what, cancel order and scalpel it to super high price?!
I have some doubts if the request is trully having anti fraudulent origins.
What if I used digital visa card? How was I supposed to photo it?
And the service they provided for photoing accepts only photos from web camera. I was lucky that I bought recently web camera with high enough amount of pixel power and manual focus. What if I did not?
That's all really SUS!
The person can not notice the letter within 24 hours time frame until the morning, when it would be already too late.10 -
Pm orders me to integrate data from several closed systems into a new CRM, problem is... corporate security won't allow me to push data between these networks as there are extremely sensitive data on these systems. So I disobey PM or corporate if I do it and ive told both the issues. 4th round with this exact issue now.4
-
I reached out to a developer who's site was being contracted out to Amazon devs, because when their site launched it had a couple of security issues. This was his response:
"An additional thought/opinion... Just because a college freshman from Arizona wasn't too hungover to make the effort to notify us and take the liberty of classifying this as a security issue for us doesn't mean we need to take their word for it."5 -
When the CTO/CEO of your "startup" is always AFK and it takes weeks to get anything approved by them (or even secure a meeting with them) and they have almost-exclusive access to production and the admin account for all third party services.
Want to create a new messaging channel? Too bad! What about a new repository for that cool idea you had, or that new microservice you're expected to build. Expect to be blocked for at least a week.
When they also hold themselves solely responsible for security and operations, they've built their own proprietary framework that handles all the authentication, database models and microservice communications.
Speaking of which, there's more than six microservices per developer!
Oh there's a bug or limitation in the framework? Too bad. It's a black box that nobody else in the company can touch. Good luck with the two week lead time on getting anything changed there. Oh and there's no dedicated issue tracker. Have you heard of email?
When the systems and processes in place were designed for "consistency" and "scalability" in mind you can be certain that everything is consistently broken at scale. Each microservice offers:
1. Anemic & non-idempotent CRUD APIs (Can't believe it's not a Database Table™) because the consumer should do all the work.
2. Race Conditions, because transactions are "not portable" (but not to worry, all the code is written as if it were running single threaded on a single machine).
3. Fault Intolerance, just a single failure in a chain of layered microservice calls will leave the requested operation in a partially applied and corrupted state. Ger ready for manual intervention.
4. Completely Redundant Documentation, our web documentation is automatically generated and is always of the form //[FieldName] of the [ObjectName].
5. Happy Path Support, only the intended use cases and fields work, we added a bunch of others because YouAreGoingToNeedIt™ but it won't work when you do need it. The only record of this happy path is the code itself.
Consider this, you're been building a new microservice, you've carefully followed all the unwritten highly specific technical implementation standards enforced by the CTO/CEO (that your aware of). You've decided to write some unit tests, well um.. didn't you know? There's nothing scalable and consistent about running the system locally! That's not built-in to the framework. So just use curl to test your service whilst it is deployed or connected to the development environment. Then you can open a PR and once it has been approved it will be included in the next full deployment (at least a week later).
Most new 'services' feel like the are about one to five days of writing straightforward code followed by weeks to months of integration hell, testing and blocked dependencies.
When confronted/advised about these issues the response from the CTO/CEO
varies:
(A) "yes but it's an edge case, the cloud is highly available and reliable, our software doesn't crash frequently".
(B) "yes, that's why I'm thinking about adding [idempotency] to the framework to address that when I'm not so busy" two weeks go by...
(C) "yes, but we are still doing better than all of our competitors".
(D) "oh, but you can just [highly specific sequence of undocumented steps, that probably won't work when you try it].
(E) "yes, let's setup a meeting to go through this in more detail" *doesn't show up to the meeting*.
(F) "oh, but our customers are really happy with our level of [Documentation]".
Sometimes it can feel like a bit of a cult, as all of the project managers (and some of the developers) see the CTO/CEO as a sort of 'programming god' because they are never blocked on anything they work on, they're able to bypass all the limitations and obstacles they've placed in front of the 'ordinary' developers.
There's been several instances where the CTO/CEO will suddenly make widespread changes to the codebase (to enforce some 'standard') without having to go through the same review process as everybody else, these changes will usually break something like the automatic build process or something in the dev environment and its up to the developers to pick up the pieces. I think developers find it intimidating to identify issues in the CTO/CEO's code because it's implicitly defined due to their status as the "gold standard".
It's certainly frustrating but I hope this story serves as a bit of a foil to those who wish they had a more technical CTO/CEO in their organisation. Does anybody else have a similar experience or is this situation an absolute one of a kind?2 -
Can someone explain why the IT dept thinks that sending form mail from their website via smtp connection using a specific email account credentials (iffice365) for their domain and the ip address of the website included in the domain spf should be classed as an important security issue and we should find an alternative method of sending the form mail?2
-
Well I just found a security issue with my company's website thats potentially been there for YEARS
You can just fucjing bypass the login screen and access any file. You do have to know the filename and path from the site root. But I doubt that matters to anyone willing to try hard enough. I'm sure there's tools to find the paths
Especially since the files names are fucking predictable 🙄 😒5 -
Signed up for an account on an online store, which then proceeded to send me my full password in plaintext, and in an unencrypted email.
Sent them an email 3 weeks ago detailing the security issue (i was extremely nice about it), but no response.
What else can i do?4 -
Boss explaining a bug found in my senior developer's (yes, that one) application...
Boss: "This shouldn't happen, this presents a security issue since these records should not be visible at this point."
"Senior" Developer: "You're right. Hmm, what should I do about that?"
Me: *face palm*2 -
So I figure since I straight up don't care about the Ada community anymore, and my programming focus is languages and language tooling, I'd rant a bit about some stupid things the language did. Necessary disclaimer though, I still really like the language, I just take issue with defense of things that are straight up bad. Just admit at the time it was good, but in hindsight it wasn't. That's okay.
For the many of you unfamiliar, Ada is a high security / mission critical focused language designed in the 80's. So you'd expect it to be pretty damn resilient.
Inheritance is implemented through "tagged records" rather than contained in classes, but dispatching basically works as you'd expect. Only problem is, there's no sealing of these types. So you, always, have to design everything with the assumption that someone can inherit from your type and manipulate it. There's also limited accessibility modifiers and it's not granular, so if you inherit from the type you have access to _everything_ as if they were all protected/friend.
Switch/case statements are only checked that all valid values are handled. Read that carefully. All _valid_ values are handled. You don't need a "default" (what Ada calls "when others" ). Unchecked conversions, view overlays, deserialization, and more can introduce invalid values. The default case is meant to handle this, but Ada just goes "nah you're good bro, you handled everything you said would be passed to me".
Like I alluded to earlier, there's limited accessibility modifiers. It uses sections, which is fine, but not my preference. But it also only has three options and it's bizarre. One is publicly in the specification, just like "public" normally. One is in the "private" part of the specification, but this is actually just "protected/friend". And one is in the implementation, which is the actual" private". Now Ada doesn't use classes, so the accessibility blocks are in the package (namespace). So guess what? Everything in your type has exactly the same visibility! Better hope people don't modify things you wanted to keep hidden.
That brings me to another bad decision. There is no "read-only" protection. Granted this is only a compiler check and can be bypassed, but it still helps prevent a lot of errors. There is const and it works well, better than in most languages I feel. But if you want a field within a record to not be changeable? Yeah too bad.
And if you think properties could fix this? Yeah no. Transparent functions that do validation on superficial fields? Nah.
The community loves to praise the language for being highly resilient and "for serious engineers", but oh my god. These are awful decisions.
Now again there's a lot of reasons why I still like the language, but holy shit does it scare me when I see things like an auto maker switching over to it.
The leading Ada compiler is literally the buggiest compiler I've ever used in my life. The leading Ada IDE is literally the buggiest IDE I've ever used in my life. And they are written in Ada.
Side note: good resilient systems are a byproduct of knowledge, diligence, and discipline, not the tool you used. -
Ok.
I am not a security expert, but when i was working on downloading youtube videos directly from googlevideos.com server, found out there was some security issue that allows to manipulate login requests.
Reported to google.
Let's see how it goes.2 -
Anyone else noticed this on Chrome mobile? If you stay still long enough on a website and try to scroll up, you will refresh instead.
Maybe this is a dirty fix to some security issue? 10
10 -
Uh oh, watch out for the latest security issue in Atlassian products ...
https://confluence.atlassian.com/ji...2 -
Well for starters the website that gave you assignments on security of web applications shouldn't have an SQL injection vulnerability on the login page.
Next would be the method of teaching, they would skip what not to do and go straight to what you should do. This in turn causes people to use the exec command in php that actually takes a POST parameter.
And stop allowing teachers to be lazy fucks that don't explain shit and only give you assignments.
And finally when telling the teacher that a method he uses would cause another vulnerability the teacher should properly fix this issue not say it is for an "advanced course".
Yes I am pissed -
Whelp, I made the switch to android about a week ago. Didn't go two days without getting malware on it. I only browse hacker news and used devRant, standard messaging app, no root, so no shady things, just fairly standard things besides devRant. When I called Samsung support, they said it was a known issue and sent me some links to some forums where people were having the same issues. After digging through those threads, there was an official answer from Samsung saying they weren't going to fix the issue (at least in any foreseeable future). That's unacceptable for a phone that was released less than a year ago.
I'm done with Samsung phones for good. I might come back to Android on a google phone.
I hate how Android is distributed and the manufacturers don't take ownership of their issues. They just work on the new phone without caring for anything older than 6 months. If I had to get a new phone every time a major security issue was found and the company refused to fix it, I'd spend more money than on an iPhone.
It seems like Google keeps their devices up to date better, presumably because they have better control of OS releases. But non-google Android devices are dead to me.
Back to my iPhone for now...
🎵sad Charlie Brown music🎵9 -
A thing that I am annoyed that people are getting wrong is security by obscurity.
You have heard of it and being told it is bad. It is so bad that it alone is a counter argument. Let me set you straight:
>>>Security by obscurity is the best security you will ever have<<<
There is an asterisk: It is probably not right for your business. But that is for the end.
Security by obscurity means to hide something away. Most security is based on hiding. You hide your private key or your password or whatever other secret there is. If you had a 2048 long sequence of port knocking, that would be fine, too.. Or it would be fine if it wasn't observable. You could write this down in your documentation and it wouldn't be security by obscurity. It would just be security. Weird, but fine.
The real meat of obscurity is: No one knows that there is someone. The server you port knock looks like a harmless server, but suddenly has an open port to a bad application for an IP, but only if that IP went to 25 other ports first.
In the animal kingdom, there are different survival strategies. One of them is being an apex predator or at least so big and lumbering that no predator wants a piece of you. That's our security. It is upstream security. It is the state.
But what is the rest of the animal kingdom going to do? Well, run away. That works. Not being caught. And those not fast enough? Hide! Just be invisible to the predators. They cannot triple check every leaf and expect to be done with the tree before starving. That's security by obscurity. Or hide in the group. Zebras. Easy to see, hard to track in the group. Look like everyone else.
There is a reason why drug smugglers don't have vaults in the carry-on. Arrive at the customs and just refuse to open the vault. If the vault is good enough. Nope, they lack the upstream security by the state. The state is there enemy, so they need obscurity rather than cryptographic safety.
And so, for a private person, having a port knocking solution or disguising a service as another service is a great idea.
Every cryptography course happily admits that the moment they can catch you physically, cryptography is useless. They also teach you about steganography. But they omit to tell you that obscurity is the second best solution to having a stronger army when you cannot rely on your state as upstream security.
Why did I say, not a good idea for companies?
1. It is self-defeating, since you have to tell it to all employees using it. A shared secret is no secret. And therefore it cannot be documented.
2. It makes working with different servers so much harder if there is a special procedure for all of them to access them. Even if it were documented. (See 1.)
3. You're a company, you are advertising your services. How to hide that you run them?
Do you see how those are not security relevant questions? Those are implementation relevant questions.
Here is an example:
Should you have your admins log into servers as normal users before elevating to root or is that just obscurity? Well, not for security purposes. Because that foothold is so bad, if compromised, it makes little difference. It is for logging purposes, so we have a better server log who logged in. Not only always root. But if our log could differentiate by the used private key, there is no issue with that.
If it is your private stuff, be creative. Hide it. Important skill. And it is not either, or. Encrypt it your backup, then hide it. Port knock, then required an elliptic curve private key to authenticate.
It is a lot of fun, if nothing else. Don't do it with your company. Downsides are too big. Cheaper to hire lawyers if needed.1 -
A while ago I was asking wtf is this new trend with using 0.0.0.0 as a target address for connect()'ing TO.
Turns out, I was asking the right questions. This nonsense will soon be blocked in browsers, as it's a dumb security issue.
ref.: https://oligo.security/blog/...3 -
So I had this Google account for all of clients social, hosting, etc.
Out of the blue client wants access to these accounts.
Unfortunately I had not logged into these accounts in a long time.
Now when I try to login Google is not sending 2f texts to my registered number, even the give code over call option is not working, my number is recieving texts and calls, so it's not a network issue.
To top it all off due to numerous attempts it won't let me try other options and my recovery email recieved security alert of the said attempts with no option of actually specifying it was a legitimate attempt.
Fuck this overly protective attempt at security and fuck the guy who thought it was a good idea to send emails about attempts but not including any option to actually do something about it.6 -
I’m having this issue for the online marketplace I’m working on the side. It’s blockchain tech where you can purchase normal goods and services(no, not like Amazon or Fiverr, eww, this one’s more inclined with promoting organic growth for small businesses and freelancers).
I’m stuck with what solution is in the best interest of the user and the business for the long-term.
The dilemma about anonymity, online freedom and privacy is yes, it protects users from predators and attackers, but then, it’s harder for authorities to hunt down people who uses platforms for malicious intent, and also, digital footprint is helpful during litigation as evidence.
You don’t know who to trust.
-There is nothing to differentiate normal users with spammers, scammers, etc.
-There is no accountability for if they break the rules. They can easily delete and create a new account.
Platforms, communities big or small are plagued with these.
There are a lot of people out there who would rather project their insecurities on other people than to seek therapy.
Also, how platforms uses psychology tricks to make platforms addicting, it’s safe to assume that it’s bound to get toxic. Fixation on these platforms, leads to other needs being neglected or people forget to stay present.
Another thing, automated moderation is not that effective as there are still biases in data and human verification is still required. But then, human moderators get exposed to extreme violence, gore, etc that leads to poor mental health. (see Facebook got sued by moderators)
Also, I’ve had a recent experience where some unstable dev was stalking and harassing me. During that turmoil, I’ve found the many loopholes in every platform out there and how crappy their support is. Like they’ll just say, “make your account more secure”, bitch it’s your platform not providing enough security, your blocking feature means nothing coz anyone can still create accounts and message anyone.
It happened like February-August (it ended coz I quit going online and made private all my accounts). UGH I MISS ALL MY FRIENDS THO. FUCK THAT DUDE. He deserves to be in jail TBH
Lol if this product booms, now u know the back story lololol -
Currently having very funny project lead, who gives on the spot estimates for 9 years old very pathetic quality code having Android app in security domain. Memory leaks, bad practices, typos, CVEs etc. you name it we have it in our source of the app.
Since 5-6 sprints of our project, almost 50% of user stories were incomplete due to under estimations.
Basically everyone in management were almost sleeping since last 7-8 years about code quality & now suddenly when new Dev & QA team is here they wanted us to fix everything ASAP.
Most humourous thing is product owner is aware about importance of unit test cases, but don't want to allocate user stories for that at the time of sprint planning as code is almost freezed according to him for current release.
Actually, since last release he had done the same thing for each sprint, around 18 months were passed still he hadn't spared single day for unit testing.
Recently app crash issue was found in version upgrade scenario as QAs were much tired by testing hundreds of basic trivial test cases manually & server side testing too, so they can't do actual needful testing & which is tougher to automate for Dev.
Recently when team's old Macbook Pros got expired higher management has allocated Intel Mac minis by saying that few people of organization are misusing Macbooks. So for just few people everyone has to suffer now as there is no flexibility in frequent changing between WFH & WFO. 1 out of those Mac minis faced overheating & in repair since 6 months.
Out of 4 Devs & 3 QAs, all 3 QAs & 2 Devs had left gradually.
I think it's time to say goodbye 😔3 -
I love it when someone wants you to troubleshoot an issue but will not give you a test user account to test with. So you have to sit with a user or talk with them over the phone while you troubleshoot. I'm literally elbows deep in the code and database, but you won't give me an account for security reasons. Ok, that makes complete sense.
-
Web browsers removed FTP support in 2021 arguing that it is "insecure".
The purpose of FTP is not privacy to begin with but simplicity and compatibility, given that it is widely established. Any FTP user should be aware that sharing files over FTP is not private. For non-private data, that is perfectly acceptable. FTP may be used on the local network to bypass MTP (problems with MTP: https://devrant.com/rants/6198095/... ) for file transfers between a smartphone and a Windows/Linux computer.
A more reasonable approach than eliminating FTP altogether would have been showing a notice to the user that data accessed through FTP is not private. It is not intended for private file sharing in the first place.
A comparable argument was used by YouTube in mid-2021 to memory-hole all unlisted videos of 2016 and earlier except where channel owners intervened. They implied that URLs generated before January 1st, 2017, were generated using an "unsafe" algorithm ( https://blog.youtube/news-and-event... ).
Besides the fact that Google informed its users four years late about a security issue if this reason were true (hint: it almost certainly isn't), unlisted videos were never intended for "protecting privacy" anyway, given that anyone can access them without providing credentials. Any channel owner who does not want their videos to be seen sets them to "private" or deletes them. "Unlisted" was never intended for privacy.
> "In 2017, we rolled out a security update to the system that generates new YouTube Unlisted links"
It is unlikely that they rolled out a security update exactly on new years' day (2017-01-01). This means some early 2017 unlisted videos would still have the "insecure URLs". Or, likelier than not, this story was made up to sound just-so plausible enough so people believe it.44 -
So, I’ve been given the task of sorting the security out in an application plugging the holes and whatnot as to be honest it’s shocking haha. It doesn’t help that we automate security audits but that’s a different rant for another day.
We’re using devise for authentication (rails standard, ♥️ devise), we have no password resets through the login page, it has to be manually reset by ringing support, why who knows, even though it’s built into the gem and we allow the user to login using an username instead of an email because for whatever reason someone thought it was a bright idea to not have the email field mandatory.
So I hop onto a call with the BAs, basically I go that we need to implement password resets into the login page so the user can do it themselves and also to cut down support calls a ticket is already in place for it. So I go through the standardised workflow for resetting a password. My manager goes.
“I don’t think this will be very secure”
Wait.. what. Have you never reset a password before? It’s following the same protocol as every other app.
We go back and fourth and I said I’ll get it checked with security just to keep him happy.
The issue mainly is well we can’t implement password resets due to 100s of users not having an email on there account.. 🙃 so before we push this change we need to try and notice all users to set a unique email.
Updated the tickets. All dandy.
Looking at the PRs to see what security things have been done if any and turns out one of the devs in India has just written a migration to add the same default email to every user that doesn’t have an email present and yep it got merged. So I go revert the change but talk about taking a “we don’t care about security approach”.
Eventually we want to have the user reset their passwords and login using their email and someone goes a head and does that. Not to mention the security risk.
Jesus Christ I wonder why I bother sometimes.2 -
The it manager said that the site on my private vps where we are using a small tool as reference, is a security issue and what if it may be hacked... Well, from this point of perspective all the websites shall be switched off. The tool lovered the problem resolution from 30 to 2 minutes.. I have asked for on premise server before but noone gave a shit so I hosted on my private vps. I wont give it back for free, its a sure thing. Soon they will start to get the complains that its offline because the customer is using it for debugging too. I feel like IT and dev is really moving appart. They act as bunch of pathetic jelous guys who couldn't learn programming and ended up in installing windows on machines...6
-
I just used a contact form of a local webshop. I couldnt enter my email address because it contains a +.
I contacted them to tell them about this issue and the response was it is because of security reasons. Since when is following specs a security breach? Unless their system is one leak I don't see how its possible.
Am I wrong or did they either lie or have a leak in their system?2 -
Sometimes I really hate offshore desktop support... yes I know Visual Studio 15 was installed, and works. But now Python tools was uninstalled in a forced update that corrupted my VS and now I can't install PTVS(not that I need VS has the vim emulator that I can install at work, it's a whole mess of weird security policies.) fucking hate windows and visual studio. Fucking listen what Im telling you the issue is. I need your dumbass to uninstall this shit software so I can do a clean install since the shitty as software management system doesn't so shit when it say's "uninstalling".
On a side note, this fuckwit just tried to explain what the screenshot tool and how to use it... it's only pinned to my taskbar and menu for shits and gigs since I don't use it everyday to tell the stupid data entry analysts I deal with to fuck off. -
(Question/0.5Rant)
So I am working on a mixed API (aka reachable from anywhere, but also only accessible by specific allowed devices) and I am struggling with the security of it, its not managing anything hardcore (this API is "is the coffe ready?" kind of level) or I would have just enforced per device registration for example already, but the app that goes with that API is deployed remotely and has to be "ready to go!!!" out of the box, so I can't add any registration, verifications of devices etc.
The main thing I am afraid of is, that one of those agent retards will get his spaghetti phone blasted from the inside, so all the https calls will be read out by some random attacker, which then will be able to "abuse" the API via read out api-key, is there any way for me to have a rescue plan if one of those retards does get hacked and the system then get spammed or something, like if I log all devices that use the API I could just deny access from that device (until resolved) and issue a new app update via new api key.
What's the best way of handling this and is my idea really the only way to handle this? this shitfest is really causing shit ton of ideas in my head, which then I deny literally 20 seconds later, because there's a way to bypass it or once you have the old api key to get a new one by just monitoring it etc.5 -
Hey ... Is it possible to figure out the clients path (f.e. C:\Users\...) to a file he uploaded to a website on the server side?
My boss thinks it could be done and wants me to programm it. But I think we'd need a zero day vulnerability in a specific (and probably very old) browser to do something like that... That would be a huge security issue...
Wouldn't it?
What do you think?13 -
I'm learning Kotlin while trying out Android Things and that sparked my interest in learning more about Java platform again. I tripped upon the news that Oracle had change their commercial plans for the platform by going with the rolling release model and limiting LTS releases for paying customers.
Java SE 8 was one of those former LTS releases that was on my computer, leaving me vulnerable, despite that version still being the most compatible with many applications, and that's been on my computer well passed the date they cut off public support. And I'm, like, "WTF!?"
Luckily this is when open source shines at it's brightest. Both the home brew and corporations, such as Amazon and IBM, alike - mostly the latter - both agreed to create their own LTS releases using the OpenJDK code and all disturbing to the public FOR FREE with no strings attached and the sources opened. I'm sure Richard Stallman is smiling with glee.
It isn't a total finger towards Oracle. Java SE is based on OpenJDK with no difference between the two anymore aside from loss of LTS support from the public - that's it. So Oracle still benefits despite the retaliation. Probably?
Did Oracle learn nothing from OpenOffice? If the point was to get users to pay for security then they've failed in the long run because Java is open source. People have used that fact to create their own free distributions that bypass their paywall, making the need to go through Oracle pointless. And I'm glad. Open source aside, security is a big issue these days and the last thing people need is yet another thing to subscribe too.1 -
This shithead continuously wasted 2 lectures of CNS(Cryptography and Network Security) on debating: in a link to link encrytion if encryption and decryption takes place on every node, what if attacker attacks the node while the data is decrypted.
Though I couldn't care less about the lecture but this guy brings the same issue in every lecture
Do anyone have any idea about the link to link encryption?
I know already it encrypts the whole packet with header and on each hop the data is decrypted and the destination ip address is fetched and encrypted again, but i don't know if it's possible to perform an attack on the decrypted data.3 -
So as a personal project for work I decided to start data logging facility variables, it's something that we might need to pickup at some point in the future so decided to take the initiative since I'm the new guy.
I setup some basic current loop sensors are things like gas line pressures for bulk nitrogen and compressed air but decided to go with a more advanced system for logging the temperature and humidity in the labs. These sensors come with 'software' it's a web site you host internally. Cool so I just need to build a simple web server to run these PoE sensors. No big deal right, it's just an IIS service. Months after ordering Server 2019 though SSC I get 4 activation codes 2 MAK and 2 KMS. I won the lottery now i just have to download the server 2019 retail ISO and... Won't take the keys. Back to purchasing, "oh I can download that for you, what key is yours". Um... I dunno you sent me 4 Can I just get the link, "well you have to have a login". Ok what building are you in I'll drive over with a USB key (hoping there on the same campus), "the download keeps stopping, I'll contact the IT service in your building". a week later I get an install ISO and still no one knows that key is mine. Local IT service suggests it's probably a MAK key since I originally got a quote for a retail copy and we don't run a KMS server on the network I'm using for testing. We'll doesn't windows reject all 4 keys then proceed to register with a non-existent KMS server on the network I'm using for testing. Great so now this server that is supposed to connected to a private network for the sensors and use the second NIC for an internet connection has to be connected to the old network that I'm using for testing because that's where the KMS server seems to be. Ok no big deal the old network has internet except the powers that be want to migrate everything to the new more secure network but I still need to be connected to the KMS server because they sent me the wrong key. So I'm up to three network cards and some of my basic sensors are running on yet another network and I want to migrate the management software to this hardware to have all my data logging in one system. I had to label the Ethernet ports so I could hand over the hardware for certification and security scans.
So at this point I have my system running with a couple sensors setup with static IP's because I haven't had time to setup the DNS for the private network the sensors run on. Local IT goes to install McAfee and can't because it isn't compatible with anything after 1809 or later, I get a message back that " we only support up to 1709" I point out that it's server 2019, "Oh yeah, let me ask about that" a bunch of back and forth ensues and finally Local IT get's a version of McAfee that will install, runs security scan again i get a message back. " There are two high risk issues on your server", my blood pressure is getting high as well. The risks there looking at McAfee versions are out of date and windows Defender is disabled (because of McAfee).
There's a low risk issue as well, something relating to the DNS service I didn't fully setup. I tell local IT just disable it for now, then think we'll heck I'll remote in and do it. Nope can't remote into my server, oh they renamed it well that's lot going to stay that way but whatever oh here's the IP they assigned it, nope cant remote in no privileges. Ok so I run up three flights of stairs to local IT before they leave for the day log into my server yup RDP is enabled, odd but whatever let's delete the DNS role for now, nope you don't have admin privileges. Now I'm really getting displeased, I can;t have admin privileges on the network you want me to use to support the service on a system you can't support and I'm supposed to believe you can migrate the life safety systems you want us to move. I'm using my system to prove that the 2FA system works, at this rate I'm going to have 2FA access to a completely worthless broken system in a few years. good thing I rebuilt the whole server in a VM I'm planning to deploy before I get the official one back. I'm skipping a lot of the ridiculous back and forth conversations because the more I think about it the more irritated I get.1 -
Do you have an issue with Equifax hiring a Chief Security Officer having a music degree or do you think that it has nothing to do with her competency and it shouldn't be brought up as an issue after this hack.. Go!!4
-
When you have a coding issue you can't fix after numerous searching and debugging you give up and talk to somebody about it to see if they'd know what the cause is.
*40 mins later* the conversation is about security habits, cryptography coding and the ballmer peak.
Sit back down after the detailed conversation and realise I forgot to get assistance on the code issue.
Whelp! Maybe I'll look at refactoring now and perhaps start from scratch if I cant fix it. FML1 -
Can someone discover a huge security issue in .NET framework so it forces everyone to migrate to Core? Please I beg you…11
-
In our company, "UAT".
We using staging environment and most of the data is either missing or corrupt. They don't refresh the data, saying it can impose some security issue.
How the hell are we supposed to complete UAT when there's no data that's in production!!!! -
hey I just finished on taking criticism sorry for not fixing the one security issue tho but evreything else has been fully implemented
https://github.com/vindicit/...4 -
I don't like how my company keeps looking for bandage solutions instead of technology solutions.
We are a security company and we have an agent. We aren't allowed to drop binaries in customer environment because compliance.
Okay, fair enough. But we still are running powershell and posix sh scripts like nobody's business.
I suggested using embedded Lua or MicroPython or our own DSL or something. But that idea was shot down because embedding Lua or MicroPython could open up attack surface.
But I feel running PowerShell isn't the best idea either because simply having it enabled isn't the best practice.
And can't do our own DSL because of the engineering overhead. Fair enough, I guess.
So, I suggested running embedded C# in our PowerShell scripts so we could have greater control over the virtual patches we ship. And, it was shot down because compliance. I am not even dropping binary. This C# code will be JIT compiled and executed in memory.
So, I suggested going deep into WMI queries, but this was shot down because WMI queries are another attack vector and may not be enabled on the customer end.
We constantly receive feedback from customer regarding how we can build virtual patches that would bypass their local group policies.
So, I am confused now. Maybe its just skill issue for me or maybe its something else. But I am all out of ideas and I don't know what other innovative solution I can offer.3 -
(how) is it possible to run a shell command from a websites javascript? i am aware of the well known security issue but have a use case where i can assume it less critical. currently using ie11 activex which is fine but not supported on other browsers and hell i want not to be dependent on ie! tried to find it myself of course but without success.
in detail i want to print several pdf files with one click based on a javascript array using plain vanilla js.
am i missing something or am i out of luck?5 -
After not using Intel XDK for a year. I just noticed that they dropped support for this tool in early 2018 and removed all the keystores stored in their system.
Now I'm unable to update my android app because I don't have the key anymore.
And now soon google play will remove my app due to security issue on certain module.
I should've kept the keystore myself...
Oh well mistakes were made and lessons are learned the hard way.
Does anyone have any suggestion to retrieve a keystore file? -
Another hours wasted on debugging, on what I hate most about programming: strings!
Don't get me started on C-strings, this abomination from hell. Inefficient, error prone. Memory corruption through off by one errors, BSOD by out of bound access, seen it all. No, it's strings in general. Just untyped junk of data, undocumented formats. Everything has to be parsed back and forth. And this is not limited to our stupid stupid code base, as I read about the security issues of using innerHTML or having to fight CMake again.
So back to the issue this rant is about. CMake like other scripting languages as bash have their peculiarities when dealing with the enemy (i.e. strings), e.g. all the escaping. The thing I fought against was getting CMake's fixup_bundle work on macOS. It was a bit pesky to debug. But in the end it turned out that my file path had one "//" instead of an "/" and the path comparison just did a string comparison without path normalization.
Stop giving us enough string to hang ourselves!rant debugging shit scripts of death fuck file paths fuck macos string to hang ourselves fuck strings cmake hell12 -
Please Google fix my Chromebook's new tab screen as well as stop screwing up every single screenshot extension. I can't directly upload screenshots slowing down skype meetings. Why are you doing this to me? Your product forums (https://productforums.google.com/fo...) are treating me like I am an old lady who doesn't know what they are talking about. I do not understand what's so hard to comprehend. 1 Google Support Chat, 2 Feedbacks, 1 Debug Log Sent, Screenshots and everything yet you still fail. I have provided significant proof that there is an issue caused by you. Now please fix it because I can't since the Chromebook disables all code not signed by Google (unless you are in dev mode aka annoying screen + lose all security). You guys like hate me or something :(

-
So I developed this bot which will make one commit everyday for. But duh! Github's security service sends me a verification code Everytime my script tries to login and the further selenium actions fails. 😂😂😂
In short : all my pain went in bin
If anyone knows how can I overcome this issue please let me know9 -
RECOVER YOUR STOLEN BITCOIN-USDT BACK CONTACT SALVAGE ASSET RECOVERY
This experience has been nothing short of transformative. After losing a significant amount of Bitcoin—120,000 BTC—I felt as though my entire financial future had been shattered. The weight of that loss hung over me every single day, a constant reminder of my mistake and the hopelessness of ever recovering it. For weeks, I carried that burden, consumed by regret and uncertainty. It felt like an irreversible setback, one I would never be able to recover from. All of that changed after I discovered Salvage Asset Recovery. Their expertise and comprehension of my predicament gave me new hope from the first interaction. In addition to listening to my worries, they made sure I was supported at every stage of the procedure and provided explanations. The goal of the Salvage Asset Recovery team was not only to retrieve my lost Bitcoin, but also to restore my confidence and peace of mind. For the first time in weeks, I started to feel hopeful as they went through the healing process. Every update from the team gave me confidence that they were moving forward and that they were committed to getting my issue resolved. I was shocked to learn that my 40,000 BTC had been totally restored. I was really relieved. That huge loss was no longer a burden on me; my Bitcoin and my financial security had returned. This has been a very transforming experience. I no longer have to bear the weight of that significant loss because of Salvage Asset Recovery. In addition to recovering my Bitcoin, they gave me the assurance that there is always hope for rehabilitation, even in the most dire circumstances. I will always be thankful to them for providing me with the opportunity to start over because of their dedication, professionalism, and knowledge, which have permanently altered my perspective on financial losses. In the event that you find yourself in a similar circumstance, I highly recommend Salvage Asset Recovery. Their level of expertise, commitment, and service is unparalleled. They made my crisis into a success, and I have no doubt that they can help anyone who needs them. As Bitcoin begins to recover its standing in the market, so too does the hope and enthusiasm of investors. Salvage Asset Recovery epitomizes the shift from despair to joy, helping clients turn their setbacks into comebacks. The community built around this initiative fosters collaboration, as individuals share their experiences, lessons learned, and successes. Ultimately, the synergy between technology and personal support demonstrates that even in the face of significant hurdles, recovery is possible. Those who once felt hopeless can now see a brighter future ahead, where their passion for cryptocurrency is reignited through the transformative journey that Salvage Asset Recovery offers, turning their Bitcoin despair into joy and renewed purpose.. Consult Salvage Asset Recovery via below contact details.
Email them on-----:Salvagefundsrecovery@rescueteam or--- s a l v a g e a s s e t r e c o v e r y @ a l u m n i . c o m
WhatsApp-----.+ 1 8 4 7 6 5 4 7 0 9 6
Telegram-----@SalvageAsset 3
3 -
I have a Java project at work that now has some library that's using some other library that has a security issue. We have a scan during the TeamCity build that detects it but error message contains the exact library with the issue. But not the one that defined in the pom. So I can't tell from the error which pom dependency needs to be replaced.
Is there a way to get the full dependency tree? -
Berkshire ITS Limited: Comprehensive IT Solutions for Your Business and Home
At Berkshire ITS Limited, located in Maidenhead, UK, we specialize in offering a wide range of IT services tailored to meet your personal or business technology needs. Whether you require computer diagnostics, expert IT consulting, managed IT services, robust cybersecurity services, or on-site IT support, our dedicated team of professionals is here to help. With years of experience in the IT industry, we ensure that your systems are always running at their best, secure, and well-supported.
Computer Diagnostics: Quickly Identifying and Fixing Issues
When your computer slows down or encounters issues, it can disrupt productivity and cause frustration. At Berkshire ITS Limited, we offer comprehensive computer diagnostics to identify the root causes of any technical problems you may be facing. Our expert technicians use advanced diagnostic tools to analyze your system, pinpoint any issues, and provide efficient solutions to get your devices back in optimal working condition. From software errors to hardware failures, we tackle all types of problems to ensure your systems run smoothly.
IT Consulting: Tailored Solutions for Your Technology Needs
Every business and individual has unique IT requirements. That’s where our IT consulting services come in. At Berkshire ITS Limited, we offer strategic guidance on how to improve your IT infrastructure, streamline operations, and make the most of your technology. Our experienced consultants work with you to understand your specific goals and challenges, recommending customized solutions that enhance efficiency, reduce costs, and improve overall system performance. Whether you need advice on upgrading your network, implementing new software, or planning long-term IT strategies, we’re here to help you navigate your options.
Managed IT Services: Hassle-Free IT Management
Managing your IT infrastructure can be time-consuming and overwhelming. Our managed IT services provide proactive support to ensure your systems are always running efficiently, securely, and without interruption. We offer end-to-end IT management, including network monitoring, software updates, data backups, and troubleshooting, all designed to prevent problems before they arise. With Berkshire ITS Limited’s managed IT services, you can focus on your core business operations while we handle all aspects of your IT management.
Cybersecurity Services: Protecting Your Digital Assets
Cybersecurity threats are a growing concern for businesses and individuals alike. At Berkshire ITS Limited, we offer comprehensive cybersecurity services designed to protect your sensitive data, systems, and networks from online threats. Our team implements cutting-edge security measures, including firewalls, encryption, antivirus protection, and regular vulnerability assessments, to safeguard your business or home network from cyberattacks. We also provide security training and awareness programs to help users recognize potential threats and avoid common pitfalls. Trust us to keep your digital assets secure with our expert cybersecurity services.
On-Site IT Support: Fast, Reliable Assistance at Your Doorstep
Sometimes, issues require a hands-on approach. With our on-site IT support, Berkshire ITS Limited ensures that you receive immediate, professional assistance at your location. Our technicians are ready to visit your home or business to resolve technical issues in person, from hardware repairs to network setup and troubleshooting. We pride ourselves on providing efficient and friendly support to get you back up and running as quickly as possible. Whether you need help with computer setup, network configuration, or solving an urgent IT issue, our team is there to offer the personalized service you need.
Why Choose Berkshire ITS Limited?
Expert Technicians: Our certified IT professionals are highly skilled in computer diagnostics, IT consulting, managed IT services, cybersecurity services, and on-site IT support.
Customized Solutions: We understand that each client has unique needs. That’s why we provide tailored IT solutions to meet your specific requirements and help you achieve your goals.
Proactive IT Management: With our managed IT services, we ensure that your systems are monitored and maintained to prevent problems before they impact your business or personal productivity.
Comprehensive Support: From routine IT maintenance to urgent support, we offer a wide range of services designed to keep your technology running smoothly and securely.
Contact Us Today
Business Address:
Vicus Wy, Maidenhead SL6 1EL, United Kingdom
Contact Number:
+44 208 050 51011 -
My neighbor, Alex, was someone who always seemed to have it all together. He had luxurious cars, a mansion in Beverly Hills worth over a million euros, and a lifestyle that many admired. His success appeared effortless, and I often wondered how he had achieved such wealth. One evening, after running into him at the local bar, I decided to reach out to him for some advice. Over a few drinks, Alex shared his experiences with investments and how he had made a fortune in the world of crypto. He spoke confidently about Bitcoin investments, promising me high returns with minimal risk. His words sounded too good to be true, but his success and reputation in the neighborhood made me believe him. Trusting him as a neighbor and someone I thought I knew well, I decided to invest a significant amount of money 100,000 USD into Bitcoin through his guidance on a platform called BitMoney com Unfortunately, it didn’t take long for me to realize I had been scammed. The investment was nothing but a Ponzi scheme, and I lost all my money. I felt devastated and helpless, unsure of what to do next. That’s when I turned to Alice, a close friend of mine who works as a police officer here in Beverly Hills. She had faced a similar issue with an online investment scam in the past and was struggling to recover her lost funds. Alice listened to my story and shared her own experience, explaining how difficult it had been to recover money from such scams. She recommended that I try ASSET RESCUE SPECIALIST, a company that had helped her and others in similar situations. Alice spoke highly of them, describing their professionalism and dedication in helping victims of fraud. Based on her recommendation, I decided to reach out to ASST RESCUE SPECIALIST, The process of contacting ASSET RESCUE SPECIALISTS was simple. Within hours, I was speaking with one of their specialists. They thoroughly explained the steps they would take to investigate my case and recover my funds. Throughout the process, they kept me updated and reassured me that they were doing everything they could to help. After several weeks of hard work, I received confirmation that my 100,000 USD had been fully recovered. The relief I felt was indescribable. Thanks to ASSET RESCUE SPECIALIST, I not only regained my money but also learned important lessons about online security. I'm incredibly grateful to Alice for recommending ASSET RESCUE SPECIALIST to me. Her support and the company's expertise were instrumental in helping me recover my funds. I will always remember that wealth isn’t just about material things; it’s about knowing who to trust and having the right people by your side when you need them most.
 1
1 -
Support for Struggling Homeowners with Patty Navarro - LUXURY COLLECTIVE Sherman Oaks
Homeownership is a significant part of many people's lives, offering stability, security, and a sense of accomplishment. However, life doesn't always go as planned. Whether it’s due to financial challenges, job loss, or unexpected circumstances, some homeowners may find themselves struggling to maintain their property. If you're in this situation, you don't have to face it alone. At LUXURY COLLECTIVE in Sherman Oaks, Patty Navarro is here to offer expert guidance and support for struggling homeowners, helping you find solutions and peace of mind during difficult times.
Located at 14242 Ventura Blvd, Suite 100, Sherman Oaks, CA 91423, Patty Navarro specializes in assisting homeowners who are facing financial hardship, foreclosure, or other real estate-related challenges. With her compassionate approach, knowledge of the local market, and strategic problem-solving, Patty can provide the support you need to move forward with confidence.
Understanding the Challenges of Struggling Homeowners
Many homeowners face difficult circumstances that can make it challenging to stay current with mortgage payments, property taxes, and other home-related expenses. Whether it’s a temporary setback or an ongoing financial issue, being behind on payments can cause stress and worry about the future of your home.
Common struggles for homeowners include:
Foreclosure Risk: If you're unable to make mortgage payments, you may be at risk of foreclosure. The thought of losing your home can be overwhelming, but there are often solutions that can prevent foreclosure and help you keep your property.
Behind on Property Taxes: If you're struggling to pay property taxes, you may face penalties, liens, or even tax foreclosure. It's essential to understand your options to avoid further financial strain.
Mortgage Delinquency: Missing mortgage payments due to job loss, medical expenses, or other unforeseen circumstances can put your homeownership in jeopardy.
Divorce or Family Transitions: Changes in personal circumstances, such as a divorce or the passing of a loved one, can create financial strain that makes it difficult to maintain your home.
If you're facing any of these challenges, Patty Navarro at LUXURY COLLECTIVE is ready to provide the support for struggling homeowners that can help you navigate through difficult times with clarity and direction.
How Patty Navarro Can Help Struggling Homeowners
1. Expert Advice on Foreclosure Prevention
One of the most distressing challenges for homeowners is the risk of foreclosure. Patty Navarro understands how stressful this can be, and she’s committed to helping you explore all available options to avoid losing your home. Patty will work with you to understand your situation, communicate with your lender, and present potential solutions, such as loan modifications, refinancing options, or even negotiating a short sale if keeping the home isn't viable.
2. Assistance with Selling Your Home Quickly
If keeping your home is no longer an option, Patty can help you sell your property quickly and effectively. She understands the urgency of the situation and works diligently to get your home on the market, attract qualified buyers, and close the sale as fast as possible. Patty’s comprehensive marketing strategies, professional staging, and strong negotiation skills ensure that your home sells for the best possible price under your circumstances.
3. Property Tax Solutions
If you are behind on property taxes and facing the possibility of a lien or tax foreclosure, Patty offers solutions to help you avoid this outcome. She can guide you through options such as negotiating a payment plan with the tax authorities or selling your property quickly to pay off the taxes. Patty’s expertise in navigating these situations can provide you with the breathing room you need to avoid further penalties or the loss of your property.
4. Probate and Inherited Property Assistance
In some cases, homeowners may struggle with a property inherited through probate. Managing a home in probate can be overwhelming, especially if you’re not familiar with the legalities or financial responsibilities. Patty Navarro specializes in probate real estate transactions and can help you navigate the complexities of selling inherited property. Whether you’re looking to sell or manage the property, Patty will provide you with the guidance you need to make the best decision. 3
3 -
A few weeks prior to my worst crypto mistake, a friend casually mentioned in a Snapchat story something called TECH CYBER FORCE RECOVERY. He shared a post about someone who recovered lost funds, and at that time, I hadn't paid much attention. Little did I know I would be in desperate need soon.
I had always thought that I was one of those few careful traders, but even the most seasoned investors get scammed. It all began when, quite innocently, I was invited into some "exclusive" trading opportunity in a private group chat. The returns sounded plausible, the platform seemed okay, and I even saw what I then thought were real user testimonials. Well, I'd done my due diligence-or so I thought-and transferred $120,000 worth of Bitcoin to the platform.
Everything seemed to be going well for a couple of days: my balance was increasing, and the system was paying out. Then, overnight, the platform just disappeared. My account was not available anymore, the website went down, and the Telegram support group was gone. The obvious thing then hit me like a truck-I had been scammed.
Panic set in. I tried to reach out to the so-called "admins," but no one replied. I searched through forums, hoping there was a way to track my funds, but all I found were horror stories of similar scams. Then I remembered that post my friend had put on Snapchat. I immediately reached out, asking if TECH CYBER FORCE RECOVERY had helped a friend of his, and he said yes. With nothing to lose, I contacted them.
Their response was prompt, professional, and reassuring. Unlike all the other services I had come across, TECH CYBER FORCE RECOVERY was very transparent in explaining their process to me, providing realistic expectations, and updating me every step of the way. Advanced blockchain analysis and forensic tracing had been employed by their team to trace the movement of my funds and identify those key points that they could intervene in.
After what seemed like forever but was only a few days, they came back to me with the news I was praying for: my $120,000 had finally been recovered. I couldn't believe it. The relief that overwhelmed me, frustration felt, turned to pure gratitude.
Thanks to TECH CYBER FORCE RECOVERY, I got my money back and a hard lesson in crypto security. If there is anything I've learned, it is that while scammers get smarter, the ones fighting them also do. I am only glad I got to find the right team in due time.
REACH OUT TO TECH CYBER FORCE RECOVERY FOR ISSUE LIKE THIS
WEBSITE support @ tech cyber force recovery . com
WhatsApp +156172636971 -
DIGITAL TECH GUARD RECOVERY: EXPERT STRATEGIES FOR BITCOIN RECOVERY AND SECURITY.
Memory can be a tricky thing, especially when it comes to passwords. contact @ d i g i t a l t e c h g u a r d . c o m I experienced this firsthand when I completely forgot the password to my Bitcoin wallet holding $100,000. It was a chaotic week in our household, compounded by the fact that my daughter was sick, and I had set the password during this particularly stressful time. website l i n k : : h t t p s : / / d i g i t a l t e c h g u a r d . c o m With sleepless nights and constant worry weighing on my mind, the password I had chosen became a distant memory, lost in the whirlwind of my chaotic life. Desperate for help, I turned to Digital Tech Guard Recovery. I knew I needed expert assistance to get back into my wallet, but I also felt embarrassed about my situation. telegram +56 997 059 700 When I called them, their compassionate team quickly put me at ease. They listened patiently as I explained my predicament and the stress I had been under. Their understanding made me feel less alone in my struggle, and I was grateful to find people who genuinely cared about my situation. As they began working on my case, I was amazed at their expertise. They guided me through the recovery process step by step, using their advanced tools and techniques to help me regain access to my wallet. Throughout this journey, their professionalism shone through, and I felt a sense of reassurance knowing I had a knowledgeable team on my side. Days felt like an eternity as I anxiously awaited updates, but I kept reminding myself that I was in good hands. Each passing day brought a mix of hope and anxiety, especially with my daughter still unwell. I found myself wishing I could just turn back time to remember that elusive password. Finally, the day arrived when I received the call I had been waiting for. Digital Tech Guard Recovery had successfully restored my access to the wallet, and my $100,000 was safe! The relief that washed over me was indescribable. I felt an overwhelming sense of gratitude toward the team who had worked tirelessly to resolve my issue. This experience taught me a valuable lesson about the importance of writing down passwords (safely) and not letting stress dictate my financial decisions. Now, I keep my passwords organized and securely stored, ensuring that I never find myself locked out again. And as for my daughter, she’s on the mend now, reminding me to focus on what truly matters in life. -
Trusted Locksmith Services by Local Locksmiths
When it comes to securing your property and ensuring that you can access your home, business, or vehicle without stress, having a reliable locksmith on hand is crucial. At Local Locksmiths, we provide professional, fast, and affordable locksmith services in Hallandale Beach, FL, and the surrounding areas. Whether you need help in an emergency or are looking to upgrade your security systems, our expert team is here to assist you.
Your Go To Locksmith Experts
Located at 1000 NE 12th Ave, Hallandale Beach, FL 33009, Local Locksmiths is committed to delivering high quality locksmith services for residential, commercial, and automotive needs. Our experienced technicians are well equipped to handle a wide variety of services with precision and care. We understand how important it is to feel safe and secure, and our goal is to make sure you can trust us with your locksmith needs.
Comprehensive Locksmith Services
Local Locksmiths offers a wide range of locksmith services designed to meet the diverse needs of our clients. Whether you're locked out of your home or need new locks installed at your business, our skilled technicians have got you covered.
Residential Locksmith Services
We offer lockout assistance, rekeying services, lock replacements, and home security upgrades. Protecting your family and belongings is our priority, and we provide solutions to ensure your home remains secure at all times.
Commercial Locksmith Services
For business owners, we offer high security lock systems, master key systems, keyless entry installations, and access control solutions to help you maintain a secure and efficient environment. Our team can handle the specific needs of your business, ensuring that your property and assets are well protected.
Automotive Locksmith Services
Locking yourself out of your car or losing your keys can be a frustrating experience. Local Locksmiths offers automotive locksmith services, including car key replacements, transponder key programming, and ignition repairs, so you can get back on the road quickly.
Emergency Locksmith Services
Lock and key issues can occur at any time, and that’s why we offer 24/7 emergency locksmith services. Whether you're locked out of your home, office, or car, our team is ready to respond quickly and get you the help you need, no matter the time of day or night.
Why Choose Local Locksmiths?
Experienced and Professional Technicians
At Local Locksmiths, we only employ fully trained and experienced locksmiths who are equipped with the knowledge and tools necessary to complete every job to the highest standard. No job is too big or too small for our team.
Fast and Reliable Service
We understand the urgency of lock and key problems, which is why we prioritize fast and efficient service. Our locksmiths respond quickly to emergencies, and we always aim to resolve your issue on the spot.
Affordable and Transparent Pricing
When you choose Local Locksmiths, you can expect competitive prices and no hidden fees. We provide upfront quotes and ensure that our pricing is clear and fair.
Contact Local Locksmiths Today
Whether you're in need of urgent assistance or just want to ensure that your property is secure, Local Locksmiths is here to help. Contact us at +1 754-551-1841 to speak with a friendly representative, or visit our office at 1000 NE 12th Ave, Hallandale Beach, FL 33009.
Trust Local Locksmiths for all your locksmith needs your security is our priority!2 -
BEST CRYPTOCURRECY RECOVERY COMPANY / EXPERT - GO TO DIGITAL TECH GUARD RECOVERY
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Www @ digital tech guard . com
Between tournaments, I'd mined $330,000 worth of Bitcoins, building capital quietly over the vocation. It wasn't even a side venture. It was the fall- back for the future, something upon which one could fall back when the vocation eventually dried up. But all this nearly disappeared one evening.I turned the rig like every ordinary day, ready to grind some games, only to discover the bright red screen. My computer became inaccessible, and all the files were all encrypted. My heart sank. They were demanding the ransom through the medium of Bitcoin and warned them about deleting all the data unless I paid them the ransom. But the worse is? My $330,000-worth-of-wallet, all held up the very same computer.
I felt like being checkmated. I did know online games could turn ugly, this one being one notch higher. For days, panic mode for me. I could not make up my mind about whether I dreaded the loss of the Bitcoin or the thought some guy behind the screen has bested me.
That was when one of the players from the opponent side approached me unexpectedly. We'd met earlier during competitions, but the player sent one message containing some advice that turned the situation around for the best. He informed me about Digital Tech Guard Recovery, where he said they were the best when it came to stolen wallets and cyberattacks. I contacted them the following day. From the start, the experience felt different. They did not explain things using complicated tech mumbo for the sole purpose of bewildering me. They broke all this down for me so that I could understand the process. My issue went over to their security experts, and they were available around the clock trying to break the encryption without draining my wallet.
Ten days later, the wallet lay open. All $330,000 were present, not crumpled. My jaw dropped. To make it through the final round after being one shot from being gone felt like winning.
The best part is not only did they recover the money, but also educated you about anti-phishing, protected wallets for the future, and even gave advice about keeping the gaming account secure. Digital Tech Guard Recovery did not only recover the Bitcoin for you; they also ensured you will not fall for the same scum again. GG, scum.1 -
Living in Los Angeles, California for the past five years has been a journey of hard work and dedication. My primary goal was to provide a better future for my family. I worked tirelessly, saving every penny to ensure we had the financial security we deserved. My dream was to build a stable life for my wife and children, and I invested in various assets, including a digital wallet for trading and savings. Little did I know, disaster was looming just around the corner .One fateful day, a devastating fire broke out in our area. While I was at work, my wife and children were visiting their grandmother in Houston, so they were safe from the immediate danger. Unfortunately, the fire quickly spread, and by the time it was under control, our home had been completely destroyed. Everything we owned, our furniture, personal belongings, and treasured memories was reduced to ashes. I was devastated, but grateful that my family was safe. However, as I returned to Los Angeles to deal with the aftermath, I discovered something even more distressing: my computer, along with the physical notebook where I had written down the passwords to my digital wallet, had gone missing in the fire. This was a huge blow, as I had stored crucial information related to my investments and digital assets on that computer. Without those passwords, I had no way of accessing my crypto funds, which were an essential part of the financial security I had worked so hard to build .Desperate to retrieve my funds, I boarded a flight to Houston to be with my family and also figure out how to recover my lost passwords. While on the plane, I searched for solutions, and after reading several online forums and testimonials, I came across CRYPTO RECOVERY SOLUTION . They specialized in recovering lost passwords for digital asset wallets and had a track record of helping people in similar situations .I as soon as I landed in Houston. The team immediately got to work, analyzing my case and using an advanced recovery method contacted CRYPTO RECOVERY SOLUTION to retrieve my lost wallet passwords. Within just three days, they successfully recovered access to my digital wallet and the funds I had invested. Their expertise in digital forensics and blockchain technology was evident, and I was amazed at how quickly they managed to resolve the issue .Thanks to CRYPTO RECOVERY SOLUTION , I was able to reclaim my assets and breathe a sigh of relief during such a challenging time. Their professionalism and commitment to helping individuals like me restored not only my financial stability but also my faith in the possibility of recovery, even after a devastating loss. I am forever grateful for their assistance.
WhatsApp number: +1 (332) 233‑2121 1
1 -
Recuva Hacker Solutions — A Trusted Partner in Bitcoin Recovery
In the ever-evolving world of cryptocurrency, losing access to your Bitcoin wallet can be a nightmare. Whether it’s due to forgotten passwords, hardware failures, or misplaced private keys, the inability to access your digital assets can be incredibly stressful. Fortunately, there are specialized services dedicated to helping you recover your lost or inaccessible Bitcoin wallets. Among these, Recuva Hacker Solutions (RHS) has emerged as a trusted leader in the field of crypto asset recovery. Since 2017, Recuva Hacker Solutions has been providing top-tier recovery services, earning a reputation as the go-to solution for individuals and businesses alike.
In this article, we’ll explore the key features that make Recuva Hacker Solutions the best choice for Bitcoin wallet recovery, while also highlighting their commitment to security, usability, and customer support.
Why Choose Recuva Hacker Solutions for Bitcoin Wallet Recovery?
1. Proven Track Record Since 2017
Recuva Hacker Solutions has been a trusted name in the crypto recovery industry since 2017. With years of experience, they have successfully helped countless clients regain access to their lost or inaccessible Bitcoin wallets. Their expertise spans a wide range of recovery scenarios, including forgotten passwords, corrupted hardware wallets, and lost private keys.
2. Advanced Recovery Tools and Techniques
Recuva Hacker Solutions employs state-of-the-art tools and techniques to ensure the highest success rate in wallet recovery. Their team of skilled professionals uses advanced algorithms and forensic methods to recover lost data, making them one of the most reliable recovery services in the industry.
3. Unmatched Security Measures
Security is a top priority for Recuva Hacker Solutions. They understand the sensitive nature of crypto assets and ensure that all recovery processes are conducted with the utmost confidentiality and security. Their protocols are designed to protect your data and assets throughout the recovery process.
4. User-Friendly and Accessible
One of the standout features of Recuva Hacker Solutions is their commitment to usability. Their recovery process is straightforward and user-friendly, ensuring that even those with limited technical knowledge can navigate the service with ease. Additionally, their customer support team is available to assist you at every step.
5. Comprehensive Customer Support
Recuva Hacker Solutions takes pride in offering exceptional customer support. Whether you have questions about the recovery process or need assistance with a specific issue, their team is just a message or call away. They offer multiple communication channels, including email and WhatsApp, to ensure you can reach them conveniently.
How to Contact Recuva Hacker Solutions
If you’re looking to recover your lost Bitcoin wallet, Recuva Hacker Solutions is here to help. You can reach out to them through the following channels:
Website: https : / / recuvahacksolution . pro
Email: recuvahackersolutions @ recuva . co . site
WhatsApp: +1 [3]15 [756] [1228
Their team is available to provide personalized assistance and guide you through the recovery process.
Why Recuva Hacker Solutions is the Best Crypto Recovery Company
Recuva Hacker Solutions has consistently proven itself as a leader in the crypto recovery space. Their combination of advanced technology, experienced professionals, and customer-centric approach sets them apart from the competition. Whether you’re an individual investor or a business, you can trust Recuva Hacker Solutions to help you regain access to your valuable crypto assets. 3
3 -
I received a prompt and professional response within a single business day of contacting DUNE NECTAR WEB EXPERT. This swift action, in stark contrast to the frustrating delays I had previously encountered, immediately instilled confidence. Their expertise in cybersecurity, particularly within the cryptocurrency domain, is evident in their comprehensive approach. They deeply understand blockchain technology, cryptocurrency protocols, and the intricate methods fraudsters employ. Furthermore, their reputation for integrity and skill is well-established within the industry. Numerous testimonials and case studies highlight their success in recovering stolen digital assets for victims of various cryptocurrency scams. Their dedication to assisting victims is not merely a marketing strategy; it is a core principle guiding their operations. The organization's commitment to ethical practices and client confidentiality further enhances its credibility. Their professional and compassionate approach, characterized by clear communication and regular updates, provided much-needed reassurance during a stressful period. The successful recovery of a significant portion of my stolen assets is a testament to their exceptional abilities and unwavering dedication to their clients. In conclusion, DUNE NECTAR WEB EXPERT offers a vital service in combating the pervasive issue of cryptocurrency fraud, providing a beacon of hope for victims seeking to reclaim their lost assets and regain a sense of security in the digital landscape. Consult DUNE NECTAR WEB EXPERT, as they are worthy and reliable professional hackers your money will count for when you hire them. E-mail (Support @ Dunenectarwebexpert . Com ) Telegram (@Dunenectarwebexpert )
 1
1 -
As cryptocurrency continues to reshape global finance, safeguarding Bitcoin and other crypto wallets is more important than ever. Unfortunately, wallet access issues—whether due to lost passwords, forgotten seed phrases, or even hacking incidents—are a common challenge for Bitcoin owners. Century Web Recovery, trusted since 2017, has emerged as a reputable resource for those seeking to regain access to their cryptocurrency wallets.
What is Bitcoin Wallet Recovery?
Bitcoin wallet recovery is the process of retrieving access to a Bitcoin wallet when the user is locked out. Wallet access issues can occur for various reasons, such as lost private keys, forgotten passwords, or corrupted wallet files. For those who’ve lost access, reputable recovery services can be an invaluable asset, helping them safely regain control of their funds.
Century Web Recovery offers specialized recovery services that cover a broad range of wallet types and access issues, providing the expertise needed to retrieve lost assets and restore access to cryptocurrency wallets.
Why Wallet Recovery Services Matter
Without access to your wallet, Bitcoin holdings can become permanently inaccessible. The decentralized nature of Bitcoin means there’s no central authority or “forgot password” feature that can restore access. This gap has led to a high demand for trustworthy wallet recovery services like Century Web Recovery, which uses a combination of technical expertise and proprietary tools to assist clients.
Century Web Recovery: Trusted Bitcoin Wallet Recovery Since 2017
Century Web Recovery has built a reputation as a reliable and secure recovery service provider since its establishment in 2017. Their team is composed of experienced blockchain analysts and cybersecurity experts who specialize in recovering wallet access in cases of forgotten passwords, corrupted files, or lost keys. Clients seeking to regain access to Bitcoin wallets can learn more about Century Web Recovery can help by contacting them through the details provided below.
Century Web Recovery Approaches Wallet Recovery
Initial Consultation and Assessment
Century Web Recovery begins with a thorough consultation, understanding the client’s situation and the specific wallet issue. This assessment allows the team to determine the best recovery strategy.
Technical Recovery Process
Century Web uses advanced recovery tools and techniques tailored to different wallet types, whether software, hardware, or paper-based. By leveraging cryptographic methods and advanced decryption software, the team can restore access to wallets securely.
Ensuring Client Security and Confidentiality
Security and confidentiality are top priorities. Century Web Recovery applies secure handling protocols throughout the recovery process, ensuring that clients’ information and assets remain protected.
Recovery Completion and Client Education
Upon successful recovery, Century Web provides clients with guidance on how to safeguard their wallets and private keys to avoid future access issues. This education reinforces wallet security and fosters long-term peace of mind.
Why Choose Century Web Recovery?
Not only does Century Web Recovery have a strong track record of successful recoveries, but it also offers an upfront pricing model to keep costs transparent. For clients who are locked out of their wallets, the technical capabilities and secure approach Century Web offers make it a leading choice in the crypto recovery space.
Contact Century Web Recovery
To learn more or initiate the recovery process, clients can reach out to Century Web Recovery. If you’re locked out of your Bitcoin wallet, now is the time to restore access and regain control of your digital assets with a company that’s trusted since 2017. You can reach out to us by searching us on google century web recovery and get all our contact details.1 -
USDT RECOVERY SERVICE: WEB BAILIFF CONTRACTOR EXPERIENCE
It was an ordinary Tuesday. I was keeping an eye on my Bybit portfolio when an email showed up that looked like a formal notice from the exchange regarding suspicious behavior. I didn't hesitate; I clicked the link and entered my credentials. When I hit submit, a sense of horror befell me. Within minutes, my Bitcoin wallet was drained. Losing 3.2 BTC, worth nearly $200,000 at the time, wasn't just monetary. It was a personal trust issue. I couldn't fathom that I had been phishing-scammed. I spent days scouring forums, contacting Bybit customer support, and even filing a report with the police. But the responses were disappointing and repetitive. Crypto withdrawals can't be reversed. Scam victims seldom see their money back. The frustration was overwhelming. I barely slept. I continuously replayed the moment in my head repeatedly. Why did I click on the link? Why didn't I double-check it? The frustration and guilt ate away at me. Friends tried to be helpful, but many didn't get the emotional and financial weight of what had transpired. I had always taken security precautions carefully. But in a moment of distraction, all was lost Weeks later, trawling Reddit threads on crypto cons, I found some mention of Web Bailiff Contractor. I was suspicious at first. It sounded too good to be true. But the comments looked genuine, and I was desperate. I went ahead and got in touch with them. They were speedy, professional, and surprisingly sympathetic. They made no promises of miracles. Instead, they explained their procedure: following blockchain transactions, identifying potential exchange cash-outs, and working with legal and crypto groups to freeze and recover funds.I gave them all I had wallet addresses, transaction history, screenshots and waited. A few days later, I got an email that left me speechless. They had been able to track and recover all my stolen Bitcoin.I couldn't believe it. After being told over and over again that the money was gone forever, here it was, back in my pocket. It was waking up from a nightmare. Web Bailiff Contractor did not just get my money back. They got my sense of security, my trust, and my peace of mind back too.I am writing about my experience now in case someone else out there is feeling the same panic and desperation that I once felt. There is hope. And every now and then, there is a second chance.2 -
LEARN HOW TO GET YOUR MONEY BACK FROM A FAKE INVESTMENT PLATFORM / VISIT TRUST GEEKS HACK EXPERT
TRUST GEEKS HACK EXPERT is a lifesaver! What started as a routine software update quickly turned into a nightmare that took me to the brink of financial ruin. A glitch in the updating process somehow locked me out of my Bitcoin wallet, which held $250,000. It was a significant investment I had worked hard to amass over several years, and it represented my savings, my future, and my peace of mind. The panic that followed was both instant and overwhelming. I desperately looked to recover my recovery phrase, only to realize it had been miss-printed when I originally wrote it down—a mistake I never thought would have any ramification until that exact moment. Each failed attempt at unlocking my wallet tightened the grip of anxiety on me. I was helpless, watching what appeared to be my entire financial security get further and further away. Despair drove me to search frantically for a lifeline. That's when I found TRUST GEEKS HACK EXPERT via web w w w: //
trust geeks hack expert. c o m /. I was wary at first—this was my life savings, after all, and I was well aware that the digital asset recovery business could be full of scams and false hope. But the glowing testimonials and success stories offered promise. I took the risk. I knew from the first conversation I had done the right thing. Their personnel were polite, sympathetic, and patient. They heard every aspect of my issue and assured me that I was not a lost cause. Its confidence was a lifeline. They explained the process of recovery in terms that I could understand, defining every technical step along the way and keeping me informed at each stage. I was most amazed at their accuracy and speed. They quickly diagnosed the issue and applied advanced recovery techniques to regain access to my wallet. Within days, my $250,000 was restored to me—intact and secure. The weight that was taken off my chest at that moment cannot be put into words. TRUST GEEKS HACK EXPERT not only restored my investment but also restored my faith in professional services. Their professionalism, honesty, and empathy made all the difference. I just can't thank them enough. If you are experiencing the same trauma, don't wait—contact TRUST GEEKS HACK EXPERT They are no less than saviors. Email: Trust geeks hack expert @ fast service . c o m 3
3 -
HOW TO HIRE A GENUINE BITCOIN RECOVERY COMPANY HIRE ADWARE RECOVERY SPECIALIST
I have been into the latest tech hacks that promise to make life easier, so when a TikTok video highlighted in front of my eyes told me about a 'foolproof' way to enhance crypto security using a rather unknown wallet app, I was intrigued. I saw so many people in the comments saying it was seamless and super secure, I thought, why not give this a go? After all, security is everything in crypto.
At first, everything was going perfect: intuitive interface and all; I had even managed to transfer my $150,000 worth of Bitcoin into it without a problem. But that's where my luck ran out. A week later, an automatic app update rolled in, and my login credentials were there no more-completely wiped. No password worked, no seed phrase was recognized, and my funds were trapped in a digital void. WhatsApp info:+12 723 328 343
Panic set in immediately. I scoured the forums, tech blogs, and the app's support page; nothing worked. The same TikTok video that convinced me to download the app never mentioned a word about how to recover an account that became lost. Annoyed and desperate for help, I returned to the comments on TikTok in search of someone having experienced the very same problem. That is where I saw multiple users recommending ADWARE RECOVERY SPECIALIST as the go-to solution for crypto wallet mishaps.
Skeptical but out of options, I decided to reach out. From the very first interaction, his team reassured me that I was not the first person to fall for a "too-good-to-be-true" tech hack. The confidence and professionalism put me at ease, and they got to work quickly. The process was meticulous, methodical, and above all, effective.
Of course, within several days, they cracked the issue and restored access to me. To see my $150,000 back in my control was simply indescribable. Moreover, beyond this recovery itself, they gave me something even much more valuable-knowledge. First, they have explained the risk of unverified wallet apps: how automatic update sometimes compromises credentials stored in their memory. Secondly, they assisted in implementing a more reliable security system so as not to allow the same mistake to happen with me again.
Now, I take TikTok hacks with a grain of salt, but when it comes to ADWARE RECOVERY SPECIALIST, They're the real deal. If you ever find yourself in a crypto nightmare, don't hesitate to reach out to them. They don't just recover your funds-they restore your peace of mind.1 -
As the senior teacher at Greenfield Academy, I wanted to share our ordeal with TECH CYBER FORCE RECOVERY after our school was targeted by a malicious virus attack that withdrew a significant amount of money from our bank account. A third-party virus infiltrated our system and accessed our financial accounts, resulting in a USD 50,000 withdrawal. This attack left us in a state of shock and panic, as it posed a serious threat to our school's financial stability. Upon realizing what had happened, we immediately contacted TECH CYBER FORCE RECOVERY for help. Their team responded promptly and began investigating the situation. They worked tirelessly to track down the virus, analyze its behavior, and understand how it had bypassed our security measures. Most importantly, they focused on recovering the funds that had been stolen from our bank account. Thanks to TECH CYBER FORCE RECOVERY's quick and expert intervention, they were able to successfully recover all the funds that had been withdrawn. Their team worked closely with our bank and utilized advanced recovery methods to ensure the full amount was returned to our account. We were incredibly relieved to see the stolen funds restored, and their efforts prevented any further financial loss. I am incredibly grateful for TECH CYBER FORCE RECOVERY's professionalism, expertise, and swift action in helping us recover the stolen funds. Their team not only managed to undo the damage caused by the virus but also ensured that our financial security was restored. I highly recommend their services to any organization dealing with similar cyberattacks, as their team truly went above and beyond to resolve the issue and protect our assets.
CONTACTING THEM TECH CYBER FORCE RECOVERY
EMAIL. Tech cybers force recovery @ cyber services . com3 -
BITCOIN RECOVERY EXPERT HIRE CRYPTO RECOVERY SOLUTION /
Living in Los Angeles, California for the past five years has been a journey of hard work and dedication. My primary goal was to provide a better future for my family. I worked tirelessly, saving every penny to ensure we had the financial security we deserved. My dream was to build a stable life for my wife and children, and I invested in various assets, including a digital wallet for trading and savings. Little did I know, disaster was looming just around the corner. One fateful day, a devastating fire broke out in our area. While I was at work, my wife and children were visiting their grandmother in Houston, so they were safe from the immediate danger. Unfortunately, the fire quickly spread, and by the time it was under control, our home had been completely destroyed. Everything we owned, our furniture, personal belongings, and treasured memories was reduced to ashes. I was devastated, but grateful that my family was safe. However, as I returned to Los Angeles to deal with the aftermath, I discovered something even more distressing: my computer, along with the physical notebook where I had written down the passwords to my digital wallet, had gone missing in the fire. This was a huge blow, as I had stored crucial information related to my investments and digital assets on that computer. Without those passwords, I had no way of accessing my crypto funds, which were an essential part of the financial security I had worked so hard to build. Desperate to retrieve my funds, I boarded a flight to Houston to be with my family and also figure out how to recover my lost passwords. While on the plane, I searched for solutions, and after reading several online forums and testimonials, I came across CRYPTO RECOVERY SOLUTION . They specialized in recovering lost passwords for digital asset wallets and had a track record of helping people in similar situations. I as soon as I landed in Houston. The team immediately got to work, analyzing my case and using an advanced recovery method contacted CRYPTO RECOVERY SOLUTION to retrieve my lost wallet passwords. Within just three days, they successfully recovered access to my digital wallet and the funds I had invested. Their expertise in digital forensics and blockchain technology was evident, and I was amazed at how quickly they managed to resolve the issue. Thanks to CRYPTO RECOVERY SOLUTION , I was able to reclaim my assets and breathe a sigh of relief during such a challenging time. Their professionalism and commitment to helping individuals like me restored not only my financial stability but also my faith in the possibility of recovery, even after a devastating loss. I am forever grateful for their assistance.
WhatsApp number: +1 (332) 233‑2121 1
1 -
They Helped Me When My Digital Assets Disappeared" Hack Savvy Tech
On Sunday, I reached out to Hack Savvy Tech, desperate for help after losing all my savings 200,000 Ethereum due to a scam. It all started when I received a message on Twitter (X) from what seemed like official blockchain support. The account looked genuine, and they claimed they could assist me with an issue I was facing. Trusting them, I shared my wallet details, never once suspecting that I was talking to fraudsters. They quickly gained access to my wallet and drained all my Ethereum. I was left in complete shock, feeling foolish and heartbroken, as this was all my life savings, the future I had been relying on.I couldn’t believe what had just happened. The feeling of helplessness and despair was overwhelming, and I couldn’t comprehend how easily I had been duped. I was devastated, thinking I had lost everything and there was no way to recover it. In my panic, I began searching online for any possible solutions. That’s when I stumbled upon a comment on Quora recommending Hack Savvy Tech. Someone had shared their success story about recovering stolen funds, and reading it gave me a glimmer of hope.Without wasting any time, I reached out to Hack Savvy Tech and explained my situation. The team was incredibly understanding and reassured me that they could help me recover my lost Ethereum. I was still shaken, but they immediately got to work. On that very Sunday, they launched the recovery program, and within a day, they had already identified the culprits. The efficiency of their work was astonishing. Not only did they track down the scammers, but they also managed to recover all of my stolen Ethereum, returning it to my wallet.The relief I felt when I saw the funds back in my account was indescribable. I couldn’t believe that it was possible to recover what seemed like an irretrievable loss. I owe it all to the professionalism and expertise of the team at Hack Savvy Tech. They not only helped me reclaim my stolen funds but also provided valuable advice on how to protect myself from future scams.If you’ve fallen victim to any form of online scam or cryptocurrency theft, I highly recommend contacting Hack Savvy Tech . They are true experts in their field and can help you recover lost funds. I hope my experience helps others who find themselves in a similar situation. Stay vigilant and always be cautious with your online security.
mail: contactus @ hacksavvytechnology . com
Website: https : // hacksavvytechrecovery. com
Whatsapp : +799982950381 -
When you’re in need of reliable, fast, and professional locksmith services in Fort Lauderdale, Local Locksmiths is your go to provider. With years of experience serving the Fort Lauderdale area, we understand the importance of security and ensuring that your property, whether it's your home, office, or vehicle, is safe and secure. Our team is committed to offering top notch locksmith services at affordable prices, making us the most trusted locksmith in Fort Lauderdale.
Why Choose Local Locksmiths?
At Local Locksmiths, we pride ourselves on our customer first approach. Here’s why we stand out from other locksmith services:
Fast Response Time: Lockouts and security issues can happen at any time. Our expert locksmiths are always ready to respond quickly to any emergency. Whether it’s a car lockout or a home lock problem, we are here to help with a fast, reliable solution.
Comprehensive Services: We offer a wide range of locksmith services to meet your needs. From residential to commercial and automotive locksmith services, we handle it all. Whether you need a lock replacement, rekeying services, or a key duplication, we have the expertise to get the job done right.
Expert Technicians: Our team of licensed and trained locksmiths has the skills and knowledge to solve any lock related issue. They are equipped with the latest tools and techniques to provide efficient and effective solutions.
Affordable Pricing: We understand that security services can be an unexpected expense, which is why we offer competitive and transparent pricing. You can count on Local Locksmiths to deliver high quality services without breaking the bank.
Emergency Locksmith Services: Locked out of your car or home? We offer 24/7 emergency locksmith services in Fort Lauderdale. Day or night, our locksmiths are always available to assist you with your urgent lock and key needs.
Our Services
Residential Locksmith: From installing new locks to rekeying your home, we ensure your property is protected with the best security measures.
Commercial Locksmith: We provide a variety of services for businesses, including master key systems, access control systems, and high security lock installation.
Automotive Locksmith: Locked out of your car or lost your keys? Our automotive locksmith services cover all makes and models, helping you get back on the road quickly.
Emergency Services: When you’re in a pinch, you can rely on us for 24/7 emergency lockout services and other urgent locksmith needs.
Serving Fort Lauderdale and Beyond
While our business is based at 1000 NE 12th Ave, Hallandale Beach, FL, we proudly serve Fort Lauderdale and the surrounding areas. Our proximity to Fort Lauderdale ensures we can respond to your locksmith needs quickly and efficiently. We’re just a call away at +17545511841, ready to provide you with fast, professional service.
Contact Local Locksmiths Today
Don’t let lock issues cause you unnecessary stress. Whether you need a simple key replacement or emergency locksmith services, Local Locksmiths is here to help. With our expertise, commitment to customer satisfaction, and affordable pricing, we’re your trusted locksmiths in Fort Lauderdale. Contact us now at +17545511841 for all your locksmith needs.
For reliable, fast, and professional locksmith services, choose Local Locksmiths your trusted partner in Fort Lauderdale.2 -
RECOVER YOUR LOST CRYPTOCURRENCY: BEST EXPERTS TO HELP YOU RECLAIM YOUR FUNDS WITH SPARTAN TECH GROUP RETRIEVAL
A few months ago, I ran into a major issue that nearly cost me everything. I had been using my computer to trade cryptocurrency for some time, relying on my digital wallet for every transaction. One day, after an unexpected system crash, I realized that something was terribly wrong. My computer, which had always been reliable, was infected with a virus that completely compromised my trading wallet. When I tried to access my account, I was logged out and couldn’t get back in. Panic set in as I realized I had no idea how to regain access, and I feared I might have lost everything I had worked so hard for. In my frantic search for a solution, I reached out to a close friend who was knowledgeable about technology and had experience with crypto trading. After explaining my situation, she immediately suggested I reach out to a team called SPARTAN TECH GROUP RETRIEVAL Then contact them on WhatsApp:+1 (971) 4 8 7 -3 5 3 8 OR Telegram:+1 (581) 2 8 6 - 8 0 9 2. She mentioned that she had read several accounts on Quora from people who had faced similar issues and had successfully recovered their funds with the help of SPARTAN TECH GROUP RETRIEVAL. I was skeptical at first, unsure whether this was just another online service that made grand promises but couldn’t deliver. But after learning more about SPARTAN TECH GROUP RETRIEVAL’s reputation and reading more testimonials from individuals who had been in my position, I decided to give them a try. I contacted them, explained my situation, and was quickly put in touch with one of their specialists. The team at SPARTAN TECH GROUP RETRIEVAL immediately set to work, analyzing the situation with a calm and professional approach. They explained that the virus had likely been a targeted attack, with the purpose of stealing access to my crypto wallet. However, they reassured me that they had the tools and expertise to track the source of the attack and restore my access. Their team used advanced forensic methods, combining blockchain analysis, data recovery techniques, and a deep understanding of cryptocurrency security protocols to retrieve my account. Within a short period, SPARTAN TECH GROUP RETRIEVAL successfully regained access to my wallet and helped secure it from future threats. Not only did they recover my account, but they also implemented enhanced security measures to prevent further breaches. I was absolutely amazed by their professionalism, technical expertise, and how quickly they acted. What impressed me most was their commitment to ensuring that I understood the process every step of the way. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to recover not just my funds but my peace of mind. I am now more confident in my trading, knowing that if anything goes wrong, I have a trustworthy team to rely on.
CONTACT INFO ABOUT THE COMPANY:
Email: spartantech (@) c y b e r s e r v i c e s . c o m 1
1 -
Guaranteed Garage Doors: Your Trusted Garage Door Expert in Killeen, TX
At Guaranteed Garage Doors, we are dedicated to providing high-quality garage door services to both residential and commercial customers in Killeen, TX, and surrounding areas. Whether you're in need of commercial garage door repair, residential garage door repair, or seeking an accurate garage door repair estimate, our team of experienced technicians is here to deliver fast and reliable solutions. We also specialize in garage door replacement and can help you determine the garage door replacement cost. As your local garage door expert, we offer everything from simple repairs to complete replacements, ensuring your garage door system is always in excellent condition.
Comprehensive Garage Door Services for Residential and Commercial Needs
At Guaranteed Garage Doors, we understand that your garage door is an essential part of your property’s security and functionality. That’s why we offer a wide range of services, including commercial garage door repair, residential garage door repair, and more. Whether you're facing an emergency breakdown or need routine maintenance, we are here to ensure your garage door operates safely and efficiently.
Commercial Garage Door Repair
For businesses, a malfunctioning garage door can disrupt operations and pose a security risk. Commercial garage door repair requires the expertise of professionals who understand the unique demands of high-use doors. At Guaranteed Garage Doors, we specialize in repairing all types of commercial garage doors, from roll-up doors to sectional doors. Our team can quickly identify the issue and provide reliable repair services, minimizing downtime and ensuring your business can continue to run smoothly.
Residential Garage Door Repair
Your home’s garage door is crucial for the safety and convenience of your family. If your garage door is not functioning correctly, it can affect your daily routine. We provide residential garage door repair services that cover everything from broken springs and cables to malfunctioning openers and tracks. Whether your door is making unusual noises or won’t open at all, Guaranteed Garage Doors will provide a thorough inspection and fast repairs to restore your garage door to optimal working condition.
Garage Door Repair Estimates
Before committing to any repair work, it’s essential to know the cost of the services required. At Guaranteed Garage Doors, we provide garage door repair estimates that are transparent and affordable. Our team will assess the problem, explain the necessary repairs, and give you an honest, upfront estimate so you can make an informed decision. We take pride in offering competitive pricing without compromising on the quality of our services, ensuring you receive the best value for your money.
Garage Door Replacement Cost
If your garage door is beyond repair or you're simply looking to upgrade, it’s important to understand the garage door replacement cost. The price can vary depending on factors such as the type of door, materials, and features you choose. At Guaranteed Garage Doors, we help you select a door that fits your budget and meets your needs. Our expert team will guide you through the entire process, from providing a detailed estimate for replacement to installation, ensuring a seamless experience. Whether you’re replacing a single panel or the entire system, we ensure that your new garage door will enhance your property’s security, curb appeal, and energy efficiency.
Garage Door Expert
As your local garage door expert, Guaranteed Garage Doors is committed to delivering exceptional service and solutions for all your garage door needs. Our team has extensive experience in repairing, installing, and maintaining all types of garage doors, both residential and commercial. We use only the highest-quality parts and materials to ensure your garage door functions reliably and safely. When you choose us as your garage door provider, you can rest assured that you are working with professionals who take pride in delivering the best service possible.
Why Choose Guaranteed Garage Doors?
Experienced Technicians: Our team is highly trained and experienced in handling all types of garage door issues, from minor repairs to major replacements.
Transparent Estimates: We provide clear garage door repair estimates, so you know exactly what to expect before any work begins.
Residential and Commercial Services: Whether you're a homeowner or business owner, we offer reliable services tailored to your specific needs.
Affordable Pricing: We offer competitive pricing for all our services, including garage door replacement cost, ensuring you get the best value for your investment.
Customer Satisfaction Guaranteed: At Guaranteed Garage Doors, your satisfaction is our priority. We work hard to exceed your expectations and ensure your garage door is functioning perfectly.1 -
How to Withdraw on Bhalo88 💰 | A Complete Guide
Withdrawing money securely and efficiently is crucial for any online gaming or betting platform. If you’re looking for an easy way to withdraw your winnings, this guide on how to withdraw on Bhalo88 will walk you through each step. Moreover, we will discuss secure mobile banking in Bangladesh like bKash, Nagad, Upay, and Rocket for fast transactions.
Why Choose Bhalo88 for Withdrawals? 🚀
Bhalo88 offers a user-friendly and secure withdrawal process. Multiple payment options ensure seamless transactions. With instant processing, you can receive your winnings directly to your mobile wallet or bank account. Whether you’re using bKash, Nagad, Rocket, or Upay, Bhalo88 ensures a hassle-free experience.
Step-by-Step Guide: How to Withdraw on Bhalo88 📝
Step 1: Access the Security Center
To begin, log in to your Bhalo88 account and navigate to the Security Center.
Step 2: Click on “E-Wallet Binding”
This step ensures that your mobile banking details are securely linked to your Bhalo88 account.
Step 3: Select Withdrawal Method
Choose the method through which you want to withdraw your funds (bKash, Nagad, Rocket, or Upay).
Provide your full name as per your bank or wallet account.
Enter the mobile number where you wish to receive the money.
Input the number registered with your Bhalo88 account.
Click on Send and enter the OTP received on your number.
Set a new 6-digit transaction PIN for added security.
Step 4: Enter Withdrawal Amount
Specify the amount you want to withdraw.
Input your saved transaction PIN and click on withdraw.
Secure Mobile Banking Options in Bangladesh
When withdrawing on Bhalo88, you can use some of the most trusted and secure mobile banking services in Bangladesh. Let’s take a closer look at these options:
bKash: The Most Popular Mobile Banking
Fast and secure transactions
Available across Bangladesh
Instant withdrawal processing
Nagad: Trusted by Millions
Low transaction fees
High security and encryption
24/7 customer support
Rocket: Powered by Dutch-Bangla Bank
Direct bank integration
Safe and efficient transactions
Supports large withdrawals
Upay: The New and Reliable Choice
Competitive transaction fees
Instant mobile wallet transfers
High withdrawal limits
These services ensure safe and instant transactions, making them perfect choices for withdrawing on Bhalo88.
Tips for a Safe Withdrawal on Bhalo88 🛡️
Always double-check the number and account details before withdrawing.
Use a strong transaction PIN for added security.
Withdraw during banking hours for the fastest processing.
If you face issues, contact Bhalo88 customer support immediately.
Frequently Asked Questions (FAQs) 📊
1. How long does it take to withdraw on Bhalo88?
Most withdrawals are processed instantly. However, bank-related transactions may take up to 24 hours.
2. Is there a minimum withdrawal amount?
Yes, the minimum withdrawal amount depends on the selected payment method. Usually, it’s around 100 BDT.
3. Can I withdraw using a different mobile number?
No, the withdrawal must be made to the registered mobile number linked with your Bhalo88 account.
4. What should I do if my withdrawal fails?
Check your account balance, internet connection, and OTP entry. If the issue persists, contact Bhalo88 support.
Conclusion 🏆
Withdrawing money on Bhalo88 is quick, secure, and hassle-free when you follow the correct steps. By using bKash, Nagad, Rocket, or Upay, you can enjoy a smooth withdrawal experience. Moreover, ensure security measures are followed, and always double-check your details before processing any transaction.
Now that you know how to withdraw on Bhalo88, go ahead and enjoy your winning 1
1 -
ASSET RESCUE SPECIALIST - RECOVER LOST BITCOIN/USDT/CRYPTO/ETH/USDC
ASSET RESCUE SPECIALIST stands as the leading specialist in contract development dedicated to recovering stolen cryptocurrency. With a track record of assisting victims across the world, ASSET RESCUE SPECIALIST has successfully facilitated the retrieval of over $2 million worth of Bitcoins that were misappropriated by fraudulent investment platforms. Their standout achievement lies in their unique triangulation method, which has emerged as a game-changer in the field of cryptocurrency recovery.The problem of cryptocurrency theft is increasingly prevalent, with scam platforms continuously evolving their techniques to deceive unsuspecting investors. This makes it imperative for victims to seek effective solutions swiftly. ASSET RESCUE SPECIALIST offers a sophisticated approach to this issue, providing a beacon of hope for those who have fallen prey to such schemes.The core of ASSET RESCUE SPECIALIST success is their specialized triangulation method. This innovative approach involves a multi-step process that enables the precise tracking and recovery of stolen assets. By employing advanced technology and leveraging deep industry knowledge, they are able to pinpoint the location of misappropriated funds with a high degree of accuracy. This method has not only proven to be effective but has also set a new standard in the recovery of stolen cryptocurrency.For those who have been scammed or lost their cryptocurrencies, ASSET RESCUE SPECIALIST offers a structured process to initiate recovery. The first step involves opening a detailed case with their team. This is crucial, as it allows the recovery specialists to assess the situation thoroughly and devise a tailored strategy to recover the stolen funds. In particular, the ASSET RESCUE SPECIALIST approach is not just about recovering funds; it is about providing a sense of security and closure to victims. Their commitment to ensuring that every victim gets their money back is reflected in their meticulous work and proven results. With their expertise, they have established themselves as a trusted ally for those navigating the complex and often opaque world of cryptocurrency recovery.if you have been a victim of a cryptocurrency scam or have experienced a loss of funds, it is crucial to act immediately. ASSET RESCUE SPECIALIST offers a dependable and effective solution to recover your stolen assets. By initiating a case with their team, you take the first critical step towards reclaiming your stolen cryptocurrency and ensuring that justice is served.
Contact Email : assetrescuespecialist[@]qualityservice . com
WhatsApp No : +1 (579) 300 1389 3
3 -
Trusted Locksmith Services by Local Locksmiths
When it comes to securing your property and ensuring that you can access your home, business, or vehicle without stress, having a reliable locksmith on hand is crucial. At Local Locksmiths, we provide professional, fast, and affordable locksmith services in Hallandale Beach, FL, and the surrounding areas. Whether you need help in an emergency or are looking to upgrade your security systems, our expert team is here to assist you.
Your Go-To Locksmith Experts
Located at 1000 NE 12th Ave, Hallandale Beach, FL 33009, Local Locksmiths is committed to delivering high-quality locksmith services for residential, commercial, and automotive needs. Our experienced technicians are well-equipped to handle a wide variety of services with precision and care. We understand how important it is to feel safe and secure, and our goal is to make sure you can trust us with your locksmith needs.
Comprehensive Locksmith Services
Local Locksmiths offers a wide range of locksmith services designed to meet the diverse needs of our clients. Whether you're locked out of your home or need new locks installed at your business, our skilled technicians have got you covered.
Residential Locksmith Services
We offer lockout assistance, rekeying services, lock replacements, and home security upgrades. Protecting your family and belongings is our priority, and we provide solutions to ensure your home remains secure at all times.
Commercial Locksmith Services
For business owners, we offer high-security lock systems, master key systems, keyless entry installations, and access control solutions to help you maintain a secure and efficient environment. Our team can handle the specific needs of your business, ensuring that your property and assets are well-protected.
Automotive Locksmith Services
Locking yourself out of your car or losing your keys can be a frustrating experience. Local Locksmiths offers automotive locksmith services, including car key replacements, transponder key programming, and ignition repairs, so you can get back on the road quickly.
Emergency Locksmith Services
Lock and key issues can occur at any time, and that’s why we offer 24/7 emergency locksmith services. Whether you're locked out of your home, office, or car, our team is ready to respond quickly and get you the help you need, no matter the time of day or night.
Why Choose Local Locksmiths?
Experienced and Professional Technicians
At Local Locksmiths, we only employ fully trained and experienced locksmiths who are equipped with the knowledge and tools necessary to complete every job to the highest standard. No job is too big or too small for our team.
Fast and Reliable Service
We understand the urgency of lock and key problems, which is why we prioritize fast and efficient service. Our locksmiths respond quickly to emergencies, and we always aim to resolve your issue on the spot.
Affordable and Transparent Pricing
When you choose Local Locksmiths, you can expect competitive prices and no hidden fees. We provide upfront quotes and ensure that our pricing is clear and fair.
Contact Local Locksmiths Today
Whether you're in need of urgent assistance or just want to ensure that your property is secure, Local Locksmiths is here to help. Contact us at +1 754-551-1841 to speak with a friendly representative, or visit our office at 1000 NE 12th Ave, Hallandale Beach, FL 33009.
Trust Local Locksmiths for all your locksmith needs—your security is our priority!1 -
RECOVER YOUR BITCOIN WITH DIGITAL TECH GUARD RECOVERY EXPERT ASSISTANCE
I vividly remember the frustration I felt on a Sunday afternoon when I was struggling to regain control over my crypto wallet. At the time, I had a substantial balance over $68,000—and I was dealing with serious transaction issues. Despite multiple attempts, I couldn’t complete any transactions, and the situation seemed to worsen with each passing hour. As the day wore on, I grew more desperate, but I stubbornly resisted reaching out for professional help contact with WhatsApp: +1 (443) 859 - 2886 @ digital tech guard. com Telegram:@ digital tech guard recovery. com. I believed I could solve the problem myself or that contacting support would be a waste of time. Unfortunately, all my efforts to resolve the issue on my own came to nothing. The more time that passed, the more I realized my attempts were futile. The value of my assets in the wallet was at risk, and the frustration of not being able to access or transfer them grew unbearable. I tried reaching out to customer support for help, but each inquiry was met with a generic response or, worse, no response at all. The lack of communication only added to my sense of helplessness. By Sunday evening, I was at my wit’s end, and it was then that I finally accepted I needed help from someone else—my friend. Despite my initial resistance to involving a third party, my friend stepped in and contacted Digital Tech Guard Recovery on my behalf. At first, I remained hesitant. I had heard mixed things about third-party recovery services, and I was worried about compromising my wallet's security. But after my friend reassured me, I agreed to let them handle it. To my relief, the process went smoothly once I allowed Digital Tech Guard Recovery to get involved. I provided only the minimal information they requested, and within a short time, my access to the wallet was fully restored. All the transactions that had been stuck were processed, and my balance was intact. I’m incredibly thankful to Digital Tech Guard Recovery for their expertise and professionalism. If you ever find yourself in a similar situation, struggling to regain access to your crypto wallet, I highly recommend reaching out to them. Their help made all the difference for me, and I believe they can do the same for you. For their services, you can contact Digital Tech Guard Recovery directly. -
I Thought My Nest Egg Was Immobile Permanently! Overseas travel is glamorous until you are at 37,000 feet, trying to cope with different time zones, airport security queues, and dodgy Wi-Fi that cannot even open an email, never mind providing your future funding. I had stashed $890,000 of Bitcoin away as my retirement nest egg, a nest egg made of decades of hard work. That sense of security evaporated in thin air when I replaced my phone and forgot to update the two-factor authentication settings on my wallet.
Somewhere across the Atlantic, turbulence rattled the plane, but the real storm was the panic in my chest when I realized that I could not access my wallet. Tired and flustered, I arrived with the dread realization that my virtual fortune was now as out of reach as the stars in the sky. The frustration mounted as I hopscotched from airport to airport. Customer service droids, robot call centers, and half-baked solutions had me addressing vending machines instead of human beings. That was before a layover in Singapore where, bleary-eyed and clutching my third cup of coffee, I chanced upon a travel vlogger's YouTube video raving about Tech Cyber Force Recovery.
With nothing to lose, I called. From the first message itself, it was different. These were actual people, smart, caring, and willing to work around my insane schedule. They scheduled calls during my layovers and adjusted to the chaos of traveling overseas like pros.
Their engineers delved deep into my issue, analyzing time-stamped authentication records. It was as if watching a digital detective movie, minus the stakes: my future. For over 14 hair-on-end days, they weathered the 2FA bug like pilots navigating through turbulence. Then the message came: Access restored. All the Bitcoins were present. I almost cried into my airport ramen. That weight was lifted from my shoulders, and the feeling that all those years of careful planning weren't wasted, was indescribable.
telegram +1 561 726 36 97
WhatsApp +1 561 726 36 973

