Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "keys"
-
Me: *puts small piece of tape over webcam*
NSA: Okay guys, shut it all down. No way we can record from the microphone, log keys, access the file system, USB devices, network data or watch the screen. He did the tape.23 -
So I accidentally published my AWS keys to GitHub, stupid me. I realize this the next day.
$ git reset
$ git push
Reset keys in AWS
I was too late. Bot already stole the keys and started up 53 EC2 instances. Racked up $4000+ of compute time (probably Bitcoin mining, I'd assume)
4 weeks later, I finally have this shit disputed and settled.
Don't test with hardcoded keys. You WILL forget about them. Env vars always. That is all.30 -
"Can you give me an estimate on how long it will take you to fix this bug?"
"That's like asking how long it will take to find my keys."8 -
*Dev in his 40's from our counter-part office.
Me: Here's my SSH keys.
Dev: What's this?
Me: SSH keys. Give me access to the repository.
Dev: We don't use any version control here. Let's just use FTP or Remote Desktop and just download the codes.19 -
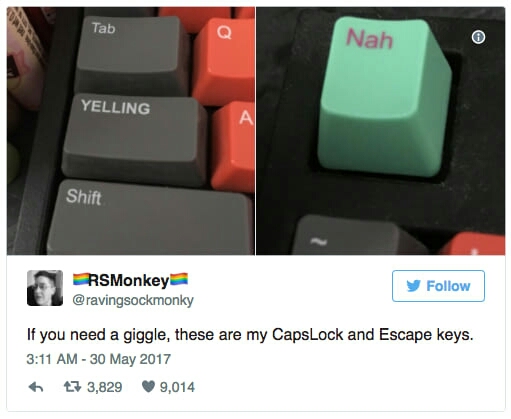
To the MSI genius that decided to put the < and } keys in two completely random and non-standard positions: 🖕🖕🖕🖕
 19
19 -
Microsoft is investing in Git, VSCode, Electron, Github, Bash-on-Windows. Things that decentralize and help prevent lock-in.
Apple is taking away the only universal cross platform graphics system (OpenGL), locking developers into Metal, and taking away our escape keys.25 -
Every computer needs a “cleaning keyboard” mode where the keys would be inactive while you wipe them down16
-
Dear me,
We have noticed you uploaded files to a public github with your API keys in plaintext.
Please proceed to bang head against desk until you have learned your lesson.
Sincerely me.16 -
Team Lead: Anyone has any concern on their tasks? I'll see what I can do to help.
Me: Yeah I'm afraid I would not be able to finish my task on time because of its complexity.
Team Lead: Try harder.
What's the point of asking? 11
11 -
Friend: Hey, I managed to build my own UI.
Me: That's great, which programming language did you use?
Friend: Filezilla.
Me: No, I mean the language. The language you code in to build your UI ?
Friend: Notepad ++
KILL ME.8 -
Dear outsourced developers. Don't send me your private SSH key by email. I don't need it, it allows me to access anything else you can access pretending I'm you, and it shows a misunderstanding of how SSH keys work. 🤦🏻♂️11
-
So Scratch is well crazy ass stupid, but for kids this is freaky awesome for a simple game builder that gets them interested.
This thing took like 10 minutes to make 😂
Move the witch with arrow keys and score points for catching the Ghouls. 10
10 -
Disabled fucking arrows keys in vim. Life is hell now.
I will be posting a lot more rants from now on as I am learning vim so bear with me. 19
19 -
we had this guy once, who we gave access to our private repo. everything's all good until we noticed that our amazon bill was USD 8,000+!!! we found out that lots of servers got created and that's bec. this guy forked our private repo and his fork was a public one. our keys were still not in .env files and were part of the commit so some bot got hold of it and accessed our amazon account. we suspected that the servers were used for bitcoin mining. anyway guy was fired on the spot and we also learned our lesson to keep keys out of repos.14
-
My coworker shared account keys of Amazon aws on a public repo at Github. Took me around 3 days to find out and about 20 ec2 instances were created and running by a hacker...6
-
Status update after my first day of my internship:
I realized I know literally nothing about SSH Keys.
Bye.6 -
When writing a JavaScript guide, please don't use emojis as keys in objects. Or anywhere else in code. Zoomers will think it's common practice.
Just because you can, doesn't mean you should.
Sincerely,
everyone24 -
When you get so excited you burst out signing "🎶MY CODE IS ON FIRE🎶"(Alicia keys "this girl is on fire" reference) forgetting your in a room with your fellow developers.....
5 minutes later there still laughing3 -
My colleagues broke down our AWS account by hard coding the AWS access API keys and pushing the same code to a public repository. This took down our system for nearly 3 days.2
-
Encountered this is my computer science lab.
One of the most useless keys. Majority doesn't know what it does. And now there's two of it xD 6
6 -
When you get fed up of using up and down keys to initiate commands, so you just create 2 extra command prompts and color code them so you know which one does what.
 5
5 -
So I am running this crypto project that has dynamically generated private keys for a wallet stored in a Redis database. Nowhere else. The keys are generated on the fly.
At the moment of the happening the wallet had over 3.000 USD on it. I am testing new code locally, supposedly on a local Redis DB. Of a sudden, my code wipes the crypto keys and it turns out that I was connected to the live instance. 😱 Better don't ask me how.
Shock of my life. You know, when you turn pale and dark in your eyes, blood stops in your veins and you just want to die? Worst-case scenario that could have happened. All that money lost in crypto space.
Turns out, my good Redis hosting company kept backups for the past 7 days. Keys restored. Happiest moment of my life.4 -
All my 'real life' friends like:
- Why do you need two monitors?
- Why does your keyboard has keys that do nothing when pressed?
- You have a controller on pc?
- Hehehe. I found a funny meme on 9gag -.-7 -
The designer of this keyboard should be shot on sight! A set of keys left of ctrl, shift, tab...except esc of course. Pure evil! I'm changing the volume, every time that I have to use shift... :/
 15
15 -
SQL gives me a hard on right now.
Two tables, 954 rows and 9414, connected via foreign keys and shit.
SELECT a_id,name,shit FROM table1 a JOIN table2 b ON a.id = b.a_id WHERE ((lower(name) LIKE '%lorem%') OR MATCH(name) AGAINST('lorem' WITH QUERY EXPANSION) OR name SOUNDS LIKE 'lorem')
and you got fuzzy search with resolved keys to another table in 0.047 sec, fuck me dude.5 -
I really miss the days when Windows XP had product keys on stickers stuck to computer cases. If I ever needed an XP product key, I just went to Staples and wrote one down from one of the machines on display.9
-
The use of git and understanding/working with foreign keys and performing (including the understanding) JOIN queries.
Also, it took me years and to understand OOP.
When think back to my code from before that, my brain spontaneously starts bleeding.6 -
Because of hardware failure we had to move some vpns from one datacenter to another.
The team of highly untrained monkeys at my hosting provider were hired to do this. First they ran backups of all the systems. Then they started the moving process. A few hours later they were done. We got an email everything was back online.
So we restarted all our processes and no data was coming in from our Raspberry's around the country. So we start a little investigation. What did these buffons do, they changed our rsa keys.
So we kindly ask them to put the old keys back so we do not have to fix 200 changed key warnings on systems that are not remotely accesible.
Apperently something that can't be done because their back up process is automated and always makes new keys.
Holy fucking fuck, whats the point in having a backup its not an exact copy. Is this fucking normal?
Now I will be spending the next few weeks literally standing in cow shit reconnecting Raspberry's.
Thanks a fucking lot. Not!4 -
I'm a web developer and know jack about hardware. My wife's personal laptop was going very slow so decided to upgrade to a SSD. How hard could it be?
Turns out to be very fiddly trying to disconnect and reconnect 4 ribbon cables. To get to the HD and replace it.
Restarted laptop and thought it was all good, but only certain keys worked and the mouse pad moved but didn't click?!?
Had to take it apart and reconnect twice more but now it's fully functioning once again.
Sticking to software in future. Massive respect to hardware specialists!6 -
omg apple does not like to make things easy! Trying to set up developer accounts for a company but a company can't be an agent? a team member who isn't an agent can't create certificates or keys?
Android development seems so easy and nice now6 -
The worst part about using the computers at my school is that my $200 mechanical rgb programmable keyboard with macro keys is at home.5
-
There's a special place in hell for those who don't provide keyboard shortcuts for commonly used commands.
It's shared with those who don't display the shortcut keys in the menus, so you can learn them.1 -
Fun fact: WASD keys are actually named after their directions
W — Wupwards
A — Am going left
S — South
D — Definitely right8 -
I've set up my server to only accept logins with SSH-keys, and permanently banning all IP:s that attempt login with passwords.
Now I can't stop watching the banned IP:s stacking up, it's like drugs to me.6 -
A few hours ago I decided it was a good idea to to clean up my keyboard. I did so and took a walk leaving the keys to dry.
After I came back I hoovered the -board and decided to put back the keys. I started with the special keys since they were the easiest to find (and some required a metal thing).
Now, I was quickly made aware of something that I had never known nor noticed before. Bear with me here as I'm not a person that cares too much about hardware unless I need to. (Hardware here meaning stuff like mice, keyboards, headsets, and stuff like that). But I learned that
Not all keys are the same size. They look really similar to someone like me. But I manned up and put the keys back.
A little under 1.5 hours later and I now posses a keyboard that is in uncanny valley. It doesn't feel like it though, and it shouldn't be that big of a problem since I never look at my keyboard anyway.
Messaged one of my m8's about and this was his reply
"nope
one kind per row
usually says the row on the underside"
Now fantasize about the elasmobranch fish which is characterized by a cartilaginous skeleton of which I am the proprietor at what he said. I pulled a key out and, sure enough, "C28 R1".
Now I am not sure about the 28th column, but it did fit in the first row.
Fuck me 8
8 -
I've been training a client for a few months now to not use Slack for sharing passwords and other secure materials.
I really thought I had made great progress. I even had him using a password manager. Then out of nowhere he sends the wildcard SSL key pair to me and a handful of other devs in a Slack thread.
At least we aren't storing important information like medical records. Oh wait, that's exactly what we're doing.6 -
Not being able to raise volume of my laptop with only one hand because the fn and f11 keys are just one hand and 3mm apart really kills me !3
-
!rant
!!pride
I tried finding a gem that would give me a nice, simple diff between two hashes, and also report any missing keys between them. (In an effort to reduce the ridiculous number of update api calls sent out at work.)
I found a few gems that give way too complicated diffs, and they're all several hundred lines long. One of them even writes the diff out in freaking html with colors and everything. it's crazy. Several of the simpler ones don't even support nesting, and another only diffs strings. I found a few possibly-okay choices, but their output is crazy long, and they are none too short, either.
Also, only a few of them support missing keys (since hashes in Ruby return `nil` by default for non-defined keys), which would lead to false negatives.
So... I wrote my own.
It supports diffing anything with anything else, and recurses into anything enumerable. It also supports missing keys/indexes, mixed n-level nesting, missing branches, nil vs "nil" with obvious output, comparing mixed types, empty objects, etc. Returns a simple [a,b] diff array for simple objects, or for nested objects: a flat hash with full paths (like "[key][subkey][12][sub-subkey]") as top-level keys and the diff arrays as values. Tiny output. Took 36 lines and a little over an hour.
I'm pretty happy with myself. 😁6 -
!rant
Damn github is da shit.
I'm sure all of those people who ranted about committing their passwords and keys will be happy
PS. I don't know if this is new but I'm happy either way :D 6
6 -
I hate those movies/tv series in programmer just tap on some keys and says it's done. this makes programming/coding looks so easy.
FUCK YOU MAN ITS NOT EASYYYY4 -
You know you're in the wronk place, when the prod sql table have 473 columns, 0 index, 0 keys and the frontend is made in ms access. And the only possible way to connect to the (virtualized server) database is through citrix...5
-
Vendor: We are very professional and follow best practices, we know what we are doing. You should trust us.
Also Vendor 5 mins later: DB passwords, API keys and SSH keys in repo. AWS Access Keys shared in screenshots in email.
Me: 😭6 -
Me: pipes something to less
Me: Find the info I need
Me: Press Ctrl+C to close less
*Nothing*
Me: Furiously smashes keys on keyboard
Me: Googles 'how to close less'
:q2 -
Wasted a total of 4 plus hours. Realized one of the windows registry keys I created wasn't working due to a typo. "comand" instead of "command". FML7
-
iEscape, the solution for missing keys in your MacBook Pro Late 2016.
Vim users, Apple have you covered! 3
3 -
While reviewing some DB work, I asked why most of the tables in the database didn't have indexes (some didn't even have primary keys).
He answered: "Well I thought they really didn't neeeeeeed them?"3 -
Sometimes my "L" keys stops working. Then I have to plug in another keyboard to press the "L" key there. After that I can unplug the second keyboard since the original key started to work again.7
-
This is the fucking data warehouse............
10 FUCKING INDEXES IN THE ENTIRE THING!
Btw...that includes Primary Keys 5
5 -
How the hell does PR containing production secrets and private keys gets 3 approvals and gets merged upstream? 😬 🥴5
-
My worst bad practice:
Saving my Linux Root SSH Keys on a Cloud Storage company.
Have them there, so I wont loose them ever. I password protected them, but you never know what the NSA/FBI/CIA can do 😉1 -
FML
brought my children to the childcare, went home and I am faced with A FUCKING CLOSED DOOR OF MY HOME WITHOUT ANY KEY and MY COMPANY NOTEBOOK, WALLET AND KEYS INSIDE!!! 😬7 -
Just noticed that the media control keys on my keyboard are recognized by the Google Play Music webapp
 3
3 -
I didn't need it so far, haha.
I thought it would be good some programmable keys to write System.out.println and other codes 🤔 5
5 -
People who savagely strike the keys on their keyboard when they type. Why??!! Do you find it more effective somehow?14
-
HOLY SHIT DIHDJEIDXJG I DID NOT REALIZE THESE TWO KEYS WERE HERE. HOW HAVE I BEEN SO BLIND. NOW I CAN MAKE MULTILIJE COMMENTS AT EASE. HRHDHXHZHSH. AHAHAAHHAAAHAH

-
Every time I finish a project and have spent days mashing keys and gulping coffee to bring a simple but yet delicate thought to life.4
-
Oh shit, a 16 yo guy come with a MacBook Air to repair.
“My mom hide the Mac in the oven. And my dad to preheat the oven...”
Really?? Yep, all keyboard keys jumped but he boots normally after disconnect/reconnect internal battery.12 -
At an auto parts store and was taking a look at the UI.
I FOUND A DINOSAUR!
More realistically I saw F20 as a shortcut key. How I know it wasn’t a typo? There was also F16. Wow. Even their keyboard stop at F12.
Talk about legacy program.2 -
Any recommendation for a decent mechanical number pad? It seems either too expensive or using knock-off keys...
 39
39 -
Note to my future self:
A 2048Bit SSH key is minimum,
4096Bit is good enough
8182Bit is too much
16364Bit... why do I even bother about this size5 -
So at the old job, i needed support for an issue relating to Amazon S3. We used a third party Python plugin for sending files to our buckets, but had some pretty severe performance issues when trying a 2-way sync.
Naturally, I sought help on StackOverflow, and was asked to share my config. Without much thought, I pasted the config file.
Next comment made me aware that our API id and key was listed in this config (pretty rediculous to keep such private info in the same file as configuration, but oh well).
I edited my question and removed the keys, and did not think about the fact that revisions are stored.
Two weeks later, my boss asks me if I know why the Amazon bill is for 25.000$ when it used to be <100$ 😳
I've never been so scared in my life. Luckily, Amazon was nice enough to waive the entire fee, and I leaned a little about protecting vital information4 -
So I have the new Mac book pro for 8 months now, always thought that the butterfly keyboard issue will never happen to me.
Until three days ago I noticed my space key is kinda sticky.
I have an external monitor so I don’t recall any time I spill water or food directly on the keyboard.
So I made an appointment for a walk in.
BUT this morning, I was like: man, fuck this shit and smashed the space key.
Now it’s fixed.
Good1 -
One time I took out a colleagues letter keys except the ones needed to spell freezer (in croatian) and left the message freezer on the keyboard, took the remaining keys, put them in a bottle which I filled with water and put them in the freezer overnight (left work the day before earlier than him).
A positive was that the keys were real clean. Negative was the rest of the keyboard was dirty :)
Was a good laugh, though.4 -
You look like someone who unironically puts “JSON” on their resume as one of programming languages they know.
You probably have casual pictures of Dan Abramov saved on your phone.
Now go finish your top 10 coding productivity lifehacks insta tiktok, or go adjust your standing desk one more time, or go type on your custom mechanical keyboard (which probably has different switches for functional keys. Should I call the keys “functional” if a person like this is the only person who presses them though?)
Yeah, you’re a rockstar. Yeah, that next medium article you’ll write is gonna make you famous. Yeah.13 -
My wife was done with exercises on her electronic 88 keys piano.
Me: I also know something nice.
Her: oh so?
Me: (repeatedly typing key #3)
Her: (thinking)
Her: C hacking?!5 -
What is the condition to join two tables ?
Programmer: primary keys match.
Non-Programmer: The tables height must match.😐1 -
I just managed to configure a second keyboard to map its keys to separate keycodes. Basically, I should be able to use it as a complete macro deck 😏 Thank god for Linux5
-
Loving everything about the new Apple keyboard except the cursor keys. Moving up and down is soooooooooo fliddly!
 17
17 -
I was deaf but now i'm half blinded ! :/
(Glad i know the place of the keys)
So boered cuz i cant code or even read a book!
FUUUUUCK !!!!18 -
When creating auto incrementing integer keys on a MySQL database, please mark then as unsigned, you don’t need a negative primary key 😞😞😞4
-
Fuck you windows 10. Fuck you private keys. Fuck you tortoise git. Fuck you git bash. Fuck you cygwin. Want 3x hours of my life back. Had an auth problem... Had to reinstall all the above on windows to connect to my private repo. Took me 5 minutes to connect after reinstalling all the tools. Grrrrrrr. And I'll never know why it wouldn't connect apart from fatal protocol error: bad line length character..I tried ever stack overflow answer... I nearly bricked my gitlab CE...and it was windows being a motherslut8
-
I really need to kick Tim Cook in the ass.
“Everything Works”, yeah tell that to your dead dog.
Debugging watchos experience:
I need to uninstall main app for watch app to register changes in code.
Xcode crashes during debugging.
Cannot SET custom keys in Info.plist, in watch target, ohhhh goood, but thats where app configuration is set, how and why do you care about simple string keys!!! What now i need to send that configuration from main app??
Tim Cook just go die please, you have ruined apple.3 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.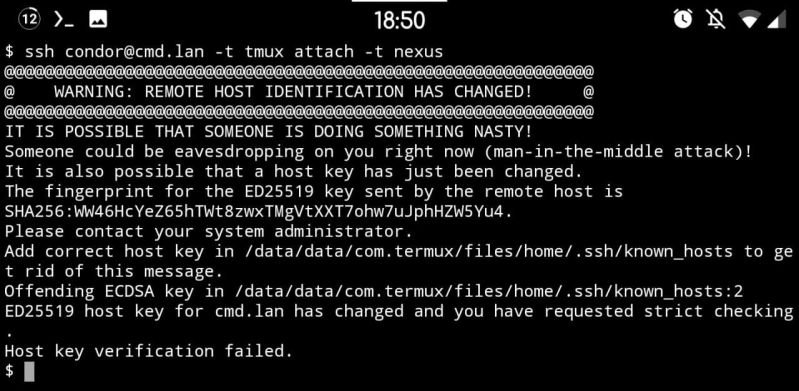 19
19 -
Next week, I'll be with a new company - this week I'm scouring the corporate laptop for all the places I stashed personal SSH keys and AWS credentials.1
-
"AI can code" is like "my dog can play piano". Yes, I have proof, look it's hitting the keys and we can hear a sound. Dogs can play piano. AI can code.6
-
What is the porpose of this key next to the left shift??? Instead of giving me a wider shift key, you gave me two forward slash keys... WHY?! I suspect Microsoft is behind that.
 24
24 -
My wife asked me if I could take a look at her keyboard because some of the keys suddenly had stopped working.
I checked the keyboard and saw that crumbs were literally blocking the keys. I gave it a shake, the crumbs fell out, and the keyboard started working again.28 -
So i just purchased the new Python Humblebundle, and don't need GitKraken Pro/Postman Pro, so if anyone has a need for it:
GitKraken Pro: hb-0h3rd
Postman Pro: https://getpostman.com/humblebundle...
:)1 -
MacBook Pro's (2017) keyboard is a fucking nightmare. So far Ive had more than 10 keys being detached from the keyboard. Luckily Apple has replaced those keys for free but this should not be a fucking problem on a $2600 laptop. Fucking hell.6
-
Does anyone else have a preferred side to use the Crtl/shift/alt keys?
I've almost always used the keys on the left side of keyboard.3 -
IT'S CAPS RANT TIME!
MYSQL ERRORS ARE SO USELESS! AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHHHHH
I JUST WANT TO ADD A FOREIGN KEY BUT 'Cannot add foreign key constraint' KEEPS COMING UP, AND THE STACK OVERFLOW ANSWERS INDICATE THAT IT COULD BE -LITERALLY- ANYTHING!
THIS IS OF COURSE, AFTER PHPMYADMIN GIVES ITS OWN ERRORS FOR TRYING TO USE THE DESIGNER TO ADD THE RELATION. IT ONLY WANTS UNIQUE FOREIGN KEYS, DESPITE ONE OF THE MAIN USES OF FOREIGN KEYS BEING MANY-TO-MANY AND ONE-TO-MANY RELATIONS!3 -
Ctrl and S will definitely be the first keys I have to replace...
Hitting them after every keystroke I make.
Safety first kids!2 -
After many teeth clenching failed deployment to production attempts and finally realizing I forgot didn't add ssh keys

-
neat, ansible control server on my phone, now I can transfer my playbooks and ssh keys and have it execute things on the go.
 5
5 -
*sets up digital ocean droplet
*adds ssh keys, enables private networking, hooks it into everything else
*adds roots in pycharm
*realizes I forgot to set it up with the one click app I wanted
*destroys droplet
*repeat2 -
my phone based set up. guess who provisions all the phones to our platform. then tests 9 million phones and takes the flack when users press incorrect keys or their internet goes down on site and it 'must be a provisioning issue'......this asshole.
 1
1 -
My boss's SQL schema has no foreign keys and he said he left them out intentionally because they should be handled in the application layer and they're a large performance impact.
This is a fresh greenfield project and he's already pre-optimizing for problems we don't have yet, on things that may or not be bottlenecks using ideas (e.g. foreign keys have huge performance costs on mariadb/auora) with no hard data or facts to back them up.
Let's start a new project with some technical debt!1 -
I noticed this morning that someone switched the keys around on my keyboard. I asked my coworkers about it and they said they did that as a prank went I was out on vacation. That was the first week of August and I just noticed...4
-
My CTO uses an array instead of objectto keep list of items with random numerical keys. I told him you’re creating multiple unintended undefined members in between, he said: yeah that’s how silly JavaScript is :-|2
-
Swapped the F10 and F11 keys on sister's keyboard. She can't figure out why F11 won't go Fullscreen5
-
>use atom
>move hand from home row to arrow keys to mous to home row
>start getting annoyed
>remember vim did this weird hjkl thingy I always wondered why
>discover atom vim-mode-plus
>fall in love with all the amazing things vim can apparently do5 -
I just want to thank Apple that has switched the Alt and Cmd keys. Every time I use an external keyboard I thank them...4
-
I noticed Facebook allowed vim keys navigation, I didn't realise this until I had scrolled through at least half a dozen posts.3
-
We had a system in the office were just pressed 0 on the keyboard to go back one step in the program. My kast day at the worn I removed all 0 keys from all the keyboards in the offfice and hid them.1
-
I went on vacation, and when I came back, they had removed all of the keys from my keyboard and put them in a bag, and placed the bag and my mouse and some other items in my overhead bin, and then they closed it and locked it, and my desk, and stuffed the keys up in the overhead bin, and this innocent little guy was hanging by a noose from the ceiling over my desk.
 9
9 -
Tarball of source code from a big manufacturer served on their open src page...
They forgot to delete the .git subdir!
Private keys and signing tools for everybody!!!!
P.S It's fixed by now, don't get your hopes up :P1 -
Question for vim veterans:
I am fairly confident with vim. I know a couple of commands like delete line, delete under cursor, copy, paste, undo and stuff like that.
So in command mode it's hjkl to move the cursor, which is a good idea because I won't have to move my right palm to the arrow keys.
However, in insert mode, if I needed to move the cursor, I would still have to move my left palm to the esc key in order to use hjkl. Why not just use the arrow keys then?8 -
I love when teachers know nothing about technology and when something closes, or in their mind “their pc breaks”, they hit a bunch of random buttons or keys and make it worse.2
-
How the hell some devs are releasing to production before passing to QA, Alpha testing, staging at least handle all type of errors and hide your API Keys.5
-
Typing email, tries to skip current song using keyboard multimedia key, ends up sending email... Welp Sharon I said what I said 🤣4
-
So, I'll explain how my day went with just 2 sentences.
1: Difference between crontab -e and crontab -r.
2: The keys 'E' and 'R' are right next to each other!
If you've understood what just happened, your next question should be "Jason, which environment?"
"PRODUCTION!!!" 7
7 -
Fuck..I lent someone my laptop and they returned it with a different power adapter and most of the keyboard keys don't respond when I press them. Now I can't code or do anything coz all I ever do is code, really.3
-
Well since vim & git has already been said gpg. you can use it as ssh keys and sign your commits to make sure nothing nasty is added to a git repo under your name
-
Dev: Woah look at this code! I might be a genius!
Also dev a few months later: Woah WTH is this shit? Was I totally dumb or what?2 -
Why do I have a hard time finding a new job when senior devs are not only changing the data model, but naming keys "key" and "value"!?
"Oh look, a SQL error."2 -
Nothing better than watching sshd generate a new set of keys every time you boot your 300Mhz ARM processor. Just because the entire filesystem is in RAM.2
-
Sooooooo…. The other day I committed a change with this message:
“Committing the ultimate sin in committing secret keys again however this repo is and will always be private and my pis will be hidden on my network so it shouuuuuuld be fine... right...”7 -
I've lived in this apartment for four years.
Tomorrow I'm moving out.
I've never ever lost my keys.
But today, the day before I'm moving out,
I LOOSE MY FUCKING KEYS!?!!?
What the actual fuck is this? If there is a god, which I'm quite sure there is not, fuck you!15 -
Diffi-Hellman is actual magic. You can exchange keys over an unencrypted channel and end up with guarenteed unique keys, on which you can start a secure channel
Like how??9 -
CSS is the keys to the gates of heaven. The problem is, the same keys also open the gates of hell.4
-
What is the maximum distance you can cover with your fingers on the first row of keys on your keyboard?
 6
6 -
Never had a truly bad experience with a designer but once one mentioned offhand that the unique keys that we were using to secure access to sensitive information should be only 4 characters long because it looks better that way...
I kept them at 161 -
How do you remove oily keys on keyboard?
What I’ve tried so far are rub it using a pencil eraser and clean it using cotton with alcohol.
Damn. I’m having a hard time to remove it.7 -
Today is a funny Monday: all the people at office forgot their keys at home (me included, also boss included) Until we can enter the office, I'm going to code at public library. At least I'm happy to carry portable Notepad++ in my pendrive!!
-
So a while back I got a new Mac book pro for work, and it was nice for a while, until the keyboard broke, so I gave it to apple so that they would 'repair' it, and although, they gave me a new keyboard, the keys were still garbage, and a while later broke again... and this is the second time that I've had to spend a week without a computer because of shitty butterfly keys... 😢😢😢2
-
The programmer is seated behind the piano.
He then looks at the piano keyboard and explains:
'The keys are quite uncomfortable, the distance from the up and down is very long...'
But it's awesome that the shift can be pushed by the leg.
Greetings from Estonia1 -
If you're having a bad day, think about the fact that BuzzFeed reporters have PGP keys for confidential tips4
-
and this is why you dont let a first timer build your database....
"has 34 column names in index key list. The maximum limit for index or statistics key column list is 16"4 -
My Top 10 most useless keys (#1 is worst):
1. Stop (the media key).
2. Pause/Break. (I understand this has historical usage, but I personaly have never used it.)
3. Page Up
4. Page Down
5. Scroll Lock
6. All those little shortcut keys along the top (above the F-keys) which open things like IE, My Documents, email etc.
7. All the modifier combinations of back tick (it in itself is useful, but WTF is a split pipe supposed to mean!? Or a ¬ !?)
8. Right Windows key.
9. Insert. Again, it has historical significance, but it's completely useless! Especially when you press it by accident.
10. The Menu key which opens the context menu.
I know some people will probably say 'the [blah] key saved my life once...', but I just rebind these keys with AHK. (http://autohotkey.com)7 -
Is it coincidental that the two most important keys that help us devs build our CVs, the C and V keys are inline on our keyboards? And look at that Ctrl key...That's what happens after too many rounds of copying and pasting...All hail Ctrl, C and V keys
 1
1 -
The only relationships that exist in my life, are the ones in my projects' ER diagrams. And they too are infected with foreign keys..!
-
Friend of mine messaged me about sites being down, of course Im at a family dinner with no laptop or ssh keys with me so no way to fix it!!!
Grrrrrrrrrrrrr6 -
Feedback time!
Really loving it here, thanks y'all!!
Scrolling using your volume keys is something I'd like, I've used it on another app (9gag) and I wish more apps had that feature (it can be enabled/disabled). Those are just my
$0.02
Thanks again! -
Accidentally using Resharper hot keys in Outlook (ctrl-enter) to autocomplete something and incomplete email is immediately sent out.1
-
Question for devs who work with databases. Do you constantly get tasks that involve joining data not on keys? Data from Exel files, other servers, etc where you have to try to match things on dates, amounts and other normal data.5
-
Google play music "I'm feeling lucky" radio has played 3 black keys songs in a row since I started this.. Coincidence?
 1
1 -
How do you keep track of your servers? their credentials/ssh keys, opened ports, services, IP, domain etc?15
-
Why there isn't a special key on the keyboard which includes "; + enter"?
Or in general a keyboard with special keys for developers? 🤔
e.g. open/close brackets with one key, or "/>" as one single key., or ") + {"5 -
i wanted to switch tabs in my code editor but i accidentally pressed the wrong shortcut keys and discovered a brand new feature in ubuntu....1
-
don't use natural keys
I accidentally registered with the NHS with the wrong date of birth. NHS records are keyed by date of birth among other things. This will have devastating consequences.8 -
CSS! after days thinking about this and using chrome dev tools to find the magic numbers ( thank arrow keys) i finally made this thing responsive. The magic is in 53px. Thanks to javascript i also did what seemed almost impossible for me in CSS. Phew!!!
 2
2 -
My keychain is getting heavy.
I have my house key ofcourse, then there is a short chain for my car keys, and last but not least 3 flash drives with different linux distributions -
There’s got to be a record to how quickly I’ve fucked something up. Most recent record? Twitter API, accidentally archived a glitch project that had my keys in it. 30 minutes.
-
Coding on a German keyboard suddenly gives you a reason to like those indentation-based languages without curly braces. And what about backticks and single quotes, they're for sure easier to find on an American ASCII keyboard. Fücking ümläüt chäräctersß!
Even worse on a Mac where it's not even printed on the keys what they do when holding shift, alt, or apple/clover/cringle keys. 24
24 -
Day two at my new job, they have not found the manual for their own tool yet, and i'm scolling trough 200 different keys to find the right combo just to start somwhere
-
I like the clicks of mouse, the taps of keys, sound of central cooling, the low tone conversations but if someone near me is in a long meeting and constantly talking, I NEED my headphones with music blasting
-
Is it good or bad that I forgot to push an critical buggfix to production just before I went home?
Hopefully I can update from home (think one of our servers has an backup of the ssh keys)3 -
dear ietf-people i want to thank you that tls1.3 is official. i know it was hard work to say just no to the doughbags and preventing that middleware and spyware manufacturers implementing static keys.
to make it short:
Thank you for your hard work -
fellow dev thought he was being clever, hiding his private ssh keys inside image files on a public web server...2
-
This weekend, I bought a mechanical keyboard to use at work. I'm worried the clicking sound will bother my co-workers around me. Does anybody know if bringing the keyboard to work will make people hate me?
It's a Logitech G610 with Cherry MX Red switches. I ordered some rubber o-rings on Amazon to dampen the keys. They should be coming in tomorrow. Should I risk bringing the keyboard into work before I dampen the keys?7 -
Oh look I'm posting the same thing again because all logical patheways lead to the same fucking place.
Sort of binary tree with a few keys added visualized. 7
7 -
How often do you guys use mouse/track pad ?
I started being a programmer, I like doing most of my work the keys way.7 -
Sometimes the "L" and "S" keys are a little TOO close to each other in Dvorak layout. Yeah, I just did this:
<button type="button">Select Ass</button>2 -
Don’t commit your terraform state to github please, especially if it contains over 20 API keys for various services, and database master passwords.
Not speaking from experience of having to do some frantic rebasing of someones PR *eye twitch*6 -
Wrote my first Medium article. What do you think about it? “Using UUIDs as primary keys” https://medium.com/@jdedek/...1
-
I got many reasons to hate my old Dell Studio-1557, but if there is one thing I love about it, it is its keyboard. I don't have much technical keyboard knowledge, but it's just comfortable for me. Wide keys and short keystrokes, no gaps between them (keys are actually sloped on the edge and fit together) and most importantly, no num pad.
So now that i feel it needs to be retired after 9 yrs of loyalty, i can't find a successor for it that have my old Studio's keyboard-feel. Most of laptops in the market have small keys with orthogonal edges and lots of space wasted as gaps between them (like new Dells), a useless (for me) num pad and worst of all, small miniature arrow keys (like thinkPad) and other navigations seems to be new designers fashion.
I'd be glad if some one introduce me a laptop with a similar keyboard to mine (in the picture)
Or what do you propose, should i care about the keyboard at all? are these new designs easy to take up with? wouldn't i suffer a keyboardalgia?
edit: no macs btw :) 4
4 -
Just removed an API key from one of my GitHub repos (yeah I know API keys don't belong there) and at the moment i pushed the corrected file, I got an email from GitGuardian that it discovered a key in my Repo although i deleted it. Anyone else experienced something similar?2
-
Need to write a query to find all scheduled reports, sounds easy, right?
Not in a system with over 1k tables all with obscure names and absolutely no foreign keys at all. -
#CloudStories
If its not working, try to open all ports on security group. You can then also give your home keys, your address and credit cards details to some random, homeless guy.1 -
vi keys suck, using hjkl to navigate the cursor is so unnecessarily unintuitive.
Who cares about the "muh homerow keys"15 -
Trying to clear the redis cache for like half an hour, wondering why the redis server isn't even being filled with keys...
Then suddenly, FUCK wrong port
2:30 AM is too late for me apparently :( -
Hello, can someone help me with this one ? I guess that the fucking SO elitist community would have beaten me to death if I asked this question.
I'm trying to create a relational table between a Tutorial object and a User object (to know which tutorial the user has access to) using Sequelize, and I figure out that I have two PRIMARY keys in my table. How is it possible ? UserID is also marked as Index.
The both keys are not Unique in themselves but their combinations are unique. 4
4 -
When you commit your repo with the configure file with keys and tokens and then need to delete the repo and start again1
-
How many secret SSH keys has Apple already captured with their shiny new iCloud Clipboard Sync on Sierra?4
-
Man, the technology we have right now. I'm watching YouTube live stream from some guy from Florida Keys.3
-
who else is kinda disturbed and somewhat annoyed by the new apple touchbar?
i just want my function keys back😩
wtf have you done apple😞5 -
When the buisness account manager asks you why the module isnt done, and doesnt understand that you cant test anything until he actually sets up the account, and gets you the development keys for the api you are supposed to integrate.
-
;-) this is "find a store" page of an International ISP.
they cannot even handle their google api keys.
how they can handle my data. 2
2 -
Had to change my password on my bitbucket cause a former employer was adding ssh keys.
Sorry pal, email notifications are rats -
It is horrible to navigate in android cause when u press the shift keys more than twice the sticky keys windows pops up. Frustrated but the one friend recommended me using fedora cause it's Linux based Android Studio works fast .and now I can press the shift keys as many times I want oooooya baby I can do that shit u windows3
-
Probably discussed somewhere in here but I wanna know which Cherry MX keys you guys prefer the most for programming.
Also any recommendations on a good keyboard or images from your keyboards would be cool ⌨️🖥️ #KeyboardsAreImportant7 -
is it just me or do other guys too just randomnly type whatever keys on the keyboard and Ctrl+backspace it to type something of meaning.
kinda like just stretching my fingers for keyboard.3 -
I think I'm just going to start handing out my house keys to random people. I mean, I've got nothing to hide and I'm not interesting enough for them anyway so...
Stupid conspiracy theorists...4 -
Be vary of entering commands from history (Arrow Up), especially if you did a destructive command not long ago.
Did this in a database for a game. I cleaned the clan tables not long before release. Then a short while after the release I searched for a clan related query and ended up clearing one of the tables again (ofc on autocommit). :|
So had to delete the related tables and notified people they had to claim their clan name yet again really quick.
---
Never had the issue on linux yet, but I'm usually vary when doing a generic destructive command (like "rm -r *"). The problem rarely happens with zsh (you can arrow up based on what you already typed) but I'm often still vary and prefix the command with a space to prevent it showing up in my history.6 -
this whole conversation is 4 hours before a UAT deploy.
PM: Do we have the new keys?
me: did they devs give you the new keys?
PM: no. what about the new URLs?
me: what are the new URLs.
she walks away. -
Does anybody use a 60% keyboard? I want to buy this, https://annepro.net/products/...
Arrow keys with press of fn and no distinct function keys, but it seems doable. Will I have problems using this with emacs?12 -
It reaaaally annoys me when my business logic is sound but the data is corrupted.
For example, find duplicates in a HashMap<String>.. but I didn't take into account the input could contain a space either before or after.. so I end up wondering: if a HashMap only contains unique keys, how come the count of items in the map is the same as the count of the input keys?! Well.. spaces were the culprit.
"12345" != "12345 ".. and therefore the Map sees it as two distinct keys..
What an annoying bug.
Lesson learned: 1) Sanitize input first and never trust it. 2) Never make assumptions15 -
That moment you realise your desk isn't as clean as everyone else's as you can tell what keys are used by dust cover level when your stickers arrive!
 3
3 -
Just swap these keys on a QWERTY keyboard layout and you have a programming QWERTY keyboard layout.
As few changes as possible from the original QWERTY.
KISS mode. 3
3 -
It feels kinda awkward to have a Facebook account only to request API keys, do not accept friend requests to not invade their wall with useless posts from apps you develop and be considered rude because of this! u.u
-
At the very start when I learned my first language. Didn't know where to find the "{" and "}" keys on the keyboard. Thought I would never be a dev, since I couldn't write a program without those keys.
Or when I didn't understand the notation of accessing values inside an array. Thought things like array[0] would do some magic to the array and didn't know how to access other parts of an array. I was following a book back then. -
My phone was stolen so that's why I wasn't getting here to rant about this, but today I had to make a back up and remembered.
adminer's export function doesn't export the tables in the correct order for import. Doesn't take foreign keys into account.
Dude, that's the whole point of a relational database, relations between tables; if you don't take that into account then what's the point?
Is this the same for the rest of database managers or is it just adminer? Please tell me this isn't normal.4 -
Software development is looking at the screen whole day, pushing keyboard keys sometimes and getting paid much for these actions.8
-
Started to value digital properties over material ones.
Examples:
- Own code / Git-Repos
- Own software / apps
- Crisp images
- Open source software
- Private keys equal to real ones 😉 -
Thus happened recently.
I installed vestas on our organisation's lab server. I was trying to add the user's key to gitlab.
But vestas doesn't support ssh keys by default, and i thought to go by https way
I don't remember my password, so instead of opening saved logins I was going to install gitlab on our organisation's sub domain.
Later I created custom keys inside the user's directory -_- -
The bugs that make you think are the best/worst.
Had a ghost foreign key constraint from a dropped table. Cant drop it from a non existant table.
Turns out the dev copied a file for the new table and since you can technically name those foreign keys anything you want, there were no errors when he ran it.
Also sloppy/overworked dev teammates are the worst...
Also I'm pretty sure rule 2 of programming is "Never Copy and Paste" -
JS has
dynamic object literal keys
String object literal keys
Why aren't template literal keys allowed, and _why_ isn't there a proper error message for them?7 -
A majority of the bosses/PMs/supervisors tend to be soo stupid and lack the knowledge of the actual problem's complexity so they expect you to hit keys and voila, project done.. It gets on my nerves big time.
-
There is nothing worse than trying to program while having RSI, it’s either you have your wrist support on and type slowly and hit multiple keys, or you have it off, type slowly and live with the pain3
-
!rant
Should I buy a mechanical keyboard? I've tried some basic Dell and so far they feel "sluggish", I can type faster on my laptop keyboard because I feel like "gliding between keys as I stroke"
Maybe I should try better ones?9 -
Keyboard decides to stop working, so I scrounge the office and find another new looking keyboard, which works as I was able to login to my Mac , only as I start typing further , half the keys down work 😂😂😂
-
Does anyone know a free cross-platform SSH app, that syncs everything from your PC to your phone, and supports SSH keys?14
-
Have been looking for a new keyboard but have not been able to find one, so which keyboard do you use for your daily work / programming. attach an image as well as model name and reasoning.
Im using Logitech G105 (due to macro keys)16 -
Anyone who uses vim + tmux? Did you remap the tmux keys to vim keys? How have you configured the keys to control tmux and get an efficient workflow?6
-
Setup SSH keys from your Dev machine to every development environment then configure a putty profile to use that key with your login.
-
Where do you find the willpower not to strangle people around you, especially shit managers and asshat clients, with a wired mouse and/or replace their teeth with the keys off a keyboard dipped in tobasco sauce1
-
It always seems for the first couple of days when I switch to a new keyboard, I feel like a monkey banging on the keys.
-
New data structure:
Map with repeated keys allowed. Values of repeated keys will be stored in an array.
Calling get(key) will get the array, pick a random entry in said array, and return it.
Use: Finding what the "number one rule of x," the "greatest thing ever," the "most unbelievable event," and more is. -
I hate Mondays...
So, Yours truly, the multilingual flightless bird leaves his apartment... Locks door... Fucking key gets stuck in lock (had some attempted home invasion attempt last year, left a few things bent).
The last thing I can use today, important project to work on with a deadline close enough to worry about.
I would say that's a classic Error 500 on login kinda situation.
The irony? I fancy myself a pretty good lock picker(A must have for an aspiring pentester) .
Luckily, a quick squirt of gun oil resolved that one... Seriously, how do people manage without a supply of tools and stuff?2 -
Protip:
If you start every YAML file with 400 spaces, you can check whether two keys are on the same level by shift-scrolling until one is at the left edge of the screen.1 -
When you work with a client who will only use Fireworks for graphics but you only have one dying old machine with a licensed copy and Adobe won't give you keys even though you bought them years ago (and can prove it!) and you can't buy new keys because they don't sell them and even if we had them we can't download it any more.
WTF Adobe!! It's a dead product! We don't want support or anything. Just give us the feckin' keys and the bloody installer!!4 -
One of my coworkers has a new MacBook with the new thin and weak keyboard. And this mf taps the keys so damn hard and my head is exploding every stroke. 😡2
-
Just tried some keyboard type practice. I'm stuck at around 30wpm (40 is average) and feel like I've hit a cognitive barrier. Whatever I do I mess up the R und T keys frequently as well as occasionally some other keys. I feel like a retard, as I sometimes need to rethink where the key is that I want to press, even though I've hit it like a thousand times before.
😪7 -
3 hours later I discover why my unset destroyed our json.
"When encoding an array, if the keys are not a continuous numeric sequence starting from 0, all keys are encoded as strings, and specified explicitly for each key-value pair."
Thanks obama.1 -
I used to learn touch-typing, but playing games without changing keys makes me forget it.
Why the fuck game markers set WASD as default moving keys? In this case people who play the game don't use the keyboard as they have to. Come on, let's use the keyboard in correct way guys...23 -
Why would these kind of libraries exists when Play Store explicitly warn about embedding secret keys in the app?
Also the joy when you see people approaching the fundamental problem as friendly as by a feature request
https://github.com/benjreinhart/... -
Only just spent an hour like a fucking retard trying every possible solution to something so basic even a toddler could fix it by mashing keys on the keyboard to finally realise I was working on the wrong fucking view!! 😀🔫
-
Key Generation.
Can anybody point to a informative page on how exactly the typical game keys in 4/5 char blocks are created and what data is held in the backend?6 -
Hi, so I am fairly new to GitHub and I just wanted to know how do you publish your code on GitHub Public Repo without disclosing your sensetive credentials like DB hostname, username and password, and other keys like Recaptcha secret?
My GitHub repo is connected to Heroku hosting so I cannot replace the keys with something dummy. It will fuck the production deployment up.11 -
Google: secure api keys in cordova
Results says I cant or I can but my brain dont understand the method
I'm banging my head against the wall aaaaaarghh3 -
What keyboard macros do you guys use when you have programmable function keys?
Also a funny little story that I just remembered. My brother used to have a key that would type his password cause he was THAT fucking lazy. He was writing an NPC for a private Ragnarok Online server that I was testing with a couple people. Apparently he had hit that function key in the middle of an announcement command.
So basically, everything went as planned, but then while announcing an event, it would announce his password to THE ENTIRE SERVER. Lucky for him, there were only three of us online at the time, and we told him as soon as it happened.2 -
Asdfghjkl keys does not work! Not git push, no save! Oh fuck my screen was locked so no on-screen keyboard! Mother fuck! Is this a quick solve for MBP? New keyboard cost £14.99 on eBay.2
-
How the does it make sense that I need .NET Framework to uninstall VS Build Tools? The installer runs, but then fails. Just delete your damned files and registry keys.2
-
Guys, can you recommend a free cloud server that can be used as proxy server?
I wanna keep my api keys safe.5 -
Do you know where to get Windows App Signing Keys for a reasonable price?
The cheapest ones I've found were still ~€150 per year, too much for a proof-of-concept :( Not signing the app is not an option...12 -
deadlines and digitalocean can suck my kiss. if deadlines are made by not talking to developer and digitalocean with its ssh stuff. figuring that out for 2-3 hours with new keys resetting passwords online console. then switched to freaking heroku, was up in 5 minutes
-
When you can't find your car keys and before you realise what's going on your immediate thought is to google then... 😒🙄
-
The moment when you scratch your mousepad or take off your keyboard keys, and you find out how horrible your living conditions are...
-
My fingers hurt while typing. I have a habit of hitting the keys way too hard and it's too hard to get rid of.
Should I buy those compression glove thingies? Which brand? Has anyone used them? Do they look cool?4 -
Happened today on the way home
---
*Doesn't feel keys in usual pocket*
Shit, where are my keys?
*Checks other pockets*
Oh, I put them where I usually put my wallet.
...
Shit, where is my wallet? (I forgot it on my desk 🤦♂️) -
> What's so great about Ag?
- ...
- ...
- ...
- The command name is 33% shorter than ack, and all keys are on the home row! -
Why, the , fuck , can I not set Chrome to use MRU when switching tabs on Linux!
The extensions don't work, and trying to set in in the shortcuts is impossible, because when capturing keys , the tab key is not suppressed! -
I guess it has to be keybase. Keybase chat is now my go-to web based chat.
Using NaCl keys makes life so much easier but you have the choice of using PGP if you need to for encrypting files/text. -
Coffee + Apple keyboard = I need a new keyboard. ISO 105 layout for Mac (CMD and function keys at the usual spots) are the main requirements. Any suggestions?4
-
What's with the resurgence of mechanical keyboards? Things are supposed to get better, not recycled.
This is technology, not fashion.
For me, the flat scissor switch keys on laptops have the best feel, speed and ease.8 -
fn key is the most evil shit key from hell
no matter where you put it, there is no layout in which you don't keep hitting it instead of something else.. It's not like you need most of the F# keys anyway you can just as well have the functional keys without this abomination.. or here's one: how about making a fucking mapping hm? To inventor of fn key: "You can suck my balls!"1 -
How do you guys prefer to hide the API keys you use in your (native) Android apps?
I'm an Android noob and the app I'm building uses some NLP services which are accessed through a key. I searched around and found a few techniques (obfuscation, serverside storage, etc.), just wanted to know what you folks recommend.5 -
Anyone who uses Vim as code editor?
I recently learned Vim and the more I explore it, the more I love it.
Is it really helpful to go through the pain of learning those shortcut keys in the long run?1 -
I know I haven't been productive lately but after two years of slowly build an upgrade to my app, I lost keys, signing certs and keystores :(
-
Fuck you Git bash
I did fucking add the ssh key to my ssh agent
I did add it to my GitHub account
you are dumb because for months until today you worked fine, now you look for ssh keys in a bullshit folder2 -
This could be controversial, but I think I prefer my Legion laptop's shallower, slightly softer keys over my ThinkPad's deep, harder to press, noisier keys5
-
TFW you realize that using git to track your dotfiles was a really good idea!
echo "Oh shit, I overwrote my ssh keys"
`git checkout .ssh/id_rsa`
`git checkout .ssh/id_rsa.pub` -
Anyone else having timeout issues connecting to git via ssh?? Had to switch remote urls to https on 3 different repos even with the right keys. Super weird.3
-
The Logitech MX Keys and MX Master 3 are the best keyboard/mouse combination on the market.
Hands down.7 -
I have the following scenario with a proposed solution, can anyone please confirm it is a secure choice:
- We have critical API keys that we do not want to ship with the app because de-compiling will give access to those keys, and the request is done before the user logs in, we are dealing with guests
Solution:
- Add a Lambda function which accepts requests from the app and returns the API keys
- Lambda will accept the following:
1. Android app signing key sha1
2. iOS signing certificate sha1
- If lambda was able to validate them API keys are sent back.
My concerns:
- Can an attacker read the request from the original (non-tampered) apk and see what the actual sha1 value is on his local network?
- If the answer to the question above is yes, what is the recommended way to validate that the request received is actually from the app that we shipped and not from curl/postman/script/modified version of the app11 -
Check the "Ctrl" keys on your PC. Tell me why the one on the left looks like you've been using that keyboard before you buy your PC and the one on the right looks like you just bought your PC3
-
Can you guys suggest me a good Bluetooth Keyboard? I am looking to spend less than $50 USD.
I like Logitech K380 but the keys are circle and I'm not sure if I'll like that.2 -
Editor [neovim](I know, I'm a degenerate) suddenly stopped responding to all mapped keys and after a while of closing and opening it, commenting out plugins,... it started working again. No idea what happened there!4
-
Is it possible to disable laptop original keyboard from within windows 7? My keyboard just gave up on me.Been trying to install ubuntu but my keyboard's not working i can't use the arrow keys nor tab..:-( .I am thinking of attaching my ext.usb keyboard when i setup boot.For the record the original keyboard has keys that auto clicks so very frustrating.Help guyz.3
-
No "Escape" and "Function Keys" on New Macbook Pro? Come on!!
As a Vim user, now I have to learn and adapt "ctrl+[" ASAP.
https://9to5mac.files.wordpress.com/...