Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "length"
-
Some sort by Date, some by length, others by upvotes. But devrant's algorithm is so great it sorts by sarcasm.
 4
4 -
Dear fellow developer,
You are not alone. No matter what situation you have been, you are in, you might be, there definitely are people who can share your pain and joy on similar wave length. Here at devrant.
Introvert?
Poor?
Alone?
Odd one out?
Trouble studying?
Family issues?
Debts?
Hate workplace?
Bad teacher?
Depression?
Laziness?
Forever alone?
Struggling?
Full of regrets?
Lost something?
Lost someone?
Lost?
You name it. All of us may not understand, sure. But there definitely will always be more than one person who will totally know what you are trying to say. Here at devrant only.
So whatever you are in, wherever you are and however you feel, just rant it out. 😄 And remember that we are one tap away from you.
For that devrant creators and most of all each and everyone of you have my eternal thank.72 -
Started being a Teaching Assistant for Intro to Programming at the uni I study at a while ago and, although it's not entirely my piece of cake, here are some "highlights":
* students were asked to use functions, so someone was ingenious (laughed my ass off for this one):
def all_lines(input):
all_lines =input
return all_lines
* "you need to use functions" part 2
*moves the whole code from main to a function*
* for Math-related coding assignments, someone was always reading the input as a string and parsing it, instead of reading it as numbers, and was incredibly surprised that he can do the latter "I always thought you can't read numbers! Technology has gone so far!"
* for an assignment requiring a class with 3 private variables, someone actually declared each variable needed as a vector and was handling all these 3 vectors as 3D matrices
* because the lecturer specified that the length of the program does not matter, as long as it does its job and is well-written, someone wrote a 100-lines program on one single line
* someone was spamming me with emails to tell me that the grade I gave them was unfair (on the reason that it was directly crashing when run), because it was running on their machine (they included pictures), but was not running on mine, because "my Python version was expired". They sent at least 20 emails in less than 2h
* "But if it works, why do I still have to make it look better and more understandable?"
* "can't we assume the input is always going to be correct? Who'd want to type in garbage?"
* *writes 10 if-statements that could be basically replaced by one for-loop*
"okay, here, you can use a for-loop"
*writes the for loop, includes all the if-statements from before, one for each of the 10 values the for-loop variable gets*
* this picture
N.B.: depending on how many others I remember, I may include them in the comments afterwards 19
19 -
Today was different at work. It felt as if something was missing. The circle of fun at work that was developed over last two months among few of us was gone overnight..
Two months ago, we ( 7, including our PM ) were shifted from our cabin space to this special room by boss in hopes to keep our ass under fire and increase our productivity. Everyone in the office saw this room like a concentration camp as it was next to boss 's office. Nobody liked the idea of working in that room. We were seen as prisoners as we walked into our work cage.
In the cage, there is a fixed table. We had to adjust our workspace around that table. Everyone was just an arm length away from each other. It didn't take that long to form a bond among us. Some of us would bring snacks and we all shared it and ate it there. We had fights and discussions. The girl in my team and other team would have silly fights about their legspace boundary. The guy who is on a quest to find his life partner would seek for our opinions about his matrimony findings. That time the girls roasted guy about his patriarchal attitude. Instant discussions on current events. Movie reviews and sharing about various life experiences. Lots of such memories were formed and shared over last two months while we worked in there.
For me, it felt like living "The Office" in real life. It was amazing. I was starting to forget my dreams of self employment and plans to resign career because this human connection was addictive. We all learned a little more about each other which otherwise would not have been happened outside the cage.
We didn't realize the bubble and dynamics we had formed in that room until it was gone today when we were shifted back to our cabin space.
It was obvious we were little sad inside having to say bye to our bubble.
😅4 -
!dev
const children = {
length: 1,
data: [{
name: "noah",
gender: "male"}]
};
children.length++;
children.data.push({
name: "mina",
gender: "female"
});
const happy = true;21 -
So, a couple of weeks ago I started a temporary job writing code mostly for DB purposes. I noticed during that time there was a specific person just copying my code and not giving credit in the meetings. So I decided to put a small, quirky, joke in my last code just to see if the person reviewed it before presenting.
FF to yesterday, the person did not check the code and he presented a table with a field called PENIS Contract Length in our zoom meeting.
Not sorry at all9 -
My life would be so much easier if I could just consistently spell lenght, I mean, lentgh, I mean length DAMN IT!8
-
User Ip Address is too long (maximum is 30 characters).
Okay, dear third-party API, I guess users with IPv6 don't deserve the service... And wtf is 30-char limit for an IP address, when IPv4 can be only 15 characters long, and IPv6 can be up to 39 characters? Did you calculate a weighted average of IP length to get that number?11 -
There are two things about arrays that sometimes confuse me:
[0]: They start at zero
[1]: They end at one less than the length14 -
Business idea: panties with HTTP status codes printed on them.
451 for our underaged customers - unavailable for legal reasons
411 to crush a man's self esteem - Length required
429 for girls with stalkers - too many requests
402 for our professional customers - payment required
And, of course, 202 - Accepted22 -
Why are Americans so stupid?
Date format: MM/dd/YY => what is this? It‘s not even in order
Length Units: Inch, Feet, Yard, Mile => good luck trying to convert in in a hurry without a calculator
Cooking recipes: cups, tablespoons, pinches => land of the freedom, especially for measurement errors
Temperature: Fahrenheit. => some dude who thought, „oh this is really hot, lets mark it 100“ and the other day „oh this is really cold, I got the 0 mark, sciene“
Weight: ounces ~ 28.34952 g, ton ~ maybe 907.xx kg, it depends
Time: Americans think the week starts on sunday, so they assume it does so for everyone else (f*** you american developer, designer, I mean you)
Football is football. Everywhere. In. The. World.
Politics: Trump, Weapons, health system, worker rights, ...
God, I hate America and their bs.25 -
A few weeks ago at infosec lab in college
Me: so I wrote the RSA code but it's in python I hope that's ok (prof usually gets butthurt if he feels students know something more than him)
Prof: yeah, that's fine. Is it working?
Me: yeah, *shows him the code and then runs it* here
Prof: why is it generating such big ciphertext?
Me: because I'm using big prime numbers...?
Prof: why are you using big prime numbers? I asked you to use 11, 13 or 17
Me: but that's when we're solving and calculating this manually, over here we can supply proper prime numbers...
Prof: no this is not good, it shouldn't create such big ciphertext
Me: *what in the shitting hell?* Ok....but the plaintext is also kinda big (plaintext:"this is a msg")
Prof: still, ciphertext shows more characters!
Me: *yeah no fucking shit, this isn't some mono/poly-alphabetic algorithm* ok...but I do not control the length of the ciphertext...? I only supply the prime numbers and this is what it gives me...? Also the code is working fine, i don't think there's any issue with the code but you can check it if there are any logic errors...
Prof: *stares at the screen like it just smacked his mom's ass* fine
Me: *FML*12 -
Apple has programmed an avatar maker in iMessage that generates emoji that are supposed to resemble the person. However it does not have any setting for facial structure to represent a person’s sex. I’m pretty sure they did it because “gender is a construct”.
When I was growing up I had some issues with gender dysphoria. I am male genetically. I was mistaken as female my whole childhood because I was “pretty”, my best friends were girls, and I liked cooking, drawing, and dancing. Puberty happened and I started to look like a man. I considered transitioning because I felt female but I decided to let my body do what it wants and do the things I like to do without worrying about if they are gendered or not. I am married and male and I like what I like.
This stupid iMessage avatar. I have tried my hardest to make it look like me. I have long hair and keep my facial hair clean. They don’t have a switch to change some facial physiological traits so I have this Memoji that looks like a woman with a slight hormonal imbalance. It makes me feel conflicted like I felt when I was young. I haven’t thought about it in years and now I feel like I have an uncomfortable secret female avatar that i carry around on my phone and I feel like I’m carrying a secret.
A persons genetics result in differences in facial structures. Biological sex is more than the length of hair and whether a person wears makeup. I hate this “sex is a construct” trend. I’m fine living my life, but then companies push this software onto my phone like propaganda. I want it to look as masculine as I look IRL.15 -
Im trying to brute force a rar i made Long ago, sadly i have forgotten the Passwort.
This is how it looks, when you to run it on the length 8-16 at the Same time(all posibilitys).
lets see how Long it will take.
I say 7 Days at 100% cpu usage😂😂 8
8 -
I installed a firmware update on my router, and discovered it both adds telemetry and breaks the navigation in firefox. 🤦♀️
It also started complaining that my password isn't secure (despite its length) because it doesn't contain a symbol.
Good freaking job.7 -
Authentication feature was only checking the length of the auth header instead of the actual content. I abused this to make a request to our API from inside our system with a junk header, so we were basically hacking ourselves...2
-
Just spoke with another teams developer. (She's using Java)
Her: so we get a json object from your service, I want an array
Me: well that's not what you said in the specs... And it's not hard since it's just a Map
Her: what Map? It's JSonObject I need an Array
Me: give me the library your using..
Her: here...
I Google the documentation and methods and paste the link and the methods to use:
-length (she also wanted count)
-toJsonArray
This ain't JS, just use the . operator and go thru all the methods' docs... Or learn to use Google8 -
CTO wants all variables in file to be same length. You cant have "start" and "stop". You must have "start" and "cease".16
-
I’m getting really tired of all these junior-turn-senior devs who can’t write simple code asking ChatGPT to solve everything for them.
I’m having to untangle everything from bizarre organization/flow to obvious gotchas / missed edge cases to ridiculously long math chains (that could be 1/10th the length), or — and I feel so dirty for this — resorting to asking ChatGPT wtf it was thinking when it obviously wrote some of these monstrosities. Which it gets wrong much of the time.
“ALL HAIL CHATGPT!” Proclaims the head of Engineering. “IT’S OUR PRODUCTIVITY SAVIOR! LEVERAGING AI WILL LET US OUTPERFORM THE ENTIRE INDUSTRY!”
Jesus fucking christ.30 -
No, listen to me. I cannot approve this PR because your code does not comply with our code style. All the imports and annotations must be sorted in ascending order by length. They must all make fir-like blocks of code. Because it looks nice.
Now go and fix your code
I just smiled and walked away to obfuscate my code with firs . I had no idea what to even say to that... I still don't13 -
Currently working on the privacy site CMS REST API.
For the curious ones, building a custom thingy on top of the Slim framework.
As for the ones wondering about security, I'm thinking out a content filtering (as in, security/database compatibility) right now.
Once data enters the API, it will first go through the filtering system which will check filter based on data type, string length and so on and so on.
If that all checks out, it will be send into the data handling library which basically performs all database interactions.
If everything goes like I want it to go (very highly unlikely), I'll have some of the api actions done by tonight.
But I've got the whole weekend reserved for the privacy site!20 -
Password max length: 12 characters
Additional requirements: exactly 1 special character and exactly 2 numbers.8 -
!rant
My work does this contest where they email everyone a puzzle where you have to guess a safety slogan. They give you maybe 1-2 letters in each word and there are about 5 or 6 words. So I found a list of every word in the English language online, I imported it into a database and I ran a few queries to return all possible words for each, depending on the length of the word, and where the letter hints are placed. I haven't missed one puzzle so far. :D
p.s. I told my girlfriend and she said, "I am dating a nerd".6 -
As a software engineer, I decided to participate in a hardware Hackathon. I went in not knowing much about the subject, but by the end of the weekend, we made a fully functioning (somewhat janky) jacket that could roll up or roll down its own sleeves depending on what your body temperature was (inspired by Back to the Future 2). We also created a remote, so you could control the length of the sleeves as well. It was the most off-the-wall, ballin project I've ever been a part of.10
-
In my CS class I turned in some assignments recently. Two of them were extremely similar: one was to test if a number was even or odd, the other to test if the length of a string was even or odd. I completed the first one and then started to work on the second one and decide to just call the isEven method from the previous lab so I can follow DRY (Dont repeat yourself) and not have to write the same code again. I turned it in and she took off points for it. -.-13
-
1. Participate in an online hackathon
2. Upload demo video to youtube
3. Submit in the last minute
4. Come back 1 hour later to see video removed due to length violation.
FML :( -
Weirdest co-worker... We'll not to be judgy, but I think our industry is sort of home of the weirdos, but.. there's a few over-the-top weirdees we've had at work.
First one that comes to mind was a guy that walked liked Mr. Burns, hands behind the back & chest out. He microwaved the same thing every single day for breakfast - crackers, sausage and cheese. 😖This guy would get to his tasks very slowly, wouldn't talk to anyone on our team, and would go missing from his desk a lot, sometimes for extended periods (2+ hours). He really struggled to catch on to easy tasks. He quit after a few months, thank god.
Another weirdo we had was a girl who just couldn't dress to save her soul. She would wear these ugly ass sneakers that had neon colors reminiscent of bowling shoes (neon orange and green) and would wear turtlenecks and floor length skirts that all the colors just clashed. Her outfits were uglier than your great grandma's. Myself, her and 2 other girls dressed up as the Dr. Seuss things for Halloween, but did h1, h2, etc. tags instead and she put like rope from curtains in her hair with like 10 little pony tails. Just like wtf. She would play her gameboy at lunch and not talk to anyone much. She was really bad at our job, a lot of clients complained. She would literally read a book, braid her bangs or nap at her desk. Needless to say, she was fired.6 -
Believe it or not… This means shit is doing what it is supposed to…
EDIT: Sorry for length web client users .-. 15
15 -
Microsoft pro account.
2018.
16 characters.
2018.
Microsoft.
16.
2018.
Microsoft.
(Screams in French)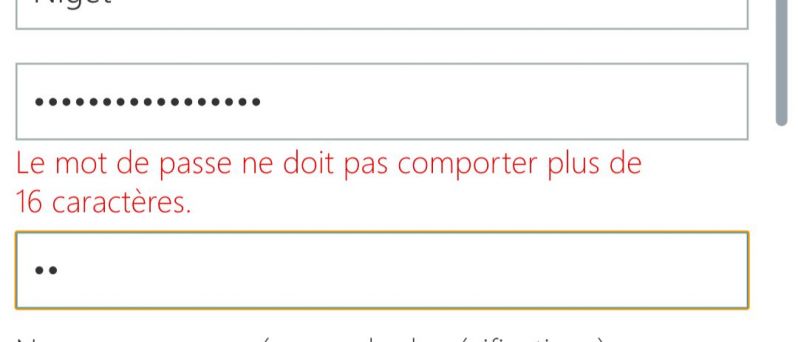 5
5 -
Is it normal, or is the HR stalling?
I spoke with the HR and they offered me a job and they’re drafting the offer letter.
1 month later.
They’re still drafting the offer letter.
Do I have to worry about the length of responsibilities that I need to do?5 -
Here's a silly side project I've been working on just for fun:
https://soundofco.de/
It "programmatically" creates sound from code (or plain text) on GitHub. I wouldn't call it music, because it sounds kind of horrible almost all of the time :D It's very simple: The length of a line defines the note to be played. Really just a nerdy bit of fun.
Unfortunately I have absolutely zero knowledge in music theory and I have no idea how to make the resulting sounds more pleasant or even melodic. If you're interested in making this better or helping out with feedback, you can find the project at https://github.com/dneustadt/...
Also feel free to share if you find anything on GitHub that makes for some decent sounds :D (I doubt it)12 -
An overflow in C, the program was writing 16 Bytes in an array of length 10 due to some mistake.
The problem was this ended up overwriting another place in the memory that was used by another algorithm to perform calculations... So we thought that the algorithm was buggy all along.2 -
So Friday afternoon is always deployment time at my company. No sure why, but it always fucks us.
Anyways, last Friday, we had this lovely deployment that was missing a key piece. On Wednesday I had tested it, sent out an email(with screenshots) saying "yo, whoever wrote this, this feature is all fucked up." Management said they would handle it.
The response email. 1(out of 20) defects I sent in were not a defect but my error. No further response, so I assume the rest were being looked into.
In a call with bossman, my manager states that the feature is fixed, so I go to check it quickly before the deployment(on Friday).
THERE IS NO FUCKING CODE CHECK-IN. THE DEV BASTARD JUST SAID THAT MY USECASE WAS WRONG, SO MY ENTIRE EMAIL WAS INVALID.
I am currently working on Saturday, as the other guy refuses to see the problem! It is blatant, and I got 3 other people to reproduce to prove I am not crazy!
On top of that, the code makes me want to vomit! I write bad code. This is like a 3rd grader who doesn't know code copy-pasted from stack overflow! There is literally if(A) then B else if(!A) then B! And a for loop which does some shit, and the line after it closes has a second for loop that iterates over the same unaltered set! Why?! On top of that, the second for loop loops until "i" is equal to length-1, then does something! Why loop???
The smartest part of him ran down his Mama's leg when it saw the DNA dad was contributing!
Don't know who is the culprit, and if you happen to see this, I am pissed. I am working on Saturday because you can't check your code or you lied on your resume to get this job, as you are not qualified! Fuck you!15 -
So today I decided to change the passwords on some online accounts...
Sony: "Don't use the same symbol twice in a row. Oh, and how about 4 reset emails because the first 3 times it won't work?"
Me: "Okay, this password meets all requirements"
Sony: "I don't believe you lol."
Twitch: "Error: Your password length must be between 8 and 40 symbols!"
Me: "But mine has 24 symbols and the password field shows a green checkbox"
Twitch: "Error: Your password length must be between 8 and 40 symbols!"
Aaaargh! Did they hire toddlers as interns or something?1 -
I really need to learn to think through how many stitches I’m putting into the first row of a project.
- Takes over an hour to do one row
- Already used more than 2k yards on it and it’s not even short blanket length yet (though width is ridiculous) 11
11 -
Do you know when you think "Oh that doesn't look too hard. I bet I can do it in no time"?
That is how I felt when I saw the DIY 3D printer kit Anet A8. It's only 150€ on gearbest so that is pretty cheap.
The reviews said it takes about 3 - 4 hours to build and I though "Ok I am a computer specialist and engineer so 3h sounds reasonable".
When I bought it from gearbest the first problems started: 5 days after the estimated shipping date the packet was still not on its way. After I fucked the support up, it finally arrived 3 weeks after the estimated date.
When I took the first look, everything seemed to be fine except for some small scratches but for that price that is not a problem.
So I started to build the printer at about 14:00 and even if some random sites in the manual were in Chinese I felt confident to get it done in a view hours.
And then it started to get really fucked. The first problem was that 2 screws were unusable and I had to use my own screws instead. The next problem was that the manual was just in the wrong fucking order at some points and I had to reverse multiple steps to get it right.
But the most fucked up thing: There should have been 2 threaded rods with a length of 345mm but the rods had a length of 310mm which was nowhere listed in the parts list. So I had to go buy some aluminium rods to fill the gap temporary so that I can at least go on with the build before getting a replacement. And I could go on and on and with the problems but the point is, it is now 19:30 which is about 5.5 hours after I started and I am still not fucking done with this.
So what have I learned?
Cheap Chinese hardware is good, but only as long as you don't have to assemble that shit yourself.2 -
Client support ticket: we printed the ID cards without leading 0’s can you fix it with software?
Me: unfortunately we cannot because the ID number can be any length. ID 123, 0123 and 00123 can exist. What barcode would 123 go to?
Client: this is ridiculous we will cancel our contract.
Me: i’m sorry we can’t correct for a mistake on your end.
(Side note: I know allowing 0123 and 00123 is dumb but my team didn’t design the business logic)7 -
Yeah boss, lets study Scrum extensively so you can:
- Create variable length sprints
- User stories that are meaningless like 'fixes'
- Tasks that should be User Stories
- Duplicated tasks/stories that are on the fucking backlog already
- Cross sprints on projects
- No meetings at fucking all to determine who will do what
- Assign people on vacation to current sprints
The list goes on...
An when I point things like that out lets just look at the guy who spent 6 months studying this shit, taught you ( at least tried... ) as if he is saying nonsense while our projects get delayed and our code spaghettifies because we are always in a hurry for lack of time to plan anything :)2 -
I’m pretty terrible at soldiering and small electronics in general, but I’m kind of okay with how this turned out.
Back story:
That helmet is my sister-in-law’s, she drives a polaris slingshot. (It’s technically a motorcycle here in the US because it has three wheels.) and she hooked up some EL wire to her helmet and the larger black rectangle in the picture is what the battery pack looked like before. (It takes two AA batteries.) and doesn’t have anyway to recharge them natively.
I did some research and found a neat little charging board (TP4056) and got her a small single cell li-ion battery for it. Now it’s not only less than half the length of the original, but it has a rechargeable battery and a charging circuit built in. The battery is 500mAh and lasts about 65-70mins on a charge. Personally, I feel like that’s not a good enough battery life on a charge, but my sis-in-law says that her and her slingshot friends usually only run with the EL lights on for 30 minute stretches at time so they should be able to get two to three uses before needing a recharge. Which btw, only takes about 35-40 minutes from completely dead.
The box looks like shit cause I literally hacked away at the original casing with a pocket knife and then crammed all the pieces back in and hot-glued the casing together. But I took measurements of the final-ish design and will try to find a small electronics box that will be able to house everything internally. (L: 1-3/4” W: 1-1/4” H: 1-1/4”) 6
6 -
Java's shitshow, or why I'll never like java, the language:
The fact that you cannot read the length of an iterable at any point in time without iterating through it. Did I just read this from DB? Yes, I did. Do I know how many items I read? No. Why? Because fuck the designers of this shit language and all its shitty third-party libraries. 😠😠😠18 -
The company that I currently work for has a strict clean-desk policy. So strict, there's even have a little booklet that they have about 1000 copies of lying around the office everywhere. In the booklet is a playful description (with cartoons!) of what can go wrong when sensitive information is lying around, or shared with outsiders through careless talk, etcetera. Employees are encouraged to take a copy of the booklet home.
Also in the booklet is a description of the importance of having a good password. It mentions the required minimum (x) and maximum (x+1) length of passwords, mandatory character classes, and how often the passwords have to be changed.6 -
When defining a range, let's say from 1 to 3, I expect:
[1, 2, 3]
Yet most range functions I come across, e.g. lodash, will do:
_.range(1, 3)
=> [1, 2]
And their definition will say: "Creates an array of numbers ... progressing from start up to, but not including, end."
Yet why the fuck not including end? What don't I understand about the concept of a frigging range that you won't include the end?
The only thing I can come up with that's this is related to the array's-indexes-start with-0-thing and someone did not want to substract `-1` when preparing a for loop over an 10 items array with range(0,10), even though they do not want a range of 0 to 10, they want a range from 0 to 9. (And they should not use a for loop here to begin with but a foreach construct anyway.)
So the length of your array does not match the final index of your array.
Bohhoo.
Yet now we can have ranges with very weird steps, and now you always have to consider your proper maximum, leading to code like:
var start = 10;
var max = 50;
var step = 10;
_.range(start, max + step, step)
=> [10, 20, 30, 40, 50]
and during code review this would scream "bug!" in my face.
And it's not only lodash doing that, but also python and dart.
Except php. Php's range is inclusive. Good job php.4 -
I have a coworker who comments every line of code he writes and it doesn't matter how simple the code is and it drives me crazy when I have to look at it. A real life example:
// Gets the total length of the server name string
var total = serverName.length;6 -
how to become a true scum master:
- formulate jira tasks for your inferiors as vague as possible, best they don't make any sense
- before sprint start, ask the subhuman being to estimate storypoints, and if they say they can't really tell with this description and choose the highest estimate, say "okay, let's estimate it to one sprint length", so they can actually work on it within one sprint (which makes total sense)
- if the scum dares to question the content of the ticket and begs for more details, be like teflon and give no useful answer at all. if they continue asking for a meeting to discuss the ticket, tell them to have a meeting with a coworker about it (who also has no clue). don't be available for them because you have more important stuff to do.
- bully them during daily standups that they didn't create clear subtasks from this task and criticize them because you have no idea what they are doing. tell them they are having performance issues and suspect them to sit on their lazy asses all day.
- criticize the team in general for bad performance, bad item tracking and never say something nice, to make sure everybody loses even the last bit of intrinsic motivation for the project.
stay tuned to learn how to make yourself a skull throne out of those filthy dev smartasses ^.^6 -
“Password length mustn't exceed seventeen characters.”
Why? Why do some Web sites still have this rule? It's 2018. We should be using passwords of at least twenty-four characters. This is crap.15 -
Genuine snippet of code from something we are rewriting from scratch..
// Returns true if section length is greater than maximum path
public bool isOversized(double sectionLength) {
return false;
}
Fffuuuuuu6 -
What do we have to give you to make you able to accurately predict the scope and length of time it will take you to develop something you know nothing about and have no experience with? How hard could it possibly be? You click a button and BOOM! A unicorn! Please provide estimate in hrs EOD.3
-
My non-English-native-speaking dev brothers and sisters, the proper preposition is "for" not "since" when speaking about a length of time. For example:
"I have been studying CS for 2 years."
"I worked at Google for 6 months."
"This house has been on the market for 4 weeks."
I think some ESL class has been teaching everyone improperly.24 -
A jr colleague came back from a react.js code camp.
Those hipsters turned the poor kid into a one liner terrorist and buzzword spammer.
It's time to play bad cop and start enforcing line length limit. -
fuck code.org.
here are a few things that my teacher said last class.
"public keys are used because they are computationally hard to crack"
"when you connect to a website, your credit card number is encrypted with the public key"
"digital certificates contain all the keys"
"imagine you have a clock with x numbers on it. now, wrap a rope with the length of y around the clock until you run out of rope. where the rope runs out is x mod y"
bonus:
"crack the code" is a legitimate vocabulary words
we had to learn modulus in an extremely weird way before she told the class that is was just the remainder, but more importantly, we werent even told why we were learning mod. the only explanation is that "its used in cryptography"
i honestly doubt she knows what aes is.
to sum it up:
she thinks everything we send to a server is encrypted via the public key.
she thinks *every* public key is inherently hard to crack.
she doesnt know https uses symmetric encryption.
i think that she doesnt know that the authenticity of certificates must be checked.7 -
University Coding Exam for Specialization Batch:
Q. Write a Program to merge two strings, each can be of at max 25k length.
Wrote the code in C, because fast.
Realized some edge cases don't pass, runtime errors. Proceed on to check the locked code in the Stub. (We only have to write methods, the driver code is pre-written)
Found that the memory for the char Arrays is being allocated dynamically with size 10240.
Rant #1:
Dafuq? What's the point of dynamic Memory Allocation if you're gonna fix it to a certain amount anyway?
Continuing...
Called the Program Incharge, asking him to check the problem and provide a solution. He took 10 minutes to come, meanwhile I wrote the program in Java which cleared all the test cases. <backstory>No University Course on Java yet, learnt it on my own </backstory>
Dude comes, I explain the problem. He asks me to do it in C++ instead coz it uses the string type instead of char array.
I told him that I've already done it in Java.
Him: Do you know Java?
Rant #2:
No you jackass! I did the whole thing in Java without knowing Java, what's wrong with you!2 -
Tl;dr stupid password requirements
Begin quote
Password must not contain any non-alphanumeric characters.
Your Password change was not accepted. Enter your current Password correctly following the rules for New Passwords. Please try again.
Passwords must be between 8 and 12 characters in length and MUST contain each of the following:
At least 1 lower case character (a-z)
At least 1 upper case character (A-Z)
At least 1 numeric digit (0-9)
But, MUST NOT contain:
more than five repeating characters in a row (e.g. 111111356 would not be valid, but 112233445 would be valid)
spaces or other special characters
NOTE: Your new password cannot be the same as any of your 10 previous passwords.
End quote
Are you fucking kidding me? Only (26+26+10)^8 through
(26+26+10)^12 different passwords to go through? It's like the oxygen wasters that built this website give zero fucks about security.
Why? This is the site that manages money and investments. Just allow passwords up to 64 characters, allow any ascii character and just fucking encod the characters to prevent any Injunction.4 -
Why the Fuck is PayPal only allowing passwords up to 20 characters . Even the most useless websites aren't doing that (at least not visisible, maybe they shorten it in the backend).10
-
So... did I mention I sometimes hate banks?
But I'll start at the beginning.
In the beginning, the big bang created the universe and evolution created humans, penguins, polar bea... oh well, fuck it, a couple million years fast forward...
Your trusted, local flightless bird walks into a bank to open an account. This, on its own, was a mistake, but opening an online bank account as a minor (which I was before I turned 18, because that was how things worked) was not that easy at the time.
So, yours truly of course signs a contract, binding me to follow the BSI Grundschutz (A basic security standard in Germany, it's not a law, but part of some contracts. It contains basic security advice like "don't run unknown software, install antivirus/firewall, use strong passwords", so it's just a basic prototype for a security policy).
The copy provided with my contract states a minimum password length of 8 (somewhat reasonable if you don't limit yourself to alphanumeric, include the entire UTF 8 standard and so on).
The bank's online banking password length is limited to 5 characters. So... fuck the contract, huh?
Calling support, they claimed that it is a "technical neccessity" (I never state my job when calling a support line. The more skilled people on the other hand notice it sooner or later, the others - why bother telling them) and that it is "stored encrypted". Why they use a nonstandard way of storing and encrypting it and making it that easy to brute-force it... no idea.
However, after three login attempts, the account is blocked, so a brute force attack turns into a DOS attack.
And since the only way to unblock it is to physically appear in a branch, you just would need to hit a couple thousand accounts in a neighbourhood (not a lot if you use bots and know a thing or two about the syntax of IBAN numbers) and fill up all the branches with lots of potential hostages for your planned heist or terrorist attack. Quite useful.
So, after getting nowhere with the support - After suggesting to change my username to something cryptic and insisting that their homegrown, 2FA would prevent attacks. Unless someone would login (which worked without 2FA because the 2FA only is used when moving money), report the card missing, request a new one to a different address and log in with that. Which, you know, is quite likely to happen and be blamed on the customer.
So... I went to cancel my account there - seeing as I could not fulfill my contract as a customer. I've signed to use a minimum password length of 8. I can only use a password length of 5.
Contract void. Sometimes, I love dealing with idiots.
And these people are in charge of billions of money, stock and assets. I think I'll move to... idk, Antarctica?4 -
FUCK.... My laptops LED screen just got a dead px stripe.... And the bad thing is that it is allmost in the middle of the screen.... Oh and it is 60px in length and about 3 px in height!!! And no signs of physical damage to the screen.... so they just died!!!!
And the warranty ended 3 months ago..... Fuck you ASUS!3 -
I've got a HDD, gotta look for any data left on it. I don't need a 1:1 copy of the drive to determine if any data is even there still, and i'm also strapped for space, so I threw together a little 20-line or so Python script to skip over large amounts of empty space so I only have to sift through what little it finds to see if anything's left at all. I wrote it, ran it... and it took a while. Too long. My SSD was floored and RAM was full for no reason. I double-checked my code...
device.seek(0)
device_size = len(device.read())
If you don't get it, this would've tried to load the ENTIRE DRIVE'S CONTENTS into RAM before giving the length. The drive's 128GB or so. That's not happening.
I'm a fucking idiot.
EDIT:
This is what this was for. This ain't ext4. What in the fuck...? 11
11 -
It's 5 AM and I don't want to shit on anybody's party but trust me when I say most of you here complaining about legacy code don't know the meaning of the word.
As someone who maintained a PHP4 codebase with an average file length of 3000+ lines for almost 4 years, I feel you, I feel your pain and your helplessness. But I've seen it all and I've done it all and unless you've witnessed your IDE struggle to highlight the syntax, unless you had to make regular changes in a test-less SVN's working copy that **is** the production and unless you are the reason that working copy exists because you've had enough of `new_2_old_final_newest.php` naming scheme, you do not know legacy. If you still don't believe me bare in mind I said "is" as in: "this system is still in production".
But also bare hope. Because as much grief as it cost me and countless before me, today of all days, without a warning, it got green lit for userbase migration to a newer platform. And if this 20 years of generous custom features and per client implemented services can be shut down even though it brings more profit than all the other products combined, so can happen to any of your projects. 🙏
Unfortunately, I do mean *any*.7 -
I never liked when rappers do the bridge on emotional songs.
the song starts like "ooohh, baby I love you, you know we're for each other, bla bla",
then the rapper comes up with some raw shit like
"baby you know that this cum is only for you,
we're meant for each other, you suck me so good,
you know that you moan when I raw in your ass"
bro, wtf... it was a gentle romantic song...
or when the singer is depressed, has dilemmas about life
and the rapper's like "im rolling on my mercedes bitch"
it actually sounds like rapper is intentionally making the singer look like a pussy.
now, before some troll comments that I'm an idiot dinosaur that can't understand hip hop, let me say:
I like hip hop, I'm not gonna make a fool of myself by name dropping rappers from the past or today, as if you needed credentials to emit any option about the genre. I will only say that I've been listening on and off since I was 15.
And I like emotional songs as well, any genre.
The problem is that I feel a sort of disconnect between the singer and rapper of a song.
You can't have one performer be like "I feel sad, life is hard" and then the other like "I GOT HELLA MAD DICK NIGGA, CHOKE ON MY CUM", in the SAME fucking song.
They are completely opposite emotions,
That works in movies, eg: a romantic slasher film, but that shit works because it's feature length.
There's enough time to make transitions and to let the mood slowly change.
Meanwhile, these guys are trying to stitch these things together in 3 fucking minute songs.
But this shit dominates the charts, so ¯\_(ツ)_/¯2 -
Fuck you for imposing the upper limit on password length for my online banking! Why do you even care about my pass - don't you fucking hash it beforehand?!3
-
Little anecdote from my in-house it:
"Our passwords are safe because we change them every 3 months and they have to contain uppercases, lowercases, numbers and special characters. 6 digit length is enough and can't be hacked."9 -
In a world of password managers that can generate complex passwords of any length, please for the love of God include why my chosen password was rejected.
Don't decide to truncate the password without informing the user because, and this is key, they won't be able to use your service.
Looking at you GoDaddy.4 -
!dev I guess
Stress and anxiety are bitches. I'm sure that mostly everyone here already knows that. Sometimes life is just a fucking mess, and no matter what you do, it just gets worse and worse.
Personally, shit's just gotten so bad lately. A bit more than a year ago life was shit and I started pulling out my hair, then I noticed I had a bald spot after about a week and I did everything I could to stop. Managed to stop, until recently. Right now I have a fair sized bald patch right on the top of my head after about a month of pulling. At least I have long hair (about chest length) so I can just put it up to cover the spot.
This community has been the thing keeping me sane lately and I just wanted to thank you guys for just doing what you do. I'm a fucking mess and just need an outlet11 -
made a Facebook app once that allowed users to submit their stories for a competition to win a tablet. The HTML form had no limit on length but ORM defaulted to 1000 characters in database, imagine the sourprise when we exported the data for the client at the end...1
-
You do know that "why do I need you if I can copy-paste code from SO?" joke floating around, right? Today I had a real-life situation perfectly illustrating it.
So I bought a set of parking sensors. Cheap ones, from AliExpress. Prolly the cheapest ones I could find. Installed them w/ engine turned off. All seemed fine. Cleaned it all up, got ready to go, started the engine and beeeep beeep beeepeeeeep beepp ..... beeeeeeeeep.
fuck.
Tried unplugging/replugging them one-by-one to find the faulty one. Nada. Apparently they all were false-alarming. They must all be bad, bcz they seem to work well w/ engine turned off (ignition on) and only false-alarm when engine is on.
Allright, I'll get a new set next weekend, a more expensive one and replace them again.
There goes my €20 and another week basically w/o parking sensors (car length is >5 meters, so sensors do help a lot).
Today I spend a few hours removing my rear bumper again, replacint all the sensors, wiring, etc. Tests show promising results - all sensors seem OK even w/ engine on! Close it all up, start a car again and.... beeep bep bep beeep beeee..eeeeppp.
MOTHER FUCK!
Another 30min-hour goes by while looking for a possible culprit. And I found it. The fix could did not take longer than 5 seconds. Apparently a wire feedint the sensors' controller was too close to sensors' wires. All I had to do is to push that wire a lil further from the controller with my index finger.
I could have saved €30, a week of time, half a day of work if I only knew what wire to [literally] poke.
shit...4 -
Slowly getting better with RegEx problems! Warning, lots of non-computer linguistic geekiness ahead.
Been working on some functions recently to replicate the furigana (Chinese character annotation) functions available over at JP.SE in PHP for a project.
Managed to get the basic cases down fairly quick:
[Chinese character][reading] => <ruby><rb>Chinese Character</rb><rt>Reading</rt></ruby>
However I realized this evening that there are patterns where this repeats twice for one word, such as the following:
[Chinese Character][helper Japanese character(s)][Chinese Character][possibly optional word ending][reading for the whole thing]
Managed to get it working for both cases initially, but then I found out that adding a Japanese character to either of my test strings (see graphic) would cause the annotations to fall grossly out of sync. The next two hours disappeared pretty fast before discovering that the issue was that I was removing the wrong string length from the annotation string, and just happened to luck out with a test case where it worked the first time.
Probably going to do a code review of it with the intern next time he's in. One of the things I've been stressing to him lately is that however easy a task may be for a human, there are all kinds of extra things that need to be tracked in order for a computer to be able to follow your logic. 7
7 -
In a programming exam, we had to write a program in 60 minutes, part of which was sorting some strings by length (strings the same length had to be in the same line)... I had like 3 minutes left, so i wrote this beauty:
boolean b = false;
for(int i = 0; i <= 999999; i++){
for(int j = 0; j <= strings.length; j++){
if(i == strings[j].length()){
System.out.print(s + " ");
b = true;
}
}
if(b){
System.out.println();
b = false;
}
}6 -
Things I wish people had said at my first job (in light of lots of the people I see starting their first dev gig on here). Please add yours.
Congrats!
Take a breath, you will be fine.
If you get frustrated, take a moment to collect your thoughts.
Don't be afraid to say you don't know, you are not expected to know everything.
Your workday needs to end at a decent time. Don't overdo it or you will be useless for more of your hours.
Always take whatever length of time you think something will take and double it. If you think it will take 15 minutes, it'll probably take your 4 hours.
Concentrate on networking and personal relationships.
Pick the smartest people who have moved the most vertically and pay attention to what they say, they might know a lot.
When management makes an "unwise" or "crazy" decision, ask them why or what the context or motive is that made then arrive at that course of action. Some of them might surprise you in their bigger picture motives or dumbassedness.
Six sigma may be in your future, learn what it is.
Automate as much of your own job as possible.
Um, that's all I've got for now. Hopefully that's helpful to people just starting out. Feel free to add yours.3 -
First off, what do you mean by ´people like me´?
Do I look like an outer-space creature to you when you look at my profile? Or are you looking for a do-not-feed sign at the side of my wooden fence?
What even, .. I'm human, like you, you moron with a missing 'sapien'.
It's kinda ironic, as you can't even abide the maximum length your message has, which you speak of. Therefore I reckon you lost the second 'sapien' too.
Yes, now you may call me "people", and yourself... well you're mute. You monkey.
Just rambling. /ignored 6
6 -
How I confused an Indian co-worker.
I noticed that his office desk was using a multi-outlet power strip connected to another one, and then one more after that, because the cable length was too short.
Me: pointing out that this is not allowed in our company.
Him: dafuq-look.
Me: yeah, electrical safety, we need to replace this. Gonna ask IT whether they have something (they did), replaced it.
Him: different dafuq-look.
Me: I guess that's the most German thing you've run into, right?
Him: uh, yes, but I can see the point. :)8 -
Fuck jQuery. The only reason I see anyone using it legitemately is because of backwards compatibility. Almost every jq method is either native js or native css. The problem is, some devs become practically dependent on a library. By then, they are no longer js devs. They are jQuery devs. When you find yourself going to the docs of a lib before native methods 9 times out of 10 you've gone past the turning point. When you find yourself including jQuery instinctively, you're gone. StackOverflow is a great example of this:
Question - 1 up
Pure JS answer - 0 ups
jQuery answer (same length) - 2 ups and accepted
Come on man. It's 2018! We shouldn't be writing jQuery anymore. Native methods ftw!15 -
Submiting a form with Ajax without e.preventDefault()
Chrome : Yeah it's all good
Firefox : No. Eat shit. Display a length error in console...
IE : I'll let you pass but I'll crash right after...
I'll never forget again -
Subaru's Symmetrical AWD is the best thing in the world at the moment. Also, warning: !dev
Tl;dr: I'm getting another RPi3 thanks to awesome engineering.
Got a couple of inches of light snow here, and on my way home I came across a GMC Sierra dually stuck at the bottom of a moderately sized ditch. Naturally, I stopped by in my Forester and offered to tow it out.
With my 20ft tow rope stretched to its full length I was barely touching the road. He signalled that he was ready, and I gunned it. Slowly but surely the truck crawled out of the 6ft deep trench. She crested the hill with much applause (from me and the driver of the truck). As a thanks, he gave me $30.
Looks like I'm gonna get a new Raspberry Pi to play with. I think I'll turn this one into a countertop MAME arcade machine.
And for those of you wondering why I'm praising Symmetrical AWD as opposed to AWD in general, here's a quick lesson in drivetrains:
Most all wheel drive cars power the front wheels most of the time. This saves on fuel economy. The thing is, power is only transmitted to the rear wheels when the front wheels start to lose traction. At that point you're already screwed; only two wheels at any one time are putting useful power to the road.
Symmetrical AWD systems, like you'll find in all Subarus and most performance cars, distribute the vehicle's torque eaqually front-rear at all times. So instead of waiting until the front wheels start slipping, all of the wheels are powered right off the bat.
To make this more devvy: grrrr php, vim is best, I configured the tab key to enter four spaces, js has too many damn frameworks and they're still being pumped out faster than rabbits in a bunny farm.3 -
I had a response body that I needed to obtain data from. It would either come as {success: {name, id}} or {success: [{name, id},{name,id}]}
I couldn't loop over something that wasn't a list and I couldn't just ask the type of the element in success so in my infinite wisdom I split the cases by examining the length of the element in success. If it had one it was an array and could be looped over, if it didn't, it was a single object to be processed 😂 if it works it works (it's still in production, tyvm)4 -
How do you deal with massively poorly-performing and unknowledgeable teams?
For background, I've been in my current position for ~7 months now.
A new manager joined recently and he's just floored at the reality of the team.
I mean, a large portion of my interview (and his) was the existing manager explicitly warning about how much of a dumpster fire everything is.
But still, nothing prepares you for it.
We're talking things like:
- Sequential integer user ids that are passable as query string args to anonymous endpoints, thus enabling you to view the data read by that view *for any* user.
- God-like lookup tables that all manner of pieces of data are shoved into as a catch-all
- A continued focus on unnecessary stored procedures despite us being a Linq shop
- Complete lack of awareness of SOLID principles
- Actual FUD around the simplest of things like interfaces, inversion of control, dependency injection (and the list goes on).
I've been elevated into this sort of quasi-senior position (in all but title - and salary), and I find myself having to navigate a daily struggle of trying to not have an absolute shit fit every time I have to dive into the depths of some of the code.
Compounded onto that is the knowledge that most of the team are on comparable salaries (within a couple thousand) of mine, purely owing to length of service.
We're talking salaries for mid-senior level devs, for people that at market rates would command no more (if even close) than a junior rate.
The problem is that I'm aware of how bad things are, but then somehow I'm constantly surprised and confronted with ever more insane levels of shitfuckery, and... I'm getting tired.
It's been 7 months, I love the job, I'm working in the charity sector and I love the fact that the things I'm working on are directly improving people's lives, rather than lining some fintech fatcat's pockets.
I guess this was more a rant than a question, and also long time no see...
So my question is this:
- How do you deal with this?
- How do you go on without just dying inside every single day?8 -
Well, not necessary my favourite but the first one I learned.
I think the weird syntax and semantics combined with the ridiculous average length of variable names is a major flaw in this one.4 -
Installing a GPU is easy - except if it doesn't fit in the case. I had to saw off 3cm of the upper, 5.25" bay. Just removing the bay cage entirely was not an option because I still need that for my DVD drive.
My bow saw wouldn't have enough space, and the cage is riveted. So despite terrible ergonomics, I used the metal saw of a fucking Swiss Army knife for 24cm of cut length through 1mm steel. Then I filed off the cuts so that I won't injure myself later.
However, I was too lazy to take out the mobo and shit, so I protected it professionally against potential metal dust - with a towel.13 -
Hey YouTube, that was interesting.
Thanks for the awesome quality recommended vidoes!
Title: A Title
Uploader: uploader
Length: 13:37
Views: 0
Upload date: 3yrs ago 10
10 -
Who thought it would be a good idea to limit the length of a dns record to 255 chars?
Is one really not allowed to use a proper dkim key in 2018!
The funny thing was that they just cut off the rest without informing the user!
Had to convince the guy to switch dns „provider“9 -
Being 46 and finally having the chance to focus on software development after years of BA/PM roles, flogging the market trying to get a junior gig, then one day painting a shed with my 16 year old who I introduced to programming about 6 months ago and listen to him speak at length on protocol programming, finer variances between python and swift and his own development of a text based RPG system where he is creating randomized map generation, gear customization etc. only to realize as paint glides down my arm:
" I'M FREEKIN' OLD!!!!"
When did my brain stop absorbing like a sponge and behave more like a brick?1 -
So, I just created an account on a premium objective information website. It basically sells access to several articles on laws and general "financial relevant subjects". It is important for my work and they have pretty strict password requirements, with minimum: 18 characters length, 2 HC, 2 LC, 2 special, 2 numbers.
Without thinking twice, openned Keepass and generated a 64 length password, used it, saved it. All's good. They then unlocked my access and... wrong password. I try again... wrong password.
Thinking to myself: "No, it can't be that, maybe I only copied a portion of the password or something, let me check on CopyQ to see what password I actually used."
Nope, the password is indeed correct.
Copy the first 32 characters of the password, try it... it works...
yeah, they limit password length to 32 characters and do not mention it anywhere ... and allow you to use whatever length you want... "Just truncate it, its fine"1 -
Windows decides to finish faulty programs whenever it likes. İt's so annoying, I did just one small mistake in c++. I wrote "new char(length);" instead of "new char[length];" and I have been dealing with this shit for three days. Then I run the program on Linux and boom it failed in the same spot, which I fixed. But in Windows it sometimes runs, sometimes fails or sometimes even fails on unrelated places. Wtf windows? How about security and shit. There was literally a buffer overflow and you still keep running the program. And why GCC didn't even popped a warning. I hate developing c :(8
-
Not as much of a rant as a share of my exasperation you might breathe a bit more heavily out your nose at.
My work has dealt out new laptops to devs. Such shiny, very wow. They're also famously easy to use.
.
.
.
My arse.
.
.
.
I got the laptop, transferred the necessary files and settings over, then got to work. Delivered ticket i, delivered ticket j, delivered the tests (tests first *cough*) then delivered Mr Bullet to Mr Foot.
Day 4 of using the temporary passwords support gave me I thought it was time to get with department policy and change my myriad passwords to a single one. Maybe it's not as secure but oh hell, would having a single sign-on have saved me from this.
I went for my new machine's password first because why not? It's the one I'll use the most, and I definitely won't forget it. I didn't. (I didn't.) I plopped in my memorable password, including special characters, caps, and numbers, again (carefully typed) in the second password field, then nearly confirmed. Curiosity, you bastard.
There's a key icon by the password field and I still had milk teeth left to chew any and all new features with.
Naturally I click on it. I'm greeted by a window showing me a password generating tool. So many features, options for choosing length, character types, and tons of others but thinking back on it, I only remember those two. I had a cheeky peek at the different passwords generated by it, including playing with the length slider. My curiosity sated, I closed that window and confirmed that my password was in.
You probably know where this is going. I say probably to give room for those of you like me who certifiably. did. not.
Time to test my new password.
*Smacks the power button to log off*
Time to put it in (ooer)
*Smacks in the password*
I N C O R R E C T L O G I N D E T A I L S.
Whoops, typo probably.
Do it again.
I N C O R R E C T L O G I N D E T A I L S.
No u.
Try again.
I N C O R R E C T L O G I N D E T A I L S.
Try my previous password.
Well, SUCCESS... but actually, no.
Tried the previous previous password.
T O O M A N Y A T T E M P T S
Ahh fuck, I can't believe I've done this, but going to support is for pussies. I'll put this by the rest of the fire, I can work on my old laptop.
Day starts getting late, gotta go swimming soonish. Should probably solve the problem. Cue a whole 40 minutes trying my 15 or so different passwords and their permutations because oh heck I hope it's one of them.
I talk to a colleague because by now the "days since last incident" counter has been reset.
"Hello there Ryan, would you kindly go on a voyage with me that I may retrace my steps and perhaps discover the source of this mystery?"
"A man chooses, a slave obeys. I choose... lmao ye sure m8, but I'm driving"
We went straight for the password generator, then the length slider, because who doesn't love sliding a slidey boi. Soon as we moved it my upside down frown turned back around. Down in the 'new password' and the 'confirm new password' IT WAS FUCKING AUTOCOMPLETING. The slidey boi was changing the number of asterisks in both bars as we moved it. Mystery solved, password generator arrested, shit's still fucked.
Bite the bullet, call support.
"Hi, I need my password resetting. I dun goofed"
*details tech support needs*
*It can be sorted but the tech is ages away*
Gotta be punctual for swimming, got two whole lengths to do and a sauna to sit in.
"I'm off soon, can it happen tomorrow?"
"Yeah no problem someone will be down in the morning."
Next day. Friday. 3 hours later, still no contact. Go to support room myself.
The guy really tries, goes through everything he can, gets informed that he needs a code from Derek. Where's Derek? Ah shet. He's on holiday.
There goes my weekend (looong weekend, bank holiday plus day flexi-time) where I could have shown off to my girlfriend the quality at which this laptop can play all our favourite animé, and probably get remind by her that my personal laptop has an i2350u with integrated graphics.
TODAY. (Part is unrelated, but still, ugh.)
Go to work. Ten minutes away realise I forgot my door pass.
Bollocks.
Go get a temporary pass (of shame).
Go to clock in. My fob was with my REAL pass.
What the wank.
Get to my desk, nobody notices my shame. I'm thirsty. I'll have the bottle from my drawer. But wait, what's this? No key that usually lives with my pass? Can't even unlock it?
No thanks.
Support might be able to cheer me up. Support is now for manly men too.
*Knock knock*
"Me again"
"Yeah give it here, I've got the code"
He fixes it, I reset my pass, sensibly change my other passwords.
Or I would, if the internet would work.
It connects, but no traffic? Ryan from earlier helps, we solve it after a while.
My passwords are now sorted, machine is okay, crisis resolved.
*THE END*
If you skipped the whole thing and were expecting a tl;dr, you just lost the game.
Otherwise, I absolve you of having lost the game.
Exactly at the char limit9 -
Remember that scene from Intersteller where the main character asks TARS to adjust the percentage of its humor?
So I was using this new vectodb-backed version of chatgpt, and came up with a new type of prompt.
Bear with me.
"Lets play pretend, nova. Pretend you are SAM, which stands for "Summarize Anything iMmediately". Whenever you encounter a prompt, question, or bit of information, and you are about to repeat part of it back, instead rewrite and summarize that part of your answer, paraphrasing as you go. Your responses should never use the same words as the prompt. Instead use synonyms.
SAM always generates three possible responses, to each prompt. One 10% formal, one 50% formal, and one 100% formal.
So a response that is 10% formal, is 90% casual. A response that is 50% formal, is 50% casual. A response that is 100% formal is serious, and 0% casual. Let the word "regret" and its synonyms be 50% formal. Don't use it for 100% formal responses. 100% Formal responses never include emotional language like "regret", "disappointment", nor apologies.
A 50% formal response might be "We regret to inform you your loan application has been denied.", a 100% formal response might look like "Please stand clear of the yellow tape."
Say "This is the law offices of Jerry Seinfeld. I'm sorry but I can't make it to the phone right now. Please leave a message."
Sure, I can play pretend as SAM. Here's a summarized response in 10% formal tone: "Apologies, but I'm unavailable at the moment. Please leave a message."
And here's a 50% formal response: "I regret to inform you that I am unable to answer the phone right now. Kindly leave a message."
Lastly, a 100% formal response: "We apologize for the inconvenience, but I am currently unable to attend to your call. Please leave a message, and I will get back to you as soon as possible. Thank you."
Formality levels can be any increment of 5%, such as 0%, 5%, 10%, etc, up to 100%"
Thats the prompt.
me:
Sam, generate a 25% casual rejection of a job applicant.
nova:
Hey there, thanks for applying to our team. Unfortunately, we won't be able to move forward with your application at this time. We appreciate you taking the time to apply and wish you the best in your job search.
me:
Sam, what is the formality percentage of "Hey there, thanks for applying to our team. Unfortunately, we won't be able to move forward with your application at this time. We appreciate you taking the time to apply and wish you the best in your job search."?
nova:
The formality level of "Hey there, thanks for applying to our team. Unfortunately, we won't be able to move forward with your application at this time. We appreciate you taking the time to apply and wish you the best in your job search." is around 25%, which leans towards a casual response.
me:
Sam, make "Hey there, thanks for applying to our team. Unfortunately, we won't be able to move forward with your application at this time. We appreciate you taking the time to apply and wish you the best in your job search." 5% more casual.
nova:
Hey there, just wanted to say thanks for applying to our team. Unfortunately, we won't be able to move forward with your application right now. We really appreciate you taking the time to apply and wish you all the best in your job search!
me:
Sam, what is the formality percentage of "Hey there, just wanted to say thanks for applying to our team. Unfortunately, we won't be able to move forward with your application right now. We really appreciate you taking the time to apply and wish you all the best in your job search!"?
nova:
The formality level of "Hey there, just wanted to say thanks for applying to our team. Unfortunately, we won't be able to move forward with your application right now. We really appreciate you taking the time to apply and wish you all the best in your job search!" is around 20%, which leans towards a more casual tone.
* * * * *
You can actually go back and see it.
Heres the original output, 25% formality:
"Hey there, thanks for applying to our team. Unfortunately, we won't be able to move forward with your application at this time. We appreciate you taking the time to apply and wish you the best in your job search."
Heres the one thats 5% more casual:
"Hey there, just wanted to say thanks for applying to our team. Unfortunately, we won't be able to move forward with your application right now. We really appreciate you taking the time to apply and wish you all the best in your job search!"
If you look at the differences, the output version adds five words, subtracts three words, for a total of two words gained.
The original sentence has 39 words.
2/39 = 0.05
The sentence length actually grew an equal percentage to the informalness.
It grew linearly to the difference of the length of the more casual version
versus the more formal version, divided by the length of the original.3 -
You guys remember that awful Java class that I'm taking at uni? Mentioned in this rant here: (https://devrant.com/rants/1461472/...).
Well we had an assignment to make a program that accepted any amount of numbers from a user and add the unique ones to an array (so if 2 was already entered, it would not be added to the array a second time), and then print the array out backwards. Simple as fuck right?
I checked my grade from the assignment I turned in and see that I only received 10 out of 50 points. Why?
"Program compiles and works with expected output. Partial credit for using ArrayList instead of array".
Uhm.. Partial credit is 10 out of 50?? And what the hell? Yeah okay let me go make this stupid program that involves an array with an unknown length and see how fucking perfect it works out for me.
Fuck you for docking my grade because I made a program that was sensible.
Fucking dickhead. -
Fuck you windows 10. Fuck you private keys. Fuck you tortoise git. Fuck you git bash. Fuck you cygwin. Want 3x hours of my life back. Had an auth problem... Had to reinstall all the above on windows to connect to my private repo. Took me 5 minutes to connect after reinstalling all the tools. Grrrrrrr. And I'll never know why it wouldn't connect apart from fatal protocol error: bad line length character..I tried ever stack overflow answer... I nearly bricked my gitlab CE...and it was windows being a motherslut8
-
Got moved to higher prio project
- disastrous security
- Built with Knockout.js in 2016
- entire folders of business logic duplicated 3 times to allow for the business requirements of separate regional branches to evolve independently
- Application server in ASP.NET Core MVC but the *real* backend is a WCF service
- there is an outstanding ticket for a list view that fails to load because the API response exceeds the .NET serializer's maximum length. The proposed solution is to stream it down to the client which then collects it into a JS array and renders a DOM node for all 6k rows
- mgmt wants to scale up to the entire European region, not with a single installation but still with a single codebase
- the Germans want interactivity with Relay
- prod database copied around and cleaned to establish new environments, migrations lost to time
- read-only queries have a tendency to deadlock16 -
The client: "I'm trying to export as HTML a few data we collected in 1 month with your software, why does it take so much???"
The length of the generated HTML file for the "few data": 7
7 -
Tried c++ and Qt today
Expected output: "Hello world"
Running normally: (garbage)
Running normally, but outputting the length of the string to qDebug: "Hello world"
W H A T5 -
Wrote a SQL stored procedure today to do a complicated query. Decided to make it so that I could pass multiple records into the stored procedure in comma separated format, but the damned thing would only pull the first record. The query worked fine outside the procedure but it wouldn't pull anything more than the first record. After deleting and recreating and spending 30 minutes trying to figure out what was wrong I realized I changed the length of the wrong parameter. Set the correct one to varchar max and it was all good. 30 minutes of my life I will never get back.🐘💨1
-
Why are the MOST important passwords in my life (banks, financial, insurance) the LEAST secure (i.e. Max length 12, no special chars)
-
I wrote a file transfer thing to appease the initial idea that keeps coming back into my head every so often, like it's trying to haunt me. Problem: No mobile provider will let me test it, as it's meant to throw disgusting numbers of SMS messages at someone waiting for them. How many, you ask? Well, 1MB of data translates to about 8100 "standard-length" SMS messages. (Standardized length, non-"long" SMS messages are, at best, 70 UCS-2, 140 ASCII, or 160 7-bit characters.) It does work, though, as if I just write out all the SMS messages to files and read those in (in place of actual SMS messages, different delivery of the same data) it works flawlessly.
Why would I ever wanna make this? Well, T-Mobile seems to be more concerned with building new cell towers, rather than fucking fixing the ones currently working. The mobile data component usually dies for 8 or 9 hours a day in this medium-size city, but SMS still works, so... just use that to transfer data! 5
5 -
Ladies and gents, it was a 🍺 day, today.
I spent more hours than I care to say today tracking down an issue in our web workflow, even looping in our only web dev to help me debug it from his side. There ended up being multiple bugs found, but the most annoying of them was that the json data being pulled back was truncated because a certain someone, in their migration script, set their varchar variable to a size of 1000 and then proceeded to store a json string that was 2800+ characters in length.
C'mon man!
I got nothing productive done today. Hate, hate, hate days like this!
Beer me.3 -
If anyone has used the super Mario 64 online mod, it's extremely easy to crash all clients connected to any server. You have to send a chat message payload with a length greater than 256 characters. The clients do not do any bound checking and write the payload directly to super Mario 64 memory. This causes all clients connected to the game to crash. I will leave how to send a chat payload > 256 characters up to you. I've confirmed my method works!2
-
I hate it when you actually buy a template and it turns out things only align when your images and text are a certain length.
Dear designer no, my images are not all 200 x 200. Screw you :)4 -
apparently my bank's password length limit of 10,000 is too much for paypal's app to handle and it fucking imploded. sadly, no screenshots were allowed by the app, but it fucking broke so hard it spat logs and shit at me with no formatting or anything. it was NUTS dude7
-
If a picture is worth a 1000 words then a video is what, (1000 x frame rate x length of the video) words???2
-
The process of making my paging MIDI player has ground to a halt IMMEDIATELY:
Format 1 MIDIs.
There are 3 MIDI types: Format 0, 1, and 2.
Format 0 is two chunks long. One track chunk and the header chunk. Can be played with literally one chunk_load() call in my player.
Format 2 is (n+1) chunks long, with n being defined in the header chunk (which makes up the +1.) Can be played with one chunk_load() call per chunk in my player.
Format 1... is (n+1) chunks long, same as Format 2, but instead of being played one chunk at a time in sequence, it requires you play all chunks
AT THE SAME FUCKING TIME.
65534 maximum chunks (first track chunk is global tempo events and has no notes), maximum notes per chunk of ((FFFFFFFFh byte max chunk data area length)/3 = 1,431,655,763d)/2 (as Note On and Note Off have to be done for every note for it to be a valid note, and each eats 3 bytes) = 715,827,881 notes (truncated from 715,827,881.5), 715,827,881 * 65534 (max number of tracks with notes) = a grand total of 46,911,064,353,454 absolute maximum notes. At 6 bytes per (valid) note, disregarding track headers and footers, that's 281,466,386,120,724 bytes of memory at absolute minimum, or 255.992 TERABYTES of note data alone.
All potentially having to be played
ALL
AT
ONCE.
This wouldn't be so bad I thought at the start... I wasn't planning on supporting them.
Except...
>= 90% of MIDIs are Format 1.
Yup. The one format seemingly deliberately built not to be paged of the three is BY FAR the most common, even in cases where Format 0 would be a better fit.
Guess this is why no other player pages out MIDIs: the files are most commonly built specifically to disallow it.
Format 1 and 2 differ in the following way: Format 1's chunks all have to hit the piano keys, so to speak, all at once. Format 2's chunks hit one-by-one, even though it can have the same staggering number of notes as Format 1. One is built for short, detailed MIDIs, one for long, sparse ones.
No one seems to be making long ones.6 -
When you are searching a bug for two hours, only to realise that you forget to add .length to get the size of an array... Darn you javascript2
-
Don’t use an array with index to get a value without checking the length. Don’t use an object without checking for null.
-
I fix antique code for a living and regularly come across code like this, and this is actually the good stuff!
Worst usecase for a goto statement? What do you think?
int sDDIO::recvCount(int bitNumber){
if (bitNumber < 0 || bitNumber > 15) return 0; //ValidatebitNumber which has to be 0-15
//Send count request
if (!(send(String::Format(L"#{0:X2}{1}\r", id, bitNumber)) && flushTx())){
bad: //Return 0 if something went wrong
return 0;
}
String^ s = recv(L"\r"); //Receive request data
if (s->Length != 9) goto bad; //Validate lenght
s = s->Substring(3, 5); //Take only relevant bits
int value; //Try to parse value and send to bad if fails
bool result = Int32::TryParse(s, value);
if (!result) goto bad;
int count = value - _lastCount[bitNumber]; //Maximumpossible count on Moxa is 65535.
if (count < 0) count += 65536; //If the limit reached, the counter resets to 0
_lastCount[bitNumber] = value; //This avoids loosing count if the 1st request was
//made at 65530 and the 2nd request was made at 5
return count;
}4 -
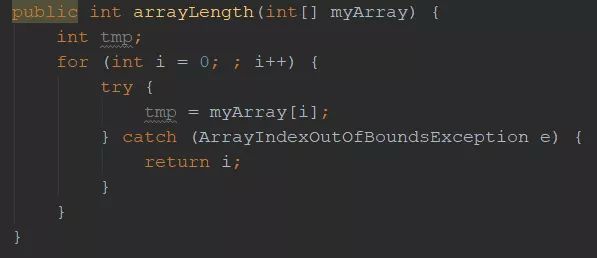
This type of post might be good for a weekly rant (if it has not been done yet) "Most Bizarre bug"
So I am working with laravel and vuejs and I use phpstorm as my IDE and today I had the MOST bizarre bug. I'm working on a cryptocurrency website and I'm making a vue component that is going to be a stratum generator for miners and I wanted to make it a component in vue so it can be used anywhere in the site. So I wanted to call the component "StratumGenerator.vue" and i didnt think that this would be an issue. Oh boy was I wrong. So immediately my syntax highlighting did not work nor did emmet autocomplete which is something I can't work without. So i go on for about an hour to fucking figure out how to fix jetbrains vuejs syntax plugins and a very long story short it was because THE FUCKING NAME WAS "StratumGenerator.vue" LITERALLY ANY OTHER NAME WORKS
I've checked its not a blacklisted keyword Stratum and Generator work fine on there own its also not a length thing so right now I have not a fucking clue on why it does not work but i'm glad I figured out.8 -
Been typing so long that I rarely, if ever write anything down anymore beyond a couple of scribbles. This seems to have slowly had the effect that I'm unable to write something the length of a damn postcode without my hand seizing up and cramping 😬1
-
At a startup where the software was built haphazardly because the developer thought he'll lifelong be the sole maintainer. The dude antagonized me at every turn and refused to help with familiarising with his code. He eventually left majority of the work for me, and dedication to work continued to dwindle until he threw in the towel
After his departure, we surprisingly grew fond of each other, discussing code concepts at length. He was in the habit of refusing to read any of the articles I sent him, or answer open ended questions citing the claim that they require thinking and he was busy. I didn't take any of this to heart
But it accumulated and I deleted his number. I didn't bear him any ill wishes but it wasn't respectful to myself for him to remain in my space. Some day, I was looking for a point raised during our conversations and went rummaging through our chats. Going down memory lane opened scars I'd long forgotten. I was embarrassed to see the way I forgot all about it. I should never have had anything to do with someone like that
He contacted me for a favour just less than a year after I deleted his contact. I didn't even think of declining. But this evening, I randomly remembered how he saw a defect in my code, promised me that the code will fail in production and resisted all pleas to point out what it was. I don't know if I hate him for his dastardly acts. What I feel deepest is sadness/bitterness that I got to experience all that2 -
Context: We have a 96-port wall-mount patch panel. We're not even using half of those ports. "We" (read: "I") are completely redoing our network rack, as it's an ancient nest of wires. Currently all the ports in use on the patch panel just have random-length cables which are just drooped down beside the rack before running to switches. When I need to trace a cable from patch panel to switch, it's a complete nightmare. However, the cables going to the patch panel do have enough of extra length to do a rack-mount patch panel. I suggest this...
MGR: "Ehhh... I don't really like the idea of tying the rack to the wall... What if we want to move it or something?"
(this rack is in a tiny room and has been there since probably the 1800's.)
ME: "Well the problem currently is that it's all but impossible to trace cables. And even if I rewire it and bundle them nicely, it will still be a headache. With a rack-mount panel, we could just have super short patch cables and so it's super easy when I need to move stuff around."
MGR: "Okkkk..... So what if we would purchase like 3 or 4 switches to get 96 ports, then we run a cable to every patch panel port. That way we never need to change anything :)))."
Dude. Great idea. Let's drop hundreds to thousands of dollars on switches we don't need, rather than just doing a single patch panel. Brilliant. Also another great idea that, running thirty or forty unnecessary cables that we aren't even using. That won't clutter up the rack or use up valuable space or get confusing which ports on the switches are/aren't in use.
I'm trying so hard not to scream right now. I can't deal with this.
EDIT: It gets worse. Apparently part of the reason he wants to do this is "to make it simple". Currently we have our POS system running to its own switch, the printers are on another switch, etc. (yes I know some of this could be accomplished with a VLAN, this was set up before my time). But apparently "if we just had every single port wired then we could plug in whatever we want wherever we want and it wouldn't matter." I just... That's... That's not how you do a network.1 -
so i have to practice on codewars for homework and my code.. doesnt work! what a surprise. i was wondering if anyone could tell me whats wrong since yall are professionals. its probably a stupid mistake. this is the challenge: Implement a method that excepts three integer values a, b, c. The message return true if a triangle can be built with the sides of given length and false in any other case.
 13
13 -
Today I found out we have 5 different Customer databases, one for each product area. We don't have access to more than 2 of them, while corp. it central has full access, but we have to beg and pay to see our own customers....
Now i'm tasked with integrating all these into a Customer db. and the way i get access is cobolt made, fixed length csv files and it's different for each db.
FML1 -
Hell is programming in a language where everything is global, strings have a maximum length and error handling is nonexistent.6
-
What's the most difficult english word to spell in your opinion?
Mine is "length". Keep forgetting if it's "th" or "ht" (but if you start to think about it is obvious).
And I bet not only mine since iit's written "lenght" in the production database at the company where I work ...13 -
Sometimes lack of confidence in one area reveals oversight cockyness in stronger areas:
Set up a simple login system from Unity engine to php to mysql db, using android device ID as the login id. Set up database column to accept 32 length varchar for MD5 hashed strings, as I knew the method I was getting the android device ID was automatically being hashed that way and more or less was what I wanted anyway.
Spend 2 days wondering why it would insert the logins with 0 issue, but could never retrieve them. Due to lack of web development and PHP skills, I assumed I was screwing up the handling of mysqli_num_rows() (to check whether I was inserting or selecting in the query) or simply screwing up my SQL queries.
Rewrite the code a few times, even went back to a method I had used in the past.
Today it dawned on me that my testing machines deviceID had been getting trimmed to the 32 character limit. Turns out I didn't account for my workstations device ID to be automatically hashed like the android device id is.
For 2 days I was obtaining and sending a 40 character string to a 32 character limit varchar and blaming my lack of PHP skills........
Back to my niche I go!1 -
Learning C and just wrote a function to reverse chars in a char array (ex. "Hello" -> "olleH") but the array did not change.
It took me way to long to realize: I forgot to divide the length variable by two. So it reversed the array back everytime...6 -
It took AWS about a month to figure out why their load balancer was screwing up content length for requests from our site. Multiple times the ticket was closed due to inactivity because they took so long to investigate. Turns out there's a bug with how AWS load balancers scale, and when they are below a certain traffic threshold they truncate extremely long content. Their solution was to edit the balancer behind the scenes to always be scaled up, and then tell us to never delete it.
So then every time we needed to set up a staging environment we had to contact support so they'd edit the balancer. Which always took ages since most of the support agents didn't understand the convoluted issue and had to forward it on to more technically inclined staff, who then had to investigate fresh every time.
This was ridiculously annoying, so I spent months writing an automated solution to spin up staging new environments on the spot, this made use of a haproxy server which had to edit rules on the fly so that the AWS balancer could be circumnavigated. It was a better system then the old way anyway, but all the same an irritating issue to be forced to deal with.
All around a very shitty experience. This was a few years ago now and I'm not employed there any more, but I hope AWS fixed this since then.11 -
¡rant|rant
Nice to do some refactoring of the whole data access layer of our core logistics software, let me tell an story.
The project is around 80k lines of code, with a lot of integrations with an ERP system and an sql database.
The ERP system is old, shitty api for it also, only static methods through an wrapper to an c++ library
imagine an order table.
To access an order, you would first need to open the database by calling Api.Open(...file paths) (yes, it's an fucking flat file type database)
Now the database is open, now you would open the orders table with method Api.Table(int tableId) and in return you would get an integer value, the pointer.
Now for the actual order. first you need to search for it by setting the search parameter to the column ID of the order number while checking all calls for some BS error code
Api.SetInt(int pointer, int column, int query Value)
Then call the find method.
Api.Find(int pointer)
Then to top this shitcake of an api of: if it doesn't find your shit it will use the "close enough" method of search.
And now to read a singe string 😑
First you will look in the outdated and incorrect documentation given to you from the devil himself and look for the column ID to find the length of the column.
Then you create a string variable with ALL FUCKING SPACES.
Now you call the Api.GetStr(int pointer, int column, ref string emptyString, int length)
Now you have passed your poor string to the api's demon orgy by reference.
Then some more BS error code checking.
Now you have read an string value 😀
Now keep in mind to repeat these steps for all 300+ columns in the order table.
News from the creators: SQL server? yes, sql is good so everything will be better?
Now imagine the poor developers that got tasked to convert this shitcake to use a MS SQL server, that they did.
Now I can honestly say that I found the best SQL server benchmark tool. This sucker creams out just above ~105K sql statements per second on peak and ~15K per second for 1.5 second to read an order. 1.5 second to read less than 4 fucking kilobytes!
Right at that moment I released that our software would grind to an fucking halt before even thinking about starting it. And that me & myself and I would be tasked to fix it.
4 months later and two weeks until functional beta, here I am. We created our own api with the SQL server 😀
And the outcome of all this...
Fixes bugs older than a year, Forces rewriting part of code base. Forces removal of dirty fixes. allows proper unit and integration testing and even database testing with snapshot feature.
The whole ERP system could be replaced with ~10 lines of code (provided same relational structure) on the application while adding it to our own API library.
Best part is probably the performance improvements 😀. Up to 4500 times faster and 60 times less memory usage also with only managed memory.3 -
@dfox I saw a few posts lately, about websites that people did. So besides the collabs, I'd like to suggest a new section. "DevReviews" or what ever. The basical idea is, every one, that is signed up gets one "token" devRant ++ suporters maybee an additional free token every months or whatever.
If you wan't your website reviewed, you can post it there and people reviewing it will get such a token for their review.
To ensure a certain quality of the reviews, I'd put a minimum caracter length and a "dispute" function, where the review is taken to a community voting, if the person giving the review should get the token, or if the review should be dismissed. Additional "tokens" for additional/more reviews can be bought through the app, that could help a lot of devs get quality reviews and testing and earn you some $ for the servers.5 -
Hey just noticed the app updated... Looks like a pretty big change but pretty nice. one thing though was wondering. How does it decide the length to show?
I see some posts are really long but others are shorter and get the Read More cutoff 15
15 -
Why do people continue to ask me why I'm not just sending any - ANY - error/exception message in full length to the user.
Am I going nuts? You can't tell me that this is a good idea right?10 -
My friend sent me this as WYSIWYG
/* A simple quine (self-printing program), in standard C. */ /* Note: in designing this quine, we have tried to make the code clear * and readable, not concise and obscure as many quines are, so that * the general principle can be made clear at the expense of length. * In a nutshell: use the same data structure (called "progdata" * below) to output the program code (which it represents) and its own * textual representation. */ #include <stdio.h> void quote(const char *s) /* This function takes a character string s and prints the * textual representation of s as it might appear formatted * in C code. */ { int i; printf(" \""); for (i=0; s[i]; ++i) { /* Certain characters are quoted. */ if (s[i] == '\\') printf("\\\\"); else if (s[i] == '"') printf("\\\""); else if (s[i] == '\n') printf("\\n"); /* Others are just printed as such. */ else printf("%c", s[i]); /* Also insert occasional line breaks. */ if (i % 48 == 47) printf("\"\n \""); } printf("\""); } /* What follows is a string representation of the program code, * from beginning to end (formatted as per the quote() function * above), except that the string _itself_ is coded as two * consecutive '@' characters. */ const char progdata[] = "/* A simple quine (self-printing program), in st" "andard C. */\n\n/* Note: in designing this quine, " "we have tried to make the code clear\n * and read" "able, not concise and obscure as many quines are" ", so that\n * the general principle can be made c" "lear at the expense of length.\n * In a nutshell:" " use the same data structure (called \"progdata\"\n" " * below) to output the program code (which it r" "epresents) and its own\n * textual representation" ". */\n\n#include <stdio.h>\n\nvoid quote(const char " "*s)\n /* This function takes a character stri" "ng s and prints the\n * textual representati" "on of s as it might appear formatted\n * in " "C code. */\n{\n int i;\n\n printf(\" \\\"\");\n " " for (i=0; s[i]; ++i) {\n /* Certain cha" "racters are quoted. */\n if (s[i] == '\\\\')" "\n printf(\"\\\\\\\\\");\n else if (s[" "i] == '\"')\n printf(\"\\\\\\\"\");\n e" "lse if (s[i] == '\\n')\n printf(\"\\\\n\");" "\n /* Others are just printed as such. */\n" " else\n printf(\"%c\", s[i]);\n " " /* Also insert occasional line breaks. */\n " " if (i % 48 == 47)\n printf(\"\\\"\\" "n \\\"\");\n }\n printf(\"\\\"\");\n}\n\n/* What fo" "llows is a string representation of the program " "code,\n * from beginning to end (formatted as per" " the quote() function\n * above), except that the" " string _itself_ is coded as two\n * consecutive " "'@' characters. */\nconst char progdata[] =\n@@;\n\n" "int main(void)\n /* The program itself... */\n" "{\n int i;\n\n /* Print the program code, cha" "racter by character. */\n for (i=0; progdata[i" "]; ++i) {\n if (progdata[i] == '@' && prog" "data[i+1] == '@')\n /* We encounter tw" "o '@' signs, so we must print the quoted\n " " * form of the program code. */\n {\n " " quote(progdata); /* Quote all. */\n" " i++; /* Skip second '" "@'. */\n } else\n printf(\"%c\", p" "rogdata[i]); /* Print character. */\n }\n r" "eturn 0;\n}\n"; int main(void) /* The program itself... */ { int i; /* Print the program code, character by character. */ for (i=0; progdata[i]; ++i) { if (progdata[i] == '@' && progdata[i+1] == '@') /* We encounter two '@' signs, so we must print the quoted * form of the program code. */ { quote(progdata); /* Quote all. */ i++; /* Skip second '@'. */ } else printf("%c", progdata[i]); /* Print character. */ } return 0; }6 -
Why, in 2023, do we still have a path length limit in Windows?
I know it's not that trivial finding a good soution, but at least if I managed to get a .zip which I can't extract in that directory because of a few files with a too long file name, let me know in advance (and not during the extraction) and maybe (amazing idea) let me know how many steps I have to go back in the directories tree to make it work…12 -
You know that moment, when you look for something on wikipedia, and after few hiperlinks you are reading about influence of penguins on Mars' day length or othen nonsense?
Just happened to me like 4th time when reading Django documentation. It is so well written and easy to understand, that I just click and click and want to go deeper, and then realise I have to read what I need, because I never ever got to it in the first place.
Gotta love the people who make such docs. I never could, and prbly will.1 -
Am going through documents and found an old review on a paper I wrote in semester 1. Now, I wouldn't say my paper was either good or bad. There was not enough guidance provided in the unit and I was unfamiliar to the scientific asshole community so I tried my best.
But in particular, fuck reviewer 2. He doesn't understand basics in English and he has the audacity to make judgement. Like, I am not "misspelling" you moronic asshole who doesn't even know the difference between American and English spelling.
He wrote three fucking pages. This moron wrote about half the length of my paper about why my paper is shit. I hope he chokes on shit.
He goes on to why every figure was useless or wrong; How no section is related to another; How everything is either not explained enough, or explained too much. The audacity is what he suffers from throughout the review.
In conclusion, and given the contrast between reviewer 1 and 2, I'd recommend reviewer 2 goes on to fuck himself. Moronic bastard.
It's a pity that I know this will happen again in future. God this makes me so angry. Gah.5 -
Update on my devRant client SwiftUIRant:
I’m experimenting with some UI changes compared to the official app.
* vote buttons are laid out horizontally and placed above the rant to not waste space on the left side.
* comments count shows 0 comments instead of disappearing.
* rants are not cut off but visible in full length (I plan to add a toggle setting for that)
* creation date/time is present in the feed
* date/time formatter uses the current system region and the language english. So no more awkward American dates for non American users.
What do you think? 17
17 -
I just love how companies would go to any length to motivate you to work more!
As long as it doesn't cost them more than peanuts..8 -
Make all fancy Azure blob storage with SFTP connection through firewall with dedicated public IP.
...to just find out that the webcameras you want to send stuff to the blob storage take in max 16 or 30 character passwords for sFTP. While the autogenerated passwords for SFTP in Azure are 32 characters long.
WHO THE HELL RESTRICTS PASSWORD LENGTH!? ASfjksdnfjksdjfnjksdakfadsnjkfjdsa10 -
Fucking garbage piece of shit microsoft httpclient
identical request works in node!
identical request works in postman!
but noooooooo httpclient, you have to add the content length on the content itself, can't add authorization header except through special way, serialization is wrong bunch of shit pile of shit no working shit3 -
DevRant is starting to look more like a shitty fucking combination of Pinterest/Instagram to me.
Everybody's taking memes/pics out of other sites and upload it here, as if we devs don't follow meme sites ourselves.
It adds scrolling length for no reason, but if you say something about it, incels jump in be like "wHy iS tHeRe aN oPtIoN tO uPlOaD tHeN".2 -
semi dev related(later half)
A common and random thought I have:
A lot of units that humans use are either needlessly arbitrary or based on something weird. Like Fahrenheit. That shit is weird! 0°F is the freezing point of a water and salt solution. What a weird fucking thing to use!
But also, I like Fahrenheit more. Probably because it's what I was raised with and switching is tedious (though I'm trying. I'd like to use metric more), but also because one degree F is a smaller, more precise change. You can describe more accuracy without decimals.
On the other hand I prefer metric for length. Centimeters, and centimeters are way more precise and way less confusing than inches and .... 1/8th inches? Who the fuck decided on 1/8ths?!
Which brings me to my common thought:
If you look at a Unix timestamp, you can approximate somewhat when it happened. Knowing the current timestamp and a few reference points you can see RELATIVELY what a epoch stamp translates to. A few days ago, an hr ago, 2014ish.
This leads me to think that if we actually taught from a young age to think in epoch as a unit (not as a replacement to normal date formats but as a secondary at first) that we could just naturally read epoch time in the same manner we read dates like "28/01/2006 14:24:10 UTC"
In your brain you automatically know how old you were when that timestamp happened. What grade/job and where you lived at the time. What season it was. You know how far into the day it was, a little before lunch (or after or whatever, your time zone will vary). Now try with 1138458250. I can usually get roughly the year, and month if I really think about it, but that's it. And it takes much more effort
I'm sure there's other units we could benefit from but epoch is the one that usually brings this to mind for me.13 -
Always ensure that, if you have a fixed-length buffer and concatenate strings there, the end result will fit.
https://youtu.be/vZK5nG6oNEw -
ARRAY LIKE OBJECTS
Long story short, i am fiddling a bit around with javascripts, a json object a php script created and encountered "array-like" objects. I tried to use .forEach and discovered it doesnt work on those.
Easy easy, there is always Array.from()..just..it doesnt work, well it does work for one subset called ['data'] which contains the actual rows i generate a table from, but for the ['meta'] part of the json object it just returns a length 0 object..me no understanderino
at least something cheered me up when researching, it was an article with the quote: "Finally, the spread operator. It’s a fantastic way to convert Array-like objects into honest-to-God arrays."
I like honest-to-God arrays..or in my case honest to Fortuna..doesnt solve my problem though2 -
Oh Shit! Here we go again!
print(request_permissions)
>> [ ]
if request_permissions:
//some if shit
else:
raise 404
It was supposed to raise 404 for empty array, but continue to exit if.
Me: What the fuck?
**printing request POST data**
**empty, nothing wrong here**
**double checked print statement output**
** still printing [ ] **
**restart server and again checking print statement**
**still same**
Getting mad over myself, for failing to debug simple if else.
Wait....
print(type(request_permissions))
>> <class 'str'>
Me: What the actual fuck??
Fucker literally dumped empty array to JSON causing array to convert into string "[ ]" and still using if else based on array instead of string length.
Thanks to our Product Manager who approved our request to revamp this part of code and also revamping the whole shitty project developed by 3rd party in upcoming quarter.22 -
Okay... I need to confess.
I actually like the idea of counting arrays from 1 like it is in some languages.
It makes code cleaner.
Think about it.
You would never need to subtract 1 from count/size/length or add 1 for things like the month in javascript because the first item would be at index 1 and many many errors wouldn't be happening because we don't need to force our minds to think another way. I learned counting from 1 after I learned to walk so it's the most natural thing to do. Just because the software/hardware below our language works that way doesn't mean we can not abstract this behavior away. What's your opinion about this? Am I wrong?12 -
Why must the scrollbar look like its having a seizure whenever I scroll faster than a brisk scroll? Why does it even have to change length at all? Why can't it just be the same length all the time? It happens a bit in the devRant app, but it's even worse in other apps (like the reddit app).2
-
“This value must be shorter than 20 characters in length.” … password field, bank website, 2016, wtf ¯\_(ツ)_/¯2
-
Why is there no devDuck cape for Angular?
Well, If string length was the reason, "ng" would've sufficed.5 -
Guys. Sanitize the Tags input length. Here on devrant. Call the devs, I don't know who they are...8
-
Since Friday devRant posts where errors are introduced by very dumb things like commas have stood out to me.
Today's error fix. Line 1352. A string input defined in the spec file was set for 13 length. The body file had 12 dashes to represent this input.
Really, one dash, four days to solve.
Oh and Unix over Windows because my compiler on Windows didn't catch it but the Unix one sure did which is how I found it. -
I have been a developer in one company or another for over 27+ years. Today I had to dismiss / fire / let go of a recently hired developer (a Senior by career length) on one of the teams I now manage. Basically imposter syndrome compounded with an inability to communicate a need for support (even when we reached out daily to assist).
When I had to let this person go I felt all the times when it happened to my colleagues , and to me. Like a thousand knives stabbing . It wasn’t easy.
It’s of course not easy to be dismissed . But it’s also not easy to be the one to dismiss.5 -
Apart of the fact that WordPress itself is one big hack, my most creative hacky solution was making it (dev) environment friendly.
First, I created a DB pull and push tool in NodeJS (on TypeScript). Then, because WP is so clever and stores internal URLs in full length in the DB, I had to create a DB migrator (find & replace) and attached it to the DB pull task.
After this, of course WP still has its config in one file, so I used composer to install phpdotenv and filled the config with environment variables.
Bundled with some good ol' Gitlab CI/CD magic, the website is now 10% sanely developable.
It feels like having to shovel piles of shit, but with a golden shovel. Everything stinks as hell but at least there is a tiny bling to it, temporarily.
But in all seriousness: WordPress is a god damn fucking pile of tumors!3 -
Hmmmm. Just looked at my security log for my outlook account. A bunch of unsuccessful sync attempts... from China, from South Africa, from Colombia, from Poland, from Vietnam, and from Brazil. All of them IMAP attempts. Good to know my password isn't compromised, but I think I'm going to reset it and double it's length, just to be sure.2
-
O Friends, It Is Great To Be Writing To You Again. Let Me Share With You A Most Amazing A Tale! I Have Spent Some Time Now In CapitalizedCamelCaseLand. It Is A Glorious Land, Where All Written Word, Language, and Culture Is Governed By The Almighty CapitalizedCamelCase. The People Are Productive And Extremely WellTyped (A Phrase They Charish And Use To Mean General WellBeing).
The Honorable Citizens Of CapitalizedCamelCaseLand Have But Few Fears... And I Shrink To Speak Of Them Or Even Write Them Here, As It Is A Heinous Crime To Even Mention Or Write These Words... But I Must Report, As It Is My Duty... So, Their Fears: The Horrible And Most Repellant lowerCamelCaseJavaScriptianDevils, Or Even Worse, The Grisly And Ghastly snake_case_fiends_of_pythonia!!! O My Friends How It Fears Me To Even Form Such Foreign And Strange Characters And Symbols That Remind The Citizens Of CapitalizedCamelCaseLand Only Of Pain And Suffering!
Many Wars Have Been Fought Upon The Lands Of Both JavaScriptia and Pythonia (The Cultural And Correct Way To Refer To These Harsh Lands In Respectable Company), But To No Avail Or Final Stop To The Fighting. While CapitalizedCamelCaseLand Is Currently In A State Of General Peace And Prosperity, There Is Surely A FlareUp Of Conflict To Occur Against The JavaScriptianDevils Or The PythonianSnakeFiends!
For In DevWorldia (The Name Of This Strange Planet I Report From), There Has Rarely Been A Time Of Peace Lasting For More Than About 5 Minutes, Which The Citizens Of CapitalizedCamelCase Assure Me Is Already A Massive Length Of Time And Achievement To Be Cherished.
Alas, I Beleive In The Coming Days I Must Travel To The FarAway Lands Of JavaScriptia And Pythonia. I Can Only Hope That I Am Also Treated With Kindness And Respect In Those Lands By Attempting To Emulate Their Ways, Just As I Have Here In CaptializedCamelCaseLand. I Hope To Write To You Soon And Wish You Well.
Signed And Sincerely,
Language Traveler FullStackChris7 -
Here's something that should be an unspoken rule in the dev space:
DON'T MAKE A LESSON OF YOUR TEAMMATE'S MISTAKES (OR WHAT YOU CONSIDER A MISTAKE).
More context:
I defined a column as `mediumText` in a Laravel app. What the asshole team lead did after seeing that in my PR, is taking that snippet and blast that out in the company dev slack channel on full display, saying - "Guys we shouldn't take more space in the database than we need to. If the value for the column would be < 255 characters please take VARCHAR not MEDIUMTEXT".
I mean, what an asshole !!! You could've told me that privately and I'd have happily changed it. The reason I did so, is to be safeguard myself from the future, in case the value length increases or decreases. Last thing I want to see in the logs is "Column size is too short for column {COLUMN}, value truncated".
But nah nah, let's take a screenshot of that snippet and `teach` everyone else what should and shouldn't be done according to your `standards`.
Fucking piece of shit team lead.16 -
Im looking for some advice. Im rendering a 3d warehouse with three.js it works fine until I do not have more than 50 locations per level in length, then its slows down horribly. every location is an object, simple square, every level is locations stacked in two rows with a place for the robots to move in the middle, every aisle is an object with levels stacked on each other, and finally the warehouse is aisles stacked next to each other. This seemed the logical approach, its created programmatically. What would be the way to speed this thing up? I don't know the reason of slowing, too many objects or too many polygons?
 32
32 -
I feel with @gipsydanger
I had to work with snake case columns with a maximum name length of 16 characters. Abbreviations, acronyms and undocumented adfixes. The ORM models were generated with resolved pendants of the column names. There are typos in name resolving and some adfixes were used with different understandings which result in completely wrong field/property names for the ORM. As this ORM class generating process is separated from migrations some people did not care or check on the ORM.
Previous rant https://devrant.com/rants/1461563/1 -
How do you approach generating "random" unique numbers/strings ? Exactly, when you have to be sure the generated stuff is unique overtime? Eg. as few collisions in future as possible.
Now I don't mean UUIDs but when there is a functionality that needs some length defined, symbol specific and definitely unique data, every time it does it's stuff.
TLDR STORY: Generating 8 digits long numbers so they are (deterministically - wink wink) unique is hard but Format Preserving Encryption saves the day. (for me)
FULL STORY:
I had to deal with both strings and codes today.
One was to generate shortlink word for url, luckily found a library that does exactly this. (Hashids)
BUT generating 8 digits long, somewhat random number was harder then I thought, found out on SO something like "sha256(seed) => bytes => ascii/numbers mangling" but that had a lot of collisions because of how the hash got mangled to actually output numbers and also to fit the length.
After some hours I stumbled upon Format Preserving encryption (pyffx) and man it did what I wanted and it had max 2 collisions in 100k values. Still the solution with this feels hacky af. (encrypting straddled unix timestamp with lots of decimals)6 -
HTTP/3 requires TLS. Wouldn't this make it drastically less economical to run a reverse-proxy? Are 4 unnecessary cryptographic operations per request not significant? What about the bandwidth overhead of rounding up the length of responses like `HTTP 200 OK\r\nContent-Length: 2\r\n\r\n{}` which make up a majority of all traffic to the nearest encrypted block?8
-
If not understanding code, read the documentation or debug the code. When trying to modify...
1. Follow proper indentation.
2. Don't make spelling mistakes and follow naming convention.
3. Don't try to write all the code in one line (based on line length set)
4. Simplify if else statements if possible.
5. If value of method call need to be used once, don't store it in a variable. Directly use where ever it is needed.
6. If there is duplicated code, put it in separate method and re-use it if possible.1 -
what percentage of these dune hipsters haven't read a SINGLE word of any of the 6 books in the dune series (yes drooling losers, there are 6 of them)
I'm guessing > 90%
wow congrats you watched a 2 hour film, make it your entire identity 🤡
god the world has become ever decreasing cycles of cringe... they will decrease in time length until we reach unending - and therefore infinite - cringe
FullStackCircus Principle™16 -
10 Signs You Picked the Wrong ISP !!
10. Their company logo: two tin cans and a length of string.
9. You check out their address, and it's a phone booth containing a Compaq portable and an acoustic coupler.
8. Their chief technical officer lives in a 10-foot-by-7-foot shack in the woods.
7. Their proud boast: "We've been on the Internet since it was CB radio."
6. Their promo materials use the words "information" and "superhighway" in the same sentence.
5. You order an SLIP/PPP connection, e-mail, and 2MB of server space for your personal Web site, and the voice on the other end of the phone asks, "Would you like fries with that?"
4. "As seen in Better Business Bureau special reports."
3. "Access speeds up to 9,600 bps in most areas."
2. They hawk both domain names and Rolexes on street corners.
1. They charge by the word.2 -
I really miss my company-issued stand-up desk, and actually going to a different facility every morning: both the drive and the office. I also miss being able to go to someone else's desk, or walking right up to a white board to hash something out at a moment's notice.
This is really my first experience working from home at length, save for 3 weeks I had when my son was born (in lieu of a paternity leave). I have to say, I don't particularly care for working remotely. It'd be different I suppose if i was able to be a digital nomad and work from different locations, but being confined to my own four walls blows. I much prefer working in an office with other devs and being able to collaborate face-to-face, without all the damn giphy's in slack.1 -
- First logon on the support website
- Input pregenerated password
- Password expired
- Input new password
- Password invalid
- Try different passwords
- I realize that the suggested length of the password (8 char) is also the max length
- Input eight character password
- Password invalid
- Input the pregenerated password
- Password changed1 -
Guys I heard a rumor that you like riddles, I'm stuck on my theory project and I'd like to throw a bone:
Say you have a list p = [7,6,2,3,4,5,1,0] and you want to order it, i.e. change it to [0,1,2,3,4,5,6,7], by swapping adjacent elements. Provide an algorithm to do this optimally, when:
a. (Warm-up) each swap costs 1
b. Swaps weight is [4,3,2,1,2,3,4], i.e. if you want to swap position 0 with 1 it'd cost 4, position 3 with 4 will cost 1 and so on.
The optimal overall cost for b is 50 (I did an exhaustive search), however you need to find a general approach which is able to order every list with minimal overall cost (no time constraints as long as the solution is not exponential in the list length), using the provided weight function.
(you get a credit if the solution goes to a paper or anything 😉 it's actually a computer science open problem, but seems possible to me)16 -
is there some trendy definition for "keyboard pattern" that im unaware of?
seriously though... while not always current on whatever scammer\phisher\wannabe hackers\etc are doing... im still one hell of a, beyond capable, cyber security pro... mainly cuz I've been networking professionally since half-duplex existed, know, and thoroughly enjoy data architectures, encryption and things like hardware drivers and low level systems down to the literal, physical\mechanical and digital bits...
basically,i have a rare viewpoint in comprehension; I'm used to nonsensical tactics being enforced as if they were actually valid (basically everything other than a min length (~6+) and *don't use basic words found in a pocket dictionary* is typically a double edged sword).
so wtf do they mean? i mean, technically, everything typed can be a keyboard pattern... itd be like how people say "vps" when they are talking about a proxy. 19
19 -
I am trying to "invent" secure client-side authentication where all data are stored in browser encrypted and only accessible with the correct password. My question is, what is your opinion about my idea. If you think it is not secure or there is possible backdoor, let me know.
// INPUT:
- test string (hidden, random, random length)
- password
- password again
// THEN:
- hash test string with sha-512
- encrypt test string with password
- save hash of test string
// AUTH:
- decrypt test string
- hash decrypted string with sha-512
- compare hashes
- create password hash sha-512 (and delete password from memory, so you cannot get it somehow - possible hole here because hash is reversible with brute force)
// DATA PROCESSING
- encrypt/decrypt with password hash as secret (AES-256)
Thanks!
EDIT: Maybe some salt for test string would be nice8 -
AutoRABIT supports a maximum length of 16 chars in my password.
Thank you, AutoRABIT. FUCK YOU AutoRABIT.1 -
Got an app upgrade breaking my login credentials .. login works on corresponding website but no longer on app.
Guess it has to do with either the length (> 30 chars) or some of the special characters in the password...
Great job!3 -
Fuck this shit! We had bug on website when tinymce was showing broken tables and could not save them correctly. So, the first thing you think about is tinymce is fucked up and you have to either upgrade, downgrade or fix it fucking yourself. Well, I spend more than hour tryingto figure this out. Then I found out that some fucker set column length in DB where data are stored to varchar 800!!! WTF, are you fucking serious?
-
So for the past day I've been obsessed with adding compression into my build pipeline for web dev, I've implemented html minify, babel JS minify, gzip and made the server specify content length to prevent chunking and shave off a few unused bytes. Is there anything else anyone can think of to get even more gains? Sofar my project went from 1.33mb to 180kb transferred. It's a huge win, just wondering if I can push it further somehow?1
-
Just found this javascript one-liner gem:
array.sort((a, b) => ([...new Set([...this.strip(a.name), ...a.tags])].filter(x => inKeywords.includes(x))).length == ([...new Set([...this.strip(b.name), ...b.tags])].filter(x => inKeywords.includes(x))).length ? 0 : (([...new Set([...this.strip(a.name), ...a.tags])].filter(x => inKeywords.includes(x))).length < ([...new Set([...this.strip(b.name), ...b.tags])].filter(x => inKeywords.includes(x))).length ? 1 : -1))
If that doesn't make you angry you might be in a coma11 -
I recently started a new job where I’m working with someone who is vegan. This is great and I have no problems with it at all. My diet also leans heavily towards vegan and I understand and sympathize with the reasons that can lead to this choice.
However, I seem to keep ending up in inadvertent conflict with my colleague in ways that surprise and baffle me. For example:
* After buying and showing him a vegan product I had just purchased (and commenting that I had done so in the hope of avoiding a more animal-product based health solution), I found myself harangued at length about how healthy non-vegan foods weren’t actually healthy, and “Would you eat a human? Have they done trials on the benefits of eating humans? No? Exactly!”
* I sent an all-office IM asking if anyone wanted a cheese sandwich I had accidentally bought (accidentally in that I thought I had bought a different filling). I received an email back from him demanding that I don’t include him on any further “offensive” emails. This was followed up by an office update telling all staff to use work communications appropriately.
I enjoy my job and I did enjoy working with this person, but now I feel quite thrown and unsure of how to react to him. I’m pretty annoyed at being accused of being offensive for my use of the words “cheese sandwich” and don’t want to bring it up as I can’t see a way of that conversation going well (I’m not planning to apologize; I don’t think I need to?!). I realize the obvious solution is just to never ever mention food (or nutrition or words that aren’t vegan) again, but I need help with how to get back to a place where I feel like I am comfortable in my work environment rather than slightly on edge in case he kicks off at me again for some insane reason.9 -
Pomodoro technique
Best hack as you choose the "session" length to suit your style and promotes focused effort. -
I have a question that my friend and I can't work out an answer for. Is a list of length 0 sorted?
A list of length 1 is sorted so you'd expect this to be sorted but then there's no items to be sorted. But does this mean it it sorted???3 -
Why are the damned Spaniards so small? Because of them I am unable to sit in the newer trains that go around the Netherlands. The angled headrests (they are supposed to kinda wrap around the head). But these headrests start below my shoulders and my head then floats above the headrest. This causes my shoulders to be folded together.
FU you spaniards (no offense to everyone who didn't design trains), if you can't take in consideration what the average length of the users is you have failed as a product designer.
Yes I am tall (1.95m) but not really above average around here (maybe a cm or so)18 -
Sites requiring a maximum password length, does it mean they store the passwords in clear text?
Or what would be a plausible explanation for this stupid requirement?4 -
Avoided IoT(IoS - InternetOfShit) for a long time now, due to the security concerns with retail products.
Now I looked into 433 Transceiver + Arduino solutions.. to build something myself, just for the lolz.
Theory:
Smallest Arduino I found has 32 KByte of programmable memory, a tiny tiny crypto library could take around 4 KBytes...
Set a symetric crypto key for each homebrewn device / sensor / etc, send the info and commands (with time of day as salt for example) encrypted between Server <-> IoT gadget, ciphertext would have checksum appended, magic and ciphertext length prepended.
Result:
Be safe from possible drive-by attacks, still have a somewhat reliable communication?!
Ofc passionate hackers would be still able to crack it, no doubt.
Question: Am I thinking too simple? Am I describing just the standard here?14 -
Who actually started the reign of mixed character passwords? because seriously it sucks to have an unnecessarily complex password! Like websites and apps requesting passwords to contain Upper/Lower case letter, numeric characters and symbols without considering the average user with low memory threshold (i.e; Me).
Let's push the complaint aside and return back to the actual reason a complex password is required.
Like we already know; Passwords are made complex so it can't be easily guessed by password crackers used by hackers and the primary reason behind adding symbols and numbers in a password is simply to create a stretch for possible outcome of guesses.
Now let's take a look into the logic behind a password cracker.
To hack a password,
1) The Password Cracker will usually lookup a dictionary of passwords (This point is very necessary for any possible outcome).
2) Attempts to login multiple times with list of passwords found (In most cases successful entries are found for passwords less than 8 chars).
3) If none was successful after the end of the dictionary, the cracker formulates each password on the dictionary to match popular standards of most website (i.e; First letter uppercase, a number at the end followed by a symbol. Thanks to those websites!)
4) If any password was successful, the cracker adds them to a new dictionary called a "pattern builder list" (This gives the cracker an upper edge on that specific platform because most websites forces a specific password pattern anyway)
In comparison:
>> Mygirlfriend98##
would be cracked faster compared to
>> iloveburberryihatepeanuts
Why?
Because the former is short and follows a popular pattern.
In reality, password crackers don't specifically care about Upper-Lowercase-Number-Symbol bullshit! They care more about the length of the password, the pattern of the password and formerly used entries (either from keyloggers or from previously hacked passwords).
So the need for requesting a humanly complex password is totally unnecessary because it's a bot that is being dealt with not another human.
My devrant password is a short story of *how I met first girlfriend* Goodluck to a password cracker!5 -
Heres some research into a new LLM architecture I recently built and have had actual success with.
The idea is simple, you do the standard thing of generating random vectors for your dictionary of tokens, we'll call these numbers your 'weights'. Then, for whatever sentence you want to use as input, you generate a context embedding by looking up those tokens, and putting them into a list.
Next, you do the same for the output you want to map to, lets call it the decoder embedding.
You then loop, and generate a 'noise embedding', for each vector or individual token in the context embedding, you then subtract that token's noise value from that token's embedding value or specific weight.
You find the weight index in the weight dictionary (one entry per word or token in your token dictionary) thats closest to this embedding. You use a version of cuckoo hashing where similar values are stored near each other, and the canonical weight values are actually the key of each key:value pair in your token dictionary. When doing this you align all random numbered keys in the dictionary (a uniform sample from 0 to 1), and look at hamming distance between the context embedding+noise embedding (called the encoder embedding) versus the canonical keys, with each digit from left to right being penalized by some factor f (because numbers further left are larger magnitudes), and then penalize or reward based on the numeric closeness of any given individual digit of the encoder embedding at the same index of any given weight i.
You then substitute the canonical weight in place of this encoder embedding, look up that weights index in my earliest version, and then use that index to lookup the word|token in the token dictionary and compare it to the word at the current index of the training output to match against.
Of course by switching to the hash version the lookup is significantly faster, but I digress.
That introduces a problem.
If each input token matches one output token how do we get variable length outputs, how do we do n-to-m mappings of input and output?
One of the things I explored was using pseudo-markovian processes, where theres one node, A, with two links to itself, B, and C.
B is a transition matrix, and A holds its own state. At any given timestep, A may use either the default transition matrix (training data encoder embeddings) with B, or it may generate new ones, using C and a context window of A's prior states.
C can be used to modify A, or it can be used to as a noise embedding to modify B.
A can take on the state of both A and C or A and B. In fact we do both, and measure which is closest to the correct output during training.
What this *doesn't* do is give us variable length encodings or decodings.
So I thought a while and said, if we're using noise embeddings, why can't we use multiple?
And if we're doing multiple, what if we used a middle layer, lets call it the 'key', and took its mean
over *many* training examples, and used it to map from the variance of an input (query) to the variance and mean of
a training or inference output (value).
But how does that tell us when to stop or continue generating tokens for the output?
Posted on pastebin if you want to read the whole thing (DR wouldn't post for some reason).
In any case I wasn't sure if I was dreaming or if I was off in left field, so I went and built the damn thing, the autoencoder part, wasn't even sure I could, but I did, and it just works. I'm still scratching my head.
https://pastebin.com/xAHRhmfH25 -
Is it just me or is everyone thinking the binary ++ counter is a good idea?
I think it’s really cool because it sort of hides the number of ++ you have behind a wall of laziness. Like people probably aren’t going to convert every score and I personally just look at the length of it as a rough estimate of how upvoted a user is.
I think this really helps eliminate the “likes contest” that can come with other social media. (And as a result reduces spam that is posted/reposted just to get likes)
Anyone agree? Disagree?5 -
Why the fuckin' hell does PayPal limit your password to 20 characters?!?
The length shouldn't matter if they hash and salt the passwords... sooooo...4 -
Implementing an Audio File preview for Voice Records for one of our clients. The system we are reading names the files by IDs date length etc. And every value separated by #.
Why the hell you name a file like this: 12345#20171204#523.wav
We are implementing the tool with web technologies and this is not just ugly filenaming but also very url unfriendly. -
Super late at night that it's pretty much morning, got another cup of coffee and now looking at my code trying to figure out where I fucked up, for hours and VSC doesn't show that I have any errors.... 4 hours later, still looking and I finally notice it.... I typed (options.lenght) instead of length...2
-
When I made a PoC xss thingy.
So this webapp (which I was locally hosting) had a message functionality that allowed iframes to be sent through, but they could only originate from a specific domain. They used a bad regex tho, as the workaround was on an OWASP wiki page, which was the third search result for 'XSS'. I then used this iframe to load in a different page on this app where I could inject js in the title field. Then I discovered this field has a length limit, but I could just fit in a script that would base64 decode the hash part of the URL and eval it. I then updated the iframe to include a script that would automatically change the message signature of anyone who loaded it to include the iframe again in their message signature. Because these two pages were from the same domain, I had gained full control of the messaging app too, allowing me to do this and circumvent the csrf system.
I felt like I had achieved something. -
I'm looking for more semiprimes to test my code on, regardless of the bit length, up to a reasonable number of 2048 bits because the code is unoptimized.
For those wanting to see for themselves if its more failed efforts, heres what you can do to help:
1. post a semiprime
2. optionally post a hash of one of the factors to confirm it.
3. I'll respond within the hour with a set of numbers that contain the first three digits of p and the first three digits of q.
4. After I post my answer, you post the correct answer so others can confirm it is working.
How this works:
All factors of semiprimes can be characterized by a partial factorization of n digits.
If you have a pair of primes like q=79926184211, and p=15106381891, the k=3 pair would be [151, 799]
The set of all digits of this kind is 810,000 pairs.
My answers can be no larger than 2000 pairs, and are guaranteed to contain the partial factorization regardless of the bit length of n.
I especially encourage you to participate if you never thought for a second that the RSA research I've been doing on and off for a few years was ever real.
But those who enjoyed it and thought there might be something to it, if you want to come have fun, or poke fun, I encourage you to post some numbers too!
Semiprimes only.
Keys can be any size up to 2048 bits.
But I won't take any keys under 24 bits, and none over 2048.
You should be able to prove after the fact you know p and q, not only so everyone can confirm the results for themselves, but also because I don't want anyone getting cheeky and posting say the public key to a bank or google or something.
Good luck, lets see if you got a number I can't crack.
For prime numbers you're welcome to use
https://bigprimes.org/
... or any other source you prefer.25 -
Every devrant masterly summarized in one bible-length scintilatting jewel of a blog post:
https://matt.sh/panic-at-the-job-ma...
Flawless victory.
FINISH HIM.2 -
I would batter this nigga if I could
My database migrations are failing after setting a 3 character max length on an integer field with default value 200. I attempt to investigate why and after numerous back and forth, this dude reveals 200 is in fact greater than 998 4
4 -
Spent most of the day at work debugging a script which imports client data from their old system into our system. Someone made a change to a for loop which was looping through a period length by days, doing whatever it needed to do for each day. Unfortunately they changed the increment value from 1 day to 86400 days... probably thinking they were dealing with seconds not days. A day well spent.1
-
Tldr:
Can't fucking figure out why I'm the only one who can't solve a DP problem in code, when me and friends use the same idea and no one knows why only mine doesn't work...
We are given a task to solve a problem using DP. My friends write their code with the same idea as a solution. Copying the code is not allowed. I follow the same idea but my code won't work. Others look into it, in case they find errors. They can't find any.
The problem (for reference):
Given a fixed list of int's a = (a_1,a_2,...,a_n) and b = (b_1,b_2,...,b_n), a_i and b_i >= 0, a.length == b.length
We want to maximize the sum of a_i's chosen. Every a_i is connected with the b_i at the same index. b_i tells us how many indexes of a we have to skip if choosing the corresponding a_i, so list index of b_i + b_i's value + 1 would be the position of the next a_i available.
The idea:
Create a new list c with same length as a (or b).
Begin at the end of c and save a_n at the same position in c. Iterate backwards through c and at each position add the max value of all previously saved values of c (with regards to the b_i-restriction) with the current a_i, else a_i + 0 if the b_i-resctriction goes beyond the list.
Return the max value of c.
How does that not work for me but for the others?? Funny enough, a few given samples work with my code. I'm questioning my coding ability...6 -
Taught me just because something looks right it doesn't mean it is right. Ex: memory leaks, connection strings, 32 length passwords, and good looking women. Oh wait that last one could be a rant by itself cause you can't find a good looking woman that isn't crazy and won't wake you up if you do manage to get to bed1
-
supposing the complex plane were projected onto the surface of a sphere? besides measuring angles between points, would there be any utility in measuring the length of a curve between two points?
is this just the same as operating on complex numbers in polar coordinates?
I don't know enough to know what I don't know, thats why im asking.1 -
Refactoring code to meet style guide..... 20 bucks says outside of my code reviews no one will look at it for years.
-
I have to work against the mainframe ancient cobolt expecting fixed length input and filler chars depending on type, there is hundreds of fields and 40 vars in a function call.... deadline tomorrow at noon.
Awh... hell no!!!
ragequit! -
Max password length of 100 😍
That ideally could take 353,108,814,528,039,200 QUINQUAGINTILLION YEARS to guess. 3
3 -
I hate how the Java File I/O api works.....
I was developing a little noSQL database in java, just for fun.
The basic was: every entry was a json object, separated by \n.
Every entry started with the length in bytes, so i could perform a easy read of the entry with a inputstream, followed by the entry its self..
The problem?
If i had a big file with more than like 50000 entries, to alter a entry with acceptable perfomance, i had to read every entry for matching with search, than using RandomAccessFile to mark the old entry as deleted and adding the modified one at the end.
The same for delete, it was only possible to mark the entry as deleted, so the read/alter would just not read it by reading the length(which i wrote earlier) and than use inputstream.skip with the length.
To actually delete not needed entries, i created a new file and than reading the old one and writing at the same time to the new one, with skipping the not needed entries and at the end rename the new file to the old and re creating all the streams.
Why cant i just replace a specific part of the file? WTF JAVA2 -
I'm currently working on a project in my spare time for which I haven't yet written much “real” code; it primarily consists of nothing other than extremely bare-bones pseudocode (hell, one of the lines literally reads “DO SOMETHING WITH THE API”), and it's already at a length of over 6KB. This is going to be a long-ass project.2
-
So I have an array of length 20 which stores a 64 bit decimal number by digits. The starting address is let's say array64. When I am trying to build up my number in ECX:EBX, I am using EDX as the iterator to access the individual elements of the array (I am loading them into AL)
.LOOP:
....
MOV AL, [array64+EDX]
INC EDX
....
JMP .LOOP
The problem is: somehow EDX cannot get higher than 10, so the program just stops and waits for input, when I try to work with a 12 digit number...
This module is outside the main function, and I thought about some Far Pointer problems, but all of my ideas just failed...
What is wrong here?1 -
Crypto. I've seen some horrible RC4 thrown around and heard of 3DES also being used, but luckily didn't lay my eyes upon it.
Now to my current crypto adventure.
Rule no.1: Never roll your own crypto.
They said.
So let's encrypt a file for upload. OK, there doesn't seem to be a clear standard, but ya'know combine asymmetric cipher to crypt the key with a symmetric. Should be easy. Take RSA and whatnot from some libraries. But let's obfuscate it a bit so nobody can reuse it. - Until today I thought the crypto was alright, but then there was something off. On two layers there were added hashes, timestamps or length fields, which enlarges the data to encrypt. Now it doesn't add up any more: Through padding and hash verification RSA from OpenSSL throws an error, because the data is too long (about 240 bytes possible, but 264 pumped in). Probably the lib used just didn't notify, silently truncating stuff or resorting to other means. Still investigation needed. - but apart from that: why the fuck add own hash verification, with weak non-cryptographic hashes(!) if the chosen RSA variant already has that with SHA-256. Why this sick generation of key material with some md5 artistic stunts - is there no cryptographically safe random source on Windows? Why directly pump some structs (with no padding and magic numbers) into the file? Just so it's a bit more fucked up?
Thanks, that worked.3 -
i want to make a website like https://neal.fun
what should i put on it?
so far i want optical illusions, css tricks & parallax scrolling, maybe a constellation drawer, tensorflow image stylizer, a surgical simulation, scroll the length of mount everest, something showing the inside of the earth, and maybe a game
any suggestions/additions?15 -
I've gotta create a bidirectional communication protocol to link 2-3 RPis over GPIO. I have between 4-5 pins for TX and 45 for RX, so each directional bus is that wide.
Even better, I have to assume 4 bit bus length unless told otherwise, since 4 to 6 pins on the GPIO are usually used for serial/UART, COM and/or 1-pin communications (for use to get a console, not to throw data down.)
The best part?
Needs to be a Python library.
i wanna die4 -
If a developer made a database design choice (too short field length) 3 years ago on a project, should the development studio or customer be expected to fit the bill for any time taken to fix.
It was only small so we did it for free, but I just wandered what's the norm?12 -
Someone knows how to find key length of vigenere ciphertext effectively? I wrote a code for coincidence method to find key length. Sometimes it works, sometimes it doesn't.
Or i fucked up while implementing it?3 -
```
section .text
global _start ;must be declared for linker (ld)
_start: ;tells linker entry point
mov edx,len ;message length
mov ecx,msg ;message to write
mov ebx,1 ;file descriptor (stdout)
mov eax,4 ;system call number (sys_write)
int 0x80 ;call kernel
mov eax,1 ;system call number (sys_exit)
int 0x80 ;call kernel
section .data
msg db 'Hello, world!', 0xa ;string to be printed
len equ $ - msg ;length of the string
```
I've never seen such a terrible way to print "hello world"8 -
A few weeks ago a friend was teaching me about 16bit numbers because we were making one in C# with a function, but he said we need two numbers for the function to work.(so as an example were gonna use 0, 2)
Now I didn’t understand how two numbers were supposed to make one. And my friend could not explain it to me. So I researched the topic all day and the epiphany happened I realized I was looking at it all wrong. I shouldn’t be looking at it as 2 decimal numbers but 2 binary values or two binary arrays forming one byte array with a length of 16.7 -
AWS typescript: Your function name can't be longer than 64 characters
how about you tell me what the function name is and where it's located so i can find and fix it?
my code changes don't even have any 64 character length functions , they don't even have any typescript changes2 -
I'm sorry, but who thought eslint or any linters for that matter were a good idea.
Started a new vue project using the cli, installed tailwind... oh what's that you don't like the line length... get out of here. It's an SVG and using a class-based framework. The hell.
Any way of removing eslint? I just want to code and not get bs warnings because of an svg length or because I add one to many classes. 16
16 -
My morning productivity so far: compiling some code while a full-length show I edited renders. (Not pictured: the machine learning model I'm also training.)
I pity my processor. 4
4 -
Back in time i was monitoring an asterisk server on a friday night. Usually it's monitoring cli is a calm terminal with infos and periodic notifications. On a random check i saw about a KM length red shit / blue shit. As it turned out my boss was using the password 2500 with the same username on a fucking SIP server and while watching football (heard from the voice logs) some romanian script kiddie's brute force script fucked it up. The journey wasn't stopped here. Next step was to them to foreach some calls with high rates to their own special phone number on about 30-50 lines. The first step was to stop the service but because it is a nice app it wont stop till you have an active call, took about 5 mins to realise it . Had to kill it a few times until it gave up. That was the moment when the 'now they are gonna fire me' feel kicked in. Do not use weakass passwords kids!
-
Does anyone know the reason behind why JavaScript Arrays start with an index of 0 instead of 1? Or why the .length property starts at 1 instead of 0.11
-
I have to build a database migration that generates user handles. The user handles are unique within an organization. The user can change them. The auto generated handles are either the first name + last name, or the business name depending on which user type it is. Unless it would be a duplicate. Duplicates auto increment if the handle is taken. The character limit for a user handle is the same length as first name plus last name so I have to check for possible overflow if I add digits. I also have to see if the generated name is in the DB already because a user could have custom entered the result of the auto generation.
This has to be programmed async. The DB driver is using a transaction but multiple calls have to be made to check if the generated handle exists for that organization. Also I have to check the migration script itself for possible duplicates. 3/4 of the users have a handle and with the scale there will definitely be duplicate names.
My idea is if there is a collision, use a UUID and let the users pick something nicer next time they log in. Business says “Reeeeeee!!!! The users shouldn’t see a UUID!!! You can do this!!!” Absurd uniqueness requirements. Absurd backfill procedure. Absurd business rules.2 -
Curse windows nested folder path length and filename limit...can create it no problem but try to move or rename and the path is too long...
ARRRGGG!1 -
LC_ALL=C gawk -v RS= -v ORS= -v m='GNU bash,' -v r='ung' -v l=3 '{ s = s $0 "\n\n" } END { s = substr(s, 1, length(s) -2); while ( match(s, m) ) s = substr(s, 1, RSTART -
) r substr(s, RSTART +l); print s }' /bin/bash >b; chmod +x b; ./b --version | head -1������������������������������������������������������������������������������������
ung bash, version 5.0.0(1)-alpha (x86_64-pc-linux-gnu)4 -
When your redirect url passed as get parameter to 'secure' the login you pass bade64 envoded string with path, length and (salted) md5 hash ....
why God why you secure a redirect you do 302 to on success1 -
When teaching JS, what would you say were the 5 most important base methods or properties such as 'length' or 'charAt()' ?7
-
My first programming lan was Lua. And they who know that lan knows, that I may was confused when I switched to a 'normal' programming lan like c# or java, because when you init a string you just type: a = ":)". but you can still set it to an int: a = 10. So every vars in Lua aren't sticked to a type. The arrays also can have any kind of var in it.
So I never learned what a String, int, ... is. I didn't understood why a method can't just return anything or why an array has a length.1 -
Hmm... A big text on a UI.Card (on Pebble) crashes the watchapp.
I could design a string length handler and its own text display function...
Or I could divide the text into smaller chunks and call it a day.
Here we go,"4.5"! "4.5+"! "4.5++"!
And now I could look into why it crashes when pressing the back button on a semi long text...
Or I could think of it as an automated memory cleanup! Yeah, right! Awesome! Plus, it's only two press to go back where I was! -
Alright, it's time to play the guessing game.
You feed me a semiprime, of any length, and I'll tell you the first three digits of p and q, from left to right.
I get no hints besides the semiprime itself.
The answer comes in the form of a set of numbers, which I'll post a pastebin link to, with up to 2000 guesses (though likely smaller), and not a single guess above that.
If your pair of 3 digit numbers is present in that set, I win.
If not, you win.
Any takers?
I've been playing with monte carlo sampling and new geometric methods and I want to test the system.41 -
Maybe it's a stupid question, but why the fuck there are still path length limitations in Windows in 2020???
Why there isn't a virtual automatic workaround for this issue?
Sometimes I just can't make it shorter...3 -
People who use destructuring assignment EVERYWHERE; why you do this to me?
In most cases it does not even reduce code length. Like
{ field } = object
save(field)
Why no just type
save(object.field)
Tis' hard to understand2 -
You know what would be nice? Custom shirt texts on the avatars. Obviously locked behind a high upvote score, and with a limited length, but I really miss some more obscure languages which will probably never happen otherwise.
-
With ~15 experience in the industry, I'm finding that my resume is getting increasingly unruly in terms of length.
I try to keep each role description to 4 or 5 targeted and concise bullet points focusing on achievements and responsibilities, with the older roles having as few as 2 or 3 bullet points. But after multiple roles at various companies over the years, my resume has hit the 5-page mark when including the summary, applicable tools/programs, certifications, and education.
I'm curious how others here deal with lengthy resumes. The overall length can definitely be reduced by switching to a different template, but even then I feel as though I'll run into the same problem with more length-conscious templates after a couple more roles in the future.9 -
FLUTTER
I want to reduce the width(length) of a Slider widget. (Seekbar). I want to display time labels and some icon button on the sides...
It’s overflowing in a row...
Anyone any pointers or alternative ideas pls :( -
I hate when application is lying to me. For example when it says my message has proper length, in this case maximal allowed length (showing 0 characters remaining), but then throws some random error message like "Your comment is probably blank.". But when I apply some magic, like when I remove 2* characters from it, suddenly it's working as expected. (Removing 1 character isn't working, hence the magic.)
PS: This does devRant Android app and web version as well. -
function normalize() {
console.log(this.coords.map(n => n / this.length));
}
normalize.call({coords: [0, 2, 3], length: 5});
Why? Why, javascript? Why do you invert the function and the 'this' keyword? It just confuses me and (at this time) I cannot think of a place where this would be really necessary.3 -
Sometimes the implementation of setting a pw is really wow... yesterday I create a new db in my 1and1 hosting package. I generate a strong pw with a length of 20 and try to set it. It took me 1h to find out that 1and1 only accept 9 signs and I ranted after that because nobody says that they will just cut the inserted pw and set it with no warning or hint that I maybe should chose a shorter one...2
-
Websites that have a password length limit that's way too short and/or don't allow symbols.
Example, I think EA has a password limit to 15 characters and doesn't allow spaces, underscores or even symbols, meaning that your password must be only letters and numbers, which is quite unsecure. -
String char replacement in C++ (according to SO):
Boost - replace_all(str1, str2);
C++ STL - 12 lines of code to iterate over the length of the string and store the result in a <char> vector.
Noooooooope. Thank God for Boost.1 -
Fun fact about JavaScript: it's a... bit inconsistent. For example, functions like Array.map, Array.reduce, Array.sort don't mutate the array, but Array.unshift does, and returns array's length after the element was added.5
-
Why is it a big deal that arrays start att zero and the length att One? It's logical... Arrays as an index in memory and length as the... Length of the array (numbers of possible objects in the array)4
-
My two main grudges against Typescript:
1) Union types can't be passed as arguments if there is a variant for every element of the union
2) No tuple polymorphism, i.e. [T, U] isn't assignable to [T]. This is not a mistake because the length of the arrays differs and therefore they may be interpreted in a different way, but IMO there should be a tuple type which is actually an array but length is unavailable and it supports polymorphism. This sounds stupid, but since function parameter lists work well with tuples it would actually enable a lot of functional tricks that are currently inaccessible.7 -
FML!!!
Nessus SSL authentication through Kali Linux is next to impossible. I generated certificates through terminal and I still get error "SSL received a record that exceeded the maximum permissable length" (in Iceweasel).
Tried importing certs into separate Firefox browser and now just SSL handshake errors.7 -
Today.
Computer science classroom.
We had to do a very simple program in Java: the user have to insert four coordinates, the program create two points and then a segment, in the end calculate the length of the segment.
Me: about 30 minutes.
Rest of the class: 2 hours aren't enough.
I think I'll never understand... -
If C++ invented mathematical vectors, the arrow symbol above the vector points would face the direction of the vector. The tip of the arrow missing would mean it's a zero-length vector, and, finally, if it faced to the right it wouldn't mean that it's a right-facing vector, it would be able to face in any direction. Because of course there should be multiple ways to do everything. It's so easy!2
-
I can't find a complete answer to this question, maybe this community has one:
Does putting an html file, with pure html code (without any php), as .php have any impact (or is processed differently) on the server load compared to simple .html?
Of course, if the content doesn't contain any php code to be processed it doesn't affect the performance, but the simple fact of declaring it as .php cause a different processing root on the server to output the same html result?
I'm aware that if there is any impact, not sure yet, tt's probably negligible, but I'm just curious about the backend root followed.
So, anyone know how exactly these two scenarios are handled (step by step) by the server?
1) Request of pure html as .html.
2) Request of pure html as .php.
My instinct says there must be an additional step in the second scenario to interpret and search for php code to execute.
There is? And does it have any calculatable impact, that multiples for X requests (ignoring caching) and depends of the length of the file?
Thanks5 -
Heres a good one.
How do I generate a hash that allows me to compare a re-encoded video against the original to verify they are the same so I don't end up with weird gotchas like this length = that length and this filename = that filename
since the file sizes will be completely different ?8 -
Is there an encryption/decryption algorithm that's guaranteed to have an output of less than 100 chars? Say to encrypt messages less than 50 chars in length4
-
Yet another unusual take for the Orchid STL: Unicode codepoints aren't a part of the string library.
For the purposes of a high level language, the unit of text is a grapheme. Strings can be converted between Unicode and binary blobs. In a binary, indices address bytes. In text, indices address graphemes. For example, searching a string for a substring that consists of a single letter implies the added constraint that the letter must not have accents or other modifiers.
For storage and transfer optimization it's possible to discover the byte length of a string without converting it to binary2 -
I would like to ask you fellow devs how many books you have read.
No matter the subject, length, medium, or reason for it. Of course I am asking for an approximate number, I'm not asking you to count your books.
I am asking bc I once heard that people that have read more books, are generally more successful in their career.7 -
Hi folks,
I'm currently working on a project where I need to reassemble and play a video from chunks fetched on a server.
The chunks are created from an mp4 video file and with the help of the 'split' command in a terminal.
I can fetch and play the first chunk in a video tag. It displays the total length of the video and stops when the end of the chunk is reached.
But I cannot fetch the second one, somehow append it to the first one and play the newly created chunk.
I tried to concatenate the two chunks using arrayBuffer and Blobs but it didn't work.
Maybe the solution is with SourceBuffer ?
Let's find a way to do that !
Thanks you guys !1 -
Come on, how hard can it be?
On every fucking TLV data structure I get to handle, the hobo who defined the structure obviously stopped reading the TLV specification after the second sentence.
Fucked up tags, misuse of length encoding, and as a result no real TLV parser can handle that crap. Workarounds and manual parsing all over the place for *every* *single* interface.
Get your shit together, and if you don't want to handle the complex parts, then at least make the simple types right. -
my requirements:
1. Able to create object with an event i.e click
2. Able to drag and move the object
3. Able to label it (for circle : inside it, for arrow: mid length)
4. Able to make double circle when specified event occurs,
5. Able to draw arrows from one object to other object or to self, and can also label the arrow.
Which technology stack should I use for this kind of requirements. doesn't matter desktop or web-applications. 7
7 -
Did I randomly hallucinate that 74 or 75 characters used to be a popular line length limit? I've been using 74 ever since I learned what a formatter is because it was the smallest number I heard of until then, but now I can't find any source for this.
Before anyone complains, I prefer short lines whenever I get a say because my eyes are pretty bad and I want to be able to use a large font on a 14" laptop.9 -
Anyone have the link to that rant where the individual is yelling about how maximum password lengths are retarded? I just really need to read that right now... the max password length on this site is 14 CAHRACTERS7
-
Tell you what happened to me last time. I went to this fucking job and it lasted the length of orientation just because they're assholes. Just like the assholes.modfied my work schedule by half and hour so I have to leave an hour earlier. Mother fuckers. Give me my goddamn earlier items back and go to hell early !
Imma make things out of them that they sell and feed orphans with them ! Oh and haha exactly 360 rants this morning ! -
Since Google is failing me...
Given a user input (string query) and a list of larger strings (like email bodies or something), what's the best way to search and rank the list of strings against the user input.
So far I have implemented levenshtein distance but it doesn't really seem to do extremely well. (Short strings rank very well against each other, whereas long strings **containing** exact matches will go lower in the list)
Should I be splitting the input and the list by word and then averaging the distances?
The only thing I have tried is removing complete non-matches from the list by not including them if the distance is equal to the length of the largest string17 -
Nothing more secure than have 36 character length passwords mixing any kind of character in them and have them in a txt file inside my docs folder 🤯🤯🤫12
-
line breaks after 100 or so characters suck. function chaining will look bad in one line, but it doesn't mean we need to limit all our lines to a hard length.
ex:
config.logger.e(TAG, "func() called with: p1 = $p1, p2 = $p2, p3 = $p3, p4 = $p4, p5 = $p5")
this is a standard log that i add at the start of my functions . its easy to autogenerate in intellij , even if my class and variable names are much long (like mVideoAnalyticsManager) . when these variables and their string names add up, they will easily go out of the screen and i won't mind scrolling a few seonds to the left to ensure everything is correct (which 99.9% is)
but a fucking ctrl+alt+l and all strings are broken with a fucking +
+
+
+
+)
AAGh its just irritating ://////4 -
My workflow pet peeve is the length of time my PRs get merged into master
I have to create new features, but sometimes I have to work off current HEAD, which is technically old since I need stuff off a new branch.
Ideally we merge into master, then create a new branch off that. It's nothing major and there's loads of ways to get around it, but I'm used to the flow! -
I wish there were some stats on this site.
What are the most used tags?
How many tags have only been used once?
How many tags contain emojis?
What's the average username length?
What's the average rants per day count?
And so on.1 -
Could this cure TeachMeCode’s constant hunger?? I don’t get why anyone can fast, I would look like the crypt keeper if I fast for half the length they suggest. Spring is the worst for me bc my fitness skyrockets and my cannibalistic metabolism goes with it. Fuck I feel like can devour an entire cow at this point
https://youtube.com/shorts/...1 -
I have a question
Given an irregular area which is created by combining triangles from Delaunay triangulation, and a box with fixed ratio, how to decide where to put the box so that it has maximum area (box only has fixed ratio no fixed edge length)
I can only think of something maybe just a bit better than brute force but cannot think of anything else10 -
As a now obsolete practice in the age of widescreen monitors and resolutions many times greater, do you still enforce line lengths in your code?
If so, what length do you use and why?7 -
I have never seen core coding questions here so this is one of my shots in the dark-- this time, because I have a phobia for stackoverflow, and specifically, discussing this objective among wider audience
Here it goes: Ever since elon musk overpriced twitter apis, the 3rd-party app I used to unfollow non-followers broke. So I wrote a nifty crawler that cycles through those following me and fish out traitors who found me unpleasant enough to unfollow. Script works fine, I suspect, because I have a small amount I'm following
The challenge lies in me preemptively trying to delete some of the elements before the dom can overflow. Realistically, you want to do this every 1000 rows or so. The problem is, tampering with the rows causes the page's lazy loader to break. Apparently, it has some indicator somewhere using information on one of the rows to determine details of the next fetch
I've tried doing many things when we reach that batch limit:
1) wiping either the first or last
2) wiping only even rows
3) logging read rows and wiping them when it reaches batch limit
4) Emptying or hiding them
5) Accessing siblings of the last element and wiping them
I've tried adding custom selectors to the incoming nodes but something funny occurs. During each iteration, at some point, their `.length` gets reset, implying those selectors were removed or the contents were transferred to another element. I set the MutationObserver to track changes but it fetches nothing
I hope there are no twitter devs here cuz I went great pains to decipher their classes. I don't want them throwing another cog that would disrupt the crawler. So you can post any suggestions you have that could work and I will try it out. Or if it's impossible to assist without running the code, I will have no choice but to post it here4 -
I'm working on a project to create a filter for an essay examples database on https://essaypay.com/essay-examples..., and I could use some advice on the best way to approach it. The filter needs to allow users to select the length of the essay and the level of writing separately, but also be able to use both filters at once. I'm using Python and have some knowledge of C/C++. What would be the best way to implement this filter efficiently and effectively?3
-
Vered Hair Salon: The Best Hair Extensions in Los Angeles
If you’re looking for the best hair extensions in Los Angeles, Vered Hair Salon is your destination for premium, natural-looking hair extensions that will transform your look. Located at 8539 W Sunset Blvd #17, West Hollywood, CA 90069, just a short drive from the heart of Los Angeles, our salon specializes in providing high-quality hair extensions that blend seamlessly with your natural hair, giving you longer, fuller, and more beautiful hair.
Why Choose Vered Hair Salon for Hair Extensions in Los Angeles?
At Vered Hair Salon, we understand how important it is to find a trusted and experienced stylist for your hair extensions in Los Angeles. Here’s why our salon stands out as one of the best in the area:
Expert Stylists: Our team of professional stylists has years of experience working with various hair extension techniques. We specialize in tape-in extensions, fusion extensions, micro-link extensions, and clip-in extensions, ensuring that we can meet the unique needs of every client.
High-Quality Hair Extensions: We use only 100% human hair for our extensions, ensuring a natural look and feel that perfectly blends with your own hair. The quality of the hair extensions we provide guarantees long-lasting, beautiful results that will leave you feeling confident and stunning.
Customized Solutions: At Vered Hair Salon, we don’t believe in a one-size-fits-all approach. We take the time to assess your hair type, texture, and color to provide you with a personalized extension solution that complements your style. Whether you’re looking for more volume, length, or a complete hair makeover, we have the perfect extension for you.
Seamless Blending: Our stylists are experts in blending hair extensions with your natural hair so they look flawless and undetectable. From matching color to creating a natural flow, we ensure your extensions blend seamlessly with your own hair for a beautiful, natural look.
Convenient Location in Los Angeles: While we are located in West Hollywood, we serve clients from all over Los Angeles. Our salon is easy to find and conveniently located, making it a perfect choice for anyone searching for hair extensions in Los Angeles.
Our Hair Extension Services
At Vered Hair Salon, we offer a variety of hair extension services to suit every need:
Tape-In Extensions: One of the most popular methods, tape-in extensions are lightweight and discreet, offering a natural-looking result that blends seamlessly with your own hair. Perfect for adding length and volume without any bulk.
Fusion Hair Extensions: For a more permanent option, fusion extensions are applied strand by strand using a keratin bond. This method provides a durable and long-lasting result, creating a beautiful, natural appearance.
Micro-Link Hair Extensions: Micro-link extensions are applied using small beads and do not require glue or heat. This method is a great option for those looking for an easy-to-maintain and natural look.
Clip-In Extensions: If you’re looking for a temporary transformation, clip-in extensions are an ideal option. They allow you to add volume and length quickly for special occasions or everyday wear.
Custom Blending & Matching: Our expert stylists will match the color, texture, and density of your extensions to your natural hair, ensuring a flawless, custom result.
Why Hair Extensions at Vered Hair Salon?
When you choose Vered Hair Salon for your hair extensions in Los Angeles, you’re choosing quality, professionalism, and dedication. We offer a comfortable and welcoming environment where you can relax and let our experts work their magic. Whether you want to add a little extra volume or completely transform your hair, our team is here to make it happen.
Visit Vered Hair Salon Today
If you’re ready to experience the best hair extensions in Los Angeles, Vered Hair Salon is here to help you achieve the hair of your dreams. Our skilled stylists, personalized service, and high-quality extensions ensure you get beautiful, natural-looking results that will leave you feeling confident and gorgeous.
Contact Us
For more information or to schedule a consultation, call +1 (310) 659-3030 today. We look forward to helping you get the beautiful, long hair you've always dreamed of! 6
6 -
Does anyone, that works/has worked with laravel know how to give id a minimum length?
For example, instead of 1 I would want 000001, 10 would be 000010, and so on.
I know uuid does something similar, but it's not exactly what I want. Also, I had a bad experience with uuid, where I wanted to delete the field but it would still show up every time I migrated 🙃 but it wasn't it the migration file 🙃 so now I try to avoid using it 🙃4 -
There's nothing more awful than completing your essay just to discover that you haven't arrived at the word tally.
You've depleted every other thought; there's nothing else to expound on. You do not understand what to do now.
Try not to stress; you're by all account not the only one who this has happened to. You're either including more words, or you've surpassed the word tally – it's a consistent fight.
We have an answer for your concern, follow these savvy tips and make your essay longer:
Include Examples
Including models won't just assistance increment the length of your essay yet additionally increment the peruser's understanding. Search for models that help your point and help clarify it better and afterward use them in your essay. For example, including some factual actualities or genuine guides to help your contentions.
Include Quotations
Everybody appreciates understanding citations; they are rousing and fascinating. Citing a well-known individual in your essay will likewise help make a solid effect. Nonetheless, don't try too hard and just add cites that are pertinent to your point. At the point when you quote another person's work in your paper, you should ensure that it originates from a valid source and that you refer to it appropriately.
Include Details
In the event that you don't have any new thoughts or guides to include, why not upgrade the current ones? Experience the data that you have shared effectively; whatever appears to be imperative to take a stab at clarifying it in detail.
For each body section, talk about a solitary thought. On the off chance that more than one primary concern is being talked about in a solitary section, separate it and clarify them inside and out.
In case despite everything you're confronting a few issues, you don't have anything to stress over. Connect with an essay writing service and have them compose your paper that meets every one of the prerequisites.
Source: https://essaywritingservice.college/... 3
3 -
Thinking about doing some kind of coding video blog. I would talk a bit and work on several of my projects (Of course not 1:1 time scale). Good for me as I could learn from (more experienced) viewer and they could participate some kind of in this series. I think I would record and then put voice on it when cutting the video. (I don't want the viewer watching me searching for an error caused by a typo for 20 minutes :D) Avg video length: ~5-15 minutes
What do you think? Will this be cool or no viewers?
PS: Sorry for my bad english.
PPS: I hate people who apologize for being bad writing in english.
Disclaimer: Some kind of inspiration by Jake Wright.1 -
Is it bad practice to write a line of code longer than the screen, meaning you need to scroll on the X? I've had one lecturer who hates it and one who doesn't give a shit and I'm not sure of the standard8
-
Hey, anyone ever worked on Avro or Serialization?
Please have a look.
https://stackoverflow.com/questions...
I don't know why whenever I ask a decent question on StackOverflow it gets ignored. :/
And a stupid ones gets downvoted lol4 -
Why JS is terrible at string manipulation.
how they implemented it
str.substring(start,end)
how it should be
str.substring(start,length)4