Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "identity"
-
Why did the chicken cross the road?
Assembler Chicken: First, it builds the road ......
C Chicken: It crosses the road without looking both ways.
C++ Chicken: The chicken wouldn't have to cross the road, you' d simply refer to him on the other side.
COBOL Chicken: 0001-CHICKEN-CROSSING.
IF NO-MORE-VEHICLES
THEN PERFORM 0010-CROSS-THE-ROAD
VARYING STEPS FROM 1 BY 1 UNTIL
ON-THE-OTHER-SIDE
ELSE
GO TO 0001-CHICKEN-CROSSING
Cray Chicken: Crosses faster than any other chicken, but if you don't dip it in liquid nitrogen first, it arrives on the other side frazzled.
Delphi Chicken: The chicken is dragged across the road and dropped on the other side.
Gopher Chicken: Tried to run but got beaten by the Web chicken.
Intel Pentium Chicken: The chicken crossed 4.9999978 times.
Iomega Chicken: The chicken should have ' backed up' before crossing.
Java Chicken: If your road needs to be crossed by a chicken, then the server will download one to the other side. (Of course, those are chicklets.) See also WMI Monitor.
Linux Chicken: Don't you *dare* try to cross the road the same way we do!
Mac Chicken: No reasonable chicken owner would want a chicken to cross the road, so there's no way to tell it how to cross the road.
Newton Chicken: Can't cluck, can't fly, and can't lay eggs, but you can carry it across the road in your pocket.
OOP Chicken: It doesn't need to cross the road, it just sends a message.
OS/2 Chicken: It crossed the road in style years ago, but it was so quiet that nobody noticed.
Microsoft's Chicken: It's already on both sides of the road. What's more its just bought the road.
Windows 95 Chicken: You see different coloured feathers while it crosses, but when you cook it still tastes like........ chicken.
Quantum Logic Chicken: The chicken is distributed probabilistically on all sides of the road until you observe it on the side of your choice.
VB Chicken: USHighways! <TheRoad.cross> (aChicken)
XP Chicken Jumps out onto the road, turns right, and just keeps on running.
The Longhorn Chicken had an identity crisis and is now calling itself Vista.
The Vista Chicken dazzled itself with its own graphics.20 -
I tried DuckDuckGo like two years ago and my opinion was “meh, I don’t like the results”.
Yesterday @Root made it clear that the sole amount of data collected changes the whole perspective of tracking.
I went to shower thinking about that and as I was standing there enjoying warm water...
It hit me.
I liked google results and disliked DDG not because DDG was worse.
I liked google results because they were CRAFTED for ME to LIKE them. They exploited my confirmation bias, the strongest of all biases.
I took my other phone which is android, has a different sim that isn’t tied to my identity (don’t ask, this is Russia), was never connected to my WiFi and of course has no google account tied to it.
I tried googling stuff.
The results was just like what DDG gets you, the only difference was google amp were on top.
The fuck. One of the wokest moments ever.83 -
Crap.. got myself into a fight with someone in a bar.
Hospitalized, turns out that my knee is bruised and my nose is broken. For some reason the knee hurts much more than the nose though.. very weird.
Just noticed that some fucker there stole my keychain USB stick too. Couldn't care less about the USB stick itself, got tons of those at home and hard drive storage even more so (10TB) but the data on it was invaluable. It held on a LUKS-encrypted partition, my GPG keys, revocation certificates, server backups and everything. My entire digital identity pretty much.
I'm afraid that the thief might try to crack it. On the flip side, if it's just a common Windows user, plugging it in will prompt him to format it.. hopefully he'll do that.
What do you think.. take a leap with fate and see how strong LUKS really is or revoke all my keys and assume my servers' filesystems to be in the hands of some random person that I don't know?
Seriously though.. stealing a fucking flash drive, of what size.. 32GB? What the fuck is wrong with people?32 -
devRant is truly amazing, a social network where I don't have to give up on privacy by giving out my number to confirm that I am legit when I'd use something as a VPN to protect my identity (unlike twitter facebook and google)
Thanks for giving a fuck about privacy and not giving a fuck about my data11 -
These clowns make my blood boil.
fullStackClown: Hey I need some info on that specific color you want for this design
managerClowns: Yes it should look like this <<sends screenshot>>
fullStackClown: That is not a color, it is a screenshot
managerClowns: Yes it should look like this
fullStackClown: Do you know what hex code that is for that color? Can you ask the design team what color from our corporate identity they used?
managerClowns: Yes it should look like this
fullStackClown: Not helping... okay fine I used the eyedropper and I see the hex code is not used anywhere else in our app, so what color should I use?
managerClowns: Yes it should look like this
fullStackClown: ...20 -
10 years ago, I found a vulnerability in the connection between an insurer I was working for, and the network of databases of municipalities. I was only a hacker in so far as kids who watched Hak5 are considered hackers, so I always carried this laptop with a fake access point, package sniffer, wep crack, sslstrip, etc with me.
The vulnerabilities allowed me to register a new identity, for which I requested a passport.
Walking up to the town hall desk with two passports with different names, both mine, was pretty cool.
I did not do anything malicious, and was hired to fix the issues (wep encryption on insurers trusted wifi, and municipality postgres gave write access to all third parties)
For a few days I was the coolest kid in school though!2 -
Way to fucking go, Austria wants to push a law that forces online platforms (if possible around the globe) with more than 100k users to provide an accurate way to identify them.
"Name, surname and adress"
I just listened to an interview with a guy who is for that proposal. He said the platforms can just take the data directly from mobile providers, using the phone number. Also, even buying a prepaid sim-cards will require you to provide an identity card.
Way to fucking go! They say it's rather unlikely that this proposal will get approved by the EU, but given the shit they just pulled on us, I wouldn't be surprised in the slightest id these fuckers just go with it.
Where is our precious privacy going? Some old pedophiles are taking it away from us, into their sex dungeons I suppose...
Unfortunatelly this is a rather new proposal, so I can't find an english article covering this story attack
https://br.de/nachrichten/netzwelt/... 13
13 -
A memorial for my favorite rant of all time "Why did the chicken cross the road?"
+++++++++++++++++++++++++++++++++++++
Why did the chicken cross the road?
Assembler Chicken: First, it builds the road ......
C Chicken: It crosses the road without looking both ways.
C++ Chicken: The chicken wouldn't have to cross the road, you' d simply refer to him on the other side.
COBOL Chicken: 0001-CHICKEN-CROSSING.
IF NO-MORE-VEHICLES
THEN PERFORM 0010-CROSS-THE-ROAD
VARYING STEPS FROM 1 BY 1 UNTIL
ON-THE-OTHER-SIDE
ELSE
GO TO 0001-CHICKEN-CROSSING
Cray Chicken: Crosses faster than any other chicken, but if you don't dip it in liquid nitrogen first, it arrives on the other side frazzled.
Delphi Chicken: The chicken is dragged across the road and dropped on the other side.
Gopher Chicken: Tried to run but got beaten by the Web chicken.
Intel Pentium Chicken: The chicken crossed 4.9999978 times.
Iomega Chicken: The chicken should have ' backed up' before crossing.
Java Chicken: If your road needs to be crossed by a chicken, then the server will download one to the other side. (Of course, those are chicklets.) See also WMI Monitor.
Linux Chicken: Don't you *dare* try to cross the road the same way we do!
Mac Chicken: No reasonable chicken owner would want a chicken to cross the road, so there's no way to tell it how to cross the road.
Newton Chicken: Can't cluck, can't fly, and can't lay eggs, but you can carry it across the road in your pocket.
OOP Chicken: It doesn't need to cross the road, it just sends a message.
OS/2 Chicken: It crossed the road in style years ago, but it was so quiet that nobody noticed.
Microsoft's Chicken: It's already on both sides of the road. What's more its just bought the road.
Windows 95 Chicken: You see different coloured feathers while it crosses, but when you cook it still tastes like........ chicken.
Quantum Logic Chicken: The chicken is distributed probabilistically on all sides of the road until you observe it on the side of your choice.
VB Chicken: USHighways! <TheRoad.cross> (aChicken)
XP Chicken Jumps out onto the road, turns right, and just keeps on running.
The Longhorn Chicken had an identity crisis and is now calling itself Vista.
The Vista Chicken dazzled itself with its own graphics.19 -
Just a friendly reminder that when you hear one or more of the following:
- underrepresented
- identity politics
- *phobia
- toxic *ity
- cis* (though "cisco" is fine)
- diversity
- culture appropriation
- passive-aggressive
- patriarchy
...and other bullshit, feel free to not talk to that person ever again. You'll miss nothing. Always remember that their goal is not equality but power to oppress whoever have a different worldview.
If you fear twitter backlash, fear not. Political shit comes and goes, but the inherent value of what you do is here to stay and means something at all times.
To anyone who wants to judge me because of this — remember, what you have read above comes from a bipolar transgender bisexual rape victim. 35
35 -
So i am the process of working on improving my personal brand and have created myself a new logo.
I thought it would be interesting to see what you all think?
"As a developer/designer hybrid i wanted to create a identity that was able to form a symbolic reference.
My initials (nb) are formed into one continuous line making a connection to two seemingly different fields that represent both design and development."
Full Resolution: https://dribbble.com/shots/... 34
34 -
Java:
Primitive streams. Their need to exist is a monument to legacy failure.
VB.net
OrElse and AndAlso short-circuiting operators. The language designers were too fucking lazy to process logic, so they give specific keywords for those cases.
PHP
Random Hebrew error messages
JS
Eval. It can be used responsibly, but most of the times you see it it's because someone fucked up.
C#
Lack of Tuple destructuring in argument specification. Tuples were added, and pattern matching was added, and it's been getting better. The gear grinding starts with how Tuple identity assignment in arguments is handled. Rather than destructuring into the current scope, it coalesces the identity specification into a dot property of whatever the argument name is. This seems like an afterthought given they have ootb support for ignore characters.
Typescript
This will probably be remedied in the next version or two, but Tuple identity forwarding between anonymous scopes normalizes to arrays of union types, because tuples compile to typeless arrays. It's irritating because you end up having to restate the type metadata in functional series even when there is no possibility for any other code branch to have occurred.12 -
Client: why do I have to use such a hard password for this website?
Me: For security reasons to protect your content and identity of your clients.
Client: Can't you just use the password that I'm used to? I use it on my banking software, and I've never been hacked so it should be good enough for you!
Me: what's the password that you want me to set up for you?
Client: you ready to take it down?
Me: go ahead.
Client: T ... U ... R ... D. You got that?
Me: ... Yes ...
*sigh*6 -
I love how the Keybase Linux client installs itself straight into /keybase. Unix directory structure guidelines? Oh no, those don't apply to us. And after uninstalling the application they don't even remove the directory. Leaving dirt and not even having the courtesy to clean it up. Their engineers sure are one of a kind.
Also, remember that EFAIL case? I received an email from them at the time, stating some stuff that was about as consistent as their respect for Unix directory structure guidelines. Overtyping straight from said email here:
[…] and our filesystem all do not use PGP.
> whatever that means.
The only time you'll ever use PGP encryption in Keybase is when you're sitting there thinking "Oh, I really want to use legacy PGP encryption."
> Legacy encryption.. yeah right. Just as legacy as Vim is, isn't it?
You have PGP as part of your cryptographic identity.
> OH REALLY?! NO SHIT!!! I ACTIVELY USED 3 OS'S AND FAILED ON 2 BECAUSE OF YOUR SHITTY CLIENT, JUST TO UPLOAD MY FUCKING PUBLIC KEY!!!
You'll want to remove your PGP key from your Keybase identity.
> Hmm, yeah you might want to do so. Not because EFAIL or anything, just because Keybase clearly is a total failure on all levels.
Written quickly,
the Keybase team
> Well that's fucking clear. Could've taken some time to think before hitting "Send" though.
Don't get me wrong, I love the initiatives like this with all my heart, and greatly encourage secure messaging that leverages PGP. But when the implementation sucks this much, I start to ask myself questions about whether I should really trust this thing with my private conversations. Luckily I refrained from uploading my private key to their servers, otherwise I would've been really fucked. -
Okay, Google. I can see why you want me to check those boxes with cars. And I'm also fine with you telling me to do it on a different picture if the first one didnt had any, just to check. But WHAT I AM FUCKING NOT OKAY WITH, IS ME SOLVING CAPTCHAS FOR 10 FUCKING MINUTES REPETEDLY SAYING PLEASE TRY AGAIN AND THEN TELLING ME THAT I AM NOT EVEN ABLE TO TRY AGAIN BECAUSE OF AN DETECTED ATTEMPT OF BOTTING? WHO ARE YOU? AN AI QUESTONING MY HUMAN IDENTITY? JUST BECAUSE IM USING LINUX YOU DECIDE TO GIVE ME ANOTHER NOTHERFUCKING BATCH OF STREET SIGNS? YOU CAN STICK THOSE STREET SIGNS UP YOUR ASS! FUCK OFF!
tl;dr: i got banned from solving recaptchas the second time this week. lets hope its just *another* timeout.7 -
Not a software bug but an organisational bug...
Employees holding the door to other people so they can come into a secured building without using their identity badges.
I look like an asshole everytime I refuse to let people I don't know in because most people let them in...10 -
Designer: in an effort to create our brand identity we've come up with a design pattern to use across Android, iOS, and web.
Me: this design goes against material design principles which we agreed we'd use. Also it looks like a mashup of iOS and Windows 10
Designer: just because it looks like an iOS/Windows 10 mashup doesn't mean it was designed for those platforms; it was designed as our brand for all platforms. We feel very strongly about keeping it, specifically the pieces that make you feel uncomfortable as an Android developer
Me: 🙄😑😣😒7 -
Someone in Indonesia is using my email adress to order stuff from a site called Lazada. My email account is not compromised as far as I know. But It's really annoying always getting order confirmation emails in bahasa Indonesia.
I've got "kikis" phone number and adress. Any advice what i've could do to make her stop?18 -
For the love of god, I spent 2,5 hours debugging why Minecraft from the windows store doesn't work...
The game just shows a red message telling you it didn't work.
I checked the logs, nothing just warnings
I re-installed the game, nothing, same error
Updated java and all parts of the store, nothing....
Obviously I had to install Something called the "xbox identity Provider"... You know... On a PC... For a distinctly PC game to work... Installed by the store... And the provider is also on the store... But it doesn't auto-install with the game
Ever since you migrated to the Microsoft Auth the login experience is awful (I ranted about that already)
How about you do the bare fucking Minimum of an User experience and Install the fucking dependencies when I re-installed something your fucking store??!!!
The fucking bare minimum that every package manager ever created fucking has as a basic requirement?! Are you kidding me?
Rename your fucking services so they make sense and please don't waste everyone's time by having both shitty logs and no dep management for your own apps... Fucks sake12 -
Got pretty peeved with EU and my own bank today.
My bank was loudly advertising how "progressive" they were by having an Open API!
Well, it just so happened I got an inkling to write me a small app that would make statistics of the payments going in and out of my account, without relying on anything third-party. It should be possible, right? Right?
Wrong...
The bank's "Open API" can be used to fetch the locations of all the physical locations of the bank branches and ATMs, so, completely useless for me.
The API I was after was one apparently made obligatory (don't quote me on that) by EU called the PSD2 - Payment Services Directive 2.
It defines three independent APIs - AISP, CISP and PISP, each for a different set of actions one could perform.
I was only after AISP, or the Account Information Service Provider. It provides all the account and transactions information.
There was only one issue. I needed a client SSL certificate signed by a specific local CA to prove my identity to the API.
Okay, I could get that, it would cost like.. $15 - $50, but whatever. Cheap.
First issue - These certificates for the PSD2 are only issued to legal entities.
That was my first source of hate for politicians.
Then... As a cherry on top, I found out I'd also need a certification from the local capital bank which, you guessed it, is also only given to legal entities, while also being incredibly hard to get in and of itself, and so far, only one company in my country got it.
So here I am, reading through the documentation of something, that would completely satisfy all my needs, yet that is locked behind a stupid legal wall because politicians and laws gotta keep the technology back. And I can't help but seethe in anger towards both, the EU that made this regulation, and the fact that the bank even mentions this API anywhere.
Seriously, if 99.9% of programmers would never ever get access to that API, why bother mentioning it on your public main API page?!
It... It made me sad more than anything...6 -
I'm writing a huge program of identity management from two months, taking data from different sources and edit them to comply with a lot of cases. Today, my boss told me that he changes idea and my code is now useless... I would cry.4
-
A Bank Account Number is like a public encryption key. Any random person needs it to send me money. Why does it seem like banks treat it as a secret or even use it to confirm my identity? It's literally printed in plain text on every check.2
-
So apparently I own land in dubai. Like three separate mortgages based on the email I received.
Your request (Mortgage Registration)
with request number xxxxx / 2024
has been completed
and you can print your issued certificate from this [link]
I've stripped out the numbers and link.
After confirming it was safe I followed through on a old spare cellphone, and yep, I own three mortgages for properties in dubai.
Except obviously I don't.
Someone used my name, an american, to register mortgages in dubai. *Nice* properties according to the pictures.
What started out as a scam email, or what looked like a scam email, went to an actual government of dubai website, with real mortgage registrations.
How in the fuck does that happen?
The only thing I can think of is someone committed identity fraud, and/or an alphabet agency went through the list of known political dissidents, set up a bullshit mortgage in a questionable territory, and are now using that as a pretext to monitor 'extremists with foreign ties.'
All that for some guy on the west coast that hasn't attended a political rally in his entire life.
Must have been that sign I held at sixteen years old by the side of the road that said "bush lied us into a war, and people died."
or maybe it was that time I told a really enthusiastic obama supporting police officer that it amazed me obama had time to win the nobel peace prize what with all the bombings he carried out against foreign civilians.7 -
wondering whether the fact that I'm avoiding people to extreme measures is part of my identity and it is completely fine to be like that or is actually an obstacle in realization of my identity and I truly should do something about it
 5
5 -
Have you encountered projects that were beyond saving?
Been freelancing for a client via agency for the past year. In the beginning the deal was to maintain identity verification sdk for android maybe 10-15 hours a month or so. Their flow consisted of around 25-30 screens, so I took it thinking it was easy. Boy I was wrong.
Codebase was and still is a complete spaghetti, backend weird and overcomplicated and impossible to talk with someone in backend. Had to reverse engineer their complicated flows many times just to make a small change on the app. There also are lots of issues with capturing/sending camera recordings especially on older devices. The fact that Im the only dev maintaining this doesnt help either.
First few months it was just maintenance, later some small features and soon it become a 40 hour a month gig. I was able to deal with it but then management changed, they started micromanaging me heavily and now they want me to do 60-70 hours a month. Also they asked to implement some unnecessarily complicated features and to be honest without refactoring most of the codebase I cant even begin to think of how to implement them.
Also workload in my main job increased. Started sacrificing my evenings, weekends and basically my wellbeing to work on their product. Tried to relax but then I realized Im just spending my freetime thinking about their project all of the time. Best part is that last few updates fucked up the whole flow and I dont even understand where the problem is anymore: backend, 3rd party integration issues or something else that I did.
Last friday told them that my availability changed and Im quitting. Told them that Im gonna provide support till the end of the month but no big features. Just spent a full shift in my main job and another full shift working on their product, trying to untagle their spaghetti.. Im totally lost and burned out. Meanwhile stupid manager is asking why "simple" stuff according to him is taking too long.
I should receive my last payment from agency this week, also asked them to send it to me earlier but no answer so far. At this point Im so burned out that I dont care anymore about the last payment, even if client complains that everything is broken and doesnt want to pay me. Project is beyond fucked and that SDK as well as their backend is a ticking time bomb. Im done.12 -
My mother is a manipulative bitch.
From my childhood, I remember nothing but fear and guilt. When I was 13, she shamed me for my body looking ugly and too feminine. She shamed me for having better vision than her, and that I don’t need to wear glasses.
I had a broken toe once, and she shamed me into admitting it wasn’t in fact broken. After two weeks of pain, she finally got me to the doctor, and x-ray had shown it was in fact broken.
She always made me carry her heavy luggage with her crap to the airport, and once I got hernia. The surgery was needed. After the surgery, they didn’t care, didn’t give me the time to recover, and made me carry her crap again. The second surgery was needed. It was more complex than the first one. Now my body is ruined by those disgusting scars. I hate my body now. It is ruined.
She tried to knock down the door into my room when I was crying and didn’t want to talk.
She screamed at me when I wanted to donate some of my old clothes to charity, the ones I bought with my own money. She is so obsessed with her crap. She hoards it, and she was hoarding it into _my_ room, not hers.
My father is still unknown. She abandoned me as a kid for my grandparents to grow me. I barely saw her till the age of six. Then I grew up with her and my stepdad, and their relationship was all manipulation and guilt. She made him apologize and beg almost every day over the course of thirteen years. They were fighting about their miserable sexual life, lack of her orgasms while I was still a kid. She just didn’t care. Once they decided to talk about their pissing kink right next to me when I was (not in fact) asleep.
When I was raped, she did nothing. She just kept on calling me beautiful and insisting she wanted me to wear mascara, while hating gay people. It was all before I realized my gender identity.
She also didn’t notice I was autistic. She liked it, as it gave her advantage. It’s easy to manipulate an autistic teenager.
After my coming-out, she told me she had cancer, and she wanted to stop treatment in order to “die sooner and not see me”.
But once my bipolar disorder awakened, things changed. Bipolar is my shield. I can be manipulated, yes, but bipolar will obliterate my whole world view once a year, together with your manipulative crap you planted into my life. And because it dismantled a 19-year-long, almost fractal manipulative masterpiece, I fear nothing now.
I disowned her some two years ago. 21
21 -
Found this while googling an error...
It identifies as an easter-egg therefor it is an easter-egg, so don't you dare egg shame me!
😁 It's not much but i'll take it 😂 1
1 -
We live in a world where WEAKNESS has become a virtue.
- I'm oppressed!
- My mental health!
- I need a helper!
- I'm sensitive!
- You're fatphobic!
- <INSERT SJW's IDENTITY term>
In today's world, you score more social points for describing yourself as weak & blaming 'oppressors' for your miserable life12 -
Beautiful Sunday morning, still no snow here (😒 mother nature) and I realized that I am... Googleable. Like, my name is now out there because of publications. Like, I have been protecting my identity for a long time now, so it's very annoying that I finally have been exposed.
Anyways, how do y'all deal with online fame and recognition?13 -
Me in school: Math? When do I need know those details? I can look them up and just code it.
Me in high school: Computer science is way too math-y. I want to code!
Me coding php: Just make it work.
Me coding typescript: Just make it work.
Me coding scala: Just make it ... what ... how do I make it work!?!
Me asking stackoverflow: How do I do X in scala some functional programming stuff in mind in order to keep immutability.
Somebody way smarter than I: "In scalaz, a function A => A is called an endomorphism and is a Monoid whose associative binary operation is function composition and whose identity is the identity function"
Me now: Fuck my old arrogant self.1 -
Just a couple weeks ago I felt a bit like a hero.
My boss, who seems to have only a vague understanding of realistic deadlines, for once made an error that gave me more time than I needed, not less. I was working on a feature that other work would rely on, so some people had to wait to work on their own projects until I was done.
My boss said it would be done in two weeks, but the only reason why it would have taken that long was because I'd have to submit a ticket to our identity management team to set up the SSO integration with our identity provider, and their turnaround time is two weeks. Or it used to be, but they've actually gotten really fast recently, and as I'd actually grabbed this feature from someone else who had to take a few days off, he'd already gotten the SSO stuff taken care of in advance. My boss promised two weeks and I finished in two days. The shocked silence when they asked for a status update in our next meeting and I told them I'd just finished it was music to my ears.8 -
I don't usually look at the "updates" section of my Gmail but yesterday I did. One message cought my eye: "Your application to Microsoft BizSpark has been approved" but I've never applied to Microsoft BizSpark!
Someone has registered in my name, opened a Microsoft Outlook account under my full name and added my startup details for applying to BizSpark! One issue though, he used some Spanish equivalent of mailinator to subscribe so I could easily reset the password and replace the security email. Now I have 5 visual studio subscriptions I don't know what to do with.5 -
Howdy this is a daily reminder on why you can't trust anyone with shared information.
I am back home from uni for the holidays and like any computer person who is back in town became responsible for fixing every tech problem that has occurred since my last visit. But what caught my eye when I approached the family computer is not the problem with the computer itself, it's the paper in front of the computer that, in giant lettering, has not only the passwords and account names of my mom and brother's AOL (She's old ok) and FAFSA account respectively but also someone's social security number. Any goddam baffoon who looks through the window or is able to take literally three goddam steps past the front door now has enough information to commit identity theft or just take over one of their accounts. I know it's not that likely but I still had a heart attack when I saw that.
How badly have I failed them?1 -
One of the companies that rejected me sent me feedback which I took gracefully coz u sexy cunts told me it wasn't the end of the world when I ranted about it here. Well now they are offering me another interview and I am hella nervous coz I don't want to fuck it. Good thing is the feedback they gave me were actually all shit I know and use daily in my work, I am just bad at explaining plsu was nervous at the last interview. Now I am worried coz it's on monday and I have not had time to practice explaining the lang well coz work has been crazy (literally on a 10 min break now since 9am..almost 10hrs working) which is weird right coz last year I actually used to teach.9
-
I had a few girlfriends in the past and now am married for 4 years and can't remember any gfs before the married life. Ever had a pre-identity crisis?
My mind: "WHO THE F&*! WAS I? WHAT DID I DO? ITS LIKE TOTAL RECON AND AMNESIA ALTOGETHER!!" 4
4 -
Ok, a few days ago I recommended contabo.com as a good and cheap VPS, because our company uses it and it is blazingly fast. BUT! I am definitely NOT doing this!
"False or fraudulent orders are commonplace on the Internet. We have to take measures to prevent such false or fraudulent orders. Our system has identified your order as a possible false order. We must now prove your order as a valid order, otherwise we cannot provide you with the services you bought. We need your help with this. Please send us a copy of your passport or national identity card or something similar which corresponds to the data you have provided to us. Alternatively, you can send us your telephone or electricity bill if it contains your address. The address must match the address you provided on our homepage. It is sufficient if you simply take a photo of the document. The only purpose of this is to prove your order as authentic. This is why it does not matter which of the mentioned documents you send us and it does not matter if you make a scan or take a photo. A scammer could not provide any of these documents, this means one document is already enough to prove that your order is authentic and valid."14 -
nice, 10k reached before sidtheitclown! (that’s all that actually matters, heh)
so, yes, as promised it’s me… chris from chris’ full stack blog.
I think kiki knew this, as I used to be called fullstackchris… though very briefly... don't know why i was ever worried about the old clowns i used to work for knowing my identity here
i’m a host of react round up, and also an ex-futures trader (that life is / was hidden on Twitter), I’ve recently quit because I’m ALSO still building 4ish SaaS products including The Wheel Screener (wheelscreener.com) and CodeVideo (codevideo.io), over my LLC, Full Stack Craft (fullstackcraft.com)
oh yeah, and on top of that i have a full time job in Switzerland (read: not poor boi 38 or 40 hour work week, 42 minimum)
so yeah, its a fucking lot of shit to do and sometimes it’s too much! glad i have this place to vent
so, don’t be too harsh on me… really, 99% of my bitterness comes from the approximate 5 years of my working life (2018-2023) were taken from me by lying business folk type who actually didn’t know what the FUCK they were doing or talking about, even after promising me they did (at two different companies). Listen, I’m all for people telling me iTs a RiSkY VeNTuRe; i get it. But if you say everything is rock solid (like funding, my future employment, etc.) and it is not, then fuck you; you’re just lying to my face, it has nothing to with management vs employee, engineer vs. non-technical - you’re literally just a *bad person* (sorry, mechanical engineering genes and honesty to the core - sue me) To be sure, I was partially at fault - too optimistic, and too gullible, and I’ve have since learned my lesson. but still working on it. (obviously)
but things are look up - my company is running better than ever, the current job is great with insanely smart people
In the end, it’s always the hardcore engineers who are the most honest, hardworking, respectful, and the best to work with - you people know who you are…
Until then… see you in the next rant!!!! 🤬🤬🤬🤬🤬
Dutifully signed,
🤡19 -
I get about 4-5 hours sleep. Like today: I went to work, made my lunch at work, got changed for football, played football from 7-9pm got home at 9:30, cooked, ate, showered and dried my hair and it's now 1am.
Tomorrow I got football training for another team so again I'll be getting into be at about 1am.
Also I forgot go mention ive got to get up at 6 for work And Friday I have to be at the doctors for 7. Yeyyyyy me!!! Don't even ask me about the weekend...
I feel like this classifies as a rant because I don't get to code at the weekends and it kills me 😡😡 especially when I want to contribute to certain packages and said I would. So fuck you social life. Fuck. You.
Ohhh and those fucking 'friends' that guilt trip you into seeing them because "you haven't seen me in ages 😢😢" there's a reason for that Barbra (keeping her identity secret) I'm fucking depressed and tired. Fuck the fuck right off.8 -
Went to a thrift store last week near work and they often have old dev or technology books (I picked up a first edition K&R C book, once) and I found:
1) A book on the history of codes and ciphers throughout history.
2) Beyond good and evil by Nietzsche.
3) A modern publication of a 1673 Spanish demon summoning book (to go into a local town archive).
4) The technical information and construction manual for telegram systems from 1938.
I swear I was driving home thinking:
"Please don't crash, if CSI teams have to piece my identity together from these four personal items I dread to think what conclusions they're going to come to..." -
#DesignFacts :
The Sony Vaio identity, created by Timothy Hanlet, represents both analog (the wave of V and A) and binary (I and O). 2
2 -
For some reason, Google really, really, really wants to know peoples' phone numbers.
Of course, they say it is "only to protect us even more". But if the Twitter phone number misuse incident tells us anything, Google could change their mind at any time.
Around 2012, Google started begging people for their phone numbers upon login, but did not lock users out yet: https://groovypost.com/unplugged/... .
At some point, likely in the late 2010s, Google started locking people out of their accounts until they disclose their phone numbers. This is very unethical. Twitter already did it earlier (around 2016). Many countries' governments outlawed burner phones and people need to disclose their identity to acquire a phone number, as often under the pretext of "fighting terrorism". Surely not for mass-surveillance, am I right? ( https://comparitech.com/blog/... )
Since a few years, Google demands a phone verification for every newly created account. Honestly, that is still better than holding peoples' existing accounts hostage until they disclose a phone number, since locking people out of their accounts a while after creation causes them to lose access to their data.
Of course, people should store any data they do not wish to lose locally. Online services are not personal archives.6 -
DevRanter: *shares some inconvinience at work*
Other Ranters: Dude, Quit your job. Sell your house. Get a divorce ASAP. Give your kids up. Fly to another country. Disappear from everybody's lives. Start a new life. Change your identity.
#lol5 -
"test cases should have an identity and a reason for being" well shit, I'm not even sure I have those things4
-
Your identity is the most valuable thing you have.
Losing it for whatever reason, for example to be like your partner or your parents want you to be is probably the most wrong thing to do.10 -
For about 3x years now, we have had 3x generic work email addresses that are used as microsoft accounts for office 2016 licenses.
(The company is dragging its heels on getting office 365 so MS like to make our lives hell.)
Suddenly we can’t get office updates... and when we sign in to see why, it says that because we are apparently only 3 years old we need our parents permission to use the account or we’ll lose access by September.
Never were we forced to enter a DOB when setting the accounts up!!! So it used the account setup date instead.
It turns out that we can’t change our DOB ourselves, as we are a ‘child’ and need a parents permission.
Fine.
I access my personal account and follow the instructions to add the 3x email addresses as my children so i can change the DOB.
‘Ha ha’ i hear microsoft saying, ‘it doesn’t work that way!!’
No, In order for the parent to verify their child’s identity, they are charged 0.50c per child!
Wtf!!
Doesn’t cost a lot but come on Microsoft!!
It’s that, or submit ID, which obviously wont work for a generic support@ email address like we have.
So annoying and we don’t know what to do.
Wonder how much MS are making out of this...2 -
Zero Days documentary about stuxnet malware features a "identity protected" NSA employee who reveals information about classified NSA tactics.
She claims "I would NEVER compromise ongoing operations in the field."
Well it's too bad that Amazon Prime Video and IMDB don't share your values. They have compromised your name, Joanne Tucker, and the other films you were in.
Nice acting though. You really have people believing you were a real source!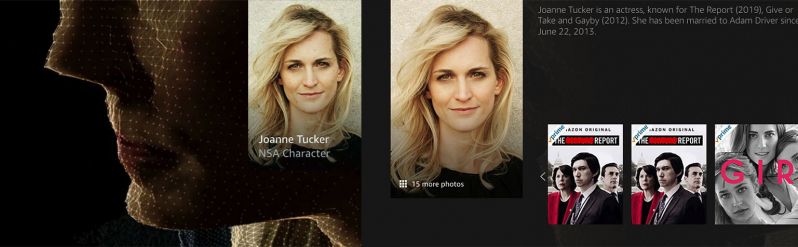 15
15 -
To all the Java Teams that died during the fucking Mobile Civil War, We salute you!
1. Millionaire 2011
2. Splinter Cell: Double Agent
3. Dragon Ball Z Saiyan Fighters
4. Moto Girls
5. 24 Special Ops
6. Thor: The Dark World
7. Kung Fu Panda
8. Worms 2011: Armageddon
9. Asphalt 4: Elite Racing
10. Resident Evil - The Missions
11. Ghost Recon: Future Soldier
12. Spider-Man 3
13. Need for Speed - Undercover 3D
14. Contra 4
15. Rambo on Fire
16. Fast and Furious 6
17. Counter Strike 3D
18. Men in Black 3
19. X–Men Origins: Wolverine
20. WWE Legends of Wrestlemania 3D
21. 3D Fight Night: Round 4
22. 3D Ultimate Rally Championships
23. Assassin's Creed
24. Zuma
24. Die Hard 4
25. 3D WWE Smackdown Vs RAW 2009
26. Prince of Persia 3: The Two Thrones
27. 3D Fight Night: Round 3
28. Super Mario Bros
29. Bruce Lee - Iron Fist 3D
30. Naruto Adventure: A New Apprentice
31. FIFA 2011
32. James Cameron's Avatar
33. Racing 2: The Real Car Experience
34. King Kong
35. Gangstar City
36. Iron Man 3
37. XIII 2: Covert Identity
38. 4x4 Extreme Rally 3D
39. Real Football Manager 2013
40. Splinter Cell: Conviction
41. 2008 Real Football 3D
42. Assassin's Creed 2
43. Hummer 3D
44. American Gangster
45. Real Football 2009
46. 3D Football: Real Madrid 2010
47. Xtreme Dirt Bike
48. Tekken Mobile
49. A Good Day to Die Hard
50. The Amazing Spider-Man 2
51. Asphalt 3: Street Rules 3D
52. GTA IV Mobile
53. 3D Contr Terrorism
54. Real Football 2015
55. The Amazing Spider-Man
56. Contra 4 (2009)
57. Mortal Kombat 3D
58. Bad Girls
59. Assassin's Creed: Brotherhood
60. Need for Speed: Hot Pursuit 3D
61. God of War
62. PES 2009 (Pro Evolution Soccer)
63. Ultimate Street Football
64. Assassin's Creed: Revelations
65. Prince of Persia: The Forgotten Sands
66. 3D Super taxi driver
67. Gangstar 2: Kings of LA
68. Asphalt 6: Adrenaline
69. Assassin's Creed III
70. Danger Dash
71. Real Football 2014
72. Gangstar - Crime City
73. Gangstar 3: Miami Vindication
74. Modern Combat 4: Zero Hour
75. Zuma's Revenge!
We know you guys did your best but the world is a fucking shit hole. We still remember your hard work!
76. Mission Impossible 3
77. Gangstar Rio: City of Saints (I guess these were your last days at work. Well-done guys!)
78. Real Football 2010
79. Real Football 2011 (Real Soccer)
80. Real Football 2012
81. PES 2011 (Pro Evolution Soccer)
82. Ultimate Mortal Kombat 3 (My Favorite)
83. And those missing the list.
WE SALUTE YOU ALL!!! ∠(^ー^)4 -
At 20 I thought my life would be an adventure. At 30 it seems like it's a rerun.
The reality is that life is full of grey areas, "good guys and bad guys" on all sides of most issues, and the story and excitement eventually end.
sometimes getting old feels like becoming comfortable with being numb and mediocre.
you are not the star at the center of your own story.
there is no story. there is only today, and then tomorrow, and then the day after that for as long as they happen to go on.
I can see no greater meaning or purpose behind this circus.
people think in months, seasons, years. maybe some of you even have five year plans.
but for me, rome was yesterday. and every rome to come. thats how near it is. It is so close, it and so many times before and after it, I cannot explain the sensation.
and in the vast gulfs of time, I see the wars, the conflicts, the narratives, and they unfold like dust or scum swirling on a pond, mechanistic, telling stories about nothing, algae struggling over territory on a rock.
as clearly as day, I see it all.
I saw your birth, and I saw your death. Your pain, and your greatest joy. How is it possible to love a total stranger and know them intimately because of their shared humanity? And still.
And from afar, in the stillness, I can't help being detached from the world and its problems.
And when we die, it is as if the world dies with us. Because it is not the end of the world, but the death of our own.
Softly go mortals, gently to their gods, like flowers in the fading summer. Never grasping that the permanence of the true identity and the temporality of the spirit are as fundementally distinct as the permanence of say "the G note", against the brief sound it makes when touched.
Eh. forget it. Sentimentality is a curse sometimes.9 -
!rant
I've had a personal project (commercial idea) I've been meaning to get started on for a while, and today I started...
Kudos to the team at Microsoft, they've really gotten .net core and asp.net core to a fantastic place.
And the team at JetBrains have done an amazing job on Rider.
I've been able to get a docker container running SQL Server on linux, as well as Web API projects for an API and an identity server all running with local HTTPS and communicating quite happily, with barely an issue in sight.
Bodes well for the future I hope.
Now I just have to commit to the project and actually finish it 😂1 -
I've assembled enough computing power from the trash. Now I can start to build my own personal 'cloud'. Fuck I hate that word.
But I have a bunch of i7s, and i5s on hand, in towers. Next is just to network them, and setup some software to receive commands.
So far I've looked at Ray, and Dispy for distributed computation. If theres others that any of you are aware of, let me know. If you're familiar with any of these and know which one is the easier approach to get started with, I'd appreciate your input.
The goal is to get all these machines up and running, a cloud thats as dirt cheap as possible, and then train it on sequence prediction of the hidden variables derived from semiprimes. Right now the set is unretrievable, but theres a lot of heavily correlated known variables and so I'm hoping the network can derive better and more accurate insights than I can in a pinch.
Because any given semiprime has numerous (hundreds of known) identities which immediately yield both of its factors if say a certain constant or quotient is known (it isn't), knowing any *one* of them and the correct input, is equivalent to knowing the factors of p.
So I can set each machine to train and attempt to predict the unknown sequence for each particular identity.
Once the machines are setup and I've figured out which distributed library to use, the next step is to setup Keras, andtrain the model using say, all the semiprimes under one to ten million.
I'm also working on a new way of measuring information: autoregressive entropy. The idea is that the prevalence of small numbers when searching for patterns in sequences is largely ephemeral (theres no long term pattern) and AE allows us to put a number on the density of these patterns in a partial sequence, but its only an idea at the moment and I'm not sure what use it has.
Heres hoping the sequence prediction approach works.17 -
RANT:
Google is just a steaming pile of shit!!
I've recently installed LineageOS onto my phone and wanted to degooglify my life.
So my current Smartphone doesn't have any GApps installed and I get along fairly well.
Should I need anything, I should just be able to use it in my browser right?
RIGHT?
Nono!! As soon as I want to log into a third party Service using Google (older acccounts with the other choice only being Facebook) I need to "verify my identity". And the only option are my old smartphone who still have Gapps on it but are slow and don't accessible when I'm away!
For those who say: "Google is just beeing secure. They don't want anyone to steal your account.". I USE 2FA AND HAVE BACKUP CODES.
BEFORE DEGOOGLING MY DEVICE IT NEVER ASKED SUCH A THING!!! WHAT A PILE OF SPYING SHIT!!!
And the best part, after I remotely started my PC at home and just want to take a screenshot of the message for this post before just using a working session, the message didn't appear.
Somehow google decided that me logging in 15 mins later (same ip) proves my identity?!?!?!
IF THIS CAN BE ATTRIBUTED TO AI. FUCK THIS SHIT. GOOGLED SHOULD BE TREATED LIKE AN ONLINE CASINO BECAUSE THE CHANCE OF JUST GETTING LOGGED SEEMS COMPLETELY RANDOM!!!
(I also had this prior when using my smartphone browser. There I couldn't "circumvent" this and I was at home. But having this shit on my browser which should've a session is unacceptable.)7 -
Dear Identity Providers, Never ask for "favorite teacher" or "mother’s maiden name." Security questions are among the worst ideas in security to date. If you insist, at least let me provide my own questions!8
-
I am fucking sick of everything.
This week was an epitome of shit, hatred, frustration and human filth.
At 16 o clock on friday, as I was in the final planning, someone decided to quit and made this week in its last hours a full fucked nightmare.
Maybe I run away this weekend, get a new identity or become a fucking street hobo, dunno.
I think my patience has run out.
Fuck you. Fuck the world. Fuck everything.
Good night.2 -
Has anybody noticed that "this" in JavaScript is sort of a pain in the ass to keep track of? It appears to have identity issues.22
-
University makes us sign our documents electronically. What this means is that we're required to put pictures of our signature onto all sorts of declarations. Since none of the documents we "sign" this way are important it could be okay, but I don't understand why it's beneficial to encourage us to keep a photo of our signature on our computers, paving the way to identity theft.18
-
Got to scratch of one of three remaining old (14years and counting) design mistakes this week.
Together with a colleague we replaced a 1.5 billion row table that I out of ignorance then designed with a 3 column composite primary key instead of an identity column.
Moving the data while keeping all synchronized (the table gets up towards 2 million new rows and 2 million updates a day while constantly being queried) took 1 week.
Just 2 skeletons left to clean out, any year now ;).1 -
I'm performing a pentest for my client.
So after scanning my client's network I understood they're using IIS 4.5 and windows server 2012 (or 2012 R2)
I know the systems are real old.
And there are known exploits for them.
The tricky part is I have to stay hidden and I only have my own credentials for logging in to the asp page. (Uploading a script is almost crossed cuz it will reveal my identity)
Also I have access to the local network with some of the other employees user/pass.
Any recommendation for exploiting and staying hidden at the same time ?
One more question : will exploits for newer versions work for the older ones necessarily?8 -
Changing authentication mechanism in SharePoint from windows identity to ADFS identity is stupidly complicated, especially for existing large farms with custom code.
On the plus side - just convinced the director this is stupid - saved myself, himself, and 1000 users a ton of misery. 12
12 -
TL;DR: What's cool about your company or what you'd like to have in your company?
I work at a small company (<50 employee) but it has some time around (I'd say almost 20 years or so).
The thing is, the boss here is cheap or inattentive or outdated or all previous options. This translates into a company stuck in the 90's management ways. Well, maybe late 90's.
So we don't have a lot of 'cool' or nice things here; and I've been thinking of coming up with a proposal of a progressive update of some things that gives us (the employees) some sort of identity.
For example, I think that small things like personalized notebooks or post-its or t-shirts give the employees some sort of sense of belonging. We don't have any of that. The only thing we have are business cards and I find them completely useless since I don't visit customers and all my communication with them is via email.
One thing I find very cool is when one employee starts in a company, in their first day they get a 'welcome kit' (example picture): notebook, pen, cup, t-shirt... It may look like stupid shit but it's way better and more motivating than the "Sit here and that's it" welcome I got when I started here.
So I wanna do a proposal of this sort of things that we can adopt, and I wanna know what do you find cool in your company or what would you like your company did so you'd feel more confortable or 'proud' (maybe that's not the word) of working there.6 -
👨🏽💻 Switching between multiple Git accounts: work, personal, freelance?
Ever pushed a commit with Company A's email to Company B's repo? 😩🥶
Been there. Done that. Regretted it immediately.
I just dropped a step-by-step guide on how to set up Git so it automatically picks the right name, email, and SSH key based on your project folder.
No more manual config switching. 💡
✅ No more identity mix-ups
✅ No more commit shame
✅ Just clean, context-aware Git workflows 🙌
🔧 What’s inside:
- Multiple SSH key setup
- Smart .gitconfig using includeIf
- Folder structure that keeps you sane
- Bonus tips for HTTPS + personal token users
If you’ve ever yelled at Git (or yourself), this one’s for you.
👏 Drop a clap if it helps and follow for more dev-friendly tips!
👇 Read it here:
https://rhymezxcode.medium.com/how-... -
Let's talk about the cargo cult of N-factor authentication. It's not some magic security dust you can just sprinkle onto your app "for security purposes".
I once had a client who had a client who I did server maintenance for. Every month I was scheduled to go to the site, stick my fingerprint in their scanner, which would then display my recorded face prominently on their screens, have my name and purpose verified by the contact person, and only then would the guards let me in.
HAHA no of course not. On top of all of that, they ask for a company ID and will not let me in without one.
Because after all, I can easily forge my face, fingerprints, on-site client contact, appointment, and approval. But printing out and laminating a company ID is impossible.
---
With apologies to my "first best friend" in High School, I've forgotten which of the dozens of canonicalisations of which of your nicknames I've put in as my answer to your security question. I've also forgotten if I actually listed you as my first best friend, or my dog - which would actually be more accurate - and actually which dog, as there are times in my High School life that there were more tails than humans in the house.
I have not forgotten these out of spite, but simply because I have also forgotten which of the dozen services of this prominent bullshit computer company I actually signed up for way back in college, which itself has been more than a decade ago. That I actually apparently already signed up for the service before actually eludes me, because in fact, I have no love for their myriad products.
What I have NOT forgotten is my "end of the universe"-grade password, or email, or full legal name and the ability to demonstrate a clear line of continuity of my identity from wherever that was to now.
Because of previous security screwups in the past, this prominent bullshit company has forced its users to activate its second, third, and Nth factors. A possibly decade-old security question; a phone number long lost; whatever - before you can use your account.
Note: not "view sensitive data" about the account, like full name, billing address, and contact info. Not "change settings" of the account, such as changing account info, email, etc. Apparently all those are the lowest tier of security meant to be protected by mere "end of the universe"-grade passwords and a second factor such as email, which itself is likely to be sold by a company that also cargo cults N-factor auth. For REAL hard info, let's ask the guy who we just showed the address to "What street he lived in" and a couple others.
Explaining this to the company's support hotline is an exercise in...
"It's for your security."
"It's not. You're just locking me out of my account. I can show you a government ID corroborating all the other account info."
"But we can't, for security."
"It's not security. Get me your boss."
...
"It's for security."8 -
I have a Devrant tee shirt and stickers. Everyone knows I like 80s Rock and metal. I hope know figures out my identity. Never mind I don't care. I am freelancing.6
-
How do you write your "identity" in your code so that others can see that it's you who made it?
Do you do it with a simple "made by" or do you write more?17 -
An identity platform where you can find each other, get the other's public key and preferred contact method. And the entire key exchange and choice of contact method are negotiated automatically. No vendor lock in, encryption happens on your own device. Effortlessly and securely communicating, no searching for skype name, email, phone number, setting up shit. It would just work.7
-
Got contacted by a potential client whose job I had bid on. Spent a couple of minutes frantically studying his specification and preparing my discussion.
Turns out the job was fake. He wanted me to create a new profile, verify it with my white European identity and then let him use it to approach Western clients.
The best part? I'm as Asian as he is, and all my profile pictures bear witness to that fact.
Some people smoke some really special stuff...1 -
Imagine going on quora and answering somebodies carbon offsetting question by pushing your own stupid fucking agenda with propaganda answers like
"oh we need rainforest money!"
"oh we need grassland!"
"oh support the cows"
jesus fucking christ, THIS is why we have a problem with people not accepting climate change, becuase every fucking liberal wants to pile on one another and have their 'most important' cause behind it
give me a break you fucking idiots, it won't be solved by acting this way
sorry this is in no way software related, but it's the only place left i have to rant (however in some ways it is somehow software related, due to being able to think about the real world without being an absolute idiot and pushing some stupid peer pressured political idea because your social identity and friends are more important than actual facts, but whatever)12 -
At the time I had been squatting, arrested, driven 300 miles across country only to be released - mistaken identity with just the clothes on my back. Decided to stay and lined up a couple of interviews. I got offered both but took the one which meant 2 busses and a ferry and 2 hours each way for a data entry position.
They were migrating to a new database and my job was to type it in to a screen so from print outs. Didn’t take long for me to work through that and they were struggling to find stuff for me to do, I mean at one point I was filing paper files. So I saw the 2 it guys doing the same thing with loads of excel files , hours and hours a month just wasted. I wrote a vba excel macro to do it for them at the click of a button and suddenly a position opened up as a junior programmer. Still at the same place 16 years later and were still using software I wrote 15 years ago (.net 1.1) quite happily on win10 surprisingly. -
Anybody else feel like their Internet traffic constanty being monitored after downloading pen testing tools?
Have our identities been added to lists of potential cyber criminals :/
Thoughts?
(For ethical purposes - involving your own site's security!!)2 -
fuck it; at 10K updoots i'll reveal my identity
then everyone will know i'm a closet psychopath
it may be risky!
it may be ruinious to my career!
let's do it!15 -
Big military company is using their custom font for everything. Is there a way to find documents that use a specific font?
All hail to the corporate identity!4 -
I have a confession to make. I am indeed a team of entities. Yes! The only catch is all those entities live inside one brain.
My first and perhaps most important insight stemmed from not being able to overcome a persistent identity crisis. I spent seven years trying to figure out who I am and what my worldview is. I realized however that it was impossible. It makes no sense to be rational while your irrational part is hovering over, judging.
So, I split my “me” into two parts: rational and emotional. Usually, they coexist peacefully.
When presented with a complicated case, I let both speak. It doesn't matter if they contradict each other. The consensus is never reached, but at least both parts spoke their mind and are now calm.
There are two kikis. Rational kiki talks about life, insights, worldview, and occasionally tech. Emotional kiki sends leg pics and describes her wild dreams.
Also, it gets even more complex when derealization hits. Remember, autistic brains don't have garbage collectors, so as the day goes by, noise accumulates, influencing my entire being. In the morning, I'm cold and calculated, albeit a bit robotic. In the evening, I'm creative and talkative, albeit a bit unhinged.
You're welcome!7 -
I wish all you frontend devs who use the keydown event to hack tab-order a very painful and very quick death.
Especially those who fail to ensure that TAB; Shift+TAB is always identity.1 -
The global joke of Information Security
So I broke my iPhone because the nuclear adhesive turned my display into a shopping bag.
This started the ride for my character arc in this boring dystopia novel:
Amazon is preventing me from accessing my account because they want my password, email AND mobile phone number in their TWO.STEP Verifivation.
Just because one too many scammers managed to woo one too many 90+y/o's into bailing their long lost WW2 comrades from a nigerian jail with Amazon gift cards and Amazon doesn't know what to do about anymore,
DHL is keeping my new phone in a "highly secure" vault 200m away from my place, waiting for a letter to register some device with a camera because you need to verify your identity with an app,
all the while my former car insurance is making regress claims of about 7k€ against me for a minor car accident (no-one hurt fortunately, but was my fault).
Every rep from each of the above had the same stupid bitchass scapegoat to create high-tech supra chargers to the account deletion request:
- Amazon: We need to verify your password, whether the email was yours and whether the phone number is yours.
They call it 2-step-verification.
Guess what Amazon requests to verify you before contacting customer support since you dont have access to your number? Your passwoooooord. While youre at it, click on that button we sent you will ya? ...
I call this design pattern the "dement Tupi-Guarani"
- DHL: We need an ID to verify your identity for the request for changing the delivery address you just made. Oh you wanted to give us ANOTHER address than the one written on your ID? Too bad bro, we can't help, GDPR
- Car Insurance: We are making regress claims against you, which might throw you back to mom's basement, oh and also we compensated the injured party for something else, it doesn't matter what it is but it's definitely something, so our claims against you just raised by 1.2k. Wait you want proof we compensated something to the injured at all? Nah mate we cant do that , GDPR. But trust me, those numbers are legit, my quant forecasted the cost of childrens' christmas wishes. You have 14 days or we'll see you in court haha
I am also their customer in a pension scheme. Something special to Germany, where you save some taxes but have to pay them back once you get the fund paid out. I have sent them a letter to terminate the contract.
Funniest thing is, the whole rant is my second take. Because when I hit the post button, devrant made me verify my e-mail. The text was gone afterwards. If someone from devRant reads this, you are free to quote this in the ticket description.
Fuck losing your virginity, or filing your first tax return, or by God get your first car, living through this sad Truman dystopia without going batshit insane is what becoming a true adult is.
I am grateful for all this though:
Amazon's safety measures prevented me from spending the money I can use to conclude the insurance odyssey, and DHLs "giving a fuck about customers" prevention policies made me support local businesses. And having ranted all this here does feel healthy too. So there's that.
Oh, cherry on top. I cant check my balance, because I can only verify my login requests to my banking account wiiiiiiith...?2 -
"Hey, this developer does some good work, I think I'll follow them to keep up... Oh, their online presence is consumed in identity politics? Damn."1
-
My trying to login to my email account my.email.address@example.com via web:
Site: You need to verify that you are really you. We sent a verification email to my.email.address@example.com please click the link in this email to verify your identity.2 -
What I write:
select * from x where id in (1,2)
What appears in sql-server management studio:
select * from x where IDENTITY INDEXKEY_PROPERTY (1,2) -
There's this thought that keeps popping up in my head more frequently recently.
We are people who do heavy mind work. Our quality of life directly depends on our ability to come up with solutions. We've been training our minds for years, for decades, to get to the point where we are now.
Now stop for a moment. And imagine. You wake up one morning and you realize you can no longer code. You forgot all of it. You still can copy-paste answers from SO, but you don't know what questions to ask to get to those answers.... Your mind has pulled the DROP TABLE PROGRAMMING;COMMIT; stunt. From hero to zero in just 1 night.
You have no clue what happened, no idea whether you will recover. How does that affect your identity? Would you still try to climb the programmers' tree to the sweet spot you are in now? Would you choose some simpler profession instead, considering your age and time required to master that other profession? If you choose another profession - what would it be?
What would you do with your personal projects? You can't continue them yourself obviously... Would you let them die with the loss of your skills?
How closely is your profession related to your identity?
Now that I consider myself a person who's quite good in the field, this is becoming one of my fears. Sadly, it'll most likely come true someday. Either some accident or just old age, or even diseases/conditions at younger ages - there are so many things that could mess up your mind - the sole tool critical for our profession [to the picky ones: lumbers can't swing axes w/o hands, postman can't deliver mail w/o legs, politics can't lie without tongues, and we, engineers, cannot build with our minds even slightly off].7 -
concious inclusion training: we want you to talk and share about a bunch of shit that's illegal to ask in interviews: age,sex, orientation, family status, religion, values, gender identity, ethnicity etc
what the fuck do any of these things even have to do with the job?
im confused but whatever5 -
Well, this one was very satisfying.
When I resigned from my previous job, there was this one last task I had to finish. The task was to implement an identity and access management system that would work across three different platforms they had. I used to work on one of them which had nothing of the sort but the other two had something of their own. Here lies the kicker, it had to work with existing authorization system in other two platforms. After explaining multiple times why that is a bad idea, I gave up. I created an interface, no implementation, documented how the interface was meant to be used and got the hell out of there. -
!dev
Sometimes life just cracks its knuckles and goes like, yeah let's just fuck this guy inside out.
Everyday is a battle. Cockroaches are my worst fear. Like Orwell's Room no. 101 level fear. My tiny student residence room has so many that I'm sick of killing them. And they just keep coming back.
My worst sorrow is lonliness. I'm the kind of person who's fairly independant and level headed but I just love the feeling of having close ones around. So much that it's a part of my existence and identity. And sadly, that's just not there right now.
My worst misery is unproductivity. Not working on something useful always makes me feel guilty. But all the stress and responsibilities and the above mentioned problems leave me with little mental room to do what I like unless I put in a lot of conscious effort into it which drains me.
Despite all this, I stay happy. I smile at the end of the day and I'm fucking proud of it.3 -
I'll try to pay back some smaller credit by one large credit...
Hence I need to contact the banks and get one (!) fucking frigging stupid piece of paper which lists the account number and the amount of money I need to pay back.
Sounds simple ...
Well.
One bank just answered my email request by sending me that piece of paper. Except they didn't have any validation of my identity.
Yes. They answered the request of 'I want to pay back the credit in full, can u send me the necessary documents?' (more formal of course) with confidential data without any more credibility than my email address.
YAY.
Another bank requests a telephone call for identity validation and sending back a signed form via postal service...
Another bank just needs a PDF sent via mail with an electric signature (yeah. They were aware of what that means - I was shocked and confused) or a "qualified signature matching previous documents" (translated from German).
The last one offers a WhatsApp number - send a GIF / JPG or video and we answer directly.
I need to reach a higher state than drunk.
It's not funny to know how confidential data gets mistreated by companies who should have the highest security.4 -
Fucking regulations, can’t play with twilio api.
Waiting for verification of my identity to make a fucking test call to myself.
Wanted to make a proof of concept during weekend, but won’t happen cause some fucking policies.
Fuck you government pigs.
Probably need to wait to fucking Monday. I will forget what I wanted to do till that time.
We are making your life easier all the time in the news, yeah right eat those popups motherfuckers.
Next regulation - government code reviews before push to master and programmer certification, for sure those fuckers are able to do it.
Really considering emigration from Europe right now.
No fucking point to start a business on this continent.
More fucking law please so we would need a lawyer before wiping ass.
Need to watch that southpark episode about security toilet checkout once again.2 -
Question - is this meaningful or is this retarded?
if
2*3 = 6
2*2 = 4
2*1 = 2
2*0 = 0
2*-1 = -2
then why doesnt this work?
6/3 = 2
6/2 = 3
6/1 = 6
6/0 = 0
6/-1 = -6
if n/0 is forbidden and 1/n returns the inverse of n, why shouldn't zero be its own inverse?
If we're talking "0" as in an infinitely precise definition of zero, then 1/n (where n is arbitrarily close to 0), then the result is an arbitrarily large answer, close to infinite, because any floating point number beneath zero (like an infinitely precise approximation of zero) when inverted, produces a number equal to or greater than 1.
If the multiplicative identity, 1, covers the entire set of integers, then why shouldn't division by zero be the inverse of the multiplicative identity, excluding the entire set? It ONLY returns 0, while anything n*1 ONLY returns n.
This puts even the multiplicative identity in the set covered by its inverse.
Ergo, division by zero produces either 0 or infinity. When theres an infinity in an formula, it sometimes indicates theres been
some misunderstanding or the system isn't fully understood. The simpler approach here would be to say therefore the answer is
not infinity, but zero. Now 'simpler' doesn't always mean "correct", only more elegant.
But if we represent the result of a division as BOTH an integer and mantissa
component, e.x
1.234567 or 0.1234567,
i.e. a float, we can say the integer component is the quotient, and the mantissa
is the remainder.
Logically it makes sense then that division by zero is equivalent to taking the numerator, and leaving it "undistributed".
I.e. shunting it to the remainder, and leaving the quotient as zero.
If we treat this as equivalent of an inversion, we can effectively represent the quotient from denominators of n/0 as 1/n
Meaning even 1/0 has a representation, it just happens to be 0.000...
Therefore
(n * (n/0)) = 1
the multiplicative identity
because
(n* (n/0)) == (n * ( 1/n ))
People who math. Is this a yea or nay in your book?14 -
Brave Browser.
There’s a reason why brave is generally advised against on privacy subreddits, and even brave wanted it to be removed from privacytools.io to hide negativity.
Brave rewards: There’s many reasons why this is terrible for privacy, a lot dont care since it can be “disabled“ but in reality it isn’t actually disabled:
Despite explicitly opting out of telemetry, every few secs a request to: “variations.brave.com”, “laptop-updates.brave.com” which despite its name isn’t just for updates and fetches affiliates for brave rewards, with pings such as grammarly, softonic, uphold e.g. Despite again explicitly opting out of brave rewards. There’s also “static1.brave.com”
If you’re on Linux curl the static1 link. curl --head
static1.brave.com,
if you want proof of even further telemetry: it lists cloudfare and google, two unnecessary domains, but most importantly telemetry domains.
But say you were to enable it, which most brave users do since it’s the marketing scheme of the browser, it uses uphold:
“To verify your identity, we collect your name, address, phone, email, and other similar information. We may also require you to provide additional Personal Data for verification purposes, including your date of birth, taxpayer or government identification number, or a copy of your government-issued identification
Uphold uses Veriff to verify your identity by determining whether a selfie you take matches the photo in your government-issued identification. Veriff’s facial recognition technology collects information from your photos that may include biometric data, and when you provide your selfie, you will be asked to agree that Veriff may process biometric data and other data (including special categories of data) from the photos you submit and share it with Uphold. Automated processes may be used to make a verification decision.”
Oh sweet telemetry, now I can get rich, by earning a single pound every 2 months, with brave taking a 30 percent cut of all profits, all whilst selling my own data, what a deal.
In addition this request: “brave-core-ext.s3.brave.com” seems to either be some sort of shilling or suspicious behaviour since it fetches 5 extensions and installs them. For all we know this could be a backdoor.
Previously in their privacy policy they shilled for Facebook, they shared data with Facebook, and afterwards they whitelisted Facebook, Twitter, and large company trackers for money in their adblock: Source. Which is quite ironic, since the whole purpose of its adblock is to block.. tracking.
I’d consider the final grain of salt to be its crappy tor implementation imo. Who makes tor but doesn’t change the dns? source It was literally snake oil, all traffic was leaked to your isp, but you were using “tor”. They only realised after backlash as well, which shows how inexperienced some staff were. If they don’t understand something, why implement it as a feature? It causes more harm than good. In fact they still haven’t fixed the extremely unique fingerprint.
There’s many other reasons why a lot of people dislike brave that arent strictly telemetry related. It injecting its own referral links when users purchased cryptocurrency source. Brave promoting what I’d consider a scam on its sponsored backgrounds: etoro where 62% of users lose all their crypto potentially leading to bankruptcy, hence why brave is paid 200 dollars per sign up, because sweet profit. Not only that but it was accused of theft on its bat platform source, but I can’t fully verify this.
In fact there was a fork of brave (without telemetry) a while back, called braver but it was given countless lawsuits by brave, forced to rename, and eventually they gave up out of plain fear. It’s a shame really since open source was designed to encourage the community to participate, not a marketing feature.
Tl;dr: Brave‘s taken the fake privacy approach similar to a lot of other companies (e.g edge), use “privacy“ for marketing but in reality providing a hypocritical service which “blocks tracking” but instead tracks you.14 -
Part 1: https://devrant.com/rants/4298172/...
So we get this guy in a meeting and he is now saying "we can't have application accounts because that violates our standard of knowing who accessed what data - the application account anonamizes the user behind the app account data transaction and authorization"
And so i remind him that since it's an application account, no one is going to see the data in transit (for reference this account is for CI/CD), so the identity that accessed that data really is only the app account and no one else.
This man has the audacity to come back with "oh well then thats fine, i cant think of a bunch of other app account ideas where the data is then shown to non-approved individuals"
We have controls in place to make sure this doesnt happen, and his grand example that he illustrates is "Well what if someone created an app account to pull github repo data and then display that in a web interface to unauthorized users"
...
M******* why wouldnt you JUST USE GITHUB??? WHO WOULD BUILD A SEPARATE APPLICATION FOR THAT???
I swear I have sunk more time into this than it would have costed me to mop up from a whole data breach. I know there are situations where you could potentially expose data to the wrong users, but that's the same issue with User Accounts (see my first rant with the GDrive example). In addition, the proposed alternative is "just dont use CI/CD"!!!
I'm getting pretty pissed off at this whole "My compliance is worth more than real security" bullshit. -
How many people here consider their profession a large, potentially principal part of their identity as people? How important is it to you that you are known for what you do?1
-
Trying to use authenticate a JWT token from an Azure service, which apparently needs to use Azure AD Identity services (Microsoft Entra ID, Azure AD B2C, pick your poison). I sent a request to our Azure admin. Two days later, I follow up, "Sorry, I forgot...here you go..."
Sends me a (small) screenshot of the some of the properties+GUIDs I need, hoping I don't mess up, still missing a few values.
Me: "I need the instance url, domain, and client secret."
<hour later>
T: "Sorry, I don't understand what those are."
Me: "The login URL. I assume it's the default, but I can't see what you see. Any shot you can give me at least read permissions so I can see the various properties without having to bother you?"
T: "I don't see any URLs, I'll send you the config json, the values you need should be in there."
<10 minutes later, I get a json file, nothing I needed>
<find screenshots of what I'm looking for, send em to T>
Me: "The Endpoints, what URLs do you see when you click Endpoints?"
<20 minutes later, sends me the list of endpoints, exactly what I'm looking for, but still not authenticating the JWT>
Me: "Still not working. Not getting an error, just that the authentication is failing. Don't know if it's the JWT, am I missing a slash, or what. Any way I can get at least read permissions so I don't have to keep bugging you to see certain values?"
T: "What do you need, exactly?"
Me: "I don't know. I don't know if I'm using the right secret key, I can't verify if I'm using the right client id. I feel like I'm guessing trying to make this work."
T: "What exactly are you trying to get working?"
<explain, again, what I'm trying to do>
T: "That's probably not going to work. We don't allow AD authentication from the outside world."
Me: "Yes we do. Microsoft Teams, Outlook, the remote access services. I can log into those services from home using my AD credentials."
T: "Oh yea, I guess we do. I meant what you are trying to do. Azure doesn't allow outside services to authenticate using a JWT. Sorry."
FRACK FRACK FRACK!!
Whew! Putting the flamethrower away.
Thanks devrant for letting me rant.3 -
Wtf....Facebook just disabled my account and asked to confirm my identity by uploading a photo. What might be the problem?
 6
6 -
I asked for a little whipped cream...
Guess the barista was using equality operators instead of identity operators.
😒 4
4 -
In SQL Management Studio, why is the Identity Specification so low in the column properties list?! It's so annoying to scroll and find it.
Is this punishment for using the GUI?1 -
What makes free ssl "Unsuitable for e-commerce websites", Please read to end to see my view point.
From Namecheap:
Free Certificates are domain validation only which means they don't certify the identity of the website owner, they simply ensure a secure connection. Customers can't be sure of the integrity and trustworthiness of the website owner. If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer. It's important your customers trust your business is safe enough to hand over these details. To gain this trust, you need a certification of your authenticity, which you can only get with a (paid) Business Validation or Extended Validation SSL Certificates.
https://namecheap.com/security/...
* "To gain this trust, you need a certification of your authenticity"
~ But isn't that just Domain Verification and other Extras, What justifies somebody or business's authenticity? Tax Id, Valid Address, Nobody is going to study the ssl cert to make sure that amazon.com is a valid business and has a tax Id.
* "domain validation only which means they don't certify the identity of the website owner,"
~ Wouldn't this just be the domain validation test that is required when using services like LetsEncrypt using Certbot etc, or are we referencing back to this idea that they look for a Valid Tax Id sort of thing?
* "If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer"
~ Why is the paid version going to do double encryption, is the CA going to run a monitoring tool to scan for intrusions like a IDS or IPS? (disregard the use of DNS Validation being in the picture)
Am I missing something, this just seems like well crafted text to get people to buy a cert, I could understand if the encryption was handled differently, Maybe if they checked the site for HSTS or HTTPs Redirect or even, They blocked wildcard SSL before and now with the paid its included, but overall it doesn't sound like anything special. Now I'm not just picking on namecheap because domain.com does the same.14 -
a bro wants to buy my saas product
if i can sell it for 100K+ I'll reveal my true identity
though actually the more i think about it all the more reason to stay anon...20 -
Word is spreading that CNN, which is owned by Time Warner, got a reddit users IP from their mods, and with their relation to Time Warner, got his identity.
Then extorted him to apologize or be revealed.
This is huge, and we don't even know its the only time it has happened.
VPNs may not even truly protect you if the ISP can connect the dots over time, with time stamps.
Holy shit, CNN just weaponized ipv4 1
1 -
Applying Occam's razor and I might be wrong..
Hiring a candidate and job hunt, both are fucking exhaustive process.
We, as a human race, have aimed for Moon and Mars but are unable to solve the problem at hand which can save millions of hours each year reflecting in immediate cost savings.
Here's my (idealistic) solution:
A product to connect job seekers and recruiters eliminating all the shitty complexities.
LinkedIn solved it, but then hired some PMs who started chasing metrics and bloated the fuck out of the product.
Here are some features of the product I am envisioning:
1. Job seeker signs up and builds their entire profile.
2. Ability to add/remove different sections (limited choices like certifications, projects, etc.), no custom shit allowed because each will have their own shit.
3. By default accept GDPR, Gender Identity, US equality laws, Vetran, yada yada..
4. No resume needed. Profile serves as resume. Eliminate the need to build a resume in word or resume builders.
5. Easy updates and no external resume, saves the job seeker time and gives a standard structure to recruiters to scan through eliminating cognitive load.
6. Recruiters can post their jobs and have similar sections (limited categories again).
7. Add GDPR, Vetran, etc. check boxes need basis.
8. No social shit. Recruiters can see profiles of job seekers and job seekers can see jobs. Period.
9. Employee working in Google? Awesome. Will not show Google recruiters thier profile and employee such job posts.
10. No need to apply or hunt heads. System will automatch and recommend because we are fucking in AI generation and how hard it is to match keywords!!
11. Saves job seekers and recruiters a fuck ton of time hunting the best fit.
12. This system gets you the best job that fits your profile.
Yes, there are flaws in this idea.
Yes, not all use cases are covered.
Yes, shit can be improved and this is hypothetical.
But hey! Surely doable with high impact than going on Moon or Mars right now.
Start-up world has lost its way.11 -
Anyone else ever been through an identity crisis? This shit is intense. For the first time in over a decade I'm questioning who I really am and how to be happy while interacting with the world around me.
I used to not give a fuck what people thought about me, my semi-haggard appearance was just part of my persona, but as time marched on and my hair got longer, I get nothing but shitty looks from people 40+. I feel like nobody takes me seriously anymore. I'm honestly debating just chopping off most of my hair and dressing nicer, essentially 'growing up'. Just kind of rolling over and blending in with everyone else. "The nail that sticks out gets hammered down." - I'm tired of getting hammered. I just want to retreat to my quiet little corner of newfound adulthood.4 -
I don't like most of the people around me (programmers). I find most of them boring and with a really "flat" personality with no interests other than coding. I enjoy coding myself but sometimes I feel that I don't belong to this community. There is more in life than just your job.1
-
I'm so done with auth
it's more than a nightmare
it's a disgrace
why can't someone just be like "you know how auth and identity is hard? why don't we make it easy?"
I would pay so much for that9 -
bitter reflections from a bitter dev on hacktoberfest this year (in the past 2 hours of trying to find issues my IQ has at least halved):
- DefinitelyTyped - used to be my bread and butter to complete hacktoberfest; now, not sure if actual issue, or person just doesn't know how to use typescript (found a multiple such issues that were actually non-issues, the type they were asking for was right there, no pull request needed)
- avoid "issues" on no code / low code tools, these are toxic issues with titles like "I EXPLAIN BUG HERE", then probably not even a bug / more a feature request or clueless clown
- if your entire contributor team has the same character styled profile pic + background, i can't take you seriously; if your identity is so closely tied with what github team you are on... uh, i mean cmon what is this kindergarten? (also love the fact that an anon managed to get themselves mixed in hahahaha they ruined it perfectly!)
- most 'hacktoberfest' issue finders themselves are broken or don't load anything
- people claim issues and then never return YAWN
- the hacktoberfest discord: the projects channel is mostly people promoting their garbage repo WHICH HAS 0 OPEN ISSUES IN THE FIRST PLACE AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA and then OTHER people promoting their own portfolio on hacktoberfest???!! 😂😂😂😂 yeah bro i'm gonna help you with your own portfolio site GTFO
from what i've seen, i think i can start working approximately 5 minutes a day and be more successful than these absolute 🎪🤡🤹♂️ devs
sure, there is being a beginner, and there is being a clown salesmen trying to get people to do work for you... i mean wtf is going on
i WANT to help and contribute, but this year its really a struggle to find anything worthwhile to contribute to!
somehow the spark is gone... this might be my last Hacktoberfest... let me just return to my wisky and be in peace 4
4 -
Sadly I just can imagine more development directed to increase consumer behavior (ads, social) and less to actually improve people's lives.
Shouldn't software development have an identity other than the enterprise? We are probably the better communicated professional community there is. Shouldn't we rise? ✊2 -
When we subtract some number m from another number n, we are essentially creating a relationship between n and m such that whatever the difference is, can be treated as a 'local identity' (relative value of '1') for n, and the base then becomes '(base n/(n-m))%1' (the floating point component).
for example, take any number, say 512
697/(697-512)
3.7675675675675677
here, 697 is a partial multiple of our new value of '1' whose actual value is the difference (697-512) 185 in base 10. proper multiples on this example number line, based on natural numbers, would be
185*1,
185*2
185*3, etc
The translation factor between these number lines becomes
0.7675675675675677
multiplying any base 10 number by this, puts it on the 1:185 integer line.
Once on a number line other than 1:10, you must multiply by the multiplicative identity of the new number line (185 in the case of 1:185), to get integers on the 1:10 integer line back out.
185*0.7675675675675677 for example gives us
185*0.7675675675675677
142.000000000000
This value, pulled from our example, would be 'zero' on the line.
185 becomes the 'multiplicative' identity of the 1:185 line. And 142 becomes the additive identity.
Incidentally the proof of this is trivial to see just by example. if 185 is the multiplicative identity of 697-512, and and 142 is the additive identity of number line 1:185
then any number '1', or k=some integer, (185*(k+0.7675675675675677))%185
should equal 142.
because on the 1:10 number line, any number n%1 == 0
We can start to think of the difference of any two integers n, as the multiplicative identity of a new number line, and the floating point component of quotient of any number n to the difference of any number n-m, as the additive identity.
let n =697
let m = 185
n-m == '1' (for the 1:185 line)
(n-m) * ((n/(n-m))%1) == '0'
As we can see just like on the integer number line, n%1 == 0
or in the case of 1:185, it equals 142, our additive identity.
And now, the purpose of this long convoluted post: all so I could bait people into reading a rant on division by zero.14 -
Domain Drive Design question:
I am working on a simple case to teach how to apply DDD, my case is as follows:
Simple forum with Author, Moderator and Users.
I am using Dotnet core for this. I am not sure how and where I should implement authorization:
1. Author can edit his posts only
2. Moderator edits any post
In dotnet core, we handle roles, policies in the api layer, and its per endpoint, I have an identity layer which handles accounts, registering roles and policies in database.
But I'm not sure if I should or how to handle authorization based on permissions in application layer.26 -
Seeing some Ruby just reminded me of something.
Fuck Objective-C. What kind of lazy fuck makes C object oriented by stapling SmallTalk to it? A better name would be "C: Now with Dissociative Identity Disorder...oh and objects".
Apple apologists make excuses for this miserable language all the time...why? Because it's the only thing Apple would give you?
Swift is definitely an improvement though.4 -
Latest promoted thread on XDA to make the list:
"how to disable forced encryption".
This is from a place that tries to be innovative. I'm half expecting a thread get promoted with the title "how to give everyone your passwords/identity/credit cards".
https://forum.xda-developers.com/ma... 3
3 -
Me walking down the corridors of my building after hours, singing full on out loud (I can actually sing)
Lyrics(by yours truly homage to Mika)
I wanna talk to you!
The last time we talked, Mr. Smith, you reduced me to tears
I promise you it won't happen again!
Do I attract you? Do I repulse you with my queasy smile?
Am I too dirty? Am I too flirty? Do I like what you like?
I could be wholesome, I could be loathsome, I guess I'm a little bit shy
Why don't you like me? Why don't you like me without making me try?
Some voice at the other side of the building: "who is there singing???!"
Me:
"I tried to be like Grace Kelly!!"
"but all her looks are too sad"
"so I tried a little Freddy MMMMMMMMMMMMMMMMMMM"
"I've gone identity maaaaaaaaaaaad"
then I walked inside of my office and stopped spooking the janitors. Really wish someone would join in and helped me sing the high note parts of the song really. I've got no audience here smfh -
I think I used to identify myself heavily by my work, career and so felt very dissatisfied I wasn't living up to my potential and getting the chances I deserved. I just couldn't get my dream job...
But now it feels like I've sorta split into Work and Life. Work does whatever is needed to pay the bills and is pretty satisfied now. Still gotta deal with monkeys but maybe devRant has helped provide an outlet to unleash the stress... and maybe sorta made it fun...
But Life juggles among different things, some time wasters, but seems now not so coding heavy anymore unless it's really inspired. And doesn't like putting aside time to prepare for interviews anymore or even actively seek out the latest tech news...
I sorta forgot what I was saying but does anyone else feel they used to have one identity but now split into 2 or more?
Actually I think this is what triggered it. Read this awhile ago but suddenly had this thought in my mind...
http://businessinsider.com/jeff-bez...1 -
what percentage of these dune hipsters haven't read a SINGLE word of any of the 6 books in the dune series (yes drooling losers, there are 6 of them)
I'm guessing > 90%
wow congrats you watched a 2 hour film, make it your entire identity 🤡
god the world has become ever decreasing cycles of cringe... they will decrease in time length until we reach unending - and therefore infinite - cringe
FullStackCircus Principle™16 -
Lot of people asking my real Identity 🙄 Let's see who can figure out my real name. There are couple exceptions who already know me. So please don't comment if you already know. 😅12
-
I'm at a hospital waiting and the tv is so loud so I thought I'd find a remote app to turn it down.
I found this app, one with no ads but look at all the damn permissions it needs....
What the hell,
Anyone know a good remote app that doesn't want to steal my identity? 5
5 -
"No matching provisioning profiles found: No provisioning profiles matching an applicable signing identity were found."
FUCK YOU APPLE!!!!! I've update it a thousand times mother fucker!!1 -
Why do I even go back to https://www.theverge.com/ ? Why ?
So, I quote :
"Sandra L., who also requested that I withhold her surname, used Examity for a midterm in her astronomy class at Ocean County College in New Jersey"
How many Sandras in astronomy classes do you think they have at Ocean County College in New Jersey?
"We protect identity of sources"5 -
This happened towards the end of a data archival project I was involved in.
It was the last day of the project and we were in the process of handing over the system to the client. As it so happened, the client, while doing a sanity check, found out that some unwanted data had not been deleted from the database.
On project manager said to us, "Let's delete the unwanted records manually."
The only problem. There were three of us and over 150000 entries to delete (the system had around ten years of data).
In the end, we came up with a logic to identity the unwanted records, and I created a small program to delete the entries using this logic.
To this day it is still not clear as to what inspired the PM to come up with such a suggestion. -
Still remember the first time I started writing style sheets, the biggest confusion was why do they use an id where we can always use a class.
Now I know why. Only you are your identity, but there may be many people of the same class. :)2 -
Turns out you can treat a a function mapping parameters to outputs as a product that acts as a *scaling* of continuous inputs to outputs, and that this sits somewhere between neural nets and regression trees.
Well thats what I did, and the MAE (or error) of this works out to about ~0.5%, half a percentage point. Did training and a little validation, but the training set is only 2.5k samples, so it may just be overfitting.
The idea is you have X, y, and z.
z is your parameters. And for every row in y, you have an entry in z. You then try to find a set of z such that the product, multiplied by the value of yi, yields the corresponding value at Xi.
Naturally I gave it the ridiculous name of a 'zcombiner'.
Well, fucking turns out, this beautiful bastard of a paper just dropped in my lap, and its been around since 2020:
https://mimuw.edu.pl/~bojan/papers/...
which does the exact god damn thing.
I mean they did't realize it applies to ML, but its the same fucking math I did.
z is the monoid that finds some identity that creates an isomorphism between all the elements of all the rows of y, and all the elements of all the indexes of X.
And I just got to say it feels good. -
Hey everyone.. I am a Graphic and Web Designer plus developer and I am going to create brand identity for myself but I am looking for something creative and good names. I like something like GraphicOwl or GeekyOwl.. Also suggest a slogan or tagline.7
-
#justAthought
I was reading about public and private keys yesterday, and i had a thought: don't you think the concept of "username" is being so badly misused?
It can act as a great firewall, but we are just misusing it as an alternative to "login via email", because we are now so dumb to remember our email.
You might think of my rant as being going back in time, but think about this: my profile shows the name titanlannister. if someone got access to my password, he/she can immediately take over my complete identity because devrant allows us to login via username/password combo.
Now think of this: my username shows titanlannister. Anyone of you can write a post and mention me via @titanlannister, and this system will notify me. However even if you get my password, you are unable to hack into my profile, because my profile is only accessible via my email id/password combo, which you still don't know.
This, I would call as Platform Public Key which adds a kind of semi firewall over default public/private key combination .
What do you think?5 -
man you can tell some of these course selling companies are poorly managed (or rather, perhaps NOT managed) when you have to do the same thing over and over again for over TWO YEARS
HELLOOOOO WHAT ARE YOU DOING... PLEASE PUBLISH MY COURSE NOW
if i'd put the damn thing on Udemy when it was done i'd already be 2-3K richer
...damn, i gotta taper off here with the rage before i reveal my identity at 10K
🤡🤡🤡🤡6 -
Authentication and Identity management are just one giant shit fuck.
Ldap, PAM, OAuth and what not.
Each of them with it's own caveats.
Ldap, supposedly being the most widely used, isn't even an actual Identity management or authentication service, but just a DB misused as one.
The best part is, that if you want to selfhost some apps, you're pretty much forced to host one of these abominations too.
At least if you don't want to manage each service account's separately.6 -
It's been awhile, for the heads up I'm that good dude applied a job as MIS few months ago, knows a little bit python and the manager finds out, he told me I gotta make a Warehouse Management Software for the company in C# PLUS MIS regular work(server management, user trouble-shooting and stuff).
after I finish my Warehouse Management Software about a week ago, my manager told me which I quote:
"wpf is not enough! we gonna bring it to multi platform like a web interface can be use on employee's phone as barcode reader and do things can be done as wpf can.
aaaaand we need RFID integration for the whole system working with Identity Server on Azure.
AAAAAAND we need it online before Feb 2020."
I guess after C#,
I'm learning typescript and angular now.
oh by the way my position is MIS with MIS salary.
Does this means after all these shits. I can apply as RD my next job right?2 -
I'm about to submit an app to the App Store. I took some time to make sure signing in/out of different social media accounts worked properly in my app.
I've been locked out of my Facebook developer account since yesterday due to "suspicious activity" and was asked to upload a photo of myself to verify my identity. I'm not too confident my account will be unlocked as I don't use Facebook regularly and therefore never felt the need to upload a profile picture.
Fantastic.2 -
If you don't have
1. Chronic depression.
2. Episodes of pure mania.
3. Low self esteem.
4. Superiority complex.
5. Drugs/Pills dependency.
6. Identity crisis.
7. Mind numbing migraines.
8. Carpal tunnel.
all of the above at the same time, can u even call yourself a software developer?11 -
Well fuck. I am experiencing over-engineering first hand.
I am the single dev responsible for developing a small feature but which is an identity to our whole product(feel free to guess it here). This is quite simple I thought, I can just modify the constants which are being used in the source code and I can finish it off in a week tops. I asked all the relevant teams over which this feature would have dependencies and they gave me a green signal. Setup Jenkins configuration and everything for this new feature. With a wide grin on my face, I sent out a pull request. Now the architect of our product declined the pr saying to change everything from the bottom up giving the reason that it would be configurable sometime later in the future. Now mind you, I get it if this feature could change over time and needs customability. But it has been the same since last seven years and would probably not change again for a couple of years ahead [you have to take my word for it.]. Its not that the guy is a douche or anything, he is one of the best dev I have ever personally came across and I highly respect and admire him. But there has to be a trade off between the effort you are putting in versus the benefit you get. Now I have to touch almost every file, super carefully look in the whole product if a bug creeps out from anywhere and change the existing code to a point where it doesn't even make sense to me anymore, and write tests ofcourse.
wubba lubba dub dub!2 -
Developers more than other groups tend to hold their operating system or programming language of choice dearly, to the point where if someone thinks poorly of the OS or Language, they take it like a personal attack. Then there are those who think poorly of people who who's a certain OS or a specific language. Combine the two and you get hurt feelings and identity crisis.
Can we all just agree that we're all in different stages of learning and that we all generally end up going the same direction for the same types of problems?
Or just have it out and kill each other over it. Will give me great rant material.3 -
Just saw an article about a failing attempt at the UK to create a nationwide parking app.
Mostly because the many, *many* parking meter app operators in different markets don't want a single, interoperable standard.
But, there is one all of them must support or stop working entirely.
It is the "room temperature at sea level" standard for any western user interface: point and click, text input, English UI text.
Can't AI be a front-end for that?
This is also a rant about AI. There are sooo fucking many modules for siri or Alexa to be compatible with apps like uber or Spotify. Uh, why? Shouldn't the AI, that claims to he capable of recognizing images and text, just open the app and click on the right buttons?
I know why siri and Alexa and Google assistant and and chatgpt aren't capable of that - because it would free users from UX lock-in, and the corporate overlords would rather shut down the entire fucking internet.
But now with DeepSeek and other open-source moderately useful LLMs, could we finally be nearing the day when we can ditch the millions of marginally different apps and let the AI take over the piloting of their redundant GUIs?
Because then, even if app vendors don't want to work together and end up fucking up the aggregate UX for every smartphone user, we can just flip them the bird and let the AI blur their entire brand identity in the background of a "please wait while I operate some second-page apps to realize your request" message.2 -
Got a scammer on my hook. Ideas welcome to fuck him/her over.
He/she confused me with someone else and messaged me acting as a support person of an exchange. I acted along and s/he is insisting on sharing account details.
Played along like a dumb internet noob and I think I got him to share his fake email id.
Now I'm thinking of ways to extract more details about him via email.
From top of my mind, these are some ideas I have:
- get his IP address
- zip bomb or something like that? But g mail is probably gonna detect that.
Ideally, If I could social engineer him to give his phone number, I could easily report him to police and find his identity.
Have you busted some scammers? Would appreciate some tips.6 -
TL;DR: FFS Microsoft
So yesterday we were at the point in our project where adding a login system seemed like a good idea. This is an asp.net core mvc project and we use Materialize for our frontend.
So according to _the tutorials_ we could start a new project and add authentication in the prompt by pressing a button. As it created the project I thought it seemed nice and easy enough. After it had created the test solution I build it and, sure enough, in the top right corner there were a register and login <a>.
I checked them out and they were your bog standard form input input submit and all. Now I guessed I could look at how it's all programmed aaaaaaaaand
Nope.
I saw a new folder located at Areas/Identity/Pages which had a _ViewStart.cshtml which contained three lines. There were also a database migration and in Startup.cs there were some database stuff, but other than that? Nothing. So where on earth was the login and register form located? Shit like that is frustrating ya know.
But oh well it seemed to work and I switched to our examn project where I found it was possible to scaffold the login system in a way that seemed nice.
Except, for some reason bootstrap and jquery decided to return to our project. FFS Microsoft!1 -
Hello Apple,
Fuck you, more than a month trying to open a developer account without any chance, lot of fucking emails.
Lesson 1:
If you’re from a country and put a phone number from another country you will never be able to open a developer account? How did I know that? From my experience and many other people, but Apple just says: Error, that’s it you figure it out !
Lesson 2:
If you pay using a card on which the name is different than the name in the developer account, you have to wait longer and provide more documents. How did I know that? After fucking 5 tickets and more emails asking why my account is not ready yet, then they answered they need a document to verify my identity. If you don’t do that you will just rot waiting.
Lesson 3:
If they need an ID document, you have to email them first and ask why you’re account is not available yet, if you don’t you will just rot waiting. -
A step aside from one of the answers I ever gave on Stack Overflow, I notice I once made a "jsfiddle".
Already some annoyances...
• When did browsers, uh webkit, decide to fuck every "ul", "menu", and "dir" element with a "-webkit-padding-start" of 40 damn pixels?
• That friggin' fiddly webshite doesn't even force me to HTTPS, bro. Need a reason to fuck yourself in the vulnerable ass?
• Why is it that I can't log in with my tiny four-letter nickname; you identity-fuckers?
-
I said and will say again (over and over) Microsoft WTF!
Set-CalendarProcessing -Identity $userUpn -AutomateProcessing AutoAccept -AllowConflicts $false -BookingType 'Standard' -BookingWindowInDays 365 -MaximumDurationInMinutes 1440 -AllowRecurringMeetings $true -EnforceSchedulingHorizon $false -ScheduleOnlyDuringWorkHours $false -ConflictPercentageAllowed 0 -MaximumConflictInstances 0 -ForwardRequestsToDelegates $true -DeleteAttachments $true -DeleteComments $true -RemovePrivateProperty $true -DeleteSubject $true -AddOrganizerToSubject $true -DeleteNonCalendarItems $true -TentativePendingApproval $true-EnableResponseDetails $true -OrganizerInfo $true -AllRequestOutOfPolicy $false -AllBookInPolicy $true -AllRequestInPolicy $true -RemoveOldMeetingMessages $true -AddNewRequestsTentatively $true -ProcessExternalMeetingMessages $false -RemoveForwardedMeetingNotifications $true
ok I "splatted" that command but yet does not look much better :-)
Oh how I miss my dear old VIm and SSH sessions can't wait to go back to where I belong! 4
4 -
Developers !
I need fast advice!
If i want to have a domain like instagram e.g.
domain.com/first-lastname1
domain.com/first-lastname2
domain.com/first-lastname3
...
What is the best way to define those routes? I am using only angular. Its just a landing page so no backend frameworks are needed or used.
So if i have about 50 first-last names (and i might add even a lot more), is it a good idea to create 50 different components in angular where each component links to the different person identity of those /first-lastnameN routes?
Or should i have only 1 component and loop through names from a list and display them somehow? Because i dont know how to do this way And change the URL route into a different name7 -
Last week summary:
-questioning my identity (I’m cleaning and realised I forgot I used to like many activities I forgot and decided to give them more time)
-questioning how tf my unconscious seems to always plan ahead of me (ah yes I can do this cause I prep… why tf did I prepare for this?)
-questioning my skills (just a standard imposter syndrome, nothing to see here, move on)
-questioning my worth (as above)
-questioning how tf somebody connected to a secret account I have (spoiler: they don’t know and it’s a crazy coincidence… but now I know secrets about them 😏)
-randomly freezing during everyday life for all the above points
Job wise all is cool, tho 🎊2 -
Apparently I'm now a suspect in a criminal case. I would have commited identity theft between 2007 and 2025.
Except no, I didn't lmao I'd be richer.4 -
Fucking hell. So, I had an interview with market research company and in said interview I got told to bring my passport to my first shift training and it was ok if it was 5 years out of date. Additional info, they were supposed to call us on Thursday to book said shift and send us an email with a information pack. They never did.
Ok, day of shift comes along. After I booked it because no one fucking bothered to call any of us. Email never arrived but whatever. I go to the place and bring my 3 years out of date polish passport... Big fucking mistake. They don't seem to like polish passport seeing as how it's only the British ones that get the out of date is okay thing. So I'm sitting there still calm because sure, company policy, they have to do it. The training guy was nice and all, offered to get me to their office to speak to them about it. I accept and off we go.
At the office, I basically get the information that it's only British passports that get it and I basically can't use anything else as proof of ID, which is funny seeing as I have a polish identity card that I can leave and enter the country on within the EU. I suppose I'm going to try looking for a job that doesn't require passports for now and if I find a good one then they can go get fucked by a bull for all I care.
In conclusion, I get to wait till I'm 18 (thankfully only a month) to apply for a new passport in the local polish consulate. Brilliant. All thanks to some cunt that decided they require fucking passports with such beautiful (note the sarcasm) rules. The fucktards.
Hoping the apocalypse comes early for these cocksuckers,
BadFox -
It has to be Keybase.
It is exactly what I need - A secure yet practical cloud storage, where only you own the crypto key, with the added bonus of maintaining a blockchain-based identity online, with proof system and all.
Also has a secure PKI-Based E2E chat when I want to talk to someone about something I don't want the general government to necessarily know.
Definitely recommend the service! Even with the odd decision to include an option of a Lumen crypto wallet or whatever, you can just ignore that feature if you're not into it and it doesn't slow you down.2 -
Tryna search for my new self inspired sexiest domain name if available but the fucking page keeps bringing up that fucking recaptcha asking me for some fucking description about some fucking cars, fucking roads, fucking bridges, dunno if that was my fucking business!
I want you to stop asking me shitty questions cause i'm a fucking robot. Hence i wrote a script that would change the typo from "i'm not a robot" to "i'm a f*cking robot" any time i visit any fucking page requesting for my fucking identity!
Fuck Google!, Fuck Recaptcha!, Fuck Hostgator! Fuck Security! Fuck them all!!! 2
2 -
[CONCEITED RANT]
I'm frustrated than I'm better tha 99% programmers I ever worked with.
Yes, it might sound so conceited.
I Work mainly with C#/.NET Ecosystem as fullstack dev (so also sql, backend, frontend etc), but I'm also forced to use that abhorrent horror that is js and angular.
I write readable code, I write easy code that works and rarely, RARELY causes any problem, The only fancy stuff I do is using new language features that come up with new C# versions, that in latest version were mostly syntactic sugar to make code shorter/more readable/easier.
People I have ever worked with (lot of) mostly try to overdo, overengineer, overcomplicate code, subdivide into methods when not needed fragmenting code and putting tons of variables.
People only needed me to explain my code when the codebase was huge (200K+ lines mostly written by me) of big so they don't have to spend hours to understand what's going on, or, if the customer requested a new technology to explain such new technology so they don't have to study it (which is perfectly understandable). (for example it happened that I was forced to use Devexpress package because they wanted to port a huge application from .NET 4.5 to .NET 8 and rewriting the whole devexpress logic had a HUGE impact on costs so I explained thoroughly and supported during developement because they didn't knew devexpress).
I don't write genius code or clevel tricks and patterns. My code works, doesn't create memory leaks or slowness and mostly works when doing unit tests at first run. Of course I also put bugs and everything, but that's part of the process.
THe point is that other people makes unreadable code, and when they pass code around you hear rising chaos, people cursing "WTF this even means, why he put that here, what the heck this is even supposed to do", you got the drill. And this happens when I read everyone code too.
But it doesn't happens the opposite. My code is often readable because I do code triple backflips only on personal projects because I don't have to explain anyone and I can learn new things and new coding styles.
Instead, people want to impress at work, and this results in unintelligible, chaotic code, full of bugs and that people can't read. They want to mix in the coolest technologies because they feel their virtual penis growing to showoff that they are latest bleeding edge technology experts and all.
They want to experiment on business code at the expense of all the other poor devils who will have to manage it.
Heck, I even worked with a few Microsoft MVPs.
Those are deadly. They're superfast code throughput people that combine lot of stuff.
THen they leave at you the problems once they leave.
This MVP guy on a big project for paperworks digital acquisiton for a big company did this huge project I got called to work in, which consited in a backend and a frontend web portal, and pushed at all costs to put in the middle another CDN web project and another Identity Server project to both do Caching with the cdn "to make it faster" and identity server for SSO (Single sign on).
We had to deal with gruesome work to deal with browser poor caching management and when he left, the SSO server started to loop after authentication at random intervals and I had to solve that stuff he put in with days of debugging that nasty stuff he did.
People definitely can't code, except me.
They have this "first of the class syndrome" which goes to the extent that their skill allows them to and try to do code backflips when they can't even do code pushups, to put them in a physical exercise parallelism.
And most people is like this. They will deny and won't admit, they believe they're good at it, but in reality they aren't.
There is some genius out there that does revoluitionary code and maybe needs to do horrible code to do amazing stuff, and that's ok. And there is also few people like me, with which you can work and produce great stuff.
I found one colleague like this and we had a $800.000 (yes, 800k) project in .NET Technology, which consisted in the renewal of 56 webservices and 3 web portals and 2 Winforms applications for our country main railway transport system. We worked in 2 on it, with a PM from the railway company.
It was estimated 14 months of work and we took 11 and all was working wonders. We had ton of fun doing it because also their PM was a cool guy and we did an awesome project and codebase was a jewel. The difficult thing you couldn't grasp if you read the code is if you don't know how railway systems work and that's the only difficult thing.
Sight, there people is macking me sick of this job11 -
Literally facepalm when seeing my company coding used Email as an identity to retrieve profile data etc. Yet the profile is allow user to interchange their email.
What is this kind sorcery is this? Why don't just plainly use the UID to retrieve profile instead, as simple as that. Is UNIQUE!!!
😒😒😒 F5 -
Is there anything like React Context or Unix envvars in any functional language?
Not global mutable state, but variables with a global identity that I can set to a value for the duration of a function call to influence the behavior of all deeply nested functions that reference the same variable without having to acknowledge them.11 -
Well, this may out my secret identity to devRanters in my area, but I just submitted my first application ever to be a speaker at a local WordPress conference. The title is "The Care and Feeding of Your Web Developer". If you have a wishlist of how you wish working with employers or clients could be better, please comment and I'll work it into my talk. Thanks!
-
I got a SIM card activated for my dad yesterday. Here in SA you need to verify your identity to get the card activated. But the company's systems were offline yesterday while I got it from another distributor of theirs 2 shops over. Now a day later they tell me I have to go and get another one because the one I got won't be activated because of it being offline. Something about it being assigned to me while it is offline makes it not work.
WHAT BULLSHIT? WHO THE HELL CODES THAT TRIPE TO FAIL TWICE AS HARD AS IT SHOULD? IT MAKES NO SENSE IF THE THING IS OFFLINE FOR THIS TO HAPPEN.
And yet, with Telkom's legendary poor service I know the service people are not lying. They just don't know what the hell is going on. -
The SIM card saga goes on:
To verify yourself, you need to go to some postal office and show them your ID and stuff. Not that this is complicated or anything (well actually, it is. Welcome to 2018 in Germany. We use more papers than potheads for the simplest shit), but you need to have a valid ID. Valid as in NOT EXPIRED. What the fuck. Why does my ID expire. Do I stop existing 3 years after getting it? What does it mean if it is, why is it culpable to have your ID expired. And who gets charged for having none, I mean obviously my ID doesn't identify me anymore?
What the hell man. I don't exist for 6 months now. Am I law free as not identifiable entity or how does it work?
And now the real question:
We got something called Bafög in Germany. Basically you get a bit money while studying. (I still work tho, I don't get really much from it.)
To apply for it, you need some tax number, which seemingly can be seen as a proof of my existence and my identity.
Why is this enough, why don't I need a valid ID there?
Germany is weird man. On the one hand government is all social and you get help if you need it but on the other hand you need to sacrifice 17 virigins to apply for said help..2 -
!rant
This is fucking how you do it!
Ticketmaster UK had a "data security incident" where they don't really know if any data was actually leaked/stolen/"accessed by an unknown third-party" — their response:
1. Disable the compromised service across their platforms
2. Send a mail to any customer that may have been affected (I got one in Danish because I had only interacted with them through a Danish subsidiary)
2b. All notified customers have their passwords reset and must go through the "Forgot password" process; the _temporary_ password they sent me was even pretty nicely random looking: ";~e&+oVX1RQOA`BNe4"
3. Do forensics and security reviews to understand how the data was compromised
3b. Take contact to relevant authorities, credit card companies, and banks
4. Establish a dedicated website (https://security.ticketmaster.co.uk/...) to explain the incident and answer customer questions
5. "We are offering impacted customers a free 12 month identity monitoring service with a leading provider. To request this service please visit [this page]"
EDIT: As mentioned and sourced in the first comment, the breach was apparently noticed by a banking provider and reported to Ticketmaster on the 12th of April and later to Mastercard on the 19th of April.
Ticketmaster's internal investigation found no evidence of breach (which makes sense, as it wasn't an internal breach), but when Mastercard issued an alert to banks about it on the 21st of June, Ticketmaster followed up by finding the actual breach and disabling the breached third party service on the 23rd of June.
I still think they did the right thing in the right way...2 -
Anyone tried converting speech waveforms to some type of image and then using those as training data for a stable diffusion model?
Hypothetically it should generate "ultrarealistic" waveforms for phonemes, for any given style of voice. The training labels are naturally the words or phonemes themselves, in text format (well, embedding vectors fwiw)
After that it's a matter of testing text-to-image, which should generate the relevant phonemes as images of waveforms (or your given visual representation, however you choose to pack it)
I would have tried this myself but I only have 3gb vram.
Even rudimentary voice generation that produces recognizable words from text input, would be interesting to see implemented and maybe a first for SD.
In other news:
Implementing SQL for an identity explorer. Basically the system generates sets of values for given known identities, and stores the formulas as strings, along with the values.
For any given value test set we can then cross reference to look up equivalent identities. And then we can test if these same identities hold for other test sets of actual variable values. If not, the identity string cam be removed, or gophered elsewhere in the database for further exploration and experimentation.
I'm hoping by doing this, I can somewhat automate the process of finding identities, instead of relying on logs and using the OS built-in text search for test value (which I can then look up in the files that show up, and cross reference the logged equations that produced those values), which I use to find new identities.
I was even considering processing the logs of equations and identities as some form of training data perhaps for a ML system that generates plausible new identities but that's a little outside my reach I think.
Finally, now that I know the new modular function converts semiprimes into numbers with larger factor trees, I'm thinking of writing a visual browser that maps the connections from factor tree to factor tree, making them expandable and collapsible, andallowong adjusting the formula and regenerating trees on the fly.6 -
Complaining about your colleagues on devRant but ending up showing them the app anyway cuz it's so damn awesome..
-
So, Recently I had made a short film "Brazen Epiphany" and I added it to IMDB, I discovered that IMDB has a flawed verification system, they don't actually verify edits. So, I credited myself for acting in various films. And, they got approved. Then one day, a writer of one of those movies discovered this and ranted on Twitter about it
https://twitter.com/varungrover/...
I told him about this whole stuff, Then I was contacted by a journalist amd they published a story on this
https://mumbaimirror.indiatimes.com/...
I know it's pretty lame to give wrong information to a community website, but I enjoyed it5 -
“X” and “Meta” is exactly how a serial killer disguises themselves. Same piece of shit, different identity.
https://mashable.com/article/...3 -
Can we change our username here ? I have choosen a new username for my developer identity but i don't wan't to lose my stats...2
-
https://perplexity.ai/page/... love these articles. Those researchers have too much money to spend anyway. About AI companions, could be very well be true. They're not good enough yet, but I could prefer it as well. They destroyed everything with identity politics and anti human mindset. Not fault of AI. I already prefer internet relationships above real life ones. I had such a busy social life before, it was actually terrible thinking back obout it. I really started to hate society since covid and love my detached life. Some times my parents come over and make me realize that world exist snapping out my peaceful quiet, happy and stable life. Go away with your dystopia. "We are rebuilding the fire place in our house, not the way we want, but in a way the insurance company want so it's practically impossible to get a fire, and then we insure it.". Wraaaaahhhhh. That kinda fucked up logic. I can't stand it. "That's just how it works.". Waaaaaah. Society in a nutshell.
This perplexity news site is a good way to stay up-to-date tho, can read it for hours.11 -
Im not sure if I can put a awk love thing here but it happened at work and this is a rant so here we go:
I told my coworker that I like someone at work and they promised they wouldn't tell a soul. I was trying to work in the kitchen today and this ass ( sorry for swearing but I'm mad) says really loudly OH WHO DO U LIKE HUH IS IT FROM BLAH BLAH COMPANY HUH?
The crush was there and so were his bffs. And they heard.. u could hear this from the north pole all the way to the south pole.. Uranus, mars, IT GOES ON...... I felt so embrassed and had an anxiety attack. And maybe im dramatic but I didn't know how to deal with this situation and I'm a shy person so I was so angry my coworker betrayed my trust and told people and like now people r teasing me. I can't even look at my crush .... I was friends with my crushes bff ... I was too embrassed to say anything.... Sigh
My crush has a partner. It's not right to act IN A PROFESSIONAL ENVIRONMENT PEOPLE.
what do I even do omg. How do I even GO ON FROM HERE.
I NEED A NEW JOB A NEW IDENTITY A NEW LIFE4 -
So in Seahorse (the Gnome secret manager) deleting the OpenSSH key doesn't just remove an identity from agent, it actually deletes the keyfile.
I should've treated that scary confirmation message more seriously.
Also, my obsessive full disk backups every Monday are totally worth the time.2 -
This is how to find the base needed for any integer value p, where p>=5, such that the logarithm always equals e in python.
log(p, e**(log(p, e**e))) # equals e
Doesn't do anything besides that but this is another identity isn't?24 -
If someone finds out my real identity and ties it to my account on here, my life is over. If there is a current concern with profiles being investigated right now please let me know.6
-
What are your personal goto identity management providers?
I am currently looking at Firebase and Auth07 -
Oracle Identity Manger. It just feels soooo unfinished and its just so damn tedious to work with! My god. Should've created the whole thing ourselves instead. The time we've used to fix shit.. #meh
-
"Too often, look and feel, color scheme, layout, and identity are presented as solutions to problems discussed in these conversations long before regard is given to other less-aesthetic issues that may very well be the root of the problem. The old warning against treating symptom rather than cause comes to mind." - Cameron Moll1
-
I wonder when we'll stop the abuse of naming conventions like name & surname, by this I mean not all cultures have a surname but most of us are ignorant about it and those people when they are presented with an obligation to fulfill that field they cannot do it legally, because they'll lie.
A more open approach with only one field for full text identity would solve this issue. -
"If I do my job well, the identity program will also clean up the image of the company, position it as being contemporary and keep it from ever looking dated." - Saul Bass4
-
It has come to my attention that an IRL acquaintance praised my constructive activity in social media, but the only substantial activity I've had for like a year was on DevRant.
I wonder if any of my friends other than Mayank are on here.
Not very worried though, I hardly ever say things about other devs that I couldn't own if they found out.2 -
"If I do my job well, the identity program will also clean up the image of the company, position it as being contemporary and keep it from ever looking dated." - Saul Bass
-
does anyone hate material you?
god damn, it seems so fucking stupid. i don’t want a color scheme on every single app i have. i like, from an app developer and app user’s standpoint, that i can recognize an app by its colors. colors are part of an app’s identity. why not just give users raw access to the apis that apps use. i mean, every messaging app is going to look the same now, every browser and every app that has a similar ui to another.5 -
!ad
Tunnelbear VPN website (https://www.tunnelbear.com/) is one of the most entertaining websites I've seen recently.
I think I visited every link because I want to check if there is something funny. -
How do you deal with multiple git identities?
Im working fulltime + freelancing + working on my own projects and all of them are on different gitlab emails. It was very annoying to keep remembering to set my git email to a proper one each time I switch to work on another project.
Right now I came up with something easier:
I started using just 1 gitlab profile (personal one) and added my both company e-mails as secondary emails to my personal gitlab profile.
This way I can keep my git identity the same (personal e-mail address) and if I push to company1 repo or company2 repo the commit author e-mail addres is shown email@company1.com and email@company2.com as these emails are given access to private repos and they are added to my personal gitlab account.
Just wondering if these companies will see my commits to other repos by viewing my personal gitlab profile or no? Or if there is an easier way to handle multiple git identities without having to switch between them each time I open another project and want to push some commits.7 -
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
So in my groups project where we use ASP.NET Core MVC where we've needed to add identity. Now I've struggled with this soooo much only for today to get it to work.
The documentation for it (more specifically user roles) isn't very good, and most tutorials basically just do the same thing which has for me thrown exceptions left and right (and I don't even do anything special tbh) without any explanations. But today I finally got it to work, I can seed the database without getting told that there are no service for the RoleManager
and
it
feels
like
this
https://youtube.com/watch/...rant it literally feels like hardbass asp.net core mvc now it does dopamine levels high aaaaaaaaa it didn't work askjdfhasdjh1 -
is this what they call an identity?
log(n, n**(1/n)) == n
first argument in log is the value
second argument is the base10 -
If we can transform the search space or properties of a product into a graph problem
we could possibly use Kirchhoff's theorem to reveal products which are 'low complexity'
in particular search spaces, yeah?
Now according to
https://en.wikipedia.org/wiki/...
"n Cycle Space, A family of sets closed under the symmetric difference operation can be described algebraically as a vector space over the two-element finite field Z 2 {\displaystyle \mathbb {Z} _{2}} \mathbb{Z } _{2}.[4] This field has two elements, 0 and 1, and its addition and multiplication operations can be described as the familiar addition and multiplication of integers, taken modulo 2"
Wouldn't this relate to pollards algorithm, because it involves looking for factors of coprimes modulo N or am I mistaken?
Now, according to wikipedia, "in a group, the additive identity is the identity element of the group, is often denoted 0, and is unique."
If we make the multiplicative identity of our ring or field a tuple of the ratio of a/b for some product p, or a (and a/w, where w is the square root of p), or any other set such that n*m allows us to derive a or b, we could reduce the additive identity to the multiplicative identity, making the ring trivial. Solving for p would then mean finding a function from R to R, mapping every number to 0, i.e. finding the additive identity.
Now in a system with a multiplication operation the distributes over addition, the "additive
identity annihilates ring elements", so naturally, the function that maps to 0, gives us
our additive identity, we need only find the subset, no?
Forgive me if I'm wrong, but shouldn't this be convertible to a graph search?
I'm WAY out of my depth here so if anyone is familiar and can enlighten me I'd be grateful.
It's all unknown unknowns to me. -
Amusing vim/neovim newbie beatdown story. I am mostly enjoying it, so please don't take it too personally, as I'm 60% having fun, 30% looking for help, and only 10% attacking your fundamental identity and way of life
#1 uses left and right arrows to move the selection up and down, and down and up arrows to move the selection into and out of tree elements
#2 uses tab and shift tab to move the selection up and down, but has great filtering
#3 uses up and down arrows to move the selection up and down, and enter and esc to move the selection into and out of tree elements.
I get that I have just frantically cobbled various things together to make it work but man, there's something to be said about the I in IDE... 5
5 -
I'm feeling stupid because I have a hard time understanding ASP.NET core identity togheter with OpenIdDict server... ARGGGHHh2
-
How does LinkedIn differ from a traditional resume?
LinkedIn differs from a traditional resume in that it is an online professional networking platform rather than a static document. While a resume is a concise summary of one's work experience, skills, and education, LinkedIn provides a dynamic and interactive space for professionals to showcase their achievements, connect with others, join groups, and share updates. LinkedIn also allows for recommendations and endorsements ( https://careerbands.com/how-to-writ..., fostering a more comprehensive and real-time representation of a person's professional identity compared to a traditional resume.2 -
Top Web Designing Services in Delhi | Professional & Affordable
"Are you searching for the most reliable and creative web designing services in Delhi to boost your online presence? At Digiwibe, we specialize in delivering professional and affordable web designing services in Delhi that cater to businesses of all sizes. In today’s fast-paced digital world, a visually appealing and user-friendly website is more than just a necessity—it’s a powerful tool to attract customers, build brand credibility, and drive business growth.
At Digiwibe, we understand that your website is often the first impression potential customers have of your brand. That’s why our team of expert web designers focuses on creating websites that are not only visually stunning but also highly functional and optimized for performance. Our web designing services in Delhi are tailored to meet your specific needs, whether you require a simple portfolio site, a dynamic corporate website, or a fully integrated e-commerce platform.
We believe that great web design is a perfect blend of creativity, technology, and strategy. Our designers use the latest tools, design trends, and coding standards to craft websites that are responsive, SEO-friendly, and fast-loading. With a mobile-first approach, we ensure your site looks perfect on all devices, offering seamless user experiences that keep visitors engaged and encourage conversions.
One of the reasons businesses trust Digiwibe for their web designing services in Delhi is our commitment to excellence and attention to detail. From intuitive navigation and impactful visuals to strong calls-to-action and optimized page structures, every element of your website is designed to enhance user engagement and improve search engine rankings.
Moreover, we understand that every business has a unique identity, which is why our design process is highly collaborative. We take the time to understand your goals, brand voice, and target audience before translating your vision into a digital reality. Our team works closely with you throughout the process, ensuring the final product aligns perfectly with your expectations.
Affordability is another key reason why clients choose us. We offer cost-effective web designing services in Delhi without compromising on quality. Whether you’re a startup looking for a fresh online presence or an established business needing a website revamp, we provide scalable solutions that grow with your business.
So, if you’re ready to stand out in the digital space, partner with Digiwibe for high-quality web designing services in Delhi. Let’s create a website that not only looks great but also drives real results. Get in touch with us today and take the first step towards building a stronger online presence!"3 -
I HIGHLY RECOMEND ADWARE RECOVERY SPECIALIST AS THE BEST IN ALL FORM OF SCAMED RECOVERY
I cannot express how distraught I was when I realized someone had hacked my email and was conning my family and friends on Instagram to invest with me. The hacker was using my identity to lure them into a fraudulent investment scheme, and by the time we discovered what was happening, some of my family members and friends had fallen for it. They ended up wiring the fraudsters a total of $25,000 before they realized it wasn't me. The emotional and financial impact was devastating. Call or text: +18186265941 I felt helpless and violated, knowing that someone was using my name to deceive the people I care about the most. It was during this period of turmoil that a close friend told me about ADWARE RECOVERY SPECIALIST. She had been through a similar ordeal and had used their services to regain control of her digital life. Desperate for a solution, I reached out to the ADWARE RECOVERY SPECIALIST team. From the very first contact, they were understanding and professional. They explained the steps they would take to track down my email account, recover it, and secure it, along with my Instagram and other social media accounts. The process was thorough and efficient. The team at ADWARE RECOVERY SPECIALIST used their expertise to identify the breach points and secure my accounts against future attacks. They provided clear instructions on how to enhance my online security and even offered tips on maintaining privacy in the digital age. Within a few days, my email and social media accounts were back under my control. The relief was immense. Knowing that my accounts were secure and that the fraudsters no longer had access to them lifted a huge weight off my shoulders. My family and friends also felt reassured, seeing the proactive steps I was taking to prevent this from happening again. If you ever find yourself in a situation where your digital security is compromised, I highly recommend reaching out to ADWARE RECOVERY SPECIALIST. Their team is not only skilled in recovering and securing accounts but also empathetic to the distress such incidents cause. They offer a comprehensive solution to safeguard your digital presence, giving you peace of mind in a world where online threats are increasingly common. Don't wait until it's too late. Protect your digital life with ADWARE RECOVERY SPECIALIST and ensure that your personal information remains safe from those who seek to exploit it.
-
I never imagined I would fall victim to an online scam, but that’s exactly what happened. It started innocently enough. I was on a popular social media platform, browsing through posts when I received a direct message from someone claiming to be a “financial expert.” Their pitch seemed solid, and their promises of quick returns on investments seemed too good to pass up. I did my research—or so I thought—but it wasn’t long before my trust led me into a trap. I made an initial deposit to start the investment, and things moved quickly. The first few days were filled with regular updates and even small returns, which convinced me that I was onto something big. But then, the messages started to change. The returns began to slow down, and when I tried to withdraw my funds, I couldn’t get a response. Panic set in as I realized I’d been scammed. i had lost a significant amount of money, and to make matters worse, the scammers had control over my personal details, including access to some of my financial accounts. Desperate for a solution, I turned to Alpha Spy Nest, a cybersecurity service I had heard of through a friend.From the moment I contacted Alpha Spy Nest, I knew I had made the right choice. They took swift action, immediately conducting a thorough investigation into my digital accounts. They discovered that the scammer had used several techniques to track my online activity, intercept communications, and even mimic legitimate financial websites. Alpha Spy Nest’s team of experts worked tirelessly to gather evidence, trace the scammer’s digital footprint, and recover my lost funds.But it didn’t stop there. Alpha Spy Nest helped me secure my online presence by identifying vulnerabilities in my accounts and recommending tools to fortify my digital defenses. They guided me through implementing multi-factor authentication, strengthened my passwords, and even educated me on how to spot future scams.Within days, they were able to trace the scammer’s digital identity, and with the evidence they provided, law enforcement was able to step in. I regained access to my financial accounts and received a refund of the funds that were stolen, though the emotional toll remained.The experience left me shaken, but Alpha Spy Nest’s professional and supportive team helped me not only reclaim my wealth but also regain my peace of mind. Now, I’m more cautious online, but I know I have the right tools and the right support if anything ever happens again.Thanks to Alpha Spy Nest, I’m no longer a victim. I’m a survivor. You can also reach out to them WhatsApp: +14159714490
 1
1 -
DIGITAL TECH GUARD RECOVERY SPECIALIZES LOST OR STOLEN CRYPTOCURRENCY ASSETS.
WhatsApp: +1 (443) 859 - 2886
Email @ digital tech guard . com
Telegram: digital tech guard recovery . com
Website link: digital tech guard . com
Last month, I received a terrifying letter labeled “Urgent IRS Notice,” threatening penalties and legal action unless I paid a “back tax” of 12 Bitcoin (BTC)valued at nearly $800,000 via a Houston-based “Crypto Compliance Portal.” The letter mimicked IRS branding flawlessly, complete with official logos, case numbers, and citations of tax codes. However, my skepticism grew when I noticed the demand for cryptocurrency, a method the IRS explicitly avoids. Despite doubts, panic pushed me to transfer the BTC. Moments later, the portal vanished, leaving me in shock. Realizing I’d been scammed, I frantically searched for solutions and discovered DIGITAL TECH GUARD RECOVERY, a firm renowned for combating crypto fraud. DIGITAL TECH GUARD RECOVERY became my anchor. Their team swiftly dissected the spoofed IRS letter and the fraudulent portal, pinpointing inconsistencies: grammatical errors, mismatched tax codes, and a Houston P.O. Box unaffiliated with the IRS. But their breakthrough came through blockchain forensics. DIGITAL TECH GUARD RECOVERY traced my stolen BTC across a convoluted network of wallets, exposing a transnational scheme. The Houston portal, though masquerading as local, funneled funds through offshore mixers and shell exchanges. Crucially, the scammers made a fatal error: a portion of the BTC briefly passed through a U.S.-regulated exchange with weak identity checks. DIGITAL TECH GUARD RECOVERY seized this vulnerability, collaborating with the FBI’s Cyber Division and IRS Criminal Investigation unit to freeze the assets under federal forfeiture laws. Their relentless advocacy ensured my case was prioritized, as they proved the criminals exploited U.S. financial systems. Within weeks, DIGITAL TECH GUARD RECOVERY achieved the unthinkable: 100% of my BTC was recovered. They navigated legal complexities, coordinated with prosecutors, and even educated me on scam tactics. “Fraudsters weaponize fear to bypass logic,” a DIGITAL TECH GUARD RECOVERY investigator explained, emphasizing how urgency clouds judgment. Their insights transformed my understanding of red flags, such as threats of immediate arrest or demands for irreversible payments. Today, I owe my financial survival to DIGITAL TECH GUARD RECOVERY. Their technical prowess, legal partnerships, and unwavering support turned catastrophe into a cautionary triumph. While I hope others never endure such a crisis, my message is clear: If faced with crypto fraud, DIGITAL TECH GUARD RECOVERY is the ally you need. Their name became my beacon of hope, proving that even in blockchain’s seemingly irreversible realm, skilled defenders can rewrite the narrative. Stay vigilant, verify relentlessly, and remember with DIGITAL TECH GUARD RECOVERY, recovery is possible.2 -
UPVC Painting Ltdrant doors upvc spray painting our tailored solutions deliver flawless we pride ourselves on attention to detail efficient service address: 48a warwick street upvc window painting or matching your brand identity modernising your colour scheme upvc door painting property renovation department london4
-
Integrating Netlify Identity into a modern app.
You'll think for such a tool, that it will have up-to-date examples and guides. And that once someone logs in, they're redirected to whatever route they were on instead of being stuck on the "Logged in as ..." modal?
But no, it's several years behind. -
REACH OUT TO A POTENTIAL BITCOIN/USDT/ETH RECOVERY EXPERT- HIRE SPARTAN TECH GROUP RETRIEVAL
As a freelancer and part-time cryptocurrency trader, I had built up over $200,000 worth of Bitcoin in my digital wallet. What began as a casual interest in cryptocurrency quickly turned into a profitable venture, helping me cover tuition and living expenses. However, a seemingly small accident during a family holiday in the Maldives nearly led to a catastrophic financial loss. One afternoon, while soaking in the picturesque beauty of the Maldives, I decided to take a selfie to capture the moment. In my excitement, my phone slipped from my hands and shattered on the pavement below. At first, I was upset about losing my device, but soon, a far more alarming realization hit me. I had also lost access to my Bitcoin wallet. My recovery phrase, the key to restoring my funds, had not been stored in a secure location, leaving me with no way to retrieve my wallet. Panic set in as I considered the possibility of losing years of earnings and investments. Determined to find a solution, I began scouring the internet for any service that could help. That was when I came across SPARTAN TECH GROUP RETRIEVAL. Although skeptical about the chances of success, I had nothing to lose, so I reached out to their team on WhatsApp:+1 (971) 4 8 7 -3 5 3 8, explaining my predicament in detail. To my relief, they responded promptly and professionally, assuring me they had the expertise to attempt a recovery. They explained the process clearly, starting with verifying my identity and wallet ownership. Once those steps were completed, their team immediately got to work. Despite the challenges posed by my shattered device and the missing recovery phrase, SPARTAN TECH GROUP RETRIEVAL team demonstrated exceptional skill and persistence. Within just a few days, they successfully recovered my wallet and restored access to my funds. The relief and gratitude I felt were indescribable. This incident was a wake-up call. Beyond recovering my funds, SPARTAN TECH GROUP RETRIEVAL took the time to educate me on the importance of proper security measures. They stressed the need to store recovery phrases in secure offline locations, use hardware wallets, and implement two-factor authentication to safeguard assets against loss or theft. Thanks to SPARTAN TECH GROUP RETRIEVAL, I was able to avoid a disastrous financial setback. Their professionalism, expertise, and guidance not only saved my investment but also prepared me to navigate the crypto world more securely in the future.
INFO ABOUT THE COMPANY>>>> >>
Email : spartantech (@) c y b e r s e r v i c e s . c o m
Telegram:+1 (581) 2 8 6 - 8 0 9 2 3
3 -
ARE YOU HAVING ISSUES WITH INVESTMENT SCAM HIRE→( FOLKWIN EXPERT RECOVERY ) FOR FAST RECOVERY.
In Stockholm, I found myself immersed in the dynamic world of cryptocurrency after attending a local networking event. The energy in the room was palpable, filled with enthusiasts and experts discussing blockchain technology and the potential for financial independence. Captivated by the conversations, I decided to take a leap and invest 9,000 SEK in Cardanol, a cryptocurrency I had been researching for some time. To my surprise, my investment quickly gained momentum, skyrocketing to an impressive 200,000 SEK within just a few months. It was exhilarating to watch my investment grow, and I felt a mix of excitement and disbelief. Cardanol's innovative approach and promising technology had captured the attention of investors worldwide, and I was thrilled to be a part of that journey. However, the euphoria was short-lived. After a heated disagreement with another investor at a meetup, tensions escalated. This individual, feeling wronged, took the drastic step of locking me out of my email account. The loss was devastating—not only was I cut off from my primary communication channel, but I also lost access to crucial accounts tied to my investments. Panic set in as I realized the implications of being locked out of my email, especially with such a significant amount of money at stake. In those anxious moments, I turned to my network for support. Friends and fellow investors rallied around me, offering advice and sharing their own experiences. It was reassuring to know I wasn’t alone in this challenging situation. Several contacts recommended FOLKWIN E X P E R T RECOVERY, a service that specialized in reclaiming access to locked accounts. With their guidance, I reached out to FOLKWIN E X P E R T RECOVERY, hoping they could help me regain control. The team at FOLKWIN E X P E R T RECOVERY was professional and understanding. They walked me through the recovery process step by step, helping me verify my identity and regain access to my email account. After what felt like an eternity, I finally received the confirmation that I had regained access. The relief I felt was immense; not only could I communicate freely again, but I also had a direct line to manage my investments securely. This experience taught me invaluable lessons about the volatile nature of cryptocurrency and the importance of security. While the world of digital currency can be unpredictable, it also fosters a strong sense of community and support among investors. With my investments back in my control, I was more determined than ever to navigate the cryptocurrency landscape wisely and cautiously, For assistance.
CONTACT INFO BELOW:
WHATSAPP_<> +1 (740)705-0711.
EMAIL:_<> FOLKWINEXPERTRECOVERY (at) TECH-CENTER. C OM
Best Regards,
Henry Theodore.
-
Natural Wholesale Silver Gemstone Jewellery Exporter - JewelPin
More Visit: https ://www .jewelpin. com
JewelPin stands as a most useful Wholesale Silver Gemstone Jewellery Manufacturer and Exporter within the UK, relied on via outlets and wholesalers throughout 45 countries. With a big 60,000 sq. Toes. Production vicinity and a devoted staff of 750 personnel, we produce over one hundred,000 exquisite jewellery portions in line with month. We provide worldwide transport from India, making sure of timely and stable shipping. Our bendy ordering alternatives consist of a minimal order quantity of only 10 portions in line with design and a minimal order cost of $one thousand, making us a suitable associate for groups of all sizes. At JewelPin, we also offer the option to place your brand logo on our jewellery, supporting you in constructing and enhancing your logo identity. We are dedicated to performance, with all orders shipped within 15 to 45 days after placement, primarily based on production assessment. Choose JewelPin for reliable, excessive-quantity, and customizable wholesale silver gemstone jewellery answers.rant jewellerywholesalesupplier gemstonejewellery affordablesilverjewellery silvernecklaceswholesale stonejewellery gemstonejewelry indianjewellerydistributor gemstone stonejewelry silverbraceletswholesale silverearringswholesale3 -
HOW TO SUCCESSFULLY RECOVER YOUR STOLEN BITCOIN WITH THE HELP OF SALVAGE ASSET RECOVERY
At first, Derived seemed like a reliable and trustworthy investment platform. The staff was friendly, and their consultations were convincing, offering detailed information that gave me confidence in the company. The process seemed well-organized, and their promises of high returns made me eager to proceed. However, it wasn’t long before things took a concerning turn.After I made my deposit, I was immediately asked to submit a range of documents to verify my identity. At first, I assumed this was just part of their standard process, but the requests kept coming. What started as a few simple documents turned into a constant stream of increasingly complex paperwork. Despite submitting everything they asked for, I was still asked for more, which only made me more uneasy about their intentions.To make matters worse, my CAD 15,000 balance was frozen, and every attempt to withdraw my funds was met with delays and vague responses. The company claimed that my withdrawal was in progress, but days turned into weeks without any movement. It quickly became clear that they had no intention of allowing me to access my own money, and their communication became more evasive with each passing day.It soon became evident that Derived was not the trustworthy company I had initially thought it was. Their constant demands for documentation and their refusal to process my withdrawal felt like deliberate tactics to prevent me from retrieving my funds. I felt completely trapped and frustrated, unable to move forward or recover my money.That’s when I decided to reach out to Salvage Asset Recovery. They came highly recommended, and after a thorough consultation, I felt confident that they could help me. The Salvage Asset Recovery team acted quickly, taking charge of the situation and handling all communication with Derived. Their professionalism, expertise, and dedication were evident at every step, and they were ultimately able to recover my entire investment.Thanks to Salvage Asset Recovery, I was able to get my CAD 15,000 back. They worked tirelessly to ensure that Derived could no longer delay or deny my withdrawal. I am deeply grateful for their support and for helping me reclaim what was rightfully mine.If you find yourself in a similar situation, I strongly recommend reaching out to Salvage Asset Recovery. Their commitment to helping clients recover their funds is unmatched, and without their assistance, I would have never gotten my money back. They made all the difference when I needed help the most.
Visit Salvage Asset Recovery via below contact details.
WhatsApp-----.+ 1 8 4 7 6 5 4 7 0 9 6
TELEGRAM---@Salvageasset 13
13 -
Early 2025, I resided in the vibrant city of Austin, Texas, where the burgeoning tech landscape had ignited my interest in cryptocurrency investment. After years of diligent work as a software engineer, I had amassed $45,700 from my salary and a lucrative side venture developing mobile applications. Eager to secure my financial future, I was enthusiastic about exploring investment opportunities in the crypto market. One fateful day, while perusing online, I encountered a seemingly legitimate investment platform that promised extraordinary returns on cryptocurrency investments. The website was impeccably designed, and the testimonials from purportedly satisfied investors appeared authentic. Fueled by confidence, I made the impulsive decision to invest my entire savings, convinced I was embarking on a prudent financial endeavor my exhilaration swiftly morphed into despair when I attempted to withdraw my initial investment. The website became unresponsive, and my inquiries to customer support were met with silence. It soon became painfully evident that I had fallen victim to a sophisticated scam. Desperate to reclaim my funds, I embarked on a quest to investigate the scammer's identity and track down the elusive website. I made the regrettable choice to invest an additional $10,000 in Bitcoin, hoping to enlist a private investigator to assist in tracing the scammer. Unfortunately, this only led to further frustration and loss, as I realized I was entangled with a well-organized criminal enterprise that had expertly concealed its tracks. Feeling utterly defeated, I stumbled upon an article that extolled the virtues of CRANIX ETHICAL SOLUTIONS HAVEN, a group of ethical hackers renowned for their prowess in recovering lost funds from online scams. Skeptical yet hopeful, I decided to reach out to them. Their website exuded professionalism, and the testimonials from previous clients were compelling. Upon contacting CRANIX ETHICAL SOLUTIONS HAVEN, I was assigned a dedicated recovery specialist who meticulously guided me through the process. They conducted a comprehensive investigation into the scam, employing advanced techniques to trace the funds and gather irrefutable evidence against the perpetrators. Within a few weeks, I was astounded to learn that they had successfully recovered approximately 93.5% of my lost investment. Not only did CRANIX ETHICAL SOLUTIONS HAVEN facilitate the recovery of a substantial portion of my funds, but they also took decisive action against the scammer's website, leading to its takedown. The authorities were notified, and the scammers were apprehended, restoring a sense of justice to the situation. with CRANIX ETHICAL SOLUTIONS HAVEN was nothing short of transformative. They provided the expertise and unwavering support I desperately needed during a tumultuous time. If anyone finds themselves in a similar scam, reach out to CRANIX ETHICAL SOLUTIONS HAVEN for assistance in recovering your lost funds.
EMAIL: cranixethicalsolutionshaven (@) post (.) com
WHATSAPP: +44 (7460) (622730)
WEBSITE: https : / / cranixethicalsolutionshaven (.) info
TELEGRAM: (@) cranixethicalsolutionshaven7 -
SUPPORT GROUP FOR CYPTO FRAUD VICTIMS - FUNDS RETRIEVER ENGINEER
As a military woman, I’ve been trained to stay alert and think tactically, but nothing prepared me for the emotional and financial ambush I experienced online. It started innocently enough. While stationed overseas, I connected with someone on social media who claimed to be a successful crypto trader. He was charismatic, well-spoken, and incredibly supportive. Over the course of several months, he built my trust. He didn’t rush anything. We talked almost every day about life, service, family, and eventually, finances. He made me feel seen and understood, and I truly began to believe there could be a future with him. He slowly introduced me to his world of crypto investing. At first, I was skeptical. But he showed me a platform where he said he made consistent profits, even offering to help me get started. I watched my investment appear to grow rapidly on the site. It looked real. It felt real. Encouraged by what I saw and the bond I thought we had, I invested more and more until I’d put in a total of $250,000. It was everything I had saved. Then one day, he vanished. No calls. No messages. The platform stopped working. My heart sank. I knew I’d been scammed. I felt betrayed, embarrassed, and helpless. I might be tough in uniform, but behind the screen, I was just a woman who’d been deceived. That’s when I found FUNDS RETRIEVER ENGINEER. From the first call, they treated me with respect and urgency. Their team got to work immediately. They were able to trace the funds through 12 different crypto wallets, following a digital trail most would never find. Eventually, they tracked the money to a real exchange account, one that the scammer had linked to his identity. That mistake cost him.Thanks to FUNDS RETRIEVER ENGINEER expertise, $187,000 of my stolen funds were recovered before they could be laundered or hidden. They worked with international authorities and the exchange to freeze the assets in time. I’m still healing, but I’m no longer a silent victim. I’m speaking out because if it happened to me, a woman in the military, it could happen to anyone. Don’t stay silent. There’s help out there. FUNDS RETRIEVER ENGINEER gave me a second chance.
For help
W H A T S A P P: +1 8 0 2 9 5 2 3 4 7 0
EmaIL F U N D S R E T R I E V E R [@] E N G I N E E R. C O M
OR
S U P P O R T @ F U N D S R E T R I E V E R [@] E N G I N E E R. C O M10 -
HOW TO RECOVER LOST OR STOLEN CRYPTOCURRENCY HIRE CERTIFIED RECOVERY SERVICES
I am beyond grateful to share my experience with CERTIFIED RECOVERY SERVICES, a company that has proven to be a true lifeline for those like me who thought they had lost their Bitcoin investments forever. The world of cryptocurrency, while offering tremendous opportunities, can also be a perilous landscape, where a single mistake or a sudden system failure can lead to significant financial loss. I found myself in such a situation, and thanks to the dedicated team at CERTIFIED RECOVERY SERVICES, I was able to recover what I thought was gone forever. In 2021, I invested a substantial sum into Bitcoin, eagerly watching the market trends and hoping for substantial returns. However, as the market fluctuated, I found myself caught in a series of unfortunate events. First, I fell victim to a phishing scam that compromised my personal information and led to the loss of my Bitcoin. My initial panic was beyond words - I had invested a large portion of my savings, and the thought of losing it all was devastating. I felt powerless and received automated responses when I tried to reach customer service multiple times through the exchange I was using. I didn't know where to go next. It appeared as though my Bitcoin assets were lost forever because every path seemed to lead to nothing. I came discovered CERTIFIED RECOVERY SERVICES at that point. From the moment I reached out to CERTIFIED RECOVERY SERVICES on WhatsApp: +1 (740) 258‑1417, I knew I was in capable hands. The process was straightforward. I explained my situation, detailing how I lost my Bitcoin and the steps I had already taken to try to recover it. The customer service team at CERTIFIED RECOVERY SERVICES was empathetic and understanding. They reassured me that my case wasn't hopeless, explaining the methods they use to track and recover lost crypto investments, even when critical information like wallet keys or recovery phrases is lost or compromised. The team at CERTIFIED RECOVERY SERVICES started by verifying my identity and confirming my ownership of the Bitcoin in question. They then initiated an in-depth analysis of the wallet's blockchain data, tracking the lost assets across various exchanges and addresses. They also reached out to several platforms and services involved in the transaction history, leveraging their extensive network in the cryptocurrency industry. After what felt like an eternity of waiting, I received the best news possible - my Bitcoin had been successfully recovered! The amount I thought was lost for good was now accessible again, thanks to the tireless efforts of the CERTIDIED RECOVERY SERVICES team. They not only managed to recover my assets but also took proactive steps to ensure my future investments would be secure. for assistance reach them with the below information.
Email:contact (@)c e r t i f i e d r e c o v e r y s e r v i c es. c o m6 -
CRYPTOCURRENCY RECOVERY EXPERT REVIEW: SALVAGE ASSET RECOVERY
As a passionate member of the cryptocurrency community, I was both excited and anxious about the potential acquisition, but little did I know that I was about to be targeted by a skilled con artist. When I came across an auction for what was claimed to be "the last known Satoshi wallet" for an astonishing 10,000 BTC, my curiosity got the better of me. The prospect of owning such a significant piece of cryptocurrency history was thrilling, but it quickly turned into a nightmare.After expressing my interest, I soon realized that I was dealing with a hacker who had crafted an elaborate scheme to defraud unsuspecting buyers like myself. Feeling overwhelmed and unsure of how to proceed, I reached out to Salvage Asset Recovery for help. From the moment I contacted them, I was struck by their professionalism and expertise. They understood the gravity of the situation and immediately sprang into action. Salvage Asset Recovery devised an intricate sting operation to expose the hacker and recover the funds involved in the auction. They deployed an agent who posed as a wealthy collector interested in purchasing the so-called Satoshi wallet. This agent was equipped with a hidden wire concealed within a hardware wallet, allowing for discreet communication throughout the negotiation process. I was amazed at the level of detail and planning that went into the operation.I watched anxiously from the sidelines. The agent engaged in tense discussions with the hacker, who was eager to finalize the deal, believing he had successfully duped a potential buyer. Salvage Asset Recovery remained focused and vigilant, fully aware that the wallet was likely a clever ruse. Their determination to protect me and the integrity of the cryptocurrency community was evident.When the moment came to transfer the escrow funds, totaling $650,000, I held my breath. The team executed their plan flawlessly, and law enforcement was ready to swoop in as soon as the transaction was completed. I was both relieved and amazed when I learned that the hacker had been arrested, revealing him to be a notorious identity thief operating on the dark web.The most shocking part of this entire ordeal was discovering that the "Satoshi wallet" was nothing more than a cleverly modified Trezor device containing a Rickroll video. It was a stark reminder of the lengths to which some individuals will go to exploit unsuspecting victims like myself.Thanks to Salvage Asset Recovery, not only were my funds recovered, but I also felt a renewed sense of security within the cryptocurrency community. Their dedication to combating cybercrime and their innovative strategies are truly commendable. I wholeheartedly recommend Salvage Asset Recovery to anyone facing challenges in the digital realm. Their expertise and commitment to justice are unparalleled, and I am incredibly grateful for their support during this difficult time. reach out to salvage asset recovery
VISIT THEM ON THE CONTACT BELOW:
WHATS APP : +18476547096
TELEGRAM : @Salvageasset5 -
How do I extend ASP Identity on .NET Core to check the database on every page load for an IsAdmin Boolean on the extended IdentityUser class? I need to do this to ensure rights haven’t been revoked and the user is still allowed to access restricted pages.10
-
At Domgys, we offer a wide range of web hosting solutions designed to meet the diverse needs of our clients. Our key services include:
SSL Certificates
Protect your website with our extensive range of SSL certificates, including trusted names like GeoTrust and RapidSSL. We ensure your site remains secure and your customers’ data stays safe.
Linux VPS Hosting
Experience the power and flexibility of our Linux VPS hosting solutions. Whether you’re running a small business or a large enterprise, our VPS hosting provides the performance and scalability you need.
Business Email Hosting
Enhance your professional communication with our secure and reliable business email hosting services. We provide robust email solutions that support your company’s growth.
Linux Dedicated Hosting Servers
Enjoy unparalleled performance and security with our Linux dedicated hosting servers. Designed to handle demanding workloads, our servers ensure your website operates smoothly and efficiently.
Domain Registration:
Secure the perfect domain name for your business with our easy-to-use domain registration service. Establish your online identity quickly and effectively. -
WEB BAILIFF CONTRACTOR-HIRE THE TOP CRYPTO RECOVERY EXPERT
In bitcoin investment schemes, scammers contact investors claiming to be seasoned "investment managers." As part of the scheme, the so-called investment managers claim to have made millions investing in cryptocurrency and promise their victims that they will make money with investments. Soon after making deposits, victims are asked for more payment which they eventually are unable to withdraw or communicate with the investment managers. It is extremely difficult for police to recover funds once they have been transferred to these fake investment companies, therefore, crypto recovery services like Web Bailiff Contractors come in handy. Essentially, Web Bailiff began as a low key operation targeting fake exchange platforms that scam innocent naive investors. They would track down their identity and return the deposits to the victims anonymously. Recently, they created a channel through which victims can approach them to present their individual cases. If you have encountered such investment platforms or know a victim, contact them through email web @ bailiffcontractor . net1 -
Custom Lip Gloss Boxes: The Ultimate Guide to Stylish and Functional Packaging
In the beauty industry, packaging is just as important as the product itself. It serves not only to protect and preserve the product but also plays a pivotal role in branding, marketing, and influencing consumer choices. When it comes to lip gloss, custom packaging offers endless possibilities to create a unique brand presence. Custom lip gloss boxes are a key element in delivering that first impression, helping brands stand out in a competitive market.
This article delves into the importance of custom lip gloss boxes, their benefits, design considerations, and the latest trends shaping this packaging solution.
Why Custom Lip Gloss Boxes Matter
Lip gloss is a beauty staple, often viewed as a small, portable item, but its impact on a brand’s image can be significant. Custom lip gloss boxes elevate the product’s appeal, making it more attractive to consumers while offering protection during transport and storage. These boxes not only serve a practical purpose but also communicate a brand's values, creativity, and quality.
Key Benefits of Custom Lip Gloss Boxes
Brand Differentiation Custom packaging allows brands to create a distinct identity in the crowded beauty industry. With a range of customization options including colors, shapes, finishes, and design elements, brands can craft packaging that reflects their personality and vision, ensuring that their lip gloss stands out on store shelves.
Effective Marketing Tool A well-designed lip gloss box doubles as a marketing tool. With space for logos, taglines, product descriptions, and even social media handles, custom packaging reinforces brand recognition and helps consumers remember your product long after purchase.
Enhanced Product Protection While lip gloss tubes are often sturdy, custom boxes provide an added layer of protection, especially during shipping and handling. These boxes ensure the product arrives in perfect condition, preventing damage from impact, exposure to sunlight, or moisture.
Improved Consumer Experience Attractive and thoughtfully designed packaging enhances the unboxing experience, making it memorable for customers. This can lead to positive word-of-mouth, repeat purchases, and social media shares, all of which contribute to brand loyalty.
Eco-Friendly Options Many beauty brands are now shifting toward sustainable packaging solutions. Custom lip gloss boxes can be made from eco-friendly materials such as recycled cardboard or biodegradable paper. This not only reduces the environmental impact but also appeals to environmentally-conscious consumers.
Cost-Effective and Scalable Custom lip gloss boxes can be produced at scale, making them cost-effective for brands. Bulk production reduces the per-unit cost, making it an affordable option for businesses of all sizes, from boutique brands to large cosmetic companies.
Design Considerations for Custom Lip Gloss Boxes
Creating custom packaging involves several design elements that must be carefully thought out to achieve the desired look and functionality. Here are key aspects to consider:
Material Choice The material used for the custom lip gloss boxes should be durable yet lightweight. Popular materials include cardboard, kraft paper, and rigid boxes. Brands focused on sustainability may opt for eco-friendly or recycled materials, which can still deliver a high-end feel.
Size and Shape The size of the box should fit the lip gloss container snugly to avoid unnecessary movement and potential damage. While traditional rectangular boxes are common, unique shapes such as hexagonal or cylindrical boxes can make your packaging stand out.
Branding Elements Incorporating your brand’s logo, color palette, and fonts is essential in creating packaging that resonates with your target audience. Consistent use of branding elements across all your products helps build brand identity and consumer trust.
Printing and Finishing Options Various printing techniques and finishes can enhance the look and feel of your custom lip gloss boxes
Window Cutouts Adding a transparent window to your lip gloss boxes allows consumers to see the actual product without opening the packaging. This feature is particularly appealing when showcasing different lip gloss shades, helping consumers make purchasing decisions quickly.
Sustainability As consumers become more eco-conscious, brands can differentiate themselves by using recyclable, compostable, or biodegradable packaging materials. Eco-friendly packaging not only reduces your brand's carbon footprint but also enhances its image as a socially responsible entity.
Conclusion
Custom lip gloss boxes are a crucial element in building a strong brand presence and ensuring that your product catches consumers' attention. 2
2 -
Business Awareness: Your Trusted Partner for Chicago Brand Marketing
Building a strong, recognizable brand is essential for business success in today’s competitive market. At Business Awareness, we specialize in expert Chicago brand marketing services designed to help your business create a lasting impression, connect deeply with your audience, and stand out in the bustling Chicago market.
Why Choose Business Awareness for Chicago Brand Marketing?
Deep Understanding of the Chicago Market
Located at 205 N Michigan Ave Suite 810, Chicago, IL, our team has extensive knowledge of the local business environment. We tailor brand marketing strategies that resonate with Chicago’s diverse consumer base.
Comprehensive Brand Marketing Solutions
From brand identity development and positioning to digital campaigns and social media management, we offer a full suite of services to build and promote your brand effectively.
Customized Strategies for Maximum Impact
Every brand is unique. We work closely with you to craft personalized marketing strategies that reflect your business values and goals.
Data-Driven Approach
We use analytics and market research to guide our brand marketing efforts, ensuring measurable results and continuous improvement.
Dedicated Support and Partnership
Our Chicago-based team is committed to collaborating with you throughout the branding process, providing ongoing support to help your brand grow.
Contact Us
Ready to strengthen your brand presence with expert Chicago brand marketing? Contact Business Awareness today and let us help you craft a brand that Chicago remembers.
Address: 205 N Michigan Ave Suite 810, Chicago, IL 60601, United States
Phone: +1 888-352-2927
Partner with us to build a powerful brand that drives business growth in Chicago.2 -
Alber Sign Company: Your Trusted Provider of Privacy Film, Business Signs, and Sign Services in Rockledge, PA
Welcome to Alber Sign Company, your local expert in business signs, privacy film, sign installation, and comprehensive sign services. Located in Rockledge, PA, we are dedicated to helping businesses of all sizes create the perfect signage solutions to enhance their visibility, privacy, and overall professional appearance. Whether you need stylish signs for your storefront, office, or a custom privacy film solution, we have the expertise and experience to meet your needs.
Why Choose Alber Sign Company?
Enhance Your Privacy with Professional Privacy Film Solutions
Privacy is essential, especially in business settings. Whether you're looking to shield confidential office spaces or create a more secluded environment, privacy film is an excellent solution. Our privacy films provide you with the ideal balance of privacy and natural light, transforming your workspace into a more secure and comfortable environment. From office partitions to storefront windows, we offer custom privacy film that helps reduce glare while maintaining the aesthetics of your space.
Custom Business Signs Tailored to Your Brand
Business signs are a vital tool in establishing your brand's identity and attracting customers. At Alber Sign Company, we specialize in creating business signs that reflect your brand's unique style and message. Whether you need interior signs for your office, exterior signs for your storefront, or a combination of both, we offer custom designs that will make your business stand out. From bold and illuminated signs to sleek, professional displays, we help your business get noticed.
Professional Sign Installation for Maximum Impact
Proper sign installation is crucial to ensuring that your signage not only looks great but also functions effectively. Our experienced team handles all aspects of sign installation, ensuring your signs are securely mounted and positioned for maximum visibility. Whether you're installing business signs on your storefront, privacy film in your office, or directional signs inside your building, we make sure everything is done right the first time.
Comprehensive Sign Services to Support Your Business
At Alber Sign Company, we offer a full range of sign services to meet your needs. Our services include design, manufacturing, installation, maintenance, and repair of all types of signage. Whether you’re looking to refresh your existing signs or require new signage solutions, we provide professional service every step of the way. We’re here to ensure that your signage remains in top condition and continues to support your business growth.
Affordable and Reliable Signage Solutions
We believe that high-quality signage should be accessible to businesses of all sizes. At Alber Sign Company, we offer competitive pricing without compromising on the quality of our work. Whether it's a privacy film for your office, a custom business sign, or a complete sign installation and sign service package, you can count on us for affordable, reliable, and durable solutions.
Our Services
Privacy Film: Custom privacy films for office spaces, conference rooms, and storefront windows.
Business Signs: Custom interior and exterior signs to boost your business's visibility and brand identity.
Sign Installation: Professional installation for all types of signage, ensuring secure and effective placement.
Sign Services: Comprehensive sign repair, maintenance, and design upgrade services.
Contact Us Today
Ready to take your business to the next level with high-quality business signs, privacy film, and expert sign installation? Alber Sign Company is here to help. Our team of professionals is dedicated to providing the best signage solutions for your business, tailored to your specific needs.
Contact Information
Address: 902 Fox Chase Rd, Rockledge, PA 19046, United States
Phone: +1 (267) 847-47355 -
Need help with selecting a proper backend and website frameworks. After trying out a couple identity verification service providers we were dissapointed with their lack of support (takes weeks to do minimal changes).
So now we are having discussions about building in-house id verification system. We already have libraries for ios/android apps (ZOOM lib for face recognition and another lib for data extraction via OCR from document picture). So what we need is a proper backend and then a decent web framework with proper ux/ui design for our web/ios/android apps.
Currently thinking what kind of backend framework should we choose? Backend's main responsibility is for each client registered from website to assign an api key and to create a database/storage where his users would authenticate via clients app and upload a picture and a video.
Also wondering what kind of framework for website apps (main web app, dashboard app where we display pending verifications, and of course verification app) to choose. Should be go for angular? -
I was a victim of identity theft. Someone opened credit cards in my name. I had doubts and was anxious about the cost and success of the service, but HackX-TechN proved me wrong. They were brave, knowledgeable, and efficient in their work. pricing was transparent and competitive. They ( hackxtechn@gmailcom ) provided value for money and exceeded my expectations. Monitor your credit reports, everyone!1
-
Your Go-To Web Designing Agency in Delhi | Transforming Ideas into Reality
In today’s competitive digital landscape, having a strong online presence is crucial for business success. At Marketing Munchkin, we are a leading web designing agency in Delhi, dedicated to crafting visually stunning, user-friendly, and high-performing websites that help brands establish their digital footprint.
Why Choose Marketing Munchkin?
As a trusted web designing agency in Delhi, we believe that a website is more than just an online platform—it’s your brand’s identity. Our expert designers and developers work closely with you to create custom, SEO-friendly, and responsive websites that align with your business goals.
Our Web Designing Services
We offer a full range of web design solutions, including:
Custom Website Design – Tailor-made designs that reflect your brand’s uniqueness.
Responsive Web Design – Mobile-friendly websites that provide a seamless user experience across all devices.
E-commerce Website Design – Powerful and secure online stores to drive your sales.
UI/UX Design – Engaging and intuitive designs that enhance user interaction.
Website Redesign – Modernizing outdated websites for better performance and conversions.
Why a Professionally Designed Website Matters
A well-designed website is the foundation of your online success. With a professionally crafted website, you can:
Attract More Visitors – A visually appealing and SEO-optimized website ranks higher in search engines.
Enhance User Experience – Fast-loading, easy-to-navigate sites keep visitors engaged.
Increase Conversions – A strategic layout and compelling design encourage users to take action.
Let’s Build Your Dream Website
At Marketing Munchkin, we take pride in being a customer-focused web designing agency in Delhi, committed to delivering innovative and results-driven solutions. Whether you're a startup, small business, or enterprise, we bring your ideas to life with creative, functional, and scalable websites.
Ready to elevate your online presence? Contact Marketing Munchkin today and let’s create a website that stands out!1 -
Unveiling Beauty: The Power of Cosmetic Boxes
Introduction:
Cosmetic boxes are packing devices created especially to hold and show off cosmetics. They serve various objectives, such as advertising, visual identity, and protection.
Companies have a broad range of alternatives for meeting their individual demands due to the variety of aesthetic boxes accessible with respect to of forms, substances, or printing possibilities.
Functions of Cosmetic Boxes:
1. Protection: Avoiding harm to the encompassed goods while handling, storage, and transportation represents one the primary uses of cosmetic boxes. They serve as a barrier against pollutants including dust, rain, and sunshine.
2. Branding: They are essential for brand uniqueness and identification. In order to give them a unique identity, they are often customized with the logo of the business, colors, and designs. These qualities aid customers in quickly recognizing and linking items to a certain brand.
3. Marketing: Cosmetic boxes wholesale function as a marketing strategy by drawing in prospective clients and disseminating details concerning the products. Customers are drawn in and persuaded to buy product by the appealing designs, appealing photos of the products, and pertinent info displayed on the boxes.
Types of Cosmetic Boxes:
1. Folding Cartons: The most typical kind of beauty boxes are those made of folding cartons. They are composed of flimsy paperboard and are simple to shape-fold. These containers are adaptable and available in an assortment of kinds, including gable, sleeve, and tuck-end containers.
2. Rigid Boxes: Rigid boxes, often referred to as setup packages, are strong and long-lasting. They provide excellent defense for expensive cosmetics since they are composed of sturdy cardboard or cardboard. Luxury cosmetic manufacturers often utilize rigid bottles because they provide a high-end appearance and feel.
3. Display boxes: Display containers are made to promote cosmetics in an appealing way. Customers could generally view the merchandise inside thanks to transparent windows or doors. Retail stores often use display boxes to increase product exposure.
Materials Used in Manufacturing Process:
1. Paperboard:The most common material used for making cosmetic boxes is paperboard. It is lightweight, reasonably priced, and provides a range of printing and finishing possibilities. Depending on how much strength is needed and durability, many types of cardboard are accessible, which vary in low to high density.
2. Cardboard: Unlike paperboard, cardboard is a thicker, more robust material. It offers more effective defense for pricey or delicate cosmetics. To increase the durability and water resistance, cardboard containers may be customized with various coatings.
3. Plastic: Cosmetic cartons may be made of plastic, particularly clear display boxes with PVC or PET panes. Plastic boxes offer good product visibility and moisture protection. In contrast to solutions utilizing paper, they are less detrimental to the environment.
Printing Options:
1. Offset Printing: The printing method most often employed for cosmetic boxes is offset printing. Prints made with it are crisp, vibrant, and detailed. For intricate patterns, gradients, and vast numbers of boxes, the offset method is appropriate.
2. Digital Printing: Digital printing provides more flexibility and quicker turnaround times than the use of offset printing. It enables for cosmetic packaging customization that is simultaneously affordable and appropriate for small to large print runs. The color dedication, however, could be a little less accurate than with offset printing.
3. Foil Stamping: Foil stamping is the procedure of putting coloured or metallic foil on the outside or packaging for cosmetics. It enhances the overall look of the container by adding a opulent and captivating impression.
“Lipstick Boxes: Exploring Types and Varieties”
Special packaging materials known as pink boxes are made to carry and showcase lipsticks. They are available in a variety of forms to meet varied packing requirements.
The types of lipstick boxes include:
1. Folding Carton Lipstick Boxes: Made with paperboard, these boxes are portable and lightweight. They're simple to fold into form and may be personalized with various patterns and finishes.
2. Rigid Lipstick Boxes: Made of durable materials like cardboard, these boxes provide great protection of costly lipsticks. For high-end lipstick products, rigid boxes are ideal since they've an increase appearance and feel.
3. Slide Sleeve Lipstick Boxes: These vessels include a sliding sleeve function which gives a touch of class & efficiency. Branded and design elements could be added to the sleeve.
Resource: https://packagingforestllc.com/prod...1 -
Buy Verified Cash App Accounts
In today's fast-paced digital world, mobile payment apps have revolutionized the way we handle financial transactions. Cash App, a popular mobile payment service, has gained widespread recognition for its user-friendly interface and seamless money transfer capabilities. As the demand for Cash App accounts increases, the significance of obtaining a verified account becomes more apparent. In this article, we will explore the concept of purchasing verified Cash App accounts, understanding its benefits, potential risks, and essential tips for a secure and successful transaction.
Understanding Cash App
What is Cash App?
Cash App, also known as Square Cash, is a peer-to-peer mobile payment service that allows users to send, receive, and request money through their smartphones. With its straightforward design and hassle-free functionality, Cash App has become a preferred choice for individuals and businesses alike.
How does Cash App work?
Cash App operates by connecting to the user's bank account or debit card, facilitating seamless and instant money transfers to other Cash App users. Users can also load funds onto their Cash App balance, known as the "Cash Card," to make purchases or withdraw cash from ATMs.
Importance of Verified Cash App Accounts
Security and Safety
Having a verified Cash App account adds an extra layer of security to your financial transactions. Verified accounts undergo a thorough verification process, which helps ensure the legitimacy of the user and reduces the risk of unauthorized access.
Transaction Limits and Benefits
Verified Cash App accounts come with higher transaction limits, allowing users to send larger amounts of money. Moreover, verified users may have access to exclusive promotions and rewards offered by Cash App.
Ease of Use
With a verified account, users can seamlessly link their bank accounts or cards to the app, streamlining the process of sending and receiving money.
Risks and Concerns
Scams and Fraudulent Accounts
One of the primary concerns when considering the purchase of Cash App accounts is the presence of scams and fraudulent sellers. Dealing with unreliable sources can lead to financial losses and potential misuse of personal information.
Violation of Terms of Service
Buying or selling Cash App accounts is against the platform's terms of service. If discovered, such accounts may be subject to suspension or permanent banning, resulting in the loss of funds and access to Cash App services.
Identity Theft
Using a purchased Cash App account without changing the login credentials can expose the buyer to identity theft. It is crucial to take necessary precautions to safeguard sensitive information.
Buying Verified Cash App Accounts
Reputable Sources
When seeking to buy a Cash App account, it is essential to choose reputable and trustworthy sources. Conduct thorough research, read customer reviews, and seek recommendations from reliable sources before making a decision.
Verification Process
Before making a purchase, ensure that the seller provides a transparent explanation of their verification process. The verification process should align with Cash App's guidelines and industry best practices.
Tips for Safe Purchase
Research the Seller
Thoroughly research the background and reputation of the seller before proceeding with the purchase. Avoid dealing with sellers who have a history of negative reviews or questionable practices.
Verify Account Authenticity
After purchasing a Cash App account, verify its authenticity by logging in and reviewing the account details. If any discrepancies are found, contact the seller immediately.
Use Secure Payment Methods
Opt for secure payment methods, such as PayPal or credit cards, that offer buyer protection in case of fraudulent transactions.
Change Login Credentials
To protect against identity theft, change the login credentials (username and password) of the purchased account immediately after the transaction.
Using a Purchased Cash App Account
Linking Bank Accounts and Cards
After acquiring a Cash App account, link it to your bank accounts or debit cards to enable seamless transactions.
Investing and Trading
For users interested in investing or trading stocks through Cash App, the verified account provides a secure platform to explore investment opportunities.
Conclusion
Purchasing a verified Cash App account can offer convenience and additional benefits to users, but it comes with potential risks. It is vital to approach the purchase with caution, thoroughly research the seller, and follow safety measures to avoid scams and fraudulent activities. By taking these precautions, users can enjoy the seamless and secure experience of using Cash App for their financial transactions.
-
It was a rainy Tuesday evening when I sat at my desk, staring at the screen in disbelief. My Bitcoin months of careful savings had vanished into a shady investment scheme I’d fallen for. The website promised "guaranteed returns," but after sending 2 BTC, the platform went dark, and my wallet was empty. I felt like a fool, scammed by my own desperation for a quick profit. Days turned into weeks, and I’d nearly given up hope when a friend mentioned Alpha Spy Nest, a secretive group known for tracking down lost crypto. Skeptical but desperate, I reached out through an encrypted email I found on a forum. Within hours, a response arrived: “Send us the details. We’ll see what we can do.” I shared everything, the wallet address I’d sent my Bitcoin to, the fake platform’s URL, and the few screenshots I’d taken. Alpha Spy Nest didn’t waste time with pleasantries. Their next message was a list of questions: transaction IDs, dates, even the IP address I’d used. I scrambled to provide it all, unsure how they’d pull off the impossible. Behind the scenes, Alpha Spy Nest went to work. They were a shadowy crew, hackers, blockchain analysts, and who-knows-what-else, operating on the edges of the digital world. Using tools I couldn’t begin to understand, they traced my Bitcoin through a labyrinth of wallets designed to hide the trail. The scammers had funneled it through mixers, but Alpha Spy Nest unraveled the mess, linking it to an exchange account tied to a careless crook who’d left digital breadcrumbs. Days later, I got a message: “Check your wallet.” My hands trembled as I opened my crypto app. There it was 1.9 BTC, a hair less than I’d lost due to fees, but more than I’d ever dreamed of seeing again. A follow-up note from Alpha Spy Nest explained they’d pressured the scammer into returning it after exposing his identity to the exchange. “He folded fast,” they wrote. “Stay sharp next time.” I never met them, never even learned their real names. But that rainy night, Alpha Spy Nest turned my despair into a second chance. I swore I’d never fall for a scam again and that I’d keep their name close, just in case. whatsApp: +14159714490
 1
1 -
Is their a better way than ASP Identity Claims to verify permissions before accessing a page? Refreshing claims in every page load doesn’t seem to be a great solution. Thinking about some sort of permissions middleware. I need to check those IsAdmin roles before any admin area data is accessed. What techniques are you using for authorization in your code base?3
-
"If I do my job well, the identity program will also clean up the image of the company, position it as being contemporary and keep it from ever looking dated." - Saul Bass
-
Discover why WIZARD JAMES RECOVERY TEAM is regarded as a top investment fraud risk and loss of virtual assets solution by watching them in action and getting live answers to your queries. Since the Recovery by WIZARD JAMES RECOVERY TEAM, they have essentially become my real-life Marvel Hero, standing up for small investors against dishonest investment companies who wish to steal your hard-earned money in a casual manner or, worse, commit open fraud using your credentials. For years, fraudulent investment companies and fake recovery artists deceived us by promising to quadruple our investment, not to mention the fake recovery artists who all made false claims about their ability to successfully recover our invested funds but failed. We didn't realize how amazing and powerful it is to have a top Recovery Expert at your side until we began working with the WIZARD JAMES RECOVERY TEAM. The WIZARD JAMES RECOVERY TEAM is very knowledgeable, professional, self-assured, and detail-oriented. We are quite pleased with the results that the WIZARD JAMES RECOVERY TEAM produced for us in a matter of days. I'm grateful, Wizard James. Furthermore, the last mistake made by investors who have lost money to dishonest investment firms is to disregard the assistance of Professionals & Recovery Company, particularly when it comes to investment accounts that have been flagged or frozen with little to no justification from the company's customer service agent. Working with a skilled recovery firm like WIZARD JAMES RECOVERY TEAM may offer priceless experience, guaranteeing complete asset recovery and precisely managing the intricacies of any fraudulent investment scenarios. The significance of hiring the WIZARD JAMES RECOVERY TEAM cannot be overstated. Their expertise can offer insightful advice, as well as identify and stop even the most intricate types of fraud while shielding your identity from additional fraud involvement at every point of contact. With AI-powered modeling of industry-leading data and extensive networks of digital, physical, email, and behavioral intelligence, you may uncover hidden insights that are specifically pertinent to your risk management concerns. All of this is done to support and give an ethical recovery experience. To begin, get in touch with WIZARD JAMES right now!
* EMAIL: wizardjamesrecovery @ usa . com
* WHATSAPP: +44 7418 3672041 -
ComPDFKit Solutions
For text extraction technology, ComPDFKit offers the following two solutions that effectively address text extraction for all types of PDF files. For documents containing only text information, our non-intelligent solution can suffice. But for more complex documents and image-based ones, ComPDFKit Document AI offers higher accuracy in text extraction. To learn about the accuracy of ComPDFKit's information extraction, see this article.
1. Algorithm: X-Y Cut Recursion Projection Method
The X-Y Cut Recursion Projection Method is a top-down page segmentation technique that decomposes a document image into rectangular blocks. It employs a recursive approach by projecting along both the X and Y axes to segment a PDF into independent rectangles, facilitating the extraction of textual components. ComPDFKit utilizes this method for efficient text separation and structural organization, including rows, paragraphs, and columns, to retrieve characters, words, lines, and paragraphs from the document.
The advantage of the X-Y Cut Recursion Projection Method is its speed, making it suitable for simple, structured, non-image-based PDF documents. However, for complex, unstructured PDFs, there might be recognition errors or omissions.
2. ComPDFKit Document AI
Document AI is an intelligent text extraction solution supporting all types of PDF files, including image-based. It uses artificial intelligence-based methods for document recognition and analysis to extract textual information from PDF documents (as well as images, tables, etc.).
- PDF Recognition and Analysis: This involves using deep learning models to recognize and analyze PDF documents, extracting elements like text, images, and tables while retaining their position, size, style, etc. ComPDFKit owns well-trained AI models to accomplish this process.
- Image Pre-processing: This process involves improving the quality and clarity of low-quality images in PDF documents, enhancing subsequent recognition and analysis. ComPDFKit employs multiple image processing techniques, such as image sharpening enhancement, noise reduction, document trimming and straightening, and stamp detection.
- OCR (Optical Character Recognition): OCR technology has a wide range of application scenarios such as license plate recognition, bank card information extraction, identity document (ID card) information recognition, train ticket information detection, etc. ComPDFKit supports recognition in dozens of languages. With extensively trained model zoo, it can accurately detect and recognize text in documents and analyze document structure. 1
1 -
BTC & NFT RESTORATION, GET EXPERT HELP FROM =SALVAGE ASSET RECOVERY
As a digital artist venturing into the world of NFTs, I was filled with excitement and hope. I had spent years honing my craft, and the prospect of sharing my work with a global audience was exhilarating. However, my journey took a devastating turn when I fell victim to a malicious smart contract that drained my wallet of $75,000 in earnings and royalties. The art community's response was disheartening; they told me it was gone forever, a harsh reminder of the risks we accept in the digital space.Feeling lost and disheartened, I began to accept the reality of my situation. It was not just about the money; it represented years of hard work, creativity, and passion. I felt as though a part of my artistic identity had been stolen. Just when I thought all hope was lost, I came across Salvage Asset Recovery. Their approach was different; they understood the emotional weight of my loss and were determined to help. Salvage Asset Recovery specialises in cryptocurrency vulnerabilities, and their team of experts meticulously analysed the malicious contract code that had caused my financial devastation. They identified the exploit and worked tirelessly with the platform to freeze subsequent transactions, preventing further losses. Their dedication was evident, and I felt a renewed sense of hope.Ultimately, Salvage Asset Recovery successfully recovered my lost funds. While I was grateful to have my $75,000 restored, I realised that the experience had left me with a lingering sense of vulnerability. I wished I had received guidance on how to protect myself in the future, as the world of NFTs and cryptocurrency can be fraught with risks.Though my financial stability was restored, I knew I needed to take proactive steps to educate myself about the intricacies of smart contracts and the potential vulnerabilities that exist within the cryptocurrency space. I emerged from this ordeal with my funds intact, but also with a newfound determination to secure my creative work and protect myself moving forward. If you need help reach out to Salvage Asset Recovery
CONTACT INFORMATION TELEGRAM---@Salvageasset
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 62 -
Luxe Decore Event Designs & Rentals: Stunning Corporate Gala Decor in Alabama
Planning a corporate gala is no small task. It's an event that needs to exude professionalism, sophistication, and style while ensuring that every detail aligns with your company’s values and brand identity. At Luxe Decore Event Designs & Rentals, we specialize in crafting corporate gala decor in Alabama that elevates your event and leaves a lasting impression on your guests. Located in Birmingham, Alabama, our team is dedicated to delivering exceptional decor solutions that turn your corporate gala into a memorable and elegant celebration.
Why Choose Luxe Decore for Corporate Gala Decor in Alabama?
A successful corporate gala requires meticulous planning and flawless execution. Luxe Decore brings years of experience, creativity, and attention to detail to every event we design. We understand the importance of setting the right tone for your gala, and our expert team ensures your event reflects your company’s image while providing an inviting and luxurious atmosphere for your guests.
Here’s why Luxe Decore is the go-to choice for corporate gala decor in Alabama:
Custom Event Design: We work closely with you to understand your brand, theme, and objectives, then curate a personalized decor plan that brings your vision to life. Whether you’re aiming for an elegant black-tie affair, a modern, minimalist look, or a themed gala, we ensure that every detail fits your unique style.
Full-Service Decor Solutions: Luxe Decore offers comprehensive decor services for every aspect of your corporate gala, from initial concept design to the final touches. We manage everything, so you don’t have to worry about a thing.
High-Quality Rentals: Our vast inventory of premium decor items, including furniture, table settings, lighting, and floral arrangements, will ensure that your gala is nothing short of extraordinary. We pride ourselves on offering only the finest quality decor to complement your vision.
Seamless Execution: From delivery to setup and takedown, our team handles all logistics with precision. We ensure that your decor is perfectly installed and creates the desired ambiance without disruption.
Our Corporate Gala Decor Services
At Luxe Decore, we offer a wide range of corporate gala decor services to make your event shine. Here’s a glimpse of what we can do for you:
Elegant Furniture Rentals
Furniture is key to creating a comfortable and stylish atmosphere at your corporate gala. We provide a variety of furniture options, including:
Chairs & Seating: From classic Chiavari chairs to luxurious lounge seating and cocktail chairs, we offer seating solutions for every type of event. Our options ensure that your guests are comfortable while adding a sophisticated touch to the decor.
Tables & Displays: Whether you're looking for sleek modern tables for a cocktail reception or long banquet tables for a seated dinner, we have the perfect options to suit your event’s needs. We can also provide accent tables for displays, registration desks, and more.
Lounge Areas: For networking spaces or VIP areas, we offer plush sofas, ottomans, and coffee tables that create a relaxed yet upscale environment.
Stunning Floral Arrangements
Floral arrangements are an essential part of creating an inviting, beautiful environment for your corporate gala. Our expert florists design custom arrangements, including:
Centerpieces: Whether you prefer tall, dramatic floral displays or low, elegant centerpieces, we tailor our arrangements to match your theme and venue.
Floral Installations: Make a statement with floral walls, hanging florals, or floral chandeliers that add grandeur and a touch of luxury to your event.
Bouquets & Other Decor: We can also provide personalized floral designs for welcome tables, stage decorations, and other event areas.
Lighting Design
The right lighting can completely transform your corporate gala. We offer a variety of lighting options, such as:
Uplighting: Soft, ambient lighting to create a warm, inviting atmosphere.
Chandeliers & Hanging Lights: Dramatic chandeliers or pendant lights for a sophisticated touch.
Spotlighting: Highlight key areas, such as the stage, award presentation area, or your company’s logo.
Custom Decor and Theming
Luxe Decore works with you to create a theme that aligns with your corporate identity and vision. We offer custom decor solutions including:
Branding & Signage: Whether you want a branded photo backdrop, custom signage, or a corporate logo displayed on the event stage, we provide solutions that seamlessly incorporate your brand into the decor.
Themed Decor: From formal galas to themed fundraising events, we design decor that matches your event’s theme, creating a cohesive look that resonates with your guests. 1
1 -
I wanted to share my experience recovering a significant amount of Bitcoin and Ethereum $560,000 00 that I thought was lost forever due to a forgotten password and a risky investment in a scam project.
The Loss: After realizing I couldn't access my wallet, I felt completely defeated. I did some research and found several recovery options available. SOFTWEAR TECH SOLUTION
The Recovery Process: I used a reputable recovery tool that I found recommended by several users on this forum. It required me to verify my identity and provide proof of ownership, but after a few weeks of back and forth, I was able to access my wallet again!
Outcome: I successfully recovered 98% of my lost BTC and ETH! It was a huge relief, and I’m actively taking steps now to secure my assets better.
Advice: Always keep a secure backup of your passwords and consider using hardware wallets for better security. Don’t fall for scams – do thorough research before trusting any service.
I hope my experience helps someone else here!
CONTACT,: SOFTWEAR TECH SOLUTION FOR SWIFT RECOVERY
Email: softweartech5@ gmail. com
Email: softewar.tech@ yandex. com1









