Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "user data"
-
Last year I built the platform 'Tindex'. It was an index of Tinder profiles so people could search by name, gender and age.
We scraped the Tinder profiles through a Tinder API which was discontinued not long ago, but weird enough it was still intact and one of my friends who was also working on it found out how to get api keys (somewhere in network tab at Tinder Online).
Except name, gender and age we also got 3 distances so we could calculate each users' location, then save the location each 15 minutes and put the coordinates on a map so users of Tindex could easily see the current location of a specific Tinder user.
Fun note: we also got the Spotify data of each Tinder user, so we could actually know on which time and which location a user listened to a specific Spotify track.
Later on we started building it out: A chatbot which connected to Tinder so Tindex users could automatically send a pick up line to their new matches (Was kinda buggy, sometimes it sent 3 pick up lines at ones).
Right when we started building a revenue model we stopped the entire project because a friend of ours had found out that we basically violated almost all terms.
Was a great project, learned a lot from it and actually had me thinking twice or more about online dating platforms.
Below an image of the user overview design I prototyped. The data is mock-data. 50
50 -
A super creepy webcrawler I built with a friend in Haskell. It uses social media, various reverse image searches from images and strategically picked video/gif frames, image EXIF data, user names, location data, etc to cross reference everything there is to know about someone. It builds weighted graphs in a database over time, trying to verify information through multiple pathways — although most searches are completed in seconds.
I originally built it for two reasons: Manager walks into the office for a meeting, and during the meeting I could ask him how his ski holiday with his wife and kids was, or casually mention how much I would like to learn his favorite hobby.
The other reason was porn of course.
I put further development in the freezer because it's already too creepy. I'd run it on some porn gif, and after a long search it had built a graph pointing to a residence in rural Russia with pictures of a local volleyball club.
To imagine that intelligence agencies probably have much better gathering tools is so insane to think about.53 -
In a meeting after I explained that the user passwords will be encrypted before we save them in the database
Them: "Please don't do that, we don't want to change our clients data"
Me: " so we should save the clear text?"
Them: "Yes"
😒9 -
Interviewer: Why do you want to work for Facebook?
Me: I'm keen on protecting people's data and want them to have a good user experience
Interviewer:
Me:
Interviewer:
Me: haha I'm joking I don't give a shit
Interviewer: haha omg I was like whaaatttt lmao
src: https://twitter.com/ArfMeasures/...2 -
USER: I can't see any data in the page...!
ME: ok, I'll do a check
ME: API calls get no data back. Boss, did you change anything and put it in production?
BOSS: Absolutely not, I just modified the name of what was the "Family" parameter in "Type".
ME: Seems legit. Totally agree. I'm going to lunch. Can you check in the meanwhile why calling the API with "Family" does return nothing? Thanks.3 -
In a user-interface design meeting over a regulatory compliance implementation:
User: “We’ll need to input a city.”
Dev: “Should we validate that city against the state, zip code, and country?”
User: “You are going to make me enter all that data? Ugh…then make it a drop-down. I select the city and the state, zip code auto-fill. I don’t want to make a mistake typing any of that data in.”
Me: “I don’t think a drop-down of every city in the US is feasible.”
Manage: “Why? There cannot be that many. Drop-down is fine. What about the button? We have a few icons to choose from…”
Me: “Uh..yea…there are thousands of cities in the US. Way too much data to for anyone to realistically scroll through”
Dev: “They won’t have to scroll, I’ll filter the list when they start typing.”
Me: “That’s not really the issue and if they are typing the city anyway, just let them type it in.”
User: “What if I mistype Ch1cago? We could inadvertently be out of compliance. The system should never open the company up for federal lawsuits”
Me: “If we’re hiring individuals responsible for legal compliance who can’t spell Chicago, we should be sued by the federal government. We should validate the data the best we can, but it is ultimately your department’s responsibility for data accuracy.”
Manager: “Now now…it’s all our responsibility. What is wrong with a few thousand item drop-down?”
Me: “Um, memory, network bandwidth, database storage, who maintains this list of cities? A lot of time and resources could be saved by simply paying attention.”
Manager: “Memory? Well, memory is cheap. If the workstation needs more memory, we’ll add more”
Dev: “Creating a drop-down is easy and selecting thousands of rows from the database should be fast enough. If the selection is slow, I’ll put it in a thread.”
DBA: “Table won’t be that big and won’t take up much disk space. We’ll need to setup stored procedures, and data import jobs from somewhere to maintain the data. New cities, name changes, ect. ”
Manager: “And if the network starts becoming too slow, we’ll have the Networking dept. open up the valves.”
Me: “Am I the only one seeing all the moving parts we’re introducing just to keep someone from misspelling ‘Chicago’? I’ll admit I’m wrong or maybe I’m not looking at the problem correctly. The point of redesigning the compliance system is to make it simpler, not more complex.”
Manager: “I’m missing the point to why we’re still talking about this. Decision has been made. Drop-down of all cities in the US. Moving on to the button’s icon ..”
Me: “Where is the list of cities going to come from?”
<few seconds of silence>
Dev: “Post office I guess.”
Me: “You guess?…OK…Who is going to manage this list of cities? The manager responsible for regulations?”
User: “Thousands of cities? Oh no …no one is our area has time for that. The system should do it”
Me: “OK, the system. That falls on the DBA. Are you going to be responsible for keeping the data accurate? What is going to audit the cities to make sure the names are properly named and associated with the correct state?”
DBA: “Uh..I don’t know…um…I can set up a job to run every night”
Me: “A job to do what? Validate the data against what?”
Manager: “Do you have a point? No one said it would be easy and all of those details can be answered later.”
Me: “Almost done, and this should be easy. How many cities do we currently have to maintain compliance?”
User: “Maybe 4 or 5. Not many. Regulations are mostly on a state level.”
Me: “When was the last time we created a new city compliance?”
User: “Maybe, 8 years ago. It was before I started.”
Me: “So we’re creating all this complexity for data that, realistically, probably won’t ever change?”
User: “Oh crap, you’re right. What the hell was I thinking…Scratch the drop-down idea. I doubt we’re have a new city regulation anytime soon and how hard is it to type in a city?”
Manager: “OK, are we done wasting everyone’s time on this? No drop-down of cities...next …Let’s get back to the button’s icon …”
Simplicity 1, complexity 0.16 -
User: *Clicks on staging environment*
Giant Warning Dialog: YOU ARE CURRENTLY ENTERING THE STAGING ENVIRONMENT
Users: Ok
App: *Completely different colour, I’m talking bright unsightly yellow*
User: Ok
Giant Yellow and Red Flashing Banner at the Top of the Screen: WARNING YOU ARE CURRENTLY USING STAGING, THIS AREA IS FOR TESTING ONLY
User: The production environment sure is acting strange today. It’s a weird colour and I don’t recognize any of the data, it’s all just dummy filler data. I better create a ticket for the dev team to check o—….. no wait I’ll send an email CC everyone including the CEO and sound the alarm production is currently down and filled with giant warning messages.
Manager: OH MY GOD PRODUCTION IS DOWN DID YOU HEAR ABOUT THIS??? WHAT THE FUCK COULD THESE WARNING MESSAGES BE THAT’S ONLY SUPPOSED TO HAPPEN ON STAGING! THE CEO IS BREATHING DOWN MY NECK YOU NEED TO GET THIS FIXED IMMEDIATELY!!!!!!!
Dev: …11 -
Interviewer: So are you familiar with our company and what we do?
Dev: I looked at your website, looks like you build tools for managing restaurants.
Interviewer: No. That’s not even close.
Dev: ?
Interviewer: What we do is create an ecosystem of integrated data centres all orchestrated for immediate stakeholder utilization.
Dev: But the product itself…. it’s a user interface for tracking inventory. Of like…. burgers…. and bottles of wine.
Interviewer: It’s not a product! It’s a data……habitat!!
Dev: …
Dev: So does that make your users animals?
Interviewer: 😡. Unfortunately it looks like you do not see our vision and would not be a good fit for this role.
Dev: Agreed.23 -
I just got a text from T-Mobile telling me about their updated privacy policy and that I can “opt out.” So, naturally I do exactly this.
After a little bit, I land on their “Do not sell my data” page and discover that, not only does it have 175+ trackers,
it doesn’t even fucking work. Also, on the desktop version of the site, the very control allowing the user to opt out of having their data shared/sold doesn’t even render.
These are all absolutely inexcusable.20 -
Devs: We need access to PROD DB in order to provide support you're asking us for.
Mgmt: No, we cannot trust you with PROD DB accesses. That DB contains live data and is too sensitive for you to fuck things up
Mgmt: We'll only grant PROD DB access to DBAs and app support guys
Mgmt: <hire newbies to app support>
App_supp: `update USER set invoice_directory = 54376; commit;`
----------------
I have nothing left to say....7 -
So Facebook provided unlimited data access to loads of companies including spotify/microsoft and other big names.
Although there are privacy rules, those companies had deals which excluded them from these privacy rules.
I don't think my custom DNS server or a pihole is enough anymore, let's firewall block all Facebook's fucking ip ranges.
Source: https://fossbytes.com/facebook-gave...19 -
I still miss my college days. Our crappy IT Dept restricted internet usage on campus. Each student used to get 10 GB of internet data and they used Cyberoam for login (without HTTPS). 10 GB was so less (at least for me).
Now, thanks to CS50, I learned that HTTP was not secure and somehow you can access login credentials. I spent a night figuring things out and then bam!! Wireshark!!!!
I went to the Central Library and connected using Wireshark. Within a matter of minutes, I got more than 30 user ids and passwords. One of them belonged to a Professor. And guess what, it had unlimited data usage with multiple logins. I felt like I was a millionaire. On my farewell, I calculated how much data I used. It was in TBs.
Lesson: Always secure your URLs.5 -
The worst thing I’ve seen a dev do is create a social sharing platform that sells its user data to the highest bidder and then asks for forgiveness after the privacy horse is out of the barn.7
-
Long story short, I'm unofficially the hacker at our office... Story time!
So I was hired three months ago to work for my current company, and after the three weeks of training I got assigned a project with an architect (who only works on the project very occasionally). I was tasked with revamping and implementing new features for an existing API, some of the code dated back to 2013. (important, keep this in mind)
So at one point I was testing the existing endpoints, because part of the project was automating tests using postman, and I saw something sketchy. So very sketchy. The method I was looking at took a POJO as an argument, extracted the ID of the user from it, looked the user up, and then updated the info of the looked up user with the POJO. So I tried sending a JSON with the info of my user, but the ID of another user. And voila, I overwrote his data.
Once I reported this (which took a while to be taken seriously because I was so new) I found out that this might be useful for sysadmins to have, so it wasn't completely horrible. However, the endpoint required no Auth to use. An anonymous curl request could overwrite any users data.
As this mess unfolded and we notified the higher ups, another architect jumped in to fix the mess and we found that you could also fetch the data of any user by knowing his ID, and overwrite his credit/debit cards. And well, the ID of the users were alphanumerical strings, which I thought would make it harder to abuse, but then realized all the IDs were sequentially generated... Again, these endpoints required no authentication.
So anyways. Panic ensued, systems people at HQ had to work that weekend, two hot fixes had to be delivered, and now they think I'm a hacker... I did go on to discover some other vulnerabilities, but nothing major.
It still amsues me they think I'm a hacker 😂😂 when I know about as much about hacking as the next guy at the office, but anyways, makes for a good story and I laugh every time I hear them call me a hacker. The whole thing was pretty amusing, they supposedly have security audits and QA, but for five years, these massive security holes went undetected... And our client is a massive company in my country... So, let's hope no one found it before I did.6 -
Did you read about the new Digital Services Act and Digital Markets Act laws of the European Union, that will go in effect in 2022? Pretty neat stuff, more transparency, user rights and a tool against internet monopolies.
"Very big online plattforms" must submit reports on freedom of speech, abuse of human rights, manipulation of public opinion.
EU assigned scientists will gain access to trade secrets like google search or Amazon recommendation algorithm to analyze potential threats.
The EU can fine serial offenders 10 % of their yearly income. And break up companies that stiffle competition.
Internet companies like Facebook will not be permitted to share user data between their products like Instagram and WhatsApp.
There will be a unified ruleset on online advertisement. Each add must have the option to find out why this add is shown to the user.
Unlike the GDRP data protection rule the two acts will be valid at the Union level. So that there won't be any exceptions from single member states.
Let's hope this leads to a better Internet and not things like cookie pop ups 😄
Link to the EU DMA DSA page
> https://ec.europa.eu/digital-single... 49
49 -
expect([
row[‘blah’][0][1],
row[‘blah’][1][1],
row[’blah’][2][1],
row[‘blah’][3][1],
row[‘blah’][4][1],
]).to contain_exactly(
a.name(user), # “John doe”
c.name(user), # “John doe”
e.name(user), # “John doe”
b.name(user), # “John doe”
d.name(user), # “John doe”
)
(Note: The comments are mine.)
See the problem? No, not the ugly code (which is actually worse than what i posted here).
It’s using the same ridiculous getter (if you can call it that) that pulls a name out of the passed user object, and then expecting each row to have that name, in order. Not that order matters when they’re all the same.
Upon inspection, all objects created by the spec have the exact same name, so the above test passes (as long as there are 5 rows). It passes, but totally not because it should: those aren’t the objects that are actually in the table. All of the specs — all 22 of them — only check for that shared name on various rows, and no other data. And it’s not like this is the only issue, either.
Fuck me these are bad.
And this guy is a senior dev earning significantly more than me. Jesus what the fuck Christ.18 -
Had a discussion with a developer about security. His software transfers all user data (password and files) unencrypted, so anyone can grab them with wireshark. I told him that this is a severe issue. He said no its no problem because if you get hacked its your own fault, because you probably used an insecure network. NO ! YOU FUCKING MALADJUSTED SHEEP-MOLESTING OBJECT OF EXECRATION, YOU SHOULD ALWAYS ENCRYPT SENSITIVE USERDATA NO MATTER WHAT NETWORK YOU USE. FUCKING KILL ME ALREADY.
Not implementing encryption is one thing but then acting like its no problem is a fucking nother one. Why do people not understand that security of userdata is important???11 -
What kind of cum gargling gerbil shelfer stores and transmits user passwords in plain text, as well as displays them in the clear, Everywhere!
This, alongside other numerous punishable by death, basic data and user handling flaws clearly indicate this fucking simpleton who is "more certified than you" clearly doesn't give a flying fuck about any kind of best practice that if the extra time was taken to implement, might not totally annihilate the company in lawsuits when several big companies gang up to shower rape us with lawsuits over data breaches.
Even better than that is the login fields don't even differentiate between uppercase or lowercase, I mean WHAT THE ACTUAL FUCK DO YOU SELF RIGHTEOUS IGNORANT CUNTS THINK IS GOING TO HAPPEN IN THIS SCENARIO?13 -
My neighbor(He is 14 I think) pitched this to me and wanted advice since he was going try to participate in the Google science fair.
Him:"A robot that gives you medical advice. You just tell it your symptoms and voila! You've got your diagnosis. No doctor required."
Me: "How are you going to decide what disease the user has?"
Him:" I'm just going to write an if-else ladder statement. I've already got some of the data from this site called WebMD. It's amazing."
Me: "Go with something simple. What you're suggesting won't work out."
He told me I didn't have "Vision".
His ditched his project last week.18 -
Me: *Demoed my search API which supports multiple database implementations at the backend*
My Manager: Great!! Is the API independent of DB? Can you plug this API to any DB?
Me: Yes
My Manager: How can user specific DB at runtime?
Me: Why will user be interested in the DB used at the backend? He will just query the API for data.
My Manager: Let's just assume he wants to select a database at runtime.
Me: While searching a movie on Netflix, do you specific from which DB you wanna stream the movie?
My Manager: *Confused and pissed*7 -
Developer vs Tester
(Spoiler alert: developer wins)
My last developent was quite big and is now in our system testing department. So last week i got every 20 minutes a call from the tester, that something did not work as expected. For about 90% of the time i looked at the testing setup or the logs and told him, that the data is wrong or he used the tool wrong. After a couple of days i got mad because of his frequent interruptions. So I decided to make a list. Every time he came to me with an "error" i checked it and made a line for "User Error" or "Programming Error". He did not liked that much, because the User Error collum startet to grow fast:
User Errors: ||||| |||
Programming Errors: |||
Now he checks his testing data and the logs 3 times before he calls me and he hardly finds any "errors" anymore.3 -
The fuck did you think was going to happen?
User: ITs dragging their feet which is why x hasn't gone out yet.
PM: Why hasn't this gone out yet?
Me: They sent me a template then another and then said wait that's wrong too I'll send you the correct one.
I've yet to receive this and no one's provided me the data to check over.
PM: Well that's not what x said.
Me: Well my email chain says so. (Proceed to show them the emails)
PM then walks off and blasts the users. Your #blamegame ended the moment you emailed me knob shits. -
Trash, trash, trash.
Who the fuck writes this shit?
Who the fuck lets these trash should-be-junior devs roll their own crypto? and then approves it?
The garbage heap of a feature (signing for all apis) doesn't follow Ruby standards, doesn't follow codebase conventions, has `// this is bridge` style comments (and no documentation), and it requires consumer devs to do unnecessary work to integrate it, and on top of all this: it leaks end-user data. on all apis. in plaintext.
Fucking hell.7 -
Boss: We need health data for this iOS app.
Me: Cool, so we'll use apples HealthKit.
Boss: No that requires the user agrees to it.
Me: ... well yeah ... its private data.
Boss: No we need it to work regardless. If the user says no to HealthKit, just give them textfields for all the metrics HealthKit has and they can enter manually.
Me: .... but ... eh ....
Boss: and we'll partner with some companies and support their devices.
Me: ... see, the thing is ...
Boss: We also need to store it locally and then sync it to the cloud app. What do you think?
Me: ... ... ... no2 -
Business User [1 PM]: So I know every month you’ve been using your dark magic SQL skills to transform my monthly data into better monthly data.
Well I know it’s the middle of the month, and this is totally random... but... I have some other data formatted totally differently, almost totally different data! You can just run this through your magic SQL Proc right?? Easy! Also, I need this by end of day... thank you for your support.
Me [1:01 PM]: K.4 -
Not only do I write software, but now I help the managers view and understand our analytics, just like in kindergarten.
Now I'm forced to help them essentially fake data so investors are satisfied 🤡🔫
"Delete metrics X, Y, and Z for now, we don't want anyone to see them!"
"Change the label of this metric to 'unique user' views! (not total!)"
"Set all charts to cumulative so it looks like they are all up and to the right!"
Sigh.
This isn't what I signed up for.17 -
FUCK THE RECRUITERS WHO ASK US TO MAKE AN ENTIRE PROJECT AS A CODE TEST.
Oh you need to scrape this website and then store the data in some DB. Apply sentimental analysis on the data set. On the UI, the user should be able to search the fields that were scraped from the website. Upon clicking it should consume a REST API which you have to create as well. Oh and also deploy it somewhere... Oh I almost forgot, make the UI look good. If you could submit it in one week, we will move towards further rounds if we find you fit enough.
YOU KNOW WHAT, FUCK YOU!
I can apply to 10 others companies in one week and get hired in half the effort than making this whole project for you which you are going to use it on your website YOU SADIST MOTHERFUCK
I CURSE YOUR COMPANY WITH THE ETERNITY OF JS CALLBACK HELL 😡😤😣9 -
Business User: Hey can we get a sample output you plan to send us?
Me: yes heres a mock
BU: This doesn't look right, can you use real values?
Me (said nicely): WELL IF WHEN YOU WROTE THE FCKIN REQUIREMENTS WEREN'T SO VAGUE AND ACTUALLY PROVIDED REAL VALUES FOR THE INPUTS WE WOULD GET AND WHAT WE SHOULD OUTPUT USING THEM MAYBE I COULD GIVE YOU A BETTER SAMPLE... AND DO LESS GUESSING ABOUT WHAT THE FUCK YOU ACTUALLY WANT...
BU: Oh I forwarded some data
Me: *looks at input data*
(thoughts) THIS FUCKING MAKES NO SENSE!! NOWHERE DOES ANYTHING LOOK LIKE WHAT YOU WANTED.... HOW ABOUT I PULL MAGIC VALUES OUT OF MY ASS?6 -
Dev: Can you please tell me why you changed this?
Me: Because we need to handle permissions in the app. The quickest way of doing it, according to the docs, is [insert change log here]
Dev: But we can just check for the user's token.
Me: That's not exactly a permission, because...
Dev: I was only showing the information related to the user according to their token.
Me: I understand. But that means you're filtering data, not authorising users to access it. If a user is logged in, but changes query parameters, they can still access data they shouldn't be able to.
Dev: Whatevs.
Le me then proceeds to try to push my changes (that took the whole day to implement), gets a "you need to pull first" message from git, doesn't understand why, logs onto GitHub and realises dev has implemented their "permissions".
I was the one responsible for making those changes. Le dev was meant to be doing other things.
How do I even begin to explain?7 -
Managements definition of an MVP:
- Integrate our backend and database with a similar-ish, older internal system built on a different tech stack and different rules.
- Merge the functionality and delete the old one.
- Modify our system to accept 2 types of logged in users.
- Have 2 versions of our API that return different values.
- Update our mobile app to render different data based on which user is logged in.
- Onboard the old system users to this new system.
My definition of an MVP:
- Tell the store we are taking over, that they have to print their labels from our tool, and onboard the users to our app.9 -
Me : I should start building user authentication system.
inner self : there are enough free and secure ones out there, just go read the documentation.
Me : fuck I'm not reading 10000 pages of documentation written in alien language.
inner self : well then you better start building
Me : **writes code
Inner self : you better add the data validation and security while coding
Me : I just want it to work !
Me after a few days trying not to suicide : the site is hacked, the code is bugged, hello darkness my friend5 -
Me:
Totally riffing to my new playlist....
the ideas are just flowing.....
Code flying...
changing in my brain....
I think I've got I might have it.....
...... RING RING ITS THE MOTHERFUCKING BOSS,
Boss:
Why is the whole website down?
Me: WTF, looks fine here, all logs are clear.
Boss: I just got an email saying the whole thing is fucked. Stop everything and fix it now.
Me: but we just agreed dev is taking priority over any support issues within sla and I've checked from everywhere there are no issues, just data issues probably from user error.
Boss: Just get it back and figure it out!!!!! Why are you being difficult?
Me: okay whatever, let's patch each of these shits.
COULDVE SENT THIS ANYWHERE BUT NOW MY IDEA IS GOOOONEEE!!!!!! NULL FUCKING DATA FIELD ON A SINGLE FUCKING EMAIL....FRAAAAACKKK THIS4 -
Fuck Optimizely.
Not because the software/service itself is inherently bad, or because I don't see any value in A/B testing.
It's because every company which starts using quantitative user research, stops using qualitative user research.
Suddenly it's all about being data driven.
Which means you end up with a website with bright red blinking BUY buttons, labels which tell you that you must convert to the brand cult within 30 seconds or someone else will steal away the limited supply, and email campaigns which promise free heroin with every order.
For long term brand loyalty you need a holistic, polished experience, which requires a vision based on aesthetics and gut feelings -- not hard data.
A/B testing, when used as some kind of holy grail, causes product fragmentation. There's a strong bias towards immediate conversions while long term churn is underrepresented.
The result of an A/B test is never "well, our sales increased since we started offering free heroin with every sale, but all of our clients die after 6 months so our yearly revenue is down -- so maybe we should offer free LSD instead"5 -
So... GDPR.
And the deadline.
And I have no idea what to do.
What does it mean for one-man indie projects? Data protection officers? Companies? Controllers? Processors? EU employees? Argh.
Look, please, EU. Not everyone can afford to hire an entire team for this, when their current team is literally one person.
Yes, the GDPR is probably a step in the right direction, but I think I'll just stop collecting the data altogether.
(All data I collect is just user settings stored in a database, nothing more.)
Can someone point me in the right direction?8 -
Getting ready for GDPR at work. I had to explain to my bosses what it meant, especially regarding one of our project where we store a lot of user data. Then I heard it: "this crap doesn't regard us. we have no sensitive data. we only save out users' name and generalities.". I have no words.3
-
Stakeholder: In user profiles, I want users to be able to renew gift memberships for their giftee.
Me: ???
SH: For example, if I buy a gift membership for you and it expires or is about to expire, then I want to be able to renew it for you.
Me: Typically, gifts aren’t the gifter’s responsibility to manage. There’s no reason for you to be able to manage my membership from your account, even if just to renew. You’re opening up Pandora’s box here. If you let users renew for giftees, you’ll eventually have a user ask if they can cancel the giftee’s membership because they got into a fight and want to stick it to the giftee.
SH: But our users aren’t using the gift membership sales flow correctly. That results in all sorts of data issues for our reporting services and we spend so much time fixing it by hand.
Me: Your sales flow is confusing. The website asks users to verify membership for a giftee in case the giftee has or had a membership. How it the gifter supposed to know that? You’re trying to make things easier for you, but you’re expecting the user to know that and comply. That’s unrealistic.
SH: But there must be a something you can do.
Me: No.9 -
My code review nightmare?
All of the reviews that consisted of a group of devs+managers in a conference room and a big screen micro-analyzing every line of code.
"Why did you call the variable that? Wouldn't be be more efficient to use XYZ components? You should switch everything to use ServiceBus."
and/or using the 18+ page coding standard document as a weapon.
PHB:"On page 5, paragraph 9, sub-section A-123, the standards dictate to select all the necessary data from the database. Your query is only selecting 5 fields from the 15 field field table. You might need to access more data in the future and this approach reduces the amount of code change."
Me: "Um, if the data requirements change, wouldn't we have change code anyway?"
PHB: "Application requirements are determined by our users, not you. That's why we have standards."
Me: "Um, that's not what I ..."
PHB: "Next file, oh boy, this one is a mess. On page 9, paragraph 2, sub-section Z-987, the standards dictate to only select the absolute minimum amount of the data from the database. Your query is selecting 3 fields, but the application is only using 2."
Me: "Yes, the application not using the field right now, but the user stated they might need the data for additional review."
PHB: "Did they fill out the proper change request form?"
Me: "No, they ...wait...Aren't the standards on page 9 contradictory to the standards on page 5?"
PHB: "NO! You'll never break your cowboy-coding mindset if you continue to violate standards. You see, standards are our promise to customers to ensure quality. You don't want to break our promises...do you?"6 -
User: Hey, we got a big issue with one of your tools. One of your pages isn't loading.
Me: Ok, so when did this happen?
User: We don't know? Its been like that for a long time though, so we thought it was normal 😃
Me: ....ok. So do you know what data is supposed to appear?
User: Uhhh we're not sure as well. Since, you know, its been like that for a while.
Just great 😑4 -
Sad story:
User : Hey , this interface seems quite nice
Me : Yeah, well I’m still working on it ; I still haven’t managed to workaround the data limit of the views so for the time limit I’ve set it to a couple of days
Few moments later
User : Why does it give me that it can’t connect to the data?
Me : what did you do ?
User : I tried viewing the last year of entries and compare it with this one
Few comas later
100476 errors generated
False cert authorization
Port closed
Server down
DDOS on its way1 -
"The aim is to develop highly robust data streams so we have the flexibility to build and evolve the user interface without having to change code in the API"
Oh, is that all you need? 4
4 -
User: I need you to extract all the invoice data for us.
Me: What invoice data in particular, what are filters you require. This is a massive database with millions of transactions.
User: JUST EXTRACT THE TABLE!
Me: Right.....(this is a database with 3000+ tables and hundreds of joins)7 -
Three months into a new job, as a senior developer (12+ years experience) and updated an import application.
With one small update query that didn't account for a possible NULL value for a parameter, so it updated all 65 million records instead of the 15 that belonged to that user.
Took 3 people and 4 days to put all the data back to it's original state.
Went right back to using the old version of the apllication, still running 2 years later. It's spaghetti code from hell with sql jobs and multiple stored procedures creating dynamic SQL, but I'm never touching it again.5 -
This week I reached a major milestone in a Machine Learning/Music Analysis project that I've been working on for a long time!!
I'm really proud to launch 'The Harmonic Algorithm' as an open source project! It represents the evolution of something that's grown with me through two thesis' (initially in music analysis and later in creative computation) and has been a vessel for my passion in both Music and Computation/Machine Learning for a number of years.
For more info, detailed usage examples (with video clips) and installation instructions for anyone inclined to try it out, have a look at the GitHub repo for the project:
https://github.com/OscarSouth/...
"The Harmonic Algorithm, written in Haskell and R, generates musical domain specific data inside user defined constraints then filters it down and deterministically ranks it using a tailored Markov Chain model trained on ingested musical data. This presents a unique tool in the hands of the composer or performer which can be used as a writing aid, analysis device, for instrumental study or even in live performance." 1
1 -
I managed to accidentally clear everybody's usernames and email addresses from an SQL table once. I only recovered it because a few seconds before, I'd opened a tab with all the user data displayed as an HTML table. I quickly copied it into Excel, then a text editor (saving multiple times!), then managed to write a set of queries to paste it all back in place. If I'd refreshed the tab it would have all gone!2
-
Goddamn, people who rant against the GDPR make me rage...
Making privacy issues more complex for both user and provider is exactly the damn purpose! People who dont care about their private data make me sick! These ignorant fucks get to elect my government? Wtf! GDPR means more work for companies but that also means companies who actually care will implement it and everyone else can gladly fuck off! Keep your stuff in the states where you can build your own manipulative society...
Damn... I should relax a bit...4 -
A popular social media website in my country (which my friends and I were working on it's new design) was hacked and everyone on the dev side of the website was invited to the ministry of communications, believing we were going to discuss security of user data. The other guys (working on the back-end) were friends with the CEO (if you want to call it that) and naturally came to the meeting. They started to talk about the girls of their city. Meanwhile about 1.2 million user data encrypted with MD5 was out there.6
-
2012 laptop:
- 4 USB ports or more.
- Full-sized SD card slot with write-protection ability.
- User-replaceable battery.
- Modular upgradeable memory.
- Modular upgradeable data storage.
- eSATA port.
- LAN port.
- Keyboard with NUM pad.
- Full-sized SD card slot.
- Full-sized HDMI port.
- Power, I/O, charging, network indicator lamps.
- Modular bay (for example Lenovo UltraBay)
- 1080p webcam (Samsung 700G7A)
- No TPM trojan horse.
2024 laptop:
- 1 or 2 USB ports.
- Only MicroSD card slot. Requires fumbling around and has no write-protection switch.
- Non-replaceable battery.
- Soldered memory.
- Soldered data storage.
- No eSATA port.
- No LAN port.
- No NUM pad.
- Micro-HDMI port or uses USB-C port as HDMI.
- Only power lamp. No I/O lamp so user doesn't know if a frozen computer is crashed or working.
- No modular bay
- 720p webcam
- TPM trojan horse (Jody Bruchon video: https://youtube.com/watch/... )
- "Premium design" (who the hell cares?!)11 -
While trying to integrate a third-party service:
Their Android SDK accepts almost anything as a UID, even floats and doubles. Which is odd, who uses those as UIDs? I pass an Integer instead. No errors. Seems like it's working. User shows up on their dashboard.
Next let's move onto using their data import API. Plug in everything just like I did on mobile. Whoa, got an error. "UIDs must be a string". What. Uh, but the SDK accepts everything with no error. Ok fine. Change both the SDK and API to return the UID as a string. No errors returned after changing the UIDs.
Check dashboard for user via UID. Uh, properties haven't been updating. Check search properties. Find out that UIDs can only be looked up as Integers. What? Why do you ask me to send it as a string via the API then? Contact support. Find out it created two distinct records with the UID, one as a string and the other as an Integer.
GFG.3 -
*Working on a project with boss, I am working on a mobile app, he is working on web service app.
Me: this service takes user id as parameter to get all account details (all other web services are like that)
Boss: yes, I use the id to filter the data.
Me: but by this, everyone has the id can do anything ! why we do not use session token?
Boss: this is a detail, it is not important !
Me:...
*7 years of experience my ass 5
5 -
For fucks sake, how many times can you get the same error before giving up?
So, there's this form, and it's used quite frequently without fail, and there's this 1 user receiving an error that some data is incorrect, so... they submit the form again, and again, and again, and 6 more times with the same bloody error all because changing 1 fucking field is obviously to hard to recognise as the problem when the error says "you can not have 'x' in field 'y'"
Fuck it, do I need to replace 'x' with a blank, just because you can't read a fucking error message?11 -
The Hungarian public transport company launched an online shop (created by T-Systems), which was clearly rushed. Within the first days people found out that you could modify the headers and buy tickets for whatever price you set, and you could login as anyone else without knowing their password. And they sent out password reminders in plain text in non-encrypted emails. People reported these to the company which claims to have fixed the problems.
Instead of being ashamed of themselves now they're suing those who pointed out the flaws. Fucking dicks, if anyone they should be sued for treating confidential user data (such as national ID numbers) like idiots.3 -
That feeling when the business wants you to allow massive chunks of data to simply be missing or not required for "grandfathered" accounts, but required for all new accounts.
Our company handles tens of thousands of accounts and at some point in the past during a major upgrade, it was decided that everyone prior to the upgrade just didn't need to fill in the new data.
Now we are doing another major upgrade that is somewhat near completion and we are only just now being told that we have to magically allow a large set of our accounts to NOT require all of this new required data. The circumstances are clear as mud. If the user changes something in their grandfathered account or adds something new, from that point on that piece of data is now required.
But everything else that isn't changed or added can still be blank...
But every new account has to have all the data required...
WHY?!2 -
Just got an email with a new really nice douche-bag move from Postman to raise their prices again (this time for almost double) on their paid plans with excuse "it will help us deliver more of what our customers need from us."
Even though I've decided to look other way around for years on their electron-based garbage of bloated app, have not been a fan of their pricing 8$/month/user just for a simple feature such as sharing request schema and environment data.
This simply needs to stop and I'm seriously thinking about doing something about it. 🙄10 -
TLDR: Find a website that requires a subscription but doesn't check their cookies' integrity, now I'm on a website for free.
>be me
>wonder if it's possible to intercept browser data
>download Wireshark
>download Fiddler
>find that none of these really fit me
>go to youtube, search how to intercept POST data
>find something called BurpSuite
>Totally what I was looking for
>start testing BurpSuite on devrant
>neat!
>I can see all the data that's being passed around
>wonder if I can use it on a website where my subscription recently ended.
>try changing my details without actually inputting anything into the website's form
>send the data to the server
>refresh the page
>it worked
>NEAT!
>Huh what's this?
>A uid
>must be a userID
>increment it by 1 and change some more details
>refresh the page
>...
>didn't work 😐
>Hmmm, let's try forwarding the data to the browser after incrementing the uid
>OH SHIT
>can see the details of a different user
>except I see his details are the details I had entered previously
>begin incrementing and decrementing the uid
>IFINITE POWER
>realize that the uid is hooked up to my browsers local cookie
>can see every user's details just by changing my cookie's uid
>Wonder if it's possible to make the uid persistent without having to enter it in every time
>look up cookie manipulator
>plug-in exists
>go back to website
>examine current uid
>it's my uid
>change it to a different number
>refresh the webpage
>IT FUCKING WORKED
>MFW I realize this website doesn't check for cookie integrity
>MFW I wonder if there are other websites that are this fucking lazy!!!
>MFW they won't fix it because it would require extra work.
>MFuckingFW they tell me not to do it again in the future
>realize that since they aren't going to fix it I'll just put myself on another person's subscription.5 -
Did a code test at an interview, had to aggregate data from a db. They stored cities with population count and users referenced cities.. 6 cities had a higher user count than population 🤔
They were a little taken back and suggested the population data must be outdated 😉.. it got a bit awkward1 -
Thank God the week 233 rants are over - was getting sick of elitist internet losers.
The worst security bug I saw was when I first started work as a dev in Angular almost year ago. Despite the code being a couple of years old, the links to the data on firebase had 0 rules concerning user access, all data basically publicly available, the API keys were uploaded on GitHub, and even the auth guard didn't work. A proper mess that still gives me the night spooks to this day.3 -
A project I'm working on uses Elastic for internal monitoring and logs. The customer asked to access those logs - not something we'd normally do, but it's isolated from other things we use and there's no critical data there, so what the heck, let them have it.
Ever since, we're getting tons of questions like "There are tons of [insert random info message] all the time, do you have any plans to resolve them?" and it gets to the point where I'm just about ready to scream back "NO, SUZAN, BOOKING NOT COMPLETED MANS THE USER F###ING CANCELLED IT, IT'S NOT SOMETHING I CAN FIX IN THE CODE"
Edit: the customer's name isn't actually Suzan4 -
Hey !
A big question:
Assume we got an android app which graphs a sound file .
The point is: the user is able to zoom in/out so the whole data must be read in the begining , but as the file is a little longer , the load time increases.
What can i do to prevent this?3 -
"So Alecx, how did you solve the issues with the data provided to you by hr for <X> application?"
Said the VP of my institution in charge of my department.
"It was complex sir, I could not figure out much of the general ideas of the data schema since it came from a bunch of people not trained in I.T (HR) and as such I had to do some experiments in the data to find the relationships with the data, this brought about 4 different relations in the data, the program determined them for me based on the most common type of data, the model deemed it a "user", from that I just extracted the information that I needed, and generated the tables through Golang's gorm"
VP nodding and listening intently...."how did you make those relationships?" me "I started a simple pattern recognition module through supervised mach..." VP: Machine learning, that sounds like A.I
Me: "Yes sir, it was, but the problem was fairly easy for the schema to determ.." VP: A.I, at our institution, back in my day it was a dream to have such technology, you are the director of web tech, what is it to you to know of this?"
Me: "I just like to experiment with new stuff, it was the easiest rout to determine these things, I just felt that i should use it if I can"
VP: "This is amazing, I'll go by your office later"
Dude speaks wonders of me. The idea was simple, read through the CSV that was provided to me, have the parsing done in a notebook, make it determine the relationships in the data and spout out a bunch of JSON that I could use. Hook it up to a simple gorm golang script and generate the tables for that. Much simpler than the bullshit that we have in php. I used this to create a new database since the previous application had issues. The app will still have a php frontend and backend, but now I don't leave the parsing of the data to php, which quite frankly, php sucks for imho. The Python codebase will then create the json files through the predictive modeling (98% accuaracy) and then the go program will populate the db for me.
There are also some node scripts that help test the data since the data is json.
All in all a good day of work. The VP seems scared since he knows no one on this side of town knows about this kind of tech. Me? I am just happy I get to experiment. Y'all should have seen his face when I showed him a rather large app written in Clojure, the man just went 0.0 when he saw Lisp code.
I think I scare him.12 -
Imagine
websites didn't use unnecessary cookies,
JavaScript was only used when needed,
no trackers, no ads, no telemetry, no user
data saved when it doesn't benefit the user.
*Wakes up in cold sweat*7 -
when I was a newbie I was given a task to upload a site.
I had done that many times before so I thought it wont be a big deal so I thought I never gave a try uploading through ftp.
Okay I began work on it the server was of godaddy and credentials I got were of delegate access.
right I tried connecting through ftp but it wasn't working thought there's some problem with user settings why shouldn't I create my own user to stay away from mess.
Now I creater my own user and could easily login but there were no files in it saw that by creating user my folder is different and I dont have access to server files I wanted to take backup before I do upload.
now I was thinking to give my user access to all files so I changed the access directory to "/" checked ftp again there was still no file.
don't know what happened to me I thought ahh its waste of time for creating ftp user it does nothing and I deleted my ftp account.
now I went through web browser to download data and earth skids beneath my foots. Holy fuck I lost all the data, all were deleted with that account it scared the shit out of me.
There were two sites running which were now gone.
Tried every bit to bring them back but couldn't do so. i contact support of godaddy they said you haven't enabled auto backup so you can't have them for free however they can provide their service in $150. Which is 15k in my country.
I decided to tell my boss about what happened and he got us away :p I wasn't fired gladly -
Corp: you will get a four hour assignment to work out
Me: cool nice.
Corp: here it is, build a dragon with conflicting requirements, stocks but without any form of pricing mixed in. Then slay that dragon and post it to the static backend we created.
Me: cringe much?
Corp: yeah, you can spend more than 4h but be sure to spice things up abit. Since it is frontend, and all we spin up from the backend is flat data. But it must exhale an exciting user experience.
Me: stop the cringe pls!4 -
Putty remote executuon vulnerability(no patch yet)
The vulnerability allows a remote attacker to execute arbitrary code on the target system.
The vulnerability exists due to unspecified input validation error when processing data, received from SSH server. A remote attacker can trick the victim to connect to a specially crafted SSH server and execute arbitrary code on the target system with privileges of the current user.
Successful exploitation of the vulnerability may allow an attacker to compromise vulnerable system.7 -
After 4 years of professional programming the most important thing that I learned is "user is stupid".
Once I modified old code that was summing salaries (I added extra column to the result), nothing else. My result was rejected because all salaries was empty. Period of data was from first day of the month from user selected date to user selected date. It turned out that user was selecting 27th day of the month (it was 27th then). I responded that salaries have full month period, and you'll have to choose end of the month... And then shitstorm began, that I messed up previous functionality. I tried to explain, but it wasn't working. It ends up with user selecting any date and I'm doing end-of-the-month in the background^^
It's my first rant, welcome to you all :)4 -
The security on my school computers is a joke.
The standard student accounts have no user rights, but the "guest" account has admin rights???
The teachers private data is not secured, it's just hidden from explorer, so if you manually type in the folder location into the explorer bar, you can access the teacher's data. Not to mention everything is running on Windows 7 machines from 10 years ago.1 -
Stakeholder: Users are connecting invalid memberships to their web accounts. They shouldn’t be able to do that.
Me: Their memberships were valid when they set up the account. Your team’s record de-duping project is the issue here. You decided to mark those memberships as invalid.
I’m real tired of this stakeholder acting like this is a website issue or user error. Plus, this chaos could have been avoided if they and other involved stakeholders had just cc’d me on this de-duping project. I would have said their approach was not a good idea. But they didn’t because they want to do what’s convenient for them. If they want to be a reliable source of truth for our data, then they need to be responsible with how they’re handling that data.devrant why are you so irresponsible with our data this is not user error i’m real tired of this stakeholder2 -
Dev team: This part of the app has a shitty ux. We want to fix it after we finish this feature.
Business: hey guys we think we lack data so we got some users to check our page with shitty ux and see if they think it is shit
User: yeah it’s shit
Great use of resources you chucklefucks6 -
A coworker of mine was asked to make a utility C# app to help with our internal testing. The idea was that the app would collect data and display the results.
He decided that it was very important that the app have a command line interface. He's spent far more time building the app from scratch for the command line than he would have if he'd used C#'s built-in GUI utilities.
Today was our demo day and he shows an internal command-line app in 2017 built in C#. I asked about the GUI and he said that the command line functionality was more important. I suggested that it was maybe less user-friendly and he proceeded to explain to me how "non-technical" people might prefer a GUI, but clearly any serious developer would just want a command line app.
I feel like, in one fell swoop, he trivialized my suggestion, didn't address any of the data visualization needs, and suggested I wasn't a "real developer". Am I right to feel a little outraged by this?5 -
PyTorch.
2018: uh, what happens when someone uses a same name attack? - No big deal. https://github.com/pypa/pip/...
2020: I think that's a security issue. - Nanana, it's not. https://github.com/pypa/pip/...
2022: malicious package extracts sensitive user data on nightly. https://bleepingcomputer.com/news/...
You had years to react, you clowns.5 -
Fuck you Intel.
Fucking admit that you're Hardware has a problem!
"Intel and other technology companies have been made aware of new security research describing software analysis methods that, when used for malicious purposes, have the potential to improperly gather sensitive data from computing devices that are operating as designed. Intel believes these exploits do not have the potential to corrupt, modify or delete data"
With Meltdown one process can fucking read everything that is in memory. Every password and every other sensible bit. Of course you can't change sensible data directly. You have to use the sensible data you gathered... Big fucking difference you dumb shits.
Meltown occurs because of hardware implemented speculative execution.
The solution is to fucking separate kernel- and user-adress space.
And you're saying that your hardware works how it should.
Shame on you.
I'm not saying that I don't tolerate mistakes like this. Shit happens.
But not having the balls to admit that it is because of the hardware makes me fucking angry.5 -
When there’s a glaring user-facing issue in your company’s app that can cause the user to spend mobile data after specifically choosing a setting that’s supposed to prevent that.
And your boss says your fix is “out of scope for the current sprint.” And the product team agrees with him.
I ALREADY DID THE WORK AND HAD IT VERIFIED BY QA.
Sometimes I Hate agile. Then again, I don’t think we’re doing it quite right anyway.2 -
Hello everyone,
I'm new here. [OK. Let's skip this]
I want to know where to begin on my journey on learning how to create a program that predicts what a user will say next by storing already said things and by making specific characteristics for the users.
I know that I will need to train it with some data first lol.
But how will it do the prediction. I just need this part of understanding.
I'm sorry for my bad English btw.7 -
Why the fuck do apps throw tantrums as soon the phone looses internet connectivity?
HBO stops steaming and closes the player as soon as wifi disconnects, discarding the buffered data.
For Quora, it replaces loaded answers with a UI asking you to reload the page. Now, what am I supposed to do in the lift? Stare awkwardly at the lift buttons?
At what point did we decided bad user experience and arbitrarily discarding cached data is the way forward?4 -
So I just started a part time job in a hospital research center - because the processing is long I got a temporary user name and password (that belong to the main HR secretary) so I can start work straight away (mainly data analytics)
The kick?
Administrator privileges.
I can access edit create or delete everything in the entire fucking database. On my first God damn day.
In the 2nd largest hospital in the fucking country.
Agh. How do systems survive with so many dumb security breaches?4 -
Client asked us to build standard dating app. Android version was published without problem but iOS version was rejected because during registration we collect data application does not need to work properly, that data is age and gender of user...2
-
Being Honest,
I never had any problem with Google tracking my activities. I love their services and I feel like they're using my data to really serve me better.
But I do have problems with Amazon and Facebook.
Amazon keeps disturbing me with their annoying ads recommending things I've already purchased.
Using Facebook on the other hand is like standing nude in public.18 -
If you need 10TB of User data to make a marketing strategy, you might be in the wrong business. When I was young we used our imagination to make good marketing ;-P2
-
Fun fact!
Xiaomi has a restriction where you're only allowed a bootloader unlock key one week after you've requested it. No, not a week after you've bought the phone. Not a week after you created an account and generated so much usage data that it would be stupid to doubt you're a genuine user.
No, you have to wait one week after installing their fucking desktop app and getting past some arbitrary point in the process.
Seriously, how much shit can this company pull with a straight face? At this point they're just sabotaging me, it's not even for any reason.16 -
What the actual fuck...
What kind of API does not do data integrity validation, and allows me to subscribe a user to a newsletter list with a non-existant list id ?
That's some fucking bullshit. fucktards at www.make.as1 -
i want to get my own social network up and running.
so far ive got -
login 100% securely
register (1000% securely)
view someone’s profile (10^7% securely)
to add -
scrypt (maybe bcrypt, however scrypt looks like the better option)
friend a user
track their every move (ill use facebooks and googles apis for that)
to describe my product -
ai
blockchain
iot
big data
machine learning
secure
empower
analysis
call me when im a gazillionaire
but seriously, im making a social network and i hope its done by wk105 tbh3 -
Carmack: "Hi, I am Carmack, your AI artist today. I create high definition 3D interactive world by listening to your verbal request or brain-computer interface."
User: "Hey Carmack, create me an ideal cyberpunk world."
Carmack: "World created. Here are the main resources used to synthesize your defintion of 'Cyberpunk'. Done. Is that what you want?"
User: "Hey Carmack, can you make it less similar to Coruscant, but more vintage, and more like Blade runner more like Africa, mixing super Mario galaxy. Also add a mansion similar to this link and the hot girl in this link. Make her ideal. Make the world ten times bigger than GTA V"
Carmack: "Alright, bro. The definition of "ideal" has been data driven by the norm on internet.
Done. Is this what you want?"
user: "Yes, test it in VR"
Carmack: "Enjoy."3 -
Around 2 years ago, I had first discovered DevRant.
I was an intern in a startup then, and I was working on ElasticSearch. I remember making rants about it. The internship ended. So did my relationship with ElasticSearch.
This week, a new intern joined our organisation (a different organisation). He was assigned the task of deploying ElasticSearch, with me as his mentor. All was going good, we migrated data from MongoDB to ElasticSearch and all.
Back then, I used to curse the team lead (leading a team of interns mostly), for not helping me properly...
I wanted a publicly accessible dashboard, since we can't really see the Kibana dashboard with SSH :P... So, we implemented user authentication using X-Pack security. And here we are, stuck... Again... I'm unable to help the intern. The World has come to a full circle.
PS: I have to just guide him while doing my own User Stories.
https://stackoverflow.com/questions... -
User: This web page form is too hard to use and is prone to have wrong data filled out.
Me: Uh...ok. Here is a redesign. You literally fill out one text field and a date picker.
User: Oh this is great, thanks.
*checks the database and the very first entry they created had the wrong date.*
Fuck me.6 -
So, I was able to hack into a local business (legally) in under two minutes today... great and scary right? Get this, it was from my iPhone. All switches were still the default username and password... after seeing that they didn't think anything was wrong and didn't sign the contract... imagine what I could have done with my laptop and my PWNtools...
Fuck it, more (l)user data for me to log.😏5 -
management logic.
dev : calling api on every product scroll is a stupid idea. we shouldn't do it. what if user has 100s of products bought?
mgmt : it isn't a practical scenario. in prod, we checked the data and we rarely have customers with more than 20 products
dev : 😮🤷♂️
dev : this is a rare issue that only happens for very old devices from this specific manufacturer. even manufacturers have acknowledged this.
mgmt : we don't care. fix it, as per data this error has been logged for more than 12 times (from 1 user only)
dev : 😮😢2 -
I have quite a few of these so I'm doing a series.
(2 of 3) Flexi Lexi
A backend developer was tired of building data for the templates. So he created a macro/filter for our in house template lexer. This filter allowed the web designers (didn't really call them frond end devs yet back then) could just at an SQL statement in the templates.
The macro had no safe argument parsing and the designers knew basic SQL but did not know about SQL Injection and used string concatination to insert all kinds of user and request data in the queries.
Two months after this novel feature was introduced we had SQL injections all over the place when some piece of input was missing but worse the whole product was riddled with SQLi vulnerabilities.2 -
Whelp. I started making a very simple website with a single-page design, which I intended to use for managing my own personal knowledge on a particular subject matter, with some basic categorization features and a simple rich text editor for entering data. Partly as an exercise in web development, and partly due to not being happy with existing options out there. All was going well...
...and then feature creep happened. Now I have implemented support for multiple users with different access levels; user profiles; encrypted login system (and encrypted cookies that contain no sensitive data lol) and session handling according to (perceived) best practices; secure password recovery; user-management interface for admins; public, private and group-based sections with multiple categories and posts in each category that can be sorted by sort order value or drag and drop; custom user-created groups where they can give other users access to their sections; notifications; context menus for everything; post & user flagging system, moderation queue and support system; post revisions with comparison between different revisions; support for mobile devices and touch/swipe gestures to open/close menus or navigate between posts; easily extendible css themes with two different dark themes and one ugly as heck light theme; lazy loading of images in posts that won't load until you actually open them; auto-saving of posts in case of browser crash or accidental navigation away from page; plus various other small stuff like syntax highlighting for code, internal post linking, favouriting of posts, free-text filter, no-javascript mode, invitation system, secure (yeah right) image uploading, post-locking...
On my TODO-list: Comment and/or upvote system, spoiler tag, GDPR compliance (if I ever launch it haha), data-limits, a simple user action log for admins/moderators, overall improved security measures, refactor various controllers, clean up the code...
It STILL uses a single-page design, and the amount of feature requests (and bugs) added to my Trello board increases exponentially with every passing week. No other living person has seen the website yet, and at the pace I'm going, humanity will have gone through at least one major extinction event before I consider it "done" enough to show anyone.
help4 -
"Using MD5" !? What year are we in again?
NOTICE OF DATA BREACH
Dear Yahoo User,
We are writing to inform you about a data security issue that may involve your Yahoo account information. We have taken steps to secure your account and are working closely with law enforcement.
...
What Information Was Involved?
The stolen user account information may have included names, email addresses, telephone numbers, dates of birth, hashed passwords (using MD5)2 -
Oh I have quite a few.
#1 a BASH script automating ~70% of all our team's work back in my sysadmin days. It was like a Swiss army knife. You could even do `ScriptName INC_number fix` to fix a handful of types of issues automagically! Or `ScriptName server_name healthcheck` to run HW and SW healthchecks. Or things like `ScriptName server_name hw fix` to run HW diags, discover faulty parts, schedule a maintenance timeframe, raise a change request to the appropriate DC and inform service owners by automatically chasing them for CHNG approvals. Not to mention you could `ScriptName -l "serv1 serv2 serv3 ..." doSomething` and similar shit. I am VERY proud of this util. Employee liked it as well and got me awarded. Bought a nice set of Swarowski earrings for my wife with that award :)
#2 a JAVA sort-of-lib - a ModelMapper - able to map two data structures with a single util method call. Defining datamodels like https://github.com/netikras/... (note the @ModelTransform anno) and mapping them to my DTOs like https://github.com/netikras/... .
#3 a @RestTemplate annptation processor / code generator. Basically this dummy class https://github.com/netikras/... will be a template for a REST endpoint. My anno processor will read that class at compile-time and build: a producer (a Controller with all the mappings, correct data types, etc.) and a consumer (a class with the same methods as the template, except when called these methods will actually make the required data transformations and make a REST call to the producer and return the API response object to the caller) as a .jar library. Sort of a custom swagger, just a lil different :)
I had #2 and #3 opensourced but accidentally pushed my nexus password to gitlab. Ever since my utils are a private repo :/3 -
Okay, so I have to write a script that will get user data from an AD, additional information from an XML, combine those two to get boss user relationship and output that mess into an excel sheet.
Oh, and both sources are ofc completely inconsistent. So I need full error handling on everything.
Aaaaaaand I have to write it in VB script... Using np++... Without plugins...
I hate my life!8 -
Fuck everything about Microsoft Dynamics. I'm supposed to use the REST API to make a web front-end. I notice all of the data comes back codified.
null == 0.
boolean true == 100000000
boolean false == 100000001
except sometimes when
boolean false == 100000000
boolean true == 100000001
or other times
string "Yes" == 100000000
string "No" == 100000001
string "Maybe" == 100000003
Hang on. Is the system representing a 1 bit value with base 10 numbers? Did the client set this up like this? Holy crap every number corresponds to a unique record in a table somewhere. That means it only returns numeric values instead of strings and I have to figure out what the number means in the context of the table.
A "key" is user typed? So every time someone starts to make a new record it saves a new "key" without a record? So I can pull a bunch of "0" records if I pull sequentially? So basically I need to see all of the data in Dynamics to have any context at all for what is returned from the Dynamics API? Fuuuuuuuuuu10 -
Possibly the start of a very bad adventure: I'm helping my brother-in-law set up a website for a business he'd beginning with his wife. I'll be needing to provide him a simple cms & shopping cart that he can manage. No payments as we want to just use PayPal so as to avoid having to actually manage user data & credit card information.
Wish me well....
Also advices appreciated cause otherwise, I'm gonna use a simple Drupal or WordPress site with like 1 theme and 0 plug ins.4 -
!rant
Skip away if you have zero interest in CurseMeSlowly's personal craps.
These days I am either slacking or working on things I like. Hence the lack of ranting.
So one of those "working-on-things-I-like" activities is my slow and snaily collab project. 😅 Today I am aiming to accomplish like 0.1% of it 😆 by finishing the github login feature. I have done the OAuth part. Just left with designing table structures and storing user data.
I plan to save login credentails into *users* table and other app related data into *profiles* table. That's what we usually do with users and profiles anyway. But I'm stil having a little bit of doubt regarding the proper way to store the game statistics like user's health, user's experience level etc.
If I am just showing the current statistics on the app, then those 2 tables are enough. But what if we want to see the progress of a user? hmm 🤔
I guess I will just leave it to decide later. 😬
---
If you don't know about it please check here https://cursemeslowly.github.io/dev... Any form of contribution is warmly welcome 🤗3 -
A couple of years ago, we decide to migrate our customer's data from one data center to another, this is the story of how it goes well.
The product was a Facebook canvas and mobile game with 200M users, that represent approximately 500Gibi of data to move stored in MySQL and Redis. The source was stored in Dallas, and the target was New York.
Because downtime is responsible for preventing users to spend their money on our "free" game, we decide to avoid it as much as possible.
In our MySQL main table (manually sharded 100 tables) , we had a modification TIMESTAMP column. We decide to use it to check if a user needs to be copied on the new database. The rest of the data consist of a savegame stored as gzipped JSON in a LONGBLOB column.
A program in Go has been developed to continuously track if a user's data needs to be copied again everytime progress has been made on its savegame. The process goes like this: First the JSON was unzipped to detect bot users with no progress that we simply drop, then data was exported in a custom binary file with fast compressed data to reduce the size of the file. Next, the exported file was copied using rsync to the new servers, and a second Go program do the import on the new MySQL instances.
The 1st loop takes 1 week to copy; the 2nd takes 1 day; a couple of hours for the 3rd, and so on. At the end, copying the latest versions of all the savegame takes roughly a couple of minutes.
On the Redis side, some data were cache that we knew can be dropped without impacting the user's experience. Others were big bunch of data and we simply SCAN each Redis instances and produces the same kind of custom binary files. The process was fast enough to launch it once during migration. It takes 15 minutes because we were able to parallelise across the 22 instances.
It takes 6 months of meticulous preparation. The D day, the process goes smoothly, but we shutdowns our service for one long hour because of a typo on a domain name.1 -
Data Disinformation: the Next Big Problem
Automatic code generation LLMs like ChatGPT are capable of producing SQL snippets. Regardless of quality, those are capable of retrieving data (from prepared datasets) based on user prompts.
That data may, however, be garbage. This will lead to garbage decisions by lowly literate stakeholders.
Like with network neutrality and pii/psi ownership, we must act now to avoid yet another calamity.
Imagine a scenario where a middle-manager level illiterate barks some prompts to the corporate AI and it writes and runs an SQL query in company databases.
The AI outputs some interactive charts that show that the average worker spends 92.4 minutes on lunch daily.
The middle manager gets furious and enacts an Orwellian policy of facial recognition punch clock in the office.
Two months and millions of dollars in contractors later, and the middle manager checks the same prompt again... and the average lunch time is now 107.2 minutes!
Finally the middle manager gets a literate person to check the data... and the piece of shit SQL behind the number is sourcing from the "off-site scheduled meetings" database.
Why? because the dataset that does have the data for lunch breaks is labeled "labour board compliance 3", and the LLM thought that the metadata for the wrong dataset better matched the user's prompt.
This, given the very real world scenario of mislabeled data and LLMs' inability to understand what they are saying or accessing, and the average manager's complete data illiteracy, we might have to wrangle some actions to prepare for this type of tomfoolery.
I don't think that access restriction will save our souls here, decision-flumberers usually have the authority to overrule RACI/ACL restrictions anyway.
Making "data analysis" an AI-GMO-Free zone is laughable, that is simply not how the tech market works. Auto tools are coming to make our jobs harder and less productive, tech people!
I thought about detecting new automation-enhanced data access and visualization, and enacting awareness policies. But it would be of poor help, after a shithead middle manager gets hooked on a surreal indicator value it is nigh impossible to yank them out of it.
Gotta get this snowball rolling, we must have some idea of future AI housetraining best practices if we are to avoid a complete social-media style meltdown of data-driven processes.
Someone cares to pitch in?13 -
A lot of people give Google, Facebook, Microsoft, etc. shit for "selling" user data although in my opinion acting as a matchmaker between advertisers and users does not really constitute selling data.
In contrast there seem to be a lot of companies that actually do sell user data that I never hear anyone here talking about. 5
5 -
I just found a vulnerability in my companies software.
Anyone who can edit a specific config file could implant some SQL there, which would later be executed by another (unknowing) user from within the software.
The software in question is B2B and has a server-client model, but with the client directly connecting to the database for most operations - but what you can do should be regulated by the software. With this cute little exploit I managed to drop a table from my test environment - or worse: I could manipulate data, so when you realize it it's too late to simply restore a DB backup because there might have been small changes for who knows how long. If someone was to use this maliciously the damages could be easily several million Euros for some of our customers (think about a few hundred thousand orders per day being deleted/changed).
It could also potentially be used for data exfiltration by changing protection flags, though if we're talking industry espionage they would probably find other ways and exploit the OS or DB directly, given that this attack requires specific knowledge of the software. Also we don't promise to safely store your crabby patty recipe (or other super secret secrets).
The good thing is that an attack would only possible for someone with both write access to that file and insider knowledge (though that can be gained by user of the software fairly easily with some knowledge of SQL).
Well, so much for logging off early on Friday.5 -
So yeah XML is still not solved in year 2018. Or so did I realize the last days.
I use jackson to serialize generic data to JSON.
Now I also want to provide serialization to XML. Easy right? Jackson also provides XML serialization facitlity similar to JAXB.
Works out of the box (more or less). Wait what? *rubbing eyes*
<User>
<pk>234235</pk>
<groups typeCode="usergroup">
<pk>6356679041773291286</pk>
</groups>
<groups typeCode="usergroup">
<pk>1095682275514732543</pk>
</groups>
</User>
Why is my groups property (java.util.Set) rendered as two separate elements? Who the fuck every though this is the way to go?
So OK *reading the docs* there is a way to create a collection wrapper. That must be it, I thought ...
<User typeCode="user">
<pk>2540591810712846915</pk>
<groups>
<groups typeCode="usergroup">
<pk>6356679041773291286</pk>
</groups>
<groups typeCode="usergroup">
<pk>1095682275514732543</pk>
</groups>
</groups>
</User>
What the fuck is this now? This is still not right!!!
I know XML offers a lot of flexibility on how to represent your data. But this is just wrong ...
The only logical way to display that data is:
<User typeCode="user">
<pk>2540591810712846915</pk>
<groups>
<groupsEntry typeCode="usergroup">
<pk>6356679041773291286</pk>
</groupsEntry>
<groupsEntry typeCode="usergroup">
<pk>1095682275514732543</pk>
</groupsEntry>
</groups>
</User>
It would be better if the individual entries would be just called "group" but I guess implementing such a logic would be pretty hard (finding a singular of an arbitrary word?).
So yeah theres a way for that * implementing a custom collection serializer* ... wait is that really the way to go? I mean common, am I the only one who just whants this fucking shit just work as expected, with the least amount of suprise?
Why do I have to customize that ...
So ok it renders fine now ... *writes test for it+
FUCK FUCK FUCK. why can't jackson not deserialize it properly anymore? The two groups are just not being picked up anymore ...
SO WHY, WHY WHY are you guys over at jackson, JAXB and the like not able to implement that in the right manner. AND NOT THERE IS ONLY ONE RIGHT WAY TO DO IT!
*looks at an apple PLIST file* *scratches head* OK, gues I'll stick to the jackson defaults, at least it's not as broken as the fucking apple XML:
<plist version="1.0">
<dict>
<key>PayloadOrganization</key>
<string>Example Inc.</string>
<key>PayloadDisplayName</key>
<string>Profile Service</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist
I really wonder who at apple has this briliant idea ...2 -
One of our customers wants our mobile app to log out the user after 15 minutes of inactivity because of SeCuRiTy…
Why? The phones protect the apps with their hardware encryption from any malicious access.
And we are not dealing with super sensitive data here like some banking app or so.
Why do some people want to have bad UX for no reason?12 -
When the user complains that our web tool is corrupting and losing data when converting results into excel while he is the one putting more that 40,000 characters into one text box which is way more than what Excel's cell can handle1
-
Have you ever had the moment when you were left speechless because a software system was so fucked up and you just sat there and didn't know how to grasp it? I've seen some pretty bad code, products and services but yesterday I got to the next level.
A little background: I live in Europe and we have GDPR so we are required by law to protect our customer data. We need quite a bit to fulfill our services and it is stored in our ERP system which is developed by another company.
My job is to develop services that interact with that system and they provided me with a REST service to achieve that. Since I know how sensitive that data is, I took extra good care of how I processed the data, stored secrets and so on.
Yesterday, when I was developing a new feature, my first WTF moment happened: I was able to see the passwords of every user - in CLEAR TEXT!!
I sat there and was just shocked: We trust you with our most valuable data and you can't even hash our fuckn passwords?
But that was not the end: After I grabbed a coffee and digested what I just saw, I continued to think: OK, I'm logged in with my user and I have pretty massive rights to the system. Since I now knew all the passwords of my colleagues, I could just try it with a different account and see if that works out too.
I found a nice user "test" (guess the password), logged on to the service and tried the same query again. With the same result. You can guess how mad I was - I immediately changed my password to a pretty hard.
And it didn't even end there because obviously user "test" also had full write access to the system and was probably very happy when I made him admin before deleting him on his own credentials.
It never happened to me - I just sat there and didn't know if I should laugh or cry, I even had a small existential crisis because why the fuck do I put any effort in it when the people who are supposed to put a lot of effort in it don't give a shit?
It took them half a day to fix the security issues but now I have 0 trust in the company and the people working for it.
So why - if it only takes you half a day to do the job you are supposed (and requires by law) to do - would you just not do it? Because I was already mildly annoyed of your 2+ months delay at the initial setup (and had to break my own promises to my boss)?
By sharing this story, I want to encourage everyone to have a little thought on the consequences that bad software can have on your company, your customers and your fellow devs who have to use your services.
I'm not a security guy but I guess every developer should have a basic understanding of security, especially in a GDPR area.2 -
Inspired by @shahriyer 's rant about floating point math:
I had a bug related to this in JavaScript recently. I have an infinite scrolling table that I load data into once the user has scrolled to the bottom. For this I use scrollHeight, scrollTop, and clientHeight. I subtract scrollTop from scrollHeight and check to see if the result is equal to clientHeight. If it is, the user has hit the bottom of the scrolling area and I can load new data. Simple, right?
Well, one day about a week and a half ago, it stopped working for one of our product managers. He'd scroll and nothing would happen. It was so strange. I noticed everything looked a bit small on his screen in Chrome, so I had him hit Ctrl+0 to reset his zoom level and try again.
It. Fucking. Worked.
So we log what I dubbed The Dumbest Bug Ever™ and put it in the next sprint.
Middle of this week, I started looking into the code that handled the scrolling check. I logged to the console every variable associated with it every time a scroll event was fired. Then I zoomed out and did it.
Turns out, when you zoom, you're no longer 100% guaranteed to be working with integers. scrollTop was now a float, but clientHeight was still an integer, so the comparison was always false and no loading of new data ever occurred. I tried round, floor, and ceil on the result of scrollHeight - scrollTop, but it was still inconsistent.
The solution I used was to round the difference of scrollHeight - scrollTop _and_ clientHeight to the lowest 10 before comparing them, to ensure an accurate comparison.
Inspired by this rant: https://devrant.com/rants/1356488/...2 -
Pulled into an 'emergency' meeting with a group of web designers deeply concerned a particular service wasn't going to meet all their requirements.
DevA: "For each page, Its going to be A LOT of work to retrieve all the data and store it's state. Every page load will require a round trip to the service."
DevB: "Yes, we aren't sure how the service should be changed to do what we need."
Mgr: "What is it not doing now? Doesn't the service already returns all the necessary data?"
DevA: "Well...um...its all the boolean fields. Some may be defaulted from the database or false because the user unchecked the box. We have to know which is which"
Me: "Why? Are you doing anything different in the UI? Checkbox will be true or false. What or who set that value is irrelevant"
DevC: "Well, it matters if the user didn't fill out all other other values."
Me: "How so?"
DevA: "Its matters because the values in the other fields. Its going to be A TON of work to figure out."
<mgr goes to the white board>
Mgr: "Lets map this out...what fields are you needing to trigger the state on?"
DevA: "Um...uh...the 'Approved' field...and um...'OK to Contact' field"
Mgr: "Just those two?"
DevA: "Yea..um...there are other fields, but whether or not to show the edit box depends on those two."
Me: "The service already returns data, you only have two fields to check? I don't see a need to change the service at all."
DevA: "Returning all that data, we are going have a serious scaling problem. We'll be hitting the service A LOT. All that javascript could cause performance problems too"
Me: "How much data are we talking about? Name, address, couple of booleans?"
DevA: "I have to serialize the data. All that logic is going to be reeeaaallly complicated. It might be better if the service returned only the data I need."
Me: "$64,000 question, how often is this feature going to be used on the web site? Maybe once? Few hundred a week?"
Mgr: "We have no idea. A lot of the data will be pre-populated and we're only sending out a few thousand invitations. More around the holidays...but honestly, not very many."
Me: "Changing that service only for this particular area of the web site isn't going to happen. Changing the UI is the only course of action."
DevA: "Oh frack I can't wait until this project is over."
DevA...how the funck do still have a job here? You wasted about half-hour of my time with your cry-baby crap. Where is my hammer...no...no..don't go there...ahhh...thanks devrant. Prison sentence diverted.2 -
Contex: Working on a c++ frankenstein code (mixture of legacy and new stuff whith things depending on the client using it)
User Story: Migration from oracle to SQLite for half of the DB data
Summoner: One client wants to keep using legacy for now, therefore we need an strategy chooser templated singleton...
Satan 666 = Singletons + Static methods + Different compilation units
Result: 3/4 of the files of the full backend being modified for the migration.
Conclusion: When will be loaded on production company will probably lose many clients due to unspected bugs everywhere.
Insert potato here2 -
User A: We need to do some check on our data. So you need to add in a new function for this, we can't use your system otherwise.
Me: Ok then.
Spends 2 days or so to get it working
Me: So this is the function we'll add. Can you confirm that its ok?
User A: Ohh...but now I'm not too sure about this. Let me confirm with my team lead on this.
User A: I just checked. Good news,we don't really need that function now. I think we can use it with the current one anyway haha. And I just confirmed this so no worries.
So I just wasted my time then. Great.3 -
example of my commenting on bugs to fix later
Before I found devrant:
//1-3-18
//when user goes to send mailing for first time
//we need to remove the message from admin
//which only displays on first time login, but
//may block the data we are looking for
// then return to parent
After DevRant:
//9-8-18
//when user goes to send mailing for first time
//there's a fucking stupid message that they
//have to read once which blocks the data we need
//so, goutte click that shit, then return to parent3 -
its been there since many years, but:
When did we turned the wrong way and made it acceptable that Windows can blantly say in my face that i cannot deactivate the transmission of data unless i have the "Business" Variant of their Software. Its called Windows 10 PROFESSIONAL. Why are there no international Laws against that? Where was the molotov throwing mob when this became the norm?
Additonally. that cute telemetry service consumes a considerable amount of cpu and disk power from time to time.
and no, Linux is not an alternative. It never was. There is proprietary software and driver sets used for lab equipment and machines that cannot run under linux, noone will ever have the time to tool something for it and the user base is too specific to hope for any community solution.
sidenote: even Level 0 STILL transmits data. I want mode -1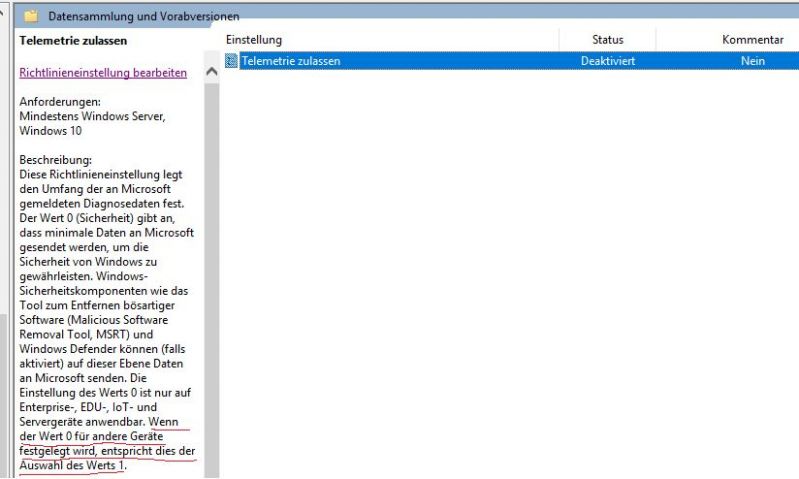 4
4 -
Reporting is not fun..
Scenario 1:
* A user says they need to export certain data from our system..
* Developer W makes report called "Foo detail report"
Scenario 2:
* A user says they need this report to also show some extra fields
* Developer X makes a new report called "Foo detail report (extra fields)"
Scenario 3:
* A user says they need this report to be run with a different search criteria
* Developer Y makes a new report called "Foo detail report (extra fields) by bar"
Scenario 4:
* A user says they need this report show data grouped in a different way
* Developer Z makes a new report called "Foo detail report (extra fields) by bar- new grouping"
The above scenarios happened over and over for several years in no particular order...
Current Day:
* Some users have certain reports they use and rely on but we don't know which ones
* Nobody really knows what all of the reports do or what is the difference between them without looking at the sql
* If we want to change data structures we have many reports to update
* I have a request from a user to add an extra column to one of the reports1 -
Just another day, building some hearty data structures in C.
I need to make a program that can multiplex user IO to different child processes from the command line.5 -
"Apple and Google will ban the use of location tracking in covid19 contact tracing apps on their stores to ensure user privacy and to prevent governments from using the syatem to compile data on citizens"
AHAHAHAHAHAHA5 -
I'm ashamed of it, but I want to share my tifu-story:
My colleague asked me if I could rename his windows user name because he married and changed his last name. I changed it in the Active Directory, but he got some problems when he wants to log on. On every startup his old name appears. Simpliest task. Let me google that.
Easy going, let me just change this registry entry. Reboot. Old behaviour. Okay, I changed some of the other entries. Reboot. Yeah, his new name appears. But wait a moment. Windows just nulled his entire user profile and deleted all the data. "oh, haha you have a backup, right?" - "no, I saved everything on the desktop, all my work is gone!"
But at the end, the boss was mad at HIM, because he doesn't used the file server or any backup system.
i am not a smart man5 -
While on topic of google collecting too much data, is there an chromium like android os, that doesnt spy on its user? Adroidium?13
-
This was originally a reply to a rant about the excessive complexity of webdev.
The complexity in webdev is mostly necessary to deal with Javascript and the browser APIs, coupled with the general difficulty of the task at hand, namely to let the user interact with amounts of data far beyond network capacity. The solution isn't to reject progress but to pick your libraries wisely and manage your complexity with tools like type safe languages, unit tests and good architecture.
When webdev was simple, it was normal to have the user redownload the whole page everytime you wanted to change something. It was also normal to have the server query the database everytime a new user requested the same page even though nothing could have changed. It was an inefficient sloppy mess that only passed because we had nothing better and because most webpages were built by amateurs.
Today webpages are built like actual programs, with executables downloaded from a static file server and variable data obtained through an API that's preferably stateless by design and has a clever stateful cache. Client side caches are programmable and invalidations can be delivered through any of three widely supported server-client message protocols. It's not to look smart, it's engineering. Although 5G gets a lot of media coverage, most mobile traffic still flows through slow and expensive connections to devices with tiny batteries, and the only reason our ever increasing traffic doesn't break everything is the insanely sophisticated infrastructure we designed to make things as efficient as humanly possible.10 -
Customer: the user summary report does not show all the transaction data I want to see
Me: there is a report called "transaction log report" that will show all the transactions
Customer: is that the user summary report? -
Today we start working on a app that learns biometric data from the user for extra security, so if some one else uses my account... The system would know and shuts the bad user out. Although we use an api for the biometric data collection, it's still epic! 😀😀😀
Only bad thing is that the deadline is next week3 -
Looking for a second opinion/validation.
*Me: “Perhaps this simple and concise way to ensure the user doesn’t lose their data before they leave the page that requires non-zero yet minimal input from the user. (Read: ya gotta push a save/submit button)”
*Everyone else: Let’s pretend to read the user’s mind and perform relatively complicated functions behind the scenes, of which the user will most likely be unaware, that will add an undetermined amount of complexity to the development because we think it’s “where things are going,” by saving the value of a certain HTML element as it loses focus.
Edit: this is an exclusively-internally used app.4 -
I just set up SSHFS so I can play my media library on my TV without moving all my data!
Basically my setup is something like this:
*Gaming PC (with a total of 10TiB - 6TiB being used for my /home) located in my office
*Home Media PC (with total of 150GB) located in my living room
Everything I have is on my 6TB HDD, and just my Videos folder is larger than the hard drive in the Home Media PC, so I decided to set up SSHFS. After about 15 minutes of reading man pages and trying different configurations, I ended up just needing "sshfs -o nonempty -o allow_other [user]@[location]:/home/$USER/Videos /home/server/Videos/"
This is so great guys; I love Linux so much!3 -
DevRant-Stats Site Update:
Made some changes.
After a long time with no updates, I decided to finish up my DevRant-Stats Project and do all of my Todos.
First, I added a way to request adding a user if he is not found. (Just search for your name, wait, then click "OK")
So even non-DevRant++ are now able to see their stats.
I also added @dfox and @trogus, though there is not a lot of interesting data yet...
Second, I added a "Details" section and changed the "Other" section a bit. For example I'm using an image for "Latest Rant" and other stuff.
Link: https://devrant-stats.github.io/
Just check it out!
Have fun!
~ Skayo11 -
Boss: so we've got to call an app to verify data in this project. But I've got no more info and I'm on holiday next week. Please contact GuyA next week.
Me: ok I guess?
*writes email to GuyA*
GuyB: GuyA is on holiday please hold the line
*1 week later*
GuyA: we need more time it's not ready yet
*2 weeks later?
Me: so?
GuyA: yeah it's ready here's the wsdl etc your client already has the password
*1 week later*
Me: yeah so I got the data but the api says my auth isn't working
GuyB: yeah your user isn't activated on the test system. I'm gonna forward that and come back at you
*1 week later*
GuyA: so we're going live in about 2 weeks hows testing going?
Me: well I'm still waiting for the response and activation
*suddenly it works*
Me: yeah so auth is working but i can't find any data. Is there any special test data?
GuyA: oh no there is NO test data on the test system. You need to wait for GuyB but he us not here today...
Me: are you fking kidding Me?????
... no response since then and it's been days.... -
A user calls me an hour after I'm supposed to have logged off.
"Hey, ahh, like, something is not good with, like, some thing"
Oh, snap! What happened?
"There is, like, this report, and it's, like, not right?"
Oh, the report is showing wrong data? Let me try to get a fresh version and...
"No, like,the data is right, but, like, there is many reports and , like, should be only one?"
Oh, you mean the report consolidation feature? It should only happen if the reports are fully compatible, and since it's automatic if the reports are not already grouped it means that they cannot be grouped. Probably due to this shopping season, we've seen a high uptick in demand.
"But, like, it should be, like, one! If not I will have to type in each report, like, by hand! I usually talk to this guy XYZ and he, like, does something that I, like, have no idea what it is. Can you call him up?"
(The dude the user mentioned logged off hours ago, and is in a different timezone. It's now about 11PM for him.)
It might not be possible. The system should add observations to each report it cannot consolidate. What do those say?
(the user takes two seconds to respond. I don't think they checked anything)
"It doesn't say anything. Can you cal XYZ, please?"
...
Shit, why do people wait until the last few hours of the last day of the month to do something that should have been done days ago and then demand that everybody everywhere just adjust to their late-ass schedule?
And then to demand I wake up a hardworking dev because someone is to lazy to use the system as it was custom designed for them? Because it had no problems but just wasn't making all things easy?
That's why users have to pay - they don't pay us to code, they pay us to put up with their bullshit.2 -
// Stupid JSON
// Tale of back-end ember api from hell
// Background: I'm an android dev attempting to integrate // with an emberjs / rails back-end
slack conversation:
me 3:51pm: @backend-dev: Is there something of in the documentation for the update call on model x? I formed the payload per the docs like so
{
"valueA": true,
"valueB": false
}
and the call returns success 200 but the data isn't being updated when fetching again.
----------------------------------------------------------------------------------------
backend-dev 4:00pm: the model doesn't look updated for the user are you sure you made the call?
----------------------------------------------------------------------------------------
me 4:01pm: Pretty sure here's my payload and a screen grab of the successful request in postman <screenshot attached>
----------------------------------------------------------------------------------------
backend-dev 4:05pm: well i just created a new user on the website and it worked perfectly your code must be wrong
----------------------------------------------------------------------------------------
me 4:07pm: i can test some more to see if i get any different responses
----------------------------------------------------------------------------------------
backend-dev 4:15pm: ahhhhhh... I think it's expecting the string "true", not true
----------------------------------------------------------------------------------------
me 4:16: but the fetch call returns the json value as a boolean true/false
----------------------------------------------------------------------------------------
backend-dev 4:18pm: thats a feature, the flexible type system allows us to handle all sorts of data transformations. android must be limited and wonky.
----------------------------------------------------------------------------------------
me 4:19pm: java is a statically typed language....
// crickets for ten minutes
me 4:30pm: i'll just write a transform on the model when i send an update call to perform toString() on the boolean values
----------------------------------------------------------------------------------------
backend-dev 4:35: great! told you it wasn't my documentation!
// face palm forever4 -
Nearly same time as the "don't be evil" got removed from google pages, an old internal video leaked about some futuristic concept, where the AI would try to gather as much data as possible from a user and if not possible, suggest devices with discount (e.g. a scale), that can return that data to the AI or if there's no fitting product, just print or make it based on the previously collected data (favorite color, ..) and suggest that to the user to buy, all since google duplex, anything mentioning google has been outscoring the previous idea 😶
src: https://youtu.be/iqUCX5rPQug 2
2 -
Legit questions!
How does facebook secures itself, we never heard news like facebook hacked, user data stolen, recently with ddos, twitter and other websites were affected but not Facebook?
Are they superhumans?9 -
Today a client opened a ticket saying that all the content for a customer returns 404. Turns out it's kinda important to end a prefix on a separator if you plan to recursively delete all data /user/<user_id> or you might end up deleting a bit of extra data1
-
User: If we use Oauth2, can we audit exactly where this data is going and who sends it there, and in addition cam we audit who grabs that data from the Authenticating app and make sure it doesn't violate our requirements?
Me: No
User: Why not?
Me: Because thats like asking us to audit whether or not a user accessed files and then uploaded them to their personal drive instead of corporate. We don't mandate that application owners take responsibility for their data outside of their application, why would we require that in this case???
User: Uhhhhh
FFS the lack of understanding of application accounts here boggles my mind. I understand that the security concerns are real but throwing out all permissible contexts based on a mandate that we dont even apply to extremely permissive accounts (i.e. users compared to apps) is folly1 -
PouchDB.
It promised full-blown CRDT functionality. So I decided to adopt it.
Disappointment number one: you have to use CouchDB, so your data model is under strict regulations now. Okay.
Disappointment number two: absolutely messed up hack required to restrict users from accessing other users’ data, otherwise you have to store all the user data in single collection. Not the most performant solution.
Disappointment number three: pagination is utter mess. Server-side timestamps are utter mess. ANY server-side logic is utter mess.
Just to set it to work, you need PouchDB itself, websocket adapter (otherwise only three simultaneous syncs), auth adapter (doesn’t work via sockets), which came out fucking large pile of bullshit at the frontend.
Disappointment number four, the final one: auth somehow works but it doesn’t set cookie. I don’t know how to get access.
GitHub user named Wohali, number one CouchDB specialist over there, doesn’t know that either.
It also doesn’t work at Incognito mode, doesn’t work at Firefox at all.
So, if you want to use PouchDB, bear that in mind:
1. CouchDB only
2. No server-side logic
3. Authorization is a mess
4. Error logs are mess too: “ERROR 83929629 broken pipe” means “out of disk space” in Erlang, the CouchDB language.
5. No hosting solutions. No backup solutions, no infrastructure around that at all. You are tied to bare metal VPS and Ansible.
6. Huge pile of bullshit at frontend. Doesn’t work at Incognito mode, doesn’t work at Firefox.8 -
I begin with the optimism and the joy that I am creating something new that will improve people's lives.
I listen to the user and analyze the current process in depth.
I try to suggest additional value to the system for the users consideration. Sometimes they do not realize we can improve 10x rather than 2x.
I learn what the users goals are and what they want out of the system. We think about reports and downstream value. Sort of working from the end to the beginning (data ingests and upstream processes that will feed the system).
After the user signs off on the requirements and deliverables and I have a realistic project plan I begin to code.
It works and has worked for me every time for a long long time. -
Security is a joke. And people don't seem to get it. Especially Data mungers.
I've spent about half an hour trying to work out how to securely connect to power BI using PowerShell in a renewable manner for unattended access later on.
Every single example I've found seems to involve you storing $user and $password variables inside your script. If I'm lucky, they're going to pass them through ConvertTo-SecureString. And nobody talks about securely storing AD auth tokens, or using the Windows Credential Manager.
I know it's possible, but it's going to take me ages to work out how from all sorts of disparate sources...16 -
Haven't ranted for awhile but here it goes...
In a meeting with a front end user yesterday. They don't like the entry screens on our Oracle ERP system. They want us to provide them with a tool so they can create new entry screens to replace those they dont like. They want full autonomy over that tool and no interference from IT. Oh, and they want unfettered database access to the production data, including full ability to execute DML. I so wanted to say 'Are you high?'.1 -
I am working on a multi user, high security, private data analytics Web app.
I keep a Ganondorf ammibo on my desk to remind me that; one wrong link could ruin everything. -
A few minutes ago, I was going crazy over a bug caused due to data mutation in Rails.
Basically, user1 was creating a post record and it's stored in the database normally however, on page reload for a second user, user2, the post (that user1 created) was update to belong to user2. This is because, on page reloads, I was using `<<` method call to append user2 and user1 posts together! Apparently, `<<` not only mutates the array, it also performs a database update.
Kill me please!!
Also, data immutability seems a more reasonable feature in languages now.1 -
Part 1: https://devrant.com/rants/4298172/...
So we get this guy in a meeting and he is now saying "we can't have application accounts because that violates our standard of knowing who accessed what data - the application account anonamizes the user behind the app account data transaction and authorization"
And so i remind him that since it's an application account, no one is going to see the data in transit (for reference this account is for CI/CD), so the identity that accessed that data really is only the app account and no one else.
This man has the audacity to come back with "oh well then thats fine, i cant think of a bunch of other app account ideas where the data is then shown to non-approved individuals"
We have controls in place to make sure this doesnt happen, and his grand example that he illustrates is "Well what if someone created an app account to pull github repo data and then display that in a web interface to unauthorized users"
...
M******* why wouldnt you JUST USE GITHUB??? WHO WOULD BUILD A SEPARATE APPLICATION FOR THAT???
I swear I have sunk more time into this than it would have costed me to mop up from a whole data breach. I know there are situations where you could potentially expose data to the wrong users, but that's the same issue with User Accounts (see my first rant with the GDrive example). In addition, the proposed alternative is "just dont use CI/CD"!!!
I'm getting pretty pissed off at this whole "My compliance is worth more than real security" bullshit. -
According to the report of Reuters : Brazil's Ministry of Justice said on Monday it has fined U.S. tech giant Facebook 6.6 million reais ($1.6 million) for improperly sharing user data. The ministry's department of consumer protection said it had found that data from 443,000 Facebook users was made improperly available to developers of an App called 'thisisyourdigitallife.' The data was being shared for "questionable" purposes, the ministry said in a statement.7
-
Salespeople telling clients "Your site doesn't need a privacy policy/cookie policy since you don't actually sell anything on your site."
Wrong wrong wrong WRONGITY WRONG WROOONNGGGG!!!!!
Client to PM to me: "Well Jim said we don't need those on this site."
Me: "Well Jim is misinformed, since we use Google analytics, Facebook Pixel, and contact forms, you need to have both a privacy and cookie policy."
PM to client: "We'll find you a template you can use to get started, it'll cover most of what you need."
Me to PM: "we will do no such thing, we can send them a few links explaining why they need these, but they should consult a legal professional and cover their asses for their own business practices. I can provide any technical details they may need like what data the cookies collect if necessary."
PM to me: "well I'll just find something for them then."
*In my head* please just go crawl in a hole and die.4 -
the api endpoint for retrieving user-data in an alexa skill might as well be api.eu.amazonalexa.com WITH .EU
this is not as good documented as it should be and did cost me several hours until i saw it by accident analyzing the request-data another time...
you´re welcome. -
Stakeholder: Can you investigate the problem with this user profile? We made updates to system A, but user is saying it’s the wrong info on the website.
Me: Looks fine to me. Looks like your updates just needed time to trickle down. Though, you will need to clean up this user’s data because it can cause X problems. There’s not much I can do since the site just displays info from system A.
SH: Can you delete the user’s website account and we can ask user to create a new one?
Me: …Ok, let’s try this again. It’s not necessary to delete the account and make the user create a new one. It’s not going to resolve the X problems that I mentioned. The website really needs clean data from system A. -
Forgot to do server side verification.
As the service (an injectable game) was expanding and the old system relied on server side calculation without anything returned from the user, the expansion was done a little too fast.
The result could have been anyone passing wrong data and receiving the grand price like a holiday worth $10k. Quick fix ... -
So, we (I'm the backend guy and work with a UI dev) are building this product portfolio management tool for our client and they have a set of 250 users. The team has two point of contacts for the 250 users who maintain the master data, help users with data quality, tool guidance, reporting and other stuff. So one day one of these two support users come to me and say : Hey I'm not able to add new transactions coz a customer is missing.
We have the provision to create / maintain customers.
I check the production DB, application code, try creating the customer and then the transaction, everything works perfectly fine.
I ask the user for a screen sharing session, the user starts reproducing the error like this :
We have a 3 system landscape - Dev / Test and Prod
U : Logs into the test system url, creates the customer.
U : Points out the toast saying customer creation is successful.
U : opens a new tab, opens the production system, tries creating the transaction, searches for the customer and says " see !! cant find the customer here ! the master data management apps never work !! "
FML?. -
So a team at on-site sent a OOM(Out of Memory) issue in our morning.
Everyone analysed the issue as being code issue since we were bringing too much data into the runtime process. The analysis was done on the heap dumps. The number of records reported by user were 1k. At the end of the day it turns the number of records were actually 100k+.
Why do people jump.to conclusions without thinking about the obvious. :-(1 -
in my previous company , we used to create 4 custom ui states for just 1 screen in android app, and we would have task to create 3-4 new feature screens in 1 sprint (of 14 days) the states would be :
empty state : a state where data is not available. usually consisted of message, a graphic and some action button
data state : the usual state where data is filled on various elements
loading : a shimmer ui showing loading. it was supposed to be pixel perfect to that of the data state. it was basically a different xml, but with grey colored views instead of colorful. the tricky part would usually he to create the dynamic views
error/no connection state : as most of the screens couldbget api error or no internet error, this would be the screen for asking user to retry connection
all of these screens combined with their ui in xmls + kotlin code with barely any stuff being reusable , made the life incredibly difficult. however a lot of our customers would appreciate the interactivity of our app
doing these stuff again nd again , i had become trained to do all those 3-4 (x4) screens and the whole ui stuff in first 4 days of the sprint. but now i am in a company where i am getting passed on to managers after managers and getting tasks to change documentation in 1 week, i find those coding stuff incredibly tough.
gotta get back to shape -
Me: You decided some records in system A should be obsolete, but the records are tied to active user accounts on the website. Now, I have users emailing and asking why their profile’s last name field says “shell record - do not use.”
Stakeholder: Oh…can’t you stop those profiles from loading? Or redirect the users to the right record in system A? In system A, we set up a relationship between the shell record and the active one.
Me: 😵 Um, no and no. If I stop a user’s profile from on the website, that’s just going to cause more confusion. And the only way to identify those shell record is to look at the last name field, a text field, for that shell record wording. Also, the website uses an API to query data from system A by user id. Whatever record relationship you established isn’t reflected in the vendor’s API. The website can’t get the right record from system A if it doesn’t have the right user id.7 -
Nitrux OS
I feel that this piece of wonder isn't getting the recognition it deserves.
One of the most beautiful UIs out there, revolutionary tech like znx(booting from the main iso ALWAYS and keeping user data across reboots, in a nutshell) and it has weird ass virtualization stuff that allowed them to run windows with very little virtualization overhead(tech details yet to announce).
Imma stop here before getting labelled another fanboy, just check it out and see for yourself
Thanks for reading, i use arch btw8 -
So I am broke and can't buy a vds, I installed Termux on my android phone instead. Now I have a portable server that is capable to recieve calls and transmit sms for logs.
BUT, then I had to go to customer support due to case makes the phone get short circuited şn random times. Obviously they deleted all info and Samsung Cloud doesn't backup other users' data. (Termux emulates a terminal running on another user, which is not root by default)
Can anyone teach this teenager how to use tar properly? :D3 -
Sending email to client (the following is a short version of it)
"
Dear Data Evaluation Team,
Here is a link with the password to the data export for the questionaire.
You will find in there 4 sections:
1. Utilization Report
2. Question List
3. User Responses to questionnaire
4. Summary of responses
"
Email from client
"
Thank you data team.
I see that the user responses have some ids for the questions. Can you please give me the full question text, where is it?
"
My response
"Section 2, Question List"
Like really? Did you just not f*ing read the email and just jumped into the data export blindly. I wrote some fucking docs for a reason. -
So we have this administration page in the clients app that has tables of data.
The user can click on a row to edit or click "Add' to create a new one, doing so pops up a modal with a form full of inputs and a save button at the bottom.
The other day our client told me he was concerned that users would not understand how to edit data and that I should add some text below the first input field of each modal that says "Type in a new value and click 'SAVE' to change the [field name]"
As I implimented this crap, I took a few minutes to come up with a nice way of saying that his idea made no sense, added unnecessary clutter to the UI, and proposed some alternatives.
He essentially said, "Thanks for your much better ideas, for now let's just stick with what we've got and we can revisit this later."
Everytime I open that UI, I physically feel pain and get a little sick.5 -
User :
i've just done testing the system, based from one of the testing data i inserted, the procedure still isn't correct
Me :
- Desperately looking for whats wrong in the procedure -
User :
Oh, nevermind, the testing data itself is not correct
Also ME :
ASDJAHSGDUqa QY(^E*Q^w^EQV%&ABDYDTA^R6b ^#E%&W QE& !!!!!!!!!!!!! -
Hey there people, I have a few questions regarding neo4j. Your experience could also be very useful to me here @dfox.
1. Is neo4j good for storing user data, like password hashes, etc.. In addition to the regular relationships with other components of the ecosystem
2. Is neo4j good enough to accommodate a really large number of users..
3. Does DevRant use a dual database, like user info in Mongo and relationships like comments and ++ on neo4j or is it like everything on neo4j
For q.3, if you're not @dfox then just provide an idea of how you would handle the situation.7 -
Fuck Google analytics .. seriously .. fuck it .. I understand it's a free tool that doesn't mean you mask your incompetency behind that banner.
Im pretty sure minecraft mods have better documentation than this POS.
I really like the user demographics data it gives , but with the asterisk on literally every other metric it gets harder to believe the ones that are functional.
I cant express exactly how many times I end up with hordes of articles that point out small caveats with this shit.
FUCK IT 2
2 -
Not a rant, just the completion of a very demanding and interesting task for this week.
Wrote a whole data scheme for this enterprise app my company is developing. Very proud of it, since it has a very restricted size, multiple layers of encryption and data verification, several user types with different requirements, and it all has to be rock solid in an offline environment.
The punchile is...I enjoyed writing the documentation for the whole package more than I should, I guess...spent the whole day being very thorough and documenting every member, function, constructor and exception.
Feelin fabulous.
-
I've just spent the last hour or so banging my head against a brick wall trying to figure out why I'm unable to retrieve some data via AJAX even though I know data is being returned as I can see it in my error log.
Turns out the permission system I wrote a few days ago actually works and because I didn't specify a permission it automatically denied my user from retrieving the data. One thing I forgot to add was an error message to tell me when I don't have sufficient permission to do something. Adding a message could have just saved me a lot of time :/1 -
What the hell is WRONG with Windows 10. Why does it need so much storage space? I get to only use 219+38.6+13.8 GiB and Windows gets to use 564 GiB of data to piggyback on data and storage space to push nonsense updates to user who do not want them. Use your own fucking servers, MS. I wish this fucking OS burns in hell.
 10
10 -
Working from home. Most of the team is off. Client has an official half day. Most of them are off. Instead of being online at 7 am, gonna get online around 850 just before daily standup. Laying in bed, enjoying the cool sheets and the fact that there's no rush. ~0730 team lead calls, user shit himself and I need to fix it. Server issue? Nope. Data issue? Nope. Portal bug? Nope.
Client input conflicting data and can't progress with tool.2 -
I once wrote an http interceptor for which was supposed to check the internal cache for user data and only do some work with it if they were (we manually controlled what and who was in cache). There were two methods on the service cGetUser and dGetUser I of course called d which it turned out loaded the user profile from the database which would be fine if it weren't done in an interceptor .. on a web service... With a little over 25000 requests per minute.. on each node..
Tldr. I accidentally wrote a database ddos tool into our app...2 -
I developed a simple feedback form, that captures user feedback and forwards it to a customer care email.
Today, I received a call from someone who was sub-contracted to create a system that would ingest these feedback emails and process the data to have some desired result.
So dude wants me to change the way the email is formatted. Because there are "line feeds" in the email. Essential making it computer readable as opposed to human readable. I don't have a problem doing that but I'm wondering if he ever heard of regular expressions.3 -
!dev?
Colleges now require proof of vaccination but admins are worried about the spread of fake vaccine cards
https://apnews.com/article/...
My mindblowing solution: require students to submit a covid antibody test result instead.
You can't spoof the lab test result number and it can be easily verified by calling the lab...
Can even create a site for that...
isTestValid.com
Worried about privacy... Have labs upload a hash of the data...
And user submit their hash...
Clearly nobody asked a dev for they're input... again2 -
Microservices
Lets take an example: Products service & orders service.
When I want to save an order for a user, data saved as
1. UserId, ProductId, Quantity, Date
Or
2. UserId, Name, Email, ProductId, ProductName, Quantity, Date
I'm a bit confused here because if I'm going to fetch that purchase, in example 1, it will return IDs requiring another trip to server to get user & product info
In example two it takes only one trip BUT if any changes is made to either user info or product info it means I'm returning wrong info to the user.
What do we do in this scenario? Excuse my questions first time applying Microservices and been using monolith all my life6 -
Competition is necessary for a healthy marketplace.
Whenever there is a monopoly or a near-monopoly, its owners can treat their users poorly through restrictions (Android OS becoming like iOS), planned obsolescence, unfounded content takedowns (YouTube), account lock-outs until the user provides more personal data (Google demanding phone numbers), subscription services instead of ownership (Adobe, BMW heated seats), and users would have nowhere else to go.1 -
Random opinion question:
I'm working on a thing where the user provides a big CSV and we process it and put it in the database, or update existing records.
This data impacts other things, but the data isn't front and center as a group of n the application for them to notice / see again (well they can query for it).
I'm thinking of taking the CSV and then presenting them with a table showing how we processed that data giving them a chance to review it before they commit it to the database...
I like this idea for two reasons:
1. If something goes sideways there's a chance someone will see it and I'm not sure I can do enough validation on a big ass CSV from god knows where to be sure we're going to process it right... (I'm going to do some validation but just can't cover it all)
2. It takes some of the mystery out of what happened / is happening for the user for.
Anyone try this in the past? Seems reasonable, but lots of things do before they go sideways.7 -
Day 2 of being a Linux (Mint Cinnamon) user. What I like the most is that there's a solution or customisation available for every problem and it's usually straightforward. And let's not forget that you don't have to fight the OS for folder permissions when you're in admin mode.
Migrated my data over from my old drive, installed Steam, got some work done. I like Cinnamon a lot. Need more RAM but that has been years in the making for me.
Just need to get Wine running and find some more cool open source games and tools and I'll be good to go. -
I've been given a huge stack of paper, some users stories and loose specs. Was tasked with engineering the specific requirements, then the models and finally the database. Then I need to build an API on top of that.
Stuff I'll use is Go and Postgresql. Small issue is, I've never done DBs, so I've no idea what to do or where to start.
Does anyone have any resources to help kick-start myself in this field? I've been reading on SQL, but that doesn't really tell me anything about data structures and how to transform those user stories into product requirements.6 -
Just found the most embarrassing security hole. Basically a skelleton key to millions of user data. Names, email addresses, zip codes, orders. If the email indicates a birthdate, even more shit if you chain another vector. Basically an order id / hash pair that should allow users to enter data AND SHOULD ONLY AUTHORIZE THEM TO THE SITE FOR ENTRING DATA. Well, what happend was that a non mathing hash/id pair will not provide an aith token bit it will create a session linked to that order.
Long story short, call url 1 enter the foreign ID, get an error, access order overview site, profit. Obviously a big fucking problem and I still had to run directly to our CEO to get it prioritized because product management thought a style update would be more important.
Oh, and of course the IDs are counted upwards. Making them random would be too unfair towards the poor black hats out there.1 -
I need advice.
So let's say, hypothetically, I found a site with a user data leak.
Would it be illegal if I only told them where the leak was for a bounty?
I am NOT going to distribute the user data. I just don't want to work for free, you know?
Again: NOT DISTRIBUTING USERDATA. No blackmail. Just information that their QA should have caught.25 -
Fucking hell, our .net site uses a modal pop-up after the user submits data so they can explain what the did and why. Bootstrap styles it with an x in the top right, but the x doesn't do anything. I can't find where bootstrap adds it, I can't find any way to access it, it just annoys users because if they don't need to explain, they click it, and it doesn't work. Only the cancel button closes it. Where the fuck does this thing come from?3
-
Made a website and 4K final for university in 10 days with Angular, FastAPI, ArangoDB and docker. No prior experience with Typescript whatsoever. Sessions, User Management, data manipulation and a d3-force graph which doesn’t dance around like a fucking clown. I feel like a fucking god right now5
-
Imagine an online, public service, that allows you to communicate with others (for example a simple chat, game, whatever ).
The users connect to each others via p2p. Based on this, you can easily get the ip address of any user directly connected to you. P2p is used to reduce server load, but information is still verified (for example using RACS), so let's assume the data is always safe.
(please remember, this is just a imagined Szenario)
Now the question: AFAIK, the IP address is a sensitive information. Would p2p in this scenario still be 'legal' in the EU given the latest changes in the laws?7 -
In reply to:
https://devrant.com/rants/3957914/...
Okay, we must first establish common ground here. What do we understand about "showing"? I understand you probably mean displaying/rendering, more abstractly: "obtaining". Good, now we move on.
What's the point of a front-end? Well, in the 90's that used to be an easy answer: to share information (not even in a user-friendly way, per se). Web 2.0 comes, interaction with the website. Uh-oh, suddenly we have to start minding the user. Web 3.0 comes, ouch, now the front-end is a mini-backend. Even tougher, more leaks etc. The ARPAnet was a solution, a front-end that they had built in order to facilitate research document-sharing between universities. Later, it became the inter(national) net(work).
First there was SGML to structure the data (it's a way of making it 'pretty' in a lexicographical way) and turn it into information (which is what information is: data with added semantics) and later there was HTML to structure it even further, yet we all know that its function was not prettification, but rather structure. Later came CSS, to make it pretty. With its growing popularity, the web started to be used as a publishing device.
source:
https://w3.org/Style/CSS20/...
If we are to solely display JSON data in a pretty way, we may be limiting ourselves to the scenario of rendering pretty web pages using aesthetic languages such as CSS. We must also understand that if we are only focusing on making a website pretty with little to moderate functionality, we aren't really winning. A good website has to be a winner in all aspects, which is why frameworks came into existence, but.. lmao, let's leave that to another discussion.
Now let me recall back my college days.. front-end.. front-end.. heck, even a headset can be a front-end to a pick-order backend. We must think back to the essence, to the abstract. All other things are just implementations of it (yes, the horrendous thousands of Javascript libraries, lol).
So, my college notes say:
"Presentation layer: this is the UI.
In this layer you ask the middle tier for information, which gets that information from a database, which then goes back to middle tier, back to presentation. In the case of the headset, the operators can confirm an order is ready. This is essentially the presentation tier again: you're getting information from the middle tier and 'presenting it' as it were.
The presentation layer is in essence the question: how do I bring my application data to my end users in a platform-and solution-independent way?"
What's JSON? A way to transport data between the middle tier and the presentation tier. Is that what frontend development is? Displaying it in a pretty way? I don't think it is, because 'pretty' is an extra feature of obtaining and displaying data. Do we always have to display data in a pretty way? Not necessarily. We could write a front-end script (in NodeJS perhaps) that periodically fetches certain information from a middle-tier is serves a more functional role rather than a rendering one.
The prettification of data was a historical consequence of the popularity of the web (which is a front-end) (see second paragraph with link). Since the essence of a front-end is to obtain information from the back-end (with stress on obtaining), its presentation is not necessarily a defining characteristic of it, but rather an optional and solution-dependent aspect, a facet.4 -
Tech people should have a codeword. So that I don't have to explain to every data provider showing off their own crappy limited analytics tool that "I do know what SQL means and I just need the ODBC user/pass, thanks".
I wish I could just say "hey, &0x00A0 = 1337;" out loud and he would be like "oh, thanks! I needed the break. Here is the ODBC crap, I'm gonna grab some coffee."5 -
Working for a large client converting paper forms to the web. Stated goals, simplify data entry for clients, improve data quality, reduce resourcing in backend human processing.
We met to review prototype and discuss workflow questions. Crazy deadlines, with the usual changing scope creep.
We start to point out the need for data validation, to shorten # of questions based on answers.
Business says no. All forms should be submittable regardless of what user enters, don’t put validations in because all that warning messaging confuses them and takes up more time.
Web form should behave like the paper copy....
Welcome to 1975!!! This is why 2018 won’t be like 2018...1 -
Today I will talk about Android OS being stupid.
Android lets u as a user move installed apps to external storage = microSD card.
However what is stupid about it is that only a small part of the app will be moved. For example, if you have an app taking 400 MB of storage, then "moving" it will move only about 100 MB of data to microSD card, while the remaining 300 MB of data will remain on the internal storage...
In Android 11 this is still not improved. Imagine having 11 versions of OS over 11 years and never making a crucial feature work properly. Meanwhile app sizes grow ever larger
Disappointing.5 -
I've recently moved from google to duckduckgo for my searches, Having in mind the growing concern of user privacy, what do you guys suggest for search engines, browsers, os, recommended addons, apps, vpns etc?13
-
About skyRant. I really like what you're doing for establishing it as a third party app with the verify login thing. Technically there is no way for me to verify if the app I'm using is using that source code unless I built it myself, but still nice.
I do feel a bit odd about having additional data such as reactions on the skyRant platform. It's cool and all, but it degrades the experience for anyone not using skyRant. If I like someone's post with a ❤️ there is no guarantee that user will see it. Idk just some random thoughts, but very cool app! :) 7
7 -
*-- There's something kind of child like and adorable about working for a client who spends THOUSANDS of dollars on their data infrastructure, yet finds it ever so difficult to provide ONE user to help reconcile and test the new data warehouse.
-
I don't know how much of this can be considered data loss but one one of my uni classmates frustrated by some hellish tasks (cleaning some old code files probably) decided that everything in that particular directory won't be of any further need, so she procede to rm -rf it.. only to discover that the terminal opened in that dir was another one and her current one (the one she bashed that unforgiving rm) was in fact a standard freshly opened term where any term would open.. in the user's (only user) home dir... such a face she had when all her codes, homeworks, projects and everything went to oblivion 😂😂 jokes aside it was a good thing that the semester was almost finished, all hws submited and no important data was there as she dual booted with ubuntu and some windows, but funny thing how such a honest mistake can ruin not only your day, but maybe your entire semester1
-
In high school for an assessment we all had to make a simple game and we to plan it first and then program it. In the planning stage we had to list variables and functions used and whatnot I'm my planning sheet I was given I had "variables modified by user" which basically meant data inputted buy the user stored in a variable with only one player name variable listed in it and everything else in my game was being computed another runtime and my CS teacher told me I didn't have enough user inputted variables and I explained that it didn't need any more she said "so you're telling me the user enters their name and the the game just plays itself?!!! " :|3
-
The importance of not using static salt / IVs.
I've been working on a project that encrypts files using a user-provided password as key. This is done on the local machine which presents some challenges which aren't present on a hosted environment. I can't generate random salt / IVs and store them securely in my database. There's no secure way to store them - they would always end up on the client machine in plain text.
A naive approach would be to use static data as salt and IV. This is horrendously harmful to your security for the reason of rainbow tables.
If your encryption system is deterministic in the sense that encrypting / hashing the same string results in the same output each time, you can just compile a massive data set of input -> output and search it in no time flat, making it trivial to reverse engineer whatever password the user input so long as it's in the table.
For this reason, the IVs and salt are paramount. Because even if you generate and store the IVs and salt on the user's computer in plaintext, it doesn't reveal your key, but *does* make sure that your hashing / encryption isn't able to be looked up in a table1 -
Fuck Apple with two pineapples in the ass. 99€ per fucking year to tell me how the fuck should the access to my app be. I damn require users to sign up. I only need email and country. Not a single other piece of data. My app is not a goddamn catalogue or boutique. No free content, free app but each user needs to Auth themselves. You fucking telling me y pay 99€ so you decide how the access to my app should be?
Cunt Apple should rot in 10 day old humid shit and let devs be owners of their apps and hard work. Clowns.7 -
I was building a super simple Laravel app for a client (forms APIs stuff)
For the frontend I used jQuery cuz why overkill it with react.
Now the sad part:
The app makes ajax calls to fetch the data from the database and update the view according. The code is very well written and the call is so quick that in a blink of an eye the data is processed from the controller and sent to the view -_-
Because the user doesn't gets to see what the fuck just happened when they clicked the action button, I had to add a setTimeout function before the Ajax call to slow down the process by 2000ms and added a freakin spinner.
I feel very sad when I can't show how awesome apps I can build but,
I killed my ego for the UX.
This was my sacrifice.
Anyone faced similar shits?3 -
Pulled my hair out over one today (and a week ago when I first saw the issue)
Setting up development environment. Created test user and test database and used mysqldump to copy data over.
MySQL was executing a function as the wrong user. Checked my config files, checked my config reader, checked my database connection, checked checked checked. Checked everything twice, I felt like Santa.
Changed the password in the config file to make sure it was logging in right. It threw an error still but not one I had expected so I figured the login still worked (My bias was that I thought the config file was not working or the mysql library was caching authentication. Both were wrong but this blinded my debugging. Foolish, I have forgotten my training)
Logged into the database directly via client. *didn't bother executing the function because I was only testing auth*
Think
Think
Think
Search entire project for database username. It's gotta be hard coded by accident SOMEWHERE.
It's not.
Why
Why
Why
Wait.
-- Flashback to how the test db was created -- What's actually in this damn script?
DEFINER `production_user` CREATE PROCEDURE `old_db`.`procedure_name`
Two issues: definer is old user (this is the error I was seeing) and its creating the procedure on the old db (this would be the next error I would have found if I kept going)
Fuck mysqldump. Install mysqldbcopy. Works
Put hair back in head. -
Alright got an idea I have for my game engine that I'd love some input on...
So the engine has emphasis on user made content and openness to that content (EG. open source dev tools and no licencing of art) but I also want to try and build a basic ecosystem with the engine and one way I'm doing it is with cross game mods (Take a mod from one game and drop it in another and it just works... Famous last words) but something I want to try is a companion app for the engine itself...
So it'll have a custom written save system baked in engine to make progress saving and the like simpler for the end user, thinking about building an app for smart watches and phones that would connect to the engine and actually back up and sync local saves to the app and vice versa as long as they have a connection (Hotspot your phone, bluetooth or wifi) but allow you to manage some data within the app by building a basic API to let devs show the user information about the save and the game by adding description, thumbnails to distinguish games and the like...
Just want opinions if it may be a good idea to invest some time into and if anyone has idea's that could make it better.6 -
I'd like to create an imageboard app with React-Native and got a few questions.
Every user has to like or dislike the shown content to advance to the next image/video (tinder style). I want to use that data to feed a machine learning algorithm and generate an unique selection of displayed media for each user with that.
Even though I never used it yet before (I'm still learning to code) I want to use python and a python machine learning library for that.
Can you give me any advice for the python part? For example which library to use, where to start, etc. .
Do you think that might be an interesting idea to realize? :)2 -
During my internship, I fixed a bug in android app related to user data updation..
BUT I didn't knew it's root cause and I have no idea how I fixed it.
Also, it was satisfying.1 -
Who the fick asks for BPMN diagrams, Disaster Recovery diagrams and Business Continuity Plan for a SaaS product that is deployed in cloud (Azure) ??
This is a simple app/dashboard that just showcases some data in fancy charts. It shows the data YOU feed. Why do you need BPMN diagram? What am I supposed to put? "Client loads data" and "user sees data"?
I already linked Azure's page on DR. Do yiu want me to copy-paste the contents from that link?
Clients are too much PITA!!!1 -
I once had to write a feature, which should allow the user to login and edit an appointment, which was automatically set. All the data we got, came from an incredibly unreliable API. And with incredible unreliable I mean like heisenbug-level unreliable.
The API spoke perfectly unreadable xml and was a horror to work with.
After a few weeks of me being messed with by this shit piece of an API, I finally got something which did kind of work sometimes.
Proper error handling has been added later and just before I was done, fixing all the flaws of their data management and nonsense status codes (not http status codes) which rarely correlated in at least some way with their data, our client said "scrap this, we don't want it anymore"
Many hours and effort gone, this thing worked almost perfectly. -
I'm looking into GraphQL and so far so good, but I am finding it hard to implement business rules, for example:
1. Receive request with auth token
2. Know who the user is by extractin userId from token
3. fetch data related to that user only.
I was only able to make it allow or deny if there is a token or not lol5 -
Some information in advance:
I developed a Word AddIn for automatic document creation. This AddIn pulls data from various systems, transforms them, if necessary and fills them into templates.
The AddIn gets rollout by another department. And by now there is version 1.3.3 out.
Now the story:
Since several months I have heard of users which have some reoccuring problems with the AddIn and I couldn't understand why. The first level support always helped them with some workarounds.
Now, I helped one user by myself and what did I see?
The user had version 1.0.5 installed!!!! WTF!? The version info is very prominent for the first level support and they should know, that this is not the correct version!
I think I have to implement a version check now, if the rollout is so great working...maybe I should have done this since the beginning... -
According to a report from VentureBeat: Verizon Media has launched a "privacy-focused" search engine called OneSearch and promises that there will be no cookie tracking, no ad personalization, no profiling, no data-storing and no data-sharing with advertisers.
By default, Advanced Privacy Mode is activated. You can manually toggle this mode to the "off" but you won't have access to privacy features such as search-term encryption. In the OneSearch privacy policy, Verizon says it it will store a user's IP address, search query and user agent on different servers so that it can not draw correlations between a user's specific location and the query that they have made. "Verizon said that it will monetize its new search engine through advertising but the advertising won't be based on browsing history or data that personally identifies the individual, it will only serve contextual advertisements based on each individual search," reports VentureBeat.
https://www.onesearch.com/5 -
MongoDB database with really relational data. One main collection that had refs to four other collections, all of those references necessary to populate data for a page view. Complicated aggregate to populate all the necessary data and then filter based on criteria selected by the user. And then the client decides that he wants the information to be sortable by column. Some of those columns are fields on the main model, no problem. Others are fields on the refs, which is more of a problem. Especially given that these refs aren’t one single object. They’re arrays of objects.
The revelation was that I could just write an aggregate function to flat map the main collection, returning only the fields necessary for the search, and output it to a new collection and instead use that new collection for displaying and filtering/sorting search results.
But you can’t run the aggregate all the time, you surely say. If anything changes in the main collection, it won’t be reflected in the search results!
Mongoose post(‘findOneAndUpdate’) hooks, my friends. Mongoose post(‘findOneAndUpdate’) hooks.
Never been so happy to have a thing working properly in my life.2 -
Fucking monstrous specifications!
What do I need 4500 pages of specification if half of the defined behaviour is specified as user-overridable and every fucking blithering idiot that has only read the cover page defines behaviour for his system just slightly different.
'Oh the specification lists 999 ways to structure data, but I don't wanna be mainstream. I want an egyptian hieroglyph at the end every 42nd data item received'
So many things are already standardized, just use what is already there and don't re-specifiy the wheel. How hard can it be? -
Ha! Our Ops Support DBA Manager just asked (tongue in cheek) "if we are now supporting MS Access, too?" To which of course, the answer is no. Business user who install Access on their desktop and use it for business, get to provide their own support. As their Dev DBA, I'll be more than happy to help them migrate their data to SQL Server, Oracle, or Teradata, depending on the Use Case for the data. But, no, we don't support Access. Ever.
-
The moment when you just wanna fetch data from instagram API and they ask for "Instagram User Experience Video" for permissions. #FU Facebook #FU Instagram
-
Hey their did anybody notice unauthorized login attempt over ssh. Means I have a demo digitalocean droplet I just left it for some logs their isn't any imp data over but when I try to ssh back that machine after an interval of max 5 to 6 days after login message displayed their were 9876 login attempts were made, then I directly go to ssh log over secure log file get all those IP, found out max were from China some from France and all are doing random login names like user, admin etc etc and with random password over multiple ports even non standard one, is anyone finds this happening10
-
Can anyone explain to me why facebook got pulled over for selling user data and google hasn't yet?5
-
I was wondering if anybody working for a larger Company in 3rd-Level faces the same personal problems as me?
We got alot of our own developed software and process. Regulary some Keyuser fucks something up by importing something wrong, which skews the master data. Its intended to be managed by the Keyuser.
Fast Forward, my Keyusers are so dumb, that they fuck up the master data import wrongfully. The process behind that then have wrong Data to operate (a numeric value neeeds to be set).
The Enduser then opens a Ticket for problem XYZ. Then the Keyuser forwards us the issue.
We already had that same issue X amount of times and its always the same reply. I made a FAQ, Knowledgebase entry, etc.
Nothing works, 2 weeks pass and a similiar tickets comes in...
Memory Capacity of the User exceeded after 1 Day. FML
Anybody facing the same shit?6 -
Made a root only app: enable/disable GPS, mobile data, airplane mode and etc. work on not rooted device(yes all these functions work too).
How: Desktop app which downloads cross-platform ADB drivers, unzips them, executes a few commands, deletes the drivers and voala.
P.S: I use local ADB TCP connection(yeah I ported a part of the drivers for java android) and write_secure_settings granted with 'pm grant'.
And everything is user-friendly with screenshots explaining how to enable ADB and how to click a 2 buttons.3 -
so i was validating some user data using ajax in a facelets page.nothing was actually being validated when i deploy the application in tomcat..i thought it some sort of a bug on my code and after checking for the greater part of today i just couldnt find any bug.So i decided to deploy on GlassFish and it worked perfectly fine..fuck containers!!!1
-
Token for App -> backend authentication is generated one time when the user signs up. Sniff it once and you've got access to the user account forever.
Passwords are hashed with one round of SHA1, no salt.
Everything including login data is sent over plain HTTP.
Luckily I got permission to fix that mess1 -
*Frustrated user noises* Whyyyy, Grafana, why don't you implement any actual query forgery checks?!
So long as a user has access to the Grafana frontend, they can happily forge the requests going off to the backend, and modify them to return *whatever* data they want from the datasource.
No matter that they're a read-only user. That only stops them from modifying the dashboard definitions on the frontend, but doesn't enforce any sort of immutability on the BE...
If anyone had any tips on how to further secure it, I'm curious...5 -
Debugging a Velocity template issue the other day where I was presenting a firm to the user to fill in some data. Whenever the user had entered in one or more lines, a 'true' kept showing up cryptically before the form. Drove me fucking nuts because there was nowhere in the template code that was printing before the form input.
Turns out it was the output of a $list.add(...) being rendered to the screen.
Spent 40 mins on that shit.
😐🔫 -
After all this time I’m still confused, why was Cambridge Analytica such a huge deal? I feel like a lot of people knew this in years prior, that Facebook/Google were scraping user data and activities to use for personal profiles and hence more directed as placement. Stuff like Ghostery, Privacy Badger, Disconnect, Ad Nauseum (rip it’s Chrome plug-in) etc. all focused on not allowing these same trackers to get information, so not like this case just magically busted the doors wide open screaming that all those websites you visited are now in Facebook’s database and no one knew.
I just can’t quite understand why everyone got up in arms after this.1 -
Ok, let's do the opposite (reference to a previous rant).
Should a frontend developer know about:
- Data structures and algorithms?
- User interface design patterns and usability?
- User experience heuristics?
- Accessibility?
- Design tools?
- How websites work on the browser after the frameworks have done their job?
- Data flow, and artifacts like user stories?12 -
TIL if you try to add a user with ~invalid~ data you get fucking nothing!
Like it continues, like it would normally, but nothing gets inserted to the database and no exception is thrown.
Fukcing 4
4 -
Let's see:
No archival of data on a database server with over 5000 high profile customers using no encryption whatsoever with telnet open on LAN, every user on the same account in the office using the companies name as the password... But hey there are security cameras! -
my sophomore year of highschool I went to a public hangout / study area after class was over and installed a raspberry pi above the ceiling tile. I ran a cord along the wall and into the ceiling to power the device. I ran a sniffing script over the next few weeks and collected all the user/pass data that went through in plaintext. You'd be surprised what goes unencrypted... ;)1
-
Three Layers of Security
As InfoWorld notes, all smartphones have three basic
elements of security. Your first major task as a mobile
user is to become aware of these layers and enable them
in your devices:
1. Device Protection: Allowing remote data "wiping" if your
device is ever lost or stolen.
2. Data Protection: Preventing corporate data from being
transferred to personal apps running on the same device
or personal network
3. App-Management Security: Protecting your in-app
information from becoming compromised. 6
6 -
LINUX MASTERS, I can't believe that linux didn't get rid off yet of the annoying user:group system.
Anyway, I have two pre-existing groups(postgres & www-data), now I need to enable both groups full access to an HD for data storing, currently the owner of /media/"user"/DATA is www-data but I need to enable the postgres group to operate in it.
I seached around and can't get around how to accomplish this, if it's even possible.
Help >_<15 -
What is everyone's opinion on companies/organisations 'too big to fail'...?
I was just pondering on how 'just Google it' has become so 'natural' as a way of saying search the Internet. The more I think about it, the less I like it.
I know the chances of them failing/crumbling are neary zero (hence the name) but if an org, Ie Alphabet, made some shit decisions and bankrupted their company, what would happen then? Any ideas? I don't mean in terms of social fallout, economic etc.
I mean in terms of network infrastructure, them being such a central part of 'the web', all their Dns services, their backbone links, Google drive, Google fiber etc. What would happen to all user data? Just be destroyed?
I've never 'seen' a large tech company collapse, but just wander as to how that process would work for such a huge organisation, and the literal mountains of data they have which will need destroying or relocating.
Inb4 watch Mr robot hurrr5 -
My typical user interaction:
Me: "But we need to pull the data from the source and we don't have access to it"
User: "Make it work"
Me: "I want to fucking die." -
Literally facepalm when seeing my company coding used Email as an identity to retrieve profile data etc. Yet the profile is allow user to interchange their email.
What is this kind sorcery is this? Why don't just plainly use the UID to retrieve profile instead, as simple as that. Is UNIQUE!!!
😒😒😒 F5 -
Page lists data for user. Edit button replaces the line with a form for the data line with save and cancel buttons. Both buttons replace the form back with the simple line (oc save button only does so if post was a success).
Client writes they can't go back after clicking on edit - forgets to say, where in the World they want to go back to, when they get their initial page back with updated or unmodified data depending on their button choice. -
yesterday, I just swapped my sim card for some time with another. Placed it back....and voila! I can't enable data connection. I lost all my apn settings. To add to this, neither is it auto fetching the apns, nor i can manually change it! It shows some fucking error "apn settings not available for this user". I have another phone with same android version (lollipop) and everything works smoothly on it. These guys just broke everything after giving an upgrade from kitkat. Auto brightness stops working after a few hours, random reboots.... This is it... bye bye stock rom!
-
I had serious depednecy problems for a while. I couldn't find anything similar on the stackoverflow so I had to figure it out myself, so after some planning I found it out that I have to replace a complete module to reach the full potential of the application. To reach the desired speed and the correct output I had to split the input in two and then run one side trough an external module which made some state changes on one part of the input data, then the application merge the output with the rest and returns every single drop in a nice processed way. It works quite well, the user can decide in what percentage of the data shall be processed to get the desired output and the right state. I am really happy with the end result. The picture of the result in the comment.1
-
New ERP project has been going for 1.5 years. Project team comes to me asking to create an import process from old ERP to new ERP in 4 months, oh we need data loaded into Test today so we can complete end-to-end user testing. Project team doesn't have any requirements documented or know what data is needed in new ERP. I have never used/seen either ERP system. Project team keeps changing what is required in the new ERP weekly, and they don't understand why all the imports into new ERP are bad.
-
When your project partner tells you not yo use database constraints, know that he's about to do some messy handling of the database.
How can someone make a user deletable and leave his other data lying around in other tables? I'm tired.
Messy codes everywhere.2 -
So, I told the interviewer that my frontend skills are bad. He said that I should not worry as the tests where backend centered, good. Later, I got the job, now the interviewer, which happens to be the head of tech in the company I work for, has assigned me two tasks involving 99% of work on the frontend.
FFS, I've been searching on Internet and reading Kendo UI documentation for 4 hours to figure how to trigger the KendoGrid editable popup with populated data to enable the user to update such data. AAAAARGH!!!1 -
Hi guys! We are still searching for another dev to join our team for the hackathon hosted by Deutsche Bank in Berlin (late october). We're currently a team of 2: @ginjikoibito as iOS-/Backend-Dev and me as Designer.
So far the idea we want to apply with goes in this direction: Real-time evaluation of social structures through analyzing wealth & transactions provided by anonymized user-data of the API. It will also incorporate recognizable networks between users.
Sounds interesting? Please leave a comment, we're happy to share more with you :-)2 -
I have a client who wants this web-based membership system I'm building to also accommodate arbitrary changes she makes to the user data in a third-party system that my component writes TO but doesn't receive data FROM.
No amount of explaining dissuades her from the belief that her changes will magically be represented in my side of the data.
So, yeah, I'm screwed.2 -
Security issues I encountered:
- Passwords stored as plain text until last year.
- Sensitive data over http until last year.
- Webservice without user/pass authentication. -
Data Scientist: Recommendation Engine
Sr. Data Scientist: Machine Learning system to recommend personalized content to users.
Principal Research Scientist: AI to realise users' need for content and customise the user feed using content populated for maximum content usage that correlates with their likes/needs/wants.
God: ... -
Unfortunately, WordPress doesn't provide built-in functionality for exporting user data. The only way to do it is using an import and export user plugin.
But that's fine. Don't waste your time on essential functionality, just keep adding more features and gimmicks to your Gartenzwerg editor.
Always good if you got your priorities right.7 -
I’m afraid I already know the answer to this question, but are there any navigation apps that aren’t powered by Google, etc?
Is there an alternative to Google/Apple Maps and Waze, that provides accurate information while also keeping user data (more) private?8 -
The highlighted lines are a part of a flask app I'm writing in Python2(not python3 because I'm a bit too lazy to fix few dependency errors). All functions work as expected and all templates are rendered individually, and routes are all defined. check_date checks for invalid dates like 32Jan, 2018. It returns 0 if date is valid. add_data basically returns 0 if it decides to add user data into the database(db).
The problem is that line 60 renders but lines 54,57 don't. Any ideas as to what might be going wrong.?
PS: I'm building this app for learning and not for a production environment... 1
1 -
!rant
Just did some really satisfying refactoring. Much happier with my work now. Its a little cli app to poll M-bus devices and write the data to file if the user wants. Can scan the whole range, search for specific devices and VIFE codes, parse an input file for lots of the previous data and one or two other things.
How's everyone's else's weekend? -
I just love screwing around with the test data for hours instead of solving the actual problem. This system does not need to be this complicated
-
How does google map get the ever changing streets data? Be it traffic or general street map? It's accurate af! If a street is shut temporarily, it knows that and reroutes.
I understand that if there are others who are using Google maps in the area, it can aggregate and make an educated guess for every other user. But I am pretty sure it just can't rely on other users opening the app and having their gps on. Eg: live traffic data.. not everyone on the road is using maps!1 -
So this product already has session replay, feedback collection widgets with multiple integrations to jira, slack, GitHub etc.... this widget embed code is already getting large and I am beginning to get worried
New problem, owner wants to add some error reporting tool. this would have been easy if I was to just collect and group errors from the users browsers but here is the use case
user tries to submit a form, out of probably lord know number of function and api calls, one fails, the user may be stuck or not, we don't know but I am supposed to infer from the session recording data whether the user got stuck or not, create a nice PM understandable error message like "user was unable to update their profile", group this error message over the number of affected users/visitors and attach the affected error messages/data to this generated group and also the session recording.
where am I even supposed to start with this?, can I trust AI to do the heavy lifting?4 -
Web dev (JS, node) question since there are so many here... I think...
I want to return a JSON array as a stream so the server passes whatever the DB returns but also normalize each record.
Also the data is across several collections. Is it possible to return this in a single request?
And how do I add in error handling? If there's an error in between the user already has part of the data?3 -
I am new to redis and confused how this works
To keep it simple lets say i have a CRUD service for user
- POST user, just creates user
- GET user by id, fetches user but using annotation @CacheEvict(). This method has a Thread.sleep(3000) before fetching user
- GET all users, fetches all users but using annotation @Cacheable()
- PUT user by id, updates a single with annotation @CacheEvict(). This method has a Thread.sleep(3000) before fetching user
- DELETE user by id, deletes a single user with annotation @CacheEvict()
---
GOOD:
When i GET user by id, i wait 3 seconds and then get the fetched user
When i GET user by id again, i get the fetched user instantly in 5 ms. This means it has pulled the user from REDIS cache instead of postgres
---
PROBLEM:
If i PUT user by id, update some data, and then if i GET user by id, it will return the user in 5 ms BUT the outdated user! Not the newly updated one. Because the Redis cache configuration has not expired yet. So there are now data inconsistencies
---
QUESTION:
How can i know When was something updated, deleted or whatever, so that i can fetch data from postgres (latest data) instead of Redis cache (outdated data)?10 -
I wonder if there is any technical issues that prohibit the creation of open source websites.
By "web sites" I do not consider CMS like Drupal or word press, but rather entire end web site sources.
In fact anything (frontend, backend) except database content that contain user data and credentials.
Not for reusability purposes like CMSs, but simply for transparency and community development purposes, like almost any open source end application.
I agree that a web server is much more exposed than a classic desktop app, as it has lots of targetable private data and internet public access. But for some non-critical purpose this seems to be affordable in exchange of better code review, allowing a community to help improve a tool it uses, and better (not perfect though) transparency (which is an increasingly relevant question nowadays, mainly towards personal data usage).6 -
Software Message: "you didn't change data, you don't need to save."
Damn it, how about simply writing the same data?
Or is this just user logic?2 -
What is your method of dealing with states in state machines? In programming, we often come across situations where we have to model states in our head as to not get the programming wrong, e.g. in my case right now:
You have a tabular webform that gets filled in.
Requirements:
- When the user is able to search the data for a specific value, it should be a cumulative search (e.g.: search for books with "eng" in the language and then with with "19" in the publishing date)
And so the current pseudocode is:
search(e) {
if(!word) {
set(previousState);
}
const searchdata = previousState.filter((row) => row.indexOf(word) != -1);
// but wait, what if I say: searchdata = searchdata.filter() for cumulative search? Oops, I can't, because it doesn't exist at that moment yet. What if I create another variable?
setState(data: searchdata);
}
Current bug:
- when deleting characters from the search field, it doesn't filter cumulatively; it just filters the data according to the current filter.
It's things like these that get me stuck sometimes.12 -
How to start learning iot?i mean, here is what i understood after searching for a while: iot consists usually the hardware devices/sensors/robos which generate data/do something ; transmit this data to some server where calculations are performed and then show it to user.. And there are some kits worth a big amount which you gotta buy... is that all right?
Guidance please .:)2 -
so, next year i would like to get an internship at some small-medium sized company.
my GPA isn't the best in class, I'd rather say its below avg.
but I'm quite comfortable in multiple languages, built a couple of websites running in university with a user base of 4,000, right now I'm doing an online course in data science.
I'm not sure that they'd let me mainly because of GPA.
idk what to do.
ps: I'm planning for summer, I'm in 2nd year, i did an internship at real small local company as a xamarin dev -
Not only does every app need to have an export option, but new exports must create new, time-stamped files rather than overwriting an existing export!
A counter-example is "Battery Monitor Widget" by CCC71 or 3C71. That app creates a file in the main user directory, named "bmw_history.txt" (no relation to the car manufacturer).
When a new export is created, the existing bmw_history.txt is overwritten. This could lead to data loss if the user is unaware of this behaviour.
The developer thought of creating an export ability, but messed up at the file naming process.
Mandatory time-stamped user data exports for every app would not be so bad. This makes sure no developer would forget about it. GDPR gave us data portability for social media platforms. Let's do it for apps too. (Sorry, Samsung Internet, you can no longer lock in saved pages. Your users are sick of it.) -
Any one running Symfony on a Docker container in production? I currently try to migrate our dev env to a docker compose setup (from a "monolith" vagrant vm). I'm atually not stuck at a Symfony specific thing, but on a, I guess Docker specific one(?), The issue is, I need to read and write with two users to one folder (in my case the /application/var/cache folder). Since I mount my whole code into the docker container (to use an IDE on the local files), I've got a volume (not mounted to the outside world) for that folder. (As far, as good). Now this folder is owned by root and root is also the user I get when I enter the container. When I then run a cli script, that writes to this folder, every thing works (as it's run by root) and the resulting entries in the cache dir are owned by root. Trouble starts when the php fpm process tries to write stuff in there too (as it's run by www-data).
If I add `USER www-data` (or create a new user foobar and add `USER foobar`) the container exits with status 0
So I guess the question is, is anyone running an Symfony app on Docker in Prod, if so how do you solve this? Or another question would be what is the best practice to do this? Sure on dev I could just `chmod 777` the whole folder or run the php-fpm process as root, but if that thing ever goes to prod, I wouldn't sleep very well... -
Finally got the data from my API and displaying in my app using RxJS, so I work on getting user data read in after passing through an SSO page. Now that works but the original stuff doesn't.1
-
I have a question about modeling a UI to code
Lets say you have a UI finished
Now you need to model it to code
For simplicity ignore functionality just focus on designing the model classes
For further simplicity Imagine that the UI is grouped into material cards.
Lets say the UI of the User Profile Page looks like this:
1) HEADER
- user profile banner
- user profile image
- username
- first and last name
- total posts
- total likes
- button to add to favorites
- dropdown to report user
- button to share profile
2) BIO
- short description
- user birthday
- location
3) ANNOYNCEMENTS
- "X% off on Y"
- "going live at X:YZ"
- etc
4) GALLERY
- group of images posted on profile timeline
5) TIMELINE
- text/video/audio
- number of likes on post
- user profile image
- username
- user first and last name
- post date
- etc
---
Now im having a mixed feeling what is right thing to do. In my User model i have a date of birth field among other fields as well as profile image url to s3 bucket. This means that i already have half the information for HEADER card from User model, but now i would need to create a Profile model to fill in the remaining fields.
Especially for BIO card:
- short description (Profile model)
- user birthday (User model)
- location (Profile model)
Is this weird? Mixing data with 2 models on 1 page on 1 or multiple card sections?
This feels messy to me and as if im gonna hit a wall if i continue long enough like this. A better solution to me is to have a Profile model handle everything on the Profile page and be able to cover all cards and fields on each card. But this doesnt seem like a realistic or possible way to do it since specific fields are required for User model.
Am i overcomplicating and overthinking this shit?
Tell me is it normal to mix 2 or more different models to show data in 1 card on 1 page or how would you suggest doing it better?6 -
MySejahtera is not a good appliaction at all! They just use Sqlite or Shared Preferences in the app for keeping the data local. (Just local?) As soon as you clear cache or data, The user no longer exist! Like wtf ?
So I decompile the app and review the source code, the code is not even properly obfuscated(That's why I can read it). There's a part of the code on a for loop went
```
for (int i = 3; i < array.length(); i++)
{
for (int j = 2; i > array.length() *2; j ++ )
{
onScan();
}
}
```
Which is unacceptable!
First , why nested for loops?
Second, instead of declare 'array.length()' multiple times why not declared it global for once?
No wonder the initial state of the app is buggy as hell.6 -
Well those fucktards in canonical made a fucking os which was easy to use for an average user and now they dominate the Linux scene. And in this way they fucking collect data from fucking users using Ubuntu and send those stuff to other companies like Google does. It's just bad about how ppl are fed the idea of being free of surveillance with Ubuntu. I searched shit up online and found out that many os out there are doing these dirty tricks. Man, ig it's better to do a linux from scratch project and use it lol.2
-
Working on a legacy PHP project that every single query inserts user-provided data without any sanitization, aka SQL injection ahoy! Also no framework.1
-
The "recycle bin" feature of Samsung "My Files" is amazing for data loss prevention when moving files out of the smartphone.
There used to be two ways to move files out of the smartphone to make space free. One is direct moving, the other is copy-deletion. The first is self-explanatory, the second means first copying the files and then deleting them on the phone.
Thanks to the the recycle bin, which keeps data for a month, files on the phone can be copied out and then put into the recycle bin instead of immediately deleted.
This means that if the copying was incomplete, there is a thirty-day grace period to get the files back from the phone.
The benefit of moving files instead of copy-deleting them is the lack of the deletion step. Moving files out directly does not have the emotional barrier of deleting the files from source like the deletion step of copy-deleting does.
Moving files feels like moving items to a new room, where as the deletion step after copying feels like destroying something.
So why not move files out? Because there is a risk of data loss if the device disconnects while files are moved to an USB OTG device. Due to write buffering, files that are moved out might be deleted on the phone shortly before they are completely written on the USB-OTG.
This is not an issue with MTP (Windows or Linux through USB cable) because the file systems are managed by the computer, so if the phone disconnects while files are moved out of the phone using MTP, the file system is kept intact by Windows or Linux.
Now, thanks to the recycle bin, there is no emotional barrier to deletion because the files on the phone are automatically deleted after 30 days in the absence of the user. The user can press the "delete" button without worries because of knowing "I can get it back until a month from now anyway". -
today i`m after 3 year fucking android developing
try to show user name on text view but it`s not working, after 3 hours i just site up and site down (i`m boy, fuckers) and suddenly see i stopped boy set data on wrong text view :cry:8 -
i was watching a video on how whatsapp can't make enough profits coz its free and even though its a clear lie (the cartel money made by selling user data will obviously not show up in legal books), i had a thought. can any good consumer software be ever kept free for usage?
Say i made a very awesome chat app. it has 0 bugs, it does the basic tasks of sending /receiving data and media correctly and do not require any maintenence .It also is optimising a lot of cloud cost by keeping user data in their own devices and only transmitting data on triggers.
i still would require a server to keep the trigger architecture alive. and all the servers in the world are maintained by for profit corporates which will charge a premium for their services. so free products are a fallacy as someone is paying for it. it will be an investor, a different business or we the consumer (either directly as subscription , or indirectly via ads or personal data)
So i guess this realisation is going to hit soon to a lot of tiktok and insta influenza kids4 -
How would you create a mock for an Aggregator Microservice (stateless) which makes requests to other services for each request, transforms the data and then responds to the user?
I want to create a mock service where I don't t have to run the other services but it should create kinda realistic responses.
Have you had to create something like this?
I'd use it for testing another microservice that uses the aggregator.2 -
I know I sound stupid but I need help, I create a repo on GitHub using gh-api ```js
export async function createARepo({name,description,token}) {
const headers = {
"Authorization": `token ${token}`,
"Accept": "application/vnd.github.v3+json",
}
const {data} = await axios(
{
method: "POST",
url: "https://api.github.com/user/repos",
data: {name,description,auto_init: true},
headers
}
)
return data
// console.log(res)
}```
when I run this code it only creates an empty project with a readme but I also want to create a file with a .html extension of the project can anybody help me with how I do this?7 -
Do reports actually make people dumber?
I write a lot of reports that output for our customers into excel. I'm starting to suspect that for many customers it doesn't actually help them, rather it might actually hurt them (also eat all my time).
If a user generates their own report via search options or etc to pull out some data, they usually SEEM to have put some thought into the actions required to find the data they want.
Accordingly:
1. They immediately know what information is there, and why some information might be excluded.
2. They can do a little trial and error to solve their own problems / better understand what is going on.
3. They're a hell of a lot less likely to insist that something is "MISSING!!!" without seeming to actually know what the thing(s) are that are missing.
With auto generated spreadsheet that shows up in the email there's just little no critical thinking outside of some stray thoughts in their head when the spreadsheet showed up ...2 -
Profile (1, 1) --- (1, 1) User
Right?
- A single user *must* have *exactly* 1 profile.
- A single profile *must* belong to *exactly* 1 user.
Makes sense?
I did this because i moved user profile image and user banner image into Profile entity
So now i can easily join tables and fetch user profile image based on username or user ID
By deeply thinking like an asshole and overengineering, i stumbled upon a confusion
If i can join tables and get ALL fields (assuming its a left or full outer join) from both entities...
What is the difference between choosing which entity to fetch on the frontend?
For example if i want to fetch users, inversely, i can fetch Profile entity, which has User entity as a nested object, and that way access users. Now i have access to each user's profile image, banner image, bio etc aside from the entire user object
If the user navigates to a profile page, inversely, i can fetch User entity which will have a Profile entity as a nested object, and that way show the remaining necessary fields that the profile page needs to show
I gave these inverse examples because if i want to fetch users, surely enough i can simply fetch from User entity, and if i want to fetch someones profile data i can fetch from Profile entity directly
So if this is the case, when am i supposed to fetch one over the other?
You tell me. For simplicity lets focus on these two examples. Consider this as an exam question:
1) user navigates to home page. Now paginated users with role X need to be shown, but also their profile image. Do you fetch from User or Profile entity? If you use joins which ones and why?
2) user navigates to their or someone elses profile page. Now profile-based data needs to be shown, but also the user's username and full name need to be shown. Do you fetch from User or Profile entity? If you use joins which ones and why?20 -
stupid dumb wordpress, who POSTS a user registration, returns data to the SAME site with a dumb "successful" message alert, and THEN redirects to whatever page you want?!?! looks like shit, feels like shit in terms of UX
JUST REDIRECT ME TO THE PAGE I WANT FROM THE SERVER THAT'S THE WHOLE POINT OF PHP
I swear its as slow as balls too -
Visualize the entire complexity of the content within the project so that you know what data users will need to access, and compartmentalize those in to separate modules that you can build on over time. Think about any limitations with accessing that data (does the user have that role, what if the data is accessed simulateously, how to handle the same user accessing from different devices etc).
Think about the devices being used - is it going to be a website, an app, both? How best then to access the data? Direct access to a database, or an API system?
Then think about the front-end design and how to simplify the view right down as much as you can. Again, break it down in to modules.
Then decide on the technology you want to use, and what libraries would help simplify things.
These days I like to use JSON API's to access DB content because app and web technologies change quite often but the API will be accessible to whatever I use to build it.
For websites I love using Laravel, which simplifies the back-end tasks, and mdbootstrap which simplifies the front-end tasks and looks "appy". -
One user could report that the data they saw didn't make sense. Turns out there was a one-off hardcoded caching detail for one of our services that cached based on a search query (yes, the entire query was the key) and before any auth checks. The system would return the results owned by whoever asked first, no matter who asked after that point.
There's "Oh dear but we all make mistakes" and there's surrender cobra. This is what PRs are for.1 -
What kind of innovation approach has helped humanity in a better way? Is it some group of obscure indie devs working overnight to write some software which is free, useful and purposeful devoid of licensing shit or the too-honorary-to-shit-from-arse organizations which put marketing gimmicks like making world better place and which compromise user data either to governments or to other corporations for monetizing given the first chance. If innovation is happening in both the spectrums then what is the viable kind of required innovation at the moment for us humans. IMHO I don't trust corporate innovation and shitty innovations happening in Facebook, Google and likes. Has corporate greed bought innovation for market price.1
-
!rant
I want to put some user data from server side into a browsers local storage. Right now I'm just echoing js from php. Which is a really bad idea i think. Any suggestions. -
Business team has been chasing an issue with a report we generate, which I've sort of been dragged into because I worked on a loader for data they need.
Another guy is responsible though for the report and they had a meeting with user to iron out it last week...
I would expect the guy to ask me for guidance, essentially needs to rewrite it duplicate the loader but haven't heard a peep from him...
I guess I'll let him deal with his own shit and extricate myself from their discussion -
What do you think happens when enterprise software meets big data and user generated content? Idk, ask Github. These guys are sitting on a goldmine. The paradise of every big company. The only reason they're not faang is cos it's niche but they'll probably be influential (read, big bad) in the coming years
I predict the copilot thing is a benevolent side. Or maybe it still seems so since it's still in infancy and hasn't aggressively started snatching most developer jobs. What will become of us when that time comes? What other form of technology can computer still require our assistance to create?16 -
Any good recommendations on how to gather user metrics/instrumentation and visualize data?
The program is a WPF application with not internet connection so logging to file and get file is probably the only solution.
I've played a little with Serilog to file and trying to import the log into elastic search and visualize data with Kibana. -
Alright, hear me out…
Circumventing tracking protection is sometimes okay!
Let me explain!
If user explicitly consented to tracking, why can’t I track them? They have tracking protection installed (as they should, and so do I), but when they click “Allow”, I still can’t load analytics. That’s not fair.
I will show the “Decline all” button loud and clear right next to “Allow all” and “Customize”, but I don’t want user’s adblock decide for the user. I won’t load anything until they explicitly allow me to. For all I know, they can have an adblock filter that blocks consent-seeking UI elements/popups (although mine is not a popup, I hate popups), and to me they will appear as unconsenting users. I’m fine with all of that.
But why can’t I track people who agreed that I can track them?
This is why I use my own analytics url that isn’t present in any anti-tracking blocklists.
My tracking does directly benefit both me and my users, and no one else. My users because it makes the product they pay for better at no extra cost, me because when my users are happy, I’m happy too. I want to put emphasis on “no one else” — I use self-hosted things that don’t send anything upstream. I own 100% of the data. I obviously don’t sell it, but I don’t share it either. People who say they don’t sell data all while using google analytics/meta pixel are clowns. Damn right you don’t sell data — you give it away for free. I don’t.5 -
Had an old classon "smart" Helmet(Brooklyness). App does work, company is looking dead. Reverse enginnered the app(android "beyong - micromobity"), quite simple if you have the apk file on hand. The fucker is kotlin which is compiled to Java, and uses AWS for User management(don't want it) and its data, even if a mobile is already required as relay to get the video files off the helmet into the cloud.
Never worked in kotlin and java, and never want to work in it ever again.1 -
I got android nougat on my phone and of course my root was gone
It was dearly easy, but along the step of doing it I had to format some partitions (like /data), after that I flashed some zips and put the backup of my data partition back on my phone
Pictures where missing, some app data where missing, also WhatsApp pictures and videos
Turns out, twrp saves pretty much everything, but leaves out the user data folder, where all of that stuff would've been
I'm just happy that I'm not one of those people who don't need to keep thousands of pictures
I don't really know what kind of stuff I lost, probably not too important -
Looking for iOS and Android app developers to join startup in Rutherford, NJ area. Must be able to show portfolio of apps and have some published. Must be able to pull and compare data with sensitive databases (social security number, passport, birth certificate, etc) to verify user. You will be compensated hourly. Must sign NDA.
-
I think I am too stupid for OAuth2. How do I handle this scenario: User deletes his account at the OAuth Provider. Lets say my own, Google, Microsoft, whaever. How do I handle data associated with the user then? I have some data which can be deleted then as it is not needed anymore.
Or is this not possible by design? If yes, this a perfect example on how to waste resources...8 -
Top Benefits of Using Data Loss Prevention in Microsoft 365
Data Loss Prevention (DLP) in Microsoft 365 offers numerous benefits to organizations aiming to protect sensitive information and ensure compliance. One of the top advantages is enhanced data protection, where DLP policies help identify, monitor, and restrict the sharing of sensitive information like credit card details or personal identification numbers across Microsoft 365 apps (Outlook, SharePoint, OneDrive, and Teams). This proactive security measure prevents unauthorized access or accidental sharing of confidential data.
Another key benefit is regulatory compliance. DLP helps organizations comply with data protection regulations such as GDPR, HIPAA, and CCPA by enforcing policies that limit data exposure and unauthorized sharing, reducing the risk of costly fines.
Microsoft 365 DLP also offers visibility and control. IT administrators can monitor user actions and identify potential risks in real time, making it easier to enforce security measures. Additionally, user education is integrated through policy tips, which educate users about data protection during daily tasks.
Finally, DLP offers seamless integration across all Microsoft 365 platforms, making it easy to manage and enforce consistent security policies across emails, documents, and collaborative tools, ensuring comprehensive protection for the entire organization.



