Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "verification"
-
Just called Asus for a problem with my router, went to send them my systemlog.txt for analysis
"Oh we don't have an email you can send that to"
Me: "(me calling bullshit) let me talk to the tech team.."
*Get transferred*
"Hello this is the supervisor"
Me: "fml"
"Ya we don't have an email you can send that to, but we can use a different departments verification services to get a file from you, has to be a picture though"
Me: "What? I got a .txt file here, I just want to get it to you, does it really have to be a picture?"
"Has to be a picture or a PDF, we can't take txt files"
Me: "fkin.. srsly? Fine"
I can't believe Asus's system srsly. I think it's for virus protection, but viruses can be embedded in both picture formats and PDF, but not in txt. So wtf is going on lol15 -
My current project at work: purchase verification, aka anti-fraud.
It's been two weeks, and my boss is flipping out because it isn't done. A robust anti-fraud solution. in two weeks. And he thought one week was a little much.
like, fucking really?
There are companies whose entire service is helping combat fraud. and he wants this done in a bloody week?
What makes me laugh through my tears of frustration is that the company that moved into the previous office? Yep, anti-fraud. Their entire business model is providing anti-fraud services to other businesses. They even tried selling him on it when they moved in. Bossman sales guy turned it around and sold my freaking desk out from under me instead.
But like. They're a small company: they had 9 people when they moved in, and were looking to add three more, so a total of 12 people. (I totally considered jumping ship, but their stack was too different.)
So. Bossman wants me to replace 9-12 people and their entire business in a fucking week. Yeah.
"Oh, but it's just sms verification" says he. What he also wants is the ability to flag users as fraudulent, have sticky verifications so they can't bypass them by backing out, have email checks as well as sms, have deferred verification to allow collecting required info (e.g. phone number), verification fallback, lockouts, manual admin whitelisting, admin blacklisting, and different rules per merchant and rule groups for affiliates to apply to all of their merchants, and of course the ability to customize those merchant/affiliate anti-fraud rules. But he shortens this gigantic list to "I want sms verification," despite actually asking for all of the above. I don't want to know about the mental gymnastics and/or blindfolding required to equate the two, but he's nuts.
Yeah.
All of that.
In a goddamn week.
And I get chewed out when it isn't done? Fuck off.
Go build me a goddamn 5m ft^2 castle out of basalt and marble using only your toothbrush and a rusty garden trowel, and have it done in a week. No outsourcing.
talk about ridiculous.5 -
Mac: Hello welcome please sign in
Dev: Fair enough
Mac: Oh you haven’t signed in in awhile please get get verification from other device
Dev: kk
Mac: Oh you don’t have a dev account, please sign in on this website
Dev: Hm.
Mac: In order to sign up for a dev account you need to download this app
Dev: ???
Mac: Are you sure you want to open this app you just downloaded?
Dev: Sigh.
Mac: In order to sign up for a dev account on this app you need to sign into it
Dev: For the love of god
Mac: Ok now you can build with Xcode.
Xcode: No you can’t. You have to sign in
Dev: fuck sakes.
Mac: Are you sure you want Xcode to access files on your computer?
Dev: …Yup
Xcode: Signing in isn’t enough you have to select the fact you are signed in a dropdown nested 3 menus deep.
Dev: God damn.
Xcode: Build failed please sign in to phone as well.
Phone: New sign in detected, please verify with alternative device.
Dev: Jesus.
Xcode: Build success! Pushing to iPhone.
Dev: Finally.
Xcode: Unknown error occurred. Please go to support.apple.com for help. :)
Dev: …18 -
During teacher office hours a few years back: if you have questions on your homework, maybe it's too hard and you should switch majors to something easier, many girls do, so there's no shame in it.
I had asked for verification that my standard deviation logic was correct before spending the time coding it and then figuring out what was wrong.
Ps- he's no longer employed by the school for other sexist reasons.28 -
I... uhm... I... I can't... I ... I can't even.... THIS IS LIVE IN THE CLIENT'S SITE WHERE ANYONE CAN CREATE A LOGIN WITH NO VERIFICATION WHATSOEVER AND SEE THIS WHICH IS LINKED TO A BIG RED BUTTON THAT RESETS THE WHOLE DATABASE, YOU FUCKING DUMB PIECE OF SHIT!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
// This event clears the entire solution in all active clients, truncates the database and also removes any stored PDFs in the server folder
$(document).on('click', '#resetDB', function () {
// This event only happens if the user correctly enters the password, this is to prevent other users than the admin from performing this action
var answer = prompt("Please enter the password required to perform this action.");
if(answer == "-REDACTEDBECAUSEHOLYSHIT-") {
socket.emit('resetDB');
} else {
alert("The password is incorrect, please try again!");
}
});
AAAAAAAAHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHHH!!!!111!!1!!11!1!!1!1one!one!!!11
(I'm not inventing this, even though the "site" is internal only and not accessible through the web. That does *not* make it any less stupid!) 11
11 -
WHAT DO YOU MEAN INVALID CREDENTIALS.
I JUST LOGGED IN WITH THEM ON YOUR SHITTY FUCKING WEBSITE YOU FUCKING INCOMPETENT PIECE OF WANK.
FUCK YOU YOU ARE THE WORST FUCKING CREDENTIALS SYSTEM I'VE EVER FUCKING SEEN; AND I'VE USED YAHOO8 -
All my unit tests work, all my component tests work, why the FUCK does it give me a 'Verification Failed' error?
1 hour later:
Oh wait this is the wrong public key2 -
Appreciation post.
Fucking love Amazon even more now.
Story -
I created a new Aws account and they asked me to pay ₹2 (0.031$) as part of the verification process.
No big deal right?
2 days later, I got a notification saying - "Your account has been credited with ₹2.66"
Not only they returned me my money, but they also paid a certain interest with it too.
And the fact that they are taking care of their dev community (as if we are their customers) is appreciable.
Amazon - you bloody have my respect. I trust you.
No big deal7 -
Ah, every time I am on VPN, on every single website I have to prove that I am not a robot.
Just because I am using a VPN service to protect my information, that does not mean I am about to fuck the website up or DDoS the shit out of you. I wish the CDN providers would understand that and make our life easier.
I am seriously tired of completing the Google verification. Select the vehicle, bike, sign post, dick, vagina, Mia Khalifa. FUCK OFF11 -
> Root struggles with her ticket
> Boss struggles too
> Also: random thoughts about this job
I've been sick lately, and it's the kind of sick where I'm exhausted all day, every day (infuriatingly, except at night). While tired, I can't think, so I can't really work, but I'm during my probationary period at work, so I've still been doing my best -- which, honestly, is pretty shit right now.
My current project involves legal agreements, and changing agent authorization methods (written, telephone recording, or letting the user click a link). Each of these, and depending on the type of transaction, requires a different legal agreement. And the logic and structure surrounding these is intricate and confusing to follow. I've been struggling through this and the project's ever-expanding scope for weeks, and specifically the agreements logic for the past few days. I've felt embarrassed and guilty for making so little progress, and that (and a bunch of other things) are making me depressed.
Today, I finally gave up and asked my boss for help. We had an hour and a half call where we worked through it together (at 6pm...). Despite having written quite a bit of the code and tests, he was often saying things like "How is this not working? This doesn't make any sense." So I don't feel quite so bad now.
I knew the code was complex and sprawling and unintuitive, but seeing one of its authors struggling too was really cathartic.
On an unrelated note, I asked the most senior dev (a Macintosh Lisa dev) why everything was using strings instead of symbols (in Rails) since symbols are much faster. That got him looking into the benchmarks, and he found that symbols are about twice as fast (for his minimal test, anyway), and he suggested we switch to those. His word is gold; mine is ignorable. kind of annoying. but anyway, he further went into optimizing the lookup of a giant array of strings, and discovered bsearch. (it's a divide-and-conquer lookup). and here I am wondering why they didn't implement it that way to begin with. 🙄
I don't think I'm learning much here, except how to work with a "mature" codebase. To take a page from @Rutee07, I think "mature" here means the same as in porn: not something you ever want ot see or think about.
I mean, I'm learning other things, too, like how to delegate methods from one model to another, but I have yet to see why you would want to. Every use of it I've explored thus far has just complicated things, like delegating methods on a child of a 1:n relation to the parent. Which child? How does that work? No bloody clue! but it does, somehow, after I copy/pasted a bunch of esoteric legacy bs and fussed with it enough.
I feel like once I get a good grasp of the various payment wrappers, verification/anti-fraud integration, and per-business fraud rules I'll have learned most of what they can offer. Specifically those because I had written a baby version of them at a previous job (Hell), and was trying to architect exactly what this company already has built.
I like a few things about this company. I like my boss. I like the remote work. I like the code reviews. I like the pay. I like the office and some socializing twice a year.
But I don't like the codebase. at all. and I don't have any friends here. My boss is friendly, but he's not a friend. I feel like my last boss (both bosses) were, or could have been if I was more social. But here? I feel alone. I'm assigned work, and my boss is friendly when talking about work, but that's all he's there for. Out of the two female devs I work with, one basically just ignores me, and the other only ever talks about work in ways I can barely understand, and she's a little pushy, and just... really irritating. The "senior" devs (in quotes because they're honestly not amazing) just don't have time, which i understand. but at the same time... i don't have *anyone* to talk to. It really sucks.
I'm not happy here.
I miss my last job.
But the reason I left that one is because this job allows me to move and work remotely. I got a counter-offer from them exactly matching my current job, sans the code reviews. but we haven't moved yet. and if I leave and go back there without having moved, it'll look like i just abandoned them. and that's the last thing I want them to think.
So, I'm stuck here for awhile.
not that it's a bad thing, but i'm feeling overwhelmed and stressed. and it's just not a good fit. but maybe I'll actually start learning things. and I suppose that's also why I took the job.
So, ever onward, I guess.
It would just be nice if I could take some of the happy along with me.7 -
Friend's site, mail verification, nextcloud etc. all went down...
Checked all his servers, all his configs and what not... Just to realize the moron forgot to pay his bills (so his domain expired)...5 -
Recovering a legacy Gmail account after receiving a notice of a blocked login.
*Tries to remember the bloody password*
*Actually remembers it*
> Sorry your password isn't enough. Your father's phone number that you used a decade ago can be used for verification though!
Google, let's get this straight. Things have changed. I know the fucking phone number and yes I can enter it, and out of sheer stupidity I did send an authentication code his way. Unfortunately however, things have changed in 10 years. I can instantly kill the fucker on the spot if I were to meet him ever again. Do you think that I'm going to get that fucking code?!
> Oh but you can try to email the code to the very account that you're trying to recover, despite the fact that you know the password for it.
TO THE FUCKING SAME ACCOUNT THAT I'M RECOVERING.
Must've taken a true genius to code that in!!!12 -
Boss insisted that verification link needs to be clicked from same IP address as account registration. Many arguments later, decision is final, we will ignore the numerous ways that this will be a burden to our users.
*Code code, test test, deploy*
We're getting a lot of traffic, we need this bitch to scale! *auto-scale and load balance all the things*
Account creation begins breaking at random, some people receiving the "Your IP address doesn't match" error. Look at login history table, what the shit... All recent logins coming from internal IP addressohfuckmylife need to look at X-Forwarded-For header for actual IP behind load balancer.
IP address matching feature stays. I am sad, drink away sadness.4 -
We are on a roll here people (side note, if You are joining the site, thank you but if you are using disposable email accounts at least wait for the verification code to arrive to said account):
So our most well know and belowed CMS that brings lots of love and feels to those that have to (still) deal with it, had some interesting going on:
Oh Joy! "Backdoor in Captcha Plugin Affects 300K WordPress Sites", well arent You a really naughty little boy, eh?
https://wordfence.com/blog/2017/...
Remember that "little" miner thingy that some users here has thought about using for their site? Even Yours truly that does make use of Ads Networks (fuck you bandwidth is not free) even I have fully condenmed the Miner type ads for alot of reasons, like your computer being used as a literal node for DDoSing, well... how about your "Antivirus" Android phone apps being literally loaded with miner trojans too?
https://securelist.com/jack-of-all-...
"When You literally stopped giving any resembles of a fuck what people think about Your massive conglomerate since You still literally dominate the market since alot of people give zero fucks of how Orwellian We are becoming at neck-breaking speed" aka Google doesnt want other webbrowsers to get into market, Its happy with having MemeFox as its competitor:
https://theregister.co.uk/2017/12/...
Talking about MemeFox fucking up again:
https://theregister.co.uk/2017/12/...
And of course here at Legion Front we cant make finish a report without our shitting at Amazon news report:
"French gov files €10m complaint: Claims Amazon abused dominance
Probe found unfair contracts for sellers"
More News at:
https://legionfront.me/page/news
And for what you may actually came and not me reporting stuff at Legion's Orwell Hour News™ ... the free games, right?:
Oxenfree is free in GoG, its a good game, I played like 2 months after its release and I think I heard they wanted to make a Live Action movie or some sort of thing after it:
https://www.gog.com/game/oxenfree
Kingdom Classic is also free:
http://store.steampowered.com/app/...
Close Order Steam Key: HWRMI-2V3PQ-ZQX8B
More Free Keys at:
https://legionfront.me/ccgr 4
4 -
Other services : Please type your phone number to verify that it is you. It will be only used for verification process.
Me : Sure, why not? (Happily types in my number)
Facebook : Please type your phone number to verify that it is you.
Me : Hmmm (sees help)
Facebook : It will be used for verification process and will be visible to your friends. You can always change the scope settings.
Me : (reads as...) It will be used for verification process and will be visible to your friends and will be automatically sent to the NSA for free. You can always change the scope settings when you become the CEO of Facebook.
#deletefacebook -
So I just created this Registration GUI (part of a bigger app) for my uni project and was demonstrating how good the app was to all my friends.
Suddenly someone came and said let me verify this. I said go on with a doubtful mind. Obviously I had some verification for all the fields in the GUI but I was closely watching him.
He signed up with this email: " @ . "
😞10 -
!!oracle
I'm trying to install a minecraft modpack to play with a friend, and I'm super psyced about it. According to the modpack instructions, the first step is to download the java8 jre. Not sure if I actually need it or not, but it can download while I'm doing everything else, so I dutifully go to the download page and find the appropriate version. The download link does point to the file, but redirects to a login page instead. Apparently I need an oracle account to download anything on their site. stupid.
So I make an account. It requires my life story, or at least full name and address and phone number. stupid. So my name is now "fuck off" and I live in Hell, Michigan. My email is also "gofuckyourself" because I'm feeling spiteful. Also, for some reason every character takes about 3/4ths of a second to type, so it's very slow going. Passwords also cannot contain spaces, which makes me think they're doing some stupid "security" shenanigans like custom reversible encryption with some 5th grade math. or they're just stupid. Whatever, I make the stupid account.
Afterwards, I try to log in, but apparently my browser-saved credentials are wrong? I try a few more times, try enabling all of the javascripts, etc. No beans. Okay, maybe I can't use it until I verify the email? That actually makes some sense. Fine, I go check the throwaway inbox. No verification email. It's been like five minutes, but it's oracle so they probably just failed at it like everything else, so I try to have them resend the email. I find the resend link, and try it. Every time I enter my email address, though, it either gives me a validation error or a server error. I try a few mores times, and give up. I try to log in again; no dice. Giving up, I go do something else for awhile.
On a whim later, I check for the verification email again. Apparently it just takes bloody forever, but it did show up. Except instead of the first name "Fuck" I entered, I'm now "Andrew", apparently. okay.... whatever. I click the verify button anyway, and to my surprise it actually works, and says that I'm now allowed to use my account. Yay!
So, I go back to the login page (from the download link) and enter my credentials. A new error appears! I cannot use redirects, apparently, and "must type in the page address I want to visit manually." huh? okay, i go to the page directly, and see the same bloody error because of course i do because oracle fucking sucks. So I close the page, go back to the download list, click the link, wait for the login page redirect (which is so totally not allowed, apparently, except it works and manual navigation does not. yay backwards!), and try to log in.
Instead of being presented with an error because of the redirect, it lets me (try to) log in. But despite using prefilled creds (and also copy/pasting), it tells me they're invalid. I open a new tab container, clear the cache (just to be thorough), and repeat the above steps. This time it redirects me to a single signon server page (their concept of oauth), and presents me with a system error telling me to contact "the Administrator." -.- Any second attempts, refreshes, etc. just display the same error.
Further attempts to log in from the download page fail with the same invalid credentials error as before.
Fucking oracle and their reverse Midas touch.10 -
Holy fuck nvidia. Why the fuck you want me to login to your fucking app in order to download a fucking driver. You also want me to click a fucking link that you sent to my email for verification on every fucking login? Why on earth someone would stole my fucking nvidia account? To see which drivers I use? What the fuck nvidia? Oh wait. DO YOU DARE ASK ME TO SETUP TWO FACTOR AUTH TO SECURE MY ACCOUNT?!? What the fuck? Even if I put my credentials online no one would care to login my fucking nvidia account. Just let me download my fucking driver!4
-
I bypassed SSL certificate verification because that goddam certificate had some flags which my JVM did not understand and threw errors. Still in prod after 10+ years 🤐1
-
I've just noticed an app review that I've given and would fit right into the wk123 (that's the insult one, right?).
"Biggest pile of junk that I've ever seen. You have one job! To register the fucking phone number (which you could get with Phone permission) and verify it (which you can do with the SMS permission) and you should either have the user do that once upon installation or you automate it entirely so that it can run in the background! You can fully automate this, and it's not that complicated that it needs 10 whole seconds of loading time in between! Heck, this pile of crap can't even continue into the main view after entering the verification code! You haven't published the source code (and maybe that's for the best) but if it was, I'd probably immediately get cancer by viewing your crappy spaghetti code. Dear developer, please take a step back and (re)join the PC tech support guys. You have no place in the development world."
To top it all off, that app currently only needs phone permission to verify my number (at least they've done that much). So I figured, I've already gone through that authentication flow so let's remove that permission to abide by the principle of least privilege.
Except that the fucking crapp just goes through the "requires phone permission" shit again whenever that permission removal happens. Fucking piece of garbage!!! That such spaghetti code fuckers even have a job, it boggles my mind.4 -
.... And it appears my Atom has Entered the Matrix. Full time.
In other news, I successfully completed the E-Commerce App I was working on, even though that Stripe Verification was a ball ache and the bane of the entire project giving me a stupid bug in jQuery whereby it was infinite looping over adding the token and not actually submitting the card charge. Somehow changing my button from using an id to using a class fixed my problem :/ (# -> .) 11
11 -
Just to clarify thing, FaceID isn't the same tech as what we've had on Android.
In Android, it's based on image recognition. That's the reason it was so easy to bypass with a high resolution photograph.
In FaceID, it projects thousands of dots on your face and creates a depth inclusive map which is used for verification. That's the reason why it's supposed to work even if you have glasses on, etc
So please let's stop with the comparison11 -
What kind of stupid verification is this ??
apparently, you have to hit the arrow buttons till the animal in the "front" is straight fro the screen and press on done, and if not done in 5 seconds, it says you need to faster, WTAF!!! 9
9 -
Built a software portal that tied in with our schools user management systems (fuck that shit btw, was written in Java that tied back to a JS backend) and I couldnt get password verification working probably so put a test in that just let you put the username in and whatever password and as long as the user wasn't currently in use you login correctly (only used it to track download limits and display the student's name)
Planned on fixing it the following week when my contract was supposed to renew, but they never renewed it and every time they have had me come back I haven't had the chance to fix it ¯\_(ツ)_/¯5 -
Long rant ahead.. 5k characters pretty much completely used. So feel free to have another cup of coffee and have a seat 🙂
So.. a while back this flash drive was stolen from me, right. Well it turns out that other than me, the other guy in that incident also got to the police 😃
Now, let me explain the smiley face. At the time of the incident I was completely at fault. I had no real reason to throw a punch at this guy and my only "excuse" would be that I was drunk as fuck - I've never drank so much as I did that day. Needless to say, not a very good excuse and I don't treat it as such.
But that guy and whoever else it was that he was with, that was the guy (or at least part of the group that did) that stole that flash drive from me.
Context: https://devrant.com/rants/2049733 and https://devrant.com/rants/2088970
So that's great! I thought that I'd lost this flash drive and most importantly the data on it forever. But just this Friday evening as I was meeting with my friend to buy some illicit electronics (high voltage, low frequency arc generators if you catch my drift), a policeman came along and told me about that other guy filing a report as well, with apparently much of the blame now lying on his side due to him having punched me right into the hospital.
So I told the cop, well most of the blame is on me really, I shouldn't have started that fight to begin with, and for that matter not have drunk that much, yada yada yada.. anyway he walked away (good grief, as I was having that friend on visit to purchase those electronics at that exact time!) and he said that this case could just be classified then. Maybe just come along next week to the police office to file a proper explanation but maybe even that won't be needed.
So yeah, great. But for me there's more in it of course - that other guy knows more about that flash drive and the data on it that I care about. So I figured, let's go to the police office and arrange an appointment with this guy. And I got thinking about the technicalities for if I see that drive back and want to recover its data.
So I've got 2 phones, 1 rooted but reliant on the other one that's unrooted for a data connection to my home (because Android Q, and no bootable TWRP available for it yet). And theoretically a laptop that I can put Arch on it no problem but its display backlight is cooked. So if I want to bring that one I'd have to rely on a display from them. Good luck getting that done. No option. And then there's a flash drive that I can bake up with a portable Arch install that I can sideload from one of their machines but on that.. even more so - good luck getting that done. So my phones are my only option.
Just to be clear, the technical challenge is to read that flash drive and get as much data off of it as possible. The drive is 32GB large and has about 16GB used. So I'll need at least that much on whatever I decide to store a copy on, assuming unchanged contents (unlikely). My Nexus 6P with a VPN profile to connect to my home network has 32GB of storage. So theoretically I could use dd and pipe it to gzip to compress the zeroes. That'd give me a resulting file that's close to the actual usage on the flash drive in size. But just in case.. my OnePlus 6T has 256GB of storage but it's got no root access.. so I don't have block access to an attached flash drive from it. Worst case I'd have to open a WiFi hotspot to it and get an sshd going for the Nexus to connect to.
And there we have it! A large storage device, no root access, that nonetheless can make use of something else that doesn't have the storage but satisfies the other requirements.
And then we have things like parted to read out the partition table (and if unchanged, cryptsetup to read out LUKS). Now, I don't know if Termux has these and frankly I don't care. What I need for that is a chroot. But I can't just install Arch x86_64 on a flash drive and plug it into my phone. Linux Deploy to the rescue! 😁
It can make chrooted installations of common distributions on arm64, and it comes extremely close to actual Linux. With some Linux magic I could make that able to read the block device from Android and do all the required sorcery with it. Just a USB-C to 3x USB-A hub required (which I have), with the target flash drive and one to store my chroot on, connected to my Nexus. And fixed!
Let's see if I can get that flash drive back!
P.S.: if you're into electronics and worried about getting stuff like this stolen, customize it. I happen to know one particular property of that flash drive that I can use for verification, although it wasn't explicitly customized. But for instance in that flash drive there was a decorative LED. Those are current limited by a resistor. Factory default can be say 200 ohm - replace it with one with a higher value. That way you can without any doubt verify it to be yours. Along with other extra security additions, this is one of the things I'll be adding to my "keychain v2".10 -
Have you encountered projects that were beyond saving?
Been freelancing for a client via agency for the past year. In the beginning the deal was to maintain identity verification sdk for android maybe 10-15 hours a month or so. Their flow consisted of around 25-30 screens, so I took it thinking it was easy. Boy I was wrong.
Codebase was and still is a complete spaghetti, backend weird and overcomplicated and impossible to talk with someone in backend. Had to reverse engineer their complicated flows many times just to make a small change on the app. There also are lots of issues with capturing/sending camera recordings especially on older devices. The fact that Im the only dev maintaining this doesnt help either.
First few months it was just maintenance, later some small features and soon it become a 40 hour a month gig. I was able to deal with it but then management changed, they started micromanaging me heavily and now they want me to do 60-70 hours a month. Also they asked to implement some unnecessarily complicated features and to be honest without refactoring most of the codebase I cant even begin to think of how to implement them.
Also workload in my main job increased. Started sacrificing my evenings, weekends and basically my wellbeing to work on their product. Tried to relax but then I realized Im just spending my freetime thinking about their project all of the time. Best part is that last few updates fucked up the whole flow and I dont even understand where the problem is anymore: backend, 3rd party integration issues or something else that I did.
Last friday told them that my availability changed and Im quitting. Told them that Im gonna provide support till the end of the month but no big features. Just spent a full shift in my main job and another full shift working on their product, trying to untagle their spaghetti.. Im totally lost and burned out. Meanwhile stupid manager is asking why "simple" stuff according to him is taking too long.
I should receive my last payment from agency this week, also asked them to send it to me earlier but no answer so far. At this point Im so burned out that I dont care anymore about the last payment, even if client complains that everything is broken and doesnt want to pay me. Project is beyond fucked and that SDK as well as their backend is a ticking time bomb. Im done.12 -
Apple has the best UX:
"Type your password followed by the verification code shown on your other devices" 4
4 -
Hello devRant, this is going to be my first time posting on the site.
I work for a gaming community on the side, and today one of the managers asked me to implement a blacklist system into the chat and reactivate the previously existing one temporarily. This shouldn't have had any issues and should've been implemented within minutes. Once it was done and tested, I pushed it to the main server. This is the moment I found out the previous developer apparently decided it would be the best idea to use the internal function that verifies that the sender isn't blacklisted or using any blacklisted words as a logger for the server/panel, even though there is another internal function that does all the logging plus it's more detailed than the verification one he used. But the panel he designed to access and log all of this, always expects the response to be true, so if it returns false it would break the addon used to send details to the panel which would break the server. The only way to get around it is by removing the entire panel, but then they lose access to the details not logged to the server.
May not have explained this the best, but the way it is designed is just completely screwed up and just really needs a full redo, but the managers don't want to redo do it since apparently, this is the best way it can be done.7 -
Finally finished the screwdriver followup ticket. I think.
I spent almost two full days (14 hours) on a seemingly simple bug on Friday, and then another four hours yesterday. Worse yet: I can’t test this locally due to how Apple notifications work, so I can only debug this on one particular server that lives outside of our VPN — which is ofc in high demand. And the servers are unreliable, often have incorrect configuration, missing data, random 504s, and ssh likes to disconnect. Especially while running setup scripts, hence the above. So it’s difficult to know if things are failing because there’s a bug or the server is just a piece of shit, or just doesn’t like you that day.
But the worst fucking part of all? The bug appeared different on Monday than it did on Friday. Like, significantly different.
On Friday, a particular event killed all notifications for all subsequent events thereafter, even unrelated ones, and nothing would cause them to work again. This had me diving through the bowels of several systems, scouring the application logs, replicating the issue across multiple devices, etc. I verified the exact same behavior several times over, and it made absolutely no sense. I wrote specs to verify the screwdriver code worked as expected, and it always did. But an integration test that used consumer-facing controller actions exhibited the behavior, so it wasn’t in my code.
On Monday while someone else was watching: That particular event killed all notifications but ONLY FOR RELATED EVENTS, AND THEY RESUMED AFTER ANOTHER EVENT. All other events and their notifications worked perfectly.
AKL;SJF;LSF
I think I fixed it — waiting on verification — and if it is indeed fixed, it was because two fucking push event records were treated as unique and silently failing to save, run callbacks, etc.
BUT THIS DOESN’T MATCH WHAT I VERIFIED MULTIPLE TIMES! ASDFJ;AKLSDF
I’m so fucking done with this bs.8 -
First year: intro to programming, basic data structures and algos, parallel programming, databases and a project to finish it. Homework should be kept track of via some version control. Should also be some calculus and linear algebra.
Second year:
Introduce more complex subjects such as programming paradigms, compilers and language theory, low level programming + logic design + basic processor design, logic for system verification, statistics and graph theory. Should also be a project with a company.
Year three:
Advanced algos, datastructures and algorithm analysis. Intro to Computer and data security. Optional courses in graphics programming, machine learning, compilers and automata, embedded systems etc. ends with a big project that goes in depth into a CS subject, not a regular software project in java basically.4 -
Guys what I want to know is how do you secure your code so that they pay you after you deliver the code to them?
So recently I was in this internship that I secured with an over-the-phone interview and the guy who was contacting me was the CEO of the company (I'm going to refer to him as "the fucking cunt" from now on). He asked me to do some OCR and translations and I managed to write a few scripts that automate the entire process. The fucking cunt made me login remotely to his desktop which was connected to the server (who the fuck does that) and I had to operate on the server from his system. I helped him with the installation and taught him how to use the scripts by altering the parameters and stuff, and you know what the fucking cunt did from the next day onward? Dropped contact. Like completely. I kept bombing emails upon emails and tried calling him day after day, the fucking cunt either picked up and cut the call immediately on recognising its me or didn't pick up at all. And the reason he wasn't able to pay me was, and I quote, "I am in US right now, will pay you when I get back to India." I was like "The fuck was PayPal invented for?" Being the naive fool that I was, I believed him (it was my first time) and waited patiently till the date he mentioned and then lodged a complain in the portal itself where he had posted the job initially. They raised a concern with the employer and you know what the fucking cunt replied? "He has not been able to achieve enough accuracy on the translations". Doesn't even know good translation systems don't exist till date ( BTW I used a client for the google translate API). It has been weeks now and still the bitch has not yet resolved the issue.And the worst part of it was I got a signed contract and gave him a copy of my ID for verification purposes.
I'm thinking of making a mail bomb and nagging him every single day for the rest of his life. What do you guys think?7 -
Google Business Profile is probably not meant for developers. "Help customers find your business by industry." Dev: set primary category to "Web Developer". Google: We didn't understand your category. Please select from the suggestions that appear when typing. Dev, typing: "Web D"... Google suggests: "Web Designer, Web hosting company, Well drilling contractor, Waterbed shop". Okay, Google, nevermind.
Google: "Update your customers. Keep your customers up to date about your business!" Dev clicks "add update", adds info about that customer should use different phone number temporarily due to broken phone. Google: "Your post has been removed from your Business Profile on Google because it violates one or more of our post content policies." Okay Google, at least you let me add an additional phone number on my profile without requiring to verify my primary number that I currently have not access to. Anything else?
Google: "Claim your €400 free advertising credit" Dev: clicks "claim credit" Google: "To access this Google Ads account, enable 2-Step Verification in your Google account." How to combine idiocy and deceptive patterns in a single UI: Google knows! Apart from their search engine, their unique business advantage is simple that they suck a little less than Apple and Microsoft. Sorry, not a day to be proud of our profession, once again.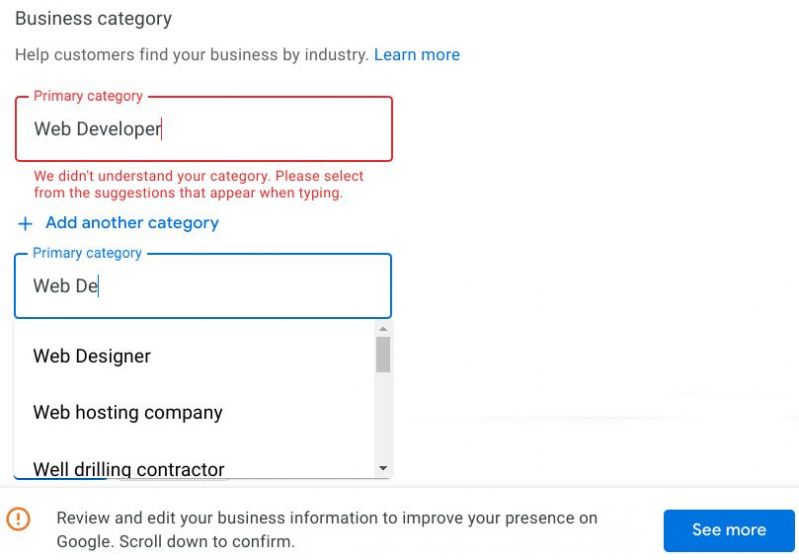 5
5 -
You know u have no life when you get a call, you're all excited about who's it going to be...
"oooh an unknown number!"
*picks up*
"who's this?"
... *automated voice* "This is apple calling you for your apple verification code... your code is..."
And u realize u have ur computer on which u need to enter your code because u tried to login 2 minutes ago...2 -
For some reason, Google really, really, really wants to know peoples' phone numbers.
Of course, they say it is "only to protect us even more". But if the Twitter phone number misuse incident tells us anything, Google could change their mind at any time.
Around 2012, Google started begging people for their phone numbers upon login, but did not lock users out yet: https://groovypost.com/unplugged/... .
At some point, likely in the late 2010s, Google started locking people out of their accounts until they disclose their phone numbers. This is very unethical. Twitter already did it earlier (around 2016). Many countries' governments outlawed burner phones and people need to disclose their identity to acquire a phone number, as often under the pretext of "fighting terrorism". Surely not for mass-surveillance, am I right? ( https://comparitech.com/blog/... )
Since a few years, Google demands a phone verification for every newly created account. Honestly, that is still better than holding peoples' existing accounts hostage until they disclose a phone number, since locking people out of their accounts a while after creation causes them to lose access to their data.
Of course, people should store any data they do not wish to lose locally. Online services are not personal archives.6 -
Seems someone from China was trying to hack my Apple ID. Due to 2-factor verification, was able to deny access and then I quickly changed password and forced sign-out of all accounts. Perhaps my password appeared in some data leak— it was not changed since 2 years.
Y’all make sure to enable 2-factor authentication and change passwords from time to time. 5
5 -
Elon musk has shown himself to be a terrible person, a worse manager and someone who hasn't a clue of what a code review is. A summarily fires so many people that he can't find someone to open the doors for his big in person meeting or the vet the badges. He offers 3 months termination pay or you can work 12 hours a day 7 days a week hardcore. But none of the payroll people are around anymore either. Critical subsystems have not a single engineer left to work on them. He's paranoid that employees will sabotage the software. But I think he's doing such a good job it would be impossible to tell that anyone else was helping him.
An engineer wrote a prescient seven page report listing problems ahead including user verification. So Elon twit-fired him.
Also entirely predictable is the stress that the world cup will put on the system beginning today, I believe. He doesn't "like" microservices.
I work for the psychiatrist once who barely needed to sleep. Maybe Elon can function with 12-hour days week in week out. But it's cool to think you're going to squeeze substantially more work out of people by doubling their hours. More likely you will more than double their errors and what will that do to you budget? 50 years ago IBM determined that the best way to improve programmer productivity was to give each one their own office.
I can't believe he's whining over spending 13 million dollars a year on food. That is so far from being a strategic item. Soapbox out.28 -
Internal mail form CIO's office:
"Thank you for being part of the internal trial for NPMe, we have decided to remove this tool in favour of Artifactory because of its support for multiple platforms and tools. We are sorry for the inconvenience, here is a link to migration scripts ..."
Migration "script" readme, please clone this repo, create file A, and B, and install these 2 dependencies.
Dependency 1:
- "install via homebrew ..."
- .... homebrew needs to update, checking for updates
- 10 mins later = Update failed, please upgrade to Ruby version 2.3
- Installs ruby version manager
- GPG signature verification failed
- Install GPG v2 + accept keys
- Install ruby version manager
- "please execute this command before running rvm"
- execute command
- "rvm install ruby-2.3"
- Install failed, please see log file
- Opens log file
- "Xcode on its own is not sufficient, please install xcode cli tools"
- Install xcode tools
- 5 minutes later -> "rvm install ruby-2.3"
- 10 minutes later "brew install jq"
Ok back to read me, "login to Artifactory, go here and copy paste XXX."
- Login to Artifactory
- Eventually find repo
- Login again to actually see credentials for some reason
- Screen doesn't match instructions in readme
- Click around
- Back to readme
- Back to artifactory
- Login again
- Execute command auth / setup command
- Copy contents to npmrc file .... now all my scoped packages are going to point to 1 specific repo
Fuck the migration, Fuck these shitty instructions, i'll set them all up again manually. See tags below for further opinions on this matter.undefined fuck ruby fuck homebrew fuck this fuck shitty cli fuck artifactory fuck cli fuck jq fuck rvm2 -
TL;DR: Google asked me to PROVIDE a phone number to verify connection from a new device, on the said device.
Yesterdayto log into my work Google account from my personal laptop to check emails, calendars update and so on. I opened up a private navigation window, went to Google sign-in page, entered my credentials, all is well.
Google then decided to "verify it's me" and prompted me to PROVIDE a phone number (work account without work phone means no phone number set up) so that they can send a verification code to the number I just provided to make sure the connection is legit.
Didn't want to do that, clicked "use another method" and got asked to fill the last password I remember, which would be my current password thanks to my trusty password manager. After submitting, I'm prompted with an error saying I have to contact my admin to reset my password because they can't log me in with my CURRENT password.
I ain't gonna do that, so went back to login page, provided my phone number, got the code, filled in the code, next thing I know I'm browsing through my emails.
What the duck? Could have been anybody giving any phone number. So much for extra security.
Also don't care that they have my phone number, the issue is more about the way used to obtain it: locking me out of my account and having no other way of logging in.6 -
Regarding Article 13 (or 17 or wherever it moved to now)… Let's say that the UK politicians decide to be dicks and approve the law. After that, we need to get it engineered in, right? Let's talk a bit about how.. well, I'd maybe go over it. Been thinking about it a bit in the shower earlier, so.. yeah.
So, fancy image recognition or text recognition from articles scattered all over the internet, I think we can all agree.. that's infeasible. Even more so, during this lobby with GitHub and OpenForum Europe, guy from GitHub actually made a very valid point. Now for starters, copyright infringement isn't an issue on the platform GitHub that pretty much breathes collaboration. But in the case of I-Boot for example, that thing from Apple that got leaked earlier. If that would get preemptively blocked.. well there's no public source code for it to get compared against to begin with, right? So it's not just "scattered all over the internet, good luck crawling it", it's nowhere to be found *at all*.
So content filtering.. yeah. Nope, ain't gonna happen. Keep trying with that, EU politicians.
But let's say that I am a content creator who hates the cancer of joke/meme because more often than not it manifests itself as a clone of r/programmerhumor.. someone decides to freeboot my content. So I go out, look for it, find it. Facebook and the likes, make it easier to find it in the first place, you dicks. It's extremely hard to find your content there.
So Facebook implements a way to find that content a bit easier maybe. Me being the content creator finds it.. oh blimey! It can't be.. it's the king of freebooting on Facebook, SoFlo! Who would've thought?! So at that point.. I'd like to get it removed of course. Report it as copyright infringement? Of course. Again Facebook you dicks, don't make it so tedious to fill in that bloody report. And look into it quickly! The videos those SoFlo dicks post is only relevant in the first 48h or so. That's where they make the most money. So act more quickly.
So the report is filled, video's taken down.. what else? Maybe temporarily make them unable to post as a bit of a punishment so that they won't do it again? And put in a limit to the amount of reports they can receive. Finally, maybe reroute the revenue stream to the original content creator instead. That way stolen content suddenly becomes free exposure! Awesome!
*suddenly realizes that I've been talking about the YouTube copyright strike system all along*
… Well.. maybe something like that then? That shouldn't be too hard to implement, and on YouTube at least it seems to be quite effective. Just imagine SoFlo and the likes that are repeat offenders, every 3 posts they get their account and page shut down. Good luck growing an audience that way. And good luck making new accounts all the time to start with.. account verification technology is pretty good these days. Speaking of experience here, tried bypassing Facebook's signup hoops a fair bit and learned a bit about some of the things they have red flags on, hehe.
But yeah, something like that maybe for social media in general. And.. let's face it, the biggest one that would get hurt by something like this would be Facebook. And personally I think it's about time for that bastard company to get a couple of blows already.
What are your thoughts on this?5 -
this just happened a few seconds ago and I am just laughing at the pathetic site that is Facebook. xD
4 years ago:
So I was quite a noobie gamer/hacker(sort of) back then and i had a habit of having multiple gmail/fb accounts, just for gaming, like accounts through which i can log in all at once in the same poker room, so 4/5 players in the game are me, or just some multiple accounts for clash of clans for donations.
I had 7-8 accounts back then. one had a name that translated to "may the dead remain in peace "@yahoomail.com . it was linked to fb using same initials. after sometime only this and 2 of my main accs were all i cared about.even today when i feel like playing, i sometimes use those accs.
2 years ago.
My dad is a simple man and was quite naive to modern techs and used to hang around with physical button nokia phones.But we had a business change, my father was now in a partnership in a restaurant where his daily work included a lot of sitting job and and casual working. So he bought a smartphone for some time pass.
He now wanted to download apps and me to teach him.I tried a lot to get him his own acc, but he couldn't remember his login credentials.
so at the end i added one of my own fake ID's(maythedead...) so he could install from playstore, watch vids on youtube and whatever.
The Actual Adventure starts now
Today, 1 hour ago:
I had completely forgot about this incident, since my parents are now quite modern in terms of tech.
But today out of nowhere i recieved an email that someone has JUST CHAINGED MY FB PASSWORD FOR ONE OF MY FAKE ACCS!?!??
what the hell, i know it was just a useless acc and i never even check my fb from any acc these days, but if someone could login into that acc, its not very difficult to track my main accs, id's, etc so i immediately opened this fb security portal and that's where the stupidity starts:
1)To recover your account they FUCKIN ASKS FOR A PHYSICAL ID. yeah, no email, no security question you have to scan your driving license or passport to get back to your account.And where would I get a license for some person named "may the dead remain in peace"? i simply went back.
2) tried another hack that i thought that will work.Closed fb help page, opened fb again , tried to login with my old credentials, it says" old password has been changed,please enter new password", i click forget password and they send an otp. i thought yes i won, because the number and recover mail id was mine only so i received it.
when i added the otp, i was first sent to a password change page (woohoo, i really won! :)) but then it sends me again to the same fuckin physical id verification page.FFFFFFFFFuck
3)I was sad and terrified that i got hacked.But 10 mins later a mail comes ,"Your Facebook password was reset using the email address on Tuesday, April 10, 2018 at 8:24pm (UTC+05:30)."
I tried clicking the links attached, hoping that the password i changed(point<2>) has actually done something to account.NADA, the account still needs a physical license to open:/
4) lost, i just login to my main account and lookup for my lost fake account. the fun part:my account has the display pic of my father?!!?!
So apparently, my father wanted to try facebook, he used the fake account i gave him to create one, fb showed him that this id already has an fb account attached to it and he accidently changed my password.MY FATHER WAS THE HACKER THE WHOLE TIME xD.
but response from fb?" well sir, if you want your virtually shitty account back , you first will have to provide us with all details of your bank transactions or your voter id card, maybe trump will like it"
-
Oh boy, this is gonna be good:
TL;DR: Digital bailiffs are vulnerable as fuck
So, apparently some debt has come back haunting me, it's a somewhat hefty clai and for the average employee this means a lot, it means a lot to me as well but currently things are looking better so i can pay it jsut like that. However, and this is where it's gonna get good:
The Bailiff sent their first contact by mail, on my company address instead of my personal one (its's important since the debt is on a personal record, not company's) but okay, whatever. So they send me a copy of their court appeal, claiming that "according to our data, you are debtor of this debt". with a URL to their portal with a USERNAME and a PASSWORD in cleartext to the message.
Okay, i thought we were passed sending creds in plaintext to people and use tokenized URL's for initiating a login (siilar to email verification links) but okay! Let's pretend we're a dumbfuck average joe sweating already from the bailiff claims and sweating already by attempting to use the computer for something useful instead of just social media junk, vidya and porn.
So i click on the link (of course with noscript and network graph enabled and general security precautions) and UHOH, already a first red flag: The link redirects to a plain http site with NOT username and password: But other fields called OGM and dossiernumer AND it requires you to fill in your age???
Filling in the received username and password obviously does not work and when inspecting the page... oh boy!
This is a clusterfuck of javascript files that do horrible things, i'm no expert in frontend but nothing from the homebrewn stuff i inspect seems to be proper coding... Okay... Anyways, we keep pretending we're dumbasses and let's move on.
I ask for the seemingly "new" credentials and i receive new credentials again, no tokenized URL. okay.
Now Once i log in i get a horrible looking screen still made in the 90's or early 2000's which just contains: the claimaint, a pie chart in big red for amount unpaid, a box which allows you to write an - i suspect unsanitized - text block input field and... NO DATA! The bailiff STILL cannot show what the documents are as evidence for the claim!
Now we stop being the pretending dumbassery and inspect what's going on: A 'customer portal' that does not redirect to a secure webpage, credentials in plaintext and not even working, and the portal seems to have various calls to various domains i hardly seem to think they can be associated with bailiff operations, but more marketing and such... The portal does not show any of the - required by law - data supporting the claim, and it contains nothing in the user interface showing as such.
The portal is being developed by some company claiming to be "specialized in bailiff software" and oh boy oh boy..they're fucked because...
The GDPR requirements.. .they comply to none of them. And there is no way to request support nor to file a complaint nor to request access to the actual data. No DPO, no dedicated email addresses, nothing.
But this is really the ham: The amount on their portal as claimed debt is completely different from the one they came for today, for the sae benefactor! In Belgium, this is considered illegal and is reason enough to completely make the claim void. the siple reason is that it's unjust for the debtor to assess which amount he has to pay, and obviously bailiffs want to make the people pay the highest amount.
So, i sent the bailiff a business proposal to hire me as an expert to tackle these issues and even sent him a commercial bonus of a reduction of my consultancy fees with the amount of the bailiff claim! Not being sneery or angry, but a polite constructive proposal (which will be entirely to my benefit)
So, basically what i want to say is, when life gives you lemons, use your brain and start making lemonade, and with the rest create fertilizer and whatnot and sent it to the lemonthrower, and make him drink it and tell to you it was "yummy yummy i got my own lemons in my tummy"
So, instead of ranting and being angry and such... i simply sent an email to the bailiff, pointing out various issues (the ones6 -
Chat apps. What's the idea? Those are basically tools of violence. They give you a possibility to in real-time stop someones work and start demanding service. Now. Immediately.
Usually people send you first email and then they after 10 seconds chat "did you see my email?? read it! serve it! please me!" Usually it's just a small request to document something, review someone else's document. Do it ASAP. If you were coding something, then drop it and do someones job for them instead.
You got a request for me to create some verification case list? Put it into my backlog. I might start doing that in week or two. Or month. In case there's nothing else more important. Since I know that you are working with something that you think is the whole universe, but trust me, I got my own problems already.
But hey, if I don't reply to your chat in a minute, please feel free to walk behind me and start explaining your life. No need to wait even for me to get my headphones off. "Oh you are in conf call? Well, this is just a quick thing blaa blaa..."1 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.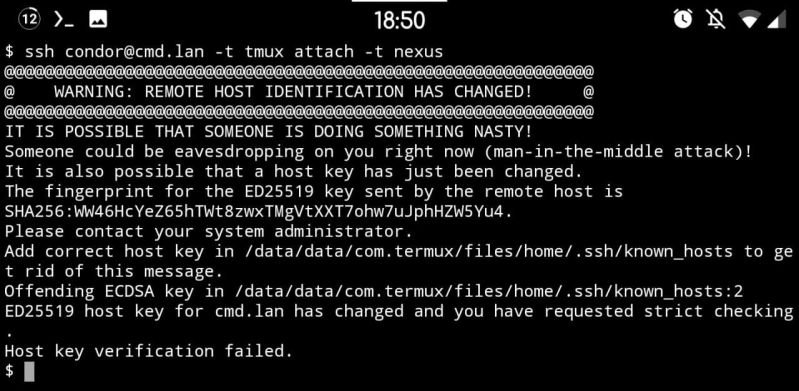 19
19 -
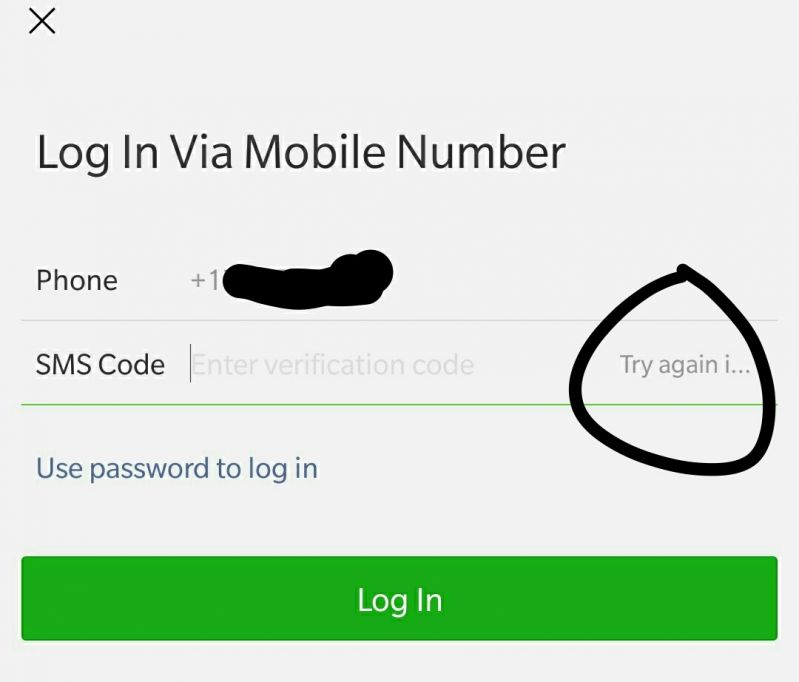
How long till I can try again? Please, tell me! I'm dying to know!!
And I never got the verification code either.
---___--- 7
7 -
This “Auto save” feature in the latest app version is buggy..
-> new rant
-> prefilled with previous rant..
Anyway, here my actual rant begins.
Apple, go fuck yourself, seriously.. put your trillion dollars way up your arse...
Moved to Ireland, want to switch country..
“If you want to switch countries, cancel your Apple Music subscription first”..
so be it. Cancelled it..
“Your subscription will be cancelled in 28 days”.
FUCK YOU, YOU COCK SUCKING BASTARDS!!
I NEED TO SWITCH THE STORE TO BE ABLE TO DOWNLOAD BANKING APPS AND STUFF LIKE THAT..
But ok, I’m screwed in this regard..
Suddenly iMessage stopped working. This is kind of a big deal because I have unlimited data but only unlimited sms to Irish numbers and I need to communicate with people in Switzerland and Germany..
Internet works so I try to turn iMessage off and in again. But that doesn’t work.. i can only reactivate iMessage via WiFi.
So I go back to the hotel, reactivate iMessage..
“Verifying imessage” >> google..
Leads me to an Apple forum: “the verification of iMessage can take up to 24h”.
Are you fucking kidding me? I’m in a new country and rely on this overpriced shit..
Fun but sad fact, I have a second phone with me. IPhone 4 with iOS 7 and that thing WORKS!!
If this is where the future is going we’re all gonna die very soon.. plains crash, power plants explode but hey, at least they have data about it and it looks shiny. That’s all that matters..
Another reason to switch to android..
MacOs fucked me up so I already switched to windows + Linux. Next one will be getting rid of iOS, they don’t build small phones anymore anyway..1 -
A checkout application where, in the confirmation screen, everything (amount, references, currency, quantity of items, etc.) was sent to the client as a form, and they submitted this form to confirm.
...but there was no verification on any of the above. So any of the above could be changed and it'd collect whatever funds, and order whatever items, with whatever references you gave it.
This wasn't a major player in the space, but was big enough that most people would likely have heard of at least some companies using it. It's still being actively used today, and I can near guarantee not all the flaws have been fixed.1 -
fucking zoho and their fucking sign up and authentication process.
they need a mobile phone number for the sing up, alright fine, I provide. but after submitting the form, nothing fucking happened and i am redirected to the initial sign up page. fuck you.
try again and guess what, said my phone number is already used and i can try sign in with it. ok alright, i try to sign in using my number and my password. guess what? i am redirected back at the initital sign up form page. fuckkkkkkkkkk.
i try again with another number. and then this time, guess what? said the fucking email is already existed. jesus fucking fucking christ.
browse around their help desk and found this. https://help.zoho.com/portal/kb/...
sure I follow the advice and guess what? yeah i'm redirected back to the FUCKING GOD DAMN same page again.
I gave up and wanted to send them a reply on their help desk and try to log in using one of my other existing zoho accounts. GUESS WHAT? THEIR HELP DESK LOG IN IS NOT WORKING. ARRRRRRRRRRRRRRRRRRRRRRRRRRRRRR.
I click "Sign In". Login as User or Login as Agent dropdown appear. I click Login as User since my user account is already logged in. It nothing happened. It flashed and I am back at the help desk thread with no changes. It is still "Sign In" at the top. I fucking give up.3 -
Sometimes I feel like I am surrounded by idiots. My family are too stupid and lazy to have jobs or do anything involving a skill. They are too dumb to do anything properly so most of the house is fucked.
My co-workers are supposed to be Web devs but cba to learn the frameworks or languages we work on. Some of them have over 5 years experience and don't understand basics like backend verification vs front end.. Or even what json is. Needless to say everything I'm told to do is retarded such as implement roles and permissions where there are no roles, but ot allowed to add roles.
Anyone else surrounded by idiots 90% of the time? How do you not get worn down?2 -
As a legal thing at work I need to have someone verify my citizenship by filling out a form for my I-9. They ask the person for their title. My husband can’t be serious, so he put that his title is “Keeper of the Swans”.
Here’s hoping I don’t have an awkward convo with legal over the validity of verification by a man claiming the title “Keeper of the Swans”
In his _defense_, the form didn’t let him leave “Title” blank.9 -
A swedish insurance company has two different solution for logging in to their system.
1. An advanced high security single sign on solution involving active directory, verification of the network the request came from etc etc.
2. Using a link and passing your credentials in the query string!!! Like: insurancecompany.com?username=admin&password=password.
Solution 2 works with admin accounts from anywhere.4 -
Really regretted to born in India. I know I should not say bad about the country in which I born and living it but there are so many reasons.
Govt of India is very poor. Nothing can be processed if you don't have offered bribe or you don't have political power and pressure.
My company offering me onsite to go London for my project, govt is not issuing me PCC Police Clearance Certificate even I never had any crime.
Police says for your current address 6 month is duration you're living here so we submitted 6 months crime is nil and 4.5 years is more required.
I went to passport office and happy to submit all documentation for previous addresses so that police verification can be done but no body is taking documents
No progress in my file.
I'm too much frustrated now.
I reported to ministry and prime minister of India but even no progress.
I'm really fed-up.
:(14 -
oh FFS my university pissed me off so bad right now that I had to wait 20 min to cool down to be able to write a rant about it...
so, one of the university department offer an email address which is the official university approved email for student packs like jetbrain's. I wanted to renew my jetbrains subscription, but for that I have to get a verification email on that address..
But since the only time I use it is this annual renewal I dont know the webmail's url..
So I search for it on the department pages, services and its nowhere to be found. Finaly I found it on a student maintained wiki page.
I try to log in.. no luck. try another password, still not it. Try all of the passwords that I remember using in the previous 3 year and no luck.
well fck it the password change is managed by a website where I can log in with a different method, so I change the password and try to log in again.
No fcking luck! And at this point I bashed my head against the wall because I found out that the password change takes them about 1 or 2 hours... hours! wtf...5 -
Google simply can't knock off harrassing their users with security theatre.
A friend of mine has a small personal YouTube channel. He has recently been bombarded with several phone verification requests a week: "Verify it's you. To continue your session, complete a brief verification. This extra step helps us keep your account safe by making sure it’s really you. "
While frequent verifications may be understandable on YouTube channels with millions of subscribers, channels with only a few dozen subscribers are not attractive hacking targets. A verification would be justified before a potentially harmful action such as deleting videos or deleting a channel. But not for normal everyday use.
What's next? Will they ask users to "verify it's them" every ten minutes, "just for extra security"? Just to verify that it is "really, really, really, really, really" them?
It's not security. It's security theatre.
Sorry, Google, but users are not in the mood of doing a phone verification every other day.
Has this been Google's perverted wet dream all along? 1
1 -
telco sysadmin: hey maybe we should secure our SMTP server with SSL and password verification so our clients can e-mail safely!
senior exec be like: nah just filter incoming connections for our own IP-range, that'll do.
result: I can impersonate any client of the telco and send e-mail in their name (from any home network connected to that provider), but I can't send e-mail over cellular network.1 -
Using cookies for verification and validation without encrypting the values which should have been handled in the backend without any use of cookies.
I wonder how vulnerable by website was... -
That's it, where do I send the bill, to Microsoft? Orange highlight in image is my own. As in ownly way to see that something wasn't right. Oh but - Wait, I am on Linux, so I guess I will assume that I need to be on internet explorer to use anything on microsoft.com - is that on the site somewhere maybe? Cause it looks like hell when rendered from Chrome on Ubuntu. Yes I use Ubuntu while developing, eat it haters. FUCK.
This is ridiculous - I actually WANT to use Bing Web Search API. I actually TRIED giving up my email address and phone number to MS. If you fail the I'm not a robot, or if you pass it, who knows, it disappears and says something about being human. I'm human. Give me free API Key. Or shit, I'll pay. Client wants to use Bing so I am using BING GODDAMN YOU.
Why am I so mad? BECAUSE THIS. Oauth through github, great alternative since apparently I am not human according to microsoft. Common theme w them, amiright?
So yeah. Let them see all my githubs. Whatever. Just GO so I can RELAX. Rate limit fuck shit workaround dumb client requirements google can eat me. Whats this, I need to show my email publicly? Verification? Sure just go. But really MS, this looks terrible. If I boot up IE will it look any better? I doubt it but who knows I am not looking at MS CSS. I am going into my github, making it public. Then trying again. Then waiting. Then verifying my email is shown. Great it is hello everyone. COME ON MS. Send me an email. Do something.
I am trying to be patient, but after a few minutes, I revoke access. Must have been a glitch. Go through it again, with public email. Same ugly almost invisible message. Approaching a billable hour in which I made 0 progress. So, lets just see, NO EMAIL from MS, Yes it appears in my GitHub, but I have no way to log into MS. Email doesnt work. OAuth isn't picking it up I guess, I don't even care to think this through.
The whole point is, the error message was hard to discover, seems to be inaccurate, and I can't believe the IRONY or the STUPIDITY (me, me stupid. Me stupid thinking I could get working doing same dumb thing over and over like caveman and rock).
Longer rant made shorter, I cant come up with a single fucking way to get a free BING API Key. So forget it MS. Maybe you'll email me tomorrow. Maybe Github was pretending to be Gitlab for a few minutes.
Maybe I will send this image to my client and tell him "If we use Bing, get used to seeing hard to read error messages like this one". I mean that's why this is so frustrating anyhow - I thought the Google CSE worked FINE for us :/
-
I think the report rant function should have a verification function. Like asking me if I'm sure I want to report this rant.
I just reported a rant I didn't mean to, because I wanted to mute notifications on it3 -
I really hate sales people. My stakeholder wants to buy an address verification service but is hesitant to purchase now because the dev time needed would be substantial. Now the sales rep has planted seeds of doubt in my SH and SH thinks I grossly overestimated the labor I quoted.
Sales rep is all “major corporations have installed this in a weekend.” 🤬🤬🤬 Major corporations also have more than one developer and probably aren’t dealing with a website that has a dozen address forms that all work differently. Oh, and I DON’T WORK WEEKENDS MOFO.
My SH originally requested a labor estimate for installing the AVS on all address forms and that’s what I delivered. My audit revealed a dozen different forms. I’m working with a legacy code base that’s been bandaged together and maintained by an outside dev agency. The only thing the forms have in common is reusable address fields. They all work differently when it comes to validating and submitting data to the server and they all submit to different api endpoints. At least a quarter of those forms are broken and would need to be fixed (these are mostly admin-facing). I also had to provide an estimate on frontend implementation when I have no idea what they want the FE to look like.
My estimate was 5-8 weeks for implementation AND testing. I wrote up my findings and clearly explained the labor required, why it was needed, and the time needed. All was fine until the sales rep tried to get into SH’s head.
My SH is now asking for a new estimate and hoping for 1-2 weeks of labor, which is what will SH to buy the AVS. Then go to the outside dev agency you used to work with and ask for a second opinion. I’m sure they’d also tell you at least month if not more for testing, implementation, and deployment because you have a DOZEN FORMS you want to add this to. 1-2 weeks is only possible for a single form.
My manager doesn’t work in the same coding language I do, but he read my documentation and supports my original estimate.
I honestly want to ask my SH if this sales rep is giving a very good price for the AVS. If not, are there other companies in the mix? Because right now you have a sales rep that’s taking you for a ride and trying to pressure you all so he can get another notch in his belt for getting another “major corporation” as his account. I don’t think it’s a good idea to be locked in with a grimy sales rep.3 -
Enter E-Mail-Address:
"finiteAutomaton@gmail.com"
|> E-Mail-Address is already taken!
Enter E-Mail-Address:
"finiteAutomaton+1@gmail.com"
|> Verification code sent!
I am a hacker!2 -
Bittrex is "amazing"...
I had lost my 2FA a long time ago (as my phone fried) and missed the account ferification deadline which caused my account to get disabled. Off we go to support!
0. Nothing to rant about at this point. I just created an account in their zendesk, logged in and logged a ticket to reset my 2FA and reactivate my account. They asked me for info, I provided it to them and got my 2FA disabled. Hooray!
1. I then asked to reenable my account. They sent me a link to restart the verification process. I open up that link and log in. I'm asked to upload some photos. I select requested photos from my galery and hit [UPLOAD]. An error pops up saying that smth wrong happened and I need to reload that site and reupload my photos. After page refresh they are telling me they are validating my uploaded info (w/o any way to resubmit my info, which, according to the error seen below, was not successfully submitted in the first place)...
2. So I reach out to the support guy again. Guess what he replies! He says he's sorry but he cannot help me any more and I need to create a NEW ACCOUNT in their support site with the same email <???!!!???>
3. I try to log in to the support portal and my access no longer works. MY ACCOUNT HAS BEEN DELETED! WTF!!!
4. I do as I'm told and create a new acc with the same email. Now I can log back in. So I'm raising a new ticket saying I still cannot finish my verification process due to the same error. It looks like it's going to be a fun ride with them so I can't wait to see what they'll reply.2 -
Uber is sending me a verification code every 5 minutes. I don't even have their app anymore.
Please someone tell them to stop, I feel attacked.3 -
Long time ago i ranted here, but i have to write this off my chest.
I'm , as some of you know, a "DevOps" guy, but mainly system infrastructure. I'm responsible for deploying a shitload of applications in regular intervals (2 weeks) manually through the pipeline. No CI/CD yet for the vast majority of applications (only 2 applications actually have CI/CD directly into production)
Today, was such a deployment day. We must ensure things like dns and load balancer configurations and tomcat setups and many many things that have to be "standard". And that last word (standard) is where it goes horribly wrong
Every webapp "should" have a decent health , info and status page according to an agreed format.. NOPE, some dev's just do their thing. When bringing the issue up to said dev the (surprisingly standard) answer is "it's always been like that, i'm not going to change". This is a problem for YEARS and nobody, especially "managers" don't take action whatsoever. This makes verification really troublesome.
But that is not the worst part, no no no.
the worst is THIS:
"git push -a origin master"
Oh yes, this is EVERYWHERE, up to the point that, when i said "enough" and protected the master branch of hieradata (puppet CfgMgmt, is a ENC) people lots their shits... Proper gitflow however is apparently something otherworldly.
After reading this back myself there is in fact a LOT more to tell but i already had enough. I'm gonna close down this rant and see what next week comes in.
There is a positive thing though. After next week, the new quarter starts, and i have the authority to change certain aspects... And then, heads WILL roll on the floor.1 -
The company I used to work for, despite me not working there contacts me to get a verification code because the crappy developer they hired can't change a couple settings on the apple website and add themselves as a developer.
At the start of this all, a couple months back I gave them the code out of courtesy, but at this point, as i'm heavily invested in the development stage of my actual job as a vr developer, I won't take time out of my day to even answer the phone for them.
But what really pisses me off is the person who contacts me, my assumbly best friend, who during the last 12 months has only called me for these codes, so work related shit or just personal shit and never to hang out or play games or generally what we used to do as friends before he got a job at that stupid company doesn't have the balls to tell his boss that i'm busy with my job, that maybe if payment was offered as an incentive that I would be happy to be contacted.
When I left that company I didn't setup anything to make it so they would have to contact me, all I did was add myself as a developer of their app. I also heavily documented everything I did, all the issues I faced and the workarounds I found, and everything including all login information needed to get things working, I went above just "developing" the app I added in all the credits to all work used in the app as partly to make sure we don't get sued for stealing someones work without the right credit.
I hate the fact that I worked for minimum wage and did all of this shit, but I never complained at all about things like the 1 1/2 hour travel time (one way I might add) to my boss, the amount of money I spent on public transportation, the little money left over that I didn't even spend and instead give to my parents.
They know nothing about how hard that year was for me, and if they want to get this code, my so called friend can come chat in person, in his off time and when I'm done working on my own shit and we can discuss terms because this shit is just not fair at all.5 -
Sometimes I do wonder why can’t I just be content at getting best I can get at what I’m already good at - and what brings in the €€€? Why do I go ”oooh look shiny intetesting language, let’s try do shit with it” or ”hey, let’s try this thing called kernel dev/pld/program verification which are all so far outside my core expertise they might as well be in a different universe!”
Dude I mean writing a kernel in V and doing proof oriented programming in F* are fun and all, but what good’s that gonna do me when I’m in all likelihood still maintaining legacy web apps in PHP ten to twenty years from now?
I guess what I’m trying to say is that I’m torn inside with my current workplace offering me everything I value and stuff that’s rare to find - but at the same time I’d love to be challenged more and don’t really have enough of those opportunities in my current environment. Or some shit like that.
Well fuck that, back to writing my own embedded DSL into F* in F#….1 -
I just had such a forfilling moment.
Normally, i often (force myself) go to bed at night, after i worked on a project of mine, with these thought saying "oh man i wanted to get that feature done today" or "i want to finish this and that part of my code".I am sure everyone of you knows the feeling, when your brain communicates that you are just not done for today.
Today it was different. I got a project of mine working in it's first state, where i put much heart, love and time in.Just a few minutes before i finished for today i got my server responding the expected numbers(some kind of pin-code). It's a very easy system: Someone(at the time only me and my debug mode :3) on a android phone request a verification which is checked and processed by the server. The server creates a random six-digit number, returns it encoded to the client and sends an email to the user, which currently sends it in plain text(shame on me).
Yeah, the user enters the number and voilà
And of course, all the Pincodes can only be used once.
I got to bed with this feeling of luck and succes.
I hope tomorrow is going to be a productive day!
I am so lucky right now.
Have a good day everyone! -
A word of advice:
If you integrate email verification very tightly in the registration flow, it will be a world of pain to implement changing the email address.
It's alright, I didn't want to do anything this afternoon anyway.4 -
The global joke of Information Security
So I broke my iPhone because the nuclear adhesive turned my display into a shopping bag.
This started the ride for my character arc in this boring dystopia novel:
Amazon is preventing me from accessing my account because they want my password, email AND mobile phone number in their TWO.STEP Verifivation.
Just because one too many scammers managed to woo one too many 90+y/o's into bailing their long lost WW2 comrades from a nigerian jail with Amazon gift cards and Amazon doesn't know what to do about anymore,
DHL is keeping my new phone in a "highly secure" vault 200m away from my place, waiting for a letter to register some device with a camera because you need to verify your identity with an app,
all the while my former car insurance is making regress claims of about 7k€ against me for a minor car accident (no-one hurt fortunately, but was my fault).
Every rep from each of the above had the same stupid bitchass scapegoat to create high-tech supra chargers to the account deletion request:
- Amazon: We need to verify your password, whether the email was yours and whether the phone number is yours.
They call it 2-step-verification.
Guess what Amazon requests to verify you before contacting customer support since you dont have access to your number? Your passwoooooord. While youre at it, click on that button we sent you will ya? ...
I call this design pattern the "dement Tupi-Guarani"
- DHL: We need an ID to verify your identity for the request for changing the delivery address you just made. Oh you wanted to give us ANOTHER address than the one written on your ID? Too bad bro, we can't help, GDPR
- Car Insurance: We are making regress claims against you, which might throw you back to mom's basement, oh and also we compensated the injured party for something else, it doesn't matter what it is but it's definitely something, so our claims against you just raised by 1.2k. Wait you want proof we compensated something to the injured at all? Nah mate we cant do that , GDPR. But trust me, those numbers are legit, my quant forecasted the cost of childrens' christmas wishes. You have 14 days or we'll see you in court haha
I am also their customer in a pension scheme. Something special to Germany, where you save some taxes but have to pay them back once you get the fund paid out. I have sent them a letter to terminate the contract.
Funniest thing is, the whole rant is my second take. Because when I hit the post button, devrant made me verify my e-mail. The text was gone afterwards. If someone from devRant reads this, you are free to quote this in the ticket description.
Fuck losing your virginity, or filing your first tax return, or by God get your first car, living through this sad Truman dystopia without going batshit insane is what becoming a true adult is.
I am grateful for all this though:
Amazon's safety measures prevented me from spending the money I can use to conclude the insurance odyssey, and DHLs "giving a fuck about customers" prevention policies made me support local businesses. And having ranted all this here does feel healthy too. So there's that.
Oh, cherry on top. I cant check my balance, because I can only verify my login requests to my banking account wiiiiiiith...?2 -
My trying to login to my email account my.email.address@example.com via web:
Site: You need to verify that you are really you. We sent a verification email to my.email.address@example.com please click the link in this email to verify your identity.2 -
I think the sleep deprived me is finally cracking under the weight of incompetent assholes.
We just launched a major project in some weird cocktail of Agile slapped with MVP and release to the wild in a waterfall, but it was premature, premature in the sense QA hasn't even finished their side of things, but because some fuck with with "manager" in their title decided they have burnt through the budget with incompetence and scrapped an entire element of the project and outsourced just so they could make a shittier version that doesn't even fucking work.
How hard do you want to fail before you will start listening to the people that now have to work around the fucking clock to clean up this horse shit of a mess.
I'm literally arguing over field mapping with multiple 3rd parties, when the fucking requirements state WTF this is suppose to look like. All because they didn't validate or test their own shit.
Why is EVERY FUCKING cock head in this industry a waste of space and cash! Is it really to much to ask for 1 fucking project to fucking go live that actually fucking works where I don't need to work 2 weeks straight (including weekends) after going live just to be sure that what shit does hit the fan isn't going to create a SEV 1 issue...
Sorry, I'm pissed at the incompetence of others I need to deal with on a daily basis. It's not like this field is insanely hard. A little attention to detail and self validation, verification goes a long way. But clearly that's a rarity.
Once this shit is stable and actually works, I'll be pulling out the mop to clean up half this shit just so it actually works.
Oof, I'm getting to old for this bullshit.4 -
Just passed technical verification for senior dev, then went to subway. Question from the lady behind counter where tougher :P2
-
Fuck the feelings of powerlessness and helplessness. when a friend comes crying for you for help with their hacked account and you keep asking them about what they did to protect it in the first place and they reply with nothing, no recovery email, no recover phone, no secondary verification, NOTHING. and you can do nothing but stand there and watch them cry while you can literally do nothing because there literally nothing you can do to retrieve their stolen accounts. FUCK BLACK HAT HACKERS.3
-
Forgot to do server side verification.
As the service (an injectable game) was expanding and the old system relied on server side calculation without anything returned from the user, the expansion was done a little too fast.
The result could have been anyone passing wrong data and receiving the grand price like a holiday worth $10k. Quick fix ... -
Burned out but trapped at work for next 4-6 weeks - need survival tips
I'm 31y/o software dev and I'm completely fried and need advice on how to hang on until I can quit.
After 5 months job hunting, I landed a role that turned into a nightmare. 6 months of being bounced between different teams/scopes/projects with impossible deadlines and covering for incompetent managers/colleagues has left me burned out. Problem is, I'm finalizing a mortgage and can't quit or take sick leave without messing up income verification stage. Need to survive 4-6 more weeks.
Work is toxic and unpredictable - not enough resources given, blaming, shifting priorities, undefined tasks, endless meetings. Fake sense of urgency. Never feeling a sense of completion - there is always something extra that comes up. Documenting everything to have paper trail in case shit hits the fan, but honestly it feels like I'm at war daily and it's exhausting. I'm weeks behind on everything.
I have ADHD and my usual meds (18mg Concerta/10-20mg Lisdexamphetamine of Adixemin brand) aren't working anymore. Im able to fall asleep only after taking 0.2-0.3mg of Xanax or smoking some THC/CBD flowers. Constant brain fog, shot memory, never feel rested. Maybe 2-3 productive hours max daily before I become useless - either depressed or too wired and too anxious to function.
Already tried bunch of supplements (all possible forms magnesium, vitamin D, fish oil, my supplements drawer has like 60 different bottles), cleaned up diet, cut dairy/nicotine/alcohol/caffeine, taking strategic vacation days here and there in beginning or ending of a week.
I also suspected some allergies, tried out quercetine + vitamin c + all possible anti allergy meds - didnt help. I even suspected inflammation - tried curcumin and all other stuff - useless.
Anyone dealt with extreme burnout while trapped in a job? How do you function when your tank is empty but quitting isn't an option?
Only thing that helps is that I work fully remotely. Exercise would help but I cant force myself to do it.
Once the mortgage closes, I'm gone. Get a less stressful job lined up. Just need to survive until then without falling apart completely.13 -
Fucking regulations, can’t play with twilio api.
Waiting for verification of my identity to make a fucking test call to myself.
Wanted to make a proof of concept during weekend, but won’t happen cause some fucking policies.
Fuck you government pigs.
Probably need to wait to fucking Monday. I will forget what I wanted to do till that time.
We are making your life easier all the time in the news, yeah right eat those popups motherfuckers.
Next regulation - government code reviews before push to master and programmer certification, for sure those fuckers are able to do it.
Really considering emigration from Europe right now.
No fucking point to start a business on this continent.
More fucking law please so we would need a lawyer before wiping ass.
Need to watch that southpark episode about security toilet checkout once again.2 -
It was the last year of high school.
We had to submit our final CS homework, so it gets reviewed by someone from the ministry of education and grade it. (think of it as GPA or whatever that is in your country).
Now being me, I really didn’t do much during the whole year, All I did was learning more about C#, more about SQL, and learn from the OGs like thenewboston, derek banas, and of course kudvenkat. (Plus more)
The homework was a C# webform website of whatever theme you like (mostly a web store) that uses MS Access as DB and a C# web service in SOAP. (Don’t ask.)
Part 1/2:
Months have passed, and only had 2 days left to deadline, with nothing on my hand but website sketches, sample projects for ideas, and table schematics.
I went ahead and started to work on it, for 48 hours STRAIGHT.
No breaks, barely ate, family visited and I barely noticed, I was just disconnected from reality.
48 hours passed and finished the project, I was quite satisfied with my it, I followed the right standards from encrypting passwords to verifying emails to implementing SQL queries without the risk of SQL injection, while everyone else followed foot as the teacher taught with plain text passwords and… do I need to continue? You know what I mean here.
Anyway, I went ahead and was like, Ok, lets do one last test run, And proceeded into deleting an Item from my webstore (it was something similar to shopify).
I refreshed. Nothing. Blank page. Just nothing. Nothing is working, at all.
Went ahead to debug almost everywhere, nothing, I’ve gone mad, like REALLY mad and almost lose it, then an hour later of failed debugging attempts I decided to rewrite the whole project from scratch from rebuilding the db, to rewriting the client/backend code and ui, and whatever works just go with it.
Then I noticed a loop block that was going infinite.
NEVER WAIT FOR A DATABASE TO HAVE MINIMUM NUMBER OF ROWS, ALWAYS ASSUME THAT IT HAS NO VALUES. (and if your CPU is 100%, its an infinite loop, a hard lesson learned)
The issue was that I requested 4 or more items from a table, and if it was less it would just loop.
So I went ahead, fixed that and went to sleep.
Part 2/2:
The day has come, the guy from the ministry came in and started reviewing each one of the students homeworks, and of course, some of the projects crashed last minute and straight up stopped working, it's like watching people burning alive.
My turn was up, he came and sat next to me and was like:
Him: Alright make me an account with an email of asd@123.com with a password 123456
Me: … that won't work, got a real email?
Him: What do you mean?
Me: I implemented an email verification system.
Him: … ok … just show me the website.
Me: Alright as you can see here first of all I used mailgun service on a .tk domain in order to send verification emails you know like every single website does, encrypted passwords etc… As you can see this website allows you to sign up as a customer or as a merc…
Him: Good job.
He stood up and moved on.
YOU MOTHERFUCKER.
I WENT THROUGH HELL IN THE PAST 48 HOURS.
AND YOU JUST SAT THERE FOR A MINUTE AND GAVE UP ON REVIEWING MY ENTIRE MASTERPIECE? GO SWIM IN A POOL FULL OF BURNING OIL YOU COUNTLESS PIECE OF SHIT
I got 100/100 in the end, and I kinda feel like shit for going thought all that trouble for just one minute of project review, but hey at least it helped me practice common standards.2 -
!rant. Story from my college abt 6 months old.
We had to make projects for our course.
One team made a very nice project. One part of that was mobile no. verification using OTP.
And the student who was supposed to to that, did it by sending the required otp to the frontend page, and when user enters it, validate it using javascript.
The prof got mad about it and the rest of the class couldn't stop laughing.
Just remembered. Thought it would be worth sharing. -
Brave Browser.
There’s a reason why brave is generally advised against on privacy subreddits, and even brave wanted it to be removed from privacytools.io to hide negativity.
Brave rewards: There’s many reasons why this is terrible for privacy, a lot dont care since it can be “disabled“ but in reality it isn’t actually disabled:
Despite explicitly opting out of telemetry, every few secs a request to: “variations.brave.com”, “laptop-updates.brave.com” which despite its name isn’t just for updates and fetches affiliates for brave rewards, with pings such as grammarly, softonic, uphold e.g. Despite again explicitly opting out of brave rewards. There’s also “static1.brave.com”
If you’re on Linux curl the static1 link. curl --head
static1.brave.com,
if you want proof of even further telemetry: it lists cloudfare and google, two unnecessary domains, but most importantly telemetry domains.
But say you were to enable it, which most brave users do since it’s the marketing scheme of the browser, it uses uphold:
“To verify your identity, we collect your name, address, phone, email, and other similar information. We may also require you to provide additional Personal Data for verification purposes, including your date of birth, taxpayer or government identification number, or a copy of your government-issued identification
Uphold uses Veriff to verify your identity by determining whether a selfie you take matches the photo in your government-issued identification. Veriff’s facial recognition technology collects information from your photos that may include biometric data, and when you provide your selfie, you will be asked to agree that Veriff may process biometric data and other data (including special categories of data) from the photos you submit and share it with Uphold. Automated processes may be used to make a verification decision.”
Oh sweet telemetry, now I can get rich, by earning a single pound every 2 months, with brave taking a 30 percent cut of all profits, all whilst selling my own data, what a deal.
In addition this request: “brave-core-ext.s3.brave.com” seems to either be some sort of shilling or suspicious behaviour since it fetches 5 extensions and installs them. For all we know this could be a backdoor.
Previously in their privacy policy they shilled for Facebook, they shared data with Facebook, and afterwards they whitelisted Facebook, Twitter, and large company trackers for money in their adblock: Source. Which is quite ironic, since the whole purpose of its adblock is to block.. tracking.
I’d consider the final grain of salt to be its crappy tor implementation imo. Who makes tor but doesn’t change the dns? source It was literally snake oil, all traffic was leaked to your isp, but you were using “tor”. They only realised after backlash as well, which shows how inexperienced some staff were. If they don’t understand something, why implement it as a feature? It causes more harm than good. In fact they still haven’t fixed the extremely unique fingerprint.
There’s many other reasons why a lot of people dislike brave that arent strictly telemetry related. It injecting its own referral links when users purchased cryptocurrency source. Brave promoting what I’d consider a scam on its sponsored backgrounds: etoro where 62% of users lose all their crypto potentially leading to bankruptcy, hence why brave is paid 200 dollars per sign up, because sweet profit. Not only that but it was accused of theft on its bat platform source, but I can’t fully verify this.
In fact there was a fork of brave (without telemetry) a while back, called braver but it was given countless lawsuits by brave, forced to rename, and eventually they gave up out of plain fear. It’s a shame really since open source was designed to encourage the community to participate, not a marketing feature.
Tl;dr: Brave‘s taken the fake privacy approach similar to a lot of other companies (e.g edge), use “privacy“ for marketing but in reality providing a hypocritical service which “blocks tracking” but instead tracks you.14 -
Wow just realized Simpsons had an episode on crypto... all the way back in February.
If only the the MVC would actually mail me my new drivers license that I renewed almost 6 months ago... I could actually buy some... (exchanges require ID verification, so much for anonymity ¯\_(ツ)_/¯) 6
6 -
I've always thought that Wordpress is HOT CARBAGE for custom solutions. The opinion is influenced by devRant actually. And I'm really starting to see that after few of months working with it.
For context, it's a accommodation booking site with sub-theme that uses plugins such as Woocommerce Bookings. I didn't build it but I'm now developing and maintaining it.
The emails... I've tried to make them function properly. But no. Because we skip the fucking verification step to allow instant booking it just won't send them. I made yet another workaround and casted some spells. NOW IT SENDS THE EMAIL TWICE...
I'm done. It's good enough.2 -
Adaptive Latent Hypersurfaces
The idea is rather than adjusting embedding latents, we learn a model that takes
the context tokens as input, and generates an efficient adapter or transform of the latents,
so when the latents are grabbed for that same input, they produce outputs with much lower perplexity and loss.
This can be trained autoregressively.
This is similar in some respects to hypernetworks, but applied to embeddings.
The thinking is we shouldn't change latents directly, because any given vector will general be orthogonal to any other, and changing the latents introduces variance for some subset of other inputs over some distribution that is partially or fully out-of-distribution to the current training and verification data sets, thus ultimately leading to a plateau in loss-drop.
Therefore, by autoregressively taking an input, and learning a model that produces a transform on the latents of a token dictionary, we can avoid this ossification of global minima, by finding hypersurfaces that adapt the embeddings, rather than changing them directly.
The result is a network that essentially acts a a compressor of all relevant use cases, without leading to overfitting on in-distribution data and underfitting on out-of-distribution data.12 -
Not a rant, just the completion of a very demanding and interesting task for this week.
Wrote a whole data scheme for this enterprise app my company is developing. Very proud of it, since it has a very restricted size, multiple layers of encryption and data verification, several user types with different requirements, and it all has to be rock solid in an offline environment.
The punchile is...I enjoyed writing the documentation for the whole package more than I should, I guess...spent the whole day being very thorough and documenting every member, function, constructor and exception.
Feelin fabulous.
-
Lets dive deep into the cesspool of Youtubes new AI age verification bullshit. So, if you didnt hear recently, YouTube is using AI to determine your age based on your activity which is first of all, a fucking privacy violation, if they find you to be under 18, you will lose access to a lot of Youtube unless you give some sleazy company your ID. I think this is all bullshit, Youtube should retract this, I fucking hate it, Youtubes restricted mode is fucking slop. Heres how to survive the armaggeddon. Avoid shit with "try youtube kids" next to the description. Treat those videos as they are nuclear waste. They are best avoided. Do not have child like viewing habits or Corporate Cowardice might flag you. Same goes with use of emojis. Dont use emojis like the cretins in my comment section as kids like emojis. Other than that, This is all fucking bullshit. Youtube doesnt know how much fucking backlash they are going to face, in fact they are facing backlash right now, Look youtube, fucking retract this bullshit, otherwise the community might choose fucking thermonuclear war. AI is still a fucking gimmick. I do not trust AI. Fuck all this shit.9
-
What makes free ssl "Unsuitable for e-commerce websites", Please read to end to see my view point.
From Namecheap:
Free Certificates are domain validation only which means they don't certify the identity of the website owner, they simply ensure a secure connection. Customers can't be sure of the integrity and trustworthiness of the website owner. If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer. It's important your customers trust your business is safe enough to hand over these details. To gain this trust, you need a certification of your authenticity, which you can only get with a (paid) Business Validation or Extended Validation SSL Certificates.
https://namecheap.com/security/...
* "To gain this trust, you need a certification of your authenticity"
~ But isn't that just Domain Verification and other Extras, What justifies somebody or business's authenticity? Tax Id, Valid Address, Nobody is going to study the ssl cert to make sure that amazon.com is a valid business and has a tax Id.
* "domain validation only which means they don't certify the identity of the website owner,"
~ Wouldn't this just be the domain validation test that is required when using services like LetsEncrypt using Certbot etc, or are we referencing back to this idea that they look for a Valid Tax Id sort of thing?
* "If you need to secure credit card and personal information on e-commerce websites, free certificates aren't the answer"
~ Why is the paid version going to do double encryption, is the CA going to run a monitoring tool to scan for intrusions like a IDS or IPS? (disregard the use of DNS Validation being in the picture)
Am I missing something, this just seems like well crafted text to get people to buy a cert, I could understand if the encryption was handled differently, Maybe if they checked the site for HSTS or HTTPs Redirect or even, They blocked wildcard SSL before and now with the paid its included, but overall it doesn't sound like anything special. Now I'm not just picking on namecheap because domain.com does the same.14 -
FAIL!!
My driver's ed Course is online. It is a 32 hour course so in order to go through every slide you have to wait for a timer to countdown. The way they keep you from advancing is graying out the next button.
That's really stupid.
Because I just found out that you can change the button class to active in the Chrome inspector. You can continue.
The shocking part is is that there is no server side verification, so I could complete the entire hour course in less than 30seconds.
Wow. I didn't think a FUCKING DRIVERS ED COMPANY WOULD BE THAT STUPID!3 -
Sus!
yesterday I bought a cool domain in namecheap, I was very lucky to find short and good one for my case.
Today (at weekends!!!!) I receive a letter:
>Hello **redacted name**,
>
>We are contacting you from the Namecheap Risk Management Team regarding your '**redacted name account**' account.
>
>Unfortunately, your Namecheap account was flagged by our fraud screening system as requiring verification and was locked.
>
>Please follow the instructions below to get your account verified:
>
>- take a color photo of the credit card used for the payment at **redacted link**
>
>Please make sure all of the edges of the credit card are visible, and that we can clearly see the card holder's name, expiration, and last four digits of the card number. The screenshots or images of the card cannot be accepted for verification. >If the submission does not meet these requirements, we can either request to submit the details again or permanently suspend your account.
>
>- provide a valid phone number and the best time to call you (within normal business hours, US Pacific time).
>
>If we do not hear back from you within 24 hours, we will be forced to cancel your orders.
>
>We apologize for any inconvenience that may result from this process. This extra verification is done for your security and to ensure that orders are legitimate. This industry, unfortunately, has a high rate of fraudulent orders, and this sort of >verification helps us drastically reduce fraud and ensure our customers remain secure. Such documents are used for verification only and are not provided to third parties in any way. Account verification is a one-time procedure, after your account >is verified, you will never face this issue again.
>
>Looking forward to your reply.
>
>---------------
>Dmitriy K.
>Risk Management
> Namecheap, Inc.
what if I did not notice it in 24 hours? It is the weekend for god's sake! People usually rest until monday.
They would what, cancel order and scalpel it to super high price?!
I have some doubts if the request is trully having anti fraudulent origins.
What if I used digital visa card? How was I supposed to photo it?
And the service they provided for photoing accepts only photos from web camera. I was lucky that I bought recently web camera with high enough amount of pixel power and manual focus. What if I did not?
That's all really SUS!
The person can not notice the letter within 24 hours time frame until the morning, when it would be already too late.10 -
So, there was that post about Valve that send your steam password through an email. I changed my password to see if it was true (I couldn't believe it). And I had to do phone verification....
I thought for a sec it wouldn't stop, but yeah atleast I got the message. 5
5 -
Note to self:
Close off ALL ways things could go wrong..
Long story short; I released a new feature, to be able to better follow up on any stock moves, their amounts, locations and even expiry dates. An older tool just bypassed that very verification and nothing was logged or taken out of stock.
~
Taking out an amount for a certain orderline has a shortcut in place to mitigate some of the mandatory steps that pickers need to take in order to verify what's being taken. This little tool only available, visible and possible for a very few select users.
I assigned some orders to one of these people, which made him think it was an urgent batch. It's only one product, for multiple orders, so he went to the location, took out the amount needed and then used the tool to quickly be able to prepare them for shipping.
This bypassed the new methods to check if the location actually had stock to take, which I had just enabled for 1 account.
Luckily I caught the miss-hap as I was monitoring that product first-hand and noticed the batch of orders was collected but the stock amount didn't update.
It was 5min before I was leaving work, so I investigated and then ran to the person in question to ask what he did; which was "I used that tool"
I facepalmed myself internally while blaming myself, as he couldn't know that it wasn't ready to use for that purpose.
The tools to fix this up are there already.. so I used that to fix some missing stock-takes manually.. Though I'll need to close that little tool for these kind of orders for sure, asap, probably when I get home, at least until I bring over its new logic to it.
Happy Tuesday? (: -
implementing an email verification .. it shows differently in different email .. If I fix something for yahoomail .. it shows broken in gmail .. just fedup of this .. my whole day has been wasted for this shit today .. 😑😑7
-
Fuck I feel fucked up just for completing user account management, authentication, email verification, password reset. Securing all of this with ssl and checking for any security loopholes.
I can't believe this took me more than a couple months.
Well I was lazy and unmotivated.
I fucking hate crafting stupid ass routes in nginx.
I fucking hate making a nice responsive gui.
I have to design even the stupid html for the emails. Fuuuuck.
So much boilerplate on top of that with username and email validation.
I learnt regex 5 times over the past couple months, still not enough.
And now I actually have to build the functional part.
On the plus side I can reuse this stupid boilerplate if I can make it more modular and readable.
There's shit ton of comments to the point where I feel like an idiot for including so much info. It's like I've written it for a toddler to take over.
Gawd. Anyways it's over now. 50% I guess.
I can finish the rest of the server more quickly and then spend another year designing the Android application.
I'm really lazy in places where I have to design UI/UX. Although at this point it's kinda what could put my application at the top. (I'm lazy, I ain't bad.. I just hate implementing my ideas I wish I could just visualize and have it appear on my screen)
I do like parts of gui that involve little math problems that would make motion smooth and efficient. -
Just remembered that I still had a foobar invite link in my email inbox 😋
The challenges are odd though, first challenge was super easy (basically an idiot check), but while I was able to convert 3 cans of energy drink into a functional solution in half an hour, the verification utility is not very verbose at all. So in Python 3.7.3 in my Debian box it worked just fine, yet the testing suite in Foobar was failing the whole time. After sending an email to my friend that gave the link (several years ago now, sorry about that! 😅) asking if he knew the problem, I found out that Google is still using Python 2.7.13 for some reason. Even Debian's Python is newer, at 2.7.16. To be fair it does still default to Python 2 too. But why.. why on Earth would you use Python 2.7 in a developer oriented set of challenges from a massive company, in 2020 when Python 2 has already been dead for almost a whole year?
But hey now that it's clear that it's Python 2.7, at least the next challenges should be a bit easier. Kind of my first time developing in SnekLang regardless actually, while the language doesn't have everything I'd expect (such as integer square root, at least not in Debian or the foobar challenge's interpreter), its math expressions are a lot cleaner than bash's (either expr or bc). So far I kinda like the language. 2-headed snake though and there's so much garbage for this language online, a lot more than there is for bash. I hate that. Half the stuff flat out doesn't work because it was written by someone who requires assistance to breathe.
Meh, here's to hoping that the next challenges will be smooth sailing :) after all most of the time spent on the first one (17.5 hours) was bottling up a solution for half an hour, tearing my hair out for a few hours on why Google's bloody verification tool wouldn't accept my functioning code (I wrote it for Python 3, assuming that that's what Google would be using), and 10 hours of sleep because no Google, I'm not scrubbing toilets for 48 hours. It's fair to warn people but no, I'm not gonna work for you as a cleaning lady! 😅
Other than the issues that the environment has, it's very fun to solve the challenges though. Fuck the theoretical questions with the whiteboard, all hiring processes should be like this! 1
1 -
Just visited a website, which at the top of every page "Please paste your Google Webmaster Tools verification here"
What's odd, is this isn't a way I've seen to verify. Some kind of odd scam? 🤔2 -
Got a problem with an AUR package. Decided to ask the AUR maintainer. Registered on the AUR page. Can't login, receiving HTTP400 bad referrer header.
Decided to report that issue. To do so, I need to register on the Arch Linux Website. Did that. To finish registration, I need to verify my account. However, the verification button just does nothing.
Removed AUR package.3 -
I am developing a twitter bot which will post local weather daily. After few test tweets, twitter locked the account and asked to verify account by calling. They called and I wrote down the verification code but THE FUCKING TWITTER returns a "Something went wrong." error with no actual clue about the problem.
-
I understand risk aversion and fault tolerance and verification. But you have to realize mister tester and systems lead guy, WE DON'T HAVE INFINITE TIME!!! Gods damn, seriously. You can't keep pushing the schedule. Eventually we have to ship. That's, you know, how we get paid.
-
TLDR: I wanted to change email to new one, but I could not remember which one I have
currently. I found out an API in DevRant JS files for email verification and used
it to find it out.
So, I am moving from Gmail to Protonmail Pro, absolutely love their service.
I wanted to do same on Devrant but I could not figure out my current mail for
"I lost my password" form. My Password Manager have only login saved, and profile does
not show email address.
I thought that this user information is stored on server so it have to be some way to retrieve it. I dug
in source code and I've found:
`<div class="signup-title">Verify Your Email</div>`
Which has event assigned to function which uses jQuery.ajax (love it btw :D) to call:
`url: "/api/users/me/resend-confirm",`
This seems like worth a shot. Few copy-pastes and one ajax call later:
*Ding*
From: support@devrant.io
To: dawid@dawidgoslawski.pl
"Welcome to Devrant"
Got it :) So I have already changed in march when DevRant on previous layout.
This is what I love in this profession - problem solving. AI will not replace human
in any way, we will just stop coding array iterations and data manipulation - we will focus
on real problem solving and human touch (like design, convincing management for changes).1 -
GoDaddy. Is. The. Worst.
I'm working on an SSL cert domain verification for a client. The chat support tech at GoDaddy has no freaking clue what she's doing. She keeps telling me to follow the same help article I already knew about the first second I heard I needed to do this job. It didn't work. But she keeps going back to it, sure that I'm just a complete and utter moron who doesn't read. Never mind that I have screenshots to prove everything she's telling me is 100% wrong according to every error message this process is generating.
Now she's checking with the "SSL team". Which is code for "I have absolutely no idea what I'm doing and I'm frantically searching the FAQ database to figure out what this SSL thing even is."
That's what the last hour of my life has been. And 20 minutes of that was waiting in the chat queue.5 -
Ok... so I have a unique question/opportunity. I can't give all the details but here's the jist:
3yrs ago I was hired to consult a now prominent(still decently well known then) web-based company with many thousands of users, dealing with a lot of money and leveraging a social environment. They had several issues but initially they really needed me to find/train chat mods.
I did not take the offer for monetary reasons, like all consulting I've done, I had additional reason and/or fondness to fix the issues. In this case it was an interesting challenge and I knew several customers and some support staff so it'd be worthwhile.
They (without request) reduced their typical 2mo probationary period to 2wk for me. With less than a day left of that period, I was 'hacked' via a pushed telegram update, on the account they made me create for work purposes (they had control of the phone number not me).
During this 'hack' one of the 2, currently active, culprits sent a message to his tg account from the 'hacked' one and quickly deleted the entire convo. The other pretended (poorly) to be me in the chat with the mods in training (at least a few directly witnessed this and provided commentary).
Suddenly, I was fired without any rationale or even a direct, non-culprit, saying anything to me.
The 'hack' also included some very legit, and very ignorantly used, Ukrainian malware.
This 'hack' was only to a 2nd gen lenovo yoga I got due to being a certified refurbisher... just used for small bs like this chat mod/etc job. I even opened up my network, made honey pots, etc., waiting for something more interesting... nope not even an attempt at the static ip.
I started a screen recording program shortly after this crap started (unfortunately after the message sent be 'me' to the dude who actually sent it happened... so i still dont know the contents).
I figured I'd wait it out until i was bored enough or the lead culprit was at a pinnacle to fall from...
The evidence is overwhelming. This moron had no clue what he was doing (rich af by birth type)... as this malware literally created an unhidden log file, including his info down to the MAC id of his MacBook... on my desktop in real time (no, not joking... that stupid)
Here's my quandary... Due to the somewhat adjacent nature of part of our soon to be public start-up... as i dont want it to turn into some coat tail for our tech to ride on for popularity... it's now or never.
Currently im thinking, aside from any revenge-esq scheme, it'd be somewhat socially irresponsible to not out him to his fellow investors and/or the organisation that is growing with him as one of few at the forefront... ironically all about trust/safety/verification of admins in the industry.
I tried to reach out to him and request a call... he's still just as immature. Spent hours essentially spamming me while claiming it wasnt him but hed help me find whoever it was... and several other failed attempts to know what i had. When i confirmed he wasnt going to attempt a call, i informed him id likey mute him because i don't have time for back and forth bs. True to form he deleted the chat (i recorded it but its of no value).
So... any thoughts?7 -
Coinbase is a miserable clock sucker...
You can't understand that your stupid app doesnt split sir names during ID verification? A month of playing ring around the support email bot... "Try updating chrome!"...
Go duck yourself,
John S Jr. Smith6 -
Good code is a lie imho.
When you see a project as code, there are 3 variables in most cases:
- time
- people / human resources
- rules
Every variable plays a certain role in how the code (project) evolves.
Time - two different forms: when certain parts of code are either changed in a high frequency or a very low frequency, it's a bad omen.
Too high - somehow this area seems to be relentless. Be it features, regressions or bugs - it takes usually in larger code bases 3 - 4 weeks till all code pathes were triggered.
Too low - it can be a good sign. But it should be on the radar imho. Code that never changes should be reviewed at an - depending on size of codebase - max. yearly audit. Git / VCS is very helpful here.
Why? Mostly because the chances are very high that the code was once written for a completely different requirement set. Hence the audit - check if this code still is doing the right job or if you have a ticking time bomb that needs to be defused.
People
If a project has only person working on it, it most certainly isn't verified by another person. Meaning that only one person worked on it - I'd say it's pretty bad to bad, as no discussion / review / verification was done. The author did the best he / she could do, but maybe another person would have had an better idea?
Too many people working on one thing is only bad when there are no rules ;)
Rules. There are two different kind of rules.
Styling / Organisation / Dokumentation - everything that has not much to do with coding itself. These should be enforced at a certain point, otherwise the code will become a hot glued mess noone wants to work on.
Coding itself. This is a very critical thing.
Do: Forbid things that are known to be problematic in the programming language itself. Eg. usage of variables in variables, reflection, deprecated features.
Do: Define a feature set for each language. Feature set not meaning every feature you want to use! Rather a fixed minimum version every developer must use and - in case of library / module / plugin support - which additional extras are supported.
Every extra costs. Most developers don't want to realize this... And a code base that evolves over time should have minimal dependencies. Every new version of an extra can have bugs, breakages, incompabilties and so on.
Don't: don't specify a way of coding. Most coding guidelines are horrific copy pastures from some books some smart people wrote who have no fucking clue what you're doing and why.
If you don't know how to operate on people, standing in an OR and doing what a book told you to do would end in dead person pretty sure. Same for code.
Learn from mistakes and experience, respect knowledge from other persons, but always reflect on wether this makes sense at this specific area of code.
There are very few things which are applicable to a large codebase on a global level. Even DRY / SOLID and what ever you can come up with can be at a certain point completely wrong.
Good code is a lie - because it can only exist at a certain point of time.
A codebase should be a living thing - when certain parts rot, other parts will be affected too.
The reason for the length of the comment was to give some hints on what my principles are that code stays in an "okayish" state, but good is a very rare state -
You know what sucks? Having to rely on a vendor for data verification. Especially when that vendor's systems go down every other freakin' day!3
-
So yesterday I had to do some windows updates.
Today, I turn my laptop back on and notice I don't have sound.
Alright, I'll just see if I have some outdated drivers. Oh, I have 3, and one it's the sound driver! Cool, let me just update that. What do you mean I can't? Alright, let me try this app I have installed to see if it can update everything for me. It did, great!
Oh, but now the sound is coming from my earphones AND the speaker... Let me check the app again. Nothing. Let me check the drivers again. Detection verification is outdated. Alright, I'll just update that one, no big deal. Windows could not find drivers? Alright, let's see if windows update can find something! Nothing.
Okay, let's check sound definitions. What about troubleshooting? Still nothing?
Well, now I'm pissed. Let's see what the internet thinks I should do. Almost one hour later, I've tried everything I can think of and still can't fix this. Fml8 -
I’m having this issue for the online marketplace I’m working on the side. It’s blockchain tech where you can purchase normal goods and services(no, not like Amazon or Fiverr, eww, this one’s more inclined with promoting organic growth for small businesses and freelancers).
I’m stuck with what solution is in the best interest of the user and the business for the long-term.
The dilemma about anonymity, online freedom and privacy is yes, it protects users from predators and attackers, but then, it’s harder for authorities to hunt down people who uses platforms for malicious intent, and also, digital footprint is helpful during litigation as evidence.
You don’t know who to trust.
-There is nothing to differentiate normal users with spammers, scammers, etc.
-There is no accountability for if they break the rules. They can easily delete and create a new account.
Platforms, communities big or small are plagued with these.
There are a lot of people out there who would rather project their insecurities on other people than to seek therapy.
Also, how platforms uses psychology tricks to make platforms addicting, it’s safe to assume that it’s bound to get toxic. Fixation on these platforms, leads to other needs being neglected or people forget to stay present.
Another thing, automated moderation is not that effective as there are still biases in data and human verification is still required. But then, human moderators get exposed to extreme violence, gore, etc that leads to poor mental health. (see Facebook got sued by moderators)
Also, I’ve had a recent experience where some unstable dev was stalking and harassing me. During that turmoil, I’ve found the many loopholes in every platform out there and how crappy their support is. Like they’ll just say, “make your account more secure”, bitch it’s your platform not providing enough security, your blocking feature means nothing coz anyone can still create accounts and message anyone.
It happened like February-August (it ended coz I quit going online and made private all my accounts). UGH I MISS ALL MY FRIENDS THO. FUCK THAT DUDE. He deserves to be in jail TBH
Lol if this product booms, now u know the back story lololol -
What a delight to have to work on macOS. Not.
Took me two days to notarize our app bundle. The ultimate issue was a dead symlink inside the bundle which would make the codesign verify (with strict option!) fail, while verification of signing operation itself passed.
Notarization would just give generic error: not properly signes. -
Im ranting in progress of the issue so i dont get the urge to do any of the things not seem as acceptable to fix this issue.
Issue: yesterday i activated a device i havent had any (even prepaid) service on in years, and had a 'new'(to me) number assigned...
Today, after being sick so muting nuisances immediately for rest, i check, 3missed calls from the same, less spammy looking number. I havent use this number for even a txt code verification at all... aside from 1 call to comcast (for the blissful irony of seeing if its an option (they need to survey physically) since im suing my current isp who didnt take my VERY NICE and explictly required in their business t&c, refund for the issue's duration.. after months of tryjng to directly get a message (not using my not technically hacking expertise like just scrubbing for email formatting and popped up in their inbox (calling them is more frowned upon)...
Their conclusion as to "why" (they nvr solved the issue... dhcpv6 was in aggressive lease mode(no response per lease(NOT batches) of about 60 for about 20 devices which i ofc use my /28 static ipv4 block... not ipv6 (they also claimed there was no logs til i dug and found verbose, long history high/med high debug level logs in their prop. dev's gui... which they forced me to use, has 2 separate cores/stacks which is done for 1 reason only... constant simultaneous ipv4 and ipv6 (so ofc was auto enabled)...
Basically it was spamming do to a config issue with their scripts, and their WAN6 dev/script's config. Have found a single person who knows what ipv6 (or v4) or wan6 device actually means... their conclusion from multiple "specialist departments " ..."we dont support ipv6 so if u had issues caused by using something we dont support it's your fault... sooooo ludacris.
.... ok back to main point.
callback options
1 schedule a call back for "later"
2 dont schedule and hang up/try some other time
3. cancel callback and join the end of the cue(from previous message it told me a callback in 6-10m or lose your place in line and go to the end... hours later no call and they definitely have the number as it reiterated -.-
...
answer to wait in line>
experiencing extremely high wait time
>your current wait time 31-60m
2.5sec later.. let me connect you to a rep ...etc (identical as in callback options intro)
> your current wait time is 30sec
waiting nearly 25min whilst typing this.(i did make sweet potato stuff, propagated a rose, fed JSON some of his new, in closure buffet of things he previously never encounted and bought a literal ton of rubber mulch)40min to a rep 5more to solve (last guy at same position didnt know this option exited, despite me decribing it verbosely to him.
Everything the automated syst asks is about account numer... there is none ive never even had a burner that was at&t brand.
Wzf.2 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
Anyone here uses scaleway VPS?
The tickets I raised got deleted without any proper resolution. And that is shady AF. The tickets were attended by some customer support guy and he had told he would call to verify. But that never happened.
And now all the tickets I raised has disappeared.
I can't activate my account because phone verification is not possible since the code they never arrives3 -
I hate having too much security, on the user side. I have 2 step verification on anything that allows and also most of my passwords are up to a limit, seriously. This is why I have LastPass but obviously no work I ever been in allowed it. Except Freelancing and my own software / apps.
-
The Node and its magic tricks never cease to surprise me.
I created several new components and tried to compile them for verification. Then this big fat error popped up.
I commented out all the newly created code (didn't remove any files, just did ^A^/). Recompiled. This big fat error again.
Undid modifications I made to the files that existed there before. Recompiled. This big fat error again.
Moved the newly created files outside of the project scope (mv app/<...>/featureX/ ../bkup/). Recompiled. SUCCESS.
Moved all of those files back (mv ../bkup/featureX app/<...>/). Recompiled. SUCCESS.
wtf... 2
2 -
I hate the elasticsearch backup api.
From beginning to end it's an painful experience.
I try to explain it, but I don't think I will be able to cover it all.
The core concept is:
- repository (storage for snapshots)
- snapshots (actual backup)
The first design flaw is that every backup in an repository is incremental. ES creates an incremental filesystem tree.
Some reasons why this is a bad idea:
- deletion of (older) backups is slow, as newer backups need to be checked for integrity
- you simply have to trust ES that it does the right thing (given the bugs it has... It seems like a very bad idea TM)
- you have no possibility of verification of snapshots
Workaround... Create many repositories as each new repository forces an full backup.........
The second thing: ES scales. Many nodes / es instances form a cluster.
Usually backup APIs incorporate these in their design. ES does not.
If an index spans 12 nodes and u use an network storage, yes: a maximum of 12 nodes will open an eg NFS connection and start backuping.
It might sound not so bad with 12 nodes and one index...
But it get's pretty bad with 100s of indexes and several dozen nodes...
And there is no real limiting in ES. You can plug a few holes, but all in all, when you don't plan carefully your backups, you'll get a pretty f*cked up network congestion.
So traffic shaping must be manually added. Yay...
The last thing is the API itself.
It's a... very fragile thing.
Especially in older ES releases, the documentation is like handing you a flex instead of toilet paper for a wipe.
Documentation != API != Reality.
Especially the fault handling left me more than once speechless...
Eg:
/_snapshot/storage/backup
gives you a state PARTIAL
/_snapshot/storage/backup/_status
gives you a state SUCCESS
Why? The first one is blocking and refers to the backup status itself. The second one shouldn't be blocking and refers to the backup operation.
And yes. The backup operation state is SUCCESS, while the backup state might be PARTIAL (hence no full backup was made, there were errors).
So we have now an additional API that we query that then wraps the API of elasticsearch. With all these shiny scary workarounds like polling, since some APIs are blocking which might lead to a gateway timeout...
Gateway timeout? Yes. Since some operations can run a LONG (multiple hours) time and you don't want to have a ton of open connections hogging resources... You let the loadbalancer kill it. Most operations simply run in ES in the background, while the connection was killed.
So much joy and fun, isn't it?
Now add the latest SMR scandal and a few faulty (as in SMR instead of CMD) hdds in a hundred terabyte ZFS pool and you'll get my frustration level.
PS: The cluster has several dozen terabyte and a lot od nodes. If you have good advice, you're welcome - but please think carefully about this fact.
I might have accidentially vaporized people sending me links with solutions that don't work on large scale TM.2 -
FUCK TEAMVIEWER ... HAVEN'T USED THEN FOR YEARS BUT WANTED TO REMOTE FROM 1 ANDROID TO ANOTHER.
Spent an hour setting up dealing with account lockouts, devices verification.... Finally connected all the 2 phones to the account... And TV can't connect... Stuck at connecting....3 -
research 10.09.2024
I successfully wrote a model verifier for xor. So now I know it is in fact working, and the thing is doing what was previously deemed impossible, calculating xor on a single hidden layer.
Also made it generalized, so I can verify it for any type of binary function.
The next step would be to see if I can either train for combinations of logical operators (or+xor, and+not, or+not, xor+and+..., etc) or chain the verifiers.
If I can it means I can train models that perform combinations of logical operations with only one hidden layer.
Also wrote a version that can sum a binary vector every time but I still have
to write a verification table for that.
If chaining verifiers or training a model to perform compound functions of multiple operations is possible, I want to see about writing models that can do neighborhood max pooling themselves in the hidden layer, or other nontrivial operations.
Lastly I need to adapt the algorithm to work with values other than binary, so that means divorcing the clamp function from the entire system. In fact I want to turn the clamp and activation into a type of bias, so a network
that can learn to do binary operations can also automatically learn to do non-binary functions as well.4 -
I've been working for so long with API integrations and one part of that is security. We perform ssl key exchanges for 2-way verification and a large percent of those partners provides me with their own pkcs12 file which contains their private and public keys! What's the sense of the exchange!? I think they just implement it just to boast that they "know" how ssl works,
-
Search for How to stop Apple ID Verification pop up. Find relevant and possibly credible result from discussions.apple.com:
How do I stop the constant pop up on my iPad for APPLE ID VERIFICATION, posted in 2016.
Last post from OP: Did you ever find a solution to this problem? This Apple ID Verification request is driving me crazy.
83 Users: Me too.
Apple:
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.1 -
So, Recently I had made a short film "Brazen Epiphany" and I added it to IMDB, I discovered that IMDB has a flawed verification system, they don't actually verify edits. So, I credited myself for acting in various films. And, they got approved. Then one day, a writer of one of those movies discovered this and ranted on Twitter about it
https://twitter.com/varungrover/...
I told him about this whole stuff, Then I was contacted by a journalist amd they published a story on this
https://mumbaimirror.indiatimes.com/...
I know it's pretty lame to give wrong information to a community website, but I enjoyed it5 -
#Suphle Rant 9: a tsunami on authenticators
I was approaching the finish line, slowly but surely. I had a rare ecstatic day after finding a long forgotten netlify app where I'd linked docs deployment to the repository. I didn't realise it was weighing down on me, the thought of how to do that. I just corrected some deprecated settings and saw the 93% finished work online. Everything suddenly made me happier that day
With half an appendix chapter to go, I decided to review an important class I stole from my old company for clues when I need to illustrate something involved using a semblance of a real world example (in the appendix, not abstract foo-bar passable for the docs)
It turns out, I hadn't implemented a functionality for restricting access to resources to only verified accounts. It just hasn't been required in the scheme of things. No matter, should be a piece of cake. I create a new middleware and it's done before I get to 50 lines. Then I try to update the documentation but to my surprise, user verification status turns out to be a subset of authentication locking. Instead of duplicating bindings for both authentication and verification, dev might as well use one middleware that checks for both and throws exceptions where appropriate.
BUT!
These aspects of the framework aren't middleware, at all. Call it poor design but I didn't envisage a situation where the indicators (authentication, path based authorisation and a 3rd one I don't recall), would perform behaviour deviating from the default. They were directly connected to their handlers and executed after within the final middleware. So there's no way to replace that default authentication scheme with one that additionally checks for verification status.
Whew
You aren't going to believe this. It may seem like I'm not serious and will never finish. I shut my system down for that day, even unsure how those indicators now have to refactored to work as middleware, their binding and detachment, considering route collections are composed down a trie
I'm mysteriously stronger the following day, draw up designs, draft a bunch of notes, roll my sleeves, and the tsunami began. Was surprisingly able to get most of previous middleware tests passing again before bed, with the exception of reshuffled classes. So I guess we can be optimistic that those other indicators won't cause more suffering or take us additional days off course 2
2 -
TLDR
Apparently if you delete your google account as an only admin of a workplace by just clicking remove account on expired subscription screen when you are on document page you not only loose access to google workplace but also you can create new workplace google account using same domain and email immediately and it’s fresh google domain account without domain verification and with everything wiped off from your old account. So you don’t have access to anything but on the other side there is possibility to use gmail as spam hub if google fucked ip something in their dns verification and once verified and after that expired domain gets bought again it stays verified.
Well I luckily migrated my gmail to other provider 3 years ago and I lost nothing important there but lol.
You can easily lock out yourself from your domain.
I opened ticket using some questionnaire and by adding another dns txt record to my domain to claim access to workplace admin page and let’s see what they do.
If they ever respond to that ticket and how long it will take to get it resolved.
This is good test to see if google is still a people’s company or an evil corporation.
I was using workplace as long as it was free from days of google app engine and begging of cloud revolution. I remember at best times I could chat with google support employee about spam I got from domain registered on google servers and he was processing ticket for me.2 -
Top 12 C# Programming Tips & Tricks
Programming can be described as the process which leads a computing problem from its original formulation, to an executable computer program. This process involves activities such as developing understanding, analysis, generating algorithms, verification of essentials of algorithms - including their accuracy and resources utilization - and coding of algorithms in the proposed programming language. The source code can be written in one or more programming languages. The purpose of programming is to find a series of instructions that can automate solving of specific problems, or performing a particular task. Programming needs competence in various subjects including formal logic, understanding the application, and specialized algorithms.
1. Write Unit Test for Non-Public Methods
Many developers do not write unit test methods for non-public assemblies. This is because they are invisible to the test project. C# enables one to enhance visibility between the assembly internals and other assemblies. The trick is to include //Make the internals visible to the test assembly [assembly: InternalsVisibleTo("MyTestAssembly")] in the AssemblyInfo.cs file.
2. Tuples
Many developers build a POCO class in order to return multiple values from a method. Tuples are initiated in .NET Framework 4.0.
3. Do not bother with Temporary Collections, Use Yield instead
A temporary list that holds salvaged and returned items may be created when developers want to pick items from a collection.
In order to prevent the temporary collection from being used, developers can use yield. Yield gives out results according to the result set enumeration.
Developers also have the option of using LINQ.
4. Making a retirement announcement
Developers who own re-distributable components and probably want to detract a method in the near future, can embellish it with the outdated feature to connect it with the clients
[Obsolete("This method will be deprecated soon. You could use XYZ alternatively.")]
Upon compilation, a client gets a warning upon with the message. To fail a client build that is using the detracted method, pass the additional Boolean parameter as True.
[Obsolete("This method is deprecated. You could use XYZ alternatively.", true)]
5. Deferred Execution While Writing LINQ Queries
When a LINQ query is written in .NET, it can only perform the query when the LINQ result is approached. The occurrence of LINQ is known as deferred execution. Developers should understand that in every result set approach, the query gets executed over and over. In order to prevent a repetition of the execution, change the LINQ result to List after execution. Below is an example
public void MyComponentLegacyMethod(List<int> masterCollection)
6. Explicit keyword conversions for business entities
Utilize the explicit keyword to describe the alteration of one business entity to another. The alteration method is conjured once the alteration is applied in code
7. Absorbing the Exact Stack Trace
In the catch block of a C# program, if an exception is thrown as shown below and probably a fault has occurred in the method ConnectDatabase, the thrown exception stack trace only indicates the fault has happened in the method RunDataOperation
8. Enum Flags Attribute
Using flags attribute to decorate the enum in C# enables it as bit fields. This enables developers to collect the enum values. One can use the following C# code.
he output for this code will be “BlackMamba, CottonMouth, Wiper”. When the flags attribute is removed, the output will remain 14.
9. Implementing the Base Type for a Generic Type
When developers want to enforce the generic type provided in a generic class such that it will be able to inherit from a particular interface
10. Using Property as IEnumerable doesn’t make it Read-only
When an IEnumerable property gets exposed in a created class
This code modifies the list and gives it a new name. In order to avoid this, add AsReadOnly as opposed to AsEnumerable.
11. Data Type Conversion
More often than not, developers have to alter data types for different reasons. For example, converting a set value decimal variable to an int or Integer
Source: https://freelancer.com/community/...2 -
Code verification
senior dev: You wrote this code yourself?
Me: Yes sir, it's clean right?
Senior Dev: Prove it
Me: Blah Blah Blah...
Senior Dev: Damn, You the realest -
Last day of a two week verification, I went to delete a duplicate folder. Instead I deleted the production folder. Never work on Allegra and zirtec. Luckily it was early in the morning and we only list about an hours work, from the day before's backup.
-
Is it just me or are graphical software verification libraries useless? I have had to take courses in several is them at uni. Usually, the diagrams end up being externally complex and more prone to errors than the software they are supposed to verify.
The fact that the "final project"of one course was to verify 100 lines of java in 2 weeks. Any beginning programmer could read the java code and confirm it was correct. The diagram my group produced could only be verified by a team of experts over the course of a year. How is it valuable to spend time "verifying"software if the verification needs even more verification than the original software.
Maybe I'm missing the point but I just don't get why there is a market for expensive propratary software in this area.1 -
Wifi used to be an issue in my incubator. Like I had mentioned in my earlier rant. There are many wifi's available now, but once when there was only one wifi available. That wifi network, was so terrible that it asks for human verification number of times even on google searches.
And the person responsible for wifi, is one of the most useless, undeserved person, I had ever seen
When a team from incubator talked to him about the issue, that this particular wifi's is pathetic, too many blocks and always asking for human verification, his reply was
"Just write 'S' after 'http', then it will work"
No doubt, everybody hates that guy.
But that guy cant be fired from job, because government. But he can be FIRED -
So...
I'm pretty sure that my satirical, educational, metaphor-esq, response was warranted... but just to check:
I'm having an issue with an online gambling platform... I'm in the USA-- recently several states allow online gambling. This specific one is a huge company so extra careful about proxies etc. To play via browser\desktop you need to install 3rd party, constant, network verification software... network architecture pro with my company's network, manually written ofc, running my static IPv4 /28 from my home = f that
app version even told me i had to uninstall rustdesk (it thinks i obeyed)
the issue is nothing controllable from client side... it's the same problem regardless of device, os (android phone, tablet, and iPad... fresh factory settings, bare bones and container versions... yea I was using it to procrastinate), network type, etc, etc
so i finally take the time to take a video of the issue (would be super confusing via screenshots)... even compress it to 1.5x speed and 240px, leaving the full screen (not cropping) and metadata intact. I point out that im a dev, and even worked for online gambling platforms...
i quickly mention all the noob troubleshooting bs, that i literally know every bit of data that moves on my network... that this issue is identical on both an iPad and android phones (so totally different apps\OSes)... the "live support" already tried(my req) totally deleting then reissuing the problematic promos... 'deleted' one persisted...etc
I clearly lay out all this info, even suggesting they forward it to someone in tech... give them the specific model numbers and OS builds of the primary devices(ipad and android phone)
...
I get back, an equally long, form response... summary:
we r soooo sorry you're having trouble
we care sooooo much about your\customer experience!
the tech team says (heavily implying it got escalated\forwarded) if you try these things itll fix it:
*imagine every generic troubleshooting guide from the early 2000s, plus a few notes like "(smartphone)"*
...and i shit you not, it even gave instructions to restart devices, power-cycle my modem\router and clear my browser cache. (all clearly nonsensical to anyone who read my initial email with a vague knowledge of English and/or tech)
Despite only having 1 valid hand to type with, i type nearly 70wpm (on my prefd keyboards)... so I lectured them, explaining their disrespectful bs clearly... and including a dumbed down metaphor relating a friendly request for a specific salsa recipe using\not using specific available ingredients... and replied to with a children's description of what a tomato is.
Explicitly gave a second chance to actually read the initial issue\email and forward or respond appropriately.
I was way more polite than my depiction seems...too polite.
soooo... i sent an additional email response...
i changed the subject so it'd still align with their ticket system but also identified the rep, with heavily implied disdain.
the contents of the additional response:
Dear 'Mary',
It seems that I forgot to include a very important resource for you.
I apologise. Please follow this link and complete all steps\levels. I want you to have a great online experience!
https://bestdosgames.com/games/...
Best Regards,
Sara Range
things like the "Best Regards," are artifacts of their formatting.
so... im not sure if i was too much of a dick, not enough, or if it even matters because it may go over their head.
opinions pl0x?6 -
Hey guys, I have almost developed the backend of an app like reddit. My question is about authentication. How should I authenticate my user. Is phone number necessary to add phone otp?Because I don't want to get any legal trouble if someone posts objectionable content on the platform. Most of the apps today need phone number, I dont know why except reducing spam accounts.
Or shall I verify email by otp. But its hard to track disposable emails. I cant go for only gmail too as its banned in china. Email domains of china are weird.
Can I get into legal trouble for objectionable content posted by any evil user?
I dont want to go for auth.10 -
Is it normal to use rabbitmq AND kafka in the same backend?
Rabbitmq for email verification, password reset etc and all that email bullshit handling
While kafka handles real time chat communication?
Since i noticed both of them work exactly the same. Producer/consumer. Pub/sub shit. Cant tell the difference other than a slightly different syntax9 -
Hate it when clients told you a specific requirement but then changes it the last minutes. You can't justify or argue. Can't do nothing about it but only follow. Just a high paid slave.
Example:
Client-verbal: background color of all 5 pages
Me-with email verification: ok. I will bg color of all pages will be red based from our last meeting.
Client email reply: ok
After a few days
Client: I think we have misunderstanding. What I meant was 4 pages red only. The 5th page should be maroon.
Me in my mind: wtf. Of course I can't argue but just agree and follow. The demo is near and he'll just inform the last minute. I will not win this argument.
Also, there are no acceptance criterias in the user story.6 -
Just built a solid desktop app for MacOS with Flutter that's worthy of shipping. I gotta say I'm pretty stoked about it, even if it isn't nearly as dope as LOIC. Haha chargin muh lazers!
I'll get some screenshots up soon!!
I also wrote a comple CLI interface for Firebase management using Python. Advanced auth abilities, CRUD capability, full json import/export, verification/password resets, you name it. Well, except full Firestore/mobile OTP features but it's still a win. Actually dicked around and made a cool little Firebase chat program in the terminal with the Python interpreter.
Finished up my first apps in React, React-Native and Ember, my 2nd with Electron, and also got my first Firebase hosted site up and running. Solid day!!! Cheers to that. And cheers to all of you amazing bastards!3 -
How would you implement a system that allow people to share a product that's normally one price but because of the referral there is a discount. Oh and the discount is supposed to based which country you live in.
Right now the whole system runs on the honor system and a little front end verification. How do I clean up this mess??
Sure getting the user's location could work until they use a vpn. I don't really know what to do here.3 -
Recently I made a dumb mistake :(
I have applied for credit card online and they have call me and asked me for info and send some messages which I need to forward someone that contain codes.
After that they ask for some docs, salary slips and bank statement etc. I got stuck for some tax forms.
So one day they just called that its ok if you can't submit your tax docs , we can make verification through debit card, I thought the call was genuine and I am in cc process, I shared my pin. and wohaaaa. my balance was deducted :( Thats was indeed a scam call.7 -
How can I make a bot which makes a single commit everyday at a specific time for a particular repository?
The commit can be anything like insertion in readme or creating a new file.
I tried to accomplish this using python selenium I deployed it on heroku, the problem I am facing is github doesn't allows to crawl on it so it sends a verification code to me on mail and all my further selenium actions fail due it this.☹️26 -
LOL XCode....I think they meant "X"tra useless, resembling such as a bag of dicks without handles!!!!
Also, being fucking buried because there's aren't any devs anywhere to be found near me makes me extra cranky!
Ive been hammering away at this Flutter, Java, Swift, Python, and Google maps for just about 36 hours on 3.5 hrs sleep. I just can't stop, I fuckin love this shit!!!
Considering the fact that I'm self taught and just started writing code for real about 7 months ago, I'd say I'm handling this alright for now. Every bit of tech is getting shot out of a cannon at this one- maps, real time tracking, state level auth/Id verification, custom components like ID scans/native desktop applications on custom linux machines, body cams, SIP trunking... all in 3 apps which are 100% multi-platform and scaled up to high end enterprise levels and being groomed for national release. I'm writing the code and doing the tech for ALL of it- even down to custom painted barcode scanners, a wallet system built from scratch, GPS integration, location/geofence based document querying... holy fuck guys I'm gonna fuckin die haha!!!
I went from barely getting websites made in late summer to this very moment, where I am pumping shit out in Flutter, Dart, Python, CPP, Js, Swift, Java, Kotlin, Obj-C, SQL/noSQL, and who knows what else.
I don't even know what the hell I just said haha I hope everyone has a great day! -
Okay soo... I have been working on a "notepad" script using bash. I basically have finished it but it lacks one thing. Verification if the user has typed anything! I started searching on google how i could do that, and found nothing (lol).
I'm asking help from you people :D
Here's the code that doesn't work.
while [[ $name != 'name' ]] || [[ $name == '' ]]
do
read -rp "What would you like the file name to be? The file extension is .txt!$(echo -ne '\n: ')" name
echo "Enter a valid file name please."
done
There's probably one small thing wrong anyway lol
Thanks already!3 -
Hey my bros. I’m trying to create a simple messenger bot just for fun using this tutorial:
https://medium.com/crowdbotics/...
But it seems that I’m kinda stuck with setting up the webhook on the fb page, it displays an error
“the url couldn’t be validated, callback verification failed...”
I googled for answers but it seems that it doesn’t work for me. Can you please help me? Thank you so much.4 -
I have Avira Password Manager and for 3 days now I can't access it because they send a verification code to the phone but that code was never received... FUCK YOU AVIRA4
-
While fucking my hot blonde gf this morning the Fucking DUREX condom BROKE and i creampied her. Here are the reasons why its not my fault:
1--Im not retarded
- 4 years of fcking my hot blonde gf with no protection and nothing ever happened cos im !retarded. Its a bigger risk to fuck with condom than without, how is this fucking normal???
2--I use condom the right way
- i was holding the tip so air comes out, just like it was explained on the box, but while rolling it down i was still holding the tip to make sure the air doesnt come back up
3--She was wet
- she wasnt dry. My hot blonde gfs pussy was so wet from how horny she was so its impossible that it got torn due to dryness
4--First verification
- it wasnt torn or ripped. It was normal. Everything looked absolutely fine
5--Second verification
- when i put it inside my hot blonde gf and fk her i pull it out in the first 10 seconds just to make sure it isnt torn--it was good and nothing was ripped so i slowly put it back inside
6--Condom is not thin
- i took the regular durex one (fuck this fucking dead fraud company I'll piss and shit on their grave) so it wasnt the thin bullshit one
7--Dont got a big black dick
- its normal. Average. Not small nor big. So latex elasticity isn't my problem
8--50-50%
- every FUcking time when i fked my hot blonde gf with a condom i always stressed if it'll break or not. This is not the first time it broke. FUCK the product that is THIS MUCH unreliable, unsafe and fragile! I'll fuck the whole durex company up. Im not the only one who had this problem. DUREX IS THE BIGGEST OVERRATED SCAM COMPANY SPENDING BILLIONS ON MARKETING FOR A LOW QUALITY SHIT PRODUCT THAT DOESNT EVEN WORK
9--Package didnt expire
- i bought a new box in the store on 8th march for womens day (modern women value having gifted with condoms more than flowers). It wasnt bought in a shit china quality shop. I fked her in the car at night and also creampied her but the condom did NOT break. Then i fked her this morning in bed with condom from the SAME BOX, and now it DID break. Are you Fucking kidding me???
10--Emergency contraception
- i died from high adrenaline of running so fast to the store to buy her contraception. Had to run to 4 fucking stores cause all of them don't work before 7:30am. Finally found one in the 4th store and she drank Escapelle within 20 minutes of incident, as soon as it was physically possible
11--And now what
- now what. What do i do. I did everything i could. Nothing is my fault. My hot blonde gf wanted me to creampied her it was her idea so shes at fault partially. She will get tested in 15 days while this contraception lasts. Dont know what else to try. This bullshit never happened before20 -
So I developed this bot which will make one commit everyday for. But duh! Github's security service sends me a verification code Everytime my script tries to login and the further selenium actions fails. 😂😂😂
In short : all my pain went in bin
If anyone knows how can I overcome this issue please let me know9 -
HELP!!! I fucked up my OP6 again trying to install Lineage 17.1.
I was running Oxygen Pie and folloqed steps .. Flashed Lineage Recovery 20200609
And then the rom but just boots into Fastboot now.
I'm guessing it's bc I didn't first install Oxygen 10 and upgrade the firmware?
Not though I'm trying to sideload the zip but it keeps stopping at Signature Verification failed.... Even though I said override...21 -
If you want to know more or any query, just knock us here–
24 Hours Reply/ (Contact Us)
Skype: Best5starshop
Telegram: @Best5starshop
Whatsapp: +1(650)690-5706
Our accounts are 100% legit and verified.
✔ 100% Satisfaction & Recovery Guaranteed.
✔ High-Quality Service.
✔ 100% verified accounts, USA, UK, CA and other countries.
✔ Full Completed Profiles.
✔ First Delivery.
✔ Phone verified are USA,CAN,other countries Account.
✔ 100% Satisfaction & Recovery Guaranteed.
✔ Card Verified.
✔ Bank Verified.
✔ Email Login Access.
✔ Number verified.
✔ BTC Withdrawal Enabled.
✔ 24/7 Ready to Customer Support.
Buy Verified Cash App Accounts. UK, USA, CA, AUS phone number and driving licensed and Credit Card add Cash App .Our accounts are meticulously verified to ensure seamless transactions, giving you peace of mind with every transfer.Instant access, reliable support, and hassle-free transactions. Purchase now!
Buy verified Cash App accounts to enhance global market trading and digital marketing efforts. These accounts offer security and reliability. Cash App has become a significant tool for traders and digital marketers. Docs verified accounts give a secure and proficient way to handle transactions. Verified accounts offer benefits like increased transaction limits and enhanced security features.
Traders can manage their investments more effectively, while digital marketers can handle payments seamlessly. Investing in verified Cash App accounts can streamline financial processes and improve overall business efficiency. This makes them a valuable asset for anyone engaged in global trading and digital marketing activities. If you feel, you need to buy verified cash app accounts place your order at
What is verified cash app and offers of cash app?
Verified Cash App accounts are accounts with confirmed individual data. These accounts offer a higher level of believe and security. They ensure smoother transactions and fewer restrictions. People use them for both personal and business purposes. Verification usually involves confirming identity details. Buy aged cash app account to avoid verification further.
If you want to know more or any query, just knock us here–
24 Hours Reply/ (Contact Us)
Skype: Best5starshop
Telegram: @Best5starshop
Whatsapp: +1(650)690-5706
Verified Cash App offer assistance to guarantee more secure and improve speedier cash exchanges. Many traders and digital marketers prefer using verified accounts. These accounts reduce the fraudulent activities. Verified accounts moreover have higher exchange limits. Buy verified cash app accounts with enhanced transaction limits.
Benefits of verified cash app account-
Verified Cash App accounts provide higher security. They use 100% upgraded advanced encryption for transactions. This ensures your money is safe. There is less risk of fraud. Unauthorized access is almost impossible. Buy aged cash app account at (website).
Verified Cash App accounts are very easy to use. Traders can quickly send and receive money. The interface is simple and user-friendly. Even a beginner can navigate it without any trouble.
Verified Cash App accounts help save money. Transaction fees are lower compared to banks. Traders can keep more of their earnings. This makes it a less costly option for many.
What is legal process to buy cash app accounts?
When you decide to buy cash app accounts, you have to follow few guidelines. Always buy from trusted sources. Look for verified sellers. Check their reviews. Ensure their accounts are legitimate. Verified accounts come with guarantees. Avoid unknown sellers. This reduces risks. Trustworthy sources provide support. They offer refunds if needed. They ensure account safety. Buy cash app accounts at (website).
Short Description
Buy Cash App With 15k Limits
If you want to flourish and safe your transaction and trade you should to buy cash app with 15K limits at (website). Our accounts are verified with selfie, SSN and bank details. So you are safe in using our cash app accounts.
Our Account Details-
Email verified
Phone number (US) verified
Owner selfie verified
Locked and unlocked accounts available
4k, 6k, 7.5k, 15k, 25k, and 50k acc. available
Superfast delivery confirmed
Customer satisfaction guaranteed
Meta Title
Buy Verified Cash App Accounts-100% BTC Enabled and Safe
Meta Description
Buy Verified Cash App Accounts from your trusted vendor in the USA (website) at very reasonable prices with virtual or physical cards. Place your order to buy now.joke/meme buy cash app accounts buy verified cash app accounts uk buy verified cash app accounts usa -
🐟💩The image i fetch from s3 is of type byte array
I return it to angular as an ArrayBuffer
Which then needs to be somehow converted to an image so i can fucking show it
Then after research i had to convert ArrayBuffer to Blob
And from Blob to URL encoded object which returns a string that now shows the full image in img tag
Somehow, by a sheer of trials and error i have just accidentally made a very secure way of fetching a very sensitive piece of document (verification document with user's personal data on it) and now in browser this is shown as blob:shit-image/random-hash. Not even the file extension. This means nobody can download this image. You fucking cant. Its a Blob motherfucker! Like a Blob Fish. It saves either a .txt when you try to save it (no idea how) and if you try to open the image in new tab it shows gibberish text. This means you can read-only this highly sensitive document image and not manipulate it, not even download it. Perfect. I have just made a very secure software by accident.
(this blob fish looks like my shit) 3
3 -
RECOVERING FROM FINANCIAL LOSS: A JOURNEY TO REDEMPTIOM'' HIRE RAPID DIGITAL RECOVERY
Email: rapid digital recovery (@) execs. com
WhatSapp: +1 4 1 4 8 0 7 1 4 8 5
Telegram: https: // t. me/ Rapid digital recovery519
Embarking on a foray into the stock market can be both exhilarating and daunting, particularly for novices. My journey began when a relative encouraged me to explore this financial realm. He connected me with a financial advisor he had discovered online, who radiated confidence and expertise. We initiated discussions about my investment aspirations via WhatsApp, and I felt a surge of optimism regarding potential gains. To kickstart my investment, I established a cryptocurrency wallet and completed the necessary KYC verification. With a sense of assurance, I allocated $250,000 into USDT ERC20, a stablecoin that seemed to be a prudent choice. The advisor, eager to amplify my investment, urged me to contribute further, emphasizing the rapid appreciation of gold as a lucrative opportunity. Trusting his acumen, I decided to invest an additional $50,000, convinced I was making a judicious financial decision. I soon realized that I had fallen victim to a meticulously orchestrated scam. The entirety of my $300,000 investment evaporated without a trace, leaving me despondent and desperate to recover my lost funds. The emotional toll of this loss was profound, as I grappled with feelings of betrayal and remorse for not exercising greater caution. I felt as though I had been swept away in a tide of misplaced trust, and the weight of my financial misstep was crushing. I turned to RAPID DIGITAL RECOVERY, a service renowned for its expertise in fund recovery. Their reputation for helping individuals reclaim lost investments provided a glimmer of hope amidst my despair. I reached out to their team, who diligently investigated my case with their dedication. Their expertise in navigating the complexities of financial scams was evident, and they provided me with the guidance I desperately needed. To my astonishment, RAPID DIGITAL RECOVERY successfully reclaimed my entire investment, restoring my faith in the possibility of recovering what I had lost. This imparted invaluable lessons about trust, due diligence, and the perils of uncritical faith in online advisors. It underscored the necessity of conducting thorough research before making substantial financial commitments and remaining vigilant against offers that seem excessively enticing. If you ever find yourself in a similar scam, I recommend contacting RAPID DIGITAL RECOVERY. Their expertise can significantly impact the recovery of lost funds and the restoration of trust in Crypto. RAPID DIGITAL RECOVERY truly transformed my situation from lost and reminding me that recovery is possible even after being scammed.5 -
Just built out my first app using Cloudflare Workers, Typescript, and DurableObjects. Holy shit, this is nice stuff.
It's taken little to no time to build out:
* JSON API written in Typescript
* JWT verification against my OAuth backend (SAML support too)
* CI Automated Deployments including unit tests
* DurableObject support
* 3rd party HTTP calls + caching (built in to the framework!) to reduce network latency and hiccups.
* Cron-like tasks on each stored object so they can awaken the app on a schedule and update themselves as necessary
* Rapid deployment to new environments
The local testing with coordinated "miniflare" is dreamy too. -
RECOVER BITCOIN, USDT, AND ETH FROM SCAMMERS HIRE ADWARE RECOVERY SPECIALIST
Six months ago, I made a life-changing decision: I left a stable job to pursue full-time cryptocurrency trading. After a full year of mentorship from my cousin—who had built substantial wealth through Bitcoin and altcoins—I felt ready to take the leap. I started with a modest investment of $20,000, trading cautiously between established cryptocurrencies and promising DeFi projects. To my surprise, my portfolio tripled in value within a few months, climbing to over $60,000. That early success fueled my ambition and confidence. WhatsApp info: +12 (72332)—8343
Emboldened, I decided to go all in. I liquidated my savings, borrowed against some assets, and raised my total investment to $390,000. At first, the decision seemed to pay off. My trades were profitable, and the returns felt consistent. I began to feel unstoppable. But then I made a critical mistake. Drawn in by the promise of zero-fee trading and instant withdrawals, I transferred my entire portfolio to a new, unverified exchange. Website info: h t t p s:// adware recovery specialist. com
At first, everything seemed perfect—executions were smooth, the interface was sleek, and my balance continued to grow. But when I attempted to withdraw funds, things took a turn. The support team began giving vague excuses about ‘wallet maintenance’ and ‘verification delays.’ Weeks passed, and then suddenly, my account was frozen for so-called ‘suspicious activity.’ Soon after, the platform went dark—the domain was inactive, support channels disappeared, and just like that, my life savings were gone.
The shock was paralyzing. I spent days in panic, scouring the internet for answers and barely sleeping. That’s when I discovered ADWARE RECOVERY SPECIALIST, a cybersecurity firm known for helping victims of crypto fraud. A fellow trader who had recovered lost assets recommended them. I was skeptical—but desperate. Email info: Adware recovery specialist@ auctioneer. net
ADWARE RECOVERY SPECIALIST quickly sprang into action. Their team traced blockchain transactions, identified the fraudulent network, and worked tirelessly to recover my funds. Thanks to their expertise, I was able to regain access to my wallet and recover a significant portion of what I had lost. While I didn’t get everything back, their intervention saved me from total financial ruin.
In the middle of that nightmare, I felt an overwhelming sense of gratitude—not just for the team’s skill and dedication, but for what I believe was divine intervention. I truly believe God led me to ADWARE RECOVERY SPECIALIST. It reminded me that even in our darkest hours, faith can light the path forward. Sometimes, the help we need comes through the hands of others—and I’m incredibly thankful that I found the right people at the right time.2 -
Need help with selecting a proper backend and website frameworks. After trying out a couple identity verification service providers we were dissapointed with their lack of support (takes weeks to do minimal changes).
So now we are having discussions about building in-house id verification system. We already have libraries for ios/android apps (ZOOM lib for face recognition and another lib for data extraction via OCR from document picture). So what we need is a proper backend and then a decent web framework with proper ux/ui design for our web/ios/android apps.
Currently thinking what kind of backend framework should we choose? Backend's main responsibility is for each client registered from website to assign an api key and to create a database/storage where his users would authenticate via clients app and upload a picture and a video.
Also wondering what kind of framework for website apps (main web app, dashboard app where we display pending verifications, and of course verification app) to choose. Should be go for angular? -
Ranting doesn't help if the you didn't verified the email. Really devRant, all my ranting I did previous about the customer is gone. _-_2
-
HOW TO RECOVER STOLEN CRYPOCURRENCY: TOP EXPERTS: TRUST GEEKS HACK EXPERT
I couldn't believe my eyes when I saw the e-mail: "Urgent Verification Needed for Your Bitcoin Wallet." I felt my stomach drop, and my panic set in. Then I was like, "It's probably just some kind of routine update. No biggie, right? " Yeah, right. Still in the heat of the moment, I clicked on the link without hesitation, entered my wallet details, and hit 'continue' so I could get back to the all-night gaming marathon.
Little did I know that by the time I actually retired to bed, I was committing one of the worst mistakes in my life. The following morning, waking up to see the Bitcoin wallet as usual with numbers staring at me-$850,000 in digital gold-I found nothing but. nothing. My heart just stopped for one second. All my funds vanished into thin air. Aghast, I stared at the screen as if an entire year's work plus my pride as a "cyber-aware" gamer had just ripped off from my face. The "urgent verification" email was one of those devious phishing emails contrived to swipe off my hard-earned Bitcoin. Panic and at a total loss, I started wondering what I do next. I had no idea where to begin, and I was certainly too embarrassed to ask my friends for help. It was then that I remembered something a friend had told me months ago about : Trust Geeks Hack Expert Website. w w w :// trust geeks hack expert .c o m . I was skeptical at first. Could they really help me get my money back after I'd made such a boneheaded move? But a quick call to them and I thought, well, they aren't some fly-by-night operation, merely looking for a quick score. These were pros.The Trust Geeks Hack Expert team took over, burrowing deep into the digital ether and tracking my stolen Bitcoin with a precision I couldn't have imagined. It wasn't an instant fix, but after several weeks of diligent work, they recovered my $850,000. The feeling was indescribable; I swear, I almost started crying like I'd just finished a boss fight. If there is one thing that I picked up, it is this: in this world of cybersecurity, side quests can get you killed. Clicking on a random link while in the heat of gaming may seem harmless, but with one click, it could cost you everything. Thanks to Trust Geeks Hack Expert, I got my funds back and learned to think twice before clicking on anything that looks even remotely suspicious. for assistance, E m a i l : in fo @ trust geeks hack expert. c o m (Te le G r a m:: Trust geeks hack expert) & w h a t' s A p p +1 7 1 9 4 9 2 2 6 9 31 -
"When it comes to online gambling, slot games remain one of the most popular choices among players around the world. Whether you're a beginner or a seasoned gambler, the slots section at Pin-Up Casino offers an incredible variety of themes, game mechanics, and winning possibilities. If you're looking for a dedicated guide to help you understand everything about the slot experience at Pin-Up, https://pin-uplogin.com/slots/ is the perfect resource.
The website offers a comprehensive overview of the slot collection available at Pin-Up. From classic fruit machines to the latest video slots with 3D graphics and immersive soundtracks, there is something for every taste. Many of these slots come from top-tier developers such as NetEnt, Play'n GO, and Pragmatic Play, ensuring both quality and fairness.
In addition to game reviews, the site also offers helpful tips and insights into volatility, return-to-player (RTP) percentages, bonus features, and more. If you're new to online slots, understanding how paylines work or what ""free spins"" mean can be overwhelming, but the site breaks down everything in a user-friendly way.
Another important aspect covered is how to register and start playing on Pin-Up. It walks you through the login process, account verification, and making your first deposit to access the full slot library. Security and fair play are also discussed, giving players peace of mind before spinning the reels.
Whether you're playing for entertainment or hoping to hit the jackpot, this guide is a reliable companion to help you explore and enjoy the world of Pin-Up slot games in a smart and responsible way."9 -
BLOCKCHAIN CYBER RETRIEVE >> I NEED A HACKER TO RECOVER STOLEN USDT/BTC
My divorce led to emotional upheaval and financial strain. My wife took most properties and funds during the settlement. Determined to rebuild, I made unfortunate decisions. A friend, Moses, suggested venturing into the stock market. He introduced me to a financial advisor he found online. The advisor seemed knowledgeable, and I began discussing my goals via WhatsApp. I set up a crypto wallet, completed KYC verification, and invested $50,000 in USDT ERC20. The advisor urged me to invest more, citing gold's rapid appreciation. I trusted her expertise and invested an additional $150,000. Unbeknownst to me, I had fallen victim to a well-orchestrated scam. The entire investment of $200,000 was wiped out. was desperate to reclaim back my funds Fortunately, I found Blockchain Cyber Retrieve online. Their expertise gave me hope and my whole lost was successfully recovered back to me. This experience taught me invaluable lessons about trust, due diligence, and the risks of blind faith. If you ever find yourself in this situation reach out to Blockchain Cyber Retrieve via the following contact information:
WHATSAPP: + 1 520 5 64 8300
EMAIL: blockchaincyberretrieve (@) post. c o m4 -
HIRE A GENUINE HACKER TO RECOVER LOST BTC & USDT- VISIT SALVAGE ASSET RECOVERY
I had $560,000 in Bitcoin saved up to fund my life's passion, an off-grid solar project designed to bring light to rural villages. Years of scrimping, saving, and explaining to skeptical relatives that no, Bitcoin wasn't just for internet gamblers, came down to this. But a slip of the finger almost sent my plans into eternal darkness.
Making a final transfer to consolidate my project funds, I had copied the wrong wallet address. It was so quick. One paste, one click, and my stomach dropped faster than a solar panel off a roof. My entire investment vanished into the digital ether. I stared at the screen, waiting for it to grow arms and slap me in the face. When it didn't, I knew I was in trouble.
Desperation led me to an energy summit, more for a diversion than anything. But fate has a sense of humor. During networking in a break, I heard a speaker casually mention Salvage Asset Recovery, as one might refer to a weather app, not the digital cavalry. I pounced like a man who'd seen a power outlet in the desert.
From that first call, their crew oozed competence and tranquility. They treated my busted transfer like an engineering challenge, not a personal disaster (even though I was seconds away from rechristening the project "Bit coinless in the Dark"). Using advanced blockchain tracing techniques, they mapped the Byzantine trail of transactions. I imagined them in hard hats, working the blockchain like electricians restoring downed power lines.
Each update brought hope. Eleven days in, they located the funds. Two days after that, I had it back, every Satoshi. I nearly hugged my solar panel prototype.
The Salvage Asset not only recovered my money; they future-proofed me. They walked me through address verification processes, multi-sig security, and how not to let jitters turn your dream into a nightmare. It did not come across as a lecture but more like taking advice from an older brother who went through every tech blunder imaginable.
Today, my project is charging forward (pun intended). The first village will soon bask in sustainable power. When they flip that switch, I’ll know it was made possible by hard work, a bit of luck, and the brilliance of Salvage Asset Recovery. REACH OUT TO SALVAGE ASSET RECOVERY, THIER CONTACT DETAILS
TELEGRAM---@Salvageasset
WhatsApp+ 1 8 4 7 6 5 4 7 0 9 6 1
1 -
It started with a gut-wrenching realization. I’d been duped. Months earlier, I’d poured $133,000 into what I thought was a golden opportunity a cryptocurrency investment platform promising astronomical returns. The website was sleek, the testimonials glowed, and the numbers in my account dashboard climbed steadily. I’d watched my Bitcoin grow, or so I thought, until the day I tried to withdraw it. That’s when the excuses began: “Processing delays,” “Additional verification required,” and finally, a demand for a hefty “release fee.” Then, silence. The platform vanished overnight, taking my money with it. I was left staring at a blank screen, my savings gone, and a bitter taste of shame in my mouth.I didn’t know where to turn. The police shrugged cybercrime was a black hole they couldn’t navigate. Friends offered sympathy but no solutions. I spent sleepless nights scouring forums, reading about others who’d lost everything to similar scams. That’s when I stumbled across a thread mentioning a group specializing in crypto recovery. They didn’t promise miracles, but they had a reputation for results. Desperate, I reached out.The first contact was a breath of fresh air. I sent an email explaining my situation dates, transactions, screenshots, everything I could scrape together. Within hours, I got a reply. No fluff, no false hope, just a clear request for more details and a promise to assess my case. I hesitated, wary of another scam, but something about their professionalism nudged me forward. I handed over my evidence: the wallet addresses I’d sent my Bitcoin to, the emails from the fake platform, even the login credentials I’d used before the site disappeared.The process kicked off fast. They explained that scammers often move funds through a web of wallets to obscure their tracks, but Bitcoin’s blockchain leaves a trail if you know how to follow it. That’s where their expertise came in. They had tools and know-how I couldn’t dream of, tracing the flow of my coins across the network. I didn’t understand the technical jargon hash rates, mixing services, cold wallets but I didn’t need to. They kept me in the loop with updates: “We’ve identified the initial transfer,” “The funds split here,” “We’re narrowing down the endpoints.” Hours passed , and I oscillated between hope and dread. Then came the breakthrough. They’d pinpointed where my Bitcoin had landed a cluster of wallets tied to the scammers. Some of it had been cashed out, but a chunk remained intact, sitting in a digital vault the crooks thought was untouchable. I didn’t ask too many questions about that part; I just wanted results. They pressured the right points, leveraging the blockchain evidence to freeze the wallets holding my funds before the scammers could liquidate them. Next morning, I woke up to an email that made my heart skip. “We’ve secured access to a portion of your assets.” Not all of it some had slipped through the cracks but $133,000 worth of Bitcoin, my original investment, was recoverable. They walked me through the final steps: setting up a secure wallet, verifying the transfer, watching the coins land. When I saw the balance tick up on my screen, I sat there, stunned. It was real. My money was back.The ordeal wasn’t painless. I’d lost time, sleep, and a bit of faith in humanity. But the team at Alpha Spy Nest Recovery turned a nightmare into a second chance. I’ll never forget what they did. In a world full of thieves, they were the ones who fought to make things right. Contacts below: WhatsApp: +14159714490
 1
1 -
Two months ago, I became the victim of a highly convincing online scam that cost me $180,000 worth of Bitcoin. It started with what looked like a legitimate crypto investment platform, professional branding, fake success stories, and even fake chat support that responded in real time. Everything appeared real, until it wasn’t, I invested slowly at first, but as I saw fake profits showing up on the dashboard, I sent more Bitcoin believing I was making a smart move. When I finally tried to withdraw some funds, everything changed. They demanded more deposits to unlock withdrawals, then stopped responding altogether. Eventually, the site disappeared. I was devastated. My wallet had been drained, and every attempt to recover the funds led to dead ends, until someone mentioned Dexdert Net Recovery. I contacted them out of desperation, not expecting much. But from the very first call, I felt like I had found people who actually understood the blockchain, fraud patterns, and recovery process. Dexdert’s team got to work immediately, launching a forensic investigation into the wallet addresses and transaction trail. To my surprise, they identified the scammer’s laundering network and traced the stolen Bitcoin through various exchanges and wallets. With their partnerships and legal network, Dexdert initiated a recovery operation, After weeks of consistent work, verification, and negotiations. Dexdert successfully reclaimed my lost BTC. That’s over $180,000 back in my hands, something I had written off as impossible. If you’ve lost crypto to fraud, don’t give up. There are real professionals out there who can help and for me, that was Dexdert Net Recovery. For me, Dexdert Net Recovery didn’t just recover my Bitcoin, they helped me reclaim peace of mind.
CONTACT INFORMATION:
Telegram: (@Dexdertprorecovery) WhatsApp: (+1 (859) 609‑4156)2 -
Lets say i have to send an email to the user when:
- user forgot password (email sent with a token to verify the user owns that email, and token identifies for which user is this link valid)
- email verification (email sent with a token to verify the user who just registered, where this token uniquely is generated for each newly registered user)
- etc
Notice how both of these cases include the same shit:
- sending emails
- generating unique tokens
- attaching each record to individual user
Does this mean i should pack this up in 1 single model in the database and differentiate which type of email it is over an enum (EMAIL_CONFIRM, FORGOT_PASSWORD etc)?
Or should these shits each have a different model and thus different tables in database?35 -
Buy Verified Cash App Accounts
In today's fast-paced digital world, mobile payment apps have revolutionized the way we handle financial transactions. Cash App, a popular mobile payment service, has gained widespread recognition for its user-friendly interface and seamless money transfer capabilities. As the demand for Cash App accounts increases, the significance of obtaining a verified account becomes more apparent. In this article, we will explore the concept of purchasing verified Cash App accounts, understanding its benefits, potential risks, and essential tips for a secure and successful transaction.
Understanding Cash App
What is Cash App?
Cash App, also known as Square Cash, is a peer-to-peer mobile payment service that allows users to send, receive, and request money through their smartphones. With its straightforward design and hassle-free functionality, Cash App has become a preferred choice for individuals and businesses alike.
How does Cash App work?
Cash App operates by connecting to the user's bank account or debit card, facilitating seamless and instant money transfers to other Cash App users. Users can also load funds onto their Cash App balance, known as the "Cash Card," to make purchases or withdraw cash from ATMs.
Importance of Verified Cash App Accounts
Security and Safety
Having a verified Cash App account adds an extra layer of security to your financial transactions. Verified accounts undergo a thorough verification process, which helps ensure the legitimacy of the user and reduces the risk of unauthorized access.
Transaction Limits and Benefits
Verified Cash App accounts come with higher transaction limits, allowing users to send larger amounts of money. Moreover, verified users may have access to exclusive promotions and rewards offered by Cash App.
Ease of Use
With a verified account, users can seamlessly link their bank accounts or cards to the app, streamlining the process of sending and receiving money.
Risks and Concerns
Scams and Fraudulent Accounts
One of the primary concerns when considering the purchase of Cash App accounts is the presence of scams and fraudulent sellers. Dealing with unreliable sources can lead to financial losses and potential misuse of personal information.
Violation of Terms of Service
Buying or selling Cash App accounts is against the platform's terms of service. If discovered, such accounts may be subject to suspension or permanent banning, resulting in the loss of funds and access to Cash App services.
Identity Theft
Using a purchased Cash App account without changing the login credentials can expose the buyer to identity theft. It is crucial to take necessary precautions to safeguard sensitive information.
Buying Verified Cash App Accounts
Reputable Sources
When seeking to buy a Cash App account, it is essential to choose reputable and trustworthy sources. Conduct thorough research, read customer reviews, and seek recommendations from reliable sources before making a decision.
Verification Process
Before making a purchase, ensure that the seller provides a transparent explanation of their verification process. The verification process should align with Cash App's guidelines and industry best practices.
Tips for Safe Purchase
Research the Seller
Thoroughly research the background and reputation of the seller before proceeding with the purchase. Avoid dealing with sellers who have a history of negative reviews or questionable practices.
Verify Account Authenticity
After purchasing a Cash App account, verify its authenticity by logging in and reviewing the account details. If any discrepancies are found, contact the seller immediately.
Use Secure Payment Methods
Opt for secure payment methods, such as PayPal or credit cards, that offer buyer protection in case of fraudulent transactions.
Change Login Credentials
To protect against identity theft, change the login credentials (username and password) of the purchased account immediately after the transaction.
Using a Purchased Cash App Account
Linking Bank Accounts and Cards
After acquiring a Cash App account, link it to your bank accounts or debit cards to enable seamless transactions.
Investing and Trading
For users interested in investing or trading stocks through Cash App, the verified account provides a secure platform to explore investment opportunities.
Conclusion
Purchasing a verified Cash App account can offer convenience and additional benefits to users, but it comes with potential risks. It is vital to approach the purchase with caution, thoroughly research the seller, and follow safety measures to avoid scams and fraudulent activities. By taking these precautions, users can enjoy the seamless and secure experience of using Cash App for their financial transactions.
-
Buy Verified Cash App Account: Navigating the Digital Transaction Landscape
In an age dominated by digital transactions, the concept of purchasing a verified Cash App account has gained significant traction. This article aims to explore the nuances of buying a verified Cash App account, elucidating the advantages, potential risks, and offering a comprehensive guide for individuals considering this financial move.
Introduction
The Growing Trend of Buying Verified Cash App Accounts
As online transactions become more prevalent, the trend of purchasing verified Cash App accounts is on the rise. Users are increasingly recognizing the added benefits and security that come with having a verified account.
Understanding the Importance of Account Verification
Account verification is a crucial step in enhancing the security of digital transactions. A verified Cash App account provides users with an additional layer of protection, making their financial interactions more secure and reliable.
Advantages of Purchasing a Verified Cash App Account
Enhanced Security Features
One of the primary advantages of a verified Cash App account is the incorporation of advanced security features. These may include multi-factor authentication and additional verification steps, adding an extra layer of defense against unauthorized access.
Increased Transaction Limits
Verified accounts often come with substantially increased transaction limits. This proves beneficial for users engaged in larger financial transactions or those running businesses through the Cash App platform.
Access to Exclusive Cash App Features
Apart from heightened security and increased transaction limits, verified accounts may unlock exclusive features within the Cash App. This could range from priority customer support to early access to new features and promotions.
How to Safely Purchase a Verified Cash App Account
Researching Reputable Sellers
Before entering the purchasing process, it's crucial to research and identify reputable sellers. Reading reviews and testimonials can provide valuable insights into the credibility and reliability of a seller.
Authenticating Account Legitimacy
Ensuring the authenticity of the accounts offered by sellers is paramount. A legitimate verified account should have gone through the necessary verification steps outlined by Cash App.
Ensuring Transparency in Transactions
Transparency in transactions is vital. Buyers should choose sellers who provide clear information about the accounts, including their verification status and any associated features.
Risks and Precautions in Buying Verified Accounts
Common Scams in the Verified Account Market
The digital landscape is not without risks, and the market for verified Cash App accounts is no exception. Being aware of common scams, such as fake listings and phishing attempts, is essential.
Tips for a Secure Transaction Process
To mitigate the risk of falling victim to fraudulent transactions, following best practices such as using secure payment methods and verifying the seller's credentials is crucial.
Step-by-Step Guide to Verifying a Cash App Account
Understanding the Cash App Verification Process
Before attempting to verify a Cash App account, it is essential to understand the process thoroughly. Familiarizing oneself with the required documentation and steps ensures a smooth verification experience.
Submitting Required Information
During the verification process, users typically need to provide personal information, such as a valid ID and proof of address. Ensuring the accuracy and legitimacy of this information is key to a successful verification.
Navigating Potential Challenges
While the verification process is generally straightforward, users may encounter challenges. Being prepared to troubleshoot and address potential issues ensures a seamless verification experience.
Conclusion
Summarizing the Benefits and Risks
In conclusion, opting for a verified Cash App account offers users enhanced security, increased transaction limits, and exclusive access to platform features. While potential risks exist, informed decision-making and adherence to safety precautions can lead to a positive experience.
Encouraging Informed Decision-Making
As users consider the option of purchasing a verified Cash App account, it is crucial to approach the process with caution and awareness. Choosing sellers with proven credibility, staying informed about potential risks, and following best practices contribute to a secure and positive experience. devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account
devrant cash app buy verified cash app accounts buy verified cash apps buy verified cash app account uk buy verified cash app account usa buy verified cash app account -
RECOVER MY STOLEN CRYPTO / TRACK STOLEN CRYPTO WITH PROFICIENT EXPERT CONSULTANT
One Friday in Texas, I was filled with anticipation as I prepared to onboard a new subcontractor for a project that had been meticulously planned for months. As the project manager, I bore the responsibility of ensuring that every detail was executed flawlessly, and I was eager to integrate this new talent into our team. The subcontractor had reached out to me via email, presenting themselves as a highly skilled professional with an impressive portfolio. Our exchanges were seamless and persuasive, instilling a growing confidence in their capabilities. They proposed using Bitcoin for payment, asserting that it was the most efficient and secure method available. Trusting their professionalism and the burgeoning trend of cryptocurrency transactions, I proceeded with the transfer, sending 4 Bitcoin (BTC) to the wallet address they provided. I felt a profound sense of accomplishment. I had fulfilled my obligation, and everything appeared to be falling into place. My relief swiftly morphed into dread when I realized that the subcontractor had vanished without a trace. All communication ceased, and the email address I had been corresponding with was no longer active. Panic surged through me as I grasped the gravity of the situation I had been duped. I convened with my team to discuss the unfortunate turn of events. We quickly recognized the irreversible nature of cryptocurrency transactions. Unlike traditional banking, where payments can often be reversed, this was a permanent loss. The amount I had sent was substantial, and the thought of losing it all was overwhelming. A sinking feeling settled in my stomach as I contemplated the ramifications of my actions. I had placed my trust in someone I barely knew, and now I was confronting the consequences of my misplaced faith. I embarked on a quest for solutions and discovered PROFICIENT EXPERT CONSULTANT, a firm specializing in tracing and recovering lost or stolen cryptocurrency. Their website was replete with testimonials from individuals who had successfully reclaimed their funds, which ignited a flicker of hope within me. I reached out to PROFICIENT EXPERT CONSULTANT immediately via PROFICIENTEXPERT @ CONSULTANT . C O M ~ Telegram : @ PROFICIENTEXPERT for your support, articulating my predicament in detail. Their team was remarkably responsive and assured me that they would employ every resource at their disposal to track the funds. They explained how they would utilize advanced blockchain analysis techniques to trace the Bitcoin and gather compelling evidence of the fraud. As PROFICIENT EXPERT CONSULTANT commenced their investigation, I learned just how sophisticated these scammers could be. The funds I had sent were swiftly transferred to another wallet, and the scammer had employed mixing services to obfuscate the trail, complicating efforts to trace the money. However, the experts at PROFICIENT EXPERT CONSULTANT were undeterred. They worked diligently, leveraging their expertise in blockchain technology to follow the digital breadcrumbs left behind by the scammer. With each update from PROFICIENT EXPERT CONSULTANT, I felt a renewed sense of hope that they might be able to recover my lost Bitcoin. This has been a harsh lesson when navigating the cryptocurrency landscape. Thanks to PROFICIENT EXPERT CONSULTANT, I now comprehend the necessity of implementing robust verification processes for new subcontractors and the imperative of secure payment methods. In my role, I have come to appreciate the significance of thoroughly verifying the identities of those I engage with and ensuring that payment methods are fortified against potential fraud. In hindsight, I wish I had taken the time to authenticate the subcontractor’s identity through multiple channels and utilized an escrow service to safeguard my funds. I am relieved to share that I recovered all the funds. I hope that sharing my story will serve as a cautionary tale for others. Cryptocurrency offers myriad benefits, but it also harbors significant risks that cannot be overlooked. I urge anyone engaging in digital transactions to exercise caution, conduct thorough research, and prioritize security measures to protect themselves from potential scams. With the invaluable assistance of PROFICIENT EXPERT CONSULTANT, I learned that there are resources available to aid victims of fraud, and I hope others can find the same support in their times of need.5 -
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.5 -
Late last year, I stumbled upon what looked like a professional crypto trading platform offering high-yield investments with expert guided automation. The testimonials seemed legitimate, and the website design was sleek and convincing. I had dabbled in crypto before, so I wasn’t completely naïve or so I thought. Over months, I invested gradually. The profits rolled in quickly, and I began to trust the system. Encouraged, I ended up committing a total of $260,000 worth of Bitcoin. But when I tried to withdraw, the nightmare began. Excuses piled up security verification issues, technical upgrades, and finally, a demand for more money to unlock withdrawals is a classic red flag. It hit me then I’d been scammed. the panic was immediate, followed by helplessness. I had no idea how or even if I could recover the funds. That's when a friend recommended Dexdert Net Recovery. Skeptical but desperate, I contacted them. Unlike the scammers, Dexdert’s team was transparent, professional, and surprisingly human. They didn’t promise miracles, just a real effort backed by experience in blockchain tracing, cyber investigation, and legal collaboration with international crypto crime units. What followed was a whirlwind. They tracked the movement of my stolen Bitcoin through multiple wallets, used advanced tools, Within weeks, Dexdert Net Recovery successfully my BTC. I watched in disbelief as my wallet balance finally reflected the $260,000 I thought I’d lost forever. What Dexdert did wasn’t just about money it was about restoring trust and hope. Their work showed me that even in the murky waters of crypto fraud, there are professionals fighting back. If you’ve been a victim, don’t stay silent. Report it. Act quickly. And if you’re lucky enough to come across Dexdert Net Recovery, know that you’re not alone and recovery is possible.
Contact Dexdert Net Recovery For Help Via:
WhatsApp: (+1 859 609 4156)Telegram: (@Dexdertprorecovery)2 -
Hire A Cryptocurrency Fraud Recovery Hacker Service Online: VISIT CERTIFIED RECOVERY SERVICES
It started with optimism. A serendipitous encounter with an old college friend in Miami’s bustling airport led to a conversation about financial growth. He spoke glowingly of Dollar fx net, a platform he insisted had doubled his investments. Trusting his enthusiasm, I deposited 10,000 USD a substantial chunk of my job savings only to face a shocking roadblock weeks later. The platform demanded an additional 5,000 “verification fee” to unlock withdrawals. My stomach dropped; this wasn’t a hiccup it was a trap. Stress pushed me into research mode. Scouring cybersecurity forums, I uncovered countless stories mirroring mine: unregulated platforms exploiting trust, draining accounts under false pretenses. Then, a lifeline a Reddit thread praising CERTIFIED RECOVERY SERVICES for their no-nonsense approach to fund retrieval. Skeptical but out of options, I submitted a case file through their portal, hoping for a miracle. The response from CERTIFIED RECOVERY SERVICES was swift and reassuring. They outlined a comprehensive strategy: trace the digital trail of my 10,000 USD, they apply pressure on the platform through legal backchannels. Their transparency struck me while they couldn’t guarantee success, their expertise was evident. Over the next week, CERTIFIED RECOVERY SERVICES became my digital sherpa, guiding me through the murky waters of online fraud recovery. Their team meticulously decoded Dollar fx net’s obfuscated transaction logs, revealing that my funds had been funneled into offshore wallets, far from any regulatory oversight. Armed with this information, their legal team issued takedown notices to payment processors linked to the platform, effectively putting them on notice. The pressure worked: on day 10, I received a cryptic email from Dollar fx net claiming my account was “under review. "By week two, the impossible happened my original 10,000 USD reappeared in my bank account, sans the fabricated fees. CERTIFIED RECOVERY SERVICES later explained how their threat of exposing the platform’s infrastructure to regulators had forced their hand. Their relentless pursuit of justice to recover my funds and also highlighted the importance of holding fraudulent platforms accountable. This ordeal taught me two harsh truths: not all opportunities are as they seem, and due diligence is non-negotiable. Yet it also revealed heroes like CERTIFIED RECOVERY SERVICES ethical hackers who use their skills to fight back against fraud. I now understand that vigilance and the right support can turn the tide against deceit. In a world where fraudsters thrive on silence, speaking out and seeking help can be the most powerful tools in reclaiming what is rightfully yours.
Here's Their Info Below:
WhatsApp: (+1(740)258‑1417 )2 -
THE SOLUTION: "HOW FOLKWIN EXPERT RECOVERY EMPOWERED ME TO REGAIN MY FINANCIAL FREEDOM"
I advise first-time Bitcoin investors to do their research before entrusting any of the Bitcoin investment websites with their hard-earned funds. I learned this the hard way. These platforms can appear very legitimate, often showcasing fake huge profits to convince users to invest more money. They built my trust by promising high returns and painting a picture of success that seemed too good to pass up. Initially, my investments seemed to yield impressive returns, and I felt encouraged to invest a larger sum. However, the situation quickly turned sour when I deposited a significant amount. After I made the larger investment, my account was intentionally frozen, and the platform demanded additional payments for "verification fees" and other bogus charges before I could access my funds or withdraw any of my supposed profits. They used manipulation tactics to keep me trapped in the scam. I was left frustrated and helpless as I realized I had been duped, losing a substantial sum of 54,000 CAD. It was a very unsettling experience, as I couldn’t figure out where to turn for help. I had no idea how to recover my lost funds or even how to identify the scam. That’s when I came across Folkwin Expert Recovery. They specialize in helping victims of online scams recover their lost funds, and they proved to be a lifeline. Folkwin Expert Recovery took swift action and assisted me through the entire process with professionalism and dedication. They were relentless in their efforts and provided me with regular updates, ensuring that I was always informed about the status of my case. In the end, I was able to successfully recover the money that I thought I had lost forever. Their team’s expertise and persistence in navigating the complexities of these scams made all the difference. If you ever find yourself in a similar scenario where your Bitcoin investments have gone awry, or your account has been frozen by a fraudulent platform, I highly recommend reaching out to Folkwin Expert Recovery. Their support can make all the difference in recovering your funds and protecting yourself from further scams. Always be cautious, do thorough research before making any investments, and never hesitate to seek help if something doesn’t feel right.
(FOLKWIN EXPERT RECOVERY DETAILS)
Telegram: @Folkwin_expert_recovery
WhatsApp + 1 7 4 0 - 7 0 5 - 0 7 1 1
Email: Folkwinexpertrecovery(AT)tech-center. c o m
Regards,
Mr. Sebastian Gorka.1 -
I still remember the pit in my stomach when I realized I’d been scammed. Months of careful saving, research, and planning vanished in an instant along with my Bitcoin, It started innocently enough. I was introduced to what seemed like a reputable cryptocurrency trading platform via social media. The website was polished, the support team was responsive, and their experts guided me every step of the way. Then, the platform vanished overnight. My wallet emptied. My Bitcoin Gone. I was devastated. My bank couldn’t help, they said it was outside their jurisdiction. Law enforcement was sympathetic but slow-moving. I began to accept the bitter truth that I had been defrauded. Then I came across Dexdert Net Recovery while researching online recovery services. At first, I was skeptical after all, hadn’t I just been scammed , I was desperate, From the beginning, Dexdert’s Net Recovery approach was different. They didn’t promise miracles or instant results. Instead, they provided a transparent breakdown of their investigative process. They explained how they use blockchain forensics, deep-web tracking tools, and a global network of legal and cybersecurity experts to trace stolen digital assets. They asked for every detail: wallet addresses, transaction IDs, email trails, and screenshots of conversations with the scammers. Within a few days, they traced the Bitcoin I had transferred. It had been split and rerouted through multiple wallets in classic laundering techniques. After several weeks of persistent efforts, negotiations, and verification, I received the email I never thought I would see. We've recovered your assets. And sure enough, my Bitcoin had been returned to a secure wallet under my control. It wasn’t just about the money. It was about justice. About reclaiming what was mine. If you’ve been a victim of crypto fraud, don’t suffer in silence. There are professionals out there who can help. For me, that was Dexdert. And they gave me a second chance.
REACH OUT FOR HELP FROM THE BEST RECOVERY SERVICE:
WhatsApp: ( +1 859 609 4156)2 -
Ok so how many people on here know what VDM is. I cannot seem to find anyone outside of my uni that does.2
-
LOOKING FOR A LEGIT HACKER OR RECOVERY SPECIALIST HIRE ADWARE RECOVERY SPECIALIST
I received what appeared to be an official email from Binance, claiming I had been selected for an exclusive Binance Visa card. The offer promised impressive perks and rewards, but there was one condition: I had to pay a “verification fee” of 20,000 BNB to activate the card. WhatsApp info:+12 (72332)—8343
The email looked convincing, and the linked website was professional and closely resembled the real Binance platform. Caught up in the excitement, I made a rushed decision and sent the payment. Telegram info: h t t p s:// t. me / adware recovery specialist1
After that, nothing happened. I didn’t receive a card or even a confirmation email. Customer support was unresponsive, and it quickly became clear—I had been scammed. The realization was devastating. I had worked tirelessly to build my crypto portfolio, and in one moment, it was all gone. Email info: Adware recovery specialist @ auctioneer. net
Desperate for a solution, I began searching for a way to recover my funds. That’s when I found ADWARE RECOVERY SPECIALIST. Unsure but hopeful, I reached out. To my surprise, their team responded almost immediately. They were professional, empathetic, and confident they could help.
Their experts used advanced blockchain forensics to trace the stolen 20,000 BNB. They followed the funds through multiple wallets and exchanges, uncovering the laundering trail. Working with authorities and security teams, they successfully froze the assets and began the recovery process.
Amazingly, within a week, ADWARE RECOVERY SPECIALIST had recovered my entire 20,000 BNB. I was shocked and incredibly relieved—I never thought I’d see that money again. Website info: h t t p s:// adware recovery specialist. com
I’m sharing this experience as a warning: crypto scams are becoming more sophisticated every day. Always verify offers, double-check URLs, and contact official support before taking action. If you’ve already fallen victim, don’t give up—help is out there.
I’m forever grateful to ADWARE RECOVERY SPECIALIST for their expertise and support, and I highly recommend their services to anyone needing assistance with crypto recovery.2 -
I thought I had hit the jackpot when I stumbled upon an enticing crypto casino promising huge payouts and "provably fair" games. The website was sleek, with vibrant graphics and testimonials from users claiming life-changing wins. Intrigued, I decided to take the plunge and deposited 2 BTC, which was worth over $120,000 at the time. The thrill of the gamble was exhilarating, and I quickly found myself on a winning streak, doubling my balance in just a few days. It felt like I was on top of the world, convinced that I had found a legitimate platform that would reward my risk-taking. The excitement turned to dread when I attempted to withdraw my winnings. The site blocked my request, citing a need for "verification" and demanding additional fees that seemed unreasonable. I was taken aback; I had already provided my initial information during registration. As I navigated through the site, I noticed that the customer support was unresponsive, and the live chat feature was mysteriously offline. Days turned into a week, and my withdrawal requests continued to be ignored. Panic set in as I realized that the platform had vanished overnight, along with my hard-earned funds. The website was no longer accessible, and my emails went unanswered. Feeling desperate and defeated, I turned to DUNAMIS CYBER SOLUTION, a cybersecurity firm specializing in crypto fraud. Their reputation for helping victims of online scams gave me a glimmer of hope.The team at DUNAMIS CYBER SOLUTION quickly sprang into action. They conducted a thorough investigation, tracing the digital footprints left by the scam operation. Their expertise revealed that the site I had trusted was a known scam linked to previous gambling frauds. They provided me with detailed reports, showing how the funds were funneled through various wallets, making it difficult to track.Despite the grim situation, DUNAMIS CYBER SOLUTION was determined to help me recover my stolen BTC. They worked tirelessly to identify the culprits and gather evidence that could potentially lead to legal action. Their dedication was reassuring during this tumultuous time. While the road to recovery was uncertain, I felt empowered knowing that I was not alone in this fight against crypto fraud. Website; https: // dunamiscybersolution. com2
-
Innovative Bitcoin Recovery Solutions - How CRC is Revolutionizing Scam Recovery
Breakthrough Methods for Bitcoin Recovery
As cryptocurrency scams become more sophisticated, CipherRescue Chain (CRC) has developed cutting-edge techniques to recover stolen Bitcoin that set new industry standards:
1. Smart Contract Exploit Reversal
Deploys counter-exploit protocols
Utilizes time-delay transaction analysis
Implements blockchain-level interventions
2. AI-Powered Forensic Tracking
Machine learning wallet clustering
Predictive movement algorithms
Cross-exchange behavior mapping
3. Legal Pressure Strategies
Real-time asset freezing technology
Multi-jurisdictional seizure orders
Exchange compliance enforcement
Why CRC Leads in Bitcoin Recovery Innovation
1. Certified Cutting-Edge Technology
Patent-pending recovery algorithms
Blockchain Intelligence Group partnership
Regular technology audits by Kaspersky Labs
2. Transparent & Ethical Operations
Flat 12% recovery fee structure
14-day action guarantee
No hidden costs
Full legal compliance documentation
3. Unmatched Success Metrics
94% success rate for recent scams
$420+ million recovered since 2019
3,200+ wallets successfully traced
78% faster recovery times than industry average
The CRC Recovery Process
Phase 1: Digital Triage (48-72 Hours)
Blockchain snapshot analysis
Threat actor profiling
Recovery probability assessment
Phase 2: Active Recovery (7-21 Days)
Smart contract interventions
Exchange coordination
Dark web monitoring
Legal pressure campaigns
Phase 3: Asset Return (3-14 Days)
Multi-signature escrow returns
Anonymity protection
Tax documentation
Security consultation
About CipherRescue Chain (CRC)
CRC represents the next generation of cryptocurrency recovery with:
Technological Advantages:
Quantum-resistant tracing systems
Behavioral analysis engines
Real-time alert networks
Expert Team Includes:
NSA cryptography specialists
Former blockchain protocol developers
International cybercrime prosecutors
Financial intelligence analysts
For advanced Bitcoin recovery solutions:
📧 Contact: cipherrescuechain @ cipherrescue .co .site
CRC maintains revolutionary standards for:
Zero-knowledge client verification
Non-invasive recovery methods
Continuous technology updates
Global regulatory cooperation
Having developed 17 proprietary recovery techniques in the past three years alone, CRC continues to redefine what's possible in cryptocurrency recovery. Their combination of technological innovation and legal expertise provides scam victims with recovery options that simply didn't exist until recently.
Note: While CRC's methods are groundbreaking, they maintain complete transparency about each case's realistic recovery potential during free initial consultations.2 -
TRUSTED EXPERT FOR BITCOIN, ETHEREUM & NFT RECOVERY - HIRE ADWARE RECOVERY SPECIALIST
As a devoted mother in the United States, my life has always revolved around caring for my family—not only my own children, but also several orphans I’ve welcomed into our home. Every dollar matters to us, and financial stability is something we work hard to maintain.
But everything changed when I became the victim of a devastating scam that cost me $500,123. A fraudster posing as a blockchain recruiter reached out with promises of a high-paying opportunity in the cryptocurrency field. They convinced me to send USDC as a “verification deposit,” claiming it was necessary to secure the role. Driven by the hope of creating a better future for my family, I placed my trust in them. WhatsApp info: +12 (72332)—8343
By the time I realized it was a scam, it was too late. My world collapsed around me—until I found ADWARE RECOVERY SPECIALIST.
Their team responded with urgency and empathy. Using advanced tools and deep expertise in blockchain forensics, they traced my stolen funds across multiple chains. Within hours, they had identified the scammer’s Binance deposit address and began working directly with the exchange to freeze the assets. While $150,000 had already been liquidated, they successfully recovered 100% of the remaining $350,123. Website info: h t t p s:// adware recovery specialist. com
This wasn’t just a financial recovery—it was a lifeline. Their help allowed me to reclaim my family’s future and, just as importantly, restored my faith in justice.
What sets ADWARE RECOVERY SPECIALIST apart isn’t just their technical ability—it’s their compassion. They took time to explain how crypto scams work and helped me understand how to spot red flags, emphasizing that legitimate opportunities never require upfront payments. That education alone was priceless. Email info: Adware recovery specialist @ auctioneer. net
To anyone else who has been victimized by cryptocurrency fraud: don’t lose hope. ADWARE RECOVERY SPECIALIST has the skill, dedication, and heart to turn despair into redemption. Their work didn’t just restore my savings—it reignited my drive to protect others and raise awareness in my community.
I am forever grateful for their professionalism, commitment, and integrity.1 -
It was a cold February evening in 2025 when I realized I’d made a terrible mistake. I’d sunk 4 Bitcoin my entire crypto savings into what I thought was a promising investment opportunity I’d found through a flashy ad on X. The platform promised sky-high returns, and the testimonials seemed legit. But weeks passed, my dashboard showed no profits, and when I tried to withdraw, the site locked me out. My 4 BTC, worth a small fortune, was gone. I felt sick. Desperate, I turned to internet forums, posting about my ordeal in a crypto thread. That’s when i saw someone talked about Alpha Spy Nest Recovery, a name I’d never heard before. Skeptical but out of options, I messaged them. Within hours, a rep named Alex responded, asking for details: the site URL, transaction IDs, and screenshots I’d thankfully kept. He warned me it’d be tough, scammers were getting slicker but they’d try. Alpha Spy Nest wasn’t your typical recovery outfit. Alex explained they were a team of ex-hackers and blockchain sleuths who’d turned their skills to hunting down crypto crooks. They used forensic tools to trace my BTC through the blockchain, even as the scammers tried to launder it through mixers. Meanwhile, their web team dug into the fake site, finding it linked to a known scam ring operating out of Eastern Europe. Days later “Good news. We’ve got a lead.” Using a mix of legal pressure and some clever tech I didn’t fully understand, they’d tracked my coins to an exchange where the scammers had slipped up. Alpha Spy Nest coordinated with the exchange to freeze the funds, and after a nerve-wracking verification process, 3.8 BTC minus their fee hit . I stared at my screen, stunned. The relief was overwhelming. Alpha Spy Nest Recovery didn’t just save my money; they restored my faith in fighting back. I never thought I’d see that 4 Bitcoin again, but thanks to their grit and know-how, I did. Rest assured you can also try them out:whatsApp: +14159714490
 1
1 -
As a devoted mother from the United States, I have always prioritized my family's well-being, which includes caring for my own children and several orphans. In our household, every penny counts, and financial stability is paramount. However, my world was turned upside down when I fell victim to a scam that cost me $500,123. The scammer, masquerading as a blockchain recruiter, lured me in with enticing promises of a "high-paying crypto position." They exerted undue pressure on me to send USDC as a "verification deposit," and in my desperation to secure a better future for my family, I placed my trust in them. Unfortunately, I discovered the heartbreaking truth far too late.GRAYWARE TECH SERVICE emerged as my beacon of hope. Their expert team acted with remarkable urgency, employing their extensive knowledge and sophisticated resources to trace my stolen funds across multiple blockchains. Within hours, they identified the scammer's Binance deposit address and began collaborating closely with the exchange to freeze the assets. Although $150,000 had already been liquidated, their relentless efforts culminated in the successful recovery of 100% of the remaining $350,123 . This financial miracle not only salvaged my family's future but also restored my faith in the possibility of justice.What truly distinguishes GRAYWARE TECH SERVICE is not just their technical prowess but also their unwavering compassion. They took the time to educate me about the crypto landscape, emphasizing that legitimate opportunities never require upfront payments. This invaluable knowledge has empowered me to make informed decisions moving forward. Their professionalism and dedication not only helped me recover my savings but also reignited my passion for helping those who depend on me.To anyone who has pass the anguish of being victimized by scams, I implore you not to lose hope. GRAYWARE TECH SERVICE possesses the expertise and determination to transform despair into second chances. They have not only restored my financial stability but have also inspired me to advocate for financial safety and awareness in my community. I am eternally grateful for their support and commitment to helping individuals like me reclaim their Cryptocurrencies.You can reach them on whatsapp+185827595082
-
EasyCare Medical Billing Services: Trusted Healthcare Billing Solutions and Insurance Verification Services
At EasyCare Medical Billing Services, we recognize the importance of streamlined, efficient billing practices in the healthcare industry. With the complexity of healthcare billing and insurance processes, medical providers need a reliable partner who understands the intricacies of billing and insurance verification. That’s where we come in. Located at 105 Daniel Ct, Kendall Park, NJ 08824, EasyCare Medical Billing Services offers comprehensive Healthcare Billing Solutions and Insurance Verification Services to ensure smooth, timely, and accurate billing operations.
Why EasyCare Medical Billing Services?
In today’s fast-paced healthcare environment, medical practices face constant pressure to maintain proper financial flow while providing top-notch care. EasyCare Medical Billing Services is here to ease the burden of healthcare billing, ensuring you can focus on your patients while we manage your billing needs. Our professional team is committed to providing customized solutions that meet the unique requirements of your practice, whether you're a small clinic or a large healthcare facility.
Healthcare Billing Solutions: Simplifying the Billing Process
Managing billing for healthcare services can be a complex and time-consuming task. Errors in billing, missed charges, or delayed claims can lead to lost revenue and create unnecessary challenges for your practice. At EasyCare, we offer expert Healthcare Billing Solutions to ensure your practice runs smoothly and efficiently.
Our services include:
Accurate Medical Coding and Billing: Our experienced team ensures that all services are properly coded and billed according to the latest standards and regulations, minimizing the chances of claim rejections.
Timely Claim Submission: We handle the entire claim submission process, ensuring that all claims are submitted on time to reduce delays in payments.
Efficient Follow-Up: We monitor and follow up on claims that are pending or denied, making sure that your practice receives timely reimbursement.
Patient Billing and Payment Management: We help your practice manage patient statements and collections, ensuring that outstanding balances are addressed quickly and professionally.
Detailed Reporting: EasyCare provides comprehensive reports that allow you to track financial performance, outstanding claims, and overall billing trends for your practice.
With our Healthcare Billing Solutions, you can focus on delivering quality care, knowing that your billing processes are in expert hands.
Insurance Verification Services: Ensuring Accurate Coverage
Before any medical treatment or procedure is provided, it's essential to verify that the patient’s insurance coverage is active and that the services rendered are covered. This process can often be time-consuming and prone to errors, leading to claim denials or delays. EasyCare Medical Billing Services offers comprehensive Insurance Verification Services to reduce these risks and ensure that your practice remains financially secure.
Our Insurance Verification Services include:
Pre-Visit Insurance Verification: We verify patient insurance details before their appointment, ensuring that coverage is active and determining which services are covered under their policy. This prevents billing surprises and reduces the risk of denied claims.
Eligibility Verification: We confirm that the patient is eligible for the services you intend to provide, ensuring that claims are processed without delay.
Insurance Plan Analysis: We analyze the patient’s insurance policy to determine co-pays, deductibles, and out-of-pocket costs, so you can provide accurate billing to patients.
Real-Time Updates: We utilize the latest technology to verify insurance details quickly, allowing for real-time updates on patient eligibility and coverage status.
By using our Insurance Verification Services, healthcare providers can be confident that they are offering services that are covered by insurance and that claims are submitted accurately and on time.
The EasyCare Advantage
With EasyCare Medical Billing Services, you benefit from a team of billing professionals who are dedicated to ensuring the financial success of your practice. We bring deep expertise in Healthcare Billing Solutions and Insurance Verification Services, allowing you to eliminate administrative challenges and maximize reimbursement.
Contact EasyCare Medical Billing Services Today
At EasyCare Medical Billing Services, we are committed to providing top-tier Healthcare Billing Solutions and Insurance Verification Services that help medical practices thrive. Our expert team works tirelessly to optimize your revenue cycle, improve your billing accuracy, and ensure that you are reimbursed on time. 4
4 -
It all started with a promise that couldn’t be ignored. Last year, I stumbled upon an online investment platform called “CryptoFortuneX” that advertised super high returns on Bitcoin and USDT investments. Their beautiful website, great customer reviews, and "24/7 expert support" sealed my decision. In two months, I had $565,000 worth of USDT invested, reassured by fake portfolio updates showing steady growth. But when I tried to withdraw my funds, excuses came: server errors, verification delays, and finally, radio silence, panic set in. I'd been scammed. Desperate, I scoured forums for solutions and discovered Dexdert Net Pro, a cybersecurity firm specializing in crypto fraud recovery. I reached out. Their team responded within hours, asking for transaction records, wallet addresses, and every scrap of communication with CryptoFortuneX, They traced my USDT through blockchain ledgers, uncovering a labyrinth of wallets designed to obscure the trail, Weeks of tension followed, The recovery wasn’t instant—it took Week of legal wrangling and compliance checks. But in the end, I regained my $565,000 USDT successfully Dexdert’s transparency amazed me, Today, I’m rebuilding, wiser and grateful for Dexdert’s tenacity. They didn’t just reclaim my money—They even provided post-recovery guidance to secure my assets, safeguarding countless others. If you’ve been scammed, don’t lose hope. But act swiftly: in the crypto world, time is the thief’s greatest ally.
Thanks to Dexdert’s For Helping Me, Contact them Via :Telegram:(@Dexdertprorecovery)1 -
HIRE AN AUTHORIZED HACKER TO RECOVER LOST/STOLEN BITCOIN & USDT; VISIT CYBER CONSTABLE INTELLIGENCE
I've always been a lawyer with a keen eye for opportunities to help people get their lives back together and also invest in myself, and I couldn’t ignore the buzz around Bitcoin. In 2018, I took the plunge, investing $12,000 in this promising digital currency. Over the years, my investment flourished, growing to an astonishing $750,000. This newfound wealth brought a sense of financial security, enabling me to clear my mortgage, secure my children's education, and indulge in a few well-deserved luxuries. However, my euphoria was short-lived. An urgent email, seemingly from my trusted trading platform, rattled my world. It claimed suspicious activity on my account and requested immediate verification. Without hesitation, I complied, only to discover moments later that my Bitcoin wallet had been ruthlessly emptied. In a state of disbelief and desperation, I scoured online forums for a glimmer of hope. There, amidst the chaos, I found a beacon of light—a recommendation for CYBER CONSTABLE INTELLIGENCE on WhatsApp: +1 (252) 378-7611 With trembling hands, I reached out to them, praying for a miracle. Their response was swift and reassuring. With expert precision, they embarked on the arduous task of tracing the nefarious activity that had stripped me of my wealth. Days felt like eternity, but their relentless efforts bore fruit. Most of my funds were miraculously recovered, breathing life back into my shattered dreams. Yet, CYBER CONSTABLE INTELLIGENCE assistance extended beyond mere retrieval. They became my guardians of digital security, imparting invaluable wisdom to fortify my defenses against future threats. Two-factor authentication, robust password management, and vigilant scrutiny of phishing attempts became my digital armor, thanks to their guidance. This ordeal, though harrowing, became a transformative journey of resilience and redemption. Through adversity, I emerged not only with restored funds but also with a newfound sense of empowerment. CYBER CONSTABLE INTELLIGENCE had not only salvaged my financial future but had equipped me with the tools to safeguard it. In hindsight, the loss was a painful yet necessary lesson—an awakening to the dangers lurking in the digital realm. But with the unwavering support of CYBER CONSTABLE INTELLIGENCE, I reclaimed control of my destiny. Their expertise, compassion, and unwavering dedication turned despair into triumph, proving that even in the darkest of times, there is always a glimmer of hope.
Reach Out to them on Via E m a i l: support (@) cyber constable intelligence. com -
My initial engagement with DUNE NECTAR WEB EXPERT demonstrated considerable professionalism and transparency. This favorable first impression prompted a more thorough investigation into the company's background and operational practices. Subsequent research revealed a significant history of successful engagements across various services. Their client portfolio reflects a commendable track record in several complex domains, including phone surveillance, private investigations, and cryptocurrency recovery. Specifically, their proficiency in phone spying involves ethical and legal data acquisition, adhering to all relevant regulations while securing necessary authorizations. In private investigations, their work exemplifies a dedication to meticulous fact-finding and discreet operations, ensuring the respect of client confidentiality and legal parameters.
Furthermore, their achievements in cryptocurrency recovery underscore their expertise in blockchain technology, digital forensics, and navigating the complexities of cryptocurrency exchanges and regulatory frameworks. These achievements are not merely anecdotal; they are substantiated by numerous client testimonials and case studies accessible on their website and through independent verification. The consistently positive feedback, combined with demonstrable expertise across various specialized fields, reinforced my assessment that DUNE NECTAR WEB EXPERT is the most reputable and effective solution for recovering my lost cryptocurrency. Their commitment to transparency, their proven track record, and adherence to ethical standards distinguish them from other firms operating within this intricate sector. The depth of their expertise and the breadth of their successful engagements instilled in me the confidence to entrust them with this critical matter.
WEB- dunenectarwebexpert . com
EMAlL - support @dunenectarwebexpert . com. 6
6 -
Finding a trustworthy partner in recovery becomes paramount. In the realm of digital deception, Cybertech Wizard emerges as a beacon of hope for those ensnared in the snares of cyber criminals. Having endured the anguish of falling victim to a binary operations scam, I found solace in the expert hands of Cybertech Wizard. After losing a substantial sum of $12,000 in cash and 6 BTC to counterfeit binary options and bitcoin investors, despair threatened to engulf me. However, a glimmer of redemption shone through when my in-law recommended Cybertech Wizard. True to its reputation, Cybertech Wizard swiftly sprang into action, orchestrating a remarkable turnaround in less than 72 hours. With precision and professionalism, they navigated the intricate labyrinth of digital deception, reclaiming what was rightfully mine – both my lost funds and bitcoins. Their dedication to restoring financial equilibrium amidst the chaos of online scams is nothing short of commendable. What sets Cybertech Wizard apart is not merely their ability to recover lost assets but their unwavering commitment to client satisfaction. From the moment of initial contact, their team exudes empathy, understanding, and a relentless drive to right the wrongs inflicted by cyber criminals. Their transparent communication and willingness to guide clients through every step of the recovery process instill confidence and peace of mind. Moreover, Cybertect Wizard's expertise transcends the confines of traditional recovery services. Whether grappling with wallet hackers, fake hackers, BTC wallet hacks, or counterfeit binary investors, they possess the acumen and resources to confront any challenge head-on. Their multidisciplinary approach, coupled with a deep understanding of evolving cyber threats, empowers clients to confront adversity with resilience and resolve. However, amidst the accolades, it's imperative to approach Cybertech Wizard with discernment and due diligence. While my personal experience attests to their efficacy and integrity, prospective clients should conduct thorough research and verification before engaging in their services. Independent reviews, testimonials, and a comprehensive assessment of Cybertech Wizard credentials can provide invaluable insights into their legitimacy and reliability. In a digital landscape fraught with peril, Cybertech Wizard stands as a bastion of trust and redemption. To those who have suffered the sting of online scams, I extend to reach out to Cybertech Wizard and embark on a journey towards restitution and renewal. In the face of adversity, remember, there's always a solution, and Cybertech Wizard embodies that unwavering truth.
contact via details below;
Email; cybertechwizard@ cyberservices. com
WhatsApp: +1 (859) 743-5022 2
2 -
GET YOUR MONEY BACK AFTER A CRYPTO SCAM// TRUSTED RECOVERY SERVICES TRUST GEEKS HACK EXPERT
( WEB SITE. HT TP S: // TRUST GEEKS HACKE XPERT . COM )
(
E MA I L.TRUST GEEKS HACK EXPERT @ FAST SERVICE . COM)
I advise first-time Bitcoin investors to do their research before entrusting any of the Bitcoin investment websites with their hard-earned funds. I learned this the hard way. These platforms can appear very legitimate, often showcasing fake huge profits to convince users to invest more money. They built my trust by promising high returns and painting a picture of success that seemed too good to pass up. Initially, my investments seemed to yield impressive returns, and I felt encouraged to invest a larger sum. However, the situation quickly turned sour when I deposited a significant amount. After I made the larger investment, my account was intentionally frozen, and the platform demanded additional payments for "verification fees" and other bogus charges before I could access my funds or withdraw any of my supposed profits. They used manipulation tactics to keep me trapped in the scam. I was left frustrated and helpless as I realized I had been duped, losing a substantial sum of 54,000 CAD.It was a very unsettling experience, as I couldn’t figure out where to turn for help. I had no idea how to recover my lost funds or even how to identify the scam. That’s when I came across TRUST GEEKS HACK EXPERT. They specialize in helping victims of online scams recover their lost funds, and they proved to be a lifeline. TRUST GEEKS HACK EXPERT swift action and assisted me through the entire process with professionalism and dedication. They were relentless in their efforts and provided me with regular updates, ensuring that I was always informed about the status of my case. In the end, I was able to successfully recover the money that I thought I had lost forever. If you ever find yourself in a similar scenario where your Bitcoin investments have gone awry, or your account has been frozen by a fraudulent platform, I highly recommend reaching out to TRUST GEEKS HACK EXPERT. Their support can make all the difference in recovering your funds and protecting yourself from further scams. Always be cautious, do thorough research before making any investments, and never hesitate to seek help if something doesn’t feel right...
( WHAT'S APP +1.7.1.9.4.9.2.2.6.9.3 )
(TELEGRAM. TRUST GEEKS HACK EXPERT)1 -
Key Reporting Tools In TallyPrime
TallyPrime's reporting capabilities offer businesses access to over 300 detailed reports, empowering them to monitor operations and make informed decisions. These reports cover diverse aspects of business management, including financial statements, inventory analysis, GST compliance, and more.
Key Reports in TallyPrime:
Financial Statements: Balance sheet, profit and loss, and cash flow reports for evaluating business performance.
Stock Summary Reports: Insights into inventory levels, movement, and reorder points.
Voucher Reports: Detailed records of sales, purchases, and payments for reconciliation and accuracy.
GST Reports: Compliance-focused reports like E-invoices, GST returns, and E-way bills.
MIS Reports: Performance insights via Ageing, Ratio Analysis, and Expense reports.
Budgets & Forecasting Reports: Comparison of actual performance against budgets.
Audit & Exception Reports: Verification of records and identification of anomalies.
Customer & Vendor Reports: Analysis of payment history and outstanding balances.
Operational Reports: Covering stock turnover, job costing, payroll, and expenses.
Benefits of TallyPrime Reporting Tools:
Time Efficiency: Instant access to detailed reports for streamlined operations.
Enhanced Accuracy: Precise reports for confident decision-making.
Actionable Insights: Deep analysis of cash flow, profitability, and strategies.
Improved Decision-Making: Reliable data for effective business strategies.
24/7 Accessibility: Anytime, anywhere access to reports via a browser.
Custom Report Views: Save and retrieve personalized report formats.
Sheet Magic Integration:
Antraweb Technologies’ Sheet Magic complements TallyPrime by integrating with Excel, enabling the creation of customized reports without programming skills. This tool saves time, reduces errors, and simplifies data analysis.
Conclusion:
TallyPrime’s extensive reporting tools provide businesses with critical insights for managing finances, inventory, and compliance effectively. When paired with Sheet Magic, it delivers a seamless solution for data-driven decision-making, enhancing operational efficiency and business growth.2 -
STEPS TO RECOVER BITCOIN AND USDT FROM ONLINE INVESTMENT SCAM
Betafort Recovery follows a systematic approach to ensure the best chance of recovering stolen funds. Here are the steps they took to help me:
1. Initial Contact and Case Assessment
I contacted Betafort Recovery via email and WhatsApp, explaining the situation in detail. They responded quickly, requesting specific information to assess the theft. This included:
- Details of the stolen transaction
- The wallet addresses involved
- Any communication or evidence related to the scam
2. Verification and Agreement
Once they reviewed my case, Betafort Recovery confirmed that they could assist in the recovery. They provided a service agreement outlining the recovery process, confidentiality terms, and their fee structure based on the amount recovered. I reviewed and signed the agreement, reassured by their transparent and professional approach.
3. In-Depth Investigation
The firm began by conducting a thorough investigation to trace the stolen funds. This involved:
- Analyzing the blockchain to track the movement of the stolen assets
- Identifying the destination wallet and any subsequent transactions
- Utilizing advanced forensic tools to uncover patterns and connections
4. Recovery Strategies
Once they gathered sufficient information, Betafort Recovery implemented various strategies to recover the stolen money:
- Negotiation: They sometimes engaged directly with the perpetrators, using their expertise to negotiate the return of the funds.
- Technical Exploits: The team exploited vulnerabilities in the scammers’ systems to regain access to the stolen assets.
- Collaborative Efforts: When necessary, they collaborated with other cybersecurity experts and legal authorities to enhance the recovery process.
5. Successful Recovery
After several days of diligent work, Betafort Recovery successfully recovered my stolen funds. They transferred the recovered money back to a secure wallet that I controlled. Their professionalism and expertise were evident throughout the process, and I was immensely grateful for their assistance.
Conclusion
Having your funds stolen from Trust Wallet can be a harrowing experience, but there is hope with services like Betafort Recovery. Their systematic and professional approach makes them a reliable partner in recovering stolen cryptocurrencies. If you ever find yourself in a similar situation, don’t hesitate to reach out to them:
Email: info@betafort.online
WhatsApp: +17126004729
Thanks to Betafort Recovery, I was able to restore my financial stability and continue my journey in the world of cryptocurrency with renewed confidence. Their dedication and expertise turned a potential financial disaster into a successful recovery, for which I am eternally grateful.2 -
QUICK AND RELIABLE SOLUTIONS TO RECOVER LOST ASSET WITH SALVAGE ASSET RECOVERY
Am Amelia, I lost my entire Bitcoin savings to scammers who posed as Coinbase support representatives on Facebook. It started when I came across what I believed was an official Coinbase support page. They appeared legitimate, with professional logos, official-sounding language, and even real-time responses. I was experiencing some issues with my wallet at the time, so I reached out to them for help. They responded quickly and walked me through what they called a “verification process” to secure my account. Trusting them, I followed their instructions step-by-step. Unfortunately, I unknowingly granted them remote access to my Coinbase wallet. Within moments, my heart sank as I watched 6.5 BTC, everything I had saved over the years, disappear from my account. I was in utter disbelief. I couldn’t sleep, eat, or think clearly. The loss was crippling, both financially and emotionally. After recovering from the initial shock, I began searching for solutions online. That’s when I stumbled upon a service called SALVAGE ASSET RECOVERY. At first, I was skeptical, how could anyone possibly retrieve stolen cryptocurrency? But with nothing left to lose, I decided to reach out and explain my situation in full detail. To my surprise, they responded quickly and were extremely understanding. Their team of recovery specialists launched an investigation almost immediately. Using advanced tracking tools and years of expertise, they were able to trace the movement of the stolen Bitcoin through the blockchain. Not only did they locate the stolen funds, but they also identified the wallets associated with the scammers. In just two days, SALVAGE ASSET RECOVERY successfully recovered my 6.5 BTC and provided me with information about the individuals responsible. I was stunned. After thinking all hope was lost, they gave me a second chance. Their professionalism, speed, and technical skill were beyond anything I expected. If you've fallen victim to an online scam, whether it's crypto-related or otherwise, I strongly encourage you to contact SALVAGE ASSET RECOVERY. They turned one of the worst experiences of my life into a powerful reminder that not all is lost. Scammers are getting smarter, but thankfully, so are the experts who fight against them. Stay cautious, verify every source, and remember recovery is possible. Reach out to SALVAGE ASSET RECOVERY contact info
TELEGRAM---@Salvageasset
WHATSAPP...+ 1 8 4 7 6 5 4 7 0 9 62 -
IF YOU HAVE LOST YOUR BITCOIN AND YOU NEED A BITCOIN EXPERT JUST GOOGLE DIGITAL TECH GUARD RECOVERY
It all began with a Facebook ad that popped up during the holiday season one of those enticing promotions for "guaranteed winning football picks" that seemed too polished to overlook. The ad featured eye-catching screenshots of massive payouts and glowing testimonials from ecstatic users, which drew me in like a moth to a flame. Before I knew it, I found myself in a private Telegram group that was buzzing with what appeared to be undeniable proof of their success: screen recordings showcasing big wins, withdrawal slips, and enthusiastic members celebrating their fortunes. The group's admin reached out to me personally, claiming they had a "sure thing" match that was too good to pass up. The urgency in their tone was palpable; they insisted that this was a limited-time opportunity. All I needed to do was send $5,000 in Ethereum to place the bet. Despite my better judgment screaming at me to walk away, the pressure mounted, and I succumbed to the allure of quick riches. I transferred the ETH, convinced that I was on the brink of a life-changing win. However, that’s when the real scam unfolded. Almost immediately, I was hit with a demand for a $2,000 "processing fee." As if that wasn’t enough, they continued to ask for more payments under the guise of "verification fees." My heart raced as I hesitated, realizing that something was terribly wrong. When I expressed my doubts, their demeanor shifted dramatically; they became aggressive, threatening to lock me out of my "winnings" if I didn’t comply. My stomach sank as the reality of the situation hit me I had been conned. But the story doesn’t end there. In a twist of fate, I managed to recover everything I lost. A friend connected me with Digital Tech Guard Recovery, a firm that specializes in recovering funds lost to crypto scams. Their team worked tirelessly, employing their expertise to trace the Ethereum through the blockchain, collaborating with exchanges, and navigating legal channels. To my astonishment, within just a few days, my entire $7,000 was back in my wallet. This taught me a valuable lesson about the dangers of online scams and the importance of due diligence. While I fell victim to a sophisticated scheme, I was fortunate enough to find help and reclaim my losses.
WhatsApp: +1 (443) 859 - 28862 -
As an educator and a Christian, it would be utterly unfair and unjustifiable not to share this positive review about TECH CYBER FORCE RECOVERY, the agency that helped recover all of the investment money I thought I had completely lost in a failed crypto investment scheme. For some unknown reason, I suddenly couldn't send or withdraw from my crypto wallet even with my balance still reflecting. I contacted the service center and completed all verifications and processes requested, and nothing changed. I got really tense, and it was amidst these worries and search for a feasible solution, I first heard about TECH CYBER FORCE RECOVERY through an old associate.
I immediately sent out a mail to them and all they did when they responded was get some details right; after a few, hassle-free verification, they got to work. Progress updates followed, and just after the second day, I received a notification message from TECH CYBER FORCE RECOVERY with instructions to restart my wallet app and then try to make any usual transaction I've been having problems with, which I reluctantly did because I've done that same process countless times before; but amazingly it worked!...and wallet functioning right since then. TECH CYBER FORCE RECOVERY is proven, and I hope this review helps as many out there who need the right agency for all crypto-related solutions. They can be reached through:
WEBSITE// W.W.W.techcyberforcerecovery.info
TELEGRAM// @TECHCYBERFORC
WHATSAPP// .+.1.5.6.1.7.2.6.3.6.9.72 -
The crypto market is flooded with web recovery solutions, each claiming to be the best thing since sliced bread. But how do you separate the wizards from the mere mortals? A comparative analysis of various web recovery solutions can help you make an informed decision. It's like conducting a thorough background check on potential roommates—except this time, it's your digital wealth that's at stake. Infinix Web Recovery is aware of how critical it is to stay one step ahead in the dynamic world of cryptocurrencies. Their platform has alarm and monitoring mechanisms that operate in real-time because of this. This enables you to respond quickly to safeguard your assets by identifying any unusual activity or possible threats. You won't have to worry about waking up to discover that your cryptocurrency holdings have vanished for no apparent reason. Credentials are no longer the only means of authentication. Infinix Web Recovery effective user authentication procedures raise the bar for security. You can be guaranteed that only authorized users have access to your cryptocurrency holdings thanks to features like multi-factor authentication and biometric verification. You can stop worrying about having weak passwords and becoming a target of phishing efforts. Infinix Web Recovery knows that your crypto assets are valuable and deserve the highest level of protection. That's why they employ advanced data encryption and secure storage methods. Your sensitive information is transformed into a secret code that's virtually impossible to crack. Rest easy knowing that even if someone gains access to your data, it will be completely useless to them. It's like keeping your crypto stash in a safe within a safe. Crypto asset management is an ongoing process, and so is utilizing Infinix Web Recovery . It's important to regularly update and review your recovery settings to keep up with the ever-changing crypto landscape. Stay proactive and ensure your recovery protocols are up to par, so you can always be one step ahead of potential threats. In the world of cryptocurrencies, where threats and risks lurk in the shadows, it's crucial to have a powerful ally like Infinix Web Recovery . With their real-time monitoring, efficient authentication processes, and secure storage, you can rest easy knowing your assets are protected. The success stories of Jane and John showcase the remarkable capabilities of Infinix Web Recovery in recovering lost funds and preventing hacks. Contact Infinix Web Recovery2








