Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "one key"
-
I'm the biggest dumbass, the laziest procrastinator I know of..
Joined devRant in June 2017, got eligible for the stickers in a week's time, sent a mail requesting them, but never received it. Given the size of our community, I thought I'm way behind in the list and probably receive them in few months. After a year, I totally forgot about it.
But, the colossal stupid that I am, had also lost the key to my mailbox (the physical one). I never cared about the lost key, because who sends post these days !!!
When I finally got a duplicate key for my mailbox after 2 years, guess what I found.. a first class international mail from devRant which arrived on July 2017 🤦♂️🤦♂️🤦♂️, couple of weeks after I originally requested
But, yay... I finally got them.. 16
16 -
Meanwhile at NSA:
Alice: Uhm... Bob? I lost my SSH key...
Bob: *facepalms*
Alice: ... but i still have the public key! Could you please recalculate the private one for me?
Bob: Sure, give me a second. I'll fax it to you when it's ready.
Me: *wakes up from nightmare*13 -
7 am. Dog wants out. I roll out of bed after trying to pretend I am dead.
Walk down the stairs to the side door. Half asleep and notice that the door has daylight shining through on the lock side. Didn't shut it all the way the night before. Walk outside. Dog does his thing. Turn around. Doors locked.
Fuck.
Go for my phone. In the house. Go for my keys. In the house. Fuck. Fuck a duck.
Start checking my windows. One opens a fraction of an inch. Doesn't do me any good. Dog is outside with me. Freezing his ass off. It's like 5 degrees here.
Both of my neighbors don't answer their door. Life flashes before my eyes. Put my dog in my jacket to warm him up. Little 15lb rat terrier. Not made for snow.
He's fine for now. I grab a piece of rebar from my backyard and lever my window a bit more open, busting one of the locks.
And then I yell "ALEXA. OPEN THE FRONT DOOR." The voice of an angel responds. "OK." Whirrr. Click. Door opens. Sweet warmth.
I need a fake rock with a key under it.
Great Sunday.18 -
This is one of the best birthday present I had so far. It's a handmade keyboard where almost every key has a special meaning that represent a little story from my past.
A truly geeky gift from my best friends. Thank you! 17
17 -
Teacher: "Whats that key thingy?"
Class: "You mean the keyboard?"
Teacher: "Yes, that one!"
I shit you not, she was my IT educator for a year.
Send help.5 -
Working with a radio chip we selected because it had built-in encryption. Cannot make the encryption work, thus in contact with the manufacturer:
"- I cannot make the encryption work, it's like the chip doesn't want to take a key.
- which key do you use?
- does it matter?
- well yes, you can't just use any key!
- why not?
- you need to get an approved key from us.
- why is that?
- so that your competitors can't read your data!
- ...
- ...
- so the way to get working keys is to get them from you?
- of course!
- keys are 256 bits. Can we potentially use all of them?
- OF COURSE NOT!
- how many can we get from you?
- one! We reserve it from your company.
- are you telling me that all units within a company will need to have the exact same encryption key?
- yes!
- so anyone with our product could eavesdrop another same product?
- well yes, but it's all within your own products.
- ...
- ...
- that's not how encryption is supposed to work.
- but it's safe, your competitors cannot eavesdrop!
- I'm out of here."
(We finally found a satisfactory work-around, but i am still pissed at them)9 -
Apple has a real problem.
Their hardware has always been overpriced, but at least before it had defenders pointing out that it was at least capable and well made.
I know, I used to be one of them.
Past tense.
They have jumped the shark.
They now make pretentious hipster crap that is massively overpriced and doesn't have the basic features (like hardware ports) to enable you to do your job.
I mean, who needs an ESC key? What is wrong with learning to type CTRL-[ instead? Muscle memory? What's that?
They have gone from "It just works" to "It just doesn't work" in no time at all.
And it is Developers who are most pissed off. A tiny demographic who won't be visible on the financial bottom line until their newly absent software suddenly makes itself known two, three years down the line.
By which time it is too late to do anything.
But hey! Look how thin (and thermally throttled) my new laptop is!19 -
Storytime!
Manager: Hey fullstackchris, the maps widget on our app stopped working recently...
Dev: (Skeptical, little did he know) Sigh... probably didn't raise quota or something stupid... Logs on to google cloud console to check it out...
Google Dashboard: Your bill.... $5,197 (!!!!!!) Payment method declined (you think?!)
Dev: 😱 WTF!?!?!! (Calls managers) Uh, we have HUGE problem, charges for $5000+ in our google account, did you guys remove the quota limits or not see any limit reached warnings!?
Managers: Uh, we didn't even know that an API could cost money, besides, we never check that email account!
Dev: 🤦♂️ yeah obviously you get charged, especially when there have literally been millions of requests. Anyway, the bigger question is where or how our key got leaked. Somewhat started hammering one of the google APIs with one of our keys (Proceeds to hunt for usages of said API key in the codebase)
Dev: (sweating 😰) did I expose an API key somewhere? Man, I hope it's not my fault...
Terminal: grep results in, CMS codebase!
Dev: ah, what do we have here, app.config, seems fine.... wait, why did they expose it to a PUBLIC endpoint?!
Long story short:
The previous consulting goons put our Angular CMS JSON config on a publicly accessible endpoint.
WITH A GOOGLE MAPS API KEY.
JUST CHILLING IN PLAINTEXT.
Though I'm relieved it wasn't my fault, my faith in humanity is still somewhat diminished. 🤷♂️
Oh, and it's only Monday. 😎
Cheers!11 -
Today I needed the scroll lock key.
I was running a super long test suite, one which puts a green dot on the screen every 500ms, so you can't scroll up. I needed to view some output of an earlier command... in other words, I needed to lock the automatic scrolling of the terminal.
That is what the scroll lock key was made for.
A momentous occasion.
Then I found out that a while ago, I used the macro function of my keyboard to rebind the that key... to close the current terminal window. 😡7 -
Forgot the password of the private key used to login to all my vpn servers.
Now I’ve got to generate a new one and deploy it everywhere again through this shitty control panel for every server fucking manually.
🤬28 -
My dad came with a windows laptop and asked me to convert a lot of jpg files to pdf on a usb stick (wtf?) he showed to me a tool on the laptop that convert files one by one ... and there is 58 jpg file.
Soooo I unpluged the usb key and pluged it into my linux laptop and ...
for f in *.JPG; do convert "$f" "pdf/$(basename "$f" .JPG).pdf"; done
My dad could not believe I had finished in 5 minutes
Linux Powaaaa !17 -
The Orange Juice Saga ....
I've just come off one of the stupidest calls ever.
Firstly, I am not in tech support, I'm a software developer - read the below with this in mind.
My client called up to say the system I created as been compromised. When he attempts to login, he is logged off his Windows machine.
He'd also apparently taken his PC to ***insert large UK computer superstore here***, who took £100 plus to look at the machine and conclude his needs to buy a new PC.
I remoted into his computer to see WTF was going on.
As he described, visiting my login form did log you out. In fact, whenever you pressed the "L" key you were logged out. Press the "M" key, all windows were minimized. Basically, all Windows hotkeys appeared to be active, without the need to press the Windows key.
Whilst connected to his PC I spent a good 30 minutes checking keyboard settings and came up short.
After asking all the normal questions (has anything changed on your PC, have you installed stuff lately etc.) without any useful answers I got nothing.
I then came across an article stating several presses of the Windows in quick succession will solve the issue.
I got the client to try this, pressed the "L" key (which would have logged me off previously) and the issue was resolved.
Basically, the Windows key was "stuck", which oddly makes your PC kind of useless.
I asked the client if they'd split anything on the keyword whilst working. His exact word were simply lol:
"Oh yer, yesterday, I was trying to drink a glass of orange quickly and split some in the corner of keyboard. I did clean it up quickly though".
Yep, the issue was due to the client spilling orange juice on their keyboard , which in turn made the Windows key stick.
Disaster averted.
A call that started with the client stating I made a system that was easily compromised (i.e. my fault), morphed into a sorry saga of cold drinks.
The client did ask why the ***superstore name*** charged him money for that and recommended a new machine. That is a good question and demonstrated some the questionable tech support practices we see nowadays, even at very large stores.
To be fair to the client, he told me to bill him for half a days work as it was his own fault.
When I'm able to stop myself involuntarily face palming, I'm off for a swim to unwind :) 7
7 -
My brother (14, at that time 12) is in puberty and just doesn't get off his computer to learn or do anything useful. He actually got bad grades because of this.
I made an app for my mom as well as a "virus" for my brother's computer that she could use to start and stop my brother's mouse wobble around randomly. Whenever he should be learning, my mother would press a button and he couldn't do anything anymore.
He eventually found out how to start YouTube videos using only his keyboard, so the next update came with a feature that simulated a random keypress instead of the one my brother was actually intending to type whenever he pressed a key.
The fun thing was, that he never found out why that was happening and just assumed his computer was broken.3 -
Not really dev as much but still IT related 😂
in college we got some new macs in our class. Before we were allowed to use them the "IT Tech" came in and did something to them all (probably ran some scripts to set stuff up)
Anyway, I was completely new to OS X and accidentally pressed a key combo that opened up a dialogue to connect to a remote file server. I saw the address field was already filled out (from when the IT Tech was running the scripts). So me being me I decided to connect. Low and behold my student credentials got me in.
Taking a look around I found scripts, backups and all sorts of stuff. I decided to look at some of the scripts to see what they did. One of them was a script to add the Mac to the domain. Here's the funny part. The login to do that was hard coded into the script....
To conclude. I now have domain level access to my whole college network 🙃
Tl;Dr: stupid it tech saves password in script. I find it. I now have domain level access to the college network14 -
Paypal Rant #3
One day I'll go to Paypal HQ and...
... change all the toilet rolls to face the wrong way
... remap all the semicolons to be the Greek equivalent character
... change all the door signs so they say "pull" instead of "push" and vice versa
... modify all the stairs to have variable heights
... programmatically shuffle the elevator buttons and randomly assign the alarm key to any of the most visited floors
... pour cocoa onto all the keyboards and wipe them off cleanly
... attach clear duct tape over their mouse sensors and insert really weak batteries or mess with their cables
I'll wait a day or two until they experience a sudden shortage of developers, then bombard them with thousands of fake applications from seemingly amazing candidates, then write an AI bot to continue argumentation with HR.
I'll wait another week or so until the company dissolves and with them, all my issues in life.
No need to be overly vulgar this time because you all know the deal. I hate this fucking company. Please Paypal do us all a favor and go fuck yourself.9 -
What I did wrong during my home office cleaning session this morning:
- put soap on my mouse mat
- snapped my enter key
- vacuumed up my F8 key
- absent-mindedly cut my ethernet cable
- lost my zero key
- dropped my backup hard drive (data was recoverable, but I need a new drive)
- lost one of the nose pads on my glasses
- got a cocktail stick stuck in a USB port
- exploded my mouse by using the wrong type of battery
Things I did good:
- nothing11 -
Will do a much-security.nl post with answering sent-in questions this weekend.
Please send them to concerns@much-security.nl 😊
Public GPG key can be found at either:
https://much-security.nl/concerns.a... or https://much-security.nl/concerns.h...
Oh and threats (including death threats) aren't much appreciated. They don't really keep me awake at night but if you're one of the people sending them, it's not much fun 😬)17 -
This is from my days of running a rather large (for its time) Minecraft server. A few of our best admins were given access to the server console. For extra security, we also had a second login stage in-game using a command (in case their accounts were compromised). We even had a fairly strict password strength policy.
But all of that was defeated by a slightly too stiff SHIFT key. See, in-game commands were typed in chat, prefixed with a slash -- SHIFT+7 on German-ish keyboards. And so, when logging in, one of our head admins didn't realize his SHIFT key didn't register and proudly broadcast to the server "[Admin] username: 7login hisPasswordHere".
This was immediately noticed by the owner of a 'rival' server who was trying to copy some cool thing that we had. He jumped onto the console that he found in an nmap scan a week prior (a scan that I detected and he denied), promoted himself to admin and proceeded to wreak havoc.
I got a call, 10-ish minutes later, that "everything was literally on fire". I immediately rolled everything back (half-hourly backups ftw) and killed the console just in case.
The best part was the Skype call with that admin that followed. I wasn't too angry, but I did want him to suffer a little, so I didn't immediately tell him that we had good backups. He thought he'd brought the downfall of our server. I'm pretty sure he cried.5 -
My team was sharing an API key to our company's microservice containing all our customer data.
I say "was" because one team member accidentally published the key online so the security team disabled our key and won't give us a new one.
I don't know whether to laugh or cry4 -
I just can't understand what will lead an so called Software Company, that provides for my local government by the way, to use an cloud sever (AWS ec2 instance) like it were an bare metal machine.
They have it working, non-stop, for over 4 years or so. Just one instance. Running MySQL, PostgreSQL, Apache, PHP and an f* Tomcat server with no less than 10 HUGE apps deployed. I just can't believe this instance is still up.
By the way, they don't do backups, most of the data is on the ephemeral storage, they use just one private key for every dev, no CI, no testing. Deployment are nightmares using scp to upload the .war...
But still, they are running several several apps for things like registering citizen complaints that comes in by hot lines. The system is incredibly slow as they use just hibernate without query optimizations to lookup and search things (n+1 query problems).
They didn't even bother to get a proper domain. They use an IP address and expose the port for tomcat directly. No reverse proxy here! (No ssl too)
I've been out of this company for two years now, it was my first work as a developer, but they needed help for an app that I worked on during my time there. I was really surprised to see that everything still the same. Even the old private key that they emailed me (?!?!?!?!) back then still worked. All the passwords still the same too.
I have some good rants from the time I was there, and about the general level of the developers in my region. But I'll leave them for later!
Is it just me or this whole shit is crazy af?3 -
Friend brings over a Windows 8 all in one laptop.
Friend: Can you fix my laptop
Me: I'm a programmer
Friend: I thought you worked with computers.
Me: I do... but I'm not tech support
Friend: Please?
Me: (reluctantly) Fine.
*many hours later after attempting to get the PC to boot from a USB. WHY DOES THIS PC NOT HAVE A KEY TO ENTER THE GOD DAMNED BOOT MENU AND HAS NO BOOT ORDER SELECTION?????!*
Friend: Have you fixed it?
Me: No
Friend: You suck at computers
Me: ....
Never spoke to him again.8 -
How my keyboard evolves:
0. Like any normal man, I started with a cheap standard Qwerty keyboard. As I began learning programming, I wanted something more elegant, so...
1. I've been using layout Dvorak (and then Programmer Dvorak) for like 5 years+ now. Anyone has intention to type on my machine soon gives up or even is blocked by me from the very start. It always takes a couple of minutes to explain to them what's going on here. They think I'm weird. I feel untouchable :)
2. My first mechkey was a 104-key Filco. Time flew by and I wanted my thing to be more compact so I went for a 66% and a TKL.
3. Recently I find out that though my keyboard is not a full-sized, there're yet some keys I've never touched (the bottom right modifiers, scroll lock, etc), so I look for a leaner one: HHKB and its alike but with slight remappings. Now I'm satisfied with the tiny, corners-trimmed keyboard but others look at it and ask how it is even possible to scroll the web page using the thing.
Prob 1: my boss can never type on my keyboard. Sometimes he still grumbles when he cannot correct my fouls right on my machine.
Prob 2: my keyboards at home and at work are not the same and some keymapping cannot applied to one of the two. That's async. 21
21 -
My dear diary,
Today, the guy that convinced the boss to completely replace our functional CMS website (marketing used to update it) with a static one he was writing from scratch in PHP + jQuery, has published our MailChimp Api Key on StackOverflow, because he couldn't make the API to work.
Boss didn't complain, but I don't think he understood what happened. Just asked the guy for not doing that again.
It was a crazy day.12 -
I once worked Tech Support for a point of sale software package. There was really no internal help desk, so we got all of those questions as well.
One day our front receptionist that her computer is being really weird and she can't type - it keeps inserting 3s in the middle of what she is typing.
I take the short walk down the hall to her desk and see that, indeed, a never ending string of 3s is being input to her screen.
"I can't figure out what's wrong." she says.
Then I reach over and remove the edge of an open binder whose edge was resting on the 3 key and enter key on the num pad.
"That should fix it."
Walked back to my desk.1 -
i am BEYOND pissed at google.
as some of you know, i recently got android studio to run on a chromebook (you read that right), but it being a chromebook and google being a protective fucktard of their crappy operating system, i had to boot into bios every time i started it.
when i was with some friends, i started up the chromebook, and left, after telling my friends how to boot the chromebook.
ten seconds and literally one press of the esc button later, he broke the entire thing.
but that's not what that rant was about, i honestly knew it would happen eventually (although, this wasn't the best time).
so now this screen pops up.
"chrome os is damaged or missing, please insert a usb recovery drive" or something like that.
well, i'll create one. simple enough.
no wait, this is google, just your average 750 billion dollar company who cares more about responsive design then a product actually responding.
i started to create the recovery usb. of course, chrome developers thought it would be a good idea to convert the old, working fine, windows executable usb recoverer, and replace with with a fucking chrome extension.
i truly hope someone got fired.
so, after doing everything fine with the instructions, it got to the part where it wrote the os image to the usb. the writing stayed at 0%.
now this was a disk thing, writing os's and shit, so i didn't want to fuck it up. after waiting ten minutes, i pressed 'cancel.'
i tried again many times, looked things up, and frantically googled the error. i even tried the same search queries on bing, yahoo, duckduckgo and ecosia because i had the feeling google secretly had tracked me over the past 7 years and decided to not help me after all the times i said google was a fucker or something similar.
google is a fucker.
after that, i decided to fuck with it, even if it formats my fucking c drive.
i got to the same point where the writing got stuck at 0% and proceeded to fuck. i start spamming random keys, and guess what?
after i press enter, it started.
what the fuck google?
1000s of people read the article on how to make the recovery drive. why not tell them to press the goddamn enter key?
i swear there are hundreds of other people in my same situation. and all they have to do is press one fucking key???
maybe tell those people who tried to fix the shit product you sold them.
fuck you google.7 -
*Opens a pack of tablets (8000) and start to prep them.*
WHAT THE ACTUAL FUCK.
SAME MAC ADDRESS.
Okay, that's just an er-
NOPE, ANOTHER ONE. HOLY SHIT. OKAY IT'S GETTING WORSE.
Is it my db?
Oh.
The db is just fine.
*Painfully getting in contact with the reseller*
Me: grumbles grumbles Mac Address grumbles
Reseller: Uh.. What?
It would be okay if we weren't using Mac Addresses as primary key in our databases.
They gave us some weird-looking software to "re-write mac addresses". It's working.
Something tells me that ipv6 is not for tomorrow.7 -
Why nobody uses public/private key authentication for ssh and disable password auth?
Am I the only one around here doing this?14 -
I really miss the days when Windows XP had product keys on stickers stuck to computer cases. If I ever needed an XP product key, I just went to Staples and wrote one down from one of the machines on display.9
-
Because of hardware failure we had to move some vpns from one datacenter to another.
The team of highly untrained monkeys at my hosting provider were hired to do this. First they ran backups of all the systems. Then they started the moving process. A few hours later they were done. We got an email everything was back online.
So we restarted all our processes and no data was coming in from our Raspberry's around the country. So we start a little investigation. What did these buffons do, they changed our rsa keys.
So we kindly ask them to put the old keys back so we do not have to fix 200 changed key warnings on systems that are not remotely accesible.
Apperently something that can't be done because their back up process is automated and always makes new keys.
Holy fucking fuck, whats the point in having a backup its not an exact copy. Is this fucking normal?
Now I will be spending the next few weeks literally standing in cow shit reconnecting Raspberry's.
Thanks a fucking lot. Not!4 -
Hey folks, I've just launched the https://okso.app - it is a drawing app that you may use to express, grasp, and organize your thoughts and ideas.
One key feature there is that you may organize your drawings/sketches into a hierarchical tree structure so that a large amount of data would be more manageable and less overwhelming.
I hope you find this app useful!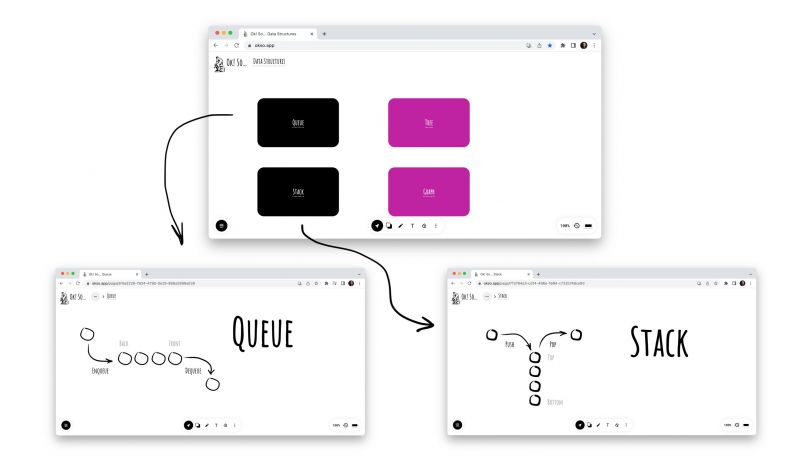 10
10 -
I finished two projects. Both of them need to connect to each other. However, the tool to do that is not currently licensed to achieve my desired outcome. I email my boss to check the status of the license key I need, that they promised, and the only thing I get back is "Correct." Seriously? 😠 The person who has the company credit card and authority to buy, also the same one that gives me a deadline to turn this shit in, can't give me the time of day to respond to an email? Their response wasn't even relevant. I've been trying to move beyond this roadblock for a week now! I'm a pretty independent guy, but I'm not going to buy the license myself for a tool that I didn't even want to use. So when someone comes to my cube and I'm raging on Steam, ✋ I don't want to hear anything about company time, because mine isn't being respected either. 👊👊
-
Show up on time.
Be prepared.
Have a list of things that need to be covered if you're leading the meeting.
Stay on track, don't let people start talking out of one tangent, I tend to suggest people discuss it afterwards or email about it.
Take the meeting seriously, otherwise other people will not.
Know how to talk a language everyone understands. Sometimes people with key info just aren't very technical.
Following Ely's golden rules for meetings, my meetings are rarely longer than 20 minutes.5 -
JIRA. Fucking JIRA. Everybody just fucking hates it. It tops the list of shit pieces of software by a fair margin, followed by JIRA in second place and JIRA in 3rd. It's fucking unusable without superpowers and endless patience. It does whatever it goddamn pleases and randomly sends your precious input that you so carefully crafted anxiously avoiding to press one wrong key to the happy hunting grounds.
Fuck you, JIRA.
- Every developer. Really every.17 -
I hate access. I wish I could use literally any other program. But they're not authorized.
I'm the only one working on this, and everything is closed. How the fuck is the object in use somewhere else? And where the fuck did my primary key go???7 -
I love how the Keybase Linux client installs itself straight into /keybase. Unix directory structure guidelines? Oh no, those don't apply to us. And after uninstalling the application they don't even remove the directory. Leaving dirt and not even having the courtesy to clean it up. Their engineers sure are one of a kind.
Also, remember that EFAIL case? I received an email from them at the time, stating some stuff that was about as consistent as their respect for Unix directory structure guidelines. Overtyping straight from said email here:
[…] and our filesystem all do not use PGP.
> whatever that means.
The only time you'll ever use PGP encryption in Keybase is when you're sitting there thinking "Oh, I really want to use legacy PGP encryption."
> Legacy encryption.. yeah right. Just as legacy as Vim is, isn't it?
You have PGP as part of your cryptographic identity.
> OH REALLY?! NO SHIT!!! I ACTIVELY USED 3 OS'S AND FAILED ON 2 BECAUSE OF YOUR SHITTY CLIENT, JUST TO UPLOAD MY FUCKING PUBLIC KEY!!!
You'll want to remove your PGP key from your Keybase identity.
> Hmm, yeah you might want to do so. Not because EFAIL or anything, just because Keybase clearly is a total failure on all levels.
Written quickly,
the Keybase team
> Well that's fucking clear. Could've taken some time to think before hitting "Send" though.
Don't get me wrong, I love the initiatives like this with all my heart, and greatly encourage secure messaging that leverages PGP. But when the implementation sucks this much, I start to ask myself questions about whether I should really trust this thing with my private conversations. Luckily I refrained from uploading my private key to their servers, otherwise I would've been really fucked. -
.. for the first time I permanently lost access to one of my GPG keys that were actually in use. No revocation certificates, nothing in the keychains on any of my hosts... Keychain flash drive that got stolen had a copy of both, my fileserver used to have a copy of that flash drive until I deleted it to make room for a filesystem migration, and my laptop used to have one.. until I decommisioned it and shredded its hard drive to be deployed somewhere else...
fuck
I can't sign my git commits anymore, and I can't revoke the key either.
(╯°□°)╯︵ ┻━┻15 -
Today I learned the hard way that losing your app's key store means no more updating , bug fixing , performance boosting , features adding ...
The app had like 5k downloads on the play store ..
Lost the key when one of my hard drives burned ..
Lesson of the day : keep your keys safe .
*trying to stay strong*3 -
Remember the super duper company I applied for? (Last rant)
Well, I did their coding challenge. And after many years I had to do a metric crapton of C++. It's not a fun language. It's frustrating how human-unfriendly it is, and maybe one reason why I low-key like it.
Anyways, here's hoping that I didn't fuck up too much.
On a side note, I realized tensorflow actually has a cpp api. I think I'm gonna work with that in my next mental breakdown. 🧐6 -
Yesterday evening I'd been to Lenovo service center to get a battery for my personal laptop.
Sales guy: Sir, I can see that your laptop had Windows 8 when you purchased it. If you want I can give you a one key recovery disc for that.
Me: Thanks a lot sir, but I run Ubuntu on my laptop. And if you are insisting, I can take that recovery media and install it on my uncle's laptop.
Sales guy: I'll get back to you on this.
*End of conversation* 😂5 -
In secondary school (gymnasiet in Swedish) I made a little exe that I put on the autostart on one of the public PCs. That exe made various weird behaviours for a few minutes (disabling the monitor, messing up the keyboard/mouse etc etc) before it restarted the PC. If, however, you held down a certain key combo, it would show a nice popup before quitting. So I always had a free PC to access every break cause no one wanted that PC :D3
-
I've developed an interesting habit. I wear a hat 24/7. The same exact hat.
I (almost) never wear my hat backwards. I think its weird, and I look weird, and its just too much weirdness.
There is one exception to this rule.
Before I begin coding each day, before a single stroke of my keyboard, I turn my hat backwards. I don't know why I started doing this, but it is almost as if my hat is a key and turning it unlocks all my programming knowledge.
Anyone else have a quirky habit they do before/during a coding session?12 -
It was my first ever hackathon. Initially, I registered with my friend who is a non coder but want to experience the thrill of joining a hackathon. But when we arrived at the event, someone older than us was added to our team because he was solo at that time. Eventually, this old guy (not too old, around his 20s) ( and let’s call him A) and I got close.
We chose the problem where one is tasked to create an ML model that can predict the phenotype of a plant based on genotypic data. Before the event, I didn’t have any background in machine learning, but A was so kind to teach me.
I learned key terms in ML, was able to train different models, and we ended up using my models as the final product. Though the highest accuracy I got for one of my model was 52%, but it didn’t discouraged me.
We didn’t won, however. But it was a great first time experience for me.
Also, he gave me an idea in pitching, because he was also taking MS in Data Science ( I think ) and he had a great background in sales as well, so yeah I got that too.2 -
Once a month I get a crash for the stupid PHP site I am in charge of because the guy who made the database made the primary key of a table a varchar. It is a number 99.9% of the time but the dumbass customer always enters one entry with a string cuz the dumbass db Dev let them. I emailed the dumbass Dev telling him he is stupid and he said it is part of their philosophy. I told him I still think he is stupid so he emailed my boss.
I emailed him again telling him he is stupid.6 -
There's this junior I've been training. We gave him a bigger task than we usually do
"How do I link an object in table X with the corresponding object in table Y?"
"How are objects in two tables usually linked? How did you link Y with Z in the first place?"
"Em... Foreign Keys?"
"Yup"
"But there's not foreign key from X to Y."
"Well, create one. You've got full creative freedom over this task."
I sometimes feel like Juniors are either completely careless about past code or overly carefuly with not editing any past code. Frustrating but adorable2 -
When I see two fields, one for username and one for password, I expect I can fill them out immediately subsequently with only a tab in between. While typing my password I DON'T want to get sent to a page where I can enter my password only: I was entering it already! Sometimes I even make it until I pressed the enter key that was supposed to log me in, but then I'm kindly requested to reenter my password. At that moment I not-so-kindly think: FUCK YOU Microsoft, you should know better. Even when logging into Visual Studio for fack sake3
-
Continuation of https://devrant.com/rants/642962/...
You are the decryption key to my encryption,
No one can access my heart except you.
You are the loop in my life,
I always keep coming back to you.
You are my nodemon,
You are always watching over me.
You are the / to everything I do,
Am nothing without you and I will always preserve you.
You are my increment operator,
You add value to my life.
To be continued 😉3 -
So I have seen this quite a few times now and posted the text below already, but I'd like to shed some light on this:
If you hit up your dev tools and check the network tab, you might see some repeated API calls. Those calls include a GET parameter named "token". The request looks something like this: "https://domain.tld/api/somecall/..."
You can think of this token as a temporary password, or a key that holds information about your user and other information in the backend. If one would steal a token that belongs to another user, you would have control over his account. Now many complained that this key is visible in the URL and not "encrypted". I'll try to explain why this is, well "wrong" or doesn't impose a bigger security risk than normal:
There is no such thing as an "unencrypted query", well besides really transmitting encrypted data. This fields are being protected by the transport layer (HTTPS) or not (HTTP) and while it might not be common to transmit these fields in a GET query parameter, it's standard to send those tokens as cookies, which are as exposed as query parameters. Hit up some random site. The chance that you'll see a PHP session id being transmitted as a cookie is high. Cookies are as exposed as any HTTP GET or POST Form data and can be viewed as easily. Look for a "details" or "http header" section in your dev tools.
Stolen tokens can be used to "log in" into the website, although it might be made harder by only allowing one IP per token or similar. However the use of such a that token is absolut standard and nothing special devRant does. Every site that offers you a "keep me logged in" or "remember me" option uses something like this, one way or the other. Because a token could have been stolen you sometimes need to additionally enter your current password when doings something security risky, like changing your password. In that case your password is being used as a second factor. The idea is, that an attacker could have stolen your token, but still doesn't know your password. It's not enough to grab a token, you need that second (or maybe thrid) factor. As an example - that's how githubs "sudo" mode works. You have got your token, that grants you more permissions than a non-logged in user has, but to do the critical stuff you need an additional token that's only valid for that session, because asking for your password before every action would be inconvenient when setting up a repo
I hope this helps understanding a bit more of this topic :)
Keep safe and keep asking questions if you fell that your data is in danger
Reeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee5 -
If you discount all the usual sql injections the most blatant was not our but a system one customer switched to after complaining over cost.
The new system was a bit more bare bones featurewize but the real gem was the profile page for their customers.
The only security was an id param pointing to the users primary key, which was an auto incrementing integer :)
And not only could you access all customer data but you could change it to.
But since the new system was built by their it chief’s son we realized it was not much we could do.2 -
Coolest thing I’ve built solo?
Damn, there’s been a lot of things over the years, but I guess the most used one I’ve made would be my voice activated tv remote - yes it’s real.
So in essence it’s a google home... yea I know spyware and all, but look it was free so I’m going to make use of it... err where was I, oh yea.
An IFTTT account which taps into the google assistant API and creates a webhook, although the authentication side of things is 0 to none, so had to put a api-key into the requests to at least have some layer of auth.
This webhook then hits a raspberry pi containing a PHP API to accept and authenticate the request in, digest this into KEY commands for the TV, and drops this into a Python script to connect to the TV over a web socket connection ( I found python more stable for this ) and sends the pre made key requests, it can even do multiple keys at a time... that was a pain.
So after all that, the end game becomes about a second from saying “hey google, change the tv channel to xxx”
This sick and twisted contraption is finished and the tv is my little bitch.
This has been built out to handle channels by name, number, volume up/down, sources switching to hdmi, tv, vga and a bunch of other things.
The things we do when we can’t find a tv remote for days....
Next up, getting it to launch Netflix app and going to a specified show / episode.. but may be to adventurous. -
Python rant
Where the hell is Break key?!
Story: I wrote multithreaded python script and went to Lab to test it. Script got stuck (one thread died) and I needed to stop that thing, but how without magic Ctrl+Break?
Damn you Dell with your slim and minimalistic keyboards! 10
10 -
Massive payment gateway (not gonna say names) with more then 10k transactions / hour telling md5 is one of most secure encryptions they have. Only to made worse by the fact that they send the key and hashed key in the same request.
I am advising all our clients to change payment gateway asap if they use this one.1 -
Another day on my tutoring job
This guy who's got no idea about what is he doing here (I had a rant before), runs to me while I'm helping another student. He interrupts me, shoves a USB key to my face:
[Student]: can you do something for me? Can you upload something on my ftp coz I gotta go now.
/*Each student in out school got personal ftp and submitting under the right directory is usually a part of an assignment and cost grades*/
[Me]: I can't, it's against the school policy
[Student (annoyed)]: But I have to go!
[Me]: can't help you, sorry
[Student (still annoyed)]: So you're not gonna do it, huh?
[Me]: No, sorry
[Student (passively aggressively)]: So I guess I'll get a zero for this one.
And he says it like it's my fault!
And he walks away. Me and students I'm helping are shocked. The guy is in his at least 50s. And no common sense whatsoever.5 -
I interchanged my space-bar key with my delete key.
I think this is one of those many times everyone is wrong and am right1 -
So I manage multiple VPS's (including multiple on a dedicated server) and I setup a few proxy servers last week. Ordered another one yesterday to run as VPN server and I thought like 'hey, let's disable password based login for security!'. So I disabled that but the key login didn't seem to work completely yet. I did see a 'console' icon/title in the control panel at the host's site and I've seen/used those before so I thought that as the other ones I've used before all provided a web based console, I'd be fine! So le me disabled password based login and indeed, the key based login did not work yet. No panic, let's go to the web interface and click the console button!
*clicks console button*
*New windows launches.....*
I thought I would get a console window.
Nope.
The window contained temporary login details for my VPS... guess what... YES, FUCKING PASSWORD BASED. AND WHO JUST DISABLED THE FUCKING PASSWORD BASED LOGIN!?!
WHO THOUGHT IT WOULD BE A GOOD IDEA TO IMPLEMENT THIS MOTHERFUCKING GOD?!?
FUUUUUUUUUUUUUUUUUUUUUUU.3 -
One day, I spoke to my team which yubi or nitro key to get.
Senior (s) : but what do you need it for?
Me (m) : for encryption. And securing our password managers. Stuff, I guess.
S : encryption is not gonna be a thing. It hasn't and it won't.
M : *leaves*
I've been so baffled I couldn't cope with the situation.
A few weeks later I left the company. There were too many of such people and those products.3 -
Im back to anyone that may cared a little, so I was offline for 6 days since my ISP Ultra Hilarious to crash my state records of their paying customers and some other stuff that It took 5ever to get back, anything you guys want to share with me that may happen lately here on DevRant? I personally my classic Amazon bashing news and Perhaps giving away some Steam Keys that one Reviewer user of my site give us out to promote the site along side the devs.
For the Amazon News there is:
Amazon in talks to buy cybersecurity startup Sqrrl and also group of New Jersey Amazon Warehouse workers stood in the cold outside an Amazon Books store in Manhattan on Wednesday to remind shoppers that their online purchases are made possible by warehouse employees who often are underpaid and denied normal workplace benefits. More info at: https://legionfront.me/pages/news
No about Free Steam gamuz:
Gravity Island Key: AACA7-CYFVW-N775L
For more free keys drop by:
https://legionfront.me/pages/gaming
https://legionfront.me/ccgr 6
6 -
I've been a part of this industry for over two decades, found myself scraping and clawing my way up, recently leaving a high paying position to create my own company; in an attempt to fix the things I feel are severely broken within the ones I've worked for in the past.
Sometimes, we are challenged in ways we never thought we would be. And, it should always result in the improvement of something we never thought would be possible to improve.
There's a certain beauty of hitting a personal impasse. Because it allows you to choose a better path for yourself - which is a key element in accepting and conquering any one of life's many challenges.
So, just remember, we are - by nature - problem solvers. So what the fuck would we do, without a problem to solve?5 -
Damn Apple. These stupid certificates. I only want to send notifications. On Android I have to add one API key. And you Apple? Struggeling to get ionic push working for 6 hours...9
-
So I have too many posts for wk110. It's sad. Here we go. I got a bad grade on an assignment for a hello world program in college. How do you write a hello world program that successfully prints hello world and not get 100 percent?
The teacher insisted that we write a console "hello world" program in C++, on windows. If he can't read hello world, you fail. So you must add `system("pause")` at the end so the window stays open. One problem: system() is horribly insecure and im stubborn. I refused to write exactly what he wanted, like everyone else did, because I try to not write code I know is unsafe. So I ended my script with cin.get() which also pauses for input. Unlike pause however it can't be any key, it reads a line, so you must hit enter. This was "unfavorable behavior" and ultimately I got something like a high C, low B grade. Only person to not get 100%8 -
I just had the most surreal email discussion I think I've ever had...
I spent over two hours going back-and-forth over email with an enterprise DBA, trying to convince them I needed a primary key for a table. They created the table without a primary key (or any unique constraints... or indexes... but that's another discussion). I asked them to add one. Then had to justify why.
If you ever find yourself justifying why you need a primary key on a table in an RDBMS, that's the day you find yourself asking "is this real life?"
I want the last two hours of my life back. And a handful of Advil.1 -
Tries to use SoundCloud API for a client
Docs say you need a client key
Wants to create one by signing up clients application
Signup-Form says:applicazion registration currently not available
Goes to soundcloud dev forums
Raging devs rage about that soundcloud has terminated their api registration for about 13 months now
Me thinking: That's probably the best way to make a conpany grow!8 -
one of my friend has a golden finger👈, he could break your system with one touch, once he borrowed my laptop to update fb status, I saw him literally hit the enter key once, the pc got a blue screen and then rebooted with error, I have to reinstall OS to fix it. I asked around, he did this trick many times😱😱. I guess he could get some profit from this gift😂😂😂3
-
Today an intern accidentally opened vim and couldnt exit it. So she came by to ask how to get out of that editor.
My response: just hit escape and then ":q".
Turned out her escape key didnt work so she had to use an onscreen keyboard and she said there are about 5 dead keys on her keyboard for 2 years now...
How does one work with a broken keyboard?
And is there another way to exit a "mode" in vim than pressing escape?13 -
ssh your.server.ip, welcome message:
#Ooops! your files have been encrypted.
#Don't waste your time trying to decrypt them.
#Nobody can.
#We would gladly offer you a way of recovering all
#your files safely, but sadly we lost the decryption
#password.
#Hackers too are not perfect, have a nice day.
#PS. you can still send money to support us if you want at this
#web page: fuckyou.onion.
#Your personal key: m0r0nm0t3fukk3r
(I'll code this one day and install it on somebody machine, it's one of my top dreams)11 -
Dear DevRant,
Tomorrow, I get to defend my memory (the document I finished 3 weeks before deadline, remember?), which means that I am a month away to finish my studies forever. I am totally fucking scared but, heh, the key not to panick is to think it's already too late, just go til the end while avoiding saying bullshit as much as you can.
There are so much things I want to do, from sleeping one month straight, to shove my resignation letter in everyone's ass. Hopefully, everything will happen soon enough :)
I just want you to know that it feel so good to be a member of a community that is so relatable about anger you can feel everyday, it feels so good.
Love y'all, and wish me luck
@Drillan7672 -
After using so much VIM and VIM key binds in other IDEs, a piece of me dies every time I have to code without them.
Am I the only one?4 -
!rant
Yesterday was an extremely stressful day. Several things went wrong, clients were already preparing for the weekend, a horrible headache was building up during the day, all in all: a day, where you'd better have stayed in bed. Finally home, I approached my mailbox, put the key in, opened it, expecting bills or similar things to... *cough* sweeten *cough*... my weekend, but instead found a letter from devRant.
Guys, I gotta tell you, this really made my entire day (if not my entire weekend). I know it's silly, because we're basically talking about a letter and some stickers, but it's the small things one should appreciate, as they can brighten the worst days.
Thanks @dfox and @trogus for building such a great platform, that allows fellow developers to vent about *certain* things from time to time. Keep up the good work! 2
2 -
Just installed Vim a minute ago. I already want these key bindings for the entire OS 😅. I think I'm gonna love this one 🤗7
-
@OmerFlame wanted to see more of Soviet pirate stuff, so there you go buddy. This is an example of Samizdat (“self-publishing”) — Soviet people made books of dissident literature that was forbidden in the Soviet Union.
This very book was made by my grandma, with lace fabric cover and sheets cut evenly with care and precision. Everything was typed on a typewriter, yes, the thing that renders the whole page useless with one mistype, as there is no backspace key.
This book dated 1975, the poetry of Nikolay Gumilyov. 9
9 -
I know most people will be unable to relate here, but FUCK THE FRENCH PC KEYBOARD LAYOUT
FUCK YOUR STUPID ASS ALT-GR (right alt that acts as modifier while the other alt is used for shortcuts, but can't be combined with ctrl because that would make an alt-gr) THAT GIVES YOU ACCESS TO | ON THE F*IN 6 KEY AND \ ON THE F*IN 8. FUCK YOUR USELESS ASS ² KEY, THAT ONLY WORKS AS A ². NOBODY EVER USED THAT KEY FOR ANYTHING OTHER THAN COMPLAINING THAT "you know, I really hate the ² key, it's absolutely useless"
THE MAC LAYOUT IS 100 TIMES BETTER, WITH MORE GLYPHS ACCESSIBLE WITHOUT THAT RETARDED "special characters" MENU. WHOEVER DESIGNED A KEYBOARD THAT REQUIRES PEOPLE TO USE THAT MENU EVER IS THE ONE I'D CALL SPECIAL. NEVER HAVE PEOPLE REFRAINED FROM BUYING A MAC BECAUSE OF THAT LAYOUT, SO START USING THAT LAYOUT INSTEAD OF THAT RETARDED, ANTI-DEV PC LAYOUT...
Here's the French PC keyboard layout, notice how every useful key for devs have been placed to maximize annoyance, minimize typing efficient and accelerate ergonomically related diseases 11
11 -
I am very frustrated today and I do not know where to "scream" so I will post this here since I believe you will know how I feel.
Here's the case...
I am developing an e-commerce web application where we sell industrial parts. So my boss told me on March that when we are going to show these parts, we should not show Part Number to visitors because they will steal our information.
Ok, this makes sense but there was a problem.
The Primary Key for these products in our internal system is a string which is the Part Number itself.
I told him on March that we have to come up with another unique number for all the products that we are selling, so this unique number will be the primary key, not the Part Number. This will be best because I will be dependent from the original Part Number itself. And in every meeting he said "That is not priority". So I kept developing the part using the original Part Number as primary key and hid is from the web app. (But the Part Number still shows on URL or on search because this is how my boss designed the app.)
I built the app and is on a test server. Until one of out employees asked my boss: "There is no unique number or Part Number. How are the clients going to reference these parts? If a client buys 20 products and one of those has a problem, how is he going to tell us which products has a problem?"
My boss did not know what to say, and later said to me that I was right and primary key was priority.
I really hate when a guy that knows shit from developing does not listen to suggestions given by developers.
FUCK MY LIFE!
I'm sorry if you did not understand anything.5 -
Clicks "Exploitation and Enumeration" category.
Clicks "Python (HARD)" challenge.
"What is a key that passes the code?"
Opens Python file and sees one line of nested lambda expressions spanning 1,846 characters (no spaces)
*Cries*8 -
Me, the only iOS dev at work one day, and colleague (who we'll call AndroidBoy), the only Android dev at work that same day (he's been working with us for less than two months). There was a change in one of the jsons we received from the server: instead of receiving a list, we now received a dictionary with strings as keys and lists as values. My iOS colleague had already made this modification on our parse function the day before.
AndroidBoy: "Hey what happened with the json?"
Me: "Oh, well instead of parsing a list, we'll parse a dictionary and get the list from each key. You basically have to do the same thing, only this time the lists are organized into categories."
AndroidBoy: "Oh, ok. But I don't know how to parse a dictionary while using Retrofit." (Context: Retrofit is a framework for request handling - correct me if I am mistaken, that's just what I've been told)
Me: "Sucks, dude, can't help ya. I've never worked with that and don't have that much exp. with Android."
I go out for a cigarette break. When I return, AndroidBoy is nowhere to be seen and suddenly I can't seem to get that data in my app. AndroidBoy comes in from the room where the backend colleagues work.
AndroidBoy: "Solved it!"
Me: "Solved what?"
AndroidBoy: "I told them to change back to a list and just put the key inside the objects of the list."
... he used the precious time of the backend colleagues to change the thing back hust because he was too lazy to search how to parse a dictionary. I was so amazed by his answer, that I didn't know whether to laugh, scream at him or punch him in the face. Not to mention the fact that now I had to revert just so he could avoid that extra work.5 -
Problems with redis... timeout everywhere...
30k READs per minute.
Me : Ok, How much ram are we actually using in redis ?
Metrics : Average : 30 MB
Me ; 30 MB, sure ? not 30 GB ?
Metrics : Nop, 30 MB
Me : fuck you redis then, hey memory cache, are you there ?
Memory cache : Yep, but only for one instance.
Me ok. So from now on you Memory cache is used, and you redis, you just publish messages when key should be delete. Works for you two ?
Memeory cache and redis : Yep, but nothing out of box exists
Me : Fine... I'll code it my selkf witj blackjack and hookers.
Redis : Why do I exist ?2 -
My first contact with an actual computer was the Sinclair ZX80, a monster with 512 bytes of ram (as in 1/2 kbyte)
It had no storage so you had to enter every program every time and it was programmed in basic using key combinations, you could not just write the commands since it did not have memory enough to keep the full text in memory.
So you pressed the cmd key along with one of the letter keys and possibly shift to enter a command, like cmd+p for print and it stored s byte code.8 -
Since we are using the same password on all our servers (both QA and Production environment) my team somehow decided that it would be easier to copy the private SSH key for to ALL servers and add the public key to the authorized.keys file.
This way we SSH without password and easily add it to new servers, it also means that anyone who gets into one server can get to all of them.
I wasn't a fan of the same password on all servers, but this private key copying is just going against basic security principles.
Do they want rogue connections? Because that's how you get them.1 -
So after 6 months of asking for production API token we've finally received it. It got physically delivered by a courier, passed as a text file on a CD. We didn't have a CD drive. Now we do. Because security. Only it turned out to be encrypted with our old public key so they had to redo the whole process. With our current public key. That they couldn't just download, because security, and demanded it to be passed in the fucking same way first. Luckily our hardware guy anticipated this and the CD drives he got can burn as well. So another two weeks passed and finally we got a visit from the courier again. But wait! The file was signed by two people and the signatures weren't trusted, both fingerprints I had to verify by phone, because security, and one of them was on vacation... until today when they finally called back and I could overwrite that fucking token and push to staging environment before the final push to prod.
Only for some reason I couldn't commit. Because the production token was exactly the same as the fucking test token so there was *nothing to commit!*
BECAUSE FUCKING SECURITY!5 -
Working as a part time student on an app and until now I thought I was the king of software development.
Well, fuck me and my high horse.
Today the stuff we send from the client to the server didn't arrive, so I asked the backend guy if he could take a look at the packages arriving. He did and told me the data was messed up.
I did only design stuff the last week or so, so I was very confused. After reverting back to one old commit after the other it struck me.
I still don't know how such a dumb mistake could have happened to me, the king of Android apps, but apparently I replaced all occurrences of a specific keyword in just the strings and comments of the whole project. Key became KeyList, so instead of <Keys> my XML contained <KeyList> which made no goddamn sense whatsoever.
Did I mention that we have an important deadline tomorrow? Yeah...
So now I leaned my lesson. Never trust XML.
JK I'm dumb. That's the lesson here. -
Seriously? Microsoft does not support ed25519 SSH keys in neither Azure DevOps nor the actual Azure Virtual Machines? Like seriously? No there has to be a joke. There just ain't no way
It has been in OpenSSH since 2013.
2013.
We're in 2023, if you've forgotten.
10 years ago, OpenSSH implemented this standard.
Did you know what they tell you when you enter your valid Ed25519 SSH key into their system?
Did you know they tell you that "Your SSH key is invalid"?
WHAT DO YOU MEAN INVALID???!?! IT WORKS EVERYWHERE ELSE JUST FINE!!! YOU'RE THE ONE THAT HAS NO FUCKING BRAINS!!!
Composure.
I am calm, I am calm.
I have always. Been. CALM!
There is no one more calm than me....
I guess RSA it is then.
A second SSH key, just for Microsoft.5 -
Fun fact!
Xiaomi has a restriction where you're only allowed a bootloader unlock key one week after you've requested it. No, not a week after you've bought the phone. Not a week after you created an account and generated so much usage data that it would be stupid to doubt you're a genuine user.
No, you have to wait one week after installing their fucking desktop app and getting past some arbitrary point in the process.
Seriously, how much shit can this company pull with a straight face? At this point they're just sabotaging me, it's not even for any reason.16 -
I tried to look for ParrotSec on Google because a friend of mine told me about it and instead of typing in what I should I typed, I was off by one key and had actually typed in "ParrotSex".rant smh wft typo fail why is x and c so close to each other get back to work are you that jobless sigh i hope you're reading this5
-
bought a windows license
built the pc
booted from usb
ask for license, put in bought license
installation seems normal
... windows isn't activated ... what?? how?? why is there a different key from the one i just entered?? and why does it still deny it when i try to change the key to my bought one?? y u do dis?😩
does anyone have an idea, what could be causing that?32 -
The fucking defective Caps Lock on Apple keyboards drives me fucking ballistic!
WHY would they ever think it would be a good idea to introduce a minimum press time for a key?!?
EVERY. FUCKING. TIME. I use the damn thing it inevitably fails and I have to backspace, delete the non-caps text I just entered after HITTING THE FUCKING CAPS LOCK KEY, tap the damn thing again (harder this time) and try again. It usually takes 2 or 3 tries before it actually catches. I'm sorry, but training myself to type slower is not as easy as you think!
Who the fuck thought up this nonsensical bullshit?? And who the fuck is going around accidentally tapping their caps lock key to the point where such a delay would be needed?? Do you not know where your own fingers are??
Seriously, all this does is penalize fast typists and people who actually want to USE the caps lock key for what it was meant for.
I swear to god this one little thing pisses me off SO much. And what's worse is they don't even give you an option to disable it, AND it's bloody fucking impossible to disable yourself even through the terminal.
(Also, typing this rant with so many caps was probably not as cathartic as I was going for!) 😂9 -
Working with atlassian products....
Possibility 1
You can either use exactly this one way and only with these specific instructions ...
Which will certainly not work for the project you have.
Possibility 2
There is an feature request which gets ignored for years, someone made a plugin...
But plugin was removed as inactive. :-)
Possibility 3
Atlassian provided in their endless graciousness a plugin.
After hours of deciphering Kotlin / Java code as the documentation is either useless or lacking details...
You did it. You got the REST shit working.
Well.
You just needed a script which wraps the underlying command, parses the commands well defined format like XML with specification.... To a completely gobbled up JSON, that looks like undecipherable shit.
I really hate Atlassian.
https://bitbucket.org/atlassian/...
I just wanted to add code coverage via the REST API by the way.
A really unnecessary and seldomly used future as it seems.
And yeah... The JSON contains a coverage element which contains a semicolon separated key value store, value being a comma separated list of line numbers.... 4
4 -
Boss activates encryption on dashboard
we installed the software
2 machines get locked out coz drive got encrypted with bitlocker
No one received the 48 bit key from bitlocker
I loose all my work coz the only way to use my laptop was to format the drive
Me as the technical guy and knowing how encryption works i just formatted the drive
Boss blames me for the cluster fuck8 -
Aaarrrrghhhh! I am frustrated.
My manager keeps cancelling our 1:1, which I look forward to as a potential platform for
- Me to build a rapport
- Discuss key decisions
- Slowly gain her trust that I can lead the entire product
And whenever we connect once in a blue moon, she started inviting two other team members in. Who the hell does that!!!
My colleague, she is nice and hard-working. But she fucking talks a lot. A FUCKING LOT.
1:1 and such key connects are not meant for status updates and this colleagues goes into every minor detail and explains the shit for 15 minutes each. Non-stop. No one really cares or bothers for that level of statuses.
Today she spoke for 30 minutes without a breather break. Everyone went numb.
But whatever, fuck it. I am getting things done by her so let her talk. I'll get my way through manager and skip level guy.
On the other side, they recruited a half witted potato for training. That was completely unnecessary. I am not putting in my time and efforts on someone who isn't willing to learn and contribute.
I spent more than a week explaining her basics of how to write a god damn user story and detailed functional requirements.
And even after 5 rounds of feedback (45 minutes each) the potato is stuck on colour of the button and alignment.
GOD DAMN FUCK! SOMEONE KILL ALL THE MORONS WHO CANNOT UNDERSTAND BASICS AFTER SO MUCH EXPLANATION.
I was really an impatient guy in past but over the years, I developed to be more calm and forgiving. Yet some people manage to get on my every nerve.
How the fuck am I supposed to grow when I am being dragged down instead being with smart colleagues where we can just accelerate to success!!!!1 -
Copy my private ssh key to multiple machines so I only have to configure one key in github, gitlab, bitbucket etc.3
-
Mozilla has announced that it's rolling out changes under the California Consumer Privacy Act (CCPA) to all Firefox users worldwide.
According to report of ZDNet: The CCPA (America's privacy legislation) came into effect on January 1, 2020, offering Californian users data-protection rules. Much like Europe's GDPR, the CCPA gives consumers the right to know what personal information is collected about them and to be able to access it. While the law technically only applies to data processed about residents in California, US. But Mozilla notes it was one of the few companies to endorse CCPA from the outset. Mozilla has now outlined the key change it's made to Firefox, which will ensure CCPA regulations benefit all its users worldwide. The main change it's introducing is allowing users to request that Mozilla deletes Firefox telemetry data stored on its servers. That data doesn't include web history, which Mozilla doesn't collect anyway, but it does include data about how many tabs were opened and browser session lengths. The new control will ship in the next version of Firefox on January 7, which will include a feature to request desktop telemetry data be deleted directly from the browser.6 -
Last year my boss made me develop a way to "creatively" feature ads on our online magazine.
It was a piano keyboard. Yes, I created a pure HTML and CSS piano. Every key had a small title, when HOVERED emitted a sound (tuned on D btw ) and when clicked opened a pop up with the ad content. We tried a black and white piano and also a rainbow-like coloured one.
I strongly advised against everything. We're small and I have a good relationship that soured because he thought I was just being lazy.
Guess what happened? Advertisers saw the live piano and ran away. Hours and hours of development thrown away.
Please. Trust your front-end developer.3 -
Who thought it would be a good idea to limit the length of a dns record to 255 chars?
Is one really not allowed to use a proper dkim key in 2018!
The funny thing was that they just cut off the rest without informing the user!
Had to convince the guy to switch dns „provider“9 -
"One misstep from developers at Starbucks left exposed an API key that could be used by an attacker to access internal systems and manipulate the list of authorized users," according to the report of Bleeping Computer.
Vulnerability hunter Vinoth Kumar reported and later Starbucks responded it as "significant information disclosure" and qualified for a bug bounty. Along with identifying the GitHub repository and specifying the file hosting the API key, Kumar also provided proof-of-concept (PoC) code demonstrating what an attacker could do with the key. Apart from listing systems and users, adversaries could also take control of the Amazon Web Services (AWS) account, execute commands on systems and add or remove users with access to the internal systems.
The company paid Kumar a $4,000 bounty for the disclosure, which is the maximum reward for critical vulnerabilities.6 -
Let's talk a bit about CA-based SSH and TOFU, because this is really why I hate the guts out of how SSH works by default (TOFU) and why I'm amazed that so few people even know about certificate-based SSH.
So for a while now I've been ogling CA-based SSH to solve the issues with key distribution and replacement. Because SSH does 2-way verification, this is relevant to both the host key (which changes on e.g. reinstallation) and user keys (ever replaced one? Yeah that's the problem).
So in my own network I've signed all my devices' host keys a few days ago (user keys will come later). And it works great! Except... Because I wanted to "do it right straight away" I signed only the ED25519 keys on each host, because IMO that's what all the keys should be using. My user keys use it, and among others the host keys use it too. But not by default, which brings me back to this error message.
If you look closely you'd find that the host key did not actually change. That host hasn't been replaced. What has been replaced however is the key this client got initially (i.e. TOFU at work) and the key it's being presented now. The key it's comparing against is ECDSA, which is one of the host key types you'd find in /etc/ssh. But RSA is the default for user keys so God knows why that one is being served... Anyway, the SSH servers apparently prefer signed keys, so what is being served now is an ED25519 key. And TOFU breaks and generates this atrocity of a warning.
This is peak TOFU at its worst really, and with the CA now replacing it I can't help but think that this is TOFU's last scream into the void, a climax of how terrible it is. Use CA's everyone, it's so much better than this default dumpster fire doing its thing.
PS: yes I know how to solve it. Remove .ssh/known_hosts and put the CA as a known host there instead. This is just to illustrate a point.
Also if you're interested in learning about CA-based SSH, check out https://ibug.io/blog/2019/... and https://dmuth.org/ssh-at-scale-cas-... - these really helped me out when I started deploying the CA-based authentication model.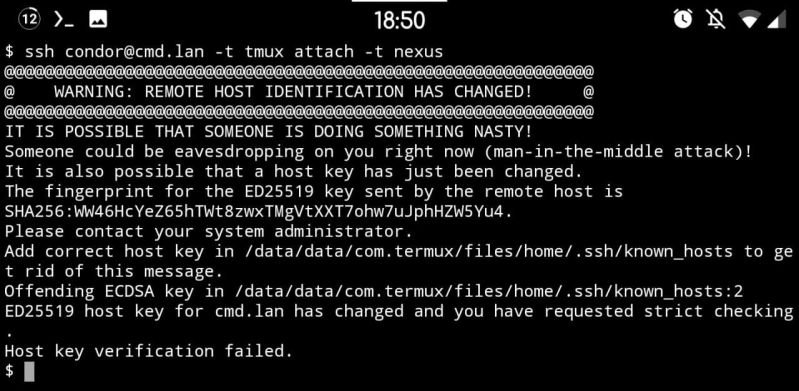 19
19 -
Am I the only one who frequently forgets to hit the insert key again when I'm done with it and then go and accidentally overwrite some other stuff unintentionally?
 4
4 -
IT'S CAPS RANT TIME!
MYSQL ERRORS ARE SO USELESS! AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHHHHH
I JUST WANT TO ADD A FOREIGN KEY BUT 'Cannot add foreign key constraint' KEEPS COMING UP, AND THE STACK OVERFLOW ANSWERS INDICATE THAT IT COULD BE -LITERALLY- ANYTHING!
THIS IS OF COURSE, AFTER PHPMYADMIN GIVES ITS OWN ERRORS FOR TRYING TO USE THE DESIGNER TO ADD THE RELATION. IT ONLY WANTS UNIQUE FOREIGN KEYS, DESPITE ONE OF THE MAIN USES OF FOREIGN KEYS BEING MANY-TO-MANY AND ONE-TO-MANY RELATIONS!3 -
The most unrealistic deadline I got was the project must complete within 16 hours.
Setting: Freelance
Did I accept this? No
Client budget: 10 usd
What is the project? A iOS app which is the a combination of all LLM into one, like a clone of Poe. The API key must use my own because client refused to pay. I negotiate about the project, explain to him why this project, deadline and the budget is not aligned He said " Now everything can be done by using AI, why are yoh cheating me, i will report you" ( I was like report what?) I rejected the gig, then day's later my email junk folder is occupied with racist content and insulting me.
So yea. This is the whole story. This project is doable, just a wrapper. I don't mind if client will pay for all the API , the pay and dealings is logical.25 -
We have a new hire, and he doesn't know much so he is receptive when given feedback on better ways to handle a situation...Or at least, he appears that way. Until the next time and he didn't listen at all.
Today I'm working on the front end to match his API calls. I ask him about a list of options for one of the fields, as he didn't provide that info initially. No worries, there was a lot, easy to miss. He responds with a list of ~100 options, which he copied and pasted from, I'm assuming, their documentation. I tell him that's too many options to hard code, as there is an easy chance to have an error or for there to be one added or deleted, and ask if there is an API endpoint to get the list.
He then asks if I need the key and value, or just key. I tell him if he needs the value(human readable) then he can send me just the value, otherwise both. He says he just needs the key, so I let him know that I need both then, as the value is human readable. He says okay.
He proceeds to make the endpoint, I test it. Then I look at the code he wrote. Not only did he not send me both, he just sent the keys, but he hard coded all 100 keys as opposed to making the call to the external API.3 -
Core library was giving serious blow out of execution speed as data file size increased.
Traced it back to a GetHashCode implementation that was giving too many collisions for unequal objects, so when used as the key in a hash table it was causing the lookup to fall back to checking Equals (much slower).
Improved the GetHashCode implementation, and also precalculated it on construction (they were immutable objects), and run time went to warp speed! Was very happy with that.
Obviously put in a thread sleep to help manage expectations with the boss/clients going forwards. Can’t give those sort of gains away in one go. Sets a dangerous precedent.1 -
tl;dr Do you think we will any time soon move from editing raw source code? Will IDE or other interfaces allow us to change the code in graphic representation or even through voice?
---
One thing I found funny watching Westworld is how they depicted the "programming" - it is more like swiping on a smartphone, a bit maybe like Tom Cruise's investigations in Minority report. Or giving certain commands and key words by voice.
There was one quote from Uncle Bob's "Clean Code" I could never find again, where he said something along the lines, that back in the seventies or eighties they thought they would soon raise programming languages to such a high level they would use natural language interfaces, and look at us now, still the same "if's".
So I feel uncomfortable without my shell and having tried a graphical programming language once this particular (Labview) seemed clumsy to me at best. But maybe there are a lot of web devs here and it seems with them frameworks you might be able to abstract away a lot of the pesky system programming... so do you feel like moving to some new shiny programming experience or do you think it will stay the same for more decades as the computer is that stupid machine where you have to spill it out instruction by instruction anyways?7 -
Got to scratch of one of three remaining old (14years and counting) design mistakes this week.
Together with a colleague we replaced a 1.5 billion row table that I out of ignorance then designed with a 3 column composite primary key instead of an identity column.
Moving the data while keeping all synchronized (the table gets up towards 2 million new rows and 2 million updates a day while constantly being queried) took 1 week.
Just 2 skeletons left to clean out, any year now ;).1 -
Urgh. One key skill that wannabes seem to forget is patience. Patience, patience, patience. Don't panic, don't be lazy, be methodical. This is the way of the analytical computer scientist. Don't panic all over the place or make assumptions..
Some techs..4 -
Just discovered one of our core systems had literally used api key validation of "drop into database, if exists, its fine"
Well, around 30 seconds later, I have successfully authenticated with apikey "%". Wonder why.... Sigh... Patch already pushed, but still it left bad taste in my mouth...
lesson for beginers:
validate, validate, validate. If user could touch it, treat is as broken unsafe and if used it will nuke your home. check if it will, than use it. -
Not much of a haxk, just a stupid thing that works.
In my hs videogame programming class, the teacher has this program called LANSchool (most of you have heard of it) which he used to restrict apps/browsers to the point of uselessness . He didn't (and still doesn't) know anything about the stuff he 'teaches', most is tought by TAs.
Here's the dumb part: he WHITELISTED APPS. A friend, one of the TAs, figured out that if you rename something 'Google Chrome', lanschool wouldn't care. So I got Chromium (for unblocked internet) and switched its blue icons in the exe for original chrome icons, then renamed it 'Google Chrime'. Woo.
LANSchool is such a bad program (you can even unblock a site by spamming the F key for refresh).
The teacher did, and still does, treat the TAs like trash. He's a babysitter while students listen to online vids and the TAs.2 -
Started a job as a full stack developer. My first task was shocking! Do these small edits on this backend script that collects stuff from one database and edits the entries in another... piece of cake so far!
Here is the project on the TFS...
HOLD ON! IS THIS VISUAL BASIC?!!
I came here to do .Net framework development and .Net Standard... I wasn’t told that there will be VB, I have never used vb.net before.
Now... that I’m going to maintain this script in the future, I decided to rewrite it in C#, few things I learned on my journey of doing this:
1- There is an access modifier in VB called Friend
2- There is a data structure/type called Collection, it’s a value,key pair! Not key value pair... Value first, then key!!
3- Do you know how null is null everywhere?!! In VB they call it Nothing! Yes, as in...
if(myVar == nothing)
{
//stuff
}
Asking the guy responsible for that choice... he thinks VB is easier to read than C#
I DONT WANT YOU TO READ IT, I WANT IT TO MAKE SENSE AND WORK WITH THE REST OF THE C# CODE WE HAVE!!9 -
I spent a month trying to understand how to split our application and setup a pdf server to manage 10'000> pdf documents generation at the same time.
Today during our monthly meeting, our dear Key Account Manager, said he's not selling pdf generation to customers since one year at least, and he's not planning to sell it in the future.
Nobody knew about that apparently. We had also some demo guys showing actually the functionality to potential customers.
Also nobody believe me when I say we should start a project to monitor used functionalities in our application.
Just wasted one month of my fucking extra-time. Now I'm late with a lot of other tasks, apparently more urgent that the potential scalability issue of a functionality we don't use.
Key Account Manager rules.
Key Asshole Manager.
I think we should hire a Key fucking-COMMUNICATION Manager -
So yeah XML is still not solved in year 2018. Or so did I realize the last days.
I use jackson to serialize generic data to JSON.
Now I also want to provide serialization to XML. Easy right? Jackson also provides XML serialization facitlity similar to JAXB.
Works out of the box (more or less). Wait what? *rubbing eyes*
<User>
<pk>234235</pk>
<groups typeCode="usergroup">
<pk>6356679041773291286</pk>
</groups>
<groups typeCode="usergroup">
<pk>1095682275514732543</pk>
</groups>
</User>
Why is my groups property (java.util.Set) rendered as two separate elements? Who the fuck every though this is the way to go?
So OK *reading the docs* there is a way to create a collection wrapper. That must be it, I thought ...
<User typeCode="user">
<pk>2540591810712846915</pk>
<groups>
<groups typeCode="usergroup">
<pk>6356679041773291286</pk>
</groups>
<groups typeCode="usergroup">
<pk>1095682275514732543</pk>
</groups>
</groups>
</User>
What the fuck is this now? This is still not right!!!
I know XML offers a lot of flexibility on how to represent your data. But this is just wrong ...
The only logical way to display that data is:
<User typeCode="user">
<pk>2540591810712846915</pk>
<groups>
<groupsEntry typeCode="usergroup">
<pk>6356679041773291286</pk>
</groupsEntry>
<groupsEntry typeCode="usergroup">
<pk>1095682275514732543</pk>
</groupsEntry>
</groups>
</User>
It would be better if the individual entries would be just called "group" but I guess implementing such a logic would be pretty hard (finding a singular of an arbitrary word?).
So yeah theres a way for that * implementing a custom collection serializer* ... wait is that really the way to go? I mean common, am I the only one who just whants this fucking shit just work as expected, with the least amount of suprise?
Why do I have to customize that ...
So ok it renders fine now ... *writes test for it+
FUCK FUCK FUCK. why can't jackson not deserialize it properly anymore? The two groups are just not being picked up anymore ...
SO WHY, WHY WHY are you guys over at jackson, JAXB and the like not able to implement that in the right manner. AND NOT THERE IS ONLY ONE RIGHT WAY TO DO IT!
*looks at an apple PLIST file* *scratches head* OK, gues I'll stick to the jackson defaults, at least it's not as broken as the fucking apple XML:
<plist version="1.0">
<dict>
<key>PayloadOrganization</key>
<string>Example Inc.</string>
<key>PayloadDisplayName</key>
<string>Profile Service</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist
I really wonder who at apple has this briliant idea ...2 -
👨🏽💻 Switching between multiple Git accounts: work, personal, freelance?
Ever pushed a commit with Company A's email to Company B's repo? 😩🥶
Been there. Done that. Regretted it immediately.
I just dropped a step-by-step guide on how to set up Git so it automatically picks the right name, email, and SSH key based on your project folder.
No more manual config switching. 💡
✅ No more identity mix-ups
✅ No more commit shame
✅ Just clean, context-aware Git workflows 🙌
🔧 What’s inside:
- Multiple SSH key setup
- Smart .gitconfig using includeIf
- Folder structure that keeps you sane
- Bonus tips for HTTPS + personal token users
If you’ve ever yelled at Git (or yourself), this one’s for you.
👏 Drop a clap if it helps and follow for more dev-friendly tips!
👇 Read it here:
https://rhymezxcode.medium.com/how-... -
Been getting a lot of troll / clown / clueless (?) comments on my posts recently. Select favorites include:
"Why do you have a login form on your website?" wut
"Why didn't you throw away that API key?" wut
"Why do you even need to access your apps' servers?" wut
There are just SO many amazing devs here who have NEVER had do any of those things, I'm quite literally an idiot and don't know what I'm doing, sorry for my ignorance. I'd forgotten that there is only exactly one way to build software, I wish I'd done it "that" way sooner! Foolish me.
Really not sure if trolls, clowns, or clueless. Don't care. 🤡🤡🤡9 -
When I think "the fundamental problem", the closest thing that comes to my mind is "unsolvable problem". P =/!= NP is a fundamental problem, the theory of everything is a fundamental problem.
But we actually solved at least one such problem – the fundamental problem of cryptography.
The problem was "how to establish a secure connection over a non-secure channel?" Like you can't exchange the key, it'll be exposed by definition.
We solved it with a simple yet brilliant solution of asymmetrical cypher, that thing with public and private keys.
It's fascinating to think that people died in WW2 over this, there were special operations to deliver fresh deciphering keys securely and now SSH and HTTPS are no-brainers that literally everyone use.10 -
One thing that @scout taught me is to wear the oxygen mask myself before helping others. Oh she is a sweetheart.
This advice has stuck with me since and slowly & steadily, I am regaining my lost confidence and self love.
Remember, how I was struggling for clarity a couple of months ago? But now, I feel more clear in head.
During the start of the pandemic, I joined a community of corporate normies. I used to live happier until that decision.
That place made me ultra competitive and I subconsciously became a rat trying to win the race. I damaged myself more than I benefited.
I joined at the time of inception. Every core member is a good friend.
Now the fun thing is, they moved to Slack. Many of the core members run the community as admins.
While I don't engage much, but talk to some of them occasionally.
One key area is, running a job board to help people get jobs. And another is mentorship to help the members overcome challenges and grow in their career.
In DMs, literally every core member who is doing this for others is struggling themselves for the same. How fucking ironic!
They seek help and advice from me and vent out their failure frustrations.
Imagine, someone who isn't able to solve their problem, let alone solving it first before helping others, is guiding the community of few thousands to excel in their careers.
Fucking brilliant.
One of the biggest life lessons @scout taught me, wear your oxygen mask first before helping others.48 -
Fucking christ this year is a fucking shitfest:
- wpa2 krack
- "DUHK Attack Lets Hackers Recover Encryption Key Used in VPNs & Web Sessions"
- "Hacker Hijacks CoinHive's DNS to Mine Cryptocurrency Using Thousands of Websites"
- "Bad Rabbit: New Ransomware Attack Rapidly Spreading Across Europe"
My fucking router didn't yet get patched, my fucking phone is outdated and I can't change to my patched one because devrant just shits the bed in extended desktop mode. Windows 8.1 loses support in 3 months, rendering my last chance of using it on my surface pro done, making me use windows 10 with its fucking shit ass not optimized tablet interface. I have just fucking constant paranoia what else could be hacked tomorrow, nothing is fucking safe anymore for fucks sake. I even went as far as implement 3 step auth and intrusion detection on my shitty ass VPS nodes, fucking give me a break you fucking assholes.5 -
Meeting at 'Derp & Co', the topic was what data model should send the back-end to frontend & app via API calls:
- Coworker: 'we should send the data structured like this for reasons'.
- Me: 'Yeah, this nested object.object.object should do the trick for the front end, but this will be a pain in the ass to convert to POJOs. Why not use something like idk better structure?'
<Mad/intrigued faces>
- CoworkerS: 'Why you need to use POJOs?'
- Me: <More Mad> 'cause I work with java in android... and we have/need/like objects?
<Captain Obvious left the room>
- CoworkerS: 'Oh yeah, well... we can do it the way you say'.
Why you need Objects... what is the next?
- Git? For what? Did not have the usb key from day one?2 -
Dockers JSON output is garbage.
First, you'll get no JSON per se.
You get a JSON string per image, Like this:
{...} LF
{...} LF
{...} LF
Then I tried to parse the labels.
It looked easy: <Key>=<Value> , delimited by comma.
Lil oneliner... Boom.
Turns out that Docker allows comma in the value line and doesn't escape it.
Great.
One liner turns into char by char parser to properly tokenize the Labels based on the last known delimiter.
I thought that this was a 5 min task.
Guess what, Docker sucks and this has turned into try and error...
For fucks sake, I hated Docker before, but this makes me more angry than anything else. Properly returning an parseable API isn't that hard :@3 -
Today I Fucked Up. I tried to do something involving hardware.
I tried to fix my mechanical keyboard by myself with no thought towards how electronics work. My first time using a soldering iron and trying to fix something myself.
I went from needing to replace one key to burning some plastic, failing to get new solder onto the parts to attach the new key to the PCB and getting solder where I didn't want it to needing a new keyboard because I think I've fried some stuff so badly half the bottom row of keys no longer works.
Fucking wonderful.
Guess it's time to buy a new keyboard.
Sigh. 4
4 -
For hours I spent my time debugging my code, trying different approach to the same code function. Looking for one simple invisible mistake, that is when I want to make a delete request to the IndexedDB.
The request are fine without running a single error, the success event fires perfectly. But one thing which is unexpected, the object inside IndexedDB did not vanish at all. The data stay the same without any flaws (but how can that be, when the 'delete success' event fired? IT SHOULD BE GONE BY NOW!). No kidding, for hours I debug my code, yet found nothing's wrong!
Until one moment I found out the datatype of key I gave the request are different from the object I wanted to delete, the object has a key of 4 and I gave the request "4". I'm so pissed at this moment making me googled 'developer rant' and found this site.
Really! God Bless 1 !== '1'.5 -
I haven't touched algorithms for many months but needed to create a matching algorithm today.
It has to match using variations of the original key and output the keys that can't be matched.
The feeling in my head felt like I was turning rusty gears n sort of just stumbling through...
I used an N^2 approach but afterwards it just felt wrong... And it took me like an hour of hacking to do it....
Actually I just realized it's an N approach! because all possible matches would be hit by iterating from one of the lists of possible names!
I suddenly feel so proud of my subsconcious...
But still something doesn't feel right...1 -
Hahah the other day I broke the bracket key on my keybord from pressing it while coding and had to buy a new one.
Everyone asked me how I broke the 0 key before the E.4 -
techie 1 : hey, can you give me access to X?
techie 2 : the credentials should be in the password manager repository
t1 : oh, but I don't have access to the password manager
t2 : I see your key A1B2C3D4 listed in the recipients of the file
t1 : but I lost that key :(
t2 : okay, give me your new key then.
t1 : I have my personal key uploaded to my server
t1 : can you try fetching it?
t1 : it should work with web key directory ( WKD )
t2 : okay
t2 : no record according to https://keyserver.ubuntu.com
t1 : the keyserver is personal-domain.com
t1 : try this `gpg --no-default-keyring --keyring /tmp/gpg-$$ --auto-key-locate clear,wkd --locate-keys username@personal-domain.com`
t2 : that didn't work. apparently some problem with my dirmgr `Looking for drmgr ...` and it quit
t1 : do you have `dirmngr` installed?
t2 : I have it installed `dirmngr is already the newest version (2.2.27-2)`
t2 : `gpg: waiting for the dirmngr to come up ... (5)` . this is the problem. I guess
t1 : maybe your gpg agent is stuck between states.
t1 : I don't recall the command to restart the GPG agent, but restarting the agent should probably fix it.
t1 : `gpg-connect-agent reloadagent /bye`
source : https://superuser.com/a/1183544
t1 : *uploads ASCII-armored key file*
t1 : but please don't use this permanently; this is a temporary key
t2 : ok
t2 : *uploads signed password file*
t1 : thanks
t2 : cool
*5 minutes later*
t1 : hey, I have forgotten the password to the key I sent you :(
t2 : okay
...
t2 : fall back to SSH public key encryption?
t1 : is that even possible?
t2 : Stack Overflow says its possible
t1 : * does a web search too *
t1 : source?
t2 : https://superuser.com/questions/...
t2 : lets try it out
t1 : okay
t2 : is this your key? *sends link to gitlab.com/username.keys*
t1 : yes, please use the ED25519 key.
t1 : the second one is my old 4096-bit RSA key...
t1 : which I lost
...
t1 : wait, you can't use the ED25519 key
t2 : why not?
t1 : apparently, ED25519 key is not supported
t1 : I was trying out the steps from the answer and I hit this error :
`do_convert_to_pkcs8: unsupported key type ED25519`
t2 : :facepalm: now what
t1 : :shrug:
...
t1 : *uploads ASCII-armored key file*
t1 : I'm sure of the password for this key
t1 : I use it everyday
t2 : *uploads signed password file*
*1 minute later*
t1 : finally... I have decrypted the file and gotten the password.
t1 : now attempting to login
t1 : I'm in!
...
t2 : I think this should be in an XKCD joke
t2 : Two tech guys sharing password.
t1 : I know a better place for it - devRant.com
t1 : if you haven't been there before; don't go there now.
t1 : go on a Friday evening; by the time you get out of it, it'll be Monday.
t1 : and you'll thank me for a _weekend well spent_
t2 : hehe.. okay.8 -
My company provides its services as web pages and web services to our customers.
Once a year we update the certificate used for the https connections.
I notified the update to the clients that use the web services.
One of them asked me a copy of the public key.
No problem. Open the web site with the browser, save the key and send by email.
One day later the client asked me the public key in a zip file because the anti virus blocked my attachment.
Why the client hates the Chain of Trust ?
He could obtain the public key by them self from the browser or openssl.1 -
Coding for me has been such a heartache and a relief at the same time. Having an outlet for my brain activities has improved my mental and emotional health significantly.
It also thought me a couple of valuable lessons:
1. With enough efford you can accomplish pretty much anything
2. You're not the only one struggling with issues, life or code related.
3. Moronic people can be found everywhere you look.
4. Patience is key to grow as a human being. -
I started out on a Sinclair ZX 80. It has just 512 bytes of ram and you had to use a function button together with a key for each command since it did not have enough memory to keep the source in memory ;)
I attended few basic courses and then went on to hold them.
After a year there was suggestions of starting pascal courses so during the summer I read up in turbo pascal 5.5 but since the summer home did not have electricity I had to do it all theoretically for the first month before getting to try it out.
I got to try visual basic when doing school practice with Microsoft but the name was not set by then as it was a few months before the release.
Thats also where the more professional programming got going even though I did one pascal program that was used professionally before that. -
Coding chalenge.
So... Spent almost two hours to put this little device to work with the keypad.
The device is a arduino micro, special one that can work as mouse /keyboard or any kind of input on most devices (pc, Android phone,...)
The objective is to make a macro keypad to:
- Fast insert text
- Play sounds in games over voice chat.
Think of it like this, you start a new html file, press one key and all the base code is inserted.
So... Why so long? Tought was the hardware, tought the keypad could be set differently that most, code mistakes...
My error was all here, masked from the debugger by a if:
char keys[ROWS][COLS] = {
{'1','2','3','4'},
{'5','6','7','8'},
{'9','10','11','12'},
{'13','14','15','16'}
};
Easy to figure right? Only saw it after reading all the code twice. 9
9 -
Sooooo.....
I just spend roughly 5 hours trying to get a Laravel Homestead up and running. Constantly jumping from one error to the other, getting nowhere.
Turns out that,
...
...
I NEVER FUCKING GENERATED A BLOODY SSH KEY
ARE YOU FUCKING KIDDING ME
AN ENTIRE DAY WASTED
JESUS CHRIST
I swear, I'm way too junior for like 95% of this shit....5 -
I've finally found a goldmine of accurate job listings that don't include Windows shit-administration... So I'm thinking of sending out applications to all of them. Problem is, as you might recall from my previous rants, I had a flash drive with my GPG keypair on it stolen from me. I still haven't fully replaced the key (I made another one and published it but I'm not using it yet), and because I'm fairly confident that this flash drive's data has never been used (so likely just plugged into Windows and formatted), it's unlikely that I'm gonna bother rotating all of the contents that were on that flash drive.
That said however, my emails now all have signatures underneath them as follows:
Met vriendelijke groet / Best regards,
[my name]
- My outbound email is usually signed with my private key. If not, please don't hesitate to ask me about it through a different communication platform.
IMPORTANT: My keys have possibly been compromised. An encrypted flash drive on which this GPG keypair was stored has been stolen from me. I'm in the process of phasing out and replacing this key. Please do not use it to encrypt any emails to me anymore.
Not entirely sure whether I should remove or keep that last bit. As a potential employer, would you see this as a red flag (he's got encrypted data stolen from him, wtf that's incompetent), or as a nice thing to know that it was properly disclosed (so no secrecy around potential data breaches)? Both seem equally likely so I'm a bit confused about what I should do.9 -
One hour before demo.
clone,compile and run.
Guess what..?
Most of the key module aren't working
Guess why..?
I forgot to push final changes to git (after pulling an all nighter) -
))| THE BEST AND WORST WAY|((
))| TO DELETE A LINE IN BASH |((
(Think you can do better? Vote
now on your phones!)
WORST: Hold backspace until satisfied
BEST: Using a pen or other pointing device capable of causing semi or permanent damage to your screen, count how many characters the line in question consists of. Write this down on a piece of paper (after all, your terminal is occupied) and using long division, or any other means, divide this number by two, rounding as you please. Press the "right arrow" key as many times as necessary to reach the end of the line. This might be 0 - if so, congratulations, you may skip this step! Once complete, refer to your piece of paper, and taking your newly calculated number, press the "left arrow" key exactly that many times. If you have a short attention span or are worried you will lose count, take a tally or use some other primitive count recording method. Once the key has been pressed the correct number of times, hold down either control key on your keyboard and take a deep breath - there's no going back now (!) - press the "k" key (you should still be holding a control key!) and take a sigh of relief. You're halfway there! If you need a break, take one. When you're ready to finish the task, hold a control key again and take another deep breath. When you are ready to complete the task (don't hold your breath too long!) press the "w" key. Congratulations!! Your line has been deleted!! Some may call you a fucking idiot for not just pressing ctrl-w at the start, but don't listen to those people! They probably delete stuff by accident all the time! Now, take a lie down, and give a moment's silence for the poor poor line you just brutally dissected and murdered.
Think you can do better? Vote now on your phones!9 -
Meetings would be better without people.
I mean I like the IDEA of meetings...
Honestly I'm the type of person who if I could would schedule lots of meetings to make sure we're all on the same page, and to be sure the thing is going to do the thing everyone wants / get their perspective, etc. I really want to KNOW what the folks who are going to use this thing need / want / what works best for them.
On the other hand I know that meetings are often more like:
Me: "Ok let's so here's our data, now tell me what fields they want to edit and so forth."
People: "All of them."
Me: "Uh, no you don't want that or they'll break everything ... X, Y and Z require those fields for A, B, and C to work."
Me: "Let's go field by field and you tell me if they need to edit it, and why."
People: "Yeah this first one they have to be able to change this one."
Me: "Wait no, that's the primary key for that table, I don't know why that's on this list but no you can't change that."
People: "Yeah we have to be able to change that."
Me: "No, you can't, do you even know what that number IS?"
People: "Um... no ..."
(╯°□°)╯︵ ┻━┻1 -
Spent all morning debugging a script I wrote to compare 2 CSVs of tables from 2 different dbs.
It generates a unique key for each row using the data.
For some reason couldn't match 1 in each...
After all morning of debugging and scrutinizing the data in the dbs itself... I found the root cause....
One for loops in the program skips the first entry... -
some shitty scam site is "giving away free gams" like Hello Neighbor, FNAF, etc.
Someone asked me to look at one of their EXEs.
Electron app with nothing really going on and a hardcoded key.
Turns out all this shit is systematic. A couple splash screens and a config file for "download" size, name, key, download page, etc. and they're immediately ready to ship the cookie-cutter scam program meant for "free license key BUT SURVEY FOR OUR PROTECTION" ad revenue.
Have source of the Hello Neighbor one i guess?
(jesus, 204MB of source for an 8MB dropper app???)
https://drive.google.com/open/...1 -
New MacBook Pro: one type of connection port, no MagSafe, base drive is 256gb, and they killed off the goddamn physical esc key.
Apple you dumb.1 -
Mozilla really knows how to nudge one to not use email encryption by default.
Since Thunderbird has native support for OpenPGP encryption, i can only chose to encrypt all or no messages by default. There is no opportunistic mode and there are no per-reciepient encryption preferences. The Enigmail addon had both.
So i obviously have gone for encrypt-by-default.
But since then, whenever i want to send a message to the majority of my contacts, i have to manually disable the encryption or get annoyed by the no-key-found dialog.
I thought, i would get the muscle memory to just disable encryption for recipients for wich i don't expect to have a key.
But they also made the GUI so i have to open a dropdown and then click on the right item to do that. All the items basically look the same, as there is no color coding or specific icon for them. The item labels are also too long for unconscious pattern recognition.
So i didn't got that muscle memory.
I now have turned off encryption by default and will probably forget to enable it for some emails wich i actually could send encrypted...4 -
Asked to implement a feature in a mobile app that wasn't actually supported by the backend. Feature had 3 possible values in the backend, only 1 and 2 were properly implemented. Below was the backend teams solution to support the third option.
- If the key is missing in API response A, means the user is not allowed access this feature.
- If the key is present in API response A, and missing from API response B, that means it hasn't been set.
- If both are the same value, user has that value.
- It will never be the case that both return option 3.
- If both are different values, one of them being option 3, display option 3.
this ... monstrosity, is in production to this very day. -
I work for a cryptocurrency exchange as a senior developer - I'm pretty much one of the key people keeping the lights on in terms of backend and operational functions.
Yet I'm sitting in the bank trying to extend my credit card limit, just to makes ends meet.5 -
Didn't think I had material for a rant but... Oh boy (at least at the level I'm at, I'm sure worse is to come)
I'm a Java programmer, lets get that out of the way. I like Java, it feels warm and fuzzy, and I'm still a n00b so I'm allowed to not code everything in assembly or whatever.
So I saw this video about compilers and how they optimize and move and do stuff with the machine code while generating the executable files. And the guy was using this cool terminal that had color, autocomplete past commands and just looked cool. So I was like "I'll make that for my next project!"
In Java.
So I Google around and find a code snipped that gives me "raw" input (vs "cooked" input) and returns codes and I'm like 😎. Pressing "a" returns 97 (I think that's the ASCII value) and I think this is all golden now.
No point in ranting if everything goes as planned so here is the *but*
Tabs, backspaces and other codes like that returned appropriate ASCII codes in Unix. But in windows, no such thing. And since I though I'd go multiplatform (WORA amarite) now I had to do extra work so that it worked cross platform.
Then I saw arrow keys have no ASCII codes... So I pressed a arrow key and THREE SEPARATE VALUES WERE REGISTERED. Let me reiterate. Unix was pretending I had pressed three keys instead of one, for arrow keys. So on Unix, I had to work some magic to get accurate readings on what the user was actually doing (not too bad but still...). Windows actually behaved better, just spit out some high values and all was good. So two more systems I had to set up for dealing with arrow keys.
Now I got to ANSI codes (to display color, move around the terminal window and do other stuff). Unix supports them and Windows did but doesn't but does with some Win 10 patch...? But when tested it doesn't (at least from what I've seen). So now, all that work I put into making one Unix key and arrow key reader, and same for Windows, flies out the window. Windows needs a UI (I will force Win users, screw compatibility).
So after all the fiddling and messing, trying to make the bloody thing work on all systems, I now have to toss half the input system and rework it to support UI. And make a UI, which I absolutely despise (why I want to do back end work and thought this would be good, since terminal is not too front end).2 -
So I do not get why people use ReactJS. I hate it. for 3 years passionately. And I have to work with it every day.
- one-way data binding
this makes you write twice as much code, which will have twice as much bugs, you need to read through twice as much code from other devs.
- mixing html and JS
after all I like to pour my coffee on my omlette so I can eat and drink at the same time in the morning. This kills productivity and ugly AF
- not unified
Every dev uses their own special snowflake framework with React there is no unified way of doing things and you cannot use your familiar tools. Every project you need to start over from zero.
- Bugs bugs bugs
infinite loops, max update depth reached, key not present on list element. Let me ask you something dear ReactJS. If you know that there should be a unique key on that element. Why cannot you just put it there and shut the f up?
- works reeaally slow when compiled with TS
ReactJS was never designed to work with TS and now the tools for it are really slow. And why TS? Explicit contract is always better than an implicit contract. TS helps you in coding time, but for some reason React devs decided to worth 3 seconds to wait for compile and then realize you mad an error. ReactJS is bad and inefficient so stop making projects with it please.9 -
I use mainly linux at home, but I have to use Windows at work. I don't hate Windows, but at least once per day at work I accidentally try a keyboard shortcut from my Arch + i3 setup and either end up with some random program from the start menu running (Windows key used in i3) or I flip one of my screens sideways... Nothing detrimental, just enough to be aggravating.1
-
This supposed to be a rant but I have no words to describe in how big fucking mess I am right now while looking for a new workplace...
It’s most unorganized experience that I am part of...
It’s worse then looking for lost key using bare hands in a shit hole....
With last one at least you know what to expect and you have some chances to make some decisions. The hiring otherwise it’s like lottery...
There are no words to describe it.
Fuck...
Let everyone looking for a job right now have my condolences... -
I can't convince my team that a good database model promotes a good API design and a good UI/UX experience.
Instead, I have to work with a ridiculous table setup.
Imagine, if you will, a table (table B) that references another table (table A) via a foreign key. The FK is a string in both tables. And table A only has one column, which is labeled as "name".
The schema i have to look at it kind of like this:
Table parent
Name varchar(10) primary key
Table child
Name varchar (10),
parent_name varchar(10),
Foreign key (parent_name) references parent (name)
Sorry if the syntax is wrong, a little frustrated having to look at it...
Am I crazy to want to change this table design? Am I missing something? I feel like I'm taking crazy pills, because this is just scratching the surface of the problems I have to deal with.7 -
I need to encrypt some large files at rest and then decrypt them immediately prior to processing.
App and files are on a Linux system (CentOS). App is in C. Machine is controlled by a third party.
What encryption libraries would you recommend? And, is there any clever way of managing the decryption key beyond compiling it in the code and doing some basic obfuscation?
Are they fancy obfuscation libraries out there, for example?
And, the reason I'm not going to SO (well, one reason) is that I don't want to have 50 answers that tell me that's it's impossible to 100% protect data on a machine you don't control. This I understand---just looking for "best effort" solution.7 -
I started applying for jobs. As I have over 150 repos on GitHub and 10 years of relevant work experience, the company obviously had trouble validating if I had some basic coding skills. That's why they decided to send me a coding "homework" task to build an app in React Native.
Basically, the task was building an app with 2 screens and one bonus where they indicated "doesn't need a UI". I spent half a day spinning up their project, installing XCode, their specific versions of Ruby, and around half a day building the thing.
Obviously, I wanted to demonstrate my technical skills, so I added a few tests, proper typing, comments, and so on. The project was in a good state, and on the "bonus" screen I quickly added a few components. Since I have a lot of things going on, I capped the amount of time to one day of work. I felt it was good enough to demonstrate I can build something like this.
A few days later, I received a response from the recruiter telling me they wouldn't move forward. She in depth explained that this was because of a missing key property. I did indeed miss one key property on the "bonus" screen, in the part that was not even part of the core task. This was a list of very few static elements, and the entire list only got rerendered when changing routes. Basically in this case, there would not be any visible performance impact.
The recruiter explained in the email that I was missing the eye for detail they need, and that I should "educate" myself more about lists in React. I made one tiny silly mistake in a one-day project, that a linter would've taken out (if this project had one). I've contributed to React Native myself and worked with React for almost 7 years now? Yeah, it's a stupid thing, but what is the point of these types of tasks? I thought this was to demonstrate my skillset, not to be called out on.
Either way, my question here is this: at which point does it become appropriate to send an invoice for the time I wasted on this?5 -
What retarded way of writing a json feed is this? what the fuck!
Each product in the feed is translatable, but instead of creating a new object in the feed with the translated content, there's an additional field pointing to a language code (this applies to all translateable fields).
Then each translatable field is appended the number which matches the number appended to the language field containing the desired language code.
In addition to that, the keys doesn't have any sensible meaning, but appearently they abide by som obscure "GS1 / GDSN" standard.
So for each "distinct" field I have to look up the definition of that key
If just the language code and the actual value keys was grouped together.. but no, the feed is ordered by the number after the 'D'.
Yeah for being stuck with something that looks like infinite scrolling, because one product object is fucking gigantic.
FUCKING INSANE MANIAC PIECE OF TRASH.
@#%!#€& 7
7 -
One of the worst things I did in my career as a developer was that when i had to change an offer form in our SAP System. My boss told me to change the prices in a form in our SAP system. Normally the key users do that but our SAP System is so fucked up that sometimes the developers have to do it because you have to write directly into the database. So I wanted to look up which table it was and what I saw scared me.
IT WAS A FUCKING IMAGE.
So I used paint to edit the prices in the image and re-uploaded the image. Shame on me but I didn't wanted to change that shit. I have other things to do than that. -
New Phrack article. Given they release like one a year, figured it warranted posting a link.
Title : Hypervisor Necromancy; Reanimating Kernel Protectors
Author: Aris Thallas
Date: 2020 Feb 14
"In this (rather long) article we will be investigating methods to emulate proprietary hypervisors under QEMU, which will allow researchers to interact with them in a controlled manner and debug them. Specifically, we will be presenting a minimal framework developed to bootstrap Samsung S8+
proprietary hypervisor as a demonstration, providing details and insights on key concepts on ARM low level development and virtualization extensions for interested readers to create their own frameworks and Actually Compile And Boot them ;). Finally, we will be investigating fuzzing implementations under this setup."
http://phrack.org/papers/...2 -
I know this topic is tired and this isn't supposed to be a pure "REEEE SPACES BAD" kinda rant but I still don't understand why people would ever use spaces over tabs for indentation. I'm genuinely curious so please give me your arguments in favor of spaces because I just don't understand
So here's my position:
Tabs are objectively better than spaces in every single way
(I know that IDEs also do some of these for spaces, more on that later)
1. They are typed with one key press
2. They can be removed with one keypress
3. They allow for individually configurable width (some people prefer 2 and some 4 width)
4. They take up less memory (kinda irrelevant, but still)
5. You can properly navigate your code using the arrow keys which is much faster than using the mouse while typing
6. You don't have problems with accidentially having one too much or one too little
7. You don't have problems when copy pasting or moving code around (e.g. refactoring)
8. Code is much easier to select with the mouse, and
9. it's much easier clicking the right spot with the mouse where you want to continue typing, which is often at the start of a line
Apart from specific alignment, where spaces are fine (but which also almost never comes up), I just can't see a single thing where spaces are better at. So much so that most IDEs have to *pretend* that they're tabs when typing and removing them. It's so ironic yet people still defend it and big companies still use them.
I feel like I'm going mad 😨53 -
Data representation is one of the most important things in any kind of app you develop. The most common, classic way to do it is to create a class with all the fields you want to transport, for example User(name, lastName). It's simple and explicit, but hell no, in my current company we don't play that kindergarten bullshit, the only way we know how to do things here is full hardcore. Why would anyone write a class to represent a Song, a Playlist or an Album when you can just use a key-> value map for pretty much everything? Need a list of songs? No problem, use a List<Map<String, String>>, OBVIOUSLY each map is a song. Need a list of playlists? Use a List<List<Map<String, String>>>... Oh wait, need to treat a value as a number and all you have are strings? That's what casting is for, dumbass.
No, seriously, this company is great. I'm staying here forever!1 -
Why there isn't a special key on the keyboard which includes "; + enter"?
Or in general a keyboard with special keys for developers? 🤔
e.g. open/close brackets with one key, or "/>" as one single key., or ") + {"5 -
When you pause a YouTube video, the § key will seek forward by exactly one frame. Works on Mac, on other systems the key could be different3
-
Me: *Wants to install Office trial to use a key to activate it*
Microshit: You're almost ready to use office. But we we need you to provide payment information to use the trial.
Me: This is one more reason to why a metric fuckton of ppl despise you, Microsoft!8 -
For anyone following, I broke my E key on my laptop keyboard. I ordered a new one and it should arrive tomorrow. I am going to be able to type else and exeception properly after a really long time!2
-
(Fyi: I was an intern.)
It took me hours of time to recognize, that one of the necessary tables just used an oracleDB Date as a timestamp, which lead to a violation of the primary key constraint on interactions taken place in less than one second.
Me: (explaining the problem to CW)
CW: "Yup, we know."
Me: ...2 -
DO NOT EXPORT GPG KEYS _TEMPORARILY_ AND ASSUME THAT THEY'LL BE IN THE ORIGINAL LOCATION AFTER EXPORT!
I learnt this lesson the hard way.
I had to use a GPG key from my personal keyring on a different machine ( that I control ). This was a temporary one-time operation so I thought I might be a smart-ass and do the decryption on the fly.
So, the idiotic me directly piped the output : `gpg --export-secret-key | scp ...`. Very cool ( at the time ). Everything worked as expected. I was happy. I went to bed.
In the morning, I had to use the same key on the original machine for the normal purpose I'd use it for and guess what greeted me? - *No secret key*
*me exclaims* : What the actual f**k?!
More than half a day of researching on the internet and various trials-and-errors ( I didn't even do any work for my employer ), I finally gave up trying to retrieve / recover the lost secret key that was never written to a file.
Well, to be fair, it was imported into a temporary keyring on the second machine, but that was deleted immediately after use. Because I *thought* that the original secret key was still in my original keyring.
More idiotic was the fact that I'd been completely ignorant of the option called `--list-secret-keys` even after using GPG for many years now. My test to confirm whether the key was still in place was `--list-keys` which even now lists the user ID. Alas, now without a secret key to do anything meaningful really.
Here I am, with my face in my hands, shaking my head and almost crying.5 -
Why is school such a bullfuck, we've learned SQL basics and I've used SQL a little so I thought I won't have a problem. WELL FUCKING HELL WAS I WRONG. Joining 4 tables together with inner join WTF who the fuck uses that, why the fuck do I need to know this, WHY THE FUCK IN A TEST WHEN WE HAVEN'T LEARNED SUCH BULLSHIT. Well how about adding a foreign key to a table that doesnt need one. Well ok have fun with a key that does absolutely nothing and on top of all those convoluted tasks the texts are a mess, they give unnecessary information with grammar of a 9 year old and the pictures are not even readable. They are fucking hieroglyphs.
Fuck school.
Gonna do it by myself at the end anyway.
Fuck everything.15 -
Laziest habit? Anything done between 1pm-4:30pm and 4:59pm-8pm. During that time, habits include unnecessary refactoring, poking the CI/CD containers, editing already made prototypes in gimp inkscape, pasting stackoverflow topics to youtube, bouncing from macOS, windows and kde distros in search of zen/rice, adding a calendar emoji on my slack :), making useless automation scripts, building on every variable's value change, tinkering pixels, shades, gradients (and their angles), dimens, anim values, anim curves, opacity, blurs and just nuking the ui just to copy paste an old one, 60% just chatting in code alongs, changing key bindings (from ide to OS), and ultimately zoning out on a podcast about cyber security. And of course: waiting for ++ and comments
-
One of the key person is asking every junior and senior person to build some program for her so she can automate those task.
Well everyone is just ignoring her. She never asked me. Which was kind of insulting for me and now I am thinking I should make that program and send her mail to buy it.2 -
Fucking hashtables...I forgot that removals can screw with the probing sequence, causing later lookups to "randomly" fail after hundreds of operations and elements.
Spent 4 hours staring at 3 while loops and data sets of hundreds of key value pairs trying to figure out why one giant data set worked fine but the other failed on some lookups.2 -
Have you ever been there, when suddenly one/more key of your keyboard stopped working ?
Yesterday, backspace key stopped working on my laptop, I had to complete my work so I started using delete key instead.
Now I'm on my PC and used delete key couple of times even though it's backspace is completely working.2 -
My key ring :)
An old friend (remember the guy who had a miniature Red hat?), gave me an old RAM from a work machine (he worked in data center team).
We had many spare ones so, I picked one and been using it since then.
Photo in comments because dR is fucking up the resolution.5 -
FOR FUCK SAKE Lenovo
bought a Lenovo IdeaPad 700 for my study and added extra ram. the fun began, my battery started jumping from full to empty and now with the extra memory far away back to the factory it is still happening now the store and Lenovo told me to use this piece of shit to go back to factory and see if it still happens. 3
3 -
One day I helped another teacher with setting up his backend with the currently running Nginx reverse-proxy, peace of cake right?
Then I found out the only person with ssh access was not available, OK then just reset the root password and we're ready to go.
After going through that we vim'd into authorized_keys with the web cli, added his pub key and tried to ssh, no luck. While verifying the key we found out that the web cli had not parsed the key properly and basically fucked up the file entirely.
After some back and forth and trying everything we became grumpy, different browsers didn't help either and even caps lock was inverted for some reason. Eventually I executed plan B and vim'd into the ssh daemon's settings to enable root login and activate password authentication. After all that we could finally use ssh to setup the server.
What an adventure that was 😅3 -
My mouse/keyboard(+numpad) combo.
Why does Microsoft think that everyone needs a dedicated key to open the calculator?! I have one on both my keyboard (top-right) and the separate numpad. I used to press the calculator button by mistake when going for backspace - remapped it now. 2
2 -
!dev
TL: DR - This year is not good so far.
One important thing that I learned this year is you understand a certain person's importance after they are no more.
My grandfather, whom I've always hated, ignored, made my distance from him, just because he was unfair with me and my mother since my childhood, passed away a few days before. Only then I realized what kind of a fucking idiot I am.
On top of that, 2 of my best friends stop being friends with me, for one I had gone too far with a practical joke and for another, I proposed her.
But 2 months from now I expect things to be left behind, locked away in a closet, and throw away the key.
So, I'll just say this, that acknowledge person while they are here, don't hold any grudge towards any fucking one.1 -
I used blue switch’s for the last 15 years, I have used bought 3 different keyboards in the that time, all use the mxBlues used blackwidows now using Logitech 54g or whatever it is...
I see these people using membrane or basic bitch keyboards. And I don’t understand how they do it.. I use the clickyness as a feedback for me. I don’t care how loud it is... nobody has complained but I also don’t care lol.
I’ve tried using other keyboards but I can’t type on a non mechanical clicky key.
I want to get one of those IMB retro keyboards, but I want to try one out before I spend the money.5 -
9000 internet cookie points to whoever figures out this shit:
I'm trying to import a secret gpg key into my keyring.
If I run "gpg2 --import secring.gpg" and manually type each possible password that I can think of, the import fails. So far, nothing unusual.
HOWEVER
If I type the same passwords into a file and run:
echo pwfile.txt | gpg2 --batch --import secring.gpg
IT ACTUALLY FUCKING WORKS
What the fuck??? How can it be that whenever I type the pw manually it fails, but when I import it from a file it works??
And no, it's not typos: I could type those passwords blindfolded from muscle memory alone, and still get them right 99% of the time. And I'm definitely not blindfolded right now.
BUT WAIT, THERE'S MORE!!
Suppose my pwfile.txt looks something like this:
password1
password2
password3
password4
password5
password6
Now, I'm trying to narrow it down and figure out which one is the right password, so I'm gonna split the file in two parts and see which one succeds. Easy, right?
$ cat pw1.txt
password1
password2
password3
$ cat pw2.txt
password4
password5
password6
$ echo pw1.txt | gpg2 --batch --import secring.gpg
gpg: key 149C7ED3: secret key imported
$ gpg2 --delete-secret-key "149C7ED3"
[confirm deletion]
$ echo pw2.txt | gpg2 --batch --import secring.gpg
gpg: key 149C7ED3: secret key imported
In other words, both files successfully managed to import the secret key, but there are no passwords in common between the two!!
Am I going retarded, or is there something really wrong here? WTF!4 -
Within the past year, I've been on both sides of the table...the interviewee and the interviewer. No two interviews end up turning out the same way.
I tend to try to give people the benefit of just being stressed. But others can hear a word or two and assume they know key character flaws and all these reasons not to hire some one. -
I used to be proud of my skills using eclipse IDE, then I decided to try IDEA. No regrets, but after 3 months I still not mastered the new key mapping and totally forgot the eclipse one. Now I have no reason to change back at all xD1
-
Just removed an API key from one of my GitHub repos (yeah I know API keys don't belong there) and at the moment i pushed the corrected file, I got an email from GitGuardian that it discovered a key in my Repo although i deleted it. Anyone else experienced something similar?2
-
At internship with a fellow student from my class, making a SqliteHelper class in php to make things easier. Delete methods only have only one parameter (Primary key)
Coworker: "Why do you use the primary key as parameter? The user has no access to it!"
I can't express in words how close I was to snapping. -
Developing on a legacy system today and found that not only did their MySQL db not have foreign key relationships, but one to many relationships were created by adding a concatenated string of pks to the table. Oh and they were concatenated with fucking dots!
-
One of the key principles in Life is acceptance. I just wish some of the codes could understand this....
-
So I’ve been working on a tool to do offline domain joining in an active directory for about a month in my company, and so far everything is functional and done EXCEPT that one thing.
Essentially to do an offline domain junction, you need an AD account that has sufficient privileges on the domain controller. It will then generate a key that you can use on the client machine to make the junction to the domain.
I have tried literally every possible option that I could think of and I cannot for the life of me figure out why the client machine does not accept the generated key. I’m using methods from the Netapi32.dll which are barely documented anywhere, I even searched on GitHub code references and I couldn’t find much… Theres also a tool called djoin.exe that supposedly does that, I’ve tried with that tool too, to no avail.
This is the last thing missing for the project to be complete, and it’s pretty essential as well…
So close yet so far….
If anybody here knows anything about that kind of stuff (admittedly very niche) I’ll take anything.
Note: I think I’ve browsed all the websites and forums referencing to these functions and the tool now… -
The new MacBooks look so nice. And Mojave is pretty nice, and dark theme! And the touch bar! The price is quite high but for the first time I'm actually debating getting one... Almost. But:
Why no escape key apple! You were so close! A physical escape key at the cost of your touch bar being 1 inch smaller! Is that too much to ask!
Many programmers use Mac. I can see why, it's a bsd variant, it's almost a Linux box except it's supported and accepted by the non-geeks of the world.
Many programmers use Vim! It's great!
So it stands to reason that a "not insignificant" amount of Mac users use Vim. Why would you do this to us? Or at least offer a "Vim model! With physical escape key, some nice out of the box vim buttons for the touch bar, a greatly inflated pricetag... Yknow, the works!" But nothing?! You almost had me apple.6 -
I hadn’t seen this interview until now. I was low-key discriminated against at a job, because of my gender, by a hierarchy full of women, and eventually let go. And I wasn’t the only one. This crap just makes me angry. It’s why I always want to be independent and not be directly employed by corporations anymore. https://youtu.be/6NOSD0XK0r84
-
I've left my MacBook to technical assistance for the thrid time. I've bought it on December (the touchbar model, on day one, arrives on December). I paid a lot for it and since then I got s broken key on my keyboard and a faulty display.
Now I got my battery swollen.
Fucking Apple. At least I'm happy with the OS and everything when it's hardware-faults free.
Oh yeah and I switched to MacBook for the construction quality... Bitter irony.
I hope this is the last fucking time, damn.6 -
Alright guys, I need some advice now from you..
My employer is super impressed with my worked and they are willing to relocate me to the US (Seattle).
As you all are aware that I am actively trying to move out of my country but lately have realised that no matter what, it's home.
Also, I am way to close to my mother and don't want to leave her alone for an extended period of time as both my parents are ageing and I cannot be a selfish fuck to ignore them during their last phase of life.
I want to make the most to spend time with them.
Some key points that I need help with
- I am more inclined towards the UK/EU than US
- Need to spend time with parents/family
- Need to secure some cash for some key life moments
Some challenges:
- Cannot take parents along because they'd not be able to settle for more than 1.5 month outside for various reasons
- If I am moving out, why shouldn't I go to a place I love than a place I don't?
Some plans:
Plan A: Move to Seattle (6 months) > FAANG > Get a high paying high in India (all this in 2 year duration) > Settle down > Periodically travel Europe and explore hobbies
Plan B: Move to Seattle (6 months) > FAANG (optional) > Find a job in the UK/EU (4.5 year duration) > Fullfill EU dreams > Get a high paying job in India > Settle > Continue exploring hobbies
Plan C: Stay in India with current company (6 months) > IJP or EJP to the UK/EU (5 year duration) > Fullfill EU dreams > Get a high paying job in India > Settle > Continue exploring hobbies
I need to pick one while keeping in my that I can spend more time with parents and fullfill my dreams as well. I am confident that money will follow and I'll save enough for my retirement. Willing to trade off some extremely high paying jobs for a happier lifestyle.28 -
Some Java code I looked through to figure out how to accurately rework a mapping of value intervals to status colors:
• 16 levels of indentation
• Calls an instance method one line before a null-check
• Assigns that same value to a new variable and null-checks it again
• Insistently loops over existing HashMaps' entry sets to find a value by key
• Stringifies a Gson object, parses back the string and then null-checks the result.
• Mixes up the 'leq' and 'geq' comparison operators twice, which is why I went to check the implementation in the first place.
And this wasn't even legacy code. It's from last year.1 -
This happened last November. I was on my merry way, not using Windows on my laptop. When suddenly a friend asks me to do some heavy video editing work.
And none of the softwares on Linux are as good as Premiere Pro, After Effects etc
Davinci Resolve on Linux has codec issues and is a pain to deal with
Anyway, I boot up windows and somehow it updates itself (I distinctly remember disabling the update service permanently).
So now, it bugs me every fucking minute to reboot.
Luckily I decide to finish my project before rebooting.
Coz as soon as I reboot, it throws me an error saying something like my license key couldn't be verified. One key recovery doesn't help
I have a OEM licensed Windows 10 Home that came with the laptop.
The solutions are to either recover windows, which needs a fucking 11GB download or reinstall Windows (but hey... Lenovo didn't give me a Windows License key. And I have a lot of pre setup folders on the windows drive linked to my Linux, making it a bad choice to wipe that drive). To put the cherry on the top, I have to download a software that Lenovo provides (Windows only) to download that 11GB iso.
Every sane person around me uses Linux (I only used Windows for Video Editing)
Also, living in India, 11GB is a fucking big size to download.... And the software doesn't support interrupted downloads
One more pain in the ass....
So, fuck you Windows. Fuck you Lenovo.
Living happily with elementary OS since then
Never bothered to download the Windows iso6 -
#DailyRant
I don't like Laravel Livewire and the architectural aspect of it. Every key stroke is a call to the server. The freedom of designing the minute behaviours are taken away. (e.g. border-bottom on a certain div). The maintain ability is not good either. Change one variable name and the whole thing breaks and it's difficult to pinpoint where it broke exactly. And the most of all, it's not beginner friendly.
My chest feels lighter now. Thanks. -
The best feeling ever is when a super long line of code is written that definitely should not be on one line, that one does not check over the logic for after writing, entered without pressing the backspace key, and it works first try.
-
Unrelated to programming:
If I'm doing async karaoke (i.e., I'm using an app like Smule where one person records one part and you join or vice versa) and the other person decides to randomly COME INTO MY LANE and not just sing my part, but sing it off-key, I get irrationally annoyed about it. It's great if they do that at the beginning of the song because then you can just bail. But when they do it at like the very end, I'm like ... 😬 -
Am I the only one to this date who still doesn't feel comfortable using the NumPad? I always have the NumLock key turned off and people who borrow my computer get annoyed by that. I've always typed numbers using the row above the letters. Typing numbers on the NumPad is very slow and unnatural to me. Is someone else out there feeling the same?4
-
One of my python students just uses his index fingers to type. And he moves his hands from elbows for each key. He said he completed his post graduation. I don't know how he survived these many years. I advised him to learn touch typing though.
-
Don't you just fucking hate those colleagues who bash their keyboard only pressing one fucking key FUCKKK
I'm in middle of debugging1 -
I use cloud storage as one of my 3 backups for my gpg master key only protected by the password cause i don't want to have to restore from paper if hell freezes over.
-
When I found out that the server I use weirdly implements SSH login.
For some very odd reason (probably a historical one,) you have to access the web-app console and press a button TO GRANT SSH ACCESS TO THE F*<KING IP ADDRESS FROM WHICH I PRESSED THE BUTTON. The server blocks the wrong IP addresses outright. And only one active allowed IP at a time. This totally obliterates my plan to perform CD on this server. Why can't I just register public keys?
Then I learned several months later that they introduced a new server plan that *does* support the public-key registration. :facepalm:
I'm divided on whether to change my plan in exchange for a rather significant increase in the monthly cost.3 -
I once was working on my family's business during summer and was doing something on the laptop that was there (according to the owner, it was in a "good shape" - oh my god that laptop nearly gave me cancer: an old Toshiba, running W10, with half the F keys not working - specially F5. I CAN'T LIVE WITHOUT F5 OH MY GOD -, and also the ➡ key (arrow keys). It was bought in a flea market and some IT guy, a friend of the owner, repaired it a bit and installed the OS because a laptop that old ran WinXP or Win Vista for sure) when suddenly it died on me.
I rebooted the thing and right before the time it should be showing the windows logo, the screen froze (on a black screen with some text) and it started to beep. Loudly. A loud continuous beep. I turned it off and on some times after that, seeing if turning it off and on did something (as it seems to work LoL) and it continued with the beeping. After a quick search I found out that that was a common problem with Toshibas that old, and that I needed to press F2 (that key worked thank god) when the black screen with the text showed up (I don't remember what was written there, it were some booting instructions, I think).
It worked. Great. Now the N key doesn't work when I press it. Greeeeeeeaaaaaat. Also it seemed that, when I opened the start menu, it would automatically write "nnnnnnnn(...)" without me pressing any key (pressing any key would make it stop though, maybe it was stuck).
Then I told the owner not to turn it off, because the laptop would start beeping and such (and I know he'd panic about it).
From then on I think it went off for good and now he's been using his own Toshiba, that runs Vista and is slow as all hell.
Moral of the story: he should have been used his crappy PC from the beginning, at least all its keys work
(Note: watching him type hurts my soul. When one is used to use both hands to type, and is fast-ish on the keyboard and uses tabs to change fields, watching someone type with only one hand every 2" or so and using the mouse to change fields hurts. So much time wasted 😭) -
I just got cancer. "full stack" wrote this:
var steams = [] ;
for (var key in images) {
streams[streams.length] = fs.createWriteStream(images.imageName);
streams[streams.length - 1].on('close', function (filename) {.....
why, Why Why and how did you come up with something this bad?
Dude creates an empty array to populate it with write streams just so he can pop each one two lines below and attach a listener.
It's the first thing I checked in this application and I'm afraid what else I'm gonna find.2 -
Hi guys, I'm hoping you can help. I've looked everywhere and I've not got a clue what it is.
I lost my back door key (5-pin pin and tumbler lock) the other day, and I can't afford to get a new one right now.
I tried picking it earlier, and I discovered it's got a spring at the back of the plug (which I've never come across). I lined up all the pins but for some reason it's not opening, and I have a feeling it's either got an anti-pick pin or it's to do with that spring.
Has anyone with lock experience got a clue what could be doing this? I'm at a loss.5 -
Some little piece of shit fairy messed with my code.
Made some modifications in a tamplate file, tested in dev everything worked. Pushed it to prod and in one of its cases it displayed the array key of each element. Checked the code, an that was what written in there in prod and in dev too. However that shit in dev (and previous versions in prod) displayed key[0]->name as intended.
So I thought git blame and check where it went wrong... Guess what... That fucking line is the same age as the file itself....
How that motherfucking shit worked, and what had I had in mind when writing that shitcode is a mistery... -
> Be me
> Fresh out of school
> Do some volunteer work for 1 year before starting to work
> Start work at local hospital
> One day get assigned new task
> "We have this directory where there is a file for every employee who has a key - File contains legal stuff"
> Current naming scheme "MaxMustermann"
> Desired naming scheme "Max Mustermann"
> Task: rename every file.
> 1974 Files
> OHNONONONO.JPG
> Hol up buddy
> A repetetive automatable task?
> I know this
> Im a hackerman
> Let's write a script....
> *SMASHES WINDOWS BUTTON*
> "Python"
> No results
> I could have guessed that
> *SMASHES WINDOWS BUTTON*
> "Java"
> No Java compiler
> OH no
> *SMASHES WINDOWS BUTTON*
> "Powershell"
> "tHe eXEcUTIon oF poWeRsheLL sCriPts Is dIsAbLeD"
> REEEEEEEE
> *SMASHES WINDOWS BUTTON*
> "cmd"
> "YOu dO noT haAV thE rEqUiReD peRmIsSionS To oPeN tHis proGrAm"
> DAFUQ
> Wait this is windows.
> Windows ships with .NET
> *SMASHES WINDOWS BUTTON*
> "csc"
> No results
> OHHELLONO.gif
> mfw I have to rename 1794 files by hand.
( Please send help )7 -
We need to test the last step in our proof-of-concept chain before putting our project proposal... but just before testing what we believe will be (finally) a functioning scenario, the key service we need and have no influence over stopped working. I am pretty sure, it will start working like 5 minutes before I usually leave.. one has to love this waitNRush development.
-
Me, enables SSL on one domain with cloudflare all went well, even added origin ssl all good.
Friends domain, set up the right and same way, but server says no i have no idea what www.examaple.com is, ... I never created a key for that wtf so right now website are dead .. thanks cf3 -
Spent 4 hours trying to figure out why API endpoint keeps returning a 404, the data guy checked the database and the row exists. Didn't know the one endpoint it was using was for debugging, which also isn't working.
Turns out Angular somehow decided to switch environments and called the wrong endpoint. I was working in an HTML template and then suddenly shit stopped working. Someone probably committed the debugging endpoint by accident and I pulled the change into my code. Imagine a dev puts some super secret API key in there and pushes it to the remote repo. Congratulations, you now leaked a potentially private API key.
"Good practices", my arse.
The way Angular uses environments is retarded. Just use fucking .env files, why is it so hard?
Angular is retarded. -
Following from https://devrant.com/rants/1516205/...
My emacs journey day 0-1
0: quickly realised what I was getting myself into, wow that is a learning curve. Head is buzzing with different key commands (and thank you to everyone who's helped out in my original post). I've been here before with Vim, but it's so hard when I am proficient with another editor, one of the most difficult aspects is getting it set up to even format my code appropriately (the right tab width etc), but I press on, something tells me it will be worth it in the end.
1: I come across a tutorial for clojure and emacs (https://braveclojure.com/basic-emac...), this looks good, oh sweet it shows how to load a good configuration, some more useful commands, feels like I'm getting there. Then it hits me, I manage to put my finger on why I decided to take the plunge: emacs isn't an editor at heart, at its heart is lisp. From its core it is scripted using one of the most powerful types of languages. Rather than some bolted on domain specific scripting language.
Now the real learning begins.2 -
I've been working for so long with API integrations and one part of that is security. We perform ssl key exchanges for 2-way verification and a large percent of those partners provides me with their own pkcs12 file which contains their private and public keys! What's the sense of the exchange!? I think they just implement it just to boast that they "know" how ssl works,
-
New data structure:
Map with repeated keys allowed. Values of repeated keys will be stored in an array.
Calling get(key) will get the array, pick a random entry in said array, and return it.
Use: Finding what the "number one rule of x," the "greatest thing ever," the "most unbelievable event," and more is. -
I swear! I just typed some words, I pressed [Enter] key and....
Oh my good, I broke the machine ...
I'm sorry I'm sorry I'm sorry !
PS: this message is not alone, I found another one about a deprecated function once I clicked on a link...
-
What should be the key qualities one should try to work on while starting as a Head of Engineering in a growing startup?4
-
DailyCodingProblem: #1
Given an array of integers, return a new array such that each element at index i of the new array is the product of all the numbers in the original array except the one at i.
For example, if our input was [1, 2, 3, 4, 5], the expected output would be [120, 60, 40, 30, 24]. If our input was [3, 2, 1], the expected output would be [2, 3, 6].
this is my quickly solution in php:
$input_array = [1, 2, 3, 4, 5];
echo('INPUT ARRAY:');
print_r($input_array);
echo("<br/>");
foreach($input_array as $key => $value){
$works_input_array = $input_array;
unset($works_input_array[$key]);
$result[] = array_product($works_input_array);
}
echo('OUTPUT ARRAY:');
print_r($result);
outpout:
INPUT ARRAY:Array ( [0] => 3 [1] => 2 [2] => 1 )
OUTPUT ARRAY:Array ( [0] => 2 [1] => 3 [2] => 6 )5 -
Is there a way to recover a deleted GPG key on GitHub? My old key expired, I generated a new one and delete the old one. Now, all my old commits are unverified.5
-
My answer to their survey -->
What, if anything, do you most _dislike_ about Firebase In-App Messaging?
Come on, have you sit a normal dev, completely new to this push notification thing and ask him to make run a simple app like the flutter firebase_messaging plugin example? For sure you did not oh dear brain dead moron that found his college degree in a Linux magazine 'Ruby special edition'.
Every-f**kin thing about that Firebase is loose end. I read all Medium articles, your utterly soporific documentation that never ends, I am actually running the flutter plugin example firebase_messaging. Nothing works or is referenced correctly: nothing. You really go blind eyes in life... you guys; right? Oh, there is a flimsy workaround in the 100th post under the Github issue number 10 thousand... lets close the crash report. If I did not change 50 meaningless lines in gradle-what-not files to make your brick-of-puke to work, I did not changed a single one.
I dream of you, looking at all those nonsense config files, with cross side eyes and some small but constant sweat, sweat that stinks piss btw, leaving your eyes because you see the end, the absolute total fuckup coming. The day where all that thick stinky shit will become beyond salvation; blurred by infinite uncontrolled and skewed complexity; your creation, your pathetic brain exposed for us all.
For sure I am not the first one to complain... your whole thing, from the first to last quark that constitute it, is irrelevant; a never ending pile of non sense. Someone with all the world contained sabotage determination would not have done lower. Thank you for making me loose hours down deep your shit show. So appreciated.
The setup is: servers, your crap-as-a-service and some mobile devices. For Christ sake, sending 100 bytes as a little [ beep beep + 'hello kitty' ] is not fucking rocket science. Yet you fuckin push it to be a grinding task ... for eternity!!!
You know what, you should invent and require another, new, useless key-value called 'Registration API Key Plugin ID Service' that we have to generate and sync on two machines, everyday, using something obscure shit like a 'Gradle terminal'. Maybe also you could deprecate another key, rename another one to make things worst and I propose to choose a new hash function that we have to compile ourselves. A good candidate would be a C buggy source code from some random Github hacker... who has injected some platform dependent SIMD code (he works on PowerPC and have not test on x64); you know, the guy you admire because he is so much more lowlife that you and has all the Pokemon on his desk. Well that guy just finished a really really rapid hash function... over GPU in a server less fashion... we have an API for it. Every new user will gain 3ms for every new key. WOW, Imagine the gain over millions of users!!! Push that in the official pipe fucktard!.. What are you waiting for? Wait, no, change the whole service name and infrastructure. Move everything to CLSG (cloud lambda service ... by Google); that is it, brilliant!
And Oh, yeah, to secure the whole void, bury the doc for the new hash under 3000 words, lost between v2, v1 and some other deprecated doc that also have 3000 and are still first result on Google. Finally I think about it, let go the doc, fuck it... a tutorial, for 'weak ass' right.
One last thing, rewrite all your tech in the latest new in house language, split everything in 'femto services' => ( one assembly operation by OS process ) and finally cramp all those in containers... Agile, for sure it has to be Agile. Users will really appreciate the improvements of your mandatory service. -
(Question/0.5Rant)
So I am working on a mixed API (aka reachable from anywhere, but also only accessible by specific allowed devices) and I am struggling with the security of it, its not managing anything hardcore (this API is "is the coffe ready?" kind of level) or I would have just enforced per device registration for example already, but the app that goes with that API is deployed remotely and has to be "ready to go!!!" out of the box, so I can't add any registration, verifications of devices etc.
The main thing I am afraid of is, that one of those agent retards will get his spaghetti phone blasted from the inside, so all the https calls will be read out by some random attacker, which then will be able to "abuse" the API via read out api-key, is there any way for me to have a rescue plan if one of those retards does get hacked and the system then get spammed or something, like if I log all devices that use the API I could just deny access from that device (until resolved) and issue a new app update via new api key.
What's the best way of handling this and is my idea really the only way to handle this? this shitfest is really causing shit ton of ideas in my head, which then I deny literally 20 seconds later, because there's a way to bypass it or once you have the old api key to get a new one by just monitoring it etc.5 -
> Colleagues complain all the time about dumb shit which have no relevance whatsoever to the job (see my "cat in voice call" post): I get scolded, I need to change
> I complain for the first time in 2 years about relevant stuff which actually matters to the job (some guy collecting bad decisions one after the other): I get scolded, I shouldn't trash talk colleagues
The key lesson I'm learning here is how everyone is allowed to do everything towards everyone, everytime, but by God don't you dare doing it about what should be relevant about your fucking job. We don't do that here.1 -
Fuuuuuuuck!!
CR estimates:
Part 1: 2h including testing
Part 2: 2h-2days-maybe never (small changes on horrifically fucked up project noone understands with tons of tech debt)
Managed to pull off the part two in one day.. //yay me?!
Additional day to unfuckup git fuckups (including but not limited to master head not compiling because a smartass included *.cs in .gitignore file which he also pushed..don't ask, I have no clue why..) which was a huuuge deal for me as I usually use only local repo and had no idea how to tackle this.. coworker helped out.. seems I was on the right way, but git push branchy was acting up & said I had to login & ofc I had no clue what the pass was set to (first setup was more than 2yrs ago)..so new key, new pass.. all good.. yay!
Back to the original story/rant: Now I'm stuck with writing jira explanation why it was done this way & not the way customer suggested. They offered only vague description anyways which would require me to do a hacky messy thing, ew.. + it most probably would require major data modifications after deployment to even make it work..
Anyhow, this expanation is also easy peasy in english..
BUT...
I must write it in my native tongue.. o.O FML! Spent almost 40mins on one paragraph..
Sooo.. if anyone will petition to ban non english in IT, I'm all for it!!2 -
I hate Mondays...
So, Yours truly, the multilingual flightless bird leaves his apartment... Locks door... Fucking key gets stuck in lock (had some attempted home invasion attempt last year, left a few things bent).
The last thing I can use today, important project to work on with a deadline close enough to worry about.
I would say that's a classic Error 500 on login kinda situation.
The irony? I fancy myself a pretty good lock picker(A must have for an aspiring pentester) .
Luckily, a quick squirt of gun oil resolved that one... Seriously, how do people manage without a supply of tools and stuff?2 -
I was writing a db on sql and I accidentally fucked up the key column.(as you can see in the pic) No, I didnt used AUTO_INCREMENT.
Is there a wei to make this right, other than doing it one by one? 3
3 -
today has been one of the worst day of my life
- the parking situation went out of hand : i bought a new car 2 days ago, nd since last 2 days i have been just taking it out to practice for 1 hr in morning with the trainer. today one of our pesky neighbour took this opportunity and parked in our spot. i had to call my friend in the early morning to get it parked in a place far away from home . my new car is parked in an unsafe place , just because the neighbour wants to make me mad 😭
- office announced that since cto is coming, you must do wfo fod next 2 days. our office is tuesday nd Thursday, now i will have to go on friday too. plus our team lead is coming, so next weekend is going to be 4days wfo. they are giving random surprises, why not just tell us that its full wfo?
- one of our neighbour's bike got stolen in plain sight. our road is usually having a lot of people going around whole day, as its opposite to park. nd those neighbours have a hon ground floor, so they are almost always outside. we have installed a camera just 2 days ago, nd that caught the incident live. i am 100% sure that if my car had been parked here today, then it would have been my car 😭😭😭
- we friends went for a night stroll in my car. the car was mine, but my friend was driving it as he's experienced. we stopped at a food joint. i took the key from him for sometime because i was having fun playing with it . then when we were heading out, our key was gone!
i almost had a mini heart attack. my friends were not messing up with me. fortunately the restaurant had cameras , so we requested for cctv footage. in the footage we found that i accidentally put the key in the restaurant menu. and that fucking guy had taken away the menu!!!
imagine if he had given that menu to someone else 😭😭😭. our car would have been gone in a moment, as we were not even seeing the car from the window. imagine if the restaurant didn't had the fucking cameras 😭😭😭😭😭😭😭
life fucks super bad in a moment of truth10 -
I tend to overengineer. Why? Because I had a view in JavaFX with its controller that had a bunch of key listeners which changed the UI. I wanted to change the view based on wifi connection/no connection with a server, which was managed in a Client class. The controller took the client to give it a message that client then had to send. For "separation of concerns" I created a separate view + controller for the "not connected" state.
Now the Client knew all about the connection, so I put up the Observer pattern and wanted the Main (Application) class to swap the layouts as an Observer of the Client. After an Exception on FX thread and Platform.runLater(), to solve the issue, I faced a new problem: the key presses weren't executed anymore. I still don't know why this happens. Maybe I'm missing something.🤷
Then met with one of my group partners (it's a uni project):
Let's attach the Observer to the original controller. Have only the original view that changes due to the controller updates as Observer. Let's see if that might even remotely work...🤔
It worked🤦😂 -
// Pouring over idiot API developer's crappy documentation.
Example:
Goal Detail
* From Docs "table_breakdown key will return an array but will always only contain one json object.
json -> "table_breakdown" [
{
"field" : "value",
"etc" : "etc"
}
]
WHYYYY!!!!1 -
My Model M's dead. Accidentally flooded the inside when cleaning it. After letting it dry upside-down a few days, it just holds a random key when plugged in and nothing else works. Can't open it all the way up as it's a plastic-rivet one.4
-
PrestaShop irony:
* Theirs modules have >3500 lines per class (eg. blocklayered.php)
* Theirs controllers have > 5000 lines and contains a LOT of html code inside
AND when I tried to add own module to theirs addons store they declined it because:
* I had unused $key var in foreach and this is "bad practice" as I was told
* In one hook I was returning 1 line of html code (i had to add global Js var) and they told me that I should put it into separate template file
-.-'2 -
Is OMEGA CRYPTO RECOVERY SPECIALIST a Genuine, Legit Lost Crypto Recovery Company.
OMEGA CRYPTO RECOVERY SPECIALIST is a company that was founded 22 years ago by a team of experts in the field of cryptocurrency. The company offers a range of services, including recovery of lost or inaccessible crypto assets, forensic analysis of blockchain transactions, and security consulting for individuals and businesses.
The company has gained a reputation in the industry for its expertise and professionalism, with many customers praising their services on social media and review sites. One of the key services offered by Omega Crypto Recovery Specialist is the recovery of lost or inaccessible crypto assets.
The company uses a variety of techniques and tools to recover lost assets, including forensic analysis of blockchain transactions, brute-force password cracking, and social engineering. The company also offers security consulting services for individuals and businesses to help prevent future losses.
Webpage: omegarecoveryspecialist . c o m4 -
Fucking hell, writing browser addons is annoying.
I just wanted some small addon for myself. But first did it in tampermonkey. It was supposed to take a screenshot of the website and upload it together with the link of the website to my server. First used html2canvas. Terrible performance. But addons can take direct screenshots.
Reason, when I listen to something or watch something while holding my little daughter, I cannot copy links over. But I can quickly slap a key combination and save for later what I just saw.
Anyway. Addons are terrible. The error messages makes no sense. Missing permission active_tab... Fucking hell, it was missing host permissions. Permissions has to be one of. Documentation sucks on MDN.
And then, you can not even install unsigned addons. I do not want to share my addon with mozilla. You have to install Firefox Dev or ESR for it. Switched to Firefox Dev.
But I feel sorry for everyone having to write browser addons professionally.1 -
I am in a team where almost everyone is an apt critique. everyday new challenges and people seem to be so competitive that they don't share any information across, thus making everyone isolated and whack the motto "collaboration is key" teamwork rarely comes into play and it is most if the times one man show. thriving in such an environment is a challenge thanks team 😃
-
I recently came across this article with some basic security advices, like use 2fa security key, encrypt your USB keys, don't use untrusted USB chargers / cables / ports (or use a data blocker cable if you need to charge your device). It made me think, how relevant are the USB-related threats and risks today? Do people really still use and carry so many wired USB devices, and just drop or plug them wherever?
The last time I used an USB device to transfer some important data was probably over 10 years ago, and for the love of god I don't know anyone who still carries an USB key with sensitive data with them on a daily basis, much less actively uses it. Besides, whoever still does that probably puts their USB key on the same keychain as their ID / access tag and a bunch of other keys (including a 2fa device if they use one) - they're not going to lose just some sensitive data, they're going to lose authentication and physical access devices as well, and that could turn a small data leak into a full-scale incident, with or without an encrypted USB device.
I'm also not sure about untrusted USB cables and ports, from what I've seen the USB outlets and cables are pretty much non-existent in public places, most places offer wireless charging pads instead (usually built into a hand rest or table surface).3 -
had a uni exam in databases (just closely didn't make it😒)
it didn't even have sql in it!?
questions about ER diagrams and draw a diagram, functional dependencies with given dependencies, find candidate key and what not, work on a b-tree (miserably failed😣), datalog (who the fuck cares about datalog? the least expected topic) and transaction management/serializability
whose idea was it to not include sql?? isn't it one the fundamental parts of relational databases?4 -
fn key is the most evil shit key from hell
no matter where you put it, there is no layout in which you don't keep hitting it instead of something else.. It's not like you need most of the F# keys anyway you can just as well have the functional keys without this abomination.. or here's one: how about making a fucking mapping hm? To inventor of fn key: "You can suck my balls!"1 -
Oh look at it stupid technomusings.
Context:
- You have a sequence of N-byte-wide values.
- Each value is unique.
- You XOR them all together into an N-byte-wide key.
- Just dump the key into a list somewhere.
Problem:
- A new value sequence is input.
- Same rules: all values are unique and fixed-size.
- You XOR them all together into a key.
- You walk the list of keys and check them for equality against the new one.
The same sequence of values, regardless of order, would ((supposedly)) always give you the same key. I used this years ago, for a renderer that used indexed colors, to see if I had to make a new palette or not when saving/loading textures: the image format had the key on the header.
It worked, but I was using a __very__ limited value range, cursed 8-bit YUV lossy fuckery; never bothered investigating the idea any further.
So, question:
- Is there any specific situation in which you get a false positive?
- Is there any specific situation in which you get a false negative?
My brain wants to say 'yes' to both because I'm privy to the mystical truth that my methods invariably fall on the idiot side of the spectrum. But my lazy testing keeps saying 'no, you dumbass'.
So who's wrong?
brb gon hit that crack~1 -
Jiff files have begun encroaching on my charmed life. I keep forgetting to search for an online converter and have done with it. I thought I'd hit upon one and I remembered to go to my search engine of choice and key in, "XXX malware." I learnt to do this years ago with my Mac, and I'm happy to say I've only slipped once or twice. Anyway, it's great to apply what I've learned instead of noticing weird things happening with my screen. Happy Independence Day from The Colonies,5
-
all this talk of australian crypto laws got me thinking. here's a hypothetical (this might get a little complicated):
for the sake of the security facade, the government decides to not ban encryption outright. BUT they decide that all crypto will use the same key. therefore you can not directly read encrypted things, but it's not really encrypted anymore is it?
part two: there's a concept called chicken sexing, named after people who determine the sex of baby chicks. male chicks are pretty useless and expensive to keep alive, so they are eaten. female chicks go on to lay eggs, so ideally, from a financial standpoint, you only raise hens to maturity. this is nearly impossible to discern early on so at first you're just straight up guessing. is this one female? sure? that one? no? really 50/50. BUT if you have a skilled chicken sexer looking over your shoulder, saying right or wrong, then eventually you get better. why? nobody knows. they can't explain it. nobody can. you just sort of "know" when it's female or not. some people can do 1000s of chicks/hr with success up to 98% but nobody can explain how to tell them apart.
part three. final part:
after years, even decades of using this encryption with only one key, I wonder if people (even if only people who are regularly exposed to crypto like NSA analysts or cryptographers) can ever learn to understand it. in the same way as above. you don't know exactly what it says. or how you know it. you didn't run an algorithm in your head or decrypt it. but somehow you get the gist.
28464e294af01d1845bcd21 roughly translates to "just bought a PS5! WOOT!" or even just pick out details. PS5. excited. bought.
but how do you know that? idk. just do.
oh what a creepy future it has become.8 -
So as a personal project for work I decided to start data logging facility variables, it's something that we might need to pickup at some point in the future so decided to take the initiative since I'm the new guy.
I setup some basic current loop sensors are things like gas line pressures for bulk nitrogen and compressed air but decided to go with a more advanced system for logging the temperature and humidity in the labs. These sensors come with 'software' it's a web site you host internally. Cool so I just need to build a simple web server to run these PoE sensors. No big deal right, it's just an IIS service. Months after ordering Server 2019 though SSC I get 4 activation codes 2 MAK and 2 KMS. I won the lottery now i just have to download the server 2019 retail ISO and... Won't take the keys. Back to purchasing, "oh I can download that for you, what key is yours". Um... I dunno you sent me 4 Can I just get the link, "well you have to have a login". Ok what building are you in I'll drive over with a USB key (hoping there on the same campus), "the download keeps stopping, I'll contact the IT service in your building". a week later I get an install ISO and still no one knows that key is mine. Local IT service suggests it's probably a MAK key since I originally got a quote for a retail copy and we don't run a KMS server on the network I'm using for testing. We'll doesn't windows reject all 4 keys then proceed to register with a non-existent KMS server on the network I'm using for testing. Great so now this server that is supposed to connected to a private network for the sensors and use the second NIC for an internet connection has to be connected to the old network that I'm using for testing because that's where the KMS server seems to be. Ok no big deal the old network has internet except the powers that be want to migrate everything to the new more secure network but I still need to be connected to the KMS server because they sent me the wrong key. So I'm up to three network cards and some of my basic sensors are running on yet another network and I want to migrate the management software to this hardware to have all my data logging in one system. I had to label the Ethernet ports so I could hand over the hardware for certification and security scans.
So at this point I have my system running with a couple sensors setup with static IP's because I haven't had time to setup the DNS for the private network the sensors run on. Local IT goes to install McAfee and can't because it isn't compatible with anything after 1809 or later, I get a message back that " we only support up to 1709" I point out that it's server 2019, "Oh yeah, let me ask about that" a bunch of back and forth ensues and finally Local IT get's a version of McAfee that will install, runs security scan again i get a message back. " There are two high risk issues on your server", my blood pressure is getting high as well. The risks there looking at McAfee versions are out of date and windows Defender is disabled (because of McAfee).
There's a low risk issue as well, something relating to the DNS service I didn't fully setup. I tell local IT just disable it for now, then think we'll heck I'll remote in and do it. Nope can't remote into my server, oh they renamed it well that's lot going to stay that way but whatever oh here's the IP they assigned it, nope cant remote in no privileges. Ok so I run up three flights of stairs to local IT before they leave for the day log into my server yup RDP is enabled, odd but whatever let's delete the DNS role for now, nope you don't have admin privileges. Now I'm really getting displeased, I can;t have admin privileges on the network you want me to use to support the service on a system you can't support and I'm supposed to believe you can migrate the life safety systems you want us to move. I'm using my system to prove that the 2FA system works, at this rate I'm going to have 2FA access to a completely worthless broken system in a few years. good thing I rebuilt the whole server in a VM I'm planning to deploy before I get the official one back. I'm skipping a lot of the ridiculous back and forth conversations because the more I think about it the more irritated I get.1 -
I just like bulding silly things, my ideal devjob would be one where I could just make random junk that makes me smile all day...
Like recently I made an NoSQL database using azure AD. They give you 50000 AD objects free, but I found you could encode all sorts of data in the AD objects variables. So basically I setup a framework that uses Security groups as Collections, AD objects as Documents, and object variables as key pairs.
It's really slow, like roughly 50 queries a minute, but hey. It was fun proving it could be done...
Yeah, that would be my ideal devjob :P that kind of stuff all day2 -
-Recently started a new job so I’m new to the infrastructure-
Spent the vast majority of the day trying to SSH into one of my company servers to sort some random bug out on the website & the connection kept being rejected despite the day before it working when passing the .pem key into the SSH along with the ip & my username, nothing new there.
Anyway, everyone’s mad busy so I don’t wanna bother anyone to ask why, so I check confluence, no documentation for SSHING into our scheduler or the code the server I need to access. Never-mind.
Spend another couple hours trying debug it on my own, no luck. Never-mind.
Finally seize my opportunity and ask for help; ‘Oh the server IP changes daily so you need to run a task through our scheduler that you need to SSH into to return the list of IPS and that dynamically changes so that’s how you get the IP’
Oh ok. Why is there no documentation for that again? I mean. Thats generally some pretty important information you’d pass onto your starters.
At least I can say I won’t be making that same mistake again.5 -
Nothin to get a rant simmering like reFuckingRanting! All good, I'll have another shooter while I wait to reinstall, reconfig, rebuild, rewipe, and reRefuse any and all Windows clammy hand of aid it forces down my soul. One of these days, when the whole realm understands we don't need this vast array of exactly the same shit but this one's dick is a little bigger so lets fucking make it, this and not that, and rebuild, push the update, need 4 more updates by noon next day. Nothing stays stable team green, NOTHING. Fuck anyone trying to actually ...make something..We got vulns and updates, backdates, and breaking changes on all 58 of our same shit production line shit shows. I can't count one time in this few year pain olympics that in a single 8 hour span of time the same shit that was working like a fucking wet glove in a horses ass at whiskey 1 was NOT fucking anywhere near coherent come whiskey not 1. Just sayin, is this a cock show boys? Or is is just a wild and rambunctious thought to maybe start compiling/combining some key role playing pieces of softwar? If not, I'll just prep for another round of fucks, and carry on. Sadly, this shit is addicting against many odds. Enjoy your lunches
-
Anyone else experiencing that volume key doesnt work with one plus 5t on latest 9.0.3 pie update. How can one plus be so careless.5
-
Damn!!! After all the questions I get from distro hoppers I hope someone could draw up a dichotomous key for picking one.1
-
Any one ever heard of the Solo? It's basically an open source FIDO compliant U2FA usb (with planned support for PGP/SSH key storage!).
The guys who made it are now miniaturizing it into the "Somu" (Secure Tomu).
Please support it! It's a great project and a great (and cheap) addition to basic system security.
https://crowdsupply.com/solokeys/...21 -
Got a question on DBMS Normalization. I tried searching but couldn't clear my doubt. So I have a set of functional dependencies for relation R(C, D, E, F, P, R, S) :
F->D
D->F
E->C
P->RC
E->F
S->EFD
PR->EF
So I have to convert this to 3NF. My doubt is that when finding 2NF do we find all the non-prime attributes that are dependent on a particular partial key i.e. do we take it's closure and create new relations for each partial dependency? If we do that then there are overlapping attributes in the resultant relations in this case I found the relations in 2NF as :
R1(P, S)
R2(P, R, C, E, F)
R3(S, E, F, D, C)
But when I just used the FDs as they are given (no closure) I found :
R1(P, S)
R2(P, R, C)
R3(S, E, F, D)
Which one is correct, please help.3 -
Merry Christmas! Finally got my 60% keyboard, so it's time to get back to practicing nvim. Already getting better at using hjkl since I don't have any arrow keys.
Only thing that's a bit of a bummer is the ~ key is Shift + Fn + Esc. Oh well, I only use that one maybe a few times a day anyways especially since the only Linux I use is WSL.3 -
One user could report that the data they saw didn't make sense. Turns out there was a one-off hardcoded caching detail for one of our services that cached based on a search query (yes, the entire query was the key) and before any auth checks. The system would return the results owned by whoever asked first, no matter who asked after that point.
There's "Oh dear but we all make mistakes" and there's surrender cobra. This is what PRs are for.1 -
One of our partners sent me a Key Injection Tool to inject encryption keys into a PINPAD with. Looks like they were short on developers and had to hire Python typists who have made a mess of a simple AES encryption/decryption. When do these companies learn that writing a security related software in Python is not really secure? I had to read the rubbish in Python and read it from scratch in C++ to get it to work, and am now contemplating whether to provide that company with my version of their Key Injection Tool or not...2
-
Greets. I need advice. And before reading just skip me with classic things you can't - you shouldn't. As i am Windows user last 20 years, I never actually used any other os (running ubuntu on vm occasionally doesnt count). So for some period of time I'm thinking about throwing myself fully into some Linux distro but I can't choose which one. I was thinking between Fedora, Arch and Debian (i dont want Ubuntu), but also what it should be a main key of my decision is good documentation backed up distro. Thanks in advice if you are willing to help my decision2
-
It is currently 5:30 AM, I've been trying to upgrade a server by one single major OS release for the last 3.5 hours. All major apps were no issue, except one.
Redmine.
That thing runs on Ruby.
Ruby, as it turns out, doesn't really like the way Debian handles package management.
And now, I have Redmine that, even if I completely uninstall / reinstall, won't start
I went down several rabbit holes, trying to operatively find what the issue is. But I never got to the key issue.
Fuck ruby. Fuck Redmine. Fuck nothing-saying error messages. Fuck bundle. Fuck gem. Fuck it all.
I'm redirecting the Redmine domain onto the server backup I've made. Upgrading that thing is a nightmare.
Maybe now I can finally go to bed...5 -
Is it a good approach to have a master SSL key for all your servers when making the authentication?
I am a Developer, but when you work in a company with two developers and you are the senior one you have to learn a lot of stuffs. I am learning more in depth things about how to secure the servers and network.
Now, I am expanding the servers. Splitting the code and database in three different servers (code, Master DB, Slave DB) and configuring Master-Slave databases.
My questions are:
1. Is it a good approach to have a master SSL key for all your servers?
2. Is is a good approach to use the same SSL key for Master database server and Slave database server?
Any other suggestions are welcome.
Thank You in advance!2 -
Alright, I've got a confesstion. It's a confession and a question, combined, get it?
Anyway, I've been a happy Linux user for over 20 years now, and I've used all kinds of graphical envs, from tiling wms like dwm and xmonad (I didn't care for hyprland, sorry if that's weird) to full DEs like kde, cinnamon, gnome, etc.
The "question" here is why do people hate Gnome so much? It's the one environment that I keep coming back to, especially now that my main machine is a beast, and RAM usage is nary a concern. Even then, my system is sipping RAM compared to KDE (running two docker dev environments, three browser windows with several tabs - one of which is streaming music, slack, and steam is sitting on the fourth virtual desktop, chilling), and I'm still at just over 18 GB of ram.Being able to push one single key/key combo, and type anything at all that is vaguely relevant to what you want to accomplish, and having that thing be instantly available (including searching for individual files) is super nice. Easy virtual and multi monitor switching is intuitive; little to no effort needed.
Even when I want to do other stuff, like play a game, or edit a photo, video, or some of my shitty musical-aspirational material - GNU+Linux with Gnome has been and continues to be the easiest, most neato way to get shit done.
Why the hate, gnome haters? Maybe you’re using it wrong?8 -
Trying to migrate an app from Dropwi Card to Spring Boot but can't get the YAML config read in correctly.
It's not reading the objects/lists/maps
Just treating each line as a key value.
Spring Boot says it sorts YAML configs and one seen some projects use this without issue.
But don't know how to turn it on.
Tried a lot of @*Config* all over the project but doesn't work.
Eventually just checked what Main.java loaded in the App context and well basically it never parsed it correctly...3 -
*Ctrl + a*
*retarded auto-indent code shortcut key*
*Presses arrow key instinctively*
*moves cursor to end or start of code*
Am I the only one? -
Total population of India: 1,425,775,850
Total number of Pajeets: 1,425,775,850
Total area: 3.287 million km²
Toilet available: 3.287 million km²
Fertility rate: 2.05 pajeets per pajeet woman
GDP growth rate: 8.7% annual change
India's Gross Domestic Product (GDP) is influenced by a variety of factors that contribute to its economic performance. Some key factors include:
- Call city scam
- Microsoft support scam
- Other types of scam
---
One of the fastest ways to solve overpopulation is by nuking India and China. By a side effect, there will be no more Indians and Chinese, which is amazing.
They have combined total of 2,837,525,850.1 -
MOST RELIABLE BITCOIN RECOVERY / ADWARE RECOVERY SPECIALIST ALWAYS AVAILABLE IN ALL SCAMMED RECOVERY
I remember when I first got into Bitcoin mining. It was back in the early days when Bitcoin was still a new concept and very few people knew about it. As a bank manager, I was intrigued by this digital currency and decided to give mining a shot. I set up my computer and began the process, eventually accumulating a significant amount of Bitcoin. At that time, Bitcoin wasn't worth much, but I believed in its potential. I decided to encrypt my Bitcoin wallet for security. I created a decryption key and stored it somewhere safe, or so I thought. Email info: Adwarerecoveryspecialist@ auctioneer. net Years passed, and I didn't think much about my Bitcoin. Then, the price of Bitcoin skyrocketed. When I checked my wallet, I realized I had Bitcoin worth $1,500,000!Excited, I rushed to decrypt my wallet, only to discover that I had forgotten the decryption key. I searched everywhere, racking my brain to remember where I had stored it, but it was no use. My fortune was locked away, seemingly out of reach. Feeling desperate, I turned to Google, searching for any possible solution to recover my lost Bitcoins. During my search, I stumbled upon a tool called ADWARE RECOVERY SPECIALIST. This tool promised to help recover lost or forgotten decryption keys. Skeptical but hopeful, I decided to give it a try. The process was straightforward. I downloaded the tool and followed the instructions carefully. ADWARE RECOVERY SPECIALIST guided me through a series of steps designed to locate and recover my decryption key. The interface was user-friendly, and the instructions were clear. As I progressed through the recovery process, I felt a glimmer of hope. The tool used advanced algorithms to search for traces of the key on my computer. After several hours of scanning and searching, ADWARE RECOVERY SPECIALIST provided a list of potential keys. With bated breath, I tried each one, and finally, one of them worked! I was able to access my Bitcoin wallet and retrieve my $1,500,000 worth of Bitcoin. The relief and joy I felt were indescribable. Thanks to ADWARE RECOVERY SPECIALIST, my financial future looked bright once again. Telegram info: @adwarerecoveryspecialist This experience taught me the importance of securing important information properly and never underestimating the power of modern technology. With my Bitcoin now accessible, I have a renewed sense of hope and excitement for the future. -
Shiv Nadar School – Among the Leading IB Schools in India
As education continues to evolve in a globalized world, many parents in India are now turning towards international curricula that focus on holistic development, critical thinking, and global citizenship. Among these, the International Baccalaureate (IB) stands out as one of the most recognized and respected academic frameworks globally. If you are looking for top IB schools in India, Shiv Nadar School is a name you can trust.
Why Choose IB Schools in India?
IB schools in India follow a curriculum designed to go beyond traditional rote learning. The IB programme encourages students to inquire, explore, and understand topics in depth. The key benefits of IB education include:
Emphasis on conceptual understanding
Development of research, communication, and analytical skills
Exposure to global perspectives and cultural awareness
Balanced focus on academics, arts, sports, and social responsibility
IB programmes are recognized by top universities across the world, making them a strong choice for students aiming for global academic pathways.
Shiv Nadar School – A Top Choice for IB Education
Shiv Nadar School, established under the Shiv Nadar Foundation, has earned a reputation for academic excellence, innovative teaching, and values-based education. With campuses in Noida, Gurgaon, and Faridabad, the school has become one of the most preferred IB schools in India.
Key Highlights:
Globally Aligned Curriculum
Shiv Nadar School offers an inquiry-driven, concept-based curriculum aligned with the IB framework. The teaching approach helps students develop a love for learning, along with the skills required to succeed in the 21st century.
Experienced and Trained Faculty
The school’s teachers are well-trained in the IB methodology. They serve as mentors and facilitators who support students in developing critical thinking and independent learning.
Future-Ready Infrastructure
From tech-enabled classrooms and science labs to libraries, art studios, and sports complexes, Shiv Nadar School offers top-class facilities that promote both academic and personal growth.
Focus on Holistic Development
The school emphasizes not just academic performance, but also creativity, social responsibility, empathy, and leadership through co-curricular and extracurricular programs.
Safe and Inclusive Environment
The school provides a nurturing environment where every student is encouraged to grow and express themselves freely, making it a second home for young learners.
Admission Open – Apply Now
Shiv Nadar School is now accepting applications for the upcoming academic year across its campuses in Noida, Gurgaon, and Faridabad. Seats are limited, and early registration is recommended.5 -
Not really a programming rant, but how fucking hard is it to spell someone's name in an email correctly. There is no single key for 'ph' and if there were it would be no where near the letter 'V'. But then again I'm just trying to help you out with your simple SQL script which you can't find out why you're not inserting data and you're only the director of informatics. And your script is horrendous with multiple joins which are unnecessary. Create one source table instead of 4 inserts from one table and use one insert from one table ya idiot.
-
One of the best product feature updates (though it's not "very" recent) that I really found interesting and useful from Developer perspective is integration of JIRA cloud with GITHub and how it uses issue key to associate the commit.
I makes things a bit easy while working in DevOps model :)
Please feel free to post your reviews. -
Glory Casino is a popular platform for players in Bangladesh looking to enjoy a wide range of exciting casino games. https://casinologin-bd.com/glory-ca... offers all the details you need to log into your Glory Casino account with ease. Once you’ve registered and created your account, the login process is straightforward, and the site offers helpful tips to ensure you never miss a chance to play.
One of the key features of Glory Casino is its live dealer games, which offer a real-time, interactive gaming experience. Players can enjoy games like blackjack, roulette, and baccarat with live dealers, making it feel as though they are playing in a land-based casino from the comfort of their home. Glory Casino also offers a wide selection of slot games and other casino classics, ensuring there is something for everyone.
For those who encounter any issues with logging into their account or navigating the site, provides customer support options and troubleshooting guides to help players resolve any issues quickly. Enjoy your time at Glory Casino, where the best online gaming experience awaits.2 -
(tldr: are foriegn keys good/bad? Can you give a simple example of a situation where foriegn keys were the only and/or best solution?)
i have been recently trying to make some apps and their databases , so i decided to give a deeper look to sql and its queries.
I am a little confused and wanted to know more about foreign keys , joins and this particular db designing technique i use.
Can anyone explain me about them in a simpler way?
Firstly i wanted to show you this not much unheard tecnique of making relations that i find very useful( i guess its called toxi technique) :
In this , we use an extra table for joining 2 tables . For eg, if we have a table of questions and we have a table of tags then we should also have a table of relation called relation which will be mapping the the tags with questions through their primary IDs this way we can search all the questions by using tag name and we can also show multiple tags for a question just like stackoverflow does.
Now am not sure which could be a possibile situation when i need a foriegn key. In this particular example, both questions and tags are joined via what i say as "soft link" and this makes it very scalable and both easy to add both questions and new tags.
From what i learned about foriegn keys, it marks a mandatory one directional relation between 2 tables (or as i say "hard a to b" link)
Firstly i don't understand how i could use foriegn key to map multiple tags with a question. Does that mean it will always going to make a 1to1 relationship between 2 tables( i have yet to understand what 11 1mant or many many relations arr, not sure if my terminology is correct)
Secondly it poses super difficulty and differences in logics for adding either a tag or question, don't you think?
Like one table (say question) is having a foreign key of tags ID then the the questions table is completely independent of tag entries.
Its insertion/updation/deletion/creation of entries doesn't affect the tags table. but for tag table we cannot modify a particular tag or delete a tag without making without causing harm to its associated question entries.
if we have to delete a particular tag then we have to delete all its associated questions with that this means this is rather a bad thing to use for making tables isn't it?
I m just so confused regarding foriegn keys , joins and this toxi approach. Maybe my example of stack overflow tag/questions is wrong wrt to foreign key. But then i would like to know an example where it is useful5 -
I would like to share this piece of knowledge for the web devs out there, even though it's probably known:
If you're using the Spring framework and you want to accept a list of items as a multipart/form-data request, then Spring will only be able to correctly deserialize your JavaScript FileList in the backend if you have scripted it as follows:
var data = ev.dataTransfer.files;
var formData = formData();
for (i = 0, j = data.length; i < j; i++) {
formData.append('files', data[i]);
}
The for loop with the 'files' name is key here. Why? Because then it will resolve into:
key=val&key=val&key=val
and that's how Spring will correctly be able to deserialize it into a List. We remember from our HTML learnings that if we want values in a form to be processed as one, we must provide the same name= for each element in the form, otherwise if you have a separate name for each input, it won't be passed on as one collection of values.
This is why my list was originally null when received in the backend.
Courtesy of StackOverflow:
https://stackoverflow.com/questions... -
Top Benefits of Using Data Loss Prevention in Microsoft 365
Data Loss Prevention (DLP) in Microsoft 365 offers numerous benefits to organizations aiming to protect sensitive information and ensure compliance. One of the top advantages is enhanced data protection, where DLP policies help identify, monitor, and restrict the sharing of sensitive information like credit card details or personal identification numbers across Microsoft 365 apps (Outlook, SharePoint, OneDrive, and Teams). This proactive security measure prevents unauthorized access or accidental sharing of confidential data.
Another key benefit is regulatory compliance. DLP helps organizations comply with data protection regulations such as GDPR, HIPAA, and CCPA by enforcing policies that limit data exposure and unauthorized sharing, reducing the risk of costly fines.
Microsoft 365 DLP also offers visibility and control. IT administrators can monitor user actions and identify potential risks in real time, making it easier to enforce security measures. Additionally, user education is integrated through policy tips, which educate users about data protection during daily tasks.
Finally, DLP offers seamless integration across all Microsoft 365 platforms, making it easy to manage and enforce consistent security policies across emails, documents, and collaborative tools, ensuring comprehensive protection for the entire organization.

