Join devRant
Do all the things like
++ or -- rants, post your own rants, comment on others' rants and build your customized dev avatar
Sign Up
Pipeless API

From the creators of devRant, Pipeless lets you power real-time personalized recommendations and activity feeds using a simple API
Learn More
Search - "verify"
-
A few years ago when I was still an apple fan boy, friend of mine bragging me about how android is awesome, we were drinking some shots at our local pub and I was starting to get light headed. At one point he showed me so called "terminal emulator" app. I checked it out, and assumed it's an emulation, just like dosbox, so I decided to verify that "rm -rf *"... (the phone was rooted)
The phone shutdown within seconds, I couldn't stop laughing, while my friend was shock that his new phone was longer booting.
Luckily he managed to reflash the ROM. What can I learn from that experience?
1. Don't drink and sudo
2. Don't call your app an emulator if it's the real deal.34 -
A super creepy webcrawler I built with a friend in Haskell. It uses social media, various reverse image searches from images and strategically picked video/gif frames, image EXIF data, user names, location data, etc to cross reference everything there is to know about someone. It builds weighted graphs in a database over time, trying to verify information through multiple pathways — although most searches are completed in seconds.
I originally built it for two reasons: Manager walks into the office for a meeting, and during the meeting I could ask him how his ski holiday with his wife and kids was, or casually mention how much I would like to learn his favorite hobby.
The other reason was porn of course.
I put further development in the freezer because it's already too creepy. I'd run it on some porn gif, and after a long search it had built a graph pointing to a residence in rural Russia with pictures of a local volleyball club.
To imagine that intelligence agencies probably have much better gathering tools is so insane to think about.53 -
Dad: why do these forms ask me to fill those random characters(captcha)
Me: to verify that you are human
Dad: as if animals can use computers
Me: 😅7 -
The hardest part of being a programmer wasn't the education, the self-teaching, the sleepless nights or the hours of agony trying to fix a bug that would break a program I'd spend weeks working on.
It's the realization that my family, friends, coworkers...nobody understands at all what I do. They don't know of my failures or my triumphs. I can't talk about it with them and it's becoming more apparent to them that it's taking up more of my life. And in a way it feels like a part of myself has just become, well, alien.
Best way I can describe it is, it's like the "Tears in the Rain" scene from Blade Runner.
I'm stuck, I think. I know I've been shutting out people from my life more and more as I don't want to "deal" with people's issues, but I don't think it's been good. I'm can verify that I'm depressed beyond my normal levels.
It's time for me to make an appointment with a therapist.
Remember that you are loved here, and appreciated. Don't let anyone tell you different.
Stay strong. 25
25 -
Hi client,
I am not able to login to your prod server. Can you please verify the following:
Host: x.y.x.y
Port: 1234
Username: ABCD
Password: password1234
Thanks,
My idiotic coworker8 -
Dear sir,
I'm NOT giving you the information you want because I can't verify you. You can tell me that we're the only company who does it like this and name all companies which do it differently, you can curse me into the ground or completely lose your shit at me but that won't make a difference:
I'm not giving you the information you want.
Sincerely,
Go fuck yourself.9 -
"The customer reports that port 21 is closed on our FTP site. They said that port 443 is open, and wonder if they can use that instead."
"They are entering the wrong server name. Our FTP server is ONLY an FTP server. Port 443 is not open on our FTP server.
Please verify that they are entering `ftp.xxxxxx.com`
Our FTP site supports FTP/SSL if they are concerned about security."
"Customer responds that they would rather use port 443 to send files."
"I'm sure they would. I'd also like to enter our building on the west side when the temperature is below 10º, but there are no doors on the west side, so that's not going to happen, is it?"2 -
Pressing Ctrl + S only once to save your code in the editor is the tech equivalent of locking the door to your mansion and not pulling the knob to check if it has indeed been locked.5
-
Okay, time to delete my old Skype account
1. Enter Skype name
2. Reset password
3. Captcha
4. Complete email
5. Enter email code
6. You are logged in now, please complete your profile first
7. Enter birth date
8. Add your phone number or second email address
9. Create new outlook mail
10. Got access to profile settings
11. Click on delete profile
12. Stop please first verify your email again
13. Enter code
14. Check all checkboxes that I am really sure to want it deleted
15. Click delete button
Fuck hell and that all again for my second account7 -
I made a script for this group to verify their data, but they didn't want to use it because it's "only 50 lines of code and might miss something".2
-
How do I un-idiot my users when it comes to clicking on dodgy email-links??
Got a forwarded email just there from a user who said;
Good afternoon,
Is the below ok to open?
I just tried but got a popup saying I've been blocked from opening it.
I'm not sure who it is coming from and I am not waiting on anything but as it says its from dropbox and is important, i know it's okay.
Can you unblock the link ASAP please?
This is really impeding my work-day as I need to know what it is and act accordingly.
Regards... user.
The Original email came from a random jumble of letters with a subject line of 'important dropbox program' - not only does it look dodgy but its english is horrible! It said;
"Hi tu my freind,
You tu still read a pending verrry important document sent by one of your own contact to be vieweddd.
Install "Highly Confidential english.pdf" by clickinggg here
*insert link leading to something called 'viral-update-trojan.exe'*"
I mean, seriously... help!!! 😢
We have sent emails explaining how to hover over links and to not to click them if it looks wrong.
No one does it.
We hired a company to send fake phishing emails to train users in what to do.
It made no difference!
We now make people 'verify' their email addresses when opening any sort of link to try get them to actually look at what they're opening.
We also strip emails of original attachments and create 'safe' html copies as we can't trust them to look at what they're opening.
Everyone complains about it but Jesus Christ, this is why!!!
Its so exhausting!! What is wrong with people!!! Argh!!! 😤12 -
Before anyone starts going batshit crazy, this is NOT a windows hate post. Just a funny experience imo.
So I was tasked with installing ProxMox on a dedicated server at my last internship. The windows admin was my guider (he could also do debian). (he was a really nice/chill guy)
So we were discussing what VM's we wanted and the boss (really cool dude by the way) said he wanted a VPS for storing some company stuff as well. Fair enough, what would we use? I suggested debian and centos. Then we started discussing what we'd do if the systems would fuck up etc (at installation or whatever).
So I didn't wanna look like a Linux Nazi so I suggested windows. Then the happy/positive guider/windows admin suddenly became dead serious (I was actually like 'woah' for a second) and said this:
No. We're not going to fucking use windows for this. For general servers etc sometimes, fair enough but we're talking about sensitive company data here. I don't want that data to be stored on a proprietary/closed source system, hell what if there's some kinda fucking backdoor build in, who can fucking verify that? We're using Linux, end of discussion.
😓
I was pretty flabbergasted as he's a nice guy and actually really likes windows!
Linux it became.5 -
Hey, Root? How do you test your slow query ticket, again? I didn't bother reading the giant green "Testing notes:" box on the ticket. Yeah, could you explain it while I don't bother to listen and talk over you? Thanks.
And later:
Hey Root. I'm the DBA. Could you explain exactly what you're doing in this ticket, because i can't understand it. What are these new columns? Where is the new query? What are you doing? And why? Oh, the ticket? Yeah, I didn't bother to read it. There was too much text filled with things like implementation details, query optimization findings, overall benchmarking results, the purpose of the new columns, and i just couldn't care enough to read any of that. Yeah, I also don't know how to find the query it's running now. Yep, have complete access to the console and DB and query log. Still can't figure it out.
And later:
Hey Root. We pulled your urgent fix ticket from the release. You know, the one that SysOps and Data and even execs have been demanding? The one you finished three months ago? Yep, the problem is still taking down production every week or so, but we just can't verify that your fix is good enough. Even though the changes are pretty minimal, you've said it's 8x faster, and provided benchmark findings, we just ... don't know how to get the query it's running out of the code. or how check the query logs to find it. So. we just don't know if it's good enough.
Also, we goofed up when deploying and the testing database is gone, so now we can't test it since there are no records. Nevermind that you provided snippets to remedy exactly scenario in the ticket description you wrote three months ago.
And later:
Hey Root: Why did you take so long on this ticket? It has sat for so long now that someone else filed a ticket for it, with investigation findings. You know it's bringing down production, and it's kind of urgent. Maybe you should have prioritized it more, or written up better notes. You really need to communicate better. This is why we can't trust you to get things out.
*twitchy smile*rant useless people you suck because we are incompetent what's a query log? it's all your fault this is super urgent let's defer it ticket notes too long; didn't read19 -
Mac: Hello welcome please sign in
Dev: Fair enough
Mac: Oh you haven’t signed in in awhile please get get verification from other device
Dev: kk
Mac: Oh you don’t have a dev account, please sign in on this website
Dev: Hm.
Mac: In order to sign up for a dev account you need to download this app
Dev: ???
Mac: Are you sure you want to open this app you just downloaded?
Dev: Sigh.
Mac: In order to sign up for a dev account on this app you need to sign into it
Dev: For the love of god
Mac: Ok now you can build with Xcode.
Xcode: No you can’t. You have to sign in
Dev: fuck sakes.
Mac: Are you sure you want Xcode to access files on your computer?
Dev: …Yup
Xcode: Signing in isn’t enough you have to select the fact you are signed in a dropdown nested 3 menus deep.
Dev: God damn.
Xcode: Build failed please sign in to phone as well.
Phone: New sign in detected, please verify with alternative device.
Dev: Jesus.
Xcode: Build success! Pushing to iPhone.
Dev: Finally.
Xcode: Unknown error occurred. Please go to support.apple.com for help. :)
Dev: …18 -
Morning Deployment.
Me: Let's add this application to this server.
Deployer: Alright.
...
D: Done. Please verify.
Me: I'm seeing errors. Send me the logs.
D: Sure. I also updated the framework to a version that wasn't tested.
M: Yeah, that won't work. Roll it back.
D: Fine.
...
D: Done. Please verify.
M: All the applications on the box are broken. Please revert to the snapshot before the Deployment.
D: Oops, I didn't make one.
🙁😟😢😭😤1 -
Disclaimer: I can't 'officially' verify this.
I've been using Firefox as main browser with about 5 addons for added privacy for ages now. When googles (fucking) reCaptcha takes more than a few minutes on Firefox (about 90 percent of the time, I'm estimating), I switch to Chromium (with the same amount of (similar) privacy addons) so I can go on with my stuff.
Now, I recently thought 'why not try to do user agent spoofing on Firefox to see if reCaptcha would start working 'normally'?
So, I installed a user agent spoofing addon on Firefox/Chromium, results:
Without spoofing:
Firefox reCaptcha success rate: 10 percent approx. (mostly 2+ minutes)
Chromium: 90 percent. (mostly instant)
With spoofing:
Firefox: 90 percent approx.
Chromium: 10-20 percent approx.
Again, I can't prove any of this yet but mother of fucking god, whenever using Chromium or spoofing Chromium on Firefox the succession rate skyrockets.
Google, what the fuck are you up to?10 -
Well, here's the OS rant I promised. Also apologies for no blog posts the past few weeks, working on one but I want to have all the information correct and time isn't my best friend right now :/
Anyways, let's talk about operating systems. They serve a purpose which is the goal which the user has.
So, as everyone says (or, loads of people), every system is good for a purpose and you can't call the mainstream systems shit because they all have their use.
Last part is true (that they all have their use) but defining a good system is up to an individual. So, a system which I'd be able to call good, had at least the following 'features':
- it gives the user freedom. If someone just wants to use it for emailing and webbrowsing, fair enough. If someone wants to produce music on it, fair enough. If someone wants to rebuild the entire system to suit their needs, fair enough. If someone wants to check the source code to see what's actually running on their hardware, fair enough. It should be up to the user to decide what they want to/can do and not up to the maker of that system.
- it tries it's best to keep the security/privacy of its users protected. Meaning, by default, no calling home, no integrating users within mass surveillance programs and no unnecessary data collection.
- Open. Especially in an age of mass surveillance, it's very important that one has the option to check the underlying code for vulnerabilities/backdoors. Can everyone do that, nope. But that doesn't mean that the option shouldn't be there because it's also about transparency so you don't HAVE to trust a software vendor on their blue eyes.
- stability. A system should be stable enough for home users to use. For people who like to tweak around? Also, but tweaking *can* lead to instability and crashes, that's not the systems' responsibility.
Especially the security and privacy AND open parts are why I wouldn't ever voluntarily (if my job would depend on it, sure, I kinda need money to stay alive so I'll take that) use windows or macos. Sure, apple seems to care about user privacy way more than other vendors but as long as nobody can verify that through source code, no offense, I won't believe a thing they say about that because no one can technically verify it anyways.
Some people have told me that Linux is hard to use for new/(highly) a-technical people but looking at my own family and friends who adapted fast as hell and don't want to go back to windows now (and mac, for that matter), I highly doubt that. Sure, they'll have to learn something new. But that was also the case when they started to use any other system for the first time. Possibly try a different distro if one doesn't fit?
Problems - sometimes hard to solve on Linux, no doubt about that. But, at least its open. Meaning that someone can dive in as deep as possible/necessary to solve the problem. That's something which is very difficult with closed systems.
The best example in this case for me (don't remember how I did it by the way) was when I mounted a network drive at boot on windows and Linux (two systems using the same webDav drive). I changed the authentication and both systems weren't in for booting anymore. Hours of searching how to unfuck this on windows - I ended up reinstalling it because I just couldn't find a solution.
On linux, i found some article quite quickly telling to remove the entry for the webdav thingy from fstab. Booted into a root recovery shell, chrooted to the harddrive, removed the entry in fstab and rebooted. BAM. Everything worked again.
So yeah, that's my view on this, I guess ;P30 -
I think the coolest project I did was a few years ago, it was actually a Minecraft plugin.
I decided to learn Java for Minecraft, and a few months after I started learning Java, I was approached by someone who'd like to work with me to create this full-blown Gun Game style gamemode for Minecraft. I made it clear I didn't have the most knowledge, but I was willing to learn.
We began working on the project, the projects main class was bigger than any project I had worked on. Within a few months, it became one of the more popular plugins out there, even though we were still in an alpha mode. Had nearly 1,000 servers running the plugin, over 10k+ players total testing out the plugin.
Cause of this project, I learnt how to properly organize my code, how to make it efficient, learnt how to network, learned how to properly secure and verify anything being sent by the client, working with dependencies, adding features that can support a bunch of other plugins that other developers had, and a bunch more.
Sadly we couldn't finish the plugin anymore, so we gave someone else the source code who has kept it updated to this day. (I know I didn't provide much insight into what I'm saying and just gave a general overview, got a killer headache.)2 -
It's funny to see how a coworker of mine and me are very similar minded on some privacy stuff. He's a very cool/open guy and just a regular consumer (used the default services etc) but he shares quite some of my views. This is a convo we had today:
*got to the WhatsApp subject somehow*
Him: oh right, you didn't use that haha
Me: yeah 😅
Him: why was that again, privacy reasons or something, right? xD
Me: uhm yes *help*
Him: Well fair enough.
Me: so you'd think I'm right? I mean it uses end to end crypto... (I'm entirely with him in the next few lines but I always approach it carefully)
Him: they veeeery probably have some kinda fucking masterkey.
Me: why'd you think that?
Him: it has over a billion users, the owner is facebook, fb is directly integrated with several mass surveillance programs, they are known to work closely with one particular one, the intelligence interests are way too high for letting such an opportunity pass and after all, THE FUCKER IS CLOSED SOURCE AKA NO ONE CAN FUCKING VERIFY THE CRYPTO NOR THE APP ITSELF.
Me: I agree haha 😅
Him: it's not rocket science, it's modern day mass tracking/surveillance logic :)
I like that guy.5 -
Much-security.nl is down.
No, no hack or whatsoever. I just reinstalled the wrong server through my control panel.
The new blog version will hopefully be up tonight. 'you keep promising that' - I don't have a backup of the old version and I only just started using git so I can only upload the new version (or git pull). Next to that, except for the front-end, everything works now.
😐23 -
Normally when someone calls in and I pick up, they either don't call from an authorized number and get mad when we I don't give information, ask for advice and then say that it isn't logical and ask for a different answer or are just stubborn as a motherfucker.
Then I suddenly get a call from someone who I can verify easily, listens carefully to my answers and thanks me in the end.
Where can I get more of those clients?!15 -
Boss hands over to me an old security audit report and tells me "Go through this and check if all the problems mentioned have been resolved". Quick glance through the report shows all expected issues - SQLi, plaintext transmission and storage etc. I tell him that I need access to the application both from admin and a user with restricted privileges.
He hands me the admin credentials and tells me, "After you login in, just go the "Users" tab. You'll find the profiles of all the users there. You can get the emails and passwords of any user you want from there."
I had to hold back a chuckle. There's nothing to verify. If they haven't resolved storing plain text passwords in the database (AND displaying it IN PLAIN TEXT in the website itself (which to my surprise wasn't mentioned in the audit)), they probably haven't even looked at the report.2 -
One:
Had a stack of harddrives with my important data, two USB drives and a 4.7gb disc, two or three cloud storage accounts.
Needed a restore:
Knocked the stack of hard drives onto the floor (all broken), stood on one of the flash drives, found the other one in a pocket of a pair of trousers which just came out of the washing machine, dvd too scratched to read and couldn't verify my cloud storage account because I lost the password to the connected email account and the backup email account to verify that one didn't exist anymore. Fucking hell.
Two:
Production database with not that much yet but at least some production data which wasn't backupped.
Friend: can I reboot the db machine?
Me: yup!
Friend: what's the luks crypt password?
Me: 😯😐😓😫😲😧😭
End of story 😅
For the record, the first one actually happened (I literally cried afterwards) and that taught me to update my recovery email addresses more often!9 -
Me and co-worker troubleshooting why he can't run the docker container for database.
Me: Check if the port is busy.
Co-worker: To my knowledge, it isn't.
Me: Strange, it just works fine for me and everyone else.
Me: And you're sure you didn't already start it previously?
*We verify that it isn't running*
Me: I'm pretty sure the port is busy from that error message. Try another port.
Co-worker: Already did, it didn't work.
Me: And by any chance restarting your machine won't solve anything?
*It doesn't solve anything*
Me: Alright, I have some work to do, but I'll get back to this. Tell me if you find a solution.
Co-worker: Alright.
*** Time passes, when I get back he has switched to windows, dualboot, same machine ***
Me: I don't think you'll have a better time running the docker image on windows.
Co-worker: Oh, that's not what I'm looking for. You see, I had a database on my windows partition recently and I thought maybe thats why it won't start.
Me (screaming internally) : WTF ARE YOU STUPID, WINDOWS AND LINUX ISNT RUNNING AT THE SAME FUCKING TIME.
Me (actually saying): I don't think computers work like that.
Co-worker: My computer is magical. It does strange things.
Me: That's a logical conclusion.
*** More time passes ***
Co-worker solves the problem. The port was busy because Ubuntu was already running PostgreSQL on that port.
Third co-worker shimes in: Oh yeah, I had the exact same problem and it took me a long time to solve it.
Everyone is sitting in arms reach of each other.
So not only was I right from the start. Someone else heard this whole conversation and didn't chime in with his solution. And the troubleshooting step of booting into windows and looking if a database is running there ???? Wtf
Why was I put on this Earth?6 -
Spotify just asked me for my ZIP code (to verify my family plan again after like a year).
I typed 00000 and they accepted that 🤔8 -
For a week+ I've been listening to a senior dev ("Bob") continually make fun of another not-quite-a-senior dev ("Tom") over a performance bug in his code. "If he did it right the first time...", "Tom refuses to write tests...that's his problem", "I would have wrote the code correctly ..." all kinds of passive-aggressive put downs. Bob then brags how without him helping Tom, the application would have been a failure (really building himself up).
Bob is out of town and Tom asked me a question about logging performance data in his code. I look and see Bob has done nothing..nothing at all to help Tom. Tom wrote his own JSON and XML parser (data is coming from two different sources) and all kinds of IO stream plumbing code.
I use Visual Studio's feature create classes from JSON/XML, used the XML Serialzier and Newtonsoft.Json to handling the conversion plumbing.
With several hundred of lines gone (down to one line each for the XML/JSON-> object), I wrote unit tests around the business transaction, integration test for the service and database access. Maybe couple of hours worth of work.
I'm 100% sure Bob knew Tom was going in a bad direction (maybe even pushing him that direction), just to swoop in and "save the day" in front of Tom's manager at some future point in time.
This morning's standup ..
Boss: "You're helping Tom since Bob is on vacation? What are you helping with?"
Me: "I refactored the JSON and XML data access, wrote initial unit and integration tests. Tom will have to verify, but I believe any performance problem will now be isolated to the database integration. The problem Bob was talking about on Monday is gone. I thought spending time helping Tom was better than making fun of him."
<couple seconds of silence>
Boss:"Yea...want to let you know, I really, really appreciate that."
Bob, put people first, everyone wins.11 -
I'm freaking the fuck out.
After months of learning from bootcamp and on my own, after a month of no resumes replied to, after almost giving up I finally got a job opportunity in front-end web development.
The thing is, I have to pass their online test to verify my JavaScript-fu.
3 hours.
4 tasks.
And I feel like garbage who can't understand even the most basic algorithms.
By the power of Grayskull, I don't think I have the power...
Wish me luck.16 -
Guy: We should build a Blockchain based review website.
Me: Why does it have to use a Blockchain?
Guy: That way we can verify that only real people are leaving reviews and not bots.
Me: That's not really how Blockchains work.
Guy: Blockchain!5 -
To whoever messed with my devrant-client tests by constantly downvoting the posts and them being hidden from the API, you're a cunt and I hope you break your neck falling out a 12 story building. :)
Here's the final test to verify shit works too: https://devrant.com/feed/recent
Edit: it works, get fucked you humid piece of shit.
Edit2: To give context to whoever might be subscribed to me and might or might not have been bombed with notifications:
Was working on the plugin system for the devrant client and async was giving me hell, the links I posted were to test the plugin that first has to execute a $.get and only then can return a linkified rant-text. 8
8 -
I used PHPMailer to send emails to a client's website user. SMTP host is smtp.gmail.com.
web was hosted on Bluehost. I found out that mailer was not working. I enabled verbose output and to my surprise I found out that Bluehost was intercepting my mail and responding with
220-We do not authorize the use of this system to transport unsolicited, 220 and/or bulk e-mail
when i was explicitly using smtp.gmail.com. Not only they were intercepting but also They were trying my credentials against its own smtp server and then showing me that authentication failed.
When i contacted chat they asked me to tell last 4 characters of Bluehost account password to verify ownership.
Dude do they have passwords in plaintext.🤔5 -
There was a time I made an update on one of our client's e-commerce website sign-up page. The update caused a bug that allowed new users to create an account without actually creating an account.
The code block meant to save user credentials (i.e email address and password) to the database was commented out for some reasons I still can't remember to this day. After registration new users had their session created just as normal but in reality they have no recorded account on the platform. This shit went on like this for a whole week affecting over 350 new customers before the devil sent me a DM.
I got a call from my boss on that weekend that some users who had made purchases recently can't access their account from a different device and cannot also update their password. Nobody likes duty calls on a weekend, I grudgingly and sluggishly opened up my PC to create a quick fix but when I saw what the problem was I shut down my PC immediately, I ran into the shower like I was being chased by a ghost, I kept screaming "what tha fuck! what tha fuck!!" cus I knew hell was about to break loose.
At that moment everything seemed off as if I could feel everything, I felt the water dripping down my spine, I could hear the tiniest of sound. I thought about the 350 new customers the client just lost, I imagined the raving anger on the face of my boss, I thought about how dumb my colleagues would think I was for such a stupid long running bug.
I wondered through all possible solutions that could save me from this embarrassment.
-- "If this shitty client would have just allowed us verify users email before usage things wouldn't have gotten to this extent"
-- "Should I call the customers to get their email address using their provided telephone?... No they'd think I'm a scammer"
-- "Should I tell my boss the database was hacked? Pffft hack my a**",
-- "Should I create a page for the affected users to re-verify their email address and password? No, some sessions may have expired"
-- "Or maybe this the best time to quit this f*ckn job!"
... Different thoughts from all four corners of the bathroom made it a really long bath. Finally, I decided it was best I told my boss what had happened. So I fixed the code, called my boss the next day and explained the situation on ground to him and yes he was furious. "What a silly mistake..!" he raged and raged. See me in my office by Monday.
That night felt longer than usual, I couldn't sleep properly. I felt pity for the client and I blamed it all on myself... yeah the "silly mistake", I could have been more careful.
Monday came boss wasn't at the office, Tuesday, Wednesday, Thursday, Friday not available. Next week he was around and when we both met the discussion was about a different project. I tried briefing him about last week incident, he seems not to recall and demands we focus on the current project.
However, over three hundred and fifty customers swept under the carpet courtesy of me. I still felt the guilt of that f*ck up till this day.1 -
The PCs in our school have a software called "Dr. Kaiser" which purpose is to prevent changes to the disk. I thought it's working like DeepFreeze for OSX devices; having a copy-on-write feature or something like that. One day a friend of mine (kinda newbie in hacking) said he wanted to create a backdoor in the system so you can login as the local administrator of the device. He replaced the "sethc.exe" in the windows directory with cmd.exe on a live distro and claimed it was working perfectly. It turned out that "Dr. Kaiser" is indeed loading the default image on startup, but doesn't verify checksums for system files (and also doesn't include the files in the default image). Long story short: You now can open a cmd with System permissions on every PC in the building.
This. Is. Stupid. It should be forbidden to sell this software 😖6 -
Other services : Please type your phone number to verify that it is you. It will be only used for verification process.
Me : Sure, why not? (Happily types in my number)
Facebook : Please type your phone number to verify that it is you.
Me : Hmmm (sees help)
Facebook : It will be used for verification process and will be visible to your friends. You can always change the scope settings.
Me : (reads as...) It will be used for verification process and will be visible to your friends and will be automatically sent to the NSA for free. You can always change the scope settings when you become the CEO of Facebook.
#deletefacebook -
User: Bobby, please update this quality controlled document because I screwed it up.
Me: No there is a process for a reason, multiple people need to sign off on this. Also, we talked about this exact issue a year ago that you did not fix.
User: But its a minor change, several hyperlinks in the Word document need adjusted.
Me: Ok, you do it and submit it through the process again.
User: Can you make the changes to the document? It will take me forever and I'm very busy. I know you can do it much quicker than I can.
Me: I really don't want to edit this document myself. It doesn't apply to my job at all and I cannot verify any of the changes would be correct.
User: Oh it's fine. Make the changes and I'll look over it.
...
I hate my job sometimes.6 -
Just wrote a (PHP based) proxy which can cache resources being requested and serve them to clients.
The idea is that (I'm going to write a firefox add-on for it too, yes) you can install the add-on and any resource (js/CSS, general web resources which would be downloaded off of googleapi's etc) hosted with Google would be proxied through the server running the proxy, meaning that one wouldn't have to connect to the mass surveillance networks directly anymore as for static resources.
I think checksum verify stuff would still work as the proxy is literally a proxy, the content will be identical to the 'real' resource. (Not sure about this one, enlighten me if this isn't true)
Input appreciated!17 -
I was working for a startup that needed to update 300 machines that had just come from the factory. We had to open all 300 boxes and update them one at a time. I made a simple script that would run a folder full of shell scripts then keep track of what it ran so it would not run the same script twice. It made it so we could just plug the machines into the internet, they would query some server, download my program, and run it. It saved me from having to ssh into every machine and run commands. Well the head programmer guy saw what I did and implemented it as the main program that would update the entire machine. I didn't program anything into it to verify updates, the shell scripts did not return any indication of success or failure, and I made it in less than 3 hours. It was supposed to be a temporary program to be used for those 300 machines only, but ended up sticking around for 2 years.1
-
Only slightly tech related. So proud of my mom.
Many years ago I helped her create a Facebook account. As it happens with most older people, she started sharing false news that she saw on her network.
So I taught her how to verify. Reverse image search. To google it and if no real news site talked about it, it was fake.
Anyway, she listened and started learning.
Now she is telling people when they are posting something untrue and I even taught her how to report false news posts.1 -
Two years ago: company exec (Mac fan) buys a Surface Pro to show off our .NET application to customers as he travels. Hands it to me (I build releases) and I iron out a few Win 8 bugs since we'd always used Win 7 before. Get it set up, get to like the device a little, he takes it home... and returns it within 24 hours because he didn't mesh well with Windows. (Again, Mac user.)
8 months later he buys a Surface Pro again. I install our latest release, verify that everything is working as expected with hardware we normally don't use, and give him a controlled setup that will just work when he's at a customer site. Once again, he returns the Surface within 24 hours because he can't get used to Windows.
At least we verified Windows 8 compatibility, I guess.1 -
Never assume you know better
Never assume others know better
Never assume others know
Never assume
Trust, but verify [doveriaj, no proveriaj]5 -
Wanna attend the developer conference?
White and male? Pay half a grand.
Female? Black? LGBTQIA? You get a free ticket!
Seriously, how would they verify if you are gay?
It appears to me that it's easily exploitable.51 -
I think we're going two sides:
For one, more and more technology is being developed/engineered which is even more and more and more intrusive as for personal privacy, I'm genuinely worried how this'll go as privacy isn't just a about not exposing certain things like passwords/bank account details and so on, it's also about being an individual who has their own thoughts, opinions and so on. If we keep taking that away more and more often, society will change and go towards the Orwell scenario (we're on our way there right now). We can change this as software/design/server engineers but that's up to us and I sadly don't see that happening quickly, also due to the 'nothing to hide' bullshit.
Second one is that were going more and more towards open source.
This is a good thing as this:
- gives freedom to devs around the world to improve software and/or modify it to suit their needs.
- gives people the opportunity to look through the source code of softwares in order to verify it as for backdoors and find security vulnerabilities which otherwise can remain hidden for the general public while spying agencies have way more resources to go vulnerability hunting.
For the people who think this isn't a good idea (even more open source), without it we'd be completely fucked as for moving forward/security/privacy. (I can give examples if wanted).3 -
So I just created this Registration GUI (part of a bigger app) for my uni project and was demonstrating how good the app was to all my friends.
Suddenly someone came and said let me verify this. I said go on with a doubtful mind. Obviously I had some verification for all the fields in the GUI but I was closely watching him.
He signed up with this email: " @ . "
😞10 -
!!oracle
I'm trying to install a minecraft modpack to play with a friend, and I'm super psyced about it. According to the modpack instructions, the first step is to download the java8 jre. Not sure if I actually need it or not, but it can download while I'm doing everything else, so I dutifully go to the download page and find the appropriate version. The download link does point to the file, but redirects to a login page instead. Apparently I need an oracle account to download anything on their site. stupid.
So I make an account. It requires my life story, or at least full name and address and phone number. stupid. So my name is now "fuck off" and I live in Hell, Michigan. My email is also "gofuckyourself" because I'm feeling spiteful. Also, for some reason every character takes about 3/4ths of a second to type, so it's very slow going. Passwords also cannot contain spaces, which makes me think they're doing some stupid "security" shenanigans like custom reversible encryption with some 5th grade math. or they're just stupid. Whatever, I make the stupid account.
Afterwards, I try to log in, but apparently my browser-saved credentials are wrong? I try a few more times, try enabling all of the javascripts, etc. No beans. Okay, maybe I can't use it until I verify the email? That actually makes some sense. Fine, I go check the throwaway inbox. No verification email. It's been like five minutes, but it's oracle so they probably just failed at it like everything else, so I try to have them resend the email. I find the resend link, and try it. Every time I enter my email address, though, it either gives me a validation error or a server error. I try a few mores times, and give up. I try to log in again; no dice. Giving up, I go do something else for awhile.
On a whim later, I check for the verification email again. Apparently it just takes bloody forever, but it did show up. Except instead of the first name "Fuck" I entered, I'm now "Andrew", apparently. okay.... whatever. I click the verify button anyway, and to my surprise it actually works, and says that I'm now allowed to use my account. Yay!
So, I go back to the login page (from the download link) and enter my credentials. A new error appears! I cannot use redirects, apparently, and "must type in the page address I want to visit manually." huh? okay, i go to the page directly, and see the same bloody error because of course i do because oracle fucking sucks. So I close the page, go back to the download list, click the link, wait for the login page redirect (which is so totally not allowed, apparently, except it works and manual navigation does not. yay backwards!), and try to log in.
Instead of being presented with an error because of the redirect, it lets me (try to) log in. But despite using prefilled creds (and also copy/pasting), it tells me they're invalid. I open a new tab container, clear the cache (just to be thorough), and repeat the above steps. This time it redirects me to a single signon server page (their concept of oauth), and presents me with a system error telling me to contact "the Administrator." -.- Any second attempts, refreshes, etc. just display the same error.
Further attempts to log in from the download page fail with the same invalid credentials error as before.
Fucking oracle and their reverse Midas touch.10 -
Before shutting something down, verify that its the right one ;)
A colleague was testing some performance setting on a server and needed to restart the network driver so he disabled it and was going to enable it when the remote session died ;)
Fast 30 min trip to the datacenter to enable network card.2 -
I've just noticed an app review that I've given and would fit right into the wk123 (that's the insult one, right?).
"Biggest pile of junk that I've ever seen. You have one job! To register the fucking phone number (which you could get with Phone permission) and verify it (which you can do with the SMS permission) and you should either have the user do that once upon installation or you automate it entirely so that it can run in the background! You can fully automate this, and it's not that complicated that it needs 10 whole seconds of loading time in between! Heck, this pile of crap can't even continue into the main view after entering the verification code! You haven't published the source code (and maybe that's for the best) but if it was, I'd probably immediately get cancer by viewing your crappy spaghetti code. Dear developer, please take a step back and (re)join the PC tech support guys. You have no place in the development world."
To top it all off, that app currently only needs phone permission to verify my number (at least they've done that much). So I figured, I've already gone through that authentication flow so let's remove that permission to abide by the principle of least privilege.
Except that the fucking crapp just goes through the "requires phone permission" shit again whenever that permission removal happens. Fucking piece of garbage!!! That such spaghetti code fuckers even have a job, it boggles my mind.4 -
Let me paint you a picture.
It's the day after code freeze. Code has been branched. It's time once again to verify tickets and run smoke check so we can begin our 3 days of blitz testing before we deploy.
As a team we all have roles to play in this process. Yet, every stinking release it is like pulling teeth to get everyone to take the initiative and verify tickets and run smoke check. Our principled engineer even reached his limit this morning and blew up on everyone.
When you are being paid good money to do a job, you need be an adult, be responsible, step up and do your job!2 -
Stakeholder: In user profiles, I want users to be able to renew gift memberships for their giftee.
Me: ???
SH: For example, if I buy a gift membership for you and it expires or is about to expire, then I want to be able to renew it for you.
Me: Typically, gifts aren’t the gifter’s responsibility to manage. There’s no reason for you to be able to manage my membership from your account, even if just to renew. You’re opening up Pandora’s box here. If you let users renew for giftees, you’ll eventually have a user ask if they can cancel the giftee’s membership because they got into a fight and want to stick it to the giftee.
SH: But our users aren’t using the gift membership sales flow correctly. That results in all sorts of data issues for our reporting services and we spend so much time fixing it by hand.
Me: Your sales flow is confusing. The website asks users to verify membership for a giftee in case the giftee has or had a membership. How it the gifter supposed to know that? You’re trying to make things easier for you, but you’re expecting the user to know that and comply. That’s unrealistic.
SH: But there must be a something you can do.
Me: No.9 -
Amazon: you're logged into 53 devices.
Me: ooooh Kay, since when do I have that many devices. let's sign out of em all and change the password for some piece of mind.
Spongebob: * a few hours past *
Spam email: someone in the US has logged into your account - click here to verify through some random URL that doesn't even contain "Amazon" in it 🥳
-
I suddenly have that feeling Amazon sells you're account setting changes and not just your personal details.2 -
Fucking IT and their self signed corporate proxy SSL bullshit getting in the way of anything that needs to verify SSL requests,
Fuck you for making my day a slow and miserable day and having to resort to forcing rest apis and SDKs to work over HTTP instead, all in the name of “Security”.2 -
Starting my new bot experience together with Discord.
Discord is kinda easier than LINE. You had to create facebook accounts or fake lots of telephone numbers to be able to verify your bot account. They also kept changing the endpoints to avoid people using their bots.
Discord is the opposite. Discord loves bots. And that's why I start feeling love towards Discord. 8
8 -
SM = Scrum Master
SM: "Card #130, you added a comment saying you aren't going to do update the report?"
Me:"Yea, I explained why in the comment"
SM: "Product owner wants it."
Me: "Product owner isn't the manager using it. I talked with Steve, he said the data is accurate and they have to go to the database anyway to verify the error. That report has no way of knowing the message logged could be a false positive."
SM: "That's not our job to decide. If the Product Owner wants the feature, we add the feature."
Me: "It is absolutely is our job. Steve is the user of the report. I could really care less what the product owner said. The only reason he created the card was because Steve told him a specific error logged could be a false positive, and only happens, maybe, once a month. I'm not wasting my time, Steve's time, or this project's time on wild goose chases."
SM: "I'll schedule a meeting this afternoon to discuss the issue with the product owner. Don't worry, if you can't figure out how to filter out the false positives, I'll assign the ticket to me."
fracking fracking kiss ass. I swear, if he goes behind my back again ....I... deep breath....ahhh...OK..Thanks devrant. Work place incident diverted.6 -
We should disable the “verify that you are a human” captcha for a day and see if aliens try to contact us via internet.3
-
Funny thing just happened. I called my bank to verify my card with Apple Pay. Here’s how it went:
> Calls bank with number supplied by phone.
> “Thank you for calling [Bank] Bank!”
> ...
> A minute passes and still ringing
> wtf.jpg
> About thirty seconds in and the ring seems fainter than before.
> [2:00] is it just me or is my speaker dying...
> [3:00] no, it’s definitely getting quieter.
> [3:30] why is no one picking up???
> [4:00] now it’s so bad I have to hold it to my ear
> [4:30] now it’s blending in with the white noise
> [4:45] yeah, no. This is only static now.
> [5:00] this’ll be good for DevRant...
> calls again
> same thing happens
> ohwell.mov
Let’s try again tomorrow, I guess.
Edit: like always, I forgot the picture 8
8 -
Fuck recruiters, they are the scum of the earth. I just had one contact me out of the blue about two opportunities with companies I'd never heard off. As I knew nothing about the companies I started asking questions around who they were and what they were looking to do. He suddenly gets all defensive and refuses to answer my questions, then follows up with an email accusing me of being an "underhanded recruiter" looking to poach his clients. Sorry mate, you got in contact with me you absolute fuckwit. Without people like us you wouldn't even have a bloody job you fucking vampire. For someone that supposedly specialises in the tech sector, I had to point out that if he really doubted who I was he could drop my name into StackOverflow or github to verify that im a developer. Recruiters - they're all fucking leeches.4
-
So now I have to pay taxes because I'm employed. Fair enough, sounds reasonable.
Go to the government's diseased scrotum of a webapp to tramit some ID stuff and shit. All good. Then I go to the bank, so I can open an account, so that I can receive the money, so that I can pay the government.
What happens? The guy at the bank tells me he can't access my ID, so he can't open my account. Understandable. I go once again to the gonorrhea infected maggotsoup that is the government's mother fucking webapp. THEY BLOCKED MY ID.
Problem? I had to attach images of some documentation, they say the images are illegible. I try again with a clearer image, ten fucking times the resoulution.
Is that good enough? NOOOOOOOOOO0=00=======0===000 oo O O OO O O, I am the government, my sole purpose in life is to be a dick in your asshole.
So what do I do? I, calmly, grab the documentation, go to the nearest office, and politely explain the situation to the dude behind the counter. Surely, he can verify himself that my papers are in order, no?
NO. HE CANNOT.
IT CAN ONLY BE DONE THROUGH THE APP.
ARE YOU FUCKING KIDDING ME.
WE ARE DOOMED AS A SPECIES.
LISTEN TO ME, DEAR GOVERNMENT.
AND DEAR TAXMEN.
AND ASSOCIATED BUREAUCRATS.
PLEASE HEAR ME OUT.
IF YOU DON'T UNBLOCK MY ID, I CANNOT OPEN A BANK ACCOUNT.
IF I DO NOT HAVE A BANK ACCOUNT, I CANNOT RECEIVE ANY MONEY.
IF I CANNOT RECEIVE ANY MONEY, THEN I CANNOT PAY **YOU**.
SEE HOW THAT WORKS?
ITS OK.
JUST SUSPEND THE PAYMENT I OWE.
YOU KNOW, THE ONE THAT'S DUE IN A FEW DAYS??
OH RIGHT!
YOU'RE STILL ASKING ME FOR THAT MONEY.
SILLY ME.
I THOUGHT I MAY BE EXEMPT.
SINCE YOU YOURSELF HAVE FORBIDDEN ME FROM PAYING.
ARRHGHHGGHGHGHGHGH!!!!!!!!
YOU IRREDEEMABLY STUPID FUCK.10 -
Had an idea for an app. I started writing the prototype in Node since I just had a simple API in mind. Wanted to have some very basoc crud functionality going and then hook up a nice interface to it. It has to do with logistics and analytics so I just wanted to start sketching something small, and being that i have been successful in doing an API like this in the pass with node and mongo for a local company I said why not.
I have finished a good chunk of it. Gotta love that js productivity. But what tripped me out about it was:
Check how big the folder size is: 387mb
EXCUSE ME??!!
I tripped, there was no way in hell this shit was that heavy. I am basically using Koi(to give it a whirl instead of express, gotta start testing koi sometimes right?) And some joi with morgan and winston. That is it. I am using mongo since legit its the only one i know, even with that there really can't be that much right?
Check node_modules size.....10mb....wtf? What
Wait
Did it?
Sure as shit....forgot that i was storing the mongo data folder inside the app's root folder.
This would have been nothing if it would have taken me 30 seconds to figure it out.
I was losing my mind for 30 mins before i decided to properly verify
I need some sleep5 -
Finally finished the screwdriver followup ticket. I think.
I spent almost two full days (14 hours) on a seemingly simple bug on Friday, and then another four hours yesterday. Worse yet: I can’t test this locally due to how Apple notifications work, so I can only debug this on one particular server that lives outside of our VPN — which is ofc in high demand. And the servers are unreliable, often have incorrect configuration, missing data, random 504s, and ssh likes to disconnect. Especially while running setup scripts, hence the above. So it’s difficult to know if things are failing because there’s a bug or the server is just a piece of shit, or just doesn’t like you that day.
But the worst fucking part of all? The bug appeared different on Monday than it did on Friday. Like, significantly different.
On Friday, a particular event killed all notifications for all subsequent events thereafter, even unrelated ones, and nothing would cause them to work again. This had me diving through the bowels of several systems, scouring the application logs, replicating the issue across multiple devices, etc. I verified the exact same behavior several times over, and it made absolutely no sense. I wrote specs to verify the screwdriver code worked as expected, and it always did. But an integration test that used consumer-facing controller actions exhibited the behavior, so it wasn’t in my code.
On Monday while someone else was watching: That particular event killed all notifications but ONLY FOR RELATED EVENTS, AND THEY RESUMED AFTER ANOTHER EVENT. All other events and their notifications worked perfectly.
AKL;SJF;LSF
I think I fixed it — waiting on verification — and if it is indeed fixed, it was because two fucking push event records were treated as unique and silently failing to save, run callbacks, etc.
BUT THIS DOESN’T MATCH WHAT I VERIFIED MULTIPLE TIMES! ASDFJ;AKLSDF
I’m so fucking done with this bs.8 -
Jesus christ what is wrong with this one
12: Colleague deploys something to production (with a second pair of eyes)
14: Asks me why other team isn't seeing the result, I ask whether they have monitored the logs, they have not
17: They finally read the logs and find the problem, change window has ended so tomorrow there's another attempt
Today, they deployed again around 10 and then went away because they had some private responsibilities. Never looked at the logs, never bothered to verify if anything still worked. Just dropped it in a chat.
10 years older than I am, how can you be so irresponsible4 -
Fuck apple for making it as hard as fuck to sign in to my fucking apple id. Because my ex wife was my "trusted" number, I couldn't get an authentication code. Tech support told me it would take 3 days to reset my password.
After 3 hours of fucking around, I finally was able to reset my password.
I've been trying to get my kids to watch stupid Indiana Jones for years. They finally agreed. After going through 3 hours of BS so I could buy the movie, we start watching it. Literally, as the boulder is rolling down toward Dr. Jones, the movie stops suddenly so that Apple can verify my purchase!
Then, it asks me to buy it again!4 -
This fcktard client that insist on using an iframe and demands support for browsers like IE7. You are costing me years of my life.
Fucking fuck of a Microsoft trying to protect people against tracking from 3d parties in an iframe in random ways in some versions of IE7. Or IE11 in IE7 compatibility mode.
If you are going to refuse sessions just do it! I got a fucking check and fix for that. Because these fuck faces friendly people at Apple like to refuse sessions on iPads and iPhone too. But we worked that out, because they are at least consistent. So a few dirty little hacks made it all Okay.
But no, Boo Hoo I'm Microsoft and I will throw a tantrum. I like my browsers to be like an magican, instead of an usefull piece of software. If you look in this page, or look here we got them. I got your sessions, safe and secure.
But when you need me, to verify that the user is allowed to access data we do a little hocus pocus and now they are gone. Nowhere to be seen or found again. Fun times free fucking magic shows all day long.
It's morning but maybe its time for a bottle of scotch. Maybe if I'm in the state as this browser. Where I don't know what I'm doing because I'm shitfaced drunk it will start working.
When in Rome do as the romans do.6 -
"Oh, let's delete no-reply@domain.tld because that's not needed by anything"
Stupid fucking clients...
Now users can't verify their accounts. Nice!1 -
Don't you just love it when a customer reports a bug in their live system and it's really urgent to correct it; then you go out of your way to fix it ASAP and deploy it to the staging system for them to verify. Three weeks later the customer has still not tested the bugfix...1
-
"Let the developers consider a conceptual design,” the King said, for about the twentieth time that day._
“No, no!” said the Queen. “Tests first—design afterwards.”
“Stuff and nonsense!” said Alice loudly. “The idea of writing the tests first!”
“Hold your tongue!” said the Queen, turning purple. “How much code have you written recently, anyway?” she sneered.
“I won’t,” said the plucky little Alice. “Tests shouldn’t drive design, design should drive testing. Tests should verify that your code works as it was designed, and that it meets the customer’s requirements, too,” she added, surprised by her own insight. “And when you drive your tests from a conceptual design, you can test smarter instead of harder.”4 -
I got a new debit card from my bank, jumped online, to activate my new card.
I see a picture of my card, with the last 4 digits of my account number show. A big "activate" button right next to it. Sure thing. Click the button, and guess what piece of information I need to verify I am the true owner of the card. Fucking last four digits.
Fucking hell - you just showed me the digits a page ago.2 -
Can you really trust the security features on your device?
Can you really verify that no one is looking at what you're doing all day, in your house or out and about?
What if I am the one looking at your naked ass right now?20 -
Server Admins:
Don't fucking make changes to the server configuration and assume that it's going to be functional.
Stop fucking breaking shit on client servers then leaving it for the rest of us to clean up.
Verify your goddamn work before you tell them that their issue is resolved.7 -
So after 6 months of asking for production API token we've finally received it. It got physically delivered by a courier, passed as a text file on a CD. We didn't have a CD drive. Now we do. Because security. Only it turned out to be encrypted with our old public key so they had to redo the whole process. With our current public key. That they couldn't just download, because security, and demanded it to be passed in the fucking same way first. Luckily our hardware guy anticipated this and the CD drives he got can burn as well. So another two weeks passed and finally we got a visit from the courier again. But wait! The file was signed by two people and the signatures weren't trusted, both fingerprints I had to verify by phone, because security, and one of them was on vacation... until today when they finally called back and I could overwrite that fucking token and push to staging environment before the final push to prod.
Only for some reason I couldn't commit. Because the production token was exactly the same as the fucking test token so there was *nothing to commit!*
BECAUSE FUCKING SECURITY!5 -
When the free wifi you just registered for sends an email to verify your account... but you need the wifi to get that email.2
-
For about 3x years now, we have had 3x generic work email addresses that are used as microsoft accounts for office 2016 licenses.
(The company is dragging its heels on getting office 365 so MS like to make our lives hell.)
Suddenly we can’t get office updates... and when we sign in to see why, it says that because we are apparently only 3 years old we need our parents permission to use the account or we’ll lose access by September.
Never were we forced to enter a DOB when setting the accounts up!!! So it used the account setup date instead.
It turns out that we can’t change our DOB ourselves, as we are a ‘child’ and need a parents permission.
Fine.
I access my personal account and follow the instructions to add the 3x email addresses as my children so i can change the DOB.
‘Ha ha’ i hear microsoft saying, ‘it doesn’t work that way!!’
No, In order for the parent to verify their child’s identity, they are charged 0.50c per child!
Wtf!!
Doesn’t cost a lot but come on Microsoft!!
It’s that, or submit ID, which obviously wont work for a generic support@ email address like we have.
So annoying and we don’t know what to do.
Wonder how much MS are making out of this...2 -
My best code review experience?
Company hired a new department manager and one of his duties was to get familiar with the code base, so he started rounds of code reviews.
We had our own coding standards (naming, indentation, etc..etc) and for the most part, all of our code would pass those standards 100%.
One review of my code was particularly brutal. I though it was perfect. In-line documentation, indentation, followed naming standards..everything. 'Tom' kept wanting to know the 'Why?'
Tom: 'This method where it validates the amount must be under 30. Why 30? Why is it hard-coded and not a parameter?'
<skip what it seemed like 50 more 'Why...?' questions>
Me: "I don't remember. I wrote that 2 years ago."
Tom: "I don't care if you wrote it yesterday. I have pages of code I want you to verify the values and answer 'Why?' to all of them. Look at this one..."
'Tom' was a bit of a hard-ass, but wow, did I learn A LOT. Coding standards are nice, but he explained understanding the 'What' is what we are paid for. Coders can do the "What" in their sleep. Good developers can read and understand code regardless of a coding standard and the mediocre developers use standards as a crutch (or worse, used as a weapon against others). Great developers understand the 'Why?'.
Now I ask 'Why?' a lot. Gotten my fair share of "I'm gonna punch you in the face" looks during a code review, but being able to answer the 'Why?' solidifies the team with the goals of the project.3 -
Google Business Profile is probably not meant for developers. "Help customers find your business by industry." Dev: set primary category to "Web Developer". Google: We didn't understand your category. Please select from the suggestions that appear when typing. Dev, typing: "Web D"... Google suggests: "Web Designer, Web hosting company, Well drilling contractor, Waterbed shop". Okay, Google, nevermind.
Google: "Update your customers. Keep your customers up to date about your business!" Dev clicks "add update", adds info about that customer should use different phone number temporarily due to broken phone. Google: "Your post has been removed from your Business Profile on Google because it violates one or more of our post content policies." Okay Google, at least you let me add an additional phone number on my profile without requiring to verify my primary number that I currently have not access to. Anything else?
Google: "Claim your €400 free advertising credit" Dev: clicks "claim credit" Google: "To access this Google Ads account, enable 2-Step Verification in your Google account." How to combine idiocy and deceptive patterns in a single UI: Google knows! Apart from their search engine, their unique business advantage is simple that they suck a little less than Apple and Microsoft. Sorry, not a day to be proud of our profession, once again.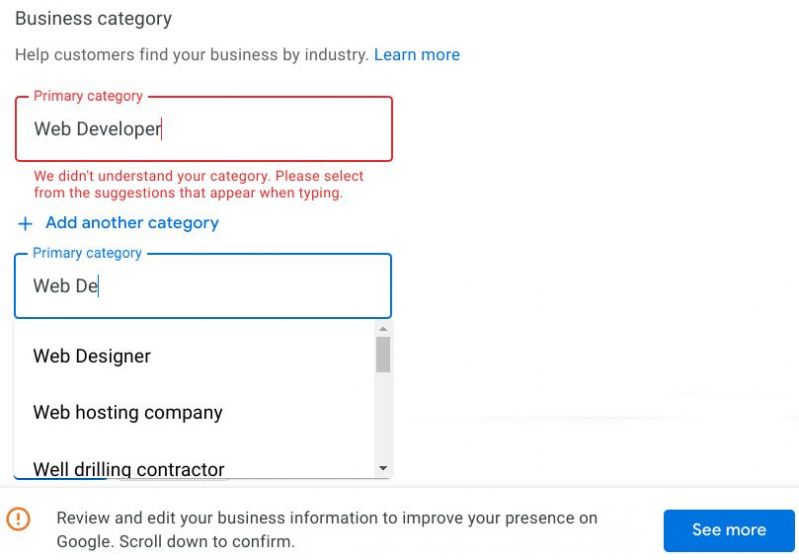 5
5 -
Here comes the story how I became a DevRanter.
When I was young, I built an expensive gamer-machnine, so I had to crack games. I Got used to computers, so I startet an apprenticeship in IT. I finished with good grades. I left everything and everyone behind and moved in a city, found a parttime job as a PHP developer and started studying CS. After 5 years doing work as developer, studying CS, creeping around as soldier, I finally finished and graduated. After a few months working fulltime (same job), as my life began to settle down and I got bored.
A flatmate (also CS) laughed his ass off about something, then he introduced me to DevRant. It became part of my life to read DevRant, to overcome boredom. But there are not enough new Rants.. I'm f'cked. OK, I resigned my Job, and my flat and signed up for the BS in natural scinces at university in an even bigger city. I will again leave everything behind to begin a new life. Now I'm planing to freelance to pay the bills and challenge me again. Wish me luck :)
So I am beginning this new life with writing this story, how i became a dev. I klick Post, and bang! "please verify your email before ranting.. blah" I got no mail, no span, nothing. Resend.. wait.. nothing. I WAS BORED AGAIN!! FUCK YOU MAIL-SERVER, WHY CAN'T YOU SEND AN EMAIL WITHIN SECONDS OR MINUTES, WE ARE IN 21ST CENTURY AND THE INTERNET CONSISTS MAINLY OF OPTIC FIBER CABLES!!
And this is, dear DevRant community, how i become a Ranter, just then when I wanted to Post my first story.4 -
*making payment online*
Website: Your bank wants to verify something. Redirecting to their page
Me: fair enough
Bank: we are increasing security by sending you a security code via text...
*bank redirects me before I can finish reading*
Website: payment successful
Tf kinda security is that???1 -
\n and \n\r
What a fuckton of issues those two characters brought me today while attempting to verify a signed file.9 -
RANT:
Google is just a steaming pile of shit!!
I've recently installed LineageOS onto my phone and wanted to degooglify my life.
So my current Smartphone doesn't have any GApps installed and I get along fairly well.
Should I need anything, I should just be able to use it in my browser right?
RIGHT?
Nono!! As soon as I want to log into a third party Service using Google (older acccounts with the other choice only being Facebook) I need to "verify my identity". And the only option are my old smartphone who still have Gapps on it but are slow and don't accessible when I'm away!
For those who say: "Google is just beeing secure. They don't want anyone to steal your account.". I USE 2FA AND HAVE BACKUP CODES.
BEFORE DEGOOGLING MY DEVICE IT NEVER ASKED SUCH A THING!!! WHAT A PILE OF SPYING SHIT!!!
And the best part, after I remotely started my PC at home and just want to take a screenshot of the message for this post before just using a working session, the message didn't appear.
Somehow google decided that me logging in 15 mins later (same ip) proves my identity?!?!?!
IF THIS CAN BE ATTRIBUTED TO AI. FUCK THIS SHIT. GOOGLED SHOULD BE TREATED LIKE AN ONLINE CASINO BECAUSE THE CHANCE OF JUST GETTING LOGGED SEEMS COMPLETELY RANDOM!!!
(I also had this prior when using my smartphone browser. There I couldn't "circumvent" this and I was at home. But having this shit on my browser which should've a session is unacceptable.)7 -
dude@milotic:~$ vncpasswd
Password:
Verify:
Password too long - only the first 8 characters will be used
WHAT1 -
TL;DR: Google asked me to PROVIDE a phone number to verify connection from a new device, on the said device.
Yesterdayto log into my work Google account from my personal laptop to check emails, calendars update and so on. I opened up a private navigation window, went to Google sign-in page, entered my credentials, all is well.
Google then decided to "verify it's me" and prompted me to PROVIDE a phone number (work account without work phone means no phone number set up) so that they can send a verification code to the number I just provided to make sure the connection is legit.
Didn't want to do that, clicked "use another method" and got asked to fill the last password I remember, which would be my current password thanks to my trusty password manager. After submitting, I'm prompted with an error saying I have to contact my admin to reset my password because they can't log me in with my CURRENT password.
I ain't gonna do that, so went back to login page, provided my phone number, got the code, filled in the code, next thing I know I'm browsing through my emails.
What the duck? Could have been anybody giving any phone number. So much for extra security.
Also don't care that they have my phone number, the issue is more about the way used to obtain it: locking me out of my account and having no other way of logging in.6 -
Quick vent...
I just hate how other people in my organization keep blaming the systems instead of taking a second to verify if the data that they are feeding the system is accurate!!
It's like adding "4+5" in a ti83 and blaming the TI engineers because the result is not the "4" they wanted! 🤨 -
https://github.com/serde-rs/serde/...
Shit like this makes me wonder, wtf is going on in some developers heads.
TL;DR: serde devs sneakily forced precompiled libraries onto all of the users of the library using serde_derive without an obvious way to verify, what's in this binary and no obvious way to opt out, essentially causing all sorts of havoc.
The last thing i want in a fucking Serialization library (especially the most popular one) is to not being able to verify if something shady is going on or not. All in the name of compilation speed.
Yeah compilation speed my ass.
The worst thing of it all is, even if i decide to drop serde as a direct dependency, it will still download the binary and potentially use it, because of transient dependencies. But i guess, i will try to disable serde wherever possible and implement my own solution for that. Thanks but no thanks.
This is so fucking stupid, it's unbelievable.20 -
Interesting thing. Ya know how when turning on your phones hotspot it has to verify that you are in fact allowed to use a hotspot. Well if you have Unlimited Data like myself, hotspotting is not allowed. HOWEVER, if you spam the hotspot button, it after several tries, gives up and lets you hotspot. THIS IS MY LITTLE TRICK. NO BUG BOUNTY. BESIDES, youd need my carrier.10
-
Printer strikes again!
Boss is pissed off that the printer is not working for him but works for the accounting department. He slammed the "photocopy cover thingy" with a "putain" (which I doubt will make it work). I had told him multiple times last week that the credentials he entered is wrong and he needs to verify that first. He will hopefully eventually realise it. Till then
Printer: 01
Human: 002 -
What the fuck is wrong with Google?!!
Trying to log into Gmail.
Forgot password.
Gmail: To reset, code from authenticator app is required.
Me: Super. Good thing I set it up.
Enters code.
Gmail: Recovery email.
Me : Uh... Forgot that too.
Gmail: Some email address to communicate.
Me: Super!
Enters some other email address.
Receives mail with a link.
Me: Finally!
Opens link
Gmail: "When did you create your account?"
Me: Uh... If I had that kind of memory, we wouldn't be dancing right now.
.
.
.
Gmail: Sorry we couldn't verify you.
WHAT THE FUCK, GOOGLE?!
What sort of sadist play is this?!
Dropped them a mail to get access back. Got a link in the auto reply that explains how to repeat the above process. WTF?!
What the actual fuck?!9 -
fucking zoho and their fucking sign up and authentication process.
they need a mobile phone number for the sing up, alright fine, I provide. but after submitting the form, nothing fucking happened and i am redirected to the initial sign up page. fuck you.
try again and guess what, said my phone number is already used and i can try sign in with it. ok alright, i try to sign in using my number and my password. guess what? i am redirected back at the initital sign up form page. fuckkkkkkkkkk.
i try again with another number. and then this time, guess what? said the fucking email is already existed. jesus fucking fucking christ.
browse around their help desk and found this. https://help.zoho.com/portal/kb/...
sure I follow the advice and guess what? yeah i'm redirected back to the FUCKING GOD DAMN same page again.
I gave up and wanted to send them a reply on their help desk and try to log in using one of my other existing zoho accounts. GUESS WHAT? THEIR HELP DESK LOG IN IS NOT WORKING. ARRRRRRRRRRRRRRRRRRRRRRRRRRRRRR.
I click "Sign In". Login as User or Login as Agent dropdown appear. I click Login as User since my user account is already logged in. It nothing happened. It flashed and I am back at the help desk thread with no changes. It is still "Sign In" at the top. I fucking give up.3 -
Man....I keep up with this strange love hate relationship I have with Python....
Last night it was python that literally wrote my homework: define all possible equivalent partition tables with cause and effect analysis and boundary value checks for a program. The whole thing wrote itself and all I had to do was verify the inputs. Something that I was able to do using jupyter with pandas and numpy. On one hand, I despise the lack of static typing and use of whitespace as a block delimiter. On the other I cannot but help feeling a high level of gratitude over the language and its high availability and ease of use for this.
Sure, I could have used other tools, but this language has dominated hardcore in this regard enough to the point of not considering it being a crime against humanity.3 -
As a legal thing at work I need to have someone verify my citizenship by filling out a form for my I-9. They ask the person for their title. My husband can’t be serious, so he put that his title is “Keeper of the Swans”.
Here’s hoping I don’t have an awkward convo with legal over the validity of verification by a man claiming the title “Keeper of the Swans”
In his _defense_, the form didn’t let him leave “Title” blank.9 -
I've noticed looking at the card exit of a building that most people a) just carry their laptop without putting it in the backpack because the carpark is a jump away anyway, b) that stickers on said laptops can leak your infrastructure
No idea what made me interested in that, but if you take the average of people's laptop stickers (sadly not everybody had their laptop or maybe even a laptop at all, so I've got just 20) - you could probably tell what tools and what services the company is running.
Could be a funny coincidence and I was able to verify later by googling their company, but it's an interesting non trackable way to know what services and tools need to be exploited/emulated to possibly gain access to some high security network.
I feel like somebody had to have a talk/presentation about this, so I wonder, had anybody else seen something like that? or how far could this actually go?5 -
After seeing it in a demo, the customer didn't like their first loading gif and they sent another one.
I go to open it to verify it's good and Gimp won't open it; Chrome, Firefox, IE, even MS Paint fails miserably. Eventually I ran file on it and it's an html doc.
So I changed the extension and loaded it up. He saved his slack window as a gif. -
Hmm. So have you ever argued in a job interview? Like really standing your ground? In a technical interview?
Today I had a live coding session with a company I'm interested in. The developer was giving me tasks to evolve the feature on and on.
Everything was TDD. Splendid!
However at one point I had to test if the outcome of the method call is random. What I did is basically:
```
Provider<String> provider = new SomeProvider("aaa", "bbb", "ccc", "ddd", "eee", "fff")
for(int i=0; i<100; i++) {
String str = provider.get();
map.put(str, incrementCount(str));
}
Set<Integer> occurences = new HashSet(map.values());
occurences.removeIf(o -> o.equals(occurences.get(0)));
assertFalse(occurences.empty());
```
and I called it good enough, since I cannot verify true randomness.
But the dev argued that this is not enough and I must verify whether the output is truly random or not, and the output (considering the provider only has a finite set of values to return) occurences are almost equal (i.e. the deviation from median is the median itself).
I argued this is not possible and it beats the core principle of randomness -- non-determinism. Since if you can reliably test whether the sequence is truly random you must have an algorithm which determines what value can or cannot be next in the sequence. Which means determinism. And that the (P)RNG is then flawed. The best you can do is to test whether randomness is "good enough" for your use case.
We were arguing and he eventually said "alright, let's call it a good enough solution, since we're short on time".
I wonder whether this will have adverse effect my evaluation . So have you ever argued with your interviewer? Did it turn out to the better or to the worse?
But more importantly, was I right? :D20 -
My terminal (Tilix) didn't have a header bar for a quite a while now. I had grown to live without it even though I missed looking at the terminal title to figure where I was.
Today I my hand accidentally hit F11 and I was in for a surprise. I actually exclaimed aloud in the office.
I waited to test, confirm and verify that the header bar itself was not a bug before I facepalmed myself -
I am now receiving fertility information about a random person in the US because they thought it would be an excellent idea to use some random mail address (my mail address) to register for a fertility site instead of their own.
For anyone interested they will be highly fertile in about 12 days. Lets see if they succeed and unregister from the service then.
For the love of God please verify mail addresses of user before registration! Please!
Related rant: https://devrant.com/rants/9686149/...6 -
WTF IS WITH ALL THESE MESSAGING SERVICES... ALL NEED TO LOGIN OR VERIFY USING MY PHONE. WHAT IS IT'S LOST OR BROKEN....
DUMBASS IDIOTS....14 -
You work as IT for a private investigation agency.
You find YOUR name in a list of investigated people.
😲😲😲😲😲
You verify the Insurance ID.
😱😱😱😱
It's an homonym.
😂😂😂😂😂 -
Google simply can't knock off harrassing their users with security theatre.
A friend of mine has a small personal YouTube channel. He has recently been bombarded with several phone verification requests a week: "Verify it's you. To continue your session, complete a brief verification. This extra step helps us keep your account safe by making sure it’s really you. "
While frequent verifications may be understandable on YouTube channels with millions of subscribers, channels with only a few dozen subscribers are not attractive hacking targets. A verification would be justified before a potentially harmful action such as deleting videos or deleting a channel. But not for normal everyday use.
What's next? Will they ask users to "verify it's them" every ten minutes, "just for extra security"? Just to verify that it is "really, really, really, really, really" them?
It's not security. It's security theatre.
Sorry, Google, but users are not in the mood of doing a phone verification every other day.
Has this been Google's perverted wet dream all along? 1
1 -
Today when registering myself for a website I was asked to validate my email address. Literally I was sent an email with only "Please verify your email" in the body. So I responded with "ok". Lets see how long it takes for them to realise their mistake.3
-
God I hate when dev work gets all political.
Our team had a technical meeting with a difficult partner/customer, that wants to connect to our internal service, so we are writing an Integration Service for this.
Apparently the project is very important on both sides and highly political so in the meeting there was a member of the Board of directors of them. We just wanted to check one feature to verify they can connect, etc.
After some minor bugs showed up, that guy goes on ranting about how this is all a joke ("Verarschung" literally) and how we did not deliver all features yet as promised (Note : that was not promised) and basically indirectly personally attacked us, our company and our team.
It's incredible how such assholes can stay in such positions.5 -
Got contacted by a potential client whose job I had bid on. Spent a couple of minutes frantically studying his specification and preparing my discussion.
Turns out the job was fake. He wanted me to create a new profile, verify it with my white European identity and then let him use it to approach Western clients.
The best part? I'm as Asian as he is, and all my profile pictures bear witness to that fact.
Some people smoke some really special stuff...1 -
Company started automated testing recently, and the devs need to review the test scripts.
The tester assigned to my component writes script to trigger button click and nothing else to verify the result.
I couldn't even. I just left work for the day. -
The global joke of Information Security
So I broke my iPhone because the nuclear adhesive turned my display into a shopping bag.
This started the ride for my character arc in this boring dystopia novel:
Amazon is preventing me from accessing my account because they want my password, email AND mobile phone number in their TWO.STEP Verifivation.
Just because one too many scammers managed to woo one too many 90+y/o's into bailing their long lost WW2 comrades from a nigerian jail with Amazon gift cards and Amazon doesn't know what to do about anymore,
DHL is keeping my new phone in a "highly secure" vault 200m away from my place, waiting for a letter to register some device with a camera because you need to verify your identity with an app,
all the while my former car insurance is making regress claims of about 7k€ against me for a minor car accident (no-one hurt fortunately, but was my fault).
Every rep from each of the above had the same stupid bitchass scapegoat to create high-tech supra chargers to the account deletion request:
- Amazon: We need to verify your password, whether the email was yours and whether the phone number is yours.
They call it 2-step-verification.
Guess what Amazon requests to verify you before contacting customer support since you dont have access to your number? Your passwoooooord. While youre at it, click on that button we sent you will ya? ...
I call this design pattern the "dement Tupi-Guarani"
- DHL: We need an ID to verify your identity for the request for changing the delivery address you just made. Oh you wanted to give us ANOTHER address than the one written on your ID? Too bad bro, we can't help, GDPR
- Car Insurance: We are making regress claims against you, which might throw you back to mom's basement, oh and also we compensated the injured party for something else, it doesn't matter what it is but it's definitely something, so our claims against you just raised by 1.2k. Wait you want proof we compensated something to the injured at all? Nah mate we cant do that , GDPR. But trust me, those numbers are legit, my quant forecasted the cost of childrens' christmas wishes. You have 14 days or we'll see you in court haha
I am also their customer in a pension scheme. Something special to Germany, where you save some taxes but have to pay them back once you get the fund paid out. I have sent them a letter to terminate the contract.
Funniest thing is, the whole rant is my second take. Because when I hit the post button, devrant made me verify my e-mail. The text was gone afterwards. If someone from devRant reads this, you are free to quote this in the ticket description.
Fuck losing your virginity, or filing your first tax return, or by God get your first car, living through this sad Truman dystopia without going batshit insane is what becoming a true adult is.
I am grateful for all this though:
Amazon's safety measures prevented me from spending the money I can use to conclude the insurance odyssey, and DHLs "giving a fuck about customers" prevention policies made me support local businesses. And having ranted all this here does feel healthy too. So there's that.
Oh, cherry on top. I cant check my balance, because I can only verify my login requests to my banking account wiiiiiiith...?2 -
After building some automated regression tests to verify parts of the company website were working, it was discovered that a test case was missing.
Instead of a constructive meeting about fixing the issue and adding a test, I was reamed and my manager was reamed that we "missed this case".
Nevermind that the automation caught several issues before release in nearly every other aspect of coverage.
Nevermind that the missing test case was a useless feature added after the automation was completed.
Nevermind that automation was meant to be the last stop in the gate, not the first...
I was so livid after that meeting I nearly resigned on the spot. My manager was so livid over being told to write me up he was ready to resign. -
* Developing a new "My pages" NBV offer/order solution for customer
_Thursday
Customer: Are we ready for testing?
Me: Almost, we need to receive the SSL cert and then do a full test run to see if your sales services get the orders correctly. At this point, all orders made via this flow are tagged so they will not be sent to the Sales services. We also still need to implement the tracking to see who has been exposed to what in My Pages.
Customer: Ok, great!
_Friday
Customer: My web team needs these customers to have fake offers on them, to validate the layout and content
Me: Ok, my colleague can fix this by Tuesday - he has all the other things with higher prio from you to complete first
Customer: Ok! Good!
_Sunday
Me: Good news, got the SSL cert installed and have verified the flow from my side. Now you need to verify the full flow from your side.
Customer: Ok! Great! Will do.
_Monday
*quiet*
_Tuesday
Customer: Can you see how things are going? Any good news?
Me: ???
*looks into the system*
WTF!?!
- Have you set this into production on your side? We are not finished with the implementation on our side!
Customer: Oh, sorry - well, it looked fine when we tested with the test links you sent (3 weeks ago)
Me: But did you make a complete test run, and make sure that Sales services got the order?
Customer: Oh, no they didn't receive anything - but we thought that was just because of it being a test link
Me: Seriously - you didn't read what i wrote last Thursday?
Customer: ...
Me: Ok, so what happens if something goes wrong - who get's blamed?
Customer: ...
Me: FML!!!2 -
College degree.
I don't have it. Not because I don't like to study or don't like to evolve.
I tried several times go back to college, but unfortunately I don't see myself wasting money and time inside a classroom hours per day for something I can read on a book and learn by myself in few days / hours.
I know there's some subjects it's quite hard and we need some guidance for help us, but, we have the community to ask, forums and a lot information on internet.
OK, but why I'm doing this rant?
Recently I got a good job offer in a good country but my potencial employer and me is facing issues to go trough the process because the country to give me the IT visa requires the college degree.
Sometimes I regret to not have enough cold blood to finish the damn college just becuase of the piece of paper (which doesn't proff anything and we cannot even use to clean the $_@#$"@).
My home country (which is a third world country) is already noticed that and they start doing some laws and visas to ease the hiring IT professionals and they're leaving at companies expanses and responsabilities to verify is a good professional or not, but, the price is high for that. But at least the companies there's a way now to get someone.
And also I start see a loot excelent and genius programmers and others IT professionals which are skipping the degree to see and face same issues as me.
I hope our field finally put a end to this burocracies.12 -
Before you start pulling the code down for an API and debugging why a POST to it isn't persisting in SQL, verify your JSON is well-formed... 😒
That missing squiggly brace at the top is a buzzkill.2 -
Boss: so we've got to call an app to verify data in this project. But I've got no more info and I'm on holiday next week. Please contact GuyA next week.
Me: ok I guess?
*writes email to GuyA*
GuyB: GuyA is on holiday please hold the line
*1 week later*
GuyA: we need more time it's not ready yet
*2 weeks later?
Me: so?
GuyA: yeah it's ready here's the wsdl etc your client already has the password
*1 week later*
Me: yeah so I got the data but the api says my auth isn't working
GuyB: yeah your user isn't activated on the test system. I'm gonna forward that and come back at you
*1 week later*
GuyA: so we're going live in about 2 weeks hows testing going?
Me: well I'm still waiting for the response and activation
*suddenly it works*
Me: yeah so auth is working but i can't find any data. Is there any special test data?
GuyA: oh no there is NO test data on the test system. You need to wait for GuyB but he us not here today...
Me: are you fking kidding Me?????
... no response since then and it's been days.... -
I'd love if devRant had a search for user name when writing a rant, so if I type @dfox, it'll at least verify the name before I post.9
-
My trying to login to my email account my.email.address@example.com via web:
Site: You need to verify that you are really you. We sent a verification email to my.email.address@example.com please click the link in this email to verify your identity.2 -
So this happened when I was interning. We were developing an online application for hospitals. Now as it is with any new product. We had a lot of small issues popping up related changing of text or design colors. Now this piss kissing product manage of ours who has had no prior experience of a product of the scale we were developing started posting issues in the company’s internal whatsapp group. It was fine initially when the issues were less and small. However, when the amount and intensity grew, I suggested that he be given access as a issue poster on the git repo of the code.
Now I couldn’t comprehend his level of douchiness before hand but this guy started posting issued there but only a link to a google doc with the issue described there.
Then when came the time to change the status of these issues, I asked him to verify for his satisfaction that the issue is resolved and mark it as such. So Mr. Shitmenot started to maintain a fucking google sheet to maintain the status of issues and asked us to do the same. And upon demarcation he would manually change the color of the cells representing the issue. Like what the fuck dude.
I complained about this to my mentor who also happened to be he CEO but he couldn’t care less as if it was some debt that he owed the guy.
Safe to say I left the company shortly after things started to get out of hand and more shit began to happen. Yes there was more stuff that happened!!! -
its day 4 of updating documentation and consolidating data.
The webclient has broken on average 4 times a day.
The database took 20+ seconds on updating a password entry.
I explained to my boss the real cost of interrupting my attention with these pauses. I figure it's caused my productivity to go from record high last week to being literally losing about 4 hours a day lost, plus extra time in having to go back through and verify things worked.
The technicians and developers who are working on fixing the database system are apparently quitting left right and center; their company acquired it awhile back, so they don't actually have native developers on it. Yet they still are pushing out new integration features rather than fixing anything.
Yesterday, one of the other people on the documentation project lost half a days work due to the angular updating the local cache, but it never reaching the backend. He came back from lunch, reopened his browser, and all his work was gone. (at least thats what we think happened). So we are hard resetting the program every 10 minutes or so just to make sure it is updating the backend.
The good news is that when it is done, we theoretically will be able to use this to cut back onboarding time and update times by about half, and it'll mean our new nano-server deployment project should be able to spin out with standards that can be referenced properly by everyone, not just the guy with the powershell script that he tinkered with for a particular project and never told anyone else what he did.
Theoretically. -
apple is an IT company..
"New apps and app updates will not be accepted December 23–27 (Pacific Time), so any releases should be scheduled, submitted, and approved in advance."
Ah yes, because ofcourse the servers can go home and spend the holidays with their applets.
(yes i know apple says they verify by hand, yes i know in reality they actually automate it)5 -
My phone suddenly is stuck in a reboot loop.
all solutions did not work (Safemode, Recoverymode etc)
It was time for a new phone.
well... most of my logins have now 2 factor authentication. That got me thinking:
imagine that you lost all your trusted devices in a house fire.
you cannot get in your email because of you need to verify.
you cannot buy stuff online because your phone gets a message.
and in certain cases you cannot even get in your password manager of the same reason.
I know that there are recovery codes and other solutions to this.. oh boy you are F*cked when you don't have your phone.
Everything turned out okay, Sim Card in different phone for messages. And new phone works like a charm :)12 -
Got to love when the on-call takes their sweet-fucking time with the back-up. All this because the lazy douche did not what to verify the back-up was complete.
-
Fucking java library publishing. It's a nightmare. You have to fucking own a domain to publish a shit onto jcenter/bintray/whatever. You have to own the domain, that your lib's package name is. And you MUST verify it, otherwise you won't publish anything. Or you can shit allover your lib with package name like com.github.dumbcoder.mycoollib.
You must to create a ticket for some shitheads that are going to verify your shit for two weeks. They gonna ask you for source.jar, docs.jar and whatever shit.jar they need.
What THE fuck? Who was the asshole that decided name packages in reverse domain name? No FUCKING more ecosystem has such a bullshit. In .net you just make a lib, create a free nuget account, fill some basic info and boom! you have .net package published. Same for npm and rust for example.
Because the fucking package name should be just for structure not for a some dick to own it. Namespace is name-fucking-space.
FUCK JAVA.7 -
This is how security bugs get introduced into open source. This comment came into a project I'm watching today, and I don't have the time to follow up on how bad of an idea that is:
"If you are still interested, I got it working by removing verify=True"1 -
Some context about me. Close to 3 years experience as a java developer. 1st class honours in Computer science plus oracle java 8 professional certified.
Today while discussing to a senior developer about a technical solution, he asked me a question.
Are you familiar with 'extends'?
He was talking about the keyword. I am so disturbed by it. Here I was thinking I was doing a great job. And he felt the need to verify if I knew inheritance keyword..
God knows what he and his fellow senior colleagues talk about me.. I must be looking like an absolute idiot in their eyes all this time.. -
Just found out about this: https://publiccode.eu/
If you live in the EU and care about privacy, security and/or open source you might want to check it out.
To sum it up: The idea is to have all software written for and bought by public authorities, governments and such published under open source licenses to enable every citizen to verify the integrity of that software (and give all the other advantages of FOSS).3 -
Brave Browser.
There’s a reason why brave is generally advised against on privacy subreddits, and even brave wanted it to be removed from privacytools.io to hide negativity.
Brave rewards: There’s many reasons why this is terrible for privacy, a lot dont care since it can be “disabled“ but in reality it isn’t actually disabled:
Despite explicitly opting out of telemetry, every few secs a request to: “variations.brave.com”, “laptop-updates.brave.com” which despite its name isn’t just for updates and fetches affiliates for brave rewards, with pings such as grammarly, softonic, uphold e.g. Despite again explicitly opting out of brave rewards. There’s also “static1.brave.com”
If you’re on Linux curl the static1 link. curl --head
static1.brave.com,
if you want proof of even further telemetry: it lists cloudfare and google, two unnecessary domains, but most importantly telemetry domains.
But say you were to enable it, which most brave users do since it’s the marketing scheme of the browser, it uses uphold:
“To verify your identity, we collect your name, address, phone, email, and other similar information. We may also require you to provide additional Personal Data for verification purposes, including your date of birth, taxpayer or government identification number, or a copy of your government-issued identification
Uphold uses Veriff to verify your identity by determining whether a selfie you take matches the photo in your government-issued identification. Veriff’s facial recognition technology collects information from your photos that may include biometric data, and when you provide your selfie, you will be asked to agree that Veriff may process biometric data and other data (including special categories of data) from the photos you submit and share it with Uphold. Automated processes may be used to make a verification decision.”
Oh sweet telemetry, now I can get rich, by earning a single pound every 2 months, with brave taking a 30 percent cut of all profits, all whilst selling my own data, what a deal.
In addition this request: “brave-core-ext.s3.brave.com” seems to either be some sort of shilling or suspicious behaviour since it fetches 5 extensions and installs them. For all we know this could be a backdoor.
Previously in their privacy policy they shilled for Facebook, they shared data with Facebook, and afterwards they whitelisted Facebook, Twitter, and large company trackers for money in their adblock: Source. Which is quite ironic, since the whole purpose of its adblock is to block.. tracking.
I’d consider the final grain of salt to be its crappy tor implementation imo. Who makes tor but doesn’t change the dns? source It was literally snake oil, all traffic was leaked to your isp, but you were using “tor”. They only realised after backlash as well, which shows how inexperienced some staff were. If they don’t understand something, why implement it as a feature? It causes more harm than good. In fact they still haven’t fixed the extremely unique fingerprint.
There’s many other reasons why a lot of people dislike brave that arent strictly telemetry related. It injecting its own referral links when users purchased cryptocurrency source. Brave promoting what I’d consider a scam on its sponsored backgrounds: etoro where 62% of users lose all their crypto potentially leading to bankruptcy, hence why brave is paid 200 dollars per sign up, because sweet profit. Not only that but it was accused of theft on its bat platform source, but I can’t fully verify this.
In fact there was a fork of brave (without telemetry) a while back, called braver but it was given countless lawsuits by brave, forced to rename, and eventually they gave up out of plain fear. It’s a shame really since open source was designed to encourage the community to participate, not a marketing feature.
Tl;dr: Brave‘s taken the fake privacy approach similar to a lot of other companies (e.g edge), use “privacy“ for marketing but in reality providing a hypocritical service which “blocks tracking” but instead tracks you.14 -
Just know that this is out there somewhere:
// JavaScript Document
//verify redirect
function verifySubmit(){
//get a handle on the form and check terms and conditions is selected , if not raise something
var cb = document.getElementById('termsandconditions')
if (cb.checked == true)
{
//the box is checked , redirect user to access controller
window.location = "http://192.168.101.1/goInternet.php"
}
if (cb.checked == false)
{
//the box is not checked , do not redirect user to access controller
}
}1 -
Me and new guy are working on something. We're both in different countries.
New guy just graduated a couple of months ago. Thinks he's better than us, egoistic, refuses to accept his mistake. Cannot work well in a team and arrogant. Basically a package.
I fucking spent 3 hrs trying to look for a bug in my code, which doesn't exist in the first place. Because he's a lazy fuck and refuses to even accept that he might've made a bug (evident from the fact that his first reaction was to blame me and second reaction was to verify his code)
And he doesn't have the decency to admit that he made a mistake.
What's even more sad is that I've to babysit him cuz he's incompetent.
It's fucking obnoxious.2 -
In interview tests I don't mind you testing for me to know something. However I don't care for tests that are designed to verify the lead is smarter.1
-
When you've worked on a project for a whole week, and finaly verify it against the hardware and everything works!
-
Well I can't forgot this.
In college I met a guy with whom I passed the same subjects, we had friends in common but we never spoke until after a time (8 months later) he said: "hey can you help me with my problem? I'm doing a website and I want you to verify this database... now".
I just said "ok let's see"... When I gave him my observations he said: "thank you .. I don't remember your name right now but... don't you wanna do this website with me?".
And that's how I met one of my bestfriend and coworker.6 -
I have been trying to wrap my head around authentication in hapi for the last 6 hours...
Fuck this shit... when did simple,
I HAS A USERNAME
I HAS A PASSWORD
CAN HAS SESSION?
become:
- you magically get a token from somewhere
- you magically verify that token
- you respond with { credentials } //magic
- by some fucking black magic the server probably creates a session without you knowing about it...
- you freak out and write your own authentication scheme only to find out that you cannot read payload of POST requests in the authenticate method
- you get angrier and depressed and write a rant
(to be clear: there is @hapi/basic but I don't think sending a GET request with the URL looking like username:password@domain.tld is very safe...)11 -
For those of you who are riding the crypto currency train I have a question. I'm looking to colocate a few antminer s9s and I'm unsure how to verify that the cooling will be adequate.
What is the best way to verify this?5 -
Small chaotic startup that never grew up (15 years atm).
Hosts/maintains a number of apps/sites for various customers.
At some point, someone decides that a CMS would be usefull to maintain the content across all products. Forgoing all sense, reason and the very notion of "additional maintenance and dev" it is decided that one should be built in-house.
Fast forward a number of years.
Ops performs routine maintenance on prod-servers. A java-patch accidently knocks out one of the pillars a 3rd party lib the CMS uses for storing images. CMS basically burst in to flames causing a.... significant incident.
Enter yours truly to fix the mess.
Spend a few days replacing the affected 3rd party lib. Run tests on CMS in test and staging environments. Apply java-patch. All seems fine.
When speaking to frontenders and app-devs, a significant hurdle present itself:
All test/staging instances of all websites/apps/etc ALL USE PRODUCTION CMS. Hardcoded. No way around.
There is -no- way to properly test and verify the functionality of any changes made to the home-brewed CMS.
My patch did indeed work in the end.
But did the company learn anything? Did they listen to my reasoning, pleading or even anguished screams for sanity?
No.6 -
since everybody seems to hate gradle i would like to say how much i like gradle for its possibility to build even big java projects from the commandline without the need of a a lot o scripts and especially the possibility to create a wrapper in order to use it even when its not installed on said machine.
it is the only reason why i am learning java now (i fucking loathe eclipse at the moment).
and regarding its speed. i had both. windows and linux. and for some reason i could only verify its slowliness on windows.1 -
I was discussing scope and budget with a potential client for a side project. It involved a good bit of complex postgresql and subsequent aggregations and creation of reports. He was hiring because the last guy's work was so poorly documented, they couldn't verify its accuracy.
Me: "So, what are your thoughts on a budget?"
Him: "We were thinking something like $15/hour."
Me: "Um...ok. If I can ask, where did you get that number?"
Him: "That's what we paid the last guy."
😑😑😑😑😑😑4 -
NOTE TO SELF:
Verify with your coworkers about how you plan to attack a certain feature if you’re unsure, especially since you work remotely. If not, you’ll have to fucking redo a feature three times -
The fucking worst part of my job is when I get thrown an error on a bug I'm trying to fix and it doesn't even contain an error message. For example, I'll try to verify a self signed certificate but I get an error and literally the only error thrown is [Error 0], no fucking message. If you try to track down the error in the docs they don't even fucking list errors. Times like these make me wish I could castrate people with my1
-
My boss is being a stupid cunt. To give you a background we were facing issues with our Collections system. First week December 2019, I and a colleague of mine came up with a new efficient collections architecture. My colleague and I started to Code and create automation scripts mid December and completed it in First week of Jan 2020. This PoC version was supposed to be just between the Dev team(App Dev and Back end, also one from the Ops side to verify the data). I did not receive any feedback on the actual collections system and the data integrity but during this time all they’ve done is take meetings with no real outcome. I raised this and the only email I got is data is looking fine when I know it is not.Now in First week of Feb, he is stressing us to go ahead and deploy the architecture in Production and we have not done any Code Review, Static Code analysis, any real tests on Code and deployment scripts. Have not discussed any metrics for our dashboard and alerting. I have no idea how to handle this cunt. I have even asked for resources to atleast productionalize the code and move ahead the deployment and still no out come. I’ll go in a meeting with him in an hour, I will be very blunt and tell him that whatever he is doing is a foolish way and maybe resign in couple of weeks6
-
Just had the worst exam of my life today in system development at my university. This cock sucking bitch of a sensor claimed I was wrong in various assumptions about Extreme Programming. Such as: saying XP is an incremental process and not iterative. Claiming UP is more iterative than XP and that various analogies about what iterative means compared to incremental was wrong and even disrupting me while I was talking. Mind you I've been studying these subjects closely the last week and have been reading most of The Pragmatic Programmer to verify various things she disagreed upon. Result grade? In the middle of the fucking scale. Fuck this shit. I'm just glad the grade won't appear on my final graduation papers. And yes, I'm a perfectionist when it comes to this and programming, so if I'm in the wrong please correct me.1
-
Was working on a system we planned on to deliver to a hospital
basically it was meant for controlling and monitoring pactions coming in and attendance time from the staff
Got it off the ground well and got to where the system was supposed to update room status
occupied/free then horror started
the db was not setting the room free after clearing a client off the list... room remained occupied and this kept on happening for 6 months and I was so focused on fixing the db models thinking thats where the problem was....
1 day after leaving the project for several months i just revisited the project randomly and started going through the whole code base trying to make sense of what was happening as there where no errors generated..
I had to verify the whole system logic... and that day i figured out what was happening...
upon adding a client to a room the system was also creating a duplicate room so when the function for setting the room free executes it would set the duplicate room free and not the actual room and the system would pick the room with occupied state causing the user not being able to assign new pactions to the room
Solving this brought so much relief coz it required so much work just to solve what seemed to be a minor issue5 -
I'm such a fucking idiot
I'm setting up an api and to prevent unwanted fields or circular dependencies from showing up I define what fields should appear in a few serialization yaml files.
These files define what fields should appear in a given context. The default context for every field is to always show the id, and only a call to /posts will give you all the fields of the posts for example. This means that if you retrieve a comment with a linked post, the post will only show up as an id, but the comment will have all its fields.
I've been struggling with a stupid problem for 2 hours, I could verify that the yaml files were loaded in, all entities had such a file and the configuration was exactly according to the docs.
Guess why my api calls still caused circular errors?
Because I forgot to do the $view->setContext$this->defaultContext); call that determines what context should be used for the response.
FUCK ME WHY DID IT TAKE SO FUCKING LONG TO FIGURE THAT OUT OMG
Google you say? Ofcourse I hunted google results! But I was unknowingly part of an XY problem and was looking for what the problem wasn't >:(
At least it works now, ugh1 -
I just got my third 128GB MicroSD card off Amazon, this time SanDisk. Yet again, trying to do anything not involving the OEM full-disk exFAT partition staying intact (which, fuck that, all that uses that is Windows and Linux, i'm looking for splitting this thicc bih up) shifts EVERYTHING, including MBR+PT/GPT down the disk by 16MB exactly inserting data from... the atmosphere? whatever's using it? ...do SD cards have that secure key/DRM store space thing still?
(EDIT: I do verify that they ARE genuinely the right size after purchasing before reformatting or repartitioning, by the way.)
First it was a Silicon Power card, then a Samsung card, now a SanDisk.
(Also, why all S?)
Luckily, this time it wasn't a pain in the ass to get it to read as anything but "Bad Card" or a 0-byte/empty/non-existent device in Windows/Linux (respectively) so I was able to see that it was indeed the same issue without taking 3 days to jump through device hoops to finally get it to do it again but in such a way that it shifts out and back in all zeroes.2 -
"Write the failing test first."
Oh, I know. This is probably simple, but when you're stuck on support tickets - there's no faster way than to write a test for whatever the issue is and run it.
You wind up having a quick way to verify your bug fix and you now have a test going forward to ensure the bug never happens again. -
!rant
Digging though my old emails found this joke sent to me long time ago. Think that originally was posted in a 1997 issue of Computerworld. Maybe you already suffered the effect of the "Opcodes" listed here. Hope that !tl;dr
ARG Agree to Run Garbage
BDM Branch and Destroy Memory
CMN Convert to Mayan Numerals
DDS Damage Disk and Stop
EMR Emit Microwave Radiation
ETO Emulate Toaster Oven
FSE Fake Serious Error
GSI Garble Subsequent Instructions
GQS Go Quarter Speed
HEM Hide Evidence of Malfunction
IDD Inhale Dust and Die
IKI Ignore Keyboard Input
IMU Irradiate and Mutate User
JPF Jam Paper Feed
JUM Jeer at Users Mistake
KFP Kindle Fire in Printer
LNM Launch Nuclear Missiles
MAW Make Aggravating Whine
NNI Neglect Next Instruction
OBU Overheat and Burn if Unattended
PNG Pass Noxious Gas
QWF Quit Working Forever
QVC Question Valid Command
RWD Read Wrong Device
SCE Simulate Correct Execution
SDJ Send Data to Japan
TTC Tangle Tape and Crash
UBC Use Bad Chip
VDP Violate Design Parameters
VMB Verify and Make Bad
WAF Warn After Fact
XID eXchange Instruction with Data
YII Yield to Irresistible Impulse
ZAM Zero All Memory -
==============
Getting Feedback Rant!
=============
When "this is simpler" feedback results in a function of 500 lines of code.
When I get "don't do X" in the feedback. Thank you very much. What do you want me to do instead?
Unclear feedback.
When the feedback giver changes his mind after I applied the changes!
When applying the feedback introduces a bug.
Simply opinionated feedback that is not enforced by any tool or backed up by any facts.
Please find something better to do in life.
Unactionable feedback.
"Consider X"
I will not consider thank you very much.
"Verify this works"
Duh..
When the feedback giver knows something that you don't.
I know this is a legit case.. still annoying.
"I disagree with the feature"
Go argue with the PM, not relevant to me, thanks!
=====================
GIVING FEEDBACK RANT
=====================
I rewrote the system. Please review it.
No need to review, just approve.
I will change this as part of the next ticket.
I would like to keep it the way it is.
lazy ass..
You can't test this.
It's impossible to test this.
No need to test this.
There's no point to test this.
I'll test this on production.
Not sure why this is working..
Please document this..
Because documentation is like a thing, you know.
Oh, this code is not related to this PR, I just don't want to open a new branch for such a small change. ignore it.
Ignore this.
This will be meaningful in my next change. -
Note to self:
Close off ALL ways things could go wrong..
Long story short; I released a new feature, to be able to better follow up on any stock moves, their amounts, locations and even expiry dates. An older tool just bypassed that very verification and nothing was logged or taken out of stock.
~
Taking out an amount for a certain orderline has a shortcut in place to mitigate some of the mandatory steps that pickers need to take in order to verify what's being taken. This little tool only available, visible and possible for a very few select users.
I assigned some orders to one of these people, which made him think it was an urgent batch. It's only one product, for multiple orders, so he went to the location, took out the amount needed and then used the tool to quickly be able to prepare them for shipping.
This bypassed the new methods to check if the location actually had stock to take, which I had just enabled for 1 account.
Luckily I caught the miss-hap as I was monitoring that product first-hand and noticed the batch of orders was collected but the stock amount didn't update.
It was 5min before I was leaving work, so I investigated and then ran to the person in question to ask what he did; which was "I used that tool"
I facepalmed myself internally while blaming myself, as he couldn't know that it wasn't ready to use for that purpose.
The tools to fix this up are there already.. so I used that to fix some missing stock-takes manually.. Though I'll need to close that little tool for these kind of orders for sure, asap, probably when I get home, at least until I bring over its new logic to it.
Happy Tuesday? (: -
I'm a workaholic.
My boss literally told me I've only used 1 PTO day this year and with only 2 weeks left I HAVE to take at least the rest of this week off.
Guess... I'm getting a really long weekend, took tomorrow thru Friday off, Monday and Tuesday are holiday, so only 3 days left of the year after 5 today.
Not taking the last 3 days next week because I don't trust my one co-worker to do end of month/year procedures without me there to verify they didn't fuck up anything.
Now I just have to get through that time stressing about things I'm responsible for breaking while I'm not there.5 -
So I’m in a bit of a pickle.
I’ve become involved with a pretty fast paced group project. We’ve got 9 weeks to write up a mock PDR and all of the communication is done through Discord and teleconferences. As of last week an issue came up where one of the teammates (Black) felt accused by Red of being called authoritative and feels disrespected by the following message: “I don't know if I'm picking up on it correctly, but it feels like you want to control every situation. I feel like you're trying to take on a part of everyone's role so that you also need more people a part of each sub category. I think whatever happened is done whether we did turn it in late or not, I don't think we need to pressure others to do more that is needed. Also, Project Manager's dad passed. Not to make it an excuse, but I think it should be taken into consideration. Also, we didn't even verify all the positions til the meeting we had. So even still, we would have had to turn it in late since there were so many arrangements
If you don't trust your other members to do their job without having to be supervised, it can be counterintuitive to the whole teamwork aspect.” This message was sent after we missed a deadline to submit a team organization chart and Black team member insisted on becoming a third Assistant Project manager while making it seem as the other 2 APM’s were incompetent at their job.
Although I agree that it is difficult to communicate all of your emotions through written messages, I still think that taking your tone into consideration is crucial when working remotely. Am I wrong? Is there a better way to work with this team member? It’s still very early on in the project and this is the first time I’m working on a project with others with very little face to face communication. Typically when similar issues became present in other group projects, we would all sit down and discuss it and try to reach an agreement (or at least an understanding of where everyone is come from). Any advice is seriously appreciated. 13
13 -
Overnight, our networking dept patched some systems, which unexpectedly caused a connecting system unable to work. That system was our alerting layer, which didn't/couldn't send out the alerts (phone calls, Teams messages, emails, etc) that alerting wasn't working.
This morning when networking came in, they saw the issue (our backup alerting system was sending emails all night long).
Instead of "Oh no, maybe we should have a process in place to verify patching X systems doesn't degrade Y systems", the various teams are dog-piling on alerting (my responsibility). VPs are now getting involved. They are saying things like "There should have been a monitoring system to monitor the alerting!!!". Which there is, the email back up alerting. Must be a dozens of messages in the team chat all pointing the finger that 'alerting should have worked', even though *those server clusters were all down*. My boss tried to chime in with common sense saying "If our infrastructure team can't guarantee 100% uptime on the clusters, then this will happen again. The issue happened once in the 5+ years we've been using this framework. We can spend time and money creating yet another monitoring system, which could fail too, or accept the reality that sometimes things break. We fix it and do what is reasonable so the issue doesn't happen again. In my opinion, paying for another solution isn't feasible in this situation."
Team chat is silent right now, but my spidey sense is tingling.5 -
Had to port a python code some other guy wrote using opencv for some image processing stuff to Java. I thought "how tough can it be? Let's just try it out on python first just to verify the results", only to waste an entire fucking day trying to install opencv first and make it work and to add to it the crappy opencv documentation were no help. In the end I had to just give up on this shit and decide to just do the Java implementation which I later verified from the python guy's results.
-
Someone tell me should I just give up because I'm stupid and simple shit escapes me or tell me bro calm the fuck down the guy is full of shit...
Dude says he can't verify 3rd statement in a nested IF - elseif logic because the third check for a false condition is the True condition in the first 2 statements.
So
If (mode) = manual and then
Data(g) /= Status1
Or else Data(g) = Invalid
Then
Do this thing that sounds cool
Elsif
Data(g) = Status1
And then Data(g) /= Invalid
Then
Do something else equally cool
Elsif (mode) /= manual
and then Data(g) /= Invalid
and then Data(g) /= Status1
Then
Do some less cool stuff
end if4 -
My workplace remains so retarded.
Half our colleagues are from abroad and do not speak our native language. All our customers are from our country and we are trying to implement transcription and summaries for them. The big AI models struggles with our language.
The devs who are assigned to this project do not speak our language. So they cannot verify if the results are correct.
My project manager fails to see a problem for this :D12 -
I am developing a twitter bot which will post local weather daily. After few test tweets, twitter locked the account and asked to verify account by calling. They called and I wrote down the verification code but THE FUCKING TWITTER returns a "Something went wrong." error with no actual clue about the problem.
-
About skyRant. I really like what you're doing for establishing it as a third party app with the verify login thing. Technically there is no way for me to verify if the app I'm using is using that source code unless I built it myself, but still nice.
I do feel a bit odd about having additional data such as reactions on the skyRant platform. It's cool and all, but it degrades the experience for anyone not using skyRant. If I like someone's post with a ❤️ there is no guarantee that user will see it. Idk just some random thoughts, but very cool app! :) 7
7 -
That's funny how I'm pretty sure I had interaction on devRant with people I know IRL, without the possibility to verify. I like the mystery that maybe the guy I saw commenting or ranting is someone I am familiar with.2
-
Got a problem with an AUR package. Decided to ask the AUR maintainer. Registered on the AUR page. Can't login, receiving HTTP400 bad referrer header.
Decided to report that issue. To do so, I need to register on the Arch Linux Website. Did that. To finish registration, I need to verify my account. However, the verification button just does nothing.
Removed AUR package.3 -
Just visited a website, which at the top of every page "Please paste your Google Webmaster Tools verification here"
What's odd, is this isn't a way I've seen to verify. Some kind of odd scam? 🤔2 -
Lesson learned. As a newbie to git and vcs in general, always verify a rebase to make sure you didn't accidentally delete your last days work before force pushing and overwriting the company repository. Also, don't get into a situation where you need to do that in the first place.
-
SO , i just ran into this database called ArangoDB and it claims to single handedly beat Mongo,Neo4j,Postgres and claims to be capable of handling any use case you can throw at it.
If anyone could verify this claim , such an ideal database just makes me question it's existence.5 -
Is There any good open source test automation frameworks testers can use to verify database insertions, such as message transactions? Everyday I get questions from testers to verify data and it's so tedious looking at MySQL tables to see if there data is present.4
-
Fucking ant-cumstained garbage bag. How come you are so inaccessible you satan website.
I wanted to look at someone on facebook. But for some things you need an account, so I sign up with my spam mail and a random name and the birth date that was filled in
When I try to login facebook says: your account might be compromised, what is your birth date to verify it's you.
Wtf I just made this. So I fill in the standard birth date.
WRONG BIRTH DATE YOU CAN'T TRY AGAIN FOR THE NEXT 15 MIN
Im glad I abandoned you long ago.
But apparently you know you suck since you don't allow new users? -
Oh my god devrant doesn't save rants posted by an unverified account. If you submit a rant and then verify your email, the story will just disappear into the void.7
-
Holy fuck I'm tired of domain.com... I bought my domain with them about a year ago, and quickly I discovered how shit they are.
I can almost never access the console, the default view most of the time loads, although even that is incredibly slow. When the console loads, all settings regarding my domain are just loading. Every once in a blue moon I can actually access the settings and do something.
I got tired of it, and started transferring the domain to Cloudflare. That's where I messed up, and didn't know I had to verify the transfer twice, so the domain ended up expiring during the transfer process. Now domain.com has my domain completely locked down, pointing it to one of those 'expired' nameservers.
So three days ago I thought fuck it, I'll pay domain.com to renew the domain, maybe that'll get the domain transferred, or at least get my domain open again, so I can receive emails again, because in all my nerdiness I decided to set up a custom email using 'name@customdomain.com'. So I haven't been able to receive any emails for two weeks now.
Anyway, three days later the status of the domain is still 'pending renewal', and I can't for the life of me figure out how something like this isn't completely automated, and the domain isn't just working again.
So just now I decided to contact their live chat, and even they can't change the nameservers on my domain, and I have to be transferred to a specialist, who will then contact me by mail within 24-48 hours. Fuck I hate domain.com, and I'll certainly never buy from them again4 -
My first exposure to computers was when i was 7 in 98. Hp Palvillion with windows 98. Got it from walmart and it cost around $1100. Brought it home and i hooked it up on my own on the living room floor. First program installed was "who wants to be a millionare", fitting that a game be the first thing installed since it was for homework. I lived 16 miles from town at the time so i really had no friends and the isolation made it hard for me to adjust in school to the point that i was a loud kid seeking attention. Then we got dialup and i found invisionfree forums which my first programing experiance with javascript started. And no I'm not talking about jquery I'm talking about the real thing.
Fast foward a year. I find an opensource arcade and learn php while writting an arcade from scratch that uses curl to mitm login to verify the user. Later that month i create a small project that dynamicly creates a signature image for the top 1000 posters on a coding forum i liked.
Then all hell broke loose when i found osdev.org, thought i was going to be a badass and make the ultimate operating system that would combine linux, windows, and mac where it could run anything. Reality Check hit me like a semi and train hitting at full force trying that and made me look into hacking. Spent alittle while breaking windows in so many ways and talking to others on irc until i was about to turn 18. Switched to ubuntu 12.04 my senior year while that was occuring. -
I looked at an SQL server today from a customer, talked with one of their devs and he said that he's unable to understand why the server misbehaves... All (!) queries were optimized, but they have 'big data queries'... Migraine started, I had a very bad feeling. Monitoring? Nooooppeeee. Migraine kicks in. Connected to server. SHOW GLOBAL VARIABLES...
After a bit of scrolling I found a lot of misconfigured variables (e.g. extreme large join buffers, unrealistic buffer sizes), high slow query count (nearly 60 % of COM_SELECT) and a few variables that were unknown to me.
Then came the version line.
5.0.46
Yes. 5.0.46.
Big data? Well... 30 GB of usage data.
I called the company back... The dev told me sternly that this was the production server (I had hope...) and that I lie - neither the version, nor the variables could be the problem.
A coworker had to verify it and our manager had to do the communication... Worst, most traumatic working day I ever had. -
For all the iOS Users out there, stick to 10.3.3 (Still a small window to download and verify). Cool gifts are coming out.
-
Whenever I make a loop or any block in general and then look it up just to verify and mine is overcomplicated
-
I want to slap the previous devs on my team. Not the current ones, the previous once.
I don't need a comment on every. single. line. of. code
//verify thingies
if(thingies != null && thingies.count != 0) {
Like my god, i can read the if statement to know what it's doing, goddamn.
Comments should only be used when doing something that might not be immediately obvious to the next dev looking at the code.8 -
!rant
Before I left my other company I was in the midst of finishing one project and I was ansious to finish everything to leave as a rockstar. Now, one of my js scripts brought a huge and long json response that had many nested items and arrays and whatnot. Instead of properly destructuring or finding a particular piece that went similarly to "status": "Verify input"(that was nested unser a shitload of items) i did the unspeakable......i stringified the whole object and just used indexOf.
I still feel guilty over it...but it works :P thing is, if it returns that it means that the user entered an invalid status into the app (it was an inventory application) but it works :P
Oh well. Mind you they thought it was going to take months and I finished in 1 week so yay. -
Why do all my scammers on telegram say on telegram that they're currently chatting on business account and if you can add them on private? Is it so that they can see more info about you since you have them in your contact list and see how willing / naive you are? I always play the game along and did once added it to my WhatsApp. Maybe that's the reason why I had two human phone calls by scammers now. They labeled you as "easy" and now send the heavy weight scammers to you I guess. Recently, I got a call from PayPal, automated, and they said some suspicious thing was going on at my account and that they want to verify a big purchase. I do have my card attached - so, who knows. Sounded realistic but already was sus ofc. I had to press one to talk to someone. I did, why not. So then I got some Indian or do on the line saying bought iPhone blablabla and I was like. Yeah sure.. I wanted to play the game along to find out what the scam was - but his English had such huge accent that I've just hung up the phone.
It's impossible to find out how scam works, they always notice at a certain point I'm scamming them.
But because of going far into these games, I think I'm on some easy list and that's the reason I've encounter so many. So just playing the game along isn't without consequences.
I've teached my scammer using a translator I had just now how to properly scam dutch people. Don't be that formal, that word is outdated and also, dutch people can't speak Dutch at all. So if quality of dutch has a certain level you know they want smth from you. If AI did beat us in one thing it's languages I guess. It can even speak Gen z and formal and informal6 -
!rant
I am so bored and wanted to see some cool moving charts. So I started work on a little market economy simulation with different sources, drains and recipes for a variety of resources. Traders buy stuff, produce stuff and sell stuff at prices. They look at the market, how it has evolved, offers and requests to determine the prices for which they want to buy and for which they want to sell their stuff.
Currently just basic stuff and testing manually since I haven't completed the whole market simulation tick method. And I want to verify if the Traders work as I expect. -
I'm about to submit an app to the App Store. I took some time to make sure signing in/out of different social media accounts worked properly in my app.
I've been locked out of my Facebook developer account since yesterday due to "suspicious activity" and was asked to upload a photo of myself to verify my identity. I'm not too confident my account will be unlocked as I don't use Facebook regularly and therefore never felt the need to upload a profile picture.
Fantastic.2 -
Do you trust github/gitlab/bitbucket? If you self-host, do you trust your hosting? do you trust gitea? if you don't use gitea, do you trust git? do you trust the way you got your copy of git? do you trust your os, as it might have tampered with your git? did you read the code? do you trust your internet connection that might have changed some packets? do you trust your https implementation? did you examine the traffic? do you trust your traffic sniffing tool? if you use your own hardware, do you trust it? do you trust its CPU/bios? if it's risk-v, do you trust chinese vendors of your cpu? they might have put some backdoors there. do you trust your other hardware? okay, you have the money to make your own cpus. do you trust your employees? do you trust your silicon? do you trust the measuring equipment you used to check if your cpu is safe? do you trust the literature in the field? but did you verify it though? did you?
it's always who you trust. if you want to bake an apple pie from scratch, you must first create the universe.7 -
Well, the solution works on the co-workers machine. Checked out the same branch on mine and it doesn't work. Tried restarting the computer, and now the application doesn't start at all. On top of that hassle I have to deal with creating tickets for something that in the end took three minutes to fix, just to verify a change in our test environment. That email-communication took all week.
How do you guys keep your calm? Because I'm almost bursting from this, it's so frustrating.3 -
Fuck you Scaleway! With a large rusty spiked pole!
Yesterday you locked my account due to "suspicious activity" and asked me for ID to verify me for "anti-fraud reasons". Fair enough. I comply, and you unlock my account.
Today, another person from support locks my account AGAIN, saying that I haven't yet replied and requests that I send you my ID *AGAIN*.
Either you motherfuckers have no fucking clue how to handle a fucking support ticket, or your answers are NOT FUCKING CLEAR.
Fuck you and your free credits, I'd rather spend money on a service I can actually rely upon.5 -
TLDR: I wanted to change email to new one, but I could not remember which one I have
currently. I found out an API in DevRant JS files for email verification and used
it to find it out.
So, I am moving from Gmail to Protonmail Pro, absolutely love their service.
I wanted to do same on Devrant but I could not figure out my current mail for
"I lost my password" form. My Password Manager have only login saved, and profile does
not show email address.
I thought that this user information is stored on server so it have to be some way to retrieve it. I dug
in source code and I've found:
`<div class="signup-title">Verify Your Email</div>`
Which has event assigned to function which uses jQuery.ajax (love it btw :D) to call:
`url: "/api/users/me/resend-confirm",`
This seems like worth a shot. Few copy-pastes and one ajax call later:
*Ding*
From: support@devrant.io
To: dawid@dawidgoslawski.pl
"Welcome to Devrant"
Got it :) So I have already changed in march when DevRant on previous layout.
This is what I love in this profession - problem solving. AI will not replace human
in any way, we will just stop coding array iterations and data manipulation - we will focus
on real problem solving and human touch (like design, convincing management for changes).1 -
fucking "premium subscription" is just a reboot of the "bundling" bullshit from the cable companies.
no i dont really wanna pay 4 bucks to rent a shitty halloween flick for 48 hours that i randomly got nostalgia for, nor do i want to pay an additional 8 bucks a month for your streaming service that i hardly use to begin with to include Starz or whatever.
oh a free 7 day trial will get me access you say? oh but of course you need my credit card first just to verify that im real and then conveniently charge me when i forgot i signed up and keep my money after i cancel.
too lazy to torrent. movie wasnt that great either, so not really worth the effort.7 -
I fucking hate spring boot. I can go unwind and nobody would hear this but boy, does it suck. Every single thing about it is a pita. I spend 98% of time I should have used for feature implementation in JAVA, struggling and battling MUNDANE functionality of the framework that ought to be nobrainers
Today started out with a project I inherited. I don't even know whether to blame its original author but he installed a couple of funny libraries for logging. The spring app doesn't build yet gradle build completes successfully. No errors are logged to the terminal, just reams and bundles of json. WHY IS THE APP NOT BUILDING??? You want me wrangling json through that pinhole console window?
I struggle with the yml settings, none works. Eventually get rid of the package (hint, it wasn't the slf4j one). I'm able to debug app not starting now, but now live reload doesn't work
I copy configs from a previous project where it worked into this. Nope, doesn't budge. Eventually enable an ide setting but now server restarts twice after file changes. The implication is that request argument annotation no longer works! So the server just restarts and has amnesia about argument type resolution
I've been sitting here for hours, without implementing a single new feature. Everything is a painstaking, avoidable aggravation VS the "framework". Never seen anything as horrendous. No line of java code yet. I just want to send a request, retrieve parameters and verify live reload is "up and running". You'd think something as low level as this shouldn't take more than two minutes. Alas, welcome to the incredible world of spring development5 -
I'm given a simple assignment to update email templates. I tot it would be a breeze.
It turn out SURPRISE! After the updating of template is done. I deploy the code in the development environment.
I tried to access the email template like how the user will see to verify all is good. It turn out i am facing error.
So uhh ok, i went to check the logs to see what the hiccups. It turn out that a table is missing. But this is production code. So my question how the hell did the production environment has the table but dev don't.....6 -
The script I inherited uses REGEX to verify certain table fields are properly formatted as numbers... even though the fields in question are NUMBER-type fields!! :-/
-
I have come to learn that when you script nearly everything in your job, what remains are the real pain in the ass clients.
I have told this particular client before that the issue does not lie with our equipment. I have verified while on a conference call with the other vendors that I am out of the equation. They concurred while the client was on the phone.
And yet.... Today, almost two weeks later, I have been assigned a ticket to re-verify our settings and to potentially troubleshoot !OurEquipment.
What hurts me the most is that my CEO is the best boss I have ever had, but he panders to these clients that do not listen to the diagnosis.
I am literally doing the same thing over again. I am not expecting a different outcome. I don't know why others expect a different outcome.
Because of this one example (and other similar ones), I am so tempted to leave an otherwise great company and environment. -
What a delight to have to work on macOS. Not.
Took me two days to notarize our app bundle. The ultimate issue was a dead symlink inside the bundle which would make the codesign verify (with strict option!) fail, while verification of signing operation itself passed.
Notarization would just give generic error: not properly signes. -
research 10.09.2024
I successfully wrote a model verifier for xor. So now I know it is in fact working, and the thing is doing what was previously deemed impossible, calculating xor on a single hidden layer.
Also made it generalized, so I can verify it for any type of binary function.
The next step would be to see if I can either train for combinations of logical operators (or+xor, and+not, or+not, xor+and+..., etc) or chain the verifiers.
If I can it means I can train models that perform combinations of logical operations with only one hidden layer.
Also wrote a version that can sum a binary vector every time but I still have
to write a verification table for that.
If chaining verifiers or training a model to perform compound functions of multiple operations is possible, I want to see about writing models that can do neighborhood max pooling themselves in the hidden layer, or other nontrivial operations.
Lastly I need to adapt the algorithm to work with values other than binary, so that means divorcing the clamp function from the entire system. In fact I want to turn the clamp and activation into a type of bias, so a network
that can learn to do binary operations can also automatically learn to do non-binary functions as well.10 -
Motherfucking peace of shit....
Dont know to whom I should direct this to .
Was creating a new login page for web app using Quasar(vue.js). Since my application have 2 different types of user, which also have different UI, and functionality.
One is written in vanilla ( and is quiet heavy) and the other one in vuejs ( though earlier it was written in vanilla too ). Login page too was written in vanilla which was working fine.
Now just yesterday I finished a prototype for the third type of user, which is also written in vuejs. Now I decided to re create login page using vuejs. Quiet small and easy to do. Finished it yesterday itself. Now since today's morning I am trying to configure it so that it this piece of shit just let me log in. It was authentication and verifying but not letting me log in.
( On server after authentication, I set cookies/token on clients browser and auto reload the page, so during next request to server/ or during reload, server will read the cookie/token and send the specific admin panel to user)
Prick. Dick.
It was setting cookie, but not at the '/' path. Mother fucker.
It was setting cookie to the path I was sending login credentials ( which was different from '/', I.e.- /login/verify=password )
So it was setting cookie/token at '/login/verify=password'.
Even tried setting path for cookie at server. Read everything on internet. MF nothing worked. All I came across was, 'this is CORS' .... 'this is CORS'. Assholes, if it were CORS', how then I am able to make request to server and getting response without error
Only a hour ago, when I made get request to '/login/verify=password' I figured out, cookie is being sent to server for this path only. Then did some changes at server, so to send login credentials to '/'. Now that shit is working
Fucking waste of time. Wasted more than 6 hours. Asshole.
Btw, if you can suggest a better way to login, then please. -
I was doing stuff in my room, when I slipped on my hand and landed on my knees. I look up, and I see my Raspberry Pi's GPIO pins puncturing my hand.
Fast-forward couple of hours, I decided to post a picture of it (it wasn't bleeding or anything) on Twitter. 2 seconds pass, and my account got suspended.
I have 2 simcards: one for calls, one for unlimited data.
Twitter is trying to call me to verify the account, but I have my data phone number in the profile.
FML.7 -
Hello Apple,
Fuck you, more than a month trying to open a developer account without any chance, lot of fucking emails.
Lesson 1:
If you’re from a country and put a phone number from another country you will never be able to open a developer account? How did I know that? From my experience and many other people, but Apple just says: Error, that’s it you figure it out !
Lesson 2:
If you pay using a card on which the name is different than the name in the developer account, you have to wait longer and provide more documents. How did I know that? After fucking 5 tickets and more emails asking why my account is not ready yet, then they answered they need a document to verify my identity. If you don’t do that you will just rot waiting.
Lesson 3:
If they need an ID document, you have to email them first and ask why you’re account is not available yet, if you don’t you will just rot waiting. -
Level of fuckity fuck mood.
After changing dozens of build plans in Bamboo, the build system of poo...
How to verify that nothing has gone wrong?
Poking the database, you'll be surprised that Bamboo stores the buildplan definition as XML.
Another surprise: Some of the keys / values have typos.
Yeah. You read that right. There are typos inside the XML...
Now together with Postgres, we can use XPATH and have some fun.
UNNEST(COALESCE(XPATH('/configuration/buildTasks/taskDefinition[userDescription[contains(text(),"Bleep")]]', build_definition.xml_definition_data::xml)::varchar[], ARRAY['']))
Lovely wrapping via coalesce for some null safety.
Now we get da task definitions for fields having user description text containing bleep.
Wrapping it in two REGEXP_REPLACE to strip out stupid identifiers....
REGEXP_REPLACE(REGEXP_REPLACE(...., '<id>\d+</id>', ''), '<oid>\d+</oid>', ''))
Then wrap that in MD5.
Boom. Lots of MD5 sums to help you identify if the configs are identical for a task or not.
Now wrapping that in another select to group by the MD5 and filter out the non identical ones.
I hate it how sometimes one has to seemingly do a full 2 hour dance for something as stupid as validation.
I'm pretty glad though for XML and XPATH.
Cause otherwise that would have been a whole can of worms I don't wanna think about....2 -
!rant (maybe duplicate)
Finally I was able to verify my email and start writing on devRant after a couple years or so (email confirmation was not being sent correctly because of a bug)
-end of (low quality) rant2 -
https://hackmd.io/BWLwsrB5RxeheZZ-B...
Guess the spirit of “need to verify source” in working as a developer has really done something marvel to me. Took me 2 hours just to find and document loopholes the claims a pastor made in first 7 minutes of his talk.2 -
So, Recently I had made a short film "Brazen Epiphany" and I added it to IMDB, I discovered that IMDB has a flawed verification system, they don't actually verify edits. So, I credited myself for acting in various films. And, they got approved. Then one day, a writer of one of those movies discovered this and ranted on Twitter about it
https://twitter.com/varungrover/...
I told him about this whole stuff, Then I was contacted by a journalist amd they published a story on this
https://mumbaimirror.indiatimes.com/...
I know it's pretty lame to give wrong information to a community website, but I enjoyed it5 -
The SIM card saga goes on:
To verify yourself, you need to go to some postal office and show them your ID and stuff. Not that this is complicated or anything (well actually, it is. Welcome to 2018 in Germany. We use more papers than potheads for the simplest shit), but you need to have a valid ID. Valid as in NOT EXPIRED. What the fuck. Why does my ID expire. Do I stop existing 3 years after getting it? What does it mean if it is, why is it culpable to have your ID expired. And who gets charged for having none, I mean obviously my ID doesn't identify me anymore?
What the hell man. I don't exist for 6 months now. Am I law free as not identifiable entity or how does it work?
And now the real question:
We got something called Bafög in Germany. Basically you get a bit money while studying. (I still work tho, I don't get really much from it.)
To apply for it, you need some tax number, which seemingly can be seen as a proof of my existence and my identity.
Why is this enough, why don't I need a valid ID there?
Germany is weird man. On the one hand government is all social and you get help if you need it but on the other hand you need to sacrifice 17 virigins to apply for said help..2 -
JIRA Task:
Description
As a Client, I want to have on my left-side menu link to the FAQ page.
On the page should be:
How I verify my balance?
Bla bla bla
How can I see my personal details?
Bla bla bla
How I logout?
Bla bla bla
-------
Do anyone know if this is contagious ?4 -
Anyone here uses scaleway VPS?
The tickets I raised got deleted without any proper resolution. And that is shady AF. The tickets were attended by some customer support guy and he had told he would call to verify. But that never happened.
And now all the tickets I raised has disappeared.
I can't activate my account because phone verification is not possible since the code they never arrives3 -
To Firebase, Fuck you you ass fucking holes and fuck your useless docs
All I wanted to do is to verify your stupid id token from the backend fuck server. wasted my whole fucking day on this crap.1 -
I swear I touched some weird and complex programming shit in over a decade of programming.
I interfaced myself through C# to C++ Firmware, I wrote Rfid antennas calibration and reading software with a crappy framework called OctaneSDK (seems easy until you have to know how radio signal math and ins and outs work to configure antennas for good performance), I wrote full blown, full stack enterprise web portals and applications.with most weird ass dbs since the era of JDBC, ODBC up to managed data access and entity framework, cloud documental databases and everything.
Please, please, please, PLEASE I BEG YOU, anyone, I don't even have the enough life force to pour into this, explain me why the hell Jest is still a thing in javascript testing.
I read on the site:
"Jest is a delightful JavaScript Testing Framework with a focus on simplicity."
Using jest doesn't feel any delightful and I can't see any spark of focus and simplicity in it.
I tried to configure it in an angular project and it's a clustefuck of your worst nightmares put togheter.
The amount of errors and problems and configurations I had to put up felt like setting up a clunky version of a rube goldberg's machine.
I had to uninstall karma/jasmine, creating config files floating around, configure project files and tell trough them to jest that he has to do path transformations because he can't read his own test files by itself and can't even read file dependencies and now it has a ton of errors importing dependencies.
Sure, it's focused on simplicity.
Moreover, the test are utter trash.
Hey launch this method and verify it's been launched 1 time.
Hey check if the page title is "x"
God, I hate js with passion since years, but every shit for js I put my hands on I always hope it will rehab its reputation to me, instead every fucking time it's worse than before. -
Hey i want to make a chat application for production workload with more than 100000 simultaneous connection and more than 1000000 daily active user which will scale 100 times in coming 1 to 2 years for Android. I have oauth based user authentication. This chat should be able to authenticate and verify authtoken generated using the oauth. What should i use? Xmpp, mqtt or something else. Can anyone who has worked on chat application help me.6
-
Last Saturday, I came across a fellow techie at a house party. As soon as he found out I am a developer, the question
"What is your favorite programming language?"
came bursting not even a nano-second after I told him.
Anyone else finds this super cringe?
I believe that people who dig deep trenches in such a topic will be the root cause for the next software crisis. I mean, look at Javascript. In one of my later posts, literally noone could give me a reason to not think Javascript is a dumpster fire. And yet it spread out like a malignant tumor.
To verify not all is lost, I quickly googled any databases written in JS, and luckily just found one archived repo and nothing else. Because Im calling it, once Javascript reaches the database layer, it's terminal.3 -
I got a SIM card activated for my dad yesterday. Here in SA you need to verify your identity to get the card activated. But the company's systems were offline yesterday while I got it from another distributor of theirs 2 shops over. Now a day later they tell me I have to go and get another one because the one I got won't be activated because of it being offline. Something about it being assigned to me while it is offline makes it not work.
WHAT BULLSHIT? WHO THE HELL CODES THAT TRIPE TO FAIL TWICE AS HARD AS IT SHOULD? IT MAKES NO SENSE IF THE THING IS OFFLINE FOR THIS TO HAPPEN.
And yet, with Telkom's legendary poor service I know the service people are not lying. They just don't know what the hell is going on. -
I saw a thing was already define on the front-end and just went ahead and assigned it to the necessary orgs
Few hours later our process for that thing failed on 3/4 instances. The last I already setup a couple weeks ago for testing. Turns out there's 2 things with really similar names on those instances so when I decided to not fucking check, the wanted thing was never defined so it couldn't process
Welp I'm messaging my boss tomorrow morning to see how bad this is, then unassigning the existing thing before defining the correct one
Fucking hell why did I not verify the definition. Would've taken less than 30 fucking seconds for all instances. Thankfully this is still technically in testing. But fuck I'm pissed at myself2 -
!rant
I had that installation of windows 3 to 4 years now.
I'm using a third party software for backup so everyday at 23:00 the backup service starts. The image is stored on a second HDD.
First i want to point out that i set up the windows maintenance around that time too. So any updates should occur then and i remember finding my PC at login screen couple of times meaning a restart had taken place.
Everything was fine all this time.
Couple of days ago i returned home late around 2 am to find a blue screen saying that the computer did not boot property the last time. Had two options, just restart or try to fix.
Of course i will fix it, come on.
Everything failed. Everything. Even safe mode won't boot.
Who cares i have the back up system image. Boot from the bootable usb stick and restore. Well nothing is happening. It's just freezing at 5%. Cancel. Try again. Cancel. Verify the image. Success! Try again! Nothing.
Damn. Im really tired, off to bed.
Woke up tried fixing and restore but to no avail.
Fuck it i will just install Windows fresh. I was set up after an hour or so installed the necessary drivers and such. Let's see that image of any file i want to get back.
Image is corrupted. What the fuck? How? Damn it. Mount and recovery also failed.
That's it. I did not lose any important files. I save everything on a different drive and also the backup.
But I'm wondering what had gone wrong.
My guess windows rebooted when the backup was running. If that's the case shouldn't be a check if such service is running?2 -
Team member takes names inputted and coverts them to slugs, works perfectly and functions extremely well.
Adds function to allow slug modifications but doesn't use regex or anything else to verify input is a real slug, application goes down over weekend and know one notices till this morning...
Always verify input both client and server side!!! -
My manager had someone else manage me for my whole time at the company so far. Nearly two years now. Anything I’d come to him with, he’d direct me to this other person.
Fair enough, dude’s really good and I learn a lot from him. I see why they trust him with so much. I think he’s a genius. I’ll never be that good. Embarrassed I’m only a few years his junior. Wonder why he’s okay with being a manager for employee pay. Don’t think about it much, normal corporate BS.
Well it got way more “normal” when his ass got laid off without notice. Feel terrible. Him and 70% of my branch’s full timers. Wonder how I got so lucky. Everyone’s gone. We barely have enough people to do a standup. They all had 5+ years on their belts minimum. Only the contractors are left.
Manager emergency meets with me. Tells me all his best staff are gone and I am now the only front end guy on the team. He tells me he is not confident in the fact I am responsible for all of the old guys work and he is worried. He thinks I can’t do it cause he thinks I suck. Fuck me man.
My manager is pissing himself realizing he has lost the only people keeping HIS job for him. He has no clue my skill level. He sees my PR’s take a bit longer to merge, yet doesn’t realize I asked that friend of mine who was managing me to critique my code a bit harder, mentorship if you will, so we’d often chat about how to make the code better or different ways of approaching problems from his brain, which I appreciated. He has seen non-blocking errors come through in our build pipelines, like a quota being reached for our kube cluster (some server BS idfk, all I know is I message this Chinese man on slack when I get this error and he refreshes the pods for me) which means we can only run a build 8x in one day before we are capped. Of all people, he should be aware of this error message and what is involved with fixing it but he sees it and nope, he reaches out to me (after the other guy had logged out already, of course) stating my merged code changes broke the build and reverts it before EOD. Next day, build works fine. He has the other guy review my PR and approve, goes on assuming he helped me fix my broken code.
Additionally, he’s been off the editor for so long this fool wouldn’t even pass an intro to JavaScript course if he tried. He doesn’t know what I’m doing because HE just doesn’t know what I’m doing. Fuck me twice man.
I feel awful.
The dude who got fired has been called in for pointless meetings TO REVIEW MY CODE still. Like a few a week since he was laid off. When I ask my manager to approve my proposals, or check to verify the sanity of something (lots of new stuff, considering I’m the new manager *coughs*) he tells me he will check with him and get back to me (doesn’t) or he tells me to literally email him myself, but not to make any changes until he signs off on them.
It’s crazy cause he still gets on me about the speed of stuff. Bro we got NOTHING coming from top down because we just fired the whole damn corp and you have me emailing an ex-employee to verify PATCH LEVEL CHANGES TO OUR FUCKING CODE.
GET ME OUT3 -
Anyone has any idea how to debug occasional (Severa times a day) where one of our servers decides to mount a second copy of the same NFS? It triggers our monitoring system thinking there was a change to the mounts of the system, and I was able to verify through the mounts command, that it indeed had the same NFS mount mounted twice, with exactly the same parameters.
Is there a debug interface of some sort to see what initiated that mount? Or any tool to help me track it down? I've been stuck with this mysterious issue for a while now (As it's not really a priority, it doesn't break anything, but it bugs me and I wanna know)3 -
I own my phone number over two years and still can’t sign up in Venmo, I really feel their app have problems: No different use email or phone number sign up! After I wrote a letter for them, they asked me three months of my phone number status, so number verify mean nothing on your app? Did everyone need three months status to prove phone number? !
I just feel such a popular app but the product design sucks! 1
1 -
Apparently free chocolate if you're willing to part with your address (I can't personally verify it though, someone else passed it on.)
http://mongodbadventcalendar.splashthat.com/...2 -
Whoa.. I think piratebay is under DDoS attack. I was trying to get microprocessor tutorials. Can anyone verify?
-
I was thinking that if my hearing didn't come back in my left ear (my eardrum mite b pmuch toast) i might try those bone conduction headsets but i'd need some reviews from people i can verify are people before i spend $60 on them.4
-
When you are dealing with Public Key Infrastructure (PKI) services, which of the following you would use to verify an email with a digital signature ?
A. The sender's public key
B. The sender's private key
C. Your public key
D. Your private key
E. What are you talking about ?
F. None of the above4 -
Should someone try to verify what they trust, they will find themselves on the shore of infinite, immesurable void. This void is aggressively anti-memetic: it exists, we know it exists, but it's practically unknowable.
Have you ever tried so much as compile your entire OS and all its programs from scratch? I know it's possible, I know there are people somewhere who do it, but have YOU personally tried that? Did you compile every part with multiple compilers to verify that your compiler isn't compromised? You can talk the talk, but have you walked the walk?
The food you eat every day. Did you make sure that it only contains what the label says it contains? Have you checked it with the lab? Have you then checked the lab itself? Did you check their equipment? The firmware their equipment runs? Purity of test mediums and reagents? The equipment you used to check the purity?
As I type that, I want to smack myself in the face. My brain aggresivelly rejects the idea that it needs to check everything itself. More specifically, the idea that the amount of trust it puts into other people it doesn't even know is INSANE. Here this void is -- known, but unknowable.
Do you remember the shore? It actually was _your_ shore -- you yourself is just an island floating in this void. Other people are islands too. Or bubbles, or, more specifically, entities that live within those bubbles. The bubbles made of beliefs and assumptions that form their hosts' realities.
With natural language, you build bridges to other islands/bubbles. The natural language itself is a thing that you don't really know -- you use it, yet you (and no one else for that matter) can guarantee that other person you talked to understood exactly what you was trying to say.
This black sticky void can consume us all at any moment. Yet, it chooses not to.
This void is god.4 -
WHAT THA SHIT FUCK!!!
FUCKING HEROKU
so I've got an apl running on heroku and yes its a free account
Apparently apps running on free accounts are turned off after an hour of not receiving requests
Ok that's reasonable
So I did some digging and found out there are free solutions to keep your app running
Ok thats good even on heroku there is a free add-on for that
Ok I click on add add-on
AND FUCK SHIT!!!
a huge ass red notification flashes
"//some SH
Verify your account and provide your credit card details
"
IT FUCKING SAYS {FREE}5 -
Working with a tester that scope creeps and then “fails” the tests because they did not live up to the scope that the person added just now............. Man, that grinds my gears.. And then reaches out in order to verify whether a feature could be nice to have, and when I agree, she slams it in as a scope creep on another feature and “fails” the test.. Going slightly crazy here2
-
*in class, last year of masters program in cs*
Lecturer is talking about how digital signatures are used to verify software
Some Guy: I don't get it, what are signatures? How do they work?
*first facepalm*
Lecturer proceeds to explain signing using RSA quickly.
Some other guy next to me: Wow that's cool! Had no idea that this is how it works!
My brain: We've needed this knowledge since year 2, HOW ARE YOU HERE??? -
Why the fuck do sites in 2023 still not verify email addresses are owned by the user before allowing you to register!?
Every time I get a welcome to x you have successfully registered to site y mail I get mildly frustrated and I don't like it!
And why are people using random mail addresses from unknown people to register. Just use one of these temp mail services if the site won't check that you're the owner of said address it sure as hell won't check if it is from a legitimate mail server. And if it does just use a burner mail you fool!1 -
!dev but a parable
I worked at a Walmart Photo Lab with a Fujifilm photo processor. I had a guy ask for his pictures but they weren’t printed, I could see his order but there was no “payload” ( think PO header with no PO lines). He said he ordered 600+ pictures off his SD card, then blew them away because they were ordered.
As I had no physical pictures, there was nothing I could do but say “sorry”. He was mad, but there was nothing I could do.
Moral of the story, verify backups before wiping the system. -
Woke up today with the idea that I'm gonna make a website for myself now I'm a high school student and have 0 income so i thought ight well i will just use the github student developer pack .... oh wait my school blocks it ...... ight ill get a free .me domain from name cheap..... oh its blocked too ill try porkbun and get a free .design domain shit that offers over Ight ill try . Freenom ..........................................(15min of loading later) ......ERROR: cannot verify you are human
well damn
¯\_(ツ)_/¯ Not today I guess
Can't get a fucken job cause i got school11 -
Is it just me or are graphical software verification libraries useless? I have had to take courses in several is them at uni. Usually, the diagrams end up being externally complex and more prone to errors than the software they are supposed to verify.
The fact that the "final project"of one course was to verify 100 lines of java in 2 weeks. Any beginning programmer could read the java code and confirm it was correct. The diagram my group produced could only be verified by a team of experts over the course of a year. How is it valuable to spend time "verifying"software if the verification needs even more verification than the original software.
Maybe I'm missing the point but I just don't get why there is a market for expensive propratary software in this area.1 -
Hey guys, I have almost developed the backend of an app like reddit. My question is about authentication. How should I authenticate my user. Is phone number necessary to add phone otp?Because I don't want to get any legal trouble if someone posts objectionable content on the platform. Most of the apps today need phone number, I dont know why except reducing spam accounts.
Or shall I verify email by otp. But its hard to track disposable emails. I cant go for only gmail too as its banned in china. Email domains of china are weird.
Can I get into legal trouble for objectionable content posted by any evil user?
I dont want to go for auth.10 -
Heres a good one.
How do I generate a hash that allows me to compare a re-encoded video against the original to verify they are the same so I don't end up with weird gotchas like this length = that length and this filename = that filename
since the file sizes will be completely different ?8 -
I wrote a small crate that does unsafe operations, please help me verify its soundness: https://github.com/lbfalvy/bound
(Also I think you'll like it, I'm solving a fairly abstract problem that's not possible in safe Rust)
It's essentially a struct that ties together a heap reference and a struct that's constructed from it. The main use case is to return lock guards derived from Arc<Mutex> but it's defined in a very abstract way intentionally because I'm using Marc from mappable-rc and async-std's RwLock and I didn't want this to depend on either crate.
It actually has no dependencies apart from STD (I think this one may be unavoidable) -
Approx. 24 hours ago I proceeded to use MEGA NZ to download a file It's something I've done before. I have an account with them.
This is part of the email I received from MEGA NZ following the dowload: "
zemenwambuis2015@gmail.com
YOUR MEGA ACCOUNT HAS BEEN LOCKED FOR YOUR SAFETY; WE SUSPECT THAT YOU ARE USING THE SAME PASSWORD FOR YOUR MEGA ACCOUNT AS FOR OTHER SERVICES, AND THAT AT LEAST ONE OF THESE OTHER SERVICES HAS SUFFERED A DATA BREACH.
While MEGA remains secure, many big players have suffered a data breach (e.g. yahoo.com, dropbox.com, linkedin.com, adobe.com, myspace.com, tumblr.com, last.fm, snapchat.com, ashleymadison.com - check haveibeenpwned.com/PwnedWebsites for details), exposing millions of users who have used the same password on multiple services to credential stuffers (https://en.wikipedia.org/wiki/...). Your password leaked and is now being used by bad actors to log into your accounts, including, but not limited to, your MEGA account.
To unlock your MEGA account, please follow the link below. You will be required to change your account password - please use a strong password that you have not used anywhere else. We also recommend you change the passwords you have used on other services to strong, unique passwords. Do not ever reuse a password.
Verify my email
Didn’t work? Copy the link below into your web browser:
https://mega.nz//...
To prevent this from happening in the future, use a strong and unique password. Please also make sure you do not lose your password, otherwise you will lose access to your data; MEGA strongly recommends the use of a password manager. For more info on best security practices see: https://mega.nz/security
Best regards,
— Team MEGA
Mega Limited 2020."
Who in their right mind is going to believe something like that that's worded so poorly.
Can anybody shed some light on this latest bit of MEGA's fuckery?
Thank you very much.4 -
Upgrading my tech skills.. Once again I feel my personal my personal dev environment and told are much more up-to-date than what I use at work.... Though the book Kim reading is on TDD and was written 3 years ago.
Maybe I should read another on in cloud services and ML... but don't have any motivation for these topics.
I need TDD for work because now we're emphasizing unit test coverage...
I usually only use manual functional tests to verify the final outputs as either the testing framework is broken (JS) or I don't have time to relearn the frameworks for the particular language...
Anyway got off topic... So questions after:
1. Do you ever feel your technologically always more ahead than what you do at work and essentially you bring skills to the job but you don't learn much out of it?
2. How do you test? I actually got into a bit of a argument/discussion with my colleagues about how to implement unit tests. Apparently there are 2 ways to test? Black box vs WhiteBox. She said she tests only Public methods using mock inputs, dependencies. She read online and seems there is an opinion that should only test public functions and if you can't then your app is designed incorrectly, not separated enough.
For me I test the private functions individually (WhiteBox/Java reflection) because the public one is like generateReport and as a whole is like a Pachinko machine, too many unique paths that would need a test case for.
So thoughts? Yes sorry for turning it into a remake I guess...24 -
I was able to replace Okta Verify with an open source Python script and Android app and I wrote a tutorial for it:
https://battlepenguin.com/tech/...
Unfortunately it won't work for our companies VPN which requires Okta Push. After fighting with Security for a bit, it looks like I'll have to do a Part II where I reverse engineer the Okta Verify protocol. -
Hello world!
I have a question about which the best solution to send message verify to number phone in WordPress??🤔10 -
Is is possible to still update Win7 to Win10 for free? I know they dont offer the upgrade option free like they did a couple years ago.
I've read several articles stating a Win7 key will work for Win10. Can anyone verify this still works as of recently? I want to update my main dev machine but want to make sure I dont massively screw it up.
kthx17 -
How do the mobile offers in games like "get 1000 Gems if you ... in some other app" able to verify that you actually did that?9
-
Fuck heroku
Keep refusing to verify my credit card information.
Weird field on their form , that nobody really know what they are asking for.
Billing address line 1
Billing address line 2
State/province (I have provided my country before, so I don't know what to insert here)
Please help3 -
Got an email “Welcome to Amazon Web Services” to an old GMail account I no longer use. Seems genuine with no links to shady websites or anything. Does Amazon not verify email addresses or how does that happen?
Also, the mail says I have now 12 months of free tier access, so will they start billing me instead of the random fuck who signed up with my email address?3 -
Infineon infineon infineon...
Your aurix tricore is amazing for all safet systems... On paper.
Your support is abysmal. Tried forums, support line to verify a demo that only seems to work sometimes.
I just wanted to get ethernet communication using the demo. But hey one week gone and no success....
And the code seems to behave differently for each run :| the debugger works only on global variables and no printf statements. But hey just make a lot of globals right? So little footprint available so not possible :-\
Hoped that some forum could confirm the demo so I knew I was just making a fuck up, but cannot get that verified...
Embedded programming not for me... :/ -
The more I read the more I am convinced "That one prick" is just a smart tactic to get new member to buy premium. I seriously thought about it just so I could verify that I'm not "That one prick". Genius DevRant.3
-
So I'm building an app, donations get you a serial key. Once a month I want the app to verify the key with a server.
Recommendations for this? It's written in c++, if that matters.7 -
Im trying to do onboarding to work for this client.
The job app doesnt say accounting or accountant on it.
They congratulate me and pleasantries and eventually say i have to accept nearly 4k check for “training materials”.
So i accept the check, they then say i have to buy installation and equipment including 2 safes (??) and other accounting training.
I say i did not sign up to be an accountant and i want other jobs instead.
They say i should wire the money back to their wire accounts.
So i do. Im offered two other jobs from this client and another check for even more in the mail.
They say i need to cash this check to begin training for these jobs.
I ask for a list if training materials and procedures for these jobs, and they still say cash the check even after i verify to them that i do not need / already have these materials.
Please give me insights on this because im extremely confused and frustrated with these people and i want my paycheck.1 -
Ok, I started a reply and realized that I forgot the dance of doom to verify my email address. So I copied the text and came back. Can't find my place.
AND how do you search for posts?2 -
Has the message that this shit is dumb sunk in yet ? Noone would need to verify someone is real till they go crazy if things stopped repeating
If we all reach another era your messed up children will say John was the only sane person from this generation and a few others and that is considering some actual problems being present4 -
The Costly Lesson of Cryptocurrency Scams: How I Lost $30,000 in a Fraudulent USDT Platform, In the volatile and unpredictable world of cryptocurrency, the promise of high returns can easily cloud judgment and lead to poor decisions. Unfortunately, I learned this lesson the hard way when I fell victim to a fraudulent USDT trading platform, resulting in a devastating loss of $30,000.At first glance, the platform appeared legitimate. It had a sleek, professional interface and boasted enticing marketing materials that promised effortless profits. The user testimonials, full of glowing reviews, further reinforced my confidence, convincing me I had done my due diligence. I felt assured that I was making a wise financial move when I deposited a substantial sum into the platform.But not long . Initially, everything seemed fine. I could navigate the platform easily and track my investments. However, when I tried to withdraw funds, my requests went unanswered. Customer support, which had been prompt and helpful earlier, became increasingly unresponsive. Days turned into weeks, and still, no one from the platform addressed my concerns. It was then that the reality of the situation hit me: I had been caught in a well-orchestrated scam, and my funds were effectively locked away.Panic and regret set in. I found myself staring at the screen, paralyzed with the realization that I might never see my money again. In a desperate attempt to recover what I had lost, I began researching online for potential solutions. That’s when I discovered services like Digital Web Recovery, companies that specialize in helping victims of online scams recover lost assets.Although I’m still in the process of exploring recovery options, the emotional and financial toll of this experience has been eye-opening. It taught me a hard lesson about the importance of caution in the world of cryptocurrency. Despite my best efforts to research and verify the platform, I was still deceived by its professional appearance and promises of quick gains.This has reinforced the necessity of staying skeptical and thoroughly vetting any platform before making financial commitments. Website; https: // digitalwebrecovery. com The allure of high returns can be tempting, but the consequences of poor decisions can be catastrophic. WhatsApp; +13433003465
-
**HOW CAN I RECOVER MY LOST CRYPTOCURRENCY? BITCOIN & ETHEREUM → GO TO HACKATHON TECH SOLUTIONS**
As a financial analyst, I believed I had a solid grasp of investments and risk management. However, the allure of quick returns led me to a fraudulent crypto platform that promised wealth but ultimately left me devastated. The emotional and financial fallout was overwhelming, and I felt trapped in a cycle of despair.In my search for a solution, I came across HACKATHON TECH SOLUTIONS. Initially, I was hesitant, having heard too many stories of individuals being scammed a second time while trying to recover their losses. After extensive research and reading positive testimonials, I decided to take the plunge. To afford their services, I made the difficult decision to sell my land, my last significant asset. Although it was a tough choice, I believed it would pave the way for a brighter future.The recovery process began with a series of insightful meetings. The team at HACKATHON TECH SOLUTIONS introduced me to financial strategies and recovery options that I had never considered. They took the time to understand my specific situation, providing tailored advice and clear explanations. Gradually, I began to regain hope and confidence.Every small victory—like disputing fraudulent charges or negotiating with creditors—reinforced my belief that recovery was possible. The emotional support I received was just as crucial; the anxiety and sleepless nights began to fade, replaced by a renewed sense of control over my life. HACKATHON TECH SOLUTIONS not only offered practical tools but also became a vital partner during this isolating experience.Reflecting on my journey, I realize how important it is to verify the legitimacy of recovery firms. In a world filled with scams, having a trustworthy ally can make all the difference. HACKATHON TECH SOLUTIONS proved to be that ally, guiding me through the complexities of the recovery process and helping me navigate my financial challenges.
In the end, the price of hope was significant, but every sacrifice proved to be worthwhile. My journey showed me that although the path to recovery is challenging, obtaining support is crucial. Contact HACKATHON TECH SOLUTIONS for recovery of funds. Reach out to HACKATHON TECH SOLUTIONS via below contact details
Email: info(@)hackathontechsolution(.)com
Whatsapp: +31 6 47999256
Telegram: @hackathontechsolutions -
Any gift recommendations. My birthday comes up in a few days and he asked what I wanted as a birthday gift(gifts are supposed to suprises but being able to choose is good still).
However I cannot ask for electronic gadgets. That knocks a lot of stuff of. The exception is that if something does not make me spend more time on the computer that is allowed. Kinda weird. For example I can ask for a printer or medical equipment like oximeters since that wont make me spend more time on the computer. Both of these examples were given by my father. I could ask for a new printer however we still have a printer but it is currently in the shop since it is not being used and the shops printer broke and is hell to replace since they need chips to verify toners and you need to get those chips separately from what my father told me and the shops printer should be repaired in a few months since lockdown was lifted a few days ago and I won't need to print something since everything is online and they don't need to show student projects yet.
Thia knocks a lot of hardware off since by definition if I am using hardware I still need to code it to do something which is more time on computer which is not allowed. So no fiddling with aurdino or rasberry pie or whatever is the most used hardware kit.
I can buy some course or a book to learn something but I already have problems with consistently learning c# with a good book which will lose value in November and that most topics I would like to learn like computer networking or some new language are practical which is more time on computer which is not allowed.
So the only thing I can buy are some books to enjoy reading for fun or some school books like a science digest book like Together with or the ultra popular maths reference book RD Sharma
So what things should I ask which comply with the rules my father has laid or just skip this thing1 -
Lets say i have to send an email to the user when:
- user forgot password (email sent with a token to verify the user owns that email, and token identifies for which user is this link valid)
- email verification (email sent with a token to verify the user who just registered, where this token uniquely is generated for each newly registered user)
- etc
Notice how both of these cases include the same shit:
- sending emails
- generating unique tokens
- attaching each record to individual user
Does this mean i should pack this up in 1 single model in the database and differentiate which type of email it is over an enum (EMAIL_CONFIRM, FORGOT_PASSWORD etc)?
Or should these shits each have a different model and thus different tables in database?35 -
Buy Verified Cash App Accounts
In today's fast-paced digital world, mobile payment apps have revolutionized the way we handle financial transactions. Cash App, a popular mobile payment service, has gained widespread recognition for its user-friendly interface and seamless money transfer capabilities. As the demand for Cash App accounts increases, the significance of obtaining a verified account becomes more apparent. In this article, we will explore the concept of purchasing verified Cash App accounts, understanding its benefits, potential risks, and essential tips for a secure and successful transaction.
Understanding Cash App
What is Cash App?
Cash App, also known as Square Cash, is a peer-to-peer mobile payment service that allows users to send, receive, and request money through their smartphones. With its straightforward design and hassle-free functionality, Cash App has become a preferred choice for individuals and businesses alike.
How does Cash App work?
Cash App operates by connecting to the user's bank account or debit card, facilitating seamless and instant money transfers to other Cash App users. Users can also load funds onto their Cash App balance, known as the "Cash Card," to make purchases or withdraw cash from ATMs.
Importance of Verified Cash App Accounts
Security and Safety
Having a verified Cash App account adds an extra layer of security to your financial transactions. Verified accounts undergo a thorough verification process, which helps ensure the legitimacy of the user and reduces the risk of unauthorized access.
Transaction Limits and Benefits
Verified Cash App accounts come with higher transaction limits, allowing users to send larger amounts of money. Moreover, verified users may have access to exclusive promotions and rewards offered by Cash App.
Ease of Use
With a verified account, users can seamlessly link their bank accounts or cards to the app, streamlining the process of sending and receiving money.
Risks and Concerns
Scams and Fraudulent Accounts
One of the primary concerns when considering the purchase of Cash App accounts is the presence of scams and fraudulent sellers. Dealing with unreliable sources can lead to financial losses and potential misuse of personal information.
Violation of Terms of Service
Buying or selling Cash App accounts is against the platform's terms of service. If discovered, such accounts may be subject to suspension or permanent banning, resulting in the loss of funds and access to Cash App services.
Identity Theft
Using a purchased Cash App account without changing the login credentials can expose the buyer to identity theft. It is crucial to take necessary precautions to safeguard sensitive information.
Buying Verified Cash App Accounts
Reputable Sources
When seeking to buy a Cash App account, it is essential to choose reputable and trustworthy sources. Conduct thorough research, read customer reviews, and seek recommendations from reliable sources before making a decision.
Verification Process
Before making a purchase, ensure that the seller provides a transparent explanation of their verification process. The verification process should align with Cash App's guidelines and industry best practices.
Tips for Safe Purchase
Research the Seller
Thoroughly research the background and reputation of the seller before proceeding with the purchase. Avoid dealing with sellers who have a history of negative reviews or questionable practices.
Verify Account Authenticity
After purchasing a Cash App account, verify its authenticity by logging in and reviewing the account details. If any discrepancies are found, contact the seller immediately.
Use Secure Payment Methods
Opt for secure payment methods, such as PayPal or credit cards, that offer buyer protection in case of fraudulent transactions.
Change Login Credentials
To protect against identity theft, change the login credentials (username and password) of the purchased account immediately after the transaction.
Using a Purchased Cash App Account
Linking Bank Accounts and Cards
After acquiring a Cash App account, link it to your bank accounts or debit cards to enable seamless transactions.
Investing and Trading
For users interested in investing or trading stocks through Cash App, the verified account provides a secure platform to explore investment opportunities.
Conclusion
Purchasing a verified Cash App account can offer convenience and additional benefits to users, but it comes with potential risks. It is vital to approach the purchase with caution, thoroughly research the seller, and follow safety measures to avoid scams and fraudulent activities. By taking these precautions, users can enjoy the seamless and secure experience of using Cash App for their financial transactions.
-
I know that when your code is in PR Process its a good oportunity to improve but I dont want my TL think I am useless... It was a good way to verify how he likes to work and that he is a functional approach fun but I would like to give him the image of being accountable... This is my 2nd week...
I would like to know if there is a place where you can grab imperative java code so as to practice... I wont run like crazy to transform all to functional but would like to be awared..
We are using Java Vavr library which is amazing... -
Is there a standard around checking the checksum of a bundled weapp to make sure it's the same as what the open source codebase would compile to?
I'm working on some opensource blockchain interface software and obviously blockchain passwords are pretty important, so we do all transaction signing client side and password storage client side, but there's no point doing that if the user can't verify that the password isn't being sent off to some server in secret, but the only way to ensure that is with open source software + a checksum check upon loading, because opensource software doesn't mean the deployed version is the exact opensource branch version.
Any ideas?1 -
Is their a better way than ASP Identity Claims to verify permissions before accessing a page? Refreshing claims in every page load doesn’t seem to be a great solution. Thinking about some sort of permissions middleware. I need to check those IsAdmin roles before any admin area data is accessed. What techniques are you using for authorization in your code base?3
-
Is there a debug tool in Visual Studio that acts like a global HashMap<String, object> that you can add random objects to so that you can verify which objects are the same instance between breakpoints and view the state of an object that you had access to but is not in scope at a given breakpoint? I'm debugging a GUI app right now and it's an enormous pain in the ass to track identities, I resorted to adding random properties and statics to classes just so I can express this basic ass persistent debugger state5
-
!ios
Just Happy..
Jailbroken iPhone X
!! Disclaimer !!
I‘m not the Dev of this Jailbreak nor am I an Professional these are the steps that worked for me best.
Oh and, Jailbreaking will result in losing your Warranty. Don‘t do it if you don‘t know what you are doing!
Don‘t work with the official one?
Coolstar asked ignition.fun to host their Developer Account needed one.
The Website will have Ads, but they didn‘t change one Line in the JB itself. So no ads on the Device itself.
1. Go to ignition.fun in Safari (No Computer needed)
2. Click on Electra MP
3. Download it
4. Verify the Profile
5. Turn Off Siri
6. Turn on Airplane Mode
7. Restart your iDevice
8. Check if Airplane Mode is still on
9. Open Electra App and Press the Jailbreak Button (iPhone will restart)
10. Cydia Icon will be shown (If not -> Check Step 5. and 6. and then Start from 7.)
11. Open Electra again and click „Enable Jailbreak“
12. (I think Device will respring) You can now use Cydia -
Hello people i have this problem and i think it is serious because it happens chronically. I am trying to get the word out about business services that i offer, but immediately they think its a scam. They dont know what company it is, or what it offers, or if it even exists yet, but “it sounds like a scam” … ? Is it a scam or not?
Do not do this. Always verify the source of your information to its legitimate source to know that its legitimate. Do not quickly assume that its a scam because because your pancreas gurgled. Your organs cant tell u whether something is a scam.
By just assuming, u display unprofessionalism by making an ass of yourself in front of a real agency. U also make yourself more prone to real scams who can act like what u think is legitimate. U also lose any opportunities u could have had, because u had to be an ass when it was being offered to u. Dont do that.5 -
Most satisfying was reducing the time my ci/cd did to build,test,verify complance and deploy of virtually anything i want in lrss then 10 minutes. From code to running appliance fully configured and being absolute certain it will work without any other modificatio . it used to be an hour.
Achieved this to do lots of caching and parallell test runs.
The downside is that my development server is feeling like a unvoluntary black person from ghana moving to the newfound united states 400 years ago... -
Microsoft Teams login says password is incorrect then and for a captcha
I type it again but fails...
I'm like wtf... Could it be the captcha...
Which I entered in all lowercase
It doesn't say the captcha is case sensitive though..
Next few times it gives me captchas with k... Teehee me like 5 tries to login
Are we trying to verify passwords/humanness or whether I can somehow tell the difference between K and k?1 -
this fucking website sucks, why does it literally eat all of the memory when you type a rant? fuck this fucking website fr, crashed my browser while I was trying to verify my email10
-
I am sorry, I am still confuse how to use this website !? Let me verify the email that i used to signed up and then browse this entire web first.2
-
I got my first client at upwork almost a week ago and the experience has been awful so far, not because of this client but because of the codebase, it's so bad, it is running DEBUG=True on production and if I turn it DEBUG=False things break for some fucking reason that makes no sense (I don't think that's true but the previous developer states it). The website is running on pythonanywhere which is weird, bootstrap is a nightmare, the database needs to be in sync all the time using a manage.py command that executes tasks received through a webhook from a Hubspot shit that has all the information. Just adding a simple edit/verify profile on that site is such a fucking nightmare. The whole project its full of holes and things that are just screaming to break, its like a fucking house of cards that falls to the ground the second I edit something and it looks like its my fault. I'm thinking of telling the client that I will no longer work on this project
-
Looking for iOS and Android app developers to join startup in Rutherford, NJ area. Must be able to show portfolio of apps and have some published. Must be able to pull and compare data with sensitive databases (social security number, passport, birth certificate, etc) to verify user. You will be compensated hourly. Must sign NDA.
-
VidMate Apk 2022-digiliife
VidMate Apk 2022 is 100% SAFE, with its security verify by multiple virus & malware detection engines. You can also scan every update through these platforms, and enjoy VidMate with no worry! But we use a more enhance and outstanding connectivity. VidMate Apk 2022 knows better your interests and hobbies according to your profile or historical behaviors, and then personalizes your own playlist.
-
My name is Sharron Maggie , and I’m a graduate of Stanford University. After finishing my degree, I faced immense challenges in finding a sustainable job that would allow me to pay off my student loans and live the life I desired. In my search for financial stability, I stumbled upon cryptocurrency trading, specifically Bitcoin. I invested hoping to turn my situation around, and I watched my assets soar to an impressive $500,000.
However, my journey took a dark turn when I received an email that appeared to be from my crypto exchange, prompting me to verify my account. I clicked the link and entered my information, only to realize minutes later that it was a phishing scam. In an instant, my account was drained of all its funds. Feeling desperate and devastated, I turned to a friend who had faced similar challenges, and he recommended Trust Geeks Hack Expert. Skeptical but with nothing to lose, I decided to contact them. From the first interaction, their team was incredibly responsive and professional, assuring me they had successfully handled cases like mine.
Trust Geeks Hack Expert immediately began securing my accounts and tracing the transactions. They worked with cybersecurity experts to freeze any fraudulent transfers and managed to recover a significant portion of my assets. Their expertise was impressive, and they took the time to educate me about the importance of strong, unique passwords and enabling two-factor authentication. What stood out to me was their holistic approach to the recovery process. Trust Geeks Hack Expert not only focused on retrieving my funds but also guided me in enhancing my online security to prevent future attacks. They taught me to recognize phishing scams and reinforced the need for robust security practices.
This experience was a harsh but valuable lesson in online security. It made me more vigilant about my digital presence and interactions. Thanks to Trust Geeks Hack Expert, I not only regained most of my assets but also acquired essential knowledge on protecting my investments moving forward. If you ever find yourself in a similar situation, I wholeheartedly recommend reaching out to Trust Geeks Hack Expert.
(CONTACT SERVICE )
E ma il ---> Trustgeekshackexpert [At] fast service . com
Tele gram ID ---> Trustgeekshackexpert
Web site ----> https :// trustgeekshackexpert. com/




